1. Introduction
Physical layer secret key (SK) generation technology is a promising technique for achieving one-time-pad encryption approach in wireless communication systems. This is possible due to the reciprocity, space-time uniqueness, and fast time-varying nature of the wireless channel. With this approach, both legitimate communication parties can independently generate SKs in real-time using the wireless channel features as a random source, without the need for key transmission [
1]. SK generation techniques rely on time-varying characteristic of the wireless channel. Therefore, in static environments, the keys cannot be updated quickly, which can eventually result in lower security protection.
The intelligent reflecting surface (IRS) has received a lot of attention in recent years, due to its capability of ameliorating the wireless channel environment through software-controlled reflections [
2]. Specifically, the IRS consists of a large number of low-cost passive reflecting elements, each can independently make changes to the incident signal [
2,
3], and thus it has great potential to increase the SK generation rate in real time [
4,
5,
6,
7]. Most of the current research works on IRS-assisted SK generation focused on optimization problems to maximize the SK generation rate or SK capacity at the legitimate user by optimizing the phase shift coefficients or using random phase shifting of IRS [
5,
6,
7].
For example, an IRS-assisted SK generation scheme was proposed in order to overcome the problem of low SK rate in a static environment, by using discrete phase shift [
5]. This scheme maximized the SK rate by optimizing the IRS phase switching time, but there was no implementation details such as quantization method for the estimated channel state information (CSI). On the other hand, phase shift optimization schemes for the IRS were proposed [
6,
7]. A lower bound on the SK capacity was derived for an IRS-assisted wireless network with multiple eavesdroppers, and an IRS reflection coefficient optimization framework was introduced [
6]. The design principle of IRS-assisted SK generation was proposed, and its performance improvement in SK rate was verified [
7].
However, both of the above two schemes incurred complexity compared with the random phase shifting scheme. Furthermore, a technique to maximize the SK capacity was introduced for SK generation process based on CSI, by adjusting the layout of the IRS elements [
8]. It also proposed the process of SK generation based on CSI, but there was no detailed description for each step.
On the other hand, a number of studies reported quantization methods used during the SK generation process [
9,
10,
11,
12,
13,
14]. Although binary quantization method is simple and easy to implement [
9], it can only generate a single SK bit. Multi-level equiprobable quantization methods were utilized to increase bit generation rate [
10,
11]. In this case, selecting the appropriate quantization levels and interval partitioning are crucial issues that require a trade-off between information preservation and SK length. For example, previous studies presented multi-level phase quantization (PQ) methods to increase SK generation rate [
12,
13,
14]. However, the complexity of quantization process is also increasing as the number of quantized bits. This is because the number of quantization levels is exponentially increasing with the number of quantized bits.
As a solution to the above mentioned problems of the existing works, this paper proposes an efficient IRS-assisted SK generation scheme with a computationally efficient PQ method. The first novelty of the proposed scheme lies in the hybrid method of extracting CSI for initial key generation. Phase information is first extracted from the direct channel, and then extracted from the combined channels with the IRS. This is because the IRS usually changes the phase of the reflecting signals almost without amplitude variations. This way of hybrid extraction of CSI from different channels will contribute to increasing the randomness of key generation, and eventually lead to the increment in SK generation rate. The second novelty of the proposed scheme is utilization of a new and computationally efficient PQ method to generate SK from the extracted CSI. We first form a new complex number by using the amplitude and phase information extracted from the proposed hybrid method, and then quantize the phase in the complex plane. This paper presents the details of extracting phase information from the estimated CSI of the proposed hybrid method. The proposed method is universally applicable to any m-level quantization method, and the quantization level can be adaptively regulated.
The remainder of this paper is organized as follows.
Section 2 describes the related works including the system model for an IRS-assisted SK generation and the conventional quantization methods.
Section 3 first presents the hybrid way of extracting CSI, and then details the proposed PQ method. In order to verify the merits of the proposed scheme,
Section 4 first presents a number of performance measures, and then provides the simulation results. Finally, the paper is concluded in
Section 5.
2. Related Works
2.1. System Model
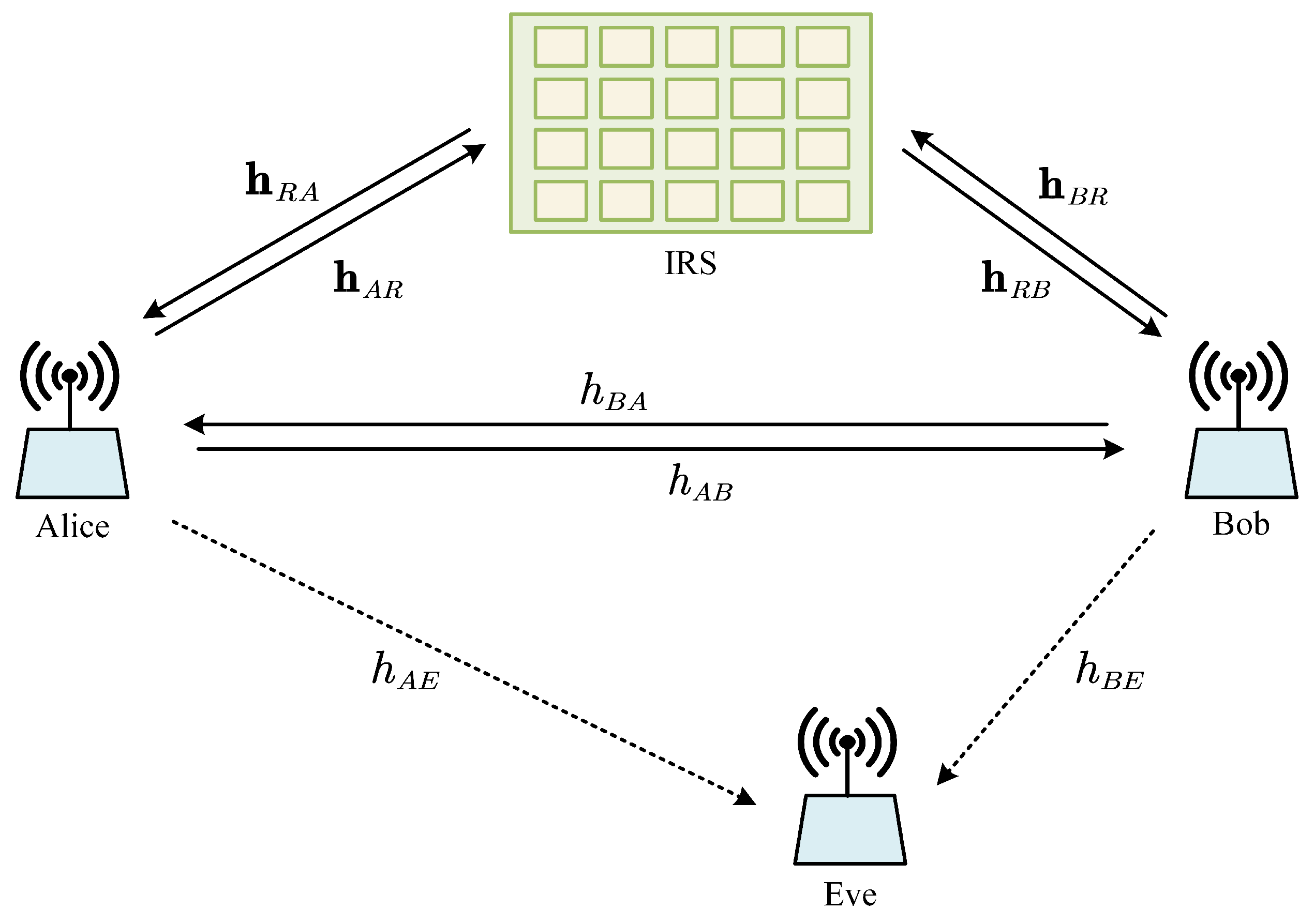
Figure 1 shows a system model for an IRS-assisted wireless communication system, where data transmission is encrypted with SK generated with the aid of IRS in order to achieve secure communications [
4]. The legitimate communication parties Alice and Bob send probe signals to each other in time-division duplex (TDD) mode, and extract SK from their correlated measurements before encrypted data transmission. Because the block fading channel remains constant during a long coherence time, an IRS is adopted to increase for randomness by configuring its phase shift. Each of
N reflecting elements receives a superimposed multipath signal from the sender and then reflects the signal in random phase, with a diagonal IRS phase shifting matrix
, where
is the phase shift of the
n-th element. The eavesdropper Eve is assumed to be a few wavelengths away from the legitimate users, so that Eve taps an eavesdropping channel that is independent of the legitimate channel. They are equipped with a single antenna.
In each block, Alice and Bob send the probe pilots alternatively to generate the SK during the first
L time slots of the coherence time. After key generation, the data is encrypted with the generated keys before its transmission during the remaining coherence time. The received signals at Alice and Bob in each probe round can be expressed as follows, respectively [
4,
15]:
where
and
are the CSIs of the direct channel from Alice to Bob and Bob to Alice, respectively,
and
are the CSI vectors from Alice and Bob to the IRS, and
and
are the reflected CSI vectors from the IRS to Alice and Bob, respectively. In addition,
is the probing signal vector sent by Bob and Alice, and
and
denote the complex additive white Gaussian noise (AWGN) at Alice and Bob, where
is the identity matrix.
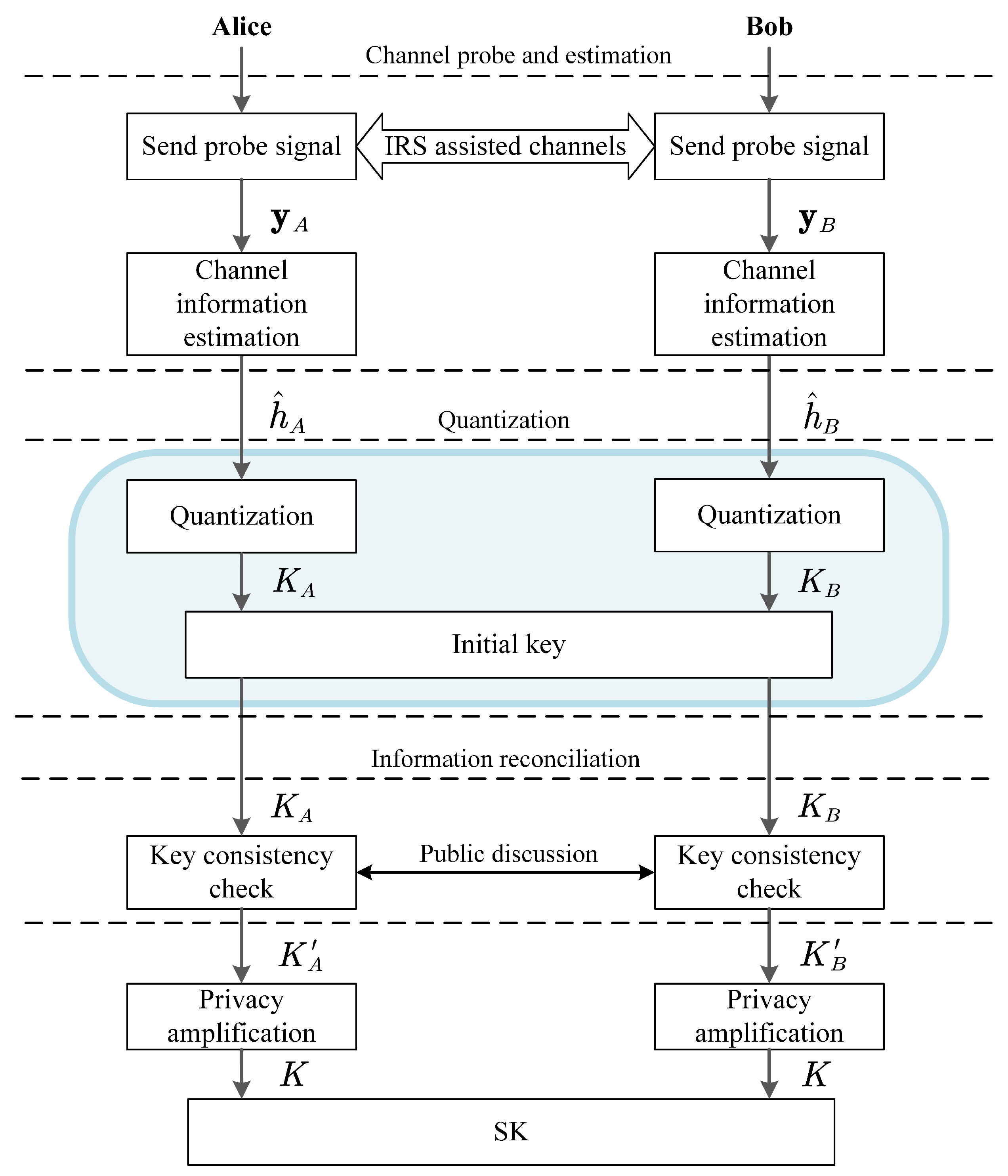
In this case, the channel estimates at Alice and Bob can be calculated from their reciprocally combined channels of the direct and reflected channels as follows:
where
and
denote the estimation errors at Alice and Bob, respectively. These channel estimates are used to generate SK at the quantization process, and the generated keys are used for information reconciliation as shown in
Figure 2. Finally, the privacy amplification algorithm based on hash function is applied to avoid information leakage [
8]. Through the above process, both communication parties complete the same key establishment.
2.2. Quantization of CSI
Based on the above channel estimates of
and
, the initial key value is generated by converting the estimated value to binary bits. There have been binary quantization methods, namely absolute value-based quantization (AVQ) and difference value-based quantization (DVQ) [
9]. Since these methods converts the channel estimates in to a single bit, SK rate becomes low.
Multi-level quantization methods can be used to increase SK rate [
10,
11,
12,
13,
14]. For example, an equiprobable quantization method was proposed [
10], given the probability density function (PDF) of the input signal
x, the decision thresholds for the
m-level quantization method was determined as follows:
where
is the PDF of
x,
is the
i-th decision threshold,
. By this way, each of
m quantization regions, i.e.,
is selected with equal probability, and it is mapped to
bits using Gray coding. Furthermore, a method to improve bit agreement ratio was proposed by inserting guard bands between two consecutive quantization levels [
11]. We note that the complex numbered CSI does not have a uniform distribution, and thus
cannot be simply determined. This eventually leading to a complex quantization problem.
Since the phase information of the CSI has uniform PDF, quantization of the phase may lead to a simple quantization process. A PQ method was proposed by using a uniform quantization method for a phase information of the channel estimates [
12]. Furthermore, a phase shift quantization method which is similar to phase shift keying (PSK) demodulation method was proposed [
13]. This method quantized the phase value,
with a
m-level uniform quantizer as follows [
14]:
for
. Therefore, the quantization of each phase value generates
secret bits. In order to extract
bits, the above quantization method requires of 1 to
m comparison operations, and thus average
operations per extracted CSI.
3. Proposed Methods
3.1. SK Generation Protocol
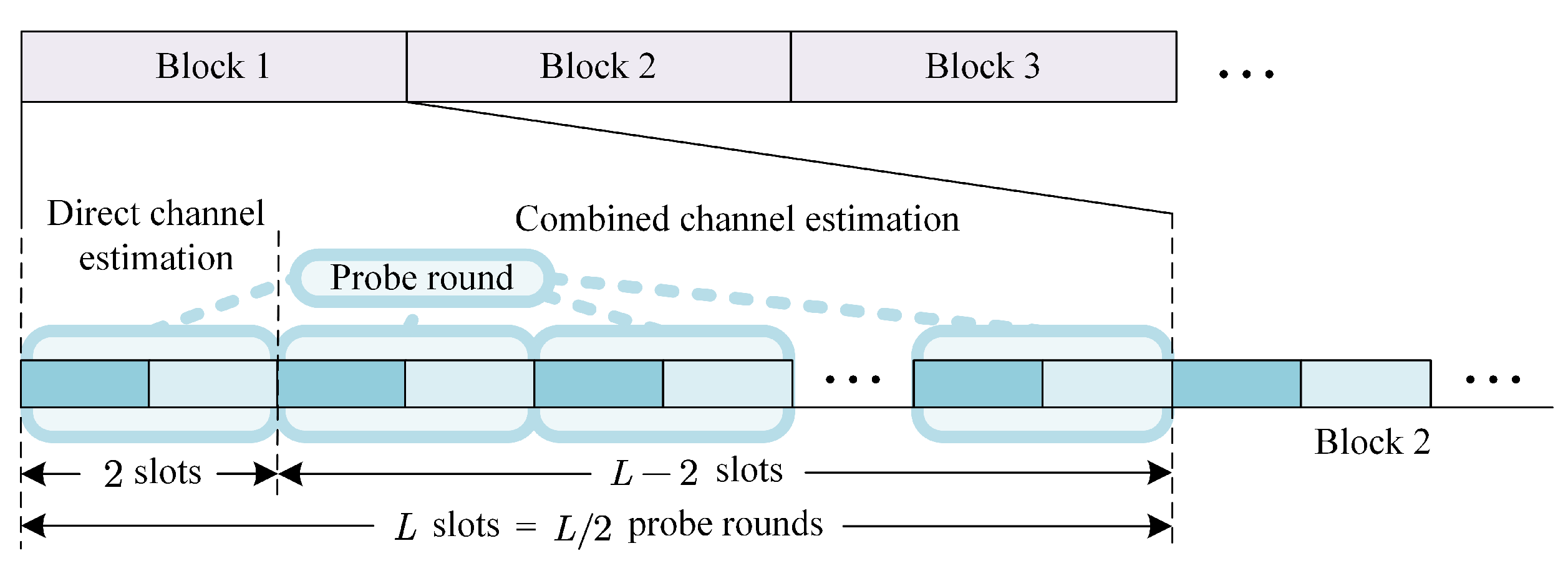
In order to fully exploit the randomness, we propose a hybrid approach to extracting CSI in order to generate the SK, as shown in
Figure 3. In each block, there are total
L time slots, and we assume that the channel does not change within a block, i.e., the length of each block is equivalent to the coherence time of the channel. In addition, Alice and Bob alternatively send probe signals every two time slots, and thus there are total
probe rounds in each block. Specifically, in the first probe round, Alice and Bob alternatively send probe signals while the IRS is turned off. Then, the received signals at Alice and Bob can be expressed as follows, respectively:
Upon receiving
and
in (
5) at Alice and Bob, respectively, channel estimations are conventionally performed using the least square (LS) method, and the channel estimates at Alice and Bob can be presented as follows [
6]:
The phase information of these channel estimates will be jointly quantized to form the initial key bit sequence.
Afterwards, Alice and Bob alternatively extract the channel estimates from the combined channels which are composed of the direct and reflected channels, using (
2) during the subsequent
time slots. In this case,
is randomly switched at every 2 time slots to impose randomness. Similarly, the phase information of these channel estimates with linear normalization will be jointly quantized to generate the initial key bit sequence. The detailed process of the quantization for the proposed method is explained in the next section.
3.2. Compact Phase Quantization Method
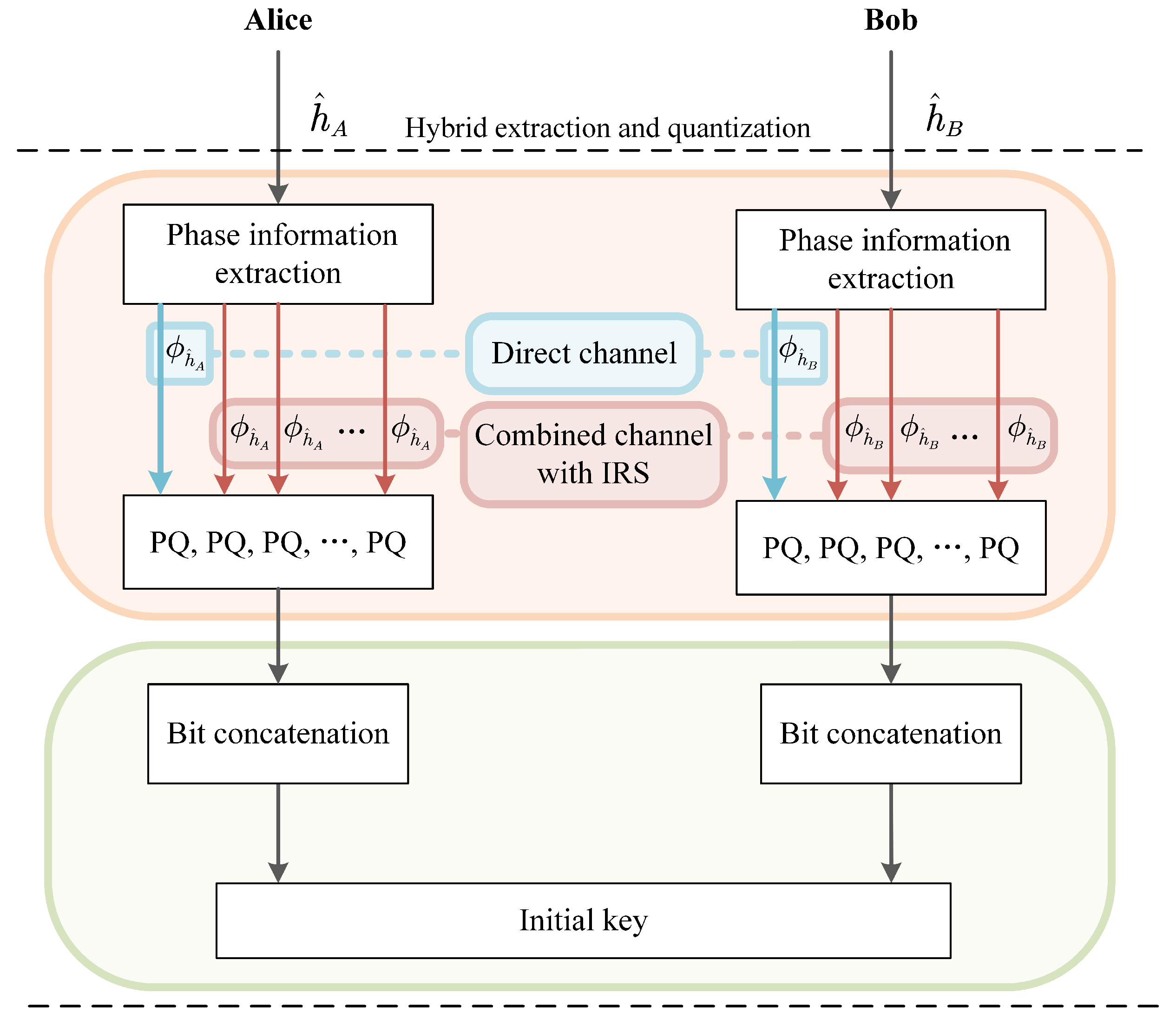
We propose a new efficient
-level PQ method using the phase information of
and
in (
2) and (
6) to generate
p quantized bits, respectively, as shown in
Figure 4. We set quantization thresholds which equally divide the complex plane into
regions, and allocate
p bits in each region by using the Gray coding, which allows to extract
p bits from the phase information.
We note that the main purpose of the proposed hybrid CSI extraction is to compensate low SK rate during the static environment, by using an efficient quantization method. Since we assume low amplitude variation of
, the IRS is activated to impose phase dynamics of the CSI. This implies that it is not necessary to allocate multiple bits to amplitude in the channel probing stage. Instead, multiple bit allocation to phase information obtained from IRS would contribute to increase the dynamics of the CSI. In addition, phase information is uniformly distributed from 0 to
, PQ would provide better randomness than AQ to secrete key information. Therefore, we extract phase information in the total time slots. It is also important to have computationally efficient quantization methods, i.e., a compact and easily extendable method. Considering the above facts, we refer to the constellation diagrams of PSK. modulation scheme with Gray coding and its soft demapping principle introduced in [
16], and tailor them for our purpose.
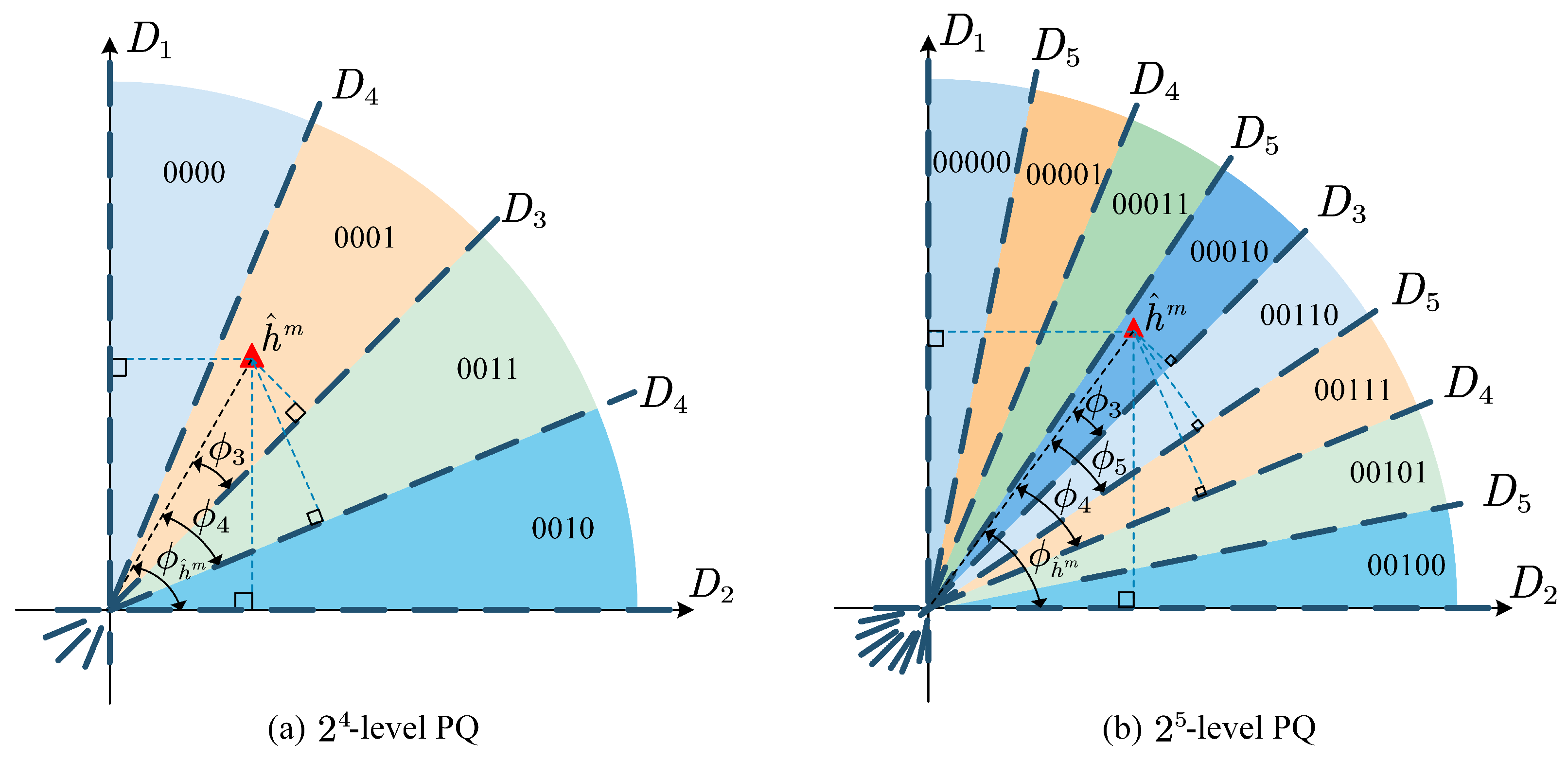
In order to visualize the PQ, we represent the extracted CSI of and as and , respectively, where is the amplitude, is the phase, is the real part, and is the imaginary part of the complex number x, respectively. We equally divide the complex plane into separated phase regions. In the following sections, we present the proposed PQ examples of 4 to 32 levels, and this can be extendable to any -level schemes.
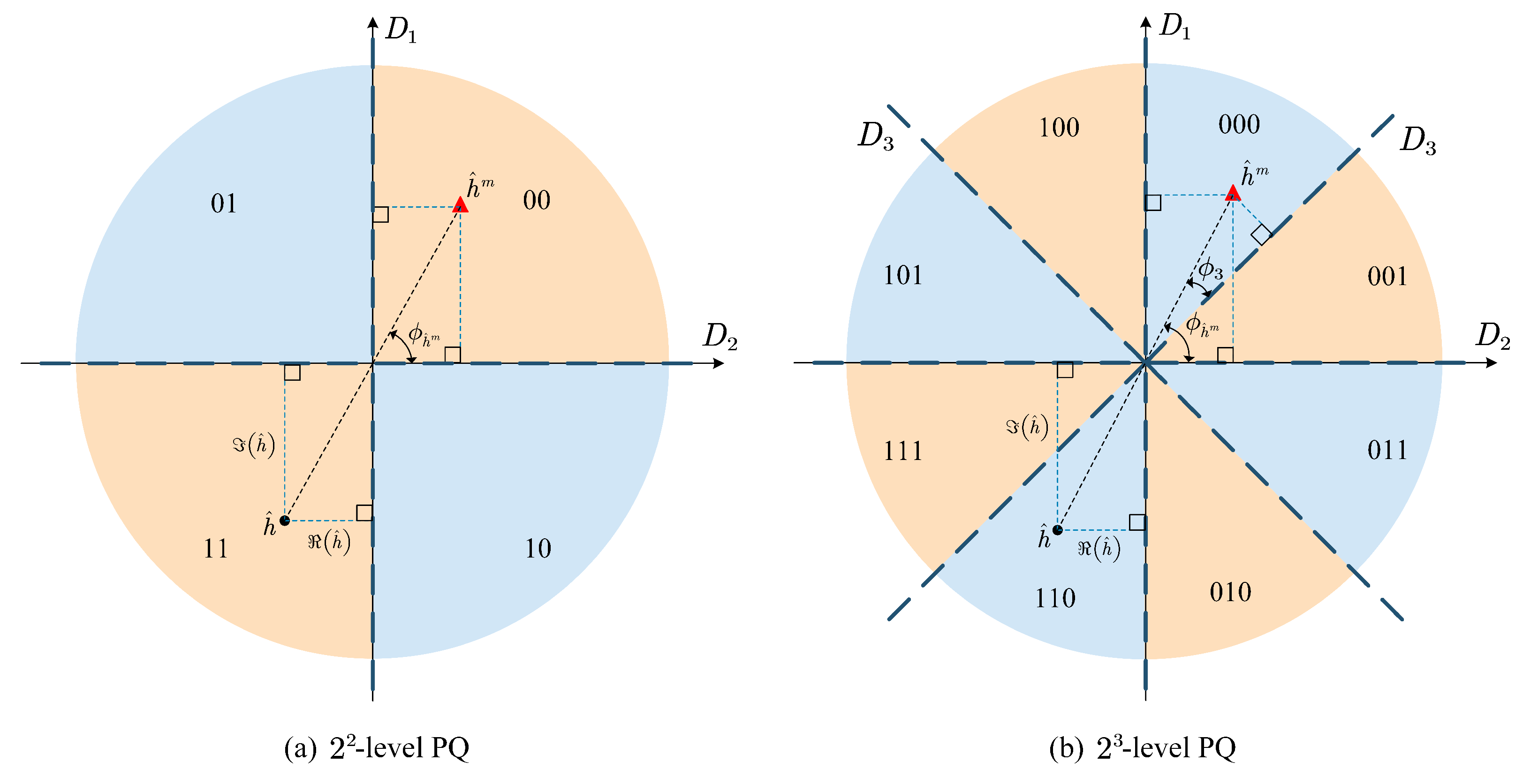
3.3. Examples of 4 to 32 Level PQ
For a
-level PQ, the quantization bit mapping is made by Gray coding principle. For convenience, here we denote the estimated CSI of either Alice or Bob as
, because the quantization processes for
and
are the same.
Figure 5 shows the bit mapping and decision threshold lines for
and
-level PQ methods for the estimated CSI,
in the complex plane, where
indicates the decision threshold for the
i-th quantized bit
.
Referring to
Figure 5, we can find that the first and second bits can be estimated by taking the signs of real and imaginary parts of
, i.e.,
and
. Then, these
and
provides sufficient information on in which quadrant of the complex plain
locates. By using this, we map
in the first quadrant of the complex plain, that is
, where
, so that its phase value is in the region of 0 to
. This makes the third bit of
-level PQ can be estimated by taking the sign of the distance between the threshold line
to
located in the first quadrant, that is,
The above principle, then can be extended to any
-level PQ.
Figure 6 shows the bit mapping with Gary coding and decision threshold lines for
and
-level PQ methods, where
is mapped in the first quadrant of the complex plane. It is clear that
to
can be estimated exactly the same way as in the above
and
-level PQ method. In addition, the remaining bits can be estimated recursively by using the previously estimated information. For example,
.
By generalizing the above principle to
-level PQ, we can have the following recursive equation:
where
. The following Algorithm 1 describes the proposed PQ method. After the quantization process, the quantized bits are concatenated together to obtain the initial key bit sequence for Alice and Bob, respectively.
|
Algorithm 1:Proposed PQ |
- 1:
- 2:
- 3:
- 4:
- 5:
fordo
- 6:
- 7:
- 8:
end for
|
We note that the proposed PQ in Algorithm 1 can be applied any p bit PQ scheme, and thus a single quantizer can be universally applied to various multi-level quantization systems. In particular, when we adopt an adaptive quantization scheme to generate a time-varying p bits, the proposed scheme may have a strong advantage for its universal applicability.
4. Secrecy Performance
4.1. Performance Measures
We evaluate the proposed SK generation scheme in terms of a number of secrecy performance measures including the SK capacity, SK randomness, initial key disagreement probability, and effective key length. All of the above performance measures of the proposed schemes are compared with those of the conventional schemes.
The SK capacity,
C is defined as
, where
denotes the estimated CSI at Eve. Since the channel estimates in different probe rounds are independent random variables [
4], the SK capacity in the
s-th probe round,
is also a random variable. Assuming the eavesdropper Eve is a wavelength or more away from either Alice or Bob, the SK capacity in the first probe round without IRS,
is upper bounded by the mutual information [
10,
17]:
In this case, due to the channel reciprocity within the coherent time, we have
. In addition, we can assume that
and
are independent and identically distributed random variables without loss of generality, and thus
. Therefore, (
9) can be simplified as:
The SK capacity in the remaining probe rounds with IRS,
,
, is upper bounded by the conditional mutual information [
10,
17]. In this case, we have
, where
is the variance of the
n-th reflected channel. Thus,
can be derived as follows [
8]:
The above derivation result shows that the SK capacity of the proposed system is certainly dependent on , and it is proportional to N. Therefore, we can expect the enhanced SK capacity in the proposed system due to the increased randomness introduced by the IRS.
Finally, the SK capacity of the proposed scheme,
across all
L slots is upper bounded as follows [
15]:
On the other hand, the SK capacity of the conventional scheme without IRS, is upper bounded by .
The second performance measure to be investigated is the SK randomness which is defined as the proportion of ’1’ in the generated binary initial key bit sequence, thus we have:
where
is the total number of investigated probe rounds for the estimation. The closer to 0.5 the
r, the better the randomness of the key. In other word, when the proportion of ’1’ and ’0’ in the key sequence is uniform, the randomness of the key is better.
The third performance measure is the initial key disagreement probability. Suppose that Alice and Bob convert each of their estimations
and
to
and
, respectively, then the initial key disagreement probability,
is the probability of inconsistent bits between Alice and Bob. Therefore, it is defined as the ratio of the number of inconsistent bits to the key sequence length as follows:
The last performance measure is effective key length
(bits/block). It describes the length of error-free SK that can be generated per block, and it can be represented as follows:
4.2. Simulation Results and Discussions
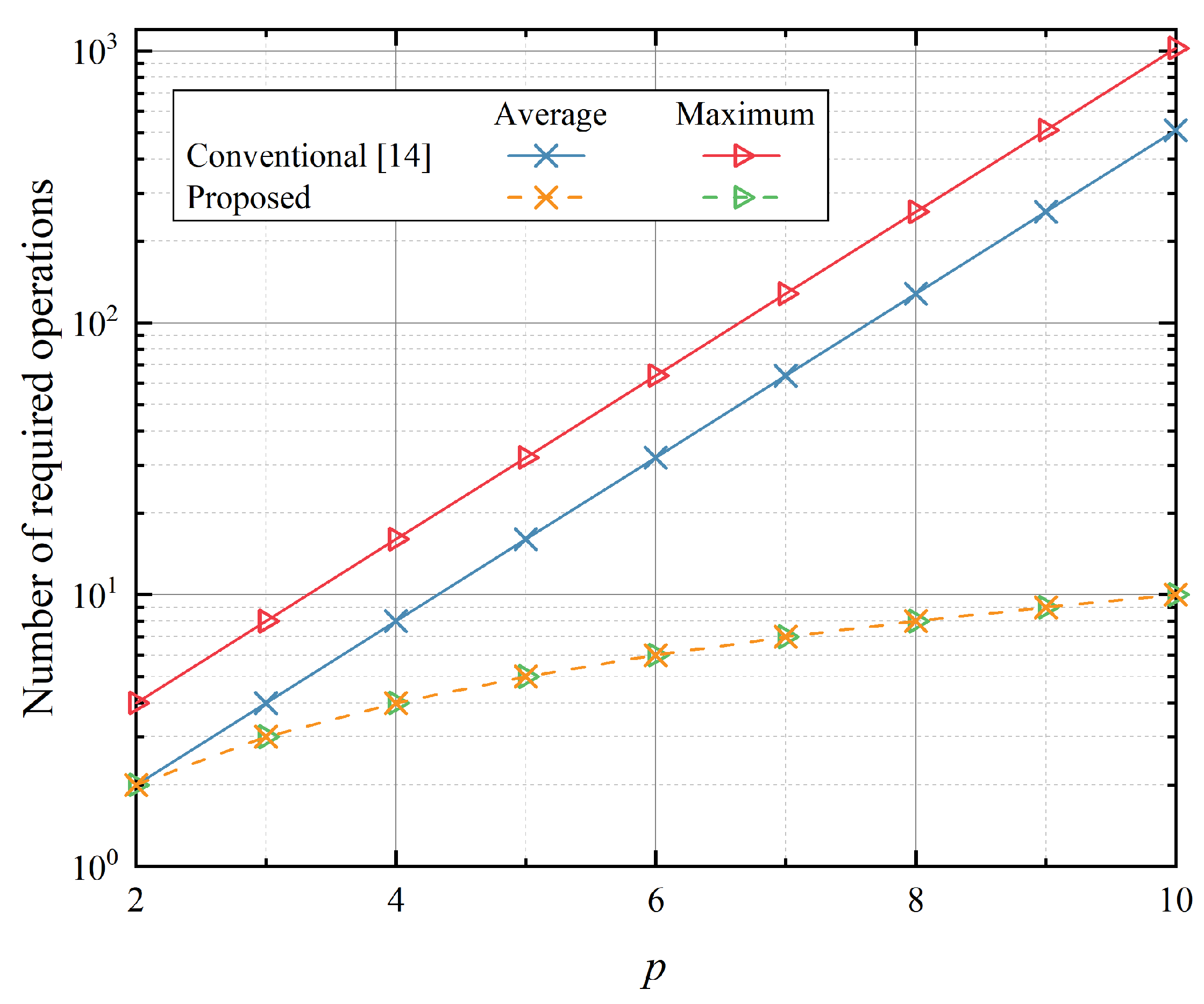
Before we compare the secrecy performance measures presented in the previous section, the computational complexities of the proposed and conventional PQ methods are compared in terms of the number of the required operations for PQ. As shown in
Table 1 the proposed method requires linearly increasing complexity by
p, and it requires a constant number of operations regardless of the estimated CSI value. On the other hand, the conventional PQ method requires exponentially increasing complexity by
p, and it requires one to maximum of
comparisons, resulting in
comparisons on average.
Figure 7 illustrates this.
We simulate the secrecy rate of various quantization method, as shown in Fig. **/Table **.
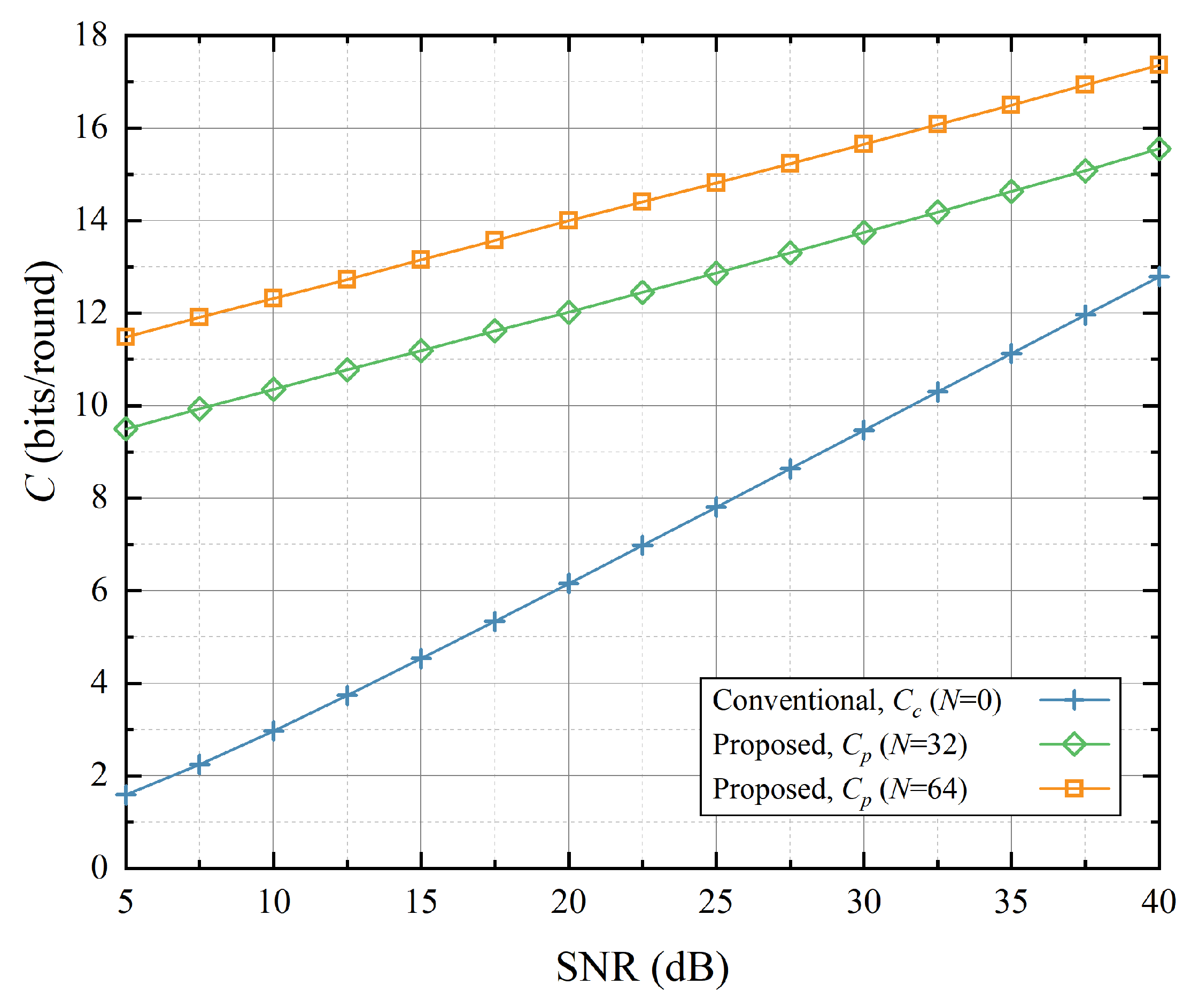
Next, we compare performance simulation results of the proposed scheme to that of the conventional schemes. First,
Figure 8 shows the SK capacity variation by signal-to-noise ratio (SNR). It is evident that the SK capacity of the proposed scheme with IRS assistance is higher than the conventional one, and the SK capacity increases with an increase in the number of IRS elements
N.
Second,
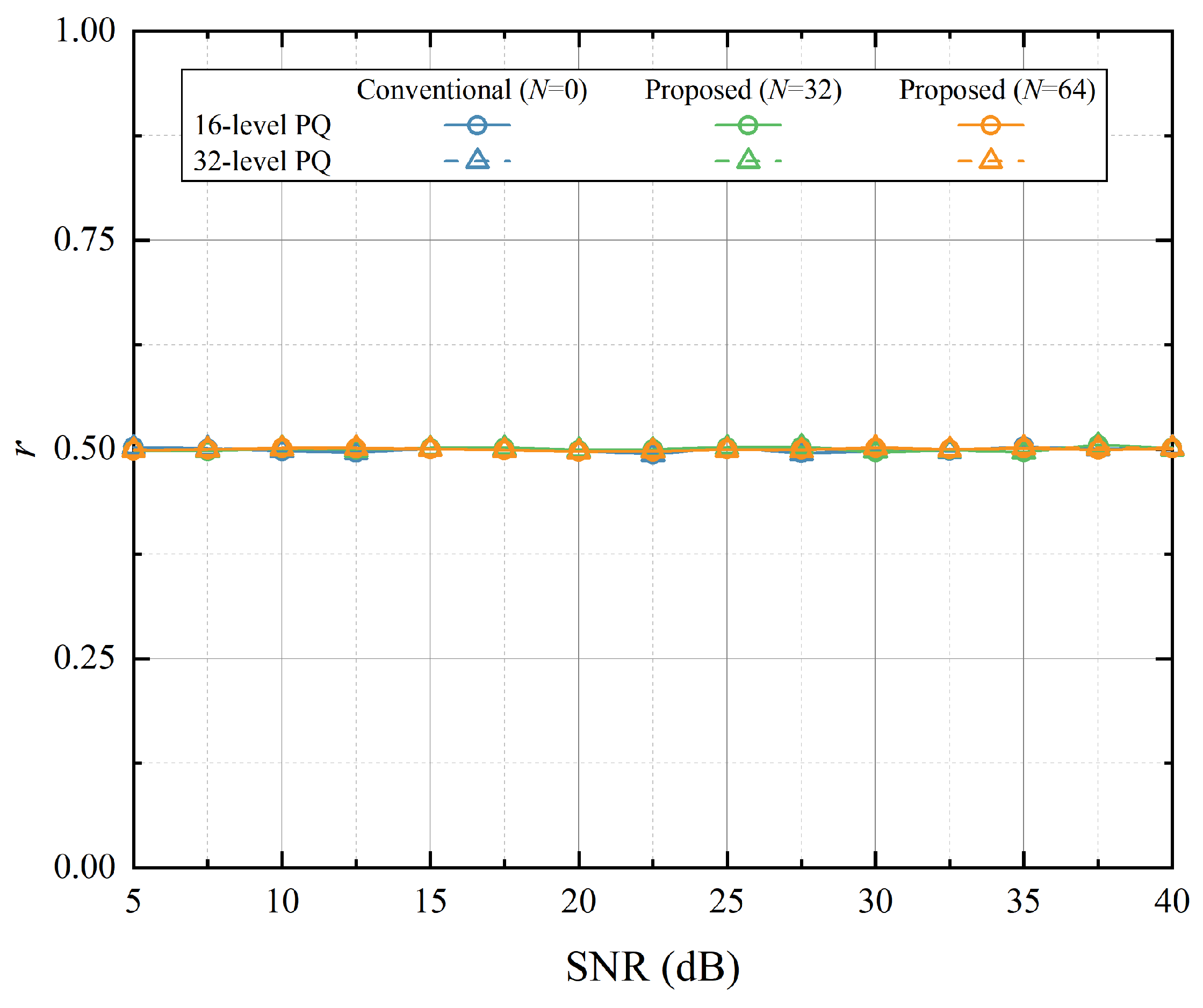
Figure 9 compares the SK randomness,
r. We can see that the SK randomness of the all PQ methods remains stable, showing almost a constant value of about 0.5 across all the investigated SNR ranges. In other words, the assistance of IRS in the proposed mehtod does not alter randomness performance. This is primarily due to the property of PQ having a uniform PDF and its quantization regions being equally probable and uniformly distributed. Consequently, both ’1’ and ’0’ are uniformly quantized, leading to the preservation of SK randomness.
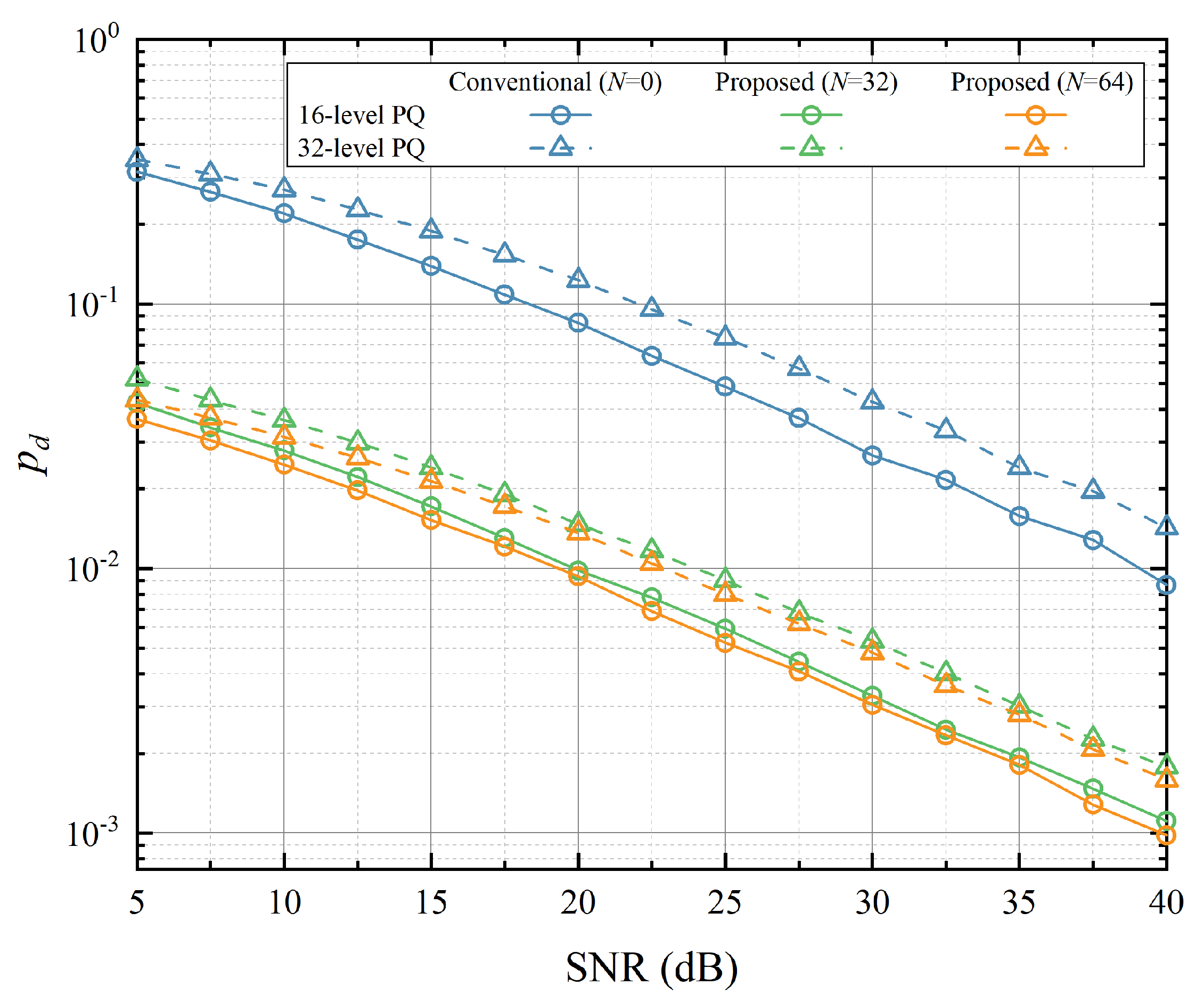
Figure 10 compares the initial key disagreement probabilities. As shown in the figure, the lower the quantization level, the smaller the initial disagreement probability. Giving the quantization level, the proposed PQ outperforms the conventional PQ method without IRS. It can also be seen that as the number of IRS elements
N increases, the disagreement probability decreases.
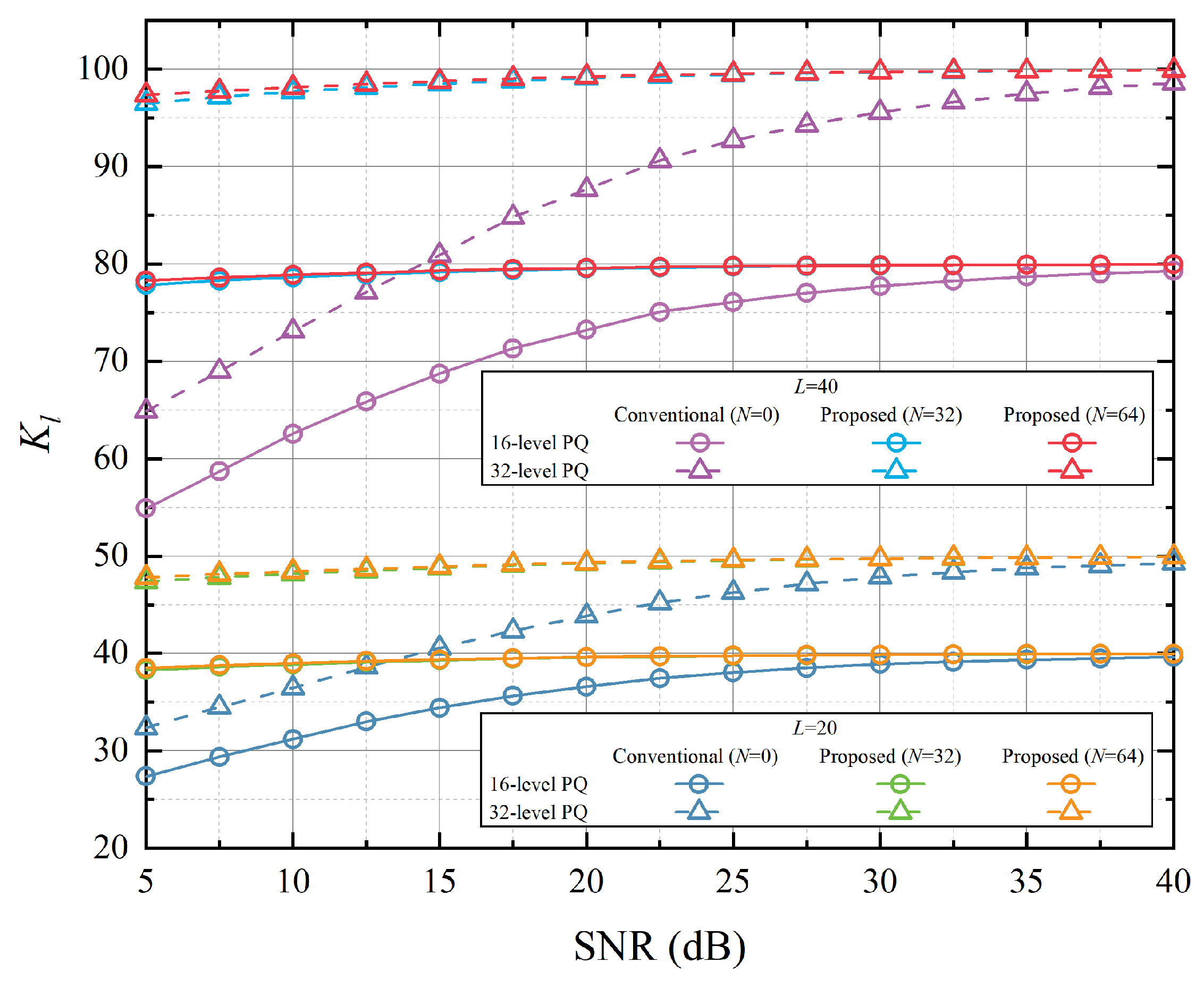
Figure 11 compares the effective key length,
of the proposed method with that of the conventional method, when the number of probe rounds is set to 10 and 20, i.e.,
and
. It is evident that higher quantization levels result in longer effective key length. Furthermore, when compared to the conventional PQ without IRS, as
L increases, our proposed scheme with IRS demonstrates superior performance, with its effective key length increasing with the rise of
N. In the static environment, the channel features extracted by Alice and Bob have low correlation and high initial key disagreement rate, thus affecting the effectiveness of the subsequent information reconciliation stage. Configuring the IRS as a new random source and extracting phase information means that our proposed scheme can obtain initial keys with a lower key disagreement probability, making information reconciliation easier to achieve during SK generation.
5. Conclusions
In this paper, we proposed an efficient IRS-assisted physical layer SK generation scheme with random phase shifts in static environment. By extracting the phase information from the combined channel estimation from both sides of the legitimate communication parties, a better random key sequence can be generated. Specifically, this paper proposed a simple and computationally efficient PQ method by using a symmetric bit allocation, which can be easily extended to any -level quantization scheme and can be universally applied. Simulation results demonstrated that the proposed scheme can improve various performance measures including the SK capacity, effective key length, and the SK disagreement probability, without sacrificing the randomness.
Funding
This research was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (NRF-2021R1A2C1003121).
Data Availability Statement
Not applicable.
Acknowledgments
The authors extend their appreciation to the Yangzhou University Graduate International Academic Exchange Fund Project (YZUF2022204) and the Young Backbone Teachers Project of Yangzhou University.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| SK |
Secret key |
| CSI |
Channel state information |
| IRS |
Intelligent reflecting surface |
| PQ |
Phase quantization |
| TDD |
Time-division duplex |
| AWGN |
Additive white Gaussian noise |
| AVQ |
Absolute value-based quantization |
| DVQ |
Difference value-based quantization |
| PDF |
Probability density function |
| PSK |
Phase shift keying |
| LS |
Least square |
| SNR |
Signal-to-noise ratio |
References
- Maurer, U.M. Secret key agreement by public discussion from common information. IEEE Trans. Inf. Theory. May. 1993, 39, 733–742. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Towards smart and reconfigurable environment: Intelligent reflecting surface aided wireless network. IEEE Commun. Mag. Jan. 2019, 58, 106–112. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Beamforming optimization for wireless network aided by intelligent reflecting surface with discrete phase shifts. IEEE Trans. Commun. Mar. 2019, 68, 1838–1851. [Google Scholar] [CrossRef]
- Ji, Z.; Yeoh, P.L.; Chen, G.; Pan, C.; Zhang, Y.; He, Z.; Yin, H.; Li, Y. Random shifting intelligent reflecting surface for OTP encrypted data transmission. IEEE Wireless Commun. Lett. Jun. 2021, 10, 1192–1196. [Google Scholar] [CrossRef]
- Hu, X.; Jin, L.; Huang, K.; Sun, X.; Zhou, Y.; Qu, J. Intelligent reflecting surface-assisted secret key generation with discrete phase shifts in static environment. IEEE Wireless Commun. Lett. Sep. 2021, 10, 1867–1870. [Google Scholar] [CrossRef]
- Ji, Z.; Yeoh, P.L.; Zhang, D.; Chen, G.; Zhang, Y.; He, Z.; Yin, H.; et al. Secret key generation for intelligent reflecting surface assisted wireless communication networks. IEEE Trans. Veh. Technol. Jan. 2021, 70, 1030–1034. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, M.; Xu, J.; Gong, S.; Hoang, D.T.; Niyato, D. Boosting secret key generation for IRS-assisted symbiotic radio communications. In Proceedings of the 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring). IEEE; 2021; pp. 1–6. [Google Scholar]
- Lu, X.; Lei, J.; Shi, Y.; Li, W. Intelligent reflecting surface assisted secret key generation. IEEE Signal Process. Lett. 2021, 28, 1036–1040. [Google Scholar] [CrossRef]
- Zhang, J.; Rajendran, S.; Sun, Z.; Woods, R.; Hanzo, L. Physical layer security for the Internet of Things: Authentication and key generation. IEEE Wireless Commun. 2019, 26, 92–98. [Google Scholar] [CrossRef]
- Ye, C.; Reznik, A.; Shah, Y. Extracting secrecy from jointly Gaussian random variables. In Proceedings of the 2006 IEEE International Symposium on Information Theory. IEEE; 2006; pp. 2593–2597. [Google Scholar]
- Zeng, K.; Wu, D.; Chan, A.; Mohapatra, P. Exploiting multiple-antenna diversity for shared secret key generation in wireless networks. In Proceedings of the 2010 Proceedings IEEE INFOCOM. IEEE; 2010; pp. 1–9. [Google Scholar]
- Sayeed, A.; Perrig, A. Secure wireless communications: Secret keys through multipath. In Proceedings of the 2008 IEEE International Conference on Acoustics, Speech and Signal Processing. IEEE; 2008; pp. 3013–3016. [Google Scholar]
- Shehadeh, Y.E.H.; Alfandi, O.; Tout, K.; Hogrefe, D. Intelligent mechanisms for key generation from multipath wireless channels. In Proceedings of the 2011 Wireless Telecommunications Symposium (WTS). IEEE; 2011; pp. 1–6. [Google Scholar]
- Wang, Q.; Su, H.; Ren, K.; Kim, K. Fast and scalable secret key generation exploiting channel phase randomness in wireless networks. In Proceedings of the 2011 Proceedings IEEE INFOCOM. IEEE; 2011; pp. 1422–1430. [Google Scholar]
- Lu, T.; Chen, L.; Zhang, J.; Cao, K.; Hu, A. Reconfigurable Intelligent Surface Assisted Secret Key Generation in Quasi-Static Environments. IEEE Commun. Lett. 2021, 26, 244–248. [Google Scholar] [CrossRef]
- Zhang, M.; Kim, S. Universal soft demodulation schemes for M-ary phase shift keying and quadrature amplitude modulation. IET Communications 2016, 10, 316–326. [Google Scholar] [CrossRef]
- F. Rottenberg, T. Nguyen, J.D.F.H.; Louveaux, J. CSI-Based Versus RSS-Based Secret-Key Generation Under Correlated Eavesdropping. IEEE Trans. Commun. 2021, 69, 1868–1881. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).