Submitted:
29 January 2023
Posted:
30 January 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
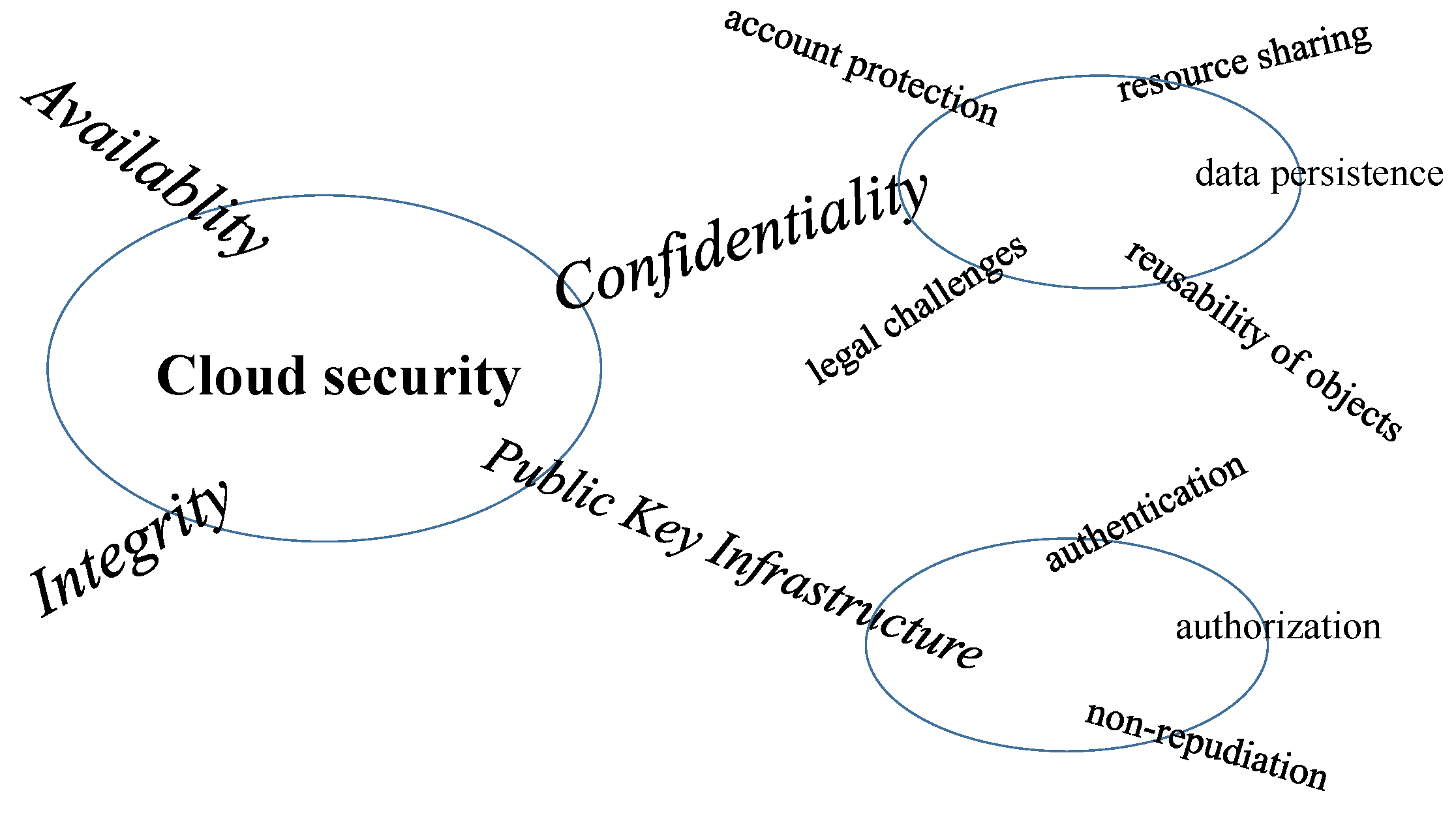
2. Approach
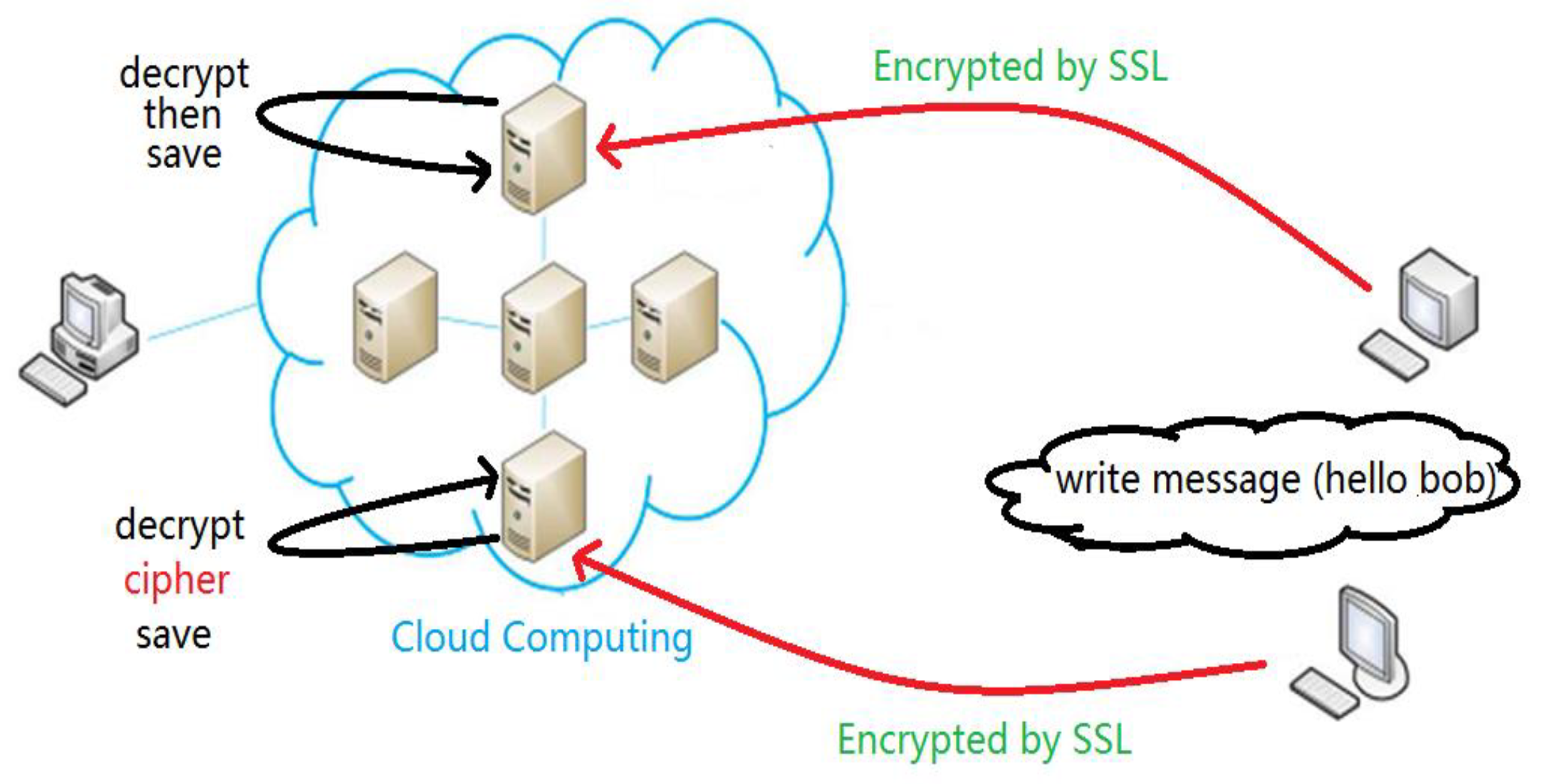
3. Encountered Obstacles
- The kind of NoSQL DB types (key-value, document-oriented, column-oriented, graph-oriented).
- The choice of which one of these types we will be working on.
- NoSQL DB is designed to provide real-time performance while managing a large amount of data poses a challenge for encryption operations.
- NoSQL DB couldn’t assure ACID properties (atomicity, consistency, isolation, and durability).
- Few open sources NoSQL DB available.
4. Model

References
- Darwazeh, N.S.; Al-Qassas, R.S.; AlDosari, F.; others. A secure cloud computing model based on data classification. Procedia Computer Science 2015, 52, 1153–1158. [Google Scholar] [CrossRef]
- Oppermann, A.; Toro, F.G.; Thiel, F.; Seifert, J.P. Secure cloud computing: Reference architecture for measuring instrument under legal control. Security and Privacy 2018, 1, e18. [Google Scholar] [CrossRef]
- Youssef, A.E.; Alageel, M. A framework for secure cloud computing. International Journal of Computer Science Issues (IJCSI) 2012, 9, 487. [Google Scholar]
- Stergiou, C.; Psannis, K.E.; Kim, B.G.; Gupta, B. Secure integration of IoT and cloud computing. Future Generation Computer Systems 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Kara, M.; Laouid, A.; AlShaikh, M.; Bounceur, A.; Hammoudeh, M. Secure key exchange against man-in-the-middle attack: Modified diffie-hellman protocol. Jurnal Ilmiah Teknik Elektro Komputer dan Informatika 2021, 7, 380–387. [Google Scholar] [CrossRef]
- KARA, M.; LAOUID, A.; BOUNCEUR, A.; HAMMOUDEH, M.; ALSHAIKH, M. Perfect Confidentiality through Unconditionally Secure Homomorphic Encryption Using OTP With a Single Pre-Shared Key. Journal of Information Science and Engineering 2023, 39, 183–195. [Google Scholar] [CrossRef]
- Kara, M.; Laouid, A.; Bounceur, A.; Hammoudeh, M.; Alshaikh, M.; Kebache, R. Semi-Decentralized Model for Drone Collaboration on Secure Measurement of Positions. The 5th International Conference on Future Networks & Distributed Systems, 2021, pp. 64–69.
- Kahla, M.E.; Beggas, M.; Laouid, A.; Kara, M.; AlShaikh, M. Asymmetric Image Encryption Based on Twin Message Fusion. 2021 International Conference on Artificial Intelligence for Cyber Security Systems and Privacy (AI-CSP). IEEE, 2021, pp. 1–5.
- Habib, A.; Laouid, A.; Kara, M. Secure Consensus Clock Synchronization in Wireless Sensor Networks. 2021 International Conference on Artificial Intelligence for Cyber Security Systems and Privacy (AI-CSP). IEEE, 2021, pp. 1–6.
- Chait, K.; Laouid, A.; Laouamer, L.; Kara, M. A Multi-Key Based Lightweight Additive Homomorphic Encryption Scheme. 2021 International Conference on Artificial Intelligence for Cyber Security Systems and Privacy (AI-CSP). IEEE, 2021, pp. 1–6.
- Kara, M.; Laouid, A.; Yagoub, M.A.; Euler, R.; Medileh, S.; Hammoudeh, M.; Eleyan, A.; Bounceur, A. A fully homomorphic encryption based on magic number fragmentation and El-Gamal encryption: Smart healthcare use case. Expert Systems 2022, 39, e12767. [Google Scholar] [CrossRef]
- Kara, M.; Laouid, A.; Euler, R.; Yagoub, M.A.; Bounceur, A.; Hammoudeh, M.; Medileh, S. A homomorphic digit fragmentation encryption scheme based on the polynomial reconstruction problem. The 4th International Conference on Future Networks and Distributed Systems (ICFNDS), 2020, pp. 1–6.
- Kara, M.; Laouid, A.; Hammoudeh, M.; Alshaikh, M.; Bounceur, A. Proof of Chance: A Lightweight Consensus Algorithm for the Internet of Things. IEEE Transactions on Industrial Informatics 2022, 18, 8336–8345. [Google Scholar] [CrossRef]
- Kara, M.; Laouid, A.; Bounceur, A.; Lalem, F.; AlShaikh, M.; Kebache, R.; Sayah, Z. A Novel Delegated Proof of Work Consensus Protocol. 2021 International Conference on Artificial Intelligence for Cyber Security Systems and Privacy (AI-CSP). IEEE, 2021, pp. 1–7.
- Kara, M.; Laouid, A.; AlShaikh, M.; Hammoudeh, M.; Bounceur, A.; Euler, R.; Amamra, A.; Laouid, B. A compute and wait in pow (cw-pow) consensus algorithm for preserving energy consumption. Applied Sciences 2021, 11, 6750. [Google Scholar] [CrossRef]
- Kara, M.; Laouid, A.; Bounceur, A.; Hammoudeh, M. Secure Clock Synchronization Protocol in Wireless Sensor Networks 2023.
- Kara, M. A Lightweight Clock Synchronization Technique for Wireless Sensor Networks: A Randomization-Based Secure Approach 2023.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




