1. Introduction
Mobile communications face several challenges in delivering signals with a good signal-to-noise ratio (SNR) and high transmission rates to users. One is multipath propagation, which is present mainly in large urban centers, with increasingly larger buildings and many users sharing the spectrum. This study proposes the implementation of strategically positioned reflecting surfaces to enhance the channel SNR and deliver a clearer, less interfered signal.
Large, intelligent surfaces have been one of the biggest innovations in digital communications in recent years. The term has variants such as large reflecting surfaces or intelligent reflecting surfaces. They consist of a grid of reflecting units composed of a metamaterial with a controllable reflection coefficient that can be digitally controlled using an optimization algorithm to strengthen the channel’s LoS.
According to Zhang et al. [
24], a cost-effective and energy-efficient solution is presented to enhance signal coverage and improve system capacity in mobile communications. However, the Large Intelligent Surfaces face challenges such as multiplicative fading effects arising from composite channels between the LIS and base stations and between the LIS and users. Additionally, the LIS encounters difficulties in enhancing communication systems when a strong direct link is present. Almekhlafi et al. [
2] investigated a scenario where a base station transmits signals to multiple users using a single antenna. They developed an algorithm to jointly optimize power allocation to users and phase shifts induced by the LIS. In contrast to other studies that perform optimization processes in a decoupled manner, the authors propose two solutions: one utilizing linear transformation to reduce the number of variables for optimization and another employing an element-wise Karush-Kuhn-Tucker approach to derive closed-form expressions for phase shifts in a multi-user scenario.
Researchers are actively involved in discussions about the sixth generation and beyond the fifth generation (B5G) of mobile communications in several countries [
2,
4,
5,
6]. To meet this advancement, the community faces a series of challenges, encompassing algorithmic and mathematical complexities, as well as issues related to hardware and materials [
7,
8,
9,
10].
Tataria et al. [
11] contributed significantly to addressing the challenges associated with the real-time implementation of LIS. In the same vein, Wang et al. [
12] presents a remarkable system proposal employing a reconfigurable smart reflective surface in a MIMO cognitive radio environment. Their approaches strive to optimize the system secrecy rate by jointly optimizing base station transmit beamforming, and RIS reflected beamforming, considering the complexities of dynamic environments.
Despite being a relatively new topic, there are older references in the LIS literature [
13]. The term LIS has gained evidence and prominence and become a relevant bet for the technological industry and also academic research as a promising alternative to improve spectral efficiency (since it can act passively, without energy expenditure), decrease the bit error probability, and allow the erasure of channels for eavesdroppers using beamforming techniques allowing a more elaborate approach of Physical layer security.
The ability of the LIS to adapt to the channel and generate a resulting channel with different statistics allows us to, in a way, think of a controllable and adjusted channel. The channel between the transmitter and the LIS, as well as the channel between the end-user and the LIS, can be generically modeled using the Nakagami-m distribution, with the
m parameter allowing a generic analysis of the environment’s behavior [
14] before considering the presence of the LIS. In addition, it is prudent to consider a possible direct channel between the user and the transmitter and channels between the transmitter and an eavesdropper; without losing the generality, we can consider all these channels as Nakagami-m. However, each one has its parameter
m; for users close to the base station, the parameter
m in the Nakagami distribution for the direct channel will be large between the user and the transmitter and may not even need the LIS, whereas a user outside the LoS may have
and fall into the Rayleigh fading scenario (without LoS) where the LIS will create a channel resulting from the composition of all the links that result in a channel with LoS and a lower bit error rate [
15].
The literature on mobile communication network optimization has been limited to two-point operations, with some strategies only for the transmitter (a base station) and the receiver. However, LIS changed this reality and created new possibilities to achieve even lower bit error rates, better spectral efficiency, decreased transmission power, and increased SNR. According to Gong et al., [
16] the LIS allows modifying the channel characteristics and canceling its phase; in addition to projecting the beam towards the user, the adjustable reflector panels of the LIS can match the signals that reach them, thus enabling a smart radio environment that learns to beat the channel, even when its characteristics change.
Wu et al.[
17] developed a framework in the form of a tutorial for implementing the LIS; the authors present the channel model, including the reflectors, discuss hardware aspects and practical issues related to the system deployment and point out future possibilities for this technology.
Sánchez et al. [
18] present performance analyses regarding physical layer security (PLS) in an environment assisted by LIS, considering the possibility of phase errors. The authors assume that it is possible to model an equivalent scalar fading channel including the LIS, as shown by recent work [
19] and show that the eavesdropper’s channel is Rayleigh distributed. The fading coefficient is statistically independent of the channel between the transmitter and the legitimate user; they also present the scaling laws for the SNR of the legitimate channel and the eavesdropper concerning the number of LIS reflectors.
Most preliminary articles on LIS present strategies for estimating the channel assisted by the LIS via least squares and other related methods, considering perfect knowledge of the CSI. However, this scenario is not close to reality since they are passive reflectors that intelligently reflect the inside electromagnetic waves to improve system performance. Nadeem et al. [
20] present one of the first and most relevant contributions in studying a multi-user system assisted by LIS assuming imperfect CSI. The authors use the
a priori knowledge of the fading statistics to feed a Bayesian minimum mean squared error (MMSE) estimator for the resulting fading, thus proposing a joint design of the precoder and the power allocation for transmission considering the application of beamforming in the LIS and show the impact of the channel estimation error on the efficiency of the designed system.
Basar et al. [
21] present a script for the analytical calculation of the symbol error probability (SEP) in the transmission through the LIS in a generic scenario, in addition to presenting alternative modeling that considers the LIS as an access point (AP), which can or not knowing the phases of the channel.
The statistical analysis of cascaded MIMO channels poses a considerable challenge, complicating the modeling of resulting fading due to including both linear and non-linear transformations of random variables in its definition. However, by using the central limit theorem (CLT), it is possible to obtain, with great accuracy, the fading statistical model, taking into account the continuous phase errors committed by the LIS after the phase adjustment. The composite channel is the product of two channels with distribution Nakagami-
m [
14] with different coefficients modeling what goes to the LIS and what goes to the user and a complex phase error modeled as Von Mises distributed. Ferreira et al. [
15] obtained the distribution of the resulting channel considering only one antenna in the receiver; in this work, we approach a more complex and more comprehensive system model, which includes all the analyses made by the authors, for a special case in which the number of antennas of the user is unitary.
This study investigates the fading distribution of a LIS-aided channel with multiple transmitters and users enabling the increase of SINR, allowing the strengthening of a LoS or improving spectrum sharing. It examines the impact of channel parameters (the number of LIS reflectors, users, the Von Mises error concentration parameter, and the number of transmitter antennas) on the bit error probability and the secrecy outage probability. The aim is to assess the impact of LIS design on performance and help design the system based on quality and information security metrics, evaluating performance that can be calculated directly through simple algebraic expressions involving the parameters of the statistical modeling of the system.
2. System Model
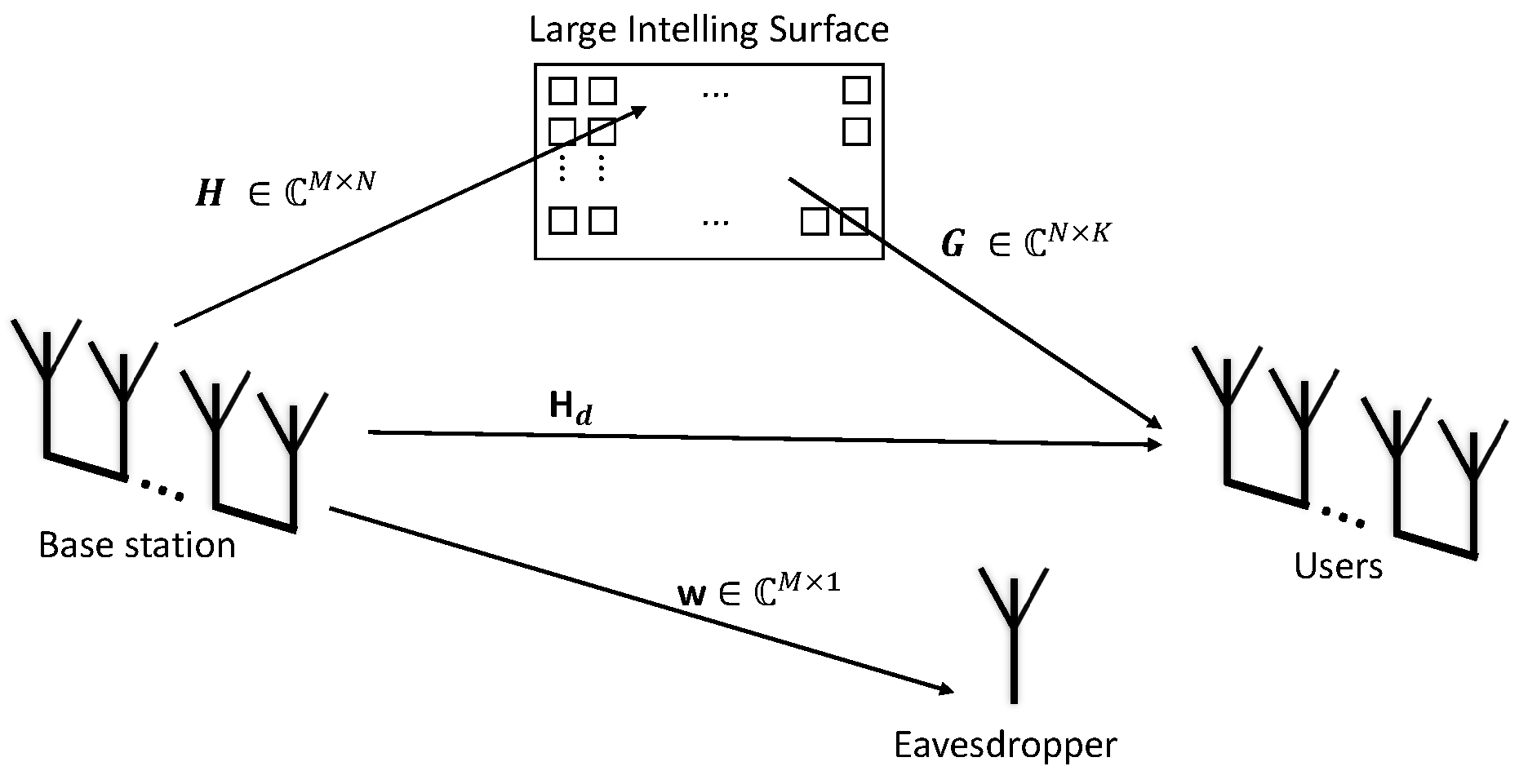
This work considers a base station composed of
M uncorrelated antennas and
K uncorrelated users represented as an antenna array, as shown in
Figure 1. The base station sends the same message to all users; however, it applies a normalized precoding vector for each one of the fading channels.
The signal received by the uncorrelated antenna array at the user side is
where
is the channel between each one of the uncorrelated antennas at the base station and each one of the LIS reflectors,
is the channel between the LIS reflectors and the users,
is the phase matrix with the phase shifts applied by the LIS in the incoming signals,
is the direct link between the base station and each user. The eavesdropper link is
and will be considered only for the secrecy outage probability analysis. Therefore, it will be neglected in the first analysis.
One possible strategy to cancel the channel phase is to apply a precoding matrix at the base station; in this case, the sub-optimal solution is the normalized hermitian of the overall channel.
Let
whose dimensions are
, and the elements of the matrix
are the
vectors.
The scalar elements of have a Nakagami distribution with parameters and , the elements of have a Nakagami distribution with parameters and , the elements of follow the complex normal distribution with mean zero.
The mean of a variable
T with Nakagami-
m distribution with parameters
m and
can be calculated by
and the second order moment
.
The transmitted symbols after the application of the precoder are
where
P is the power gain and
A is the precoding matrix, and for analysis purposes the
symbols are generated as complex normal distributed
.
The sub-optimal precoding matrix, considering complete knowledge of the Channel State Information (CSI) is given by
where
is the Frobenius norm. The precoding vector for each user is given by
and each one of the
has dimensions
.
The scalar definition of each element of the
vectors is
after the application of the LIS, these coefficients can be rewritten as
where
,
and
are the phases of each channel.
To nullify the overall channel phase, the phase shift applied by the LIS panel must be equal to
where
is the residual error of the LIS phase correction.
The elements of the overall channel matrix for each user are
where
and
are the lines of the matrix
.
The norm of the overall channel for each user can be written as
and the SINR at the user antenna
k will be
where the terms
The SINR can be rewritten as
where
.
Since the summation terms of the equation (
10) are complex variables, then
where
Considering that the complex number
thus
in which
and
By substituting the imaginary and real parts of the complex scalar
, it follows that
since the real and imaginary parts of the direct path
are Gaussian and uncorrelated.
Let be
and
, therefore we can rewrite
as
then
consider that
Therefore, the SINR can be written in terms of these two coefficients as
Since is the sum of squared Gaussian random variables, it is reasonable to assume that is Gamma distributed with parameters and . The term is the sum of Gamma random variables, and it is supposed to be also Gamma distributed with parameters and .
The SINR is the ratio between the variables and and also is supposed to be Gamma distributed. This study proposes an approximation for the SINR distribution to obtain the error and secrecy outage probability. Although not an exact solution, the approximation is very accurate, even for small values of M, N, and K.
The parameters of the SINR distribution can be obtained by calculating the moments of . Since is the ratio of and , therefore the statistics of the numerator and the denominator must be evaluated.
The variables and are correlated, and because of this, the covariance between them must be taken into account.
According to Kendall et al., [
22], the mean of the ratio between the Gamma random variables will be
where
and
.
The variance can be approximated by
where
and
.
The term
can be computed as
, by considering the definition of the covariance and considering that all the coefficients
are equally distributed, then
Given the covariance
, the variance of
can be derived as
where
is an approximation for
.
Since
thus
with the overall channel moments, the fading parameters
and
can be computed as follows
where
and
are the shape and rate parameters of the SINR
.
2.1. Error Probability
The error probability of a LIS-aided communication system was derived by Ferreira et al. [
19], considering that the transmitted symbols are
M-QAM signals transmitted through a Gamma fading channel, in this scenario, the probability will be
Since the mu-MIMO LIS channel is considered as Gamma distributed, therefore this expression for will be used. The parameters are identically distributed and therefore .
2.2. Secrecy Outage Probability
Secrecy outage probability is a metric used in communication systems to quantify the likelihood of unauthorized information disclosure. It represents the probability that the confidential information transmitted between parties becomes susceptible to interception or eavesdropping. A lower secrecy outage probability indicates a higher level of security, where the confidential information is less likely to be compromised during transmission.
The SOP is the probability that the instantaneous secrecy capacity,
C, be less or equal to a given capacity threshold,
, which is expressed as
the instantaneous secrecy capacity can be written as
where
is the SINR of the channel between the source and the eavesdropper and
is the SINR of the channel between the source and the correct destination (the user).
Ferreira et al. [
15] derived the exact formula of the SOP for a Nakagami-
m distributed eavesdropper channel as (
34).
3. Numerical Results
This section demonstrates the performance of the LIS for a multi-user system through simulations using the Monte Carlo method and analyzing the validity of the proposed approximations for various analysis scenarios in terms of the number of antennas at the LIS panel, the number of users in the system, the number of antennas at the base station, and the Von Mises parameter for the phase error distribution.
In this study, the SINR was simulated for each user using the parameters of each channel involved in the total link, being the Nakagami-m channels from the base station to the LIS, from the LIS to the user, and the complex normal direct channel from the base station to the user, which may be strong for near-field communications and weak for far-field communications. The SINR histograms were generated by the Monte Carlo method, simulating the resulting channel several times, and the contours of the histograms are shown close to the PDF of the Gamma distribution.
3.1. Probability Distribution
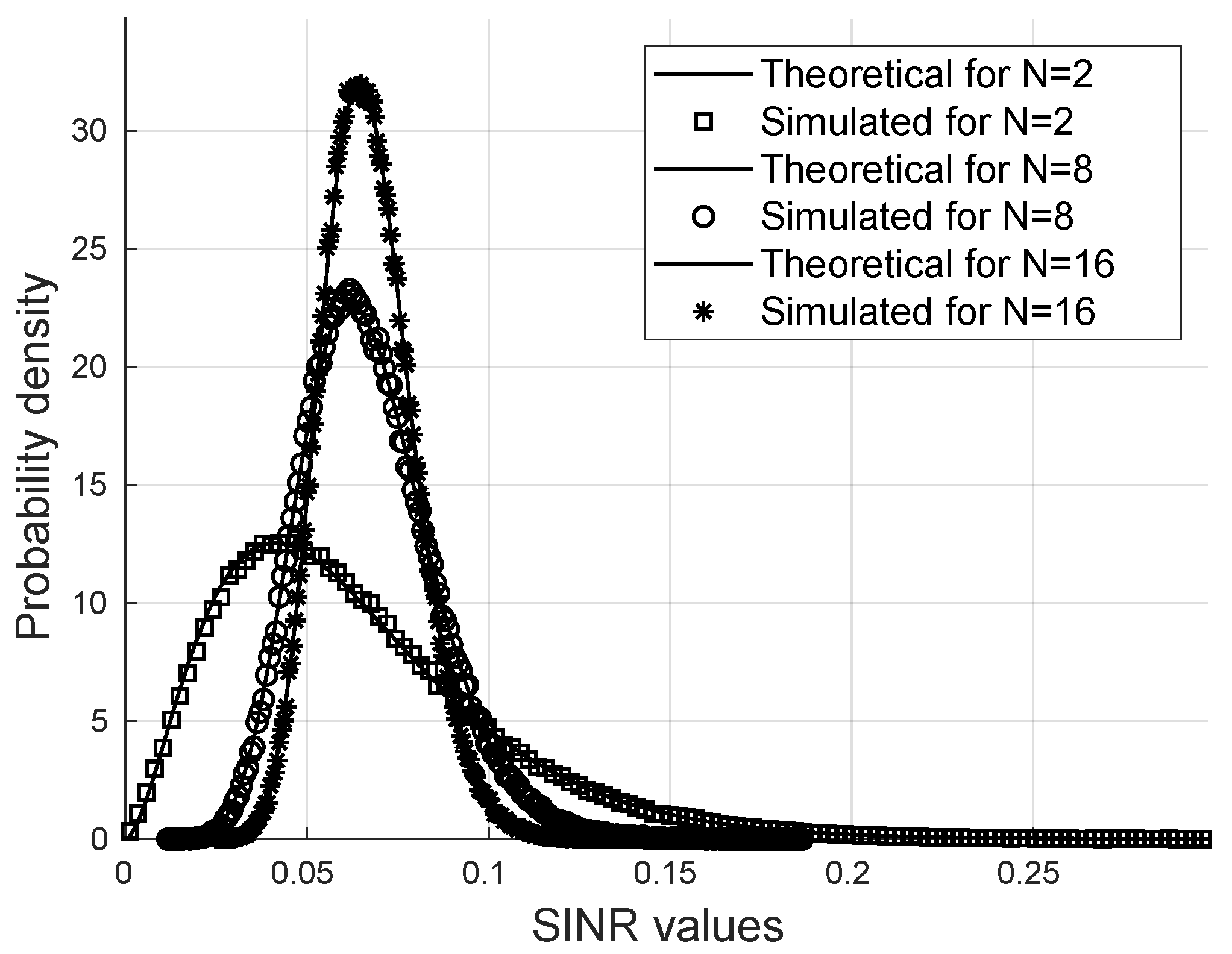
For
iterations of the Monte Carlo method, it is shown in
Figure 2 that the probability density function of the SINR is close to the Gamma distribution.
Figure 2 shows a comparison between the exact Gamma distribution and the simulated PDF of the SINR via the Monte Carlo method for
users, and
for different values of the number of reflectors
N.
It is possible to note that the SINR follows a gamma distribution for a wide variety of parameters in such a way that the analytical calculations of the moments and the statistical parameters of the SINR are valid for the formulas proposed for the Probability of bit error and the Secrecy outage probability.
3.2. Bit Error Probability
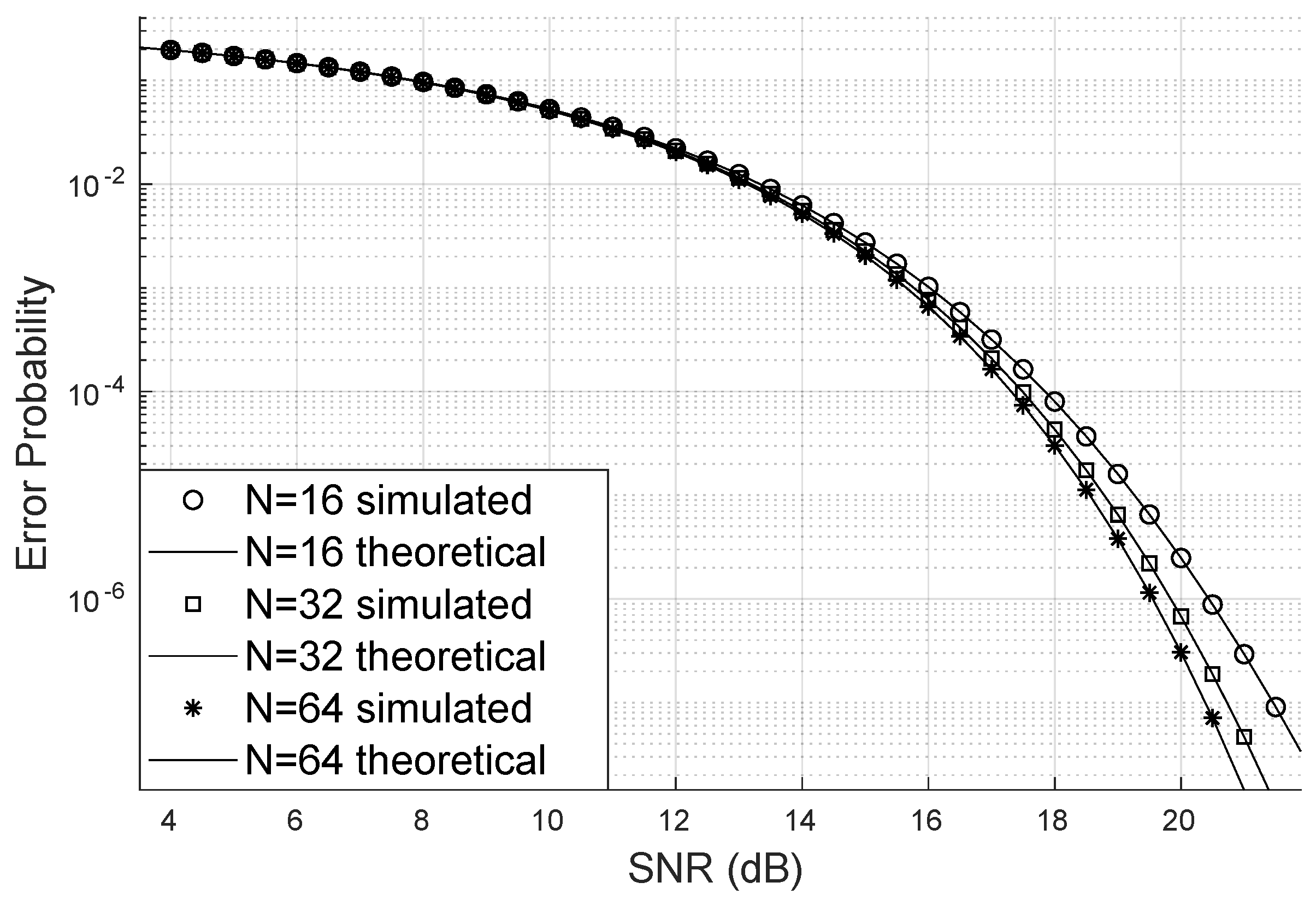
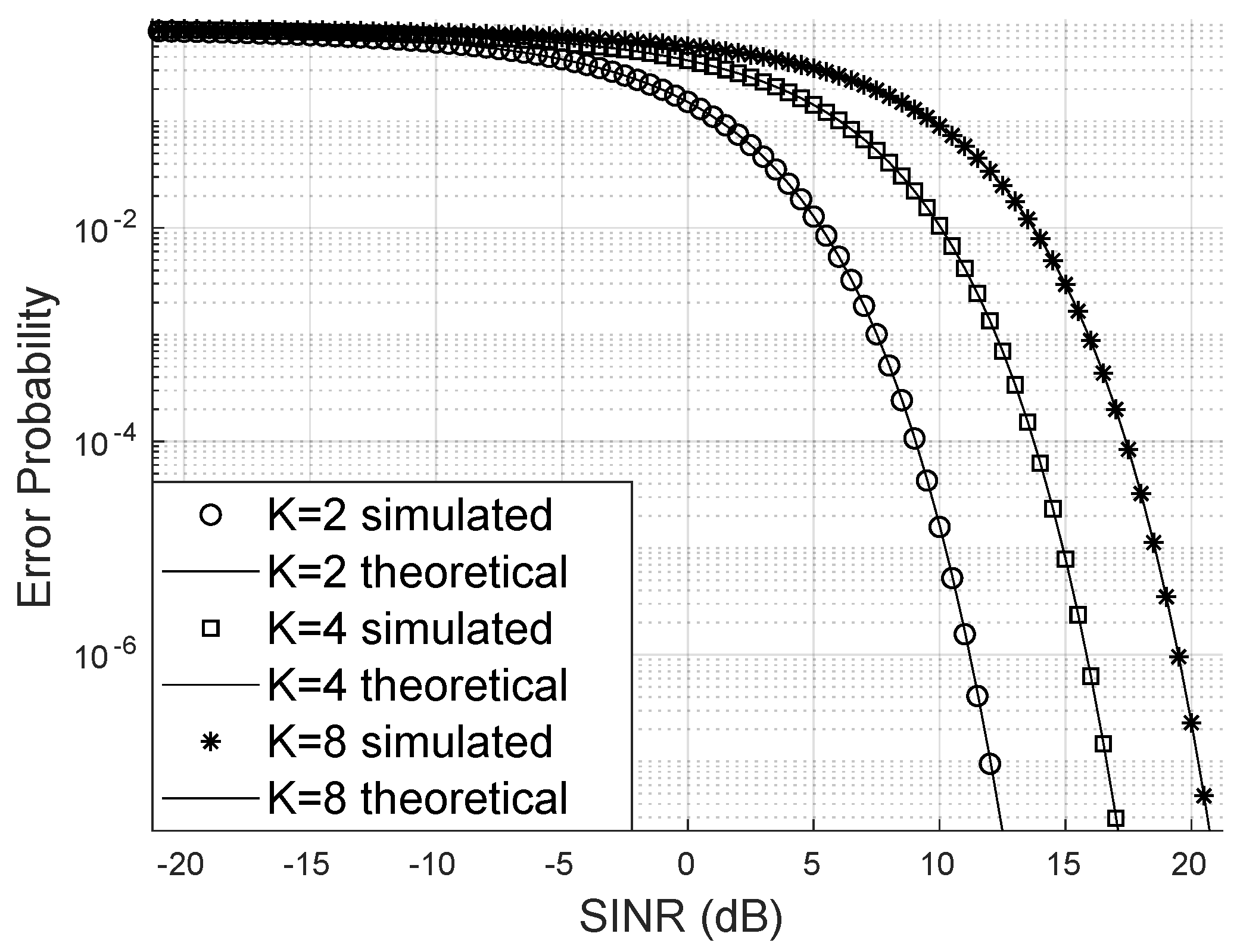
One possible way to demonstrate that the LIS can improve the SINR is by showing how the bit error probability varies, increasing the number of antennas at the base station, the number of reflecting elements, and the concentration parameter of the phase error distribution.
Figure 3 illustrates how the bit error probability decreases when the number of reflectors increases. This scenario has four users, eight transmitting antennas, the Nakagami parameter
, and the Von Mises
. Notably, although the bit error probability is low, the values do not change significantly from
to
as much as from
to
reflectors. This may be because the channel already has LoS. Additionally, and beyond a certain number of reflectors, the SINR becomes optimal with the assistance of LIS, which is something this type of analysis can help discover.
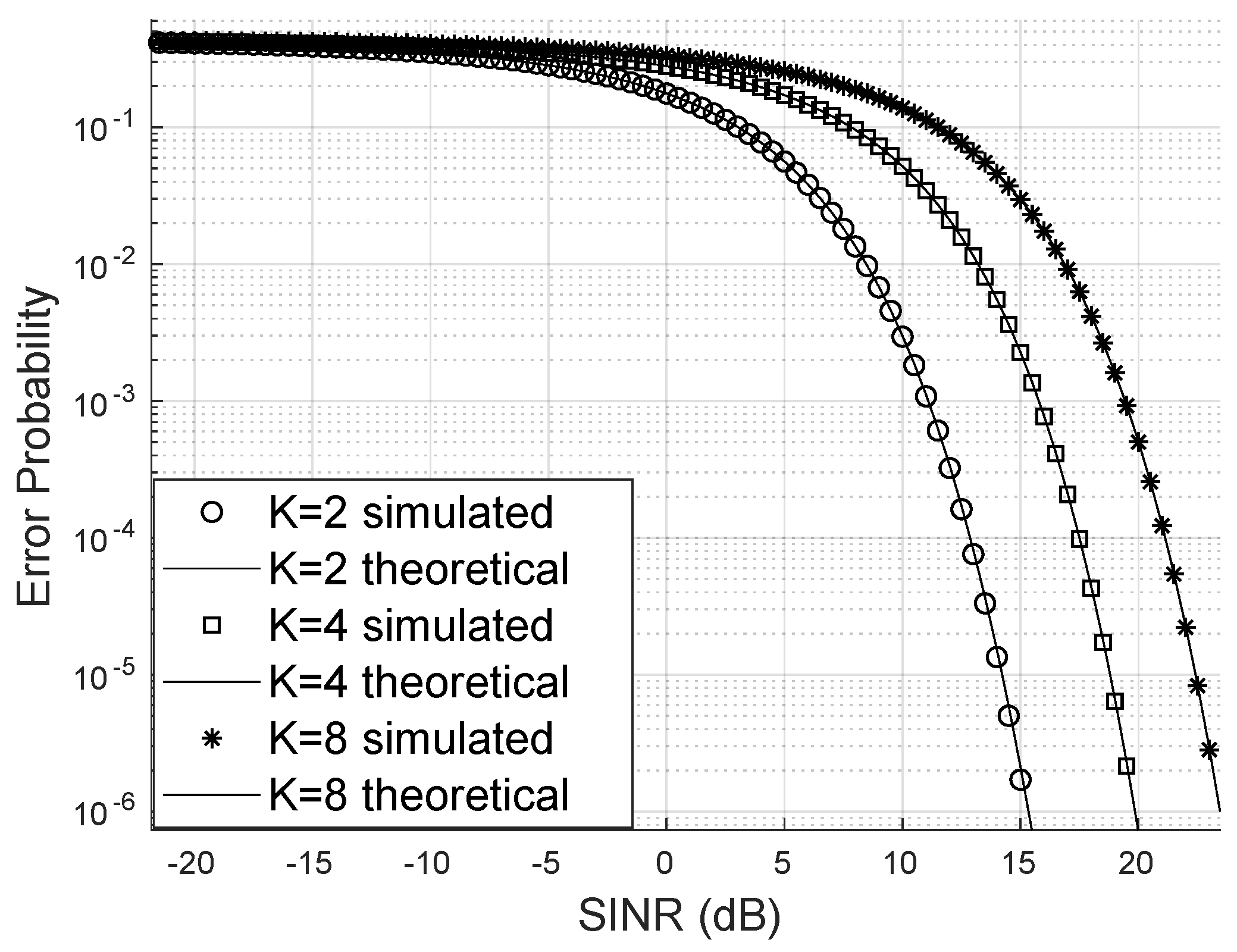
Figure 4 demonstrates that increasing the number of system users raises the bit error probability when keeping the number of LIS reflectors, base station antennas, and the Von Mises parameter constant. In this scenario, the transmission of 16-QAM signals was considered. One strategy to mitigate the increase of the error probability is to use many reflectors to enhance the LIS’s capacity to serve more users with higher SINR and consequently reduce the bit error probability.
For the scenario depicted in
Figure 7, in which signals from the 4-QAM constellation are transmitted, the approximation of SINR by the gamma distribution continues to hold, and the bit error probability remains higher when the system accommodates more users.
When there is no Line of Sight as in
Figure 6, where the scenario with SINR channels following a Rayleigh distribution (Nakagami with
) is analyzed, it is noticeable that the exact bit error probability continues to approximate the simulated bit error rate closely. In this case, a higher SINR was required compared to
Figure 5 to reduce the bit error rate promoted by the LIS. In this simulation, the number of reflectors was kept constant. However, it is worth noting that one case deals with the
constellation and the other with the
constellation.
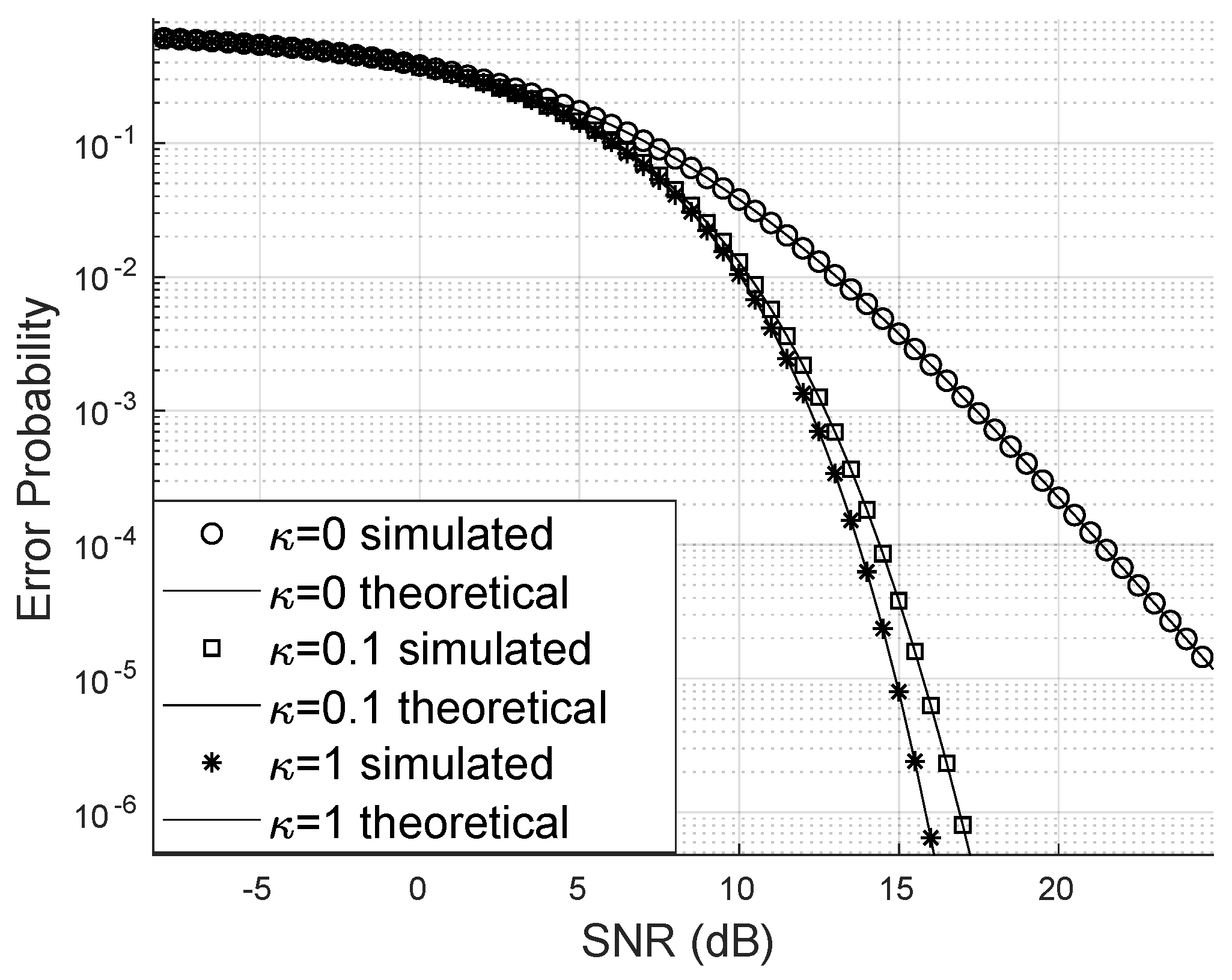
Regarding the Von Mises parameter, it is notable that the bit error probability decreases faster for larger values of
, as observed in
Figure 7. The worst-case scenario is when
and the error distribution is uniform. In this case, large and small phase errors have the same probability density and occur when the phase error has been poorly corrected.
Figure 7.
Error probability for different values.
Figure 7.
Error probability for different values.
If the phase error is concentrated around the mean (in this study, the mean phase error is zero), the PDF of the phase error approaches a delta function at the origin. In this case, the SINR will be higher because the sum of phasors will be greater if their phase is zero, and the complex exponential vanishes, leaving only the magnitudes.
3.3. Secrecy Outage Probability
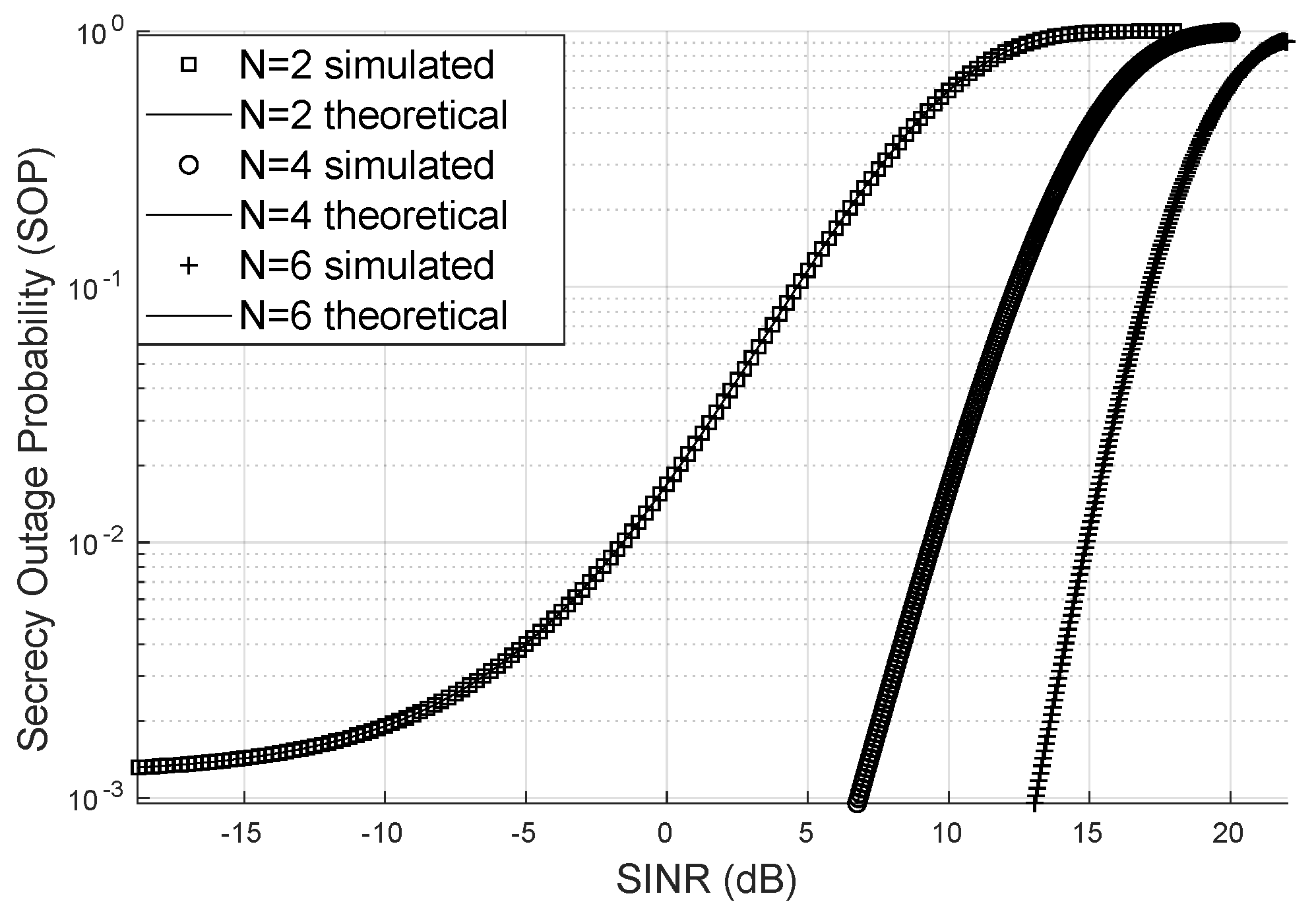
To simulate the Secrecy Outage Probability (SOP), the SINR corrected by the LIS was generated, and an additional eavesdropper channel with a Nakagami distribution with LoS access to the LIS signal was considered. This additional channel has a Line of Sight. The summation was truncated at index 100 to calculate the SOP, and the approximation closely matched the simulated SOP values via Monte Carlo. It was assumed that the Von Mises concentration parameter is , and the direct link has unity variance.
It can be observed in
Figure 8, where an eavesdropper channel with
and
is considered, that the higher the number of reflectors, the lower the SOP will be. This demonstrates that the LIS contributes to the confidentiality of information.
4. Conclusions
This study shows that Mu-MIMO channels formed by links with Nakagami-m fading, when assisted by Large Intelligent Surfaces, have a SINR with Gamma distribution and can considerably reduce their bit error probability by increasing the number of reflectors or the efficiency of the phase optimization algorithm (related to the parameter of the phase error distribution).
The worst case, considering the Nakagami-m fading channel is the Rayleigh fading (for ), this study shows that Rayleigh channels can be converted to Gamma fading channels by applying the phase shift matrix of the LIS. It was also shown that creating a line of sight in scenarios where a LoS did not exist was possible. This study presented the probability distributions of SINR compared to the PDF of the Gamma distribution. It showed that the exact formula for the probability density is very close to the one generated by the histogram obtained from the channel simulation.
It was possible to show that the LIS can enable a low secrecy outage probability, even for a few reflecting units and low bit error probability values, when increasing the number of LIS elements or improving the quality of phase correction. Our study assumes complete knowledge of the channel state information. It considers phase errors due to the behavior of the reflecting panel when attempting to correct the phase of many signals simultaneously (and not being able to optimize this for all) or due to the influence of the superposition of electromagnetic signals.
Funding
This work was partially funded by CNPq (Grant Nos. 302077/2022-7, 403612/2020-9, 311470/2021-1, and 403827/2021-3), by São Paulo Research Foundation (FAPESP) (Grant No. 2021/06946-0), by Minas Gerais Research Foundation (FAPEMIG) (Grant No. APQ-00810-21) and by the project "Resource-aware Machine Learning Model Optimization for Edge Computing" supported by xGMobile – EMBRAPII-Inatel Competence Center on 5G and 6G Networks, with financial resources from the PPI IoT/Manufatura 4.0 from MCTI grant number 052/2023, signed with EMBRAPII.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A. Statistical Parameters of Z k
Appendix A.1. Expected Value of Z k
The expected value of
will be
since the expected value is a linear operator, then
where the term
must be calculated, but first of all the terms
and
are needed.
The expected value
of the real part of
can be defined as
since
and the summation terms are independent and equally likely. Therefore
The moments of the fading channels are , , , , , , , , , , , and most of then will appear in the following equations.
The expected value
of the imaginary part of
can be computed as
since
and the summation terms are independent and equally likely, then
but the Von Mises variable
has a pdf that is symmetric about zero, and the phase errors are zero mean, so
, therefore
The expect value
of the magnitude of
can be obtained as
where
and
by expanding the terms (
A9), it follows that
that can be rewritten as
and since
and the expected value is a linear operator so
by separating the independent coefficients, it follows that
To compute
, four situations must be considered,
times the event
and
will occur in the summation,
times the event
and
will occur,
times
and
and
times
and
, then
The expected value
of the squared magnitude of
can be calculated as
that can be rewritten as
After expanding and simplifying the terms, it follows that
that can be simplified to
and since
. Therefore
To compute the expected value
substituting (
A8) in (
A2) then
After substituting (
A17) and (
A22) in (
A23) it follows that
Appendix A.2. Variance of Z k
To compute the variance of
, consider that
in terms of the real and imaginary parts, the equation can be rewritten as
since the variance of the sum of random variables can be computed in terms their covariances, then
where
and
To compute the previous variances, the covariances
and
are needed, consider that
and
since the expected value
can be obtained as
thus
To compute the expected value
, it is needed to change the summation indexes as
After applying the product and considering the independent indexes, it follows that
by expanding the previous equations, then
Assuming that
which can be simplified to
The term
, assuming that
can be computed as follows
by expanding the previous equation, then
and can be rewritten as
by substituting the statistical moments of the random variables, it follows that
that can be simplified to
since
therefore
The covariance
can be computed as
then
and covariance
can be calculated as
The variances
and
can be computed as
that can be rewritten as
since
then
The variance
can be calculated by
The variance
can be defined as
and the correlation
is
The term
can be calculated as
the term
can be computed as
then
will be given by (
A58).
The terms can be computed as , , , , , , , , , , , , , , , , , , , , , , , , , , , , .
Given
, it follows that
therefore, the variance will be
Appendix B. Statistical Parameters of F k
Appendix B.1. Expected Value of F k
Since
then the expected value of
can be calculated as
since the expected value of
was previously computed, therefore
Appendix B.2. Variance of F k
The variance
can be defined in terms of the statistics of
as
since the terms are independent and equally likely, then
considering that
where
that can be rewritten as
by expanding the product, it follows that
since
, then
For
by expanding the terms, it follows that
By expanding the terms of
, the expected value can be rewritten as (
A73).
Through the recursive expansion of the expression and analyzing the varying scenarios where the variables might be interdependent or independent, based on their index values, it can be inferred that, for
, the expected value
will be given by (
A74). For
, it can be calculated by (
A75).
Therefore,
can be calculated by (
A76).
The expected value
, for
where the expected value
can be calculated as
by expanding this equation and removing the null terms, then
can be obtained by (
A79).
by expanding the terms, it is easy to note that many expressions are equal to zero because of the expected value of the sine of a zero mean Von Mises random variable. The fourth order trigonometric moment of the phase is
, since
, therefore
The expected value
, considering that
, can be computed as
where
can be defined as
by expanding and removing the null terms, then
can be calculated by (
A85).
by expanding the summations and evaluating the expected values recursively, it follows that for
and
can be obtained by (
A87).
Therefore, the term
will be given by (
A88).
Appendix C. Statistical Parameters of γ k
Appendix C.1. Expected Value of γ k
The expected value of
, considering the gamma distribution in
since
and
are already known, we can compute using the derived expressions.
Appendix C.2. Variance of γ k
The variance of
can be computed considering the moments of
and
as
since
,
,
,
and
were previously derive, these parameters can be substituted here.
References
- Zhang, Z.; Dai, L. Reconfigurable Intelligent Surfaces for 6G: Nine Fundamental Issues and One Critical Problem. Tsinghua Science and Technology 2023, 28, 929–939. [Google Scholar] [CrossRef]
- Almekhlafi, M.; Arfaoui, M.A.; Assi, C.; Ghrayeb, A. A Low Complexity Passive Beamforming Design for Reconfigurable Intelligent Surface (RIS) in 6G Networks. IEEE Transactions on Vehicular Technology 2023. [Google Scholar] [CrossRef]
- Dang, S.; Amin, O.; Shihada, B.; Alouini, M.-S. What should 6G be? Nature Electronics 2020, 3, 20–29. [Google Scholar] [CrossRef]
- Pan, C.; Ren, H.; Wang, K.; Kolb, J.F.; Elkashlan, M.; Chen, M.; Di Renzo, M.; Hao, Y.; Wang, J.; Swindlehurst, A.L.; et al. Reconfigurable intelligent surfaces for 6G systems: Principles, applications, and research directions. IEEE Communications Magazine 2021, 59, 14–20. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Kak, A.; Nie, S. 6G and beyond: The future of wireless communications systems. IEEE Access 2020, 8, 133995–134030. [Google Scholar] [CrossRef]
- Pereira de Figueiredo, Felipe Augusto, et al. Massive MIMO channel estimation considering pilot contamination and spatially correlated channels. Electronics Letters 2020, 56, 410–413. [Google Scholar] [CrossRef]
- Inserra, D.; Li, G.; Dai, J.; Shi, J.; Wen, G.; Li, J.; Huang, Y. Dual-orthogonal polarization amplifying reconfigurable intelligent surface with reflection amplifier based on passive circulator. IEEE Transactions on Microwave Theory and Techniques 2024. [Google Scholar] [CrossRef]
- Rana, B.; Cho, S.-S.; Hong, I.-P. Review paper on hardware of reconfigurable intelligent surfaces. IEEE Access 2023. [Google Scholar] [CrossRef]
- Chen, K.; Song, W.; Li, Z.; Wang, Z.; Ma, J.; Wang, X.; Sun, T.; Guo, Q.; Shi, Y.; Qin, W.-D.; et al. Chalcogenide phase-change material advances programmable terahertz metamaterials: a non-volatile perspective for reconfigurable intelligent surfaces. Nanophotonics 2024. [Google Scholar] [CrossRef]
- Li, X.; Sato, H.; Fujikake, H.; Chen, Q. Development of Two-dimensional Steerable Reflectarray with Liquid Crystal for Reconfigurable Intelligent Surface Application. IEEE Transactions on Antennas and Propagation 2024. [Google Scholar] [CrossRef]
- Tataria, H.; Tufvesson, F.; Edfors, O. Real-time implementation aspects of large intelligent surfaces. In ICASSP 2020-2020 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP); 2020; pp. 9170–9174. [Google Scholar] [CrossRef]
- Wang, X.; Wang, X.; Ge, J.; Liu, Z.; Ma, Y.; Li, X. Reconfigurable Intelligent Surface-Assisted Secure Communication in Cognitive Radio Systems. Energies 2024, 17, 515. [Google Scholar] [CrossRef]
- Jull, E.; Ebbeson, G. The reduction of interference from large reflecting surfaces. IEEE Transactions on Antennas and Propagation 1977, 25, 565–570. [Google Scholar] [CrossRef]
- Karagiannidis, G.K.; Sagias, N.C.; Mathiopoulos, P.T. N*Nakagami: A Novel Stochastic Model for Cascaded Fading Channels. IEEE Transactions on Communications 2007, 55, 1453–1458. [Google Scholar] [CrossRef]
- Ferreira, R.C.; Facina, M.S.P.; de Figueiredo, F.A.P.; Fraidenraich, G.; de Lima, E.R. Secrecy Analysis and Error Probability of LIS-Aided Communication Systems under Nakagami-m Fading. Entropy 2021, 23, 1284. [Google Scholar] [CrossRef]
- Gong, S.; Lu, X.; Hoang, D.T.; Niyato, D.; Shu, L.; Kim, D.I.; Liang, Y.-C. Toward Smart Wireless Communications via Intelligent Reflecting Surfaces: A Contemporary Survey. IEEE Communications Surveys & Tutorials 2020, 22, 2283–2314. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, S.; Zheng, B.; You, C.; Zhang, R. Intelligent Reflecting Surface-Aided Wireless Communications: A Tutorial. IEEE Transactions on Communications 2021, 69, 3313–3351. [Google Scholar] [CrossRef]
- Vega Sánchez, J.D.; Ramírez-Espinosa, P.; López-Martínez, F.J. Physical Layer Security of Large Reflecting Surface Aided Communications With Phase Errors. IEEE Wireless Communications Letters 2021, 10, 325–329. [Google Scholar] [CrossRef]
- Coelho Ferreira, R.; Facina, M.S.P.; de Figueiredo, F.A.P.; Fraidenraich, G.; de Lima, E.R. Large Intelligent Surfaces Communicating Through Massive MIMO Rayleigh Fading Channels. Sensors 2020, 20, 6679. [Google Scholar] [CrossRef]
- Nadeem, Q.-U.-A.; Alwazani, H.; Kammoun, A.; Chaaban, A.; Débbah, M.; Alouini, M.-S. Intelligent Reflecting Surface-Assisted Multi-User MISO Communication: Channel Estimation and Beamforming Design. IEEE Open Journal of the Communications Society 2020, 1, 661–680. [Google Scholar] [CrossRef]
- Basar, E. Transmission Through Large Intelligent Surfaces: A New Frontier in Wireless Communications. In 2019 European Conference on Networks and Communications (EuCNC); 2019; pp. 112–117. [Google Scholar] [CrossRef]
- Kendall, M.G. The advanced theory of statistics. Vols. 1. Charles Griffin and Co., Ltd., 42 Drury Lane, London, 1948.
- Coelho Ferreira, R.; Facina, M.S.P.; de Figueiredo, F.A.P.; Fraidenraich, G.; de Lima, E.R. Large Intelligent Surfaces Communicating Through Massive MIMO Rayleigh Fading Channels. Sensors 2020, 20, 6679. [Google Scholar] [CrossRef]
- Ferreira, R.C.; Facina, M.S.P.; de Figueiredo, F.A.P.; Fraidenraich, G.; de Lima, E.R. Secrecy Analysis and Error Probability of LIS-Aided Communication Systems under Nakagami-m Fading. Entropy 2021, 23, 1284. [Google Scholar] [CrossRef] [PubMed]
Short Biography of Authors
 |
Ricardo Coelho Ferreira was born in Espirito Santo, Brazil, in 1995. He received his B.S. degree in Electrical Engineering from the Federal University of Ouro Preto (UFOP), Brazil, in 2018. He completed his M.Sc. degree in Electrical Engineering at the University of Campinas (UNICAMP), Brazil, in 2021. Since then, he has been pursuing his Ph.D. degree in Electrical Engineering at the University of Campinas (UNICAMP). His research interests include digital signal processing, digital communications, random matrix theory, machine learning, and electromagnetic wave propagation. |
 |
Gustavo Fraidenraich is graduated in Electrical Engineering from the Federal University of Pernambuco (UFPE), Brazil. He received his M.Sc. and Ph.D. degrees from the State University of Campinas, UNICAMP, Brazil, in 2002 and 2006, respectively. From 2006 to 2008, he worked as a Postdoctoral Fellow at Stanford University (Star Lab Group) - USA. Currently, Dr. Fraidenraich is Associated Professor at UNICAMP - Brazil and his research interests include Multiple Antenna Systems, Cooperative systems, Radar Systems, Machine Learning applications to Communication problems, and Wireless Communications in general. He has been associated editor of the ETT journal for many years. Dr. Fraidenraich was a recipient of the FAPESP (Fundação de Amparo à Pesquisa do Estado de São Paulo) young researcher Scholarship in 2009. He has published more than 70 international journal papers and more than a hundred conference papers of the first line. He is the president of the technical board of Venturus Company, a branch of Ericsson Company. |
 |
Felipe A. P. de Figueiredo received the B.S. and M.S. degrees in telecommunications from the Instituto Nacional de Telecomunicações (INATEL), Minas Gerais, Brazil, in 2004 and 2011, respectively. He received his Ph.D. from the State University of Campinas (UNICAMP), Brazil, in 2019. He has worked in the Research and Development of telecommunications systems for over fifteen years. His research interests include digital signal processing, digital communications, mobile communications, MIMO, multicarrier modulations, FPGA development, and machine learning. |
 |
Eduardo Rodrigues de Lima received a degree in electrical engineering from the Pontifícia Universidade Católica do Rio de Janeiro, Brazil, in 1997, and the M.Sc. and Ph.D. degrees from the Universidad Politecnica de Valencia, Spain, in 2006 and 2016, respectively. He is currently a project manager at Instituto Eldorado, Brazil. His research interests include DVB-S2, IEEE 802.15.4g, circuit design, and wireless communications in general. |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).