I. Introduction
As technology advances at an unprecedented rate, the landscape of information technology is constantly altered, with cloud computing developing as a foundation for data processing and storage [
1]. Its integration provides unprecedented comfort and efficiency, transforming the way enterprises and industries function [
2]. However, atop this transformative potential is a primary concern: protecting sensitive data from ever-changing cybersecurity threats.
Cloud computing’s attractiveness is clear, as it promises scalable resources, cost-effectiveness, and seamless accessibility [
3]. However, this allure highlights the need for strong security measures [
4]. The increasing nature of cyber threats necessitates proactive methods to strengthen defenses, particularly in information-critical sectors such as healthcare and finance, where the stakes are extremely high.
In this paper, we will take a comprehensive look at the intricate web of issues and concerns that surround cloud computing security in information-critical industries. Our focus goes beyond simply acknowledging these difficulties; we go deeply into understanding their complexities and implications. We analyze the multiple facets of cloud security, from data breaches to regulatory compliance.
Furthermore, we seek to highlight the route forward by presenting practical solutions customized to the specific requirements of vital businesses. Our goal is not only to identify the challenges to general acceptance of cloud computing but also to provide actionable advice for efficiently overcoming them. By providing companies with the knowledge and resources they need to safely navigate the digital frontier, we hope to promote a culture of trust and resilience in the face of growing cybersecurity threats.
II. Understanding and Implementing Cloud Security Measures
Cloud computing has transformed how businesses work, providing scalability, flexibility, and cost-effectiveness. However, transferring data and apps to the cloud creates additional security challenges. Cloud security refers to the rules, methods, and procedures that protect data, applications, and infrastructure in cloud settings. This research digs into the ever-changing environment of cloud security, emphasizing three critical segments.
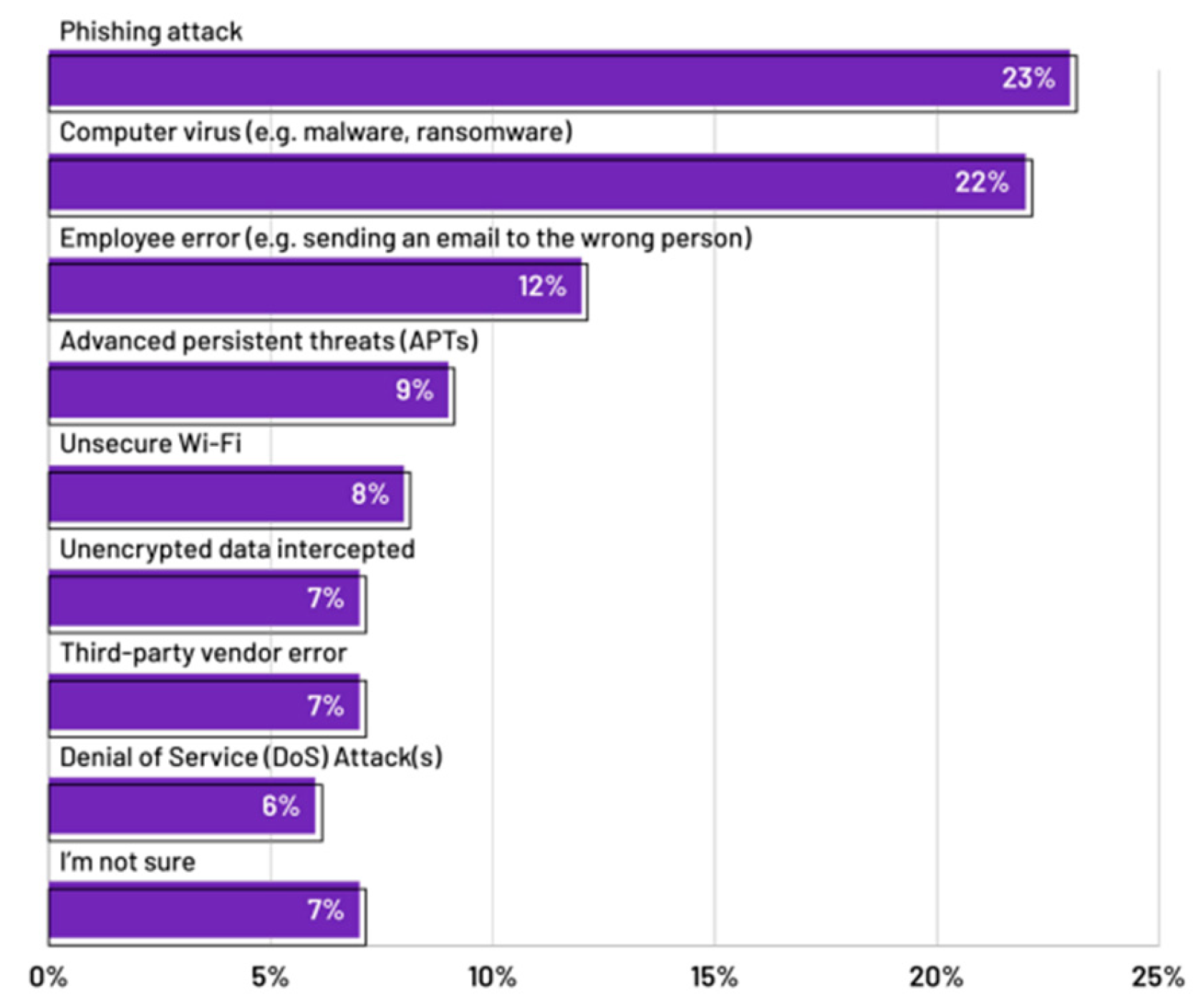
Figure 1.
Different Types Of Attack Happening [
19].
Figure 1.
Different Types Of Attack Happening [
19].
A. Shared Security Responsibility Model
Cloud providers and clients share responsibility for cloud security. Depending on which service model is being utilized, different jobs are assigned differently (IaaS, PaaS, or SaaS). Customers are responsible for preserving their data, apps, and configurations on the cloud, while cloud providers are in charge of maintaining the foundational framework. Businesses need to understand this shared concept to implement effective cloud security solutions. Consider a company that is moving its customer data to a cloud-based system. The cloud provider would be responsible for the physical security of the data center, while the organization would be in charge of safeguarding the database and managing access permissions [
5].
B. Data Encryption and Access Controls
Security of data is crucial when using the cloud. Encryption jumbles data, rendering it unintelligible to unauthorized individuals while it’s in transit or at rest. Organizations should select encryption solutions based on their unique security needs, as cloud providers give a range of options. Strong access controls are also necessary. Granular access control policies guarantee that sensitive data in the cloud environment can only be accessed by authorized users and apps. Consider a situation where a company’s marketing department requires access to client email addresses for a campaign. By granting them read-only access, you reduce the possibility of unintentional data breaches or unwanted modifications.
C. Threat Detection, Response, and Compliance
Cloud security is an ongoing process that necessitates continuous monitoring and threat detection capabilities. Cloud providers offer security tools and services to monitor for suspicious activity, such as unusual login attempts or unauthorized data access. Additionally, organizations can leverage their security solutions to provide a layered defense. Having a well-defined incident response plan is crucial to promptly address security breaches and minimize damage. Furthermore, compliance with relevant data privacy regulations is essential for organizations operating in the cloud. Imagine a company experiencing a data breach in the cloud. A well-defined response plan would outline steps to investigate the breach, contain the damage, and notify affected individuals. Additionally, strong compliance practices ensure adherence to data privacy regulations, mitigating legal risks.
D. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) solutions play a pivotal role in modern cybersecurity frameworks. These robust platforms are designed to collect, correlate, and analyze security event data from diverse sources, both within and outside the organization’s network. By aggregating logs and telemetry data from endpoints, servers, applications, network devices, and cloud services, SIEM solutions provide comprehensive visibility into the organization’s digital environment.
The capacity of SIEM solutions to offer real-time threat detection and response capabilities is one of its main advantages. By keeping an eye on all incoming security occurrences, SIEM platforms can swiftly identify suspicious activities, anomalies, and potential threats. Through sophisticated correlation and analysis techniques, these tools can prioritize security alerts, allowing security teams to focus their efforts on the most critical issues.
In the context of cloud computing, SIEM solutions play a vital role in enhancing security posture. As organizations increasingly migrate their workloads and data to cloud environments, the need for effective threat detection and response mechanisms becomes paramount. SIEM tools extend their capabilities to cloud platforms, enabling organizations to monitor and protect their cloud infrastructure, applications, and data.
Furthermore, SIEM solutions facilitate compliance with regulatory requirements and industry standards by providing centralized logging, auditing, and reporting capabilities. This ensures that organizations can demonstrate adherence to security policies and regulatory mandates, mitigating the risk of non-compliance penalties.
In summary, SIEM solutions serve as a cornerstone of modern cybersecurity strategies, empowering organizations with enhanced threat detection, rapid incident response, and regulatory compliance capabilities in both on-premises and cloud environments [
9].
Implementing robust cloud security measures is crucial to protect sensitive data and ensure the integrity of cloud-based applications and services. By understanding the fundamentals of cloud security, following best practices, and leveraging security service offerings, organizations can enhance their overall security posture in the cloud.
III. Supply Chain Security: Fortifying the Links in the Digital Age
The modern business landscape thrives on interconnectedness. Global supply chains play a crucial role in delivering goods and services, but this very interconnectedness introduces vulnerabilities. Supply chain security focuses on identifying, mitigating, and managing risks associated with the entire chain of suppliers, vendors, and partners involved in delivering a product or service. This report explores the growing importance of supply chain security, highlighting three key subtopics that are critical for building resilience [
6].
A. Risk Assessment and Threat Identification
Effective supply chain security begins with a comprehensive risk assessment. This involves mapping the entire supply chain and identifying all participants and their locations. Organizations need to understand the security practices of their vendors, potential vulnerabilities within their systems, and the types of threats each link in the chain might face. These threats can range from cyberattacks targeting critical infrastructure to physical theft or counterfeit components being introduced into the manufacturing process. Imagine a company relying on a sole supplier for a critical component in their product. A risk assessment might reveal that this supplier has weak cybersecurity practices, making the entire production line vulnerable to a cyberattack targeting the supplier’s systems.
B. Security Controls and Vendor Management
Security Controls and Vendor Management Once risks are identified, organizations can implement security controls to mitigate them. This might involve mandating specific security standards for vendors, conducting regular security audits, and enforcing data encryption practices throughout the supply chain.
Building strong relationships with vendors and fostering open communication is crucial for collaborative risk management. By establishing clear contractual agreements that outline security expectations and compliance requirements, organizations can ensure that vendors understand and adhere to the necessary security measures. Regular vendor performance monitoring allows organizations to assess and verify that vendors are maintaining the required security standards.
To further enhance supply chain security, organizations can leverage industry best practices and available security frameworks. These frameworks provide guidelines and recommendations for implementing comprehensive security controls across the entire supply chain. By aligning with recognized security standards, organizations can establish a robust security posture and ensure consistency in security practices throughout their vendor network.
For example, when partnering with a new overseas manufacturer, implementing security controls such as requiring multi-factor authentication and conducting penetration testing of the vendor’s systems can significantly reduce the risk of unauthorized access or malicious software infiltration. These measures help protect sensitive information and prevent potential security breaches that could compromise the integrity of the supply chain.
In conclusion, implementing security controls and effective vendor management practices are essential for mitigating risks and ensuring the security of the supply chain. By mandating security standards, conducting audits, enforcing data encryption, and fostering collaboration with vendors, organizations can establish a strong security posture and protect against potential threats. Leveraging industry best practices and security frameworks further enhances the overall security of the supply chain ecosystem.
C. Incident Response and Continuity Planning
Security breaches can happen even with the greatest safeguards in place. For a supply chain security event to be quickly contained and handled, a clear incident response strategy is necessary. This plan should outline procedures for identifying the breach, isolating the affected areas, and implementing recovery measures. Additionally, business continuity planning ensures minimal disruption to operations in the event of a supply chain disruption. This might involve diversifying suppliers, building redundancy into critical processes, and maintaining a backup stock of essential components. Imagine a cyberattack crippling a key supplier’s operations. An effective incident response plan would allow the organization to isolate the issue, identify alternative suppliers, and minimize production delays [
8].
IV. Securing the Billions of Connected Things
The Internet of Things (IoT) revolution is transforming our world. Billions of devices, from smart thermostats to connected cars, are being woven into the fabric of our lives. However, this interconnectedness comes with a security challenge. IoT Security refers to the strategies and practices employed to safeguard these internet-connected devices from cyberattacks. This report explores the complexities of IoT security, highlighting three crucial subtopics that are critical for a secure connected future
A. Device Security and Patch Management
Many IoT devices are resource-constrained, with limited processing power and memory. This often translates to weak security features out of the box. Insecure default configurations, outdated firmware, and the lack of timely security patches leave these devices vulnerable to exploitation. Strong IoT security begins with securing the devices themselves. Manufacturers need to prioritize robust security features, implement secure coding practices, and provide regular firmware updates to address vulnerabilities. Organizations deploying IoT devices should actively manage patches, ensuring their systems are up-to-date and protected against known threats. Imagine a scenario where a home security camera has a critical vulnerability in its firmware. An attacker could exploit this vulnerability to gain access to the camera’s feed, potentially compromising the homeowner’s privacy.
B. Network Segmentation and Access Control
Not all IoT devices require full internet access. Segmenting the network creates isolated zones for different device types, limiting the potential damage an attacker can inflict if they compromise a single device. Additionally, implementing granular access controls restricts communication between devices and ensures that only authorized devices can access sensitive data on the network. Organizations can leverage network segmentation and access control solutions to create a layered defense against cyberattacks within the IoT ecosystem. Imagine a smart light bulb in a home network. Segmenting the network can isolate it from critical devices like computers, minimizing the risk of an attacker pivoting through the compromised light bulb to access more sensitive systems.
C. Threat Detection and Vulnerability Management
Continuous monitoring is essential for effective IoT security. Security teams need to deploy tools to detect suspicious activity on the network, identify potential vulnerabilities in connected devices, and respond promptly to security incidents. This might involve leveraging anomaly detection systems, vulnerability scanners specifically designed for IoT devices, and security information and event management (SIEM) solutions. Organizations should establish a proactive approach to threat detection and vulnerability management to stay ahead of evolving cyber threats. Imagine a large company deploying thousands of connected sensors in their manufacturing facilities. Proactive threat detection can identify unusual data patterns or communication attempts, potentially revealing a compromised device being used for malicious purposes within the network.
V. Cybersecurity for Remote Work
The rise of remote work has transformed the way businesses operate. While it offers flexibility and cost benefits, it also introduces new cybersecurity challenges. Cybersecurity for remote work encompasses the strategies, tools, and practices employed to protect an organization’s data, applications, and systems when employees work outside the traditional office environment. This report explores this critical topic, highlighting three key areas to ensure a secure remote work environment.
A. Endpoint Security and Access Control
In a remote work environment, traditional network security perimeters lose some of their significance. To protect individual devices, like as laptops and mobile phones, used by distant employees, endpoint security solutions are crucial. To recognize and stop threats on distant devices, these solutions offer capabilities including intrusion detection, anti-virus, and anti-malware protection. Putting in place robust access controls is also essential. By adding a layer of protection on top of passwords, multi-factor authentication (MFA) increases the difficulty for unauthorized users to access critical data. Suppose that an employee works from home and their laptop gets infected with malware. By identifying and containing the danger, endpoint security software stops malware from proliferating throughout the corporate network.
B. Secure Network Connectivity and Data Encryption
In a remote work environment, traditional network security perimeters lose some of their significance. To protect individual devices, like as laptops and mobile phones, used by distant employees, endpoint security solutions are crucial. To recognize and stop threats on distant devices, these solutions offer capabilities including intrusion detection, anti-virus, and anti-malware protection. Putting in place robust access controls is also essential. By adding a layer of protection on top of passwords, multi-factor authentication (MFA) increases the difficulty for unauthorized users to access critical data. Suppose that an employee works from home and their laptop gets infected with malware. By identifying and containing the danger, endpoint security software stops malware from proliferating throughout the corporate network.
D. Additional Measures to Enhance Security
Multi-factor authentication (MFA): To provide an additional degree of protection, use MFA for all remote access to systems and apps.
Frequent Software Updates and Patch Management: To fix known vulnerabilities, keep all systems and software up to date with the most recent security patches.
Tight Password Regulations: Implement stringent guidelines for passwords, requiring them to be lengthy, difficult, and changed frequently.
Network Segmentation: To separate important systems and lessen the possible effect of a security compromise, use network segmentation.
Incident Response Plan: To ensure a timely and efficient response to security concerns, develop and test an incident response plan regularly.
Employee Monitoring and User Behavior Analytics: To identify and address questionable activity or internal threats, make use of monitoring technologies and user behavior analytics.
Data Backup and Recovery: To reduce the effects of data loss or ransomware attacks, regularly back up important data and create a solid data recovery strategy.
Mobile Device Security: Put in place safeguards for mobile devices, such as secure app installation, remote wipe capabilities, and encryption.
Frequent Security Audits and Assessments: To find vulnerabilities and make sure security standards are being followed, conduct regular security audits and assessments.
Ongoing Security Training and Awareness: To keep staff members up to date on the newest dangers and best practices, provide them with regular security training and awareness programs.
By implementing these additional measures, organizations can further enhance their security posture and protect against a wide range of cyber threats.
VI. Cybersecurity for Healthcare: Protecting Patients and Preserving Trust
Patient medical records are among the most sensitive data that the healthcare sector protects. Because cybercriminals can profit greatly from this information, healthcare is a major target for hacks. Healthcare cybersecurity refers to the methods and tools used to prevent unwanted access, use, disclosure, disruption, modification, or destruction of electronic patient data, medical equipment, and healthcare infrastructure. Three important themes are highlighted in this report’s exploration of the crucial field of healthcare cybersecurity.
A. Data Security and Compliance
Protecting patient data is crucial. HIPAA and GDPR require strict security measures to protect patient data. Healthcare organizations must implement strong access restrictions, data encryption, and activity monitoring to prevent data breaches and unauthorized access. Audits and vulnerability assessments are needed to identify and fix security posture issues. Consider this scenario: A hospital’s database with patient medical records is hacked. Fraudulent use or dark web sale of stolen data. Strong data security procedures can prevent these security breaches and protect patient privacy.
B. Phishing Awareness and Workforce Training
Cyberattacks often begin with phishing emails and other social engineering. Healthcare workers are easy targets because they handle sensitive data. Frequent security awareness training helps employees spot phishing and social engineering. Training should emphasize secure password handling, suspicious behavior reporting, and data reporting. Creating a cybersecurity culture in healthcare companies can greatly reduce human errors that lead to security incidents. Imagine a nurse receiving a phishing email requesting patient data. Social engineering training helps them spot warning signs and protect private data [
10].
Figure 2.
Percentage of Phishing Attacks Happening In HTTPS Hosted Site [
20].
Figure 2.
Percentage of Phishing Attacks Happening In HTTPS Hosted Site [
20].
This training should emphasize several key areas:
Robust Password Management: Creating and maintaining strong, unique passwords for all accounts is crucial. Training should cover best practices for password complexity, avoiding reuse, and secure storage methods (avoiding sticky notes!).
Secure Data Handling: Healthcare staff must be well-versed in data handling protocols to ensure patient information remains confidential. This includes understanding access controls, proper data encryption methods, and the importance of following established procedures when transmitting sensitive data.
Reporting Suspicious Activity: Encouraging staff to report any suspicious activity, emails, or attempts to access data is vital. A culture of open communication fosters a proactive approach to cybersecurity and allows for swift investigation and mitigation of potential threats.
Building a Culture of Cybersecurity Awareness:
By fostering a culture of cybersecurity awareness within the organization, healthcare institutions can significantly reduce the risk of human error leading to security incidents. Imagine a scenario where a nurse receives a phishing email disguised as a legitimate request for patient information. Training in social engineering tactics can equip them to identify red flags such as:
Urgent or threatening language
Inconsistent sender addresses (e.g., a “.ru” domain for supposedly internal communication)
Grammatical errors or typos
Requests for sensitive data outside of usual workflows
By recognizing these red flags and understanding proper procedures for reporting suspicious activity, the nurse can avoid compromising sensitive data and potentially prevent a security breach.
Training is important, but layers work best. Multi-factor authentication and email filtering boost security. Simulations of phishing attacks can also test staff and identify training and procedure gaps [
11].
C. IoT Security and Medical Device Protection
For patient monitoring and treatment, healthcare is increasingly using internet-connected medical devices (IoMT). These devices have many benefits but also new security risks. Insecure IoMT devices can be used to steal patient data, disrupt medical services, or alter device operations with fatal consequences. Healthcare organizations must secure IoMT devices to separate them from other network systems. These include safe setups, timely patching, and network segmentation. Imagine a hacker taking over a pacemaker. The patient’s health may suffer dramatically. IoMT security is essential for patient safety in the connected medical device era. [
12]
VII. Cybersecurity in Government Infrastructure
Cybersecurity is of utmost importance in government infrastructure, as government entities handle vast amounts of sensitive and confidential information. Protecting this information from cyber threats is crucial to ensure the integrity, availability, and confidentiality of government systems and data. Here are some key considerations for cybersecurity in government infrastructure [
13,
14].
A. Risk Assessment and Management
Government entities should conduct comprehensive risk assessments to identify potential vulnerabilities and threats. This includes evaluating the security of networks, systems, and applications, as well as assessing the potential impact of cyber incidents. By understanding the risks, appropriate security measures can be implemented to mitigate them effectively.
B. Robust Network Security
Robust network security protocols ought to be implemented for government infrastructure. This entails putting intrusion detection and prevention systems, firewalls, and secure network design into practice. Frequent network traffic analysis and monitoring can assist in quickly identifying and addressing such threats [
15].
C. Secure Configuration Management
Government systems and devices should be configured securely, following industry best practices and security guidelines. This includes disabling unnecessary services, applying security patches and updates promptly, and implementing strong password policies. Regular audits and vulnerability assessments can help identify and address any configuration weaknesses.
D. Access Control and User Management
Strict access controls should be implemented to ensure that only authorized personnel can access government systems and data. This involves implementing strong authentication mechanisms, such as multi-factor authentication, and regularly reviewing and updating user access privileges. User activity monitoring can help detect any unauthorized access attempts or suspicious behavior.
E. Incident Response and Recovery
Government organizations must establish clearly defined plans for incident response to efficiently handle and resolve cyber problems. This entails defining precise roles and duties, carrying out practice sessions regularly, and keeping backup copies of important information. Cyberattacks can be lessened and government activities can continue with prompt incident response. [
17]
G. Continuous Monitoring and Security Assessments
Regular monitoring and security assessments are essential to identify and address any vulnerabilities or weaknesses in government infrastructure. This includes conducting penetration testing, vulnerability scanning, and security audits to ensure ongoing compliance with security standards and regulations.
H. Employee Training and Awareness
Government personnel should receive regular cybersecurity training to understand the latest threats, best practices, and their role in maintaining a secure environment. This includes educating employees about phishing attacks, social engineering tactics, and safe browsing habits. By promoting a culture of cybersecurity awareness, government entities can significantly reduce the risk of successful cyberattacks.
cybersecurity in government infrastructure is critical to protect sensitive information, maintain public trust, and ensure the smooth functioning of government operations. By implementing robust security measures, conducting regular assessments, and fostering collaboration, government entities can enhance their cybersecurity posture and effectively defend against evolving cyber threats. [
16]
VIII. Conclusions
In the digital age, data security is of paramount importance Cloud computing has revolutionized the way we store and access data, but it also presents unique challenges when it comes to security and privacy. Critical industries such as healthcare and banking have been hesitant to fully embrace cloud computing due to concerns about the safety of their sensitive data. However, with the implementation of proper security measures and a shared responsibility model, these concerns can be addressed and overcome. Cloud computing offers numerous benefits, such as cost efficiency and scalability, but it also raises concerns about data location, transparency, and privacy. To address these concerns, organizations must prioritize measures such as secure network connectivity, data encryption, and supply chain security. Furthermore, organizations must ensure that they adhere to cybersecurity best practices and implement robust security measures to protect their data. By authorizing and authenticating users, ensuring data confidentiality, and guaranteeing availability, organizations can mitigate the risks associated with cloud computing. In conclusion, while cloud computing may have its challenges in terms of security and privacy, it should not hinder the adoption of cloud services in critical industries. With proper measures and a comprehensive understanding of cloud security, organizations can secure their data in the digital sky and reap the benefits of cloud computing without compromising on security and privacy in conclusion, securing data in the digital sky is crucial for maintaining the trust of users and ensuring the confidentiality, availability, and integrity of sensitive information.
References
- M. Armbrust, A. Fox, R. Griffith, A. D. Joseph, R. Katz, A. Konwinski,. & M. Zaharia, “A view of cloud computing,” Communications of the ACM, vol. 53, no. 4, pp. 50-58, 2010. [Online]. Available: https://doi.org/10.1145/1721654.1721672. [CrossRef]
- V. Chang, R. J. Walters, and G. Wills, “The state of cloud computing security research,” in Cloud Computing Security, Springer, Cham, 2018, pp. 1-20. [Online]. Available: https://doi.org/10.1007/978-3-319-60774-0_1. [CrossRef]
- P. Mell and T. Grance, “The NIST definition of cloud computing,” National Institute of Standards and Technology, vol. 53, no. 6, pp. 50, 2011. [Online]. Available: https://doi.org/10.6028/NIST.SP.800-145. [CrossRef]
- Q. Zhang, L. Cheng, and R. Boutaba, “Cloud computing: state-of-the-art and research challenges,” Journal of Internet Services and Applications, vol. 1, no. 1, pp. 7-18, 2010. [Online]. Available: https://doi.org/10.1007/s13174-010-0007-6. [CrossRef]
- Microsoft, “Shared Responsibility in the Cloud,” Microsoft Azure Security Fundamentals, [Online]. Available:[https://learn.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility].
- N. Leibold, “Securing the Supply Chain: An Overview,” Security Management, vol. 65, no. 3, pp. 42-47, Mar. 2019. [Online].Available:https://www.asisonline.org/security-management-magazine/monthly-issues/security-management-magazine-archives/.
- Hammi, B., Zeadally, S., & Nebhen, J. (2023). Security threats, countermeasures, and challenges of digital supply chains. ACM Computing Surveys, 55(14s), 1-40. [CrossRef]
- Ahmad, A., Desouza, K. C., Maynard, S. B., Naseer, H., & , R. L. (2020). How integration of cyber security management and incident response enables organizational learning. Journal of the Association for Information Science and Technology, 71(8), 939-953. [CrossRef]
- N. Smith, “The Role of SIEM Solutions in Modern Cybersecurity Frameworks,” Security Today, vol. 27, no. 5, pp. 42-47, May 2023. [Online]. Available: https://www.securitytoday.com/Home.aspx.
- Kohn, T., & Newman-Landwirth, S. (2020, December). Best Practices for Preventing Phishing Attacks in Healthcare. The HIPAA Journal. https://www.hipaajournal.com/healthcare-prevent-phishing-attacks/.
- “A study of cyber attacks: In the healthcare sector”. https://ieeexplore.ieee.org/document/9598947 (accessed Apr. 22, 2024). [CrossRef]
- “A Security Awareness and Protection System for 5G Smart Healthcare Based on Zero-Trust Architecture”. https://ieeexplore.ieee.org/document/9273056 (accessed Apr. 23, 2024). [CrossRef]
- “Risk Analysis Framework for Cyber Security and Critical Infrastructure Protection of the US Electric PowerGrid”.https://ieeexplore.ieee.org/document/8735651 (accessed Apr. 22, 2024). [CrossRef]
- “Cybersecurity principles for industry and government: A useful framework for efforts globally to improve cybersecurity”. https://ieeexplore.ieee.org/document/5978798 (accessed Apr. 23, 2024).
- “Network Security by Merging two Robust Tools from the Mathematical Firmament”. https://ieeexplore.ieee.org/abstract/document/9751501 (accessed Apr. 23, 2024). [CrossRef]
- “Employee Cyber-Security Awareness Training (CSAT) Programs in Ireland’s Financial Institutions | IEEE Conference Publication | IEEE Xplore”. https://ieeexplore.ieee.org/document/10032683 (accessed Apr. 23, 2024). [CrossRef]
- “Research on the construction of supply chain collaboration system based on information sharing”. https://ieeexplore.ieee.org/document/6339704 (accessed Apr. 23, 2024). [CrossRef]
- “Research on SWIM Cooperative Emergency Response and Resilient Disaster Recovery Based on Survivability”.https://ieeexplore.ieee.org/document/10092065 (accessed Apr. 23, 2024). [CrossRef]
- D.-M. Neamţu, “Empirical research on the gap between level of education and employability based on work satisfaction,”SpringerLink,https://link.springer.com/chapter/10.1007/978-3-031-20382-4_13 (accessed Apr. 23, 2024). [CrossRef]
- (PDF) comparing social isolation effects on students attrition in online versus face-to-face courses in computer literacy, https://www.researchgate.net/publication/320672593_Comparing_Social_Isolation_Effects_on_Students_Attrition_in_Online_Versus_Face-to-Face_Courses_in_Computer_Literacy (accessed Apr. 23, 2024). [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).