Submitted:
22 April 2023
Posted:
23 April 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Literature
- Trust in online banking
- Perceived ease of use and perceived usefulness
- Perceived Security
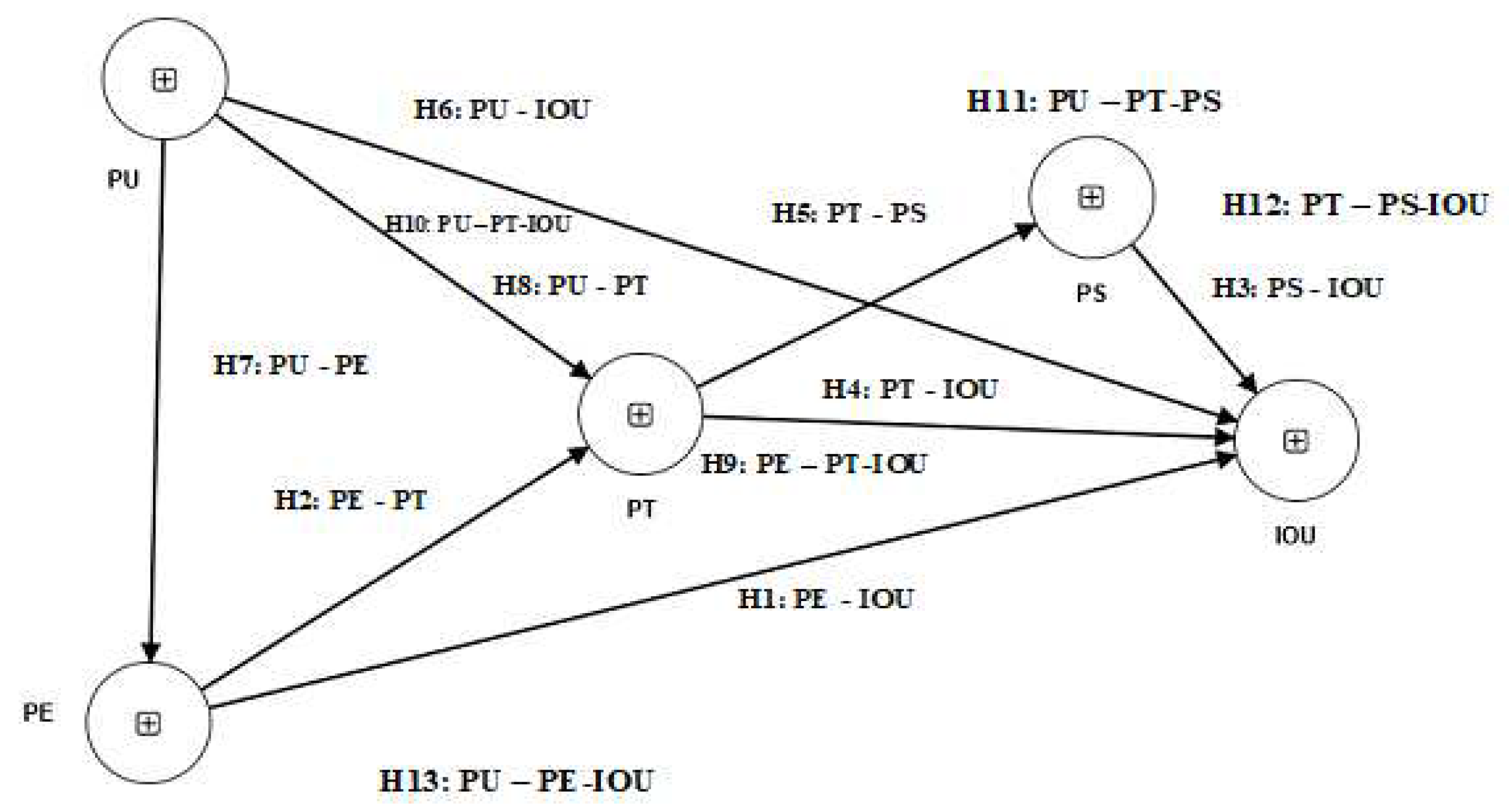
- Research Model
2.1. Methodology
| Construct | Indicators |
| Perceived Trust | (1) Digital Banking is reliable as a system of banking |
| (2) Digital banking fulfill the commitments that it assumes | |
| (3) Digital banking delivers the services promised | |
| (4) I trust digital banking | |
| Perceived Security | (1) Your operations are protected from any digital banking threats (offense; attack; theft of money, documents, information, passwords, etc.) |
| (2) My personal information is kept confidential while using digital banking | |
| (3) My sensitive information is secure while using digital banking | |
| (4) Transactions conducted through digital banking are secure. | |
| Perceived usage | (1) Digital banking saves time |
| (2) Digital banking is accessible anywhere | |
| (3) Digital banking is available at all times | |
| (4) Digital banking saves cost | |
| Perceived ease of use | (1) Digital banking is extremely convenient |
| (2) Digital banking is extremely easy | |
| (3) Learning to use digital banking is easy | |
| Intention to use | (1) I use digital banking regularly |
| (2) I recommend digital banking to others | |
| (3) I use digital banking for my banking needs |
2.2. Data Collection Process
| Profile | Particulars | Frequency |
|---|---|---|
| Age | 20-24 | 5 |
| 25-29 | 14 | |
| 30-34 | 17 | |
| 35-39 | 15 | |
| 40-44 | 12 | |
| 45-49 | 22 | |
| 50-54 | 7 | |
| 55-59 | 5 | |
| 60-64 | 1 | |
| Gender | Females | 20 |
| Males | 78 |
3. Results
3.1. Normality Test
3.2. Common Method Bias
3.3. Assessment of the Reflective Constructs
3.4. Assessment of structural model
| Path | Beta | Std Err | T stat | LLCI | ULCI | Remark | R2 | F2 | Q2predict |
| PE-IOU | 0.326 | 0.135 | 2.418*** | 0.108 | 0.551 | Supported | 0.794 | 0.110 | 0.734 |
| PE-PT | 0.230 | 0.137 | 1.681** | 0.020 | 0.466 | Supported | 0.622 | 0.038 | |
| PS-1OU | 0.174 | 0.125 | 1.391** | -0.021 | 0.386 | Supported | 0.029 | ||
| PT-IOU | 0.055 | 0.073 | 0.756 | -0.057 | 0.178 | Not supported | 0.005 | ||
| PT-PS | 0.774 | 0.062 | 12.559*** | 0.649 | 0.850 | Supported | 0.599 | 1.494 | 0.661 |
| PU-IOU | 0.389 | 0.109 | 3.552*** | 0.200 | 0.569 | Supported | 0.141 | ||
| PU-PE | 0.855 | 0.044 | 19.355*** | 0.759 | 0.907 | Supported | 0.731 | 2.716 | 0.734 |
| PU-PT | 0.583 | 0.125 | 4.664*** | 0.368 | 0.776 | Supported | 0.242 | 0.601 |
| Path | Beta | Std Err | T stat | LLCI | ULCI | Remark |
| PE-PT-IOU | 0.013 | 0.019 | 0.651 | -0.006 | 0.061 | Not Supported |
| PU-PT-IOU | 0.032 | 0.028 | 0.721 | -0.028 | 0.120 | Not Supported |
| PU-PT-PS | 0.451 | 0.103 | 4.373*** | 0.279 | 0.615 | Supported |
| PT-PS-IOU | 0.135 | 0.098 | 1.371 | -0.011 | 0.310 | Not Supported |
| PU-PE-IOU | 0.279 | 0.272 | 2.373*** | 0.095 | 0.479 | Supported |
3.5. Mediation Analysis
4. Conclusion
References
- Agitaputri, 1998. Robin Hill Sample Size. Interpersonal Computing & Technology: An electronic journal for the 21st century, Volume 6, pp. 3-4.
- Akturan, U., & Tezcan, N, 2012. Mobile banking adoption of the youth market. Marketing intelligence and Planning, 30(4), pp. 444-459. [CrossRef]
- Alderson Wroe, 1965. Dynamic Marketing Behavior. Homewood II: Richard D. Irwin.
- Andrew Burton Jones, 2009. Minimizing Method Bias Through Programmatic Research. MIS Quarterly, 33(3), pp. 449-491. [CrossRef]
- Anshuman et al., 2021. Does SMS advertising still have relevance to increase consumer purchase intention? A hybrid PLS-SEM-neural network modelling approach. Computers in Human Behavior, pp. 1-16. [CrossRef]
- Avolio, B. J. et al., 1991. Identifying Common Methods Variance With Data Collected From A Single Source: An Unresolved Sticky Issue. Journal of Management, 17(3), pp. 571-581. [CrossRef]
- Babin, J. B., & Boles, J. S, 1998. The Effects of Perceived Co-Worker Involvement and Supervisor Support onService Provider Role Stress,. Journal of Retailing, 72(1), pp. 57-75. [CrossRef]
- Bashir I and Madhavaiah C, 2015. Consumer attitude and behavioural intention towards Internet banking adoption in India. Journal of Indian Business Research, 7(1), pp. 67-102. [CrossRef]
- Bernstein, N. a., 2017. Psychometric Theory. USA : McGrawHill.
- Bhattacherjee, A., & Premkumar, G, 2004. Understanding Changes in Belief and Attitude toward Information technology usage : A theoretical model and longitudnal test. MIS Quarterly, 28(2), pp. 229-254. [CrossRef]
- Bitkina and Kim et al., 2022. Measuring user perceived characterstics for banking services : Proposing a methodology. International Journal of Environmental Research and Public Health, pp. 1-15. [CrossRef]
- Brown, S. A., Massey, A. P., Montoya-Weiss, M. M., &, 2002. Do I Really Have to? User Acceptance of Mandated Technology. European Journal of Information Systems, 11(4), pp. 283-295. [CrossRef]
- Campbell, D. T., & Fiske, D. W, 1959. Convergent and discriminant validation by the multitrait multimethod matrix. Psychological bulletin, 56(2), pp. 81-105. [CrossRef]
- Cepeda et al., 2017. Mediation analysis in PLS SEM : Guidelines and Empirical Examples. H. Latan & R. Noonan (Eds.), Partial Least Squares Path Modeling: Basic Concepts, Methodological Issues and Applications, pp. 173-195.
- Cheryl Jarvis Burke et al., 2003. A Critical Review of Construct Indicators and Measurement Model Specification in Marketing and Consumer Research. Journal of Consumer Research, 30(2), pp. 199-218. [CrossRef]
- Chou et al., 1991. Scaled test statistics and robust standard errors for Non Normal data in covariance structure. British Journal of Mathematical and Statistical Psychology, 44(2), pp. 347-357. [CrossRef]
- Claudia et al., 2014. A comparative study of CB-SEM and PLS-SEM for theory development in family firm research. Journal of Family Business Strategy, 5(1), pp. 116-128. [CrossRef]
- Cohen, J., 1988. Statistical Power Analysis for the Behavioral Sciences (2nd ed.). Hillsdale, New Jersey : Lawrence Erlbaum Associates, Publishers. [CrossRef]
- D. Straub, M. Keil, W. Brenner,, 1997. Testing the technology acceptance model across cultures: a three country study. Information and Management, 33(1), pp. 1-11. [CrossRef]
- Davis F.D., 1989. erceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly, 13(3), pp. 319-340. [CrossRef]
- Davis FD, Bagozzi, RP and Warshaw PR, 1989. User acceptance of computer technology : A comparison of two theoretical models. Management Science, 35(8), pp. 982-1003. [CrossRef]
- Davis, F.D., 1986. A Technology Acceptance Model for Empirically Testing New End-User Information Systems: Theory and Results.. Sloan, Massachusetts : Sloan School of Management, Massachusetts Institute of Technology..
- Dr Regina Connolly & Frank Bannister, 2007. Consumer Trust in Internet Shopping in Ireland: Towards the Development of a More Effective Trust Measurement Instrument. Journal of Information technology, Volume 22, pp. 102-118. [CrossRef]
- E. Karahanna, D.W. Straub, 1999. he psychological origins of perceived usefulness and ease of use,. Information and Management, 35(4), pp. 237-250. [CrossRef]
- E. Karahanna, D.W. Straub, n.d. The psychological origins of commerce, Internet Research: Electronic Networking Appli-.
- Edwards J.R. and Bagozzi R.P, 2000. On the nature and direction of relationships between cosntructs and measures. Psychological methods, Volume 52, pp. 155-74. [CrossRef]
- Efron, B, 1987. Better bootstrap confidence intervals. Journal of the American Statistical Association, 82(397), pp. 171-185. [CrossRef]
- Ennew C and Sekhon H, 2007. Measuring trust in financial services : the trust index. Consumer Policy Review, Volume 17, pp. 62-8.
- F.D. Davis, 1989. Perceived usefulness, perceived ease of use and user acceptance of information technology. MIS Quarterly, 13(3), pp. 319-340. [CrossRef]
- Faul F et al., 2009. Statistical power analysis using G* Power 3.1 : Tests for correlation and regression analysis. Behavior Research Methods, 41(4), pp. 418-432. [CrossRef]
- Field A, 2009. Discovering statistics using SPSS. London : SAGE. [CrossRef]
- Fishbein, M., & Ajzen, I, 2010. Predicting and changing behavior: The reasoned action approach.. New York : Psychology Press.
- Fishbein, M. &. A. I., 1975. Belief, attitude, intention and behavior: An introduction to theory and research. Reading : MA Addison Wesley.
- Fornell, C. G., & Larcker, D. F., 1981. Evaluating structural equation model with unobservable variables and measurement error. Journal of Marketing Resaerch, 18(1), pp. 39-50. [CrossRef]
- Fornell, C., & Larcker, D. F., 1981. Structural Equation Models with Unobservable Variables and Measurement Error: Algebra and Statistics.. Journal of Marketing Research, Volume 18, pp. 382-388. [CrossRef]
- Gao, L.; Waechter, K.A.; Bai, X, 2015. Understanding consumers’ continuance intention towards mobile purchase: A theoretical farmework and empirical study. Computer Human Behaviour, Volume 53, pp. 249-262. [CrossRef]
- Gay, L. R., & Diehl, P. L, 1992. Research Methods for Business and Management. In Hill, R. (1998) (Ed.), What Sample Size Is “Enough’ in Internet Survey Research”? Interpersonal Computing and Technology:. An Electronic Journal for the 21st Century..
- Geisser, S., 1974. A Predictive Approach to the Random Effect Model. Biometrika, Volume 64, pp. 101-107. [CrossRef]
- George D. & Mallery M, 2010. SPSS for Windows Step by Step : A Simple Guide and Reference. Boston : Pearson.
- Hair et al., 2010. Multivariate data analysis. New Jersey : Prentice hall.
- Hair et al., 2017. A Primer on Partial Least Squares Structural Equation Modelling (PLS SEM), Chapter 7. Thousands Oaks, CA : Sage.
- Hair et al., 2019. When to use and how to report the results of PLS-SEM. European Business Review, pp. 1-24. [CrossRef]
- Hair et al., 2011. PLS SEM : Indeed a silver bullet. The Journal of Marketing Theory and Practice, 19 (2), pp. 139-151. [CrossRef]
- Hair et al., 2014. A primer on partial least squares structural equation modeling (PLS-SEM). Thousands Oaks : Sage publication.
- Hair et al., 2017. A Primer on Partial Least Squares Structural Equation Modelling (PLS SEM). Thousand Oaks California: Sage Publisher.
- Hair, J.F. et al., 2012b. An assessment of the use of partial least squares structural equation modeling in marketing research. Journal of the Academy of Marketing Science, Volume 40, pp. 414-433. [CrossRef]
- Hair, J.F., Hult, G.T.M., Ringle, C.M. and Sarstedt, M., 2017. A Primer on Partial Least Squares Structural Equation Modeling (PLS-SEM).. Thousand Oaks, CA : Sage Publications Inc.
- Henseler, J et al., 2015. A new criterion for assessing discriminant validity in variance-based structural equation modeling. Journal of the Academy of Marketing Science,, 43 (1), pp. 115-135. [CrossRef]
- Herman Wold, 1980. Model construction and evaluation when theoretical knowledge is scarce. In J. Kmenta and J. B. Ramsey. Evaluation of econometric models, pp. 47-74.
- Hsiu-FenLin, 2011. An empirical investigation of mobile banking adoption: The effect of innovation attributes and knowledge-based trust. International Journal of Information Management, 31(3), pp. 252-260. [CrossRef]
- Hulland et al., 2018. Marketing survey research best practices: Evidence and recommendations from a review of JAMS article. Journal of the Academy of Marketing Sciences, 46(1), pp. 92-108. [CrossRef]
- James C. Anderson and James A. Narus, 1990. A Model of Distributor Firm and Manufacturer Firm Working Partnerships. Journal of Marketing, 54(1), pp. 42-58. [CrossRef]
- Jarvenpaa et al, 2000. Consumer trust in internet store. Information Technology and Management, Volume 1, pp. 45-71. [CrossRef]
- John Hulland et al., 2018. Marketing Survey research best practices : Evidence and recommendations from a review of JAMS article. Journal of the Academy Marketing Sciences, Volume 46, pp. 92-108. [CrossRef]
- Jose Benitez et al., 2010. How to perform and report an impactful analysis using partial least squares: Guidelines for confirmatory and explanatory IS Model. Information and Management, pp. 1-16. [CrossRef]
- Joseph et al., 2019. When to use and how to report the results of PLS-SEM. European Business Review, pp. 1-24. [CrossRef]
- Joseph F. Hair et al., 2019. When to use and how to report the results of PLS SEM. European Business Review, 31(1), pp. 1-24. [CrossRef]
- K.A. Bollen, R. Stine, 1990. Direct and indirect effects: classical and bootstrap estimates of variability. Sociological Methodology, 20(1), pp. 115-140. [CrossRef]
- K.J. Preacher and A.F. Hayes, 2008. Asymptotic and resampling strategies for assessing and comparing indirect effects in multiple mediator models. Behavior Research Methods, 40(3), pp. 879-891. [CrossRef]
- Kaur A and Malik G, 2019. Examining factors influencing Indian customers intentions and adoption of internet banking: Extending TAM with electronic service quality. Innovative Marketing, 15(2), pp. 42-57. [CrossRef]
- Kenny, B. R. a. D., 1986. The Moderator - Mediator Variable Distinction in Social Pyschological Research : Conceptual, Strategic, and Statistical Considerations. Journal of Personality and Social Psychology, 51 (6), pp. 1173-1182. [CrossRef]
- Khalilzadeh, J et al., 2017. Security-related factors in extended UTAUT model for NFC based mobile payment in the restaurant industry. Computer Human Behavior, Volume 70, pp. 460 -474. [CrossRef]
- Komiak et al., 2004. Understanding consumer trust in agent mediated electronic commerce. Web mediated Electronic Commerce and Traditional Commerce, 5(1-2), pp. 181-207. [CrossRef]
- Lee and Turban, 2001. A Trust Model for Consumer Internet Shopping. International Journal of Electronic Commerce, 6(1), pp. 75-91. [CrossRef]
- Lewis A Friedland, 2001. Communication, Community, and Democracy: Toward a Theory of the Communicatively Integrated Community. Communication Research, pp. 358-391. [CrossRef]
- Liao Cheung et al., 2002. Internet-based e-banking and consumer attitudes: an empirical study. Information and Management, 39(4), pp. 283-295. [CrossRef]
- Loonam, Mary, and Deirdre O’Loughlin, 2008. Exploring E-service Quality: A Study of Irish Online Banking.. Marketing Intelligence & Planning, pp. 759-80. [CrossRef]
- Mardia K.V., 1970. Measures of multivariate skewness and kurtosis with applications. Biometrika, pp. 519-530. [CrossRef]
- Mayer et al., 1995. An Integrative Model of Organizational Trust. The Academy of Management Review, 20(3), pp. 709-734. [CrossRef]
- McKnight et al., 1998. Initial trust formation in new organizational relationships. The Academy of Management Review, 23(3), pp. 473-90. [CrossRef]
- Mcknight, D. & Chervany, Norman, 2001. Trust and Distrust definition : One bite at time. Trust in Cyber Societies, Volume 2246, pp. 27-54. [CrossRef]
- Melody A Hertzog, 2008. Considerations in determining sample size for pilot studies. Research in Nursing & Health, Volume 31, pp. 180-191. [CrossRef]
- Memon et al., 2018. Mediation Analysis : Issues and recommendation. Journal of Applied Structural Equation Modeling, 2 (1), pp. i - ix. [CrossRef]
- Ned Kock, 2015. Common method bias in PLS-SEM: A full collinearity assessment approach. International Journal of e collaboration, 11(4), pp. 1-10. [CrossRef]
- Nitzl et al., 2016. Mediation analysis in partial least squares path modeling: Helping researchers discuss more sophisticated models. Industrial Management Data Systems, pp. 1849-1864. [CrossRef]
- Nitzl et al, 2016. Mediation Analyses in Partial Least Squares Structural Equation Modeling : Helping Researchers discuss more sophisticated model. Industrial Management and Data Systems, 119 (9), pp. 1849-1864. [CrossRef]
- Nitzl, C, Roldan, J.L. and Cepeda, 2016. Mediation analysis in partial least squares path modeling: Helping researchers discuss more sophisticated models. Industrial management & data systems, 116(9), pp. 1849-1864. [CrossRef]
- P. Ratnasingham, 1998. The importance of trust in electronic commerce. Internet Research : Electronic Networking Applications and Policy, 8(4), pp. 313-321. [CrossRef]
- P.E. Shrout, N. Bolger, 2002. Mediation in experimental and nonexperimental studies: new procedures and recommendations. Psychological Methods, 7(4), pp. 422-445. [CrossRef]
- Philip M Podsakoff et al, 2012. Sources of method bias in social science research and recommendations on how to control it. Annual review of psychology, Volume 63, pp. 539-569. [CrossRef]
- PL Alreck and RB Settle, 2002. The hurried consumer: Time-saving perceptions of Internet and catalogue shopping. Journal of Database Marketing and Customer Strategy Management, Volume 10, pp. 25-35. [CrossRef]
- Podsakoff, P.M. et al., 2003. Common method biases in behaviorial research : A critical review of literature and recommended remedies. Journal of Applied Psychology, 88(5), pp. 879-903. [CrossRef]
- R. Agarwal, E. Karahanna,, 2000. Time flies when you’re having computer technology: a comparison of two theoretical. IS Quarterly, 24(4), pp. 665-694. [CrossRef]
- R.E. Wood et al., 2008. Mediation testing in management research: a review and proposals. Organizational Research Methods, 11(2), pp. 270-295. [CrossRef]
- Rahi, Samar & Ghani, Mazuri & Ngah, Abdul., 2016. Investigating the role of UTAUT and e service quality in internet banking adoption setting. The TQM Journal, 31(3), pp. 491-506. [CrossRef]
- Reio, T. G., 2010. The Threat of Common Method Variance Bias to Theory Building. Human Resource Development Review,, 9(4), pp. 405-411. [CrossRef]
- Robert M. Morgan and Shelby D. Hunt, 1994. The Commitment-Trust Theory of Relationship Marketing. Journal of Marketing, 58(3), pp. 20-38. [CrossRef]
- Roger C. Mayer et al., 1995. An Integrative Model of Organizational Trust. Academy of Management Review, 20(3), pp. 709-734. [CrossRef]
- Rungtusanatham et al., 2014. Theorizing, testing and concluding for mediation in SCM research: Tutorial and procedural recommendations. Journal of Operations Management, 32(3), pp. 99-113. [CrossRef]
- Sarstedt et al., 2016b. Estimation issues with PLS and CBSEM : Where the bias lies. Journal of Business Research, 69(10), pp. 3998-4010. [CrossRef]
- Sarstedt et al., 2020. Beyond a Tandem Analysis of SEM and PROCESS : Use of PLS SEM for Mediation Analysis. International Journal of Marketing Research, 62 (3), pp. 288-299. [CrossRef]
- Sarstedt M et al., 2017. Partial Least Squares Structural Equation Modeling. In : Homburg C Klarmann, M and Vomberg A (Eds). Handbook of Market Research, New York et al. New York: Springer.
- Sarstedt Ringle et al., 2017b. Treating unobserved heterogeneity in PLS-SEM: a multi method approach in Noonan R and Latan H (Ed). Partial Least Squares Structural Modeling : Basic Concepts, Methodological Issues and Applications, pp. 197-217.
- Saunders, M., Lewis, P. and Thornhill, A., 2009. Research Methods for Business Students. New York : Pearson.
- Shmueli, G., Sarstedt, M., Hair, J.F., Cheah, J.-H., Ting, H., Vaithilingam, S. and Ringle, C.M, 2019. Predictive model assessment in PLS-SEM: guidelines for using PLSpredict. European Journal of Marketing, 53(11), pp. 2322-2347. [CrossRef]
- Sonja Grabner Krauter & Rita Faullant, 2008. Consumer acceptance of internet banking: the influence of internet trust. International Journal of Bank Marketing, 26 (7 ), pp. 483-504. [CrossRef]
- Stone, M, 1974. Cross-Validatory Choice and Assessment of Statistical Predictions.. Journal of the Royal Statistical Society. Series B (Methodological),, 36(2), pp. 111-147. [CrossRef]
- Strickland, L. H, 1958. Surveillance and trust. Journal of Personality, Volume 26, pp. 200-215. [CrossRef]
- Suh and Han, 2002. Effect of trust on customer acceptance of Internet banking. Electronic Commerce Research and Applications, Issue 3-4, pp. 247-263. [CrossRef]
- V. Venkatesh, F.D. Davis, 2000. A theoretical extension of the technology acceptance model four longitudinal field studies. Management Science, 46(2), pp. 186-204. [CrossRef]
- Venkatesh, V., & Davis, F. D., 2000. A theoretical extension of the technology acceptance model: Four longitudinal field studies.. Management Sciences, Volume 46, pp. 186-204. [CrossRef]
- Vishwanathan & Kayande, 2012. Commentary on Common Method Bias in Marketing : Cause, Mechanisms and Procedural Methods. Journal of Retailing, 88(4), pp. 556-562. [CrossRef]
- Vukovic M. et al., 2019. Technology acceptance model for internet banking acceptance in split. Business Systems Research : International Journal of Society for Advancing Innovation and Research in Economy, 10(2), pp. 124-140. [CrossRef]
- W. Chin, J.-H. Cheah, Y. Liu, H. Ting, X.-J. Lim and T.H. Cham, 2020. Demystifying the role of causal-predictive modeling using partial least squares structural equation modeling in information systems research. Industrial Management & Data Systems, 120(12), pp. 2161-2209. [CrossRef]
- Wang et al., 2003. Determinants of User Acceptance of Internet Banking: An Empirical Study. International Journal of Service Industry Management, 14(5), pp. 501-513. [CrossRef]
- Wold, H.O.A, 1985. Partial least squares”, in Kotz, S. and Johnson, N.L. (Eds). Encyclopedia of Statistical Sciences, pp. 581-591. [CrossRef]
- X. Zhao, J.G. Lynch, Q. Chen, 2010. Reconsidering Baron and Kenny: myths and truths about mediation analysis. Journal of Consumer Research, 37(2), pp. 197-206. [CrossRef]
- Yao et al., 2015. Wine brand category choice and confucianism: A purchase motivation comparison of caucasian, Chinese and Korean consumers. Advances in national brand and private label marketing, pp. 19-33. [CrossRef]
- Ye, C. et al., 2008. The Role of Innovation and Wealth in the Net Neutrality Debate. J. Am. Soc. Inf. Sci. Technol., Volume 59, pp. 2115-2132. [CrossRef]
- Yousafzai S.M. et al., 2010. Explaining internet banking behavior : theory of reasoned action, theory of planned behavior or technology acceptance model. Journal of Applied Social Psychology, 40(5), pp. 1172-202. [CrossRef]
- Zhang, Z., & Yuan, K. H, 2018. Practical statistical power analysis using Webpower and R.. China, beijing : ISDSA Press. [CrossRef]
- Zhao et al., 2010. Reconsidering Baron and Kenny : Myths and Truths about Mediation Analysis. Journal of Consumer Research, 37(3), pp. 197-206. [CrossRef]

| Construct | Item | Scale | Loading/Weight | AVE/t-value | Composite reliability (rho_a) | Cronbach's Alpha | Composite reliability (rho_c) |
|---|---|---|---|---|---|---|---|
| Perceived Usage | PU1 | Reflective | 0.843 | 0.740 | 0.886 | 0.883 | 0.919 |
| PU2 | 0.859 | ||||||
| PU3 | 0.854 | ||||||
| PU4 | 0.884 | ||||||
| Perceived ease of use | PE1 | Reflective | 0.913 | 0.830 | 0.900 | 0.898 | 0.936 |
| PE2 | 0.898 | ||||||
| PE3 | 0.922 | ||||||
| Perceived Trust | PT1 | Reflective | 0.929 | 0.841 | 0.938 | 0.937 | 0.955 |
| PT2 | 0.903 | ||||||
| PT3 | 0.918 | ||||||
| PT4 | 0.917 | ||||||
| Perceived Security | PS1 | Reflective | 0.905 | 0.796 | 0.914 | 0.914 | 0.940 |
| PS2 | 0.896 | ||||||
| PS3 | 0.893 | ||||||
| PS4 | 0.874 | ||||||
| Intention to Use | IOU1 | Reflective | 0.942 | 0.866 | 0.924 | 0.923 | 0.951 |
| IOU2 | 0.929 | ||||||
| IOU3 | 0.922 |
| IOU | PEOU | PS | PT | PU | |
|---|---|---|---|---|---|
| IOU | 0.931 | ||||
| PEOU | 0.847 | 0.911 | |||
| PS | 0.827 | 0.852 | 0.892 | ||
| PT | 0.730 | 0.728 | 0.774 | 0.917 | |
| PU | 0.859 | 0.854 | 0.854 | 0.780 | 0.860 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




