Submitted:
22 December 2023
Posted:
26 December 2023
You are already at the latest version
Abstract
Keywords:
0. Introduction
- A novel cyber risk assessment approach has been developed which considers a Federated Identity Management (FIM) framework with connected IoMT and MCPS devices to meet the next generation healthcare demand and enable safe collaboration among service providers.
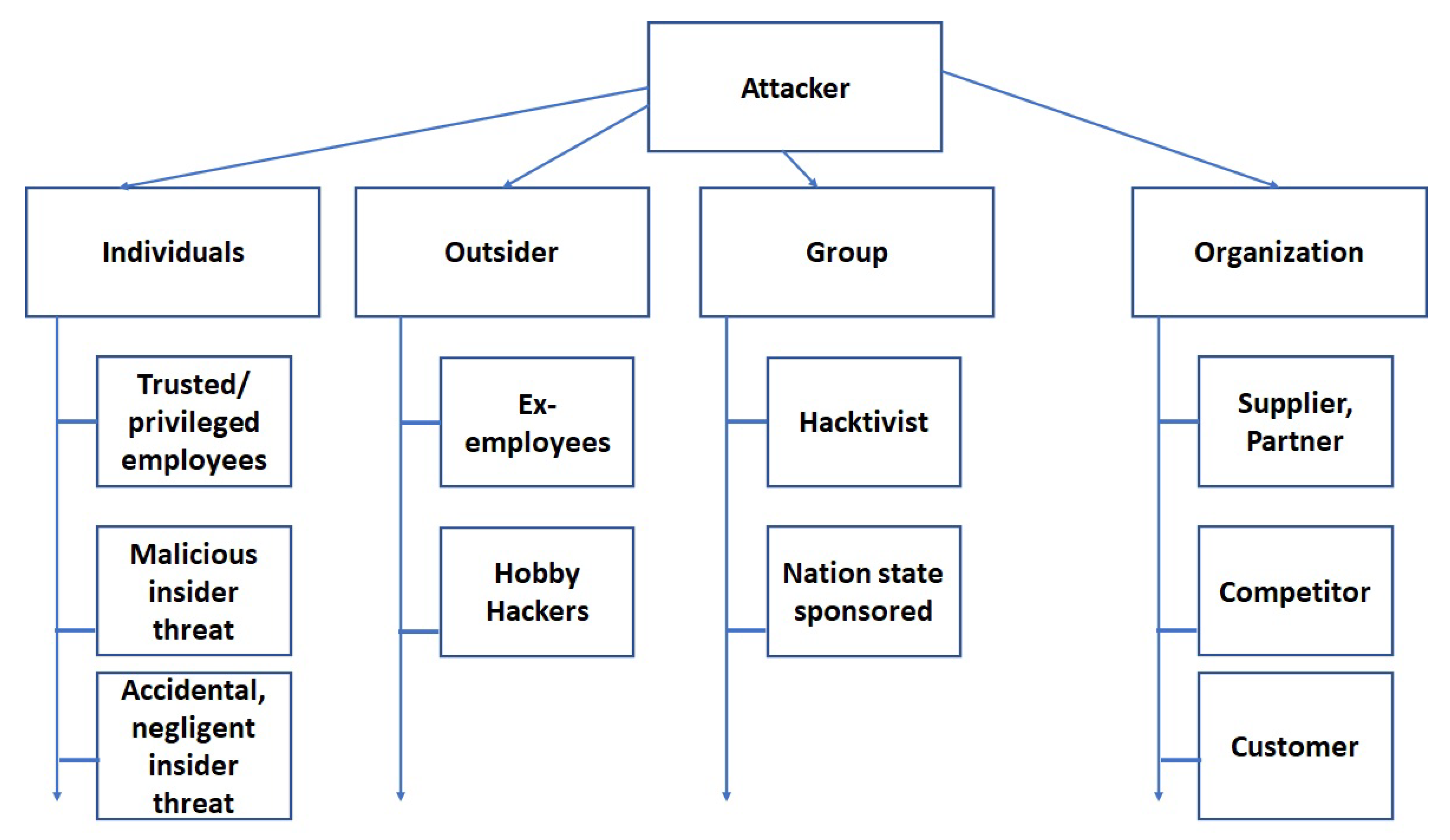
- A detailed threat modeling of FIM based federated healthcare has been developed that help identify, prevent, detect, respond and recover against cyber threats to the federated healthcare ecosystems by combining two major standards including CRR and NIST.
1. Related Work
2. Proposed methodology
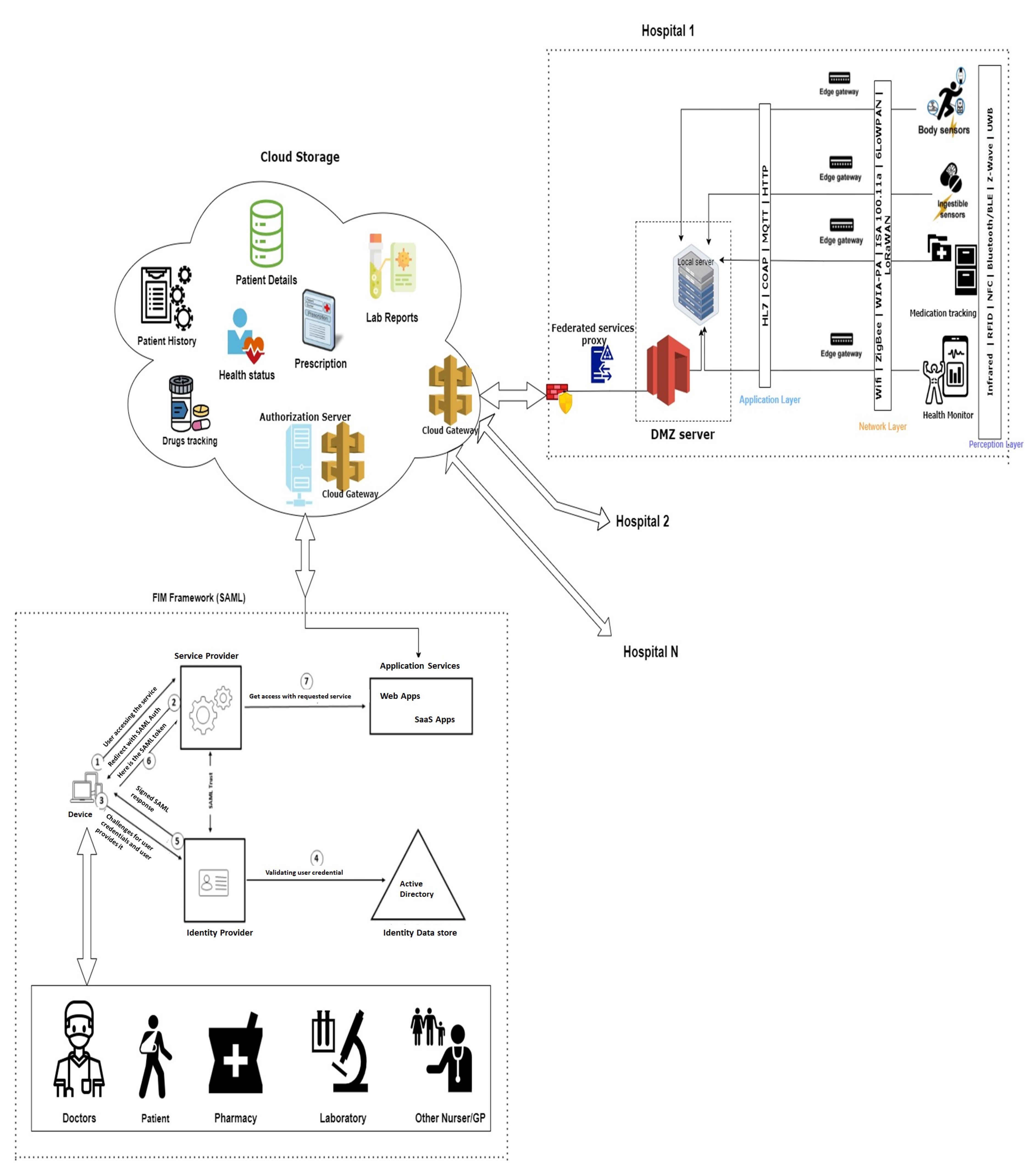
2.1. Proposed risk assessment approach to FIM based hospital framework with IoMT and MCPS
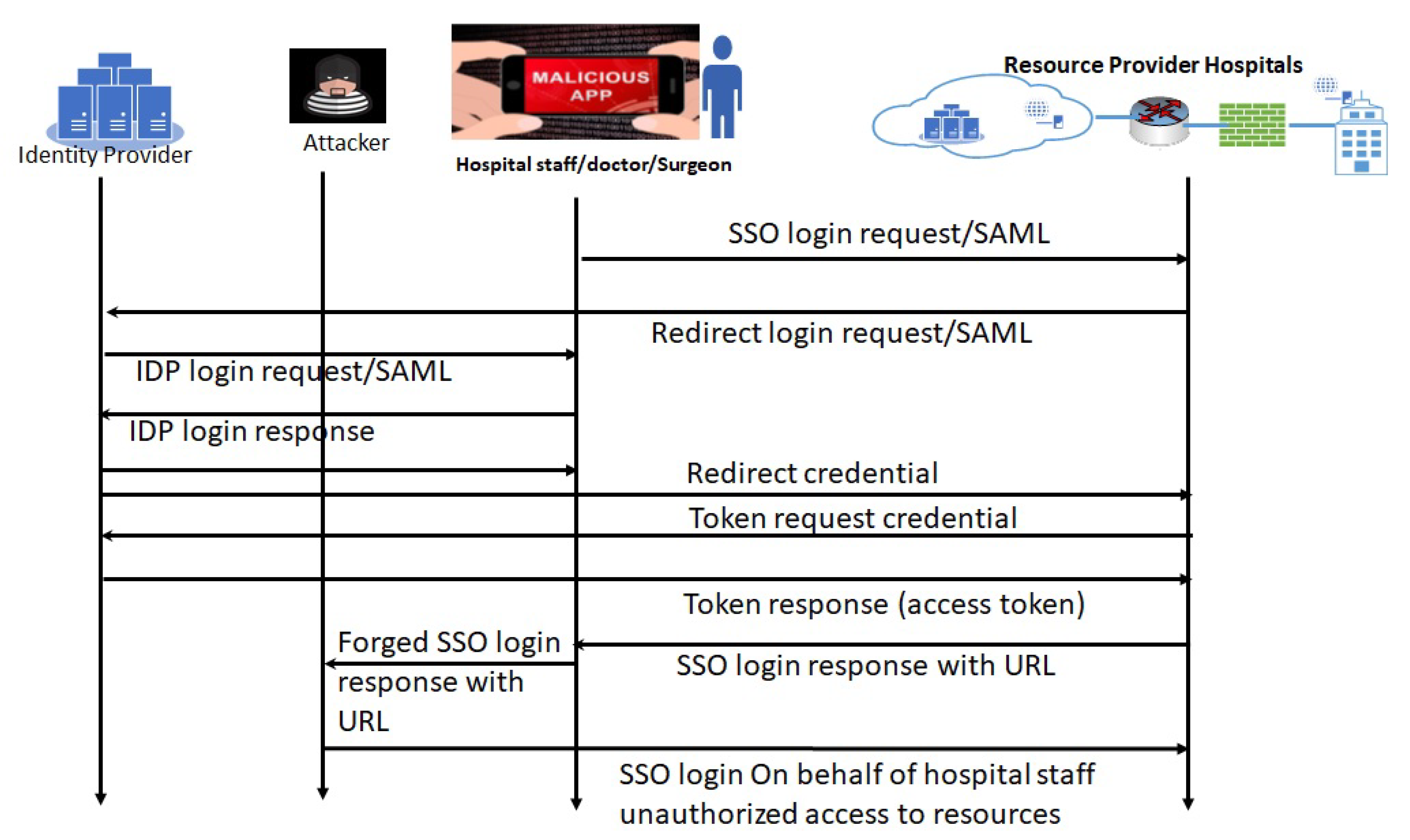
- Clinician would like to access for a system/application from Service Provider (SP), it generates SSOlogin.Request which is sent to SP.
- Then the SP re-sends the SSO login request to Clinician which then send the request to the IDP. Here Clinician’s browser acts as a relay agent.
- the IDP starts a channel with the clinician for credential verification of client directly and verifies the client’s identity with the supplied Clinician’s username and password.
- At this stage, there are different version of IDP response, one version is the IDP then sends the signed SAML response to clinician which has the authentication status. In other version, the IDP sends a session ID to the SP using the redirect channel and then SP send SSO.login response to clinician which allows clinician to access the service.
- Once SP receives the SAML token/session ID either from clinician or from IDP, SP verifies the authorization privileges.
- SP provider grants clinician the access to requested service.
- At last, clinician is able to access to the system/application/service.
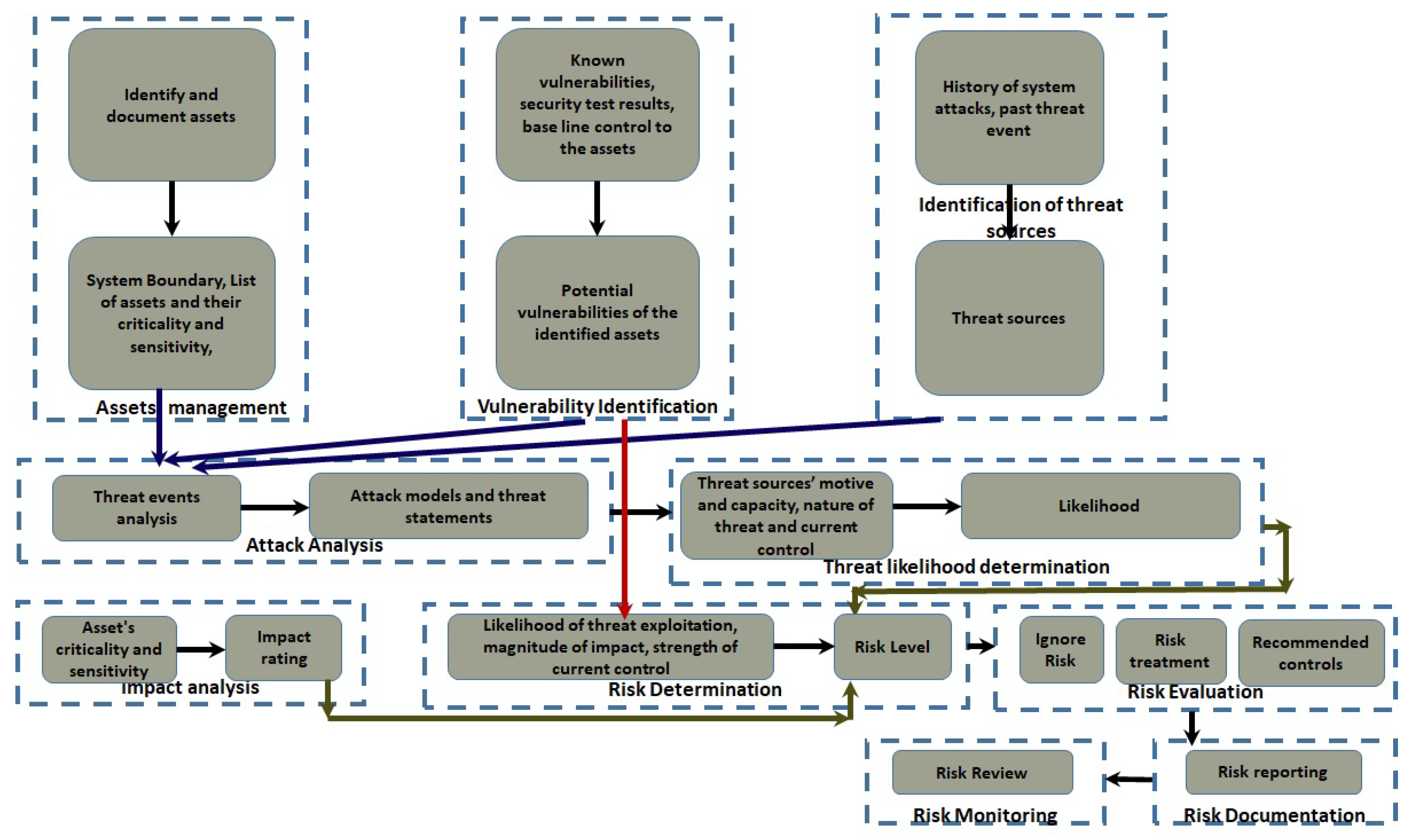
2.2. Details framework of the proposed methodology
- Accept the risk: If the likelihood and impact rating is low, the risk is accepted.
- Mitigate the risk: In this case appropriate security control is applied in place to lower the risk level.
- Transferring risk: Risk is transferred to a third party, for example to an insurance company who buys risk as their business [48].
- Risk avoidance: If the risk is extreme high and cannot be mitigated within the current scope of the project, it is avoided.
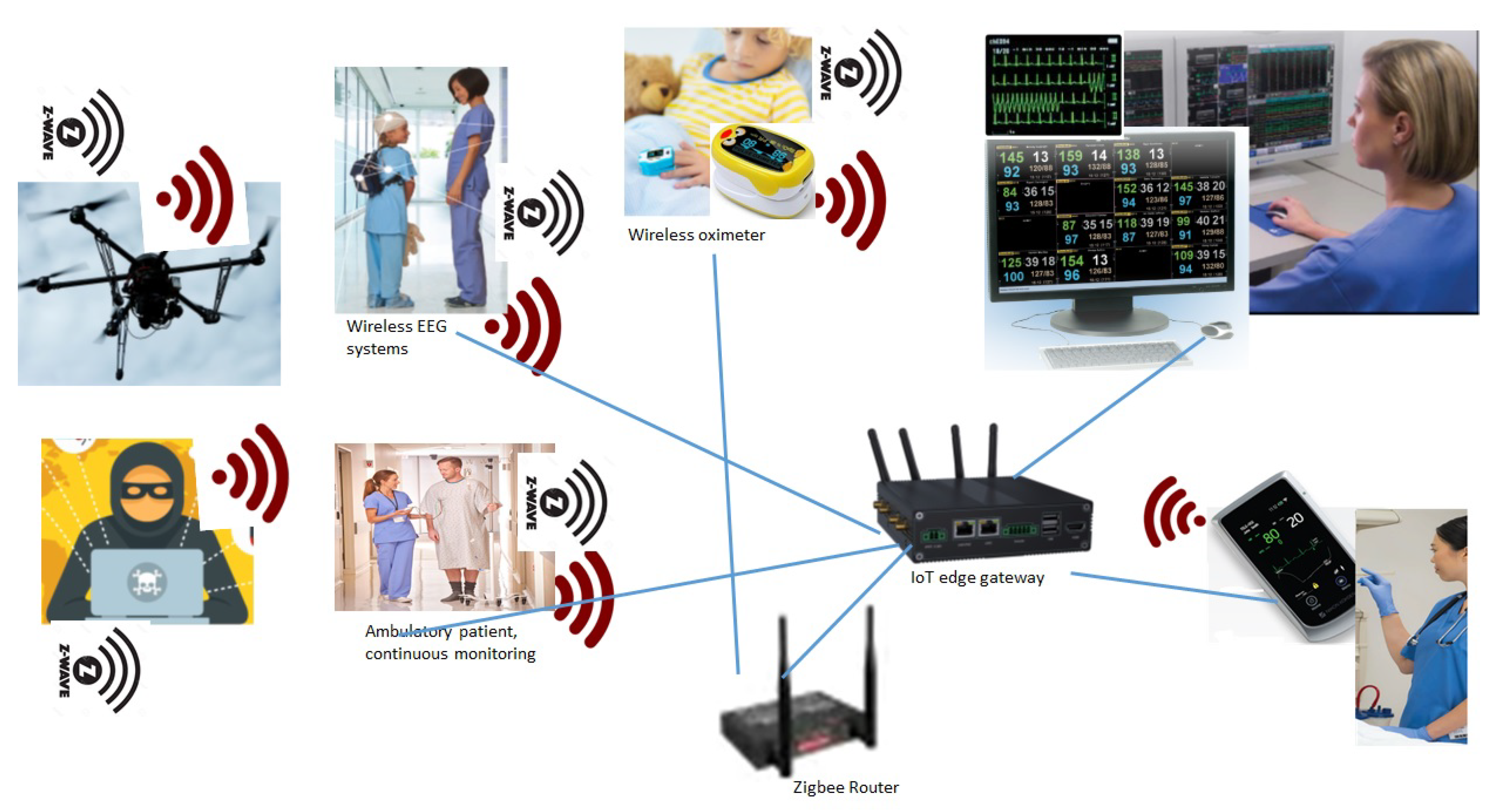
- IoMT and MCPS Devices
- Rest of IoT Ecosystem Devices
- Communication related devices
- Infrastructure
- Platform and Backend
- Application and Services
- Information
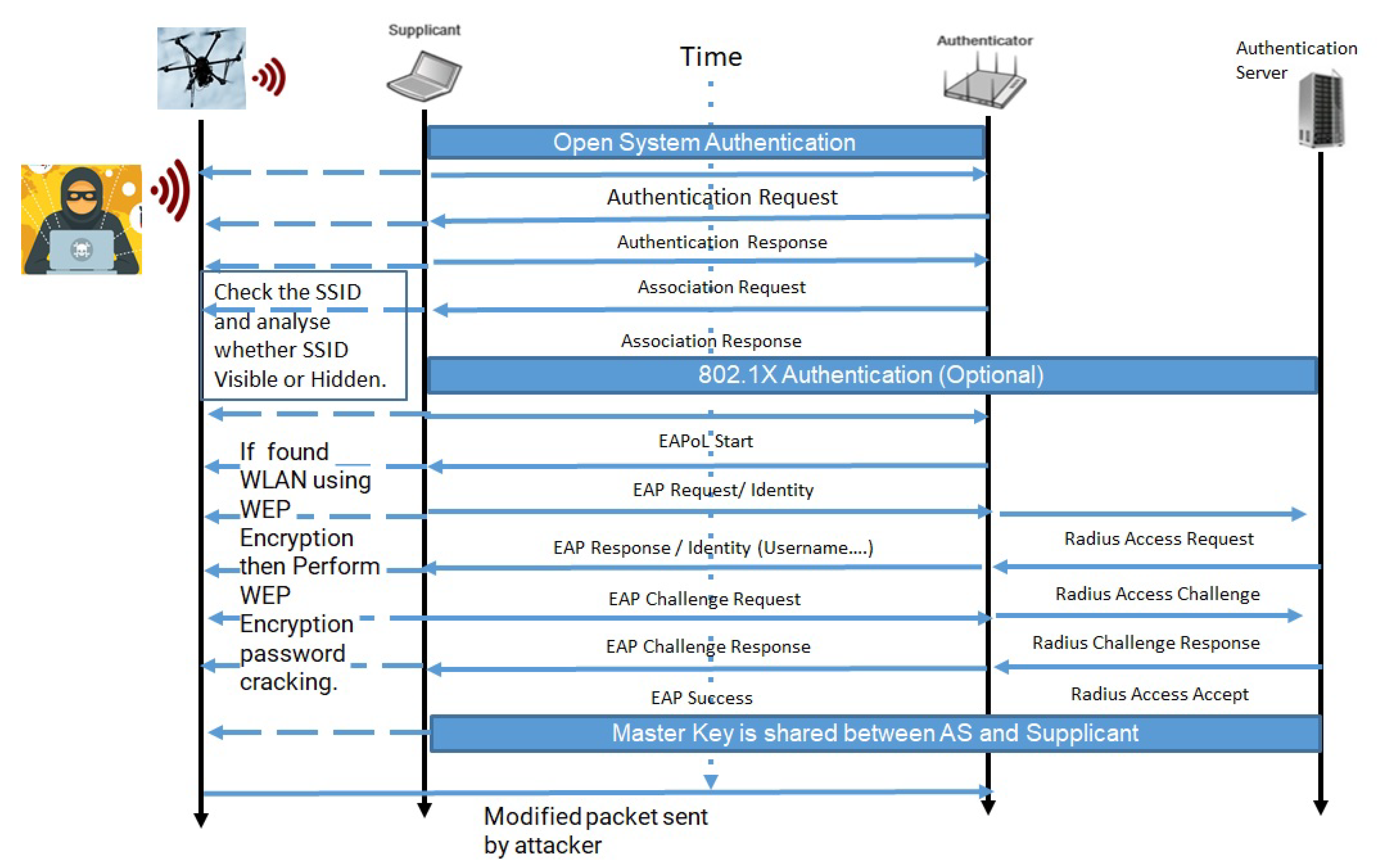
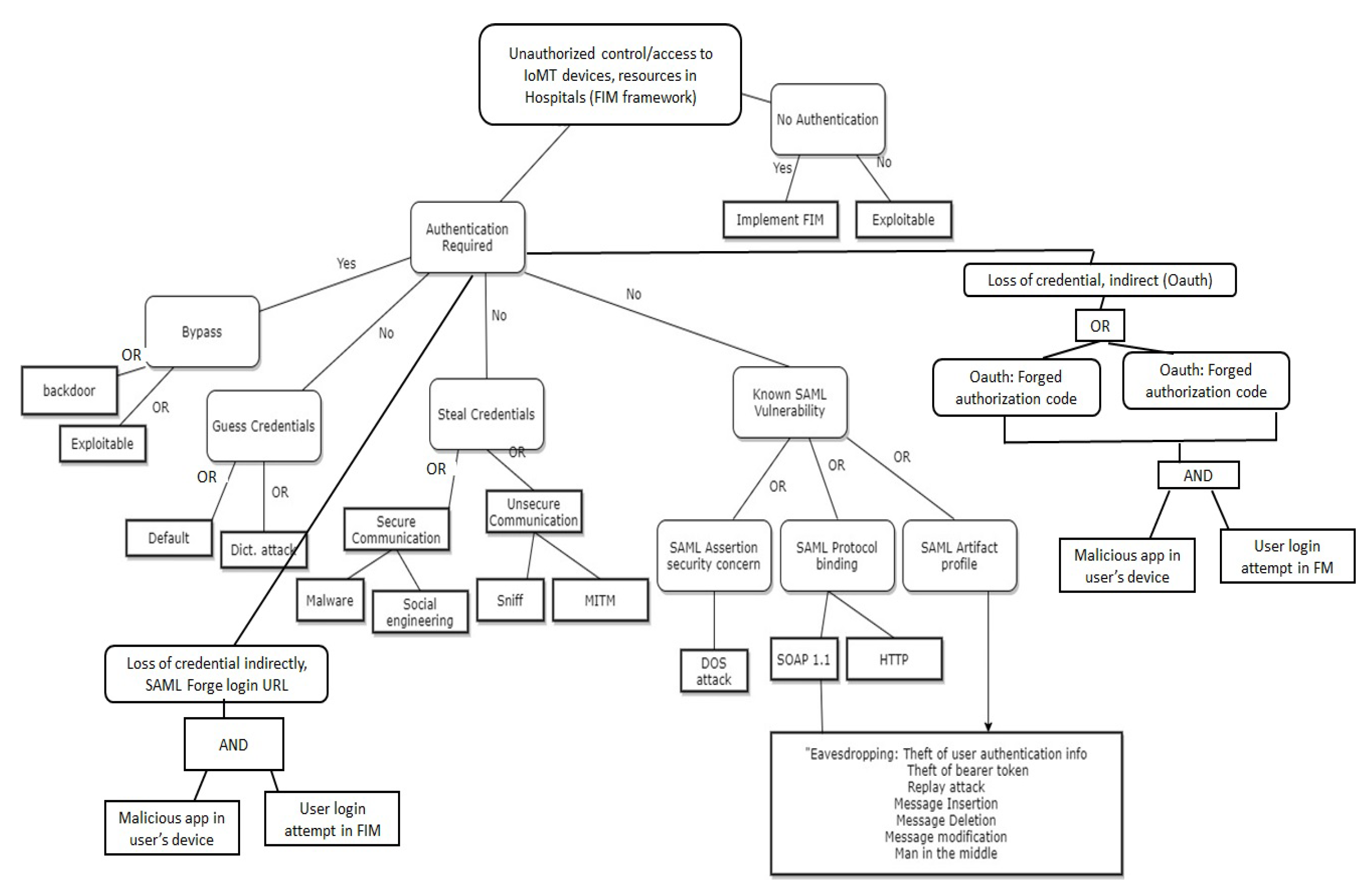
2.2.1. Threat modeling in the proposed approach for FIM protocols and IoT protocols in federated Hospital
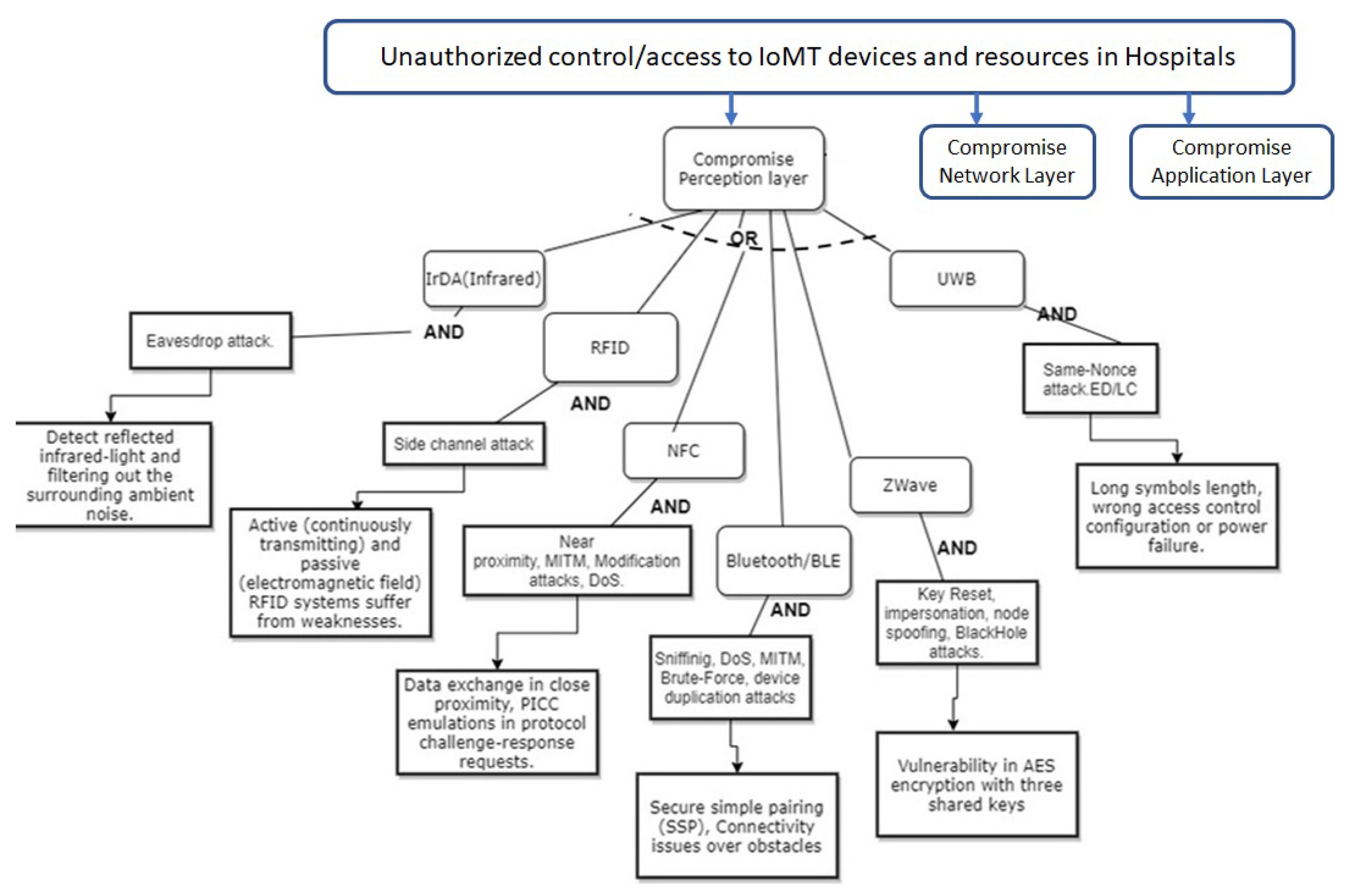
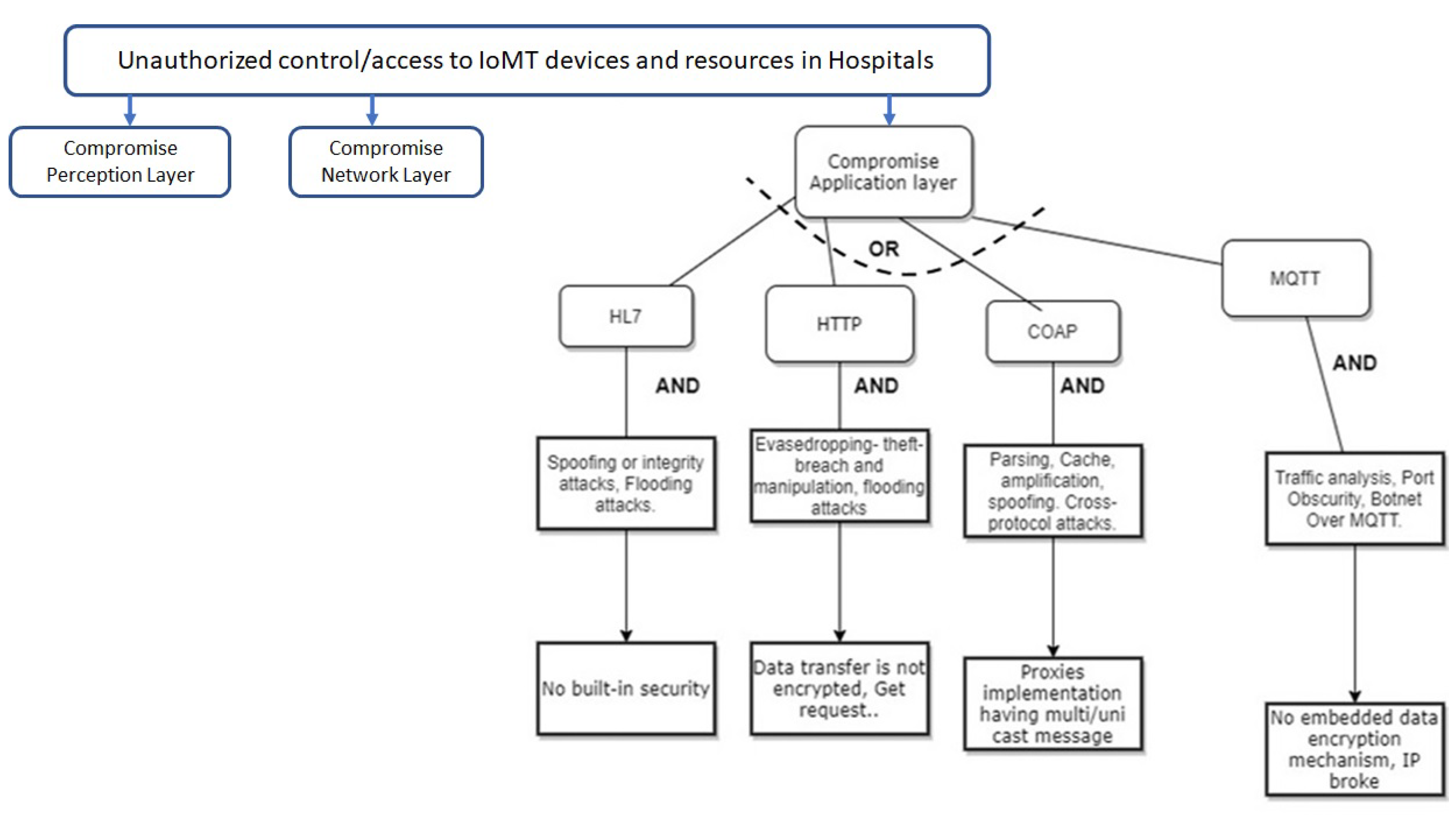
2.2.2. Threat modeling in the proposed approach for perception layer IoT protocols in federated Hospital
3. Results and discussion
3.1. Risk Determination Treatment and Mitigation
| Asset Group (ID) | Assets | Vulnerabilities in the Assets |
|---|---|---|
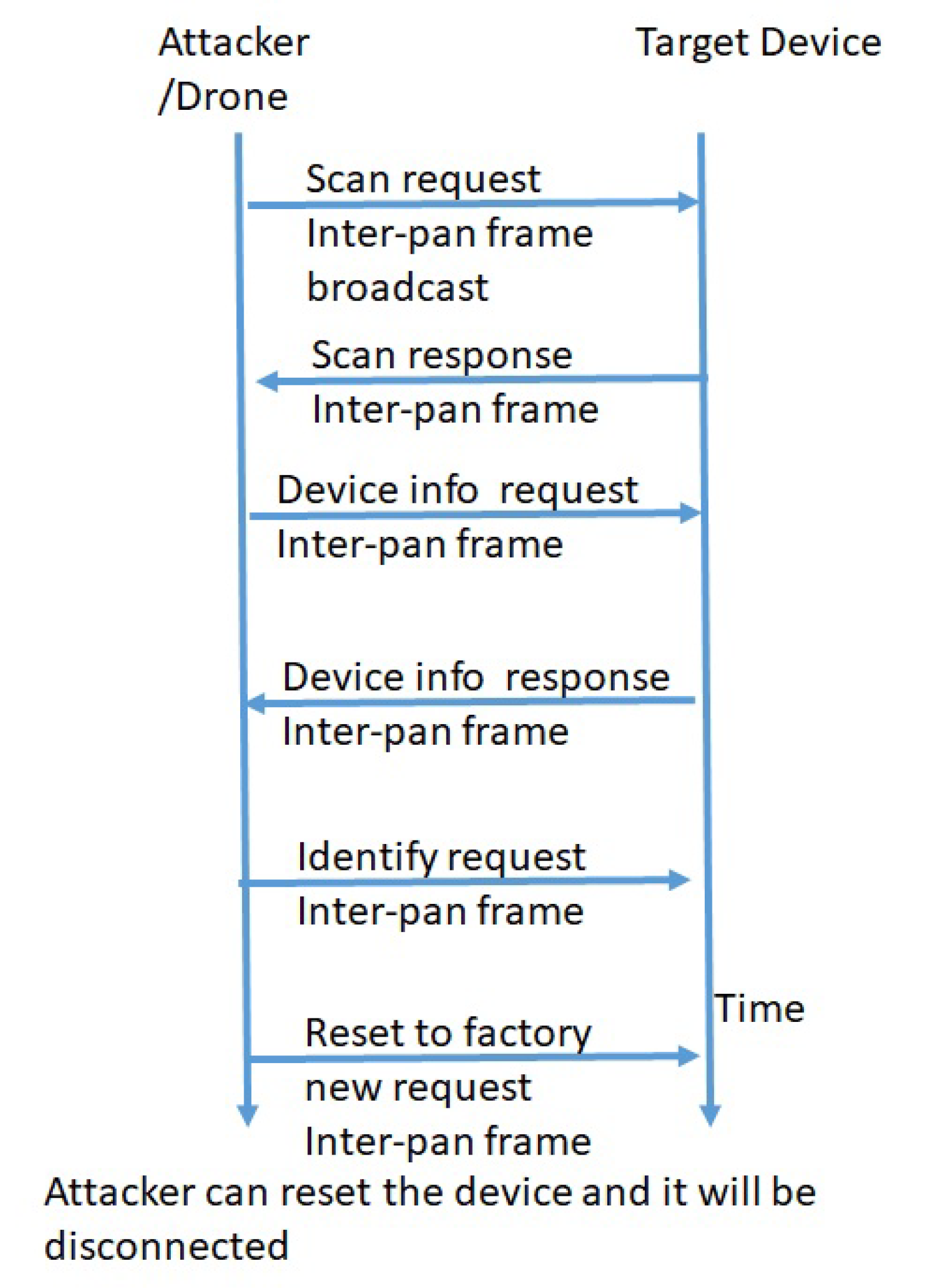
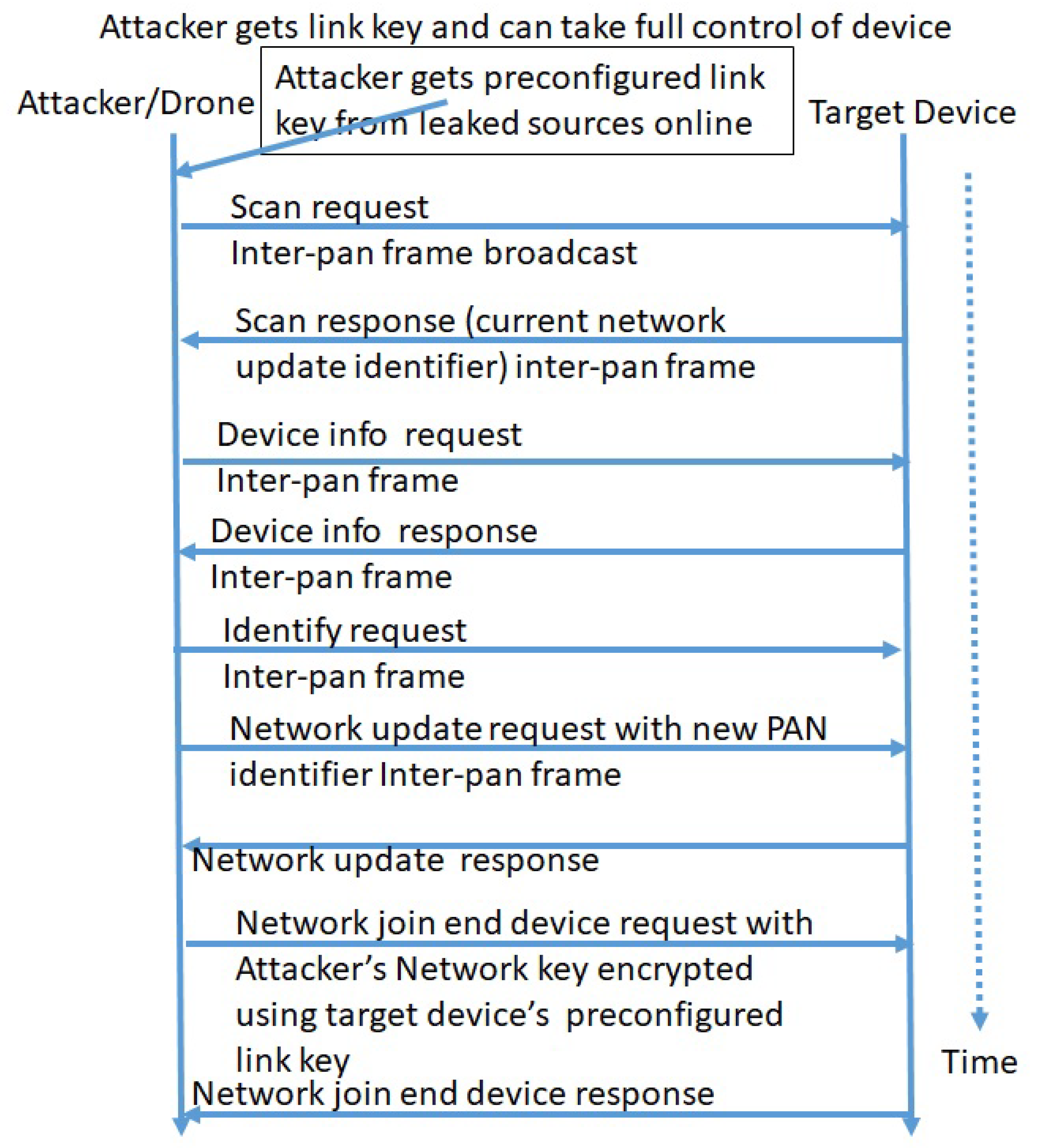
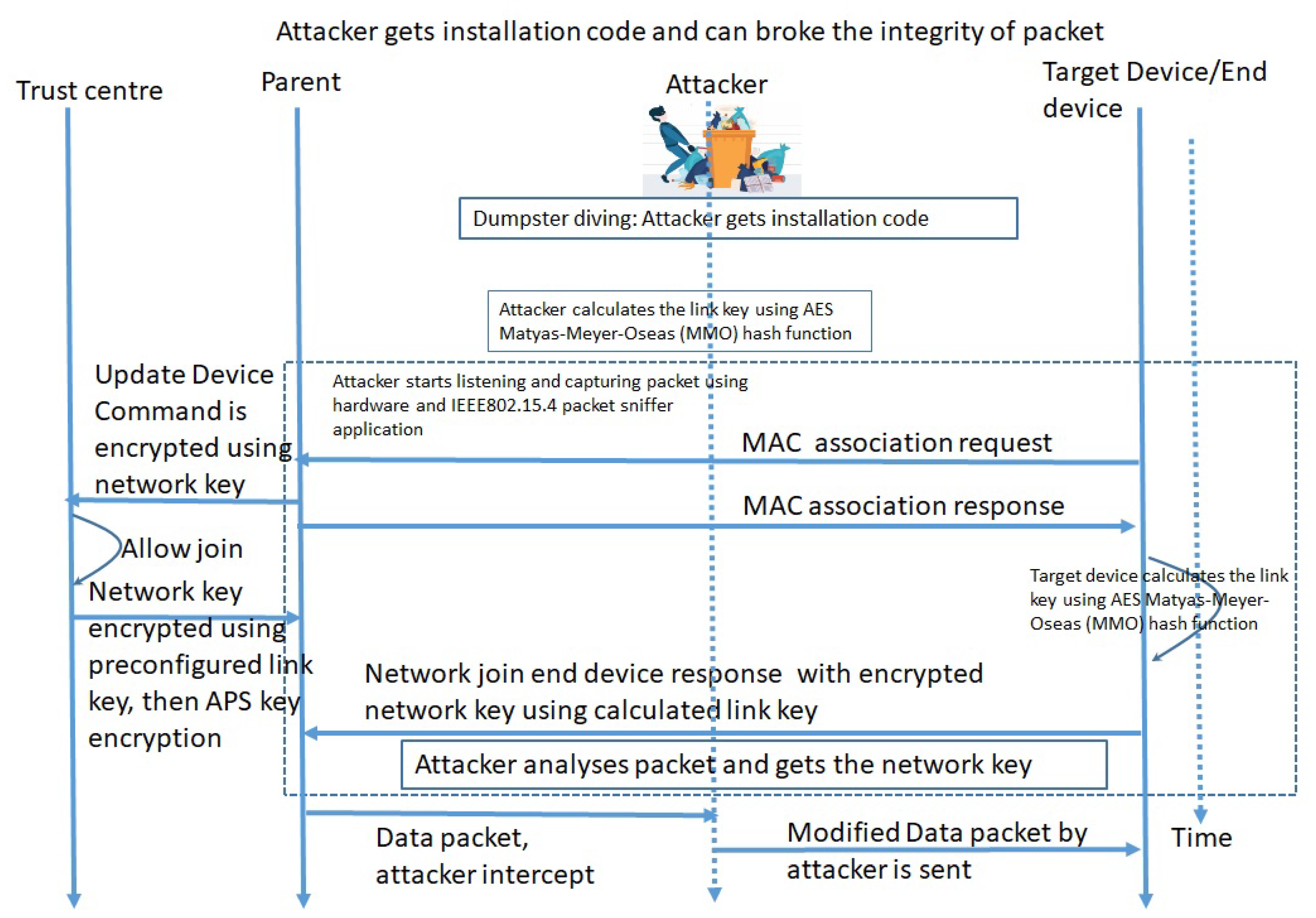
| IoMT Device (1) | Hardware | Hardware: Design Flaw Buffer Overflow Low Processing Power Software: 0-day Vulnerabilities Firmware or operating system vulnerabilities Sensor and actuator: Weak encryption or no encryption emanations or radiation from devices by visible or non-visible spectrum that causes data leakage Insecure key storage ( availability of link-key online availability of installation code) default link key values Unauthorized commissioning |
| Software | ||
| Sensor | ||
| Actuators | ||
| Other IoT Ecosystem Devices (2) | Devices to interface with things | Device to interface: insecure interfaces, Improper IT Assets or business processes design inadequate specifications of IT products, design errors, Device to manage: inadequate usability, policy or procedure flows, Embedded system:lack of mutual authentication between the client and the server |
| Devices to Manage things | ||
| Embedded System | ||
| Infrastructure (3) | Routers | Routers: Buffer overflow, Anonymous proxies, vulnerabilities on the routing path Gateways: lack of appropriate segmentation and security architecture, improper segregation Power supply and Security assets: Management protocols are not secure, often no encryption. |
| Gateways | ||
| Power Supply | ||
| Security Assets | ||
| Platform and Backend (4) | Web Based Services | Web Based Services: Design Flaw, Buffer overflow complex monitoring due to high traffic gap between service provider, Cloud Infrastructure: data owner security control mis-configuration inherently exposed to external access |
| Cloud Infrastructure and Services | ||
| Application and Services (5) | Data Analytics and Visualization | Data Analytics: Code injection, SQL injection, Path injection, Inference, aggregation Network and device Management and usages: Default configuration and password, clear text PDU in management protocol, no encryption in management packet exchange |
| Devices and Network Management | ||
| Device Usages | ||
| Information (6) | Patients’ medical record, medical imaging and picture | Lack of proper storage with encryption and poor encryption for data transmission,weak access control |
| Authentication: FIM framework (SAML): SAML Protocol, SAML Profiles, SAML artefacts, (7) | Client’s device (BYOD), Organization device, workstation, Clinician’s own workstation and similar devices | SAML binding does not require any authentication , susceptible to all attacks, No authentication and confidentiality requirement for SAML response and assertions, no authentication for service provider to use SAML assertion |
| IOT devices: Network protocols, Perception layer, Application layer (8) | Wireless Sensor Network (WSN) | lack of encryption, SNMP agent default community string, Heartbleed bug, Factoring RSA export keys, Lack of Monitoring, insufficient authentication and authorization, poor configuration management, lack of physical security, lack of transport layer encryption, Design Flaw, Buffer overflow, Low Processing Power, default credential, no authentication |
| Radio Frequency Identification (RFID) services | ||
| Web Based Services | ||
| Cloud Infrastructure and Services | ||
| Data Mining Application | ||
| Data Processing and Computing | ||
| FIM framework: Oauth (9) | OAuth protocols and related application software | Lack of proper authentication to verify the authorization server, insecure transmission of query parameters in URI, CSRF bug |
| Assets | Threat Event | Likelihood | Vulnerability Rating | Impact | Risk | Level of risk | Central patient monitoring devices | IoMT end devices | MCPS (Surgical robots, other MCPS in hospital) | Risk treatment |
|---|---|---|---|---|---|---|---|---|---|---|
| IoMT Device: Hardware | Unauthorized access to facility Theft, Fraud, Sabotage, Vandalism, Hardware malfunction Supply chain attack " | 5 | 3 | 9 | 135 | Low | low | low | low | "Applying Physical Control, Proper Control in Supply Chain" |
| IoMT Device : Software | Access to device software, Alteration of Software, Abuse of 0-day Vulnerabilities" | 8 | 7 | 9 | 504 | High | High | High | High | Manage and maintain strong password policy, update on patch and technology, Regular Vulnerability Assessment and Penetration Testing (VAPT), Disable unwanted functions Anti-DDoS tool, IPS,IDS installation, Monitoring and Update, |
| IoMT Device: Sensor | Rating modification, Deletion Supply Chain attack | 8 | 4 | 8 | 256 | Moderate | Moderate | Moderate | Moderate | Proper Monitoring Proper Control in Supply Chain |
| IoMT Device: Actuators | Loss of integrity via compromised communication | 5 | 7 | 7 | 245 | Moderate | Moderate | Moderate | Moderate | "Proper Monitoring Proper Control in Supply Chain" |
| IoT Ecosystem : Devices to interface with things | Supply Chain attack | 5 | 3 | 5 | 75 | Very Low | Very Low | Very Low | Very Low | "Message encryption, Anti DDoS, Backup, Proper Control in Supply Chain" |
| IoT Ecosystem : Devices to Manage things | "Man in the middle Supply Chain attack" | 8 | 3 | 5 | 120 | Low | Low | Low | Low | "Message encryption, Anti DDoS, Backup, Proper Control in Supply Chain" |
| IoT Ecosystem : Embedded System | "Eavesdrop attack, Spoofing attacks. Replay attack, Message Deletion Modification, DOS attack" | 5 | 5 | 9 | 225 | Moderate | Moderate | Moderate | Moderate | "Proper Control in Supply Chain Message encryption" |
| Infrastructure: Routers | Sniffinig, DoS, MITM, Brute-Force, device duplication attacks. | 9 | 7 | 9 | 567 | High | High | High | High | Anti-DDoS tool, IPS installation, Monitoring and Update, network segmentation and segregation, appropriate boundary protection, installation of DMZ server and separate critical data assets and critical devices |
| Infrastructure: Gateways | Key Reset, impersonation, node spoofing, Black Hole attacks. | 9 | 7 | 9 | 567 | High | High | High | High | Monitoring and Incident response |
| Infrastructure: Power Supply | ED/LC, Same-Nonce attack. | 9 | 7 | 8 | 504 | High | High | High | High | Monitoring and Incident response |
| Infrastructure: Security Assets | Web application attacks , injection attacks (Code injection: SQL, XSS) DoS, DDoS, Replay, Channel collision, Application layer attack i.e. Ping of Death , XDoS, WinNuke , HTTP Floods" | 9 | 9 | 9 | 729 | Very High | very High | very High | very High | "Anti-DDoS tool, IPS installation, Monitoring and Update" |
| Assets | Threat Event | Likelihood | Vulnerability Rating | impact | Risk | Level of risk | Central patient monitoring devices | IoMT end devices | MCPS (Surgical robots, other MCPS in hospital) | Risk treatment |
|---|---|---|---|---|---|---|---|---|---|---|
| Platform and Backend: Web Based Services | Installing default link keys or sending security headers in clear text on auxiliary frames, logging that causes DoS, euses of Initiation Vectors which may lead to key compromise, energy-consuming attacks. | 9 | 9 | 9 | 729 | Very High | very High | very High | very High | Anti-DDoS tool, IPS installation, Monitoring and Update, strong remote access mechanism, logging and alert system to targeted server functions, regular scanning and evaluation of interface and code including , proper control for configuration and change management |
| Platform and Backend: Cloud Infrastructure and Services | Sybil, DoS, wormhole, Jaming , traffic analysis attack. | 5 | 5 | 9 | 225 | Moderate | Moderate | Moderate | Moderate | IPS installation, Anti-Virus , Malware deployment, Monitoring and Update, Robust configuration/change control, data storage communication encryption, training of system administrators |
| Application: Data Analytics and Visualization | Replay attacks, recovery of passwords, malicious message modification, battery exhaustion and DoS. | 9 | 5 | 9 | 405 | Moderate | Moderate | Moderate | Moderate | Message encryption,Anti-DDoS,input validation, output throttling, anonymization |
| Application: Devices and Network Management | Spoofing or integrity attacks, Flooding attacks, Worms/ Trojans, Rootkits, Elevation of Privileges, | 9 | 5 | 9 | 405 | Moderate | Moderate | Moderate | Moderate | |
| Application: Device Usages | Eavesdropping- theft- breach and manipulation, flooding attacks, Abuse of Information Leakage | 9 | 9 | 9 | 729 | Very High | Very High | Very High | Very High | |
| Patients’ medical record, medical imaging and picture | At Rest: Parsing, Cache, amplification, spoofing. Cross-protocol attacks. | 9 | 9 | 9 | 729 | Very High | Moderate | low | low | Boundary protection, strong password, Encryption in storage, Antimalware, Port authentication, Log monitoring, Use of SIEM, output throttling system, Tokenization of data, regular backup, Data Loss Prevention (DLP)" |
| Patients’ medical record, medical imaging and picture | In Transit: Traffic analysis, Port Obscurity, sniffing and password cracking in wireless communication, get user detail, installation of backdoor on digital imaging and communications in medicine (DICOM) server | 9 | 9 | 9 | 729 | Very High | Moderate | low | low | |
| Patients’ medical record, medical imaging and picture | In use: Import of patient data from media storage which has malware embedded, back door installation in this way | 8 | 8 | 8 | 512 | High | Moderate | low | low |
| Assets | Threat Event | Likelihood | Vulnerability Rating | Impact | Risk | Level of risk | Central patient monitoring devices | IoMT end devices | MCPS (Surgical robots, other MCPS in hospital) | Risk treatment |
|---|---|---|---|---|---|---|---|---|---|---|
| FIM SAML: Cleint’s device (BYOD), Organization device, workstation, | Eavesdropping: -Theft of user authentication info -Theft of bearer token, malicious app installed in client’s device, XMLDSIG’s canonicalization algorithms provides weak protection that allow attackers to bypass authentication by creating identical cryptographic signature using XML documents, XML parsing problem can cause incorrect authentication in the SAML assertion" | 9 | 9 | 9 | 729 | Very High | Very High | Low | Very High | Educate clinicians, monitor the log, alert system, tracking clients, Proper Installation of SAML scanner:SOAP encryption and message integrity, SOAP binding level digital signature, authentication for service provider for SAML assertion and artifacts match, and change management of servers, regular evaluate and asses SAML codes, Mobile device management installed, limit apps installation, Blockchain for digital identity management,managing privacy preferences |
| FIM SAML: Cleint’s device (BYOD), Organization device, workstation, | Replay | 2 | 5 | 5 | 50 | High | Very High | Low | Very High | |
| FIM SAML: Cleint’s device (BYOD), Organization device, workstation, | Message Insertion | 2 | 5 | 5 | 50 | Very Low | Very High | Low | Very High | |
| FIM SAML: Cleint’s device (BYOD), Organization device, workstation, | Message Deletion | 2 | 5 | 5 | 50 | Very Low | Very High | Low | Very High | |
| FIM SAML: Cleint’s device (BYOD), Organization device, workstation, | Message modification | 8 | 8 | 8 | 512 | High | Very High | Low | Very High | |
| FIM SAML: Cleint’s device (BYOD), Organization device, workstation, | Man in the middle | 9 | 8 | 10 | 720 | High | Very High | Low | Very High | |
| IOT devices: Wireless Sensor Network (WSN) | Jamming, Tampering, Exhaustion, Collision, Unfairness | 8 | 8 | 10 | 640 | High | High | High | High | FHSS,DSSS, Regulated transmitted power, Raising Alarm, Rate Limiting, Error -Correction Code, Small Frames Transmission |
| IOT devices:Radio Frequency Identification (RFID) | Permanently disable tag, Temporarily disable tag, Replay Attack | 7 | 8 | 10 | 560 | High | High | High | High | Public-key cryptography Distance Limiting |
| IOT devices:Web Based Services | DoS, Replay, Channel collision, Spoofing attacks. | 5 | 5 | 10 | 250 | Moderate | Moderate | Moderate | Moderate | "Public-key cryptography, Strong Password Management, Monitoring, Supply chain Monitoring, Anti malware tool, Port authentication, Network and Application policy enforcement etc." |
| IOT devices: Cloud Infrastructure and Services | Installing default link keys or sending security headers in clear text on auxiliary frames, Energy-consuming attacks. | 5 | 5 | 8 | 200 | Moderate | Moderate | Moderate | Moderate | |
| IOT devices: Data Mining Application | Sybil, DoS, Wormhole, Jaming , Traffic analysis attack. | 7 | 7 | 7 | 343 | Moderate | Moderate | Moderate | Moderate | |
| IOT devices: Data Processing and Computing | Use of malicious intermediary network nodes, Signal jamming, traffic analysis, attackers selectively prevent correct packet reassembly. | 10 | 8 | 10 | 800 | Very High | Very High | Very High | Very High |
| Assets | Threat Event | Likelihood | Vulnerability Rating | Impact | Risk | Level of risk | Central patient monitoring devices | IoMT end devices | MCPS (Surgical robots, other MCPS in hospital) | Risk treatment |
|---|---|---|---|---|---|---|---|---|---|---|
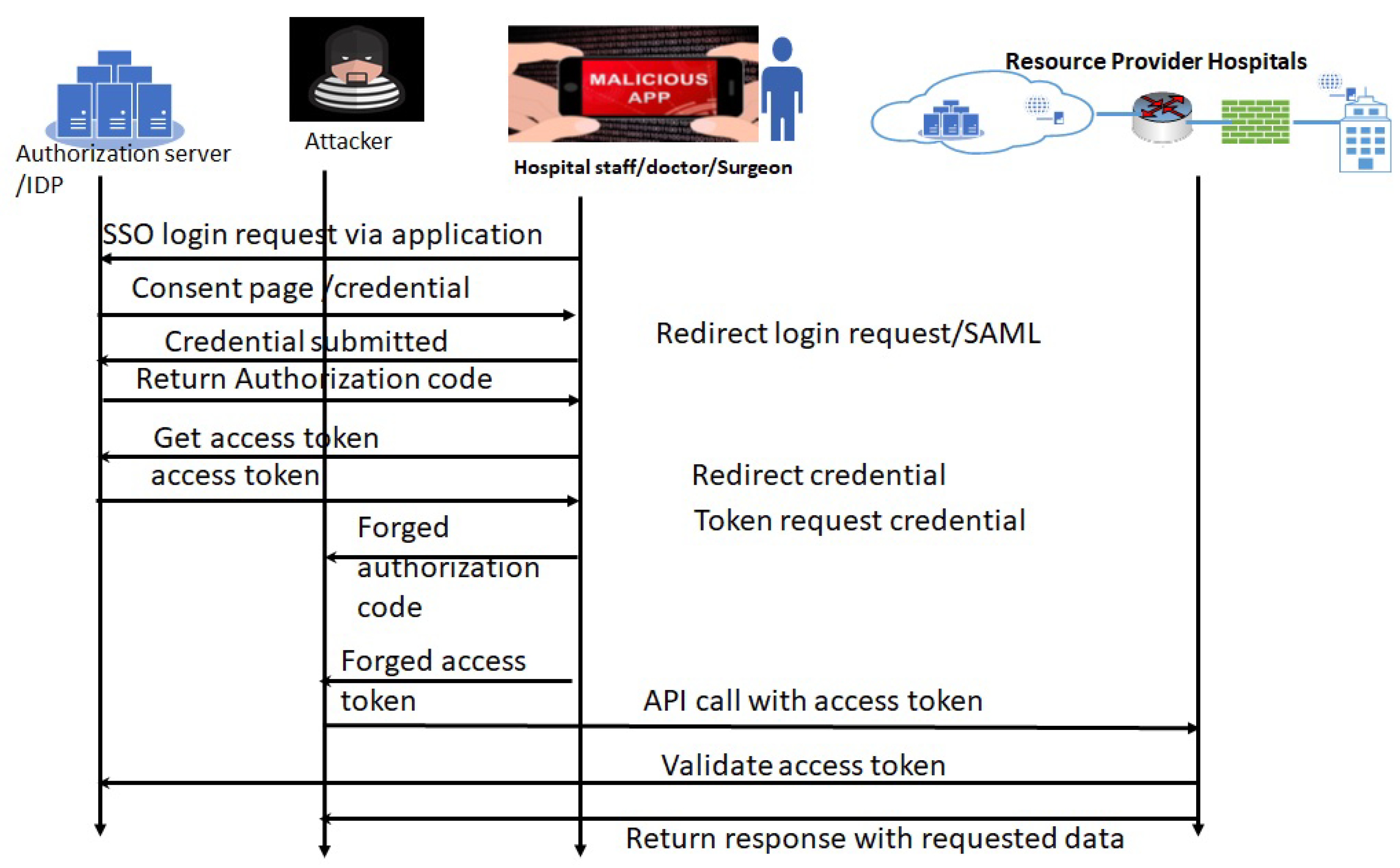
| Oauth related services and applications | ARP Spoofing, Cache Poisoning, Cross-Site scripting, Man-in-The-Middle (MITM), Drown attack, Denial of Service(DoS) attack, buffer overflow, injection attack, hijacking, Flooding Attacks, EternalBlue attack, trojan horse attacks, shell script attacks, directory harvest attack, Malfunction, Remote Code Execution, Unauthorized Access. | 9 | 9 | 9 | 729 | Very High | Very High | Very High | Very High | Educate clinicians, monitor the log, use of alert system, tracking of clients location, patching updating of systems, continuous configuration and change management of servers, regular evaluate and asses OAuth interfaces and codes , Mobile device management software installed including device tracking, wiping, policy enforcement, limit apps installation, use tools to verify between code and user, in the implementation redirect-URL should use SSL TLS, use of vulnerability scanner such as OAuth scanner, Perform Blockchain for digital identity management (consider the managing privacy preferences) in healthcare system, Perform industrial IoT Blockchain to secure searchable encryption approach. |
| Oauth related services and applications | Replay attack | 7 | 7 | 7 | 343 | Moderate | Very high | Moderate | Very high | |
| Oauth related services and applications | Message modification | 5 | 5 | 5 | 125 | Low | Very high | Moderate | Very high | |
| Oauth related services and applications | Man in the middle, stolen credential | 9 | 9 | 9 | 729 | Very high | Very high | Moderate | Very high | |
| Oauth related services and applications | Impersonation attack: Stolen access token, stolen authorization code, malicious app installed, mis-configuration and incorrect implementation of interface in the web application for implicit grant flow and authorization code allows cross-site request forgery (CSRF) and redirection of endpoint to the attackers. | 9 | 9 | 9 | 729 | Very high | Very high | Moderate | Very high | Educate clinicians, monitor the log, use of alert system, tracking of clients location, patching updating of systems, continuous configuration and change management of servers, regular evaluate and asses OAuth interfaces and codes , Mobile device management software installed including device tracking, wiping, policy enforcement, limit apps installation, use tools to verify between code and user, in the implementation redirect-URL should use SSL/TLS, use of vulnerability scanner such as OAuth scanner, Perform industrial IoT Blockchain to secure searchable encryption approach |
4. Future Research Scope
5. Conclusions
Author Contributions
Conflicts of Interest
References
- Sun, Y.; Lo, F.P.W.; Lo, B. Security and Privacy for the Internet of Medical Things Enabled Healthcare Systems: A Survey. IEEE Access 2019, 7, 183339–183355. [CrossRef]
- Nair, M.; Tyagi, A.; Goyal, R. Medical Cyber Physical Systems and Its Issues. Procedia Computer Science 2019, 165, 647–655. [CrossRef]
- Razdan, S.; Sharma, S. Internet of Medical Things (IoMT): Overview, Emerging Technologies, and Case Studies. IETE Technical Review 2021, 0, 1–14.
- Food, U.; Administration, D. Cybersecurity Vulnerabilities Affecting Medtronic Implantable Cardiac Devices, Programmers, and Home Monitors: FDA Safety Communication. https://www.fda.gov/medical-devices/safety-communications/cybersecurity-vulnerabilities-affecting-medtronic-implantable-cardiac-devices-programmers-and-home.
- Bryce Alexander, Victor Neira, e.a. Implantable Cardioverter-Defibrillator–Cybersecurity. Arrhythmia and Electrophysiology 2020, PP, 1–1.
- Mersini, P.; Sakkopoulos, E.; Tsakalidis, A. APPification of hospital healthcare and data management using QRcodes. In Proceedings of the IISA 2013. IEEE, 2013, pp. 1–6.
- Crossley, G.H.; Boyle, A.; Vitense, H.; Chang, Y.; Mead, R.H.; Investigators, C. The CONNECT (Clinical Evaluation of Remote Notification to Reduce Time to Clinical Decision) trial: the value of wireless remote monitoring with automatic clinician alerts. Journal of the American College of Cardiology 2011, 57, 1181–1189.
- Das, S.; Siroky, G.P.; Lee, S.; Mehta, D.; Suri, R. Cybersecurity: the need for data and patient safety with cardiac implantable electronic devices. Heart Rhythm 2021, 18, 473–481.
- Floyd, T.; Grieco, M.; Reid, E. Mining hospital data breach records: Cyber threats to U.S. hospitals. 09 2016, pp. 43–48. [CrossRef]
- Bhargav-Spantzel, A.; Squicciarini, A.C.; Bertino, E. Establishing and protecting digital identity in federation systems. In Proceedings of the Proceedings of the 2005 workshop on Digital identity management, 2005, pp. 11–19.
- Omnipod. Omnipod Improper Access Control: Cybersecurity Vulnerability Summary. https://www.omnipod.com/product-security/security-bulletins/march-18-2020.
- Healthcare, G. CCARESCAPE Central Station. https://www.gehealthcare.com/products/patient-monitoring/patient-monitors/carescape-central-station.
- Food, U.; Administration, D. Cybersecurity Vulnerabilities in Certain GE Healthcare Clinical Information Central Stations and Telemetry Servers: Safety Communication. https://www.fda.gov/medical-devices/safety-communications/cybersecurity-vulnerabilities-certain-ge-healthcare-clinical-information-central-stations-and.
- Zeljka Zorz, Managing Editor, H.N.S. MDhex vulnerabilities open GE Healthcare patient monitoring devices to attackers. https://www.helpnetsecurity.com/2020/01/24/vulnerabilities-patient-monitoring-devices/.
- Sun, Y.; Lo, F.P.W.; Lo, B. Security and privacy for the internet of medical things enabled healthcare systems: A survey. IEEE Access 2019, 7, 183339–183355.
- HIPAA Journal on Aug 23, . July 2021 Healthcare Data Breach Report. https://www.hipaajournal.com/july-2021-healthcare-data-breach-report/.
- arXiv:cs.RO/1504.04339].Bonaci, T.; Herron, J.; Yusuf, T.; Yan, J.; Kohno, T.; Chizeck, H.J. To Make a Robot Secure: An Experimental Analysis of Cyber Security Threats Against Teleoperated Surgical Robots, 2015, [arXiv:cs.RO/1504.04339].
- MOTTRIE, P.A. Current use of robots in clinical practice (inside the body, on the body and outside the body) and 4ts perspective. In Proceedings of the the proceedings of Workshop on Robots in healthcare:a solution or a problem?, 05 2019.
- Fosch Villaronga, E.; Mahler, T. Cybersecurity, safety and robots: Strengthening the link between cybersecurity and safety in the context of care robots. Computer Law and Security Review 2021, 41, 105528. [CrossRef]
- Li M, Yang L, e.a. An Approach for Mitigating Potential Threats in Practical SSO Systems. Information Security and Cryptology. Inscrypt 2015. Lecture Notes in Computer Science 2016, 9589.
- Gwizdala, S. Healthcare Digital Ecosystems Hinge on Modern Identity. https://www.forgerock.com/blog/healthcare-digital-ecosystems-hinge-modern-identity.
- Xie, M.; Huang, W.; Yang, L.; Yang, Y. VOAuth: A solution to protect OAuth against phishing. Computers in Industry 2016, 82, 151–159. [CrossRef]
- Navas, J.; Beltrán, M. Understanding and mitigating OpenID Connect threats. Computers and Security 2019, 84. [CrossRef]
- Wilson, M.; Hash, J. Building an Information Technology Security Awareness and Training Program.
- Ahmed, Y.; Naqvi, S.; Josephs, M. Cybersecurity Metrics for Enhanced Protection of Healthcare IT Systems. 05 2019, pp. 1–9. [CrossRef]
- Coppolino, L.; D’Antonio, S.; Sgaglione, L.; Magliulo, M.; Pacelli, R. Protecting Critical Business Processes of Smart Hospitals from Cyber Attacks. In Proceedings of the 2019 15th International Conference on Signal-Image Technology and Internet-Based Systems (SITIS), 2019, pp. 363-367, doi:, 11 2019, pp. 363–367.
- Abouzakhar, N.; Jones, A.; Angelopoulou, O. Internet of Things Security: A Review of Risks and Threats to Healthcare Sector. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), 2017, pp. 373-378, doi: 10.1109/iThings-GreenCom-CPSCom-SmartData.2017.62., 06 2017, pp. 373–378. [CrossRef]
- Kim, D.W.; Choi, J.Y.; Han, K.h. Medical Device Safety Management Using Cybersecurity Risk Analysis. IEEE Access 2020, PP, 1–1. [CrossRef]
- Kim, D.W.; Choi, J.Y.; Han, K.H. Medical device safety management using cybersecurity risk analysis. IEEE Access 2020, 8, 115370–115382.
- Kintzlinger, M.; Nissim, N. Keep an eye on your personal belongings! The security of personal medical devices and their ecosystems. Journal of biomedical informatics 2019, 95, 103233.
- Zaki, M.; Sivakumar, V.; Shrivastava, S.; Gaurav, K. Cybersecurity Framework For Healthcare Industry Using NGFW. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV). IEEE, 2021, pp. 196–200.
- Coppolino, L.; D’Antonio, S.; Romano, L.; Sgaglione, L.; Magliulo, M.; Pacelli, R. Protecting critical business processes of Smart Hospitals from cyber attacks. In Proceedings of the 2019 15th International Conference on Signal-Image Technology and Internet-Based Systems (SITIS). IEEE, 2019, pp. 363–367.
- Ranganayaki, R.S.; Sreeja, B.; Gandhari, S.; Ranganath, P.T.; Kumar, S. Cyber Security in Smart Hospitals: A Investigational Case Study. In Proceedings of the 2021 10th International Conference on System Modeling and Advancement in Research Trends (SMART). IEEE, 2021, pp. 92–98.
- Gomi, H.; Hatakeyama, M.; Hosono, S.; Fujita, S. A delegation framework for federated identity management. In Proceedings of the Proceedings of the 2005 workshop on Digital identity management, 2005, pp. 94–103.
- Kandasamy, K.; Srinivas, S.; Achuthan, K.; Rangan, V.P. Digital Healthcare-Cyberattacks in Asian Organizations: An Analysis of Vulnerabilities, Risks, NIST perspectives, and Recommendations. IEEE Access 2022.
- Wang, Z.; Ma, P.; Zou, X.; Zhang, J.; Yang, T. Security of medical cyber-physical systems: An empirical study on imaging devices. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). IEEE, 2020, pp. 997–1002.
- Christopher J. Alberts, Sandra Behrens, R.D.P. Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) Framework, Version 1.0.
- ENISA. EBIOS:Expression des Besoins et Identification des Objectifs de Sécurité. https://www.enisa.europa.eu/topics/risk-management/current-risk/risk-management-inventory/rm-ra-methods/m_ebios.html.
- Eliash, C.; Lazar, I.; Nissim, N. SEC-CU: the security of intensive care unit medical devices and their ecosystems. IEEE Access 2020, 8, 64193–64224.
- Kumar, D.; Khan, A.H.; Nayyar, H.; Gupta, V. Cyber Risk Assessment Model for Critical Information Infrastructure. In Proceedings of the 2020 International Conference on Power Electronics and IoT Applications in Renewable Energy and its Control (PARC). IEEE, 2020, pp. 292–297.
- Abidin, Z.Z.; Abas, Z.A.; Zakaria, N.A.; Hashim, N.A.; Mardaid, E.; Ahmad, R.; Puvanasvaran, A.P. Conceptual Model of Risk Assessment for Insider Threats Detection. In Proceedings of the 2019 1st International Conference on Electrical, Control and Instrumentation Engineering (ICECIE). IEEE, 2019, pp. 1–6.
- Abouzakhar, N.S.; Jones, A.; Angelopoulou, O. Internet of things security: A review of risks and threats to healthcare sector. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData). IEEE, 2017, pp. 373–378.
- Gia, T.N.; Rahmani, A.M.; Westerlund, T.; Liljeberg, P.; Tenhunen, H. Fault tolerant and scalable IoT-based architecture for health monitoring. In Proceedings of the 2015 IEEE Sensors Applications Symposium (SAS). IEEE, 2015, pp. 1–6.
- Feras M Awaysheh, Mamoun Alazab, e.a. Next-generation big data federation access control: A reference model. Future Generation Computer Systems 2020, 108, 726–741.
- Cybersecurity, T.; Infrastructure Security Agency, U. CRR Supplemental Resource Guide: Volume 1, Asset Management, Version 1.1. https://www.forgerock.com/blog/healthcare-digital-ecosystems-hinge-modern-identity.
- Ross, R. Special Publication (NIST SP) - 800-30 Rev 1. In Proceedings of the Guide for Conducting Risk Assessments, Special Publication (NIST SP), National Institute of Standards and Technology), 2012, pp. 112–120. [CrossRef]
- Aljerf, L. Development of a method for classification of hospitals based on results of the diagnosis-related groups and the principle of case-mix index. EMHJ-Eastern Mediterranean Health Journal 2016, 22, 327–334.
- Johansmeyer, T. Cybersecurity Insurance Has a Big Problem. https://hbr.org/2021/01/cybersecurity-insurance-has-a-big-problem.
- Jack.. Obtaining Login Tokens for an Outlook, Office or Azure Account. https://whitton.io/articles/obtaining-tokens-outlook-office-azure-account/.
- Vanhoef, M.; Piessens, F. Key Reinstallation Attacks Breaking WPA2 by forcing nonce reuse, 2017.
- Li, V. Common Pitfalls Of Custom SAML Implementations, 2020.

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





