Submitted:
01 February 2023
Posted:
07 February 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Background and Motivation
- Sensors
- Sensor Network
- Actuators
- Communication Technologies (RFID, NFC, Z-Wave, etc.
1.1.1. Application-Based Research Areas
- Smart Economy based on Competitiveness
- Smart Governance based on Citizen participation
- Smart People based on Social and human capital
- Smart Mobility based on Transport and ICT
- Smart Environment based on Natural Resources
- Smart Living based on Quality of life
1.1.2. Trending Focus Research Areas (Alhashmi et al., 2019)
- Smart homes (smart health monitoring, smart conservation of resources (electricity, fuel, water), smart security, and safety).
- Smart Parking Lots
- Smart energy (smart metering systems, smart energy allocation, and distributed system, incorporation of traditional and renewable energy sources in the same grid).
- Energy and buildings (highly developed sustainable buildings and smart grids, enhancing the energy efficiency of sustainable housing by optimization).
1.1.3. Technological Research Areas
- Data collection (mobile devices, sensors, tags, architecture)
- Data transmission (radios, networking, topologies)
- Data storage (local storage, data warehouse)
- Data processing (data cleaning, analytics, prediction, or forecasting)
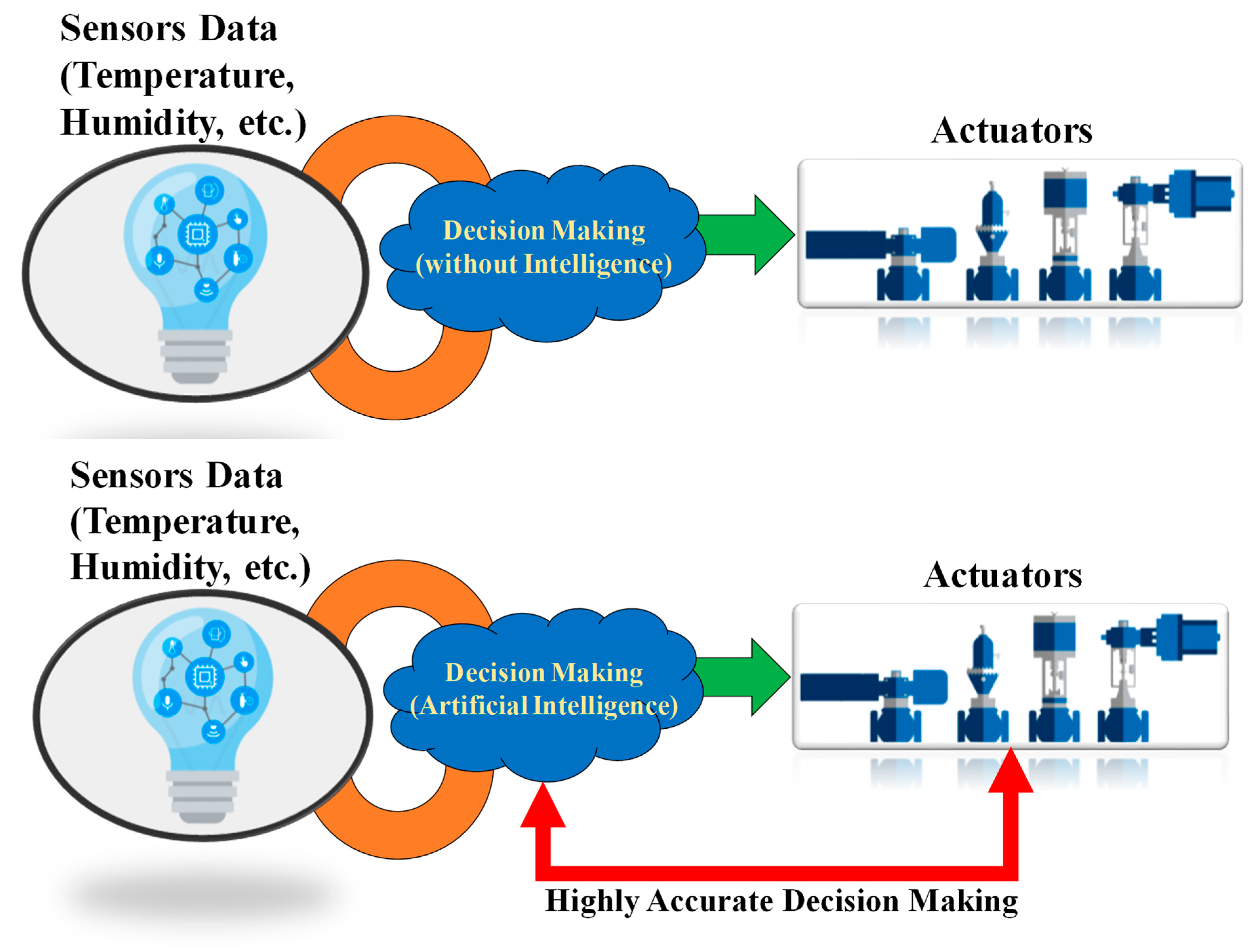
1.1.4. Mathematical Methods of Data Fusion
- Probability-Based (Bayesian analysis, statistics, recursive methods)
- Artificial Intelligence (AI) Based (Artificial Neural Network (ANN), machine learning algorithms, Convolution Neural Network (CNN), Deep Neural Network (DNN)).
- Theory of Evidence-Based (belief functions, transferable belief models)
2. Historical Developments in Smart Home
3. Smart Home and Related Research Areas
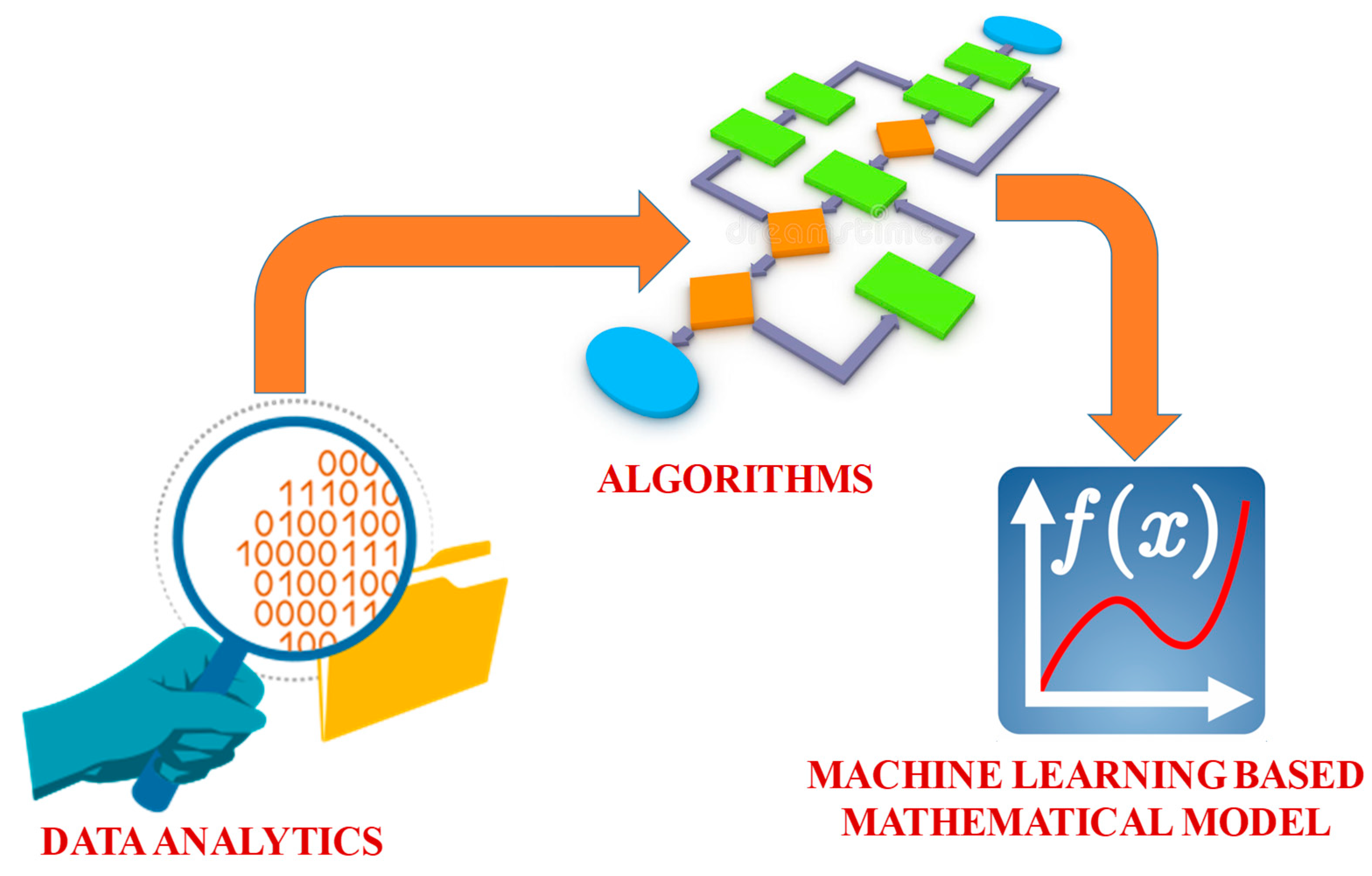
3.1. Modified Machine Learning
- Data collection
- Anomalies checklist, data missing report and data cleaning report
- Statistical performance analysis and visualize the initial screening
- Modelling of machine learning models
- Accuracy check list
- Results presentation
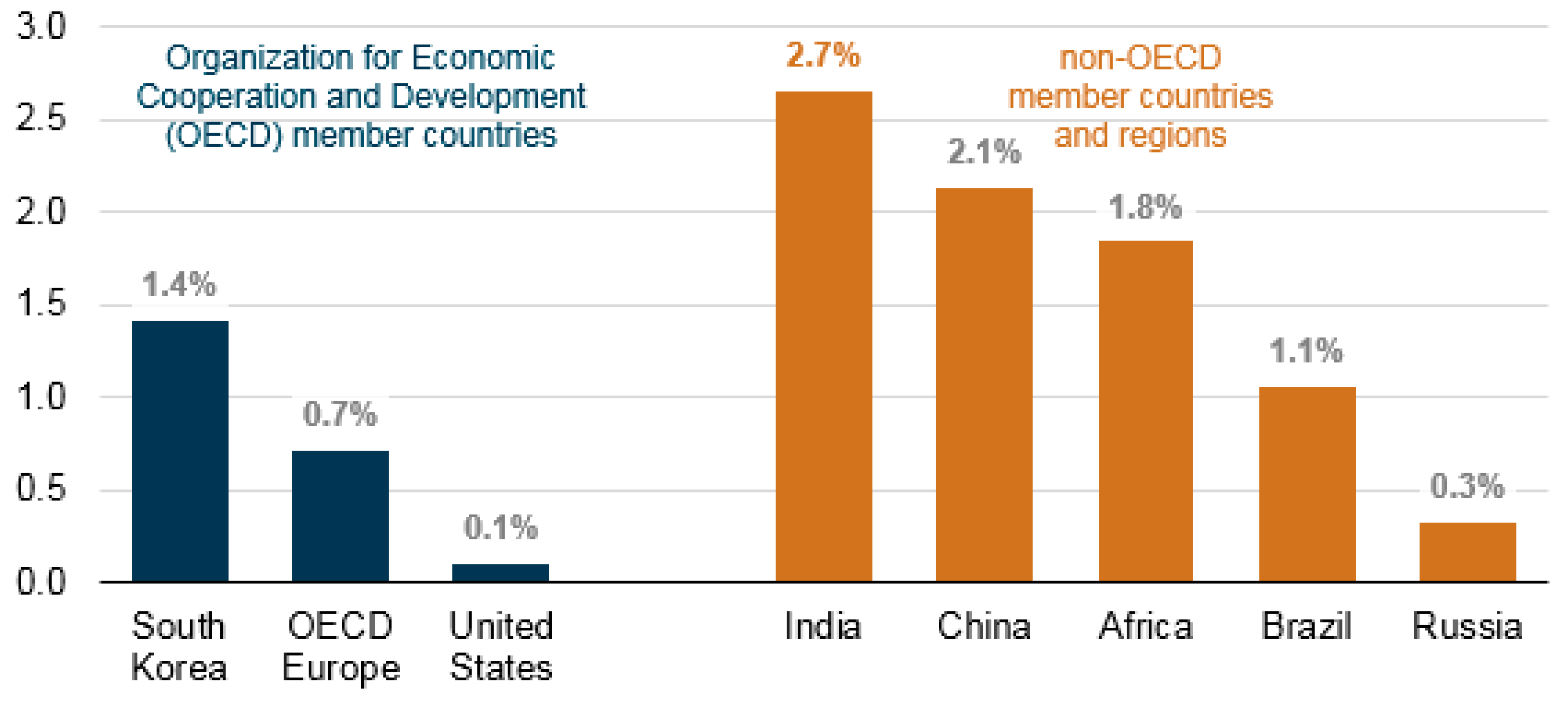
4. Energy Consumption and Human Comfort in Smart Homes
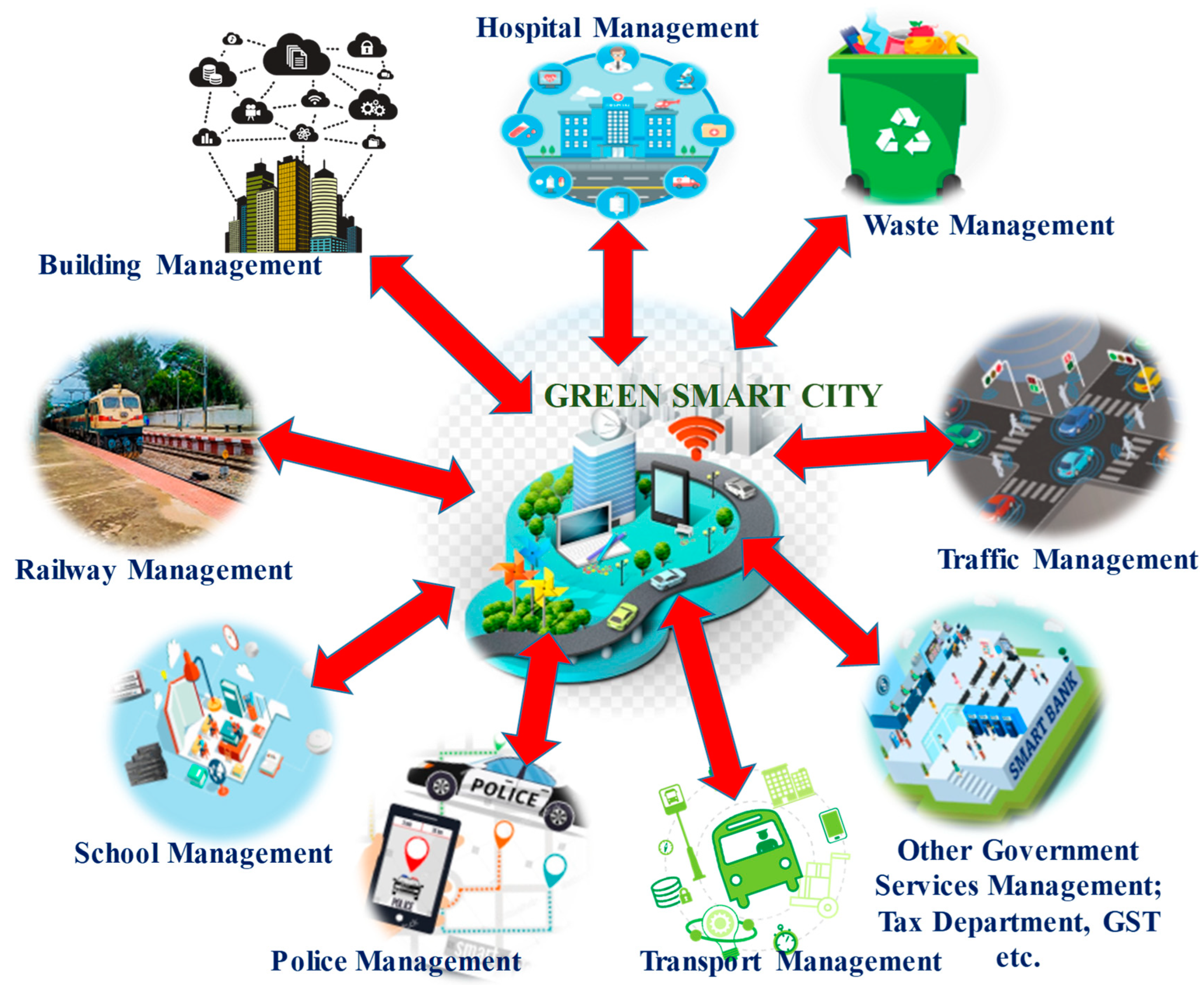
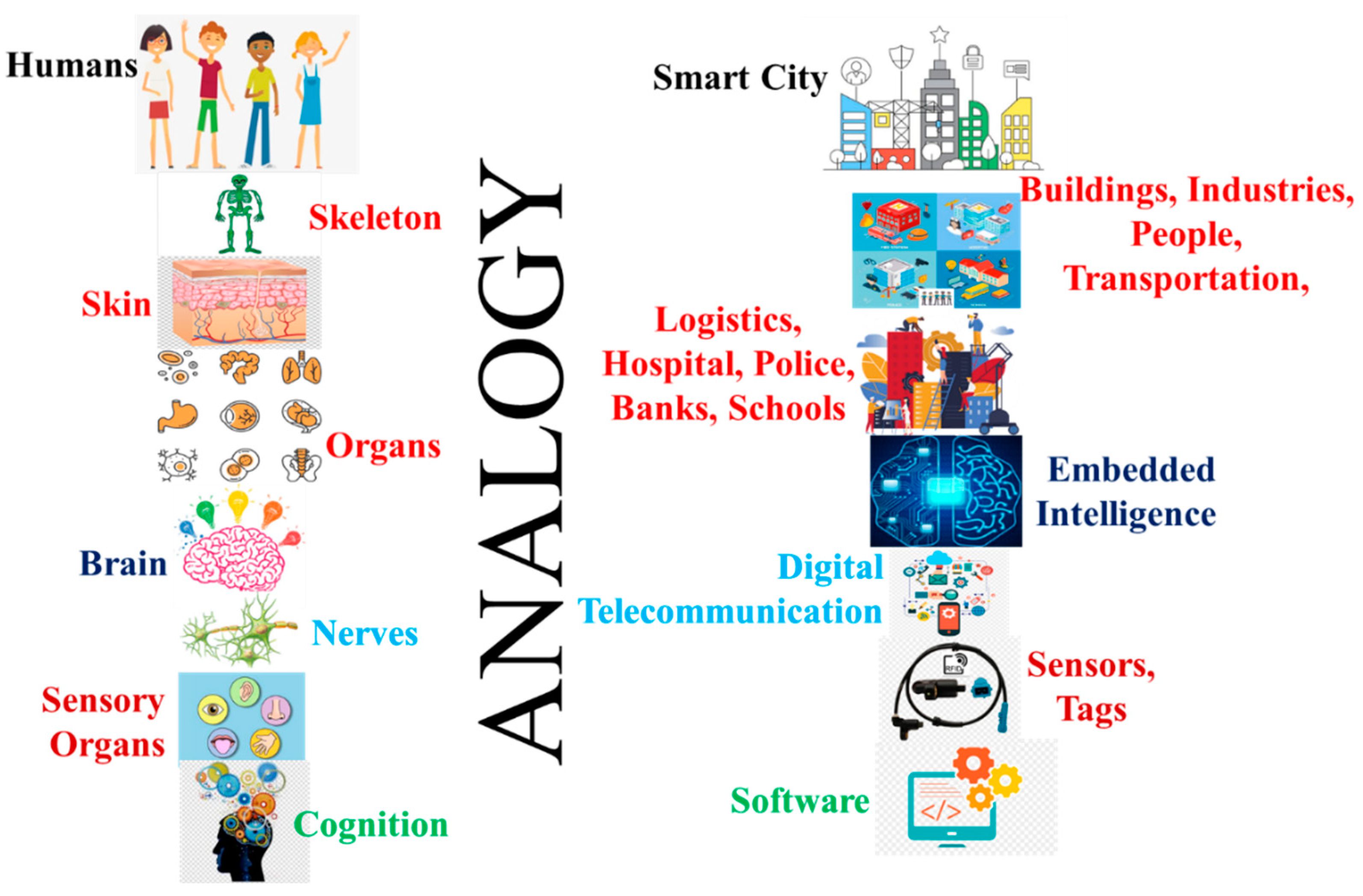
4.1. Building Management System (BMS) for Smart Cities
4.2. Future of Research in Smart Home with Machine Learning
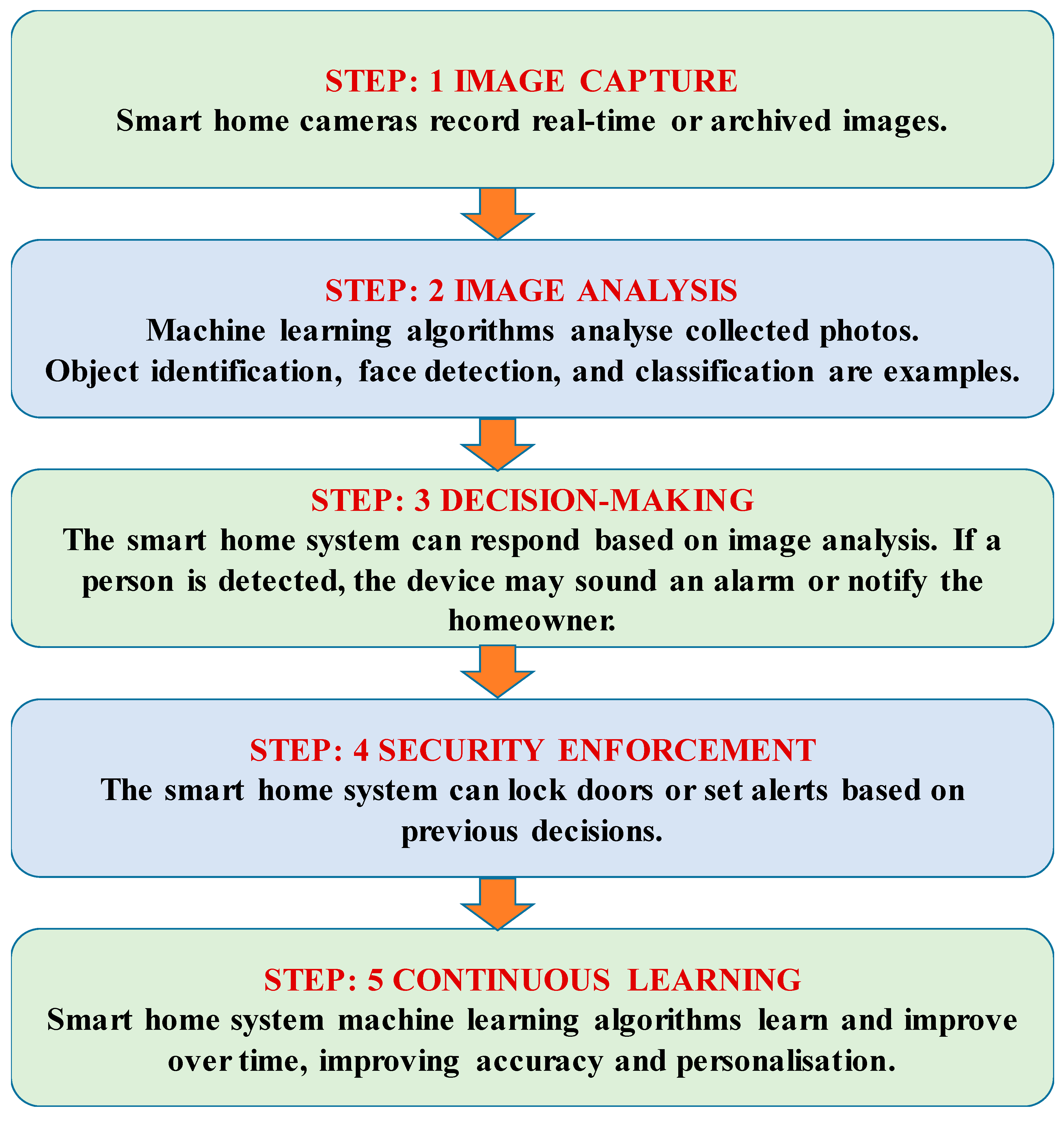
4.3. Image Protection and Security
4.3.1. Improved Security and Privacy through the Use of Various Frameworks, Models, Algorithms, and Protocols
Conclusions
Acknowledgements
Conflicts of Interest
References
- A. Rahman: M. S. Hossain, G. Muhammad et al., Federated learning-based AI approaches in smart healthcare: concepts, taxonomies, challenges and open issues. Clust. Comput. 2022. [CrossRef]
- A. Singh, A. Kumar, and A. Kumar, Network controlled distributed energy management system for smart cities. In Proceedings of the 2016 2nd International Conference on Communication Control and Intelligent Systems 2016; pp. 235–238.
- A. Srivastava, T. Badal, P. Saxena, A. Vidyarthi and R. Singh, UAV surveillance for violence detection and individual identification. Autom. Softw. Eng. 2022. [CrossRef]
- A. Verma, S. Prakash and A. Kumar, AI-based Building Management and Information System with Multi-Agent Topology for an Energy-efficient Building: Towards Occupants Comfort. ETE J. Res. 2020. [CrossRef]
- A. Verma, S. Prakash, A. Kumar, N. Aghamohammadi, “A novel design approach for indoor environmental quality based on a multiagent system for intelligent buildings in a smart city: Toward occupant's comfort. Environ. Prog. Sustain. Energy 2022, 41, e13895. [CrossRef]
- A. Verma, S. Prakash, V. Srivastava, A. Kumar and S. C. Mukhopadhyay, Sensing, Controlling, and IoT Infrastructure in Smart Building: A Review. IEEE Sens. J. 2019, 19, 9036–9046. [CrossRef]
- B. Sadasivan, M. M. Osman, Ministry of Community Development, Committee on Ageing Issues (2006). Report on the Ageing Population. Demographic Realities: Opportunities and Challenges. October 28, 2007. July 31, 2008.
- C. Patsakis, P. Laird, M. Clear, M. Bouroche, and A. Solanas, Interoperable privacy-aware E-participation within smart cities. Computer 2015, 48, 52–58. [CrossRef]
- D. Cook and, S. Das, Smart Environments: Technology Protocols and Applications. 2004.
- D. E. Rumelhart, G. E. Hinton, and R. J. Williams, Learning representations by back-propagating errors. Nature 1986, 323, 533–536. [CrossRef]
- D. Spicer, Electronic Computer for Home Operation (ECHO): The First Home Computer. IEEE Ann. Hist. Comput. 1994, 16, 59–61.
- D.-M. Han and J.-H. Lim, Design and implementation of smart home energy management systems based on zigbee. IEEE Trans. Consum. Electron. 2010, 56, 1417–1425. [CrossRef]
- Editor(s): Fereidoon, P. Sioshansi, Energy Efficiency; Academic Press, 2013; pp. 471–493.
- F. Alam, R. Mehmood, I. Katib, N. N. Albogami and A. Albeshri, Data Fusion and IoT for Smart Ubiquitous Environments: A Survey. IEEE Access 2017, 5, 9533–9554. [CrossRef]
- F. Karmali, M. Polak and A. Kostov, Environmental control by a brain-computer interface. In Proceedings of the 22nd Annual International Conference of the IEEE Engineering in Medicine and Biology Society (Cat. No.00CH37143), Chicago, IL, USA, 2000; Volume 4, pp. 2990–2992. [CrossRef]
- H. X. Zhao, F. Magoulès, A review on the prediction of building energy consumption. Renew. Sustain. Energy Rev. 2012, 16, 3586–3592. [CrossRef]
- J. K. Su, M. L. Lee, and W. C. Li, Context-aware smart home control systems. in Proceedings of the IEEE Conference on Computer Communications, 2017; pp. 1–9.
- J. Lai, Y. Mu, F. Guo, W. Susilo, and R. Chen, Fully privacy-preserving and revocable ID-based broadcast encryption for data access control in smart city. Pers. Ubiquitous Comput. 2017, 21, 855–868. [CrossRef]
- L. Li, Y. Wu, Y. Ou, Q. Li, Y. Zhou and D. Chen, Research on machine learning algorithms and feature extraction for time series. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), 2017; pp. 1–5.
- L. P. Qian, Y. J. A. Zhang, J. Huang, and Y. Wu, Demand response management via real-time electricity price control in smart grids,” IEEE J. Sel. Areas Commun. 2013, 31, 1268–1280. [CrossRef]
- L. Yao, W. H. Lim, and C. C. Lai, Self-Learning Fuzzy Controller-Based Energy Management for Smart Home. In Proceedings of the 2016 IEEE Int. Conf. Internet Things; IEEE Green Comput. Commun. IEEE Cyber, Phys. Soc. Comput. IEEE Smart Data, iThings-GreenCom-CPSCom-Smart Data 2016; pp. 87–93, 2017.
- M. Chan, E. Campo, D. Estève, J. Fourniols, Smart homes — Current features and future perspectives. Maturitas 2009, 64, 90–97. [CrossRef]
- M. Paul, S.M.E Haque and S. Chakraborty, Human detection in surveillance videos and its applications - A Review. EURASIP J. Adv. Signal Process. 2013, 176. [CrossRef]
- M. Zhang, F. Wang, H. Deng, and J. Yin, A Survey on Human Computer Interaction Technology for ATM. Int. J. Intell. Eng. Syst. 2013, 6. [CrossRef]
- N. Fumo, A review on the basics of building energy estimation. Renew. Sustain. Energy Rev. 2014, 31, 53–60. [CrossRef]
- P. Glenn, R. Daniel, W. Wall, Chapter 18 - What Comes After the Low-Hanging Fruit? ISBN 9780123978790. [CrossRef]
- P. Khaire and, P. Kumar, Deep learning and RGB-D based human action, human–human and human–object interaction recognition: A survey. J. Vis. Commun. Image Represent. 2022, 86, 103531. [CrossRef]
- P. Maurya, A. Verma, R. Gupta, Python-Based Optimization and Comparative Analysis of Temperature and PM2.5 Environmental Parameters for Energy Efficient Buildings. Int. J. All Res. Educ. Sci. Methods (IJARESM) 2022, 10, 2455–6211.
- P. O. Fanger, Thermal Comfort; Danish Technical Press. 1970 (republished by McGraw-Hill, New York); 1973.
- R. Jain, P. Jain, T. Kumar, G. Dhiman, Real time video summarizing using image semantic segmentation for CBVR. J. Real-Time Image Process. 2021, 18, 1827–1836. [CrossRef]
- R. S. Cowan, The "Industrial Revolution" in the Home: Household Technology and Social Change in the 20th Century. Technol. Cult. 1976, 17, 1–23.
- S. Gollapudi and S. Cheng, Federated machine learning for smart homes. In Proceedings of the 7th ACM Conference on Information-Centric Networking, 2020, pp. 179–187.
- S. Madakam and R. Ramaswamy, Smart Homes (Conceptual Views). In Proceedings of the 2014 2nd International Symposium on Computational and Business Intelligence, ISCBI 2014; pp. 63–66.
- S. Pellicer, G. Santa, A. L. Bleda, R. Maestre, A. J. Jara and A. G. Skarmeta, A Global Perspective of Smart Cities: A Survey. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Taichung, 2013; pp. 439–444. [CrossRef]
- T. Yamazaki, Beyond the Smart Home. In Proceedings of the 2006 International Conference on Hybrid Information Technology, Cheju Island, 2006; pp. 350–355. [CrossRef]
- U.S. Energy Information Administration, International Energy Outlook 2017 Reference case.
- V. Beltran, J. A. Martinez, and A. F. Skarmeta, User-centric access control for efficient security in smart cities. In Proceedings of the GIoTS 2017 - Global Internet of Things Summit, Proceedings, 2017.
- V. Pilloni, A. Floris, A. Meloni, and L. Atzori, “Smart Home Energy Management Including Renewable Sources: A QoE-driven Approach. IEEE Trans. Smart Grid 2016, 3053, 1.
- X. Fang, S. Misra, G. Xue and D. Yang, Smart Grid — The New and Improved Power Grid: A Survey. IEEE Commun. Surv. Tutorials 2011, 14, 944–980. [CrossRef]
- Y. Chen, J. Song, Y. Liu, and L. Liu, "A deep reinforcement learning approach for smart home energy management. In Proceedings of the 28th International Joint Conference on Artificial Intelligence, 2019; pp. 1095-1101.
- Y. Chen, Y. Wu, and C. Song, Design and Implementation of Energy Management System with Fuzzy Control for DC Micro-Grid Syst. Power Electron. IEEE Trans. 2012, 99, 1.
- Y. Li, J. Jin and C. L. Philip Chen, A real-time classification model based on joint sparse-collaborative representation. J. Real-Time Image Process. 2021, 18, 1837–184. [CrossRef]
- Y. Wang, S. Mao, and R. M. Nelms, Online Algorithm for Optimal Real-Time Energy Distribution in the Smart Grid. IEEE Trans. Emerg. Top. Comput. 2013, 1, 10–21. [CrossRef]
- Y. Xiao, Y. Jia, C. Liu, A. Alrawais, M. Rekik and Z. Shan, HomeShield: A Credential-Less Authentication Framework for Smart Home Systems. IEEE Internet Things J. 2020, 7, 7903–7918. [CrossRef]
| Timeline | Invention | Summary | Reference |
|---|---|---|---|
| 1901-1920 | Home Appliance Invention | These milestones began with the first vacuum cleaner operated by the engine in 1901. A more realistic vacuum powered by electricity was invented in 1907. For two decades, refrigerators, as well as clothes dryers, washing machines, irons, toasters, and more, might have been developed. | Cowan, 1976 |
| 1966-1967 | Echo IV: The Kitchen Computer |
ECHO IV was the first smart computer commercially marketed. This innovative system could compile shopping lists and monitor the home's temperature to put the devices on and off. | Spicer, 1994 |
| 1975 | Communication Protocol | For electrical appliances, the first communication protocol X10 was developed in 1975 to control devices. | Cook and Das, 2004 |
| 1980 | PC Interface | Since 1980, the awareness of home-operated appliances through various interfaces on a personal computer has been seen as the core of a smart home. | Karmali et al., 2000 |
| 1991-1998 | Gerontechnology | Promoting human health and well-being using assistive technology. | Sadasivan and Osman, 2006 |
| 1998-2000 | Smart Homes | Home automation started to increase in popularity in the early 2000s. Since these, various technologies have begun to evolve. Smart homes immediately became a more affordable alternative and thus a viable future technology. Home technologies, home networking, and other devices start to emerge on supermarket shelves. | Hendricks, 2014 |
| 2000-Present | Wire/Wireless Communication Protocol, ICT Tools | Latest developments in smart home feature remote mobile control, automatic lighting, controlled heating system modification, scheduling devices, mobile/email/text alert, and wireless video surveillance. Several communication protocols (LoRa, IEEE 802.11, CEBus, wireless LAN, Bluetooth, RFID) were invented in the last ten years in the 20th century. | Yamazaki, 2006; Hendricks, 2014 |
| Year | Development | Description |
|---|---|---|
| 1980s | First digital cameras | Introduction of first digital cameras enabled the capture of images for processing in smart homes. |
| 1990s | Advancements in computer vision | Significant advancements in computer vision enabled the processing of images captured by digital cameras to identify objects and perform tasks such as face recognition. |
| 2000s | Introduction of smart cameras | The introduction of smart cameras equipped with image processing capabilities allowed for real-time image analysis and recognition within smart homes. |
| 2010s | Deep learning algorithms | Advancements in deep learning algorithms, particularly Convolutional Neural Networks (CNNs), allowed for improved image classification and object recognition within smart homes. |
| 2020s | Smart cameras with AI | The integration of AI into smart cameras has enabled improved image analysis and understanding, leading to more advanced and personalized smart home systems. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





