Introduction
Federal level public policy suggests that policymakers have been, and continue to be, unsatisfied with the incidence of transfer of technologies derived from research and development conducted at universities to the private sector (university technology transfer) for use that benefits the public interest (see e.g., Daily Comp. Pres. Doc., 2011-October-28; Office of Management and Budget [OMB], 2002; OMB, 2018). Much of this research and development is federally funded.
This study aimed to address a specific gap within the literature on university technology transfer. Research on the topic has revealed quite a bit about supply-side factors that seem to correlate with various output and outcome metrics. However, there is still much about university technology transfer that is unknown. The perspective of demand-side actors and the roles of many endogenous factors have remained relatively unexamined. This study provides insight into how private sector organizations decide whether to pursue obtaining and assimilating university-created technologies and the role that technology maturity level may play in such decisions.
For purposes of the study, technology was defined as culturally influenced information that social actors use to pursue the objectives of their motivations, and which is embodied in such a manner to enable, hinder, or otherwise control its access and use.
1 University technology transfer was defined as technology (as defined above) created by university researchers through systematic methods and practices of inquiry that is knowingly and willingly conveyed to other parties who intend to apply the technology in a setting in which it has not previously been applied to achieve an end (see Footnote 2). Technology maturity level was defined as the degree to which one can use a given technology to achieve an end that is acceptable without the need for additional development.
The primary research question that the study examined was how can the incidence of university technology transfer to the private sector in the United States be increased? Of specific concern was the influence of technology maturity level which is an understudied factor with important public policy implications. If technology maturity level is not a significant factor in successful university technology transfer, policymakers and technology transfer practitioners can eliminate it from the discussion and turn their attention to other potential explanatory factors. However, if technology maturity level is in fact a significant explanatory factor, then it is prudent for the U.S. government to consider this insight in forming public policy and for practitioners to modify their practices appropriately.
Literature Review
The review of the related literature explores the discourse about relevant theories, constructs, concepts, and research findings pertinent to the examination of how technology maturity level may influence the incidence of university technology transfer to the private sector in the United States. It is organized thematically because the discourse related to technology transfer in general, and specifically university technology transfer, draws upon various fields and is therefore interdisciplinary.
The literature review begins with an examination of the typical approaches to studying university technology transfer and the gaps in the understanding of the determinants of success. From this examination, technology maturity level surfaces as a potentially important but understudied explanatory factor. Consequently, the literature review proceeds to explore the discourse related to understanding technology maturity level as a possible explanatory factor in the incidence of university technology transfer and associated outcomes.
Because technology transfer is fundamentally a business decision on the demand side of the process (Barriers to Domestic Technology Transfer, 1992, p. 145), the literature review then delves into the perspectives of organization studies, economic theory, and decision theory. At least four possible broad explanations for the role that technology maturity level may play in influencing whether a private sector organization pursues, obtains, and assimilates a given technology can be found in these literatures. The first relates technology maturity level with the motivations and goals of organizations. The second and third possible explanations lean towards the postmodern perspective of organization studies in that they take into account the human element of organization. The fourth posits the interplay between organization structure and technology maturity level.
Approaches to Investigating University Technology Transfer
The discourses on university-industry relationships and absorptive capacity are the most relevant streams of technology transfer literature. However, most research on university-industry relationships has been from the perspective of universities and research institutions (i.e., a supply-side perspective) and not private sector organizations that obtain and assimilate the technology – what one might appropriately term a demand-side perspective (Bengoa, Maseda, Iturralde, & Aparicio, 2020). Research on absorptive capacity, which is commonly defined in the literature as “a firm’s ability to recognize, assimilate, and apply external knowledge and learning processes” (Bengoa, Maseda, Iturralde, & Aparicio, p. 25), generally falls within the discipline of organization studies. Most studies in this stream of research have focused on understanding the factors that influence the absorptive capacity of firms (i.e., for-profit commercial enterprises), when and how absorptive capacity can be a source of competitive advantage for firms, and the relationship between absorptive capacity and firm performance (Bengoa, Maseda, Iturralde, & Aparicio). It appears that the absorptive capacity literature does not address why firms choose to obtain and assimilate some technologies and not others.
The major theories used to examine university technology transfer include transaction cost economic theory, the resource-based view (RBV), and the knowledge-based view (KBV) (Anatan, 2015). Other frameworks, such as institutional theory (Anatan) and the contingent effectiveness model (Bozeman, 2000) have also been proposed as frameworks to guide investigations of the phenomenon of university technology transfer. Although these frameworks and theories have been successfully applied to study university technology transfer, their usefulness in understanding the role that technology maturity level may play in the occurrence of university technology transfer is limited. Their underlying assumptions and premises are either problematic or do not adequately capture the nature of university technology transfer. These include assumptions regarding profit maximization, internal resources as the source of sustained competitive advantage, and survival-driven organization behavior. University technology transfer can and does occur in the absence of a profit motive (Association of University Technology Managers, 2021). From the perspective of private sector organizations, university-created technologies are external resources, not internal ones. Moreover, the degree to which an organization’s existence is in jeopardy waxes and wanes over time. Therefore, not all organizational behavior is driven by survival.
Another problem in applying these various theories and frameworks to understand university technology transfer is that they seem to reify the construct of organization. This imposes limitations on their application and usefulness in examining the topic. Additionally, studies of technology transfer in general, and university technology transfer specifically, seem to have mostly focused on factors exogenous to the technology and technology transfer process. Moreover, they tend to examine the topic from the perspective of supply-side actors.
Finally, quantitative studies of university technology transfer generally use some form of multiple regression analysis. This too has its shortcomings. Implicit in this approach is the idea that there is one best path to produce the outcome of interest. Moreover, it assumes that the effects of individual variables are non-interactive and can be isolated and combined in an additive manner (Ragin, 2000). However, causal complexity is indicative of social phenomena (Ragin), and university technology transfer is very much a social phenomenon. Therefore, university technology transfer is likely subject to conjunctural causation, equifinality, and causal asymmetry of outcomes.
Determinants of Success in University Technology Transfer
Several determinants of university technology transfer success can be found in the literature. These include researcher characteristics, features of university technology transfer offices, and institutional factors (see e.g., Arshadi & George, 2008; Baek, Hwang, & Park, 2018; Dolmans, Shane, Janowski, Reymen, & Romme, 2016; Heisey & Adelman, 2011; Kundu, Bhar, & Pendurangan, 2015; Markma, Gioaniodis, & Phan, 2009; Wu, Welch, & Huang, 2015; York & Ahn, 2012). However, most of the determinants identified are supply-side factors. In reviewing the literature on technology-related factors that may drive the incidence of university technology transfer, technology maturity level does surface as a consideration that might provide significant insight into the policy problem of how to improve the incidence of university technology transfer. However, an examination of the literature suggests that scholars have barely scratched the surface when it comes to understanding the potential influence of technology maturity level on the occurrence of university technology transfer.
In a survey of 300 industry licensing executives at business units that license external technologies, nearly 33 percent of the responses from respondents indicated the primary reason their organization did not license university technologies was that the development stage of university research tends to be too early (Thursby & Thursby, 2001). Interpreting this result is not straightforward. Moreover, the study provides no insight into how mature is mature enough for private sector organizations. However, the finding can be taken as prima facie evidence that technology maturity level is a relevant determinant of the occurrence of university technology transfer.
In another survey of more than 500 private sector organizations that sought to examine factors that hinder collaboration between universities in the United Kingdom (U.K.) and the private sector, roughly one-third of the respondents indicated that university research in the U.K. has an extreme orientation towards pure science (Bruneel, D’Este, & Salter, 2010). While the results of this study are likely to be somewhat generalizable to universities in the United States, they do not provide an answer as to how mature university technologies must be to interest private sector organizations. Moreover, it is not clear whether the respondents in the study considered such orientation towards pure science to be a barrier to collaboration; this seems to be an unverified assumption that the authors make.
A study of differences in the maturity level of technologies pursued by established firms compared to startup firms found that the odds ratio of invention licensing by startup firms relative to invention licensing by established firms was lower for later stage inventions and higher for earlier stage inventions while invention licensing by established firms was positively correlated with later invention development stage (Munteanu, 2012). If one takes the results of the study at face value, they only posit an explanation for the distribution of university technologies transferred to the private sector between established firms and startup firms. They do not explain the overall incidence of university technology transfer and the role that technology maturity level may play.
Insights into the Role of Technology Maturity Level
The literature specific to university technology transfer provides limited information about the role of technology maturity level. It is, therefore, necessary to turn to the broader literature to understand how technology maturity level might influence the incidence of university technology transfer in the United States. The literature on the “valley of death”, organization studies, economic theory, and decision theory provide useful insights to help explain the role of technology maturity level in the occurrence of university technology transfer.
The Valley of Death in University Technology Transfer
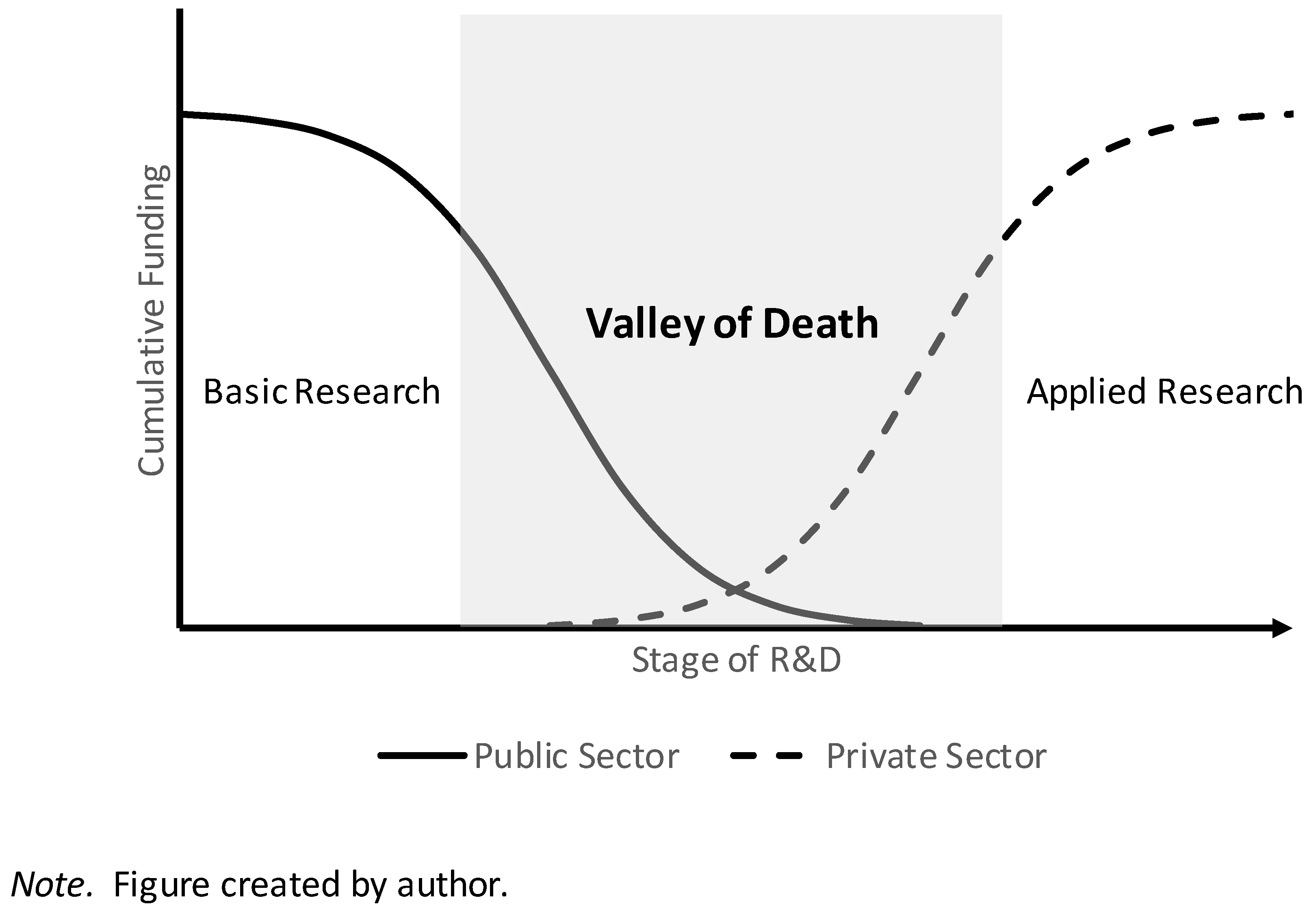
Discussions among technology transfer practitioners about the so-called “valley of death” seem to imply that any given technology must progress to a certain minimum maturity level before it can be successfully transitioned to the private sector. The term valley of death is used in the contexts of research and development funding, new products development (NPD), and entrepreneurship with a slightly different connotation in each. Regarding research and development funding, it generally refers to the gap between funding provided by the federal government for basic research that produces scientific discoveries and funding provided by the private sector for applied research and development activity directed toward the exploitation of such discoveries in specific applications (see e.g., Ferguson, 2014; Guldbrandsen, 2009; Hudson & Khazragui, 2013). Many technology transfer practitioners point to this gap as a primary impediment to successfully transferring technologies to the private sector.
In the context of research and development funding, the valley of death is shorthand for a phenomenon in which promising technologies are often abandoned because of an inability to attract sufficient funding to support the R&D activities necessary to further their development (
Figure 1). Studies on the topic seem to allude to an association between technology maturity level and successful technology transfer (see, e.g., Markham, 2002; Markham, Ward, Aiman-Smith, & Kingon, 2010; Tirpak, 2017; Wessner, 2005).
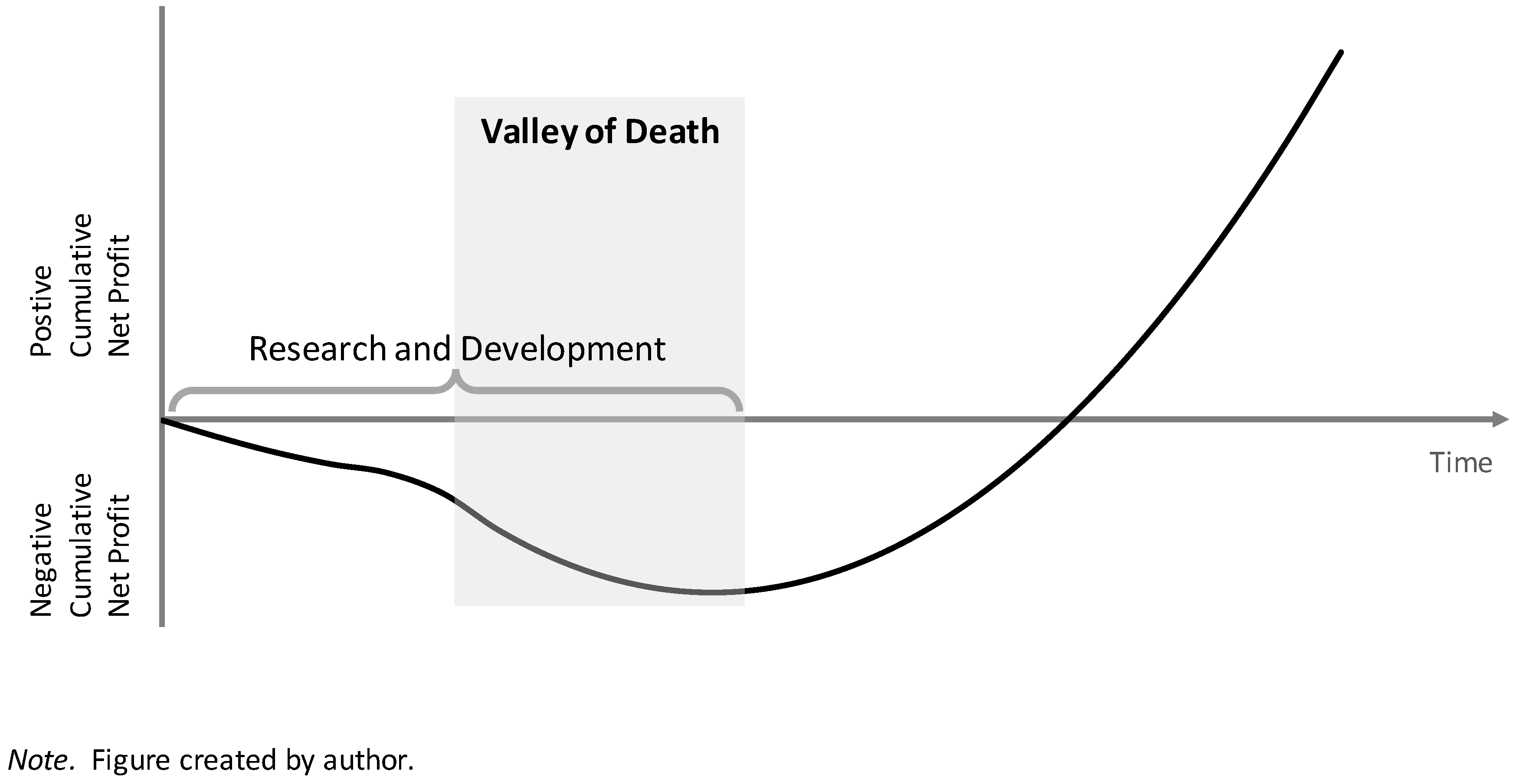
In the context of NPD and entrepreneurship, the valley of death refers to the trend of increasing negative cumulative net profits over time until a product achieves market success at which point negative cumulative net profit begins to decrease and eventually cumulative net profit turns positive (
Figure 2). New products and new business ventures either fail or are abandoned if they cannot attract sufficient funding to support activities until reaching the point where cumulative net profit turns positive. This connotation of the valley of death is relevant given that a significant amount of university technology transfer is pursued as new product development or new business venture initiatives (Song, Park, & Park, 2017).
The existence of the valley of death phenomenon is additional prima facie evidence in support of the hypothesis that technology maturity level is a significant factor in the incidence of university technology transfer. However, it is not definitive proof. There may be other scenarios that could produce the phenomenon. For example, it could simply be a matter of labor supply. Some scholars have posited that product champions, driven by some motivation, shepherd projects across the valley of death (Markham 2002; Markham, Ward, Aiman-Smith, & Kingon, 2010). Technology maturity level may not be a significant factor for these champions. The phenomenon we call the valley of death could be nothing more than an imbalance between the supply of champions and the demand for champions much like shortages seen in other professions and industries, such as the dearth of engineers or programmers. Another scenario is that some factor other than technology maturity level, such as technology category or field of application, is the primary determinant between those technologies that successfully cross the valley of death and those that do not. Additionally, considerations concerning industry trends and economies of scale play a significant role in venture capital investment practices (Zider, 1998). These could just as easily explain any unwillingness of venture capital markets to fund the commercialization of technologies that happen to have a low maturity level.
Economic Profit and Uncertainty
Examining the influence of technology maturity level on how private sector organizations respond to university technology transfer opportunities requires considering the system by which members of a society allocate resources among themselves (i.e., the economic system). Information is something that members of a society use either directly or indirectly to make goods (as the term is used in economics) to satisfy their needs (i.e., the process of production). In this sense, information is a resource. If one conceptualizes technology in terms of information, then technology is also a resource. Consequently, technology transfer is an exercise in acquiring and allocating resources.
In modern society, money is the primary means of obtaining the necessary resources to satisfy needs and achieve ends. This reliance on money necessitates the need for organizations to either generate economic profit (in the case of for-profit organizations) or at least achieve resource equilibrium in their operations (in the case of non-profit organizations which must secure at least as many resources as they consume to pursue their ends).
The concept of economic profit has implications for the influence of technology maturity level on the incidence of university technology transfer. Economic profit requires uncertainty (Knight, 1921). In an economic context, uncertainty exists when the probability distribution of a future event is either unknown or unknowable (Knight, 1921; Rose, 2001). Risk, on the other hand, exists when the probability distribution of a future event is measurable and known (Knight; Rose). This differs from the use of the term risk in everyday language.
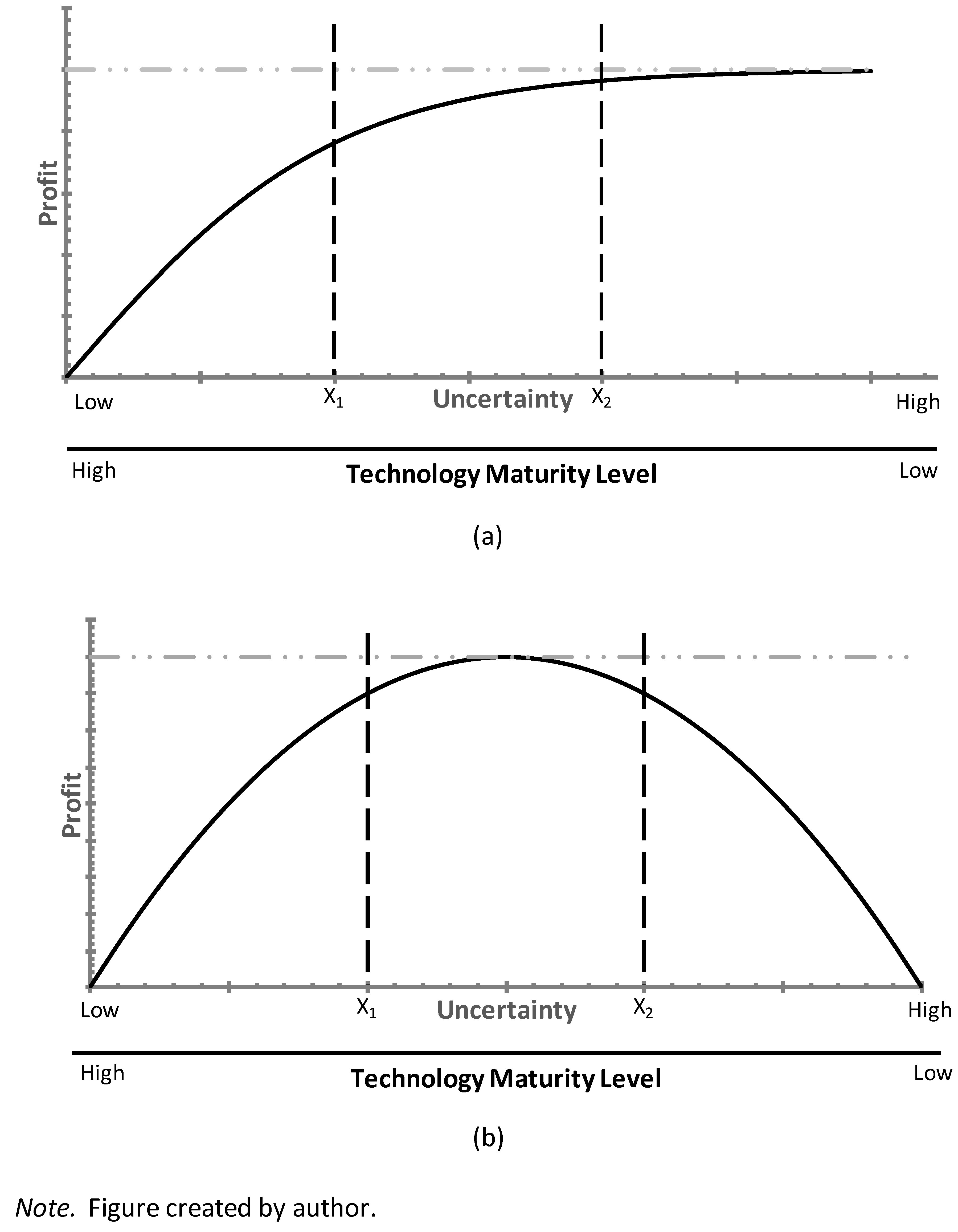
If economic profit requires uncertainty as Knight (1921) argued, one can surmise that there is generally a positive relationship between profit and uncertainty. However, such a positive relationship is unlikely to hold indefinitely. This suggests that the relationship between profit and uncertainty at the very least resembles a hyperbolic tangent function that approaches an asymptote of maximum possible profit (
Figure 3a). This implies that there is a level of uncertainty beyond which no significant additional profits can be achieved (point X2 on
Figure 3a). Organization members might use technology maturity level as a proxy for uncertainty by associating a high technology maturity level with low uncertainty and a low technology maturity level with high uncertainty. If this is the case, then there would be a technology maturity level below which organization members would presume that there would be no significant additional economic profits to obtain. Thus, there would be no economic incentive to pursue obtaining and assimilating technologies with unnecessarily low maturity levels. One might expect the incidence of university technologies transferred to the private sector to be low if the typical maturity level of such technologies is less than this inflection point.
There is an interesting aside to this analysis. The scenario described suggests that it is possible for the maturity level of a given technology to be too high to result in transfer to the private sector (point X1 on Figure 8a). This too makes sense if high technology maturity level is indicative of low uncertainty and uncertainty is necessary for economic profit. Uncertainty reduced to zero would eliminate profits. This possibly helps explain why an organization would pursue anything less than a fully matured technology in the context of the valley of death phenomenon.
The actual existence of such a correlation between technology maturity level and economic uncertainty is not necessary to influence the behavior of demand-side university technology transfer decision-makers. It is only necessary that the demand-side decision-makers believe such a correlation exists. According to the Thomas Theorem, what an individual subjectively perceives as real is real in its consequences (Thomas & Thomas, 1928, pp. 571-572). If demand-side technology transfer decision-makers believe such a correlation exists, they will act as if it does exist.
Cyert & March (1963) observed from empirical research that organizations avoid uncertainty. This seems rather ironic at first blush given the argument by Knight (1921) that uncertainty is necessary for economic profit. However, it does make sense that organizations would actively avoid excessive levels of uncertainty if the relationship between economic profit and uncertainty resembled a downward opening parabola akin to an inverted U-shape (
Figure 3b) the apex of which would represent the maximum possible profit. Such a relationship would suggest that there is a range of uncertainty for which significant economic profits can be earned. On either side of this range, profits rapidly decline toward zero. If members of private sector organizations use technology maturity level as a proxy for uncertainty, it would make sense that they would avoid technologies with maturities below some level that is associated with excessively high uncertainty (point X2 on
Figure 3b). A low incidence of university technologies would be transferred to the private sector if the maturity level of most technologies created by universities happens to fall below this point of inflection. As with the previous analysis, this scenario also suggests that it is possible for the maturity level of a given technology to be too high to result in transfer to the private sector.
The tendency towards uncertainty avoidance of organizations manifests itself in various ways. It is reasonable to assume that organizations faced with uncertain choices regarding technology that they can obtain to help achieve their desired ends will seek additional data and information to try to reduce excessive uncertainty surrounding the likelihood of being able to successfully assimilate the technology. These include meta-information about the technology itself (i.e., information about information). According to bounded rationality, organization members in such situations should and will use heuristics to make their decisions (March, 1997). Members of private sector organizations may use technology maturity level as a kind of meta-information or as an element in one or more heuristics in evaluating technology transfer opportunities. In such cases, members of private sector organizations may use technology maturity level as a proxy for uncertainty as they try to avoid excessive uncertainty.
Decision Premises and Technology Maturity Level
The quest to understand the role that technology maturity level plays in determining whether organizations (as collectivities of individual persons) will pursue, obtain, and assimilate technologies created at U.S. universities in many respects is an exercise in understanding a specific type of organization behavior, namely organizational decision making. Although the theory of the firm treats organizational decision-making as purely an economically rationale process (Cyert & March, 1963), descriptive theory demonstrates that this is not the case in reality. The rational agent model of decision-making has been thoroughly rebutted. Moreover, organizational decision-making is both psychological and sociological (Simon, 1997). A host of non-economic phenomena are involved. Simulations and laboratory-based experimental investigations have demonstrated a socio-political dimension to decision-making in organizations (Hodgkinson & Starbuck, 2008). Decision-making is a function of not only the quantity, accuracy, objectiveness, and timeliness of data and information but also social processes such as sensemaking and sensegiving (Balogun, Pye, & Hodgkinson, 2008). Sociological phenomena can even modify and distort the judgments of decision-makers in group contexts (Asch, 1951; Asch, 1956).
The essential activities of an organization are physical tasks (i.e., actions) performed by its members that are deemed necessary to achieve the ends of the organization (Simon, 1997). Before a physical action is performed by a member of the organization there must be a decision to perform the action (Simon). Every action involves a decision about whether to act and what action among multiple alternatives to take if action is in fact warranted. Therefore, the operative activities of an organization can be conceptualized as a series of decision-action couplets (Simon). Thus, focusing on the decision-making process is a viable approach to understanding the behavior of individuals and groups in an organizational context, such as university technology transfer.
Humans make decisions in an organizational context based on beliefs about the nature of the physical and social world and their perceptions of the way things "ought" to be (Simon, 1997). Every decision made by organization members is composed of two distinct types of belief (Simon). The first type of belief is a factual proposition that one can empirically determine to be true or false in an absolute or objective sense (Simon). The second type of belief is a value proposition that one cannot empirically determine to be true or false in an absolute or objective sense (Simon). The factual and value propositions one uses to arrive at and justify decisions to act are called decision premises (Simon).
In the framework outlined by Simon (1997), one could argue that factual premises are rooted in data and information while value premises are rooted in emotions and preferences. Value premises are essentially imperative declarations that select one possible future state as desired and thereby exclude all others (Simon). As Simon explained, value premises are beliefs about the way things "ought" to be. They are ethical or normative in nature (Simon). Many decisions of organization members in roles at the higher levels of an organization hierarchy function as nothing more than value decision premises meant to guide the decisions and actions of members in roles at lower levels in the organization hierarchy (Simon).
Some of the nomenclature that Simon (1997) used is a bit confusing. In the ordinary use of the term, “factual” tends to mean that a statement or assertion is true in an absolute or objective sense. However, in the framework described by Simon, factual propositions are not necessarily true although they can empirically be determined to be true or false in an absolute or objective sense. Consequently, a factual decision premise can be either true or false, accurate or inaccurate. As used by Simon, a factual decision premise is more accurately described as an assertion or proposition (in the epistemological use of the terms) about the nature of cause-and-effect relationships among events and phenomena of the physical and social world in which the individual employing the assertion or proposition has a propositional attitude of belief that the assertion or proposition corresponds with reality. It, therefore, seems more appropriate and less confusing to use the term causation decision premises, which is the term that shall be used going forward.
Organization decision-making is a “decision-fabricating process” (Simon, 1997, p. 24). In some ways, this is analogous to formulating a natural language argument as in a line of reasoning to support a position, claim, or conclusion. Natural language arguments, as described by Fisher (2004), are created by combining independent reasons, compound reasons, and necessary intermediate conclusions to provide the justification for the main conclusion. The veracity of only one of several independent reasons is enough to justify a conclusion while the veracity of all compound reasons must be established to justify a resulting conclusion (Fischer). Likewise, organization members combine value decision premises and causation decision premises (including antecedent decisions serving as decision premises for subsequent decisions) in a Boolean fashion to guide the decision-making process and produce a given organization decision aimed at resulting in a given action and outcome.
The ultimate decisions of organizations regarding university technology transfer opportunities are likely complex decisions requiring several antecedent decisions. Moreover, it is likely that at least some of the decision premises are compound premises meaning that affirmation of all the premises is required to result in the action. If technology maturity level is a factor in the decisions of private sector organizations about whether to pursue, obtain, and assimilate a given university-created technology, it probably manifests as one or more decision premises in either the ultimate decision or an antecedent decision. Moreover, an insufficient technology maturity level in and of itself will be sufficient to result in a decision not to pursue a university technology transfer opportunity if it is part of a set of compound decision premises at any decision point in the decision chain.
From a pragmatic standpoint, it is unlikely that members in the upper hierarchy of an organization can provide a comprehensive set of decision premises to guide the actions of members below them in the organization hierarchy in all situations. As such, any given organization member probably must supplement organization decision premises with additional decision premises that originate from other sources. These could be decision premises derived from the judgment and personal experiences of the individual members. They could also be decision premises introduced from outside the organization. Scholars have postulated that in addition to organizational cultures, communities of occupations create occupational cultures that extend across organizations, influence the activities of organizations, and contribute to the similarities among organizations (Rojot, 2008). This suggests that there exists an occupational culture for technology transfer practitioners which may have produced one or more decision premises about technology maturity level that causes private sector organizations across the spectrum to seek technologies at maturity levels that are higher than the typical maturity levels of technologies available from U.S. universities.
The Perspective of Descriptive Decision Theory
Organization decision-making is both sociological and psychological (Simon, 1997). The psychology of individual decision-making is still necessary to understand organization decision-making as it relates to the potential influence of technology maturity level on the incidence of university technology transfer. Descriptive research has demonstrated that actual decision-making very often deviates from what is considered optimal according to economically based normative decision theory (Hodgkinson & Starbuck, 2008). Simon (1957) introduced the concept of bounded rationality to explain how individuals cope with such constraints in decision-making. Because of bounded rationality, organization members often use heuristics to facilitate their decision-making (March, 1997; Tversky & Kahneman, 1974).
Research suggests that humans engage in two distinct modes of thinking when forming judgments and making decisions (Kahneman, 2011). Evolutionary pressures have resulted in an intuitive mode of thinking that is the foundation of human judgment and decision-making. This intuitive mode of thinking (what Kahneman called System 1 thinking) happens automatically without effort, is always active, operates through human emotions and association, and is optimized for cognitive ease (Kahneman). The second mode of thinking (what Kahneman referred to as System 2 thinking) is intentional and analytical (Kahneman). It requires mental effort and must be triggered, which often occurs by the failure of the intuitive thinking mode to readily produce a solution to a problem requiring judgment and decision making (Kahneman). It is the intuitive thinking mode which serves as the foundation for judgment and decision-making, causes humans to rely on heuristics, and makes human judgment and decision-making susceptible to biases. These phenomena do not simply disappear if decision-making occurs in an organizational context, which is the context for most decision-making regarding university technology transfer opportunities. As such, these phenomena likely affect the decisions of demand-side university technology transfer actors as they relate to technology maturity level.
Human decision-making is largely driven by emotion which is the core mechanism of the intuitive mode of thinking. Even important decisions that demand intentional statistical thinking are influenced, if not governed, by the intuitive mode of thinking (Kahneman, 2011). Evolution has tuned the human intuitive thinking mode to survival. The prospects for survival increase with aversion to novelty (Kahneman). This likely has profound implications for university technology transfer, and technology transfer in general, for which novelty is a defining characteristic.
Moreover, the human intuitive thinking mode defaults to confirmation and is biased towards belief and uncritical acceptance of suggestions (Kahneman, 2011). Even the intentional mode of human thinking defaults to a positive test strategy when evaluating explanatory propositions and searching for confirming evidence of judgments formed through the intuitive thinking mode (Kahneman).
There are several possible scenarios in which the heuristics and biases that result from this dual mode of thinking might be at play when it comes to the potential influence of technology maturity level on the incidence of university technology transfer. The intuitive mode of thinking relies on association. Categorization is a form of association. Humans think of categories in terms of stereotypical representations of a normal member of a category (Kahneman, 2011). This is particularly relevant in between-subjects decision conditions (Kahneman), which is likely the scenario for most decisions regarding university technology transfer opportunities. This suggests that demand-side technology transfer practitioners rely on stereotypes of different categories of technology maturity level. Each stereotype is likely associated with certain characteristics. It is this association of characteristics that might cause a demand-side technology transfer practitioner to decide against pursuing a technology that he or she has categorized as a low maturity technology.
Another possible scenario involves the phenomenon of substitution that the intuitive thinking mode appears to employ. Kahneman (2011) proposed that when an individual encounters difficulty producing a satisfactory answer to a complex question, the intuitive thinking mode will substitute a related easier question often without the individual realizing it. Because technology maturity level is such an abstract, complex concept that is often difficult to characterize and quantify for a given technology, demand-side technology transfer practitioners might be susceptible to the substitution phenomenon. While they might intend to answer the question “What is the maturity level of this technology?” they may in fact be substituting another question such as “How well do I understand this technology?” or “What is a plausible scenario for successfully assimilating this technology?” In such a scenario, demand-side technology transfer practitioners may associate low maturity levels with technologies they do not understand well or for which they cannot easily generate plausible scenarios for successful assimilation.
Prospect theory demonstrates that when making decisions individuals evaluate their alternatives in terms of expected utility relative to a reference point rather than on an absolute basis (Kahneman & Tversky, 1979; Kahneman & Tversky, 2013; Tversky & Kahneman, 1992). This relative evaluation determines whether individuals judge an alternative to be a gain or a loss. How alternatives are framed (i.e., losses versus gains) influences whether an individual tends towards risk-aversion or risk-seeking in decision making (Kahneman, 2011; Tversky & Kahneman, 1986), as the terms are used in everyday language.
Prospect theory asserts that there is a fourfold pattern to preferences. In one pattern, when individuals perceive that an option has a high probability of loss, their inclination is to act to avoid the loss and thus their decision-making tends toward risk-seeking (Kahneman, 2011). This effect (called the certainty effect) causes individuals in such situations to reject favorable alternatives (Kahneman). It is possible that the lower that demand-side technology transfer decision-makers perceive the maturity level of a technology to be, the higher they perceive the probability of failing to assimilate the technology to the point that they perceive failure to assimilate the technology as a near certainty. Failure to assimilate a technology is tantamount to a significant financial loss for the organization as well as possible personal and social losses (e.g., standing within the organization) for the individual. Applying prospect theory to this scenario, one would predict a low incidence of university technology transfer where demand-side technology transfer practitioners perceive the maturity level of technologies to be low. To avoid the loss associated with the perceived near certainty of failing to assimilate a technology, demand-side technology transfer decision-makers might seek the risk associated with searching for or waiting for the opportunity to pursue, a higher maturity level technology, which likely has a low chance of occurring (i.e., a risky proposition). Moreover, if demand-side technology transfer practitioners perceive the probability of failure as relatively high for all but the most mature technologies, then one would expect the incidence of university technology transfer to be anchored towards a low rate absent any kind of government intervention.
Organizational Structure and Technology Maturity Level
Several studies have attempted to relate the characteristics of other various elements of organizational structure to technology transfer outcomes (see e.g., Arshadi & George, 2008; Markman, Gianiodis, & Phan, 2009; Wu, Welch, & Huang, 2015; York & Ahn, 2012). However, these studies typically examine the issue from the perspective of the university (i.e., supply-side perspective). Bahcall (2019) provides insight on the demand-side of the equation into the possible interplay between organization structure as it relates to the number of organization members and technology maturity level.
The number of organization members is in part a function of how activities are divided and the amount of organization capacity desired. Bahcall studied what he called “loonshots”
2 which, based on his description, one can conceive as ambitious, expensive, and risky or uncertain endeavors that have the potential to confer significant benefit to an organization, but which are counterintuitive to conventional wisdom. Bahcall explored the question of why an organization may favor loonshots at one point in its history but disfavor loonshots at another. He argued that organizational structure rather than organizational culture explains this transition from propensity to support so-called loonshots to a tendency to quash loonshots in favor of what he referred to as franchise projects – endeavors with lower costs and lower risk or uncertainty that build upon previous successes.
Bahcall (2019) theorized that the number of employees (), below which a given organization will tend to nurture loonshots and above which the organization will favor franchise projects because politics will set in, has a direct relation with equity fraction (), management span (), and organizational fitness () and an inverse relation with salary growth rate up the organization hierarchy (). The overall relationship is described by the formula , which implies that any organization of any given size can influence its propensity to favor loonshots or franchise projects by manipulating its structure along these parameters. Based on several assumptions, Bahcall argues that the threshold at which an organization will typically transition from nurturing loonshots to quashing them in favor of franchise projects is about 150 company employees (i.e., organization members).
In the context of university technology transfer, it may be that low maturity level technologies are akin to loonshots and high maturity level technologies are analogous to franchise projects. However, it is also quite possible that most, if not all, efforts to transfer newly created technologies to the private sector are essentially loonshots regardless of technology maturity level.
One interpretation of the theory offered by Bahcall (2019) suggests that organizations (e.g., for-profit commercial enterprises) with 150 or fewer members would favor low maturity level technologies while organizations with greater than 150 members would tend to pursue high maturity level technologies. This is consistent with the idea that startup firms favor early-stage technologies while established firms favor later-stage technologies (see Munteanu, 2012), assuming the number of organization members is correlated with the age of the organization and its lifecycle stage. But this does not explain the incidence of university-created technologies that are transferred to the private sector for use that benefits the public interest. If it is the case that low maturity level technologies are akin to loonshots and high maturity level technologies are akin to franchise projects, one would simply expect the proportion of low maturity level and high maturity level technologies transferred to the private sector to mirror the distribution of firms with 150 or fewer employees versus those with greater than 150 employees. The theory also does not explain why an organization would choose one loonshot over another or one franchise project over another, all other things being equal, which is the challenge if it is the case that most, if not all, efforts to transfer newly created technologies to the private sector are essentially loonshots regardless of maturity level.
Data and Methods
Having established a theoretical and conceptual framework for the study, the discussion now turns to the data and methods used to conduct the study. It begins by re-stating the research question and specifying the theoretical propositions examined. It then details what data were collected, how the data were collected, and how the data were analyzed.
Research Question and Theoretical Propositions
The study employed a comparative case study approach from the perspective of private sector organizations (i.e., a demand-side perspective). Case study research is appropriate when the main research question is a “how” or “why” question about a contemporary phenomenon and the researcher has little or no control over behavior or events (Yin, 2018). At the core, the research question that the study sought to address was:
Why is the incidence of university technology transfer to the private sector in the United States lower than desired?
An alternative way of framing the research question for public policy purposes is as follows:
How can the incidence of university technology transfer to the private sector in the United States be increased?
To gain insight into these questions, the study focused on the demand-side of university technology transfer by exploring the following question:
Why do private sector organizations in the United States pursue, obtain, and assimilate any given university-created technology?
More specifically, the study investigated the following question:
How does technology maturity level influence whether a private sector organization in the United States will obtain and assimilate any given university-created technology?
It is proposed that the decision of members of private sector organizations to pursue, obtain, and assimilate a given externally created technology is largely driven by the perceived maturity level of the technology in conjunction with other conditions. The study posits that an acceptable technology maturity level is a necessary condition for private sector organizations to pursue, obtain, and assimilate a given externally created technology. The criteria for what members of private sector organizations consider to be an acceptable technology maturity level are established by economic factors, organizational dicta produced through sociological processes, as well as the judgments and cognitive biases of organization members. It is proposed that the minimum technology maturity level that tends to satisfy these criteria happens to be greater than the typical maturity level of technologies created at universities in the United States.
Given that case study research does not use data from random samples as with survey research or randomization as in experimental designs, it does not attempt hypothesis testing or statistical inference (Yin, 2018). Instead, case study research focuses on research questions and theoretical propositions (Yin). Therefore, the term theoretical proposition is used rather than the term hypothesis to emphasize that the study aimed to make logical inferences rather than statistical inferences.
The study examined several theoretical propositions that would give insight into answering the research questions above. The first theoretical proposition focused on the most idealistic situation regarding the maturity level of university technologies:
- Prop1:
A technology maturity level () that happens to be greater than the typical maturity level of technologies created at U.S. universities () is a necessary and sufficient condition alone for the occurrence of university technology transfer (UTT).
Examining plausible rival explanations is considered good methodological practice for case study research and helps to increase the robustness of the study findings (Yin, 2018). The study examined several plausible rival explanations concerning the possibility of there being one or more explanatory factors that are commingled with technology maturity level:
- Prop2:
> is a necessary but not sufficient condition for UTT.
- Prop3:
> is a sufficient but not necessary condition for UTT.
- Prop4:
> is a necessary part of at least one configuration of causal conditions that is sufficient for UTT.
The literature on technology transfer posits that early-stage firms prefer less mature technologies and later-stage firms prefer technologies with higher maturity levels because they each have a comparative advantage in assimilating the respective technologies (see e.g., Munteanu, 2012). As such, another theoretical proposition focused on the possibility that the age of the private sector organization () moderates the influence of technology maturity level as a causal condition for the occurrence of university technology transfer:
- Prop5:
> is necessary for UTT when > 5 years.
An additional plausible rival explanation is concerned with the structure of private sector organizations as it relates to the number of organization members. The literature suggests that the structure of an organization in terms of the number of members influences whether the organization favors loonshots or franchise projects (see e.g., Bahcall, 2019). If the transfer of technologies created at U.S. universities to the private sector is essentially a loonshot endeavor, the number of members (e.g., employees) of the private sector organization () might act to moderate the influence of technology maturity level as a causal condition for the occurrence of university technology transfer as expressed in the following theoretical proposition:
- Prop6:
> is necessary for UTT when ≥ 151 people.
A multiple case study research design was used to examine these research questions and theoretical propositions. Case study research is a mode of inquiry on par with experimental research, survey research, historical research, and statistical research (Yin, 2018). As with experimental research designs, case study research is generalizable to theoretical propositions but not populations or universes (Yin). However, the goal of a case study research design is to make analytical generalizations or logical inferences rather than statistical generalizations or statistical inferences (Yin).
Conceptualization and Operationalization of Key Constructs
For the purposes of the study, technology was operationalized as information that is embodied in such a way that a contractual agreement that can be enforced through the coercive powers of the state (e.g., a license) can be employed as the mechanism for controlling the private sector organization’s access to and use of the information. The study operationalized technology transfer as an announcement or other evidence that a private sector organization either executed or pursued a contractual agreement (as described above) with a university for technology that the university either owned or controlled. In practical terms, this is a narrow conceptualization and operationalization because most such announcements are likely to be for agreements based on financial transactions with for-profit commercial enterprises. However, it does not preclude transfers of technology that are not driven by profit or do not involve financial transactions.
The primary factor of interest was technology maturity level. The study used an adaptation of the NASA technology readiness level (TRL) scale to operationalize technology maturity level. Specifically, the study used the maturity level of the technology relative to the typical maturity level of technologies created at U.S. universities.
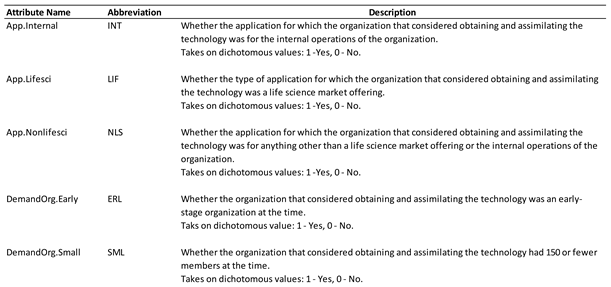
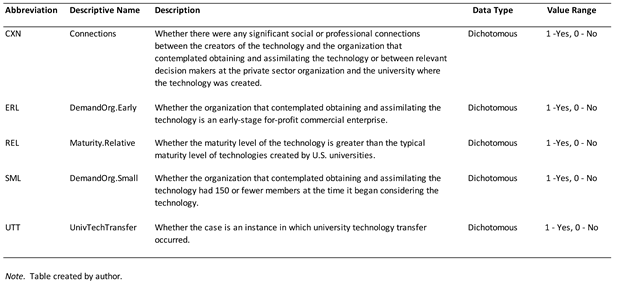
In addition to technology maturity level, case data were collected about other factors that the literature suggested may be explanatory (
Table 1). Although secondary factors collected for multiple case studies are not the primary focus, they may be important for the interpretation of any relationship that may be found between the dependent factor and primary independent factor of interest (Kaarbo & Beasley, 1999). Moreover, causal complexity is a basic premise of the methodology used. Multiple conditions and attributes may have a causal role in the occurrence of university technology transfer.
Data Collection
The data for the study consisted of two parts. The first was data used to determine the typical maturity level of technologies created at U.S. universities (
). A sample of technologies was analyzed to establish
(
Table 2). This consisted of taking a random sample of 30 patent applications for inventions assigned to U.S. universities that were filed with the U.S. Patent and Trademark Office (USPTO) and published in 2019. Patent applications is a broader category than allowed patents. Thus, this approach avoided an overly narrow operationalization of technology. To eliminate idiosyncratic variation, only one person rated the maturity level of the technologies in the sample using an adaptation of the NASA TRL scale specified in the case attribute coding guidelines (
Table 3). These data were then used to determine the lowest maturity level that was at least as high as the level for 80 percent of the technologies in the sample (
). This 80th percentile ranking was used as the benchmark for
. Thus
≤
was the calibration for
in the analysis.
The second part of the data set concerned instances of potential university technology transfer in which a private sector organization considered obtaining and assimilating a university-controlled technology. Prior to identifying cases and collecting case data, it was necessary to construct case coding guidelines (see
Table 3). The case coding guidelines directed the collection of evidence to code the conditions and attributes for each case used in the study (see Kaarbo & Beasley, 1999). The case coding guidelines specified in advance what evidence was necessary to make a judgment about the value of a case attribute and how that value was to be coded (see Kaarbo & Beasley).
The goal was to collect data on at least 20 cases of potential university technology transfer. Two primary criteria were used to screen potential cases. To be included in the study the cases needed to have occurred during or around calendar year 2019 and the technology must have been created at a U.S. university.
Various methods were used to locate potential cases for the study. Trade journals, newspapers, and newswires were searched to locate articles and news releases with the terms “licenses” and “university” in the headline. The ABI/INFORM Collection database was used to conduct the search. The search was limited to annual reports, articles, cover stories, industry reports, market reports, market research, and news reports from January 1, 2019 through December 31, 2019 found in magazines, newspapers, trade journals, and wire feeds. These search criteria produce a list of 11 potential cases for consideration. However, not all these cases satisfied the criteria for inclusion in the study.
The cases identified through a search of the ABI/INFORM Collection database were augmented with cases identified from a search of the Technology Transfer eNews archive of entries, which is not indexed or abstracted in any research database. Technology Transfer eNews (
https://techtransfercentral.com/category/tech-transfer-enews/) is a free blog targeted at technology transfer and intellectual property professionals. It is produced and published by 2MarketInformation, Inc. Although slower than using a robust search function, simply browsing entries allowed the quick identification of potential cases for inclusion in the study.
The initial search produced fewer cases than desired for the study. Consequently, the date parameters for the search were expanded. Additional cases were identified with a general Google search using the terms “university licenses”, “licenses from”, or “COMPANY licenses from university” where “COMPANY” was the name of a specific company of interest that was identified through other means.
A preliminary analysis and review of cases revealed that there were no cases in which the private sector organization had more than 150 employees or members. Additional cases with this attribute were identified by searching the Electronic Data Gathering, Analysis, and Retrieval (EDGAR) database of the U.S. Securities and Exchange Commission. The keywords “license” and “university” were used as search terms. Candidates were screened based on the number of employees listed on their profile on Yahool! Finance, in their Form 10-K annual reports, or their Form 5500 Series
3 return.
For multiple case study research designs, the literature recommends that cases be selected with variation in the dependent (i.e., outcome) factor (see Kaarbo & Beasley, 1999). This presented a challenge. Demand-side private sector organizations do not make announcements about or publicize technologies that they decide not to pursue. Using other sources as the case sampling frame, such as U.S. Patent and Trademark Office databases or the National Science Foundation awards database, was not practical because the low incidence of technology transfer would require a very large number of potential cases to be reviewed to ensure that enough instances of university technology transfer were among the cases selected. Moreover, determining whether university technology transfer (as operationalized in the study) did or did not occur for any given case would have been a more laborious and uncertain process.
To identify cases of the non-occurrence of university technology transfer, the technology transfer records of Saint Louis University were reviewed. Additionally, technology transfer practitioners from other U.S. universities were asked to provide up to three (3) cases of the non-occurrence of university technology transfer that satisfied the criteria to be included in the study.
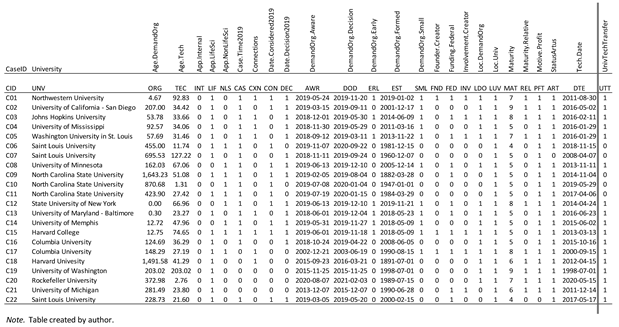
Case data were documented in case notes and used to determine each case’s membership within several condition sets believed to be causal for university technology transfer. As evidence was accumulated for each case from various sources, the factors were coded in accordance with the case coding guidelines. These data were summarized in a case data matrix (
Table 4). Only one individual coded the cases to eliminate the potential for idiosyncratic variation.
The collection of evidence and coding of cases was an iterative process. For each case identified and selected, additional content analysis of patent applications, allowed patents, technology summaries published by the universities, and other publicly available resources were conducted as necessary to collect the data required to code the maturity level of the technology in each case as well as the other conditions and attributes used in the analysis.
Data Analysis
The data set that was collected for the study did not contain a random sample of a population or universe of potential university technology transfer cases. Rather it contained a theoretically guided arbitrary sample of instances of potential university technology transfer occurring during a specified period of time for which an announcement was made by one or more parties involved or for which access to technology transfer records at universities could be obtained. Consequently, statistical inference methods were not appropriate for analyzing the data. Instead, logical inference methods were the appropriate tools for analyzing them.
The study used qualitative comparative analysis (QCA) to analyze the case data. QCA is rooted in set theory. “The notion of sets and their relations is almost unavoidably invoked when forming concepts or when verbally formulating (causal) relations between social phenomena” (Schneider & Wagemann, 2012, p. 2-3). Set-theoretic methods facilitate an understanding of the physical and social world based on the configuration of conditions (Schneider & Wagemann). Sufficiency and necessity are the basis of the interpretation of set relations in set-theoretic methods (Schneider & Wagemann). Set-theoretic methods are also useful for capturing nuances of social science phenomena such as equifinality, conjunctural causation, and asymmetry of causation (Schneider & Wagemann).
In using QCA to analyze the data, the study employed a different philosophical approach to examining social phenomena than that which underpins other comparative methods, traditional statistical inference methods, and common qualitative research approaches. QCA ascribes to the notion that focusing on isolated effects of variables under ceteris paribus conditions is unrealistic, phenomena are caused by various combinations of multiple conditions, and phenomena are subject to causal complexity which consists of conjunctural causality, equifinality, and asymmetry of causation for the occurrence and non-occurrence of outcomes (Schneider & Wageman, 2012; Thomann, 2021).
Traditional methods of analysis are not particularly well-suited for analyzing phenomena subject to causal complexity. Traditional methods assume that there is one best path in the data for producing an outcome (Thomann, 2021). Techniques, such as multiple regression analysis (MRA), attempt to find the one path that best fits all the data. Evidence in the literature suggests that this may not be the case with university technology transfer. Many MRA-based studies of university technology transfer exhibit low R-squared (R2) and chi-squared () values and more non-significant variables than significant ones (see e.g., Dolmans, Shane, Jankowski, Reymen, & Romme, 2016; González-Pernía, Kuechle, & Peña-Legazkue, 2013; Markman, Gianiodis, & Phan, 2009; Munteanu, 2012; Wu, Welch, & Huang, 2015). This suggests that the phenomenon of university technology transfer is likely caused by a combination of conditions and that it is possible that there may be multiple combinations of conditions that lead to either the occurrence or non-occurrence of university technology transfer. Moreover, the conditions that tend to result in the non-occurrence of university technology transfer may not necessarily be the mirror opposite of the conditions that tend to produce the occurrence of university technology transfer. QCA is particularly well-suited to examine such phenomena.
The R programming language in the RStudio integrated development environment (RStudio, 2019) and R packages for QCA (Thiem, Baumgartner, Dusa, & Spoehel, 2018; Dusa, 2021) were used to perform the analysis. The study focused on four causal conditions and one outcome (see
Table 5). The primary causal condition of interest was the relative maturity level of the technology (REL) – that is, whether
>
.
To analyze the data, the study employed crisp-set QCA (csQCA), which is one of two main variants of QCA. To perform csQCA, data for each case was translated into a truth table. Cases were characterized as either members or non-members of the condition sets with membership scores of either 0 (complete non-member) or 1 (complete member).
The analysis of the case data for the study began by organizing the data into a matrix (see
Table 4 above). Each row of the table constitutes a single case. The columns of the table represented the various factors and attributes of each case. The factors used in the analysis were converted into dichotomous conditions and each case was assigned a membership score in those conditions. Each intersection of row (case) and column (condition) in the table indicates whether the condition is present or not for the case.
Next, the data matrix was converted into truth tables (
Table 6). Converting the data matrix into a truth table entailed identifying all logically possible configurations of conditions, assigning each case to one of the truth table rows, and defining the outcome value for each truth table row (i.e., condition set). The truth table represents the total number of logically possible combinations of conditions, which is equal to
where
is the number of possible values of each condition
(Cronqvist & Berg-Schlosser, 2009). When all conditions are limited to only two possible mutually exclusive values, the product equation can be reduced to 2k, where k is the number of conditions (Cronqvist & Berg-Schlosser; Schneider & Wagemann, 2012). Consequently, the truth table for the analysis comprised 16 logically possible combinations of the 4 conditions. Each case could belong to only one truth table row; however, each truth table row could contain multiple cases (see Schneider & Wegemann).
An evaluation of the outcome of the cases that fell into each truth table row was used to determine the outcome value for the truth table row. The raw consistency of each truth table row was used to determine the outcome value assigned to the row. A value of “1” in the outcome condition indicated either the occurrence or non-occurrence of university technology transfer, depending on which phenomenon was being analyzed. Impossible logical remainders were evaluated for removal from the analysis; however, none were found.
Converting the case data into a truth table produced the sets of conditions that are necessary or sufficient for the outcome of interest, which is either the occurrence or non-occurrence of university technology transfer. This can be represented in its complex form by the Boolean expression:
A condition set can be either necessary (or sufficient) for the outcome, not necessary (or not sufficient) for the outcome, or a logical remainder (i.e., condition sets for which there are no cases, indicated by a “?” in the truth tables).
The truth tables were reviewed to identify true logical contradictions (TLCs), which are logically possible combinations that fail the criteria to be considered sufficient for both the occurrence and non-occurrence of the outcome of interest simultaneously. No TLCs were identified. Once the truth tables were compiled, the causal influence of each truth table row (i.e., condition set) could be determined.
In accordance with QCA best practices, necessity was analyzed before sufficiency (see Schneider & Wagemann, 2012). Evaluating necessity before evaluating sufficiency avoids the problem of hidden necessary conditions and false necessary conditions (Schneider & Wagemann, 2012). Moreover, the occurrence and non-occurrence of university technology transfer were analyzed separately.
The analysis of necessity focused only on those cases in which the outcome of interest was present. Necessity was evaluated by determining which conditions and disjunctions (logical “OR” combinations) were present in all cases. Consistency, coverage, and relevance of necessity (RoN) were the parameters of fit (POFs) used to evaluate necessity. Several benchmarks for consistency of necessity were used to accommodate the imprecise nature of social phenomena and social science research methods. Disjunctions were further evaluated to determine whether they were conceptually substantive.
Once the evaluation of necessity was completed, sufficiency was analyzed. Sufficiency is a separate analytical consideration from necessity. One is not a byproduct of the other (Schneider & Wagemann, 2012). The process of analyzing sufficiency for the outcome of interest began by determining the conservative (i.e., most complex) solution, which assumes that logical remainders are not sufficient to produce the outcome of interest (i.e., either the occurrence or non-occurrence of university technology transfer). The logical remainders were removed from the analysis and the remaining condition sets were tested for sufficiency. The truth table was logically minimized to identify the sufficient paths for the outcome of interest.
In QCA, different solutions are produced depending on the assumptions made about logical remainders that are present simply because there were no cases for the condition sets in the data although such condition sets could theoretically exist – what Schneider & Wagemann (2012) called clustered remainders. The parsimonious solution is determined by assuming that all logical remainders are sufficient to produce the outcome of interest. The intermediate solution also assumes that logical remainders are sufficient to produce the outcome of interest, but it also removes implausible and incoherent counterfactuals. The analysis did not identify any implausible or incoherent counterfactuals that required removal. Additionally, the intermediate solution takes into consideration the directional expectations of each condition’s contribution to the occurrence or non-occurrence of the outcome of interest. For the analysis, the presence of the CXN condition was expected to contribute to the occurrence of university technology transfer. No other directional expectations were made regarding the other conditions.
The truth tables for evaluating the occurrence of university technology transfer were not applicable for evaluating the non-occurrence of the outcome. The process started anew for each situation. Additionally, the analysis of sufficiency required accounting for the assumptions that were made in the analysis of necessity. It also required the evaluation of contradictory simplifying assumptions (CSAs) which occur when the same logical remainders are assumed to result in both the occurrence and non-occurrence of the outcome of interest. However, the analysis did not reveal any contradictory simplifying assumptions.
Results and Findings
The presentation of the results is arranged according to the phases of the study and the theoretical propositions examined to answer the research questions. This section begins by presenting the results of the first phase of the study, which sought to characterize the typical maturity level of university technologies. It then describes the case-level descriptive statistics to demonstrate the extent to which the cases selected for the analysis in the second phase of the study represented the same population. Next, the results of the qualitative comparative analysis (QCA) are presented. Although the data were used to analyze both the occurrence and non-occurrence of university technology transfer in accordance with QCA methodology, the presentation emphasizes the results for the occurrence of university technology transfer, which was the focus of the study. The results of the analysis of necessary conditions, conjunctions, and disjunctions are discussed. Following that, the results of the analysis for sufficient conditions, conjunctions, and disjunctions are covered. Finally, the robustness of the findings is briefly addressed.
Typical Maturity Level of University Technologies
To characterize the typical maturity level of university technologies, the study used nonparametric statistical methods and measures of central tendency for the maturity level of the technologies described in the utility patent applications. Nonparametric statistical methods were used because the data sample violated assumptions for parametric statistical tests. Specifically, it is not known if the population of utility patent applications is normally distributed with regard to technology maturity level and there is no apparent theoretical basis to believe that it is. Moreover, the values of the primary variable of interest (i.e., technology maturity level) were measured on an ordinal scale rather than an interval or ratio measurement scale.
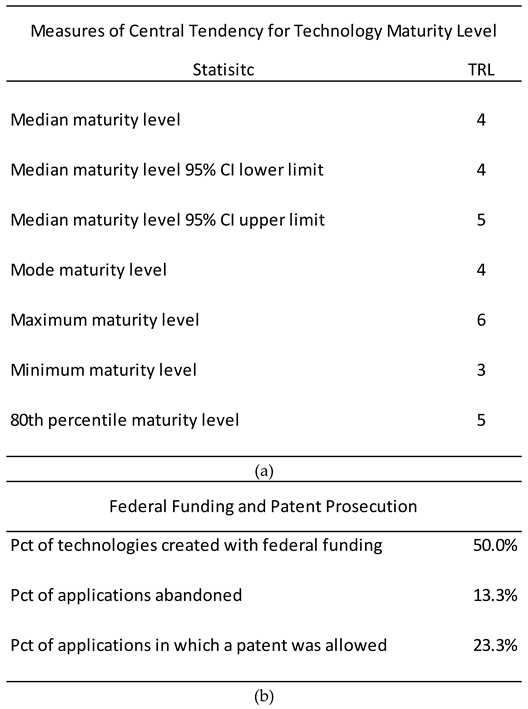
Descriptive statistics about the maturity level and federal funding were calculated to characterize the typical maturity level of university technologies (
Table 7). The median maturity level for the sample of technologies was determined to be a TRL-4 on the NASA technology readiness level (TRL) scale. The most frequent maturity level (i.e., mode) was also a TRL-4 on the NASA TRL scale. The minimum and maximum maturity levels were TRL-3 and TRL-6, respectively. The 80th percentile maturity level (i.e., the maturity level that was less than or equal to the maturity level of 80 percent of the technologies in the sample) was a TRL-5.
Case Level Descriptive Statistics
Data and information on 22 cases of potential university technology transfer (as operationalized in the study) were obtained and case attributes were coded in accordance with pre-defined coding guidelines. For all but three of the cases, the private sector organization began considering obtaining the technology in question between September 1, 2015 and November 30, 2019 (
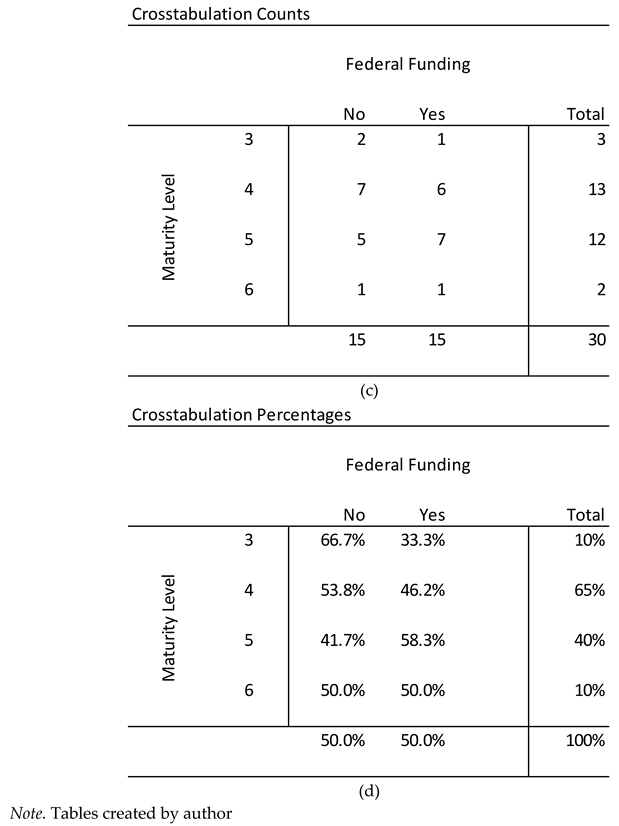
Figure 4a). In one case, the private sector organization began considering obtaining the technology in December of 2002. This case was removed from the analysis to minimize potential susceptibility to temporal-based confounding factors. Overall, the number of cases was about evenly split between those in which federal funding was used to create the technologies and those in which there was no federal funding used (
Figure 4b).
The case data were analyzed using qualitative comparative analysis. The model used for the analysis comprised four (4) conditions that were selected based on theoretical and empirical evidence found in the literature (see
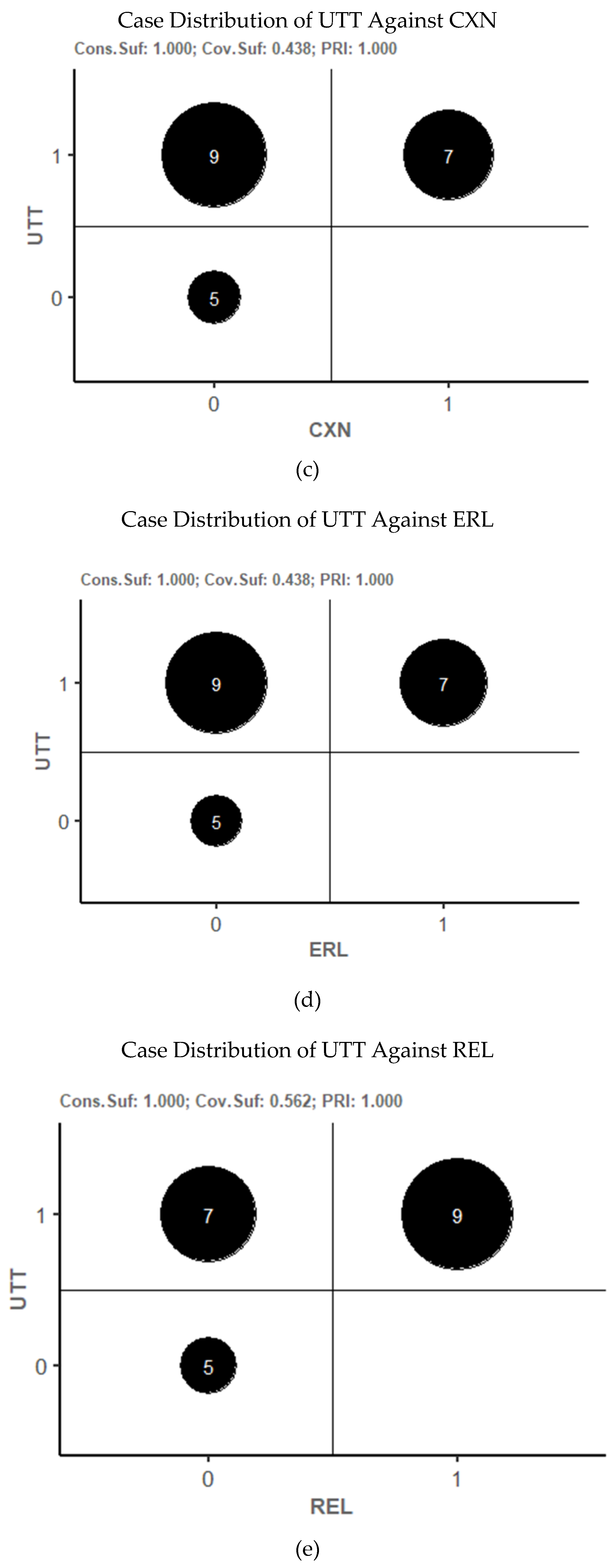
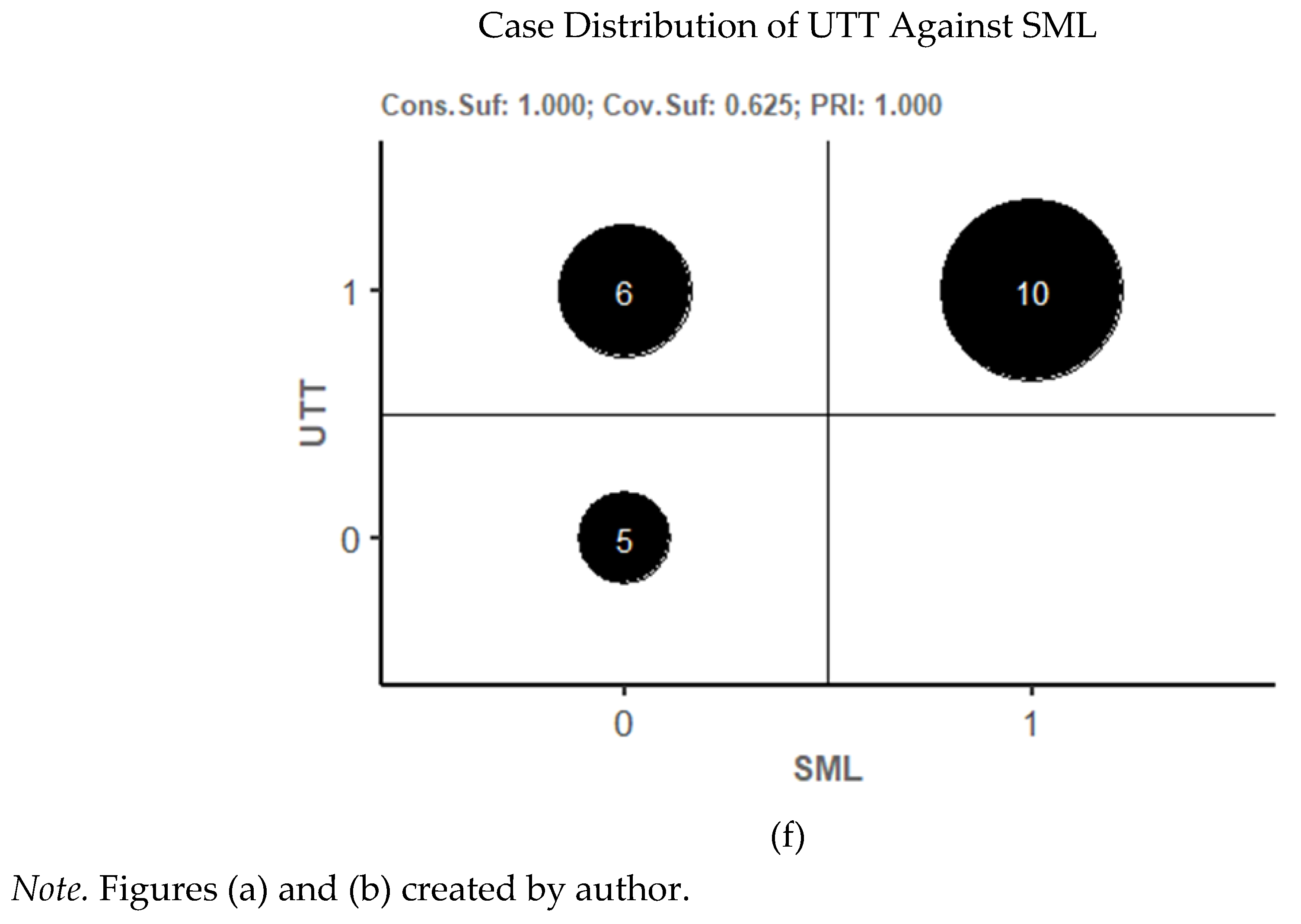
Table 5 above). For the 21 cases included in the analysis, bivariate bubble charts of UTT against CXN, ERL, REL, and SML show the distribution of cases relative to each condition (
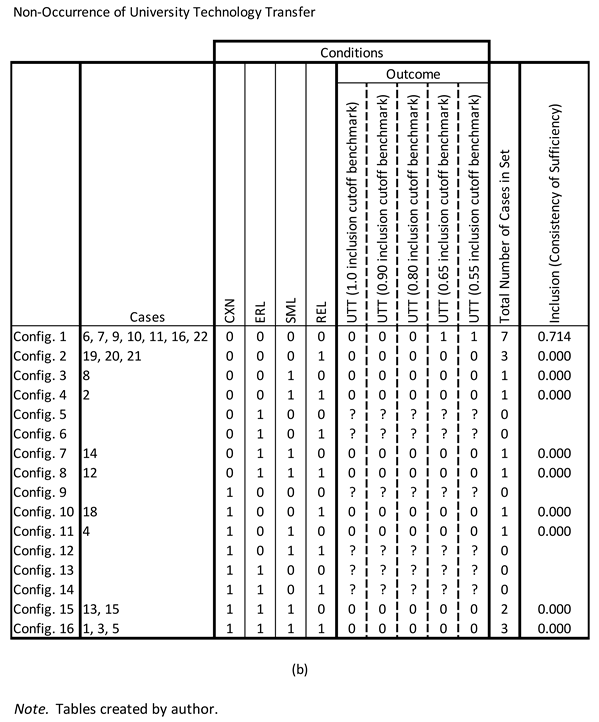
Figure 4c–f). There were cases that exhibited three of the four possible condition combinations for each pair. There were no cases represented in the study in which CXN, ERL, REL, or SML was present and UTT did not occur. This did not affect the analysis of necessity. Cases in which a condition is present, but the outcome does not occur are not directly relevant to the determination of the necessity (see e.g., Oana, Schneider, & Thomann, 2021, pp. 66-67). Moreover, the absence of such cases is consistent with the sufficiency (pp. 88-89).
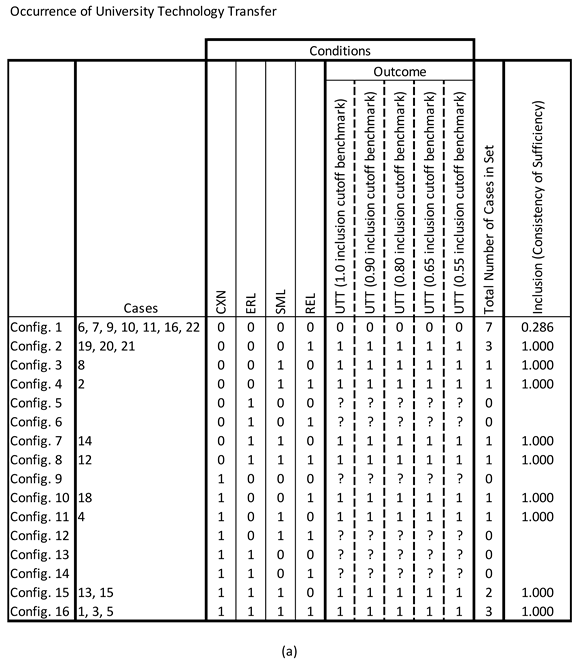
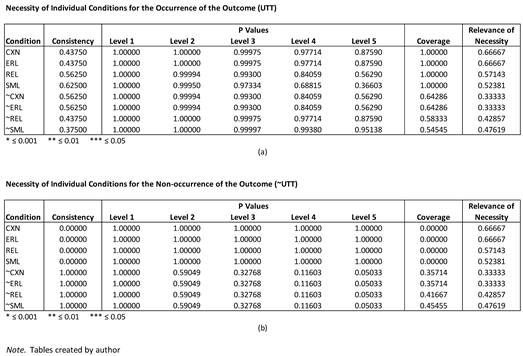
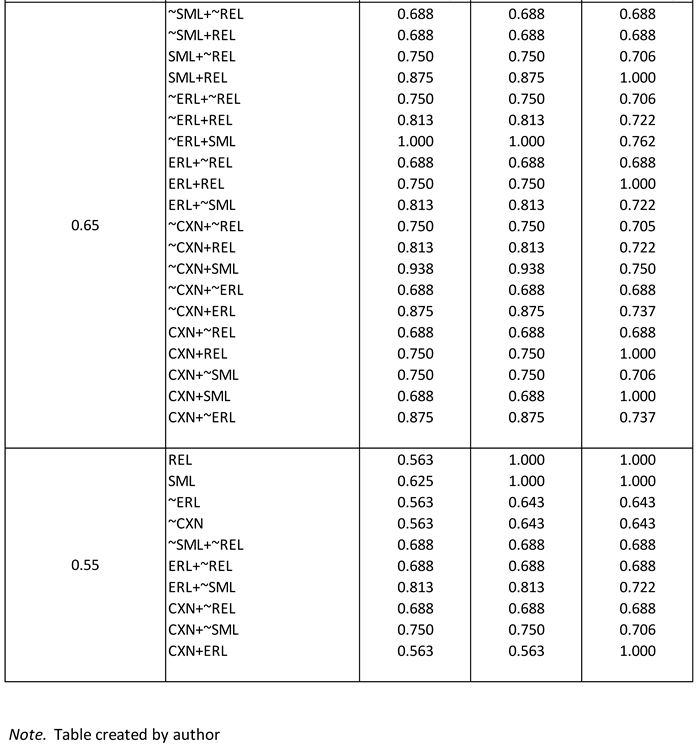
Necessity for the Occurrence of University Technology Transfer
The necessity of each individual condition (both their presence and absence) for the occurrence of UTT was examined using a minimum consistency (inclusion cutoff) that ranged from 1.0 to 0.55 (
Table 8). Consistency, coverage, and relevance of necessity (RoN) parameters of fit (POFs) for each individual condition were calculated (
Table 9a). If condition (or condition set) X is necessary for outcome Y, then it is a superset of outcome Y; however, if condition (or condition set) X is sufficient for outcome Y, then it is a subset of outcome Y (see Schneider & Wagemann, 2012).
The maximum consistency POF for any individual condition was 0.625. Four (4) conditions exhibited a consistency POF of at least 0.55. These included the presence of the conditions REL and SML and the absence of conditions CXN and ERL (i.e., ~CXN and ~ERL). The coverage POF for both REL and SML was 1.0 and the RoN POF for each was 0.571 and 0.524, respectively. The coverage and RoN POFs for both ~CXN and ~ERL were 0.643 and 0.333, respectively.
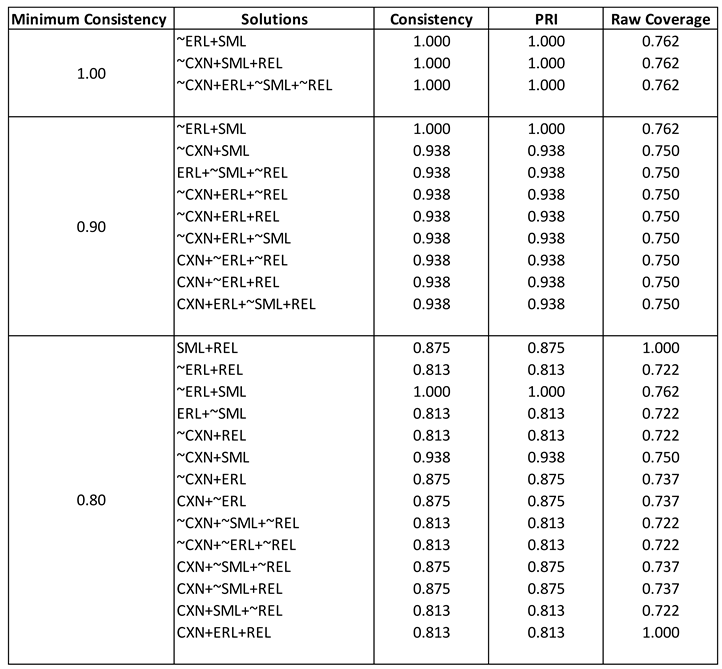
The necessity of conditions and disjunctions of conditions (both their presence and absence) for the occurrence of UTT was examined using a minimum consistency that ranged from 1.0 to 0.55. Consistency, proportional reduction of inconsistency (PRI), and raw coverage POFs for each condition and disjunction were calculated (
Table 10). The raw coverage was above 0.70 for many of the conjunctions and disjunctions. However, none of them were substantively relevant because they were not indicative of higher-order constructs.
Sufficiency for the Occurrence of University Technology Transfer
The sufficiency of each individual condition (both their presence and absence) for the occurrence of UTT was examined using minimum consistencies that ranged from 1.0 to 0.55. Consistency and coverage POFs for each individual condition were calculated (
Table 11a). The consistency POF value was 1.0 for the presence of each individual condition. The highest consistency POF value for the absence of any individual condition was 0.643. However, the highest coverage POF value for the presence or absence of any individual condition was 0.625. The p-values were all less than 0.05 for the consistency POF values for the presence of each individual condition only at minimum consistencies of 0.65 and 0.55.
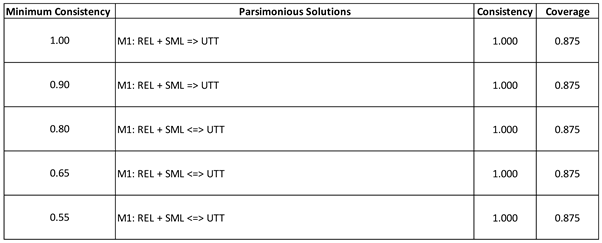
The sufficiency of conditions and disjunctions of conditions (both their presence and absence) for the occurrence of UTT were examined using minimum consistency benchmarks ranging from 1.0 to 0.55. Conservative, parsimonious, and intermediate solutions were determined for each consistency benchmark (
Table 12). All solutions exhibited consistency POF values of 1.0 and coverage POF values of 0.875.
There was model ambiguity in the calculation of the conservative solution. Two models each comprising four conjunctive disjunctions represented the data equally well:
Both models were stable over the range of minimum consistency benchmarks used in the analysis although at the minimum consistency benchmarks of 0.80, 0.65, and 0.55 the solution shifted from being sufficient to being necessary and sufficient. The two models differed only in one of the four conjunctive disjunctions.
The calculation of the parsimonious solution resulted in a single solution that was stable over the range of minimum consistency benchmarks used in the analysis. The parsimonious solution was as follows:
Under the assumptions of the parsimonious solution calculation, the presence of either the REL condition or the SML condition was sufficient for the occurrence of UTT. Again, the model shifted from sufficient to necessary and sufficient at the 0.80, 0.65, and 0.55 minimum consistency benchmarks.
The calculation of the intermediate solution also produced a single solution that was stable over the range of minimum consistency benchmarks used in the analysis. The calculation of the intermediate solution ensured that statements about necessity were not contradicted, and no implausible or incoherent counterfactuals were included in the analysis. Additionally, it accounted for possible contradictory simplifying assumptions (CSAs). It also incorporated directional expectations regarding the CXN condition, whose presence was expected to contribute to the occurrence of UTT according to theory and empirical analyses found in the literature. This produced the following solution:
As with the conservative and parsimonious solutions, the intermediate solution shifted from sufficient to necessary and sufficient at the 0.80, 0.65, and 0.55 minimum necessity benchmarks.
Robustness of Findings
The study findings were robust. Although the solutions were stable only when the frequency cut-off threshold was fixed at a level of one case, they were insensitive to the range of raw consistency benchmarks. There was no change in the solution formula over the range of raw consistency benchmarks and the parameters of fit were stable.
Discussion
The preceding section presented the results of the data analysis. This section aims to interpret those results. It presents the major findings and discusses conclusions drawn from those findings. Next, the implications for public policy and the practice of university technology transfer are discussed as well as recommendations for future research. The section concludes with a synthesis that represents the essential aspects and breadth of what the research study has attempted.
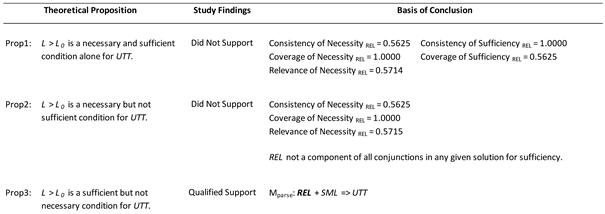
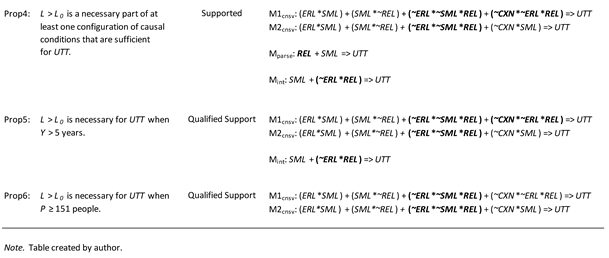
Table 13 summarizes the conclusions drawn from the analysis results. The study provided either support or qualified support for four of the six theoretical propositions.
Theoretical Proposition 1
The study findings did not support the theoretical proposition that L > L0 is a necessary and sufficient condition alone for UTT. If and only if this proposition were true, the analysis would have produced the following solution:
However, the analysis produced no such result. Moreover, the superset criteria would have been exhibited by a consistency of necessity POF value for the occurrence of UTT and a consistency of necessity POF value for the non-occurrence of UTT equal to or greater than 0.80 with a coverage of necessity POF value between 0.70 and 0.90 and a relevance of necessity (RoN) POF value equal to or greater than 0.80. The necessity POFs for the condition REL alone were all below these benchmarks. Thus, one can logically infer that L > L0 alone is not a necessary and sufficient condition for the occurrence of university technology transfer. The condition REL would have been a superset of the instances of UTT indicating that REL must be present for UTT to occur and absent when UTT does not occur. Simultaneously, the presence of REL in and of itself would have been sufficient for UTT.
Theoretical Proposition 2
The study findings did not support the theoretical proposition that L > L0 is a necessary but not sufficient condition for UTT. If this proposition were true, the REL condition would have been a superset of the instances of UTT indicating that the REL condition must be present
for UTT to occur and absent when UTT does not occur. As described above, the REL condition did not satisfy the consistency of necessity POF benchmarks. Additionally, the REL condition would have been a component of all conjunctions sufficient for UTT. This was not the case. The study findings demonstrated that L > L0 was not a necessary but insufficient condition for the occurrence of university technology transfer as operationalized in the study.
Theoretical Proposition 3
The study findings provided qualified support for the theoretical proposition that L > L0 is a sufficient but not necessary condition for UTT. Only one of the models was consistent with this theoretical proposition. The derivation of the parsimonious solution, which assumes that logical remainders are sufficient for UTT, produced the following solution:
This solution indicates that either L > L0 or P < 151 people are each alone sufficient, but not necessary, for UTT. When one condition is present the other is condition is not necessary for UTT. Although L > L0 is sufficient for UTT under the assumptions of the parsimonious solution, it is not necessary if the condition P < 151 people is satisfied.
Theoretical Proposition 4
The study findings did support the theoretical proposition that L > L0 is a necessary part of at least one configuration of causal conditions that is sufficient for UTT. All models were consistent with this theoretical proposition. The conservative solution for sufficiency was indicative of causal complexity but also exhibited model ambiguity. It assumed that logical remainders are not sufficient conditions for UTT. The analysis produced the following two conservative solutions:
Each model contained four (4) conjunctions. The first three conjunctions of both models were the same and the REL condition was a necessary part of one of those conjunctions. The third conjunction indicated that L > L0 in combination with P ≥ 151 people and Y > 5 years is sufficient for the occurrence of university technology transfer.
The fourth conjunction of the conservative solution differed between the two models. In one of the models, the REL condition in combination with the absence of both the CXN and ERL conditions is sufficient for the UTT to occur. This indicated that L > L0 in combination with Y > 5 years and there not being any relevant social or professional connections between the private sector organization and the university is sufficient for the occurrence of university technology transfer.
The parsimonious solution was also consistent with the theoretical proposition that L > L0 is a necessary part of at least one configuration of causal conditions that is sufficient for UTT. As explained above, the parsimonious solution assumes that logical remainders are sufficient for the occurrence of university technology transfer. The analysis produced the following parsimonious solution:
The REL condition is sufficient for UTT to occur, but it is not necessary. UTT can still occur when the REL condition is not present if the SML condition is satisfied.
The intermediate solution also supported the proposition that L > L0 is a necessary part of at least one conjunction that is sufficient for UTT. It too was indicative of causal complexity. When considering the directional expectation of the presence of relevant social or professional connections between the private sector organization and the university to contribute to the occurrence of university technology transfer, the analysis produced the following solution:
The intermediate solution indicated that L > L0 in combination with Y > 5 years is sufficient for UTT. However, this conjunction is not necessary for the occurrence of university technology transfer because of causal complexity.
Theoretical Proposition 5
The analysis provided qualified support for the theoretical proposition that L > L0 is a necessary condition for UTT when Y > 5 years. Three of the four models were consistent with this theoretical proposition. The conservative solution, which assumed that none of the logical remainders are sufficient for UTT, contained two conjunctions that supported this proposition. Although there was model ambiguity in the conservative solution, both models contained the following conjunction:
Additionally, one of the conservation solution models also contained the following conjunction:
These conjunctions suggest that L > L0 is a necessary condition for UTT in cases where Y > 5 years but only when either P ≥ 151 people or when there are also no relevant social or professional connections between the private sector organization and the university.
The intermediate solution, which assumed that logical remainders are sufficient for UTT and that the presence of the CXN condition contributes to UTT, contained the conjunction:
As explained above, this conjunction suggests that L > L0 is a necessary condition for UTT in cases where Y > 5 years and that no other conditions are necessary.
Theoretical Proposition 6
The analysis provided qualified support for the theoretical proposition that L > L0 is necessary for UTT when P ≥ 151 people. This was the case only when logical remainders were assumed not to be sufficient for UTT. As explained above, the conservative solution contained the following conjunction in both models across all minimum consistency levels used in the analysis:
This conjunction indicates that L > L0 is a necessary condition for the UTT in cases where P ≥ 151 people and Y > 5 years.
Implications for Policy and Practice
These study findings have implications for the design of public policy and the practice of university technology transfer. They suggest that it would be prudent for policymakers to rethink the supposition that it is the responsibility of the private sector to mature technologies. The issue seems to be more nuanced. Economic and social factors seem to disincentivize private sector actors from pursuing technologies with maturity levels below a certain point.
The incidence of university technology transfer may be significantly increased if the government takes this into consideration in its research funding mechanisms and practices. Providing sufficient funding that enables university researchers to mature technologies to at least a TRL-6 on the NASA technology readiness level scale might significantly increase the chances for technologies to be transferred to the private sector and increase the overall incidence of university technology transfer.
This does not necessarily require increasing the aggregate amount of federal funding allocated to university researchers. Instead, the federal government could split its allocation of university research and development funding by technology maturity level. The government could specifically reserve a portion of its funding to be directed to support the maturation of technologies to at least a TRL-6 maturity level. That is, maturation to TRL-6 would be a technical objective of the grant. Such a scheme can be implemented at the policy subsystem level through the regulations mechanism. For example, the scheme could be incorporated into the Small Business Innovation Research (SBIR) and Small Business Technology Transfer Research (STTR) programs. Moreover, it could be implemented in an incremental manner, which would likely be politically expedient and more palatable to key stakeholders since the change would be more gradual.
The federal government may also be able to implement policy that mitigates the economic and social factors that disincentivize private sector organizations from pursuing less mature technologies. According to basic economic theory, taxing a good tends to result in less of the good being produced while subsidizing a good tends to result in the production of more of the good than what would ordinarily occur (see e.g., Musgrave, 1959; Stiglitz & Rosengard, 2015). Subsidies may be a viable mechanism for encouraging more university technology transfer. There is already precedent for such an approach as it relates to research and development. Under Section 41 of the U.S. Internal Revenue Code, companies may receive a tax credit for research and development costs (Economic Recovery Tax Act of 1981, 26 U.S.C § 41, Pub.L. 97-34). A similar scheme could be created to provide a tax credit to companies that license low maturity level technologies derived from federally funded research provided that they advance the technologies to some minimum maturity level or introduce a market offering in which the technology is a core element. This might make lower maturity level technologies created at U.S. universities more appealing to private sector organizations. However, such an approach might encounter resistance from coalitions that perceive such policies as a form of “corporate welfare.”
Federal public policy could also be aimed at altering the behavior of universities and other organizations to encourage them to develop technologies to higher maturity levels. For example, it might be possible to use the patent regulations to encourage such behavior. Utility, or usefulness, is one of the criteria for obtaining a patent under U.S. patent law. However, the term remains very ambiguous in the laws and regulations. This could be leveraged to encourage university researchers and others who seek patents to mature technologies further. Demonstrating that an invention has been developed to at least the equivalent of a TRL-6 on the NASA technology readiness level scale could be specified as a criterion for establishing utility. Moreover, this is something that could be implemented at the policy subsystem level through the rules and regulations. For example, from 1790 to 1870, the United States required patent applicants to submit three-dimensional representations of inventions called “patent models” to demonstrate utility (Dood, 1983; Ireland, 2009). Although the practice has since been discontinued, under current law the Commissioner of Patents may still require a model if he or she deems it necessary (Dood, 1983; United States Patent and Trademark Office, 2022, p. R-119). It might be feasible to require patent applicants to submit models that demonstrate some specified minimum technology maturity level (e.g., TRL-6) as a means of satisfying the utility criterion, which is necessary to receive a patent. The use of computer-based three-dimensional modeling would eliminate the need for physical space to store the models.
University administrators may also find it beneficial to incorporate technology maturity level into their decision-making processes for awarding internal funding to research projects and when deciding whether to pursue intellectual property protection for any given technology and its transfer to the private sector. Universities may be able to significantly increase the proportion of technologies created at their institutions that are transferred to the private sector by linking financial support for research projects to technology maturation milestones.
However, there are cultural factors that pose challenges to implementing such a change. Academic freedom is a sacred tenet of university culture. It generally enables university faculty to research and teach without undue or unreasonable institutional interference or restraint (Reichman, 2019). Promotion and tenure decisions at universities are heavily influenced by publication success which places pressure on researchers to publish when technologies are less mature (Yeung, 2019). Academic culture still values basic research more than applied research (Bently, Gulbrandsen, & Kyvik, 2015). University faculty will likely resist attempts to push them to pursue research that will produce higher maturity level technologies if they perceive it as an assault on academic freedom or emphasizing applied research at the expense of basic research or if they consider the tactics used to be heavy-handed.
University administrators may be able to sidestep such potential pushback from faculty by framing these efforts in terms of the university’s responsibility to prepare students to succeed. The vast majority of doctoral candidates in the so-called STEM
4 disciplines will not obtain positions in academia (Carey, 2020; Carron, 2013). Instead, their career paths will take them to the private sector. One can argue that universities have a legal, ethical, and moral obligation to provide the best preparation possible to help these students achieve success. Creating opportunities that enable them to hone their skills by conducting research that aims to mature technologies would do just that.
Additionally, university technology transfer practitioners may find benefit in limiting the pursuit of intellectual property protection and commercialization efforts to technologies that have been matured to, or stand a reasonable chance of being matured to, the equivalent of at least a TRL-6 on the NASA technology readiness level scale. The budgets of technology transfer offices at universities are likely insufficient to pursue patent prosecution for all technologies that are disclosed to them. Consequently, university technology transfer staff must triage the disclosures. Using technology maturity level as one of the criteria in this triage process is one possible approach. These may be particularly helpful strategies for universities in which faculty have limited social and professional connections with private sector organizations that would be the logical prospects for technologies derived from the research being conducted at their institutions.
Finally, there has been discussion about including technology transfer activity into faculty tenure and promotion decisions (see e.g., Genshaft, Wickert, Gray-Little, Hanson, Marchase, Schiffer, & Tanner, 2016; Sanberg, Gharib, Harker, Kaler, Marchase, Sands, Arshadi, & Sarkar, 2014; Stevens, Johnson, & Sanberg, 2011). However, such efforts could decrease the incidence of university technology transfer depending on how they are implemented. Patent activity is often identified as an important metric that should be considered in tenure and promotion decisions. But there is usually a finite window for faculty to pursue tenure. Moreover, it is not unheard of for patent prosecution taking up to 3 years or more. These factors would likely cause faculty to push for patenting of their technologies earlier in the development process when the technologies are less mature and have less of a chance of being successfully transferred to the private sector. This might be less of an issue for promotion decisions. But even in those scenarios, it would still be more advantageous for faculty to push for patenting of their technologies earlier rather than later.
Study Limitations
As with all research, this study has limitations. There are limitations and challenges with applying QCA in multiple case study research designs. Avoiding subjectivity in the analysis is a significant challenge because the cases, conditions, and attributes selected have a strong impact on the research results and conclusions drawn about causal relations (Sehring, Korhonen-Kurki, & Brockhaus, 2013). Careful consideration of each of these elements is required. Also, only a limited number of factors can be included in QCA to keep the analysis and interpretation of results manageable. This tends to limit the variety of cases that can be included in QCA. While this provides for a better comparison of cases, it limits the generalizability of the results (Sehring, Korhonen-Kurki, & Brockhaus). This also makes QCA susceptible to the effects of limited empirical diversity.
In an ideal analysis, all possible combinations of conditions, except for those that are physically impossible, would be represented in the sample of cases. This is generally not the situation given the nature of social phenomena, the constraints for conducting research studies, and the limitations regarding the number of cases that can be included in QCA. This restricts the validity of inferences drawn from QCA (Sehring, Korhonen-Kurki, & Brockhaus).
The binary approach of crisp-set QCA (csQCA) may be limited in its representativeness of the phenomena of university technology transfer and the associated constructs used in the study. Many social phenomena are appropriately conceptualized in binary terms but manifest in terms of degrees (Schneider & Wagemann, 2012). Consequently, the study is more revealing of differences in kind rather than differences in degree. Many proponents of csQCA would argue this is more interesting and more explanatory (Sehring, Korhonen-Kurki, & Brockhaus, 2013). However, applying fuzzy-set QCA (fsQCA) might produce more nuanced insights.
The operationalization of the relevant social or professional connections condition (CXN) is another limitation. The study used publicly available information to code this condition. However, not all such connections are revealed in public manners. It is possible that relevant social or professional connections existed for a case that was coded as a non-member of this condition set. Whether such a scenario for one or more cases would significantly impact the results of the analysis is not known.
Finally, although the study design emphasized the perspective of demand-side actors in university technology transfer, it did not explicitly examine demand-side technology transfer decision-makers as subjects or the decision-making process. One must infer that the action of pursuing and executing a license for a given technology was preceded by a decision by the members of the demand-side organization to obtain and assimilate the technology based on the premise that every action taken on behalf of an organization is coupled with at least one decision.
Recommendations for Future Research
There are several opportunities to improve and extend this study. For example, using fuzzy-set QCA (fsQCA) to analyze the cases could be fruitful. This approach might be more representative of the phenomenon and conditions and could produce more nuanced insights about differences in degree.
There is also the possibility of increasing the number of cases in the analysis. Doing so might mitigate the issue of limited diversity. This could include specifically searching for and sampling cases in which one or more of the conditions used in the study are absent, but university technology transfer occurred. One could also search for cases with the attributes of logical remainders.
The study used an adaptation of the NASA technology readiness level scale to measure technology maturity level. This scale lacks a certain degree of precision and does not fully capture the multidimensional nature of technology maturity level. Using an improved instrument for measuring technology maturity level in the study might reveal important and useful nuances about the relationship between technology maturity level and the occurrence or non-occurrence of university technology transfer.
The operationalization of the relevant social or professional connections condition (CXN) could be improved. In addition to reviewing publicly available information, one could also interview the relevant individuals involved in the case to uncover such connections that may not be revealed in publicly available sources. However, such an approach will likely require an Institutional Review Board (IRB) submission because the questions will need to delve into information about human subjects.
Incorporating a temporal aspect into the analysis might be worthwhile. The study primarily focused on cases that occurred during a narrow five-year window. Replicating the study with data from different timeframes or adding a temporal condition would help ascertain whether the results of the study are temporally stable.
Examining other conditions not included in the study might also prove worthwhile. For example, the literature gives reason to believe that there might be an interplay between technology maturity level and the absorptive capacity of the private sector organization considering the technology. Alternatively, the relevant social or professional connections condition (CXN) used in the study could be disaggregated to focus on specific kinds of connections. Additionally, the presence of the CXN condition was not a necessary part of any configuration of causal conditions in the solution models. This is a rather interesting result given what was found in the literature and probably warrants further investigation. The presence or absence of federal funding might also influence whether a given technology is transferred to the private sector or not. However, there is also the question of whether the presence or absence of federal funding determines the maturity level that a technology attains or whether the maturity level determines whether federal funding is successfully obtained.
Although this study focused on the demand-side perspective of university technology transfer, it might be worthwhile to incorporate relevant supply-side factors. For example, one might argue that whether a university has the financial resources to enable the research necessary to mature technologies is an important consideration. This could be incorporated as a causal condition, but its operationalization might be challenging. While the amount of research expenditures for a university might appeal to some as a way to operationalize this condition, it would likely be inadequate and problematic. The amount of funding required to sufficiently mature a technology will vary by technology. Additionally, even if the university appears to have available funding in aggregate, it does not necessarily mean that the technologies created will be more mature because the funding mechanism might restrict the nature of the projects to so-called “basic research.” Moreover, even if the university has access to less restricted funding sources over which it has more discretion, it does not necessarily mean that any given technology would receive funding to facilitate its maturation.
A related consideration is whether there are any relevant relationships with national laboratories or industry-university consortia (e.g., industry-university cooperative research centers) for a given case. Such relationships might provide universities with access to the financial resources to mature technologies enough to warrant the interest of private sector organizations. Relationships with industry-university consortia might be particularly relevant because industry partners tend to have significant input in selecting technology development projects and establishing development objectives.
A closer examination of causation is another potential line of research. The study demonstrated causal conditions for the occurrence of university technology transfer. However, various mechanisms could link these causal conditions to the outcome. A more specific exploration of the causal mechanisms operating under these causal conditions might also produce valuable and useful insights that could advance university technology policy and practice.
A more thorough examination of the non-occurrence of university technology transfer also presents an opportunity to extend this study. Although the results presented focused on the occurrence of university technology transfer, the non-occurrence of university technology transfer was analyzed. However, the results of the study did not produce solutions of sufficiency for the non-occurrence of university technology transfer at the more stringent consistency benchmarks. This lends further credence to the notion that the phenomenon of university technology transfer is subject to casual complexity. Understanding the conditions that are necessary or sufficient for resulting in the non-occurrence of university technology transfer (i.e., conditions that impede the occurrence of university technology transfer) would significantly inform public policy and professional practice. It is often easier to design and implement policy that constrains an outcome than to design and implement policy that enables an outcome (Ragin, 2000, p. 203-204). However, constraining the non-occurrence of university technology transfer will not be sufficient in and of itself to enable the occurrence of university technology transfer because of causal complexity.
Finally, the role of technology maturity level as a potential casual condition in university technology transfer to the public sector is another gap that this study did not address. Different motivations drive activity in the private sector and the public sector. It is unlikely that the causal conditions that tend to produce university technology transfer to the private sector are the exact same as those that tend to result in technology transfer to the public sector. Specifically, technology maturity level likely plays a different role in technology transfer to the public sector than what the findings of this study suggest is its influence on university technology transfer to the private sector.
Conclusions
This study extends the work of previous researchers in the areas of technology maturity level and university technology transfer. The aim of the study was to answer two primary research questions. First, how can the incidence of university technology transfer to the private sector in the United States be increased? Second, how does the maturity level of a university technology influence whether the technology is successfully transferred to the private sector?
The study findings suggest that university technology transfer is subject to causal complexity. The conditions that tend to produce the occurrence of university technology transfer are not simply mirror images of the conditions that tend to impede the occurrence of university technology transfer. Consequently, the incidence of university technology transfer in the United States can be increased by understanding which conditions are conducive to its occurrence and which tend to impede its occurrence. This will allow policymakers and practitioners to implement public policy and practices that promote the former and prevent the latter.
Regarding technology maturity level, the study findings suggest that a maturity level equivalent to at least a TRL-6 on the NASA technology readiness level scale is most likely an insufficient but necessary part of one or more unnecessary but sufficient configuration of conditions that tends to result in the occurrence of university technology transfer. However, under certain circumstances, a technology maturity level of at least TRL-6 alone could be sufficient but unnecessary for the occurrence of university technology transfer. Therefore, it may be possible to increase the incidence of university technology transfer in the United States by implementing public policy and practices that incentivize university researchers to mature technologies to at least the equivalent of TRL-6 on the NASA technology readiness level scale. However, there are also options to incentive private sector organizations to obtain and assimilate lower maturity level technologies created at U.S. universities.
Finally, this study makes important contributions to technology transfer research methodology. It demonstrated the feasibility and viability of using configurational comparative methods to examine university technology transfer. This enables further exploration of causal complexity in this social phenomenon and raises the possibility of new and useful insights. Additionally, the study demonstrated practical alternative operationalizations of technology and university technology transfer. It also showed the viability of using alternatives to AUTM data for conducting research. These contributions expand the possibilities for future lines of research on the topic of university technology transfer.
Funding
The author did not receive funding support from any organization to assist with this work or the manuscript.
Data Availability Statement
Most of the data generated or analyzed during this study are included in this article. All other data generated or analyzed during the current study that are not included in this article are available from the corresponding author on reasonable request.
Acknowledgments
I would like to acknowledge Mr. Brian Eller of North Carolina State University who provided case data used in this study. I would also like to thank Dr. Robert A. Cropf and Dr. James F. Gilsinan of Saint Louis University and Eric W. Anderson, J.D. of the University of Missouri – Kansas City, who served on the advisory committee for my dissertation research on which this work is based.
Conflicts of Interest
The author has no relevant financial or non-financial interests to disclose.
References
- Anatan, L. (2015). Conceptual issues in university to industry knowledge transfer studies: A literature review. Procedia - Social and Behavioral Sciences, 211, 711-717. [CrossRef]
- Arshadi, N., & George, T. F. (2008). The Economics of University Research and Technology Transfer. Research Management Review, 16(1), 1-19. Retrieved from http://lib.slu.edu.
- Asch, S. E. (1951). Effects of group pressure upon the modification and distortion of judgments. In H. Guetzkow (Ed.), Groups, leadership and men; Research in human relations. (pp. 177-190). Pittsburgh, PA: Carnegie Press.
- Asch, S. E. (1956). Studies of independence and conformity: A minority of one against a unanimous majority. Psychological Monographs. 70 (9): 1-70. [CrossRef]
- Association of University Technology Managers. (2021). Better world project [Data set]. Retrieved January 19, 2021 from https://autm.net/about-tech-transfer/better-world-project/about-better-world/.
- Baek, S., Hwang, S., & Park, Y. I. (2018). Determinants of Technology Transfer and Commercialization in National Research and Development: Focusing on Korea Railroad Research Projects. Asian Journal of Innovation & Policy, 7(3), 438-456. [CrossRef]
- Bahcall, S. (2019). Loonshots: How to nurture the crazy ideas that win wars, cure diseases, and transform industries. New York, NY: St. Martin's Publishing Group.
- Balogun, J., Pye, A., & Hodgkinson, G. P. (2008). Cognitively skilled organizational decision making: Making sense of deciding. In G. P. Hodgkinson & W. H. Starbuck (Eds.), The Oxford handbook of organizational decision making (pp. 234-249). New York, NY: Oxford University Press.
-
Barriers to domestic technology transfer: Hearing before the Subcommittee on Oversight and Investigations of the Committee on Energy and Commerce, House of Representatives, 102nd Congress, First Session (1992).
- Bengoa, A., Maseda, A., Iturralde, T., & Aparicio, G. (2020). A bibliometric review of the technology transfer literature. The Journal of Technology Transfer. [CrossRef]
- Bentley, P. J., Gulbrandsen, M., & Kyvik, S. (2015). The relationship between basic and applied research in universities. Higher Education, 70(4), 689-709. [CrossRef]
- Bozeman, B. (2000). Technology transfer and public policy: A review of research and theory. Research Policy, 29(4,5), 627-655. Retrieved from http://lib.slu.edu.
- Bruneel, J., D’Este, P., & Salter, A. (2010). Investigating the factors that diminish the barriers to university–industry collaboration. Research Policy, 39(7), 858-868. [CrossRef]
- Carey, K. (2020). The bleak job landscape of adjunctopia for Ph.Ds. The New York Times, 5. Retrieved from https://www.nytimes.com/2020/03/05/upshot/academic-job-crisis-phd.html.
- Carron, L. (2013). The changing PhD: How can higher education institutions prepare science PhDs for alternate careers. In Progress. Retrieved from http://inprogressjournal.net/archives/current-issue-2/the-changing-phd-how-can-higher-education-institutions-prepare-science-phds-for-alternate-careers/.
- Cronqvist, L., & Berg-Schlosser, D. (2009). Multi-value QCA (mvQCA). In B. Rihoux & C. C. Ragin (Eds.), Configurational comparative methods: Qualitative comparative analysis (QCA) and related techniques (pp. 69-86). Thousand Oaks, CA: SAGE Publications.
- Cyert, R. M., & March, J. G. (1963). A behavioral theory of the firm. Engelwood Cliffs, NJ: Prentice-Hall.
-
Daily compilation of presidential documents. (2011, October 28). Retrieved from https://www.govinfo.gov/app/collection/CPD/.
- Dolmans, S. A. M., Shane, S., Jankowski, J., Reymen, I. M. M. J., & Romme, A. G. L. (2016). The evaluation of university inventions: Judging a book by its cover? Journal of Business Research, 69(11), 4998-5001. [CrossRef]
- Dood, K. J. (1983). Patent models and the patent law: 1790-1880 (Part I). Journal of the Patent Office Society, 65(5), 187-216. Retrieved from https://heinonline-org.ezp.slu.edu/HOL/Page?handle=hein.journals/jpatos65&id=261&collection=journals&index=.
- Dusa, A. (2021). QCA: A package for qualitative comparative analysis (Version 3.11). Comprehensive R Archive Network. Retrieved from https://rdrr.io/cran/QCA/man/QCA.package.html.
- Economic Recovery Tax Act of 1981, Pub.L. 97-34, 95 Stat. 172, 26 U.S.C. § 41. (1981). https://www.congress.gov/public-laws/97th-congress.
- Ferguson, W. K. (2014). A Policy Framed Analysis of the Valley of Death in U.S. University Technology Transfer. University of Southern Mississippi. Available from http://www.proquest.com/en-US/products/dissertations/individuals.shtml.
- Fisher, A. (2004). The logic or real arguments (Second Ed.). New York: Cambridge University Press.
- Genshaft, J., Wickert, J., Gray-Little, B., Hanson, K., Marchase, R., Schiffer, P. E., & Tanner, R. M. (2016). Consideration of technology transfer in tenure and promotion. Technology & Innovation, 17(4), 197-204. [CrossRef]
- González-Pernía, J. L., Kuechle, G., & Peña-Legazkue, I. (2013). An assessment of the determinants of university technology transfer. Economic Development Quarterly, 27(1), 6. Retrieved from http://lib.slu.edu.
- Gulbrandsen, K. E. (2009). Bridging the valley of death: The rhetoric of technology transfer. Iowa State University, Ann Arbor. Available from http://www.proquest.com/en-US/products/dissertations/individuals.shtml.
- Heisey, P. W., & Adelman, S. W. (2011). Research expenditures, technology transfer activity, and university licensing revenue. Journal of Technology Transfer, 36(1), 38-60. [CrossRef]
- Ireland, C. (2009). History on a small scale. The Harvard Gazette. Retrieved from https://news.harvard.edu/gazette/story/2009/07/history-on-a-small-scale-2/.
- Hodgkinson, G. P., & Starbuck, W. H. (Eds.). (2008). The Oxford handbook of organizational decision making. Oxford, United Kingdom: Oxford University Press.
- Hudson, J., & Khazragui, H. F. (2013). Into the valley of death: research to innovation. Drug Discovery Today, 18(13-14), 610-613. Retrieved from https://purehost.bath.ac.uk/ws/files/9594981/Hudson_Drug_Discovery_Today_2013.pdf.
- Kaarbo, J., & Beasley, R. K. (1999). A practical guide to the comparative case study method in political psychology. Political Psychology, 20(2), 369-391. Retrieved from http://www.jstor.org/stable/3792081.
- Kahneman, D. (2011). Thinking, fast and slow. New York, NY: Farrar, Straus, and Giroux.
- Kahneman, D., & Tversky, A. (1979). Prospect theory: An analysis of decision under risk. Econometrica, 47(2), 263-292. Retrieved from http://lib.slu.edu.
- Kahneman, D., & Tversky, A. (2013). Prospect theory: An analysis of decision under risk. In Handbook of the fundamentals of financial decision making: Part I (pp. 99-127). World Scientific.
- Knight, F. H. (1921). Risk, uncertainty and profit. New York, NY: Houghton Mifflin Company.
- Kundu, N., Bhar, C., & Pandurangan, V. (2015). Managing Technology Transfer: An Analysis of Intrinsic Factors. South Asian Journal of Management, 22(3), 69-95. doi:Retrieved from http://lib.slu.edu.
- March, J. G. (1997). Understanding how decisions happen in organizations. In Zur Shapria (Ed.), Organizational decision making (pp. 9-32). New York, NY: Cambridge University Press.
- Markham, S. K. (2002). Moving technologies from lab to market. Research-Technology Management, 45(6), 31-42. Retrieved from https://www.researchgate.net/profile/Stephen_Markham/publication/228686775_Moving_Technology_from_Lab_to_Market/links/5405e1c60cf2bba34c1dd7cd/Moving-Technology-from-Lab-to-Market.pdf.
- Markman, G. D., Gianiodis, P. T., & Phan, P. H. (2009). Supply-Side Innovation and Technology Commercialization. Journal of Management Studies, 46(4), 625-649. [CrossRef]
- Markham, S. K., Ward, S. J., Aiman-Smith, L., & Kingon, A. I. (2010). The valley of death as context for role theory in product innovation. Journal of Product Innovation Management, 27(3), 402-417. Retrieved from http://lib.slu.edu.
- Merriam-Webster. (2021a). Loony. In Merriam-Webster.com dictionary. Retrieved January 10, 2021 from https://www.merriam-webster.com/dictionary/loony.
- Merriam-Webster. (2021b). Moonshot. In Merriam-Webster.com dictionary. Retrieved January 10, 2021 from https://www.merriam-webster.com/dictionary/moonshot.
- Munteanu, R. (2012). Stage of development and licensing university inventions. International Journal of Management and Enterprise Development (1). [CrossRef]
- Musgrave, R. A. (1959). The theory of public finance: A study in public economy. New York, NY: McGraw-Hill.
- Oana, I., Schneider, C. Q., & Thomann, E. (2021). Qualitative comparative analysis using R: A beginner’s guide. Cambridge, United Kingdom: Cambridge University Press.
- Office of Management and Budget. (2002). The President's Management Agenda. Retrieved from http://www.dtic.mil/dtic/tr/fulltext/u2/a394421.pdf.
- Office of Management and Budget. (2018). The President's Management Agenda. Retrieved from https://www.whitehouse.gov/wp-content/uploads/2018/03/Presidents-Management-Agenda.pdf.
- Ragin, C. C. (2000). Fuzzy-set social science. Chicago, IL: University of Chicago Press.
- Reichman, H. (2019). The future of academic freedom. Baltimore, MD: John Hopkins University Press.
- Rojot, J. (2008). Culture and decision making. In G. P. Hodgkinson & W. H. Starbuck (Eds.), The Oxford handbook of organizational decision making (pp. 134-151). New York, NY: Oxford University Press.
- Rose, M. (2001). Risk versus uncertainty, or Mr. Slate versus Great-Aunt Matilda. The Library of Economics and Liberty. Retrieved from https://www.econlib.org/library/Columns/Teachers/riskuncertainty.html.
- RStudio. (2019). RStudio Desktop (version 1.2.1335). Retrieved May 10, 2019 from https://rstudio.com/products/rstudio/#rstudio-desktop.
- Sanberg, P. R., Gharib, M., Harker, P. T., Kaler, E. W., Marchase, R. B., Sands, T. D., Arshadi, N., & Sarkar, S. (2014). Changing the academic culture: Valuing patents and commercialization toward tenure and career advancement. Proceedings of the National Academy of Sciences, 111(18), 6542-6547. [CrossRef]
- Schneider, C. Q., & Wagemann, C. (2012). Set-theoretic methods for the social sciences: A guide to qualitative comparative analysis. Cambridge, United Kingdom: Cambridge University Press.
- Sehring, J., Korhonen-Kurki, K., & Brockhaus, M. (2013). Challenges and limitations of QCA. In Qualitative comparative analysis (QCA): An application to compare national REDD+ policy processes (pp. 17-20). Bogor, Indonesia: Center for International Forestry Research. Retrieved March 3, 2021 from http://www.jstor.org/stable/resrep02339.8.
- Simon, H. A. (1955). A behavioral model of rational choice. The Quarterly Journal of Economics, 69(1), 99-118. Retrieved from http://www.suz.uzh.ch/dam/jcr:ffffffff-fad3-547b-ffff-fffff0bf4572/10.18-simon-55.pdf.
- Simon, H. A. (1957). Models of man, social and rational: Mathematical essays on rational human behavior in society setting. New York, NY: John Wiley and Sons.
- Simon, H. A. (1972). Theories of bounded rationality. In C. B. McGuire & R. Radnor (Eds.), Decision and Organizations (pp. 161-176). Amsterdam, Netherlands: North-Holland Publishing Company.
- Simon, H. A. (1982). Models of bounded rationality. Cambridge, MA: MIT Press.
- Simon, H. A. (1991). Bounded rationality and organizational learning. Organization Science, 2(1), 125-134. Retrieved from https://www.jstor.org/stable/2634943.
- Simon, H. A. (1997). Administrative behavior: A study of decision-making processes in administrative organizations (Fourth Ed.). New York, NY: The Free Press.
- Song, M., Park, J. O., & Park, B. S. (2017). Determinants of R&D commercialization by SMEs after technology transfer. Asian Journal of Innovation & Policy, 6(1), 45-57. [CrossRef]
- Stevens, A. J., Johnson, G. A., & Sanberg, P. R. (2011). The role of patents and commercialization in the tenure and promotion process. Technology & Innovation, 13(3), 241-248. [CrossRef]
- Stiglitz, J., & Rosengard, J. (2015). Economics of the public sector (4th ed.). New York, NY: W. W. Norton & Company.
- Thiem, A., Baumgartner, M., Dusa, A., & Spoehel, R. (2018). QCApro: Advanced functionality for performing and evaluating qualitative comparative analysis (Version 1.1-2). Comprehensive R Archive Network. Retrieved from https://cran.r-project.org/web/packages/QCApro/index.html.
- Thomann, E. (2021). Qualitative comparative analysis (QCA): Principles and application [Presentation]. Department of Social Policy and Intervention, Oxford University. Retrieved August 24, 2021 from https://youtu.be/NxbkxfvhxgE.
- Thomas, W. I., & Thomas, D. S. (1928). The child in America: Behavior problems and programs. New York, NY: Knopf.
- Thursby, J. G., & Thursby, M. C. (2001). Industry perspectives on licensing university technologies: Sources and problems. Industry and Higher Education, 15(4), 289-294. Retrieved from http://ezp.slu.edu/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=edo&AN=ejs42368811&site=eds-live.
- Tversky, A., & Kahneman, D. (1974). Judgment under uncertainty: Heuristics and biases. Science, 185(4157), 1124-1131. [CrossRef]
- Tversky, A., & Kahneman, D. (1986). The framing of decisions and the evaluation of Prospects. Studies in Logic and the Foundations of Mathematics, 114, 503-520. [CrossRef]
- Tversky, A., & Kahneman, D. (1992). Advances in prospect theory: Cumulative representation of uncertainty. Journal of Risk and uncertainty, 5(4), 297-323.
- United States Patent and Trademark Office. (2022). Appendix R Consolidate Patent Rules – January 2022 Update. In Manual of Patent Examining Practices (MPEP). Washington, D.C.: Department of Commerce. Retrieved from https://www.uspto.gov/web/offices/pac/mpep/consolidated_rules.pdf.
- Wu, Y., Welch, E. W., & Huang, W. L. (2015). Commercialization of university inventions: Individual and institutional factors affecting licensing of university patents. Technovation, 36-37, 12-25. [CrossRef]
- Yeung, N. (2019). Forcing PhD students to publish is bad for science. Nature Human Behaviour, 3(10), 1036-1036. [CrossRef]
- Yin, R. K. (2018). Case study research and applications: Design and methods (6th ed.). Thousand Oaks, CA: SAGE publications.
- York, A. S., & Ahn, M. J. (2012). University technology transfer office success factors: A comparative case study. International Journal of Technology Transfer and Commercialisation (1/2). Retrieved from https://www.researchgate.net/profile/Mark_Ahn2/publication/264820471_University_technology_transfer_office_success_factors_a_comparative_case_study/links/5629991508aef25a243d818f/University-technology-transfer-office-success-factors-a-comparative-case-study.pdf.
- Zider, B. (1998). How venture capital works. Harvard Business Review, 76(6), 131-139.
| 1 |
The author presented and justified this definition his dissertation titled The Influence of Technology Maturity Level on the Incidence of University Technology Transfer and the Implications for Public Policy and Practice. |
| 2 |
The term “loonshot” appears to be a portmanteau that combines the term “loony”, which is an adjective meaning crazy or foolish, and “moonshot”, which is a reference to an extremely ambitious but risky project (Bachall, 2019; Merriam-Webster, 2021a; Merriam-Webster, 2021b). |
| 3 |
The Form 5500 Series return is an annual report about employee benefits plans that is mandated by the federal government. It includes information about the number of participants in a company's employee benefit program which can be used as a proxy for the number of employees. The return is filed with the U.S. Department of Labor and accessible at https://www.efast.dol.gov/5500search (U.S. Dept. of Labor, n.d.). |
| 4 |
STEM is an acronym for science, technology, engineering, and mathematics. |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).