Submitted:
07 September 2023
Posted:
08 September 2023
You are already at the latest version
Abstract
Keywords:
1. INTRODUCTION
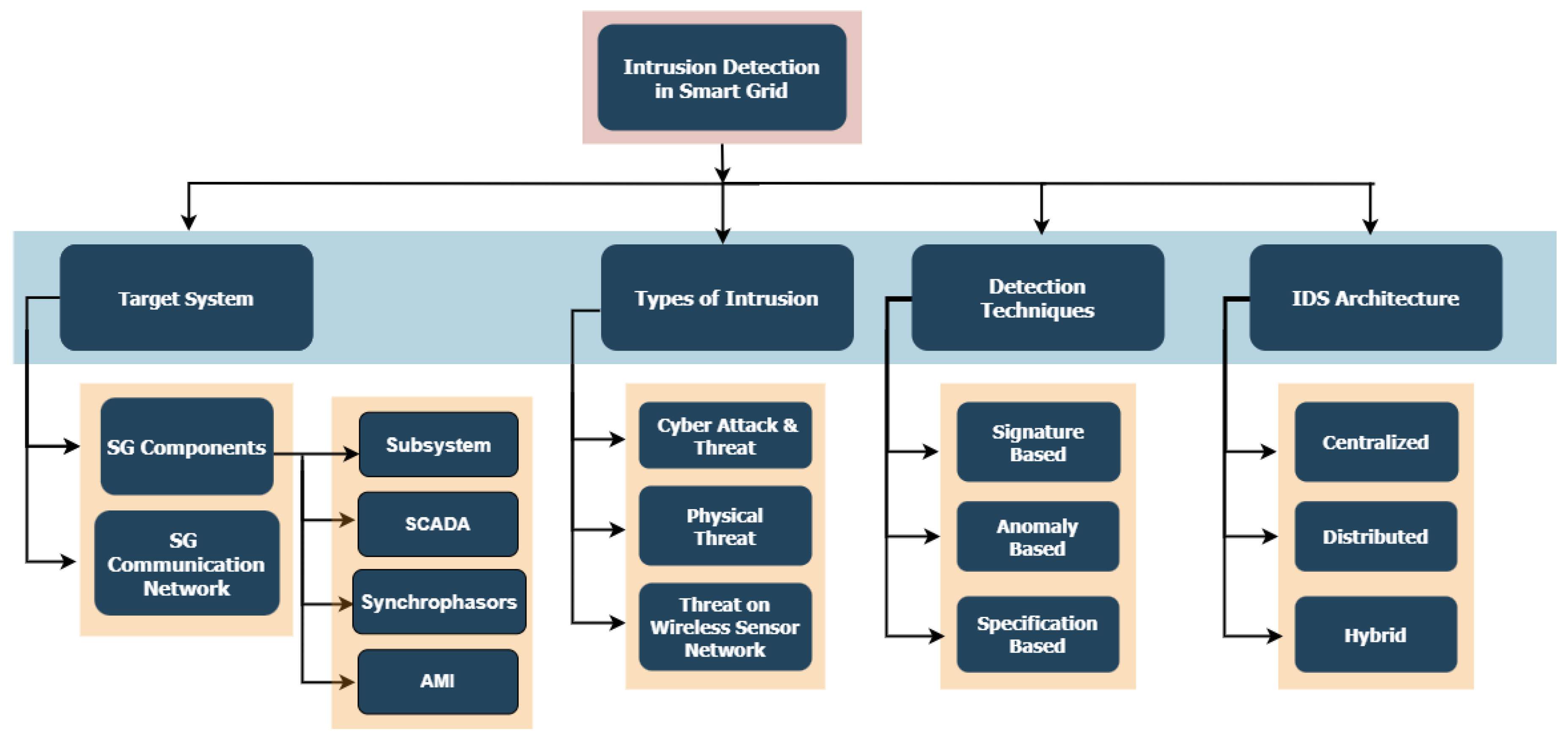
2. Overview of Intrusion Detection System
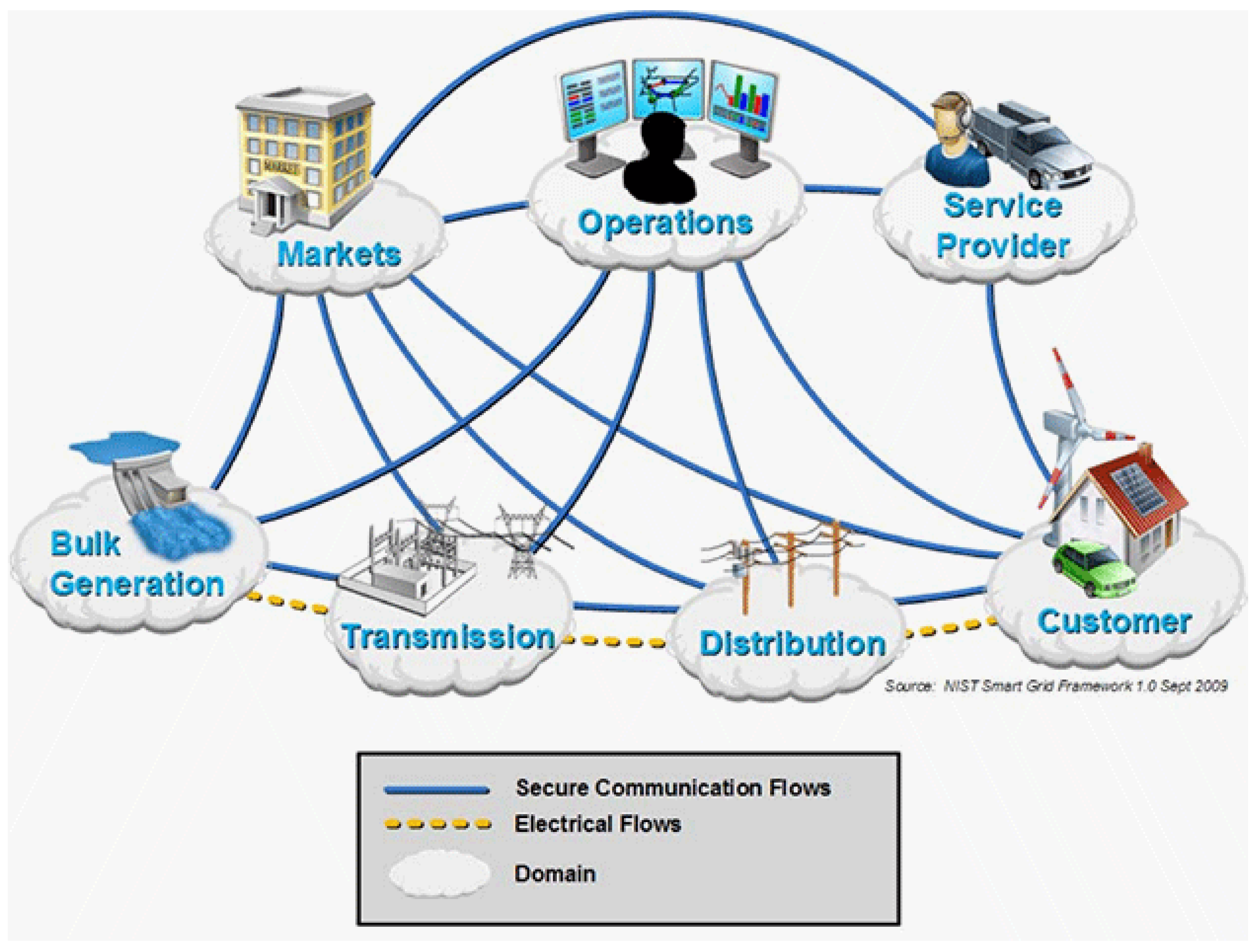
2.1. Target System: Smart Grid Paradigm
-
Intrusion on Smart Grid Components This section examines the SG paradigm’s components and related communications to give a general overview. The substations play a pivotal role in the operation of SG.
-
Substation: The substations play a pivotal role in the operation of SG. Substations operate SG’s transmission and distribution processes. A Substation Automated System (SAS) with IEDs, RTUs, and computers controls modern substation operations [9]. In particular, they participate in the generated power, set up the distribution system, and manage the power expansion. They may contain various hardware and software elements, including GPS, RTUs, HMIs, and Intelligent Electronic Devices (IEDs) [10]. The substation can be one of the most significant targets for an intruder to disrupt the system’s regular operation or functionalities and the total power supply, which may cause a cascading effect on society and nations. Modern substations must address cybersecurity risks in supervisory control and data acquisition (SCADA) systems as IEC 61850 smart substations emerge. This study presents a new IDS for IEC 61850 substation cybersecurity evaluating multidimensional physical knowledge and behaviours to deliver a comprehensive and effective cyber threat mitigation solution [11]. A 500kV smart substation cyber-physical testbed implements and validates this SCADA-specific ID.In [12], M. Kabir-Querrec et al. provides a specification-based IDPS that centres on substation communications according to IEC 61850. In particular, IEC 61850’s data object model is the foundation for their IDPS’s architecture, including a novel intrusion detection function.Using the IEC 61850 standard, H. Yoo and T. Shon [13] present an anomaly-based IDPS for the substations. The proposed IDPS zeros in on MMS and GOOSE protocols using a one-class SVM classification model to zero in on patterns that correspond exclusively to regular and legitimate network traffic.
-
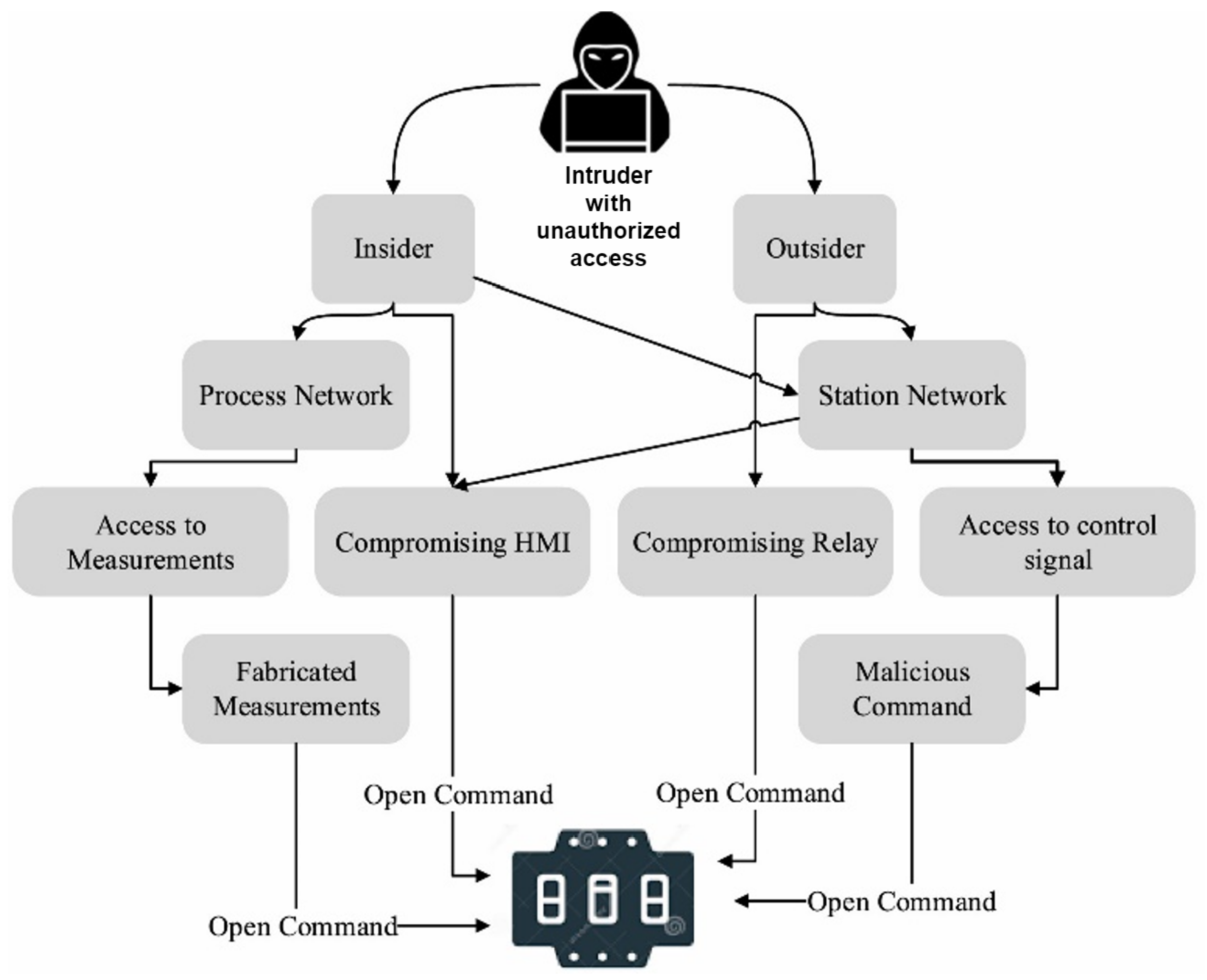
SCADA System: SG is a system based on SCADA systems, a part of the industrial control system and environment, that necessitate monitoring and managing the automated operation of other components. A SCADA system is made up of the following components in particular: a) measuring devices; b) logic controllers, such as programmable logic controllers or Remote Terminal Units (RTU); c) Master Terminal Units (MTU); d) communication network; and e) an HMI. Measurement instruments track objective quantities like temperature, pressure, and voltage. The primary duties of logic controllers include gathering data from the measuring devices, identifying unusual behaviours, and activating or deactivating technical components [9]. The system operator can give commands to logic controllers and receive data through MTU, a central host through which the logic controllers communicate. The communication network is used to realize the interface between MTU and the logic controllers. This communication system uses industrial protocols like Distributed Network Protocol 3 (DNP3) and Modbus. The interface between MTU and logic controllers is facilitated by HMI, a software package with graphical capabilities installed on MTU. All of the components of SCADA in the SG system are highly vulnerable to attack by any intrusion or hacking, as illustrated in Figure 3. Due to the interdependency of each component to run the whole system of SCADA, any unauthorized access to any of its members by an intruder may cripple the entire SG system. E. Hodo et al. offer an anomaly-based IDS for a SCADA-simulated environment using the IEC 60870–5-104 [109] (IEC-104) protocol in [14]. S.D. Anton et al. compare four machine learning techniques for Modbus/TCP anomaly detection in [15]. They employed Lemay and Fernandez’s dataset [16] that was separated into three sub-datasets: DS1, DS2, and DS3. DS1 contains 3319 packets of MTU-to-6 RTU network traffic, including 75 malicious occurrences. DS2 has 11166 packets, with 10 malicious ones with one MTU and six RTUs. Finally, eight datasets produced 365906 packets with 2016 harmful cases in DS3. These sub-datasets provided features for machine learning algorithm training.
- Synchrophasor: A synchrophasor system is an emerging technology required for the functioning of the contemporary electrical grid. It primarily consists of Phasor Measurement Units (PMUs), Phasor Data Concentrators (PDCs), a communication network, and GUI software. A PMU is an instrument that performs numerous measurements from current/voltage waveforms, including frequency, phase angle, active power, and reactive power. A PDC takes on the task of compiling PMUs’ information and combining it into a single flow. The IEEE C37.118.2 and IEC 61850 [18] standards are typically used for communication between PMUs and PDCs. The GUI application’s final responsibility is to visualize the various data from PDCs properly. For synchrophasor systems that employ the IEEE C37.118 protocol, Khan et al. [19] presented a hybrid IDS primarily based on specification-based and signature-based approaches. The suggested system’s general design comprises two types of detectors, or HIDSs and NIDSs, respectively, called agents and sensors. Agents monitor PMUs and PDCs’ performance, while sensors control data flow throughout the network. In addition, a management server compiles and correlates data from all the sensors and agents. Any detection notice or warning is also documented in a database server. In [20], Y. Yang et al. proposes a specification-based IDPS that can secure IEEE C37.118-based synchrophasor systems. Access control, protocol-based, and behaviour-based rules are the three main categories of rules in their intrusion detection and prevention system (IDPS).
-
Intrusion on AMI: An AMI system comprises three basic parts: smart meters, data collectors, and a headend. Smart meters try to track the electrical appliances’ power usage and other metrics [21]. Data collectors must store the information produced by numerous smart meters in a particular region. The AMI headend, which receives, stores, and maintains the data collected by the data collectors, is the utility company’s central server. The utility firm can make the best decisions for the power generation, transmission, and distribution processes based on the information gathered on the AMI headend. In [22], the authors examined the recent academic approaches to intrusion detection systems and techniques for AMI and discussed the threats that could potentially affect this industry. Numerous contributions have been made to secure the AMI: In [23], authors created a specification-based Intrusion Detection System (IDS) for Home area networks (HANs) responsible for data transfer among smart meters and household devices. The IDS design targets ZigBee’s physical and medium access control layers and defines its normal behaviour based on extracted specifications. Any change from usual behaviour may signal an attack. In [24], authors suggest an IDS for AMI, consisting of three local IDSs in smart meters, data concentrators, and the head-end. The IDS uses stream data mining to identify network assaults. This paper introduces an IDS for the neighbourhood area network (NAN), an AMI subsystem connecting smart meters to data concentrators. The IDS uses data mining to detect malicious activities caused by blackhole attacks in this area.Another well-suited distributed IDS architecture for AMI is an Extreme Learning Machine (ELM). ELM’s quick training speed and robust model generalization ability are ideally suited for intrusion detection in the smart meter of the SG system. An ELM intrusion detection model based on a genetic algorithm (GA) is proposed as a solution to the issue that the ELM’s random input weights and hidden layer bias prevent the model from performing at its ideal level [25].
-
-
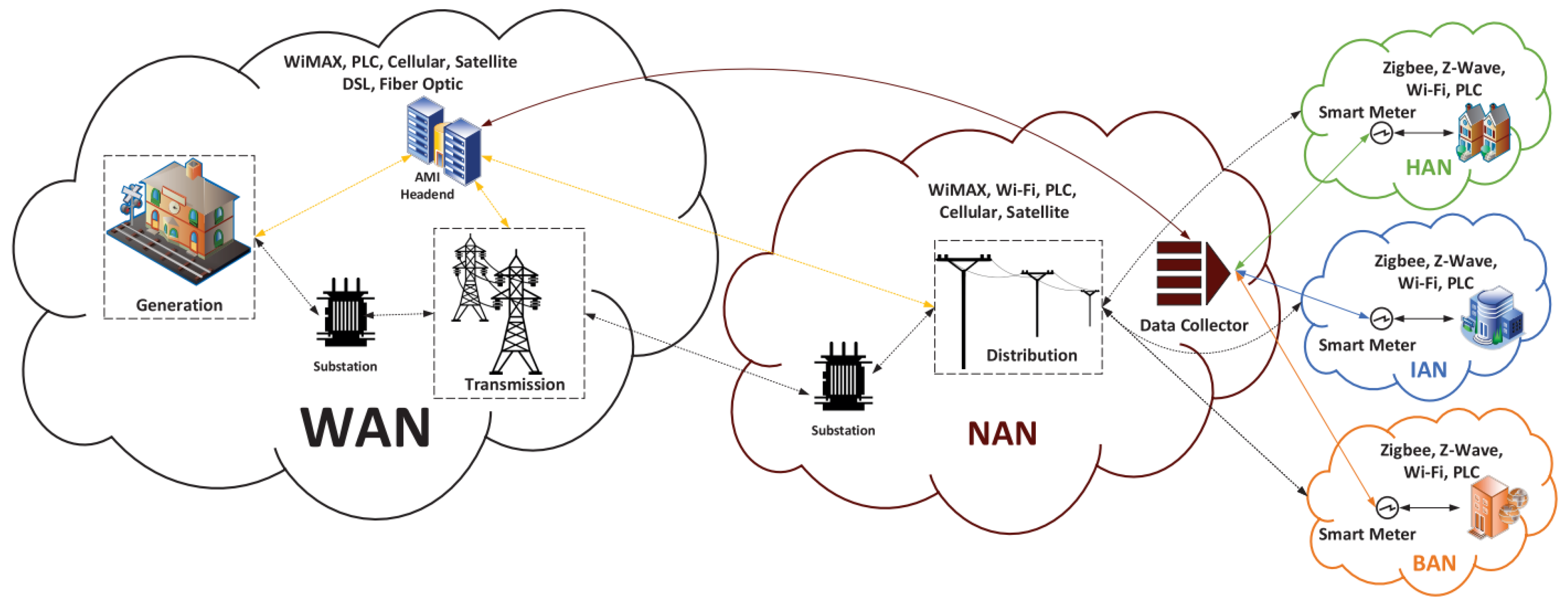
Smart Grid CommunicationA generalized SG architecture separated into communication aspects is shown in Figure 3. Three different network area types—Home Area Networks (HANs), Business Area Networks (BANs), and Industry Area Networks (IANs)—are present in the first layer and are identified by the presence of consumers. The existence of smart meters, which track and communicate information about electrical appliance energy usage, is precisely the critical feature of these network areas. A network connecting a home’s electronic and intelligent gadgets is called a HAN. The second form, or BAN, is a network comprising the hardware and software needed for an organization to operate. The IAN also specifies a network that includes all the functional components needed for industry. The devices of these networks often use ZigBee and Z-wave, as shown in Figure 4. Rarely, they may also employ Power Line Communications (PLC) or IEEE 802.11 (Wi-Fi). The authors in [26] suggested a structure for IDS deployment in the smart grid. The proposed system will collect and correlate notifications from various intelligent grid sensors. In the innovative grid network, sensors might be installed in HANs, NANs, or even the vast area network. We looked at the intrusion detection classification algorithms’ results on the ISCX2012 dataset.
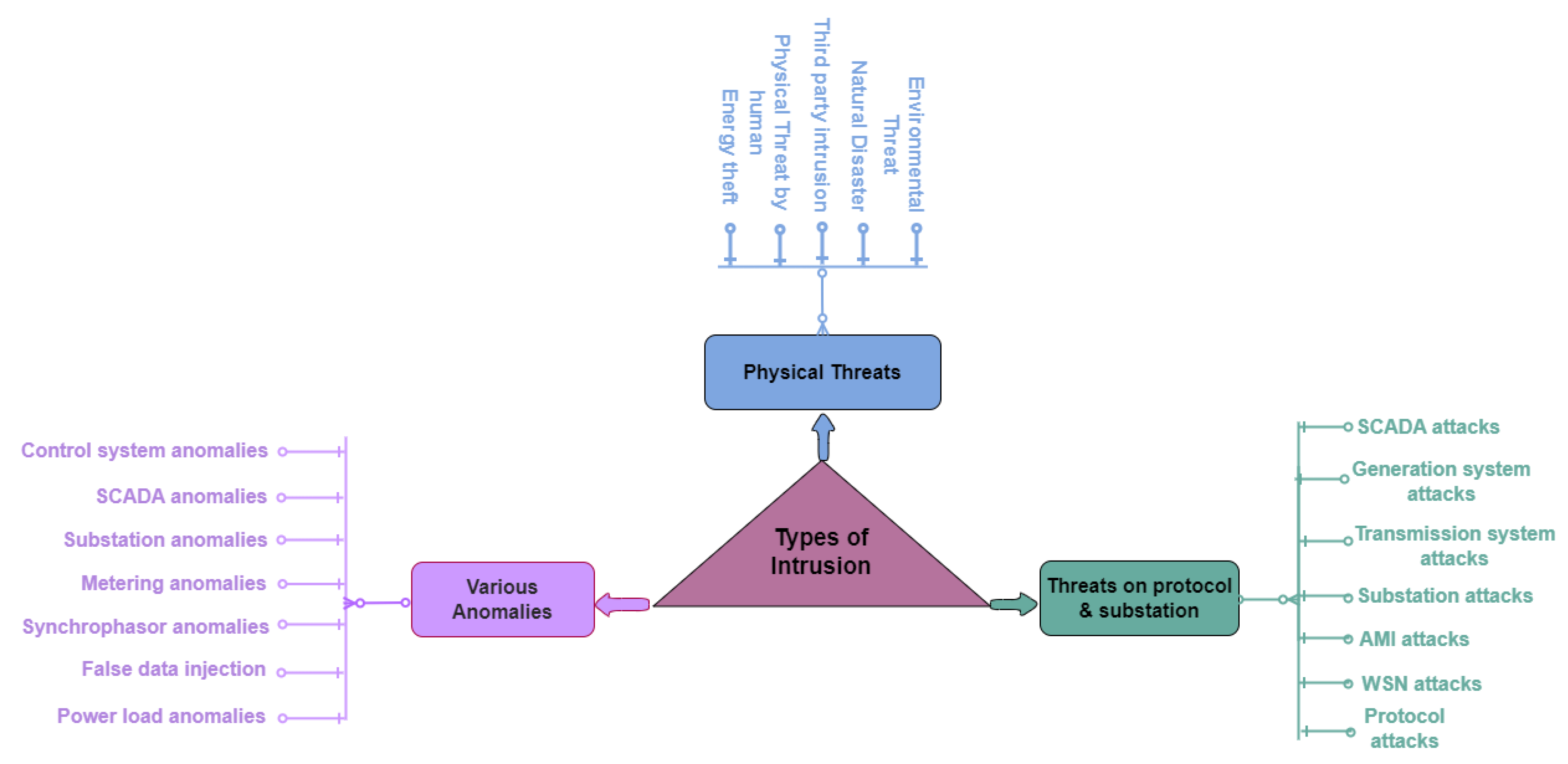
2.2. Types of Intrusion
-
Cyber Attack and ThreatRecently, the SG system is mainly prone to a crucial type of intrusion, that is, cyber-attacks or threats, which are network-based. Exploiting badly the trusted perimeter built by the set-up of firewalls with wrong inbound and wrong outbound rules is a common way for an intruder or attacker to get into the communication network system and put a malicious payload on the control system. In the first phase of this type of intrusion, the intruder gets into the network through unauthorized access, where the intruder could be either an insider or an outsider with the ill intention to do malicious action on the system and gain any profit. For instance, an intruder could wait for a legitimate user to join the trusted control system network via VPN and then take over that VPN connection. The network-based attacks mentioned above are dangerous because they allow an attacker from outside to get into the web of a trusted control system.Due to resource (device, deployment, and communication) constraints imposed by communication standards and sensor nodes, for a reliable hierarchical smart grid, it is essential that several communication standards can work together securely. The negative impacts of cyber-attacks can be mitigated by creating various intrusion detection and prevention system solutions.
-
Potential cyber-attacks: In terms of cyber-attacks, they can take many different forms, some of which include man-in-the-middle (MITM) attacks, denial-of-service (DoS) attacks, false data injection attacks (FDIA), and other cyber-physical assaults on the smart grid. These attacks include hacking into power plants or distribution network control systems, deceiving sensors and monitoring systems, or destabilizing communication networks that link different grid components. The evaluation of the state of the power system could be hampered by a significant class of cyber-attacks known as FDIA (False Data Injection Attack). The FDIA might compel the state estimator to give the system operator false data, which might have unforeseen consequences for the power system. The FDI attack was found in [33] after a series of attacks and a processed innocuous data set. Such injection assaults, whether they target the smart meter or the command line, can produce seriously abnormal load patterns or power consumption in Singapore, to quote one example [34,35]. The correctness of the calculation and analysis depends on how well the state is estimated [36,37]. A denial-of-service (DoS) attack, as defined by [38,39], is an attempt to overwhelm a targeted computer system or network with traffic or requests to disrupt routine operations and prevent authorized users from accessing it. In Man-in-the-Middle (MitM) cyber-attacks, the attacker intercepts a conversation between two parties to covertly listen in, manipulate, or impersonate one or both of the participants [40,41]. Two frequently utilized MITM attack strategies are ARP spoofing and DNS spoofing. In a replay attack, a hacker intercepts previously obtained data and maliciously retransmits it to pass it off as coming from the original sender and gain unauthorized access to a system or network. The attacker sends a packet of messages [42] to the victim host in the fake system.Another most perilous form of cyber attack is the Advanced Persistent Attack (APT). For instance, the intrusion on a Ukrainian Advanced Persistent Attack (APT) caused a blackout for more than 225,000 people, which took a prolonged period for the security specialists to coordinate in pursuit of a particular goal [3].Backdoors and holes in the network boundaries can be caused by IT infrastructure components that are weak or are set up wrong. Networking devices at the edge, like fax machines or modems that have been forgotten but are still connected, can be used to get around proper access control [43].In particular, access remote terminal units (RTUs) are used for remote management of the dial-up. Many departments don’t require a password for authentication, and the default passwords for modems attached to field equipment are often left unchangeable, making them vulnerable to attack. Also, bad guys can use the devices’ flaws to install backdoors that will let them get into the restricted area in the future. Another possible network-based entry point is through safe peer utility links.
- Cyber-attacks on common SG protocols: smart grid components use various protocols or standards that inherit security vulnerabilities. Protocols like TCP/IP and remote procedure calls (RPC) are often used. The Modbus protocol, widely used in industrial control systems like water, oil, gas, and SG, is a SCADA protocol. Since the Modbus system wasn’t designed for highly security-critical environments, it is a noteworthy concern because there are several ways to attack it. The Modbus is a simple client-server system for low-speed serial communications in process control networks. Process control systems use this to exchange SCADA information used to run and handle industrial processes [44]. The most common Modbus attacks are as follows: 1) Baseline response replay, 2) Direct slave control, 3) Modbus network scanning, 4) Passive survey, 5) Broadcast message spoofing, 6) Rogue interloper, and 7) Response delay. Suppose an attacker can sniff network traffic using a protocol analysis tool. In that case, they can potentially intercept SG Distributed Network Protocol 3.0 (DNP3) messages and obtain unencrypted plaintext frames containing vital information like source and destination addresses. Intercepted data, such as control and setting information, could be used on another SG system or intelligent equipment device (IED) later, potentially shutting down services or, at the very least, causing service disruptions.
-
-
Physical Threats: Along with these examples of cyber-attacks, a wide range of physical threats can have detrimental effects, such as damaging equipment and even creating power outages of the SG system. While our study does not focus on physical attacks of the SG, we do concur that the possibility of such attacks is more likely to be launched against the power lines themselves, in addition to transformers and substations [45]. Although uncommon, attacks on the power grid’s physical infrastructure, including power lines, transformers, and substations, could happen. However, the smart grid is more likely to be attacked physically through its softer entry points. For instance, smart meters are more likely to be attacked physically due to their ease of access and prevalence. According to research by Anderson and Fuloria [46], an attacker might remotely turn off millions of smart meters simultaneously.Apart from these, any third-party integration might cause a severe adverse impact on securing the SG system. On the other side, sometimes energy theft becomes a grave security concern for identifying intrusion in the SG system. An attacker can successfully reprogram industrial control systems by injecting malware targeting the vulnerable points of industrial control systems; one example is the Stuxnet attack [9] against the Iranian nuclear program, which exploited four zero-day vulnerabilities.Moreover, besides human errors, equipment failures account for numerous blackouts on the current SG system, including those in North America, Switzerland/Italy, London/West Midlands, Turkey, and South Australia. Research into systems for detecting incidents with the potential to lead to cascading failures was spurred by the North American Blackout [47].
-
Threats on WSN: Wireless sensor networks (WSN) are integral to the Smart Grid’s communication framework. Smart Grid network cyber security issues and their remedies have been explored in detail elsewhere due to their unique characteristics; sensor nodes in WSN present individual attack vectors, vulnerabilities, and security requirements. Communication between sensor nodes in a WSN is more concerned with the data than the address of a specific sensor node, so address-specific security threats and remedies may not apply. One of the weakest, most convoluted, and most challenging parts of Smart Grid security is the protection of WSNs. The WSN security is a multifaceted research issue as the security of the entire Smart Grid network can be built upon this. There are various kinds of attacks and threats on WSNs. In external attacks, most hacking incidents involve an intruder located beyond the coverage area of a wireless sensor network (WSN). Jamming the network, using all available resources, or launching a denial of service (DOS) attack are examples of external aggression.For internal attacks, an intruder is supposed to be an insider of WSN. This type of adversary is generally performed for physical tampering of nodes, the revelation of confidential information, causing a denial of service to authorized nodes, etc. In the active type of attack, the adversary compromises the security characteristics of WSN to modify and steal the data. An attacker carries out this type of assault to perform an adversary on data by modifying packets, injecting fake data, depleting network resources, and capturing nodes. Examples of active attacks on WSN include spoofing, jamming, wormholes, hello floods, denial of service, sinkholes, etc. On the other hand, passive attacks are performed by an intruder mainly by observing network activities by performing reconnaissance attacks. This type of attack targets the confidentiality of the network. An example of such attacks is an analysis of traffic, decryption of vulnerable data, capturing information, etc.To implement an efficient IDS, the nature of attacks should be understood beforehand to develop countermeasures at various network layers. WSNs typically employ hierarchical network architectures, which leaves the networks extremely susceptible to routing problems while switching between topologies. This paper investigates topology control for the cyber security of wireless sensor networks as an alternative to well-studied options like intrusion detection systems and cryptographic security [48]. Many authors have been surveyed recently regarding IoT-related topics, and they all tend to focus on specific parts of IDS. A review of machine learning approaches with a particular emphasis on intrusion detection systems (IDS) for WSNs and the Internet of Things [32,49]. Research by Buczak and Guven [31] indicates several concerns with approaches, particularly for the complexity of those requiring acquisition, and discusses IDS on the general system commonly used for specialized WSN and IoT.
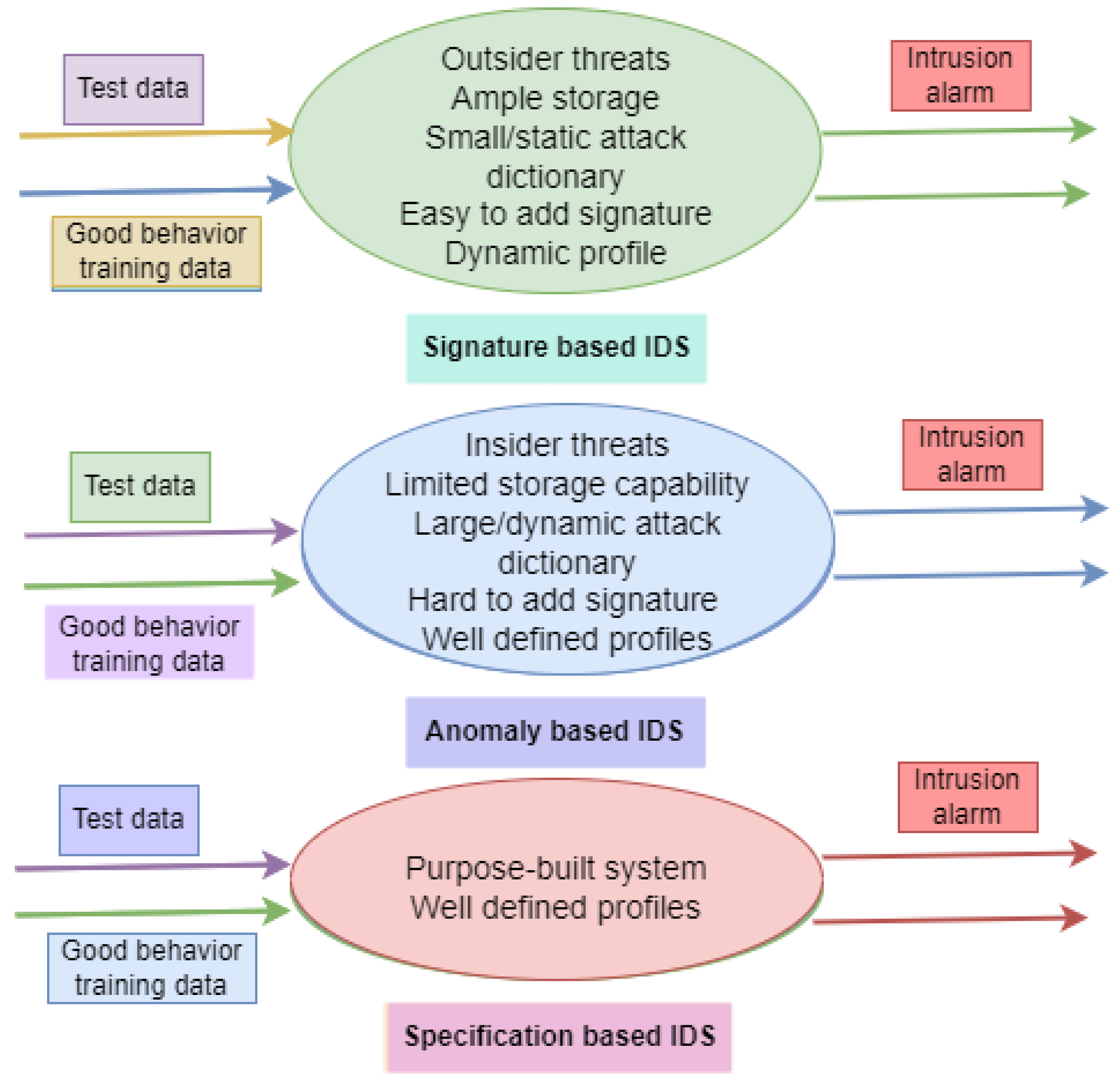
2.3. Intrusion Detection Techniques
-
Signature-Based IDS: The second category (Signature-based) works by comparing events in a computer system against a list of known malicious patterns, or "signatures." Each action is compared to each signature, and an alert is generated if a match is found. It is essential to highlight that this method necessitates complete familiarity with the tested system’s weaknesses. Although this method has a low false-positive rate and high dependability, it cannot identify attacks that do not match any known signature. USING MATLAB, an AMI IDS incorporating temporal and geographic detection approaches, was developed by the authors of [51]. The suggested system is primarily concerned with blackhole and time delay attacks. However, the time delay attacks aim to make the packet transmissions sluggish.Intrusion detection methods based on signatures examine data gathered during execution to see if it matches a known pattern of malicious activity. Misuse detection, supervised detection, pattern-based detection, and intruder profiling are used to describe this technique [32].This means that IDS employing this technique must routinely update their signature sets to account for emerging threats. However, the second method’s usefulness is predicated on labelling anomalous actions as malicious intrusions. Bayesian networks, neural networks, and Markov models are examples of the statistical analytic procedures and machine learning techniques typically used in this approach to detect hostile actions. The application of this method is less precise than its predecessor. One benefit is that it can identify previously unseen forms of cyberattack.
-
Anomaly-Based IDS:Intrusion detection methods that identify anomalies in runtime behaviour are called "anomaly-based." The commonplace can be defined in two ways: regarding a set of training data (semi-supervised) or the past of the test signal (unsupervised). Unsupervised machine learning is illustrated through clustering.Anomaly-based detection finds intrusive behaviour that deviates from the allowed range or the white list. It can identify unusual suspicious behaviour in the smart grid. An anomaly-based intrusion detection technique trains the model using a normalized baseline against which every activity is analyzed [52]. Attackers are likelier to experiment with novel approaches to undermine the intelligent grid system, and attacks are more likely to be discovered by anomaly-based intrusion detection.Denning [53] established the first anomaly detection model as an adjunct to misuse-based detection techniques. The purpose of statistical models that describe typical behaviours is to detect outliers. An anomaly-based IDS operates under the hypothesis that routine activities can be predicted statistically and that outliers indicate malicious intent. Point, contextual, and collective anomalies are the three deviations identified by [54]. Anomaly detection studies typically centre on point anomalies and single data instances. Each data object carries contextual attributes and behaviour characteristics, making contextual anomalies conditional anomalies. Sequence, graph, or spatial data exhibits a collective abnormality.ARIES, as detailed in [55], is a novel anomaly-based intrusion detection system (IDS) that can reliably safeguard SG communications against intrusion. ARIES has three detection layers—(a) network flows, (b) Modbus/Transmission Control Protocol (TCP) packets, and (c) operational data—to identify potential cyberattacks and irregularities. The ARIES Generative Adversarial Network (ARIES GAN) was built utilizing cutting-edge error reduction techniques to detect anomalies in operational data (i.e., time series electricity measurements), with a focus on the third layer (operational data-based detection).
-
Specification-Based IDS Finally, the third method (Specification-based) relies on predefined rules that characterize the typical operation of the system under test. Specifications refer to these guidelines. An alert is sent when an action’s properties deviate from one of the requirements. Because it can identify potential irregularities, this approach can reveal previously unknown attacks. This method differs from the signature-based approach in that it is predicated on the idea that the system’s security policy can’t be breached if all specifications are met. However, this is different from the signature-based method. The word "hybrid" is now used to describe an IDPS combining two or more approaches mentioned above.A specification-based intrusion detection framework has been developed to categorize substation scenarios and detect cyber-attacks in [56]. The proposed intrusion detection approach uses Bayesian networks to graphically encode causal links among available information to build patterns with temporal state changes. This lets the proposed system identify cyber assaults and substation scenarios. A modified 2-bus 2-generator system from the IEEE 9-bus 3-generator system is used to explore the non-pilot directional over the current relay protection technique. Nine power system scenarios were devised and implemented for the case study. On the other hand, to maintain the reliability and stability of the grid’s distribution infrastructure, a specification-based intrusion detection sensor has been introduced to monitor advanced metering infrastructures (AMI) [57]. To check for device security and compliance with a security policy, this sensor analyzes network, transport, and application levels of communication between meters and access points. It detects all security policy violations by imposing limitations on C12.22 standard protocol transfers. Using a formal framework, these limitations were confirmed, and a sensor prototype was tested with genuine AMI network traffic. An associated warning is exported if an action’s characteristics don’t match one of the specifications. Because it can identify potential anomalies, this approach can identify undiscovered attacks. This technique is predicated on the presumption that the system’s security policy cannot be compromised, unlike the signature-based method, if all requirements are followed. The signature-based process, in contrast, does not rely on any such presumption. It’s important to note that the term "hybrid" is now commonly used to denote an IDPS that combines two or more approaches.
2.4. Intrusion Detection Functions and Performance Metrics
2.5. Intrusion Detection System Architecture
- Centralized Architecture: C-IDS is typically used in centralized infrastructure. Because of this, the LLN can collect and send data across international borders. As a result, centralized IDS may examine all data travelling between the LLN and the Internet. Since it is challenging to monitor each node during an ongoing attack [61], it is not sufficient to identify attacks affecting nodes within the LLN. The primary objective is to determine how to defend against a botnet attack. Kasinathan et al. [62,63] @devised a centralized placement that allows them to think about beating DDoS assaults so that even if one were to occur, the transmission of IDS data would continue unabated. Wallgren et al. [64] implemented a centralized method for detecting attacks on the physical domain in the border router.
- Distributed IDS: Every LLN node uses D-IDSs, and those used in nodes with limited resources are optimized as much as possible. Because of this, a lightweight distributed IDS was introduced. Light methodology matching attack signatures and packet payloads were identified by Oh et al. [65], and alternative methods requiring fewer matches were proposed. By assigning nodes to monitor their neighbours in the distributed placement, Lee et al. [66] provide a lightweight way of keeping tabs on a node’s power consumption. These nodes serve as "watchdogs" in a network. Cervantes et al. [67] proposed a method to detect and mitigate sinkhole attacks by combining their ideas of trust and reputation with the watchdog nodes. This method is called "Intrusion detection of Sinkhole attacks on IPv6 over Low -Power Wireless Personal- Area Networks (6LoWPAN) for IoT"(INTI). Because of this, the node’s function may shift every time the network is reconfigured or an attack occurs.
-
Hybrid IDS: H-IDS uses the advantages of both centralized and distributed deployments, eliminating both limitations. The first method divides the network into clusters, with the cluster’s primary node hosting an IDS instance and then being responsible for monitoring its neighbours. This means a hybrid IDS deployment can be configured to use more resources than a standard IDS deployment [68].Le et al. [69] also successfully organized the network into smaller clusters, each with its cluster head, from the same number of initial nodes. Each cluster head might host an IDS instance, with nodes relaying information about themselves and their neighbours to the central node. The second method involves inserting IDS modules into the border router and many additional network nodes in addition to a centralized hub. Using the Routing Protocol Low-power and Lossy (RPL) network data, Raza et al. [70] developed the IDS they called SVELTE, in which the hosts of the border routers are tasked with processing-intensive IDS modules that are responsible for detecting any intrusion attempt. According to Pongle et al., [71], network nodes are to blame for any observable shifts in their immediate vicinity. Additionally, network nodes communicated neighbourhood details to a centrally located module hosted by a border router tasked with data storage and analysis. This facilitates the detection of intrusions and the early detection of attacks. Thanigaivelan et al. presented an IDS in [72] that divides tasks between individual nodes and the router’s perimeter. The IDS module can monitor its neighbouring nodes, looking for signs of intrusion and alerting its fellow IDS modules if it finds any.
3. RESEARCH TRENDS AND DIRECTION
- AMI relies on the flow of ICT that facilitates two-way communication between power distributors and consumers. It is severely vulnerable to various kinds of attacks and threats. So, the security issues related to AMI connectivity, data integrity, and availability are at stake. AMI has not been prioritized well in recent research on IDS in the SG domain, a crucial application component of SG. To our knowledge, no sheer number of research or work on the IDS focuses on the AMI.
- Lack of research addressing how to map the intrusion process to the complex smart grid architecture.
- Lack of research on eliminating False positives for fluctuations of smart meter (SM) data at the AMI headend.
- No significant idea has been found addressing the scalability issue for the IDS in the SG system.
- As the SG is a vast system, very few computational analyses have been found considering the compatibility issues incorporated with any new IDS into the SG system.
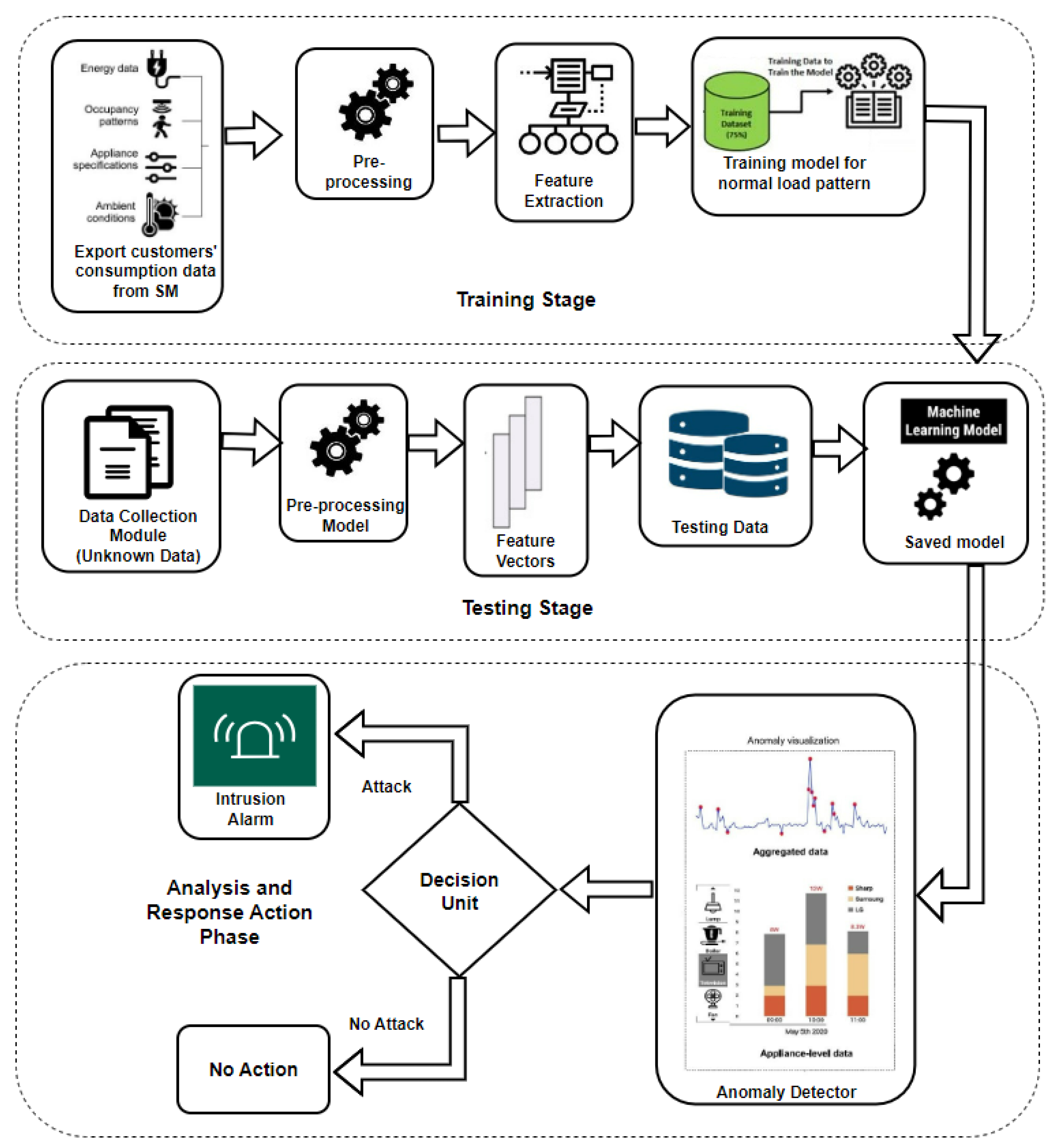
- The data gathered from SM should be considered while developing a generative model for identifying intrusion based on anomaly detection—the AMI headend and data collectors with an installed IDS made up of the proposed system. In the first stage, the IDS units monitor network traffic between the data collectors and the smart meters. After spotting potential anomalous flows, they transmit their findings to the AMI headend’s IDS department. The latter then analyses the anomalies and triggers an intrusion alarm. The entire system is based on the state-of-the-art of machine learning, which has three phases: a) training, b) testing, and c) analysis and response action.
- In more detail, the goal of the first module is to use a Bayesian Network to monitor communication traffic, identify attack activities, and train the model. It specifically keeps track of the number of data collector requests, the time, and the ID of smart meters. The second module tests the model with testing data and evaluates the outcomes. In the third module, secondary analysis is done upon careful analysis of the pattern of anomalies from the modelled data. It generates intrusion alarms associated with the decision taken from the investigation before. To evaluate the system, two kinds of attacks, a) attacks on commands and b) attacks on data, will be performed behaviour simulated in an environment that would generate anomalous consumption metrics indicating intrusion caused by these assaults. Suppose a potential cyberattack or unusual behaviour is identified. In that case, the alarm will be triggered immediately, estimating the system’s state into three levels of indication of intrusion: a) normal, b) abnormal, and c) uncertain.
- The proposed IDS generates an alarm whenever an irregularity deviates from or does not match the normalized baseline. This is certainly a unique component of this model when the abnormality exceeds the threshold values for each meter data. The decision tree technique would be considered to implement this part of the model.
- These alerts can also be sent off by unexpected user logins, new IP addresses trying to join the intelligent grid network, newly added devices accepted to the network without permission, and other events. Because they alert to even the most negligible abnormal behaviour in the network, anomaly-based intrusion detection solutions may have more excellent false-positive rates.
- For another single system, it is much easier to deploy IDS in commodity networks because of lots of bandwidth everywhere and lots of computational power. However, in the SG, some parts of the network have very little bandwidth, particularly at the AMI. Likewise, many devices have low computational power.
- For full-fledged intrusion detection, we need to consider this compatibility issue of the IDS within the SG system. Our proposed model consists of two parts. The computationally intensive part would be deployed in AMI headend, where a lot of bandwidth can handle big data. The utility end would be employed in the last part of generating an intrusion alarm. This is computationally less hard where the outcome from the first phase would be less amount of data that can be dealt with the low amount of bandwidth,
- Considering the issue with the scalability, we recommend our intrusion detection methodology be mapped to the SG architecture. As AMI is widely segregated and easily accessible to anyone, it is important to address the scalability issue here. The first phase of our proposed intrusion detection technique can be deployed distributively in each AMI, where the machine learning model will be applied right after the data collection process. The last phase would be performed at the utility end with a rigorous analysis of the outcome from the prior phase to eliminate False positives for fluctuations of meter data and generate an alarm based on the decision model.
4. Conclusions
References
- Avi, Avi Gopstein, Cuong Nguyen, Danielle Sass Byrnett, Kerry Worthington, and Villarreal Christopher. Framework and roadmap for smart grid interoperability standards regional roundtables summary report. US Department of Commerce, National Institute of Standards and Technology, 2020. [CrossRef]
- Jesús Lázaro, Armando Astarloa, Mikel Rodríguez, Unai Bidarte, and Jaime Jiménez. A survey on vulnerabilities and countermeasures in the communications of the smart grid. Electronics, 10(16):1881, 2021. [CrossRef]
- Defense Use Case. Analysis of the cyber attack on the ukrainian power grid. Electricity Information Sharing and Analysis Center (E-ISAC), 388(1-29):3, 2016.
- Gregg Keizer. Is stuxnet the best malware ever? 2010.
- Nadia Boumkheld, Mounir Ghogho, and Mohammed El Koutbi. Intrusion detection system for the detection of blackhole attacks in a smart grid. In 2016 4th International Symposium on Computational and Business Intelligence (ISCBI), pages 108–111. IEEE, 2016. [CrossRef]
- Priti Prabhakar, Sujata Arora, Anita Khosla, Rajender Kumar Beniwal, Moses Ndole Arthur, José Luis Arias-Gonzáles, Franklin Ore Areche, et al. Cyber security of smart metering infrastructure using median absolute deviation methodology. Security and Communication Networks, 2022, 2022. [CrossRef]
- James P Anderson. Computer security threat monitoring and surveillance. Technical Report, James P. Anderson Company, 1980.
- Zhong Fan, Parag Kulkarni, Sedat Gormus, Costas Efthymiou, Georgios Kalogridis, Mahesh Sooriyabandara, Ziming Zhu, Sangarapillai Lambotharan, and Woon Hau Chin. Smart grid communications: Overview of research challenges, solutions, and standardization activities. IEEE Communications Surveys & Tutorials, 15(1):21–38, 2012. [CrossRef]
- Panagiotis I Radoglou-Grammatikis and Panagiotis G Sarigiannidis. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. Ieee Access, 7:46595–46620, 2019. [CrossRef]
- V Cagri Gungor, Dilan Sahin, Taskin Kocak, Salih Ergut, Concettina Buccella, Carlo Cecati, and Gerhard P Hancke. A survey on smart grid potential applications and communication requirements. IEEE Transactions on industrial informatics, 9(1):28–42, 2012. [CrossRef]
- Yi Yang, Kieran McLaughlin, Lei Gao, Sakir Sezer, Yubo Yuan, and Yanfeng Gong. Intrusion detection system for iec 61850 based smart substations. In 2016 IEEE Power and Energy Society General Meeting (PESGM), pages 1–5. IEEE, 2016. [CrossRef]
- Maelle Kabir-Querrec, Stéphane Mocanu, Jean-Marc Thiriet, and Eric Savary. Power utility automation cybersecurity: Iec 61850 specification of an intrusion detection function. In ESREL 2015-25th European Safety and Reliability Conference. CRC Press, 2015. [CrossRef]
- Hyunguk Yoo and Taeshik Shon. Novel approach for detecting network anomalies for substation automation based on iec 61850. Multimedia Tools and Applications, 74:303–318, 2015. [CrossRef]
- Ersi Hodo, Stepan Grebeniuk, Henri Ruotsalainen, and Paul Tavolato. Anomaly detection for simulated iec-60870-5-104 trafiic. In Proceedings of the 12th international conference on availability, reliability and security, pages 1–7, 2017. [CrossRef]
- Simon Duque Anton, Suneetha Kanoor, Daniel Fraunholz, and Hans Dieter Schotten. Evaluation of machine learning-based anomaly detection algorithms on an industrial modbus/tcp data set. In Proceedings of the 13th international conference on availability, reliability and security, pages 1–9, 2018. [CrossRef]
- Antoine Lemay and José M Fernandez. Providing {SCADA} network data sets for intrusion detection research. In 9th Workshop on Cyber Security Experimentation and Test (CSET 16), 2016.
- Abolfazl Rahiminejad, Jordan Plotnek, Ribal Atallah, Marc-André Dubois, Dorian Malatrait, Mohsen Ghafouri, Arash Mohammadi, and Mourad Debbabi. A resilience-based recovery scheme for smart grid restoration following cyberattacks to substations. International Journal of Electrical Power & Energy Systems, 145:108610, 2023. [CrossRef]
- Petr Matoušek. Description of iec 61850 communication. In Technical Report. Brno University of Technology, 2018.
- Rafiullah Khan, Abdullah Albalushi, Kieran McLaughlin, David Laverty, and Sakir Sezer. Model based intrusion detection system for synchrophasor applications in smart grid. In 2017 IEEE Power & Energy Society General Meeting, pages 1–5. IEEE, 2017. [CrossRef]
- Yu Yang, Kieran McLaughlin, Sakir Sezer, Timothy Littler, Bernardi Pranggono, Paul Brogan, and HF Wang. Intrusion detection system for network security in synchrophasor systems. 2013. [CrossRef]
- Zakaria El Mrabet, Naima Kaabouch, Hassan El Ghazi, and Hamid El Ghazi. Cyber-security in smart grid: Survey and challenges. Computers & Electrical Engineering, 67:469–482, 2018. [CrossRef]
- Weiming Tong, Lei Lu, Zhongwei Li, Jingbo Lin, and Xianji Jin. A survey on intrusion detection system for advanced metering infrastructure. In 2016 Sixth International Conference on Instrumentation & Measurement, Computer, Communication and Control (IMCCC), pages 33–37. IEEE, 2016. [CrossRef]
- Paria Jokar, Hasen Nicanfar, and Victor CM Leung. Specification-based intrusion detection for home area networks in smart grids. In 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm), pages 208–213. IEEE, 2011. [CrossRef]
- Mustafa Amir Faisal, Zeyar Aung, John R Williams, and Abel Sanchez. Securing advanced metering infrastructure using intrusion detection system with data stream mining. In Intelligence and Security Informatics: Pacific Asia Workshop, PAISI 2012, Kuala Lumpur, Malaysia, May 29, 2012. Proceedings, pages 96–111. Springer, 2012. [CrossRef]
- Ke Zhang, Zhi Hu, Yufei Zhan, Xiaofen Wang, and Keyi Guo. A smart grid ami intrusion detection strategy based on extreme learning machine. Energies, 13(18):4907, 2020. [CrossRef]
- Imtiaz Ullah and Qusay H Mahmoud. An intrusion detection framework for the smart grid. In 2017 IEEE 30th Canadian Conference on Electrical and Computer Engineering (CCECE), pages 1–5. IEEE, 2017. [CrossRef]
- Abdulla Amin Aburomman and Mamun Bin Ibne Reaz. A survey of intrusion detection systems based on ensemble and hybrid classifiers. Computers & security, 65:135–152, 2017. [CrossRef]
- Chenfeng Vincent Zhou, Christopher Leckie, and Shanika Karunasekera. A survey of coordinated attacks and collaborative intrusion detection. computers & security, 29(1):124–140, 2010. [CrossRef]
- Junaid Arshad, Muhammad Ajmal Azad, Roohi Amad, Khaled Salah, Mamoun Alazab, and Razi Iqbal. A review of performance, energy and privacy of intrusion detection systems for iot. Electronics, 9(4):629, 2020. [CrossRef]
- Daniel S Berman, Anna L Buczak, Jeffrey S Chavis, and Cherita L Corbett. A survey of deep learning methods for cyber security. Information, 10(4):122, 2019. [CrossRef]
- Anna L Buczak and Erhan Guven. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Communications surveys & tutorials, 18(2):1153–1176, 2015. [CrossRef]
- Robert Mitchell and Ray Chen. A survey of intrusion detection in wireless network applications. Computer Communications, 42:1–23, 2014. [CrossRef]
- Mohamed I Ibrahem, Sherif Abdelfattah, Mohamed Mahmoud, and Waleed Alasmary. Detecting electricity theft cyber-attacks in cat ami system using machine learning. In 2021 International Symposium on Networks, Computers and Communications (ISNCC), pages 1–6. IEEE, 2021. [CrossRef]
- Soo Wan Yen, Stella Morris, Morris AG Ezra, and Tang Jun Huat. Effect of smart meter data collection frequency in an early detection of shorter-duration voltage anomalies in smart grids. International journal of electrical power & energy systems, 109:1–8, 2019. [CrossRef]
- Shampa Banik, Sohag Kumar Saha, Trapa Banik, and SM Hossain. Anomaly detection techniques in smart grid systems: A review. arXiv preprint arXiv:2306.02473, 2023. [CrossRef]
- Gaoqi Liang, Junhua Zhao, Fengji Luo, Steven R Weller, and Zhao Yang Dong. A review of false data injection attacks against modern power systems. IEEE Transactions on Smart Grid, 8(4):1630–1638, 2016. [CrossRef]
- Danda B Rawat and Chandra Bajracharya. Detection of false data injection attacks in smart grid communication systems. IEEE Signal Processing Letters, 22(10):1652–1656, 2015. [CrossRef]
- Ercan Nurcan Ylmaz, Bünyamin Ciylan, Serkan Gönen, Erhan Sindiren, and Gökçe Karacayılmaz. Cyber security in industrial control systems: Analysis of dos attacks against plcs and the insider effect. In 2018 6th international istanbul smart grids and cities congress and fair (icsg), pages 81–85. IEEE, 2018. [CrossRef]
- K Narasimha Mallikarjunan, K Muthupriya, and S Mercy Shalinie. A survey of distributed denial of service attack. In 2016 10th International Conference on Intelligent Systems and Control (ISCO), pages 1–6. IEEE, 2016. [CrossRef]
- Patrick Wlazlo, Abhijeet Sahu, Zeyu Mao, Hao Huang, Ana Goulart, Katherine Davis, and Saman Zonouz. Man-in-the-middle attacks and defence in a power system cyber-physical testbed. IET Cyber-Physical Systems: Theory & Applications, 6(3):164–177, 2021. [CrossRef]
- Shampa Banik, Trapa Banik, SM Hossain, and Sohag Kumar Saha. Implementing man-in-the-middle attack to investigate network vulnerabilities in smart grid test-bed. arXiv preprint arXiv:2306.00234, 2023. [CrossRef]
- Junfeng Zhao, Jing Wang, and Lei Yin. Detection and control against replay attacks in smart grid. In 2016 12th International Conference on Computational Intelligence and Security (CIS), pages 624–627. IEEE, 2016. [CrossRef]
- Yilin Mo, Tiffany Hyun-Jin Kim, Kenneth Brancik, Dona Dickinson, Heejo Lee, Adrian Perrig, and Bruno Sinopoli. Cyber–physical security of a smart grid infrastructure. Proceedings of the IEEE, 100(1):195–209, 2011. [CrossRef]
- Modbus Application Protocol Specification. V1. 1b. Modbus Organization, 2006.
- Lindah Kotut and Luay A Wahsheh. Survey of cyber security challenges and solutions in smart grids. In 2016 cybersecurity symposium (CYBERSEC), pages 32–37. IEEE, 2016. [CrossRef]
- Ross Anderson and Shailendra Fuloria. Who controls the off switch? In 2010 First IEEE International Conference on Smart Grid Communications, pages 96–101. IEEE, 2010. [CrossRef]
- Eric H Allen, Robert B Stuart, and Thomas E Wiedman. No light in august: power system restoration following the 2003 north american blackout. IEEE Power and Energy Magazine, 12(1):24–33, 2013. [CrossRef]
- Lipi Chhaya, Paawan Sharma, Govind Bhagwatikar, and Adesh Kumar. Wireless sensor network based smart grid communications: Cyber attacks, intrusion detection system and topology control. Electronics, 6(1):5, 2017. [CrossRef]
- R Vijayanand, D Devaraj, and B Kannapiran. Intrusion detection system for wireless mesh network using multiple support vector machine classifiers with genetic-algorithm-based feature selection. Computers & Security, 77:304–314, 2018. [CrossRef]
- JE Albuquerque Filho, Laislla CP Brandão, Bruno JT Fernandes, and Alexandre MA Maciel. A review of neural networks for anomaly detection. IEEE Access, 2022. [CrossRef]
- Mohamed Attia, Hichem Sedjelmaci, Sidi Mohammed Senouci, and El-Hassane Aglzim. A new intrusion detection approach against lethal attacks in the smart grid: temporal and spatial based detections. In 2015 Global Information Infrastructure and Networking Symposium (GIIS), pages 1–3. IEEE, 2015. [CrossRef]
- Chih-Che Sun, Adam Hahn, and Chen-Ching Liu. Cyber security of a power grid: State-of-the-art. International Journal of Electrical Power & Energy Systems, 99:45–56, 2018. [CrossRef]
- Dorothy E Denning. An intrusion-detection model. IEEE Transactions on software engineering, (2):222–232, 1987. [CrossRef]
- Varun Chandola, Arindam Banerjee, and Vipin Kumar. Anomaly detection: A survey. ACM computing surveys (CSUR), 41(3):1–58, 2009. [CrossRef]
- Panagiotis Radoglou Grammatikis, Panagiotis Sarigiannidis, Georgios Efstathopoulos, and Emmanouil Panaousis. Aries: A novel multivariate intrusion detection system for smart grid. Sensors, 20(18):5305, 2020. [CrossRef]
- Shengyi Pan, Thomas H Morris, and Uttam Adhikari. A specification-based intrusion detection framework for cyber-physical environment in electric power system. Int. J. Netw. Secur., 17(2):174–188, 2015.
- Robin Berthier and William H Sanders. Specification-based intrusion detection for advanced metering infrastructures. In 2011 IEEE 17th Pacific rim international symposium on dependable computing, pages 184–193. IEEE, 2011. [CrossRef]
- Nitasha Sahani, Ruoxi Zhu, Jin-Hee Cho, and Chen-Ching Liu. Machine learning-based intrusion detection for smart grid computing: A survey. ACM Transactions on Cyber-Physical Systems, 7(2):1–31, 2023. [CrossRef]
- Safa Otoum, Burak Kantarci, and Hussein T Mouftah. Mitigating false negative intruder decisions in wsn-based smart grid monitoring. In 2017 13th International wireless communications and mobile computing conference (IWCMC), pages 153–158. IEEE, 2017. [CrossRef]
- Bruno Bogaz Zarpelão, Rodrigo Sanches Miani, Cláudio Toshio Kawakani, and Sean Carlisto de Alvarenga. A survey of intrusion detection in internet of things. Journal of Network and Computer Applications, 84:25–37, 2017. [CrossRef]
- Ashfaq Hussain Farooqi and Farrukh Aslam Khan. Intrusion detection systems for wireless sensor networks: A survey. In International Conference on Future Generation Communication and Networking, pages 234–241. Springer, 2009.
- Prabhakaran Kasinathan, Claudio Pastrone, Maurizio A Spirito, and Mark Vinkovits. Denial-of-service detection in 6lowpan based internet of things. In 2013 IEEE 9th international conference on wireless and mobile computing, networking and communications (WiMob), pages 600–607. IEEE, 2013. [CrossRef]
- Prabhakaran Kasinathan, Gianfranco Costamagna, Hussein Khaleel, Claudio Pastrone, and Maurizio A Spirito. An ids framework for internet of things empowered by 6lowpan. In Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security, pages 1337–1340, 2013. [CrossRef]
- Linus Wallgren, Shahid Raza, and Thiemo Voigt. Routing attacks and countermeasures in the rpl-based internet of things. International Journal of Distributed Sensor Networks, 9(8):794326, 2013. [CrossRef]
- Doohwan Oh, Deokho Kim, and Won Woo Ro. A malicious pattern detection engine for embedded security systems in the internet of things. Sensors, 14(12):24188–24211, 2014. [CrossRef]
- Tsung-Han Lee, Chih-Hao Wen, Lin-Huang Chang, Hung-Shiou Chiang, and Ming-Chun Hsieh. A lightweight intrusion detection scheme based on energy consumption analysis in 6lowpan. In Advanced Technologies, Embedded and Multimedia for Human-centric Computing: HumanCom and EMC 2013, pages 1205–1213. Springer, 2014.
- Christian Cervantes, Diego Poplade, Michele Nogueira, and Aldri Santos. Detection of sinkhole attacks for supporting secure routing on 6lowpan for internet of things. In 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), pages 606–611. IEEE, 2015. [CrossRef]
- Jean-Paul A Yaacoub, Ola Salman, Hassan N Noura, Nesrine Kaaniche, Ali Chehab, and Mohamad Malli. Cyber-physical systems security: Limitations, issues and future trends. Microprocessors and microsystems, 77:103201, 2020. [CrossRef]
- Anhtuan Le, Jonathan Loo, Kok Keong Chai, and Mahdi Aiash. A specification-based ids for detecting attacks on rpl-based network topology. Information, 7(2):25, 2016. [CrossRef]
- Shahid Raza, Linus Wallgren, and Thiemo Voigt. Svelte: Real-time intrusion detection in the internet of things. Ad hoc networks, 11(8):2661–2674, 2013. [CrossRef]
- Pavan Pongle and Gurunath Chavan. Real time intrusion and wormhole attack detection in internet of things. International Journal of Computer Applications, 121(9), 2015. [CrossRef]
- Nanda Kumar Thanigaivelan, Ethiopia Nigussie, Rajeev Kumar Kanth, Seppo Virtanen, and Jouni Isoaho. Distributed internal anomaly detection system for internet-of-things. In 2016 13th IEEE annual consumer communications & networking conference (CCNC), pages 319–320. IEEE, 2016. [CrossRef]
- Mustafa Amir Faisal, Zeyar Aung, John R Williams, and Abel Sanchez. Data-stream-based intrusion detection system for advanced metering infrastructure in smart grid: A feasibility study. IEEE Systems journal, 9(1):31–44, 2014. [CrossRef]
- Saranya Parthasarathy and Deepa Kundur. Bloom filter based intrusion detection for smart grid scada. In 2012 25th IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), pages 1–6. IEEE, 2012. [CrossRef]
- Xiao Chun Yin, Zeng Guang Liu, Lewis Nkenyereye, and Bruce Ndibanje. Toward an applied cyber security solution in iot-based smart grids: An intrusion detection system approach. Sensors, 19(22):4952, 2019. [CrossRef]
- Hao Li, Guangjie Liu, Weiwei Jiang, and Yuewei Dai. Designing snort rules to detect abnormal dnp3 network data. In 2015 International Conference on Control, Automation and Information Sciences (ICCAIS), pages 343–348. IEEE, 2015. [CrossRef]
- BooJoong Kang, Kieran McLaughlin, and Sakir Sezer. Towards a stateful analysis framework for smart grid network intrusion detection. In 4th International Symposium for ICS & SCADA Cyber Security Research 2016 4, pages 124–131, 2016. [CrossRef]
- Yi Yang, Hai-Qing Xu, Lei Gao, Yu-Bo Yuan, Kieran McLaughlin, and Sakir Sezer. Multidimensional intrusion detection system for iec 61850-based scada networks. IEEE Transactions on Power Delivery, 32(2):1068–1078, 2016. [CrossRef]
- Pin-Han Wang, I-En Liao, Kuo-Fong Kao, and Jyun-Yao Huang. An intrusion detection method based on log sequence clustering of honeypot for modbus tcp protocol. In 2018 IEEE International Conference on Applied System Invention (ICASI), pages 255–258. IEEE, 2018. [CrossRef]
- Ahmed Patel, Hitham Alhussian, Jens Myrup Pedersen, Bouchaib Bounabat, Joaquim Celestino Júnior, and Sokratis Katsikas. A nifty collaborative intrusion detection and prevention architecture for smart grid ecosystems. Computers & Security, 64:92–109, 2017. [CrossRef]
- R Vijayanand, D Devaraj, and B Kannapiran. Support vector machine based intrusion detection system with reduced input features for advanced metering infrastructure of smart grid. In 2017 4th International conference on advanced computing and communication systems (ICACCS), pages 1–7. IEEE, 2017. [CrossRef]
- Fadwa Abdul Aziz Alseiari and Zeyar Aung. Real-time anomaly-based distributed intrusion detection systems for advanced metering infrastructure utilizing stream data mining. In 2015 International Conference on Smart Grid and Clean Energy Technologies (ICSGCE), pages 148–153. IEEE, 2015. [CrossRef]
- Paria Jokar and Victor CM Leung. Intrusion detection and prevention for zigbee-based home area networks in smart grids. IEEE Transactions on Smart Grid, 9(3):1800–1811, 2016. [CrossRef]
- Zihao Feng, Sujuan Qin, Xuesong Huo, Pei Pei, Ye Liang, and Liming Wang. Snort improvement on profinet rt for industrial control system intrusion detection. In 2016 2nd IEEE International Conference on Computer and Communications (ICCC), pages 942–946. IEEE, 2016. [CrossRef]
- Szu-Chuang Li, Yennun Huang, Bo-Chen Tai, and Chi-Ta Lin. Using data mining methods to detect simulated intrusions on a modbus network. In 2017 IEEE 7th International Symposium on Cloud and Service Computing (SC2), pages 143–148. IEEE, 2017. [CrossRef]
- YooJin Kwon, Huy Kang Kim, Yong Hun Lim, and Jong In Lim. A behavior-based intrusion detection technique for smart grid infrastructure. In 2015 IEEE Eindhoven PowerTech, pages 1–6. IEEE, 2015. [CrossRef]
- Junho Hong, Chen-Ching Liu, and Manimaran Govindarasu. Detection of cyber intrusions using network-based multicast messages for substation automation. In ISGT 2014, pages 1–5. IEEE, 2014.
- Shengyi Pan, Thomas Morris, and Uttam Adhikari. Developing a hybrid intrusion detection system using data mining for power systems. IEEE Transactions on Smart Grid, 6(6):3104–3113, 2015. [CrossRef]
- Niv Goldenberg and Avishai Wool. Accurate modeling of modbus/tcp for intrusion detection in scada systems. international journal of critical infrastructure protection, 6(2):63–75, 2013. [CrossRef]
- Y Yang, K McLaughlin, S Sezer, YB Yuan, and W Huang. Stateful intrusion detection for iec 60870-5-104 scada security. In 2014 IEEE PES General Meeting| Conference & Exposition, pages 1–5. IEEE, 2014. [CrossRef]
- Yi Yang, Kieran McLaughlin, Tim Littler, Sakir Sezer, Bernardi Pranggono, and HF Wang. Intrusion detection system for iec 60870-5-104 based scada networks. In 2013 IEEE power & energy society general meeting, pages 1–5. Ieee, 2013. [CrossRef]
| SL# | Literature Work | Target System | Attacks | Detection Techniques |
|---|---|---|---|---|
| 1 | The 2015 Ukraine Blackout [3] | The SCADA of the Ukraine Grid | False Data Injection (FDI) and Denial-of Services (DoS) | Not provided |
| 2 | IDS Framework [26] | HAN and NAN and many IDS sensors in WAN. | Denial-of Services (DoS) | Anomaly based. |
| 3 | IDS for Advanced Metering Infrastructure [73] | Advanced metering infrastructure (AMI) | Denial-of Services (DoS) | Data-Stream based |
| 4 | Bloom Filter Based IDS [74] | SCADA | HMI compromise, Man-in-the-middle attack | Anomaly based |
| 5 | Cyber Security Solution towards IDS [75] | DNP3 in SCADA | Length Overflow Attack, DFC Flag Attack, and Reset Function Attack | Protocol-based detection rules |
| 6 | The Snort detection rule template for anomaly DNP3 [76] | DNP3 in SCADA | Protocol anomalies, reconnaissance attack, Denial-of Services (DoS) attack | Signature-based |
| 7 | A Stateful Analysis Framework of IDS [77] | Substation | Denial-of Services (DoS), Port scanning, MMS, SNMP attacks | Specification-based |
| 8 | Multidimensional IDS [78] | Substation | DoS, MiTM, Packet Injection attacks | Specification-based |
| 9 | IDS based on log sequence clustering of honeypot [79] | Modbus TCP in SCADA | Reconnaissance, DoS attacks | Anomaly based |
| 10 | A nifty collaborative IDS [80] | Entire SG | DoS, Packet splitting, Command injection, Duplicate insertion, Payload mutation | Anomaly based |
| 11 | Support vector machine based IDS [81] | AMI | Worms, Fuzzer, DoS, Backdoor attacks | Anomaly based |
| 12 | IDS for blackhole attacks in a smart grid [5] | AMI | Blackhole attack | Anomaly based |
| 13 | Case analysis based IDS for SG [9] | AMI | L2l, DoS, Botnet, Secure shell attacks | Anomaly based |
| 14 | Real-time anomaly-based distributed IDS for AMI [82] | AMI | Port scanning, DoS attacks | Anomaly based |
| 15 | IDS and prevention for ZigBee-based home area networks in SG [83] | AMI | Spoofing, Radio Jamming, Replay, Black-off manipulation | Specification-based |
| 16 | Machine learning-based IDS on an industrial Modbus/TCP data set [15] | Modbus TCP in SCADA | Reconnaissance, DoS attacks | Anomaly based |
| 17 | The IDS for Profinet DCP [84] | Profinet in SCADA | Reconnaissance, DoS, MiTM, Protocol anomalies | HYbrid |
| 18 | Data mining methods to detect simulated intrusions on a Modbus network [85] | Modbus TCP in SCADA | Reconnaissance, DoS, Command injection, Response injection attacks | Anomaly based |
| 19 | A behavior-based intrusion detection technique for smart grid infrastructure [86] | Substation | Port scanning, DoS, GOOSE, MMS, SNMP attacks | Specification based |
| 20 | Power utility automation cybersecurity: IEC 61850 specification of an IDS [12] | Substation | Not provided | Specification based |
| 21 | IDS of cyber intrusions using network-based multicast messages for substation automation [87] | Substation | Replay, DoS attacks | Specification based |
| 22 | IDS for IEC 61850 based smart substations [11] | Substation | Packet injection, MiTM, DoS attacks | Specification based |
| 23 | a hybrid IDS using data mining for power systems [88] | Synchrophasor | Single-line-to-ground faults, Replay attack, Command injection, Disable relay attack | Hybrid |
| 24 | Model based IDS for synchrophasor applications in SG [19] | Synchrophasor | ARP spoofing, Port scanning, GPS scanning, Replay attack, Command injection, Physical attacks | Hybrid |
| 25 | IDS for network security in synchrophasor [20] | Synchrophasor | Reconnaissance, MiTM, DoS attacks | Specification based |
| 26 | Accurate modeling of Modbus/TCP for IDS in SCADA [89] | Modbus TCP in SCADA | Not provided | Anomaly based |
| 27 | Stateful IDS for IEC 60870-5-104 SCADA security [90] | SCADA | Packet injection, Replay attack, Data manipulation | Specification based |
| 28 | IDS for IEC 60870-5-104 based SCADA networks [91] | SCADA | Unauthorized read/reset command, Spontaneous packet storm, Buffer overflow | Hybrid |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).