Submitted:
03 May 2024
Posted:
06 May 2024
You are already at the latest version
Abstract
Keywords:
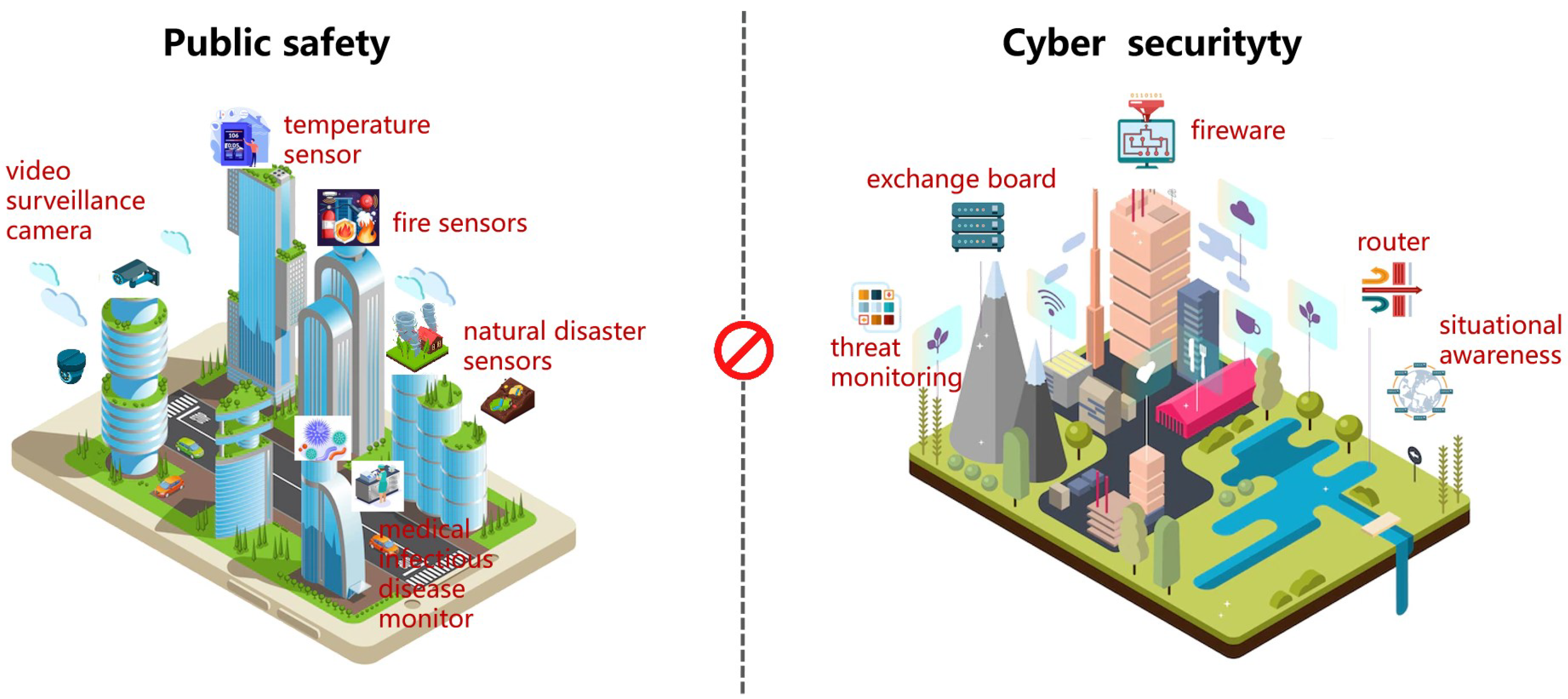
1. Introduction
2. Models and Methods
2.1. The Basic Principles of CPCSIS
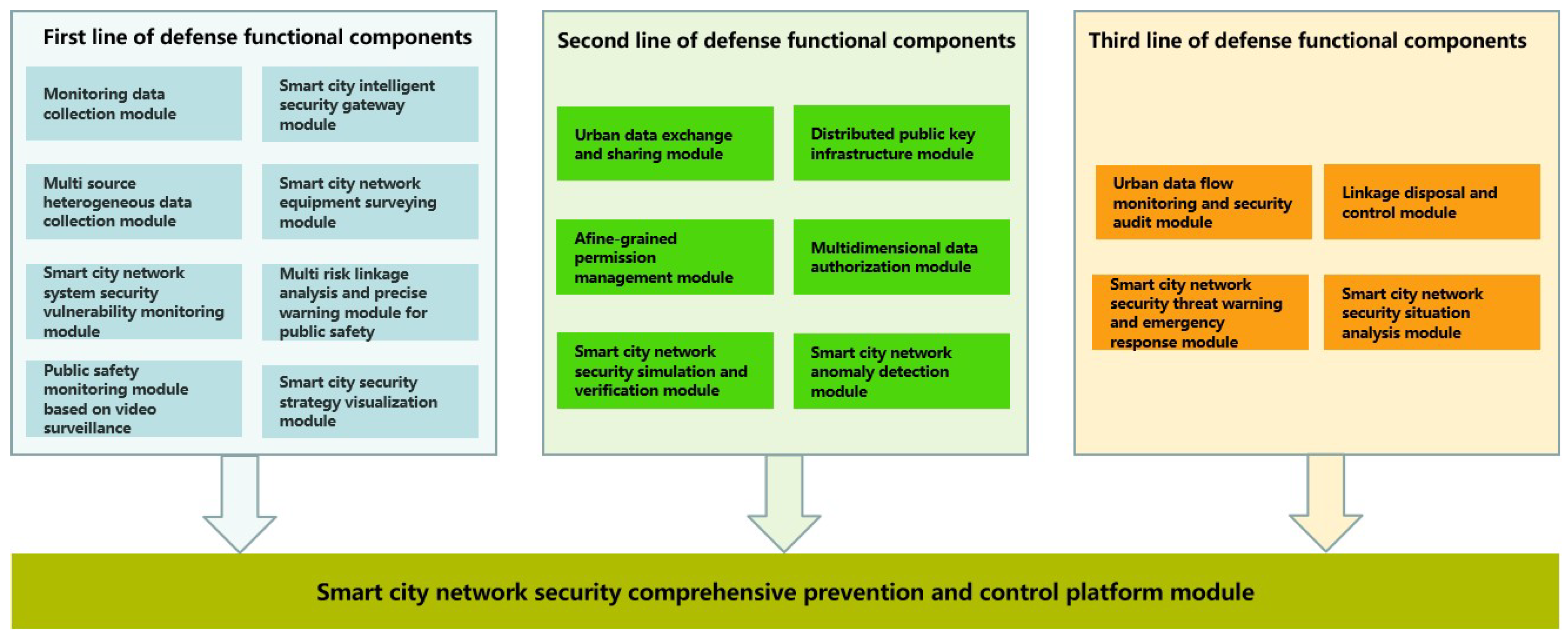
2.2. The Basic Components of CPCSIS
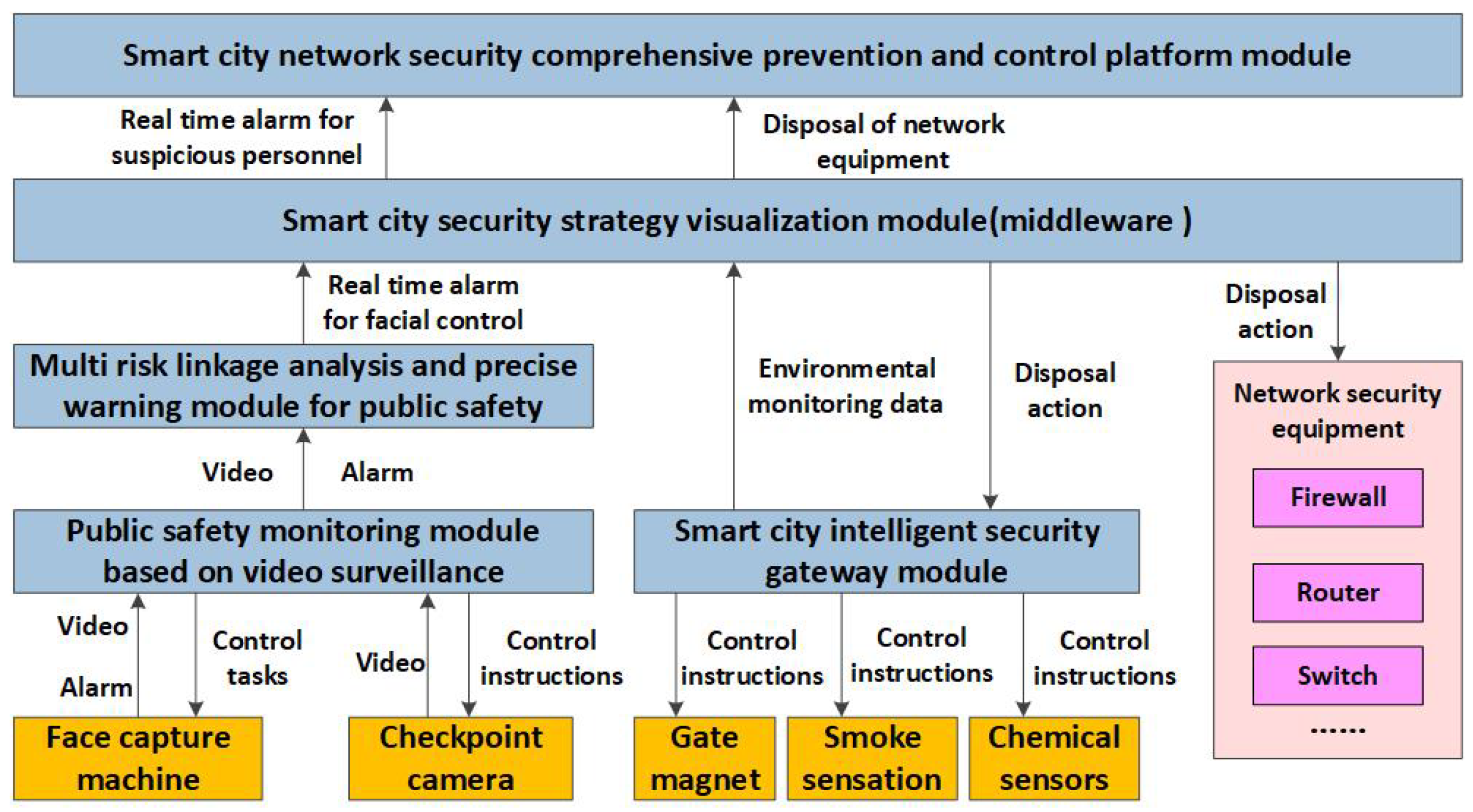
2.3. The Collaborative Protection Method of CPCSIS
| Algorithm 1 Part of the Smart City Network Space Security Threat Level |
|
3. Experiment and Analysis of Models
3.1. Experimental Purpose
3.2. Experimentation
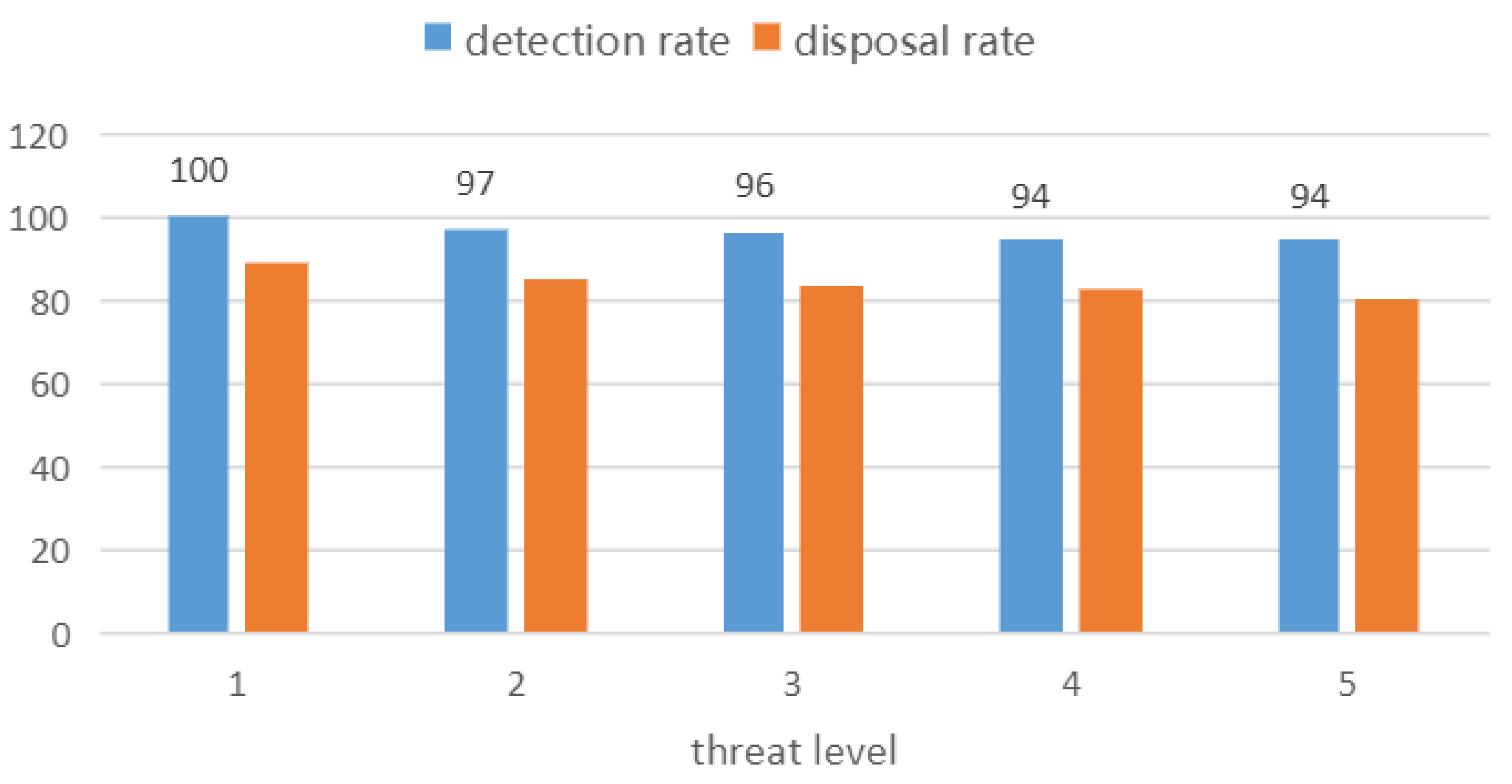
3.3. Experimental Result
4. Discussion and Conclusions
Acknowledgments
References
- National Cybersecurity Strategy 2023. White House. https://www.whitehouse.gov/wp-content/uploads/ 2023/03/National-Cybersecurity-Strategy-2023.pdf(February 21, 2024).
- Elena Lisova, Irfan Sljivo, and Aida Čaušević. Safety and Security Co-Analyses: A Systematic Literature Review. IEEE Systems Journal 2019, 1, 2189–2200.
- G.Suciu, I. Hussain, G. Iordache, C. Beceanu, R. A. Kecs and M. Safety and Security of Citizens in Smart Cities. 2021 20th RoEduNet Conference: Networking in Education and Research (RoEduNet), Iasi, Romania, November 4, 2021.
- Z. Liu, Q. Wang, Y. Li, and Y. Zhao. “CMSS: Collaborative Modeling of Safety and Security Requirements for Network Protocols," IEEE Intl Conf on Parallel and Distributed Processing with Applications, Big Data and Cloud Computing, Sustainable Computing and Communications, Social Computing and Networking (ISPA/BDCloud/SocialCom/SustainCom), 2021.
- J. Fan, K. Hu, Z. Chen, and J. Li. Research on Information Sharing and Fusion of Public Security Information Under Big Data Environment. Fresenius Environmental Building 2022, 31, 6115-6123.
- W. Dimitrov, K. Spasov, I. Trenchev, S. Syarova, “Complexity Assessment of Research Space for Smart City Cybersecurity, " IFAC Workshop on Control for Smart Cities (CSC), 2022.
- S. Sengan, V. Subramaniyaswamy, S.K. Nair, et al., “Enhancing cyber–physical systems with hybrid smart city cyber security architecture for secure public data-smart network,"Future generation computer systems 2020, 112, 724-737. [CrossRef]
- W. Fang, N. Cui, W. Chen, et al., “A trust-based security system for data collection in smart city, " IEEE Transactions on Industrial Informatics, 2020, 17, 4131-4140. [CrossRef]
- R. Paul, N. Ghosh, S. Sau, et al. “Blockchain based secure smart city architecture using low resource IoTs," Computer Networks 2021, 196, 198-207. [CrossRef]
- E. Farzadnia, H. Shirazi, and A. Nowroozi, “A novel sophisticated hybrid method for intrusion detection using the artificial immune system, " Journal of Information Security and Applications, 2021, 58, 199-223. [CrossRef]
- D.J. Prathyusha, G. Kannayaram, “A cognitive mechanism for mitigating DDoS attacks using the artificial immune system in a cloud environment, " Evoluationary Intelligence, 2021, 14, 607-618. [CrossRef]
- N.M. Grigorieva, S.A. Petrenko, “Biological Metaphor for Cyber Immunity. 2023 XXVI International Conference on Soft Computing and Measurements (SCM)," 2023.
- L.E. Jim, N. Islam, M.A. Gregory, “Enhanced MANET security using artificial immune system based danger theory to detect selfish nodes, " Computers & Security 2022, 113, 67-69. [CrossRef]
- J. He, T. Li, B. Li, X. Lan, Z. Li and Y. Wang, “An immune-based risk assessment method for digital virtual assets, " Computers & Security 2021, 102, 102-134. [CrossRef]
- R. Fotohi, “Securing of Unmanned Aerial Systems (UAS) against security threats using human immune system," Reliability Engineering & Sysstem Safety 2019, 193, 237-253. [CrossRef]
- B. Yang, “Network Layer Security Detection Model of Internet of Things Based on Immune System, " Annual International Conference on Information System and Artificial Intelligence (ISAI), 2020.
- H. He, Z. Zhu and J. Zhang, “An immune system-based defence system of robot network security, " Journal of Physics: Conference Series 2021, 1873, 012082. [CrossRef]
- S. Kodati, N Sreekanth, K.S.R.K. Sarma, P. Chandra Sekhar Reddy, Archana Saxena and B. Palajonna Narasaiah. Ensemble Framework of Artificial immune system based on Network Intrusion Detection System for Network Security Sustainability, International Conference on Materials Processing and Characterization (ICMPC 2023), Newcastle upon Tyne, UK, FEB 15 2024.
- R. V. Melo, D.J.M., Douglas, K. Diego, D.B. Alessandra, M.F. Mauricio, “ISM-AC: an immune security model based on alert correlation and software-defined networking," International Journal of Information Security 2022, 21, 191-205. [CrossRef]
- B.S. Carrie, L. Debra, “New public management and the extension of police control: community safety and security networks in Canada, " POLICING & SOCIETY 2019, 29, 566-578. [CrossRef]
- K. Naveed, H. Wu. Celosia, “An Immune-Inspired Anomaly Detection Framework for IoT Devices, "IEEE Conference on Local Computer Networks (LCN), 2020.
- (ADD-12) Popa Tache, C.E., & Săraru, C.-S. (2023). Lawfare, Between its (Un)Limits and Transdisciplinarity. Precedente Revista Jurídica, 23, 37-66. [CrossRef]
- HWolf-Ostermann, “The role of collagen in immune health. NutraCos 2021, 20, 8-10.
- S. Robert, K. Jolanta, C. Maciej, “Mechanisms of evasion of the innate immune system response by human coronaviruses, " Alergia Astma Immunologic 2023, 28, 85–94.
- M. Chiara, T. Mauro, M. Fernanda, T.E. Rotondo, J. Charles, “Probiotics Mechanism of Action on Immune Cells and Beneficial Effects on Human Health, " Cells 2023, 12, 231- 242. [CrossRef]
- Z. Shao, L. Chen and T. Zhang, “Dynamic Deployment of Power IoT Security Components with Unified Resource Scheduling, " IEEE Joint International Information Technology and Artificial Intelligence Conference (ITAIC), 2020.
- R. Mahfouzi, A. Aminifar, S. Samii, P. Eles, & Z. Peng, “Security-aware Routing and Scheduling for Control Applications on Ethernet TSN Networks, "ACM Transactions on Design Automation of Electronic Systems, 2020,25, 1–26.
- X. Jing, W. Qin, H. Yao, X. Han and P. Wang, “ Resilience-oriented planning strategy for the cyber-physical ADN under malicious attacks, " Applied Energy,2024,353,1510-1524. [CrossRef]
- J. Ibrahim, S. Gajin, “Entropy-based Network Traffic Anomaly Classification Method Resilient to Deception.Computer Science and Information Sysstems,2022,19,87-116.
- S. Yang, L. Ning, X. Cai and M. Liu, “Dynamic Spatiotemporal Causality Analysis for Network TrafficFlow Based on Transfer Entropy and Sliding Window Approach, " Journal of Advanced Transaction, 2021,2021, 234-251.
- D. Chen, G. Xu, L. Meng, and P. Yang, “CPR-TOPSIS: A novel algorithm for finding influential nodes in complex networks based on communication probability and relative entropy, " Physica-Asia Statistic Mechanics and ITS Applications,2022,603,435-448.
- H. Guo, L. Cheng, S. Li, and H. Lin, “Regional risk assessment methods in relation to urban public safety, " Process Safety and Environmental Protection,2020,143,361-366.
- A. Imanbayeva, Y. Tursynbek, R. Syzdykova, and A. Mukhamedova, “Evaluating the effectiveness of information security based on the calculation of information entropy, " Annual Conference on Science and Technology Research (ACOSTER), 2020.
- (ADD-13) Kaššaj M, & Peráček T. 2024. Sustainable Connectivity—Integration of Mobile Roaming, WiFi4EU and Smart City Concept in the European Union. Sustainability, 16 (2):788. [CrossRef]
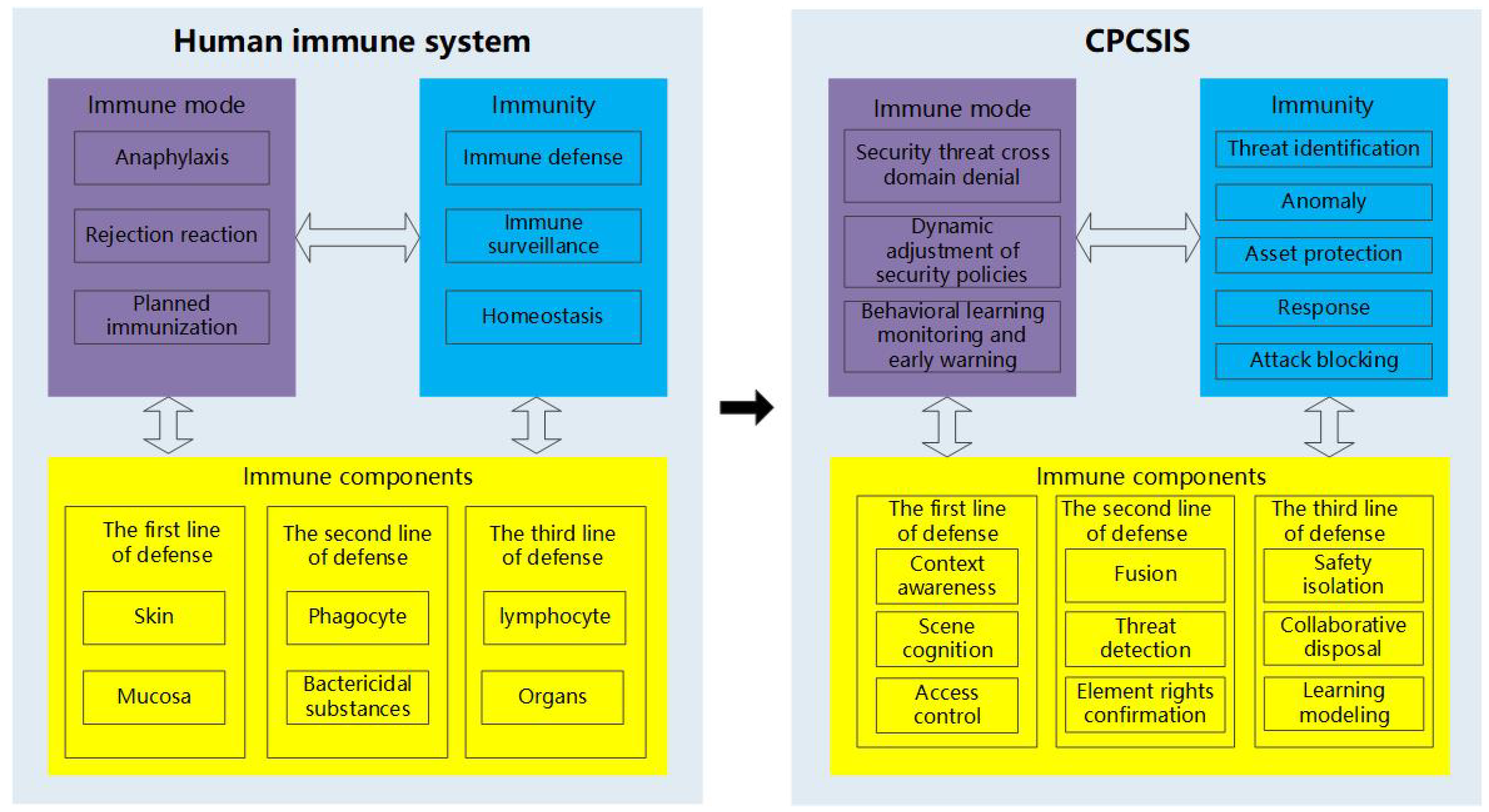


| The basic properties of immunity | Human immunity | CPCSIS |
| Immune mode | The immune system of the human body includes a series of processes such as the exclusion or elimination of foreign objects (such as allergic reactions, rejection reactions), as well as intervention measures such as planned immunity (vaccination). | The comprehensive prevention and control of network security in smart cities can also be divided into the process of discovering or disposing of network and public security threats (cross domain denial of security threats, dynamic adjustment of security strategies), as well as monitoring and warning of unknown threats through behavior learning and other methods. |
| Immunity | The human immune function includes three main tasks: immune monitoring, immune response, and immune memory. Immune surveillance identifies pathogens such as bacteria, viruses, fungi, etc; The immune response extensively clears invading pathogens and implements precise strikes against them; Immune memory exerts a stronger immune response, enabling complete elimination of pathogens. | The comprehensive immunity of smart city network information security has achieved security functions such as anomaly detection, threat identification, asset protection, emergency response, state recovery, and attack blocking through network security components and prevention and control measures, maintaining the smooth operation of the network environment. |
| Immune components | There are three immune defense lines in the human body:The first line of defense includes skin, mucous membranes, etc; The second line of defense includes phagocytosis, bactericidal substances, neutrophils, etc. The first two lines of defense are natural defense functions gradually established by humans in the process of evolution. They do not target a specific pathogen and have defensive effects against multiple pathogens; The third line of defense is lymphocytes, a type of white blood cell that is responsible for combating external infections and monitoring cellular mutations in the body. | Based on the principle of human immune components, the immune components of smart cities are also composed of three lines of defense: The first line of defense emphasizes environmental awareness, scene awareness, and access control capabilities; The second line of defense completes functions such as information fusion, threat detection, and element rights confirmation; The third line of defense is equipped with safety isolation, coordinated disposal, and learning modeling. |
| Grade | Value range | Threat level |
| 1 | Normal | |
| 2 | Low | |
| 3 | Medium | |
| 4 | High | |
| 5 | Extremely high |
| Functional module | Grade 1 | Grade 2 | Grade 3 | Grade 4 | Grade 5 |
| Monitoring data collection module | • | • | • | • | • |
| Smart city intelligent security gateway module | • | • | |||
| Multi source heterogeneous data collection module | • | • | • | ||
| Smart city network equipment surveying module | • | ||||
| Smart city network system security vulnerability monitoring module | • | • | • | ||
| Multi risk linkage analysis and precise warning module for public safety | • | • | • | • | |
| Public safety monitoring module based on video surveillance | • | • | • | • | |
| Smart city security strategy visualization module | • | • | • | • | • |
| Functional module | Grade 1 | Grade 2 | Grade 3 | Grade 4 | Grade 5 |
| Urban data exchange and sharing module | • | • | • | • | |
| Distributed public key infrastructure module | • | ||||
| Afine-grained permission management module | • | • | • | ||
| Multidimensional data authorization module | • | • | |||
| Smart city network security simulation and verification module | • | ||||
| Smart city network anomaly detection module | • | • | • | • |
| Functional module | Grade 1 | Grade 2 | Grade 3 | Grade 4 | Grade 5 |
| Urban data flow monitoring and security audit module | • | • | |||
| Linkage disposal and control module | • | ||||
| Smart city network security threat warning and emergency | • | • | • | ||
| Smart city network security situation analysis module | • | • | • | • | |
| Smart city network comprehensive prevention and control platform module | • | • | • | • | • |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





