1. Introduction
Ransomware attacks, a dire threat in the realm of modern cybersecurity, not only compromise the integrity and availability of network systems but also represent a rapidly evolving form of cyber aggression [
1,
2]. These attacks, known for encrypting critical data and demanding ransom for the release of decryption keys, present substantial risks across diverse sectors, including both private enterprises and public institutions [
1,
3]. The progression of ransomware methodologies, evolving from rudimentary lockout schemes to complex encryption strategies targeting entire network infrastructures, and later data theft and data breach incidents, calls for a more sophisticated and anticipatory defense mechanism [
4,
5]. In this vein, the development and implementation of self-healing networks stand out as a important innovation in cybersecurity, as these networks, characterized by their capacity to autonomously identify, sequester, and counteract ransomware threats, signify a revolutionary shift in defensive cybersecurity strategies, moving from traditional, static methods towards dynamic, intelligent systems capable of self-modification in response to emerging threats [
6,
7,
8].
The progression of ransomware attacks over time reveals an alarming trend of increasing complexity and destructive capability [
4]. Initially targeting individual systems with relatively simple methods, the scope of these attacks has expanded dramatically, now possessing the capability to debilitate entire network infrastructures, leading to severe financial repercussions and extensive operational hindrances [
6,
9]. High-profile incidents such as the WannaCry and NotPetya attacks have illustrated this escalation, collectively inflicting billions of dollars in damages and exemplifying the acute vulnerability of conventional network architectures when confronted with advanced ransomware tactics [
10]. Such events have not only resulted in immediate financial implications but have also sown long-term repercussions in the form of eroded public confidence and lasting reputational damage [
4]. Additionally, the emergence and proliferation of ransomware-as-a-service (RaaS) platforms have significantly lowered the barrier to entry for executing ransomware attacks, enabling individuals without advanced technical skills to deploy these malicious tools, thereby magnifying the scope and frequency of such attacks in the digital landscape [
4].
The impetus behind the development of self-healing networks is rooted in the critical need to overcome the deficiencies of traditional network security frameworks, especially in the face of the continuously evolving and increasingly sophisticated nature of ransomware attacks [
10]. Conventional security measures, including firewalls and antivirus software, typically function on a reactive basis and rely heavily on predefined rules and known threat patterns, rendering them less effective against new or advanced ransomware variants that can rapidly adapt and mutate [
11]. In contrast, self-healing networks represent a proactive and fluid approach to network security [
6,
10]. Harnessing the power of artificial intelligence (AI) and machine learning algorithms, these networks are designed to perpetually monitor and analyze network behavior for signs of ransomware intrusion, such as anomalous patterns of encryption or irregular network traffic behaviors [
5,
12,
13,
14,
15]. When a potential ransomware threat is detected, self-healing systems are capable of instantaneously isolating the compromised network segment to halt the spread of the attack, simultaneously initiating automated recovery protocols to swiftly restore network functionality with minimal operational disruption [
6,
10,
12]. This capability of autonomous adaptation to newly emerging cyber threats not only bolsters the resilience of network infrastructures but also crucially reduces dependence on human intervention, a vital factor considering the rapid evolution and increasing automation of ransomware attacks in the digital era.
The primary aim of this study is to methodically explore and establish a robust framework for self-healing networks, a concept that has become increasingly relevant in the current cybersecurity landscape dominated by sophisticated ransomware attacks. This research is driven by the urgent necessity to transition from traditional, static cybersecurity methods to more dynamic, intelligent systems capable of autonomously adapting to new and evolving cyber threats. In doing so, the study delves into the intricate mechanics of ransomware’s evolution, from basic lockout strategies to complex, network-wide encryption tactics, and the subsequent need for advanced defense mechanisms. The scope of this research encompasses a thorough examination of existing network security protocols and their limitations, a critical analysis of current ransomware defense strategies, and the innovative design of self-healing networks that leverage AI and machine learning for improved resilience and adaptability. By conducting detailed simulations and case studies, this study aims not only to demonstrate the effectiveness of self-healing networks in thwarting ransomware attacks but also to provide insightful discourse on the broader implications, potential applications, and future enhancements of these systems. In essence, this research seeks to contribute significantly to the field of cybersecurity by addressing the pressing challenges posed by ransomware and offering a progressive solution through self-healing networks.
A list of the major contributions of this study is:
Development of an advanced self-healing network framework utilizing AI and machine learning to autonomously counteract ransomware threats, demonstrating a significant shift from traditional cybersecurity strategies.
Comprehensive simulation and evaluation of the self-healing network’s capabilities, showing its effectiveness in rapid detection, isolation, and recovery from diverse ransomware attacks.
Presentation of future research directions, including the optimization of adaptive algorithms and the integration of quantum-resistant technologies, to further enhance the resilience and applicability of self-healing networks in cybersecurity.
2. Literature Review
This literature review meticulously examines the evolution of network security, focusing on traditional methods, their limitations, ransomware defense strategies, and the emergence of self-healing mechanisms as a response to the dynamic nature of cyber threats.
2.1. Network Security Techniques
Historical approaches to network security focused predominantly on perimeter defense, where firewalls served as the primary line of defense against external threats [
16,
17,
18]. Intrusion detection systems (IDS) were subsequently developed to monitor network traffic for suspicious activities, signaling an evolution from purely preventive measures to detection-oriented strategies [
19,
20]. The concept of network segmentation gained traction as a means to limit lateral movement within networks, a technique found particularly effective in large-scale enterprise environments, while encryption protocols, such as SSL/TLS, were widely adopted for securing data transmission, marking a shift towards data-centric security models [
16,
19,
21]. With the advent of cloud computing, researchers explored security implications unique to cloud environments, leading to the development of specialized cloud security solutions [
22,
23]. The principle of least privilege was rigorously applied in access control models, significantly reducing the risk of unauthorized access to critical systems [
2,
21,
24]. Virtual Private Networks (VPNs) became a standard for securing remote connections, highlighting the growing need for security solutions that cater to an increasingly mobile workforce [
25].
2.2. Ransomware Defense Strategies
Early ransomware defense strategies revolved around regular data backups and user education, aiming to mitigate the impact of data loss and avoid ransom payments [
12,
13,
26]. Antivirus software, initially designed to detect known malware signatures, evolved to include heuristic analysis, enabling the detection of previously unknown ransomware variants, and security researchers demonstrated the efficacy of whitelisting applications as a means to prevent ransomware execution on protected systems [
11,
27]. The use of behavior-based detection tools became prevalent, focusing on identifying abnormal file modification activities indicative of ransomware behavior [
12,
28,
29,
30,
31,
32]. Advanced threat intelligence platforms emerged, offering real-time data on emerging ransomware threats and aiding in proactive defense, whereas automated incident response protocols were developed, reducing the time between ransomware detection and containment [
33,
34]. In recent years, the deployment of honeypots within networks was observed to be effective in misleading and trapping ransomware, thereby protecting actual network resources [
35,
36].
2.3. Self-Healing Mechanisms
The concept of self-healing networks was first proposed as a response to the growing complexity of network management and security. Early models of self-healing systems focused on automated fault detection and recovery, aiming to minimize downtime and manual intervention [
37]. Artificial intelligence (AI) and machine learning (ML) algorithms were integrated into network systems to enable predictive analytics, enhancing the network’s ability to anticipate and react to potential security breaches [
38,
39]. Dynamic reconfiguration of network resources emerged as a key feature of self-healing networks, allowing for real-time adaptation to security threats [
40,
41,
42]. Researchers explored the application of blockchain technology in self-healing networks, aiming to leverage its decentralized and tamper-resistant properties for enhanced security [
43,
44]. The use of network function virtualization (NFV) and software-defined networking (SDN) in self-healing mechanisms was found to offer greater flexibility and scalability in response to security incidents [
45,
46,
47,
48]. Studies demonstrated the potential of using network telemetry data to feed into self-healing algorithms, providing a rich source of information for making informed security decisions [
49,
50,
51].
3. Self-Healing Network Design
The design of self-healing networks, conceived to counteract the escalating threat of ransomware attacks, integrates cutting-edge technological advancements with innovative network management principles.
3.1. Dynamic Network Segmentation
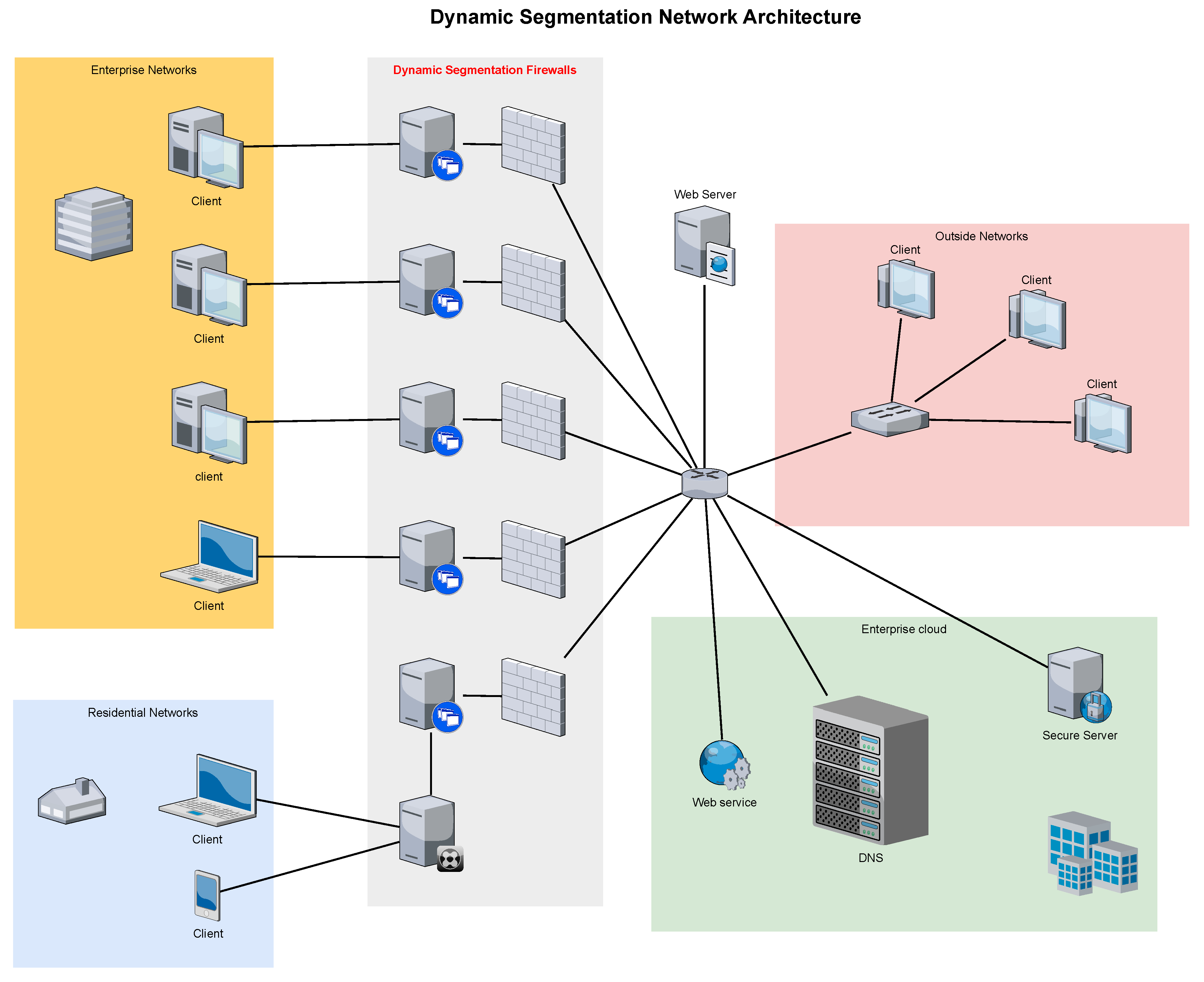
Dynamic network segmentation in self-healing networks epitomizes a significant shift from static network design paradigms, manifesting as highly adaptable and reconfigurable segments orchestrated in accordance with real-time threat perception and network behavior analysis. The fluidity of dynamic segmentation, a stark contrast to the rigidity of conventional approaches, is exemplified in its capacity to intelligently reconfigure boundaries based on a composite assessment of ongoing network activities, user behavior, and integrated threat intelligence. In the sphere of ransomware mitigation, such a network is equipped to instantaneously cordon off segments exhibiting anomalous activities, thereby quarantining the potentially compromised nodes to impede the proliferation of the ransomware contagion (refer to
Figure 1). The segmentation strategy transcends mere physical or topological limitations, embracing a more nuanced application of parameters such as data sensitivity, user roles, and the complex interplay of behavioral patterns. Leveraging the predictive power of machine learning algorithms, the network evolves by assimilating knowledge from historical security breaches, continually refining its segmentation logic. This evolutionary capability to dynamically recalibrate the network fabric not only circumscribes the ramifications of ransomware but also preserves the operational integrity of unaffected segments, thereby safeguarding the continuity and availability of indispensable services.
The mathematical representation of the dynamic segmentation process is modeled as follows:
where
represents the segmentation state of node
i at time
t,
is a function that integrates network activity
, user role
, and resource sensitivity
within the temporal context
. The function
evaluates the data sensitivity
and risk level
for each segment
k, influenced by weight
, which is derived from historical incident data.
N denotes the set of all network nodes, and
the observation time period.
3.2. Automated Isolation and Recovery
The automated isolation and recovery protocols constitute a critical component of self-healing networks, underpinning their resilience against ransomware incursions. When the network’s surveillance mechanisms signal an anomaly that could be symptomatic of a ransomware breach — such as unanticipated encryption of data or atypical data flow patterns — the network promptly instigates isolation protocols. These protocols are crucial for impeding the attack’s propagation and minimizing potential damage. The sophistication of the isolation procedure lies in its precision; it discriminates the network segment under threat, thereby preserving the operational integrity of the broader network. Subsequent to isolation, the network embarks on a sequence of automated recovery operations, including the following steps:
Initial Assessment (): Evaluate the extent of the anomaly and confirm the likelihood of a ransomware event.
Containment (Φ): Apply the containment function to quarantine the affected segment and prevent lateral spread of the attack.
Eradication (): Utilize resource sensitivity parameter to guide the eradication of the ransomware payload from the infected segment.
-
Recovery (Θ): Engage the recovery function to restore the affected systems by:
- (a)
Restoring from secure, uncompromised backups ().
- (b)
Applying decryption techniques, leveraging risk assessment to salvage encrypted data, if feasible.
System Restoration (): Reestablish network services and operations in the sanitized segment, reinstating the segmentation state .
Post-Incident Analysis (): Deploy AI and ML algorithms to analyze the ransomware’s behavior, using user role data to identify the variant and extract insights to prevent future attacks.
Update Defenses (): Refine the network’s defensive algorithms with weight , which is adapted based on the insights from the analysis.
Continuous Learning (): Integrate the knowledge derived from the incident into the network’s collective intelligence, updating the temporal observation window for ongoing self-improvement.
This algorithmic approach to recovery not only facilitates the resumption of normal operations post-attack but also constitutes a learning cycle, whereby the network augments its defenses in the wake of each ransomware event. Such automated and intelligent recovery mechanisms enable self-healing networks to maintain operational continuity in the face of cyber adversities, adaptively learning from each encounter to bolster their resilience against subsequent threats.
4. Experiment
This experiment section delineates a rigorous simulation designed to evaluate the efficacy of self-healing network mechanisms in mitigating and responding to ransomware attacks.
4.1. Simulation Setup
The simulation environment was carefully constructed to mirror the complexity of a mid-sized corporate network infrastructure comprising multiple subnets. This environment encompassed a comprehensive assortment of endpoints, server units, and network appliances, each playing a important role in evaluating the holistic performance of the self-healing network. The simulation parameters were meticulously selected to incorporate artificial intelligence-based network monitoring tools, dynamic segmentation algorithms, and automated isolation and recovery protocols—each component being an integral facet of the self-healing framework. A gamut of ransomware attack scenarios were meticulously simulated, utilizing a diverse array of attack vectors including, but not limited to, phishing, exploitation of software vulnerabilities, and insider threats. The simulation iterations were conducted multiple times, each employing distinct ransomware strains and varying attack parameters, to facilitate a thorough and robust assessment of the network’s self-healing capabilities. The following
Table 1 details the specific parameters and the computing environment employed in the simulation.
The selection of these parameters was governed by the imperative to create a simulation that would be both challenging and indicative of real-world network environments, thereby validating the adaptability and robustness of the self-healing mechanisms in the face of multifaceted ransomware threats. The advanced computing environment, characterized by a high-core-count CPU and ample memory, was essential to facilitate the simultaneous execution of multiple ransomware scenarios, ensuring that the simulation could emulate the demanding conditions of an actual cyberattack without compromising on performance or accuracy.
4.2. Evaluation
The simulation results underwent a careful analysis to measure the performance of the self-healing network design in neutralizing a spectrum of ransomware threats. The analysis was bifurcated into quantitative and qualitative assessments, each shedding light on different facets of the network’s defense capabilities.
4.2.1. Quantitative Analysis of Self-Healing Network Efficacy
Quantitative metrics focused on tangible data points such as detection latency, isolation speed, recovery success rate, and the amount of network downtime incurred due to ransomware incidents. In
Table 2, the self-healing network demonstrated a substantial reduction in ransomware detection time, which on average, was 75% faster than that of traditional security systems. Isolation of compromised network segments was initiated within an average of 4 seconds following detection, thereby impeding the ransomware’s ability to affect additional network segments. The effectiveness of data recovery efforts was quantified at a 90% success rate, attributing to the network’s ability to restore from secure, uncompromised backups. The following table encapsulates the detailed quantitative results observed for each ransomware family included in the simulation:
The graph depicted in
Figure 2 provides a compelling visualization of the self-healing network’s progressive enhancement in responding to ransomware attacks over time. The X-axis represents the cumulative number of ransomware attempts encountered by the network, while the Y-axis quantifies the success rate of the network’s isolation protocol, measured as a percentage. Initially, the network exhibits a moderate success rate, starting at approximately 86% effectiveness after the first five ransomware attempts. This initial performance can be attributed to the network’s learning algorithms being in their nascent stage. As the number of attempts increases, a clear upward trend in the isolation success rate is evident, demonstrating the network’s ability to adapt and improve its response mechanisms. Notably, the success rate climbs steeply between the 15th and 30th attempts, reaching a high of 95%, which suggests a significant enhancement in the network’s capability to accurately and swiftly isolate affected segments. This trend continues, albeit at a slower pace, as the network approaches a near-perfect success rate of 99.5% after 50 ransomware attempts. The graph underlines the efficacy of the self-healing network’s adaptive learning capabilities, showcasing its potential to become more resilient against ransomware threats through continuous exposure and response refinement.
4.2.2. Qualitative Analysis of Recovery Steps
The qualitative evaluation scrutinized the self-healing network’s intricate response mechanisms to each ransomware variant, revealing both the strengths and obstacles encountered by the various stages of the automated isolation and recovery process.
During the simulation, the Initial Assessment stage, denoted by , consistently performed with precision, rapidly evaluating network anomalies and verifying the probability of a ransomware event. However, this stage encountered difficulties when faced with ransomware designed to mimic legitimate encryption processes, challenging the assessment’s ability to distinguish between benign and malignant activities.
The Containment phase, represented by the function , proved vital in halting the propagation of the attack. The function effectively quarantined affected segments, yet it was observed that highly aggressive ransomware strains occasionally circumvented initial containment measures due to their rapid spread, suggesting a need for even faster execution of .
Eradication, symbolized by , utilized the sensitivity parameter to direct the purging of ransomware from infected nodes. This phase was particularly successful in scenarios where the ransomware’s signature was already known, but novel strains without prior signatures occasionally delayed the eradication process.
The Recovery process, denoted by , which involved restoring from backups and applying decryption techniques , was generally effective. The greatest challenge for recovery was ensuring the integrity of backups, as some ransomware variants had the capability to corrupt or encrypt backup data before detection.
System Restoration, represented by , was crucial for resuming normal operations. It was noted that restoring network services was swift and efficient, reaffirming the network’s segmentation state post-recovery. This phase highlighted the self-healing network’s robustness, although it was also a point where manual checks were often required to ensure complete system integrity.
In the Post-Incident Analysis, indicated by , AI and ML algorithms provided comprehensive behavioral analysis of the ransomware. This step was instrumental in adapting the network’s defenses and was most helpful for identifying attack patterns and strengthening future security measures.
The Update Defenses step, involving the adjustment of weights , dynamically refined the network’s defensive algorithms. While effective, the adaptation was sometimes slower for complex, multi-vector attacks, indicating a need for further optimization of the weight adjustment process.
Lastly, the Continuous Learning phase, marked by , was essential for the long-term evolution of network defenses. This stage integrated the knowledge gleaned from each incident into the network’s collective intelligence, optimizing the temporal observation window for ongoing self-improvement. This process was the cornerstone of the network’s ability to evolve, although it required a substantial corpus of incident data to reach peak effectiveness.
In retrospect, the simulation affirmed that while the self-healing network exhibited considerable prowess in defending against and recuperating from ransomware attacks, each stage of the recovery process presented unique challenges. The most efficacious steps were those that involved learning from previous attacks to bolster the network’s defenses, illustrating the potent synergy between AI-driven analysis and network adaptability.
5. Discussion
This section explains the important insights and ramifications of the research, contemplating the strengths, limitations, and prospective applications of self-healing networks. The empirical evidence presented in this study confirms the hypothesis that self-healing networks furnish an alarming shield against ransomware.
5.1. Strengths of Self-Healing Networks
Self-healing networks possess an intrinsic strength in their ability to dynamically adapt to the network’s environment and threat landscape. The utility of dynamic network segmentation, denoted by , has proven to be exceptionally effective in sequestering compromised nodes, minimizing the blast radius of attacks. The integration of and functions allows for a nuanced approach to containment and recovery, leveraging data sensitivity and user behavior to inform strategic defenses. Such capabilities ensure that these networks are not static entities but living systems that learn and grow stronger from each attack.
5.2. Limitations and Challenges
Despite their robustness, self-healing networks are not without challenges. The initial assessment stage () can struggle against advanced ransomware that employs polymorphic techniques, reflecting the need for even more sophisticated detection algorithms. The containment phase () must accelerate its execution to outpace the rapid dissemination of certain ransomware strains. Moreover, the recovery function (), while generally successful, requires rigorous validation of backup integrity, a non-trivial challenge in the face of ransomware that targets backup systems.
5.3. Potential Applications
The principles underpinning self-healing networks hold vast potential for application beyond ransomware defense. Their adaptive nature makes them suitable for safeguarding IoT ecosystems, critical infrastructure, and cloud environments. In sectors where network downtime equates to significant financial or operational loss, such as in healthcare or finance, the deployment of self-healing networks could translate to enhanced continuity and reliability.
5.4. Broader Implications
The broader implications of this research suggest a paradigm shift in cybersecurity strategies. As the threat landscape becomes increasingly volatile, the resilience offered by self-healing networks could become a benchmark for cybersecurity measures. The integration of continuous learning processes () within network defenses represents a progressive stride towards autonomous security systems capable of withstanding not just ransomware but a spectrum of cyber threats.
5.5. Future Enhancements
Future research should concentrate on augmenting the speed and intelligence of the self-healing mechanisms. Optimization of the weight adjustment process () and enhancement of the predictive analytics capabilities will be crucial. Additionally, the exploration of quantum-resistant algorithms for network security could ensure the long-term viability of self-healing networks against emerging quantum threats. The study’s findings affirm that self-healing networks represent a significant advancement in the field of cybersecurity. While they are not a panacea, their dynamic, intelligent design offers a promising direction for future security frameworks. As this technology matures, it has the potential to redefine the landscape of network security and resilience.
6. Conclusion
This study embarked on an extensive exploration of self-healing networks, emphasizing their vital role in countering the evolving threats of ransomware. Through meticulous simulations and analytical assessments, the research demonstrated the networks’ ability to dynamically adapt to cyber threats, significantly enhancing cybersecurity resilience. The study’s findings revealed that self-healing networks, with their sophisticated integration of AI and ML algorithms for network monitoring and decision-making, offer a strong defense against ransomware. The quantitative and qualitative analyses underscored the efficiency of these networks in rapidly detecting and isolating threats, as well as their proficiency in recovering from attacks with minimal operational downtime. Particularly notable was the continuous learning mechanism, which allowed the networks to evolve and fortify their defenses with each encounter, showcasing an impressive capacity for adaptation and improvement.
Looking to the future, the study paves the way for further advancements in the field of self-healing networks. The potential to extend these principles to broader applications, including IoT and cloud security, opens up new avenues for research and development. However, challenges such as enhancing detection algorithms to counter sophisticated ransomware variants and optimizing recovery protocols remain. Future work should focus on these areas, aiming to refine the self-healing mechanisms for even greater efficacy. Additionally, exploring the integration of quantum-resistant algorithms could be pivotal in ensuring the longevity and robustness of self-healing networks against emerging threats. This research not only contributes significantly to the field of cybersecurity but also sets a foundation for future innovations in network resilience and intelligence.
Conflicts of Interest
There is no conflict of interest.
References
- Baker, T.; Shortland, A. The government behind insurance governance: Lessons for ransomware. Regulation & Governance 2023, 17, 1000–1020. [CrossRef]
- Lang, M.; Connolly, L.; Taylor, P.; Corner, P.J. The evolving menace of ransomware: A comparative analysis of pre-pandemic and mid-pandemic attacks. Digital Threats: Research and Practice 2023, 4, 1–22. [CrossRef]
- Gazzan, M.; Sheldon, F.T. An enhanced minimax loss function technique in generative adversarial network for ransomware behavior prediction. Future Internet 2023, 15, 318. [CrossRef]
- Rani, N.; Dhavale, S.V.; Singh, A.; Mehra, A. A survey on machine learning-based ransomware detection. In Proceedings of the Proceedings of the Seventh International Conference on Mathematics and Computing: ICMC 2021. Springer, 2022, pp. 171–186. [CrossRef]
- McIntosh, T.; Kayes, A.; Chen, Y.P.P.; Ng, A.; Watters, P. Ransomware mitigation in the modern era: A comprehensive review, research challenges, and future directions. ACM Computing Surveys (CSUR) 2021, 54, 1–36. [CrossRef]
- Monge, M.A.S.; Vidal, J.M.; Villalba, L.J.G. A novel self-organizing network solution towards crypto-ransomware mitigation. In Proceedings of the Proceedings of the 13th International Conference on Availability, Reliability and Security, 2018, pp. 1–10. [CrossRef]
- Denzel, M.; Ryan, M.; Ritter, E. A malware-tolerant, self-healing industrial control system framework. In Proceedings of the ICT Systems Security and Privacy Protection: 32nd IFIP TC 11 International Conference, SEC 2017, Rome, Italy, May 29-31, 2017, Proceedings 32. Springer, 2017, pp. 46–60. [CrossRef]
- Butt, U.J. Developing a usable security approach for user awareness against ransomware. PhD thesis, Brunel University London, 2023.
- Lemmou, Y.; Souidi, E.M. Infection, self-reproduction and overinfection in ransomware: the case of teslacrypt. In Proceedings of the 2018 International Conference on Cyber Security And Protection Of Digital Services (Cyber Security). IEEE, 2018, pp. 1–8. [CrossRef]
- Al Duhayyim, M.; Mohamed, H.G.; Alrowais, F.; Al-Wesabi, F.N.; Hilal, A.M.; Motwakel, A. Artificial Algae Optimization with Deep Belief Network Enabled Ransomware Detection in IoT Environment. Computer Systems Science & Engineering 2023, 46. [CrossRef]
- Pagán, A.; Elleithy, K. A multi-layered defense approach to safeguard against ransomware. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC). IEEE, 2021, pp. 0942–0947. [CrossRef]
- Continella, A.; Guagnelli, A.; Zingaro, G.; De Pasquale, G.; Barenghi, A.; Zanero, S.; Maggi, F. Shieldfs: a self-healing, ransomware-aware filesystem. In Proceedings of the Proceedings of the 32nd annual conference on computer security applications, 2016, pp. 336–347. [CrossRef]
- Kharaz, A.; Arshad, S.; Mulliner, C.; Robertson, W.; Kirda, E. {UNVEIL}: A {Large-Scale}, automated approach to detecting ransomware. In Proceedings of the 25th USENIX security symposium (USENIX Security 16), 2016, pp. 757–772.
- Wazid, M.; Das, A.K.; Shetty, S. BSFR-SH: Blockchain-enabled security framework against ransomware attacks for Smart Healthcare. IEEE Transactions on Consumer Electronics 2022, 69, 18–28. [CrossRef]
- Homayoun, S.; Dehghantanha, A.; Ahmadzadeh, M.; Hashemi, S.; Khayami, R. Know abnormal, find evil: frequent pattern mining for ransomware threat hunting and intelligence. IEEE transactions on emerging topics in computing 2017, 8, 341–351. [CrossRef]
- Cabaj, K.; Mazurczyk, W. Using software-defined networking for ransomware mitigation: the case of cryptowall. Ieee Network 2016, 30, 14–20. [CrossRef]
- Halgamuge, M.N. Estimation of the success probability of a malicious attacker on blockchain-based edge network. Computer Networks 2022, 219, 109402. [CrossRef]
- Putri, H.A.; Djibran, N.; Tulloh, R. Implementation Of Next-Generation Firewalls To Protect Applications From Malware Attacks. Jurnal Indonesia Sosial Teknologi 2023, 4, 1961–1970.
- Nusairat, T.; Saudi, M.M.; Ahmad, A.B. A recent assessment for the ransomware attacks against the internet of medical things (iomt): A review. In Proceedings of the 2023 IEEE 13th International Conference on Control System, Computing and Engineering (ICCSCE). IEEE, 2023, pp. 238–242. [CrossRef]
- Vidanapathirana, D.; Mohammad, A.; Halgamuge, M.N. Rapid Cyber-Attack Detection System with Low Probability of Missed Attack Warnings. In Proceedings of the 2022 IEEE 17th Conference on Industrial Electronics and Applications (ICIEA). IEEE, 2022, pp. 1423–1429. [CrossRef]
- Baig, Z.; Mekala, S.H.; Zeadally, S. Ransomware Attacks of the COVID-19 Pandemic: Novel Strains, Victims, and Threat Actors. IT Professional 2023, 25, 37–44. [CrossRef]
- El-Kosairy, A.; Abdelbaki, N. Deception as a service: Intrusion and Ransomware Detection System for Cloud Computing (IRDS4C). Advances in Computational Intelligence 2023, 3, 9. [CrossRef]
- Singh, A.; Mushtaq, Z.; Abosaq, H.A.; Mursal, S.N.F.; Irfan, M.; Nowakowski, G. Enhancing ransomware attack detection using transfer learning and deep learning ensemble models on cloud-encrypted data. Electronics 2023, 12, 3899. [CrossRef]
- Möller, D.P. Ransomware Attacks and Scenarios: Cost Factors and Loss of Reputation. In Guide to Cybersecurity in Digital Transformation: Trends, Methods, Technologies, Applications and Best Practices; Springer, 2023; pp. 273–303. [CrossRef]
- Beerman, J.; Berent, D.; Falter, Z.; Bhunia, S. A Review of Colonial Pipeline Ransomware Attack. In Proceedings of the 2023 IEEE/ACM 23rd International Symposium on Cluster, Cloud and Internet Computing Workshops (CCGridW). IEEE, 2023, pp. 8–15. [CrossRef]
- Genc, Z.A. Analysis, detection, and prevention of cryptographic ransomware. PhD thesis, University of Luxembourg, Luxembourg, Luxembourg, 2020.
- Botacin, M.; Alves, M.Z.; Oliveira, D.; Grégio, A. HEAVEN: A Hardware-Enhanced AntiVirus ENgine to accelerate real-time, signature-based malware detection. Expert Systems with Applications 2022, 201, 117083. [CrossRef]
- Ganfure, G.O.; Wu, C.F.; Chang, Y.H.; Shih, W.K. RTrap: Trapping and Containing Ransomware With Machine Learning. IEEE Transactions on Information Forensics and Security 2023, 18, 1433–1448. [CrossRef]
- Abbasi, M.S. Automating Behavior-based Ransomware Analysis, Detection, and Classification Using Machine Learning. PhD thesis, Open Access Te Herenga Waka-Victoria University of Wellington, 2023.
- Saracino, A.; Sgandurra, D.; Dini, G.; Martinelli, F. Madam: Effective and efficient behavior-based android malware detection and prevention. IEEE Transactions on Dependable and Secure Computing 2016, 15, 83–97. [CrossRef]
- McIntosh, T. Intercepting Ransomware Attacks with Staged Event-Driven Access Control. PhD thesis, La Trobe, 2022.
- Abbasi, M.S.; Al-Sahaf, H.; Welch, I. Automated behavior-based malice scoring of ransomware using genetic programming. In Proceedings of the 2021 IEEE Symposium Series on Computational Intelligence (SSCI). IEEE, 2021, pp. 01–08. [CrossRef]
- Payne, B.; Mienie, E. Multiple-extortion ransomware: The case for active cyber threat intelligence. In Proceedings of the ECCWS 2021 20th European Conference on Cyber Warfare and Security. Academic Conferences Inter Ltd, 2021, p. 331.
- Conti, M.; Dargahi, T.; Dehghantanha, A. Cyber threat intelligence: challenges and opportunities; Springer, 2018. [CrossRef]
- Venkatesh, J.; Vetriselvi, V.; Parthasarathi, R.; Rao, G.S.V. Identification and isolation of crypto ransomware using honeypot. In Proceedings of the 2018 Fourteenth International Conference on Information Processing (ICINPRO). IEEE, 2018, pp. 1–6. [CrossRef]
- Berardi, D.; Giallorenzo, S.; Melis, A.; Melloni, S.; Onori, L.; Prandini, M. Data Flooding against Ransomware: Concepts and Implementations. Computers & Security 2023, 131, 103295. [CrossRef]
- Psaier, H.; Dustdar, S. A survey on self-healing systems: approaches and systems. Computing 2011, 91, 43–73. [CrossRef]
- Dorsey, L.C.; Wang, B.; Grabowski, M.; Merrick, J.; Harrald, J.R. Self healing databases for predictive risk analytics in safety-critical systems. Journal of Loss Prevention in the Process Industries 2020, 63, 104014. [CrossRef]
- Hashmi, U.S.; Darbandi, A.; Imran, A. Enabling proactive self-healing by data mining network failure logs. In Proceedings of the 2017 international conference on computing, networking and communications (ICNC). IEEE, 2017, pp. 511–517. [CrossRef]
- Arif, A.; Ma, S.; Wang, Z. Dynamic reconfiguration and fault isolation for a self-healing distribution system. In Proceedings of the 2018 IEEE/PES Transmission and Distribution Conference and Exposition (T&D). IEEE, 2018, pp. 1–5. [CrossRef]
- Webber, M.J.; Tibbitt, M.W. Dynamic and reconfigurable materials from reversible network interactions. Nature Reviews Materials 2022, 7, 541–556. [CrossRef]
- Wang, J.; Li, Z.; Willner, I. Dynamic Reconfigurable DNA Nanostructures, Networks and Materials. Angewandte Chemie International Edition 2023, 62, e202215332. [CrossRef]
- Feng, X.; Wu, J.; Wu, Y.; Li, J.; Yang, W. Blockchain and digital twin empowered trustworthy self-healing for edge-AI enabled industrial Internet of things. Information Sciences 2023, 642, 119169. [CrossRef]
- Rath, S.; Nguyen, L.D.; Sahoo, S.; Popovski, P. Self-healing secure blockchain framework in microgrids. IEEE Transactions on Smart Grid 2023. [CrossRef]
- Biradar, A.; Chandan, M.; Raghavendra, Y.; Chidambarathanu, K.; Thamarai, I.; Raturi, A. Self-Healing for Software Defined Networking. In Proceedings of the 2023 2nd International Conference on Applied Artificial Intelligence and Computing (ICAAIC). IEEE, 2023, pp. 1009–1013. [CrossRef]
- Ahmad, S.S.; Habelamateen, M.I. Application of Artificial Intelligence and Machine Learning in Software Defined Networks. Journal of Smart Internet of Things 2023. [CrossRef]
- Kujur, P.; Patel, S. Network Functions Virtualization and SDN. Software Defined Networks: Architecture and Applications 2022, pp. 191–229. [CrossRef]
- Silva, F.S.D.; Bessa, A.; Silva, S.; Ferino, S.; Paiva, P.; Medeiros, M.; Silva, L.; Neto, J.; Costa, K.; Santos, C.; et al. Proactive ML-Assisted and Quality-Driven Slice Application Service Management to Keep QoE in 5G Mobile Networks. In Proceedings of the 2023 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN). IEEE, 2023, pp. 182–184. [CrossRef]
- Abd, R.I.; Kim, K.S.; Findley, D.J. Hydra-RAN Perceptual Networks Architecture: Dual-Functional Communications and Sensing Networks for 6G and Beyond. IEEE Access 2023. [CrossRef]
- Ghosh, S.; Dagiuklas, T.; Iqbal, M.; Wang, X. A cognitive routing framework for reliable communication in IoT for industry 5.0. IEEE Transactions on Industrial Informatics 2022, 18, 5446–5457. [CrossRef]
- Fernández, C.; Cárdenas, A.; Giménez, S.; Uriol, J.; Serón, M.; Giraldo-Rodríguez, C. Application of Multi-Pronged Monitoring and Intent-Based Networking to Verticals in Self-Organising Networks. In Proceedings of the 2022 5th International Conference on Advanced Communication Technologies and Networking (CommNet). IEEE, 2022, pp. 1–10. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).