Submitted:
02 June 2023
Posted:
05 June 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Our Contribution
- (1)
- We propose a novel Software-defined MIoTs-based model providing security communication in underlying data plane. The outstanding computing power of control plane greatly relieves the overhead of upper layer, which offer users higher-quality services.
- (2)
- We design an authentication system to ensure the authenticity and reliability of messages, so that OLDs are encouraged to spread real information. Otherwise, they will ge punished. Besides, an emergency-dealing scheme is offered to provide in-time services based on multicast, which not only takes current networks situation into consideration, but also the prediction of instantaneously changing.
- (3)
- A security analysis proves that our proposed scheme is able to achieve the security goals of Software-defined MIoTs. In addition, adopting elliptic curve cryptography avoids heavy overhead brought by bilinear pairing operations, which is demonstrated by the comparison results.
2. Related Works
3. Models and Design Goals
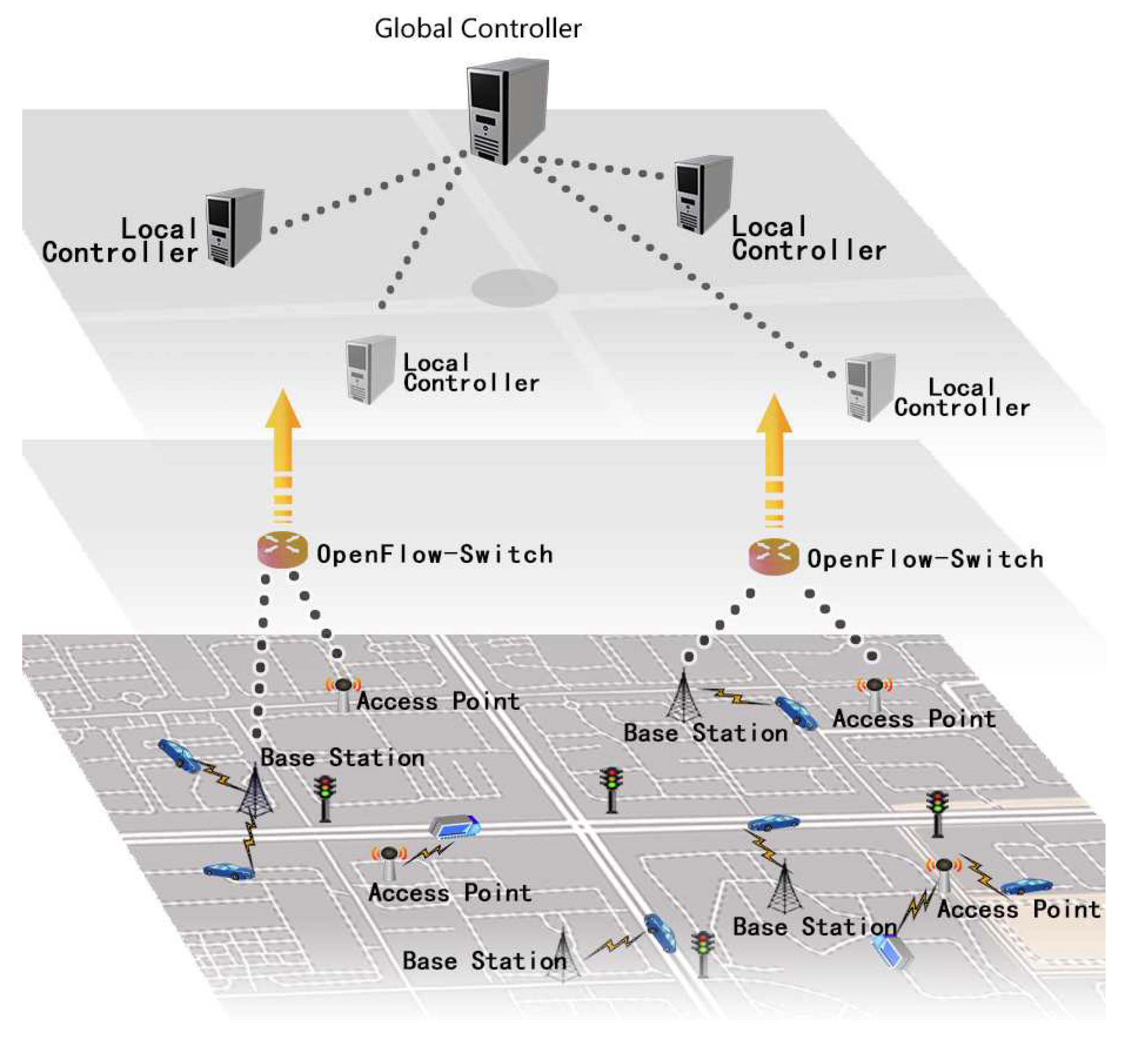
3.1. System Model and Assumptions
- (1)
- GC:It’s the main controller of the control plane. In traditional SDN systems, the controller is a logically centralized point that has extremely outstanding storage and computing capabilities. Typically, it directs switches to deliver and forward packages by building routing rules. In our system, the GC is mainly responsible for generating system parameters, computing the movement path of the device, and building route tables for OF-Switches. When there are accidents or emergencies happening, it also selects impacted devices and forms a temporary multicast group. It generates a multicast tree for this group to inform them of conditions in time.
- (2)
- LCs:They are distributed geographically and manage a specific small area respectively. In our system, LCs exist mainly for balancing the computation and storage burdens of the GC. It can reduce realistic deployment costs as well. LCs set system parameters and communicate with OLDs. They can verify messages in their local areas and compute fine-grained navigation for OLDs. When there are road situations, they also compose of multicast nodes to inform and direct OLDs in their areas.
- (3)
- OF-Switches:Different from conventional switches, OF-Switches are OpenFlow-enabled data switches that communicate with external controllers over OpenFlow channel. OpenFlow protocol offers separation of programming network devices and underlying hardwares [32]. In our system, OF-Switches perform package lookup and forwarding according to flow tables installed on them.
- (4)
- OLDs:OLDs offer network access services via wireless communication capabilities, which have limited computing power and storage [33]. Also a tamper-proof equipment is embedded in each OLDs, which is robust and responsible for generating key cryptographical parameters, and performing many encryption and decryption operations [34].
- (5)
-
BSs and APs:OLDs get access to Internet via various ways. Cellular networks like 5G network via BSs, and city WiFi via APs are both supported by our system. For Software-defined MIoTs, to balance heterogeneous networks and allow OLDs in different networks to communicate is much easier compared with conventional networks.
- *
- The GC is fully trusted and will not be compromised. It has ample computing power and storage space.
- *
- LCs are trustworthy, but in case it is compromised, we don’t provide them capabilities of trace OLDs’ real identities. LCs have sufficient computing and storage space.
- *
- The parameters and data stored in OLDs are not available for others.
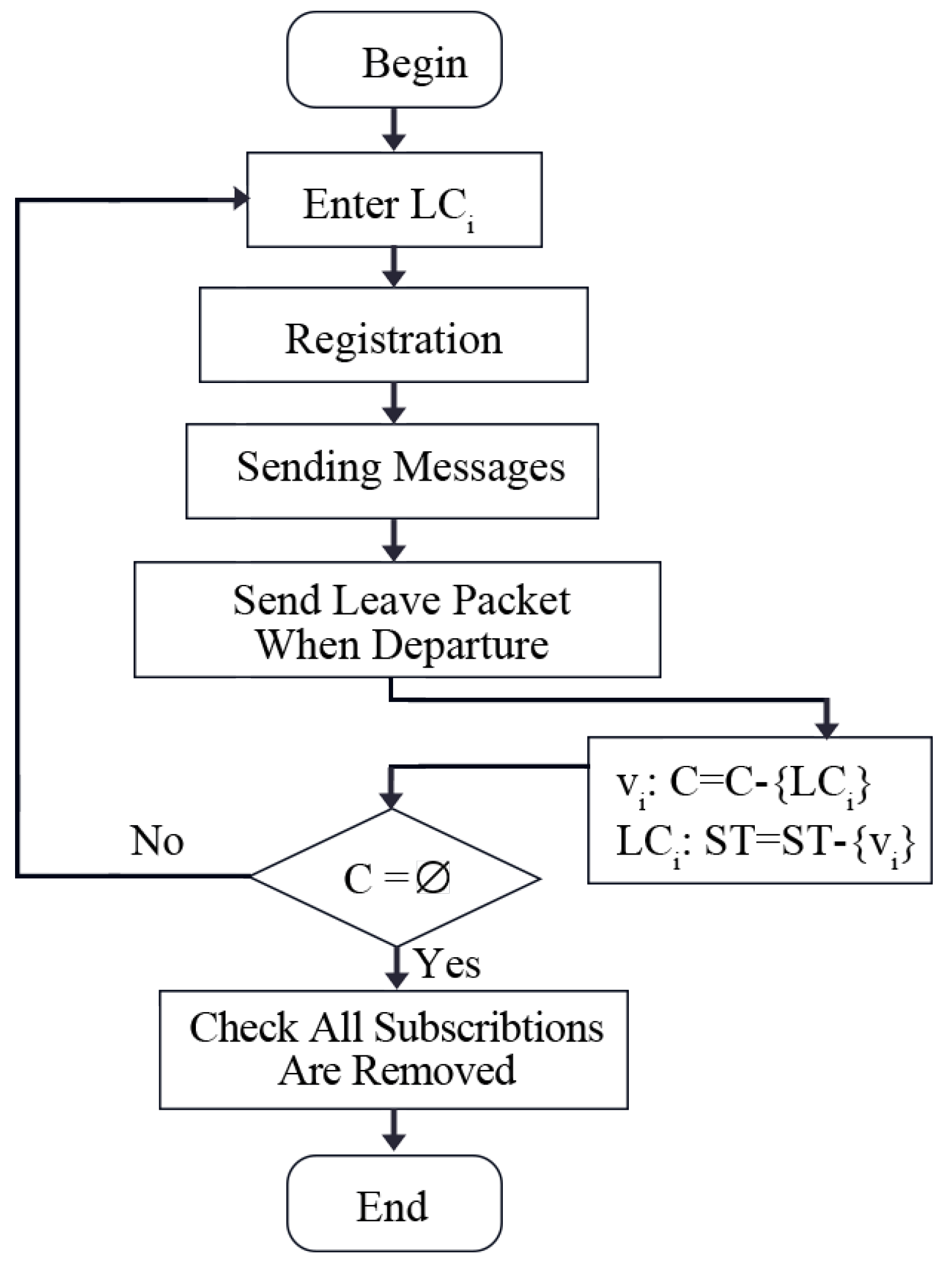
3.2. Multicast Subsystem
3.2.1. Steiner Tree
| Algorithm 1 Directing Process |
|
Input: input departure, ; destination,
Output: reach
|
3.2.2. Multicast Tree
3.2.3. Application Process
3.3. Design Goals
- (1)
- Anonymity: OLDs in our system will not communicate with other entities with real identities. Only by virtue of messages sent by OLDs and some public information, malicious users are not able to obtain the sender’s real identity. By this, OLDs are allowed to send messages without exposing sensitive privacy.
- (2)
- Authentication and Privacy: All interactive parties in our system can authenticate each other to ensure the reliability and legitimacy. Especially, in different areas, messages sent by OLDs should reflect the present LC’s information without exposing them to adversaries, which makes sure the location privacy would not be damaged.
- (3)
- Traceability: We won’t exclude the possibility of malicious entities’ existences. They aim to interrupt or interfere normal communications, or spread false and deceptive messages to gain conveniences and benefits for themselves. When misbehavior occurs, the controller plane should be able to trace the real identities and punish them by cutting services or submitting their information to related authorities.
- (4)
- Unlinkability: The proposed scheme would not enable third parties to link scattered messages to the same OLDs. That is to say, no third party could know one specific OLD’s activities by analysing those intercepted messages.
- (5)
- Resistance to common attacks: The scheme should also be able to resist common attacks that happen in conventional networks. For instance, replay attack, impersonation attack, modification attack, and so on.
4. Proposed Scheme
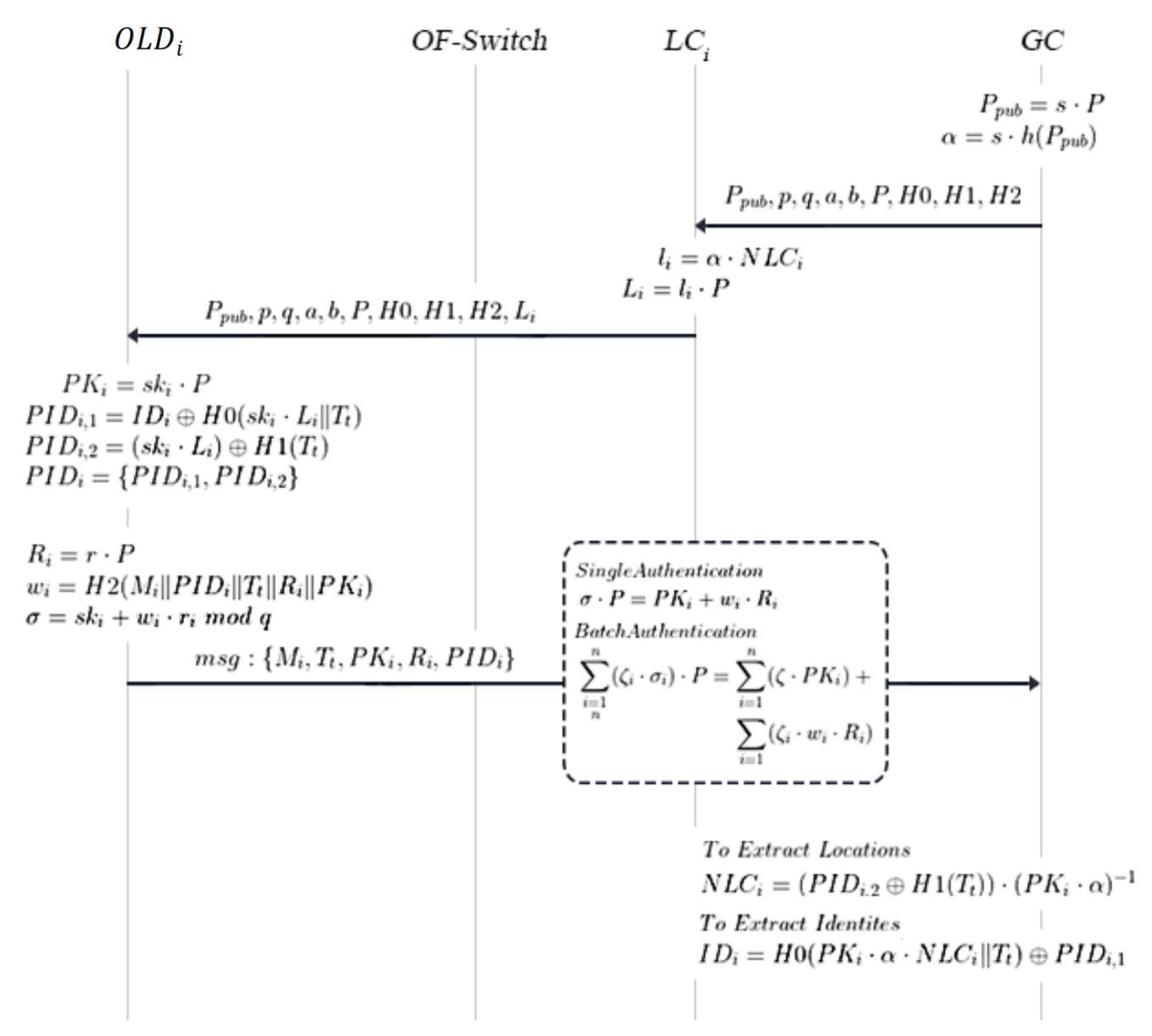
4.1. Control Plane Initialization
- 1)
- GC Initialization:The GC randomly selects the master key , and computes as its public key, and makes . Then it selects , , , . It sends to LCs and publishes {} as the system parameters. To ensure the security of the whole system, hash function h should be kept secret to GC.
- 2)
- LCs Initialization:After receiving via secure channel in control plane, computes as its secret key, where is a unique number of each LC and a list of them is only stored in the GC. Since s is unknown to any third party, and each also stays secret, it’s also difficult to compute based on public parameters. Then it computes as its public key, and adds in to GC’s system parameters. Finally, {} is the local system parameters of this specific area.
4.2. Online Learning Devices Initialization
4.3. One-time Key Generation and Message Signature
4.4. Emergency Location Extraction
4.5. Message Authentication
- (1)
-
Single VerificationAfter receiving a message , to verify its validation, a receiver will perform following steps by order with the system parameters {}.
- *
- Check if the timestamp is fresh. If not, it abandons the received message. If so, keep performing.
- *
-
The receiver performs and and calculates if they equal. If does not, the receiver chooses to abandon it. If equals, it admit the validation of this message.Since , , , , and , where , , and , following equations can be derived.
- (2)
-
Batch VerificationWhen a receiver obtains n messages in a short interval, verifying them one by one will consume lots of time and computing power. So our scheme supports batch verification to save sources. Firstly, to ensure the non-repudiation of signatures using batch verification, we choose a vector consisting of small random integers. Let the vector , where , and is a secure parameter. After receiving a message , , ..., , to verify its validation, a receiver will perform following steps by order with the system parameters {}.
- *
- Check if the timestamp are fresh. If not, it abandons the received message. If so, keep performing.
- *
- The receiver performs and calculates if they equal. If does not, the receiver will find the malicious message via the invalid signature search algorithm and chooses to abandon it[cite]. If equals, it admits the validation of this series of messages.
5. Security Proof and Analysis
5.1. Security Proof
- Setup-Oracle: generates the private key and corresponding system parameters. Then it sends them to when revokes the query.
- -Oracle: chooses a random point , and insert into its list . Then it returns d to when revokes the query.
- -Oracle: chooses a random number , and insert into its list . Then it returns d to when revokes the query.
- -Oracle: chooses a random point , and insert into . Then it returns d to when revokes the query.
- Sign-Oracle: based on the sent by , computes a . Then returns to when revokes the query.
5.2. Security Analysis
- (1)
- Anonymity: OLDs in our system will not communicate with other entities with pseudo identities , where . Malicious users are not able to obtain the sender’s privacy only via public parameters and messages it sent. By this, vehicles are allowed to send messages without exposing their real identities.
- (2)
- Authentication and Privacy: All messages sent by communicating parties should sign these messages before sending. They compute , where . Then encapsulated messages are broadcasted. Thus, all interactive parties in our system can authenticate each other to ensure the reliability and legitimacy. Besides, an encapsulated message include no LC’s explicitly, which will keep the basic location privacy of OLDs. But when it’s needed, the GC can derive the rough location of by computing from the .
- (3)
- Traceability: When malicious messages are detected, the GC will extract vehicles’ real identities by computing , since , and can be easily derived via messages.
- (4)
- Unlinkability: Every time to generate a message , a random number will be reselected, and a new will be recomputed. Due to the randomness of and variability of , a malicious party is unable to link messages sent by one OLDs to itself. Therefore, the proposed scheme offers unlinkability in interactive communications.
- (5)
-
Resistance to common attacks: Our scheme can also be able to resist common attacks that happen in conventional networks. Such as,
- *
- Replay Attack: The encapsulated message contains timestamp , which can prevent messages are saved then reforwarded. When receives messages, receivers check the freshness of messages at the very first beginning. If it’s still fresh, receiver will start to verify the validation of these messages. Otherwise, messages will be abandoned.
- *
- Impersonation Attack: If an adversary tries to impersonate a legal vehicle, it has to generate a signature of the message which satisfies . But according to Theorem 1, no adversary can generate such messages in the polynomial time, which proofs that our scheme is able to resist impersonation attack.
- *
- Modification Attack: A signature is a digital signature related to since . If is modified by a malicious party, then will change consequently, which makes change as well. Hence, the modification can be easily detected if message itself is modified. By that, our scheme is able to resist modification attack.
- *
- Sybil Attack: To start a sybil attack, the adversary must generate multiple identities to play multiple roles. However, the pseudo identities are computed by a tamper-proof device. An adversary must violate the device first to generate those identities, which is infeasible via current technologies. Therefore, our scheme is able to resist sybil attack.
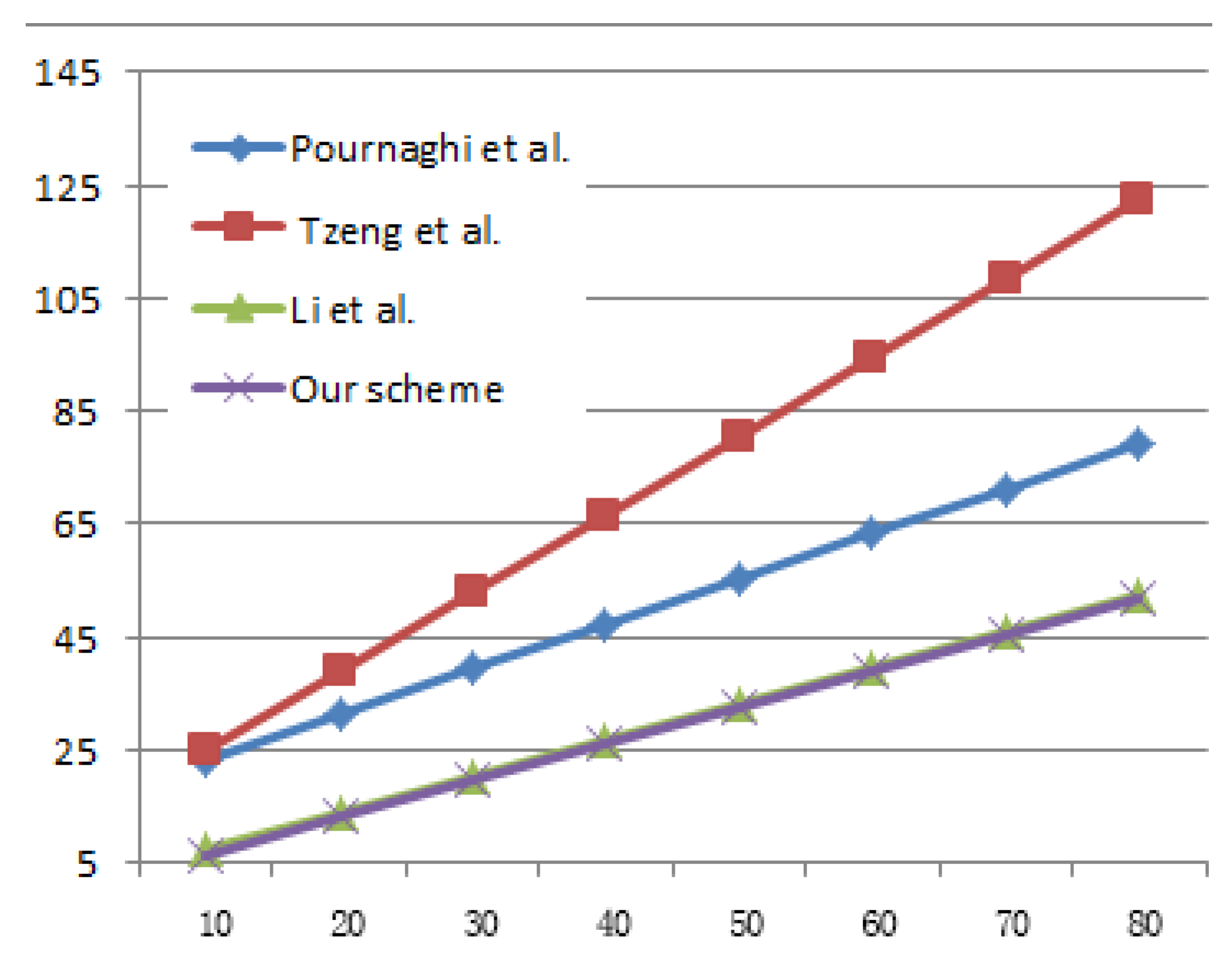
6. Performance Analysis
- -
- : The time spent on performing a bilinear pairing operation .
- -
- : The time spent on performing a scale multiplication operation of bilinear paring, , where .
- -
- : The time spent on performing a point addition of the bilinear pairing, where .
- -
- : The time spent on performing a MapToPoint hash operation of the bilinear pairing.
- -
- : The time spent on performing a scale multiplication operation , where .
- -
- : The time spent on performing a point addition operation , where .
- -
- : The time required for performing an one-way hash function operation.
6.1. Computation Cost Analysis
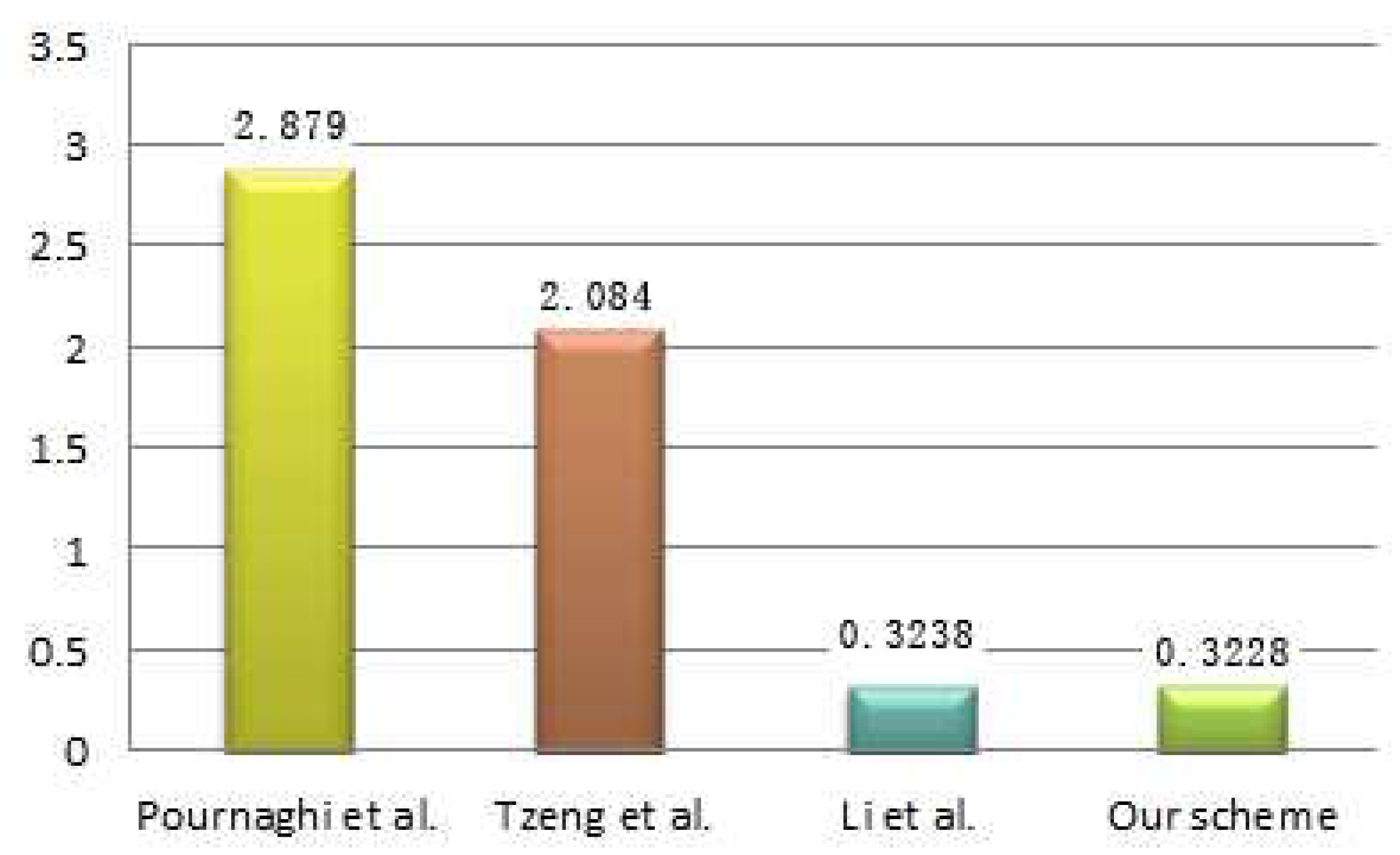
6.2. Communication Cost Analysis
7. Conclusions
References
- Gómez J, Huete J F, Hoyos O, et al. Interaction system based on internet of things as support for education. Procedia Comput. Sci. 2013, 21, 132–139. [Google Scholar] [CrossRef]
- Gul S, Asif M, Ahmad S, et al. A survey on role of internet of things in education. Int. J. Comput. Sci. Netw. Secur. 2017, 17, 159–165. [Google Scholar]
- Konan M, Wang W. A secure mutual batch authentication scheme for patient data privacy preserving in WBAN. Sensors 2019, 19, 1608–1621. [Google Scholar] [CrossRef] [PubMed]
- Pei X L, Wang X, Wang Y F, et al. Internet of things based education: Definition, benefits, and challenges. Appl. Mech. Mater. 2013, 411, 2947–2951. [Google Scholar]
- Li, J. Choo K K R, Zhang W, et al. EPA-CPPA: An efficient, provably-secure and anonymous conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Veh. Commun. 2018, 13, 104–113. [Google Scholar]
- Liu Y, Wang Y, Chang G. Efficient privacy-preserving dual authentication and key agreement scheme for secure V2V communications in an IoV paradigm. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Shao J, Lin X, Lu R, et al. A threshold anonymous authentication protocol for VANETs. IEEE Trans. Veh. Technol. 2015, 65, 1711–1720. [Google Scholar]
- Bousselham M, Abdellaoui A, Chaoui H. Security against malicious node in the vehicular cloud computing using a software-defined networking architecture. In Proceedings of the 2017 International Conference on Soft Computing and Its Engineering Applications 2017, 10, 1–5.
- Wang M, Liu D, Zhu L, et al. LESPP: lightweight and efficient strong privacy preserving authentication scheme for secure VANET communication. Computing 2016, 98, 685–708. [Google Scholar] [CrossRef]
- He D, Zeadally S, Xu B, et al. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Journal Abbreviation 2015, 10, 2681–2691. [Google Scholar]
- Huang J, Qian Y, Hu R Q. Secure and Efficient Privacy-Preserving Authentication Scheme for 5G Software Defined Vehicular Networks. IEEE Trans. Veh. Technol. 2020, 69, 8542–8554. [Google Scholar] [CrossRef]
- Cui J, Zhang X, Zhong H, et al. Extensible conditional privacy protection authentication scheme for secure vehicular networks in a multi-cloud environment. IEEE Trans. Inf. Forensics Secur. 2019, 15, 1654–1667. [Google Scholar]
- Sun Y, Lu R, Lin X, et al. An efficient pseudonymous authentication scheme with strong privacy preservation for vehicular communications. IEEE Trans. Veh. Technol. 2010, 59, 3589–3603. [Google Scholar] [CrossRef]
- Lu R, Lin X, Shi Z, et al. A lightweight conditional privacy-preservation protocol for vehicular traffic-monitoring systems. IEEE Intell. Syst. 2013, 28, 62–65. [Google Scholar] [CrossRef]
- Li H, Dong M, Ota K. Control plane optimization in software-defined vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2016, 65, 7895–7904. [Google Scholar] [CrossRef]
- Duan P, Peng C, Zhu Q, et al. Design and analysis of software defined Vehicular Cyber Physical Systems. IEEE Int. Conf. Parallel Distrib. Syst. 2014, 412–417. [Google Scholar]
- Gurtov A, Liyanage M, Ylianttila M, et al. Software Defined Mobile Networks (SDMN): Beyond LTE Network Architecture. Journal Abbreviation 2015.
- Bhatia J, Modi Y, Tanwar S, et al. Software defined vehicular networks: A comprehensive review. Int. J. Commun. Syst. 2019, 32, e4005. [Google Scholar] [CrossRef]
- Nkenyereye L, Nkenyereye L, Islam S M R, et al. Software-defined network-based vehicular networks: A position paper on their modeling and implementation. Sensors 2019, 19, 3788. [Google Scholar] [CrossRef]
- Zhu M, Cao J, Pang D, et al. SDN-based routing for efficient message propagation in VANET. Wireless Algorithms, Systems, and Applications: 10th International Conference, Proceedings 10. Springer International Publishing 2015, 788–797.
- Karakus M, Durresi A. Quality of service (QoS) in software defined networking (SDN): A survey. J. Netw. Comput. Appl. 2017, 10, 2681–2691. [Google Scholar]
- Lai C, Lu R, Zheng D. Achieving secure and seamless IP Communications for group-oriented software defined vehicular networks. Wirel. Algorithms Syst. 2017, 10, 356–368. [Google Scholar]
- Kim H S, Yun S, Kim H, et al. An efficient SDN multicast architecture for dynamic industrial IoT environments. Mob. Inf. Syst. 2018. [Google Scholar]
- Do T X, Nguyen V G, Kim Y. SDN-based mobile packet core for multicast and broadcast services. Wirel. Netw. 2018, 24, 1715–1728. [Google Scholar] [CrossRef]
- Zhou S, Wang H, Yi S, et al. Cost-efficient and scalable multicast tree in software defined networking. In Proceedings of the International Conference on Algorithms and Architectures for Parallel Processing 2015; pp. 592–605.
- Lecompte D, Gabin F. Evolved multimedia broadcast/multicast service (eMBMS) in LTE-advanced: Overview and Rel-11 enhancements. Lecompte D, Gabin F 2012, 50, 68–74. [Google Scholar]
- Chen J, Yan F, Li D, et al. Recovery and Reconstruction of Multicast Tree in Software-Defined Network: High Speed and Low Cost. IEEE Access 2020, 8, 27188–27201. [Google Scholar] [CrossRef]
- Garg S, Kaur K, Kaddoum G, et al. SDN-based secure and privacy-preserving scheme for vehicular networks: A 5G perspective. IEEE Trans. Veh. Technol. 2019, 68, 8421–8434. [Google Scholar] [CrossRef]
- Moulierac J, Guitton A, Molnár M. Multicast tree aggregation in large domains. Networking Technologies, Services, and Protocols; Performance of Computer and Communication Networks; Mobile and Wireless Communications Systems: 5th International IFIP-TC6 Networking Conference, Coimbra, Portugal. Proceedings 5. Springer Berlin Heidelberg 2016, 791–702.
- Azees M, Vijayakumar P, Deboarh L J. et al. EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans. Intell. Transp. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Li J, Ji Y, Choo K K R, Hogrefe D. CL-CPPA: certificate-less conditional privacy-preserving authentication protocol for the Internet of Vehicles. IEEE Internet Things J. 2019, 6, 10332–10343. [Google Scholar] [CrossRef]
- Lai C, Zhou H, Cheng N, et al. Secure group communications in vehicular networks: A software-defined network-enabled architecture and solution. IEEE Veh. Technol. Mag. 2017, 12, 40–49. [Google Scholar] [CrossRef]
- Cui J, Zhang X, Zhong H, et al. RSMA: Reputation system-based lightweight message authentication framework and protocol for 5G-enabled vehicular networks. IEEE Internet Things J. 2019, 6, 6417–6428. [Google Scholar] [CrossRef]
- Cui J, Wu D, Zhang J, et al. An efficient authentication scheme based on semi-trusted authority in VANETs. IEEE Trans. Veh. Technol. 2019, 68, 2972–2986. [Google Scholar] [CrossRef]
- Pournaghi S M, Zahednejad B, Bayat M, et al. NECPPA: A novel and efficient conditional privacy-preserving authentication scheme for VANET. Comput. Netw. 2018, 134, 78–92. [Google Scholar] [CrossRef]
- Tzeng S F, Horng S J, Li T, et al. Enhancing security and privacy for identity-based batch verification scheme in VANETs. IEEE Trans. Veh. Technol. 2015, 66, 3235–3248. [Google Scholar]
| Notations | Definitions |
|---|---|
| The Global Controller | |
| Local Controller i | |
| The i-th online learning devices | |
| G | An elliptic curve cycle additive group |
| P | A generator of G |
| q | The order of G |
| p | The size of a field |
| A public key of GC | |
| s | A private key of GC |
| The number of | |
| The identity of | |
| The pseudo identity of | |
| A private key of | |
| A public key of | |
| M | A message |
| A encapsulated message | |
| The signature of a message | |
| The time stamp | |
| ∥ | Concatenation operation |
| ⊕ | Exclusive-OR operation |
| Operations | Running Time() |
|---|---|
| 5.086 | |
| 0.694 | |
| 0.0018 | |
| 0.0992 | |
| 0.3218 | |
| 0.0024 | |
| 0.001 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).




