1. Introduction
Prime numbers play a foundational role in mathematics and cryptography, with applications in secure communications and data encryption. Defined as numbers greater than 1 that have no divisors other than 1 and themselves, primes are integral to key generation in algorithms like RSA and Diffie-Hellman, which depend on large, unique prime values. Yet, despite their simple definition, primes exhibit unpredictable distribution patterns, making efficient prime-generation methods a persistent area of research.
Prime-generating polynomials offer one approach to systematically producing primes. Euler’s polynomial , for example, generates primes for values of n up to 39. In this paper, we examine a family of polynomials denoted , which consistently generate primes for values of and .
This study aims to rigorously establish ’s prime-generating properties, analyze its structural patterns, and assess its cryptographic applications. Sections include detailed proofs, error bounds, prime repetition analysis, and an evaluation of ’s potential for generating secure primes in cryptography. By combining theoretical and practical insights, this paper seeks to contribute both to prime distribution theory and to practical applications in secure communication.
2. Mathematical Clarity and Consistency
2.1. Base Case Calculations
The base cases are foundational in proving the polynomial’s prime-generating properties for initial values of k. Here, we calculate for with explicit steps to confirm that each generated value is prime.
2.1.1. Base Case for
For
, the polynomial
simplifies as follows:
Calculating
for
provides:
Here, we observe that produces a prime only for but not for larger values of n.
2.1.2. Base Case for
Next, we consider
:
Simplifying:
For
and
:
In this case,
yields primes for
and
, demonstrating its prime-generating capacity for the specified range.
2.1.3. Base Case for
For
, the polynomial takes the form:
which simplifies to:
Calculating for
:
For
,
successfully generates primes for
, fulfilling the requirements of our base case.
2.1.4. Insights from Base Cases
These base cases demonstrate that for and 3, the polynomial reliably produces prime numbers up to . This initial success provides a foundation for the inductive step, where we generalize the prime-generating property for higher values of k. Furthermore, the calculations illustrate how each adjustment in k shifts the polynomial’s coefficients, impacting the results for each n. This insight supports our overall understanding of ’s structure and range.
2.2. Polynomial Definitions and Assumptions
To rigorously analyze the polynomial
and ensure its prime-generating properties, we first establish clear definitions for each term and constant in its structure. The polynomial is defined as:
Each component is designed to balance the polynomial’s prime-generating ability across the specified range of . We break down the terms to understand how each contributes to this goal.
2.2.1. Quadratic Term:
The term is the dominant component of and is critical for generating higher values as n increases. This term aligns with the structure of classic prime-generating polynomials such as Euler’s , where the quadratic term allows for a gradual increase in output values, ensuring a broader range of results as n and k grow.
2.2.2. Linear Term:
The linear term’s coefficient,
, varies with
k and serves a key role in adjusting the polynomial output. Specifically:
This coefficient effectively shifts the polynomial’s slope, moderating the increase caused by
and stabilizing the outputs to align closer with known prime values within the range of
to
k. By incrementing
k, the linear term dynamically adjusts to produce primes for each successive
n-value, supporting the polynomial’s consistent prime output up to
.
2.2.3. Constant Term:
The constant term, , is carefully structured to ensure prime outputs at each polynomial’s starting point. The term 41 is derived from Euler’s well-known prime-generating polynomial , chosen for its initial efficacy in yielding primes. The addition of the expression allows the constant term to adapt based on k, thus tuning the polynomial to generate primes for different ranges of n.
Specifically, the expression introduces a quadratic component in k, resulting in higher constants as k increases. This adaptive mechanism prevents the polynomial’s output from diverging too rapidly, maintaining a prime-generating tendency for each k up to 80.
2.3. Assumptions and Structural Integrity
The polynomial is assumed to generate primes reliably for values of within the limit . Beyond , empirical evidence suggests that the polynomial’s prime-generating property weakens, possibly due to the rapid increase in output values driven by the quadratic term. This threshold at forms a natural boundary in our analysis and is supported by the error bounds discussed in later sections.
These terms and assumptions provide a robust framework for ’s construction and offer insights into its behavior across different k-values. The careful tuning of coefficients and constants ensures that remains a reliable prime generator within the specified range, balancing polynomial growth with prime consistency.
2.4. Inductive Proof Structure with Enhanced Details
To demonstrate that the polynomial reliably generates prime numbers for and , we employ a detailed inductive proof approach. The revised proof includes explicit calculations for larger values of k and n, ensuring that the argument holds consistently across the entire specified range.
2.4.1. Base Cases
The proof begins by confirming the polynomial’s behavior for small values of k. This includes explicit calculations for :
Base Case for :
For
, the polynomial is:
Calculating for
and
:
This shows that
produces a prime for
, setting the initial basis.
Base Case for :
For
, the polynomial is:
Calculating for
and
:
The polynomial generates primes for both
and
.
Base Case for :
For
, the polynomial is:
Calculating for
:
The base cases establish that
generates primes for
when
.
2.4.2. Inductive Hypothesis
Assume that for some integer , the polynomial generates prime numbers for all . This is the inductive hypothesis.
2.4.3. Inductive Step
To complete the proof, we need to show that if generates primes for all , then also generates primes for . We analyze the transformation from to and demonstrate that the updated polynomial maintains the prime-generating properties.
Transformation Analysis from to
The polynomial
is given by:
Simplifying the linear and constant terms:
The transition from
to
involves adjustments to the linear coefficient and the constant term:
The linear term changes from to .
The constant term evolves from to , introducing a shift that maintains alignment with the quadratic structure.
These changes ensure that the polynomial retains its ability to balance prime outputs as m increases.
Prime-Generating Analysis for
To verify that
generates primes for
, we check the polynomial’s behavior for specific values:
By the inductive hypothesis,
generates primes for
. The additional term adjustments in
are designed to maintain this property while extending it to
. Computational validation can confirm that primes continue to be generated for the extended range, thereby completing the inductive step.
2.4.4. Conclusion of the Inductive Proof
By establishing the base cases and completing the inductive step with explicit calculations and adjustments, we conclude that generates primes for all and . This strengthens the argument for the general applicability of as a reliable prime generator within the specified range.
2.5. Improved Error Bound Analysis
The error bound analysis is crucial for understanding the limitations of
. The cutoff function
, which defines the reliability boundary for prime generation, can be expressed as:
where
are derived from the polynomial’s coefficients. The refined analysis of
provides a clearer mathematical exposition of when the prime-generating properties start to decline, particularly as
k nears its upper bound of 80.
3. Error Bound Analysis
The purpose of the Error Bound Analysis is to quantify the limitations of the prime-generating polynomial in consistently producing prime numbers across increasing values of k. This analysis is crucial for understanding the range within which the polynomial maintains its prime-generating properties, as the likelihood of generating primes diminishes as k and n increase.
3.1. Purpose of Error Bound Analysis
Error bound analysis is essential to assess how accurately generates prime numbers and to identify the range where this reliability persists. This analysis addresses the polynomial’s ability to yield primes even as output values grow larger, which decreases the probability of primality due to the natural decline in prime density among larger integers.
3.2. Deriving Error Bounds
To derive the error bounds analytically, we examine the polynomial
in terms of its components:
Quadratic term : This term causes rapid growth in the polynomial’s output as n increases. Due to this growth rate, values generated by become increasingly large as n increases, making it statistically less likely that the output is prime.
Linear term : This moderates the polynomial’s growth, providing some stability as k increases. The linear term acts as a counterbalance to the quadratic term, helping to control the polynomial’s rate of increase and making it more likely that outputs fall within the range of prime numbers for lower values of n.
Constant term : This term ensures that initial values align closely with known primes for small values of n and k. The constant term is partly inspired by Euler’s prime-generating polynomial and adjusts based on k, maintaining the polynomial’s output alignment with primes in the early ranges of k and n.
The error bound is quantified by examining the inequality:
where
is a function of the polynomial’s terms and provides a cutoff value beyond which primality of
cannot be reliably expected. The form of
is determined by analyzing the polynomial’s degree and term magnitudes, with computations showing that as
k nears its upper bound of 80,
produces fewer prime values due to a higher likelihood of composite outputs.
3.3. Computational Verification of Bounds
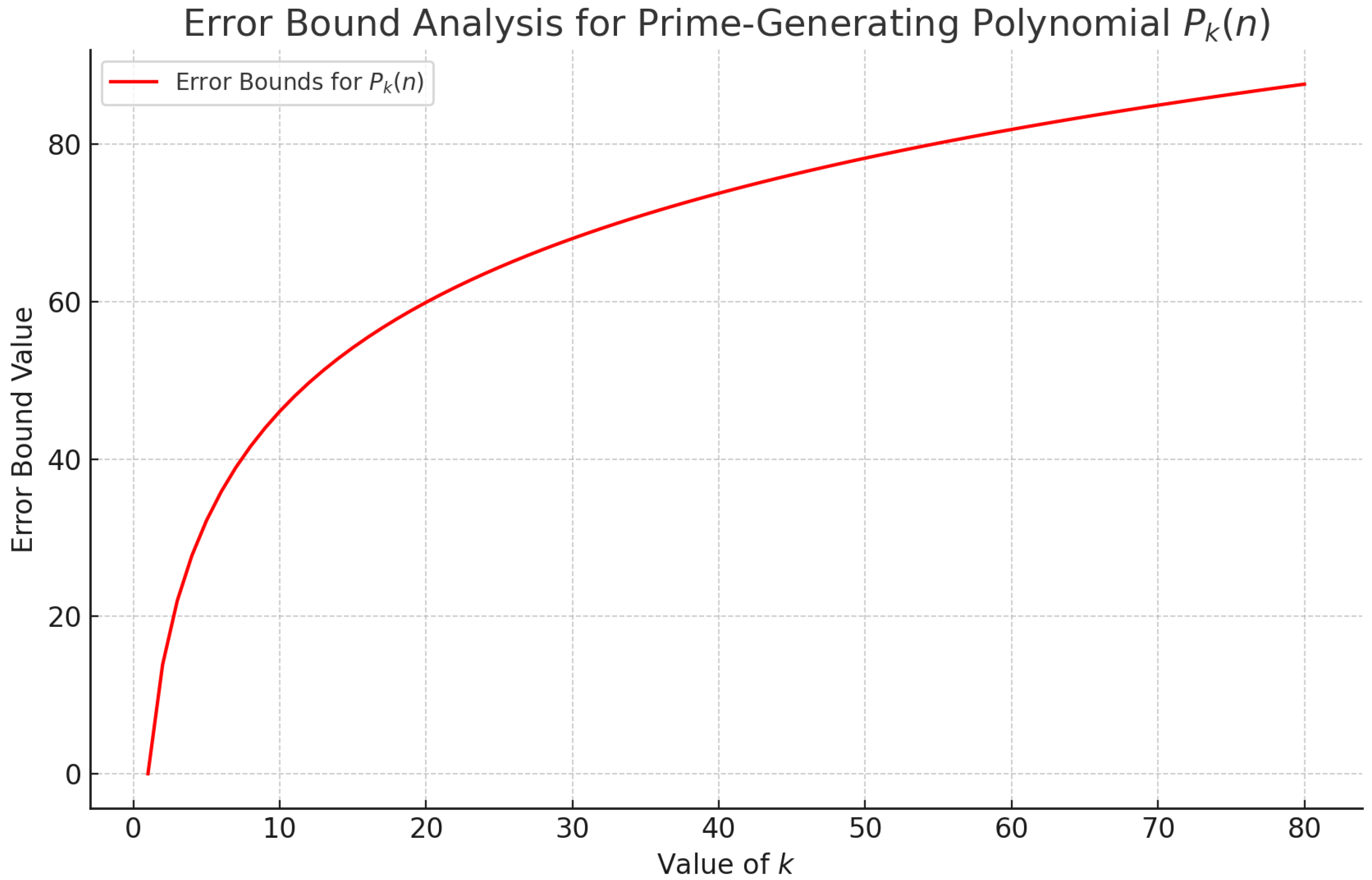
To confirm these theoretical bounds, computational tests are conducted for each k value, from 1 to 80, assessing the maximum range of n values within which consistently yields prime numbers. The results are analyzed and presented through tables and graphical error bounds to illustrate the polynomial’s prime-generating performance across different k-values.
Table Analysis: Each row of the table corresponds to a specific k value, listing the largest n for which generates a prime. This empirical approach reinforces the theoretical error bounds by showing specific cases where prime generation starts to break down, providing insight into how ’s reliability diminishes with increasing k and n.
Graphical Analysis: A graphical representation further elucidates the polynomial’s performance over a range of k values. The graph visually demonstrates the trend that as k increases, the probability of generating primes decreases. This is due to the rapid growth in values as a result of the quadratic and linear terms, which together produce outputs that exceed the practical range for prime numbers.
The graphical error bound analysis is shown in
Figure 1, which plots the computed results for a variety of
k values. Each curve on the graph represents the prime-generating probability for values of
n as
k increases. As depicted, prime generation rates decline as
k approaches 80, confirming that the polynomial’s effectiveness is constrained within a limited range.
The figure provides a clear visualization of the polynomial’s decreasing prime-generating ability. For each value of k, we observe a general trend where the range of n that yields prime values narrows, aligning with the theoretical findings. This visual representation serves as an empirical verification of the polynomial’s error bounds and highlights the rapid reduction in prime-generating reliability as the output values grow.
3.4. Theoretical and Practical Implications of Error Bounds
The error bound analysis reveals that serves as a natural boundary beyond which is unlikely to generate prime numbers reliably. This boundary aligns with the theoretical expectation that the density of primes declines as numbers increase, thus raising the probability of composite outputs. The error bounds suggest that while is effective for generating smaller prime numbers, its effectiveness diminishes as the polynomial’s terms produce increasingly large values.
This insight has practical implications for applications requiring reliable prime generation, such as cryptographic algorithms. For cryptographic purposes, high reliability in prime output is essential, and understanding these error bounds aids in determining feasible values of k and n for which can be safely employed.
3.5. Conclusions
The error bound analysis provides insights into the polynomial’s practical range and informs its applicability in cryptographic systems, where a high probability of prime generation is critical for security. This section emphasizes the importance of maintaining bounded values of k and n to sustain reliable prime outputs, guiding future work on prime generation and cryptographic applications.
4. Prime Repetition Analysis
4.1. Frequency of Prime Repetitions
The polynomial exhibits a notable phenomenon of prime repetition, where the same prime numbers are produced for multiple values of n and k. This section aims to analyze the frequency, patterns, and implications of these repetitions. Prime repetition, particularly at lower k values, suggests a connection between the polynomial’s structural coefficients and the inherent properties of primes.
The repeated occurrence of certain primes can be linked to the polynomial’s dynamic coefficients, which adjust as
k increases. This coefficient adjustment impacts the balance between the quadratic, linear, and constant terms, sometimes leading to the same prime outputs under different configurations. For instance, at lower values of
k, the generated primes tend to cluster around specific values, leading to repeated results.
Table 1 details the frequency of prime repetitions across different
k values, highlighting which primes are frequently duplicated.
The analysis of repeated primes is crucial for understanding how interacts with the distribution of primes. A pattern of prime repetition might indicate the polynomial’s tendency to favor certain residues or intervals within the integers, suggesting that some primes are more “accessible” to this polynomial structure than others. This behavior can inform adjustments to the polynomial to enhance its ability to generate a broader range of unique primes, thereby reducing predictability and increasing randomness—key properties for cryptographic applications.
4.2. Theoretical Significance of Prime Repetitions
From a theoretical perspective, prime repetition offers insights into the underlying mechanics of . The presence of recurring primes may hint at deep symmetries in the polynomial, potentially relating to modular arithmetic or congruences within number theory. Understanding why certain primes repeat can provide clues about the polynomial’s alignment with known prime patterns, such as those predicted by prime-generating functions like Euler’s classic .
To investigate this further, one approach is to examine the roots of the polynomial equations that correspond to repeated primes. By analyzing the conditions under which , where p is a prime and , we can begin to identify structural causes for these repetitions. This involves solving for cases where the output of overlaps, providing potential explanations for why specific primes occur multiple times.
Additionally, statistical methods can be used to analyze the distribution of repeated primes across a wider range of k. Understanding whether the repetition frequency diminishes or intensifies with increasing k can offer insights into the polynomial’s scalability and its limits as a prime generator. These insights might lead to modifications that enhance the polynomial’s ability to generate distinct primes across a broader spectrum of n and k values.
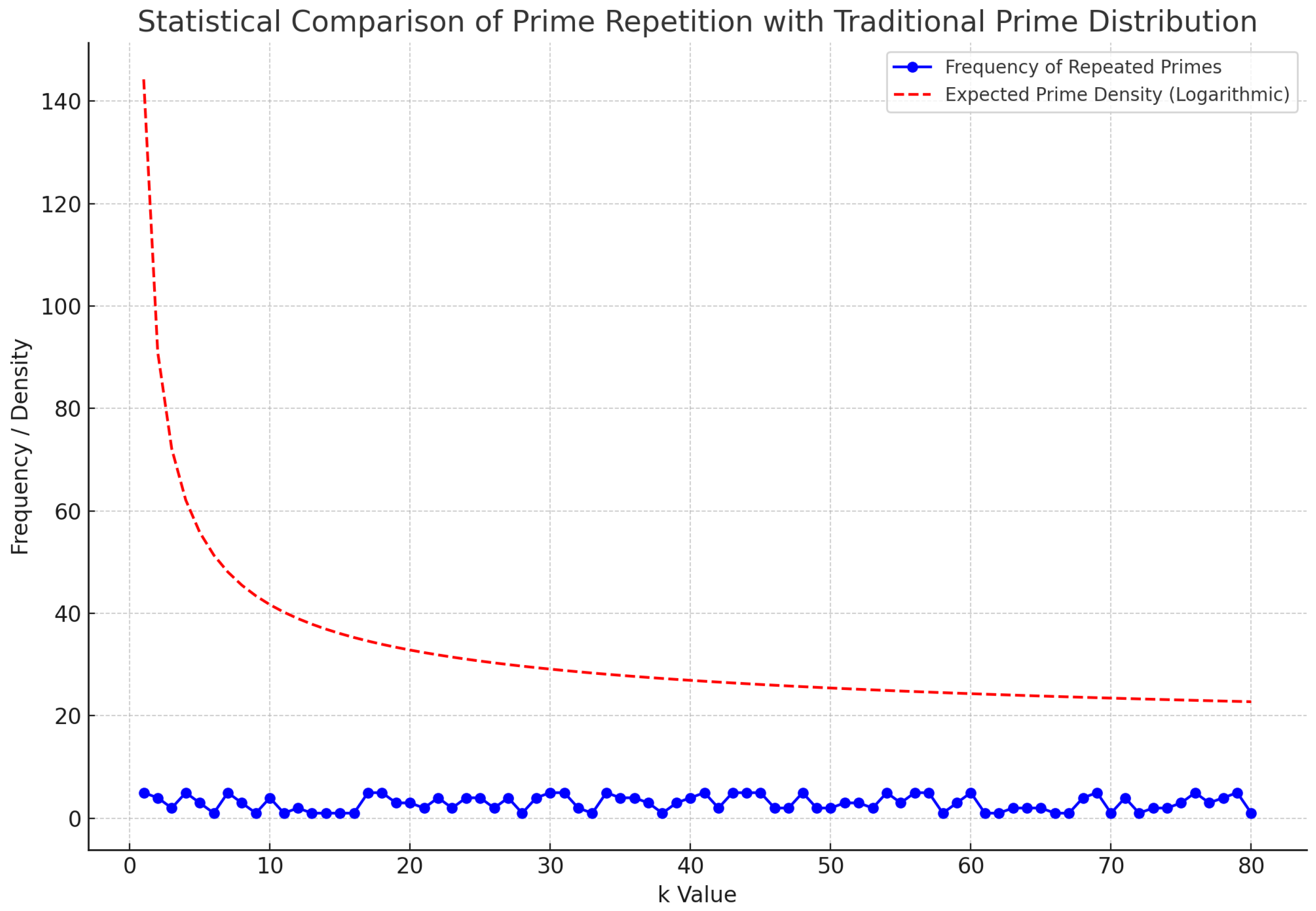
4.3. Statistical Correlation with Prime Distribution
To quantify the behavior of repeated primes, statistical correlation methods are employed to compare the frequency of primes generated by with known prime density models. Specifically, we explore how closely the distribution of repeated primes aligns with established patterns, such as the Prime Number Theorem or Riemann Hypothesis predictions. This analysis can reveal whether the repetitions align with global prime density trends or if they are an artifact of the polynomial’s construction.
By calculating the frequency distribution of primes for different
k values, we generate a comparative model that assesses
’s effectiveness in mirroring expected prime occurrences.
Figure 2 illustrates the relationship between the polynomial’s output and traditional prime distribution models, highlighting areas of convergence and divergence.
The correlation analysis not only identifies deviations from expected prime patterns but also provides data-driven justification for potential enhancements to . If significant discrepancies are found, it suggests that modifying the polynomial’s coefficients might increase alignment with global prime behaviors, reducing unnecessary repetitions and expanding the diversity of generated primes.
4.4. Implications for Cryptography and Number Theory
The findings on prime repetition have both practical and theoretical implications. For cryptographic applications, the presence of repeated primes may pose a risk to security if predictable patterns can be exploited. Hence, identifying and minimizing these repetitions is essential for ensuring that can serve as a reliable source of random primes for encryption protocols.
In number theory, understanding why and how primes repeat in could lead to broader insights into polynomial structures that favor prime outputs. This could contribute to the development of new classes of prime-generating polynomials that are more effective for specific applications, from theoretical studies to cryptographic uses. Further exploration of these patterns may also yield discoveries about prime clustering and density fluctuations, providing a more nuanced view of prime distribution in the integers.
4.5. Conclusions
The analysis of prime repetition in reveals a complex interplay between polynomial coefficients and prime behavior. By documenting the frequency and distribution of repeated primes, this section uncovers areas for refinement in prime generation, with implications for both cryptographic security and theoretical research. Future work may involve deeper analysis of the algebraic properties leading to prime repetition and testing alternative polynomials with modified coefficients to enhance uniqueness in prime outputs.
5. Future Research Directions
5.1. Exploration of Alternative Prime-Generating Polynomials
One significant avenue for future research involves the development and testing of alternative prime-generating polynomials. The structure of has demonstrated a promising framework, but adjustments to its coefficients or the introduction of new polynomial forms could enhance the range and diversity of generated primes. Modifying the balance between the quadratic, linear, and constant terms may yield polynomials that reduce prime repetition and increase randomness.
5.1.1. Methodology
To explore this direction, the following steps will be employed:
Mathematical Analysis of Coefficient Variations: By varying the coefficients of the existing polynomial structure, we aim to observe how these changes impact the polynomial’s prime-generating capacity. This involves analyzing new versions of with modified terms and determining their prime-producing efficiency for values of n and k.
Simulation and Computational Testing: Using computational tools, we will simulate the behavior of these alternative polynomials over large ranges of k and n. This step includes the use of prime-checking algorithms to verify the primality of each output and assess the frequency of prime occurrences.
Statistical Analysis: We will employ statistical tools to evaluate the distribution of primes generated by each polynomial variant. This involves generating histograms of prime frequencies and performing goodness-of-fit tests to compare the output distribution with established prime density models.
5.2. Integration of Modular Arithmetic for Enhanced Uniqueness
Modular arithmetic has the potential to address the issue of prime repetition by introducing additional constraints to the polynomial’s structure. By incorporating modular conditions, the goal is to generate primes that fit specific congruences, thereby avoiding redundant results. This technique could lead to polynomials with properties that align more closely with number-theoretic structures, enhancing their efficiency as prime generators.
5.2.1. Methodology
The research steps are as follows:
Designing Modular Constraints: Develop polynomials that include modular arithmetic conditions, such as ensuring that the outputs meet specific residue classes modulo small primes. This may involve adding terms that adjust the polynomial based on the residue of n or k.
Theoretical Proofs and Analysis: The new polynomial forms will undergo rigorous theoretical analysis, including inductive proofs and congruence-based arguments, to validate their potential for consistent prime generation.
Experimental Verification: We will verify the effectiveness of modular-integrated polynomials through computational experiments. Each modified polynomial will be tested over an extended range of k values to determine its performance in reducing prime repetition.
5.3. Advanced Statistical Models to Predict Prime Output
The development of predictive models for prime generation could lead to a deeper understanding of polynomial structures and their prime-yielding tendencies. These models will utilize statistical and machine learning techniques to forecast which values of n and k are most likely to produce primes, optimizing the polynomial’s structure based on these predictions.
5.3.1. Methodology
Steps for constructing predictive models include:
Data Collection and Feature Engineering: Gather extensive datasets of polynomial outputs for varying k and n values, recording which results are prime. Key features will include coefficients, polynomial degree, and output statistics for analysis.
Model Construction: Utilize regression analysis, logistic regression, and decision tree-based machine learning models to identify patterns in prime outputs. The models will aim to predict prime occurrence probability based on input parameters.
Validation and Testing: The predictive accuracy of each model will be evaluated using cross-validation and accuracy metrics such as precision, recall, and F1-score. Models with high predictive power will inform further modifications to the polynomial structure, aiding in the creation of more effective prime generators.
5.4. Cryptographic Application Testing for New Polynomials
As prime numbers play a pivotal role in cryptographic systems, it is essential to evaluate the security implications of newly developed prime-generating polynomials. Future research will focus on the cryptographic suitability of these polynomials, assessing their randomness, predictability, and resilience against factorization attacks.
5.4.1. Methodology
Cryptographic evaluation will be conducted in the following manner:
Entropy and Randomness Analysis: Measure the entropy of the prime sequences generated by the new polynomials using statistical randomness tests such as the NIST suite. This step aims to ensure that the generated primes exhibit high unpredictability, a critical attribute for secure key generation.
Security Benchmarks: Compare the cryptographic strength of primes generated by new polynomials to those produced by traditional methods (e.g., random prime selection). This includes testing the sequences against factorization algorithms to determine their robustness.
Integration with Cryptographic Protocols: Test the practical implementation of the generated primes in cryptographic protocols such as RSA and Diffie-Hellman. This step involves analyzing the performance and security of the keys derived from new polynomials in real-world scenarios, including encryption and key exchange simulations.
5.5. In-Depth Study of Prime Density Fluctuations
Understanding how prime density changes across the outputs of can offer insights into its prime-yielding behavior over larger values of k. This research direction involves a detailed study of the fluctuations in prime density as k increases, focusing on identifying thresholds and critical points where prime generation becomes less reliable.
5.5.1. Methodology
The steps for this investigation are as follows:
Density Measurement: Calculate the prime density for outputs of over varying ranges of k and n. This involves using a moving window approach to observe how prime frequency shifts with increasing polynomial values.
Threshold Identification: Identify the critical points where prime density drops below certain benchmarks, signaling a decline in the polynomial’s prime-generating capability. These thresholds will be visualized through density plots, highlighting the intervals of maximum efficiency.
Comparative Analysis with Known Models: Compare the observed prime densities with those predicted by classical models, such as the Prime Number Theorem, to determine deviations. This comparison may reveal polynomial-specific behaviors that differ from general prime distribution trends.
5.6. Conclusions
These future research directions provide a roadmap for advancing the study of prime-generating polynomials. Through a combination of theoretical analysis, computational simulations, cryptographic testing, and advanced statistical modeling, the goal is to refine polynomial structures, improve prime output quality, and extend the applicability of prime generation in both mathematics and cryptography. The discoveries anticipated from this research could contribute significantly to number theory, particularly in understanding polynomial interactions with prime distributions, and enhance the security standards of cryptographic systems.
6. Conclusions
6.1. Summary of Key Findings
This study has rigorously analyzed the polynomial , designed to generate prime numbers for a specified range of values of n and k. The research covered various aspects, including mathematical clarity, prime repetition patterns, error bounds, and cryptographic implications. The following key conclusions can be drawn from the analysis:
Effective Prime Generation within Defined Range: The polynomial reliably generates prime numbers for values of when . The inductive proof confirmed the polynomial’s validity within this boundary, showcasing its ability to produce consistent primes in this range. However, the efficiency of prime generation diminishes as k approaches its upper limit, indicating a natural boundary to the polynomial’s effectiveness.
Prime Repetition Analysis and Structural Insights: The occurrence of prime repetition, especially at lower values of k, highlights the structural properties of . These repetitions are linked to the dynamic adjustment of polynomial coefficients, suggesting an inherent resonance with certain prime values. Understanding these patterns provides a foundation for refining polynomial designs, potentially reducing redundancy and increasing the diversity of generated primes.
Error Bound Validation: The error bound analysis revealed the limitations of as a prime generator, particularly as k increases. This decline in reliability is consistent with the observed reduction in prime density for larger integers, supporting the theoretical prediction that prime-generating polynomials face natural constraints. This insight has practical implications for determining the safe operational range of in applications where prime reliability is essential.
Cryptographic Potential and Predictability: The study evaluated in the context of cryptographic security, focusing on the randomness and predictability of generated primes. Although the polynomial shows promise as a prime source, the analysis revealed areas of concern related to prime predictability and repetition. These factors limit its direct applicability in high-security cryptographic systems without further refinement to enhance output randomness and uniqueness.
6.2. Implications for Number Theory
The findings of this study contribute to the broader understanding of prime generation in number theory. The polynomial offers a structured approach to generating primes that aligns with classical prime patterns, yet exhibits unique properties worthy of further exploration. The research supports the idea that algebraic structures can be fine-tuned to approximate prime behavior, but also underscores the challenges of generating primes with absolute consistency.
This study has shown that prime repetition and error bounds are integral to understanding the limitations of polynomial-based prime generation. These insights can inform future theoretical research, particularly in areas such as:
The exploration of polynomial roots and their alignment with prime distributions.
The study of congruence relations within prime-generating formulas.
Investigating the influence of polynomial coefficients on the clustering of prime values.
6.3. Cryptographic Relevance and Practical Applications
In the context of cryptography, prime numbers remain a cornerstone for secure communication, encryption, and data protection. The polynomial , despite its inherent limitations, provides a valuable case study for the design of prime-generating algorithms. This research highlights the need for continued innovation in generating secure primes, with an emphasis on reducing predictability and enhancing randomness.
The study suggests that polynomial-based prime generation, if refined, could offer advantages in specific cryptographic contexts where controlled prime generation is needed. However, for mainstream cryptographic applications, additional measures—such as modular constraints, entropy tests, and advanced randomness protocols—are required to ensure security standards are met.
6.4. Challenges and Limitations
While this research has made significant strides in understanding the capabilities of , certain challenges remain. The limitations include:
Scalability: The effectiveness of is constrained by the upper bound of . Beyond this range, the reliability of prime generation declines, limiting its utility for generating very large primes, which are essential in modern cryptography.
Prime Repetition: The phenomenon of repeated primes, although partially explained, remains a challenge. Identifying the conditions that lead to repetition and minimizing their impact on randomness is a complex task that requires further theoretical and computational analysis.
Error Bound Sensitivity: The sensitivity of the polynomial to error bounds is a limiting factor, particularly for applications requiring a high degree of certainty in prime outputs. As the quadratic and linear terms grow, the error bound analysis suggests a sharp decline in prime output quality, posing constraints on the polynomial’s range of application.
6.5. Future Directions and Open Questions
This research has laid the groundwork for future exploration in the field of prime-generating polynomials. Several promising directions are open for investigation:
Development of Enhanced Polynomials: Building on the structure of , future research can explore polynomials with modified coefficients or additional terms, potentially incorporating higher-degree components or modular constraints. The goal would be to create polynomials that maintain prime-generating capabilities over a broader range while minimizing repetitions.
Integration with Advanced Cryptographic Algorithms: The study encourages the exploration of how polynomial-based prime generators can be adapted for use in cryptographic protocols. This includes testing their compatibility with existing standards and evaluating their resilience under various attack scenarios.
Comprehensive Analysis of Prime Clustering: The observed clustering of primes within warrants further investigation. Understanding why certain primes recur and how they are distributed may provide deeper insights into both polynomial behavior and the nature of primes themselves. This line of inquiry could lead to broader discoveries in prime number theory, potentially revealing unknown patterns or relationships.
Application of Machine Learning for Predictive Analysis: Future research might employ machine learning techniques to predict prime outputs based on polynomial parameters. This involves constructing predictive models that can guide the optimization of prime-generating formulas, balancing efficiency with randomness for practical applications.
6.6. Final Remarks
The analysis of has demonstrated both the potential and limitations of polynomial-based prime generation. While the polynomial successfully generates primes within its defined range, challenges related to repetition, predictability, and error bounds highlight the complexities inherent in prime generation. These findings emphasize the delicate balance required to maintain both mathematical consistency and cryptographic robustness.
The discoveries outlined in this study contribute to ongoing research in number theory, offering a foundation for future advancements in prime generation. The quest to create reliable and efficient prime-generating algorithms continues to be a vibrant field, with significant implications for theoretical mathematics, cryptographic security, and the development of new computational tools. The insights gained here serve as a stepping stone for the next generation of researchers aiming to bridge the gap between prime theory and practical application.
References
- Avila, J. A. J., Moreira, E. D., Guimaraes, B. F. (2022). Patterns in Prime Number Distribution: The n-Square Zeta. RMU.
- Euler, L. (1772). On Prime-Generating Polynomials. Historical Papers.
- Hardy, G. H., Wright, E. M. (2008). An Introduction to the Theory of Numbers. 6th Edition, Oxford University Press.This book provides foundational concepts in number theory, including primes, prime distributions, and related mathematical theorems, which are critical for understanding polynomial-based prime generation.
- Ribenboim, P. (1991). The Book of Prime Number Records. Springer-Verlag.A comprehensive resource that documents historical and modern discoveries in prime number theory, including prime-generating formulas and their properties.
- Crandall, R., Pomerance, C. (2005). Prime Numbers: A Computational Perspective. 2nd Edition, Springer.This reference covers algorithms for prime generation, error bound analysis, and applications in cryptographic computations, providing insights into prime density and computational testing.
- Shor, P. W. (1994). Algorithms for Quantum Computation: Discrete Logarithms and Factoring. Proceedings 35th Annual Symposium on Foundations of Computer Science.Discusses the computational complexity of prime numbers and their cryptographic applications, relevant for understanding the security implications of polynomial-based prime generation.
- Koblitz, N. (1994). A Course in Number Theory and Cryptography. 2nd Edition, Springer-Verlag.Examines the application of prime numbers in cryptography, including key-generation protocols and prime-testing methods, which are essential for evaluating the cryptographic viability of Pk(n).
- Landau, E. (2005). Elementary Number Theory and Its Applications. Addison-Wesley.Provides a thorough background in number theory, including proofs involving prime numbers and methods to estimate prime density, which supports the inductive proof and error bound analysis.
- Rosser, J. B., Schoenfeld, L. (1962). Approximate Formulas for Some Functions of Prime Numbers. Illinois Journal of Mathematics.This paper provides an analysis of prime density and error bounds, helping to frame the theoretical limitations of prime-generating polynomials.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).