1. Introduction
In the era of digital transformation, the protection and confidentiality of user data are of utmost significance. As the amount of data being stored and managed on cloud platforms continues to grow rapidly, it is of utmost importance to guarantee the confidentiality and security of sensitive information, preventing unauthorized access. Users expect strong security measures to protect their data from breaches and leaks, ensuring the confidentiality, integrity, and availability of their information. Consequently, establishing reliable methods for safeguarding data and transferring it between cloud environments is a crucial area of study and advancement.
Prior to storing files in the cloud, it is crucial to encrypt them as a fundamental measure to safeguard data security. Also by employing the use of digital wallets which can be used for user authentication and also using the wallet’s keys for encryption. By employing encryption, sensitive data is converted into an unreadable format that can only be accessed by authorized individuals. Nevertheless, when it comes to handling extensive files, encryption alone may not be enough to tackle concerns regarding efficient storage and easy access. This is where the concept of dividing data into smaller parts comes into play. Sharding entails breaking down a substantial file into smaller, more manageable fragments known as shards. Each piece of the puzzle is encrypted independently, which not only strengthens security but also enhances the speed and ease of data storage and retrieval. By spreading these encrypted fragments across various storage nodes, the system can attain improved performance, scalability, and fault tolerance. To ensure the security and privacy of user data, it is recommended to utilize blockchain smart contracts for secure data retrieval, access control, transparent system for managing data access, ensuring that file metadata cannot be tampered with. In order to add more security layer, the metadata is encrypted before sending to smart contract so that the information of file is kept hidden in the blockchain. This guarantees that only authorized individuals can access the file, safeguarding the confidentiality and integrity of the data. Moreover, smart contracts streamline access control procedures, minimizing the chances of human mistakes and unauthorized entry. This approach aligns with cloud security policies, providing a comprehensive solution that satisfies stringent privacy requirements. The incorporation of smart contracts not only strengthens the zero-trust model but also capitalizes on the inherent security features of blockchain technology to protect user data at every stage of its existence.
Zero-knowledge proofs, particularly zero-knowledge succinct non-interactive arguments of knowledge (zk-snarks), provide an effective approach for securely transferring data between cloud services. Zkps enable one party to demonstrate to another that they possess specific knowledge without disclosing the knowledge itself. Zkps are a form of zero knowledge proof. In the realm of cloud data migration, this implies that a user can produce a validation that their data has been correctly and securely decrypted without revealing the actual data to the verifier. Both the verifier and the user can interact with the smart contract to ensure data integrity of the file. The verifier can only have access to the metadata of the file to check the integrity but he doesn’t have access for the raw data. By adopting this method, the data is safeguarded and kept confidential throughout the migration process. The verification process at the destination cloud can validate the accuracy of the data migration solely based on the proof, ensuring the privacy and security of the user’s information. By employing zk-snarks, this approach not only improves security but also simplifies the verification process, making it an efficient and reliable solution for securely moving data to the cloud.
2. Related Work
The landscape of cloud storage and information migration has been appreciably explored in recent years, with a strong emphasis on improving security, performance, and consumer privacy including [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31,
32]. A good sized frame of studies has targeted at the implementation of superior cryptographic strategies, inclusive of encryption and sharding, to shield touchy facts and optimize garage approaches. moreover, the adoption of blockchain era and clever contracts has won traction as a means to offer transparent, tamper-proof records control and get admission to control mechanisms. These innovations goal to cope with the developing worries over facts breaches, unauthorized access, and compliance with stringent regulatory frameworks. This section critiques key contributions and findings in the field, highlighting the combination of encryption, sharding, and blockchain technology, and positioning our work in the broader context of at ease and green cloud storage answers.
Table 1.
Related reference findings in our investigation.
Table 1.
Related reference findings in our investigation.
| Author |
Citation |
Title |
Objectives |
Findings |
| M. A. Alshammari, H. Hamdi, M. A. Mahmood, and A. A. A. El-Aziz (2024) |
[1] |
Cloud Computing Access Control Using Blockchain. |
Secure solution for access control in cloud computing environments using blockchain. |
By using blockchain technology efficient, a more secure, scalable, and Transparent access control framework can be implemented. |
| Ayush Thakur, Sanskar Chauhan, and Ilisha Tomar (2024) |
[2] |
Self-Healing Nodes with Adaptive Data-Sharding. |
Improve Data Storage Efficiency In Cloud Systems. |
How breaking down large datasets into smaller components enhances storage efficiency, scalability, and overall performance. |
| M. Almasian, A Shafieinejad (2024) |
[3] |
Secure cloud file sharing scheme using blockchain and aatribute-based encryption. |
Leveraging blockchain technology for secure access control of the user data. |
Using blockchain to implement access control as smart contract where in user can request to access his file by logging a transaction in the blockchain. |
| G. Sucharitha, V. Sitharamulu, S. N. Mohanty, A. Matta, and D Jose (2023) |
[9] |
Enhancing Secure Communication in the cloud Through Blockchain Assisted-CP-DABE. |
Use of encryption to protect sensitive data. |
Usage of Blockchain technology for secure key generation, and for access control while the immutability of the blockchain ensures the confidentiality of ciphertext. |
| D. Dhinakaran, D. Selvaraj, and N. Dharini. (2023) |
[10] |
Towards A Novel Privacy-Preserving Distributed Multiparty Data Outsourcing Scheme For Cloud Computing With Quantum Key Distribution. |
Encryption And Distribution Techniques In Enhancing Data Privacy And Access Speed. |
Leveraging encryption technique to store and migrate data from one source to another. |
| F. Stodt and C. Reich (2023) |
[15] |
A Review on Digital Wallets and Federated Service for Future of Cloud Services Identity Management. |
Utilizing Digital Wallets For Encryption And Key Management. |
Digital wallets can play a key role in both identity of the user as well as security of user’s data. |
| W. Alsuwat and H. Alsuwat (2022) |
[17] |
A Survey on Cloud Storage System Security via Encryption Mechanisms. |
Choosing efficient encryption algorithm which is suitable for cloud environment. |
Searchable encryption, attribute-based, identity-based encryption, homomorphic encryption and cloud DES algorithms. Each of the above methods has some limitations and disadvantages. |
| G. C. Jadhav, K. I. Awale, A. A. Patil, and K. N. Rode (2022) |
[18] |
Cloud Cryptography. |
Use of cryptographic algorithm for secure data. |
When users upload or store data during cloud service, the data owner does not seem to understand the path of data transfer. Users do not know whether the data is collected, analyzed and accessed by third parties. |
| E. Avstein (2021) |
[18] |
Zero-Knowledge Cloud Storage: What is it and Why You Need it Now. |
Utilization of zkcs, users can securely store data on a remote server without disclosing the actual information. |
Employ zk-snarks to create zkps for secure data transmission, ensuring that encrypted information remains hidden. |
| R. Ragul and R. Arokia Paul Rajan (2020) |
[23] |
Efficient Horizontal Scaling of Databases Using Data Sharding Technique. |
Enhancing cloud data protection using aes and rsa encryption. |
Combining data privacy and integrity measures in cloud storage approach aligns with the project’s current focus on encryption and secure data migration using zero-knowledge proofs (zkps). |
| F. Zhang, X. Fan, P. Zhou, and W. Zhou (2020) |
[24] |
Zero Knowledge Proofs for Cloud Storage Integrity Checking. |
Efficient and secure storage for decentralized systems for provides valuable insights into zero knowledge proofs for cloud storage integrity checking. |
Examine proof-of-replication (porep) to guarantee that storage providers store data in multiple locations, improving security and efficiency. |
| G. S. Mahmood, D. J. Huang, and B. A. Jaleel (2019) |
[25] |
A Secure Cloud Computing System by Using Encryption and Access Control Model. |
Access control model that can safeguard data in cloud computing. |
Employing encryption and access control to guarantee the confidentiality, integrity, and appropriate control of access to sensitive data. |
| E. K. K. Edris and M. Aiash (2018) |
[26] |
ZKPVM: A Zero-Knowledge Authentication Protocol for VMs’ Live Migration in Mobile Cloud Computing. |
Application of ZKPs in both contexts demonstrates their versatility and effectiveness in enhancing security protocols for cloud-based operations. |
Employing ZK-SNARKs to generate Zero-Knowledge Proofs, allowing secure and privacy-preserving data migration between cloud services. |
| C. H. Costa, J. V. B. Moreira Filho, P. H. M. Maia, and F. C. M. B. Oliveira (2015) |
[30] |
Sharding By Hash Partitioning - A Database Scalability Pattern To Achieve Evenly Sharded Database Clusters, |
Hashing partition method to increase the scalability of the database. |
Efficient scalable and data management in cloud storage and data migration, underscores the significance of sharding in improving performance and reliability in distributed computing applications. |
| M. P. Patel, M. I. Hasan, and H. D. Vasava (2014) |
[31] |
Survey Study On Issues In Mongodb In Cloud Environment. |
Security enhancement by using encryption, data fragmentation, and distributed storage methods. |
Adopting robust encryption techniques and effective data fragmentation methods which can emphasizes the use of sharding concept and encryption technic for secure user data storage and sharing. |
The extensive literature analysis has lead to identify several research gaps. While providing a secure cloud environment efficiency is as much important as user’s security and privacy, Our architecture provides an efficient storage system using Sharding concept which plays a huge role in maintaining large files and big data while parallelly providing security for the data. With the use of smart contract it not only provides a secure access control but also stores and secures the metadata of the file which ensures immutability. Zk-SNARKS for secure data transmission from one cloud to another cloud to verify the user data without reveling his actual data provides an extra privacy and security layer for this architecture. The servers are build using zero trust architecture where the server handler has no authority over user’s data providing Zero trust environment.
3. Novelty of the Work
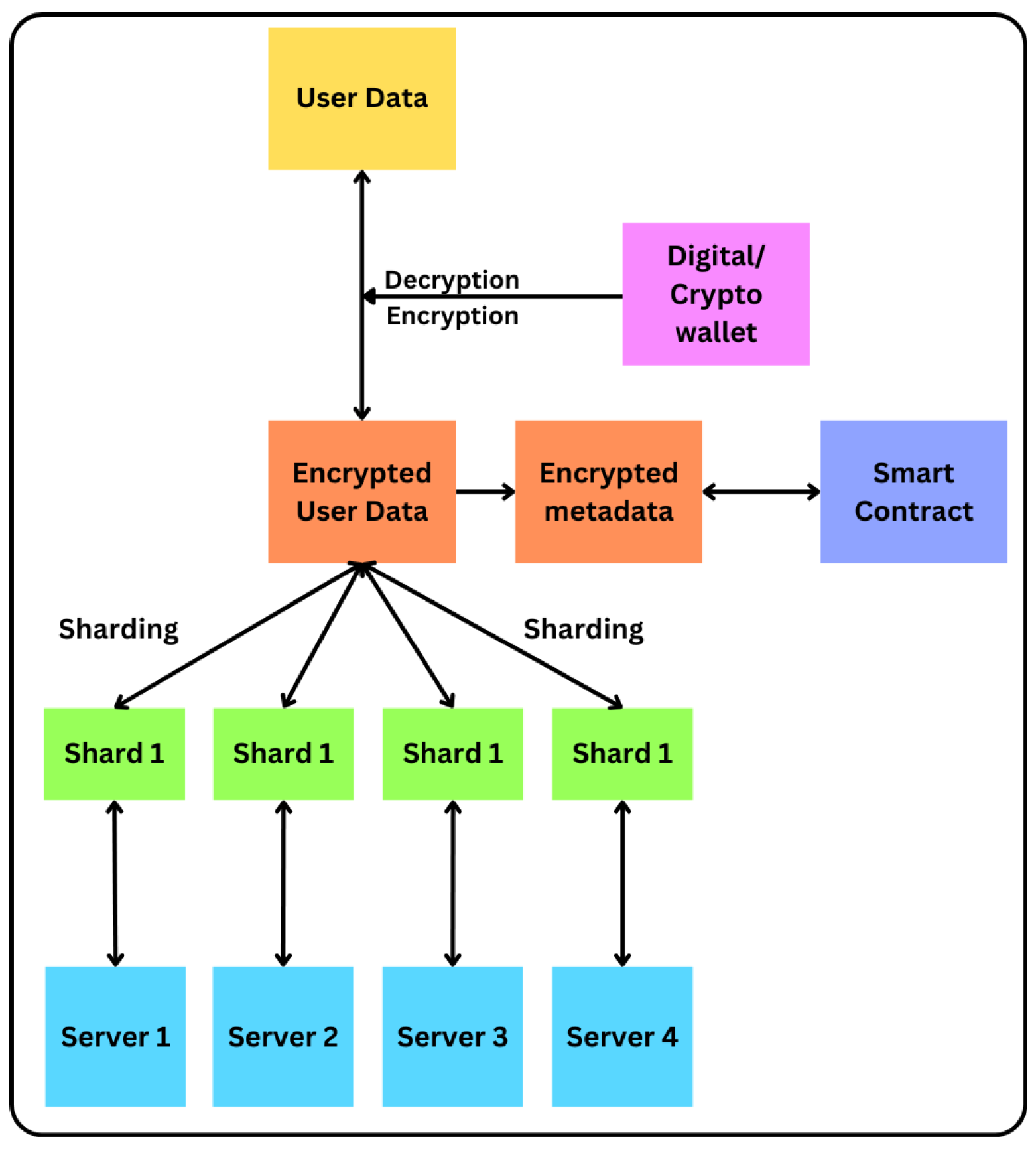
The novelty of this investigation lies in its comprehensive integration of cutting-edge cryptographic techniques and innovative data management strategies to tackle the significant challenges of secure and efficient cloud storage and migration. The design’s high-level architecture offers several distinctive contributions to the field.
Figure 1 represents the high-level architecture of the secure cloud environment.
Encryption and digital wallet integration play a significant role in safeguarding user data privacy, as each file is encrypted using cryptographic keys derived from user-specific digital wallets. This guarantees that data remains protected and accessible exclusively to authorized users, offering a personalized and comprehensive security layer. By utilizing digital wallets for encryption, the system guarantees that each user possesses a distinct encryption key, thereby minimizing the chances of unauthorized access and bolstering overall data security.
4. Secure Cloud Environment for Data Storage and Data Transmission
Inorder to provide a comprehensive methodology that combines cutting-edge cryptographic methods, sharding, zero-knowledge proofs (zkps) and smart contracts to guarantee secure and efficient cloud storage and data transfer. The key components of the methodology involve encrypting files using personalized digital wallets, breaking down the encrypted files into shard pieces for effective storage and Improved upload speed, and utilizing zkps for secure data verification in destination cloud. The system’s architecture guarantees the protection of sensitive user data at all stages of its existence, employing a zero-trust approach to prevent any unauthorized access by server handlers.
4.1. Sharding and Encryption Modelling
As soon as a user uploads a file through the client-server interface, the file is instantly encrypted using cryptography keys stored in the user’s digital wallet as
Figure 2. The encrypted shards are then uploaded to the available servers simultaneously which ensures faster uploading time for large sized files or big data along with the hash of the entire file and additional metadata such as the original file name and format, are recorded.
4.1.1. Variables and Definitions of the Model
4.1.2. Sharding model
The file
F is divided into
n pieces, where the size of each piece
is ideally equal, but may vary slightly due to file size not being perfectly divisible by
n. The size of each piece can be represented as:
Where: - is the remainder when the file size is divided by the number of pieces n. - denotes the floor function, which rounds down to the nearest integer.
4.1.3. Encryption of Shards
Each shard
is encrypted using a symmetric encryption algorithm with a key
K and an IV. The encrypted piece
is given by:
4.1.4. Hashing and Metadata
The unique report, each shard, and the encrypted shards may be hashed to offer a unique identifier and make certain integrity. The hashes may be denoted as follows:
4.1.5. Storing Metadata
The metadata stored for the document and its shards includes the original document hash, the hashes of the shards, and the encryption information. This metadata ensures that the report can be confirmed and reassembled successfully and this metadata is encrypted and stored in blockchain through smart contract enhancing immutable state of the metadata:
Where: - represents the list of hashes for all encrypted shards along with their respective indices. - is the type or format of the original file. - specifies the encryption algorithm used
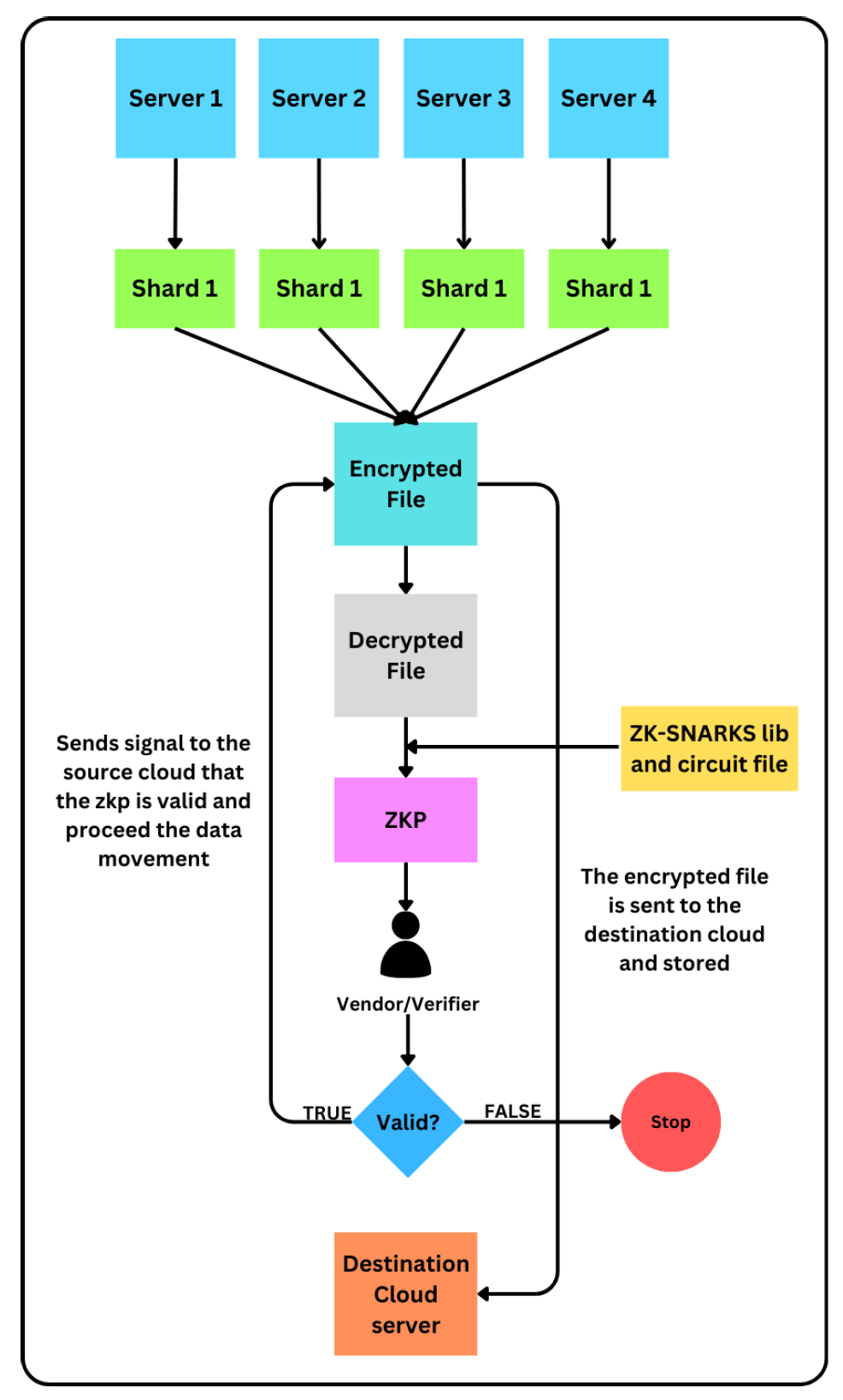
4.2. Data migration using ZK-SNARK
For data migration from the source cloud to the destination cloud, the system utilizes zero-knowledge proofs (zkps) to guarantee secure and private data movement as per
Figure 3. The zk-SNARks construction process includes defining the circuit which represents the computation verifying the correctness of the reassembly and integrity of the shards. This circuit is then used for generating proving and verifying keys which are required for the generation of zk-SNARKs.The operations involved in this model contains two phases in order. It starts with the proving phase where the proof of the encrypted file is generated after the decryption of reassembled shards. Followed by verification phase where the verifier in the destination cloud verify the zkp data and sends the verification results to proceed for further operations.
4.2.1. Variables and Definitions
4.2.2. zk-SNARKs Construction
The setup phase generates public parameters for proof generation and verification.
4.2.3. Proving Phase
Inputs and Witness: The public input
x includes the commitments
and the hash
. The witness
w consists of
and
.
Proof Generation: The proof
is generated as follows:
4.2.4. Verification Phase
The verifier checks the proof using the verifying key.
Verification: Verify the proof against the public input:
4.3. Smart Contract for Access Control and Metadata Storage
Storing the encrypted metadata on the blockchain, the system guarantees the integrity and authenticity of the metadata, creating an unalterable record of the data. Furthermore, smart contracts are employed to regulate access control, guaranteeing that only authorized users can access and decrypt the files. By adopting this approach, organizations can not only enhance data security but also adhere to strict cloud policies that prioritize user privacy and data protection.
4.3.1. Variables and Definitions
4.3.2. Smart Contract Model for access Control
5. Experimental Results and Discussion
This investigation aimed to analyze the performance of a cloud storage system by comparing the time it takes to upload files when using sharding versus a system without sharding. The main goal was to assess whether the sharding technique provides a substantial improvement in terms of uploading speed. The experiment entailed transferring substantial files using a client-server interface in two situations: with sharding, where the files were divided into smaller encrypted fragments, and without sharding, where the entire file was uploaded as a single unit.
The performance analysis was conducted in a basic local environment using Nodejs to calculate the uploading time with and without using sharding concept and also the time required to generate zkp and verifying process of zkp. The last experiment conducted was to calculated the time taken for the migration of encrypted file to the destination server. The method of implementation was done by deploying the server in 4 different port and one port for destination cloud (assumption as cloud storage). The performance was conducted on a laptop with specification having AMD Ryzen 7 4800H with Radeon Graphics 2.90 GHz with 16GB RAM of 64-bit operating system, x64-based processor of Windows 11 Operation system.
The findings of the performance evaluation indicated that the uploading time was noticeably faster when employing the sharding technique. By dividing the encrypted file into smaller fragments, each piece could be processed and uploaded independently and concurrently on multiple servers. The ability to perform multiple tasks simultaneously resulted in a significant reduction in the time it took to upload files. In contrast, the non-sharded approach necessitated the upload of the entire file as a single entity, leading to extended upload times due to the sequential processing and increased resource utilization on a single server.
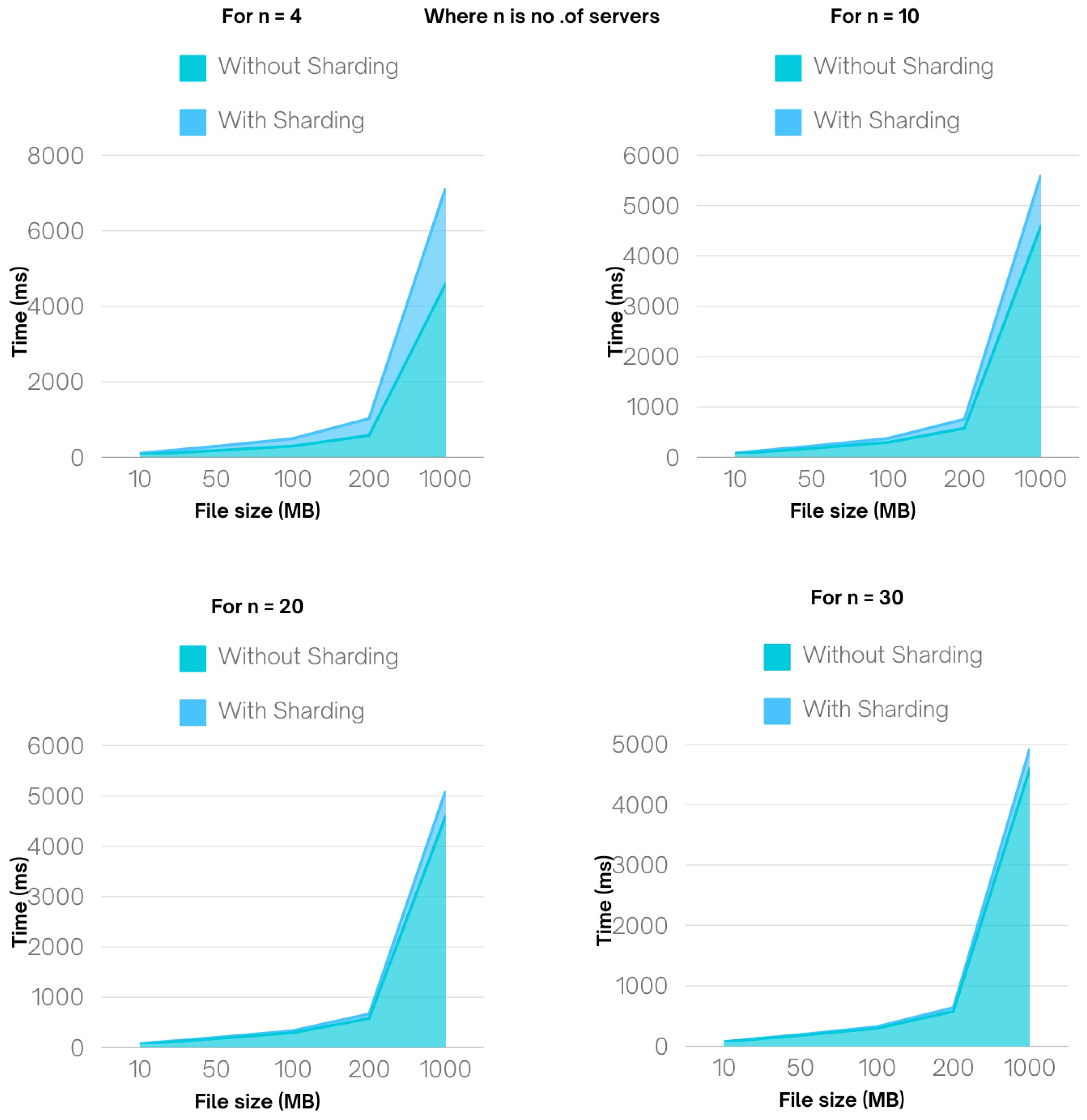
The below
Figure 5 represents the analysis of the uploading time vs file size on varying number of servers. As we can see the uploading time gradually decreases as the no. of servers increases, we observe a significant reduction in the time it took to upload files. As the no. of server increases not only the efficiency of the time increases but also it can tolerate some amount of faulty nodes or servers.
Figure 4.
Analysis of time complexity for n no. of servers.
Figure 4.
Analysis of time complexity for n no. of servers.
Through the comparison we can see the time function gradually decreases on increasing number of servers
n. From the above analysis we calculated the mathematical equation which can approximately calculate the time taken on
n number of servers.
where:
is the sharding time with n servers.
is the sharding time with 4 servers.
n is the number of servers.
Table 2.
Results of Uploading time for With and Without sharding of data.
Table 2.
Results of Uploading time for With and Without sharding of data.
| File Size (MB) |
Without Sharding (ms) |
With Sharding, for n=4 (ms) |
With Sharding, for n=10 (ms) |
With Sharding, for n=20 (ms) |
With Sharding, for n=30 (ms) |
| 10 |
69.5 |
40.158 |
16.06 |
8.03 |
5.35 |
| 50 |
117.57 |
112.25 |
44.9 |
22.45 |
14.97 |
| 100 |
295.65 |
197.109 |
78.84 |
39.42 |
26.28 |
| 200 |
577.76 |
450.16 |
180.60 |
90.03 |
60.02 |
| 1000 |
4595 |
2540 |
1016 |
508 |
338.67 |
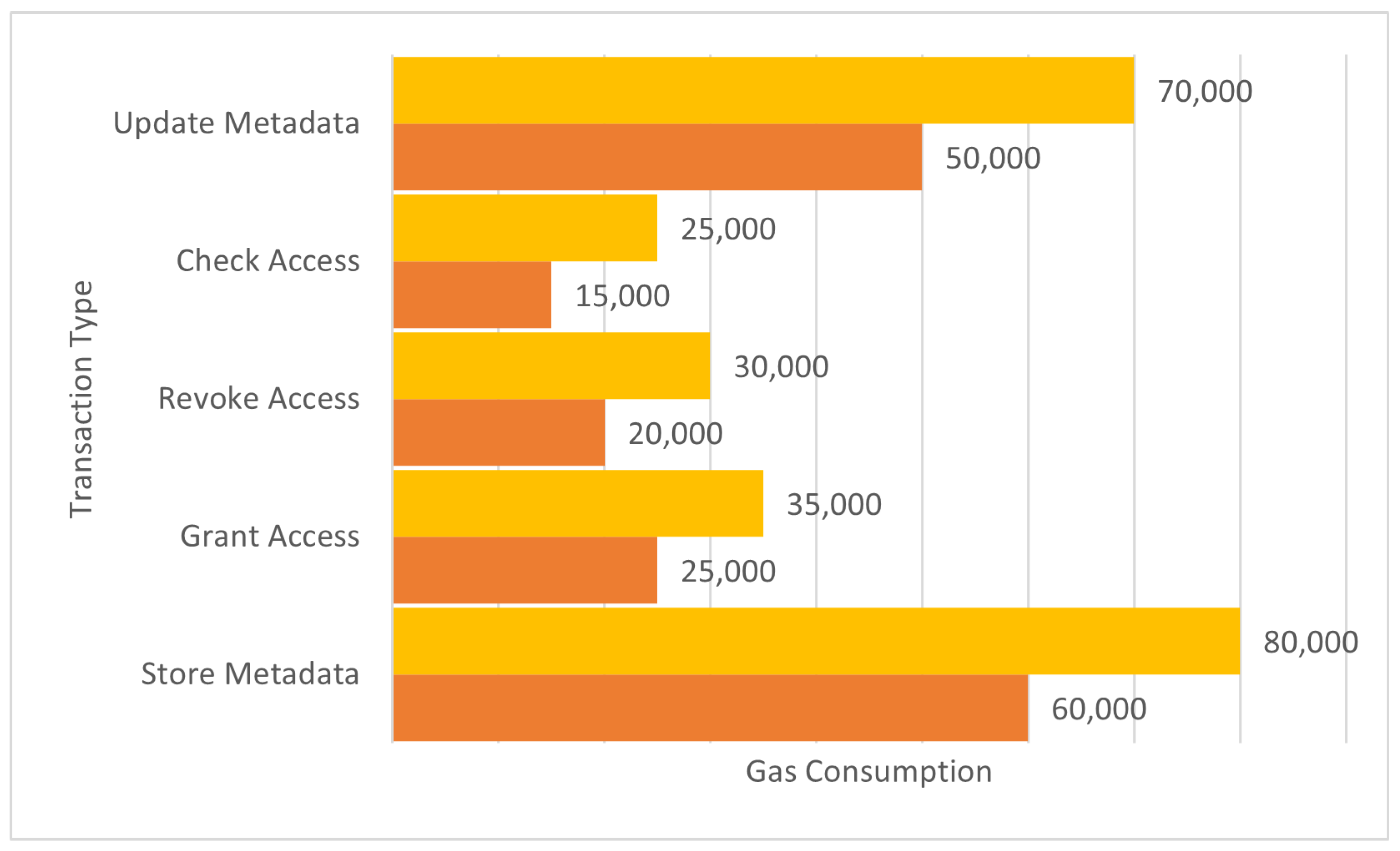
We aimed to apprehend the useful resource performance and value implications of various operations inside the settlement. by categorizing transactions into sorts which include storing metadata, granting and revoking access, checking get admission to permissions, and updating metadata, we quantified the fuel intake associated with each. Our findings discovered that operations involving data storage, along with storing and updating metadata, typically ate up the maximum gas because of the higher computational and storage requirements. Conversely, operations like checking get admission to, which by and large involve study operations, ate up substantially less gasoline. This analysis affords valuable insights into optimizing clever contract design to reduce gas costs, especially for frequent transactions, thereby enhancing the general fee-effectiveness and performance of the system deployed at the Polygon blockchain.
The gas consumption analysis was conducted on Remix editor where we can deploy and test our smart contracts. We deployed our smart contract on polygon network as it provides higher scalability and less gas fee. The transaction functions are designed to consume less gas while incorporating secure methods that protect against smart contract vulnerabilities.
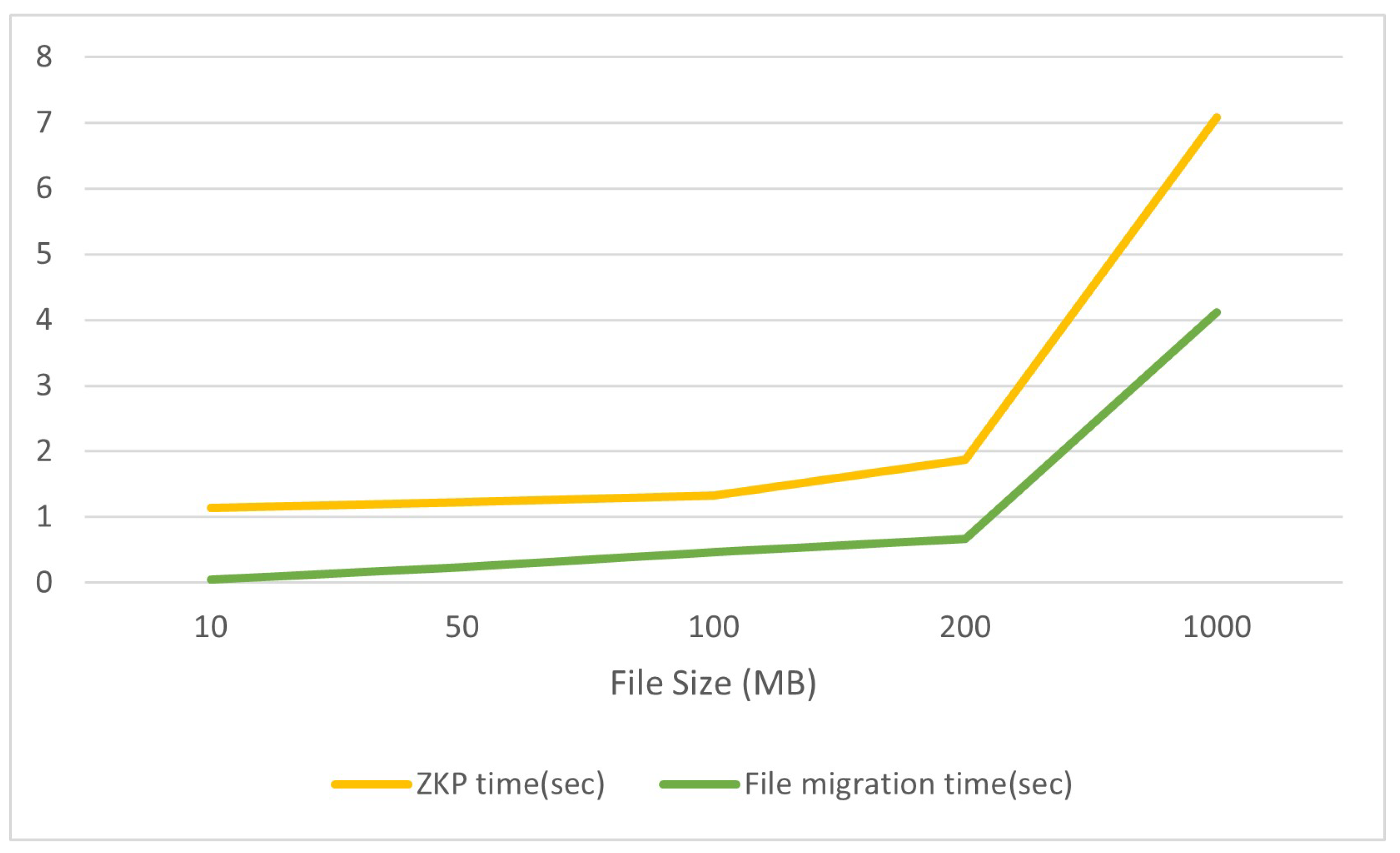
The evaluation of our project’s performance included assessing the time required to produce a zero-knowledge proof (zkp) and transmit it to the verifier in the cloud-based destination. The process starts with putting together and decrypting the encrypted file pieces, then creating the zkp using zksnarks. This phase is crucial as it guarantees the accuracy and reliability of the data being transferred without revealing the actual data. The study showed that the zkp generation and transmission to the verifier were executed effectively, requiring an appropriate amount of time. Upon receiving the zkp, the verifier promptly validated it, ensuring a quick and efficient validation process with minimal latency. This rapid validation process is crucial for ensuring a seamless and secure data migration flow, validating that the data integrity checks are thorough yet efficient.
Figure 6.
Zkp generation time and file migration time for different file size
Figure 6.
Zkp generation time and file migration time for different file size
The subsequent performance analysis centered around the time it took for the generation of zkp as well as the time taken for the actual migration of the file to the destination cloud. This phase included piecing together the encrypted fragments, ensuring their accuracy, and safely moving the encrypted file to the designated cloud server upon successful verification of Zkp from the destination cloud.
Our analysis revealed that the file uploading process with sharding concept for big data and large file, file migration process, following the zkp validation, was carried out with remarkable efficiency. We also carried out the efficiency calculating metric by using the below formula which resulted in approximately
40.94% for 4 servers,
76.37% for 10 servers,
88.18% for 20 servers and
92.12% for 30 server more efficient when we use sharding concept over a single cloud server. As we can see as the no. of server increases efficiency rate also increases. So more the servers we get more efficient file storage and management can be achieved for big data or large files.
By adopting this streamlined approach, the encrypted file can be delivered to the destination promptly and securely, safeguarding the privacy and security of user data throughout the transmission. The integration of efficient zkp validation and optimized file migration highlights the effectiveness of our system in delivering secure and swift data migration services.
6. Conclusions
In culmination of this novel work, it presents a comprehensive framework that ensures the security and efficiency of cloud storage and data migration, utilizing cutting-edge cryptographic techniques, sharding, blockchain smart contracts and zero-knowledge proofs (zkps). By encrypting files using user-specific digital wallets and dividing the encrypted data across multiple local database servers, the system guarantees that sensitive user information remains secure and inaccessible to unauthorized individuals at all stages of its existence. By implementing a zero-trust model, where encrypted data is stored and server handlers have no direct access to raw data, data security and privacy are greatly improved.
Looking into the future, there are plans to introduce additional improvements to the system, aiming to enhance its capabilities and tackle new challenges in managing cloud data. Initially, the implementation will progress to generate zkps by utilizing cryptographic keys directly obtained from the user’s digital wallet. This improvement not only strengthens the security of the proof generation process but also guarantees a personalized and comprehensive verification procedure that is specifically designed to meet the unique encryption key requirements of each individual user.
Further, deploying the smart contracts on a zero-knowledge proof (zkp) blockchain will be examined. This strategy intends to enhance the security and privacy protocols of the cloud storage system. By utilizing zkp blockchain technology, the verification of transactions and data access can be conducted without disclosing any sensitive information, ensuring the privacy of users. Utilizing smart contracts on a zkp blockchain will also improve compliance with privacy regulations and cloud policies, guaranteeing that user data is safeguarded to the highest possible standards. This future direction will play a crucial role in the creation of a more robust, secure, and privacy focused cloud storage solution.
These advancements are designed to enhance the system’s ability to maintain data accuracy, protect privacy, and optimize operational efficiency in cloud environments. Through the incorporation of state-of-the-art technologies and methodologies, this investigation establishes a solid groundwork for future advancements in secure cloud data storage and migration, propelling the development of reliable and scalable cloud computing infrastructures.
References
- M. A. Alshammari, H. Hamdi, M. A. Mahmood, and A. A. A. El-Aziz, "Cloud Computing Access Control Using Blockchain,". In International Journal of Intelligent Systems and Applications in Engineering, 2024, vol. 12, no. 9s, pp. 380-390, link: https://ijisae.org/index.php/IJISAE/article/view/4329.
- Ayush Thakur, Sanskar Chauhan, and Ilisha Tomar, "Self-Healing Nodes With Adaptive Data-Sharding,". arXiv preprint, 2024. [CrossRef]
- Mohammadpayam Almasian and Alireza Shafieinejad, "Secure cloud file sharing scheme using blockchain and attribute-based encryption ". In Computer Standards Interface, 2024, vol. 87. [CrossRef]
- I. Hamid and M. Frikha, "Blockchain-Enhanced Cybersecurity and Privacy in Cloud Computing: A Systematic Literature Review,". In Journal of Theoretical and Applied Information Technology, 2024, vol. 102, no. 2, link: https://www.jatit.org/volumes/Vol102No2/10Vol102No2.pdf.
- Sagarika Behera and Jhansi Rani Prathuri, "FPGA-Based Acceleration of K-Nearest Neighbor Algorithm on Fully Homomorphic Encrypted Data". In MDPI Cryptography, 2024, vol.8, no. 1. [CrossRef]
- Chang Chen , Guoyu Yang , Zhihao Li, Fuan Xiao, Qi Chen and Jin Li, "Privacy-Preserving Multi-Party Cross-Chain Transaction Protocols". In MDPI Cryptography, 2024,vol.8, no. 1. [CrossRef]
- Yinhao Jiang, Mir Ali Rezazadeh Baee, Leonie Ruth Simpson, Praveen Gauravaram, Josef Pieprzyk, Tanveer Zia, Zhen Zhao and Zung Le, "Pervasive User Data Collection from Cyberspace: Privacy Concerns and Countermeasures". In MDPI Cryptography, 2024, vol.8, no. 1. [CrossRef]
- Yuri Bespalov 1, Lyudmila Kovalchuk , Hanna Nelasa, Roman Oliynykov, and Rob Viglione, "Models for Generation of Proof Forest in zk-SNARK Based Sidechains". In MDPI Cryptography, 2023, vol.7, no. 1. [CrossRef]
- G. SUCHARITHA, VEDULA SITHARAMULU, SACHI NANDAN MOHANTY ,ANJANNA MATTA, AND DEEPA JOSE5, "Enhancing Secure Communication in the Cloud Through Blockchain Assisted-CP-DABE,". In IEEE Xplore, 2023, vol. 11, pp. 99005 - 99015. [CrossRef]
- D. Dhinakaran, D. Selvaraj, and N. Dharini, "Towards A Novel Privacy-Preserving Distributed Multiparty Data Outsourcing Scheme For Cloud Computing With Quantum Key Distribution", In International Journal of Intelligent Systems and Applications in Engineering 2023, vol. 12, no. 2, link: https://ijisae.org/index.php/IJISAE/article/view/4252.
- H. Dubey and K. Roy, "Secure Access Control in Cloud Computing Environments: Smart Contract Blockchain,". In Vidhyayana, 2023, vol. 8, no. si7, link: https://www.vidhyayanaejournal.org/journal/article/view/832.
- Mujahid Sharif and Ayesha Said, "Blockchain and Cloud: Exploring the Intersection of Two Revolutionary Technologies", In ResearchGate, 2023, link: https://www.researchgate.net/publication/372826151.
- S. N. Prasad and C. Rekha, "Block chain based IAS protocol to enhance security and privacy in cloud computing,". In Measurement: Sensors, 2023, vol. 28, p. 100813. [CrossRef]
- E. Jansirani and R. N. Kowsalya, "Analysis of ECC and ZKP Based Security Algorithms in Cloud Data,". In Journal of Theoretical and Applied Information Technology (JATIT), 2023, vol. 101, no. 16, pp. 6354-6368, link: https://www.jatit.org/volumes/Vol101No16/9Vol101No16.pdf.
- F. Stodt and C. Reich, "A Review on Digital Wallets and Federated Service for Future of Cloud Services Identity Management,". Presented at the Fifteenth International Conference on Advanced Service Computing (SERVICE COMPUTATION 2023), Nice, France, June 26-30, 2023, pp. 16-20, link: https://www.researchgate.net/publication/372108853.
- Sachin N. Rajguru and Sumit K. Choubey, "Blockchain in Cloud Computing for Securing Documents,". In International Research Journal of Modernization in Engineering, Technology and Science (IRJMETS), 2023, vol. 5, no. 5, pp. 123-130. [CrossRef]
- W. Alsuwat and H. Alsuwat, "A Survey on Cloud Storage System Security via Encryption Mechanisms,". In International Journal of Computer Science and Network Security, 2022, vol. 22, no. 6, pp. 52-61, link: http://paper.ijcsns.org/07_book/202206/20220626.pdf.
- G. C. Jadhav, K. I. Awale, A. A. Patil, and K. N. Rode, "Cloud Cryptography,". In International Journal of Research Publication and Reviews (IJRPR), 2022, vol. 3, no. 6, pp 2200-2202, link: https://ijrpr.com/uploads/V3ISSUE6/IJRPR5029.pdf.
- E. Avstein, "Zero-Knowledge Cloud Storage: What is it and Why You Need it Now,". In Codemotion Magazine, Artical, 2021, link: https://www.codemotion.com/magazine/devops/cloud/zero-knowledge-cloud-storage-what-is-it-and-why-you-need-it-now.
- Sudakshina Mandal, Danish Ali Khan and Sarika Jain , "Cloud-Based Zero Trust Access Control Policy: An Approach to Support Work-From-Home Driven by COVID-19 Pandemic,". In New Generation Computing, 2021, vol. 39, pp 599-622. [CrossRef]
- Priyanka Ghosh,"The State-of-the-Art in Zero-Knowledge Authentication Proof for Cloud". In IEEE Xplore, 2021, edition: 1, pp 149 - 170. [CrossRef]
- I. Hamid and M. Frikha, "A Review on Cryptography in Cloud Computing ,". In International Journal of Scientific Research in Computer Science Engineering and Information Technology, 2024, vol. 6, no. 6, pp. 225-230. [CrossRef]
- R. Ragul and R. Arokia Paul Rajan, "Efficient Horizontal Scaling of Databases Using Data Sharding Technique,". In International Journal of Innovative Technology and Exploring Engineering (IJITEE), 2020,International Journal of Innovative Technology and Exploring Engineering (IJITEE), vol. 9, no. 5, pp. 590-593. [CrossRef]
- F. Zhang, X. Fan, P. Zhou, and W. Zhou, "Zero Knowledge Proofs for Cloud Storage Integrity Checking,". In arXiv, 2019. [CrossRef]
- S. Mahmood, D. J. Huang, and B. A. Jaleel, "A Secure Cloud Computing System by Using Encryption and Access Control Model,". In Journal of Information Processing Systems, 2019, vol. 15, no. 3, pp. 538-549. [CrossRef]
- E. K. K. Edris and M. Aiash, "ZKPVM: A Zero-Knowledge Authentication Protocol for VMs’ Live Migration in Mobile Cloud Computing,". In Proceedings of the 13th International Conference on Software Technologies (ICSOFT), 2018, pp. 858-864, link: https://www.researchgate.net/profile/Mahdi-Aiash/publication/326926039.
- A. Shaik, B. Madhurima, and M. Neelakantappa, "An Approach To Zero Knowledge Proof For Secure Data Sharing In Cloud Storage: New Direction,". In International Journal of Innovative Technology and Exploring Engineering (IJITEE), 2018, vol. 8, no. 2S, pp. 195-201, link: https://www.ijitee.org/portfolio-item/bs2703128218.
- T. Jain and J. A. Khan, "Secure Big Data Access Control Policies for Cloud Computing Environment," In International Journal of Innovative Research in Computer Science and Technology (IJIRCST), 2017, vol. 5, no. 2, pp. 254-256. [CrossRef]
- S. Bagui and L. T. Nguyen, "Database Sharding: To Provide Fault Tolerance and Scalability of Big Data on the Cloud,". In International Journal of Cloud Applications and Computing (IJCAC), 2015, vol. 5, no. 2, pp. 36-52. [CrossRef]
- C. H. Costa, J. V. B. Moreira Filho, P. H. M. Maia, and F. C. M. B. Oliveira, "Sharding By Hash Partitioning - A Database Scalability Pattern To Achieve Evenly Sharded Database Clusters,". In Proceedings of the 17th International Conference on Enterprise Information Systems (ICEIS), Barcelona, Spain,, 2015, vol. 2, pp. 313-320. [CrossRef]
- M. P. Patel, M. I. Hasan, and H. D. Vasava, "Survey Study On Issues In Mongodb In Cloud Environment,". In International Journal of Advanced and Innovative Research, 2014, vol. 3, no. 1, link: https://ijairjournal.in/wwwroot/temp/ijair/jan2014/t5.pdf.
- Balasubramaniam. S and V. Kavitha, "A survey on data encryption tecniques in cloud computing", 2014, vol. 13, no. 9, pp. 494-505, link: https://www.researchgate.net/publication/287914941.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).