Submitted:
20 December 2023
Posted:
22 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
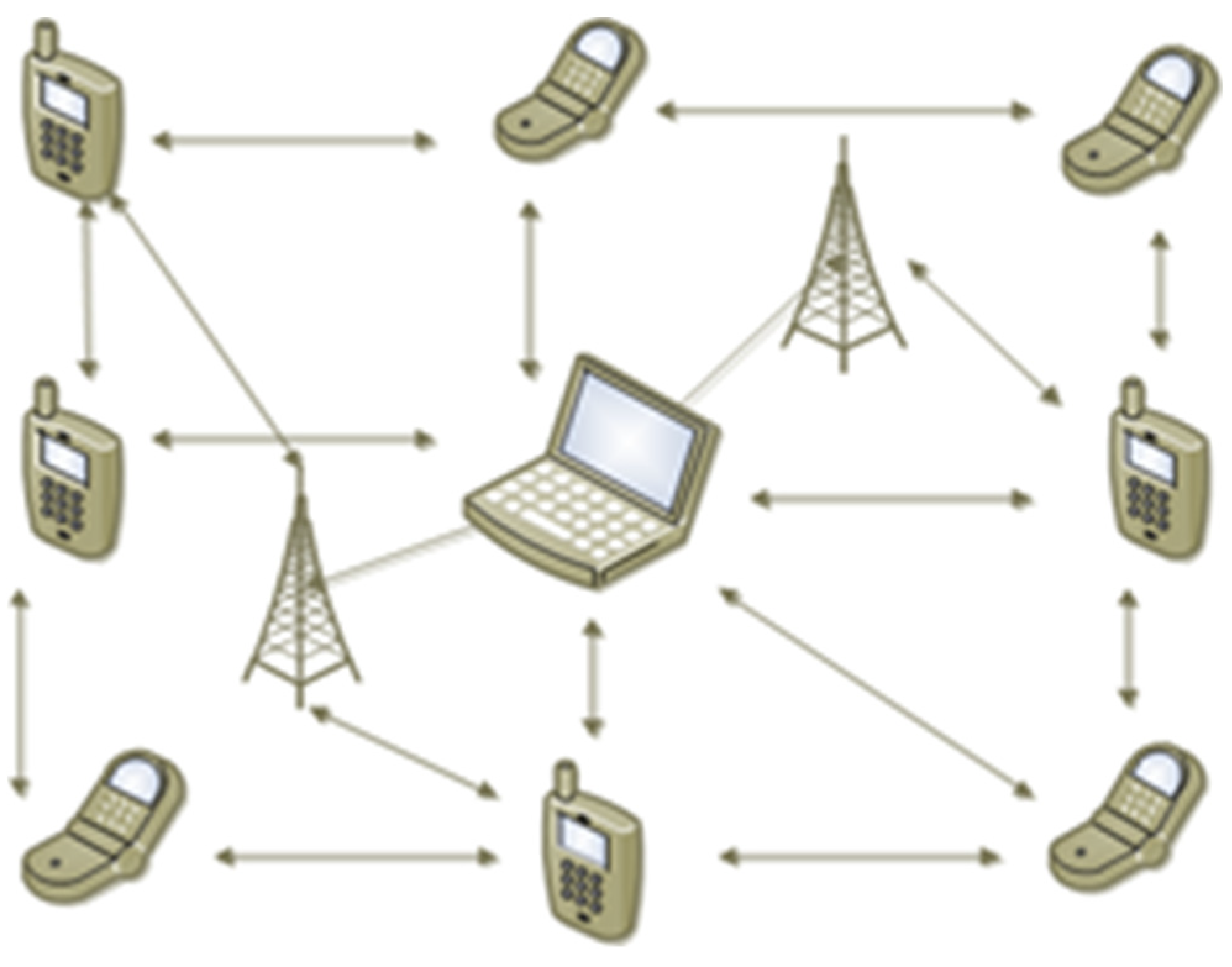
1.1. Novelty of Work
- A much more interesting attack known as collision attack is prevented through a simple and efficient CAP algorithm.
- A secured CAP algorithm is simple and comfortable in terms of cost and time consumption.
1.2. Contribution of Work
- Proposed technique is tested over various input sizes to analyze security level.
- Multiple literature techniques are collected and compared with the proposed CAP algorithm in terms of time consumption.
1.3. Organization
2. Literature Review
3. Methodology
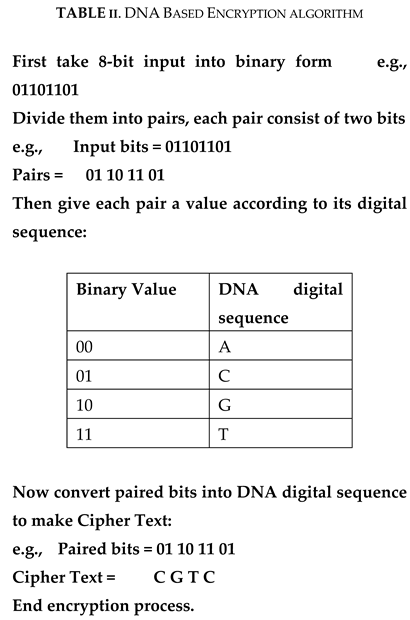
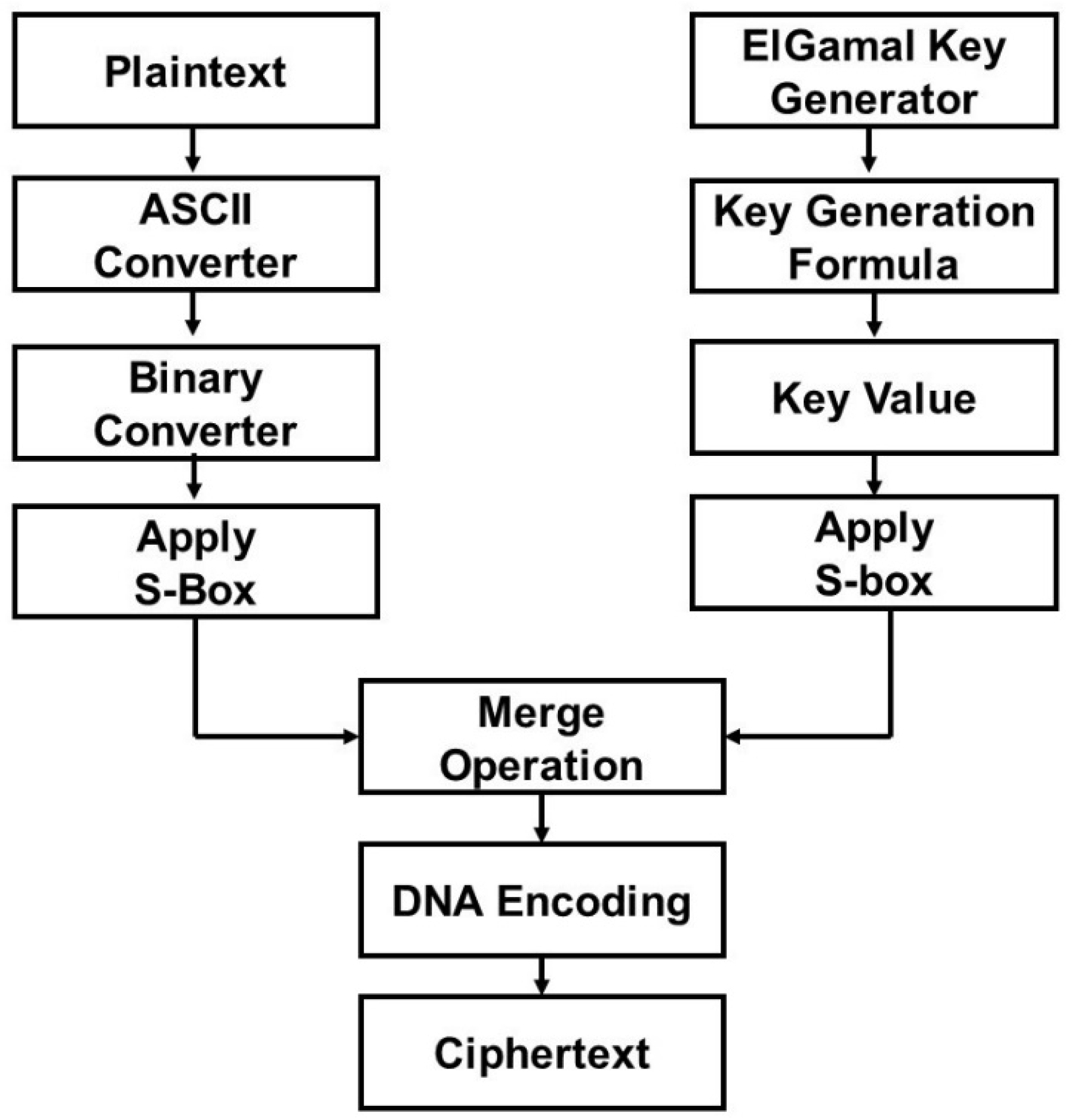
3.1. Encryption Process
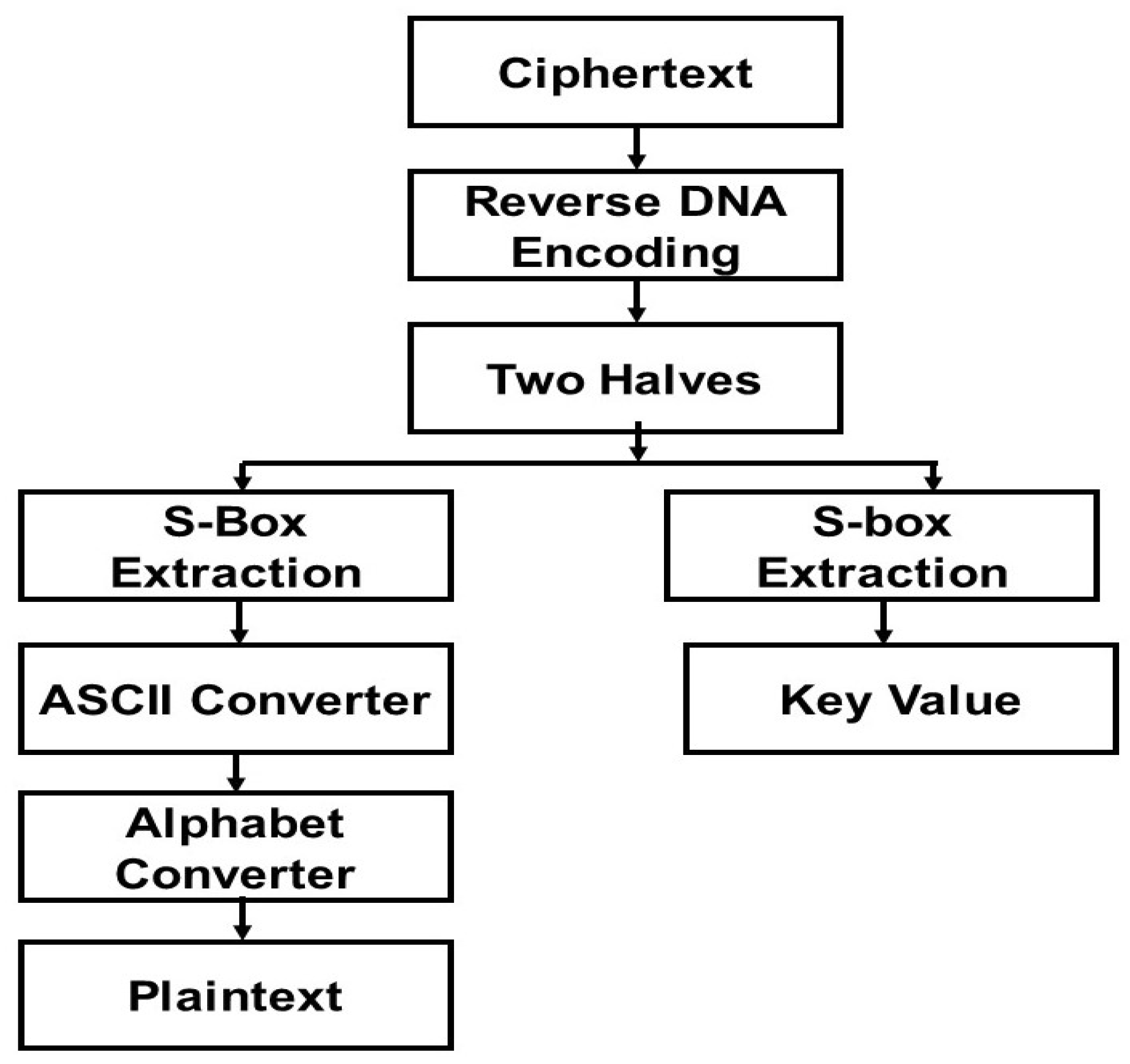
3.2. Decryption Process
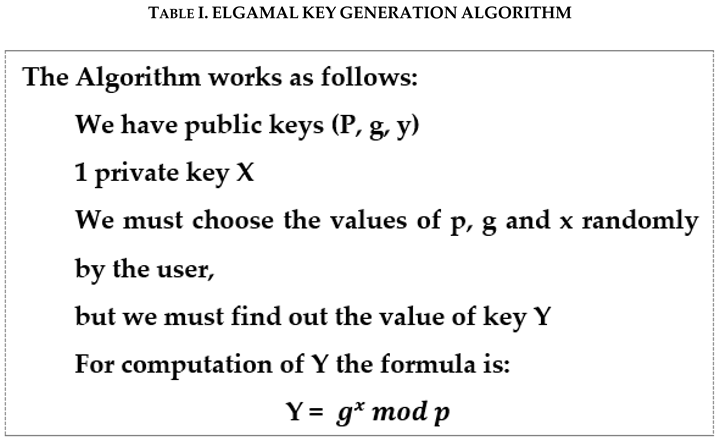
3.3. ElGamal Key Generation Algorithm
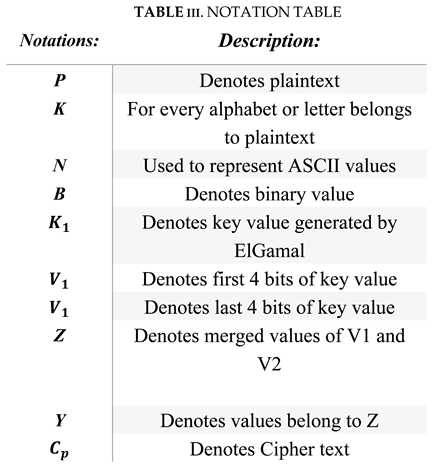
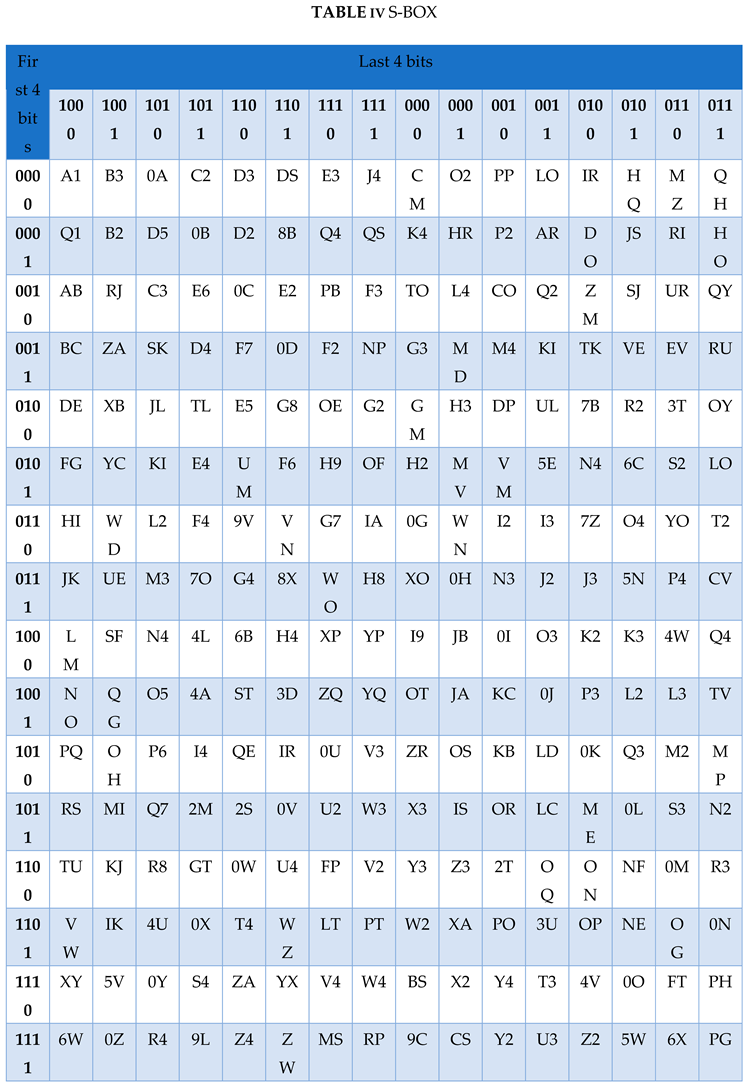

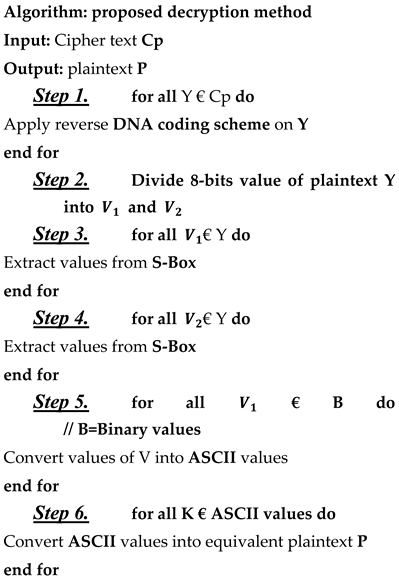
3.4. Math metical Modelling
4. Result and Analysis
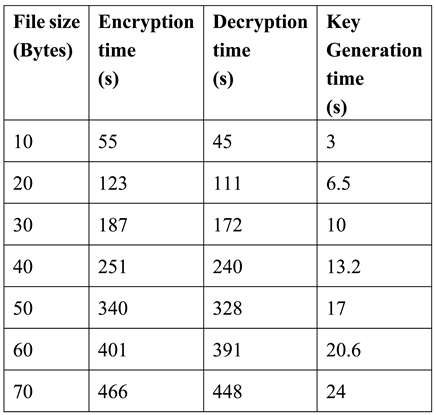
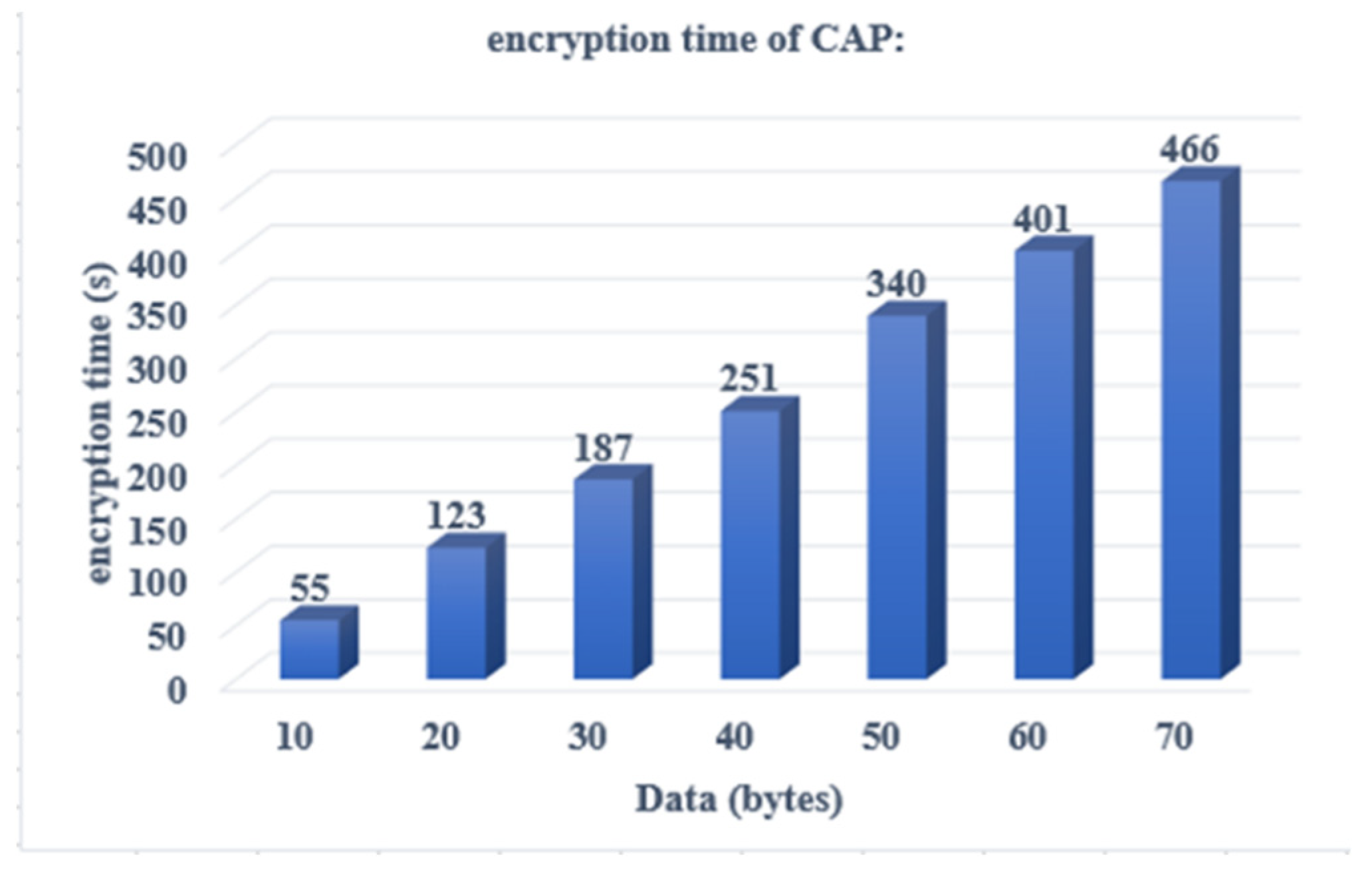
4.1. Encryption Time Complexity
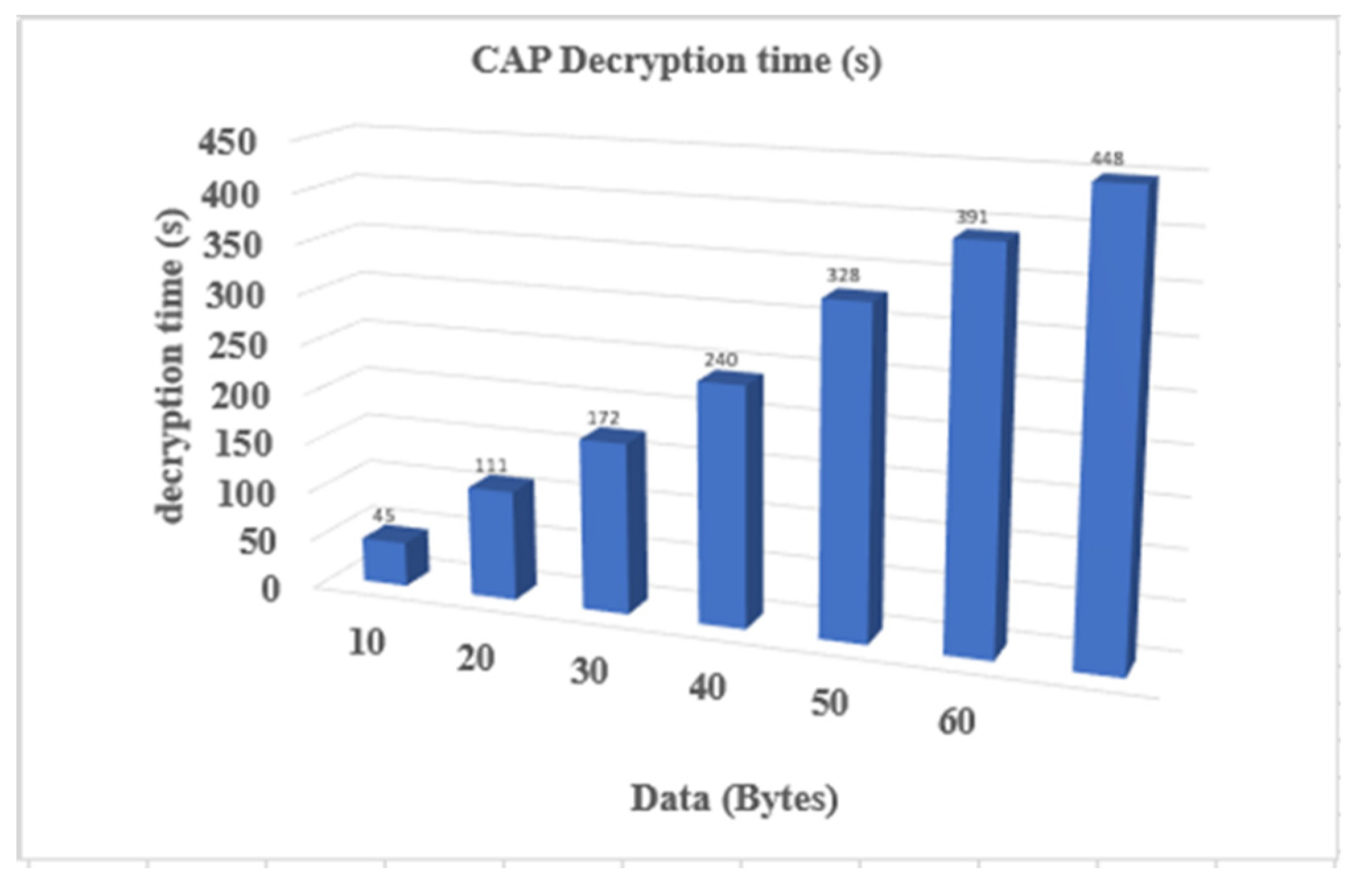
4.2. Decryption Time Complexity
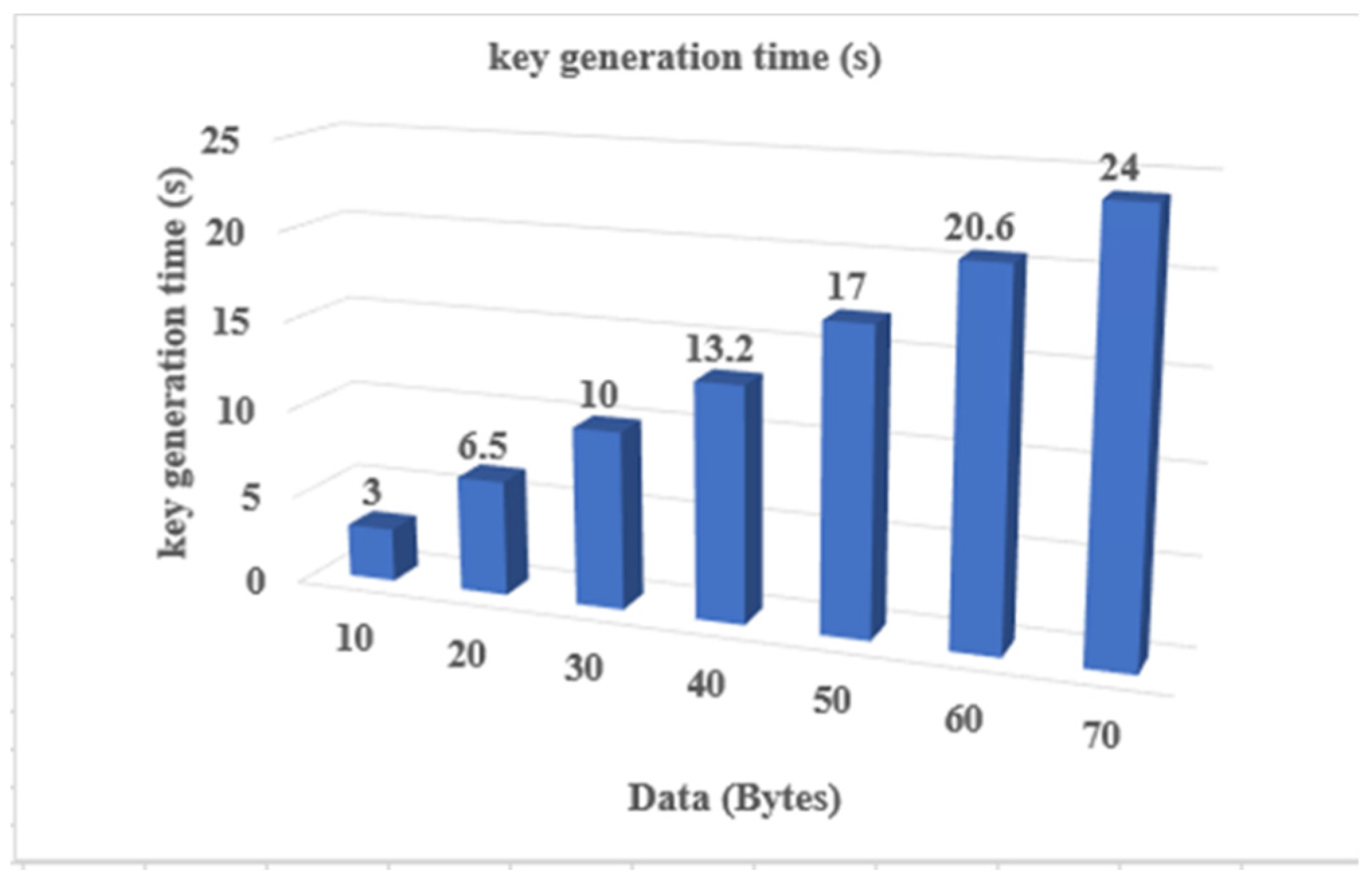
4.3. ElGamal Key Generation Algorithm
4.4. Comparative Analysis
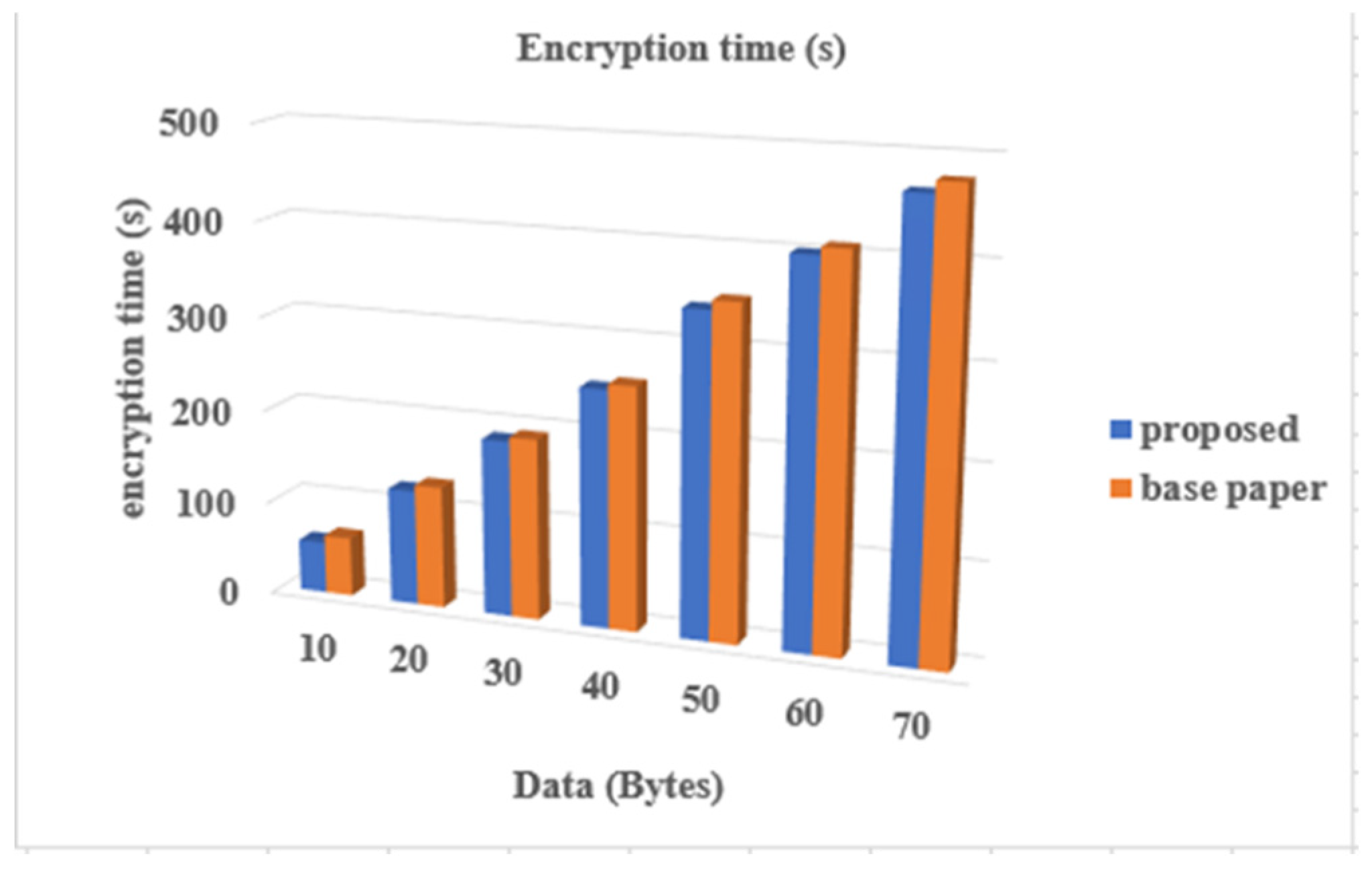
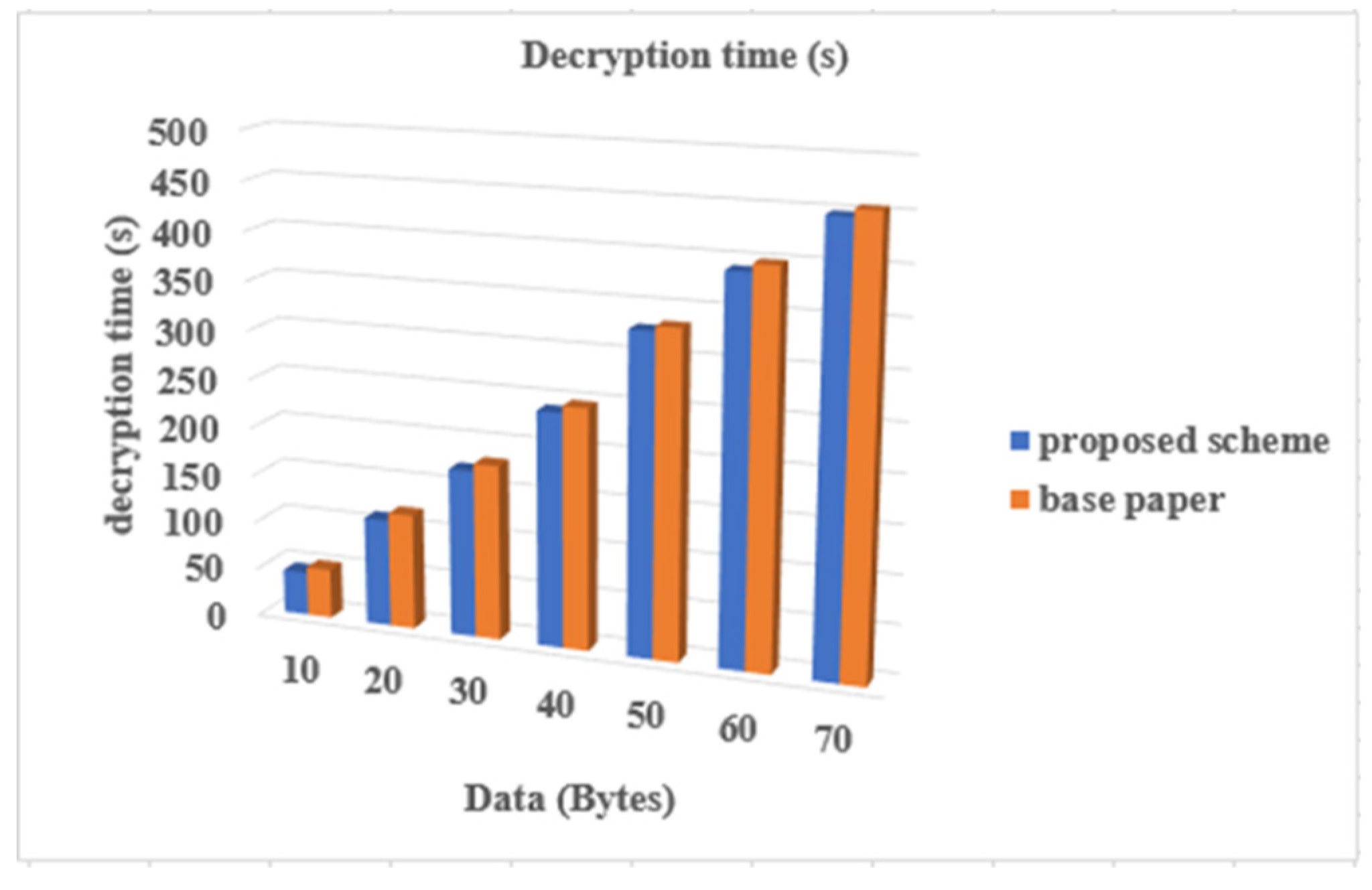
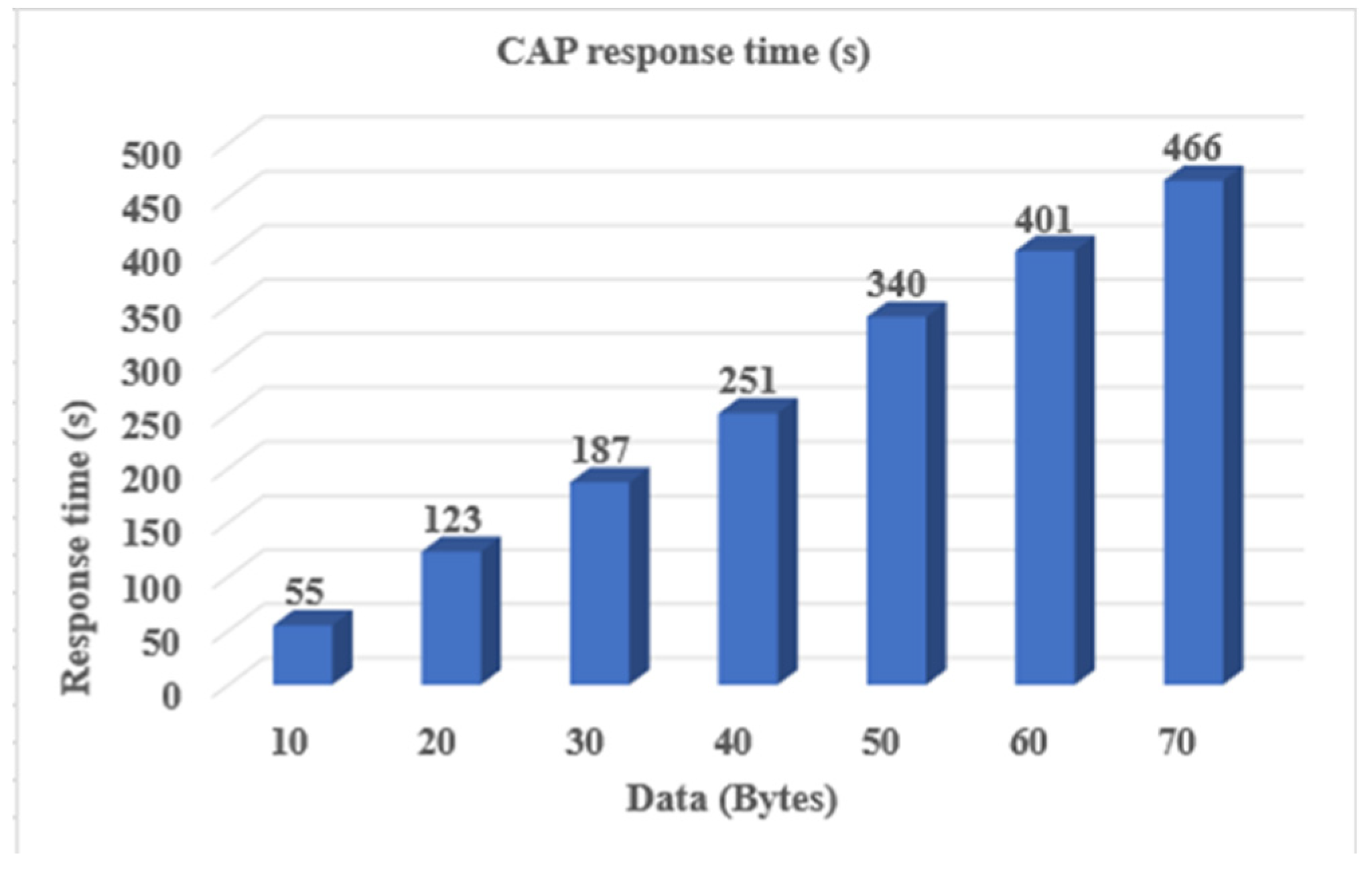
4.5. Response Time
V. SECURITY
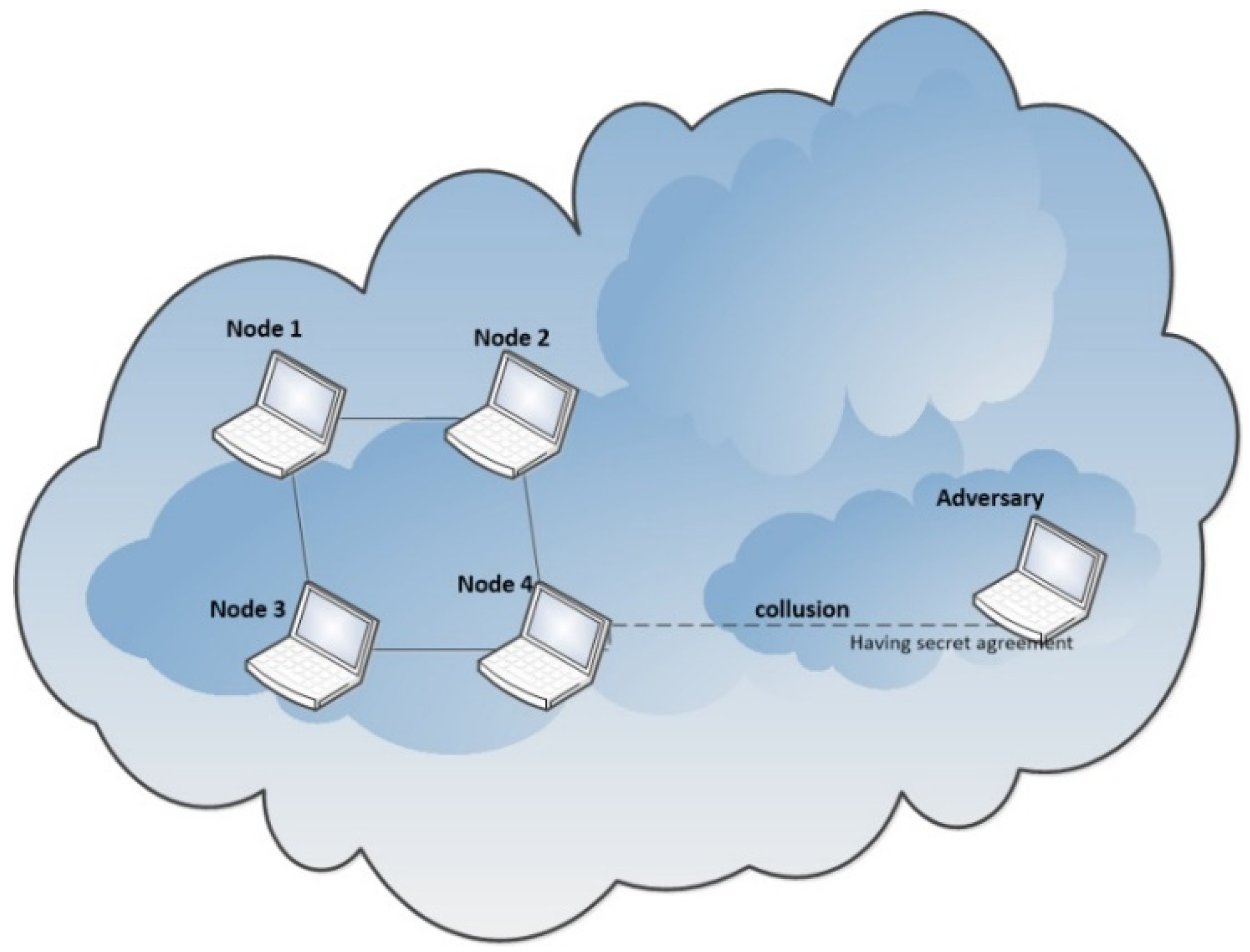
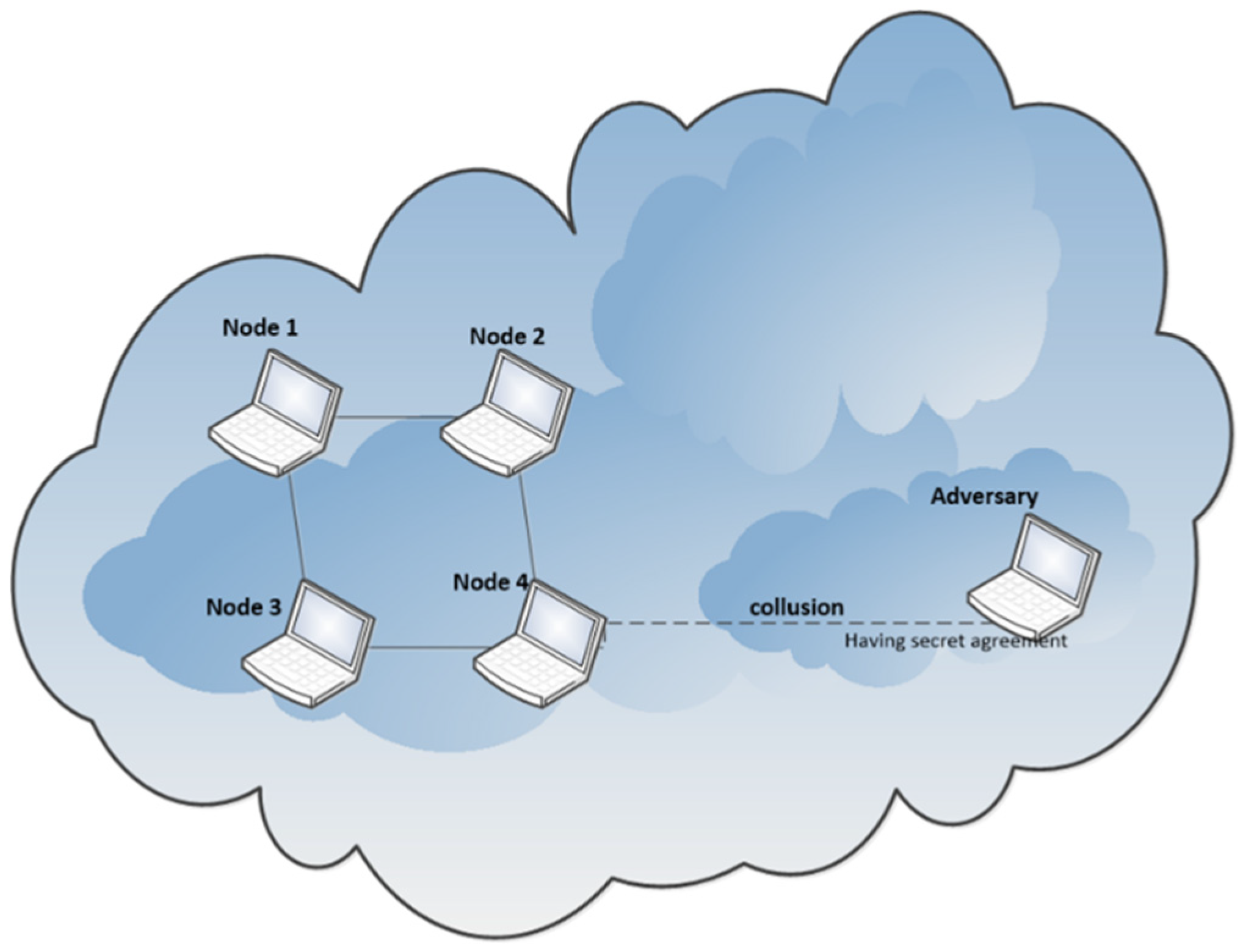
5.1. Collision Attack
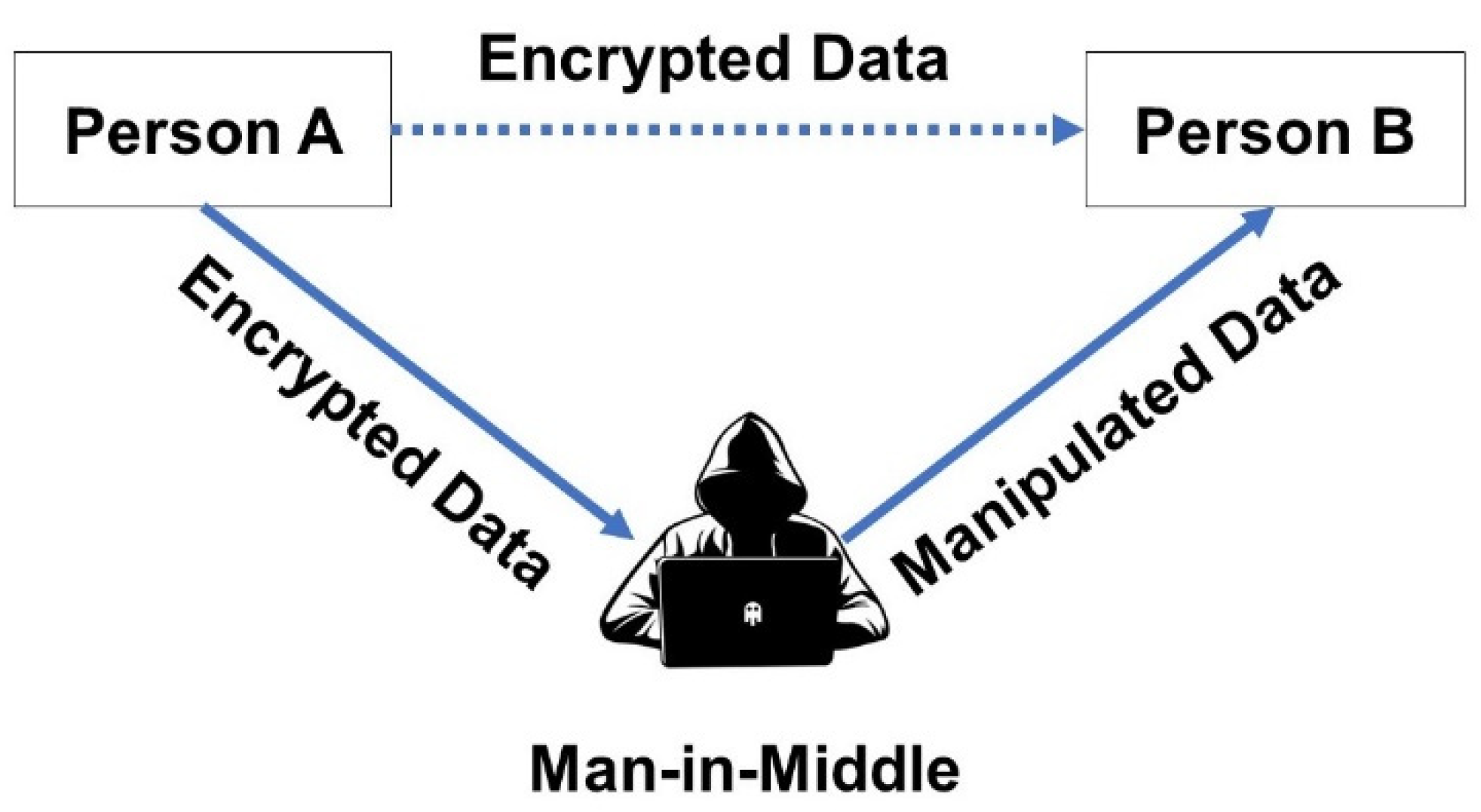
5.2. Man-In-Middle Attack
5. Conclusions
References
- B.Sowndarya, G.V.Suresh, O.SrinivasaReddy, and Dr.Sai Satyanarayana Reddy. Enhanced Adaptive Acknowledgement for Mobile Ad Hoc Network. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 4.
- Sridevi, N.; Nagarajan, V. A curve based cryptography for wireless security in MANET. Clust. Comput. 2018, 22, 4017–4025. [Google Scholar] [CrossRef]
- Markku-Juhani, O. Saarinen. Cryptanalysis of Block Ciphers Based on SHA-1 and MD5_. _c Int. Assoc. Cryptologic Res. 2003; 9. [Google Scholar]
- N. Sridevi, V. Nagarajan, and Senior Member. Enhanced Secure Wireless Communication in MANETs. Int. Conf. Commun. Signal Process. 2017, 6.
- Yan Wang and Mohan Yang. Higher Order Differential Cryptanalysis on the SHA-3 Cryptographic Hash Algorithm Competition Candidates. p. 9.
- Ritu Aggarwal. A Survey to Improve the Network Security with Less Mobility and Key Management in MANET. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2018, 3, 7. [Google Scholar]
- Santanu Sarkar and Subhamoy Maitra. Side Channel Attack to Actual Cryptanalysis: Breaking CRT-RSA with Low Weight Decryption Exponents. Int. Assoc. Cryptologic Res. 2012, 18.
- Inderpreet Kaur. A Framework to improve the Network Security with Less Mobility in MANET. Int. J. Comput. Appl. 2017, 167, 21–24. [Google Scholar] [CrossRef]
- Og˘ uzhan Ersoy. Thomas Brochmann Pedersen, Kamer Kaya, Ali Aydın Selçuk, and Emin Anarim2. A CRT-based verifiable secret sharing scheme secure against unbounded adversaries. Wiley Online Libr. Wileyonlinelibrarycom 2016, 9.
- Rohit Kumar, Yashendra Shiv, Vimal Kumar, and Manoj Wairiya. An Authentication Technique in Mobile Ad hoc Network using Elliptic Curve Cryptography. 2018 8th Int. Conf. Cloud Comput. Data Sci. Eng. Conflu. 2018, 5.
- Michael, J. Wiener and Robert J. Zuccherato. Faster Attacks on Elliptic Curve Cryptosystems. p. 11, 1999.
- N Chaitanya Kumar, Abdul Basit, Priyadarshi Singh, and V. Ch. Venkaiah. Lightweight Cryptography for Distributed PKI Based MANETS. Int. J. Comput. Netw. Commun. IJCNC 2018, 10, 15.
- et al. Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice. p. 13, 2015.
- Muhammad Usman a, Mian Ahmad Jan b, Xiangjian He c, and Priyadarsi Nanda c. QASEC: A secured data communication scheme for mobile Ad-hoc networks. Future Gener. Comput. Syst. 2018, 109, 604–610. [Google Scholar] [CrossRef]
- Sankaranarayanan. S and Murugaboopathi. G. SECURE INTRUSION DETECTION SYSTEM IN MOBILE AD HOC NETWORKS USING RSA ALGORITHM. Int. Conf. Recent Trends Chall. Comput. Models 2017, 4. [Google Scholar]
- Dr. Kartik Krishnan. Attacks On the RSA Cryptosystem. p. 5, Apr. 2005.
- V.Govindasaml, S.Sandosh, And C. Suraj Kumar. kd2sa: Key distribution scheme shuffling algorithm for heightened secure data transmission. int. conf. comput. power energy inf. commun. iccpeic, 2016; 6.
- Jayanthi Chandrashekar and Arun Manoharan. An Identity Based Key Management Technique for Secure Routing in MANET. p. 11, Jun. 2018. [CrossRef]
- T. R. Vedhavathy1 and M. S. K. Manikandan2. Triple referee incentive mechanism for secure mobile adhoc networks. Clust. Comput. 2018, 22, 255–264. [CrossRef]
- Maheswary and Dr.S.Baskar. Letter To Shape Encryption For Securing MANET Routing Protocols. IEEE p. 4, 2016.
- Mamta Martolia1, Priti Dimri2, and Nitin Arora3. PIGPEN: A Novel Approach for Securing Data. 2018, 80, 4.
- Shahwar Ali, A Humaria, M Sher Ramzan, Imran Khan, and J Zakia. An efficient cryptographic technique using modified Diffie–Hellman in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2020, 16, 24. [Google Scholar] [CrossRef]
- T. Jabeen, H. Ashraf, A. Khatoon, S.S. Band and A. Mosavi. A Lightweight Genetic Based Algorithm for Data Security in Wireless Bosy Area Network. IEEE Access 2020, 8, 1–10.
- Shafiq, M.; Ashraf, H.; Ullah, A.; Masud, M.; Azeem, M.; Jhanjhi, N.; Humayun, M. Robust cluster-based routing protocol for IoT-assisted smart devices in WSN. Comput. Mater. Contin. 2021, 67, 3505–3521. [Google Scholar] [CrossRef]
- Shahid, F.; Ashraf, H.; Ghani, A.; Ghayyur, S.A.K.; Shamshirband, S.; Salwana, E. PSDS–proficient security over distributed storage: A method for data transmission in cloud. IEEE Access 2020, 8, 118285–118298. [Google Scholar] [CrossRef]
- Talwani, S.; Singla, J.; Mathur, G.; Malik, N.; Jhanjhi, N.Z.; Masud, M.; Aljahdali, S. Machine-Learning-Based Approach for Virtual Machine Allocation and Migration. Electronics 2022, 11, 3249. [Google Scholar] [CrossRef]
- Ramamoorthy, M.; Qamar, S.; Manikandan, R.; Jhanjhi, N.Z.; Masud, M.; AlZain, M.A. Earlier detection of brain tumor by pre-processing based on histogram equalization with neural network. Healthcare 2022, 10, 1218. [Google Scholar] [CrossRef] [PubMed]
- Khalil, M.I.; Jhanjhi, N.Z.; Humayun, M.; Sivanesan, S.; Masud, M.; Hossain, M.S. Hybrid smart grid with sustainable energy efficient resources for smart cities. Sustain. Energy Technol. Assess. 2021, 46, 101211. [Google Scholar] [CrossRef]
- Kok, S.H.; Azween, A.; Jhanjhi, N.Z. Evaluation metric for crypto-ransomware detection using machine learning. J. Inf. Secur. Appl. 2020, 55, 102646. [Google Scholar] [CrossRef]
- Shafiq, M.; Ashraf, H.; Ullah, A.; Masud, M.; Azeem, M.; Jhanjhi, N.Z.; Humayun, M. Robust Cluster-Based Routing Protocol for IoT-Assisted Smart Devices in WSN. Comput. Mater. Contin. 2021, 67. [Google Scholar] [CrossRef]
- Hanif, M.; Ashraf, H.; Jalil, Z.; Jhanjhi, N.Z.; Humayun, M.; Saeed, S.; Almuhaideb, A.M. AI-based wormhole attack detection techniques in wireless sensor networks. Electronics 2022, 11, 2324. [Google Scholar] [CrossRef]
- Jabeen, T.; Jabeen, I.; Ashraf, H.; Jhanjhi, N.; Humayun, M.; Masud, M.; Aljahdali, S. A monte carlo based COVID-19 detection framework for smart healthcare. Comput. Mater. Contin. 2022, 70, 2365–2380. [Google Scholar] [CrossRef]
- Siddiqui, F.J.; Ashraf, H.; Ullah, A. Dual server based security system for multimedia Services in Next Generation Networks. Multimed. Tools Appl. 2020, 79, 7299–7318. [Google Scholar] [CrossRef]
- Ponnusamy, V. (Ed.). (2016). Biologically-Inspired Energy Harvesting through Wireless Sensor Technologies. IGI Global.
- Ponnusamy, V.; Jung, L.T.; Ramachandran, T.; Zaman, N. (2017, April). Bio-inspired energy scavenging in wireless ad hoc network. In 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT) (pp. 1-5). IEEE.
- Humayun, M., Niazi, M., Almufareh, M.F., Jhanjhi, N.Z., Mahmood, S., Alshayeb, M. Software-as-a-service security challenges and best practices: A multivocal literature review. Appl. Sci. 2022, 12, 3953. [CrossRef]
- S. Muzafar and N. Jhanjhi. DDoS Attacks on Software Defined Network: Challenges and Issues. 2022 International Conference on Business Analytics for Technology and Security (ICBATS), Dubai, United Arab Emirates, 2022, pp. 1–6. [CrossRef]
- Ilyas, Q.M.; Ahmad, M.; Zaman, N.; Alshamari, M.A.; Ahmed, I. Localized text-free user interfaces. IEEE Access 2021, 10, 2357–2371. [Google Scholar] [CrossRef]
- Kumar, K., Verma, S., Jhanjhi, N.Z., & Talib, M.N. (2020, December). A Survey of The Design and Security Mechanisms of The Wireless Networks and Mobile Ad-Hoc Networks. In IOP Conference Series: Materials Science and Engineering (Vol. 993, No. 1, p. 012063). IOP Publishing. [CrossRef]
- Hamid, B., Jhanjhi, N.Z., & Humayun, M. (2020). Digital Governance for Developing Countries Opportunities, Issues, and Challenges in Pakistan. In Employing Recent Technologies for Improved Digital Governance (pp. 36-58). IGI Global.
- Alsaade, F.; Zaman, N.; Hassan, M.F.; Abdullah, A. An Improved Software Development Process for Small and Medium Software Development Enterprises Based on Client’s Perspective. Trends Appl. Sci. Res. 2014, 9, 254–261. [Google Scholar] [CrossRef]
- Ndashimye, E.; Sarkar, N.I.; Ray, S.K. A Multi-criteria based handover algorithm for vehicle-to-infrastructure communications. Comput. Netw. 2020, 185, 107652. [Google Scholar] [CrossRef]
- Ray, S.K.; Pawlikowski, K.; Sirisena, H. (2009). A fast MAC-layer handover for an IEEE 802.16 e-based WMAN. In AccessNets: Third International Conference on Access Networks, AccessNets 2008, Las Vegas, NV, USA, October 15-17, 2008. Revised Papers 3 (pp. 102-117). Springer Berlin Heidelberg.
- Srivastava, R.K., Ray, S., Sanyal, S., & Sengupta, P. (2011). Mineralogical control on rheological inversion of a suite of deformed mafic dykes from parts of the Chottanagpur Granite Gneiss Complex of eastern India. Dyke Swarms: Keys for Geodynamic Interpretation: Keys for Geodynamic Interpretation, 263-276.
- Ray, S.K., Sinha, R., & Ray, S.K. (2015, June). A smartphone-based post-disaster management mechanism using WiFi tethering. In 2015 IEEE 10th conference on industrial electronics and applications (ICIEA) (pp. 966-971). IEEE.
- Chaudhuri, A.; Ray, S. Antiproliferative activity of phytochemicals present in aerial parts aqueous extract of Ampelocissus latifolia (Roxb.) planch. on apical meristem cells. Int J Pharm Bio Sci 2015, 6, 99–108. [Google Scholar]
- Hossain, A., Ray, S.K., & Sinha, R. (2016, December). A smartphone-assisted post-disaster victim localization method. In 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS) (pp. 1173-1179). IEEE.
- Airehrour, D.; Gutierrez, J.; Ray, S.K. A trust-based defence scheme for mitigating blackhole and selective forwarding attacks in the RPL routing protocol. J. Telecommun. Digit. Econ. 2018, 6, 41–49. [Google Scholar] [CrossRef]
- Ray, S.K., Ray, S.K., Pawlikowski, K., McInnes, A., & Sirisena, H. (2010, April). Self-tracking mobile station controls its fast handover in mobile WiMAX. In 2010 IEEE Wireless Communication and Networking Conference (pp. 1-6). IEEE.
- Dey, K., Ray, S., Bhattacharyya, P.K., Gangopadhyay, A., Bhasin, K.K., & Verma, R.D. (1985). Salicyladehyde 4-methoxybenzoylhydrazone and diacetylbis (4-methoxybenzoylhydrazone) as ligands for tin, lead and zirconium. J. Indian Chem. Soc.;(India), 62(11).
- Airehrour, D., Gutierrez, J., & Ray, S.K. (2017, November). A testbed implementation of a trust-aware RPL routing protocol. In 2017 27th International Telecommunication Networks and Applications Conference (ITNAC) (pp. 1-6). IEEE.
- Ndashimye, E., Sarkar, N.I., & Ray, S.K. (2016, August). A novel network selection mechanism for vehicle-to-infrastructure communication. In 2016 IEEE 14th Intl Conf on Dependable, Autonomic and Secure Computing, 14th Intl Conf on Pervasive Intelligence and Computing, 2nd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech) (pp. 483-488). IEEE.
- Ndashimye, E.; Sarkar, N.I.; Ray, S.K. A network selection method for handover in vehicle-to-infrastructure communications in multi-tier networks. Wirel. Netw. 2020, 26, 387–401. [Google Scholar] [CrossRef]
- Diwaker, C.; Tomar, P.; Solanki, A.; Nayyar, A.; Jhanjhi, N.Z.; Abdullah, A.; Supramaniam, M. A new model for predicting component-based software reliability using soft computing. IEEE Access 2019, 7, 147191–147203. [Google Scholar] [CrossRef]
- Hussain, S.J.; Ahmed, U.; Liaquat, H.; Mir, S.; Jhanjhi, N.Z.; Humayun, M. (2019, April). IMIAD: Intelligent malware identification for android platform. In 2019 International Conference on Computer and Information Sciences (ICCIS) (pp. 1-6). IEEE.
- Humayun, M.; Alsaqer, M.S.; Jhanjhi, N. Energy optimization for smart cities using iot. Appl. Artif. Intell. 2022, 36, 2037255. [Google Scholar] [CrossRef]
- Ghosh, G., Verma, S., Jhanjhi, N.Z., & Talib, M.N. (2020, December). Secure surveillance system using chaotic image encryption technique. In IOP conference series: Materials science and engineering (Vol. 993, No. 1, p. 012062). IOP Publishing. [CrossRef]
- Almusaylim, Z.A., Zaman, N., & Jung, L.T. (2018, August). Proposing a data privacy aware protocol for roadside accident video reporting service using 5G in Vehicular Cloud Networks Environment. In 2018 4th International conference on computer and information sciences (ICCOINS) (pp. 1-5). IEEE.
- Wassan, S.; Chen, X.; Shen, T.; Waqar, M.; Jhanjhi, N.Z. Amazon product sentiment analysis using machine learning techniques. Rev. Argent. De Clínica Psicológica 2021, 30, 695. [Google Scholar]
- Shahid, H.; Ashraf, H.; Javed, H.; Humayun, M.; Jhanjhi, N.Z.; AlZain, M.A. Energy optimised security against wormhole attack in iot-based wireless sensor networks. Comput. Mater. Contin 2021, 68, 1967–1981. [Google Scholar] [CrossRef]
- Shahid, H.; Ashraf, H.; Javed, H.; Humayun, M.; Jhanjhi, N.Z.; AlZain, M.A. Energy optimised security against wormhole attack in iot-based wireless sensor networks. Comput. Mater. Contin 2021, 68, 1967–1981. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




