1. Introduction
One of the key pillars of the digital revolution is the Internet of Things (IoT), which portends a world in which billions of connected gadgets will work together to improve convenience, productivity, and efficiency in a variety of fields. IoT technologies have penetrated almost every facet of contemporary life, ranging from wearable’s and smart homes to industrial sensors and self-driving cars. These technologies can revolutionize industries, enhance workflows, and elevate people's standard of living. But underneath all of the hype surrounding IoT, there's a sobering truth about the widespread cyber security threats that come with its quick spread. The hazards related to cyber security threats are increasing in tandem with the exponential growth of connected devices. Due to the interconnectedness of IoT ecosystems, malicious actors might use a sizable and intricate attack surface to disrupt operations, compromise sensitive data, or undermine trust in linked devices. IoT security flaws, which can range from antiquated firmware to lax authentication procedures, put people and businesses in danger of various consequences, such as system intrusions, data breaches, and unwanted access. Furthermore, there are strong privacy issues raised by the acquisition and exploitation of personal data by IoT devices, which has led to calls for stricter data protection laws and regulatory monitoring.
It is impossible to exaggerate how crucial cyber security is to the development of IoT in this scenario. In addition to ensuring the availability, confidentiality, and integrity of IoT systems, effective cybersecurity procedures are necessary to fully realize the potential of linked technologies as catalysts for innovation, economic expansion, andsocietal advancement. In light of this, this research study investigates the complex interrelationship between cyber security and the development of the Internet of Things, focusing on the difficulties, prospects, and potential paths forward in the field of linked environment security. This article intends to shed light on the crucial role of cyber security in influencing the future of IoT and provide insights into practical techniques for managing cyber security risks in IoT deployments through an analysis of current trends, case studies, and research findings.
This research paper aims to arm stakeholders with the knowledge and tools necessary to navigate the complex cybersecurity landscape of IoT and harness the transformative potential of connected technologies while protecting against emerging threats. It does this by thoroughly examining cyber security challenges, their impact on IoT advancement, best practices, and future directions. By doing this, we hope to further our understanding of the relationship between cyber security and the Internet of Things and provide stakeholders the tools they need to successfully handle cybersecurity issues in a world where connectivity is advancing.
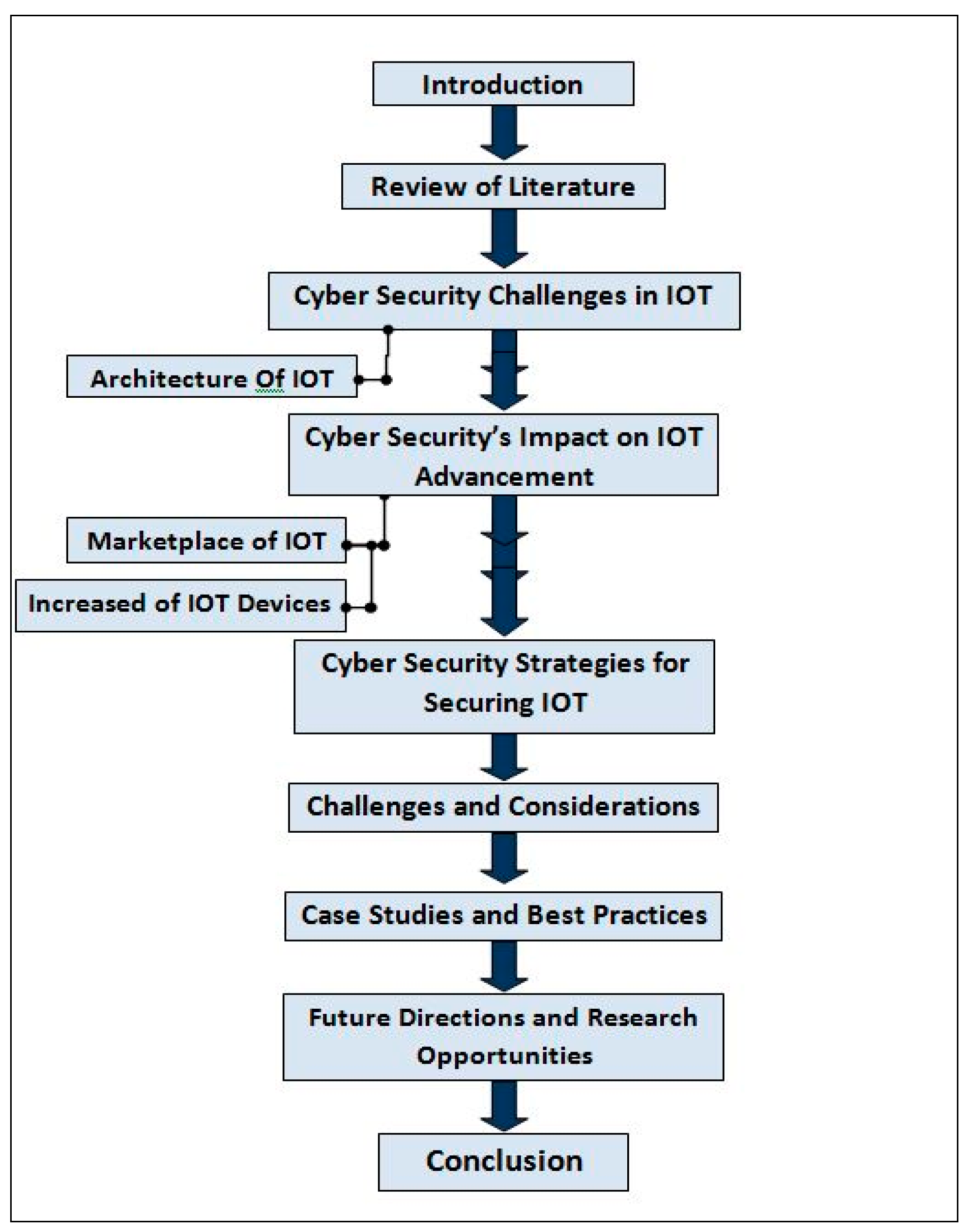
Figure 1.
Visual Representation of the Overall Paper Working Structure.
Figure 1.
Visual Representation of the Overall Paper Working Structure.
2. Review of Literature
The preparation of this work involved a review of several research publications regarding the impact of cyber security systems on the development of IoT. Examining research article [
1], this study examines cyber risk management frameworks and IoT cyber security technology. Next, a four-layer approach for managing IoT cyber risk is presented in this research. This study also uses a linear programming technique to distribute funds across several Internet of Things cyber security initiatives. This study, which is based on the referenced paper [
2], investigates machine learning's application to the Internet of Things security systems. The use of machine learning methods to recognize malicious and abnormal data in IoT systems is also thoroughly examined in this paper. After going over the research papers [
3], they came up with a theory that forecasts the suitability of machine learning techniques for static analysis of IoT systems. A research plan that tries to support the hypothesis and represent the study's ontology is provided. In their paper, they also discussed topics like systematizing the static analysis phase for Internet of Things systems and using formal models to solve machine learning problems, reviewing publications from various fields and analyzing the findings, ensuring that machine learning instrumentation is applicable at every stage of the static analysis process and proposing an intelligent framework concept for IoT system static analysis, among other things. They offer an Internet of Things testbed to address the existing and widening cyber security skills gap, as demonstrated by the analysis of research papers[
4]. IoT-CR facilitates the scalable, concurrent execution of various scenarios by a modular design and it also enables users to define and function on reconfigurable virtual and physical IoT networks. It is clear from reading the research report [
5] that theSDN paradigm and machine learning are employed in this work to harness the advantages of flexible data-driven models and programmable flow-based telemetry with IoT device management based on network activity. This study looks at the most recent cyber security concerns about critical infrastructures that are based on the Internet of Things in order to address the difficulties presented by cyber security. It also addresses potential cyber threats and vulnerabilities, as well as the primary exploitation strategies employed by cybercriminals [
6].A thorough investigation and experimental examination of federated deep learning techniques for cyber security in Internet of Things (IoT) applications are presented in this research, which can be found in [
7]. Specifically, it offers an overview of security and privacy systems based on federated learning for a range of Internet of Things applications, such as Edge Computing, Industrial IoT, the Internet of Drones,the Internet of Healthcare Things, the Internet of Vehicles, and so on. This study provides cyber security threats in light of the relevance of marine cyber security as discussed in the cited paper [
8].The goal is to determine the degree and impact of these threats. It acts as a roadmap for stakeholders to put into practice efficient preventive and remedial measures. Additionally, the impact of various cyber security concerns is examined and explored about availability, integrity, privacy, and maritime security. A hypothesis that assumes the applicability of machine-learning solutions for IoT system static analysis has been developed, as can be seen in the review of the research paper [
9].This hypothesis takes into account the need for automation and intellectualization of the work of manual experts for the progressive complexity of connections in IoT systems, increase in scale, and diversity of components. Examining the research document [
10] reveals that this study looks at multiple AI models based on performance to accurately forecast IoT device issues and attacks. The performance of the proposed method is demonstrated with four different parameters using ant colony optimization, genetic algorithms, and particle swarm optimization (PSO). As demonstrated in the paper [
12], this work presents Edge-IIOT set, a new comprehensive, realistic cyber security dataset of IoT and IIOT applications. Machine learning-based intrusion detection systems can use Edge-IIOT set in two different ways federated learning and centralized learning. As demonstrated in the paper [
13], this work offers a thorough analysis of cyber security applications, difficulties, and prospects in the Internet of Things (IoT) space. It also emphasizes the IoT architectural layer, IoT layer assaults, and associated problems. This review article in Papers [
14] examines 70 important publications that were found using a thorough Scopus literature assessment. It discusses themes in the literature regarding IIOT cyber security concerns and opportunities. Also, rather than offering any specific technical fixes to network security problems, this paper seeks to present the current discussion surrounding the Internet of Things. This chapter offers an overview of possible blockchain and AI synergies in the context of cyber security for IoT and IIOT, as can be seen in the study [
15]. This article covers the research on cyber security threats and vulnerabilities in cyberattacks on Internet of Things-based smart renewable energy and power systems, as may be seen in the study [
16].Major vulnerabilities to IoT-based smart renewable energy include replay, denial of service, brute force certificate assaults, and fraudulent data injection, according to the research. This study explores distributed computing at the edge, as demonstrated in the paper [
17], utilizing container orchestration tools and AI-enabled IoT devices to process data in real time at network edges. This study aims to increase security by detecting DDoS attacks while consuming less CPU power and taking action. This chapter emphasizes the necessity of mitigating IoT security vulnerabilities, as demonstrated in the paper [
18].Sensitive data disclosure and device cloning are also explained. As can be seen in the paper [
20], this study examines the expanding cybersecurity challenges in the context of the quickly gaining ubiquity of Internet of Things (IoT) technology, which has made itself more vulnerable to cyberattacks. Additionally, the extensive use of IoT systems has increased data traffic and intensified complex interactions between devices. It gives cybercriminals multiple opportunities to do so. Furthermore, the main goal of this research is to examine the effectiveness of various machine learning techniques for identifying cyber abnormalities in Internet of Things systems.
3. IoT Cybersecurity Challenges
The proliferation of connected devices has resulted in a major increase in the attack surface, which has raised serious concerns in the field of cyber security. The largest factor increasing the application attack surface is IoT and connected devices. The likelihood of vulnerabilities and security breaches increases with the number of devices linked to a network. Every device is a potential point of vulnerability where sensitive data or the network could be accessed without authorization. IoT devices also exist in a variety of shapes and sizes, ranging from medical equipment and industrial sensors to smart appliances and thermostats for homes. In that instance, attackers can initiate an attack by taking advantage of flaws in any of these components. Strong security measures are absent from a large number of IoT devices, which are frequently built more for cost and utility than for security.
Manufacturers are therefore unable to prioritize frequent security updates and continue to support outdated devices. IoT security flaws, which can arise from several sources such as inadequate authentication, insufficient encryption, and out-of-date firmware, can seriously endanger persons and institutions. IoT devices that are not encrypted may be accessed by unauthorized parties, endangering sensitive data in several ways. IoT devices without encryption may also be vulnerable to data manipulation or injection attacks, in which adversaries alter or add malicious material into messages that are sent over the network, potentially compromising systems or causing security lapses. IoT devices with outdated firmware may be vulnerable to security flaws and may not receive necessary security updates.
By taking advantage of these vulnerabilities in out-of-date firmware, attackers can obtain unauthorized access to devices, initiate remote code execution attacks, or utilize compromised devices as a component of botnets to initiate malicious operations such as distributed denial-of-service (DDoS) assaults.
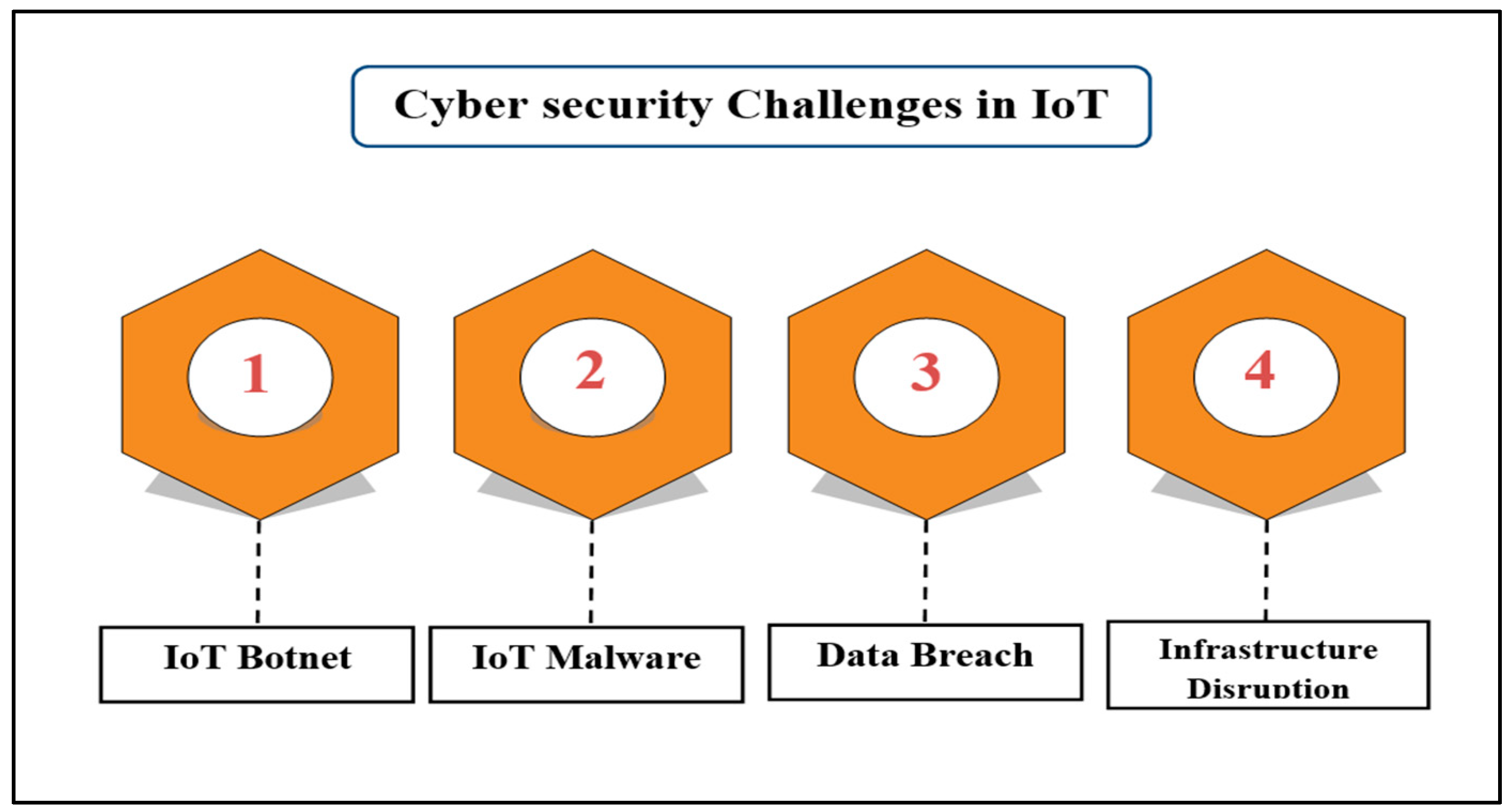
Malware, botnets, and other harmful activities targeting the IoT ecosystem pose a major threat to people, organizations, and critical infrastructure.
Botnet for the Internet of Things: A network of compromised devices under centralized command is called a botnet. Cybercriminals utilize botnets to automate massive assaults including distributed denial-of-service (DDoS) attacks, crypto mining, virus dissemination, and data theft.
Internet of Things Malware: Through attacks on IoT devices, a range of malicious software aims to compromise the security and integrity of the Internet of Things ecosystem. It is designed to exploit flaws in Internet of Things devices, such as firmware instability, default settings, and unpatched software.
Data Breach: Wide-ranging effects could result from a breach in the Internet of Things (IoT) ecosystem, affecting vital industries including infrastructure, finance, and healthcare. Secure data or operational systems could pose a serious threat to national security, public safety, and economic stability.
Infrastructure Disruption: Cyberattacks aimed at the Internet of Things (IoT) ecosystem have the potential to compromise vital services and vital infrastructure, such as energy grids, transportation networks, and medical institutions. Furthermore, ransomware attacks and DDoS attacks that target network infrastructure and operational systems, respectively, can happen.
To safeguard IoT ecosystems from botnets, malware, and privacy breaches, attentiveness, awareness, and proactive measures are necessary. A safe digital future now depends on mitigating these dangers as the IoT ecosystem changes.
Figure 2.
IoT cyber security challenges.
Figure 2.
IoT cyber security challenges.
Architecture of IoT
IoT devices communicate with one another by connecting to networks and exchanging data. A key component of IoT design is the gathering of sensitive data from a vast number of linked devices. The goal of the Internet of Things architecture is to provide simple networking, efficient data processing, and secure system operation. It is depicted by a simple image.
Figure 3.
Simple architecture of IoT.
Figure 3.
Simple architecture of IoT.
4. Cyber Security's Impact on IoT Advancement
Cybersecurity has a big impact on the acceptance and development of Internet of Things (IoT) technologies. Cybersecurity issues are one of the primary obstacles that must be solved to establish a fully integrated Internet of Things ecosystem.
Faith and Self-Belief: Stakeholders in IoT technology, organizations and consumers all gain confidence and trust from effective cyber security safeguards.
Risk Mitigation: Cyber security plays a key role in reducing the risks that come with Internet of Things deployments, such as infrastructure failures, privacy violations, and data breaches. Through vulnerability identification and remediation, preventive measures implementation, and adherence to best practices, companies can reduce the probability and effect of cyber threats directed toward IoT ecosystems.
Investment and Innovation: By fostering a climate that is favorable for research, development, and commercialization, cyber security encourages innovation and investment in IoT technology. Businesses that put cyber securityfirst stand out from the competition, draw capital, and spur innovation in fields like threat intelligence, secure hardware, and encryption technologies.
Regulatory Compliance: The development of IoT depends on adherence to industry standards and cyber security laws. Regulations and rules for safeguarding IoT devices, controlling cyber security risks, and preserving data privacy are established by regulatory frameworks including the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and cyber security standards like ISO/IEC 27001.
Security of the Supply Chain: Cyber security now covers every link in the supply chain, from manufacturers to suppliers to service providers, and goes beyond individual IoT devices. The implementation of secure supply chain procedures, such as vendor vetting, software integrity assurance, and supply chain resilience measures, can improve the credibility and dependability of Internet of Things products and services.
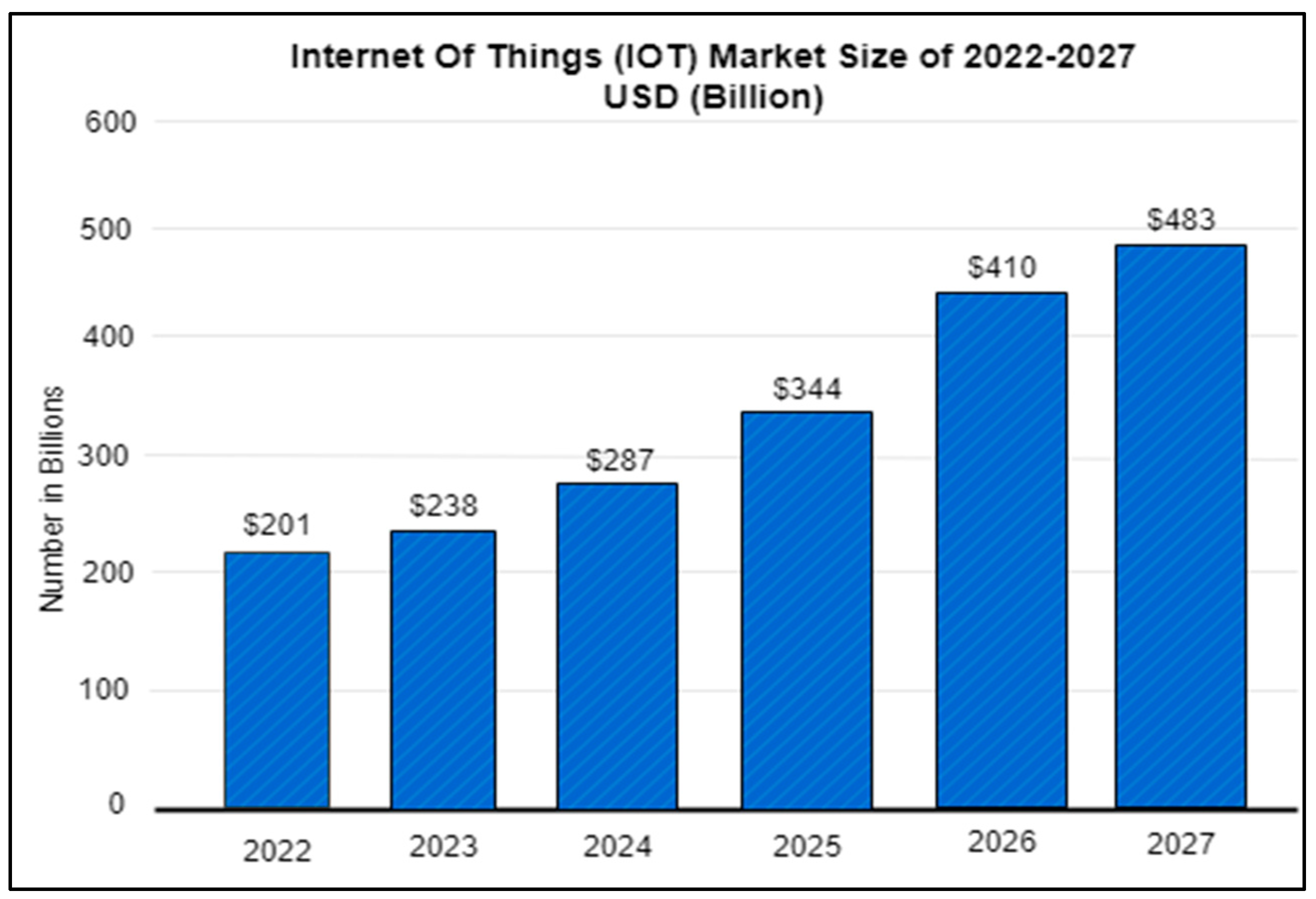
The valuation of the worldwide IoT market from 2022 to 2027 is displayed in an overview of the market's current status that is available. This document, which is based on that article, shows a graph chart that shows the market value for a particular year. The IoT market is predicted to grow from $201 billion in 2022 to $287 billion in 2024, as shown by the graph chart. The IoT market is predicted to be valued $483 billion by 2027.
Figure 4.
Marketplace of IoT, Size (2022-2027).
Figure 4.
Marketplace of IoT, Size (2022-2027).
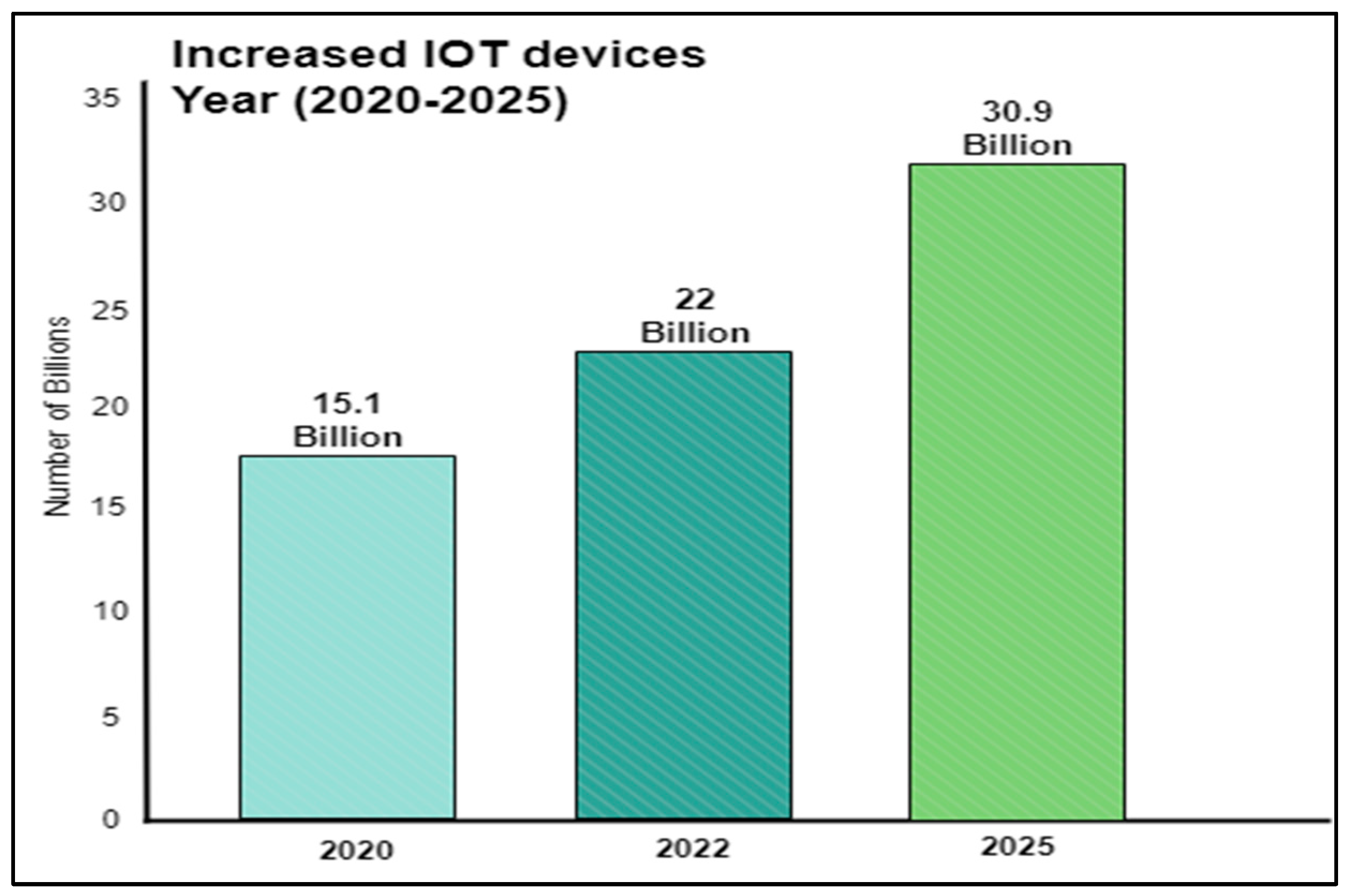
IoT device prices are rising in tandem with the demand for IoT. A report claims that by 2020, there will be about 15.1 billion IoT devices. That figure rises to 22 billion by 2022. According to the article, by 2025, there will be close to 30.9 billion IoT devices worldwide.
Figure 5.
Increased IoT devices, Size (2020-2025).
Figure 5.
Increased IoT devices, Size (2020-2025).
5. Cyber Security Strategies for Securing IoT
It is imperative to secure Internet of Things (IoT) devices to preserve data privacy, guarantee system integrity, and lessen the dangers posed by cyberattacks. The Internet of Things can be secured using a range of cybersecurity techniques. To confirm the identification of IoT devices and stop unwanted access, device authentication and access control or strong authentication mechanisms like cryptographic keys, two-factor authentication, and unique device identifiers can be used. Based on networkroles and rights, access control and least privilege policies can also be used to restrict the capabilities and permissions of Internet of Things devices. To create a secure communication protocol system, data transmission between Internet of Things devices, gateways and backend systems can be protected using encrypted communication protocols, such as Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS). To lower the risk of software vulnerabilities and stop attacker exploitation, safe coding techniques can be implemented, such as input validation, buffer overflow prevention, and secure APIs. Finding and fixing security vulnerabilities in the firmware, software, and applications of IoT devices through routine security assessments, code reviews, and penetration tests. For IoT devices, known vulnerabilities, defects, and securityflaws can be fixed with firmware updates and patch management.Using firewalls, VLANs, and network segmentation techniques, different environments can be created based on the security requirements of IoT devices. Putting in place intrusion detection systems (IDS), network access control, and network monitoring tools to find and stop suspicious behavior, lateral movement, and unwanted access in Internet of Things networks. Sensitive information kept on Internet of Things devices is safeguarded and data privacy is maintained through data encryption.
To proactively respond to cyberattacks targeting Internet of Things devices, it is also possible to incorporate security analytics, machine learning algorithms, threat intelligence feeds, and network traffic analysis. By putting these cyber security techniques into practice and taking a proactive approach to IoT security, this article seeks to empower IoT devices and ecosystems to boost resilience, reliability, and security. To combat cyber threats and prevent the exploitation of vital assets and data, cyber security must be reinforced.
6. Challenges and Considerations
Because of the large number of devices and the variety of uses for which they can be put, securing IoT ecosystems is a challenging undertaking. In the context of IoT, scalability is the capacity to effectively manage and secure an increasing number of connected devices.
Scalability Issues: Managing an increasing number of IoT devices is becoming more challenging. This entails maintaining data privacy, secure communication, and reliable performance on all devices.
Security Frameworks: For real-time threat detection and mitigation in Internet of Things networks, a thorough security framework is necessary. Hardware-based security modules, zero trust architecture, and real-time response based on Node MCU ESP8266 are a few examples of such a framework.
Proactive Measures: Resolving security issues calls for a multifaceted, proactive strategy that includes ongoing monitoring, risk analysis, and modification of security measures in response to ecosystem changes.
In IoT ecosystems, scalability and security necessitate a comprehensive strategy that includes people, procedures, and technology to make sure the system can expand without jeopardizing security.In IoT networks, finding the ideal balance between user ease and security is a complex problem. Improving user ease frequently entails simplifying procedures and cutting down on friction, which occasionally results in laxer security measures. On the other hand, complex security controls might make systems difficult to use. The ethical implications of data consumption are critical as a result of IoT devices gathering enormous volumes of personal data. It can be beneficial to use design patterns that put security and usability first. For instance, it is possible to improve Bluetooth security without materially affectingusability. It's critical to modify security protocols to stay up with the capabilities of IoT devices. To guarantee usability and promote acceptance of IoT solutions, user ease is crucial.
7. Case Studies and Best Practices
Analyzing the best practices, difficulties, and approaches for successfully securing IoT ecosystems may be gained by looking at the successful IoT security initiatives and deployments across a range of industries. Medical devices that are networked healthcare institutions have put security safeguards in place to guard against cyberattacks on linked medical devices like insulin pumps, pacemakers, and infusion pumps. Network segmentation, patient data encryption, and routine software updates are some of the steps being taken to reduce vulnerabilities and guarantee patient safety. Telemedicine systems have included robust security mechanisms, such as end-to-end encryption, secure authentication, and compliance with healthcare privacy regulations like the Health Insurance Portability and Accountability Act (HIPAA), to safeguard patient data.This study examined the significance of remote health monitoring systems, as can be seen in the paper
[21]. In addition to examining the usefulness of IoT in healthcare, this paper discusses the difficulties and how they impact medicine. To safeguard sensors, automation systems, and industrial IoT (IIOT) devices in smart factories and manufacturing facilities, manufacturers have implemented security measures. Network segmentation, anomaly detection, and intrusion prevention systems are some of the initiatives being taken to safeguard vital infrastructure, stop illegal access, and reduce operating risks. Production systems have already been the subject of numerous papers. Article research looks at the most recent IIOT network topologies, architectures, platforms, and protocols that let the smart industry boost manufacturing production by making it easier to connect to the IoT backbone.
[22]. However, to protect IoT-enabled supply chains against cyberattacks and supply chain intrusions, manufacturers have put in place supply chain security measures. Efforts to reduce supply chaininterruptions, detect counterfeit products, and verify component integrity include supply chain visibility tools, vendor risk assessments, and secure communication channels. On supply chain management, numerous publications have been written and numerous studies are being conducted. Similarly, perusing a recently released article, this research adds to the body of knowledge regarding IoT-based supply chain management by addressing the key topics, including application domains, technologies, sensors, and devices utilized in the implementation of such systems, it is cited as a research paper
[23].
IoT-enabled infrastructure, like traffic sensors, smart meters, and security cameras, has been implemented in smart cities to improve city management and urban services. Security measures to safeguard citizen data and guarantee the resilience of vital infrastructure against cyberattacks include encryption of data transmission, secure access controls, and privacy-preserving technologies. Examining the document
[24] reveals that the authors begin by outlining the notion of a smart city, the history of smart city creation, and the components of an IoT-based smart city. The research literature on recent IoT-enabled smart city development and successes enabled by AI techniques is then reviewed, highlighting the state of the art, key trends, and unmet obstacles for building AI-powered IoT solutions. To prevent cyberattacks and privacy violations, automakers have put security measures in place for connected cars and in-car technologies. To address vulnerabilities, fix software defects, and guarantee the safety and security of car occupants, initiatives include intrusion detection systems, secure software updates, and over-the-air (OTA) security updates.
Intelligent traffic management systems and networked infrastructure are examples of smart transportation efforts that incorporate security controls to guard against cyberattacks and guarantee the dependability of transportation services. To protect data integrity and sustain system availability, initiatives include traffic encryption, secure communication protocols, and authentication techniques. As can be observed in the paper
[25], the study gives policymakers and entrepreneurs useful insights on how to create an entrepreneurial ecosystem in the smart transportation sector by identifying and prioritizing IoT-based entrepreneurial prospects. These examples show how businesses in a variety of sectors are utilizing the transformative potential of IoT technologies to spur innovation, efficiency, and competitiveness while successfully implementing IoT security initiatives to safeguard vital assets, data, and services from cyber threats.
8. Future Directions and Research Opportunities
IoT cyber security is evolving, shaped by new developments in edge computing, blockchain, artificial intelligence (AI), and other technologies that will secure connected devices, networks, and apps in the future. This essay provides some insight into that. In IoT cyber security, artificial intelligence (AI) and machine learning (ML) technologies are being used more and more for threat identification, anomaly detection, and predictive analytics. AI-powered security systems, which can analyze massive volumes of IoT data in real-time, identify potential security threats and detect abnormal behaviors, enable proactive threat mitigation and incident response. IoT devices are now better able to fend off cyberattacks with the development of AI.It has been the subject of numerous recent papers and there is a great deal of research being done right now. More than 400 research articles on the teaching and learning of artificial intelligence (AI) and Internet of Things (IoT) techniques in 20 years of education were collected in a recent study [
26].The potential of blockchain technology to improve IoT ecosystem security, integrity, and trust is being investigated. IoT applications may ensure data integrity, protect transactions, and build trust between devices and parties participating in IoT interactions by utilizing blockchain's decentralized, immutable ledger. In the Internet of Things installations, blockchain can also help with secure device authentication, firmware updates, and secure data sharing. With the present technological revolution, blockchain technology is becoming popular. All industries are drawn to the intermediary-free execution capabilities of blockchain technology. Consequently, this technology is creating opportunities in most circumstances. As a result, a lot of research papers are being written about the potential applications of blockchain technology. In this research study [
27], the state-of-the-art breakthroughs in blockchain technology for IoT, cloud IoT, and fog IoT are analyzed with consideration to e-health, smart cities, intelligent transportation, and other related applications. There are also presentations of prospective answers, research gaps, and obstacles. Edge computing puts processing capacity closer to the Internet of Things devices, enabling real-time data processing, reduced latency, and improved performance. Encryption, access controls, and intrusion detection are just a few of the security measures that must be implemented at the network edge in edge computing settings to safeguard data, apps, and devices against cyberattacks. This applies to all devices, users, and applications that use IoT networks and resources. ZTA uses micro-segmentation, continuous authentication, and granular access restrictions to implement stringent security regulations and stop cyber criminals from moving laterally across IoT environments. The need to safeguard networks and connected devices in the digital era is becoming increasingly apparent, as evidenced by these new developments in IoT cyber security. By integrating edge computing, blockchain, artificial intelligence, and other cutting-edge technologies, organizations may improve the security, resilience, and credibility of their IoT deployments.This will facilitate the ongoing expansion and use of IoT solutions across many industrial sectors.
Investigating new methods and solutions for Internet of Things (IoT) ecosystem security is crucial to addressing the dynamic threat landscape and guaranteeing the robustness of apps, networks, and linked devices. Homomorphic encryption, which allows computations on encrypted data without first decrypting it, guarantees data privacy and secrecy in Internet of Things (IoT) environments.Through the use of homomorphic encryption techniques in IoT data processing and analytics, businesses may safely extract insights from confidential data while shielding it from disclosure or unwanted access.
9. Conclusion
The impact of cyber security on the Internet of Things progress is covered in the article. It also draws attention to difficulties, chances, and potential paths forward. The research highlights the necessity for robust cybersecurity systems and the growth of IoT devices in all facets of daily life through a thorough review and synthesis of the existing literature. It serves as an example of the many difficulties in deploying and maintaining IoT systems securely. The report also outlines the different opportunities that arise from the confluence of IoT and cyber security, such as the possibility for creative security solutions in blockchain, machine learning, and upcoming technologies. The study promotes a proactive strategy for cybersecurity that not only reduces risk but also encourages innovation and sustainable growth in the IoT ecosystem by examining these prospects.
References
- Lee, I. Internet of Things (IoT) cybersecurity: Literature review and IoT cyber risk management. Future Internet 2020, 12, 157. [Google Scholar] [CrossRef]
- Strecker, S.; Van Haaften, W.; Dave, R. An analysis of IoT cyber security driven by machine learning. In Proceedings of International Conference on Communication and Computational Technologies: ICCCT 2021; Springer: Singapore, 2021; pp. 725–753. [Google Scholar]
- Kotenko, I.; Izrailov, K.; Buinevich, M. Static analysis of information systems for IoT cyber security: A survey of machine learning approaches. Sensors 2022, 22, 1335. [Google Scholar] [CrossRef] [PubMed]
- Nock, O.; Starkey, J.; Angelopoulos, C.M. Addressing the security gap in IoT: towards an IoT cyber range. Sensors 2020, 20, 5439. [Google Scholar] [CrossRef] [PubMed]
- Sivanathan, A.; Gharakheili, H.H.; Sivaraman, V. Managing IoT cyber-security using programmable telemetry and machine learning. IEEE Transactions on Network and Service Management 2020, 17, 60–74. [Google Scholar] [CrossRef]
- Djenna, A.; Harous, S.; Saidouni, D.E. Internet of ThingsmeetsInternet of Threats: New concern Cyber security issues of critical cyber infrastructure. Applied Sciences 2021, 11, 4580. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Friha, O.; Maglaras, L.; Janicke, H.; Shu, L. Federated deep learning for cyber security in the internet of things: Concepts, applications, and experimental analysis. IEEE Access 2021, 9, 138509–138542. [Google Scholar] [CrossRef]
- Ashraf, I.; Park, Y.; Hur, S.; Kim, S.W.; Alroobaea, R.; Zikria, Y.B.; Nosheen, S. A survey on cyber security threats in IoT-enabled maritime industry. IEEE Transactions on Intelligent Transportation Systems 2022, 24, 2677–2690. [Google Scholar] [CrossRef]
- Kotenko, I.; Izrailov, K.; Buinevich, M. Static analysis of information systems for IoT cyber security: A survey of machine learning approaches. Sensors 2022, 22, 1335. [Google Scholar] [CrossRef]
- Alterazi, H.A.; Kshirsagar, P.R.; Manoharan, H.; Selvarajan, S.; Alhebaishi, N.; Srivastava, G.; Lin, J.C.W. Prevention of cyber security with the Internet of Things using particle swarm optimization. Sensors 2022, 22, 6117. [Google Scholar] [CrossRef]
- Ganai, P.T.; Bag, A.; Sable, A.; Abdullah, K.H.; Bhatia, S.; Pant, B. A Detailed Investigation of Implementation of Internet of Things (IoT) in Cyber Security in the Healthcare Sector. In 2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE); IEEE, April 2022; pp. 1571–1575. [Google Scholar]
- Ferrag, M.A.; Friha, O.; Hamouda, D.; Maglaras, L.; Janicke, H. Edge-IIoTset: A new comprehensive realistic cyber security dataset of IoT and IoT applications for centralized and federated learning. IEEE Access 2022, 10, 40281–40306. [Google Scholar] [CrossRef]
- Lone, A.N.; Mustajab, S.; Alam, M. A comprehensive study on cybersecurity challenges and opportunities in the IoT world. Security and Privacy 2023, 6, e318. [Google Scholar] [CrossRef]
- Raimundo, R.J.; Rosário, A.T. Cybersecurity in the Internet of Things in industrial management. Applied Sciences 2022, 12, 1598. [Google Scholar] [CrossRef]
- Tyagi, A.K. Blockchain and Artificial Intelligence for Cyber Security in the Era of Internet of Things and Industrial Internet of Things Applications. In AI and Blockchain Applications in Industrial Robotics; IGI Global, 2024; pp. 171–199. [Google Scholar]
- Rekeraho, A.; Cotfas, D.T.; Cotfas, P.A.; Bălan, T.C.; Tuyishime, E.; Acheampong, R. Cybersecurity challenges in IoT-based smart renewable energy. International Journal of Information Security 2024, 23, 101–117. [Google Scholar] [CrossRef]
- Kumari, S.; Tulshyan, V.; Tewari, H. Cyber Security on the Edge: Efficient Enabling of Machine Learning on IoT Devices. Information 2024, 15, 126. [Google Scholar] [CrossRef]
- Qamar, R.; Zardari, B.A.; Khang, A. Cyber Security for Internet of Things (IoT) Devices and Sensors. In Agriculture and Aquaculture Applications of Biosensors and Bioelectronics; IGI Global, 2024; pp. 441–457. [Google Scholar]
- Dhabliya, D.; Pandey, P.; Agarwal, V.; Gobi, N.; Dhablia, A.; Kumar, J.R.R.; Gupta, A.; Pramanik, S. Suggested Cyber-Security Strategy That Maximizes Automated Detection of Internet of Things Attacks Using Machine Learning. In Methodologies, Frameworks, and Applications of Machine Learning; IGI Global, 2024; pp. 187–200. [Google Scholar]
- Inuwa, M.M.; Das, R. A comparative analysis of various machine learning methods for anomaly detection in cyberattacks on IoT networks. Internet of Things 2024, 26, 101162. [Google Scholar] [CrossRef]
- Khan, M.A. Challenges facing the application of IoT in medicine and healthcare. International Journal of Computations, Information and Manufacturing (IJCIM) 2021, 1. [Google Scholar] [CrossRef]
- Farooq, M.S.; Abdullah, M.; Riaz, S.; Alvi, A.; Rustam, F.; Flores, M.A.L.; Galán, J.C.; Samad, M.A.; Ashraf, I. A survey on the role of industrial IoT in manufacturing for implementation of smart industry. Sensors 2023, 23, 8958. [Google Scholar] [CrossRef]
- Taj, S.; Imran, A.S.; Kastrati, Z.; Daudpota, S.M.; Memon, R.A.; Ahmed, J. IoT-based supply chain management: A systematic literature review. Internet of Things 2023, 24, 100982. [Google Scholar] [CrossRef]
- Nguyen, H.; Nawara, D.; Kashef, R. Connecting the Indispensable Roles of IoT and Artificial Intelligence in Smart Cities: A Survey. Journal of Information and Intelligence 2024. [Google Scholar] [CrossRef]
- Jami Pour, M.; Hosseinzadeh, M.; Moradi, M. IoT-based entrepreneurial opportunities in smart transportation: a multidimensional framework. International Journal of Entrepreneurial Behavior & Research 2024, 30, 450–481. [Google Scholar]
- Deshmukh, A.; Patil, D.S.; Pawar, P.D.; Kumari, S.; Muthulakshmi, P. Recent Trends for Smart Environments With AI and IoT-Based Technologies: A Comprehensive Review. In Handbook of Research on Quantum Computing for Smart Environments; 2023; pp. 435–452. [Google Scholar]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A survey on the adoption of blockchain in IoT: Challenges and solutions. Blockchain: Research and Applications 2021, 2, 100006. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).