Highlights from the Workshop
During the opening remarks, a representative from BEP (USA) highlighted that the BEP is fully committed to engaging scientists and combating biological threats worldwide by assisting in improving biosecurity, bioprotection, and pathogen surveillance. BEP delegate also emphasized that all stakeholders must work together to build sustainable capacity in biosecurity, disease surveillance, and scientific investigation.
Because of the physical properties of biological toxins and easy accessibility, biotoxins (aka zootoxins) have become attractive targets of nefarious actors [
10]. While discussing toxins and venoms research from a national security perspective, an SME highlighted that tight regulation is essential, as a tiny amount of toxins could kill millions and millions of people. SME also underlined that synthetic biology and biotechnology tools could be misused for the large-scale production of toxins, to make them more lethal, or to create a novel toxin. Toxins and venoms could be purchased or stolen from research laboratories or vendors or made in the do-it-yourself (DIY) laboratory – SME accentuated.
While deliberating dual-use materials, expertise, data, and equipment protection needs, an SME highlighted that United States Government policy for oversight of life sciences dual-use research of concern and policy for institutional oversight of life sciences dual-use research of concern could serve as a model for national oversight and institutional oversight, respectively. For assessing and managing risks associated with toxins and venoms, SME suggested that researchers and stakeholders from toxins and venom research laboratories should have answers to basic questions such as: Could this research yield information that could be intentionally misused to threaten public health, safety, and security? What is the nature of the threat and potential consequences? What is the likelihood that harm can be done? Do the potential risks outweigh the potential benefits?
During deliberating the dual-use material potential of various toxins and venoms, an SME pointed out that biological toxins (biotoxins) and venoms are the potential tools for bioterrorism. SME also highlighted that the main objective of dual-use research governance is to reduce accidents and incidents and enable their early detection and response, which could reduce future opportunities for misuse of research, tools, and knowledge without hindering the benefits of life science research.
Venom research is essential to understand venom evolution, its ecological impact, how venoms work, and search for novel biomolecules that could serve as precursors in developing new drugs and therapeutic applications. One of the SMEs shared a comprehensive overview of snake venom research in Malaysia and highlighted that snake venom research is essential for the benefit of humanity, as it facilitates the development of innovative treatments (e.g., synthetic antibodies, broad-spectrum antivenoms, small molecule inhibitors), diagnostic tools, and new therapeutic agents (e.g., anticancer, anticoagulant, antiplatelet, antiinfective, analgesics, antihypertensive, heart failure, etc.). During the deliberations, the participants learned the importance of protecting venom, cDNA/DNA clones, plasmid DNA, gene expression cassettes, and disposal of biowaste and biosecurity-sensitive materials from the venom research facilities.
Pore-forming toxins (PFTs) are a class of proteins produced by various bacteria, fungi, and other organisms [
11]. PFTs can cause tissue damage, organ failure, and even systemic effects. Not all PFTs are harmful to humans; however, dangerous PFTs could be misused by nefarious actors. An SME shared a comprehensive overview of the PFTs family, including Anthrax toxin (
Bacillus anthracis), lota toxin (
Clostridium perfringens), Tc toxin (
Photorhabdus luminescens), VCC toxin (
Vibrio cholerae), and 𝛂-Hemolysin (
Staphylococcus aureus), and highlighted that understanding the mechanisms and effects of these toxins is crucial for developing strategies to prevent and treat associated illnesses and to mitigate the biosecurity risks.
To inculcate the importance of identifying and mitigating insider and outsider threats, an SME discussed toxin scenario-based case studies and highlighted the importance of laboratory biosecurity oversight in protecting biotoxins (e.g., Botulinum, Mycotoxins, Saxitoxin, Neosaxitoxin, Abrin, Ricin, etc.) and venoms (aka zootoxins) to mitigate the risks. SME also stated that timely identification of the gaps in toxins and venom research laboratories' biosecurity program would help avoid disasters. Through scenario-based discussions, participants learned to identify the common gaps in laboratory biosecurity risk management and recognized the biosecurity threats from toxins and venoms.
In order to mitigate the biosecurity risks at toxins and venom (as well as other life sciences) research facilities, all laboratorians must be familiar with the eight pillars of biosecurity. While deliberating about how to secure toxins and venom-related dual-use materials, expertise, data, and equipment, an SME highlighted that by adhering to the eight pillars of biosecurity (biosecurity awareness, personnel reliability, physical security, material control and accountability, transport security, information security, emergency response, and management), we could strengthen our preparedness, response capabilities, and resilience in the face of biosecurity threats. From one health perspective, the SME also highlighted the importance of biosecurity best practices in safeguarding dual-use biological materials, equipment, and knowledge.
While sharing thoughts on the responsibility of scientists working with dual-use materials, an SME highlighted that researchers working with dual-use materials have a special responsibility to ensure the ethical and responsible use of their research and knowledge. Dual-use materials imply substances, technologies, data, or knowledge that can have both beneficial and potentially harmful applications. It is vital for researchers to recognize the potential risks associated with toxins, venoms, and their work and take appropriate measures to minimize associated biosecurity risks – participants learned.
To ensure appropriate measures are in place, life sciences research organizations must have an
Insider Threat Program. In this line, during deliberations on identifying and preventing insider threats, an SME highlighted that we should not ignore insider threats, as legitimate access to materials, equipment, and information could be misused to cause damage or harm to staff, the organization, or the community. SME also stated that personal risk factors (e.g., conscience, connections, ego, financial, ideology, lifestyle, nationalism, etc.), work-related risk factors (e.g., performance, violations, security weakness, etc.), and targeting risk factors (e.g., foreign travel, exposure, knowledge, and access, etc.) must be considered while identifying and preventing insider threat. Troubled insiders tend to behave in ways that can give cause for concern; hence, understanding behavioral queues is essential to identifying insider threats – workshop participants learned.
From a biosecurity perspective, identifying and preventing the exploitation of research collaboration is crucial. In this line, during deliberation on how to identify and prevent exploitation of research collaboration, one of the SMEs highlighted that establishing clear expectations, promoting open communication, and addressing potential issues early on help in protecting researchers and their organizations. SME also highlighted that meticulous due diligence (DD) and know-your-customer (KYC) best practices help in identifying red flags to avoid exploitation by nefarious actors or their proxies.
Physical security and access control are crucial for protecting toxins, venoms, biological agents, and biosecurity-sensitive material, equipment, and knowledge from laboratories for several reasons. In this line, an SME discussed the importance of physical security and access control and highlighted that physical security and access control are critical components in ensuring the safe handling, storage, and protection of valuable assets, including toxins, venoms, and biological agents.
A meticulously maintained inventory of organizations' valuable assets is crucial to mitigate biosecurity risks. Inventory encompasses the assortment of merchandise or substances an organization maintains, encompassing toxins, venoms, biological agents, chemicals, and infective or toxic materials such as tissues, tissue extracts, and DNA/RNA/protein samples. One of the SMEs highlighted that inventory, material accountability, and information security are essential for every life sciences research organization to ensure biosecurity. SME underlined the importance of recognizing no one-size-fits-all, considering the operating environment (e.g., the chain of custody, fieldwork, physical security), involving IT and security teams to advise, evaluating the needs and feasibility of the organization’s goals, and observing odd behaviours of laboratorians and stakeholders.
Prevention is always better than cure. In this line, robust preventive measures (deter, detect, delay) are always better than reactive measures (respond, recover) to mitigate biosecurity risks. However, we need to remember that adversaries have the means, motives, and capabilities to cause harm. Therefore, life sciences research organizations’ emergency response teams (ERT) should be competent and well-equipped. During deliberation on emergency and incident response, an SME highlighted that the red teaming exercise is very helpful in identifying if there are any biosecurity vulnerabilities in the organization. Red teaming exercise could be used to discover weaknesses in development and testing processes, assess internal employees' awareness about information security, understand the impact of a security breach, and test the information environment, team’s incident response capabilities, security controls, and organization’s ability to protect critical assets from real-world attacks – participants learned.
Life sciences research organizations and researchers started recognizing the importance of cyberbiosecurity [
12], as it addresses the emerging threats [
13] and vulnerabilities associated with the increasing use of digital systems, data [
14], and biotechnologies [
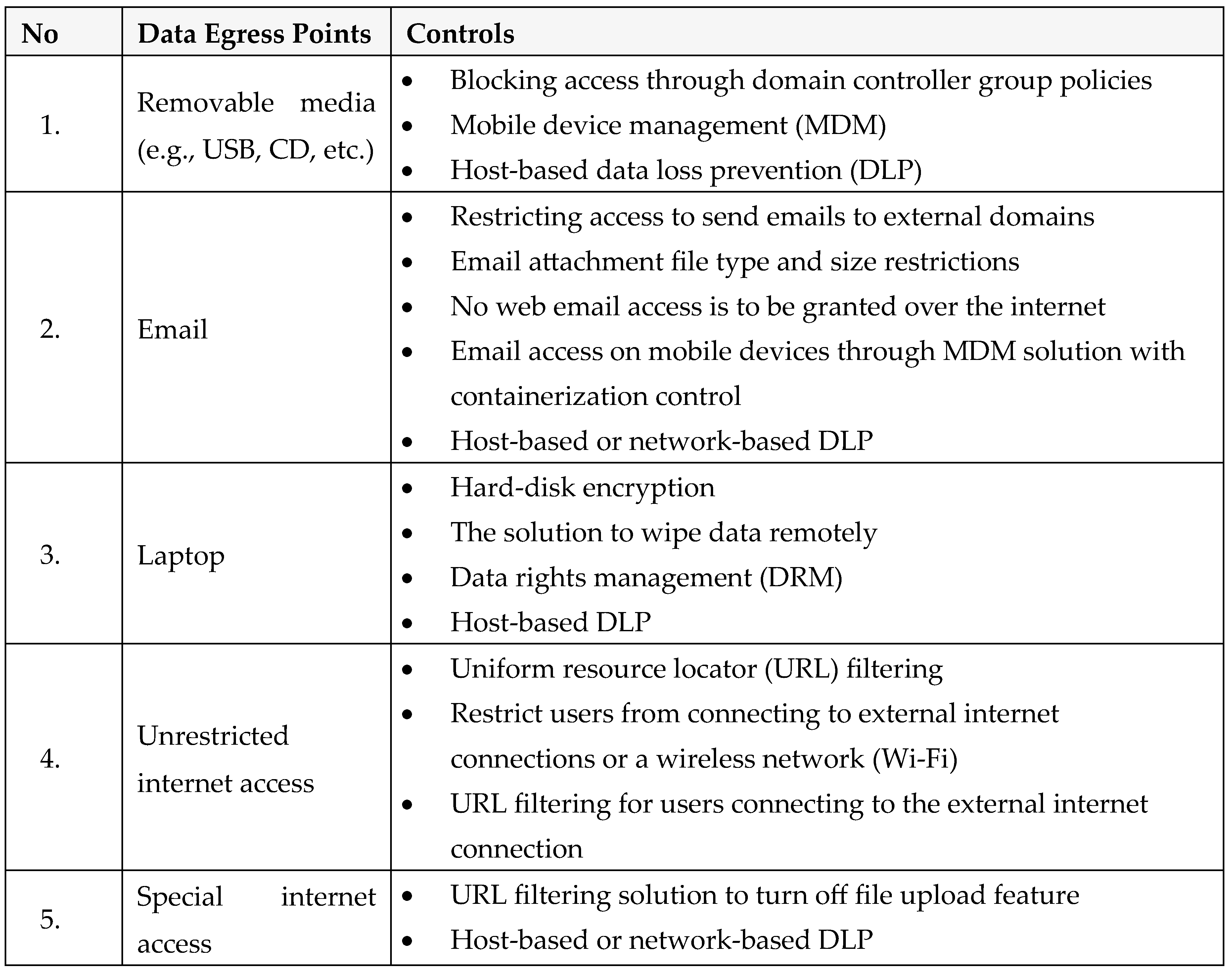
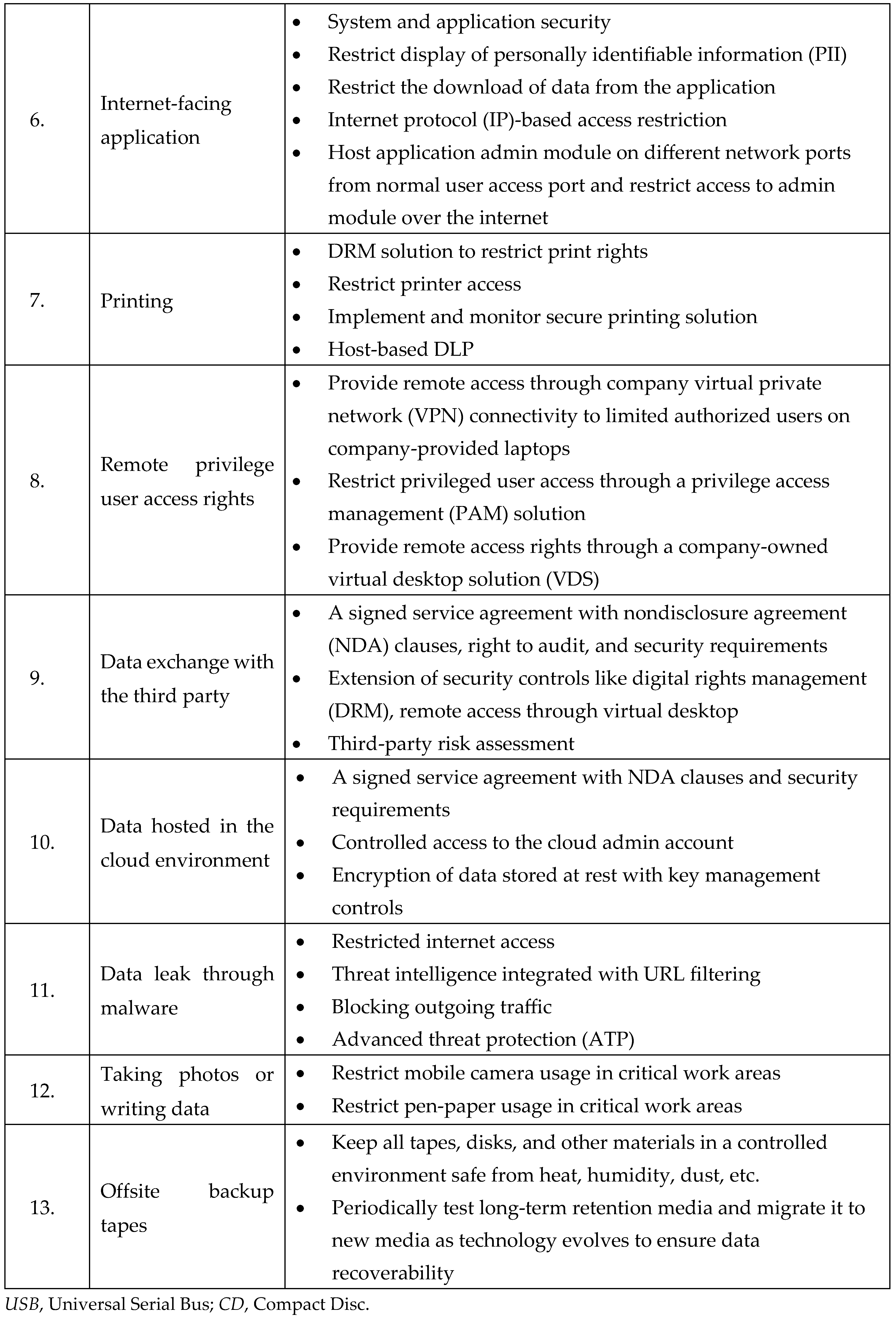
15]. During the deliberation on the best practices in cybersecurity to protect data in research laboratories, an SME highlighted that a breach in cybersecurity could have substantial adverse impacts on the supply chain, one health, safety, environment, quality, regulatory (or legal) system, economy, and reputation of organizations or countries. SME also underlined the importance of data flow analysis to identify and document life sciences research organizations' requirements, data sources, manual dependencies, processes, and data. SME stated the importance of understanding - Who will access the data? What activities will be performed on the data? What are the access rights defined? How will data flow? Where is the data stored? What are the security controls? During the discussions, participants also learned the importance of identifying and controlling data egress points (
Table 1) to mitigate the organization’s cyberbiosecurity risks.
During the guided exercises, participants were able to identify the existing mitigation measures and biosecurity-associated vulnerabilities in inventory control, information control, personnel control, physical security control, transport security control, emergency and incident response, dual-use research of concern management, and emerging technologies management at their organization. Round table discussions, case studies, lectures, and exercises helped participants to gain knowledge about biosecurity threats associated with toxins and venom (as well as biological agents) research and the challenges posed by nefarious actors.
At the end of the workshop, participants were able to recognize the importance of best practices to deal with the biosecurity and cyberbiosecurity threats associated with toxins and venom research and develop a suitable biosecurity plan to fix the vulnerabilities.