Submitted:
25 October 2024
Posted:
29 October 2024
You are already at the latest version
Abstract
Keywords:
MSC: 11R52; 15A09; 15A69
1. Introduction
2. Preliminary
2.1. Dual Split Quaternion Tensors
2.2. Basic theory with Einstein product
- ;
- and .
- ;
- ;
- ;
- .
-
The ’row block tensor’ formed by and is , andwhere .
-
The ’column block tensor’ formed by and is , andwhere .
- The map t is bijective and its inverse map exists as follows:
- t satisfies: and .
2.3. Real Representations of Split Quaternion Tensors
- ;
- ;
- ;
- ;
- ;
- ;
- ;
- ;
- ;
- .
3. The General Solution to System (2)
- The system (2) is solvable.
- The system of dual split quaternion tensor equations (2) is solvable.
-
The system of real tensor equationsis consistent.
- Dual split quaternion tensor equation is solvable.
- The following system of real tensor equations is consistent,
- .
- Dual split quaternion tensor equation is solvable.
- The following system of real tensor equations is consistent.
- .
4. Numerical Example
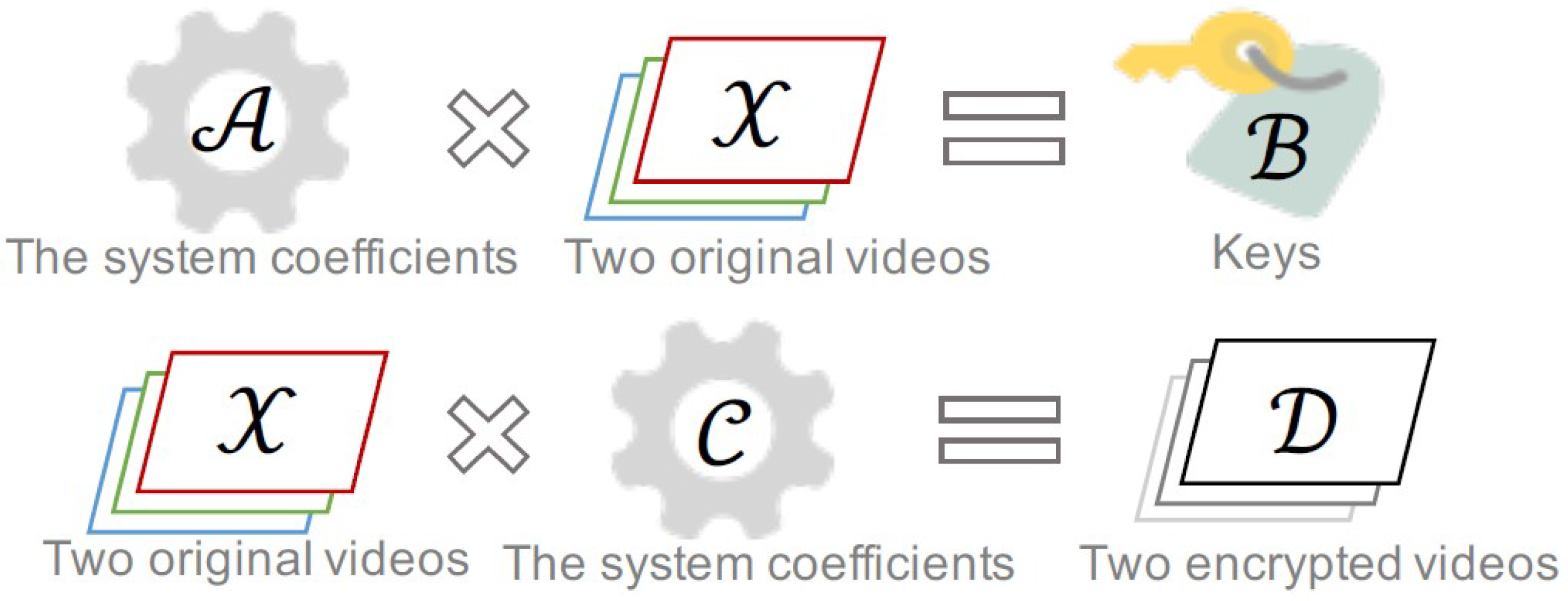
| Algorithm 1 Encryption process |
|
| Algorithm 2 Decryption process |
|

5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Hamilton, W.R. Lectures on quaternions. Landmark Writings in Western Mathematics 1640–1940, 1853. [Google Scholar] [CrossRef]
- Zhang, F.Z. Quaternions and matrices of quaternions. Linear Algebra Its Appl. 1997, 251, 21–57. [Google Scholar] [CrossRef]
- Kösal, H.; Tosun, M. Commutative quaternion matrices. Adv. Appl. Clifford Algebr. 2014, 24, 769–779. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, Q.W.; Xie, L.M. The Hermitian solution to a new system of commutative quaternion matrix equations. Symmetry. 2024, 16, 361. [Google Scholar] [CrossRef]
- Cyrus, J.; Clive, C.T.; Danilo, P.M. A class of quaternion valued affine projection algorithms. Signal Process. 2013, 93, 1712–1723. [Google Scholar] [CrossRef]
- Miao, J.; Kou, K.I. Color image recovery using low-rank quaternion matrix completion algorithm. IEEE Trans. Signal Process. 2021, 31, 190–201. [Google Scholar] [CrossRef]
- Adler, S.L. Quaternionic quantum mechanics and quantum fields. International Series of Monographs on Physics. 1995, 88. [Google Scholar] [CrossRef]
- Cockle, J. On systems of algebra involving more than one imaginary and on equations of the fifth degree. Philos. Mag. 1849, 36, 434–437. [Google Scholar] [CrossRef]
- Kula, L.; Yaylı, Y. Dual split quaternions and screw motions in Minkowski 3-space. Iran. J. Sci. Technol. Trans. A Sci. 2006, 30, 245–258. [Google Scholar] [CrossRef]
- Alagöz, Y.; Oral, K.H.; Yüce, S. Split quaternion matrices. Miskolc Math. Notes. 2012, 13, 223–232. [Google Scholar] [CrossRef]
- Erdoğdu, M.; Özdemir, M. On eigenvalues of split quaternion matrices. Adv. Appl. Clifford Algebras. 2013, 23, 615–623. [Google Scholar] [CrossRef]
- Erdoğdu, M.; Özdemir, M. On complex split quaternion matrices. Adv. Appl. Clifford Algebras. 2013, 23, 625–638. [Google Scholar] [CrossRef]
- Kula, L.; Yaylı, Y. Split quaternions and rotations in semi Euclidean space E24. J. Korean Math. Soc. 2007, 44, 1313–1327. [Google Scholar] [CrossRef]
- Özdemir, M.; Ergin, A.A. Rotations with unit timelike quaternions in Minkowski 3-space. J. Geom. Phys. 2006, 56, 326–332. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, Q.W.; Xie, L.M. Dual quaternion matrix equation AXB=C with applications. Symmetry. 2024, 16, 287. [Google Scholar] [CrossRef]
- Diatta, A.; Manga, B.; Sy, F. On dual quaternions, dual split quaternions and Cartan-Schouten metrics on perfect Lie groups. arXiv:2310.02114, arXiv:2310.02114. 2023. [CrossRef]
- Erdoğdu, M.; Özdemir, M. Split quaternion matrix representation of dual split quaternions and their matrices. Adv. Appl. Clifford Algebr. 2015, 13, 787–798. [Google Scholar] [CrossRef]
- Atasoy, A.; Ata, E.; Yayli, Y. et al. A new polar representation for split and dual split quaternions. Adv. Appl. Clifford Algebras. 2017, 27, 2307–2319. [Google Scholar] [CrossRef]
- Rao, C.R.; Mitra, S.K. Generalized inverse of matrices and its applications. Sankhyā: The Indian Journal of Statistics. 1971, 33, 289–300. [Google Scholar]
- Khatri, C.G.; Mitra, S.K. Hermitian and nonnegative definite solutions of linear matrix equations. SIAM J. Appl. Math. 1976, 31, 579–585. [Google Scholar] [CrossRef]
- Wang, Q.W. Bisymmetric and centrosymmetric solutions to systems of real quaternion matrix equations. Comput. Math. Appl. 2005, 49, 641–650. [Google Scholar] [CrossRef]
- Li, F.L.; Hu, X.Y.; Zhang, L. The generalized reflexive solution for a class of matrix equations (AX=B,XC=D). Acta Math. Sci. 2008, 28, 185–193. [Google Scholar] [CrossRef]
- Yuan, Y. Least-squares solutions to the matrix equations AX=B, XC=D. Appl. Math. Comput. 2010, 216, 3120–3125. [Google Scholar] [CrossRef]
- Xie, L.M.; Wang, Q.W. A system of dual quaternion matrix equations with its applications. arXiv:2312.10037, 2023; arXiv:2312.10037. 2023. [Google Scholar] [CrossRef]
- Wang, Q.W.; Lv, R.Y.; Zhang, Y. The least-squares solution with the least norm to a system of tensor equations over the quaternion algebra. Linear Multilinear Algebra. 2020, 70, 1942–1962. [Google Scholar] [CrossRef]
- Wang, Q.W.; Xu, X. Iterative algorithms for solving some tensor equations. Linear and Multilinear Algebra. 2018, 67, 1325–1349. [Google Scholar] [CrossRef]
- Liang, M.L.; Zheng, B.; Zhao, R.J. Tensor inversion and its application to tensor equation with Einstein product. Linear Multilinear Algebra. 2018, 67, 843–870. [Google Scholar] [CrossRef]
- Xie, M.; Wang, Q.W. ; Reducible solution to a quaternion tensor equation. Front. Math. China. 2020, 15, 1047–1070. [Google Scholar] [CrossRef]
- Xie, M.; Wang, Q.W.; Zhang, Y. The Minimum-Norm Least Squares Solutions to Quaternion Tensor Systems. Symmetry. 2022, 14, 1460. [Google Scholar] [CrossRef]
- Qi, L.Q.; Ling, C.; Yan, H. Dual quaternions and dual quaternion Vectors. Commun. Appl. Math. Comput.. 2022, 4, 1494–1508. [Google Scholar] [CrossRef]
- Einstein, A. The formal foundation of the general theory of relativity. Sitzungsber. Preuss. Akad. Wiss. Berlin (Math. Phys.), 1914; 1030–1085. [Google Scholar]
- Sun, L.; Zheng, B.; Bu, C.; Wei, Y. Moore-penrose inverse of tensors via einstein product. Linear and Multilinear Algebra. 2015, 64, 686–698. [Google Scholar] [CrossRef]
- Chen, C.; Surana, A.; Bloch, A.; et al. Multilinear time invariant system theory. 2019 Proceedings of the Conference on Control and its Applications. 2019, 118–125. [Google Scholar] [CrossRef]
- Brazell, M.; Li, N.; Navasca, C.; Tamon, C. Solving multilinear systems via tensor inversion. SIAM J. Matrix Anal. Appl. 2013, 34, 542–570. [Google Scholar] [CrossRef]
- He, Z.H.; Navasca, C.; Wang, Q.W. Tensor decompositions and tensor equations over quaternion algebra. arXiv preprint arXiv:1710.07552, arXiv:1710.07552. 2017. [CrossRef]
- Liu, X.; He, Z.H. On the split quaternion matrix equation. Banach J. Math. Anal. 2020, 14, 228–248. [Google Scholar] [CrossRef]
- He, Z.H.; Wang, Q.W. The general solutions to some systems of matrix equations. Linear Multilinear Algebra. 2015, 63, 2017–2032. [Google Scholar] [CrossRef]
- Si, K.W.; Wang, Q.W. The General Solution to a classical matrix equation AXB=C over the dual split 1uaternion algebra. Symmetry. 2024, 16, 491. [Google Scholar] [CrossRef]
- Si, K.W.; Wang, Q. W; Xie, L.M. A classical system of matrix equations over the split quaternion algebra. Adv. Appl. Clifford Algebras. 2024, 34, 51. [Google Scholar] [CrossRef]
- Eduardo, B.C.; Zuleima, V.F.; Ulises, U.L. The Lorentz Group Using Conformal Geometric Algebra and Split Quaternions for Color Image Processing : Theory and Practice. IEEE Access. 2023, 11, 56785–56800. [Google Scholar] [CrossRef]
- Zhang, X.F.; Li, T.; Ou, Y.G. Iterative solutions of generalized Sylvester quaternion tensor equations. Linear and Multilinear Algebra. 2023, 72, 1259–1278. [Google Scholar] [CrossRef]
- Clifford, W.K. Preliminary sketch of bi-quaternions. Proc. Lond. Math. Soc. 1873, 4, 381–395. [Google Scholar] [CrossRef]
| Video 1 | PSNR | SSIM | FSIM |
|---|---|---|---|
| 1 | 279.8545 | 1 | 1 |
| 2 | 280.0351 | 1 | 1 |
| 3 | 279.8906 | 1 | 1 |
| 4 | 279.4681 | 1 | 1 |
| Video 2 | PSNR | SSIM | FSIM |
|---|---|---|---|
| 1 | 248.0390 | 1 | 1 |
| 2 | 248.2462 | 1 | 1 |
| 3 | 247.9977 | 1 | 1 |
| 4 | 246.5033 | 1 | 1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




