1. Introduction
Today, ensuring the privacy of communication is more critical than ever, driving the need for secure message transmission methods [
1]. Quantum key distribution (QKD) has become a leading approach for achieving secure communication, exploiting quantum mechanical properties to protect information from potential eavesdroppers [
2,
3,
4]. The B92 protocol [
5,
6] provides an efficient method for distributing cryptographic keys using non-orthogonal quantum states, ensuring high levels of security against interception. Unlike classical cryptographic techniques, where security depends on computational limitations, quantum cryptography leverages fundamental physical principles for inherent protection[
7].
Historically, cryptography focused on transforming messages into coded formats that could not be interpreted without a key, providing secrecy even if intercepted [
8]. However, classical encryption schemes, including those based on complex algorithms or key exchange methods (e.g., Diffie-Hellman), face increasing vulnerabilities as computational abilities advance and quantum computing becomes feasible [
9]. Quantum computers, with their ability to solve mathematical problems such as factorization far more efficiently than classical computers, pose a significant threat to traditional cryptography, necessitating new solutions like QKD that are fundamentally secure [
10].
A key aspect of quantum mechanics is that measuring a quantum state inevitably alters it - a concept known as measurement-induced disturbance [
11]. This, along with the no-cloning theorem, which asserts that an unknown quantum state cannot be copied perfectly, forms the foundation of QKD’s security. The B92 protocol uses exactly two non-orthogonal quantum states to establish a shared secret key, making any eavesdropping attempt detectable due to the resulting disturbances [
6].
The B92 protocol stands out for its simplicity compared to other QKD protocols like BB84, requiring only two detectors and two single-photon sources, which significantly facilitates the experimental setup. Despite this reduction in components, the security of key exchange is maintained through the use of non-orthogonal states, which ensure that any eavesdropping attempt will introduce detectable errors.
Nevertheless, with the rapid growth in the demand for educational quantum experiments in recent years [
12,
13,
14,
15,
16,
17] the implementation of a true B92 QKD system presents several practical challenges, which must be addressed to realize its full potential in real-world applications. For example, the requirement of single-photon sources, precise detection equipment, and a low-noise environment — all of which can be costly and technically demanding. These limitations make widespread adoption difficult, particularly in educational settings [
18]. To address these challenges, using pulsed lasers as classical light sources provides a more accessible emulation of the B92 protocol. Although such emulation lacks the absolute security of a true single-photon system, it offers an excellent way to explore the fundamental concepts of QKD in a practical setting.
In this work, we present an educational experiment that demonstrates the B92 quantum cryptography protocol without the need for specialized equipment, such as single-photon sources. Instead, the use of pulsed lasers allows for an accessible approximation of the protocol, which can be conducted in a standard undergraduate laboratory. While this emulation does not achieve true quantum security, since genuine protection requires that each information bit is conveyed by a single photon, it provides valuable insight into QKD fundamentals, particularly detection of eavesdropping attempts. This setup also illustrates the significance of the no-cloning theorem and the role of measurement disturbances in securing quantum communications.
The objective of this work is to simplify the experimental setup for the B92 protocol to enhance its accessibility while retaining its educational value. By using standard optical components, such as pulsed lasers, polarizers, and detectors, students gain hands-on experience in understanding the use of non-orthogonal quantum states for secure key transmission and the detection of eavesdropping, even within the constraints of classical emulation.
2. B92 Protocol with Alice and Bob
The B92 protocol is a QKD scheme that relies on the principles of quantum mechanics to provide secure communication between two parties, traditionally known as Alice (the sender) and Bob (the receiver). Unlike the BB84 protocol, the B92 protocol uses only two non-orthogonal states, simplifying the state preparation process while ensuring secure key distribution.
2.1. Protocol Overview
In the B92 protocol, Alice randomly generates a sequence of classical bits (0 or 1) and encodes each bit into one of two non-orthogonal quantum states. In our implementation:
Then, Alice sends the quantum states to Bob, who measures them in a randomly chosen basis:
The probabilities associated with Bob’s measurements are as follows:
-
If Alice sends 0 in basis +, Bob has:
A 50% probability of measuring 0 in basis +,
A 25% probability of measuring 1 in basis x,
A 25% probability of measuring 0 in basis x.
-
If Alice sends 1 in basis x, Bob has:
A 50% probability of measuring 1 in basis x,
A 25% probability of measuring 0 in basis +,
A 25% probability of measuring 1 in basis +.
2.2. Measurement Outcomes and Grant/Deny Criteria
Bob applies a "grant or deny" condition based on the measurement outcomes to determine whether the measured bit should be included in the final key:
If Bob measures 0 in basis x or 1 in basis +, he grants the bit.
Otherwise, he denies the bit.
The "granted" bits are those that are retained for further key processing, whereas the "denied" bits are discarded. This selection ensures that Bob only keeps results that are consistent with Alice’s original encoding under quantum mechanical principles.
2.3. Experimental Perspective
In an experimental setup, Alice’s quantum states can be prepared using polarized photons or other quantum systems capable of encoding qubit information. Bob’s measurement basis is typically selected using a polarizer or similar device, followed by a detector that counts the number of photons. The experimental outcomes align with the theoretical probabilities when Bob measures the received quantum state. The randomness introduced by both Alice and Bob in their choices ensures that any potential eavesdropper cannot predict the outcome without being detected, providing key security.
3. The Experimental Apparatus
In the experimental setup, Alice uses a pulsed laser source to generate light polarized in two distinct, non-orthogonal directions, corresponding to the states used in the B92 protocol. A polarizer and half-wave plate adjust the polarization of the incident light to the appropriate non-orthogonal state for key distribution. While this setup emulates a single-photon source, enabling Alice to transmit information securely, it does not achieve the true single-photon level necessary for absolute quantum security. Bob’s apparatus consists of a half-wave plate, a polarizing beam splitter (PBS), and two detectors. He randomly selects its measurement basis by rotating the polarization plate and then uses the PBS and detectors to determine whether the incoming light was transmitted or reflected, thereby identifying the bit sent by Alice.
The apparatus is designed to emulate the behavior of a true quantum key distribution system but uses classical optical components such as pulsed lasers, making it accessible for educational laboratories. In the B92 protocol, Eve’s presence as an eavesdropper can be detected if she attempts to measure the polarization of the transmitted photon, as her actions will inevitably disturb the system and introduce detectable errors. This experimental setup effectively demonstrates the basic principles of B92 quantum cryptography, including the security benefits derived from the use of non-orthogonal quantum states, while remaining simple enough for use in an undergraduate educational setting.
The reduced complexity of the B92 protocol compared to BB84 arises from the use of only two states instead of four, resulting in fewer detectors and simpler state preparation. This not only simplifies the experimental setup but also emphasizes the inherent efficiency of the B92 protocol for secure quantum communication
3.1. Introducing Eve
In a real-world scenario, the security of quantum communication is often compromised by an eavesdropper (Eve). Eve attempts to intercept the quantum channel between Alice and Bob to gain information about the key. However, the fundamental principles of quantum mechanics, including the no-cloning theorem and the disturbance caused by measurement, make eavesdropping detectable.
3.2. Eve’s Interaction with the Quantum Channel
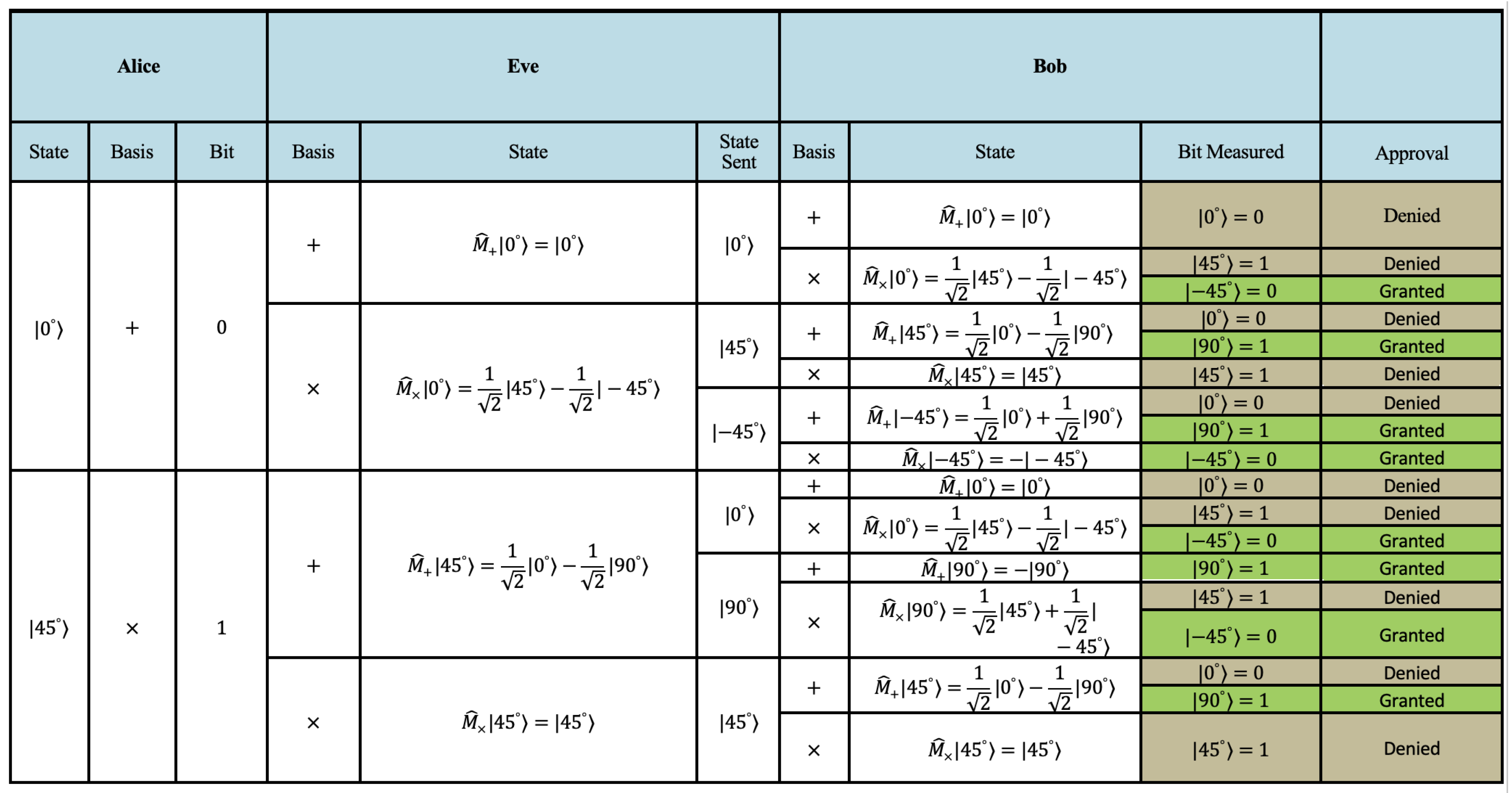
If Eve intercepts the quantum state sent from Alice to Bob, she must choose a basis in which to measure the quantum state. Given that the states used in the B92 protocol are non-orthogonal, Eve’s selection introduce an unavoidable uncertainty:
If Eve measures in the + basis or x basis, the quantum state collapses, meaning Bob may receive a state that is different from what Alice originally sent.
If Bob’s basis does not match Eve’s chosen basis, the quantum measurement statistics will reveal discrepancies between Alice’s and Bob’s results.
3.3. Detection of Eve’s Presence
The presence of Eve can be detected by comparing a subset of the granted bits that Alice and Bob have kept. If Eve measures the quantum state, her actions cause errors in Bob’s measurements. This leads to a deviation from the expected proportion of "granted" bits, thereby indicating the presence of eavesdropping.
3.4. Experimental Perspective with Eve
In an experimental implementation, the quantum channel can be monitored for error rates. The presence of an eavesdropper will introduce a higher-than-expected error rate in the bits Bob receives and ultimately grants. By comparing a subset of the final key over a classical public channel, Alice and Bob can estimate the error rate and detect the presence of an eavesdropper.
4. Theory of Experiment
4.1. One-Time Pad
The one-time pad [
19,
20] is a classical encryption technique assisted by quantum physics to meet the method’s requirements and is considered
secure in principle. While the desired message consists of a non-random sequence of 0s and 1s,the one-time pad is a single-use key consisting of a random sequence of 0s and 1s. A binary addition [
21,
22] of the message to the key results in another sequence of random bits, which is then sent as the encrypted message.
The addition rules for the bits are:
When applying a binary addition with the secure key generated by the B92 protocol to the original message, the sender can encrypt the message. By applying a binary addition with the secure key to the encrypted message, the receiver can de-crypt it and obtain the original message. An example is shown in
Table 1.
If the encrypted message is intercepted, the eavesdropper requires the key to decode the message, otherwise the random sequence cannot be interpreted. The binary sequence can be converted to strings using the American Standard Code for Information Interchange (ASCII) [
23]. An example of the one time pad is shown in
Table 1.
Table 1.
XOR Encryption and Decryption of Letters M, I, and T.
Table 1.
XOR Encryption and Decryption of Letters M, I, and T.
|
Letter |
Definition |
Binary Value |
Key (8-bit) |
XOR Result |
| M |
ASCII |
01001101 |
11010011 |
10011110 |
| Decrypted |
01001101 |
|
| I |
ASCII |
01001001 |
01101110 |
00100111 |
| Decrypted |
01001001 |
|
| T |
ASCII |
01010100 |
10100101 |
11110001 |
| Decrypted |
01010100 |
|
While computer-generated pseudo-random numbers are not truly (
) random [
24],the one-time pad requires a completely random selection of the encryption key. Nonetheless, quantum physics offers numerous possibilities for true randomness [
25], such as radioactive decay. Quantum random number generators are a key component in quantum cryptography data networks. In practice, a photon that is reflected by a beam-splitter can be interpreted as 1 and a photon that is transmitted by a beam-splitter can be interpreted as 0.
Therefore, a conventional light source with the same intensity [
26,
27], photon distribution on two single photo-detectors can be considered truly random.
Generally, B92 protocol’s core purpose is generating a secure key between the sender and the receiver.
4.2. Key Distribution
The sending unit ’Alice’ consists of a pulsed laser source [
26,
27], which is polarized in a specific direction, and a half-wave plate (
with
being the wave length), which rotates the polarization of the incident light by double the physical rotation angle of the plate. We note that the mentioned angle refers to the rotation angle of the polarization, and not of the plate.
The receiving unit ’Bob’ consists of a beam-splitter, a half-wave plate (), two polarizing beam-splitters (PBS) and four detectors to indicate whether the light sent by Alice was reflected or transmitted through the PBS.
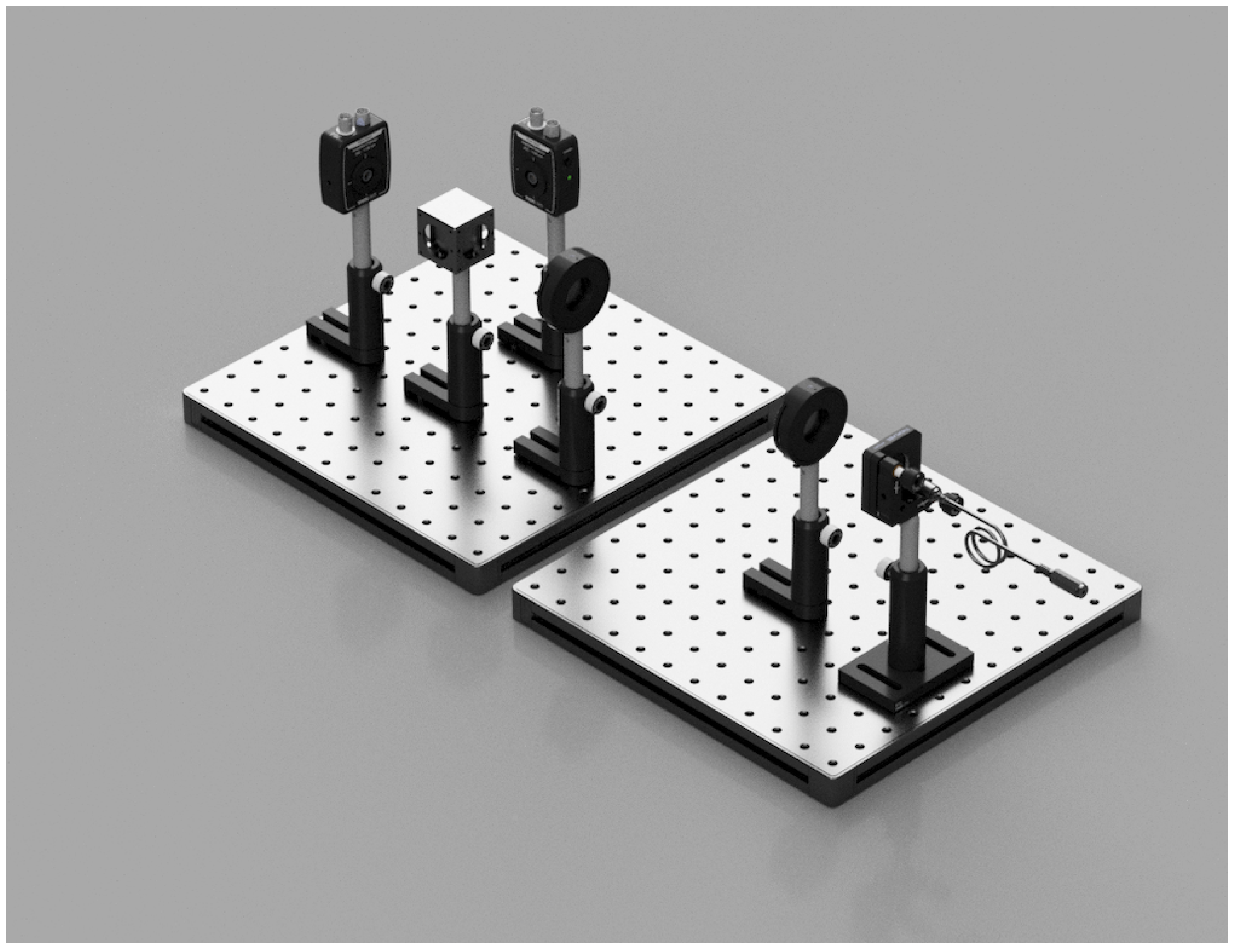
A schematic sketch of Alice and Bob is provided in
Figure 1.
Before Alice can send a message to Bob, a secure key must be generated. If Alice’s pulsed source is polarized horizontally, two bases can be defined, “+” and “”, where each contains two light polarizations. Alice can send a random bit of 0 or 1 in both bases. The “+” basis consists of and polarizations, while the “” basis consists of and polarizations. In general, either basis can be used to represent a binary bit: “0’ for and and “1’ for and .
In the B92 algorithm, we limit Alice’s options to two choices: a state of “0” in the “” basis (which corresponds to ) and a state of “1” in the “+” basis (which corresponds to ). To create a secure key, Alice randomly selects a bit and adjusts the polarization plate accordingly, which also determines the basis for the bit. After making her selection, she sends the bit to Bob using the scheme described above.
Bob randomly selects a basis, determining which of the two detectors he uses for measurement: either the detector without a half-wave plate (+” basis) or the detector with a half-wave plate (” basis). He then records which detector registered the bit.
If Alice sends “0” in the “” basis and Bob measures in the same `” basis, he will always measure “0”. However, if he measures in the “+” basis, he has a chance to measure “0” and a to measure “1”. This occurs because the polarizing beam splitter (PBS) transmits light polarized at degrees and reflects light polarized at degrees.
In the B92 protocol, not all transmitted bits are accepted as part of the final key. Some bits are discarded since we cannot be certain of their original value, as explained earlier. The accepted bits, known as ’impossible bits’, are those where Bob receives a bit that we know Alice couldn’t have sent, due to the restrictions placed on her choices. These impossible bits are: "1” in the "+” basis (corresponding to ) and "0” in the "” basis (corresponding to ).
By testing all possible combinations of Alice’s transmissions and Bob’s measurements, it becomes clear that only one transmission option from Alice can result in Bob receiving these bits. When Bob measures these bits, he can be sure that he has received exactly what Alice sent. After each measurement, Bob announces whether the bit was accepted or denied via the public channel.
The encryption key is derived only from the accepted measurements. For a complete list of transmission options, see Figure 3.
If there is no eavesdropper, the probability of accepting a single bit is
. A detailed explanation of this calculation will be provided in
Chapter 4.4.
4.3. Detection of an Eavesdropper
The eavesdropper unit ’Eve’ is positioned between Alice and Bob, as shown in
Figure 2. Eve’s setup consists of the same components, but in reverse order. It is strategically placed to measure the light coming from Alice and then transmit the same information to Bob.
As Eve cannot copy the pulsed beam transmitted by Alice without altering its state, she must randomly select the basis in which it will be transmitted to Bob. In addition, a random basis must be selected for the bit received from Alice. Therefore, two random selections are required for Eve’s bases. Alice and Bob continue their protocol as they would without Eve. However, due to Eve’s interference, there are now instances where a bit is accepted, but it is not the original bit that Alice sent. To see all transmission options, see Figure 4.
With the eavesdropper present, Bob accepts
of the bits. Eve is detected because this acceptance rate is
higher than expected. A detailed explanation of this calculation will be provided in
Chapter 4.4.
Table 2.
Quantum Cryptographic Encoding and Decoding of Letters M, I, and T Using Random Bitwise Keys for Secure Message Transmission.
Table 2.
Quantum Cryptographic Encoding and Decoding of Letters M, I, and T Using Random Bitwise Keys for Secure Message Transmission.
| Message |
M |
|
| Binary Message |
0 |
1 |
0 |
0 |
1 |
1 |
0 |
1 |
|
| + |
|
|
|
|
|
|
|
|
|
| Random Key |
1 |
1 |
0 |
1 |
0 |
0 |
1 |
1 |
|
| Encrypted Message |
1 |
0 |
0 |
1 |
1 |
1 |
1 |
0 |
|
| + |
|
|
|
|
|
|
|
|
|
| Random Key |
1 |
1 |
0 |
1 |
0 |
0 |
1 |
1 |
|
| Decrypted Message |
0 |
1 |
0 |
0 |
1 |
1 |
0 |
1 |
|
| Message |
M |
|
| |
| Message |
I |
|
| Binary Message |
0 |
1 |
0 |
0 |
1 |
0 |
0 |
1 |
|
| + |
|
|
|
|
|
|
|
|
|
| Random Key |
0 |
1 |
1 |
0 |
1 |
1 |
1 |
0 |
|
| Encrypted Message |
0 |
0 |
1 |
0 |
0 |
1 |
1 |
1 |
|
| + |
|
|
|
|
|
|
|
|
|
| Random Key |
0 |
1 |
1 |
0 |
1 |
1 |
1 |
0 |
|
| Decrypted Message |
0 |
1 |
0 |
0 |
1 |
0 |
0 |
1 |
|
| Message |
I |
|
| |
| Message |
T |
|
| Binary Message |
0 |
1 |
0 |
1 |
0 |
1 |
0 |
0 |
|
| + |
|
|
|
|
|
|
|
|
|
| Random Key |
1 |
0 |
1 |
0 |
0 |
1 |
0 |
1 |
|
| Encrypted Message |
1 |
1 |
1 |
1 |
0 |
0 |
0 |
1 |
|
| + |
|
|
|
|
|
|
|
|
|
| Random Key |
1 |
0 |
1 |
0 |
0 |
1 |
0 |
1 |
|
| Decrypted Message |
0 |
1 |
0 |
1 |
0 |
1 |
0 |
0 |
|
| Message |
T |
|
4.4. Mathematical Description in Dirac Notation
The four polarization states in this experiment are
,
,
,
, where
are the states of the "+ " basis and
are the states of the "
" basis. They are defined using Dirac’s bra-ket notation [
28], where
denotes a vector that represents a quantum state, and
denotes a linear map that maps a vector to a number in the complex plane.
Consequently, the linear functional acting on a vector is written as
, corresponding to a scalar product for two states [
29,
30]. The scalar product of two orthogonal states is:
, whereas the squared absolute value of the scalar product represents the probability that a
polarized pulsed beam passes through a polarizer oriented in a
direction. The scalar product of the same two states is:
.
These states can be expressed as linear combinations of the other basis:
. Since the scalar product must be normalized:
, all four states can be expressed by a superposition of the others:
Thus, for example, the probability of a
polarized pulsed beam passing a
oriented polarizer is
:
The probability for the other states and bases can be derived similarly.
Here, we re-derive the projections of the measurement operators for both possible and impossible bits in the context of eavesdropping in the B92 protocol. Specifically, we examine the projections for the possible bits at angles and , and for the impossible bits at and , which could result from an eavesdropper (Eve).
The base operators, which are linear maps that input a ket
and output a ket
, are introduced to describe a measurement in either of the bases.
The operators act on a given state, and when an operator acts on a basis that matches the polarized state, the eigenvalue corresponds to the state itself. Note that an eigenvalue of corresponds to transmission and is assigned as bit 0.
The same can be derived for
operating on the
base. However, if an operator acts on the opposite basis, it is possible to show that the transmission probability of a pulsed beam through a polarizer is
:
Similarly, for the other cases:
By re-analyzing the projections on the basis states associated with (for and bases) and (for and bases), we can quantify the probability distributions and detection rates that serve as eavesdropping indicators. This derivation provides insight on how each of Eve’s basis choices affects the measured statistics, and how the expected and observed rates of impossible bits compare.
Figure 4 and
Figure 3 shows different cases for Alice and Bob with and without an eavesdropper.
5. Experimental Procedure
The light source in the experimental system is a pulsed laser rather than a single-photon source, meaning that full prevention of interception cannot be guaranteed. Therefore, to eavesdrop, Eve must separate a portion of the light transmitted from Alice, analyze part of it, and send the remainder to Bob without detection. However, the sequence of the protocol in this experiment is identical to that of a true quantum encryption system. To avoid biased randomization, all bases and bits for Alice, Bob, and Eve should be generated simultaneously. The complete experimental setup is shown in
Figure 2.
5.1. Calibration
The model of the lasers in the system is CPS635R (Thorlabs) [
31]; collimated laser diode module: 635 nm, 1.2 mW, Gaussian profile beam. The detectors models are EDU-QCRY1/M by Thorlabs.
Before conducting the experiment, the light source and the detectors were calibrated [
26,
27]. The pulsed laser was calibrated by a polarizer to a horizontal polarization of
. Both Bob’s and Eve’s detectors were aligned so that transmitted and reflected light would reach the desirable detector. Both detectors were also tested for each base and bit.
5.2. Key Transmission Without Eve
Alice randomly chooses a bit (0 or 1), while Bob randomly selects his basis (+ or
), as illustrated in
Figure 3. Alice adjusts her wave plate accordingly, and Bob determines which sensor pair he will use to receive the signal. The random selection of bases and bits is made using a computational script, which is explained later in the paper. The laser pulse is then sent through the setup, and Bob records whether he measured a 0 or 1 bit, along with the chosen basis. He then transmits, via the public channel, whether he accepted or denied the bit. At the end of the process, the bits accepted by Bob form the shared encryption key. Using this key, Alice can encrypt the message and send it to Bob. Bob can then decrypt the message using the same key.
5.3. Key Transmission With Eve
The complete key distribution process in the B92 protocol can be described through a series of steps illustrating how information is prepared, transmitted, measured, and how potential eavesdropping can be detected.
Briefly, Alice randomly selects a bit (0 or 1) and prepares a photon polarized at one of two non-orthogonal states. Bob randomly selects a measurement basis (+ or
) to detect the photon, while Eve, as an eavesdropper, intercepts and retransmits the photon using randomly chosen bases. If the bases are mismatched, inconsistencies arise in Bob’s measurements, enabling the detection of eavesdropping, as illustrated in
Figure 4. Below are the detailed steps involved in the protocol:
Step 1: The pulsed laser is set to one of two non-orthogonal polarization angles. For example, Alice prepares a state polarized at 45°, representing one of the two non-orthogonal states used in the B92 protocol.
Step 2: Alice sends the prepared state using the pulsed laser, emulating a single-photon state. The specific state to be sent is chosen randomly. For example, Alice may send the state representing "1" (polarized at 45°).
Step 3: Eve intercepts the photon, chooses a random basis, and measures the state by projecting it along one of the two non-orthogonal states used by Alice. If Eve’s chosen basis matches Alice’s polarization state (i.e., Eve chooses 45° in our example), she will measure the state with high certainty. Otherwise, the result is probabilistic. Let us assume that in our example Eve indeed chooses 45°, thus successfully measuring the state.
Step 4: If Eve successfully measures the state, she records the result as "1" and prepares a new state to send to Bob. In the B92 protocol, one state (e.g., 45°) corresponds to a successful detection, representing a "1" bit, while the other state (e.g., 0°) ideally results in no detection, effectively indicating the absence of an encoded bit. However, if Eve’s measurement basis does not match Alice’s transmitted state, she may still obtain a result, but it will be probabilistic and can be projected into a different state. Consequently, the bit Eve retransmits could differ from Alice’s original bit, leading to inconsistencies in Bob’s measurements. These inconsistencies manifest as detectable errors, signaling the presence of eavesdropping. In our example, let us assume that Eve successfully measures "1" and retransmits it.
Step 5: Eve prepares the transmitted photon with the same polarization she measured and sends a new laser pulse, emulating the single-photon state detected from Alice.
Step 6: Bob chooses a random measurement basis. In the B92 protocol, Bob uses a detector corresponding to one of the two non-orthogonal states. In our example, let us assume that Bob chooses the same basis as Alice (i.e., 45°). Thus, he successfully detects the photon and records the bit as "1".
Step 7: If Bob’s measurement basis matches Alice’s original state, he successfully detects the pulse and records the correct bit ("1") with certainty. If Bob’s basis does not match Alice’s original state, the result is probabilistic, introducing the chance of an incorrect detection due to the nature of non-matching basis measurements.
Step 8: Alice continues the process by sending subsequent bits, repeating the steps for each bit in her message.
These steps are repeated for all subsequent bits in the key distribution process, with each bit undergoing the same sequence of preparation, transmission, measurement, and eavesdropping detection to ensure the security and integrity of the protocol.
6. Computational Procedure
For the B92 protocol, MATLAB scripts were developed to simulate two primary cases: one involving only Alice and Bob, and another including an eavesdropper between Alice and Bob. The simulations were designed to analyze the convergence of granted bit rates, allowing us to compare theoretical expectations with simulated outcomes. In the first case, only Alice and Bob are involved, with Bob measuring the bits transmitted by Alice based on their chosen measurement bases. The second case introduced Eve, who intercepted and measured Alice’s bits before retransmitting them to Bob, thus impacting the overall bit error rates and convergence due to probabilistic measurement interference.
Both cases were simulated in a series of increasing bit sample sizes, defined by the following values:
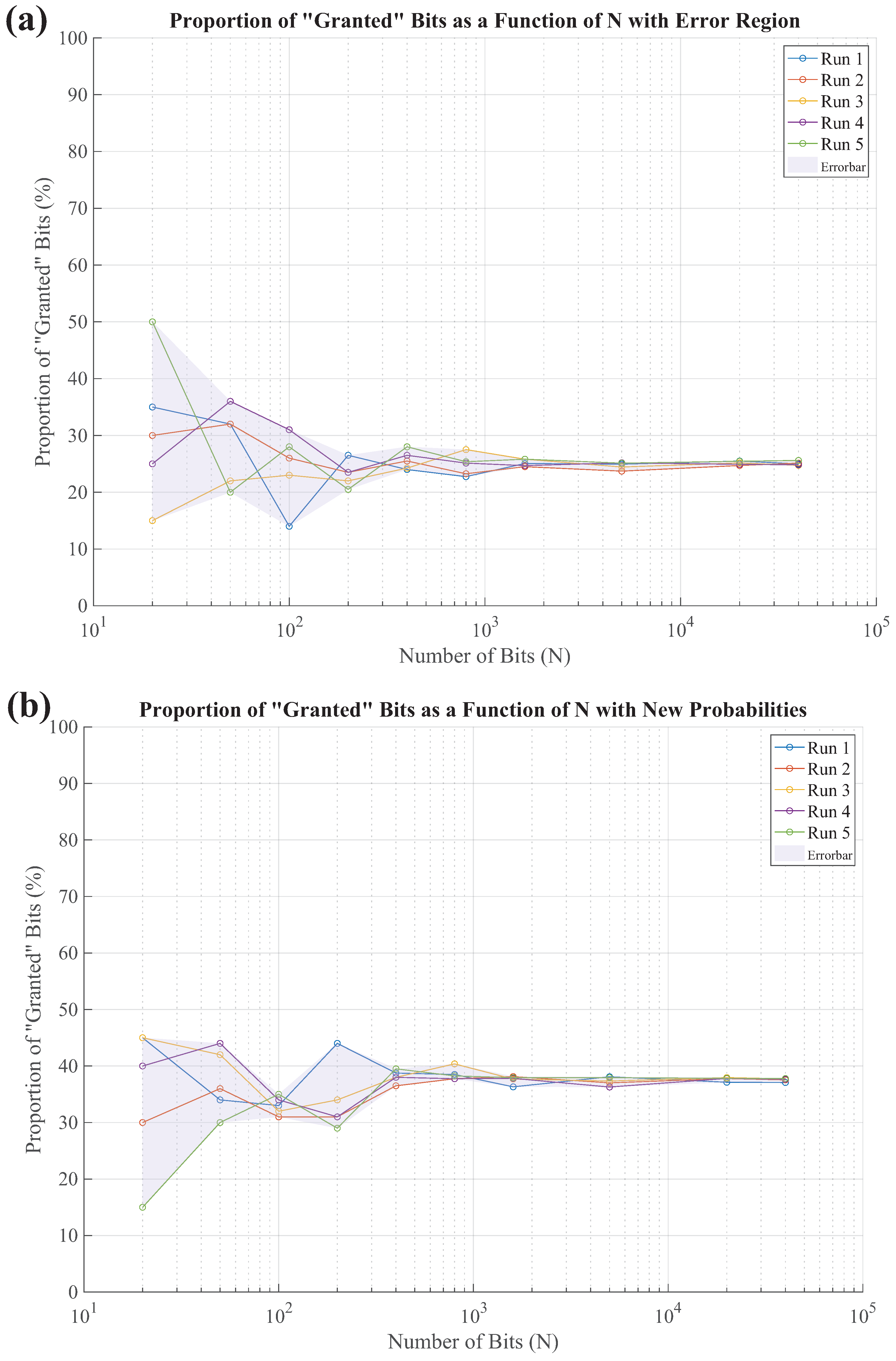
The results showed convergence toward the expected granted bit rates: approximately 25% in the Alice-Bob configuration, indicating successful bit retention in the absence of an eavesdropper, and around 37.5% in the Alice-Eve-Bob configuration, reflecting the additional errors introduced by Eve’s interference.
On a single core of an Intel Xeon E5-2697v2 CPU, the average running time for each of these simulations over the chosen
was 26 seconds. In contrast, running the simulations on an M4 Pro achieved a significantly faster average runtime of 1.15 seconds. A comparison of the average simulation run time on various CPUs is shown in
Table 3. This efficient performance, especially on modern processors, underscores the feasibility of using MATLAB for large-scale simulations of quantum key distribution protocols, enabling practical analysis of convergence behavior in B92 under realistic computational constraints.
This approach effectively illustrates the theoretical foundations of the B92 protocol and its sensitivity to eavesdropping, evidenced by the measurable increase in granted bits when Eve is active in the communication channel. The simulation code for the B92 protocol can be found on GitHub [
32].
Figure 5.
Simulation results for the proportion of "granted" bits as a function of the number of transmitted bits N. The runs correspond to the values , showcasing convergence behavior. Error bars represent the variability across different runs, with the expected granted bit rate approximating 25% for the Alice-Bob setup (a) and 37.5% for the Alice-Eve-Bob setup due to errors introduced by the eavesdropper (b).
Figure 5.
Simulation results for the proportion of "granted" bits as a function of the number of transmitted bits N. The runs correspond to the values , showcasing convergence behavior. Error bars represent the variability across different runs, with the expected granted bit rate approximating 25% for the Alice-Bob setup (a) and 37.5% for the Alice-Eve-Bob setup due to errors introduced by the eavesdropper (b).
7. Results
All tables, summarizing the results for each part, including the random generated bases and bits, are given in
Appendix A.
7.1. Alice and Bob Without Eve
First, we generated 45 and 100 random bits by selecting two non-orthogonal bases. This was achieved through two nested loops: one to determine the bit value and another to select the basis. For generating
, we used the bit value ’0’ with the ’+’ basis, whereas for generating
, the bit value ’1’ was combined with the ’x’ basis. This process was implemented using the initial stage of the experimental setup, with Alice being the first isle in
Figure 1.
Subsequently, Bob , the second isle in
Figure 1, generated a random sequence of 45 bases, which he used in conjunction with his two detectors to measure the incoming bits from Alice. Bob retained only the “impossible bits”, defined as instances where the measurement outcomes could not align with Alice’s original bit values due to the protocol’s design. Specifically, these impossible bits occur when Alice transmits
and Bob measures
in the ’+’ basis, or when Alice transmits
and Bob measures
in the ’x’ basis.
It is important to note that these impossible bits correspond to specific polarization states: the bit value ’1’ in the ’+’ basis, associated with , and the bit value ’0’ in the ’x’ basis, associated with . This distinction plays a critical role in the security of the B92 protocol, as the detection of such bits allows Bob to identify key bits with absolute certainty, assuming no eavesdropping occurs. The procedure highlights the reliance on quantum mechanical principles, particularly the disturbance induced by measurements, to ensure secure communication.
7.2. Alice and Bob with Eve
In this case, Eve is introduced into the communication channel between Alice and Bob, as depicted in
Figure 2, where it occupies the middle isle of the experimental setup. Eve intercepts and measures the quantum states sent by Alice and then retransmits the measured states to Bob, while attempting to remain undetected. This interception introduces disturbances into the communication channel due to the fundamental principles of quantum mechanics, which ensure that measurements of non-orthogonal quantum states cannot be performed without altering their original properties.
In our experiment, we monitor Eve’s presence by analyzing the proportion of "granted" bits - the subset of bits retained by Bob after matching his measurement basis with the transmitted state. This proportion is then compared against the expected theoretical values derived from the protocol. As illustrated in
Figure 5, the deviation in the proportion of "granted" bits serves an indicator of Eve’s interference. In a secure, undisturbed channel between Alice and Bob, the proportion of "granted" bits stabilizes around
. However, when Eve is introduced, this value rises to approximately
, as summarized in
Table 4.
The increase in the "granted" bit proportion is a direct consequence of Eve’s interference. The experimental data shows that when Eve intercepts a quantum state, she must choose a basis for measurement. If her chosen basis matches Alice’s transmitted basis, Eve can measure the state with high accuracy and retransmit it to Bob. However, if her basis does not match Alice’s, Eve’s measurement collapses the quantum state into a new one, deviating from Alice’s original encoding. Evidently, this probabilistic disturbance is propagated to Bob, who may receive altered states that do not align with the original protocol design. Consequently, we observe that this disruption changes the statistical probabilities of Bob’s measurements, increasing the likelihood of granting bits that deviate from the expected pattern in direct Alice-Bob communication.
8. Discussion
The presented experiment effectively showcases the principles of the B92 quantum cryptography protocol, offering an educational and accessible framework for exploring fundamental QKD concepts. By employing classical optical components such as pulsed lasers and polarizers, the setup avoids reliance on costly single-photon sources, significantly reducing the barriers to be implemented by institutions and individuals interested in quantum cryptography. This practical approach not only enables hands-on exploration of the B92 protocol but also bridges the gap between theoretical quantum mechanics and its real-world applications. The experimental results closely align with theoretical predictions, demonstrating the protocol’s robustness in detecting eavesdropping through observable deviations in granted bit rates.
The B92 protocol’s reliance on just two non-orthogonal quantum states and a pair of detectors highlights its simplicity and effectiveness for educational and experimental applications. This minimalistic design not only simplifies experimental setups, making it ideal for introductory quantum communication courses and workshops, but also demonstrates the protocol’s inherent efficiency as a practical introduction to secure quantum communications. Compared to BB84, the most commonly used QKD protocol, B92 requires a less complex experimental setup, utilizing only two detectors and a single pulsed laser source. In contrast, BB84 employs four distinct quantum states and multiple detectors to account for all possible measurement outcomes, increasing alignment complexity and equipment demands. While BB84 enables detection across a broader range of states, the simple design of B92 significantly reduces technical and financial demands, making it particularly suitable for institutions focused on illustrating the foundational principles of QKD.
Although the current implementation emphasizes the B92 protocol, this experiment provides a versatile foundation that can be expanded in several ways. One potential use is the inclusion of additional QKD protocols, such as the Differential Phase Shift (DPS) protocol [
33]. The DPS protocol, introduced in 2002, uses the relative phase difference between consecutive coherent light pulses to encode key information [
34]. Including the DPS protocol in the experimental setup would enable to explore a phase-based QKD scheme, contrasting it with the prepare-and-measure approach of B92. This comparison would improve our understanding of different encoding mechanisms, security features, and the practical considerations of implementing phase-coherent protocols.
Incorporating the DPS protocol could also inspire discussions about its practical applications, particularly its suitability for long-distance QKD in optical fiber networks [
35]. The DPS protocol’s robustness against photon-number-splitting (PNS) attacks and its compatibility with coherent light sources make it a strong candidate for scalable and efficient implementations. A hybrid experimental setup combining the non-orthogonal state preparation of B92 with the relative phase encoding of DPS could further enrich the learning experience. Such a set-up would provide insight into multiprotocol systems designed for specific challenges, such as high-loss environments or metropolitan QKD networks [
36,
37].
In real-world contexts, the DPS protocol’s advantages make it a compelling addition. Its efficient use of coherent pulses and relative phase encoding align with the practical requirements of fiber-based quantum networks, offering robustness and simplicity for deployment in large-scale infrastructure. Adapting the experimental setup to include DPS-like capabilities would highlight these practical aspects, further emphasizing the relevance of QKD protocols in addressing contemporary cyber-security challenges [
38].
The presented experiment serves as both an accessible introduction to quantum cryptography principles and a scalable platform for advanced research and practical applications. Its modular design and adaptability enable future enhancements, such as integrating phase modulators, quantum random number generators, or additional detection systems, transforming it into a fully functional QKD system capable of supporting various protocols [
39]. This flexibility not only ensures its continued relevance for educational and research purposes but also highlights its potential to inspire innovations in low-cost, high-security communication systems, positioning it as a cornerstone for advancements in quantum cryptography.
Author Contributions
Conceptualization, supervision, software and methodology, G.G.R.; Software, validation, formal analysis, investigation, writing, S.P.G; Project administration, review and editing, A.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The simulations mentioned in this article are available online [
32]. Experimental data is available in the supplementary material.
Acknowledgments
We thank Prof. Haim Suchowski, Prof. Shimshon Bar-Ad, and the School of Physics and Astronomy in Tel Aviv University for providing us with the necessary tools and laboratory equipment to carry out this study. We extend our gratitude to Prof. Ady Arie for his invaluable guidance, wisdom, and unwavering support. The authors also thanks Prof. Wolfgang Ketterle for his mentorship and steadfast encouragement.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Raw Data
Table A1.
Alice and Bob’s Basis and Bit Values for 45 bits.
Table A1.
Alice and Bob’s Basis and Bit Values for 45 bits.
| Alice Basis |
Alice Bit |
Bob Basis |
Bob Bit |
| |
| x |
1 |
+ |
0 |
| x |
1 |
x |
1 |
| x |
1 |
x |
1 |
| x |
1 |
x |
1 |
| x |
1 |
+ |
0 |
| x |
1 |
+ |
1 |
| + |
0 |
+ |
0 |
| + |
0 |
+ |
0 |
| + |
0 |
+ |
0 |
| x |
1 |
+ |
1 |
| x |
1 |
+ |
0 |
| x |
1 |
x |
1 |
| x |
1 |
x |
1 |
| + |
0 |
x |
1 |
| + |
0 |
x |
1 |
| + |
0 |
x |
1 |
| + |
0 |
+ |
0 |
| + |
0 |
+ |
0 |
| x |
1 |
+ |
0 |
| + |
0 |
x |
0 |
| x |
1 |
+ |
0 |
| x |
1 |
+ |
1 |
| + |
0 |
+ |
0 |
| + |
0 |
x |
0 |
| x |
1 |
x |
1 |
| + |
0 |
+ |
0 |
| x |
1 |
+ |
0 |
| x |
1 |
+ |
1 |
| + |
0 |
x |
0 |
| + |
0 |
x |
1 |
| + |
0 |
+ |
0 |
| x |
1 |
+ |
1 |
| + |
0 |
x |
1 |
| x |
1 |
x |
1 |
| + |
0 |
+ |
0 |
| + |
0 |
+ |
0 |
| x |
1 |
+ |
1 |
| x |
1 |
+ |
1 |
| x |
1 |
x |
1 |
| + |
0 |
+ |
0 |
| + |
0 |
+ |
0 |
| + |
0 |
x |
1 |
| x |
1 |
+ |
1 |
| x |
1 |
+ |
0 |
| + |
0 |
x |
0 |
Table A2.
Alice and Bob’s Basis and Bit Values for the Extended Dataset.
Table A2.
Alice and Bob’s Basis and Bit Values for the Extended Dataset.
| Alice Basis |
Alice Bit |
Bob Basis |
Bob Bit |
| |
| x |
0 |
x |
0 |
| x |
1 |
x |
1 |
| + |
1 |
+ |
1 |
| + |
0 |
+ |
1 |
| x |
0 |
x |
0 |
| + |
1 |
x |
1 |
| x |
1 |
+ |
1 |
| + |
1 |
+ |
1 |
| x |
1 |
x |
1 |
| + |
1 |
+ |
1 |
| x |
1 |
+ |
0 |
| + |
1 |
x |
0 |
| x |
1 |
+ |
0 |
| + |
1 |
+ |
1 |
| x |
0 |
+ |
0 |
| + |
0 |
x |
1 |
| + |
0 |
+ |
0 |
| + |
1 |
+ |
1 |
| + |
0 |
+ |
0 |
| x |
0 |
+ |
0 |
| + |
1 |
+ |
1 |
| + |
1 |
x |
0 |
| + |
0 |
+ |
0 |
| x |
0 |
+ |
0 |
| + |
1 |
+ |
1 |
| + |
0 |
x |
1 |
| + |
1 |
+ |
1 |
| x |
1 |
x |
1 |
| + |
0 |
+ |
0 |
| + |
1 |
x |
0 |
| x |
0 |
+ |
0 |
| + |
1 |
x |
0 |
| x |
0 |
x |
0 |
| x |
1 |
x |
1 |
| x |
1 |
x |
1 |
| x |
0 |
x |
0 |
| x |
0 |
x |
0 |
| + |
0 |
x |
1 |
| x |
0 |
x |
0 |
| + |
0 |
+ |
0 |
| x |
1 |
x |
1 |
| x |
0 |
x |
0 |
| + |
1 |
+ |
1 |
| + |
0 |
+ |
0 |
| x |
0 |
+ |
0 |
| + |
1 |
+ |
1 |
| x |
0 |
x |
0 |
| x |
1 |
x |
1 |
| + |
1 |
+ |
1 |
| x |
1 |
x |
1 |
| + |
1 |
x |
0 |
| + |
0 |
+ |
0 |
| + |
1 |
+ |
1 |
| x |
1 |
x |
1 |
| x |
1 |
+ |
1 |
| + |
0 |
+ |
0 |
| x |
1 |
x |
1 |
| x |
1 |
+ |
0 |
| x |
1 |
x |
1 |
| x |
1 |
x |
1 |
| + |
1 |
+ |
1 |
| x |
0 |
x |
0 |
| + |
0 |
x |
1 |
| x |
1 |
x |
1 |
| + |
0 |
x |
1 |
| + |
1 |
+ |
1 |
| + |
1 |
+ |
1 |
| + |
1 |
x |
0 |
| + |
0 |
+ |
1 |
| + |
0 |
x |
1 |
| x |
1 |
x |
1 |
| x |
0 |
+ |
1 |
| + |
0 |
+ |
0 |
| + |
1 |
+ |
1 |
| + |
1 |
x |
0 |
| x |
1 |
+ |
0 |
| x |
1 |
x |
1 |
| x |
0 |
+ |
0 |
| + |
0 |
x |
0 |
| x |
0 |
+ |
1 |
| x |
1 |
x |
1 |
| x |
0 |
+ |
1 |
| x |
1 |
x |
1 |
| + |
0 |
+ |
0 |
| x |
0 |
+ |
0 |
| x |
0 |
+ |
0 |
| x |
1 |
+ |
0 |
| + |
0 |
+ |
0 |
| + |
1 |
+ |
1 |
| + |
0 |
x |
0 |
| x |
1 |
+ |
0 |
| + |
1 |
+ |
1 |
| x |
0 |
+ |
0 |
| + |
1 |
x |
0 |
| + |
0 |
x |
0 |
| x |
0 |
+ |
1 |
| x |
0 |
x |
0 |
| x |
0 |
x |
0 |
| + |
1 |
+ |
1 |
| + |
1 |
x |
0 |
Table A3.
Alice, Eve, and Bob’s Basis and Bit Values for 45 bits.
Table A3.
Alice, Eve, and Bob’s Basis and Bit Values for 45 bits.
| Alice Basis |
Alice Bit |
Eve Incident Basis |
Eve Basis Transmitted |
Bob Basis |
Bob Bit |
| |
| + |
0 |
x |
x |
+ |
1 |
| + |
1 |
x |
+ |
x |
0 |
| + |
0 |
x |
x |
x |
1 |
| + |
0 |
x |
x |
x |
1 |
| x |
0 |
+ |
x |
x |
1 |
| + |
0 |
x |
x |
x |
1 |
| x |
0 |
+ |
x |
x |
0 |
| x |
0 |
+ |
x |
x |
1 |
| + |
0 |
+ |
x |
x |
0 |
| x |
1 |
x |
x |
x |
1 |
| x |
0 |
x |
x |
x |
1 |
| x |
1 |
+ |
x |
x |
1 |
| + |
1 |
+ |
+ |
+ |
1 |
| + |
0 |
+ |
+ |
+ |
0 |
| x |
0 |
+ |
x |
x |
1 |
| + |
0 |
+ |
x |
x |
0 |
| x |
1 |
x |
x |
x |
1 |
| x |
0 |
+ |
+ |
+ |
1 |
| x |
1 |
x |
+ |
+ |
1 |
| + |
1 |
+ |
x |
x |
0 |
| + |
0 |
+ |
+ |
+ |
1 |
| x |
1 |
x |
x |
+ |
0 |
| x |
1 |
x |
x |
+ |
0 |
| + |
0 |
x |
+ |
+ |
1 |
| + |
0 |
+ |
+ |
+ |
0 |
| + |
0 |
x |
x |
x |
1 |
| x |
0 |
+ |
+ |
+ |
1 |
| + |
1 |
x |
+ |
x |
1 |
| x |
0 |
+ |
+ |
x |
1 |
| x |
1 |
+ |
+ |
+ |
1 |
| x |
1 |
x |
+ |
+ |
1 |
| + |
0 |
+ |
+ |
+ |
0 |
| x |
1 |
x |
x |
+ |
0 |
| + |
1 |
+ |
x |
+ |
0 |
| x |
1 |
x |
+ |
+ |
1 |
| + |
1 |
x |
+ |
+ |
1 |
| + |
0 |
x |
x |
+ |
0 |
| + |
1 |
+ |
+ |
+ |
1 |
| + |
1 |
+ |
x |
+ |
1 |
| + |
0 |
x |
+ |
x |
1 |
| + |
0 |
+ |
+ |
+ |
0 |
| + |
1 |
x |
+ |
+ |
1 |
| + |
0 |
x |
x |
x |
1 |
| + |
0 |
+ |
+ |
x |
0 |
| x |
1 |
+ |
+ |
x |
1 |
| + |
1 |
+ |
x |
x |
1 |
| x |
0 |
+ |
x |
+ |
0 |
Table A4.
Alice, Eve, and Bob’s Basis and Bit Values for 100 bits.
Table A4.
Alice, Eve, and Bob’s Basis and Bit Values for 100 bits.
| Alice Basis |
Alice Bit |
Eve Incident Basis |
Eve Basis Transmitted |
Bob Basis |
Bob Bit |
| |
| 0 |
+ |
1 |
x |
0 |
x |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 0 |
+ |
0 |
x |
0 |
x |
| 0 |
+ |
1 |
x |
0 |
+ |
| 0 |
+ |
1 |
x |
1 |
x |
| 1 |
x |
0 |
+ |
1 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 1 |
x |
1 |
x |
1 |
+ |
| 0 |
+ |
0 |
x |
0 |
x |
| 0 |
+ |
0 |
+ |
0 |
x |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 0 |
+ |
1 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
x |
| 0 |
+ |
0 |
x |
0 |
x |
| 0 |
+ |
1 |
x |
0 |
+ |
| 1 |
x |
0 |
+ |
1 |
+ |
| 1 |
x |
1 |
x |
1 |
x |
| 1 |
x |
0 |
+ |
0 |
+ |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
+ |
| 1 |
x |
0 |
+ |
1 |
+ |
| 0 |
+ |
0 |
+ |
1 |
x |
| 0 |
+ |
0 |
x |
1 |
x |
| 1 |
x |
1 |
+ |
1 |
x |
| 0 |
+ |
0 |
+ |
1 |
x |
| 0 |
+ |
1 |
x |
0 |
+ |
| 1 |
x |
0 |
+ |
1 |
x |
| 1 |
x |
0 |
+ |
1 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 0 |
+ |
0 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
+ |
| 1 |
x |
1 |
+ |
1 |
+ |
| 1 |
x |
0 |
+ |
0 |
+ |
| 1 |
x |
0 |
+ |
1 |
+ |
| 0 |
+ |
0 |
x |
0 |
+ |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 0 |
+ |
0 |
x |
0 |
+ |
| 0 |
+ |
0 |
+ |
1 |
x |
| 0 |
+ |
0 |
x |
0 |
x |
| 1 |
x |
0 |
+ |
1 |
+ |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 0 |
+ |
0 |
x |
0 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 0 |
+ |
1 |
x |
0 |
x |
| 0 |
+ |
0 |
+ |
0 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 0 |
+ |
0 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
+ |
| 0 |
+ |
0 |
+ |
0 |
x |
| 0 |
+ |
1 |
x |
0 |
+ |
| 1 |
x |
0 |
+ |
0 |
+ |
| 0 |
+ |
1 |
x |
0 |
+ |
| 0 |
+ |
0 |
x |
1 |
x |
| 1 |
x |
0 |
+ |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
x |
| 0 |
+ |
0 |
+ |
1 |
x |
| 0 |
+ |
0 |
x |
1 |
x |
| 0 |
+ |
1 |
x |
0 |
x |
| 1 |
x |
1 |
+ |
0 |
+ |
| 0 |
+ |
0 |
+ |
1 |
x |
| 1 |
x |
1 |
+ |
1 |
x |
| 1 |
x |
0 |
+ |
0 |
+ |
| 0 |
+ |
0 |
x |
1 |
x |
| 1 |
x |
1 |
x |
0 |
+ |
| 0 |
+ |
0 |
x |
0 |
+ |
| 0 |
+ |
0 |
x |
0 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 1 |
x |
1 |
x |
0 |
+ |
| 0 |
+ |
1 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
x |
| 1 |
x |
0 |
+ |
0 |
+ |
| 1 |
x |
0 |
+ |
1 |
+ |
| 0 |
+ |
1 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
+ |
| 0 |
+ |
0 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
x |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 1 |
x |
1 |
+ |
1 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 1 |
x |
0 |
+ |
1 |
+ |
| 1 |
x |
1 |
+ |
1 |
x |
| 0 |
+ |
1 |
x |
0 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 1 |
x |
0 |
+ |
1 |
x |
| 1 |
x |
1 |
+ |
0 |
+ |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 0 |
+ |
0 |
x |
1 |
x |
| 0 |
+ |
1 |
x |
0 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
| 0 |
+ |
0 |
x |
0 |
+ |
| 0 |
+ |
0 |
+ |
0 |
+ |
| 1 |
x |
1 |
x |
0 |
+ |
| 1 |
x |
1 |
x |
1 |
x |
| 0 |
+ |
0 |
+ |
0 |
x |
| 0 |
+ |
1 |
x |
0 |
x |
| 0 |
+ |
0 |
+ |
1 |
x |
| 1 |
x |
0 |
+ |
1 |
x |
| 1 |
x |
1 |
x |
1 |
+ |
References
- Williamson, S.M.; Prybutok, V. Balancing privacy and progress: a review of privacy challenges, systemic oversight, and patient perceptions in AI-driven healthcare. Applied Sciences 2024, 14, 675. [Google Scholar] [CrossRef]
- Xu, F.; others. Quantum cryptography with realistic devices. arXiv preprint 2019, arXiv:1903.09051. [Google Scholar]
- Liao, S.K.; others. Long-distance free-space quantum key distribution in daylight towards inter-satellite communication. Nature Photonics 2017, 11, 509–513. [Google Scholar] [CrossRef]
- Rozenman, G.G.; others. The quantum internet: A synergy of quantum information technologies and 6G networks. IET Quantum Communication 2023, 4, 147–166. [Google Scholar] [CrossRef]
- Bennett, C.H. Quantum cryptography using any two nonorthogonal states. Physical Review Letters 1992, 68, 3121. [Google Scholar] [CrossRef]
- Charles, H. Bennett, G.B.; Ekert, A.K. Quantum cryptography. Scientific American 1992, 267, 50–57. [Google Scholar]
- Waldvogel, C.P.; Massey, J.L. The probability distribution of the Diffie-Hellman key. International Workshop on the Theory and Application of Cryptographic Techniques. Springer Berlin Heidelberg, 1992.
- Ladd, T.D.; others. Quantum computers. Nature 2010, 464, 45–53. [Google Scholar] [CrossRef] [PubMed]
- Hassija, V.; others. Forthcoming applications of quantum computing: peeking into the future. IET Quantum Communication 2020, 1, 35–41. [Google Scholar] [CrossRef]
- Blinder, S.M. Introduction to quantum mechanics; Academic Press, 2020.
- Begimbayeva, Y.; Zhaxalykov, T. Research of quantum key distribution protocols: BB84, B92, E91. Scientific Journal of Astana IT University 2022. [Google Scholar] [CrossRef]
- Bloom, Y.; others. Quantum cryptography—A simplified undergraduate experiment and simulation. Physics 2022, 4, 104–123. [Google Scholar] [CrossRef]
- Peisakhov, G.G.R.A.; Zadok, N. Dispersion of organic exciton polaritons—A novel undergraduate experiment. European Journal of Physics 2022, 43, 035301. [Google Scholar]
- Griffiths, B.J. Cryptography in undergraduate education: perceptions of postgraduate students. Cryptologia 2021, 45, 553–562. [Google Scholar] [CrossRef]
- et al., A.A. Building a quantum engineering undergraduate program. IEEE Transactions on Education 2022, 65, 220–242. [CrossRef]
- et al., A.S.D. Development of an undergraduate quantum engineering degree. IEEE Transactions on Quantum Engineering 2022, 3, 1–10.
- et al., G.U. Undergraduate research and education in quantum machine learning. 2022 IEEE Frontiers in Education Conference (FIE). IEEE, 2022.
- Lethen, T. Bit commitment as an introduction to quantum cryptography. European Journal of Physics 2022, 43, 055402. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell System Technical Journal 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Bellovin, S.M. Frank Miller: Inventor of the one time pad. Cryptologia 2011, 35, 203–222. [Google Scholar] [CrossRef]
- Bender, A.; Beller, S. Mangarevan invention of binary steps for easier calculation. Proceedings of the National Academy of Sciences of the United States of America (Proc. Natl. Acad. Sci. USA) 2014, 111, 1322–1327. [Google Scholar] [CrossRef]
- Chrisomalis, S. Numerical Notation: A Comparative History; Cambridge University Press: Cambridge, UK, 2010. [Google Scholar]
- Mackenzie, C.E. Coded Character Sets, History and Development; Addison-Wesley Pub.: Boston, MA, USA, 1979. [Google Scholar]
- Barker, E.; Kelsey, J. Recommendation for Random Number Generation Using Deterministic Random Bit Generators. Technical report, National Institute of Standards and Technology (NIST), Gaithersburg, MD, USA, 2015.
- Bird, J.J.; Ekert, A.; Faria, D.R. On the effects of pseudorandom and quantum-random number generators in soft computing. Soft Computing 2020, 24, 9243–9256. [Google Scholar] [CrossRef]
- Born, M.; Wolf, E. Principles of Optics, 7th ed.; Cambridge University Press: Cambridge, UK, 2002. [Google Scholar]
- Fowles, G.R. Introduction to Modern Optics, 2nd ed.; Dover Publications: Mineola, NY, USA, 1989. [Google Scholar]
- Shankar, R. Principles of Quantum Mechanics; Springer Science & Business Media, 2012.
- Griffiths, D.J.; Schroeter, D.F. Introduction to Quantum Mechanics; Cambridge University Press: Cambridge, UK, 2018. [Google Scholar]
- Muller-Kirsten, H.J.W. Introduction to Quantum Mechanics: Schrodinger Equation and Path Integral; World Scientific Co. Ltd.: NJ, USA, 2012. [Google Scholar]
- ThorLabs. Laser Modules: 635 nm, 2022. Accessed on 10 January 2022.
- Sara P Gandelman, Alona Maslennikov and Georgi Gary Rozenman. Hands-On 578 Quantum Cryptography: Undergraduate Experimentation with the B92 Protocol. 2024. 579 URL: https://github.com/Sara-Gandelman/Hands-On-Quantum-Cryptography- 580 Undergraduate-Experimentation-with-the-B92-Protocol.
- Gu, J.; et al. . Differential phase shift quantum secret sharing using a twin field. Optics Express 2021, 29, 9165–9173. [Google Scholar] [CrossRef] [PubMed]
- Akihiro Mizutani, Y.T.; Tamaki, K. Finite-key security analysis of differential-phase-shift quantum key distribution. Physical Review Research 2023, 5, 023132. [Google Scholar] [CrossRef]
- Zhang, Y.; et al. . Long-distance continuous-variable quantum key distribution over 202.81 km of fiber. Physical Review Letters 2020, 125, 010502. [Google Scholar] [CrossRef]
- Chen, T.Y.; et al. . Implementation of a 46-node quantum metropolitan area network. npj Quantum Information 2021, 7, 134. [Google Scholar] [CrossRef]
- Kržič, A.; others. Towards metropolitan free-space quantum networks. npj Quantum Information 2023, 9, 95. [Google Scholar] [CrossRef]
- Sharikov, P. Contemporary cybersecurity challenges. In The implications of emerging technologies in the Euro-Atlantic Space: Views from the Younger Generation Leaders Network; Springer International Publishing, 2023; pp. 143–157.
- et al., R.L. Towards the industrialisation of quantum key distribution in communication networks: A short survey. IET Quantum Communication 2022, 3, 151–163. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).