Submitted:
26 December 2023
Posted:
26 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Fieldbus Networks in Smart Homes and Buildings
- Field-level IP protocol implementation with real-time requirements;
- Development of IoT structures for fieldbus networks;
- Assumptions for implementation of edge and fog services;
- Big data processing within the edge and cloud computing for BACS and BMS;
- Cybersecurity and data privacy;
- Energy efficiency and energy consumption reducing for wireless modules – sensors as well as actuators.
1.2. Edge and Fog Computing within Advanced Home and Building Automation Systems
1.3. Original Contributions and the Paper Strucure
- Providing a comprehensive review of the state-of-the art on IoT technics and solutions related to smart homes and buildings with distributed control systems. This review is important because it collects knowledge about adapting and using IoT technologies in a segment that is rapidly developing, but has so far been based on its own solutions for communication and data processing, in particular at the field-level;
- Opposed to other IoT technology reviews, this one analyzes and discuss the suitability of various IoT concepts and tools for smart homes and buildings. Moreover, it sheds light on trends and innovative solutions emerging from this field, that could be motivating for interested researchers and engineers;
- Providing new perspective on various IoT applications (e.g., edge and fog computing, big data processing) supported by recent research studies. To this end, this review provides some of the IoT design practices considering the unique properties of smart homes and buildings, that finally will lead to more effective data processing, control and monitoring functions execution as well as better integration;
- Presenting the major challenges, trends and pinpointing to new open research issues that need attention from researchers and domain experts, engineers. In particular, this review provides insight into the future scope of research on the integration of AI and ML capabilities, tactile internet developments, and IoT technology maturity assessment in building applications;
- Proposing general assumptions for generic IoT framework concept with SWOT analysis as well as pros and cons discussion.
2. Control Networks and Smart Technologies in Buildings
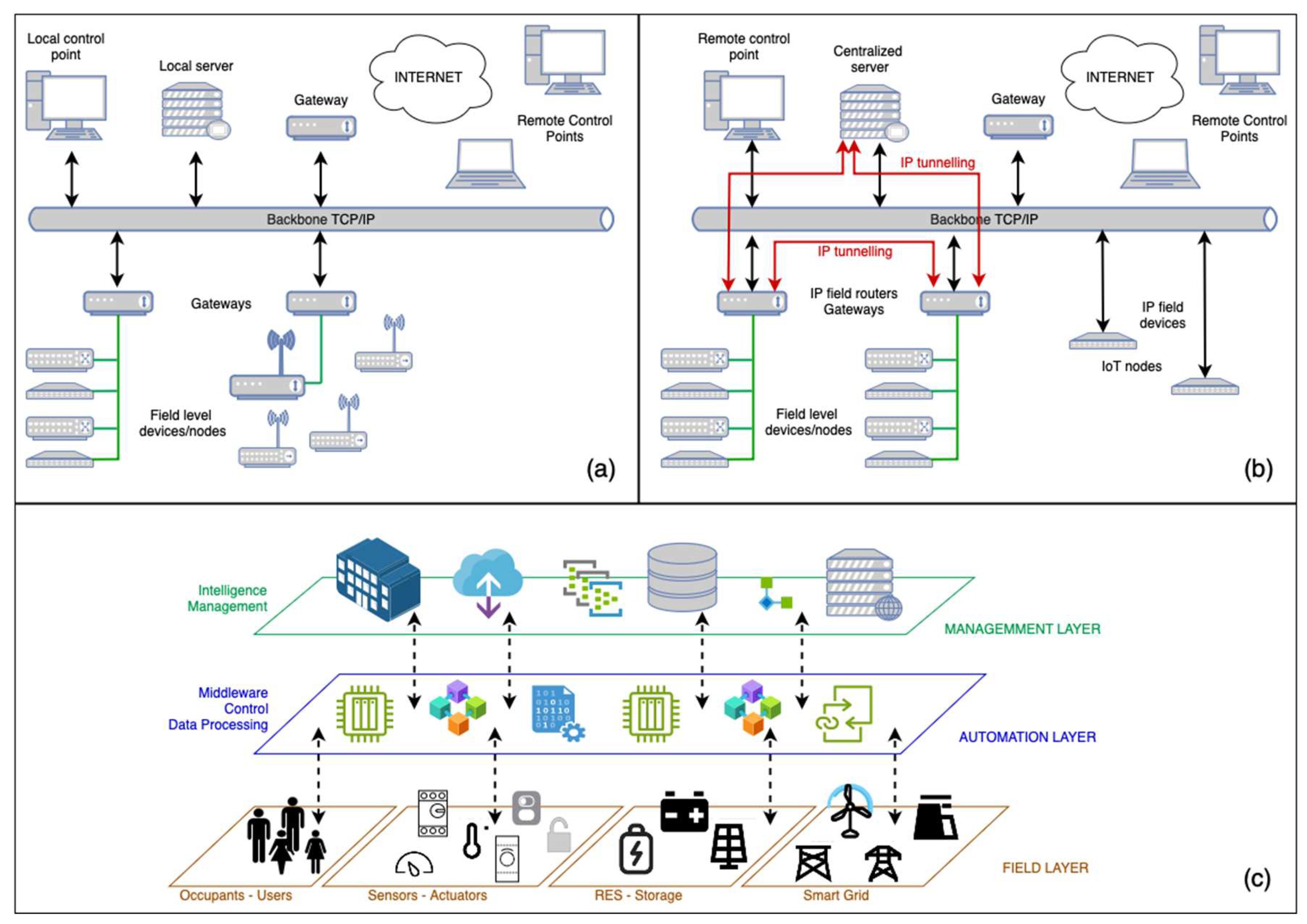
2.1. Distributed Control Approach
- Field Layer, the lowest one, where the interaction with field devices (sensors, actuators) happens as well as environmental data are collected, and parameters of the environment are physically controlled in response to commands from the system;
- Automation Layer, the middle layer, where data are processed, control loops are executed, and alarms are activated as well as processing entities also communicate values of more global interest to each other and values for vertical access by next management level are prepared (possibly aggregated);
- Management Layer, the top layer, where information from throughout the entire system is accessible as well as activities like system data presentation, forwarding, trending, logging, and archival take place. Moreover, vertical access to all BACS values is provided, including the modification of parameters such as schedules and long-term historical data storage with the possibility to generate reports and statistics is implemented as well.
2.2. IoT Structures and Technologies for Building Automation
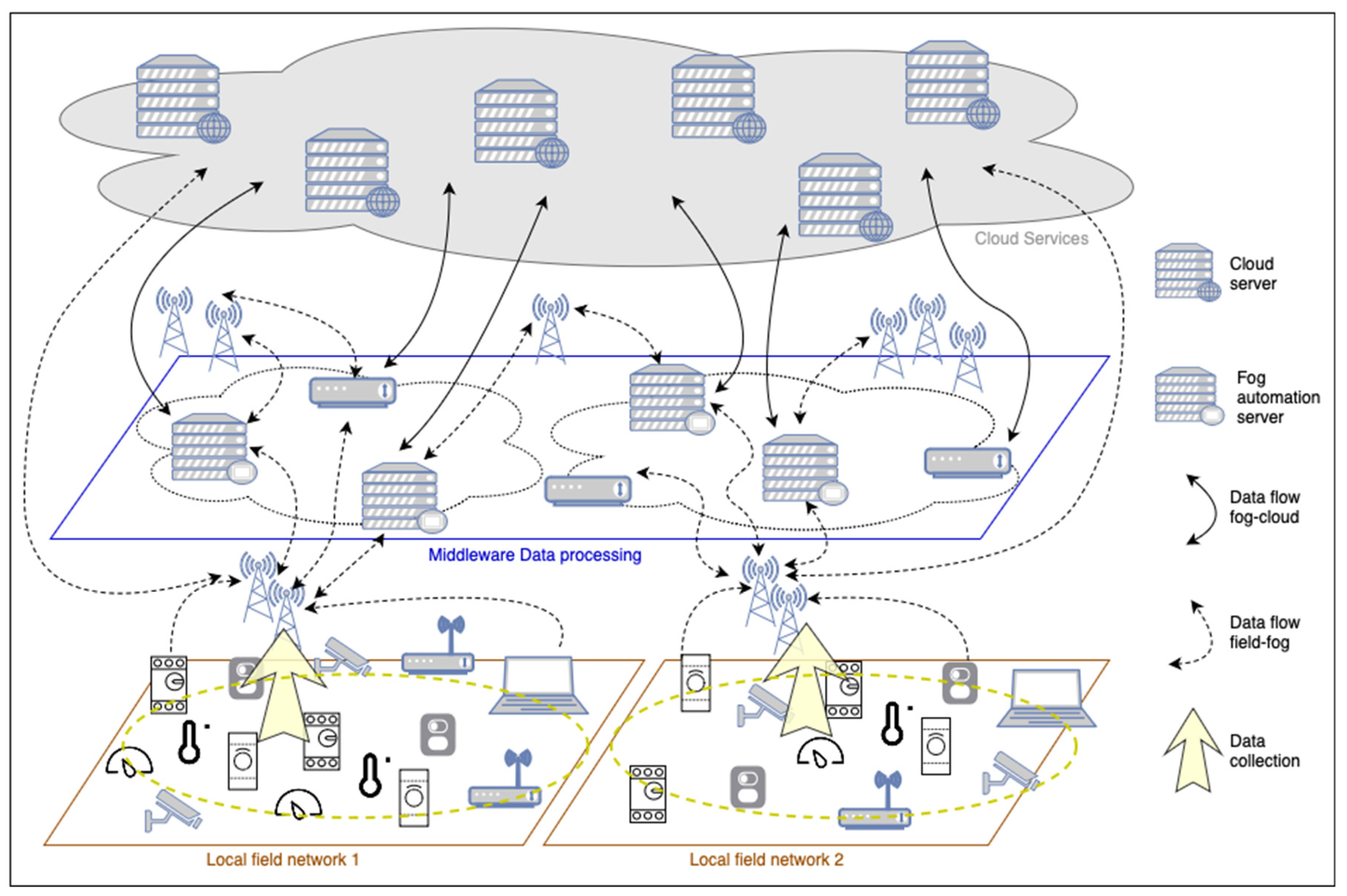
3. The IoT with Edge and Fog Computing in Buildings – Main Challenges
3.1. Service Oriented IoT and Edge and Fog Computing in BACS and BMS
3.2. Big Data Processing and Cloud Computing
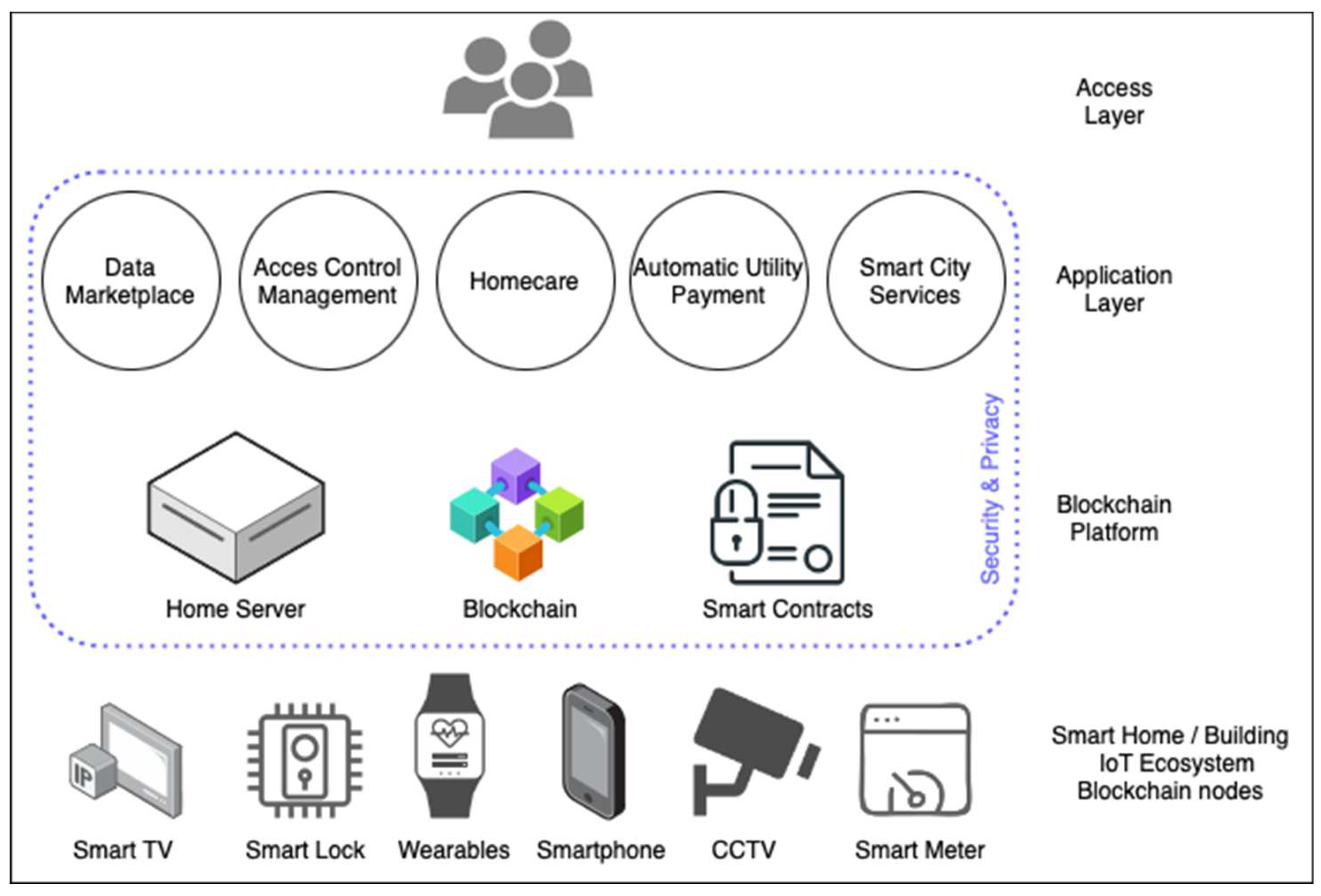
3.3. Cybersecurity, Privacy and Blockchain Solutions for Distributed IoT in Buildings
- Heterogeneity of devices and communication, resulting from the coexistence of various modules/nodes in one network structure (from small sensors, relays, to large modules of automation servers, data servers) and the fact that they are produced by various manufacturers, often with different hardware architectures, supporting various types of software tools;
- Integration of physical devices, the result of aforementioned “openness” is that an attacker is potentially able to communicate with more devices than before. If he breaks the home/building/local network protection, he is able to manipulate the lighting system, lock doors, control HVAC etc.;
- Constrained devices, the feature of many IoT devices resulting from a tendency to reduce the cost of their production. As a consequence, IoT devices have limited resources, memory space, low bandwidth etc. and these considerably reduce the possibility to implement conventional security techniques;
- Large scale, since currently there are more computers and other IoT devices connected to the Internet than number of humans on the globe and management of so large number of smart devices is very demanding task as well as inevitably raise the security risks;
- Privacy, IoT devices by their nature operate in a distributed structure, allowing communication in various wired and wireless technologies. This approach allows interaction everywhere, data communication with many other BACS network nodes, edge modules, in order to provide various services with different scope and resource use. The openness and flexibility of this structure generates additional privacy risks.
-
For fog computing
- Encryption techniques;
- Decoy technique for authentication of data;
- Intrusion detection system for denial-of-service attack (DoS attack) [81] as well as port scanning attacks;
- Authentication schemes, where fog computing network enables users to access the fog services from the fog infrastructure if they are well authenticated from the system;
- Blockchain strategy, it can prevent various malicious attacks in fog network including man-in-the-middle attack, DoS attack and data tampering.
-
For edge computing
4. New Ideas, Concepts and Trends
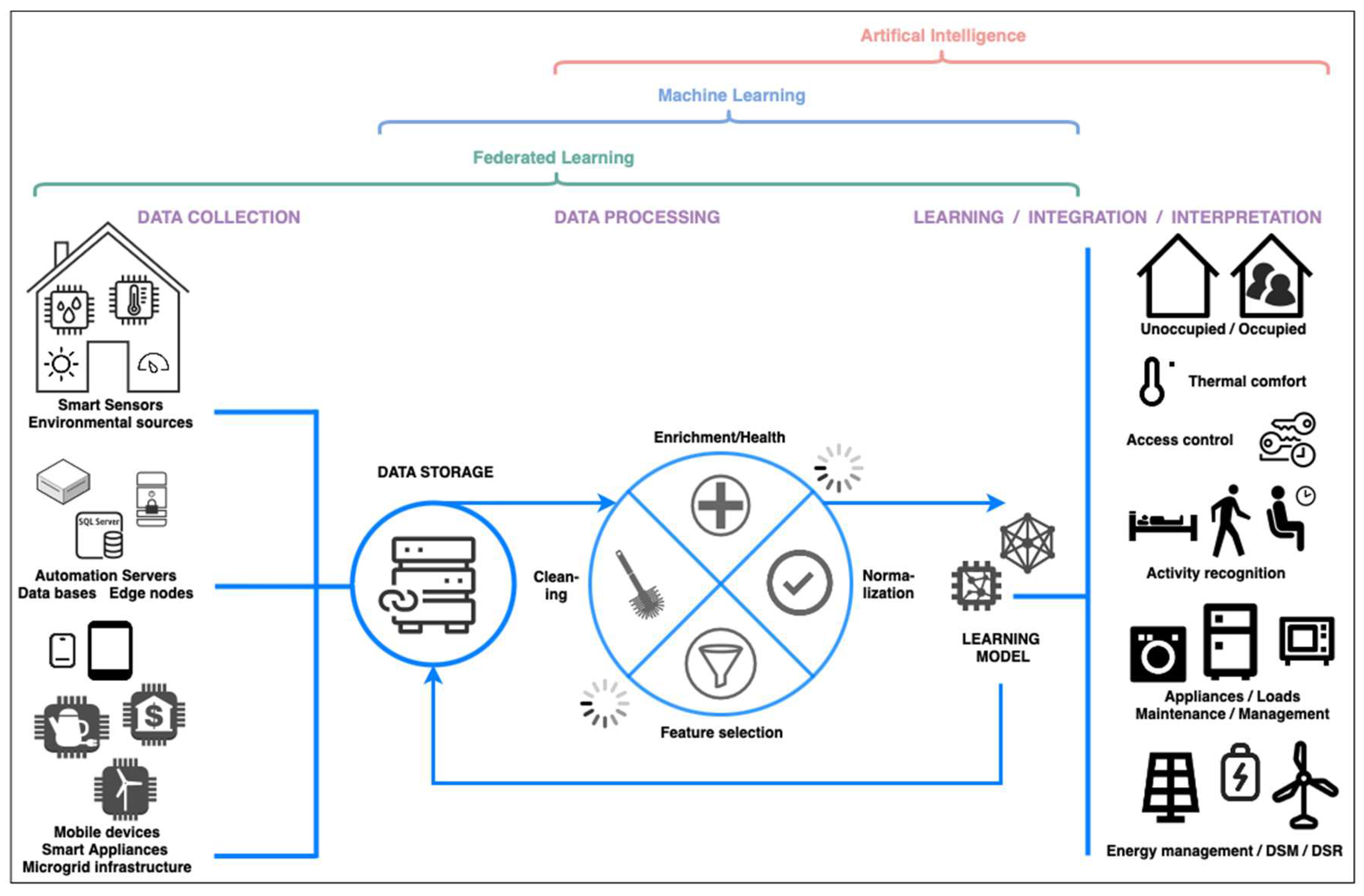
4.1. Machine Learning and Artifical Inteligence
-
Occupant-centric solutions
- Occupancy detection, prediction and estimation providing essential information for advanced control of several subsystems like HVAC;
- Activity recognition to provide better control scenarios, tailored to increased or limited user activity, e.g. in different zones of the building;
- User preferences and behavior to provide well-tailored thermal and lighting comfort, considering individual or group user preferences, as well as operating scenarios for home devices and building infrastructure tailored to the most common, recurring user behaviors;
- Authentication schemes, where fog computing network enables users to access the fog services from the fog infrastructure if they are well authenticated in the system;
- Blockchain strategy, it can prevent various malicious attacks in fog network including man-in-the-middle attack, DoS attack and data tampering.
-
Energy/device-centric solutions
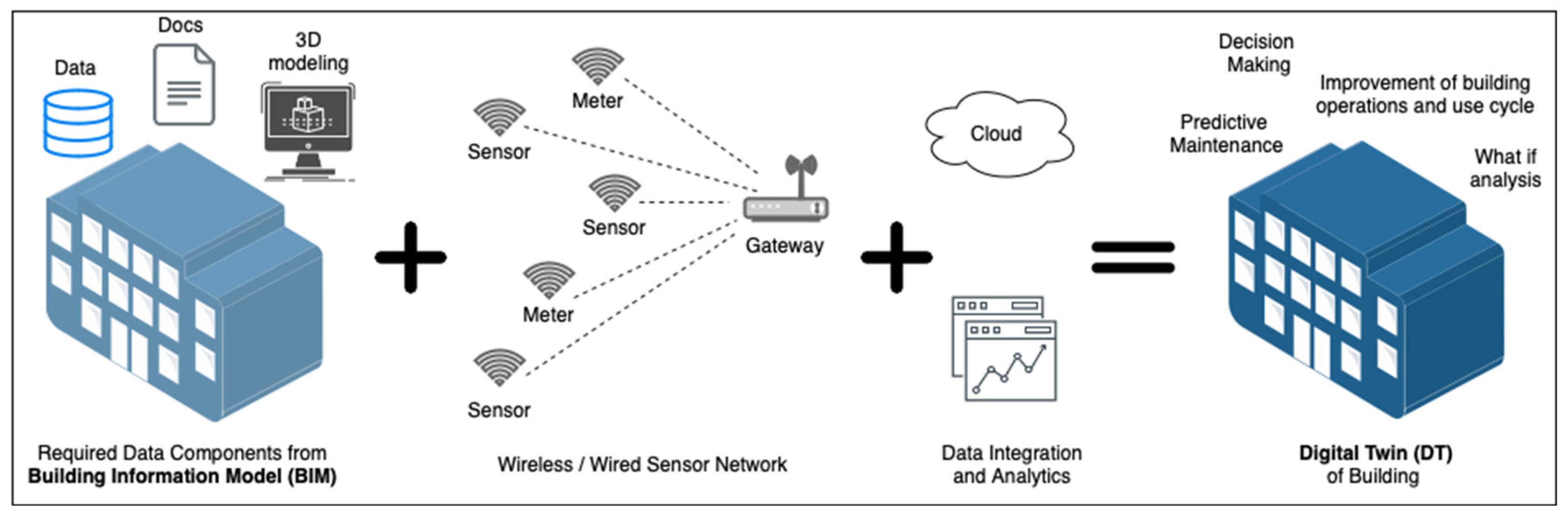
4.2. Tactile Internet, Digital Twins with Distributed Automation Newtowrks
- Collection of data and information regarding the geometry, materials, and equipment characteristics of the specific building of interest. This information is necessary for modeling the building;
- Collection of live measurements from sensors and electricity meters installed in the building to monitor its real-time operating conditions. Additionally, live weather data could be collected as well. These live data are directly incorporated as inputs into simulation tools to replicate the building operating conditions in real time;
- Simulation tools with model-based modeling are incorporated to simulate the building control and monitoring systems. Intelligent algorithms can also be used to calibrate the building parameters in order to achieve better comfort and/or improve energy efficiency ;
- Development of a software platform to integrate the three previous phases. That platform is responsible for the proper data exchange and the successful real-time execution of the simulation tools as well as to integrate monitoring and control applications and to investigate different what-if scenarios.
4.3. IoT Technology and Maturity Assessment
- Mid IoT Level, automatic control at the building level (centralized automation), firstly emerging of DALI controls for lighting as well as field-level sensors for some control functions;
- High IoT Level, automatic control at the building level (distributed automation), with networked sensors and modules-nodes to control most systems' functions with the performance analysis;
- Fully IoT Level, automatic control across all buildings/site levels (distributed networked automation) with networked sensors, all modules-nodes to control most systems' functions with the performance analysis also perform a predictive decision making.
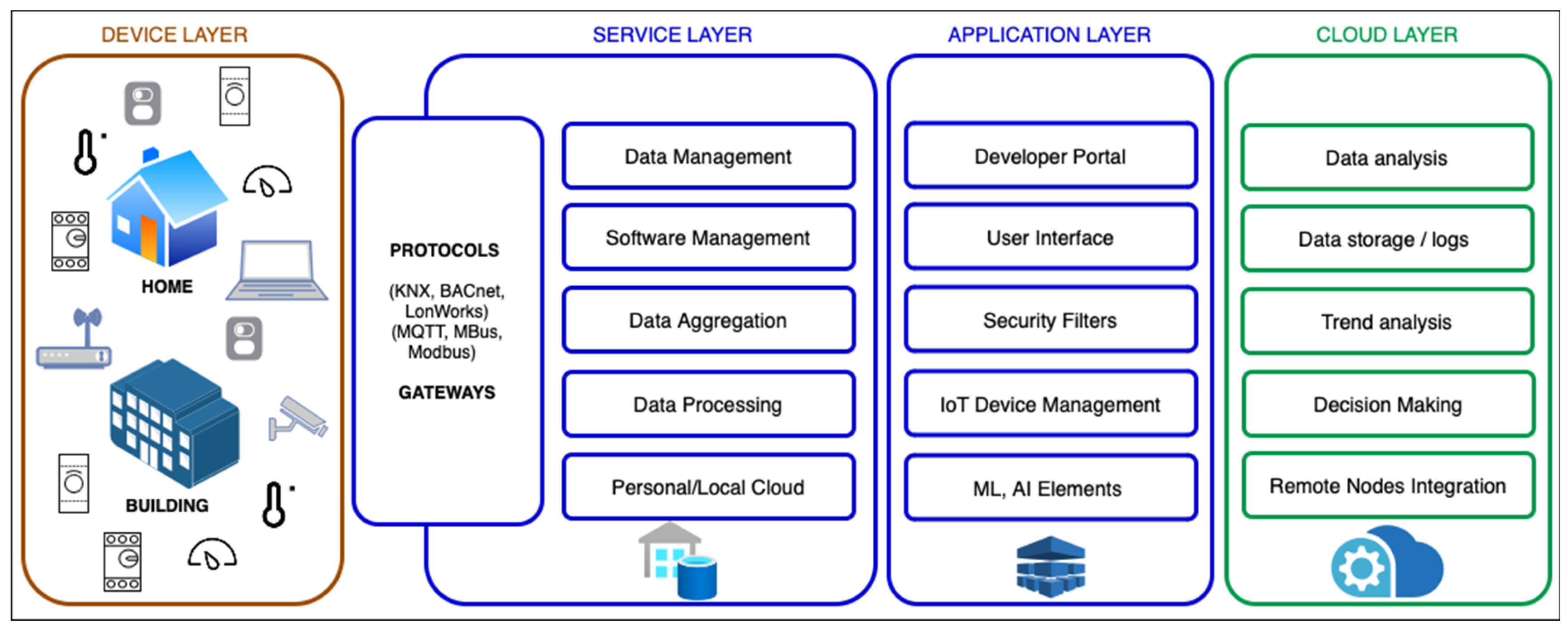
5. Generic IoT Framework – Concept, Development and Discussion
5.1. Manadatory Elements of the Framework
5.2. Optional Elements of the Framework
5.2.1. Smart Home Applications
5.2.2. Smart Building Applications
5.3. SWOT Analysis and Discussion – Main Challenges, Opportunities, Pros and Cons
- Comprehensive Integration: the incorporation of mandatory elements from the framework ensures a solid foundation for seamless device communication, data processing, and security;
- Flexibility and Scalability: the inclusion of optional elements allows for customization based on specific applications, catering to the unique needs of both smart homes and buildings;
- Advanced Capabilities: optional elements such as fog computing, machine learning, and AI enhance the framework's capabilities, providing predictive analytics, anomaly detection, and efficient resource management.
- Complex Implementation: the inclusion of various optional elements may introduce complexity in the implementation phase, requiring careful planning and expertise;
- Resource Intensiveness: certain advanced features, such as ML and AI, may demand substantial computing resources, potentially affecting system performance;
- Potential Security Risks: the complexity of the framework may introduce vulnerabilities, necessitating robust cybersecurity measures to mitigate potential risks.
- Market Growth: the rising demand for smart home and building solutions as well as IoT and TIoT presents a significant market opportunity, with the framework well-positioned to capitalize on this trend;
- Technological Advancements: ongoing advancements in IoT technologies, including edge, fog computing as well as ML and AI, offer opportunities for continuous improvement and innovation within the framework;
- Regulatory Support: compliance with emerging data privacy and energy efficiency regulations can enhance the framework's credibility and market acceptance.
- Cybersecurity Concerns: as IoT systems become more interconnected, the framework faces potential threats from cyberattacks, necessitating robust security measures.
- Integration Challenges: compatibility issues with existing systems in buildings or homes may pose challenges during implementation, requiring seamless integration strategies.
- Market, Research and Technical Competition: Rapid technological advancements may lead to increased competition, requiring continuous updates to maintain the framework's competitiveness.
6. Conclusions
Funding
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| BaaS | Building as a Service |
| BACS | Building Automation and Control Systems |
| BIM | Building Information Modeling |
| BMS | Building Management Systems |
| DoS | Denial-of-Service |
| DSM | Demand Side Management |
| DSR | Demand Side Response |
| DT | Digital Twin |
| EPBD | Energy Performance of Buildings Directive |
| FL | Federated Learning |
| FM | Facility Management |
| FoE | Fog of Everything |
| HVAC | Heating, Ventilation, Air Conditioning |
| ICT- | Information and Communications Technology |
| IoE | Internet of Everything |
| IoT | Internet of Things |
| IOTA | Internet of Things Application |
| ML | Machine Learning |
| OPC | OLE for Process Control (OLE - Object Linking and Embedding) |
| P2P | Peer-to-Peer |
| PLC- | Programmable Logic Controller |
| RES- | Renewable Energy Sources |
| SoC- | System-on-a-Chip |
| SR- | Smart Readiness Indicator |
| TIoT | Tactile Internet of Things |
| WoT | Web of Things |
References
- Benotmane, M.; Elhari, K.; Kabbaj, A. A Review & Analysis of Current IoT Maturity & Readiness Models and Novel Proposal. Sci Afr 2023, 21, e01748. [CrossRef]
- Khattak, S.B.A.; Nasralla, M.M.; Farman, H.; Choudhury, N. Performance Evaluation of an IEEE 802.15.4-Based Thread Network for Efficient Internet of Things Communications in Smart Cities. Applied Sciences 2023, 13, 7745. [CrossRef]
- Ferrández-Pastor, F.-J.; Mora, H.; Jimeno-Morenilla, A.; Volckaert, B. Deployment of IoT Edge and Fog Computing Technologies to Develop Smart Building Services. Sustainability 2018, 10, 3832. [CrossRef]
- Ali, O.; Ishak, M.K. Bringing Intelligence to IoT Edge: Machine Learning Based Smart City Image Classification Using Microsoft Azure IoT and Custom Vision. J Phys Conf Ser 2020, 1529, 042076. [CrossRef]
- Taghizad-Tavana, K.; Ghanbari-Ghalehjoughi, M.; Razzaghi-Asl, N.; Nojavan, S.; Alizadeh, A. An Overview of the Architecture of Home Energy Management System as Microgrids, Automation Systems, Communication Protocols, Security, and Cyber Challenges. Sustainability 2022, 14, 15938. [CrossRef]
- Sharma, H.; Haque, A.; Blaabjerg, F. Machine Learning in Wireless Sensor Networks for Smart Cities: A Survey. Electronics (Basel) 2021, 10, 1012. [CrossRef]
- Wang, B.; Li, M.; Jin, X.; Guo, C. A Reliable IoT Edge Computing Trust Management Mechanism for Smart Cities. IEEE Access 2020, 8, 46373–46399. [CrossRef]
- International Organization for Standardization ISO/IEC 14543-3-10:2020 Information Technology Home Electronic Systems (HES) Architecture - KNX; Geneva, Switzerland , 2020;
- International Organization for Standardization ISO/IEC 14908-1:2012 Information Technology Control Network Protocol - LonWorks; Geneva, Switzerland , 2012;
- International Organization for Standardization ISO 16484-6:2020 Building Automation and Control Systems (BACS) - BACnet; Geneva, Switzerland , 2020;
- Bovet, G.; Hennebert, J. Will Web Technologies Impact on Building Automation Systems Architecture? Procedia Comput Sci 2014, 32, 985–990. [CrossRef]
- Ożadowicz, A. A New Concept of Active Demand Side Management for Energy Efficient Prosumer Microgrids with Smart Building Technologies. Energies (Basel) 2017, 10, 1771. [CrossRef]
- Schraven, M.H.; Droste, K.; Guarnieri Calò Carducci, C.G.C.; Müller, D.; Monti, A. Open-Source Internet of Things Gateways for Building Automation Applications. Journal of Sensor and Actuator Networks 2022, 11, 74. [CrossRef]
- Froiz-Míguez, I.; Fernández-Caramés, T.; Fraga-Lamas, P.; Castedo, L. Design, Implementation and Practical Evaluation of an IoT Home Automation System for Fog Computing Applications Based on MQTT and ZigBee-WiFi Sensor Nodes. Sensors 2018, 18, 2660. [CrossRef]
- Petkov, N.; Naumov, A. Overview of Industrial Communication in Process Automation. In Proceedings of the 2022 International Conference Automatics and Informatics (ICAI); IEEE, October 6 2022; pp. 229–234.
- Secgin, S. Seven Layers of ISO/OSI. In Evolution of Wireless Communication Ecosystems; Wiley, 2023; pp. 41–50.
- Vernadat, F.B. Interoperability and Standards for Automation. In Springer Handbook of Automation; Nof, S.Y., Ed.; Springer International Publishing: Cham, 2023; pp. 729–752.
- Kato, T.; Ishikawa, N.; Yoshida, N. Distributed Autonomous Control of Home Appliances Based on Event Driven Architecture. In Proceedings of the 2017 IEEE 6th Global Conference on Consumer Electronics (GCCE); IEEE, October 2017; pp. 1–2.
- Graveto, V.; Cruz, T.; Simöes, P. Security of Building Automation and Control Systems: Survey and Future Research Directions. Comput Secur 2022, 112, 102527. [CrossRef]
- Martirano, L.; Mitolo, M. Building Automation and Control Systems (BACS): A Review. In Proceedings of the 2020 IEEE International Conference on Environment and Electrical Engineering and 2020 IEEE Industrial and Commercial Power Systems Europe (EEEIC / I&CPS Europe); IEEE, June 2020; pp. 1–8.
- Ożadowicz, A.; Grela, J. An Event-Driven Building Energy Management System Enabling Active Demand Side Management. In Proceedings of the 2016 Second International Conference on Event-based Control, Communication, and Signal Processing (EBCCSP); IEEE, June 2016; pp. 1–8.
- Pirbhulal, S.; Zhang, H.; E Alahi, M.; Ghayvat, H.; Mukhopadhyay, S.; Zhang, Y.-T.; Wu, W. A Novel Secure IoT-Based Smart Home Automation System Using a Wireless Sensor Network. Sensors 2016, 17, 69. [CrossRef]
- Ożadowicz, A. Technical, Qualitative and Energy Analysis of Wireless Control Modules for Distributed Smart Home Systems. Future Internet 2023, 15, 316. [CrossRef]
- Prakosa, S.; Nugraha, A.; Atiq, M.’ Miniature SmartHome Dengan Sonoff. Jurnal Riset Rumpun Ilmu Teknik (JURRITEK) 2023, 2.
- Yang, H.; Kim, B.; Lee, J.; Ahn, Y.; Lee, C. Advanced Wireless Sensor Networks for Sustainable Buildings Using Building Ducts. Sustainability 2018, 10, 2628. [CrossRef]
- Anush, K.S.; Sasikala, S.; Arun, K.S.; Arunan, R.; Asfaq, M.A. Enhanced and Secured Smart Home Using Z-Wave Technology. In Proceedings of the 2nd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation, ICAECA 2023; Institute of Electrical and Electronics Engineers Inc., 2023.
- Singhai, R.; Sushil, R. An Investigation of Various Security and Privacy Issues in Internet of Things. Mater Today Proc 2023, 80, 3393–3397. [CrossRef]
- Nasir, M.; Muhammad, K.; Ullah, A.; Ahmad, J.; Wook Baik, S.; Sajjad, M. Enabling Automation and Edge Intelligence over Resource Constraint IoT Devices for Smart Home. Neurocomputing 2022, 491, 494–506. [CrossRef]
- Lăcătușu, F.; Ionita, A.D.; Lăcătușu, M.; Olteanu, A. Performance Evaluation of Information Gathering from Edge Devices in a Complex of Smart Buildings. Sensors 2022, 22, 1002. [CrossRef]
- Babar, M.; Grela, J.; Ożadowicz, A.; Nguyen, P.; Hanzelka, Z.; Kamphuis, I. Energy Flexometer: Transactive Energy-Based Internet of Things Technology. Energies (Basel) 2018, 11, 568. [CrossRef]
- Faqiry, M.; Edmonds, L.; Zhang, H.; Khodaei, A.; Wu, H. Transactive-Market-Based Operation of Distributed Electrical Energy Storage with Grid Constraints. Energies (Basel) 2017, 10, 1891. [CrossRef]
- Pratt, A.; Krishnamurthy, D.; Ruth, M.; Wu, H.; Lunacek, M.; Vaynshenk, P. Transactive Home Energy Management Systems: The Impact of Their Proliferation on the Electric Grid. IEEE Electrification Magazine 2016, 4, 8–14. [CrossRef]
- Ożadowicz, A. A Hybrid Approach in Design of Building Energy Management System with Smart Readiness Indicator and Building as a Service Concept. Energies (Basel) 2022, 15, 1432. [CrossRef]
- Laroui, M.; Nour, B.; Moungla, H.; Cherif, M.A.; Afifi, H.; Guizani, M. Edge and Fog Computing for IoT: A Survey on Current Research Activities & Future Directions. Comput Commun 2021, 180, 210–231. [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All One Needs to Know about Fog Computing and Related Edge Computing Paradigms: A Complete Survey. Journal of Systems Architecture 2019, 98, 289–330. [CrossRef]
- Huang, Z.; Lin, K.-J.; Tsai, B.-L.; Yan, S.; Shih, C.-S. Building Edge Intelligence for Online Activity Recognition in Service-Oriented IoT Systems. Future Generation Computer Systems 2018, 87, 557–567. [CrossRef]
- Filho, G.P.R.; Meneguette, R.I.; Maia, G.; Pessin, G.; Gonçalves, V.P.; Weigang, L.; Ueyama, J.; Villas, L.A. A Fog-Enabled Smart Home Solution for Decision-Making Using Smart Objects. Future Generation Computer Systems 2020, 103, 18–27. [CrossRef]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog Computing: A Taxonomy, Survey and Future Directions. In Internet of Everything: Algorithms, Methodologies, Technologies and Perspectives; Di Martino Beniamino and Li, K.-C. and Y.L.T. and E.A., Ed.; Springer Singapore: Singapore, 2018; pp. 103–130.
- Alnajar, O.; Barnawi, A. Tactile Internet of Federated Things: Toward Fine-Grained Design of FL-Based Architecture to Meet TIoT Demands. Computer Networks 2023, 231, 109712. [CrossRef]
- Sun, H.; Yu, H.; Fan, G.; Chen, L. Energy and Time Efficient Task Offloading and Resource Allocation on the Generic IoT-Fog-Cloud Architecture. Peer Peer Netw Appl 2020, 13, 548–563. [CrossRef]
- Li, W.; Wang, S. A Fully Distributed Optimal Control Approach for Multi-Zone Dedicated Outdoor Air Systems to Be Implemented in IoT-Enabled Building Automation Networks. Appl Energy 2022, 308, 118408. [CrossRef]
- Ge, X.; Yang, F.; Han, Q. Distributed Networked Control Systems: A Brief Overview. Inf Sci (N Y) 2017, 380, 117–131. [CrossRef]
- Islam, R.; Rahman, Md.W.; Rubaiat, R.; Hasan, Md.M.; Reza, Md.M.; Rahman, M.M. LoRa and Server-Based Home Automation Using the Internet of Things (IoT). Journal of King Saud University - Computer and Information Sciences 2022, 34, 3703–3712. [CrossRef]
- Bhatt, J.; Verma, H.K. Design and Development of Wired Building Automation Systems. Energy Build 2015, 103, 396–413. [CrossRef]
- Merz, H.; Hansemann, T.; Hübner, C. Building Automation; Signals and Communication Technology; Springer International Publishing: Cham, 2018; ISBN 978-3-319-73222-0.
- Dietrich, D.; Bruckner, D.; Zucker, G.; Palensky, P. Communication and Computation in Buildings: A Short Introduction and Overview. IEEE Transactions on Industrial Electronics 2010, 57, 3577–3584. [CrossRef]
- Wang, S. Intelligent Buildings and Building Automation; Routledge, 2009; ISBN 9781134025107.
- Domingues, P.; Carreira, P.; Vieira, R.; Kastner, W. Building Automation Systems: Concepts and Technology Review. Comput Stand Interfaces 2016, 45, 1–12. [CrossRef]
- Lobaccaro, G.; Carlucci, S.; Löfström, E. A Review of Systems and Technologies for Smart Homes and Smart Grids. Energies (Basel) 2016, 9, 1–33. [CrossRef]
- NORDIC Semiconductor Nordic Semiconductor Delivers Industry-Wide Support for KNX IoT Protocol Following Membership of KNX Association Available online: https://www.nordicsemi.com/Nordic-news/2023/06/nordic-delivers-industry-wide-support-for-knx-iot-protocol-following-membership-of-knx-association (accessed on 8 December 2023).
- HAGER Connecting the World of Digital Objects and Services with KNX Available online: https://assets1.sc.hager.com/turkey/files/IoT-Controller.pdf (accessed on 8 December 2023).
- EXOR Powerful IoT-Ready Interfaces with KNX Interface Available online: https://www.exorint.com/corporate/press-release/knx-2020 (accessed on 8 December 2023).
- Kortuem, G.; Kawsar, F.; Sundramoorthy, V.; Fitton, D. Smart Objects as Building Blocks for the Internet of Things. IEEE Internet Comput 2010, 14, 44–51. [CrossRef]
- Bin, S.; Guiqing, Z.; Shaolin, W.; Dong, W. The Development of Management System for Building Equipment Internet of Things. In Proceedings of the 2011 IEEE 3rd International Conference on Communication Software and Networks; IEEE, May 2011; pp. 423–427.
- Jarvinen, H.; Litvinov, A.; Vuorimaa, P. Integration Platform for Home and Building Automation Systems. In Proceedings of the 2011 IEEE Consumer Communications and Networking Conference (CCNC); IEEE, January 2011; pp. 292–296.
- Jung, M.; Reinisch, C.; Kastner, W. Integrating Building Automation Systems and IPv6 in the Internet of Things. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing; IEEE, July 2012; pp. 683–688.
- Lilis, G.; Conus, G.; Asadi, N.; Kayal, M. Towards the next Generation of Intelligent Building: An Assessment Study of Current Automation and Future IoT Based Systems with a Proposal for Transitional Design. Sustain Cities Soc 2017, 28, 473–481. [CrossRef]
- Lilis, G.; Conus, G.; Kayal, M. A Distributed, Event-Driven Building Management Platform on Web Technologies. In Proceedings of the 2015 International Conference on Event-based Control, Communication, and Signal Processing (EBCCSP); IEEE, June 2015; pp. 1–8.
- Conus, G.; Lilis, G.; Zanjani, N.A.; Kayal, M. Toward Event-Driven Mechanism for Load Profile Generation. In Proceedings of the 2017 22nd IEEE International Conference on Emerging Technologies and Factory Automation (ETFA); IEEE, September 2017; pp. 1–6.
- Mansour, M.; Gamal, A.; Ahmed, A.I.; Said, L.A.; Elbaz, A.; Herencsar, N.; Soltan, A. Internet of Things: A Comprehensive Overview on Protocols, Architectures, Technologies, Simulation Tools, and Future Directions. Energies (Basel) 2023, 16, 3465. [CrossRef]
- Ramprasad, B.; McArthur, J.; Fokaefs, M.; Barna, C.; Damm, M.; Litoiu, M. Leveraging Existing Sensor Networks as IoT Devices for Smart Buildings. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT); IEEE, February 2018; pp. 452–457.
- BaaS Consortium Partners Building as a Service. Final Report of the Project Funded by the European Community in the 7 Th Framework Programme ICT for Sustainable Growth; 2016;
- Baccarelli, E.; Naranjo, P.G.V.; Scarpiniti, M.; Shojafar, M.; Abawajy, J.H. Fog of Everything: Energy-Efficient Networked Computing Architectures, Research Challenges, and a Case Study. IEEE Access 2017, 5, 9882–9910. [CrossRef]
- Wildenauer, A.; Mbabu, A.; Underwood, J.; Basl, J. Building-as-a-Service: Theoretical Foundations and Conceptual Framework. Buildings 2022, 12, 1594. [CrossRef]
- Wildenauer, A.; Basl, J. Building-as-a-Service: The Opportunities of Service-Dominant Logic for Construction. Marketing Science & Inspirations 2022, 17, 41–53. [CrossRef]
- 2018; 66. European Parliament Directive (EU) 2018/844 of the European Parliament and the Council on the Energy Performance of Buildings; EU, 2018;
- 2020; 67. Verbeke Stijin; Aerts Dorien; Reynders Glenn; Ma Yixiao; Waide Paul FINAL REPORT ON THE TECHNICAL SUPPORT TO THE DEVELOPMENT OF A SMART READINESS INDICATOR FOR BUILDINGS; 2020;
- Ramezani, B.; Silva, Manuel.G. da; Simões, N. Application of Smart Readiness Indicator for Mediterranean Buildings in Retrofitting Actions. Energy Build 2021, 249, 111173. [CrossRef]
- Mancini, F.; Lo Basso, G.; de Santoli, L. Energy Use in Residential Buildings: Impact of Building Automation Control Systems on Energy Performance and Flexibility. Energies (Basel) 2019, 12, 2896. [CrossRef]
- Fokaides, P.A.; Panteli, C.; Panayidou, A. How Are the Smart Readiness Indicators Expected to Affect the Energy Performance of Buildings: First Evidence and Perspectives. Sustainability 2020, 12, 9496. [CrossRef]
- Vasilopoulos, V.G.; Dimara, A.; Krinidis, S.; Almpanis, P.; Margaritis, N.; Nikolopoulos, N.; Ioannidis, D.; Tzovaras, D. An IoT M2M Architecture for BMS Using Multiple Connectivity Technologies: A Practical Approach. In Proceedings of the 2021 6th International Conference on Smart and Sustainable Technologies (SpliTech); IEEE, September 8 2021; pp. 1–6.
- Fetahi, E.; Ajdari, J.; Zenuni, X.; Hamiti, M. A Cloud Centric Smart City Construction with an IoT Enabled Traffic Prediction Mechanism. In Proceedings of the 2022 11th Mediterranean Conference on Embedded Computing (MECO); IEEE, June 7 2022; pp. 1–6.
- Chen, Y.-C.; Chang, Y.-C.; Chen, C.-H.; Lin, Y.-S.; Chen, J.-L.; Chang, Y.-Y. Cloud-Fog Computing for Information-Centric Internet-of-Things Applications. In Proceedings of the 2017 International Conference on Applied System Innovation (ICASI); IEEE, May 2017; pp. 637–640.
- Sahil; Sood, S.K. Fog-Cloud Centric IoT-Based Cyber Physical Framework for Panic Oriented Disaster Evacuation in Smart Cities. Earth Sci Inform 2022, 15, 1449–1470. [CrossRef]
- NVIDIA Developer Jetson Nano Developer Kit Available online: https://developer.nvidia.com/embedded/jetson-nano-developer-kit (accessed on 14 December 2023).
- Yar, H.; Imran, A.S.; Khan, Z.A.; Sajjad, M.; Kastrati, Z. Towards Smart Home Automation Using IoT-Enabled Edge-Computing Paradigm. Sensors 2021, 21, 4932. [CrossRef]
- Alshaikhli, M.; Elfouly, T.; Elharrouss, O.; Mohamed, A.; Ottakath, N. Evolution of Internet of Things From Blockchain to IOTA: A Survey. IEEE Access 2022, 10, 844–866. [CrossRef]
- Singhai, R.; Sushil, R. An Investigation of Various Security and Privacy Issues in Internet of Things. Mater Today Proc 2023, 80, 3393–3397. [CrossRef]
- Parikh, S.; Dave, D.; Patel, R.; Doshi, N. Security and Privacy Issues in Cloud, Fog and Edge Computing. Procedia Comput Sci 2019, 160, 734–739. [CrossRef]
- Alwakeel, A.M. An Overview of Fog Computing and Edge Computing Security and Privacy Issues. Sensors 2021, 21, 8226. [CrossRef]
- Ullah, A.; Ullah, S.I.; Salam, A. Internal DoS Attack Detection and Prevention in Fog Computing. In Proceedings of the 2021 International Conference on Information Technology (ICIT); IEEE, July 14 2021; pp. 763–768.
- Huso, I.; Piro, G.; Boggia, G. Distributed and Privacy-Preserving Data Dissemination at the Network Edge via Attribute-Based Searchable Encryption. In Proceedings of the 2022 20th Mediterranean Communication and Computer Networking Conference (MedComNet); IEEE, June 1 2022; pp. 122–130.
- Xu, R.; Palanisamy, B.; Joshi, J. QueryGuard: Privacy-Preserving Latency-Aware Query Optimization for Edge Computing. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE); IEEE, August 2018; pp. 1097–1106.
- Alam, T. Blockchain-Based Internet of Things: Review, Current Trends, Applications, and Future Challenges. Computers 2022, 12, 6. [CrossRef]
- Moniruzzaman, Md.; Khezr, S.; Yassine, A.; Benlamri, R. Blockchain for Smart Homes: Review of Current Trends and Research Challenges. Computers & Electrical Engineering 2020, 83, 106585. [CrossRef]
- Taneja, S.; Rana, I.; Tyagi, S. Blockchain for Iot Security and Privacy: Smart Home-A Review. International Journal of Advances in Engineering and Management (IJAEM) 2023, 5, 1293.
- Afzal, M.; Huang, Q.; Amin, W.; Umer, K.; Raza, A.; Naeem, M. Blockchain Enabled Distributed Demand Side Management in Community Energy System With Smart Homes. IEEE Access 2020, 8, 37428–37439. [CrossRef]
- Tyagi, A.K.; Dananjayan, S.; Agarwal, D.; Thariq Ahmed, H.F. Blockchain—Internet of Things Applications: Opportunities and Challenges for Industry 4.0 and Society 5.0. Sensors 2023, 23, 947. [CrossRef]
- Arif, S.; Khan, M.A.; Rehman, S.U.; Kabir, M.A.; Imran, M. Investigating Smart Home Security: Is Blockchain the Answer? IEEE Access 2020, 8, 117802–117816. [CrossRef]
- Abed, S.; Jaffal, R.; Mohd, B.J. A Review on Blockchain and IoT Integration from Energy, Security and Hardware Perspectives. Wirel Pers Commun 2023, 129, 2079–2122. [CrossRef]
- Djenouri, D.; Laidi, R.; Djenouri, Y.; Balasingham, I. Machine Learning for Smart Building Applications. ACM Comput Surv 2020, 52, 1–36. [CrossRef]
- Shayeghi, H.; Shahryari, E.; Moradzadeh, M.; Siano, P. A Survey on Microgrid Energy Management Considering Flexible Energy Sources. Energies (Basel) 2019, 12, 2156. [CrossRef]
- Hou, P.; Yang, G.; Hu, J.; Douglass, P.J.; Xue, Y. A Distributed Transactive Energy Mechanism for Integrating PV and Storage Prosumers in Market Operation. Engineering 2022, 12, 171–182. [CrossRef]
- Pipattanasomporn, M.; Kuzlu, M.; Rahman, S.; Teklu, Y. Load Profiles of Selected Major Household Appliances and Their Demand Response Opportunities. IEEE Trans Smart Grid 2014, 5, 742–750. [CrossRef]
- Bouchabou, D.; Nguyen, S.M.; Lohr, C.; LeDuc, B.; Kanellos, I. A Survey of Human Activity Recognition in Smart Homes Based on IoT Sensors Algorithms: Taxonomies, Challenges, and Opportunities with Deep Learning. Sensors 2021, 21, 6037. [CrossRef]
- Suman, S.; Etemad, A.; Rivest, F. Potential Impacts of Smart Homes on Human Behavior: A Reinforcement Learning Approach. IEEE Transactions on Artificial Intelligence 2022, 3, 567–580. [CrossRef]
- Machorro-Cano, I.; Alor-Hernández, G.; Paredes-Valverde, M.A.; Rodríguez-Mazahua, L.; Sánchez-Cervantes, J.L.; Olmedo-Aguirre, J.O. HEMS-IoT: A Big Data and Machine Learning-Based Smart Home System for Energy Saving. Energies (Basel) 2020, 13, 1097. [CrossRef]
- Shah, S.; Iqbal, M.; Aziz, Z.; Rana, T.; Khalid, A.; Cheah, Y.-N.; Arif, M. The Role of Machine Learning and the Internet of Things in Smart Buildings for Energy Efficiency. Applied Sciences 2022, 12, 7882. [CrossRef]
- Kawa, B.; Borkowski, P. Integration of Machine Learning Solutions in the Building Automation System. Energies (Basel) 2023, 16, 4504. [CrossRef]
- Vassiliades, C.; Agathokleous, R.; Barone, G.; Forzano, C.; Giuzio, G.F.; Palombo, A.; Buonomano, A.; Kalogirou, S. Building Integration of Active Solar Energy Systems: A Review of Geometrical and Architectural Characteristics. Renewable and Sustainable Energy Reviews 2022, 164, 112482. [CrossRef]
- Fambri, G.; Badami, M.; Tsagkrasoulis, D.; Katsiki, V.; Giannakis, G.; Papanikolaou, A. Demand Flexibility Enabled by Virtual Energy Storage to Improve Renewable Energy Penetration. Energies (Basel) 2020, 13, 5128. [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Gupta, B. Ensemble Machine Learning Approach for Classification of IoT Devices in Smart Home. International Journal of Machine Learning and Cybernetics 2021, 12, 3179–3202. [CrossRef]
- Alnajar, O.; Barnawi, A. Tactile Internet of Federated Things: Toward Fine-Grained Design of FL-Based Architecture to Meet TIoT Demands. Computer Networks 2023, 231.
- Zhang, C.; Xie, Y.; Bai, H.; Yu, B.; Li, W.; Gao, Y. A Survey on Federated Learning. Knowl Based Syst 2021, 216, 106775. [CrossRef]
- Mammen, P.M. Federated Learning: Opportunities and Challenges. 2021.
- Zubaydi, H.D.; Varga, P.; Molnár, S. Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review. Sensors 2023, 23.
- Yazdinejad, A.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G.; Karimipour, H. Secure Intelligent Fuzzy Blockchain Framework: Effective Threat Detection in IoT Networks. Comput Ind 2023, 144, 103801. [CrossRef]
- Khan, M.A.; Abbas, S.; Rehman, A.; Saeed, Y.; Zeb, A.; Uddin, M.I.; Nasser, N.; Ali, A. A Machine Learning Approach for Blockchain-Based Smart Home Networks Security. IEEE Netw 2021, 35, 223–229. [CrossRef]
- Panchalingam, R.; Chan, K.C. A State-of-the-Art Review on Artificial Intelligence for Smart Buildings. Intelligent Buildings International 2021, 13, 203–226. [CrossRef]
- Rodriguez-Garcia, P.; Li, Y.; Lopez-Lopez, D.; Juan, A.A. Strategic Decision Making in Smart Home Ecosystems: A Review on the Use of Artificial Intelligence and Internet of Things. Internet of Things 2023, 22, 100772. [CrossRef]
- Genkin, M.; McArthur, J.J. B-SMART: A Reference Architecture for Artificially Intelligent Autonomic Smart Buildings. Eng Appl Artif Intell 2023, 121, 106063. [CrossRef]
- Hou, Z.; She, C.; Li, Y.; Niyato, D.; Dohler, M.; Vucetic, B. Intelligent Communications for Tactile Internet in 6G: Requirements, Technologies, and Challenges. IEEE Communications Magazine 2021, 59, 82–88. [CrossRef]
- Fanibhare, V.; Sarkar, N.I.; Al-Anbuky, A. A Survey of the Tactile Internet: Design Issues and Challenges, Applications, and Future Directions. Electronics (Basel) 2021, 10, 2171. [CrossRef]
- N., A.; Rai, K.H.J.; M.K., H.; Ramesh, R.; Hegde, R.; Kumar, S. Tactile Internet: Next Generation IoT. In Proceedings of the 2019 Third International Conference on Inventive Systems and Control (ICISC); IEEE, January 2019; pp. 22–26.
- Promwongsa, N.; Ebrahimzadeh, A.; Naboulsi, D.; Kianpisheh, S.; Belqasmi, F.; Glitho, R.; Crespi, N.; Alfandi, O. A Comprehensive Survey of the Tactile Internet: State-of-the-Art and Research Directions. IEEE Communications Surveys & Tutorials 2021, 23, 472–523. [CrossRef]
- Eneyew, D.D.; Capretz, M.A.M.; Bitsuamlak, G.T. Toward Smart-Building Digital Twins: BIM and IoT Data Integration. IEEE Access 2022, 10, 130487–130506. [CrossRef]
- Coupry, C.; Noblecourt, S.; Richard, P.; Baudry, D.; Bigaud, D. BIM-Based Digital Twin and XR Devices to Improve Maintenance Procedures in Smart Buildings: A Literature Review. Applied Sciences 2021, 11, 6810. [CrossRef]
- Hadjidemetriou, L.; Stylianidis, N.; Englezos, D.; Papadopoulos, P.; Eliades, D.; Timotheou, S.; Polycarpou, M.M.; Panayiotou, C. A Digital Twin Architecture for Real-Time and Offline High Granularity Analysis in Smart Buildings. Sustain Cities Soc 2023, 98, 104795. [CrossRef]
- Khajavi, S.H.; Motlagh, N.H.; Jaribion, A.; Werner, L.C.; Holmstrom, J. Digital Twin: Vision, Benefits, Boundaries, and Creation for Buildings. IEEE Access 2019, 7, 147406–147419. [CrossRef]
- Baghalzadeh Shishehgarkhaneh, M.; Keivani, A.; Moehler, R.C.; Jelodari, N.; Roshdi Laleh, S. Internet of Things (IoT), Building Information Modeling (BIM), and Digital Twin (DT) in Construction Industry: A Review, Bibliometric, and Network Analysis. Buildings 2022, 12, 1503. [CrossRef]
- Arsenijević, D.; Stankovski, S.; Ostojić, G.; Baranovski, I.; Oros, D. An Overview of IoT Readiness Assessment Methods. In Proceedings of the 8th International Conference on Information Society and Technology; 2018; pp. 48–53.
- Metwally, E.A.; Farid, Ayman.A.; Ismail, M.R. Development of an IoT Assessment Method: An Interdisciplinary Framework for Energy Efficient Buildings. Energy Build 2022, 254, 111545. [CrossRef]
- EN 15232; European Committee for Standarization Energy Performance of Buildings - Impact of Building Automation, Controls and Building Management; Brussels, 2017;
- ISO 52120-1:2021, I. 205 T.C. Energy Performance of Buildings Contribution of Building Automation, Controls and Building Management; Geneva, Switzerland, 2021;
- Ali, Z.; Mahmood, A.; Khatoon, S.; Alhakami, W.; Ullah, S.S.; Iqbal, J.; Hussain, S. A Generic Internet of Things (IoT) Middleware for Smart City Applications. Sustainability 2022, 15, 743. [CrossRef]
- Wei Wang; Lee, K.; Murray, D. Building a Generic Architecture for the Internet of Things. In Proceedings of the 2013 IEEE Eighth International Conference on Intelligent Sensors, Sensor Networks and Information Processing; IEEE, April 2013; pp. 333–338.
- Wang, W.; Lee, K.; Murray, D. A Global Generic Architecture for the Future Internet of Things. Service Oriented Computing and Applications 2017, 11, 329–344. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




