1. Introduction
Currently there are a significant number of small and medium-sized companies that close their operations unexpectedly. The effect it causes is the decrease in sources of employment at the local and even regional level. Since their emergence, which is linked to the global economic crisis of recent decades, SMEs have contributed to reducing the consequences of unemployment and poverty, through the creation of small artisan workshops and family maquiladoras, some of which have even become developed into large companies [
1].
In fact, in Latin America they represent 99.50% [
2]. In Ecuador, there are 849,831 active companies, of this total 91.89% are microenterprises; and 7.65% are small and medium-sized companies [
3]. While it is true, startups manage to grow and become micro-businesses and some of them into large companies with national and international recognition [
4]. However, not all of them have achieved this exponential growth due to many factors that have limited their expansion, such as: Lack of administrative management, lack of financing, unskilled labor, lack of knowledge of economies of scale, market analysis, among others [
5].
This situation has caused micro, small and medium-sized companies to carry out their processes in a traditional way, not establish strategies to improve their organizational performance, and worse still use indicators that allow them to measure their management to achieve institutional objectives. The lack of a management model that allows turning strategies into action, and then measuring their results to apply improvement measures to meet the objectives in SMEs, is due to ignorance of the existence of this type of methodologies, as well as also the cost of implementation until subsequent monitoring and control. Some companies that have adopted this type of methodologies have not been able to complete the process, due to the lack of commitment on the part of management and the excessive number of indicators to control.
The main problem consists of business stagnation, due to the lack of definition of strategies to meet the objectives of this type of organizations. The vast majority of micro, small and medium-sized companies do not measure their management, they make decisions without having indicators that allow them to determine if it is correct or not and if it will bring positive results that improve organizational performance. Contributing to this problem is the absence of controls, monitoring and measurement of the results obtained, through an administrative management model defined exclusively for SMEs, with the support of ICT.
The existence of these threats, which can even remain hidden for a long period of time, generates uncertainty and puts the proper management of SMEs at risk. To reduce the inventory of risks due to threats that could cause the closure of this type of organizations, risk assessment is a primary aspect, since it allows us to determine what they are exposed to and propose immediate solutions, such as: mitigate, share, avoid and minimize risk.
Apart from the risk assessment, it is important to carry out an analysis and establish a measurement model for business management in this sector. In order to provide useful information for adequate decision making, compliance with objectives and the effectiveness of established strategies. Finally, a prototype will be established to minimize the risk of bankruptcy in SMEs.
The results are a conceptual model for risk evaluation and minimization, risk prototype, algorithm to prevent the risks of bankruptcy of companies.
It is concluded that the proposed prototype to detect threats and vulnerabilities provides an optimal security model for small and medium-sized SMEs; According to the simulation carried out, the greater the number of risks and threats, the higher the probability that a closure will occur in companies.
2. Materials and Methods
The articles, presentations and conference proceedings that were compiled served as a basis for analyzing risk prototypes and administrative management models, with the aim of establishing the most appropriate and optimal one applicable to small and medium-sized companies. For the design of the prototype, the administrative structure of small and medium-sized SMEs was considered, validated by the different administrative management models.
2.1. Materials
2.1.1. Related Works
The reasonableness of the information is crucial for the survival of SMEs, since it affirms that the figures presented are real and consistent with business reality, minimizing the threats of bankruptcy risk that endanger the continuity of the companies [
6]. When unexpected closures occur due to company bankruptcies, there is a risk of affecting other companies in their production chain, even more so when they are small and medium-sized companies [
7]. The authors in this research establish the objective of providing an exhaustive review of the current literature on risk management to minimize bankruptcies and unexpected closures of small and medium-sized companies, with one of the most important components being the evaluation of risks [
8].
They define the situational management process of production systems, based on a comprehensive scorecard, establishing indicators and selecting options for management decisions [
9]. They determined that the Balanced Scorecard allows verifying compliance with the goals that a company sets for itself when implementing its strategies [
10].
The business world provides precise information on the threats and vulnerabilities, the positive and negative effects of closing a microenterprise, such as the dismissal of people, illiquidity, non-compliance with obligations with third parties, etc. [
11]. The ISO 31000 Risk Management Standards establish a comprehensive methodology for risk management for SMEs, however, this regulation does not clearly indicate how to manage risks [
12].
Bankruptcy has been a problem and cause for concern, due to its negative effects on areas of the economy, society and politics. The purpose of this research is to develop a model to predict bankruptcy that allows predicting the probability of financial difficulties of the company, we worked with random forest regression methods and synthetic minority sampling techniques, however, the results obtained are not significant to define that the model can be adapted to any type of company [
13].
They propose how to introduce their risk adversity into decision making with risk estimation, using the best coherent risk measure derived from the risk adverse utility of the decision maker, a dynamic risk minimization problem is analyzed in the decision making process. Markov decision [
14]. However, there are many risk models for the phenomenon of bankruptcy, the authors point out that none of the existing models can be applied in a plural way, and that many of them consider the cash flow between companies, for which they present a model multi-agent bankruptcy contagion based on cash flow graph [
15].
It is also important to consider the support provided by ICTs in predicting bankruptcy; Indeed, one of the strategies to predict bankruptcy is to implement parallel computing and the use of prediction algorithms (CBR) based on historical data, which has satisfactory results, but has low performance at the time of calculation, due to the enormous historical financial data [
16]. The development of an intelligent information system for the evaluation of the bankruptcy risk of a company based on fuzzy logic and the synthesis of neural network technologies is a contribution that not only allows for a current evaluation of the bankruptcy risk of the company, but also provides the opportunity to track how it changes when one or several indicators with inadequate current values vary. The implementation of such a capability makes it possible to simulate development, select an appropriate way to normalize a level of bankruptcy risk, and make timely management decisions [
17].
The COBIT method calculates the maturity level of a process. This allows the risks and threats to be determined in order to predict whether or not there is a risk of bankruptcy from the IT environment, becoming an important factor in a financial company [
18]. The methodology known as the Chinese Wall that regulates the "Conflict of Interest" relationship, whose acronym is CIR, allows you to identify the risks and threats and the consequences that conflicts of interest entail among the stakeholders of a company [
19].
Adequate risk management focuses on determining the threats and vulnerabilities that affect companies, to establish the impact on each process [
20]. The authors present six types of risks as detailed in
Table 1 [
21].
2.2. Methods
2.2.1. List of Risks and Threats of Bankruptcy
The threats that could cause the bankruptcy of companies, especially small and medium-sized ones, have been pointed out by some authors as detailed in
Table 2.
2.2.2. Methodologies and Models of Risks and Administrative Management
Regarding the administrative management models, which allow the improvement of processes and therefore minimize the risk of company closure, the following are defined: Canvas, Six Sigma, Kanban, comprehensive dashboards, among others.
2.2.2.1. Canvas Model
It is a management tool designed by Osterwalder and Pigneur [
27] for the development of new business models that understand the company as a whole. The model is made up of nine modules that represent the key areas of the company that must be taken into account in the business model to achieve its income [
28]. The modules are: Key partnerships, key activities, value propositions, customer relationships, market segments, key resources, channels, cost structure and revenue sources.
2.2.2.2. Six Sigma Model
As for the Six Sigma model, it is a continuous business improvement strategy that seeks to find and eliminate the causes of errors, defects and delays in business processes, focusing on those aspects that are critical for the client [
29]. The 6σ strategy is based on a highly systematic and quantitative methodology aimed at improving business results with three priority areas of action: customer satisfaction, reduction of cycle time and reduction of defects [
30].
2.2.2.3. Kanban Model
Kanban, on the other hand, is a methodology that seeks to achieve a productive, organized and efficient process. This technique was created at Toyota to monitor the progress of work performed throughout a supply chain. Kanban is part of the Lean Manufacturing methodology that is based on the use of just-in-time (JIT) techniques. The main objective of Kanban is to ensure sustainable production to avoid excess final product, bottlenecks and delivery delays [
31].
2.2.2.4. Balanced Scorecard (BSC) Model or Balanced Scorecard
The Balanced Scorecard (BSC) is a powerful tool in the management of an organization. The implementation of a management model based on a balanced scorecard allows companies to define strategies and measure their management [
32]. Balanced Scorecard (BSC) created by professors Robert Kaplan and David Norton [
33]. It is a methodology that translates strategy into action, and its subsequent monitoring. Its analysis is based on four perspectives: financial, customer, internal processes, learning and growth. The balanced scorecard allows you to create strategic maps that help obtain a complete visual representation of the strategy in an organization.
For Zamora [
34] The objective of organizational performance is to change the culture, defined in its traditions, systems and outdated procedures, promoting innovative means different from those of the past, maintaining and improving what has been done well and therefore must continue. In this context, the Balanced Scorecard is a powerful management tool that helps design strategic maps, balanced scorecards, define management indicators, and above all, align business strategies. SMEs seek to achieve growth and positioning indicators for their products and services in the markets. This tool will allow them to monitor progress in meeting the proposed goals.
Having a control panel based on indicators designed based on the four perspectives of the BSC, allows the owners, managers and administrators of SMEs to have at hand a tool that helps verify if they are on the right path. In the event that there are deviations, delays, non-compliance, the control panel provides alerts to managers so that they can implement improvement actions immediately. Thus contributing to organizational development, leading them to the objectives they want to achieve, based on an evaluation of the organization that considers its structure, activities, purpose, budget and resources it has to carry out its function.
The Balanced Scorecard and the Canvas model can be linked as complementary tools for entrepreneurs. The first develops objectives and operational measures in four main perspectives to achieve the mission and strategy. The second has meant a revolution in the generation of business models, establishing nine sections that reflect its logic [
35].
2.2.2.5. COSO Report
This report addresses the need for organizations to improve their risk management approach to meet the demands of an evolving business environment. Align performance and risk management to understand the impact of risk on performance.
The focus of the report is based on five aspects:
Governance and Culture: Governance is responsible for managing institutional risks and establishing responsibilities. Culture refers to ethical values, desired behaviors and understanding of risk.
Strategy and goal setting: business risk management, strategy and goals (strategic planning)
Performance: Risks that may impact the achievement of the strategy and the business
Review: When reviewing entity performance, an organization can consider how well enterprise risk management components are working over time
Information, communication and reporting: It is a continuous process of obtaining and exchanging the necessary information, from internal and external sources [
36].
2.2.2.6. Risk Matrix
To The risk matrix is one of the methodologies most used by companies to measure the risk levels to which they are exposed. For this purpose, elements such as: Impact and Probability are used [
36], considering the ranges established in detail in
Table 3.
The methodology also establishes the probabilities of a risk occurring, according to
Table 4.
Likewise, the following importance criteria for a risk were used.
Table 5 contains the importance index that risks can have.
To determine the risk value in the indicated matrices, the following formula will be used:
Where:
PO = Probability of occurrence
I = Impact
VR = Risk Level
With the matrices and the indicated formula,
Table 6 was prepared, which establishes the risk level of each identified risk factor.
In the example cited, the table shows that if there are values that do not exceed 5 points, there is no risk, up to 10 points generate a relatively low risk and those that exceed 20 points are extremely high and must be monitored.
2.2.3. Methodology
2.2.3.1. Conceptual Model
The references [
31,
32,
36] served as a basis for the development of the conceptual model of the prototype of bankruptcy risks in SMEs.
2.2.3.2. Security Prototype
For the construction of the prototype to prevent risks and threats, the following references were taken into account: Phases to obtain the value of a risk [
38], Risk Categories [
39].
2.2.3.3. Algorithm
The references cited below were used in the construction of the algorithm [
13,
14,
18,
22,
23], were taken into account; for this purpose, the phases of the bankruptcy risk prototype were defined; At the end a formula will be defined to verify the stability of the algorithm.
2.2.3.4. Construction of the Formula
The variables used to construct the formula were the number of risks and the companies' mitigation capacity. For this purpose, security level tables were used to improve the prototype.
2.2.3.5. Simulations
The simulations help determine if there is a probability that a problem will occur, for which five different scenarios were analyzed.
3. Results
The objective of this research is to reduce the bankruptcy risks of small and medium-sized companies. To explain the results, they have been divided into four parts.
Conceptual model to minimize risks
Risk control prototype
Algorithm to prevent the risks of bankruptcy and closure of small and medium-sized companies.
Analysis and evaluation of risks.
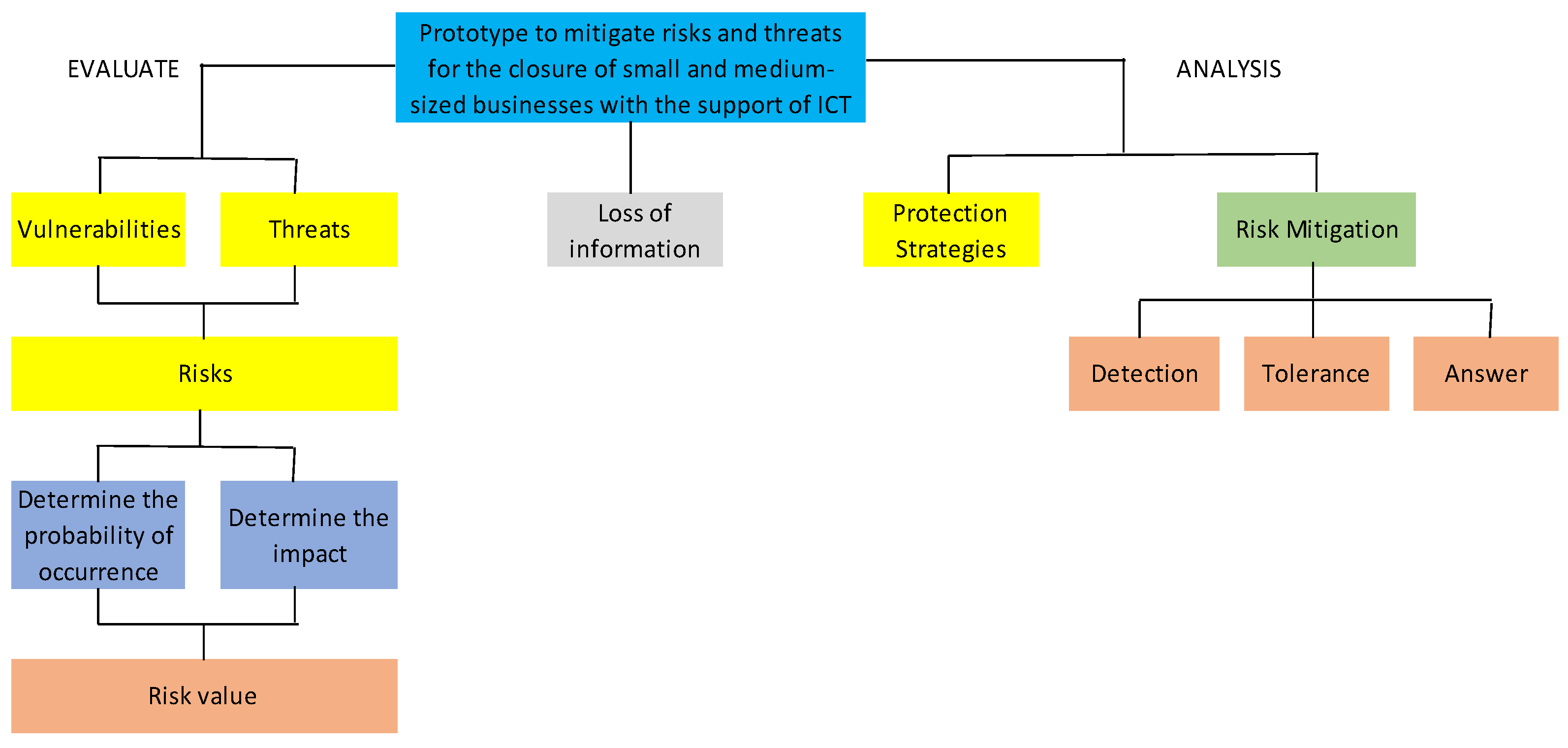
3.1. Conceptual Model to Evaluate and Minimize Risks
The proposed model allows minimizing the availability of threats and vulnerabilities of small and medium-sized companies, in order to determine what they are exposed to in order to propose immediate solutions, such as: mitigate, share, avoid and eliminate the risk. The model is detailed in
Figure 1 below.
The model presented in
Figure 1 allows the following activities to be carried out: Evaluate the vulnerabilities and threats that may affect organizational performance; Determine the actual risk mitigation capacity; Determine the probability of impact on organizational performance; And establish the value of the risks, for this purpose, the probability of occurrence will be multiplied by the impact of each risk [
37].
Below is the formula used to calculate the prototype of the conceptual model
Where:
X = Average of mitigation indicators
D = Mitigation Detection (range value 0 - 10)
T = Mitigation Tolerance (range value 0 - 10)
R = Mitigation Response (range value 0 - 10)
Where:
CM = Actual Mitigation Capacity
CME = Estimated Mitigation Capacity
Where:
P (R) % = Probability that risks affect companies
R = Number of Risks
Where:
EP = Mitigation Efficiency of the prototype, which will be verified in
Table 7.
Example:
If we have a company that presents a mitigation (Detection = 10, Tolerance = 8, Response = 9), in which 9 risks were found. If we apply formulas 2, 3, 4 and 5 we have:
According to
Table 5, the prototype for the scenario presented in the example shows that it is optimal.
3.2. Risks Prototype
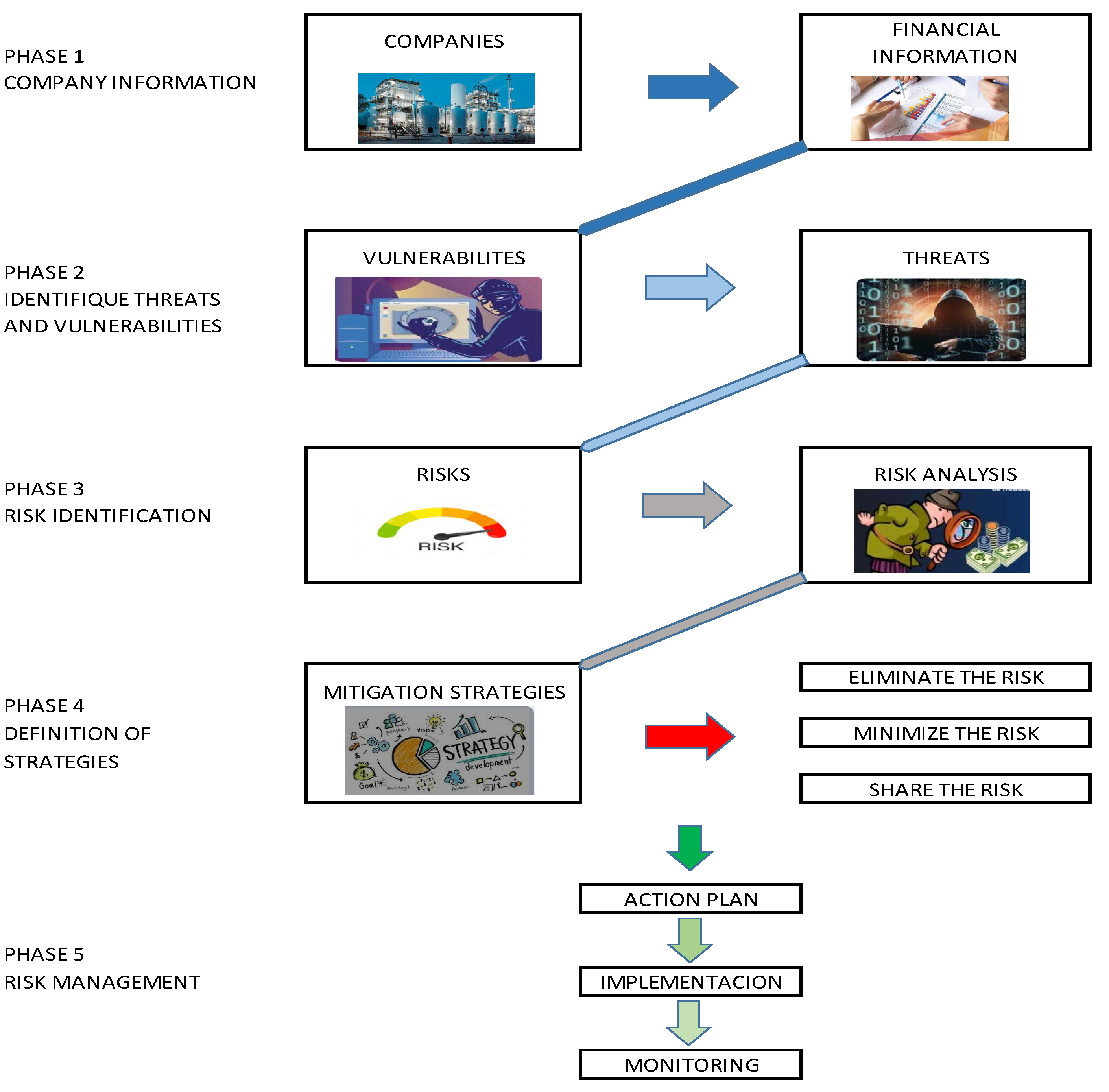
The prototype proposes to minimize the risks that can cause bankruptcy in companies, by identifying the vulnerabilities and threats that erroneous financial information can generate. Select mitigation strategies in order to design and implement an action plan, until its monitoring.
Mitigation strategies are important for risk mitigation, since they can be shared, minimized and eliminated.
The proposed prototype is the following:
Figure 2 shows the five phases of the prototype
First phase:
In this phase, the administrative and financial information of the companies, employees, clients, suppliers, investors, etc. is detailed
Second stage:
It allows identifying vulnerabilities that cause risks that threaten the survival of small and medium-sized businesses:
Third phase:
Once the risks have been identified, they must be analyzed and classified according to their level of impact and probability, in order to implement risk mitigation strategies.
Fourth phase:
This stage allows risks to be mitigated, for which risk response categories are established, such as: eliminate, minimize and share the risk.
Fifth Phase:
In the final phase, an action plan must be made that will contain mitigation strategies. Subsequently, it will be monitored to make corrections and suggestions.
Figure 2.
Risk Prototype.
Figure 2.
Risk Prototype.
3.3. Prototype Flowchart
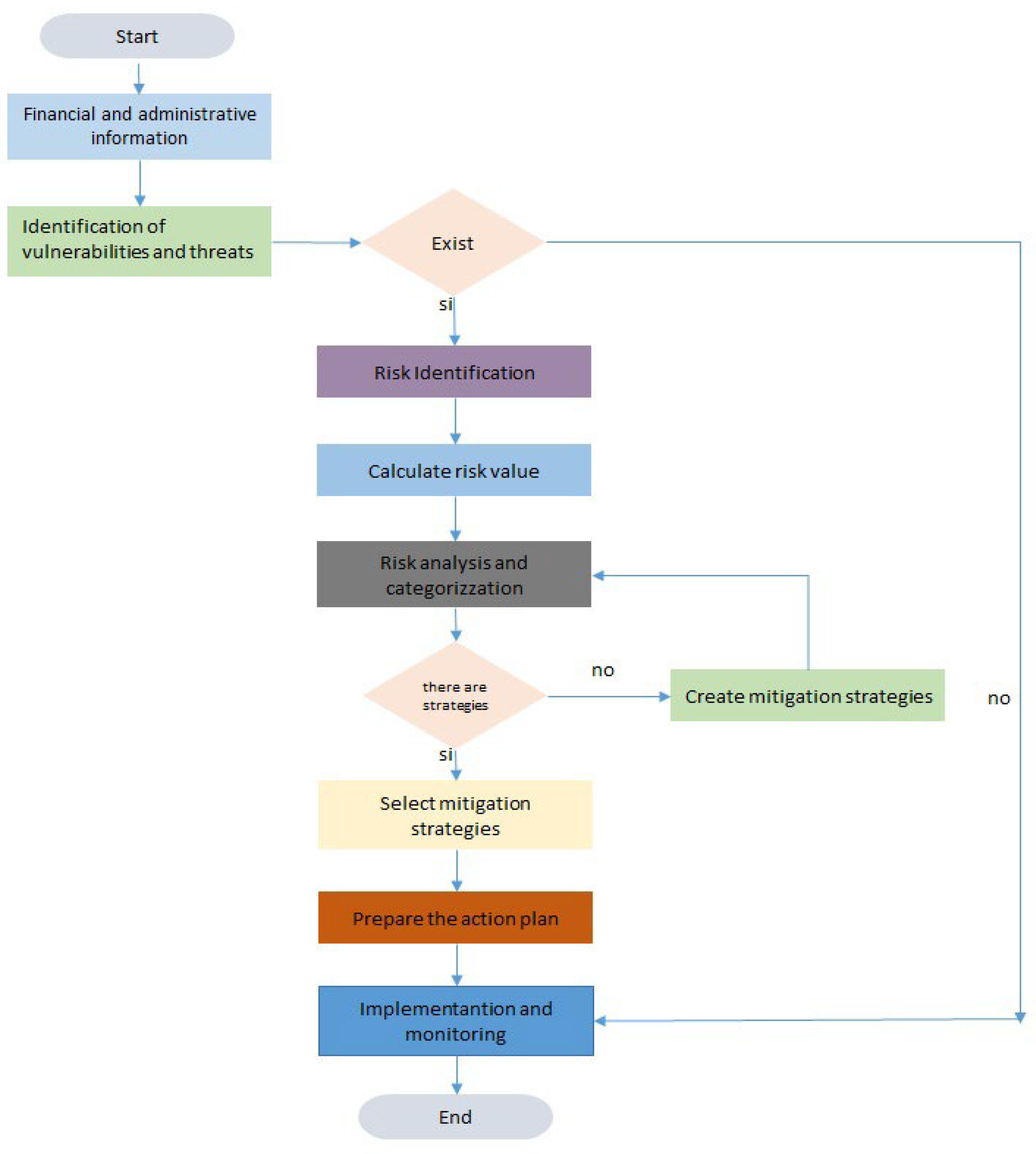
The algorithm and flowchart of the proposed methodology establish the activities that companies must execute to mitigate vulnerabilities, threats and risks to prevent company closure.
Figure 3 describes the algorithm in a flow chart, and what its phases are.
Description:
Phase 1.- Administrative and Financial Information: An administrative and financial diagnosis must be carried out to determine which aspects may be compromised if any negative event occurs that affects the survival of SMEs.
Phase 2.- Vulnerabilities and threats: Once they are identified, the existing risks in SMEs can be determined. If the prototype determines that they do not exist, the process ends.
Phase 3.- Risks measurement: To carry out this phase it is necessary to determine the value of the risks. Which is calculated by multiplying the probability of occurrence by the impact it can generate. Then they must be categorized, giving importance to those that can cause serious consequences that require inmediate attention.
Phase 4.- Mitigate risks: Risks are analyzed to design mitigation strategies, which can be: Eliminate, minimize or share. If there are no mitigation strategies, the risks must be created and reanalyzed.
Phase 5.- Risk Management: In this phase, strategies must be selected, described, executed and monitored based on the action plan.
Next, the respective algorithm is defined.
Phase 1: Administrative and Financial Information. - Financial and non-financial management indicators are detailed.
Phase 2: Identification of threats and vulnerabilities. - Vulnerabilities and threats are described. If they do not exist, the process will be terminated.
Phase 3: Risk identification and mitigation. - The risks are categorized and the value of each one is calculated.
Phase 4: Risk Management. - With the selected strategies, an action plan must be created, which will be implemented and monitored.
Figure 3.
Prototype algorithm expressed in a flow chart.
Figure 3.
Prototype algorithm expressed in a flow chart.
Once the prototype has been created, it must be demonstrated that it is stable; for this purpose, the formulas mentioned above will be used.
Where:
R = Number of risk
R * = Number of high and critical risks
Po = Security level
CM = Mitigation capacity
s = Algorithm stability percentage [
37].
Example:
A company that has the following mitigation indicators: (Detection = 9, Tolerance = 8 Response = 7) in which 8 risks were found, of which 4 are high and critical levels:
The results are the following:
1- 4
P0 = 8
0.8
P0 = 0.6250
Therefore, the safety percentage is as follows:
S = 0.6250 (100%)
S = 62.50%
The security percentage is 69.44%, according to the ranges established in Table 11, the algorithm is optimal to implement it.
Table 8.
Security algorithm percentage [
37].
Table 8.
Security algorithm percentage [
37].
| Scale |
Assessment |
Safe Level |
| 76-100 |
Excellent rating |
Excellent |
51-75
25-50 |
Optimal valuation
Regular Assessment |
Optimun
Regular |
| 0-24 |
Poor valuation |
Deficient |
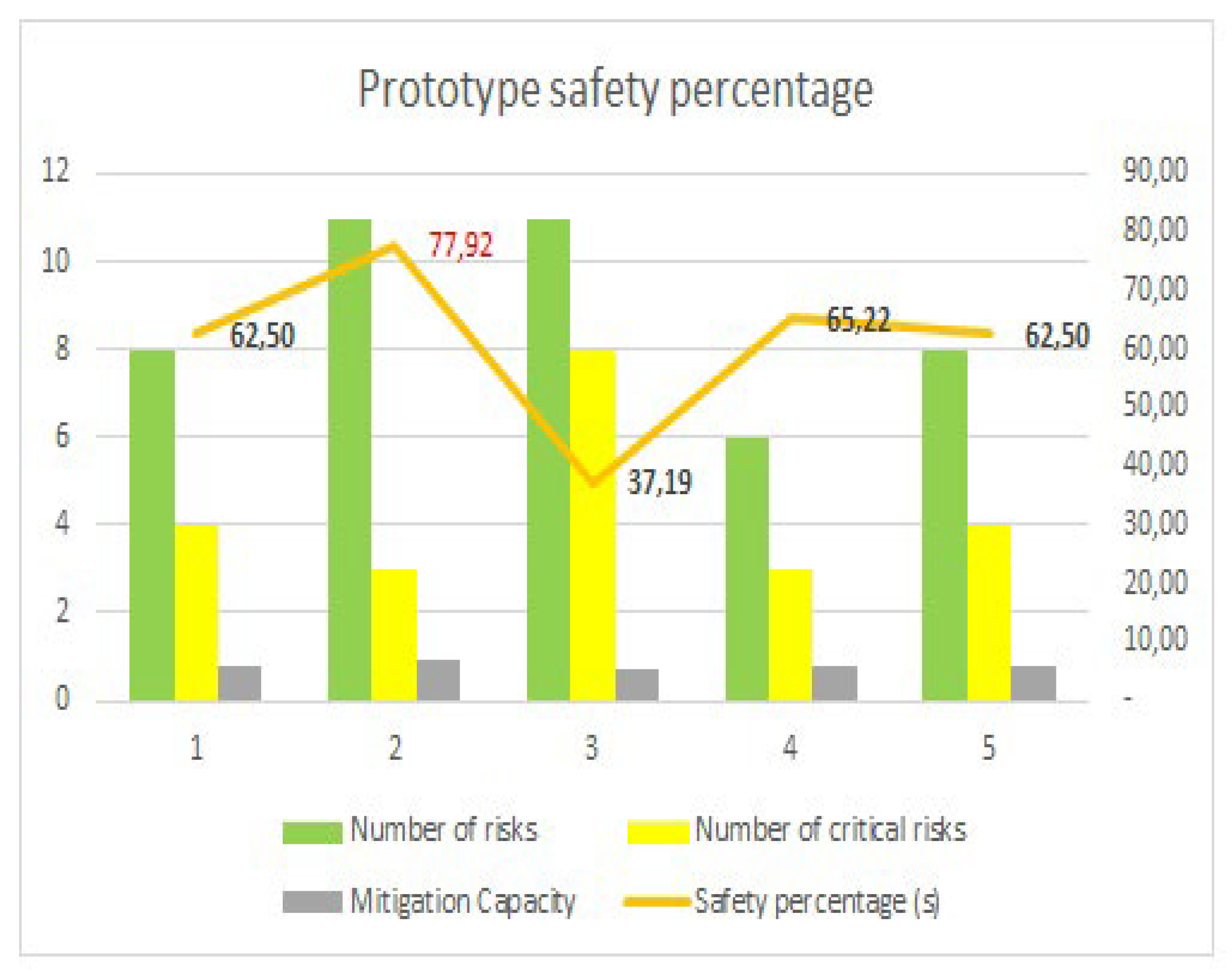
In order to obtain more security in the algorithm, five scenarios were carried out, where values related to the number of identified risks, the number of high and significant risks and the mitigation capacity were modified according to the data presented in the table.
Table 9.
Percentage of security in five scenarios.
Table 9.
Percentage of security in five scenarios.
| Values |
Scenario 1 |
Scenario 2 |
Scenario 3 |
Scenario 4 |
Scenario 5 |
| Detection |
9 |
10 |
8 |
7 |
9 |
| Tolerance |
8 |
9 |
7 |
8 |
8 |
| Answer |
7 |
9 |
7 |
8 |
7 |
| Number of risks |
8 |
11 |
11 |
6 |
8 |
| Number of critical risks |
4 |
3 |
8 |
3 |
4 |
| Mitigation Capacity |
0,80 |
0,93 |
0,73 |
0,77 |
0,80 |
| Security Level (Po) |
0,63 |
0,78 |
0,37 |
0,65 |
0,63 |
| Safety percentage (s) |
62,50 |
77,92 |
37,19 |
65,22 |
62,50 |
Figure 4.
Percentage of security in five scenarios.
Figure 4.
Percentage of security in five scenarios.
As can be seen, scenario 2 obtained the highest percentage of security.
3.4. Determination of the Formula to Detect the Probability of Closing as SME
With the following formula, the probability of closure problems occurring in companies can be determined, taking into account the number of risks and threats.
Where:
P (n) = Probability of a problem occurring in the company
n = Number of threats
#R = Number of system risks [
37]
For this purpose, a simulation was carried out of a problem occurring that ends with the closure of a company, considering a scenario of 9 risks and 12 threats. By replacing in formula (12) the result was a percentage of 7.27% of occurrence that could cause a closure of the company.
3.5. Risk Analysis and Evaluation
After having analyzed the risk and administrative management methodologies and models, it was determined that the identification and evaluation of risks is the most critical process within an organization. Indeed, the Coso report, the risk matrix and the characterization of risks, allow prioritizing the impact of risks, to determine an indicator of threats to companies and the damage they may cause.
The ability of companies to mitigate risks is compromised by compliance with various parameters, measured through quantitative scales and for this purpose, formulas were used to determine if the prototype is stable and will allow minimizing risks and threats that compromise continuity. Of companies and be able to determine actions that mitigate vulnerabilities, threats and risks.
4. Discussion
As a result of the analysis, it was established that there are several risk and administrative management methodologies and models. In the investigation, a model based on the methodology of the Coso report and the risk matrix was applied. It is important to note that the prototype does not determine the implementation values, this will depend on each organization.
In the article [
13] Random Forest Regression methods and synthetic minority sampling techniques were used to develop a model to predict bankruptcy that allows predicting the probability of financial difficulties of the company. In the article [
14] a dynamic risk minimization problem in the Markov decision process is analyzed to introduce its risk adversity in decision making with risk estimation. A multi-agent bankruptcy contagion model based on the cash flow graph is presented in paper [
15]. The support provided by ICTs in predicting bankruptcy is important; In the article [
16], parallel computing and the use of prediction algorithms (CBR) are implemented to predict bankruptcy.
According to the administrative and risk management models, risk management is essential because it allows us to know what the main threats and vulnerabilities are that can cause the closure of small and medium-sized businesses.
As a result of the simulations, a security percentage of 77.92% was established, which means that the greater the number of risks and threats, the greater the probability that a small and medium-sized company will close.
Companies must apply risk prototypes to mitigate vulnerabilities, threats that can cause the closure of small and medium-sized companies with high bankruptcy rates.
5. Future Work and Conclusions
In the future, research should be carried out to define a methodology to diagnose small companies and formulate strategies to avoid company bankruptcy.
It was concluded that the proposed prototype to detect threats and vulnerabilities provides an optimal security model for small and medium-sized companies; As a result of the simulations, a security percentage of 77.92% was established, which means that the greater the number of risks and threats, the greater the probability that a small and medium-sized company will close.
The results obtained from the simulation demonstrate that companies must have a good mitigation capacity for the efficiency percentage to be high.
The present investigation allowed us to propose a conceptual map that shows the mitigation efficiency formula of the prototype. Determining that each phase helps avoid the loss of information to minimize the threats detected. On the other hand, the algorithm was established to verify that the protocol is optimal against the risks obtained in small and medium-sized companies, with the proposed formula it was possible to verify the mitigation efficiency of the prototype
Finally, the simulation showed the possibilities of a company closure occurring given the number of threats and risks.
Acknowledgments
The authors thank the, Programa del Doctorado en Tecnologías de Información de la Universidad de Guadalajara de México (UDG), Universidad de las Fuerzas Armadas (ESPE), Universidad Católica de Santiago de Guayaquil (UCSG), Economy Faculty, Politécnico do Porto (ISCAP) - Portugal, Instituto Tecnológico Superior Rumiñahui (ISTER), Research Group: Information and Communications Technologies for Scientific and Technological Development "TICDESTC" and the Secretaría de Educación Superior, Ciencia, Tecnología e Innovación (Senescyt).
References
- R. Rodríguez-Mendoza and V. Aviles-Sotomayor, “Las PYMES en Ecuador. Un análisis necesario,” 593 Digit. Publ. CEIT, vol. 5–1, no. 5, pp. 191–200, 2020. [CrossRef]
- OECD/CAF, “Índice de Políticas PYME: América Latina y el Caribe 2019 Políticas para PYMEs competitivas en la Alianza del Pacífico y países participantes de América del Sur,” 2019. [Online]. Available: https://www.oecd.org/latin-america/Indice-Politicas-PYME-LAC-Mensajes-Principales.pdf.
- Instituto Nacional de Estadística y Censos, “Estadística de las empresas,” pp. 3–17, 2021.
- G. S. Marco Dini, MIPYMES en América Latina Un frágil desempeño y nuevos desafíos para las políticas de fomento. 2018. [Online]. Available: https://repositorio.cepal.org/bitstream/handle/11362/44148/1/S1800707_es.pdf.
- D. De La, O. Cordero, and R. Monge-González, “Factores que influyen en el desempeño de las PYMEs: una perspectiva cualitativa de los empresarios costarricenses Factors that influence the SMEs performance: a qualitative perspective of Costa Rican entrepreneurs,” Ran, vol. 4, no. 2, p. 2019, 2019.
- Maciejewska, “Risk factors for an audit process in the developed IT environment: The concept of research based on experiences from small audit practices in Poland,” in Iberian Conference on Information Systems and Technologies, CISTI, 2014, pp. 1–4. [CrossRef]
- D. I. Roque and A. Caicedo Carrero, “Detección de insolvencia financiera mediante el modelo Z-Altman en empresas colombianas no cotizantes durante el periodo 2016-2019,” Contab. y Negocios, vol. 17, no. 33, pp. 167–192, 2022. [CrossRef]
- M. H. Zahedi, A. R. Kashanaki, and E. Farahani, “Risk management framework in Agile software development methodology,” Int. J. Electr. Comput. Eng., vol. 13, no. 4, pp. 4379–4387, 2023. [CrossRef]
- Khanova, O. Protalinsky, I. Bondareva, and Y. Khanova, “Situational management of production systems based on a balanced scorecard,” in 2020 International Conference Engineering and Telecommunication, En and T 2020, 2020, pp. 1–5. [CrossRef]
- T. B. Novikova, L. Z. Davletkireeva, and E. V. Romanova, “Balanced Scorecard Modeling: An Effective Management Tool,” in 2020 International Multi-Conference on Industrial Engineering and Modern Technologies, FarEastCon 2020, 2020, pp. 0–5. [CrossRef]
- M. del R. Fátima-Robles-Robles, M. de los Á. Romero-Espinoza, and N. G. Romero Vivar, “Efectos económicos y operativos preliminares del COVID-19 en las Mipymes de Sonora, México Preliminary economic and operational effects of COVID-19 on MSMEs in Sonora, Mexico,” Econ. Soc. y Territ., vol. XXI, no. 67, pp. 631–655, 2021.
- International Organization for Standardization, Norma Internacional ISO 31000. 2018, p. 25. [Online]. Available: https://auto-q-consulting.com.mx/Muestra24.IATF.2020/Norma.ISO.31000.2018.Espanol.pdf.
- Tran Duc Quynh; Tran thi Lan Phuong, “Improving the bankruptcy prediction by combining some classification models,” in 12th International Conference on Knowledge and Systems Engineering (KSE), 2020, pp. 263–268.
- Y. Yoshida, “Markov Decision Processes with Coherent Risk Measures: Risk Aversity in Asset Management,” in Proceedings - 2019 IEEE Conference on Cognitive and Computational Aspects of Situation Management, CogSIMA 2019, 2019, no. i, pp. 147–151. [CrossRef]
- J. Zhang, “Structured Multi-Agent-Based Model for Bankruptcy Contagion With Cash Flow,” vol. 8, 2020. [CrossRef]
- D. S. Rahayu, “Parallel Implementation in Case-based Reasoning Bankruptcy Prediction System”.
- E. V. Telipenko and S. P. Sopova, “Software for bankruptcy risk assessment of the enterprise,” in RPC 2018 - Proceedings of the 3rd Russian-Pacific Conference on Computer Technology and Applications, 2018, pp. 1–4. [CrossRef]
- R. Rooswati and N. Legowo, “Evaluation of IT Project Management Governance Using Cobit 5 Framework in Financing Company,” in Proceedings of 2018 International Conference on Information Management and Technology, ICIMTech 2018, 2018, no. September, pp. 81–85. [CrossRef]
- T. Y. T. Y. Lin, “Chinese wall security policies information flows in business cloud,” in Proceedings - 2015 IEEE International Conference on Big Data, IEEE Big Data 2015, 2015, pp. 1603–1607. [CrossRef]
- H. Fabric, “A Hyperledger-based P2P Energy Trading Scheme using Cloud Computing with Low Capabillity Devices,” 2019, pp. 2019–2021. [CrossRef]
- J. S. Suroso, A. Januanto, and A. Retnowardhani, “Risk Management of Debtor Information System at Bank XYZ Using OCTAVE Allegro Method,” in 2019 International Conference on Electrical Engineering and Informatics (ICEEI), 2019, vol. 2019-July, pp. 261–265. [CrossRef]
- W. Altamirano Salazar, “La Contabilidad Creativa en el Gobierno Corporativo de las empresas,” Ciencias Adm., no. 12, p. 027, 2017. [CrossRef]
- Elizabeth and G. Santiago, “Riesgo de fraude y el desempeño financiero en las cooperativas de ahorro y crédito del Ecuador Fraud risk and financial perfomamnce in savings and credit cooperatives in Ecuador Resumen,” pp. 5206–5216, 2023.
- J. Wu, S. Member, K. Lin, D. A. N. Lin, and G. Student, “Financial Crimes in Web3-Empowered Metaverse : Taxonomy , Countermeasures ,” IEEE Open J. Comput. Soc., vol. 4, no. February, pp. 37–49, 2023. [CrossRef]
- J. Yao, J. Zhang, and L. Wang, “A financial statement fraud detection model based on hybrid data mining methods,” in 2018 International Conference on Artificial Intelligence and Big Data, ICAIBD 2018, 2018, pp. 57–61. [CrossRef]
- C. Tai, “Identifying Money Laundering Accounts,” 2019 Int. Conf. Syst. Sci. Eng., pp. 379–382, 2019.
- Osterwalder and Y. Pigneur, “Esfuerzan Por Desafiar Los Modelos Comerciales Pasados De Moda Y Escrito Por,” 2010. [Online]. Available: https://www.camarabaq.org.co/wp-content/uploads/2020/11/Generacion-de-Modelos-de-Negocio-2010.en_.es_.pdf.
- E. G. Cuzco Simbaña, J. C. Erazo Álvarez, C. I. Narváez Zurita, and G. I. Andrade Mena, “El modelo Canvas como fundamento del plan de negocios para empresas de servicios de software de la ciudad de Cuenca,” Cienciamatria, vol. 5, no. 1, pp. 781–804, 2019. [CrossRef]
- J. Malpartida, D. Olmos, S. Quiñones, M. J. Ledesma, G. Garcia Curo, and J. R. Diaz Dumont, “Six Sigma process improvement strategy applied to the textile,” Alpha Centauri, vol. 2, no. 3, pp. 72–90, 2021.
- J. F. Ramírez Pérez, V. G. López Torres, S. A. Hernández Castillo, and M. Morejón Valdés, “Lean Six Sigma E Industria 4.0, Una Revisión Desde La Administración De Operaciones Para La Mejora Continua De Las Organizaciones,” UNESUM-Ciencias. Rev. Científica Multidiscip. ISSN 2602-8166, vol. 5, no. 4, pp. 151–168, 2021. [CrossRef]
- L. Castellano Lendínez, “Kanban. Metodología para aumentar la eficiencia de los procesos. 3C Tecnología. Glosas de innovación aplicadas a la pyme,” 3C Tecnol. Glosas innovación Apl. a la pyme, vol. 8, no. 1, pp. 30–41, 2019.
- G. V. Carvajal Zambrano, A. C. Chávez López, M. L. Velásquez Vera, and D. Nogueira Rivera, “Balanced Scorecard: A look from its evolution,” Rev. Venez. Gerenc., vol. 27, no. 97, pp. 224–256, 2022. [CrossRef]
- Kaplan S.Robert.; and David. P. Nurton, BALANCED SCORECARD The balanced scorecard translating strategy into action [1996].pdf. 2000.
- M. Zamora, “El Desarrollo Organizacional Como Generador De Un Cambio Significativo En Las Organizaciones De La Sociedad Civil.,” Rev. Extrem. Ciencias Soc., vol. 10, pp. 87–109, 2018.
- H. Añaguaya, “Integración del Cuadro de Mando Integral (CMI) con el Modelo Canvas como Estrategia de Gestión Empresarial,” INF-FCPN-PGI Rev. PGI, vol. 1, no. 8, pp. 135–138, 2021, [sOnline]. Available: https://ojs.umsa.bo/ojs/index.php/inf_fcpn_pgi/article/view/70.
- Committee_of_Sponsoring_Organizations_of_Treadway_Commission, Enterprise Risk Management Integrating with Strategy and Performance, no. June. 2017.
- S. M. T. Toapanta et al., “Prototype to Mitigate the Risks, Vulnerabilities and Threats of Information to Ensure Data Integrity,” Adv. Sci. Technol. Eng. Syst. J., vol. 7, no. 6, pp. 139–150, 2022. [CrossRef]
- L. Huang, Y. Shen, G. Zhang, and H. Luo, “Information system security risk assessment based on multidimensional cloud model and the entropy theory,” in ICEIEC 2015 - Proceedings of 2015 IEEE 5th International Conference on Electronics Information and Emergency Communication, 2015, pp. 11–15. [CrossRef]
- Alsalamah, “Security risk management in online system,” in Proceedings - 2017 5th International Conference on Applied Computing and Information Technology, 2017 4th International Conference on Computational Science/Intelligence and Applied Informatics and 2017 1st International Conference on Big Data, Cloud Compu, 2017, pp. 119–124. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).