Submitted:
29 May 2023
Posted:
31 May 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Problem description
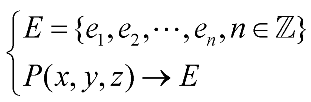
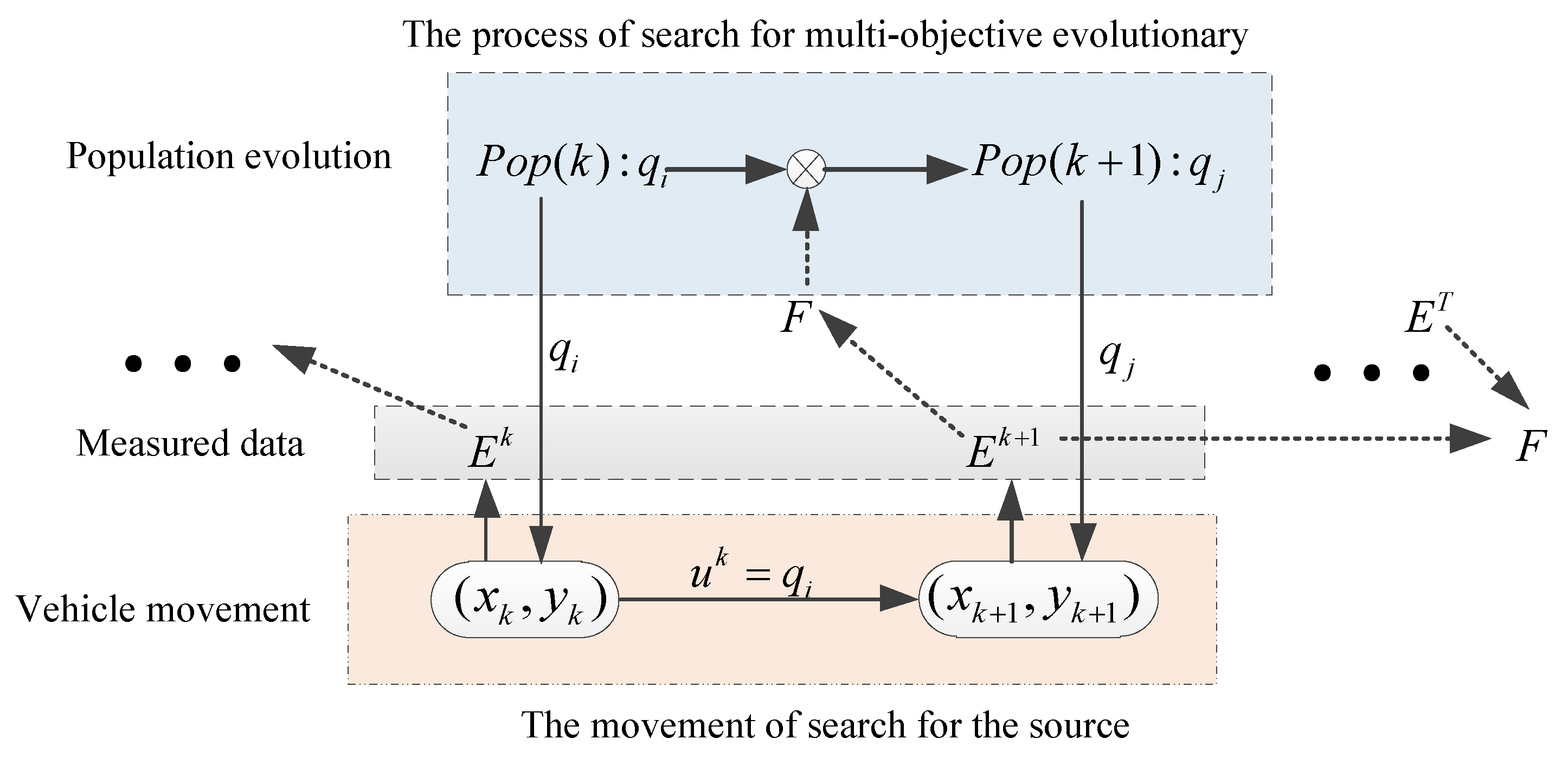
3. A source seeking method based on balanced searching strategy
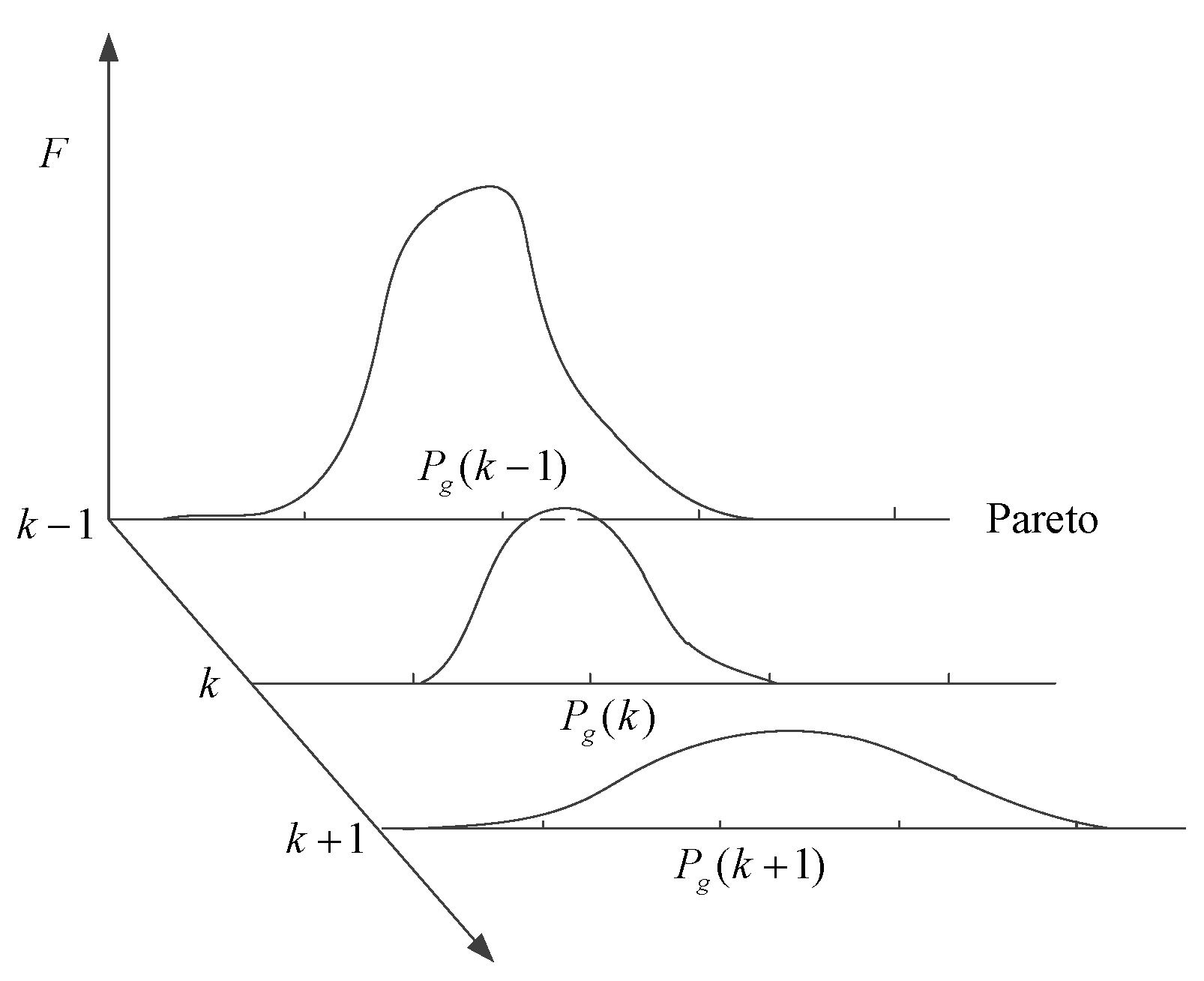
3.1. Characteristic analysis of the source of implicit information field
3.2. Source seeking behavior of implicit information field based on motion path
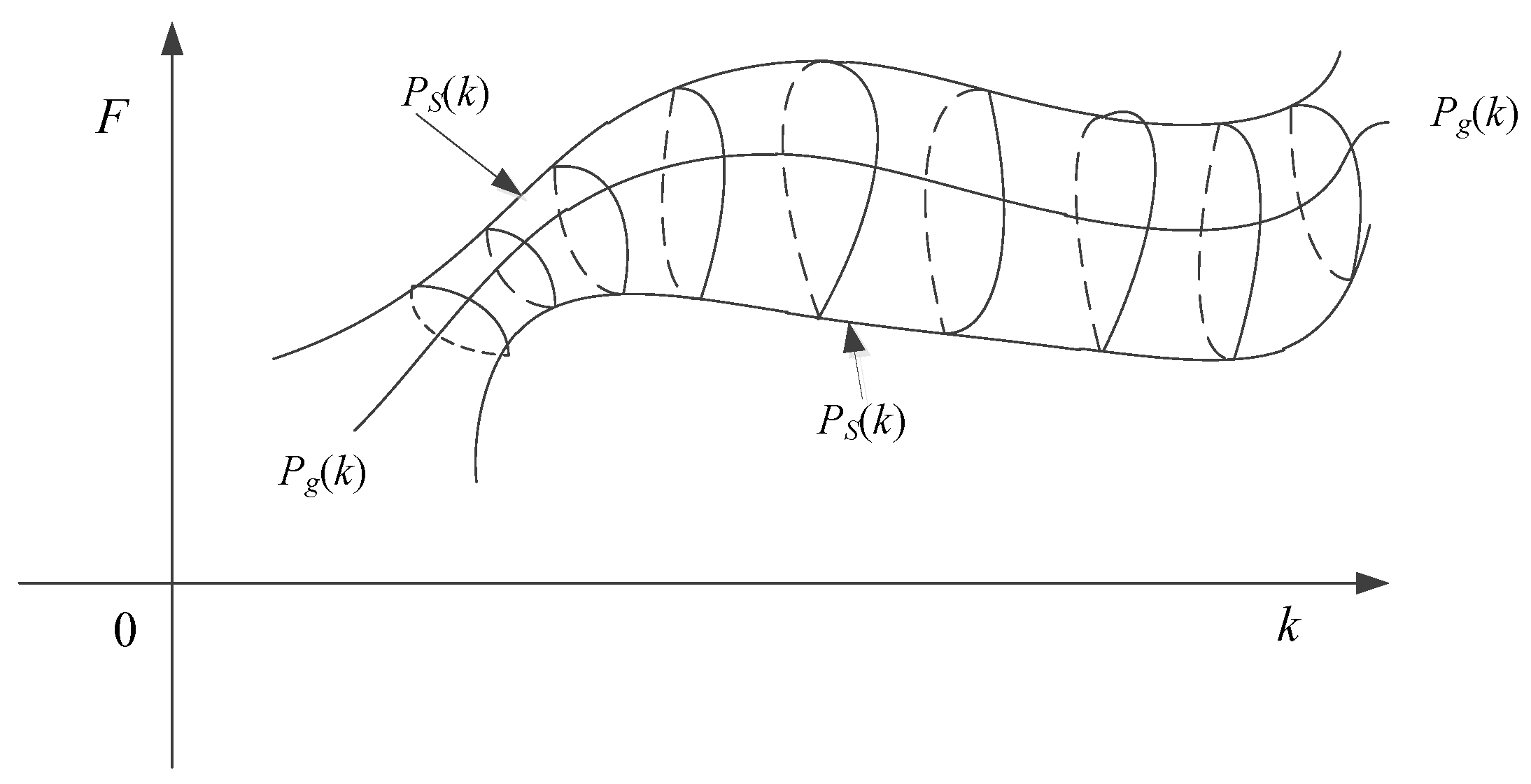
3.3. Balance searching strategy
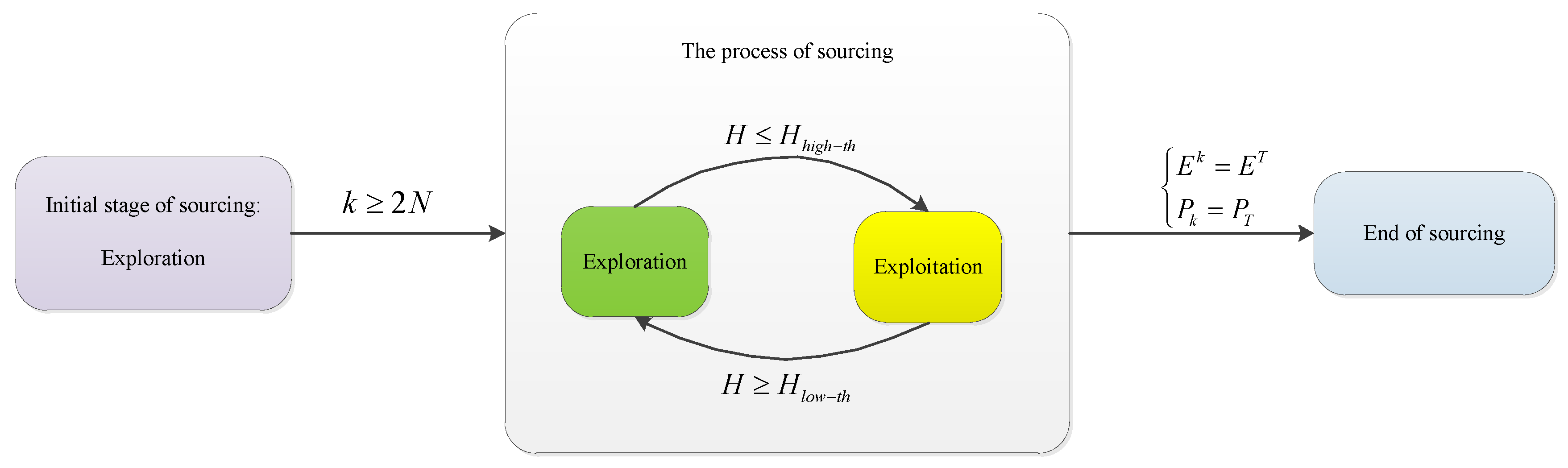
3.3.1. Exploration and exploitation
3.3.2. The algorithm of source seeking
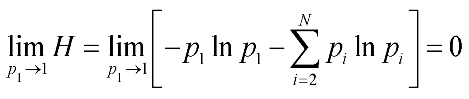
4. Algorithm performance analysis
4.1. Analysis for the convergence of the algorithm
4.2. Analysis for the performance of source seeking
5. Experiment
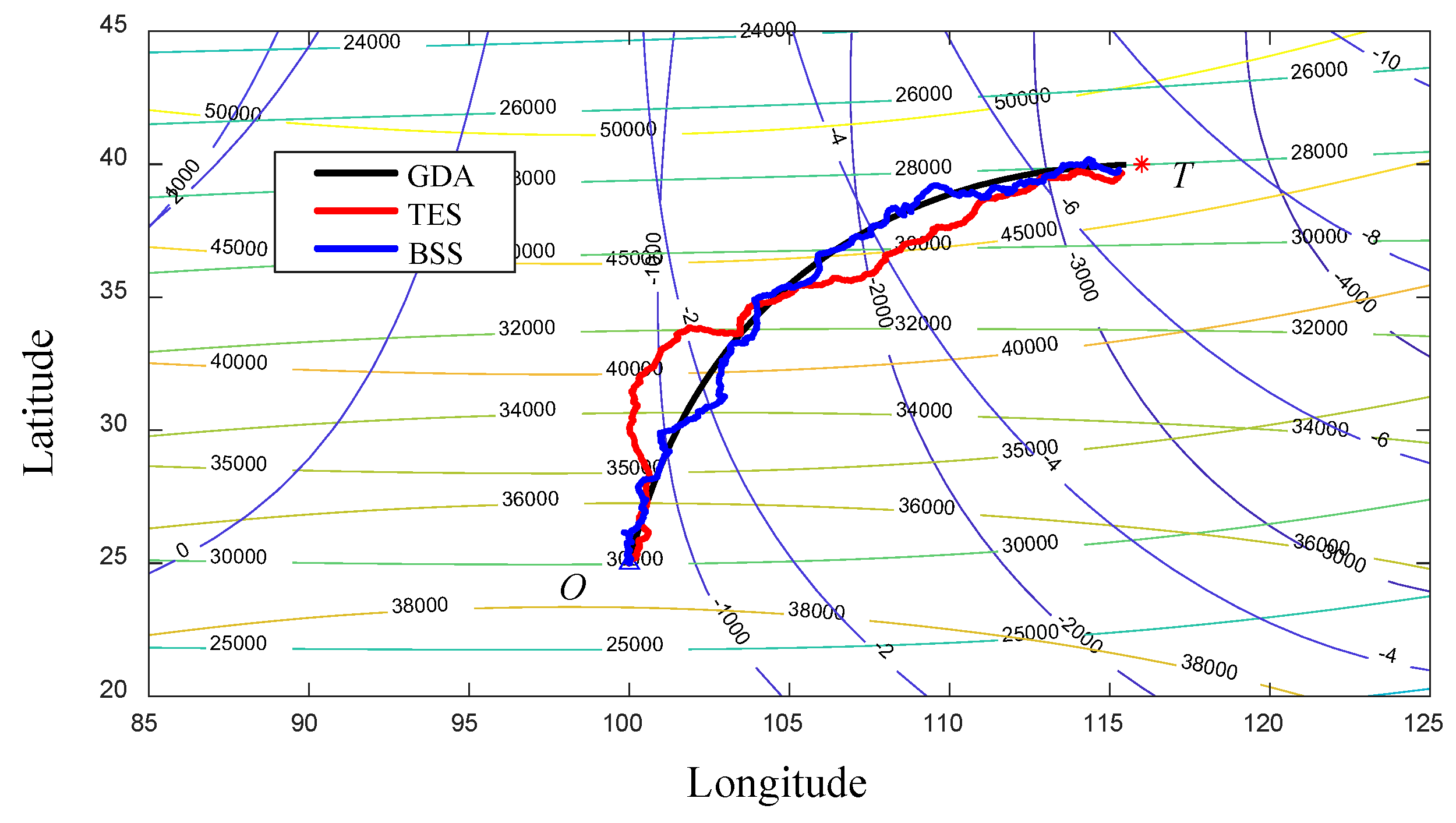
5.1. Simulation background field and source-seeking parameter setting
5.2. Comparison of different algorithms
5.3. Influence of different parameters on algorithm performance
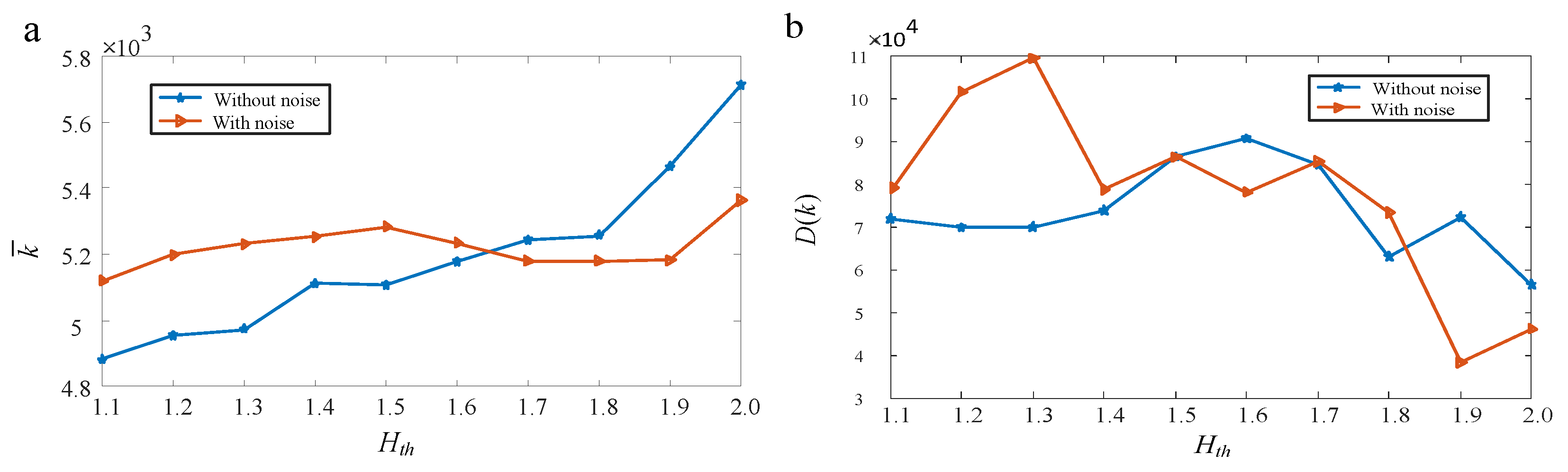
5.3.1. Analysis of the influence of
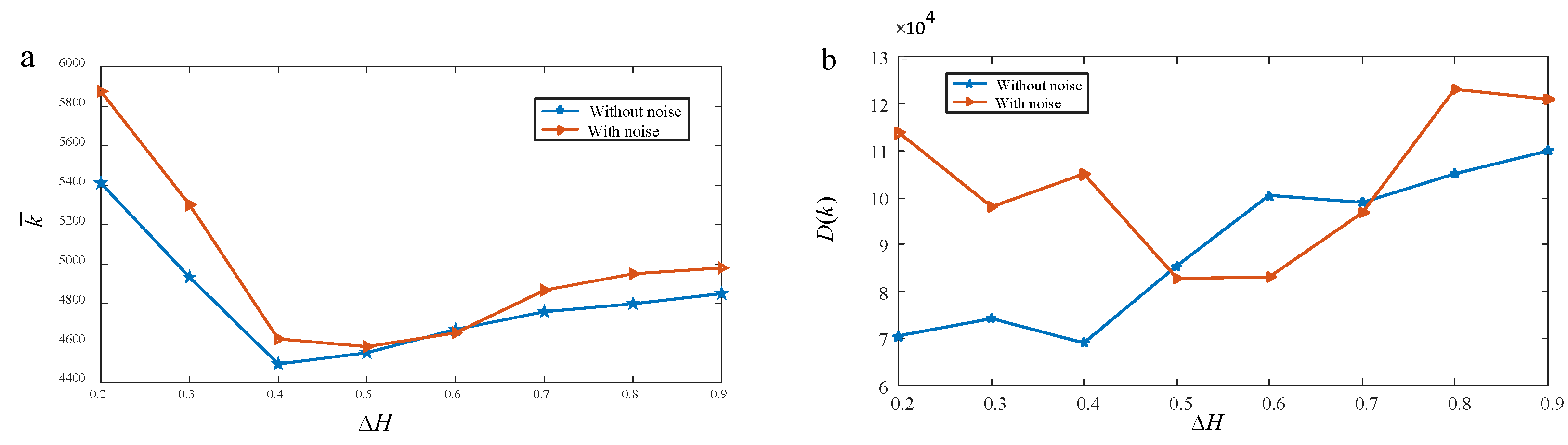
5.3.2. Analysis of the influence of
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhang, C. , et al. "Source Seeking with Nonholonomic Unicycle Without Position Measurement---Part I: Tuning of Forward Velocity," Systems & Control Letters, vol. 56, no. 3, pp. 245-252, 2007.
- Cochran, J. , et al. "Source seeking with a nonholonomic unicycle without position measurements and with tuning of angular velocity — Part II: Applications," Proceedings of the IEEE Conference on Decision and Control (2007), pp. 1951-1956.
- Khyade, V. B. , and E. R. Kandel. "Geomagnetic Field and Animal Orientation." International Journal of Social Science and Humanities Research, vol. 6, no. 4, 2018, pp. 27-42.
- Putman N, F. “Animal Navigation: Seabirds Home to a Moving Magnetic Target,” Current Biology, vol. 30, no. 14, pp. 802-804, 2020.
- Willis, M. A. "Odor-modulated Navigation in Insects and Artificial Systems," Chemical Senses, vol. 30, no. 1, pp. 287-288, 2005.
- Anderson, R. B. , et al. "Mobile Robotic Radiation Surveying with Recursive Bayesian Estimation and Attenuation Modelling," E Transactions on Automation Science and Engineering, vol 19, no. 1, pp. 410-424, 2020.
- Oconnor, Alan, P. Setlur, and N. Devroye. "Single-sensor RF emitter localization based on multipath exploitation," IEEE Transactions on Aerospace & Electronic Systems, vol. 51, no. 3, pp. 1635-1651, 2015.
- Jing, T., Q. Meng, and H. Ishida. "Recent Progress and Trend of Robot Odor Source Localization." IEEJ Transactions on Electrical and Electronic Engineering, vol. 16. no. 7, pp.938-953, 2021.
- Golov, Y. , et al. "Navigation in an odorant-landscape: mate finding and mate choice in a nocturnal moth." Entomologia Generalis, vol. 42, no. 2, pp. 323-334, 2021.
- Atanasov, N. A., J. L. Ny, and G. J. Pappas. "Distributed Algorithms for Stochastic Source Seeking with Mobile Robot Networks: Technical Report," Journal of Dynamic Systems Measurement & Control, vol. 137, no. 3, DOI:10.1115/1.4027892, 2015.
- Wu, W., I. D. Couzin, and F. Zhang. "Bio-inspired Source Seeking with no Explicit Gradient Estimation," IFAC Proceedings Volumes, vol. 45, no. 26, pp. 240-245, 2012.
- N. Atanasov, J. Le Ny, N. Michael and G. J. Pappas, "Stochastic source seeking in complex environments," 2012 IEEE International Conference on Robotics and Automation, doi: 10.1109/ ICRA.2012.6225289, pp. 3013-3018, 2012.
- M. Q. Liu, B. Li and Y. F. Chen et al., “Location Parameter Estimation of Moving Aerial Target in Space-Air-Ground Integrated Networks-Based IoV,” IEEE Internet of Things Journal.
- M. Q. Liu, C. H. Liu and M. Li et al., “Intelligent passive detection of aerial target in space-air-ground integrated networks,” China Communications, vol.19, no.1, pp.52–63, 2022.
- Paliotta, C., D. Belleter, and K. Y. Pettersen. "Adaptive Source Seeking with Leader-Follower Formation Control," Ifac Papersonline, vol. 48, no. 16, pp. 285-290, 2015.
- Gronemeyer, M., M. Alpen, and J. Horn. "Limited Gradient Criterion for Global Source Seeking with Mobile Robots," IFAC-PapersOnLine, vol. 53, no. 2, pp. 15288-15293, 2020.
- Massimo, V., V. Emmanuel, and B. I. Shraiman. "'Infotaxis' as a strategy for searching without gradients," Nature, vol. 445, no. 7126, pp. 406-415, 2007.
- Loisy, A. , and C. Eloy. "Searching for a source without gradients: how good is infotaxis and how to beat it," arXiv e-prints, vol. 478, no. 2262, Article Id.20220118, 2022.
- M. Q. Liu, Z. L. Liu and W. D. Lu et al., “Distributed Few-Shot Learning for Intelligent Recognition of Communication Jamming,” IEEE Journal of Selected Topics in Signal Processing.
- M. Q. Liu, J. K. Wang and N. Zhao et al., "Radio Frequency Fingerprint Collaborative Intelligent Identification Using Incremental Learning, " IEEE Transactions on Network Science and Engineering.
- Mingqian Liu, Chunheng Liu, Yunfei Chen, Zhiwen Yan,Nan Zhao, Radio Frequency Fingerprint Collaborative Intelligent Blind Identification for Green Radios, IEEE Transactions on Green Communications and Networking.
- Mingqian Liu, Hongyi Zhang, Zilong Liu, Nan Zhao, Attacking Spectrum Sensing With Adversarial Deep Learning in Cognitive Radio-Enabled Internet of Things, IEEE Transactions on Reliability, DOI: 10.1109/TR.2022.3179491, 2022.
- Mingqian Liu, Zhenju Zhang, Yunfei Chen, Jianhua Ge, Nan Zhao. Adversarial Attack and Defense on Deep Learning for Air Transportation Communication Jamming, IEEE Transactions on Intelligent Transportation Systems, 2023, DOI: 10.1109/TITS.2023.3262347.
- Fuqing Zhao, Lixin Zhang, Jie Cao, Jianxin Tang, "A cooperative water wave optimization algorithm with reinforcement learning for the distributed assembly no-idle flowshop scheduling problem, " Computers & Industrial Engineering,vol. 153. No. 1082, pp. 1-16, 2021.
- F. Zhao, S. Di, J. Cao, J. Tang and Jonrinaldi, "A Novel Cooperative Multi-Stage Hyper-Heuristic for Combination Optimization Problems," in Complex System Modeling and Simulation, vol. 1, no. 2, pp. 91-108, 2021.
- Crepinsek, Matej, S. H. Liu, and M. Mernik. "Exploration and exploitation in evolutionary algorithms: A survey," ACM Computing Surveys, vol. 45, no. 3.
- Nguyen, Ttv, MD Phung, and Q. V. Tran. "Behavior-based Navigation of Mobile Robot in Unknown Environments Using Fuzzy Logic and Multi-Objective Optimization," International Journal of Control and Automation, vol. 10, no. 2, pp. 349-364, 2017.
- Anagnostopoulos, G. G., M. Deriaz, and D. Konstantas. "A Multiobjective Optimization Methodology of Tuning Indoor Positioning Systems," 2017 International Conference on Indoor Positioning and Indoor Navigation (IPIN), pp. -8.
- Giagkiozis, I. , and P. J. Fleming. "Methods for multi-objective optimization: An analysis," Information Sciences, vol. 293, no. 1, pp. 338-350, 2015.
- Salazar, J. Z. , et al. "Balancing exploration, uncertainty and computational demands in many objective reservoir optimization," Advances in Water Resources, vol. 109, no. 1, pp. 196-210, 2017.
- Liu M, Liu K, Li H, et al. “A Study of Bio-Inspired Geomagnetic Navigation Using Timing Evolution Searching Strategy.” Journal of Northwestern Ploytechnical University, vol.32, no.6, pp.894–898, 2014.
- H. Li, M. Liu and K. Liu, "Bio-inspired geomagnetic navigation method for autonomous underwater vehicle," Journal of Systems Engineering and Electronics, vol. 28, no. 6, pp. 1203-1209,2017.
| Algorithm | Source seeking Task | ||||
|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | |
| GDA | 2787 | 2266 | 2406 | 2490 | 2413 |
| TES | 5828 | 4868 | 5036 | 5168 | 5110 |
| BSS | 5016 | 4223 | 4406 | 4486 | 4398 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





