Submitted:
02 March 2023
Posted:
06 March 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Models and Services
2.1. Microsoft Azure Services
2.2. Microsoft Azure Models
- 1)
- public
- 2)
- private
- 3)
- hybrid cloud
2.2.1. Public Cloud
2.2.2. Private cloud
2.2.3. A hybrid cloud
2.3. AWS Services
2.3.1. Infrastructure as a Service (IaaS)
2.3.2. Platforms as a service (PaaS)
2.3.3. software as a service (SaaS)
2.4. AWS Models
2.4.1. Cloud
2.4.2. Hybrid
2.4.3. On-premises
2.5. Google Cloud Models and Services
- Access to IT infrastructure services like computation, capacity, organizing, and virtualization is given through framework as a benefit (IaaS). It gives you the foremost control over your IT resources and is the foremost comparative to ordinary on-premises IT
- All the computer hardware and software capital required for the creation of cloud applications are provided via the platform as a service (PaaS). With PaaS, businesses can completely concentrate on developing applications without having to worry about managing and maintaining the supporting infrastructure.
- Software as a Service (SaaS) offers the whole application stack, from the supporting foundation to upkeep and overhauls for the app computer program, as a benefit. A SaaS arrangement is as often as possible an end-user application where the cloud benefit supplier oversees and keeps up both the foundation and the benefit.[35,36,37,38]
3. Load Balancing
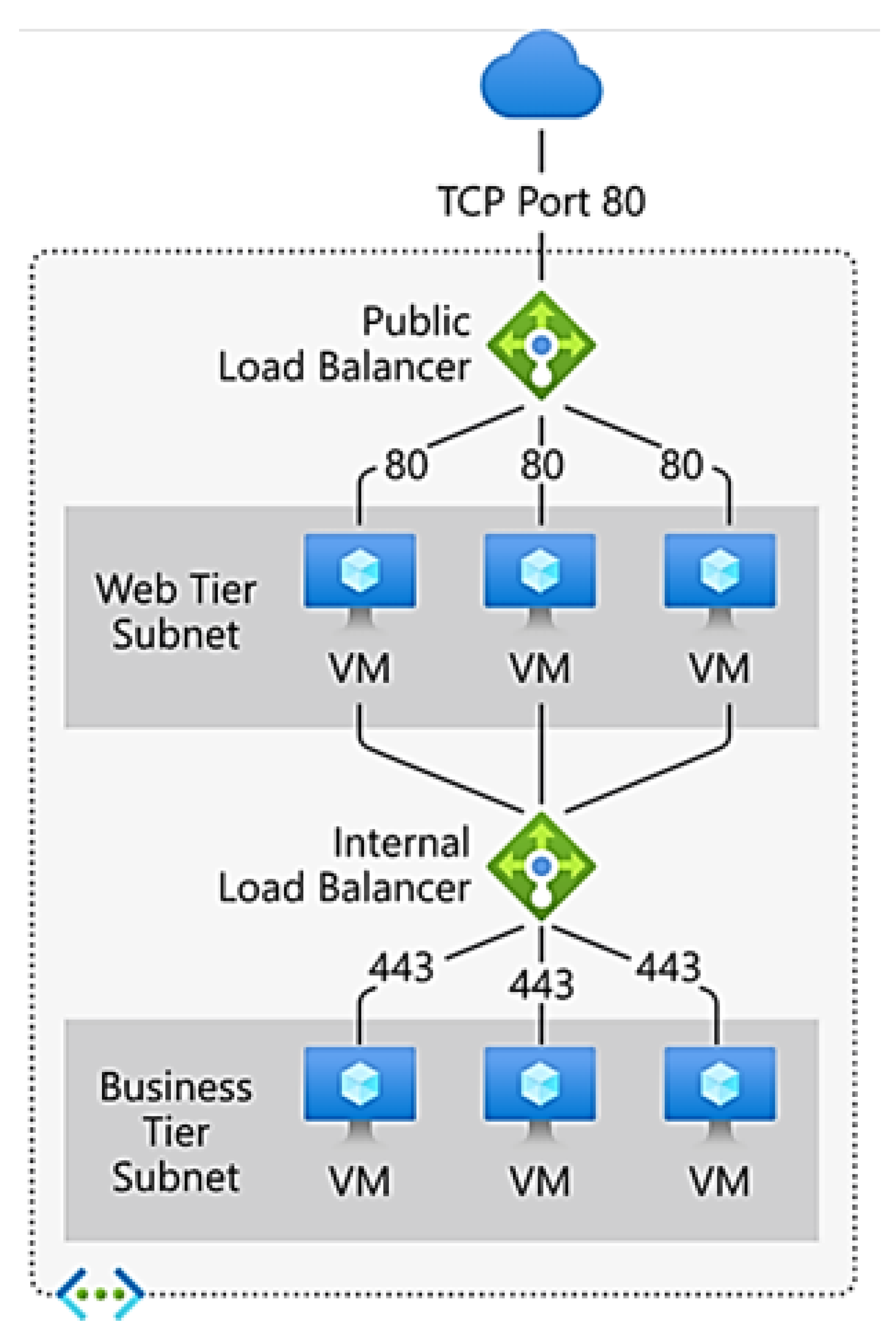
3.1. Azure Load Balancing
- Public load balancer: Connections for virtual machines within a virtual network can be made using a public load balancer. This feature is enabled by converting private IP addresses into public ones. The load balancer is then used to balance the traffic between your virtual machines and the internet.
- Internal (or private) load balancer Private IPs are required at the front end when using an internal load balancer. These are then used inside a virtual network to carry out load-balancing operations. A load balancer can be accessed from a hybrid network
3.2. AWS Load Balancing
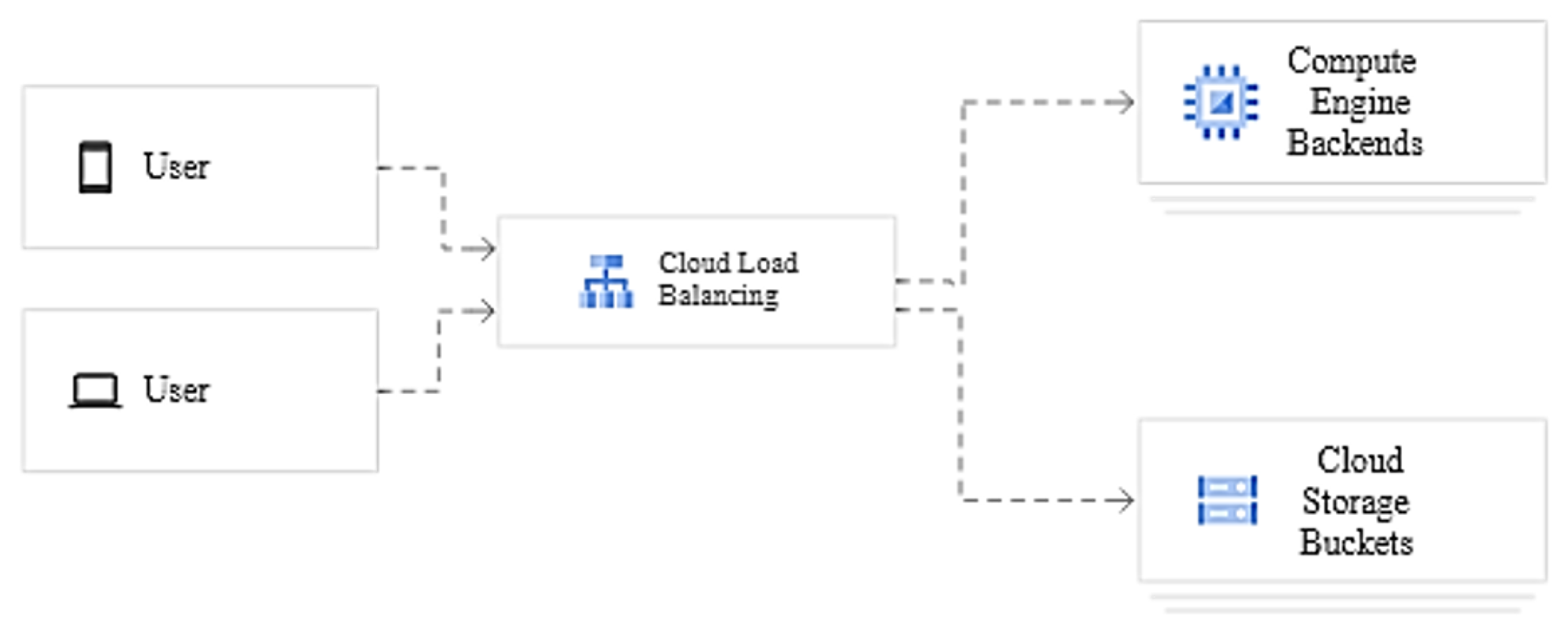
3.3. Google Cloud Load Balancing
4. Cloud Security
4.1. Security in Google Cloud
- 1-
- Virtual Private Cloud (VPC): With virtual networking, networks may be segmented and secured more effectively.
- 2-
- Data Encryption: In GCP, data is encrypted both in transit and at rest.
- 3-
- Access to logs in almost real-time to improve security visibility.
- 4-
- Only trusted containers are allowed to be installed on the Kubernetes Engine due to binary authorization. Intrusion Detection System (IDS): Cloud-native threat detection.
- 5-
- Protect sensitive data from leakage by preventing data loss.
- 6-
- Web app and API protection: DDoS mitigation, WAF, bot defense, and API security
4.2. Security in AWS
- Identify and access management: You’ll be able safely oversee personalities, resources, and authorizations at scale with the assistance of AWS Character Administrations. To urge begun rapidly and control get to to your workloads and apps, AWS offers personality administrations for your workforce and customer-facing applications.
- Detection: By persistently watching the arrange action and account behavior inside your cloud environment, AWS recognizes dangers.
- Network and application protection: You’ll actualize fine-grained security approach at arrange control focuses all through your organization by utilizing organize and application protection administrations. You’ll be able utilize AWS administrations to look at and channel activity at the have-, arrange-, and application-level boundaries to halt illicit asset get to.
- Data Protection: You’ll utilize AWS administrations to defend your information, accounts, and workloads against illicit get to. In arrange to persistently screen and protect your accounts and workloads, AWS information security administrations offer encryption, key administration, and risk location.
- Compliance: Based on the AWS best hones and industry measures your organization follows to, AWS gives you with a careful see of your compliance status and persistently screens your environment.
5. Database Technology
5.1. AWS
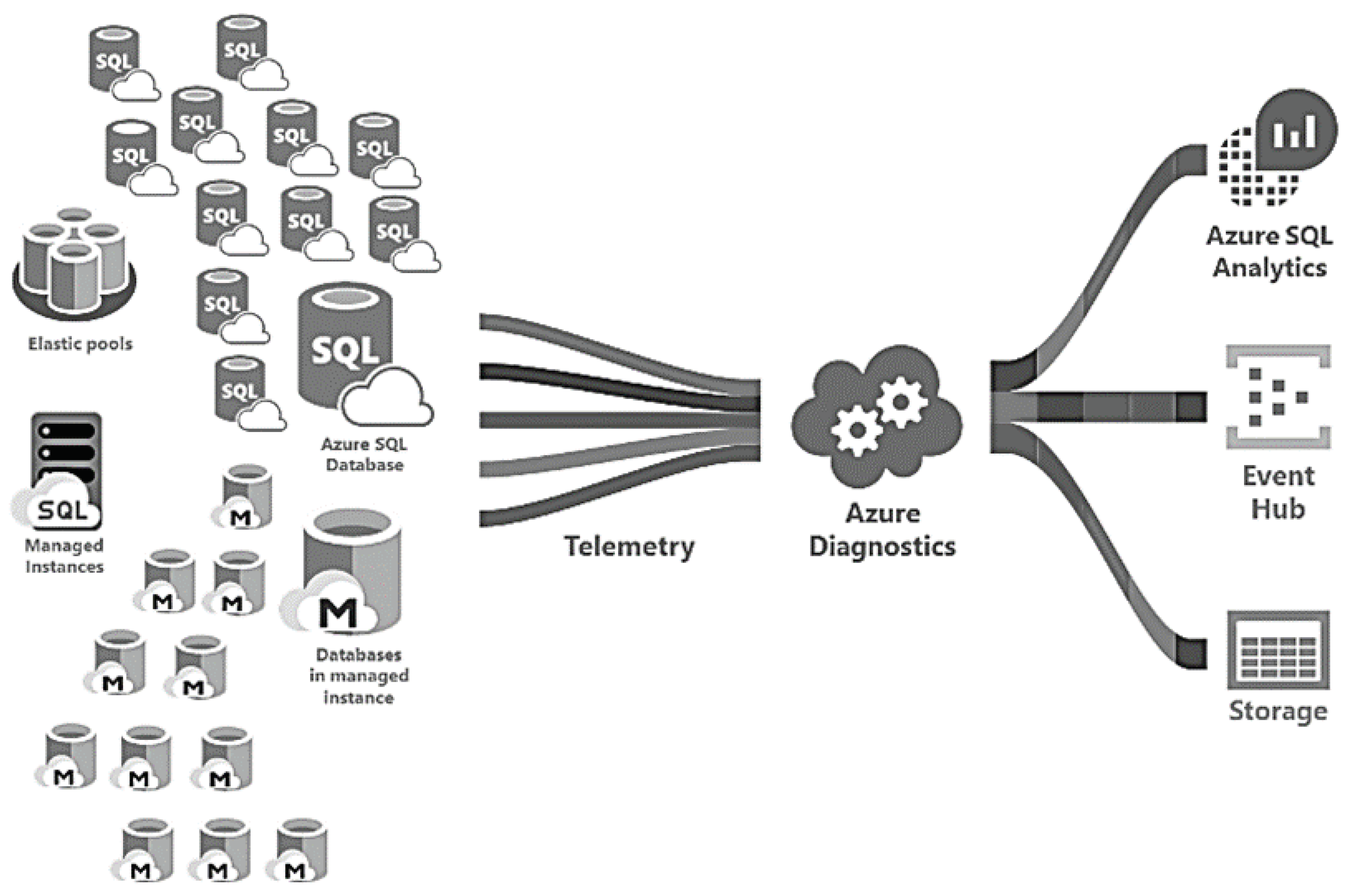
5.2. Azure
5.3. Google
6. Conclusions
Acknowledgments
References
- Ucuz, D.; others. Comparison of the IoT platform vendors, microsoft Azure, Amazon web services, and Google cloud, from users’ perspectives. 2020 8th International Symposium on Digital Forensics and Security (ISDFS). IEEE, 2020, pp. 1–4.
- Gorelik, E. Cloud computing models. PhD thesis, Massachusetts Institute of Technology, 2013.
- Abousamra, R.; Hosam, O. Quantitative Classification of Cognitive Behaviors for Industrial Projects’ Managers in the MENA Region. 8th International Conference on Information Technology Trends (ITT. IEEE, 2022. [CrossRef]
- Hosam, O.; Abousamra, R. Enhancing Deep Training of Image Landmarking with Image CAPTCHA. 8th International Conference on Information Technology Trends (ITT. IEEE, 2022. [CrossRef]
- Kundra, V. Federal cloud computing strategy. White House 2011. [Google Scholar]
- Gupta, P.; Seetharaman, A.; Raj, J.R. The usage and adoption of cloud computing by small and medium businesses. International journal of information management 2013, 33, 861–874. [Google Scholar] [CrossRef]
- Hosam, O.; BinYuan, F. A Comprehensive Analysis of Trusted Execution Environments. 8th International Conference on Information Technology Trends (ITT. IEEE, 2022. [CrossRef]
- Hosam, O. An earthquake query system based on hidden Markov models. International Journal of Embedded Systems 2022, 15, 149–157. [Google Scholar] [CrossRef]
- Berisha, B.; Mëziu, E.; Shabani, I. Big data analytics in Cloud computing: an overview. Journal of Cloud Computing 2022, 11, 1–10. [Google Scholar] [CrossRef] [PubMed]
- Liu, B.; Xiao, L.; Long, J.; Tang, M.; Hosam, O. Secure Digital Certificate-Based Data Access Control Scheme in Blockchain. IEEE Access 2020, 8, 91751–91760. [Google Scholar] [CrossRef]
- Lei, Q.; Xiao, L.; Hosam, O.; Luo, H. A novel watermarking algorithm based on characteristics model of local fragmentary images. International Journal of Embedded Systems 2020, 12, 11–21. [Google Scholar] [CrossRef]
- Copeland, M.; Soh, J.; Puca, A.; Manning, M.; Gollob, D. Microsoft azure and cloud computing. In Microsoft Azure; Springer, 2015; pp. 3–26.
- Hosam, O. Intelligent Risk Management using Artificial Intelligence. Advances in Science and Engineering Technology International Conferences (ASET, 2022, pp. 1–9. [CrossRef]
- Hu, J.; Liang, W.; Hosam, O.; Hsieh, M.; Su, X. 5GSS: a framework for 5G-secure-smart healthcare monitoring. Connection Science 2021, p. 1–23. [CrossRef]
- Youssef, A.E. Exploring cloud computing services and applications. Journal of Emerging Trends in Computing and Information Sciences 2012, 3, 838–847. [Google Scholar]
- Ali, M.; Jung, L.T.; Hosam, O. A new text-based w-distance metric to find the perfect match between words. Journal of Intelligent and Fuzzy Systems 2019, 9, 1–12. [Google Scholar] [CrossRef]
- Hany, M.; Youssef, B.; Darwish, S.; Hosam, O. Intelligent Watermarking System Based on Soft Computing. International Conference on Advanced Intelligent Systems and Informatics; Springer: Cham, 2019; pp. 24–34. [Google Scholar] [CrossRef]
- Hosam, O.; M, H. Modified Fast Gray Level Grouping Approach for Enhancing Image Contrast. Journal of Theoretical and Applied Information Technology 2019, 97.
- Wankhede, P.; Talati, M.; Chinchamalatpure, R. Comparative study of cloud platforms-microsoft azure, google cloud platform and amazon EC2. J. Res. Eng. Appl. Sci 2020, 5, 60–64. [Google Scholar] [CrossRef]
- Huang, W.; Li, R.; Xu, J.; Huang, Y.; Hosam, O. Intellectual property protection for FPGA designs using the public key cryptography. Advances in Mechanical Engineering 2019, 11, 16–22. [Google Scholar] [CrossRef]
- Hosam, O. Hiding Bitcoins in Steganographic Fractals. 2018 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT. IEEE, 2018. [CrossRef]
- Hosam, O. Toxic Comments Identification in Arabic Social Media. International Journal of Computer Information Systems and Industrial Management Applications 2019, 11, 219–226. [Google Scholar]
- Azure, M. What is a private cloud? Retrieved July 7, 2017.
- Chen, Y.; Xiao, L.; Hosam, O. A Performance Evaluation Method of Coal-Fired Boiler Based on Neural Network. International Conference on Smart Computing and Communication; Springer: Cham, 2019; pp. 277–285. [Google Scholar] [CrossRef]
- Ahmad, M.H.; Hosam, O. Hybrid design for cloud data security using combination of AES, ECC and LSB steganography. International Journal of Computational Science and Engineering (IJCSE 2019, 19. [Google Scholar] [CrossRef]
- Zhu, W.; Hosam, O.; Zheng, X. A secure hierarchical community detection algorithm. International Journal of Computational Science and Engineering (IJCSE) 2019, 19. [Google Scholar] [CrossRef]
- Golden, B. Amazon web services for dummies; John Wiley & Sons, 2013.
- Liang, W.; Xie, Y.; Chen, X.; Hosam, O.; Chen. A Two-step MF Signal Acquisition Method for Wireless Underground Sensor Networks. Computer Science and Information Systems 2016, 13. [CrossRef]
- Hosam, O.; Ben Halima, N. Adaptive block-based pixel value differencing steganography. Security Comm. Networks 2016. [Google Scholar] [CrossRef]
- Hosam, O. Colored Texture Classification with Support Vector Machine and Wavelet Multiresolution Analysis. The IEEE Symposium on Signal Processing and Information Technology (ISSPIT’05, 2015. Abu Dabhi, UAE. [CrossRef]
- Wang, L.C.; Chen, C.C.; Liu, J.L.; Chu, P.C. Framework and deployment of a cloud-based advanced planning and scheduling system. Robotics and Computer-Integrated Manufacturing 2021, 70, 102088. [Google Scholar] [CrossRef]
- Halima, N.B.; Hosam, O. Bag of Words Based Surveillance System Using Support Vector Machines. International Journal of Security and Its Applications 2016, 10, 331–346. [Google Scholar] [CrossRef]
- Hosam, O.; Halima, N.B. A HYBRID ROI-EMBEDDINGBASED WATERMARKING TECHNIQUE USING DWT AND DCT TRANSFORMS. Journal of Theoretical and Applied Information Technology 2015, 81. [Google Scholar]
- Halima, N.B.; Hosam, O. Embedding Image ROI Watermark Into Median DCT Coefficients. IRECOS 2015, 10. [Google Scholar] [CrossRef]
- Varia, J.; Mathew, S.; et al. Overview of amazon web services. Amazon Web Services 2014, 105. [Google Scholar]
- Hosam, O. Car License Plate Localization Using Hole Filling and Support Vector Machine. International Review on Computers and Software (IRECOS 2014, 9. [Google Scholar] [CrossRef]
- Hosam, O.; Halima, N.B.; Dakroury, S.; Abdel-Rahman, E.O. RECONSTRUCTING, AUGMENTING AND MANIPULATING 3D SCENE FROM SEQUENCE OF IMAGES. Journal of Theoretical and Applied Information Technology 2017, 73, 12–17. [Google Scholar]
- Hosam, O.; Malki, Z. Steganography Technique for Embedding Secure Data into the Image Regions with Abrupt Changes. Life Sci J 2014, 11, 126–130. [Google Scholar]
- Anupama, K.; Nagaraja, R.; Jaiganesh, M. A Perspective view of Resource-based Capacity planning in Cloud computing. 2019 1st International Conference on Advances in Information Technology (ICAIT). IEEE, 2019, pp. 358–363.
- Hosam, O.; Yang, L.; Liang, W.; Sun, X. Watermarking 3D Triangular Mesh with High Visual Quality. JDCTA: International Journal of Digital Content Technology and its Applications 2010, 4, 107–116. [Google Scholar] [CrossRef]
- O. Hosam, X.S. Three Dimensional Reconstruction Using Enhanced Shape From Stereo Technique. the proceeding of “2009 Eight IEEE/ACIS International Conference on Computer and Information Science”, 2009, p. 627–632. [CrossRef]
- Alam, T. Cloud Computing and its role in Information Technology. IAIC Transactions on Sustainable Digital Innovation (ITSDI) 2020, 1, 108–115. [Google Scholar] [CrossRef]
- O. Hosam, W.; Youssef, B.A.; Abdou, M. Public Watermarking Scheme for 3Ds Laser Scanned Archeological Models. The Seventeenth IEEE Symposium on Computers and Communications (ISCC’12); Cappadocia: Turkey, 2012. [CrossRef]
- Hosam, O. Motion Compensation for Video Codec Based on Disparity Estimation. The Seventeenth IEEE Symposium on Computers and Communications (ISCC’12); Cappadocia: Turkey, 2012. [CrossRef]
- O. Hosam, X.S. Stereo Image Reconstruction Using Adaptive Window Approach. the proceeding of 2nd International Conference on Advanced Computer Theory and Engineering, ICACTE2009, 2009, p. 33–41. [CrossRef]
- Perumal, K.; Mohan, S.; Frnda, J.; Divakarachari, P.B. Dynamic resource provisioning and secured file sharing using virtualization in cloud azure. Journal of Cloud Computing 2022, 11, 1–12. [Google Scholar] [CrossRef]
- Liang, W.; Zhang, D.; You, Z.; Li, W.; Hosam, O. A Survey of Techniques for VLSI IP Protection. Information Technology Journal 2013. published June 12, 2013.
- Hosam, O.; Alraddadi, A.S. Novel Image Watermarking Technique Based on Adjacent Pixel Position Switch. JNIT 2013, 4, 81–88. [Google Scholar] [CrossRef]
- Hosam, O. Side-Informed Image Watermarking Scheme Based on Dither Modulation in the Frequency Domain. The Open Signal Processing Journal 2013, 5, 1–6. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




