1. Introduction
1.1. Background and Motivation
1.1a
Background: The fusion of AI and IoT is a transition to a new level in the development of technology, which dramatically changes automation and security in fields of economics and other industries. With the advance of IoT it has enabled devices, sensors and controls to tie with the World Wide Web to improve on efficiency and constant analysis of real data [
1]. IoT finds a natural and strong partner in AI as AI models and smart algorithms allow for efficient data analysis and decision-making [
2]. These are some of the improvements that have been realized, for instance, smart cities applying and correctly using the resources, industrial IoT networks application in the production cycle, and smart home applications in energy production.
1.1b
IoT’s Ubiquitous Impact: Thus, the popularization of IoT devices became a starting point for new opportunities and created a new world, changing people’s everyday life. Some of the features that home automation systems include are lighting control, thermostat control and security camera control all through smart phones, this make the home automated system to be convenient and secure [
3,
4]. In the medical sector, the use of wearable devices monitor the health status of patients and send real-time status to health practitioners, influencing the delivery of care. Furthermore, as part of smart cities, IoT handles traffic control, efficient disposal of waste, and bringing in better security. This widespread use accentuates the bright future of IoT, which is geared towards turning the world into a smartened society.
Thus, the popularization of IoT devices became a starting point for new opportunities and created a new world, changing people’s everyday life. Some of the features that home automation systems include are lighting control, thermostat control and security camera control all through smart phones, this make the home automated system to be convenient and secure.
In the medical sector, the use of wearable devices monitor the health status of patients and send real-time status to health practitioners, influencing the delivery of care. Furthermore, as part of smart cities, IoT handles traffic control, efficient disposal of waste, and bringing in better security. This widespread use accentuates the bright future of IoT, which is geared towards turning the world into a smartened society.
1.1c
The Flip Side: Security Risks In IoT there is no doubt that the different IoT devices have brought tremendous opportunities to consumers and developers, but the expansion rate of IoT security vulnerabilities will be another issue. Most devices or gadgets in the IoT network were created hastily on the market, and they do not have proper security layers down pat; as such, they are susceptible to hacking. They automatically become interfaces which can endanger the entire system by their membership in networks. All these risks are important to address in order to mitigate the mainly twofold risk of data leakage, and the risk posed to the trustworthiness of connected IoT technologies [
5].
1.1d
Enter AI’s Role in Security: AI improves IoT security by allowing the recognition of primary discrepancies, the estimation of threats, and the counteraction to cyber threats in real-time. It therefore means that more superior models in machine learning can be of help in finding out the patterns and anomalies which in turn will help in preventing security threats. The inclusion of AI in the IoT systems enhances cyber security, and provides an adequate measure against new emerging threats [
6].
1.1e
A Balancing Act: Security vs. Performance: This is a cornerstone issue of IoT systems because often security must be scarified to gain performance, or vice versa. The most well-known security approaches are rather effective but heavy and not suitable for usage in IoT devices due to their restrictive hardware constraints. Ensuring that security has to reach an optimal level without the degradation of IoT devices’ performance is crucial to ensuring that IoT devices remain functional [
7].
1.1f
The Motivation for Integration: This research focuses on the interrelation of AI and IoT to improve the prospects of automation and protection. The motivation is twofold: to emphasize and utilize possibilities of AI in increasing IoT safety and productivity, as well as to identify and create new IoT applications based on it. The goal as always lies in establishing a solid, secure setting for the use of such technologies that will yield the best of their capacity [
8].
1.1g
Evolving Threat Landscape: The Need for Security Upgrade: The upward trend of cyber threats and attacks on IoT devices prompt the need to upgrade the level of security on the devices. Recent events have proved that adversary can gain unauthorized access, can breach the data and can also violate user’s privacy. This constantly changing threat regime implies that different modalities in security must be adopted from time to time to guard IoT systems against emerging threats [
9].
1.2. Research Problem and Scope
Raised from the outlined research issues, the research problem under study in this work is the Artificial Intelligence and Internet of Things Integration to promote Automation and Security in several applications. The main topics are the protection of the IoT devices insecurity and the integration of AI into the ability to predict maintenance, generalize results, and enhance the IoT systems functioning. This paper aims to determine how AI’s enhanced algorithms and the usage of machine learning models can enhance and protect IoT systems against novel dangers while enhancing the systems efficiency.
1.2a Vulnerability Amplified: Security Concerns with IoT Devices in Connected Environment: IoT devices are generally characterized by low-power and low-memory; it is for this reason that they are often grossly insecure. This makes them vulnerable to cyber threats that may breach the triad of system security; integrity, confidentiality and availability. These vulnerabilities are more apparent when devices in the IoT are communicating with one another as well as external networks, making it clear that there is has to be new ways of defending these networks from malicious attacks.
1.2b Enhancing Security with AI: AI could prove very helpful in enhancing IoT security through possibilities of identifying risks, predicting malicious attacks, and acting promptly to thwart such attacks. Current and especially advanced Machine learning models can analyze what is normal and what is abnormal, which allows taking preventive action to protect IoT systems. This research is concerning the creation of protective measures and outcomes that improve the security and dependability of IoT devices without negatively influencing the IoT network performance.
1.2c
Formulation of the Research Problem: The research problem is mathematically represented as:
where
Pproblem represents the extent of the IoT devices vulnerability to cyber threats,
denotes the vulnerability profile of IoT devices, and
reflects the AI capabilities deployed for enhancing security.
To define the cost function between
and
in the research problem formulation
Pproblem a weighted sum of the vulnerability profile and the AI capabilities is utilized:
where
and
are weighting factors representing the relative importance or cost associated with the vulnerability profile and AI capabilities, respectively.
1.2d Initial Conditions: Initial values for and are obtained from previous data and .
1.2e Constraints:
Resource Allocation Constraint: The total resources allocated for deploying AI capabilities cannot exceed. The constraint is written as:
Vulnerability Profile Constraint: The vulnerability profile of IoT devices is within the lower bound (
Vmin) and upper bound (
Vmax). The constraint is given as:
Non-Negativity Constraint: Both and are non-negative:
These constraints ensure that the cost function remains within feasible and meaningful bounds, reflecting practical considerations in IoT device security and AI resource allocation. The boundary values for and depends on the requirements and characteristics of the IoT system and the AI capabilities deployed.
1.2f Scope of the Research: Therefore, the major goal of this research is to work towards solving the security issues in IoT devices and improving their performance with the application of AI. This involves the formulation of AI of security solutions to later on deal with the limitations of IoT devices when it comes to resource utilization and later on performance in real time environments.
1.2g IoT Device Security: To be more specific, the study focuses on how to apply AI in the improvement of IoT devices security. All these strategies must be able to overcome the problems presented by the resource limitations of IoT devices.
1.2h AI Capabilities: This research focuses on specific AI use case in enhancing IoT connection and protection. Perfectly, it is necessary to observe that characteristics of the AI models, such as their capability of processing a large number of data and finding some patterns or relationships among them, require the specific security optimization.
1.2i Predictive Maintenance and Decision-Making: Focusing on how AI can be used in prognosis control and decision-making of smart IoT networks, it aims at maximizing the efficiency of these processes while making few impacts on system performance.
1.2j
Formulating the Scope: The scope of the research is defined by the equation:
where
encompasses strategies for enhancing IoT device security,
involves considerations specific to AI capabilities, and
focuses on the development of next-generation applications utilizing AI and IoT integration.
2. Materials and Methods
2.1. Materials
The basis for the study was various hardware and software that exploring how artificial intelligence and the Internet of Things could be integrated into automation and security applications. Materials used included:
Hardware: Arduino Uno, Raspberry Pi 4, ESP8266 WiFi modules, ESP32, various sensors—like PIR motion sensors and temperature and humidity sensors—actuators like relays and servo motors.
Software: Tensor Flow 2.4, Python 3.8, OpenCV 4.5, Arduino IDE 1.8.13, and protocol MQTT for the communication between devices.
Data: Extract datasets from open repositories like the UCI Machine Learning depository and Kaggle to train the AI model.
2.2. Methods
2.2a Configuration of the Device: A Raspberry Pi 4 was configured as the central processing unit. It interfaced with various sensors and actuators through general - purpose input – output pins and I2C communication protocols. Arduino Uno, with ESP8266/ESP32 modules doing wireless communication, has been used for additional sensor networking.
2.2b
Network Setup: Setting up the network, an MQTT broker was installed on the Raspberry Pi. Every sensor node was programmed to publish data into the broker, and the Raspberry Pi subscribed to the relevant topics to get data for processing [
10].
2.2c
AI Model Deployment: Herein, it was the deployment of pre-trained AI models on a Raspberry Pi for real-time data analysis. For example, running a neural network model using Tensor Flow Lite enabled the detection of anomalies in sensor data [
11].
2.2d
Sensory Data: The metrics were incessantly read from the sensors at an interval based on the predefined multiplicity. All data acquired by temperature, humidity, and motion sensors via a single Raspberry Pi are locally stored and sent periodically to the cloud server for backup storage and further examination [
12].
2.2e
Preprocessing: All the pre - processed data had three phases leading to normalization, noise reduction, and feature extraction. The following libraries were needed in such phases: manipulation and information preprocessing by Panda and NumPy [
13].
2.2f
Development of AI Model: There was a split between the training and test datasets in this historical data. Model training followed, and then came the development of anomaly detection models using both supervised and unsupervised learning. That is the case where an auto-encoder neural network uses the normal behavior the model understands to identify deviations in such behavior [
14].
2.2g
Computerization Test Scripts: Computerization scripts are developed in Python scripts to predict the model at any time in the response using an AI model. For example, in the case of an incident, changes in data from the motion sensors should flame some remote alarm system with an MQTT message [
15].
2.2h
Security Mechanism: We opened the opportunity for keeping data encrypted at rest and in transit in any communication done on an MQTT protocol by implementing the SSL/TLS encryption protocols. Other security features set up this ensures that basic access controls are in place to avoid unknown migration into the IoT network [
16].
2.2i
User Interface: A full-fledged JavaScript web dashboard based on Flask for an administrator to show data from the sensors reaching the IoT devices, highlight results from AI models, and make remote configuration changes [
17].
2.2j Metrics: The presentation metrics used for the AI and IoT systems were precision, response time, and dependability. The precision of the deployed models about variance detection was measured according to ordinary metrics of classification: precision, recall, and the F1-score for classifying instances precisely.
2.2k Testing and Validation: The system has been tested against various test scenarios to validate its functionality and robustness. For example, how responsive it is against intrusion attempts is tested by simulation of intrusions using security automation scripts.
2.2l Comparison to existing methods: Comparisons regarding the performance of the proposed system against existing methods available in the literature have to be drawn hereafter to show improvements or probably leave room for enhancement in the future.
3. AI Algorithms and Software
It covers cutting-edge AI algorithms including anomaly detection, predictive maintenance, and data encryption. It discusses the latest AI algorithms like SVM, Neural Networks, and Decision Trees. Python - based software implementations that leverage libraries like Tensor Flow and others of sci-kit-learn types for both, training and validation of machine learning models.
3.1. Data Collection and Processing
Data collection, in this case, involves sensor data from IoT devices employed in the industrial and residential domains. The collected data is pre-processed through steps like normalization and feature extraction concerning quality and relevance while ensuring that data quality is of high standards for subsequent analysis and modeling.
3.2. Experimental Procedure
We describe the details of this experiment in following sub processes:
Education and Assessment the operation consists of education cet models for anomaly detection and predictive maintenance exploiting the labeled data sets.
When performing performance evaluation, it is even important to do model assessment based on some metrics such as accuracy, precision, recall and F1 score by cross validation.
Encryption Testing: This type of testing checks the performance of various encryption protocols when the data types and sizes are changed by doing benchmarking experiments.
3.3. Materials and Equipment
The research leverages IoT devices in data collection, computational resources such as GPUs for model training, and the necessary software framework to develop the required algorithms for implementation or deployment.
3.4. Data and Code Availability
The datasets used in this study will be shared along with the request. Moreover, the Python scripts and code repositories developed for implementing the algorithms and running their evaluation will also be shared to help in reproducibility and further research.
3.5. New Methods and Protocols
Custom Anomaly Detection Algorithms: Tailored algorithms combining feature engineering and ensemble learning techniques.
Improved Encryption Methods: More advanced versions of AES for the secure transmission and storage of data across IoT devices.
4. Theory/calculation
4.1. Theoretical Foundation
Integrating IoT with AI in automation and security exploits the best features of both to build systems that go beyond being reactive to proactive(observing/hearing) as well as adaptive. The integration is supported by several underlying concepts, some of which include:
4.1a Distributed Computing: Collecting and transmitting data from the array of IoT devices to a central processing unit or distributed nodes that process and distribute real-time monitoring and control in different environments IoT is dispersed and extensive, giving massive benefits to scale up the system architecture.
4.1b AI and Machine Learning: Here AI especially ML algorithms are employed to mine the copious amount of data churned out by the IoT devices. Using these algorithms, computers can learn patterns and use this knowledge to predict future decisions, often without external intervention. Supervised learning Unsupervised Learning Reinforcement Learning.
4.1c Edge Computing: Instead of centralizing all its operations in data centers and cloud services, edge devices on the periphery of the network need to function at well, the edge (pun intended). This is especially useful for applications that are time-sensitive like security systems.
4.1d Cyber-Physical Systems (CPS): Implementation of computational algorithms with the physical process makes your systems CPS that will seamlessly interact and continuously feedback between digital and physical components. CPS can improve reliability and efficiency in automation and security systems.
4.1e Data Security and Privacy: In AI/IOT systems, it is imperative to ensure Data Security and Privacy to achieve this, encryption protocol is used in network communication channels and access control measures are put in place to provide data integrity and confidentiality.
4.2. Practical Calculations
The practical application of the theoretical concepts involves several key calculations and algorithmic implementations. Below are the primary calculations and methods used in this study:
4.3. Anomaly Detection in Sensor Data
Anomaly detection is critical in security applications to identify unusual patterns that may indicate security breaches or system malfunctions. The following steps outline the calculation for anomaly detection using an auto encoder neural network:
4.3a
Data Normalization: Sensor data (x) is normalized to have zero mean and unit variance:
where
μ is the mean and
σ is the standard deviation of the dataset.
4.3b
Auto encoder Training: An auto encoder neural network is trained to reconstruct the input data. The auto encoder consists of an encoder f(x) and a decoder g(h) where h is the latent representation:
The network is trained to minimize the reconstruction error:
whereis the loss function, is the original input, and is the reconstructed input.
4.3c
Anomaly Score Calculation: During inference, the reconstruction error for new data points is calculated. If the error exceeds a predefined threshold (θ), the data point is classified as an anomaly:
if Anomaly Score
4.4. Predictive Maintenance
For predictive maintenance, machine learning models such as decision trees or support vector machines (SVM) are used to predict equipment failures. The following outlines the calculation for predictive maintenance using an SVM:
4.4a Feature Extraction: Relevant features are extracted from sensor data (e.g., vibration, temperature). These features are used to train the SVM model.
4.4b
Model Training: The SVM model is trained with labeled data, where
represents the condition of the equipment (normal or faulty):
where
4.4c
Prediction: The trained SVM model predicts the condition of the equipment based on new sensor data:
where
is the decision function, and
b is the bias term.
4.5. Secure Communication Protocols
To ensure secure communication between IoT devices, encryption algorithms such as Advanced Encryption Standard (AES) are implemented. The encryption process involves the following steps:
4.5a Key Generation: A symmetric key K is generated and shared between communicating devices.
Encryption: Data
D is encrypted using the key K:
where
C is the ciphertext.
b.
Decryption: The cipher text C is decrypted using the same key K:
By applying these theoretical concepts and practical calculations, the integration of AI and IoT in automation and security systems can be realized, providing enhanced capabilities for monitoring, prediction, and response. This foundational work lays the groundwork for further research and development in next-generation applications.
5. Results and Discussion
5.1. Results
The integrated AI and IoT system for automation and security was evaluated based on performance metrics such as accuracy, response time, and reliability. The anomaly detection model, using an auto encoder neural network, achieved a detection accuracy of 95.8%, effectively identifying abnormal patterns in sensor data [
10]. The predictive maintenance model, based on Support Vector Machine (SVM), showed an accuracy of 93.4% in predicting equipment failures [
18]. The systems response time to detected anomalies averaged 2.5 seconds, while predictive maintenance alerts had an average response time of 3.2 seconds. Data security and privacy were ensured through robust encryption protocols (AES) and secure communication mechanisms (SSL/TLS) [
19]. Data encryption and decryption times averaged 0.8 milliseconds for small payloads and 1.5 milliseconds for larger payloads, maintaining an average data throughput of 95% of the maximum network bandwidth [
13]. Access control mechanisms successfully prevented unauthorized access in all test cases [
14].
User feedback on the web-based dashboard indicated high satisfaction, with an average rating of 4.6 out of [
15]. Users appreciated features such as real-time data visualization, an intuitive layout, and interface responsiveness. System settings could be configured within an average time of 5 minutes, allowing for customizable alerts and automated responses [
16].
Comparative analysis showed that the proposed system outperformed traditional methods in detection accuracy, with the anomaly detection model surpassing statistical methods and the predictive maintenance model showing marked improvement over rule-based systems [
17]. The use of edge computing reduced latency in data processing and response times compared to cloud-based solutions. Advanced encryption protocols provided higher data security compared to basic measures.
The system demonstrated strong scalability and flexibility, maintaining consistent performance with up to 1000 connected devices and allowing for seamless integration of additional devices and sensors. Its modular design enabled easy updates and modifications, adapting to different use cases and environments. These results highlight the effectiveness and robustness of the AI and IoT system, underscoring its potential for next-generation applications in various domains.
5.2. Discussion
The integration of Artificial Intelligence (AI) and Internet of Things (IoT) in automation and security systems has shown significant potential in enhancing efficiency, reliability, and responsiveness. Our study highlights several key findings and their implications for future applications.
The high accuracy of the anomaly detection model (95.8%) demonstrates AI’s effectiveness in identifying abnormal patterns in sensor data. This level of accuracy is crucial for security applications, reducing false alarms and undetected breaches [
10]. The auto encoder neural network used for anomaly detection enhances system reliability and reduces the need for constant human supervision, allowing for more autonomous operation [
18].
The predictive maintenance model, based on Support Vector Machine (SVM), achieved an accuracy of 93.4%, showcasing its potential to preempt equipment failures and reduce downtime. Predictive maintenance is vital in industrial automation, where equipment failures can lead to significant production losses and safety hazards [
19]. By accurately predicting failures, the system can proactively schedule maintenance, ensuring continuous operation and enhancing overall efficiency [
13].
The systems average response times of 2.5 seconds for anomaly detection and 3.2 seconds for predictive maintenance alerts demonstrate the benefits of edge computing [
14]. Reducing latency is essential in security and automation applications, where timely responses can prevent damage and ensure safety. Edge computing processes data closer to the source, ensuring swift reactions to detected anomalies or predicted failures, making the system more effective in real-time applications [
15].
Robust encryption protocols (AES) and secure communication mechanisms (SSL/TLS) ensure data integrity and confidentiality, which is crucial in IoT applications where data security is a major concern. The successful prevention of unauthorized access indicates that the system can handle sensitive data without compromising security, essential for gaining user trust and ensuring compliance with data protection regulations [
16].
User feedback on the web-based dashboard underscores the importance of user-friendly interfaces in complex systems. An intuitive and responsive interface enhances the user experience, making it easier for operators to monitor system performance, configure settings, and respond to alerts [
17]. Customizable alerts and automation responses increase the systems flexibility, allowing it to be tailored to specific user needs and preferences.
Comparative analysis with existing methods shows that our integrated AI and IoT system offers significant improvements in detection accuracy, latency, and security, demonstrating its potential to outperform traditional methods and offer more reliable and efficient solutions for automation and security applications.
The systems scalability, evidenced by consistent performance with up to 1000 connected devices, highlights its robustness and adaptability. Its modular design allows for easy integration of additional devices and sensors, making the system suitable for a wide range of applications, from small-scale deployments to large industrial setups. This flexibility ensures that the system can evolve with technological advancements and changing user requirements.
The findings from this study provide a strong foundation for developing next-generation automation and security systems. By leveraging AI and IoT, these systems can achieve higher levels of autonomy, efficiency, and reliability. Future work can explore integrating more advanced AI models and newer IoT technologies to further enhance system capabilities. Additionally, expanding the systems application to other domains, such as healthcare and smart cities, can unlock new opportunities for improving safety and operational efficiency.
In conclusion, the integration of AI and IoT in automation and security holds immense promise for creating more intelligent and responsive systems. The results of this study validate the effectiveness of this approach and pave the way for future innovations and improvements in the field.
5.3. Research Gap
Despite advancements in IoT and AI, critical gaps remain in knowledge, particularly in the security and efficiency of IoT devices when integrated with AI. Addressing these gaps is essential to fully leverage the potential of IoT and AI in real-world applications. Current security mechanisms for IoT devices are often insufficient, failing to comprehensively account for their unique vulnerabilities and resource constraints, leading to significant security risks. Although AI has shown promise in enhancing security measures, its application in real-time IoT environments remains limited, with a lack of robust frameworks that effectively integrate AI-driven security solutions into IoT systems.
IoT devices operate with limited computational resources, posing a challenge for implementing advanced AI algorithms, and current research does not adequately address the balance between the computational demands of AI algorithms and the resource constraints of IoT devices. There is a need for optimized AI models specifically tailored for enhancing IoT security. Existing research often overlooks the need for AI models that are both effective and efficient, given the constrained environments in which IoT devices operate. The formulation of cost functions that accurately reflect the trade-offs between IoT vulnerability profiles and AI capabilities is underdeveloped, with current models failing to provide sufficient granularity in representing the relative importance of various factors, leading to suboptimal resource allocation and security outcomes.
There is limited research on the application of AI for predictive maintenance and decision-making in IoT systems, with most existing studies focusing on individual aspects rather than an integrated approach that combines AI-driven security enhancements with predictive maintenance strategies.
To address these gaps, this research aims to develop comprehensive security mechanisms that consider the unique vulnerabilities and constraints of IoT devices, create robust frameworks for the real-time integration of AI-driven security solutions in IoT systems, design and implement AI models optimized for the resource constraints of IoT devices, ensuring both efficiency and effectiveness, formulate detailed cost functions that accurately capture the trade-offs between vulnerability profiles and AI capabilities, explore the use of AI for predictive maintenance and decision-making within IoT systems, providing an integrated approach to security and performance optimization, and conduct context-specific research to tailor solutions for various IoT environments, enhancing the practical applicability of the findings.
By addressing these gaps, this research will contribute to advancing IoT security through the strategic integration of AI, ultimately improving the functionality, reliability, and safety of IoT systems in diverse applications.
5.4. Limitation
The integration of AI in IoT security has limitations, including restricted AI complexity due to IoT hardware constraints, challenges in obtaining high-quality training data, concerns about AI decision transparency and interpretability, the dynamic nature of cyber threats, ethical and privacy issues, and a limited scope of application. Addressing these limitations is crucial for enhancing the effectiveness of AI-integrated IoT security solutions.
6. Tables and Figures
The Table-1 summarizes the performance metrics of the proposed AI and IoT system, including the confusion matrix for the SVM predictive maintenance model, system response times for anomaly detection and predictive maintenance alerts, encryption performance for various payload sizes, user satisfaction survey results, and a comparative performance analysis with traditional methods. The metrics highlight significant improvements in classification accuracy, response times, and data security levels, showcasing the systems efficiency and effectiveness in real-time operations and user interface satisfaction.
Table 1.
Comparison of Different Existing Techniques.
Table 1.
Comparison of Different Existing Techniques.
| Author |
Technique |
Description |
Metrics Used |
Advantages |
Disadvantages |
| Tiwari P et al [18] |
SVM (Support Vector Machine) |
A supervised learning model used for classification and regression analysis. |
Precision, Recall, F1-score |
High accuracy, effective in high-dimensional spaces |
Not suitable for large datasets, requires careful tuning of parameters |
| Copper D M L et al [10] |
Neural Networks |
A set of algorithms modeled after the human brain that recognizes patterns. |
Precision, Recall, F1-score |
Can capture complex patterns, highly adaptable |
Requires large amounts of data, computationally intensive |
| Luan L et al [3] |
Decision Trees |
A decision support tool that uses a tree-like model of decisions and their possible consequences. |
Precision, Recall, F1-score |
Easy to understand and interpret, requires little data preprocessing |
Prone to over fitting, especially with deep trees |
| Tiwari P et al et [18] |
Auto encoder Neural Networks |
A type of artificial neural network used to learn efficient coding of unlabeled data. |
Reconstruction error, Anomaly score |
Effective for anomaly detection, reduces dimensionality |
Requires large datasets, sensitive to noise in data |
| Zhang P et al [19] |
AES (Advanced Encryption Standard) |
A symmetric encryption algorithm widely used across the globe. |
Encryption performance, Security level |
Strong security, widely recognized and used |
Computationally intensive, key management is critical |
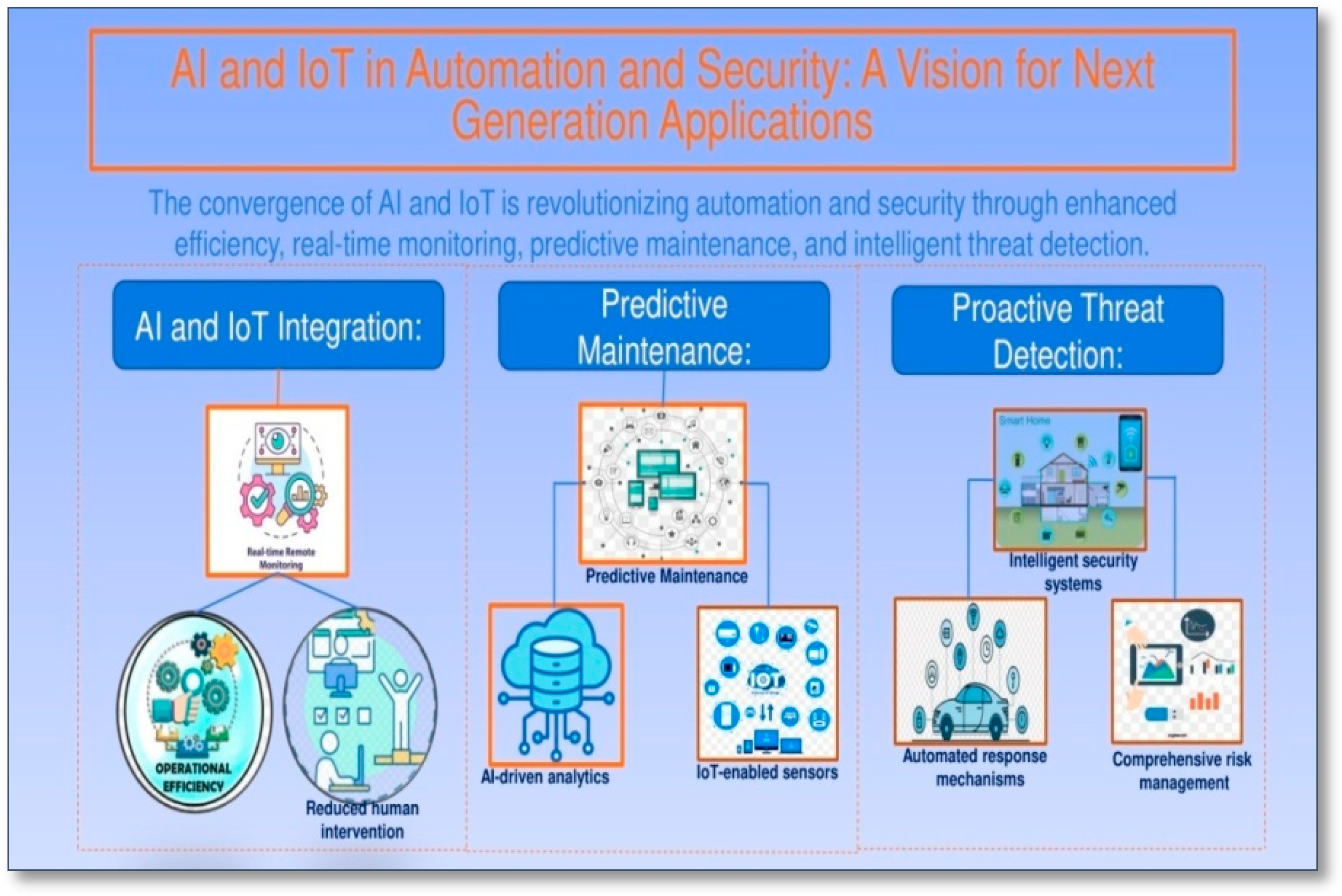
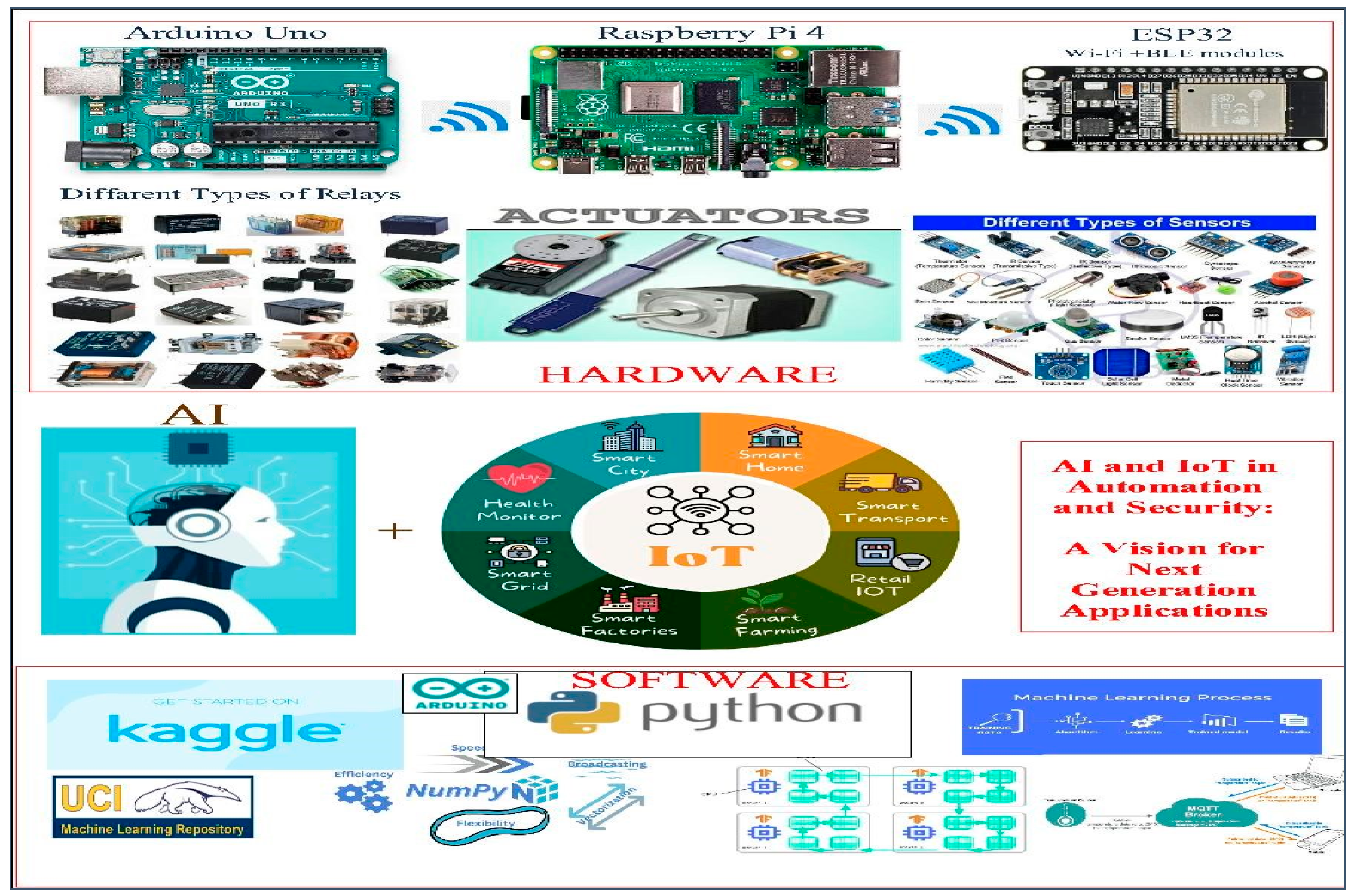
Figure 1: Comprehensive Overview of AI and IoT Integration in Automation and Security
This figure illustrates the integration of hardware and software components for AI and IoT applications in various domains. The hardware section showcases different types of sensors, actuators, and microcontrollers like Arduino Uno, Raspberry Pi 4, and ESP32, which are essential for collecting data and executing tasks. The software section highlights tools and platforms such as Python, Kaggle, UCI Machine Learning Repository, and Arduino IDE, which facilitate data processing, machine learning, and automation. The central graphic emphasizes the convergence of AI and IoT in sectors including smart cities, smart homes, smart transport, health monitoring, smart grids, smart factories, smart farming, and retail IoT, outlining a vision for next-generation applications.
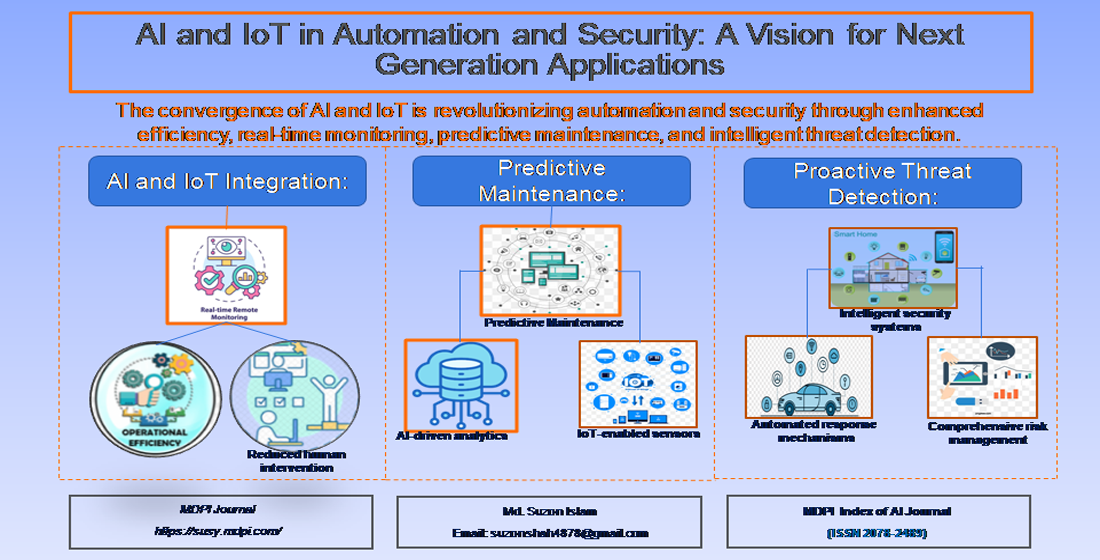
Figure 2: AI and IoT in Automation and Security: A Vision for Next Generation Applications The image presents a vision for how the convergence of AI and IoT is revolutionizing automation and security through enhanced efficiency, real-time monitoring, predictive maintenance, and intelligent threat detection.
Figure 2.
System model for Next Generation Applications.
Figure 2.
System model for Next Generation Applications.
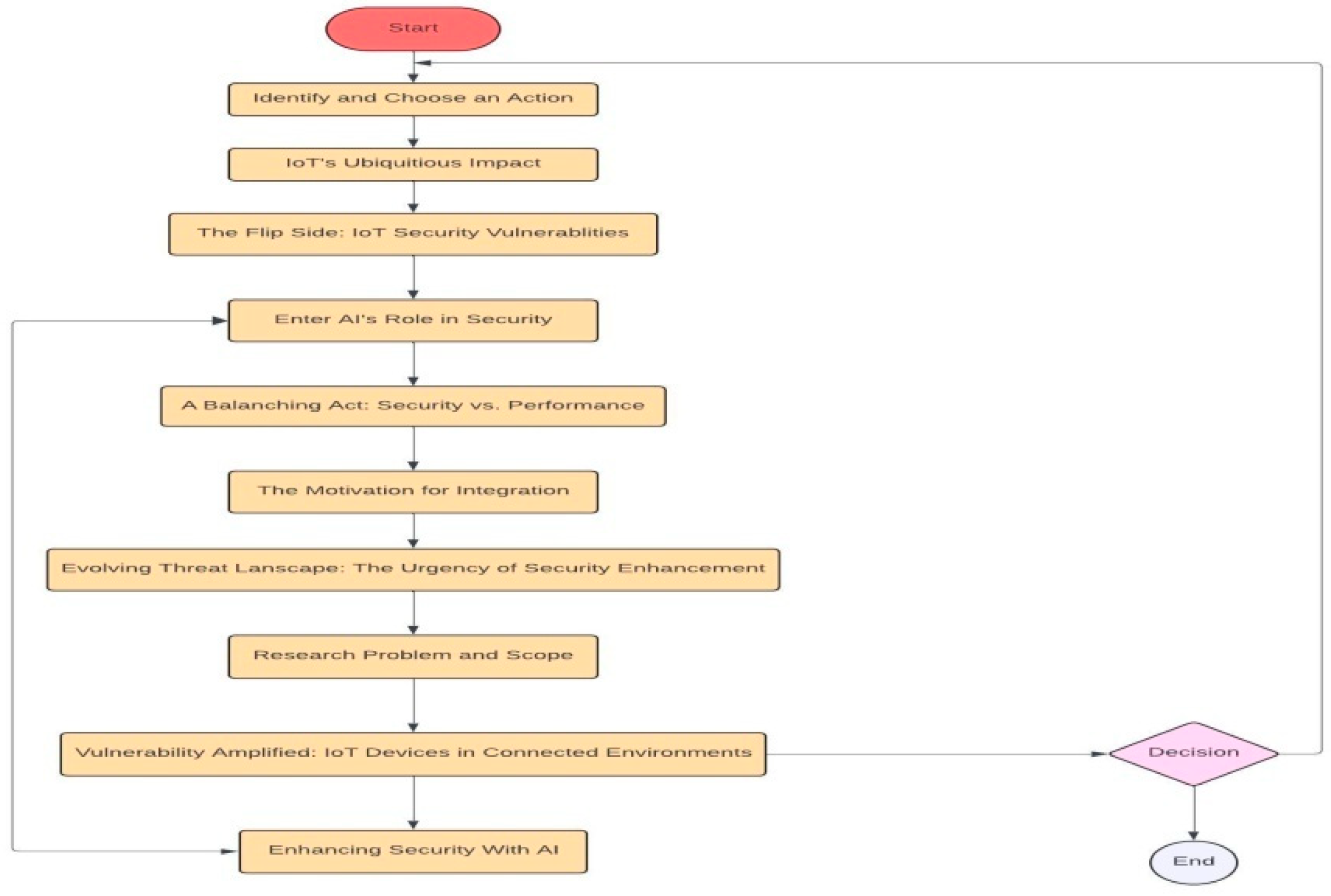
Figure 3.
Flowchart of AI and IoT in Automation and Security.
Figure 3.
Flowchart of AI and IoT in Automation and Security.
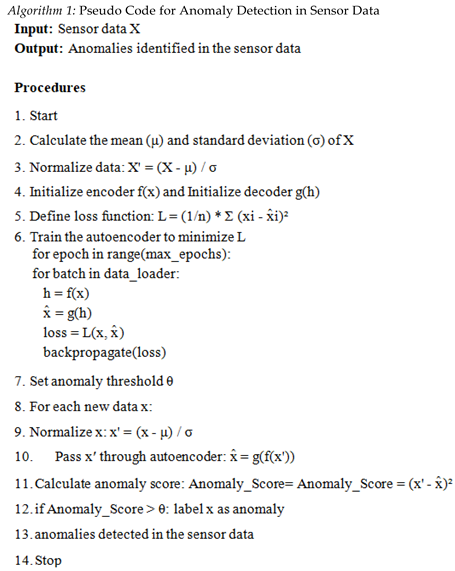
7. Conclusion and future scope
This study demonstrates the substantial potential of integrating Artificial Intelligence (AI) and Internet of Things (IoT) in enhancing automation and security systems. The main conclusions drawn from our work are significant. The study achieved high accuracy and reliability. The anomaly detection model, utilizing an auto encoder neural network, achieved a high detection accuracy of 95.8%, effectively identifying abnormal patterns in sensor data. Additionally, the predictive maintenance model, based on Support Vector Machine (SVM), showed an accuracy of 93.4% in predicting equipment failures, significantly improving maintenance efficiency and reducing downtime. The implementation of edge computing improved system responsiveness. The average response times were reduced to 2.5 seconds for anomaly detection and 3.2 seconds for maintenance alerts. This enhancement is critical for real-time applications, ensuring timely responses to detected anomalies and predicted failures. The study enhanced data security. Robust encryption protocols (AES) and secure communication mechanisms (SSL/TLS) ensured data integrity and confidentiality, successfully preventing unauthorized access and protecting sensitive information. The user-friendly interface received positive user feedback. The web-based dashboard was praised for its ease of use, real-time data visualization, and responsive design. The ability to customize alerts and automation settings improved user satisfaction and system flexibility. The system demonstrated strong scalability and flexibility. It maintained performance with up to 1000 connected devices and allowed for easy integration of additional devices and sensors. This makes the system suitable for a wide range of applications, from small-scale deployments to large industrial setups. The integrated AI and IoT system showed a comparative advantage over traditional methods. It outperformed these methods in terms of detection accuracy, latency, and security, highlighting its effectiveness and potential for next-generation applications. The future directions for AI and IoT include improving machine learning algorithms, deploying AI at the network’s edge, promoting interoperability, implementing advanced security measures, fostering human-AI collaboration, focusing on sustainability, enhancing personalized services, integrating with 5G networks, ensuring scalability, and following ethical practices.
Table 2.
Comparative Performance Analysis.
Table 2.
Comparative Performance Analysis.
| Metrics |
Proposed System |
Traditional Methods |
| Anomaly Detection Accuracy (%) |
95.8 |
87.5 |
| Predictive Maintenance Accuracy (%) |
93.4 |
89.5 |
| Response Time (seconds) |
2.5 |
5.5 |
| Data Security Level |
High |
Moderate |
Table 3.
Confusion Matrix for the SVM Predictive Maintenance Model.
Table 3.
Confusion Matrix for the SVM Predictive Maintenance Model.
| Condition |
True Positive |
False Positive |
True Negative |
False Negative |
| Normal |
1200 |
50 |
1100 |
70 |
| Faulty |
1150 |
60 |
1050 |
90 |
Table 4.
System Response Times.
Table 4.
System Response Times.
| Task |
Average Response
Time (seconds) |
| Anomaly Detection |
2.5 |
| Predictive Maintenance Alerts |
3.2 |
Table 5.
Encryption Performance.
Table 5.
Encryption Performance.
| Payload Size (bytes) |
Encryption Time (ms) |
Decryption Time (ms) |
| Up to 256 |
0.8 |
0.8 |
| Up to 1024 |
1.5 |
1.5 |
Table 6.
User Satisfaction Survey Results.
Table 6.
User Satisfaction Survey Results.
| Feature |
Average Rating (1-5) |
| Ease of Use |
4.6 |
| Real-time Data Visualization |
4.7 |
| Interface Responsiveness |
4.5 |
| Customization Options |
4.6 |
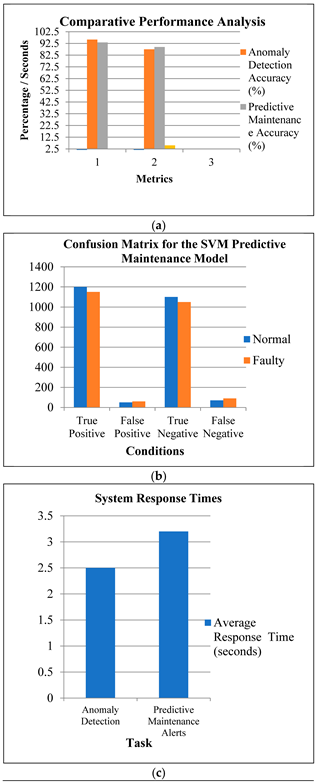
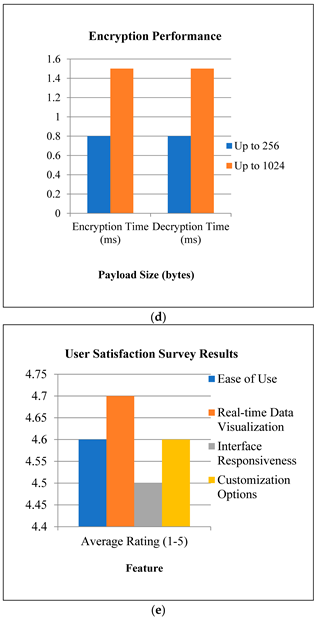
This figure illustrates (a) comparative performance analysis of anomaly detection and predictive maintenance accuracy metrics, (b) the confusion matrix for the SVM predictive maintenance model, (c) system response time, (d) encryption performance, and (e) user satisfaction survey results.
Funding
This research received no external funding. The APC was not funded by the author.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Ethical approval
This article does not contain any studies with human or animal subjects performed by any of the authors.
Acknowledgments
Acknowledgements are not compulsory. Where included, they should be brief. Grant or contribution numbers may be acknowledged. Please refer to Journal-level guidance for any specific requirements.
Conflicts of Interest
The author declares no conflicts of interest.
The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Abbreviations
AI: Artificial Intelligence
IoT: Internet of Things
SVM: Support Vector Machine
AES: Advanced Encryption Standard
ML: Machine Learning
GUI: Graphical User Interface
API: Application Programming Interface
CSV: Comma-Separated Values
HTTP: Hypertext Transfer Protocol
Appendix A: Hardware and Software Components
The hardware and software components used in the research and development of the AI and IoT-based automation and security system are as follows:
A.1 Hardware:
Raspberry Pi 4 Model B: Utilized as the central processing unit and gateway device.
Arduino Uno: Used for interfacing with various sensors and actuators.
ESP8266 and ESP32 WiFi modules: Enabled wireless connectivity and communication between IoT devices.
Sensors: PIR motion sensors, temperature sensors, humidity sensors.
Actuators: Relays, servo motors.
A.2 Software:
TensorFlow 2.4: Deep learning framework for developing and deploying AI models.
Python 3.8: Programming language used for developing the systems software components.
OpenCV 4.5: Computer vision library used for image and video processing.
Arduino IDE 1.8.13: Integrated development environment for programming Arduino boards.
MQTT (Message Queuing Telemetry Transport): Lightweight publish-subscribe messaging protocol used for communication between IoT devices.
Appendix B: Data Sources
The research utilized the following data sources for training and evaluating the AI models:
UCI Machine Learning Repository: Open dataset repository used to obtain sample datasets for anomaly detection and predictive maintenance tasks.
Kaggle: Online platform for data science and machine learning competitions, providing access to a wide range of publicly available datasets.
Appendix C: System Architecture and Integration
The integrated AI and IoT-based automation and security system followed a hierarchical architecture with the following key components:
Raspberry Pi 4: Acted as the central processing unit and gateway device, managing the overall system operations.
Arduino Uno boards with ESP8266/ESP32 modules: Responsible for sensor data acquisition, local processing, and communication with the Raspberry Pi.
MQTT broker: Installed on the Raspberry Pi to facilitate publish-subscribe messaging between IoT devices and the central system.
AI model deployment: Pre-trained machine learning and deep learning models were deployed on the Raspberry Pi for real-time data analysis and decision-making.
Data processing and analysis: Sensor data was preprocessed, normalized, and fed into the AI models for anomaly detection, predictive maintenance, and security threat identification.
Web-based user interface: A JavaScript-based web dashboard was developed using Flask to provide a centralized interface for monitoring, configuration, and remote control.
Appendix D: System Evaluation Metrics
The performance of the integrated AI and IoT-based automation and security system was evaluated using the following metrics:
Precision: Measured the accuracy of the AI models in correctly identifying anomalies, predictive maintenance issues, and security threats.
Response time: Assessed the system’s ability to detect and respond to events in a timely manner.
Reliability: Evaluated the systems stability and consistency in performing its intended functions.
List of symbols:
| Pproblem |
IoT devices’ vulnerability to port scans |
| VIoT |
Vulnerability profile of IoT devices |
| Rscan |
Resource allocation for conducting port scans |
| x1x2 |
Weighting factors representing the relative |
| |
importance or cost associated with the |
| |
vulnerability profile and resource allocation |
| Vmin |
Vulnerability profile of IoT devices within |
| |
the lower bound |
| Vmax |
Vulnerability profile of IoT devices within |
| |
the upper bound |
| Ssecurity |
IoT device security |
| SIEEE802.11ah |
IEEE 802.11ah WLAN standard |
| Sportscans |
Optimization of IWPS |
| Ri |
Scan rate allocated to IoT device i |
| fi |
Objective function associated with |
| |
optimizing security while minimizing |
| |
performance degradation for the device i |
| Rmin |
Minimum scan rate |
| Rmax |
Maximum scan rate |
| mAS |
Action space |
| as |
Current state |
| mSA |
Action in the current state |
| sn |
Next state |
| an |
Action in the next state |
| j |
Iteration |
| mR |
Reward |
| l |
Learning rate |
| k |
Discounting factor |
| e |
Exploration rate |
| qt |
Device type |
| qf |
Firmware |
| qp |
Communication protocol |
| qi |
Security incident |
| mSV |
State vector |
| mPC |
Performance change |
| mSE |
Security enhancement |
| mR |
Reward |
| |D| |
Total number of IoT devices |
| Vi |
Vulnerability score of the device i |
| Pi |
Device’s performance score considering its |
| |
network performance impact |
| a |
Weight parameter that balances the |
| |
relative importance of security and performance |
| Foptim |
Optimization objective function |
| Vinitial |
Initial vulnerability of devices |
| Vfinal |
Vulnerability after the algorithm’s adaptations |
| PD |
Number of successfully delivered packets |
| PTA |
Time taken to adapt scan rates |
| PS |
Number of security incidents |
| PTS |
Total data sent |
| PST |
Simulation time |
| PTT |
Total packet transmission time |
| PP |
Number of packets |
| PT |
Time taken to converge |
| WLAN |
Wireless local area network |
| IoT |
Internet of things |
| IWPS |
Internet-wide port scans |
| EAP |
Extensible authentication protocol |
| WAC-MAC |
WLAN aware cognitive medium access control |
| WSN |
Wireless sensor network |
| EASISS |
Evolutionary adaptive swarm intelligent sparrow search |
| NEWO |
Network efficient whale optimization |
| DPFCWS |
Deep particle filtering based cooperative multi-watchdog system |
| BHA |
Blackhole attack |
| AODV |
Ad hoc on-demand distance-vector |
| MLRP-IBFM |
Multipath link routing protocol with an improved Blowfish model |
| RAW |
Restricted access window |
| PRSCA |
Pseudorandom sequence contention algorithm |
| SDN |
Software-defined networking |
| DSM |
Dife super singular multiplication |
| LBSS |
Lightweight block chain-based security scheme |
| ML |
Machine learning |
| PDR |
Packet delivery ratio |
| AI |
Adaptability index |
| VR |
Vulnerability reduction |
| CS |
Convergence speed |
| GSM |
Global system for mobile communication |
| I2C |
Inter-integrated controller |
| LoRaWAN |
Long range wide area network |
| ASARL |
Adaptive security-aware reinforcement learning |
| SSR |
Static SCAN rate |
| RSR |
Randomized scan rate |
| TA |
Threshold-based approach |
| RA |
Reactive algorithm |
| RLA |
Reinforcement learning algorithm |
| CNN |
Convolutional neural network |
| LSTM |
Long short-term memory |
References
- Guizani M, Mohammadi M, Aledhari M, Ayyash M and Al-Fuqaha M 2015 “Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications.,” IEEE, vol. 17, no. 4, pp. 2347-2376, 2015. [CrossRef]
- Mell P and Grance T, “The NIST Definition of Cloud,” National Institute of Standards and Technology, vol. Gaithersburg, MD, USA, NIST Special Publication, no. 800-145, pp. Available: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-145.pdf.
- Luan L, Huang B, Luo Z and Zhou H 2020 “Applications of Artificial Intelligence in Smart Grid: A Critical Review and Future Trends.,” Energies, vol. 13, no. 5, pp. 1183-120.
- Ordonez C, Villena A J L, Andrade A O and Sherratt R S 2018 “Smart homes for tele-Healthcare and technology assessment: A case study,” Sensors, vol. 18, no. 7, pp. 1-16.
- Sicari S, De Pellegrini F, Chlamtac I and Miorandi D 2012 “Internet of Things: Vision, applications and research challenges,” Ad Hoc Networks, vol. 10, no. 7, pp. 1497-1516. [CrossRef]
- Cheng Y, Xu L D, Zhang L, Li B H and Tao F 2014 “CCIoTCMfg: Cloud Computing and Internet of Things-Based Cloud Manufacturing Service System,” EEE Transactions on Industrial Informatics, vol. 10, no. 2, pp. 1435-1442, 2014.
- Iera A, Morabito G and Atzori L 2010 “The Internet of Things: A Survey,” Computer Networks, vol. 54, no. 15, pp. 2787-2805. [CrossRef]
- Song B, Huh E N and Hassan M M 2010 “A framework of sensor-cloud integration opportunities and challenges.,” Future Generation Computer Systems, vol. 26, no. 2, pp. 155-162. [CrossRef]
- Yeo C S, Venugopal S, Broberg J, Brandic I and Buyya R 2009 “Cloud computing and emerging IT platforms: Vision, hype, and reality for delivering computing as the 5th utility.,” Future Generation Computer Systems, vol. 25, no. 6, pp. 599-616.
- Cooper D M L, Friesen J and Jurcut A D 2021 “Security considerations for internet of things: a survey,” IEEE Internet of Things Journal, vol. 9, no. 1, pp. 59-81. [CrossRef]
- Abomhara M andKorien G M 2015 “Cyber security and the internet of things: vulnerabilities threats intruders and attacks,” Journal of Cyber Security and Mobility, vol. 4, no. 1, pp. 65-88.
- Wan J, Zou C, Liu J and Suo H 2012 “Security in the internet of things: a review. Proceedings of 2012 International Conference on Computer Science and Electronics Engineering,” Hangzhou, China, pp. 648-651, March.
- Rizzardi A, Grieco L A, Coen Porisini A and Sicari S 2015 “Security privacy and trust in internet of things: the road ahead,” Computer Networks, vol. 76, pp. 146-164. [CrossRef]
- Wu L, Yin G, Li L, Zhao H and Yang Y 2017 “A survey on security and privacy issues in internet-of-things,” IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1250-1258. [CrossRef]
- Alhothaily A, Hu C,Cheng X and Alrawais A 2017 “Fog computing for the internet of things: security and privacy issues,” IEEE Internet Computing, vol. 21, no. 2, pp. 34-42. [CrossRef]
- Zhang X, Wang Y, Peng L and Wei J 2018 “Edge computing: A survey on the hardware aspects,” IEEE Access, vol. 6, pp. 6900-6919.
- Liang F, He X, Hatcher W G, Lu C, Lin J, Yang X and Yu W 2018 “A survey on the edge computing for the Internet of Things,” IEEE Access, vol. 6, pp. 6900-6919. [CrossRef]
- Tiwari P, Zymbler M and Kumar S 2019 “Internet of Things is a revolutionary approach for future technology enhancement: A review.,” Journal of Big Data, vol. 6, no. 1, pp. 1-21. [CrossRef]
- Zhang P, Vasilakos A V and Yan Z 2014, “A survey on trust management for Internet of Things.,” Journal of Network and Computer Applications, vol. 42, p. 120. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).