Submitted:
05 January 2024
Posted:
05 January 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- The detection of Sybil attacks using machine learning techniques requires computational resources, which can increase the overhead of the detection mechanism. Therefore, the research needs to focus on developing efficient detection mechanisms that minimize the computational overhead.
- MANETs have a dynamic network topology, which can make it challenging to detect Sybil attacks. The research needs to explore how to adapt the detection mechanism to changes in the network topology and improve the performance of the mechanism under such conditions.
| Year | Main Focus of the Survey | Major Contributions | Enhancement in Research Papers |
| 2022 | A Complete Analysis of Security Attacks in MANET | Bharti et al. [2] reviewed to provide us with various types of security attacks like Sybil Attacks, Blackhole Attacks, Security Attacks, and Rushing Attacks. This paper is useful to prevent networks from security challenges. | The researcher gives a critical study, compares outcomes, and identifies holes in all known methodologies. |
| 2022 | A Comprehensive Review of Various Attacks in Mobile Ad Hoc Networks |
Shekhar et al. [3] introduce mobile ad hoc networks (MANETs) and numerous sorts of attacks in MANETs, as well as preventative measures stated by many researchers to limit their impact on network performance. | The researcher provides a thorough comparison review of all available methodologies as well as a detailed critical critique. |
| 2022 | An Overview of Risk Identification, Intrusion Detection, and Machine Learning Techniques used concerning MANETs |
Micheal et al. [4] provide an overview of existing studies on MANETs. It also Introduces a new technique to identify the primary Risk Profile of MANETS by using machine learning techniques. It discovers new areas of probability-based methods to further enhance the existing impact-based techniques for evaluating threats within MANETs. |
The researcher provides a thorough literature study as well as a solution to detect holes in existing strategies for preventing Sybil attacks on MANETs. |
| 2021 | Review on Security Attacks and Intrusion Detection Techniques in MANETs | Alazab et al. examined intrusion detection systems in the context of the mobile ad-hoc network. In MANET, however, a single classifier was employed to detect the amount of infiltration. Using a random forest model, a hybrid intelligent approach was developed to handle the challenges associated with a mixture of classifiers and minimize the best possible false alarm rates. Though the false positive rate was reduced by using several classifiers and increasing node density at different time intervals, the strategy was not an efficient model. | The researcher provides a full literature overview of existing methodologies as well as a thorough critical critique. It also incorporates strategies based on machine learning. |
| 2022 | An Analysis of Essential Challenges and Attacks on MANET Security Appraisal | Singla et al. [5] identify a variety of attacks on MANET and strategies for countering them. This research examines various security features, challenges, attacks, and solutions for repelling attacks in several stages. | The researcher conducts a thorough critical examination of all available approaches. However, research gaps and problems are noted as well. |
| 2015 | A Review on Sybil attack detection techniques | Kamani et al. [6] The surveyed document provides a brief overview of several Sybil attack detection mechanisms in VANET. |
The researcher thoroughly describes all existing procedures and identifies a superior technique. Furthermore, future research difficulties are indicated. |
| 2015 | Review on deduction and mitigation of Sybil attack in the Network | Bhise et al. [7] A review of the deduction method of Sybil's attacks in the social network system has been provided and debated. Several strategies for mitigating the Sybil attack have been investigated. The detection rate, false positive rate, false negative rate, and non-trustworthy rate of the investigated mechanisms were all calculated. | The researcher gives a critical study, compares outcomes, and identifies holes in all known methodologies. |
- A full study is undertaken to analyze the difficulties in cutting-edge Sybil attack detection approaches.
- In this research, ML approaches are offered as the best answer to current challenges in Sybil detection in MANETs.
- The open research issues are recognized, and the relevant literature is cited.
2. Systematic Literature Review
2.1. Searching Protocol
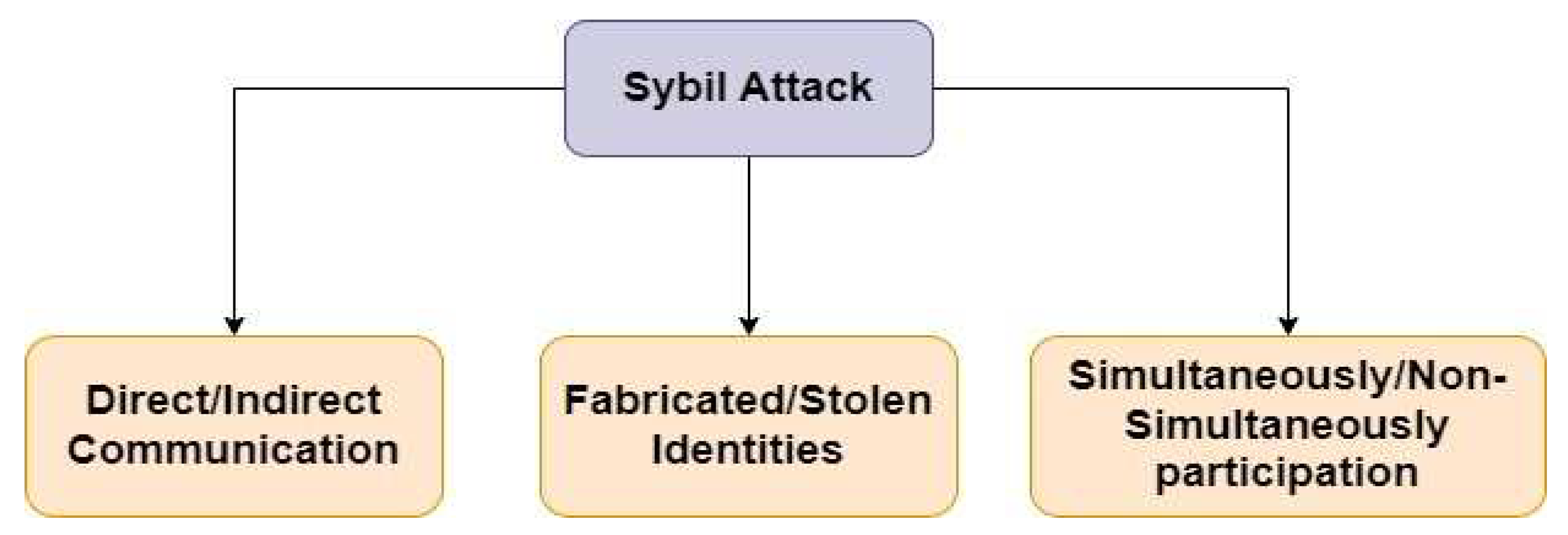
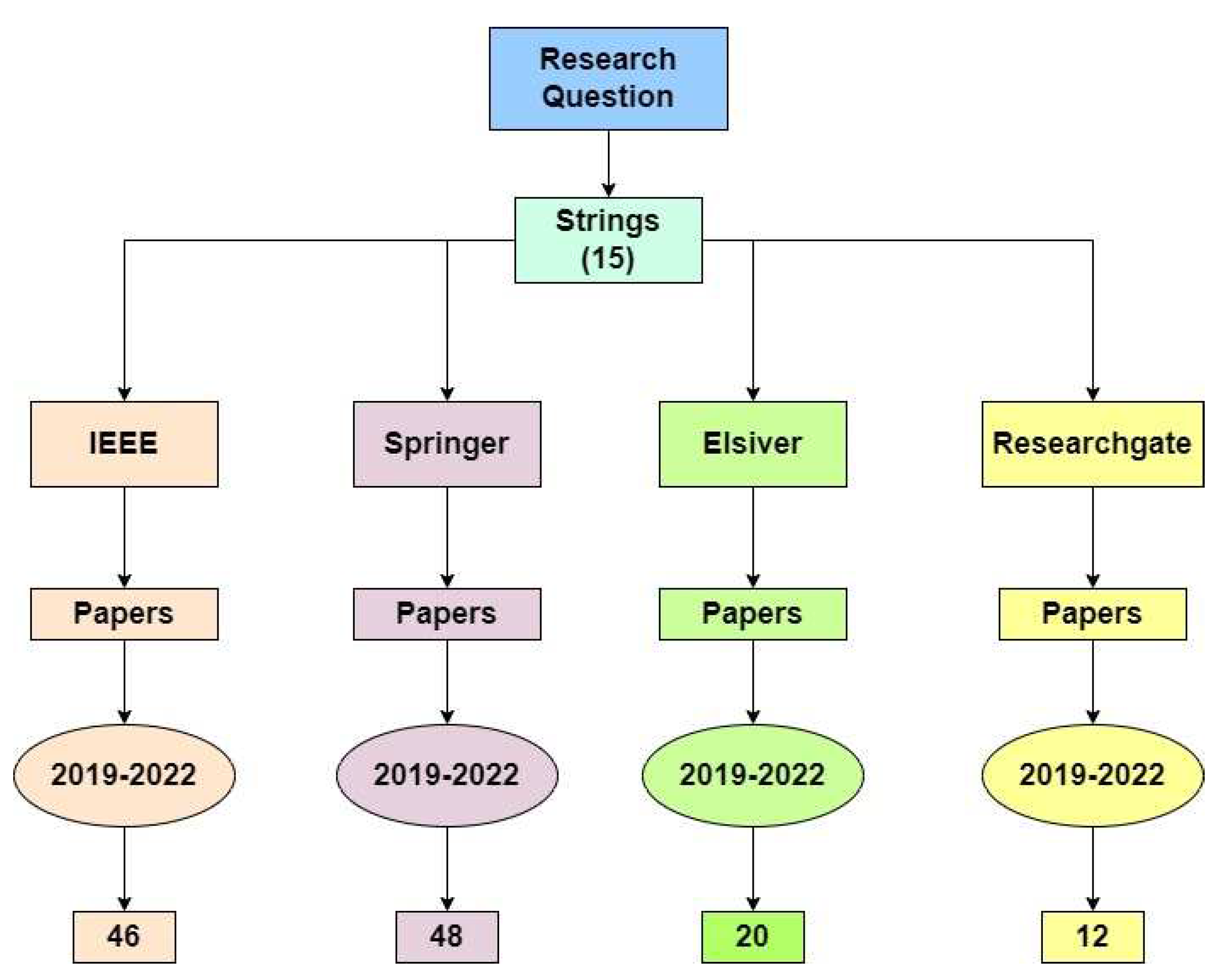
2.2. String Development
| Word | Synonym 1 | Synonym 2 | Synonym 3 |
| Detection | Identification | Recognition | Finding |
| Machine Learning based identification of Sybil attack Recognition of Sybil attack based on Machine learning Finding Sybil’s attack on MANET | |||
| Word | Synonym 1 | Synonym 2 | Synonym 3 |
| Machine Learning | Deep Learning | Artificial Neural Networks | Computational Learning |
| Detection of Sybil attack based on deep learning Role of artificial neural networks in the Detection of Sybil Attack Sybil attack detection based on computational learning | |||
2.3. Inclusion Criteria
2.4. Filtering
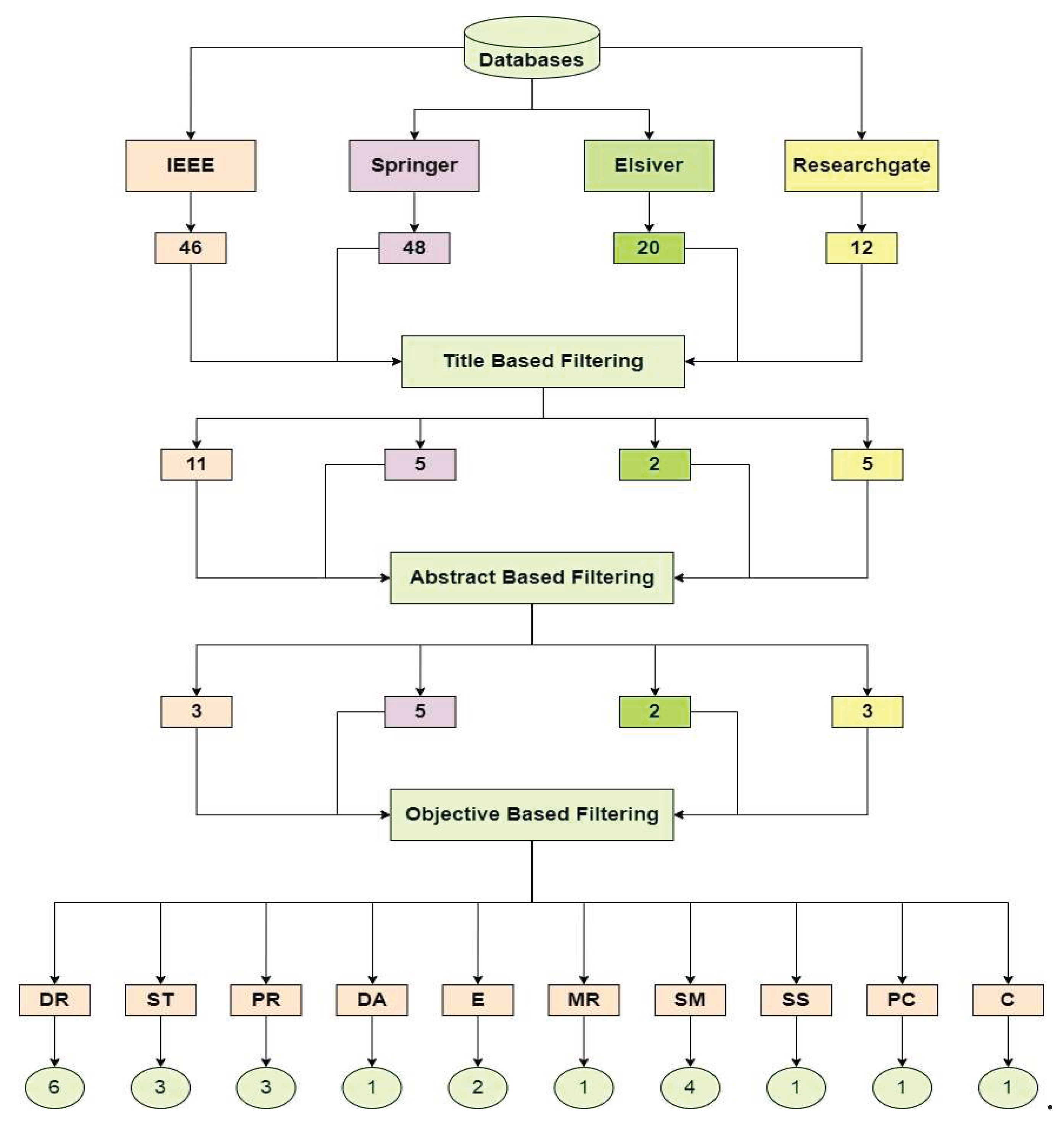
| Acronyms | Definition |
| DR | Deduction Rate |
| ST | Secure Transmission |
| PR | Performance Rate |
| DA | Detection Accuracy |
| E | Effectiveness |
| MR | Measuring Risk |
| SM | Security Measurement |
| SS | Secure Storage |
| PC | Power Consumption |
| C | Credibility |
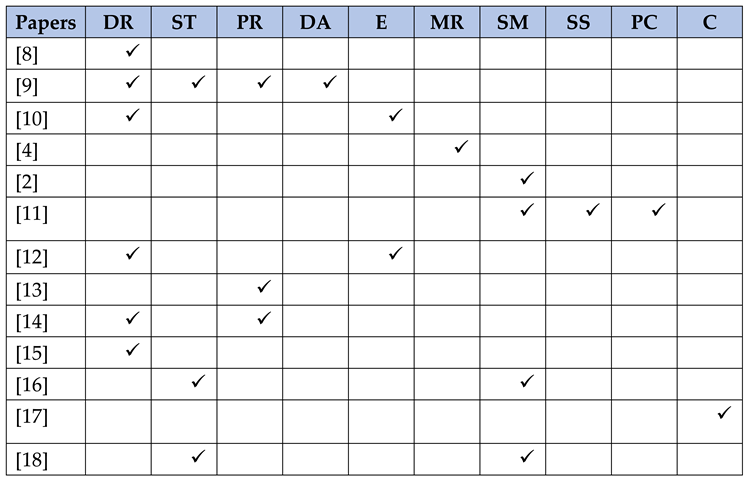 |
3. Detailed Literature
3.1. Fuzzy Logic
3.2. Machine Learning
3.3. ANN Artificial Neural Network
| Ref. | Scheme | Methodology |
| [9] | Fuzzy Logic Scheme | Fuzzy logic is a mathematical approach that allows for imprecise reasoning and decision-making by representing uncertainty and ambiguity using linguistic variables and fuzzy sets. |
| [14] | Support Vector Machines (SVM) | SVM is a supervised learning algorithm that can be used for binary classification of nodes as either genuine or Sybil based on input features such as the number of neighbors, message transmission frequency, and signal strength. |
| [9] | Decision Trees | Decision trees are another supervised learning algorithm that can be used to classify nodes as genuine or Sybil. Decision trees use a hierarchical tree structure to recursively partition the input space and make decisions based on the input features. |
| [11] | Random Forest | Random forest is an ensemble learning method that combines multiple decision trees to improve the accuracy of classification. It is a powerful technique that can handle high-dimensional feature spaces and noisy data. |
| [10] | Convolutional Neural Networks (CNNs) | CNNs are a type of neural network commonly used for image recognition. However, they can also be used for detecting Sybil attacks in MANETs. CNNs use convolutional layers to extract features from the input data and learn spatial relationships between the features. |
4. Performance Analysis
4.1. Critical Analysis
| Detection Algorithm | Effort Year | Technique | Shortcoming |
| [9] | 2022 | Fuzzy Logic Scheme | The evaluation of the IDS is limited to simulations, which may not accurately reflect the performance of the IDS in real-world MANETs [20] |
| [19] | 2020 | Support Vector Machines (SVM) | The proposed approach may not scale well to larger MANETs or more complex attack scenarios [17] |
| [14] | 2023 | Decision Trees | The paper only uses a relatively small dataset to train and test the proposed models, which may limit the generalizability of the findings [18] |
| [16] | 2020 | Random Forest | The paper evaluates the proposed system's performance using a real-world dataset, the evaluation is limited to a single scenario [19] |
| [15] | 2021 | Convolutional Neural Networks (CNNs) | The paper proposes an AI-based approach, it does not offer significant novelty compared to existing research [20] |
4.2. Identified Challenges:
| Category | Challenges | Solutions |
| Resource limitations [2] | In simulations, it is often assumed that nodes have unlimited computational resources, memory, and energy. However, in real-world MANETs, nodes have constrained resources, and the IDS needs to operate within these limitations. The impact of resource constraints on the performance and effectiveness of the IDS cannot be accurately assessed through simulations alone. | The solution to this challenge is Dataset analysis. It means analyzing real-world datasets collected from MANETs to evaluate the IDS's performance. [26] |
| Lack of Scalability [25] | MANET security mechanisms should be scalable to accommodate the dynamic nature of the network, frequent topology changes, and node mobility. The proposed approach may lack the flexibility to adapt to varying network conditions or changing security requirements. This can limit its ability to scale well and provide robust security in larger MANETs or under complex attack scenarios. | Cross-layer design strategies allow information to be sent between layers of the network protocol stack, increasing the efficiency and scalability of security measures. [27] |
| Limited Dataset [9] | Using a relatively small dataset to train and test the proposed model is a big challenge that can limit the generalizability of the findings. | Augmenting your existing dataset can help increase its size and diversity. This technique involves generating synthetic samples by applying transformations to the original data. By doing so, you can effectively expand your dataset and improve the generalizability of your models. [28] |
| Lack of significant novelty [5] | Proposing an AI-based approach without significant novelty is a big challenge because it does not provide a specific novelty compared to existing research. | Explainable AI (XAI) addresses the lack of novelty by focusing on the interpretability and explainability of the AI system. [29] |
5. Optimal Solutions
Dataset:
| Reference | Name of Dataset | Features |
| [30] | NSL-KDD dataset | It consists of approximately 1,074,992 single connection vectors each of which contains 41 features |
6. Conclusions
References
- M. ADIL, “BLACK HOLE ATTACKS PREVENTION THROUGH MAC BASED AODV PROTOCOL IN CONSTRAINT ORIENTED NETWORKS”.
- M. Bharti, S. Rani, and P. Singh, “Security Attacks in MANET: A Complete Analysis,” in 2022 6th International Conference on Devices, Circuits and Systems (ICDCS), IEEE, 2022, pp. 384–387.
- S. Shekhar, M. Mahajan, and S. Kaur, “A Comprehensive Review of Various Attacks in Mobile Ad Hoc Networks,” in 2022 6th International Conference on Trends in Electronics and Informatics (ICOEI), IEEE, 2022, pp. 638–643.
- H. Michael and A. Jedidiah, “Mobile Adhoc Networks-An Overview of Risk Identification, Intrusion Detection and Machine Learning Techniques used,” in 2022 IEEE 2nd International Conference on Mobile Networks and Wireless Communications (ICMNWC), IEEE, 2022, pp. 1–5.
- R. Singla, N. Kaur, D. Koundal, and A. Bharadwaj, “Challenges and developments in secure routing protocols for healthcare in WBAN: a comparative analysis,” Wireless Personal Communications, pp. 1–40, 2022.
- J. Kamani and D. Parikh, “A Review on Sybil Attack Detection Techniques,” vol. 01, no. 01.
- M. Bhise and S. D. Kamble, “Review on Detection and Mitigation of Sybil Attack in the Network,” Procedia Computer Science, vol. 78, pp. 395–401. 2016. [CrossRef]
- Chethana, P. K. Pareek, V. H. C. de Albuquerque, A. Khanna, and D. Gupta, “Deep Learning Technique Based Intrusion Detection in Cyber-Security Networks,” in 2022 IEEE 2nd Mysore Sub Section International Conference (MysuruCon), IEEE, 2022, pp. 1–7.
- E. Sing and S. M. C. Vigila, “Fuzzy based intrusion detection system in MANET,” Measurement: Sensors, p. 100578, 2022.
- B. Hammi, M. Y. Idir, and R. Khatoun, “A machine learning based approach for the detection of sybil attacks in C-ITS,” in 2022 23rd Asia-Pacific Network Operations and Management Symposium (APNOMS), IEEE, 2022, pp. 1–4.
- F. Abdel-Fattah, K. A. Farhan, F. H. Al-Tarawneh, and F. AlTamimi, “Security challenges and attacks in dynamic mobile ad hoc networks MANETs,” in 2019 IEEE jordan international joint conference on electrical engineering and information technology (JEEIT), IEEE, 2019, pp. 28–33.
- Y. Jiang, Y. Li, Y. Zhou, and X. Zheng, “Sybil Attacks and Defense on Differential Privacy based Federated Learning,” in 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), IEEE, 2021, pp. 355–362.
- H. Ali, I. Malik, S. Mahmood, F. Akif, and J. Amin, “Sybil Detection in Online Social Networks,” in 2022 17th International Conference on Emerging Technologies (ICET), IEEE, 2022, pp. 125–129.
- N. S. G. Bharti and P. Gulia, “Exploring machine learning techniques for fake profile detection in online social networks,” International Journal of Electrical and Computer Engineering (IJECE), vol. 13, no. 3, pp. 2962–2971, 2023.
- Vani, “Deplete And Discernment Of Security Hazards In Mobile Ad-Hoc-Networks (Manet) Using Artifical Intelligence,” International Journal of Future Generation Communication and Networking, vol. 14, no. 1, pp. 925–942, 2021.
- M. Madanan and A. Venugopal, “Designing an Artificial Intelligent MANET to reduce and detect security threats and concerns,” in Proceedings of the 2006 14th IEEE International Conference on Network Protocols, 2020, pp. 75–84.
- Kumari, S. Dutta, and S. Chakraborty, “Detection and Prevention of Black Hole Attack in MANET using Node Credibility and Andrews Plot,” 2023.
- S. Thapar and S. K. Sharma, “Attacks and security issues of mobile ad hoc networks,” in Proceedings of International Conference on Sustainable Computing in Science, Technology and Management (SUSCOM), Amity University Rajasthan, Jaipur-India, 2019.
- S. Rethinavalli and R. Gopinath, “Classification Approach based Sybil Node Detection in Mobile Ad Hoc Networks,” International Journal of Advanced Research in Engineering and Technology, vol. 11, no. 12, pp. 3348–3356, 2020.
- Chaudhary, V. N. Tiwari, and A. Kumar, “Analysis of fuzzy logic based intrusion detection systems in mobile ad hoc networks,” BVICA M’s International Journal of Information Technology, vol. 6, no. 1, p. 690, 2014.
- M. Di Mauro, G. Galatro, G. Fortino, and A. Liotta, “Supervised feature selection techniques in network intrusion detection: A critical review,” Engineering Applications of Artificial Intelligence, vol. 101, p. 104216, 2021.
- Vasudeva and M. Sood, “Survey on sybil attack defense mechanisms in wireless ad hoc networks,” Journal of Network and Computer Applications, vol. 120, pp. 78–118, 2018.
- M. Aljabri, R. Zagrouba, A. Shaahid, F. Alnasser, A. Saleh, and D. M. Alomari, “Machine learning-based social media bot detection: a comprehensive literature review,” Social Network Analysis and Mining, vol. 13, no. 1, p. 20, 2023.
- N. Goyal and A. Gaba, “A review over MANET-Issues and Challenges,” International Journal of Enhanced Research in Management & Computer Applications, vol. 2, pp. 2319–747116, Apr. 2013.
- Z. Wei, H. Tang, F. R. Yu, M. Wang, and P. Mason, “Security Enhancements for Mobile Ad Hoc Networks With Trust Management Using Uncertain Reasoning,” IEEE Transactions on Vehicular Technology, vol. 63, no. 9, pp. 4647–4658, Nov. 2014. [CrossRef]
- Khraisat, I. Gondal, P. Vamplew, and J. Kamruzzaman, “Survey of intrusion detection systems: techniques, datasets and challenges,” Cybersecur, vol. 2, no. 1, p. 20, Dec. 2019. [CrossRef]
- Anurag Das, “Cross Layer Design in Mobile Ad Hoc Networks: Issues and Solutions,”. 2018. [CrossRef]
- C. Shorten and T. M. Khoshgoftaar, “A survey on Image Data Augmentation for Deep Learning,” J Big Data, vol. 6, no. 1, p. 60, Dec. 2019. [CrossRef]
- F. Emmert-Streib, O. Yli-Harja, and M. Dehmer, “Explainable artificial intelligence and machine learning: A reality rooted perspective,” WIREs Data Mining Knowl Discov, vol. 10, no. 6, Nov. 2020. [CrossRef]
- G. G. Gebremariam, J. Panda, and S. Indu, “Localization and Detection of Multiple Attacks in Wireless Sensor Networks Using Artificial Neural Network,” Wireless Communications and Mobile Computing, vol. 2023, 2023.
- Lim, M., Abdullah, A., & Jhanjhi, N. Z. (2020). Data fusion-link prediction for evolutionary network with deep reinforcement learning. International Journal of Advanced Computer Science and Applications, 11(6).
- Alwakid, G., Gouda, W., Humayun, M., & Jhanjhi, N. Z. (2023). Diagnosing Melanomas in Dermoscopy Images Using Deep Learning. Diagnostics, 13(10), 1815.
- Tayyab, M., Marjani, M., Jhanjhi, N. Z., Hashem, I. A. T., Usmani, R. S. A., & Qamar, F. (2023). A Comprehensive Review on Deep Learning Algorithms: Security and Privacy Issues. Computers & Security, 103297.
- Pal, S., Jhanjhi, N. Z., Abdulbaqi, A. S., Akila, D., Almazroi, A. A., & Alsubaei, F. S. (2023). A hybrid edge-cloud system for networking service components optimization using the internet of things. Electronics, 12(3), 649.
- Ponnusamy, V. (Ed.). (2016). Biologically-Inspired Energy Harvesting through Wireless Sensor Technologies. IGI Global.
- Ponnusamy, V., Jung, L. T., Ramachandran, T., & Zaman, N. (2017, April). Bio-inspired energy scavenging in wireless ad hoc network. In 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT) (pp. 1-5). IEEE.
- Abbas, S. F., Shahzad, R. K., Humayun, M., Jhanjhi, N. Z., & Alamri, M. (2019). SOA Issues and their Solutions through Knowledge Based Techniques—A Review. Int. J. Comput. Sci. Netw. Secur., 19(1), 8-21.
- Humayun, M., Jhanjhi, N. Z., Talib, M. N., Shah, M. H., & Suseendran, G. (2021). Cybersecurity for Data Science: Issues, Opportunities, and Challenges. Intelligent Computing and Innovation on Data Science: Proceedings of ICTIDS 2021, 435-444.
- Kumar, P., Kumar, R., Aljuhani, A., Javeed, D., Jolfaei, A., & Islam, A. N. (2023). Digital twin-driven SDN for smart grid: A deep learning integrated blockchain for cybersecurity. Solar Energy, 263, 111921.
- Mukherjee, D., Ghosh, S., Pal, S., Akila, D., Jhanjhi, N. Z., Masud, M., & AlZain, M. A. (2022). Optimized Energy Efficient Strategy for Data Reduction Between Edge Devices in Cloud-IoT. Computers, Materials & Continua, 72(1).
- Hanif, M., Ashraf, H., Jalil, Z., Jhanjhi, N. Z., Humayun, M., Saeed, S., & Almuhaideb, A. M. (2022). AI-based wormhole attack detection techniques in wireless sensor networks. Electronics, 11(15), 2324.
- Jabeen, T., Jabeen, I., Ashraf, H., Jhanjhi, N., Humayun, M., Masud, M., & Aljahdali, S. (2022). A monte carlo based COVID-19 detection framework for smart healthcare. Computers, Materials, & Continua, 70(2), 2365-2380.
- Siddiqui, F. J., Ashraf, H., & Ullah, A. (2020). Dual server based security system for multimedia Services in Next Generation Networks. Multimedia Tools and Applications, 79, 7299-7318.
- Shahid,H.,Ashraf,H.,Ullah,A.,Band,S.S.&Elnaffar,S.Wormholeattackmitigationstrategiesandtheirimpact onwirelesssensornetworkperformance: Aliteraturesurvey. InternationalJournalofCommunicationSystems35, e5311(2022). Available online: https://onlinelibrary.wiley.com/doi/abs/10.1002/dac.5311.
- Kaur, R., Verma, S., Jhanjhi, N. Z., & Talib, M. N. (2021, August). A comprehensive survey on load and resources management techniques in the homogeneous and heterogeneous cloud environment. In Journal of Physics: Conference Series (Vol. 1979, No. 1, p. 012036). IOP Publishing.
- Alotaibi, A. F. (2021). A comprehensive survey on security threats and countermeasures of cloud computing environment. Turkish Journal of Computer and Mathematics Education (TURCOMAT), 12(9), 1978-1990.
- Al-Turjman, F. (Ed.). (2020). Drones in smart-cities: Security and performance. Elsevier.
- Ponnusamy, V., Jung, L. T., Ramachandran, T., & Zaman, N. (2017, April). Bio-inspired energy scavenging in wireless ad hoc network. In 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT) (pp. 1-5). IEEE.
- Ponnusamy, V. (Ed.). (2016). Biologically-Inspired Energy Harvesting through Wireless Sensor Technologies. IGI Global.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





