Submitted:
01 May 2023
Posted:
02 May 2023
You are already at the latest version
Abstract
Keywords:
Introduction
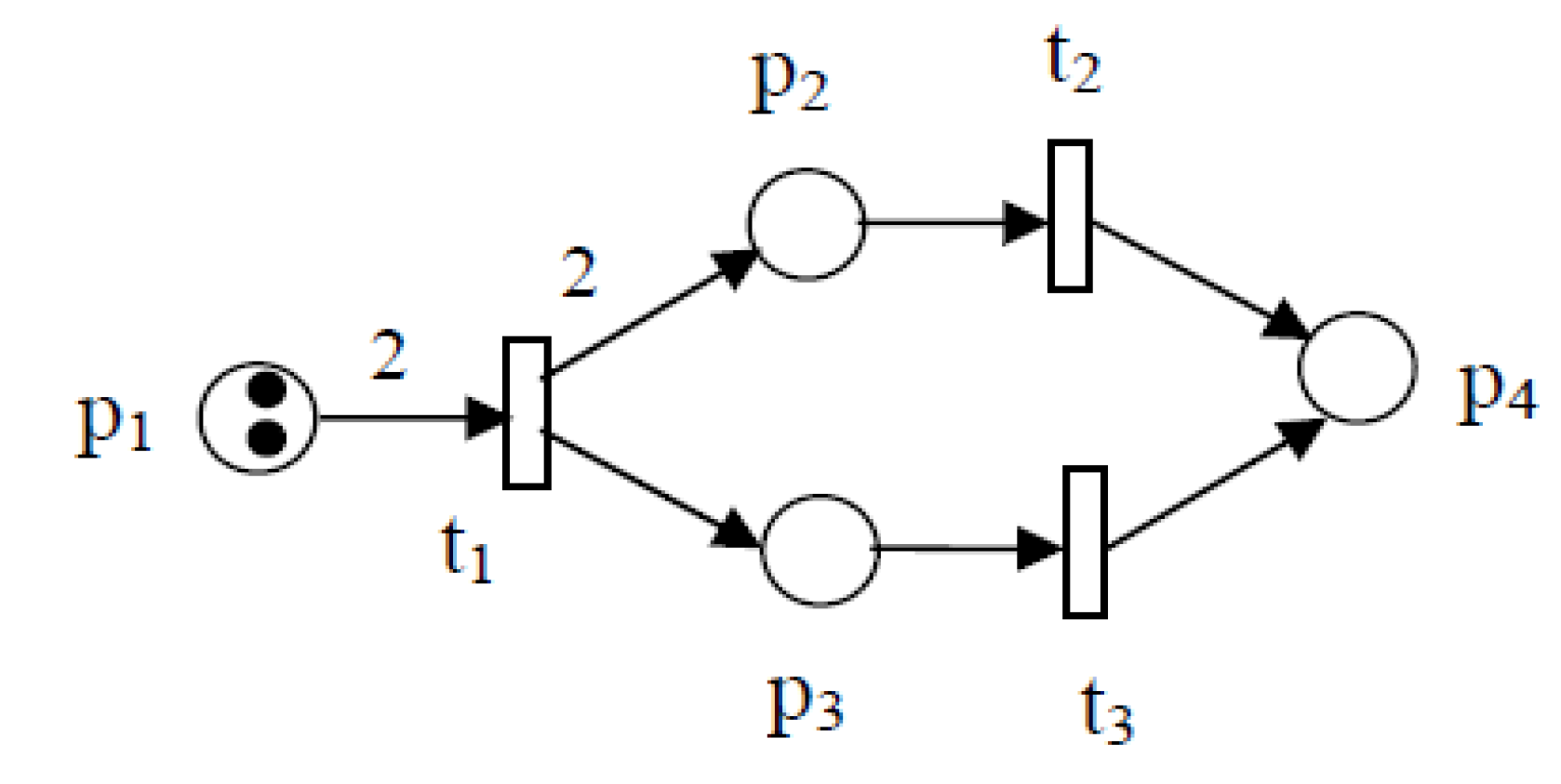
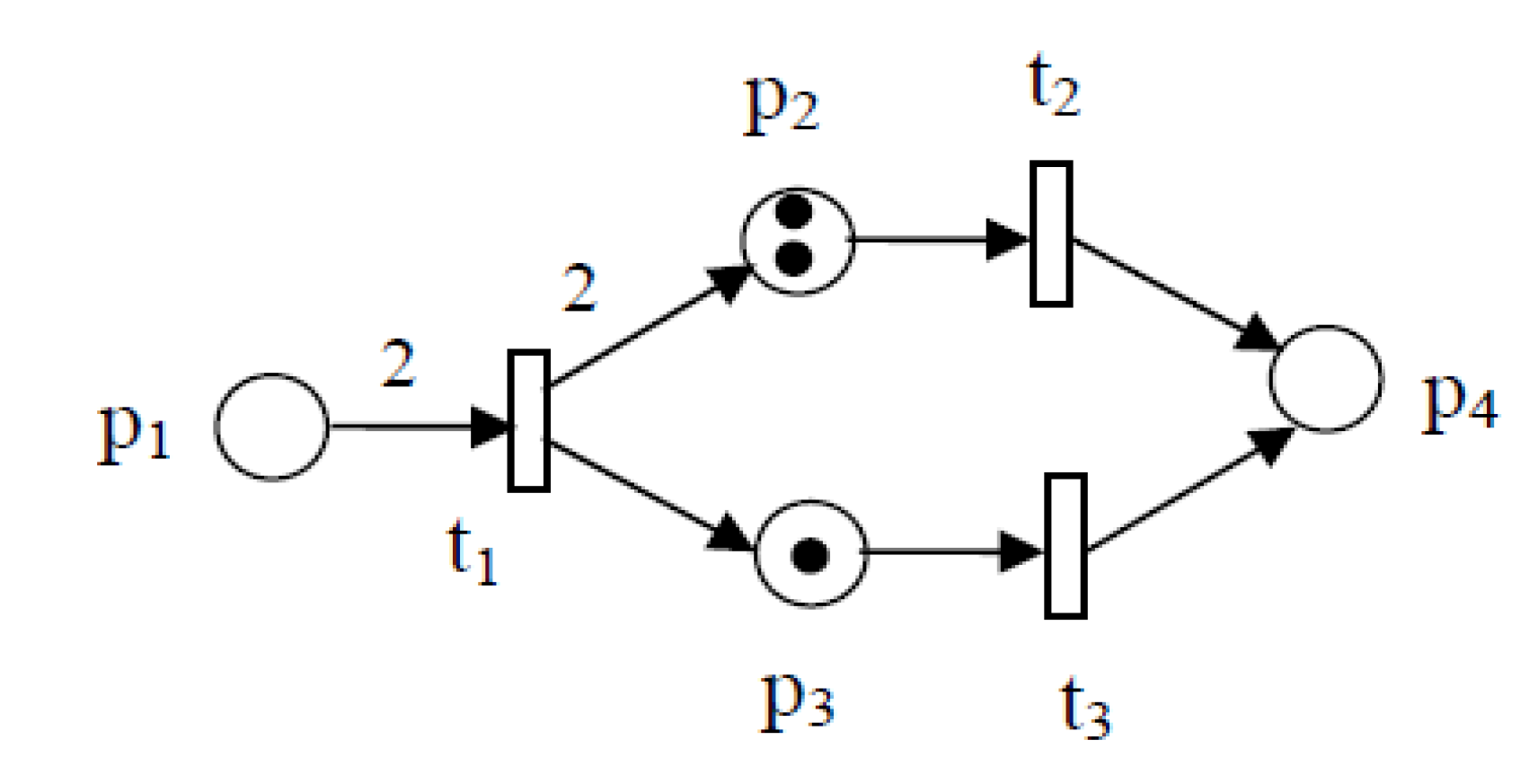
1. Mathematical Foundations
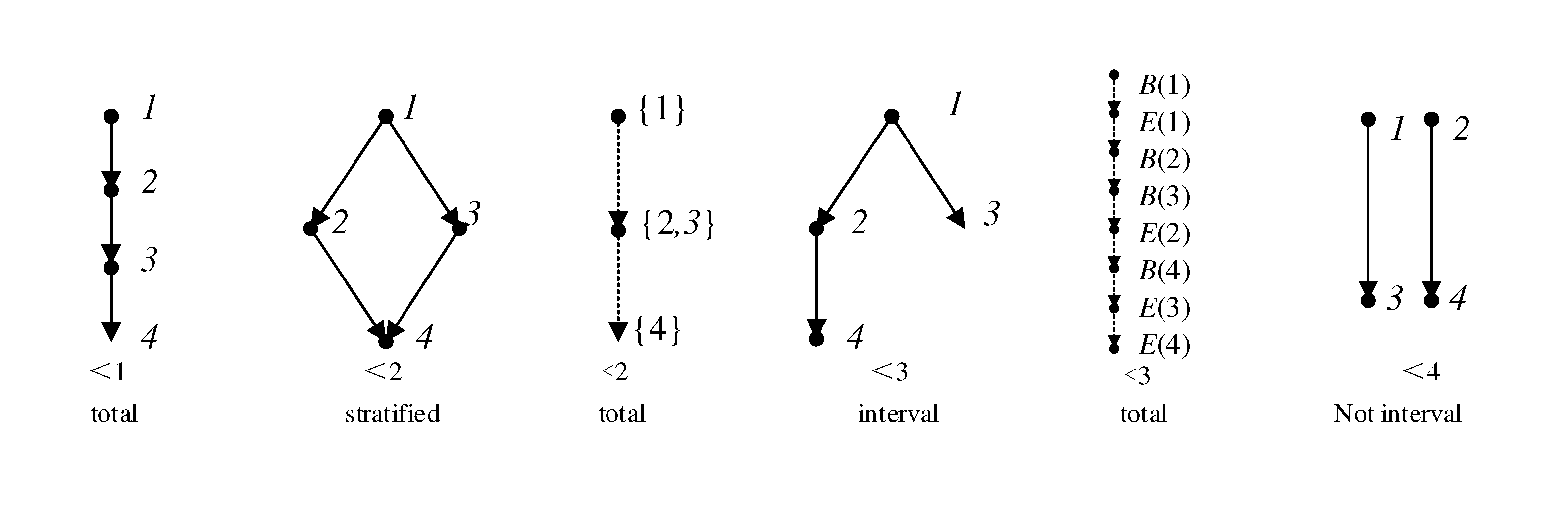
1.1. Partial orders,Stratified order and Interval order
1.2. Mazurkiewicz Traces
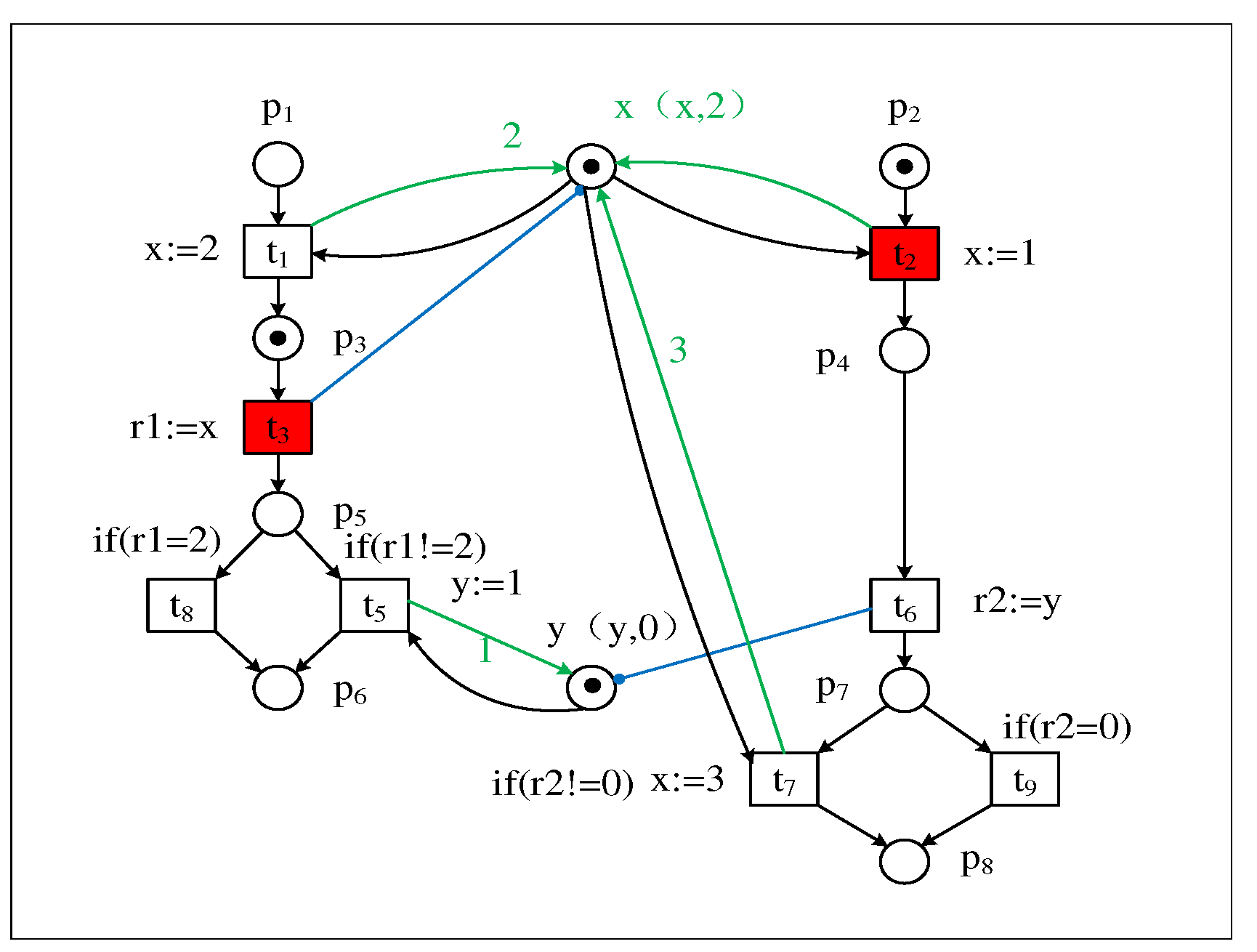
2. The proposed model
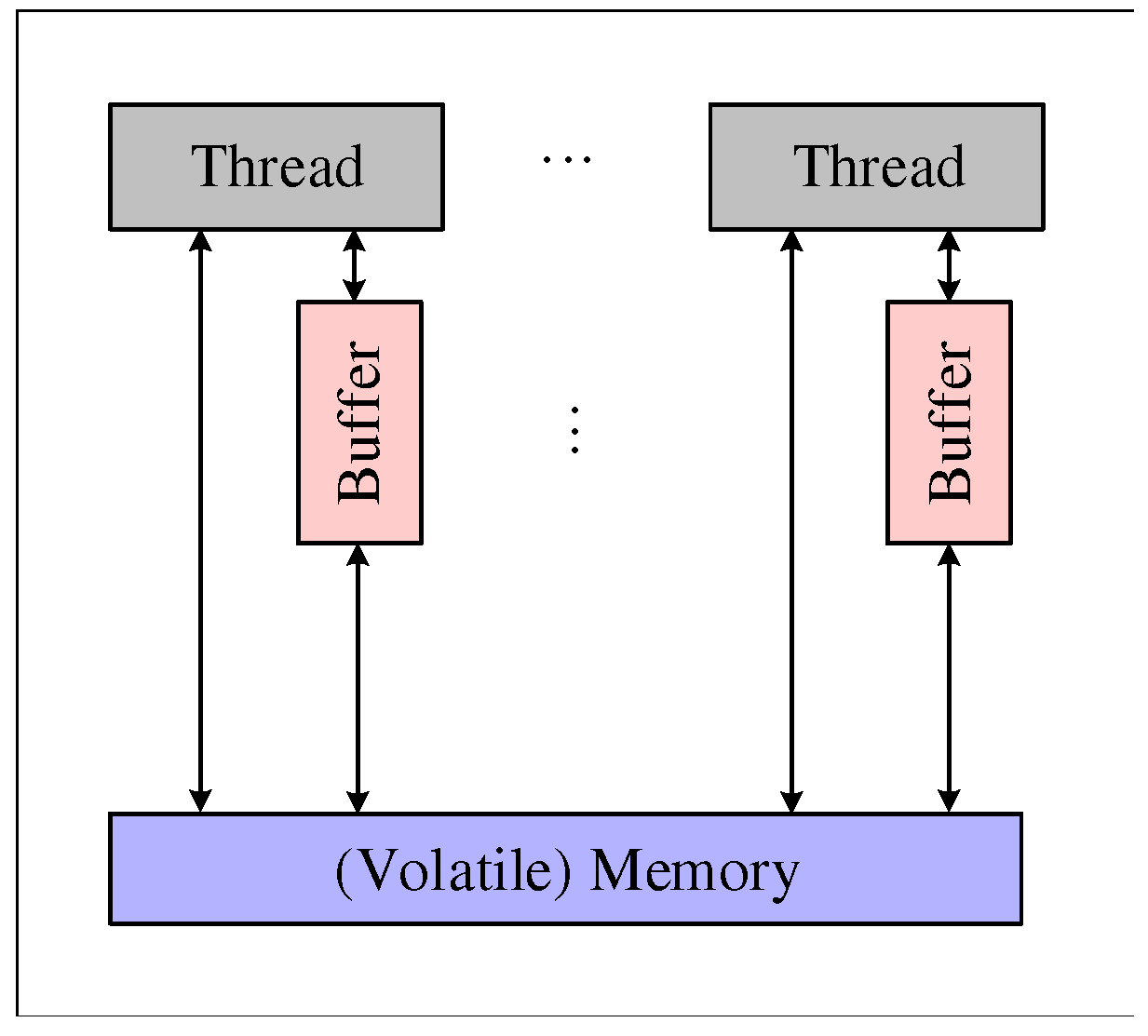
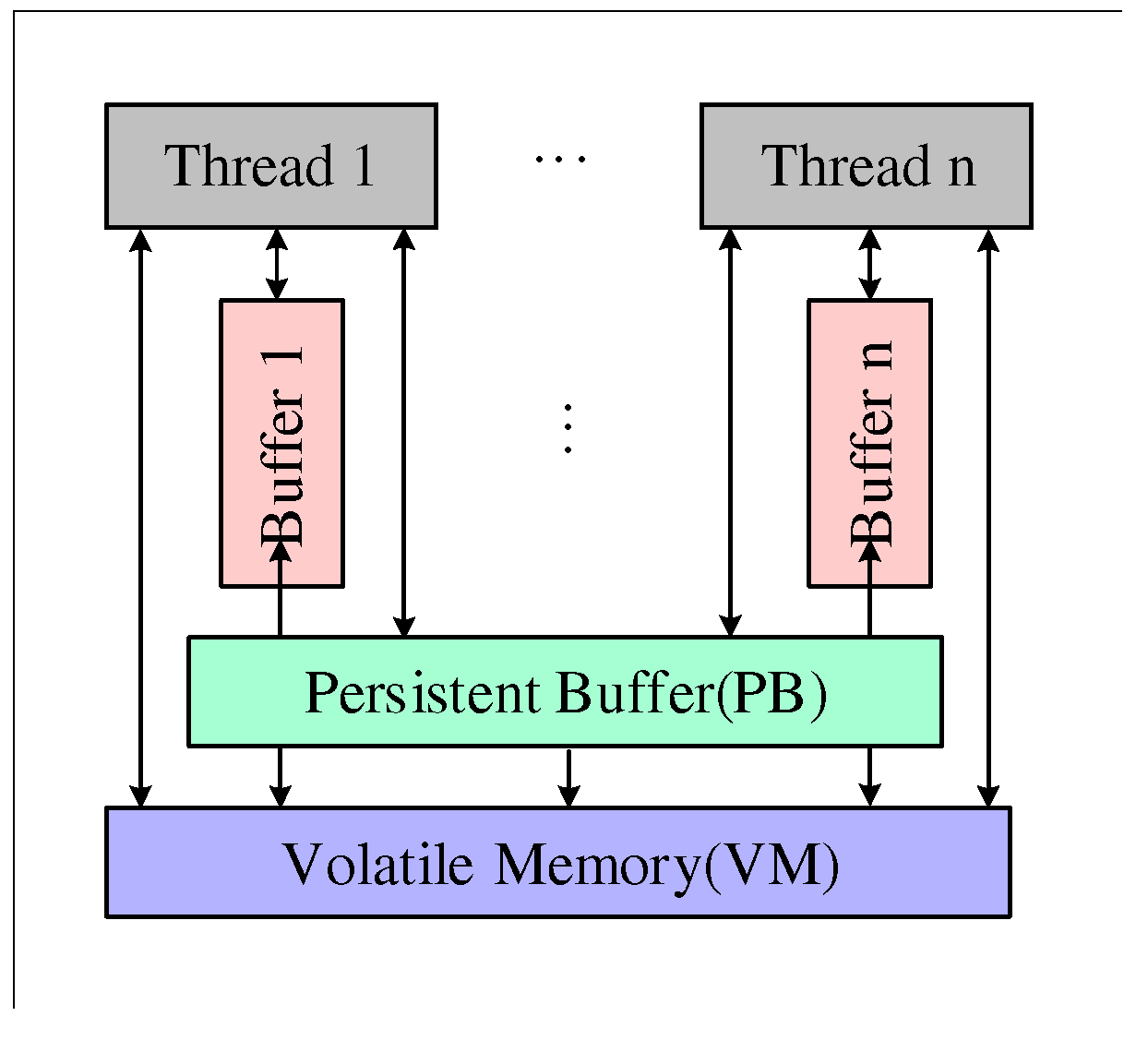
2.1. Multithreaded system
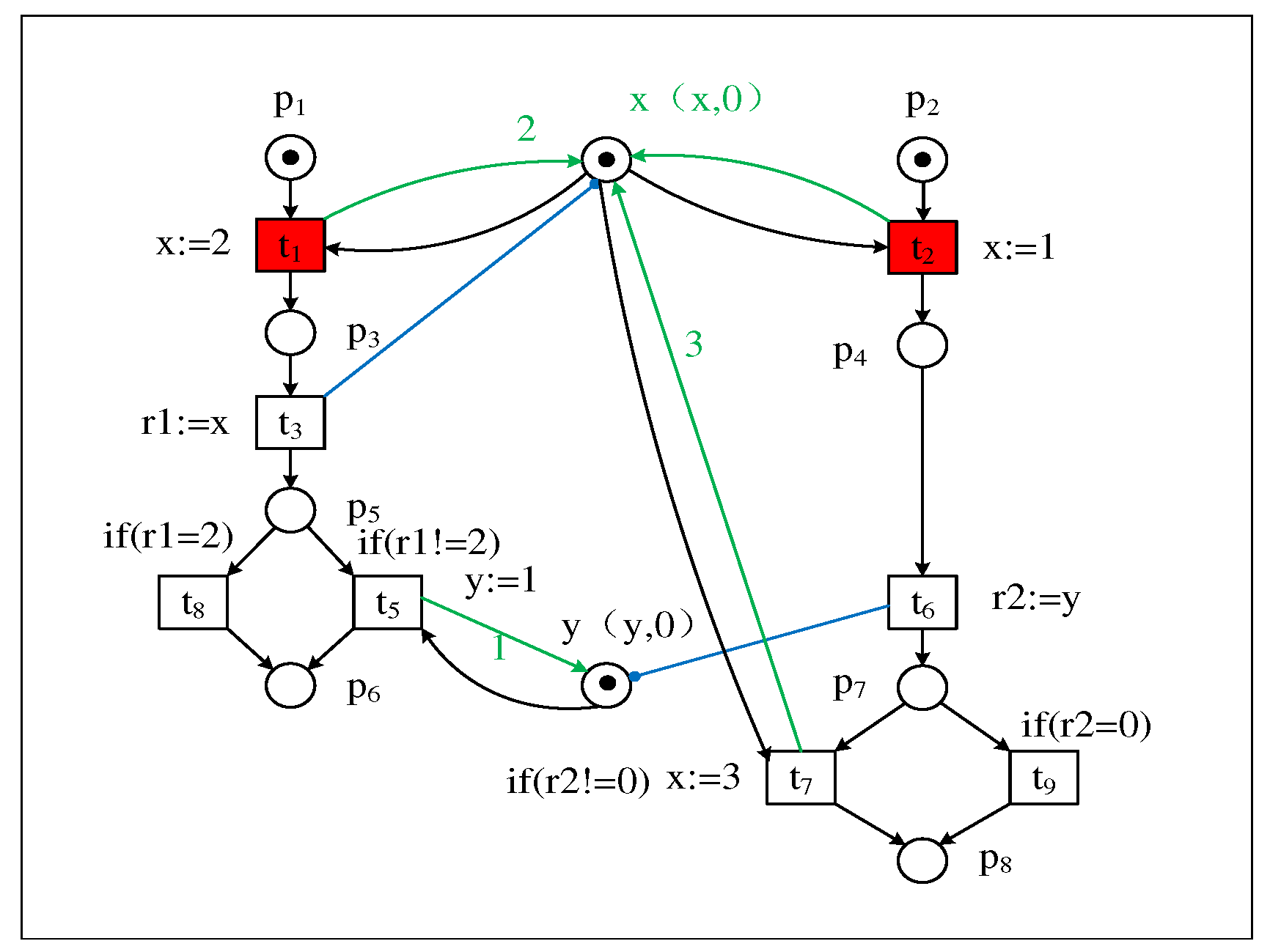
2.2. Petri net with read-write data
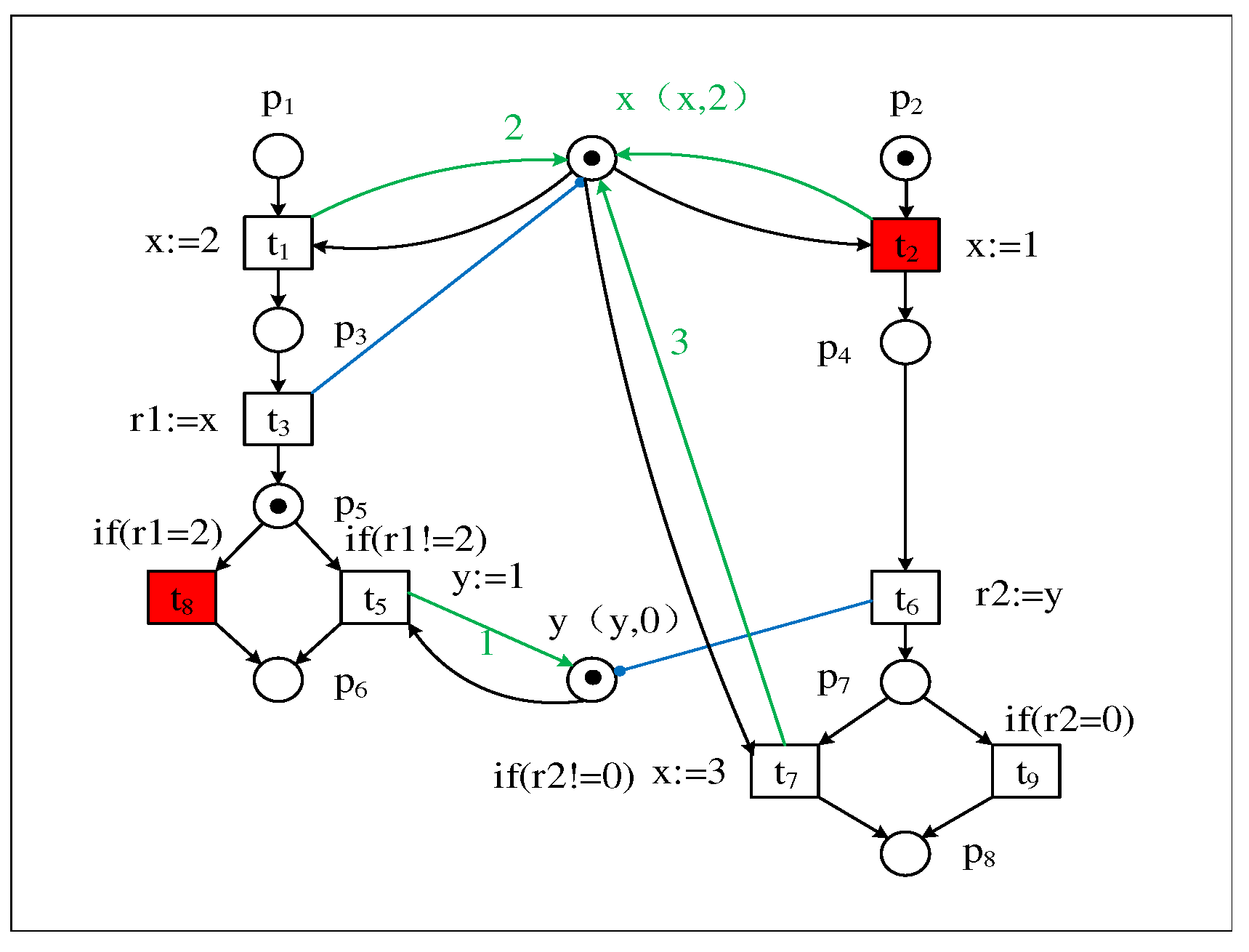
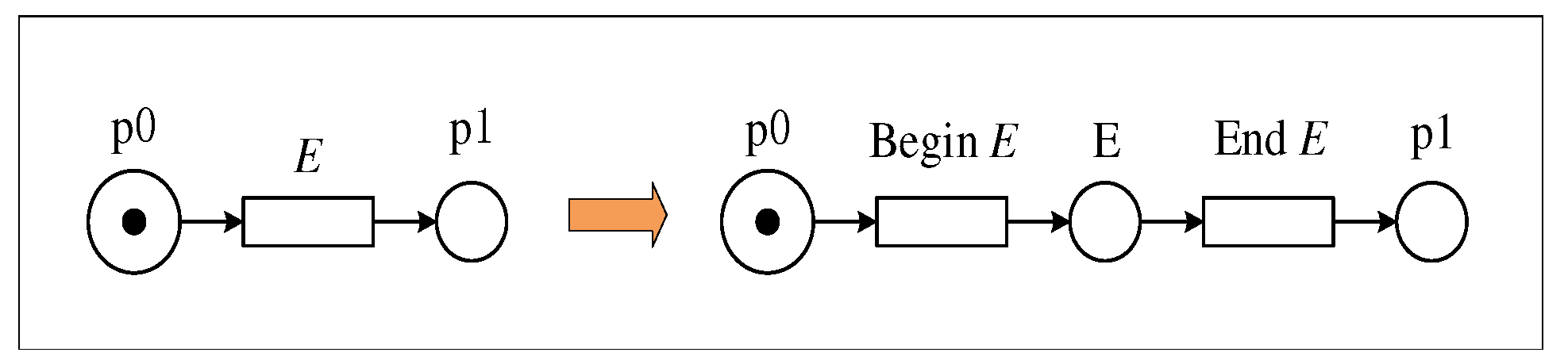
3. Convert the writing event to the Beginning and Ending event
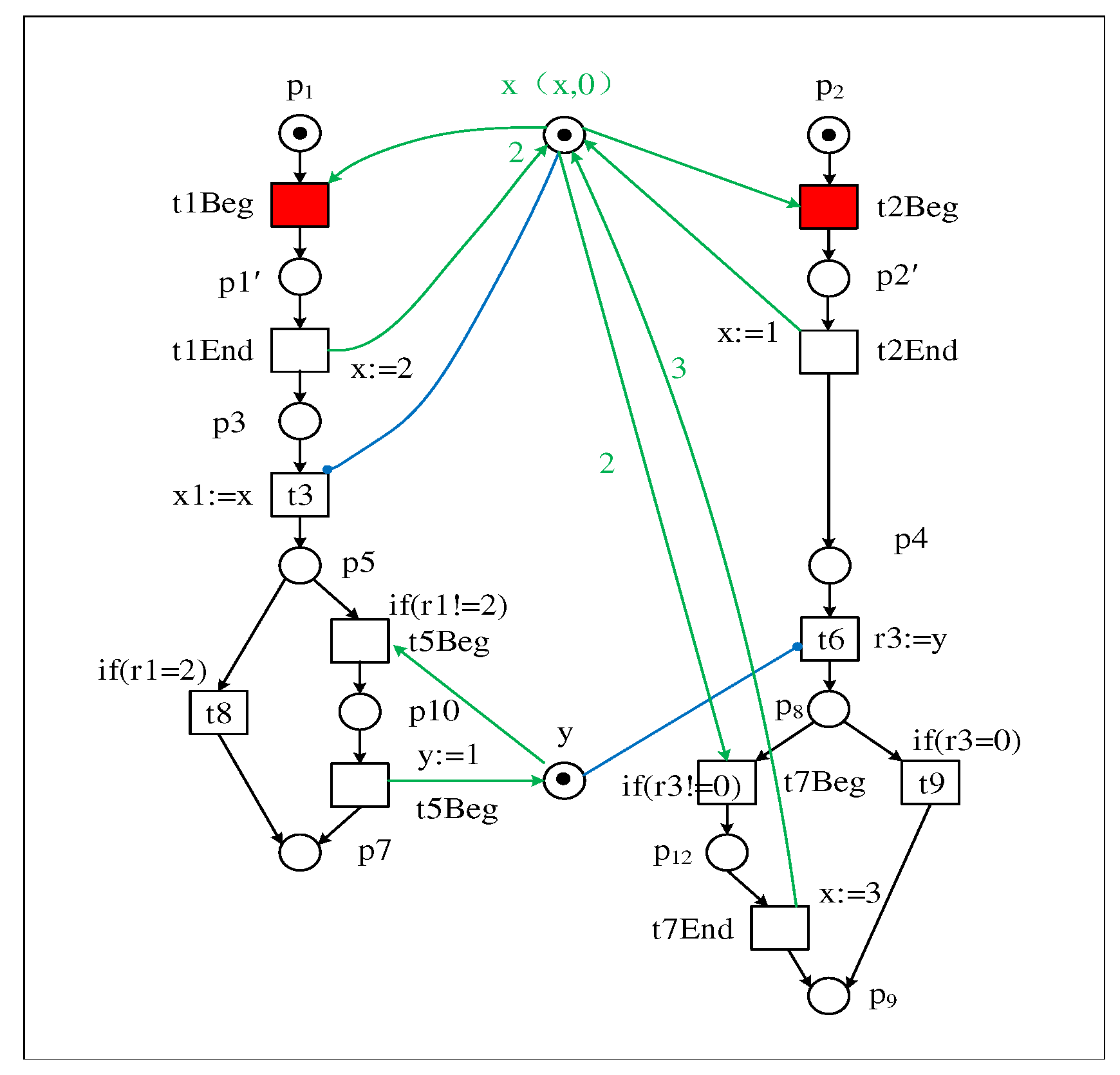
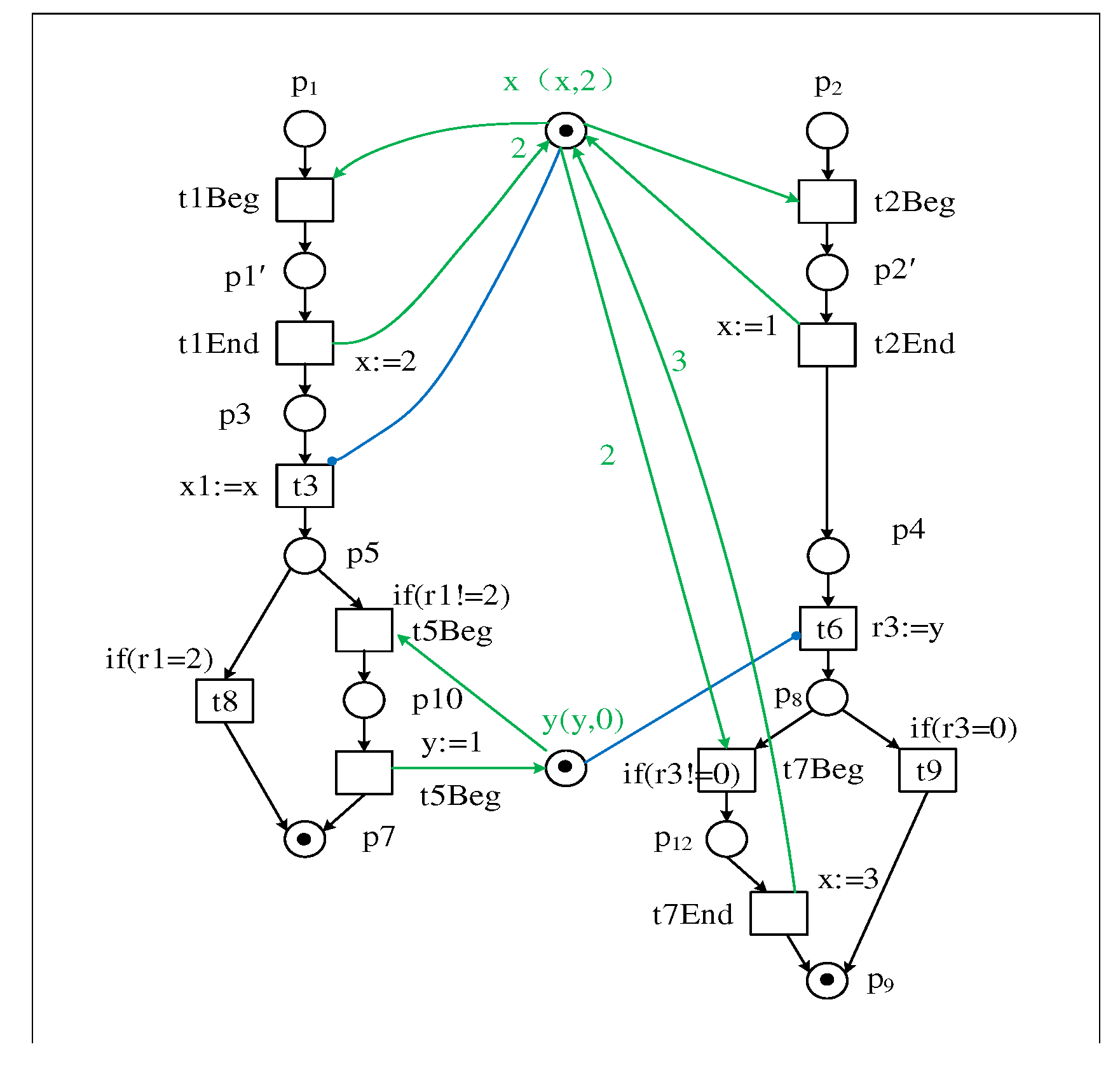
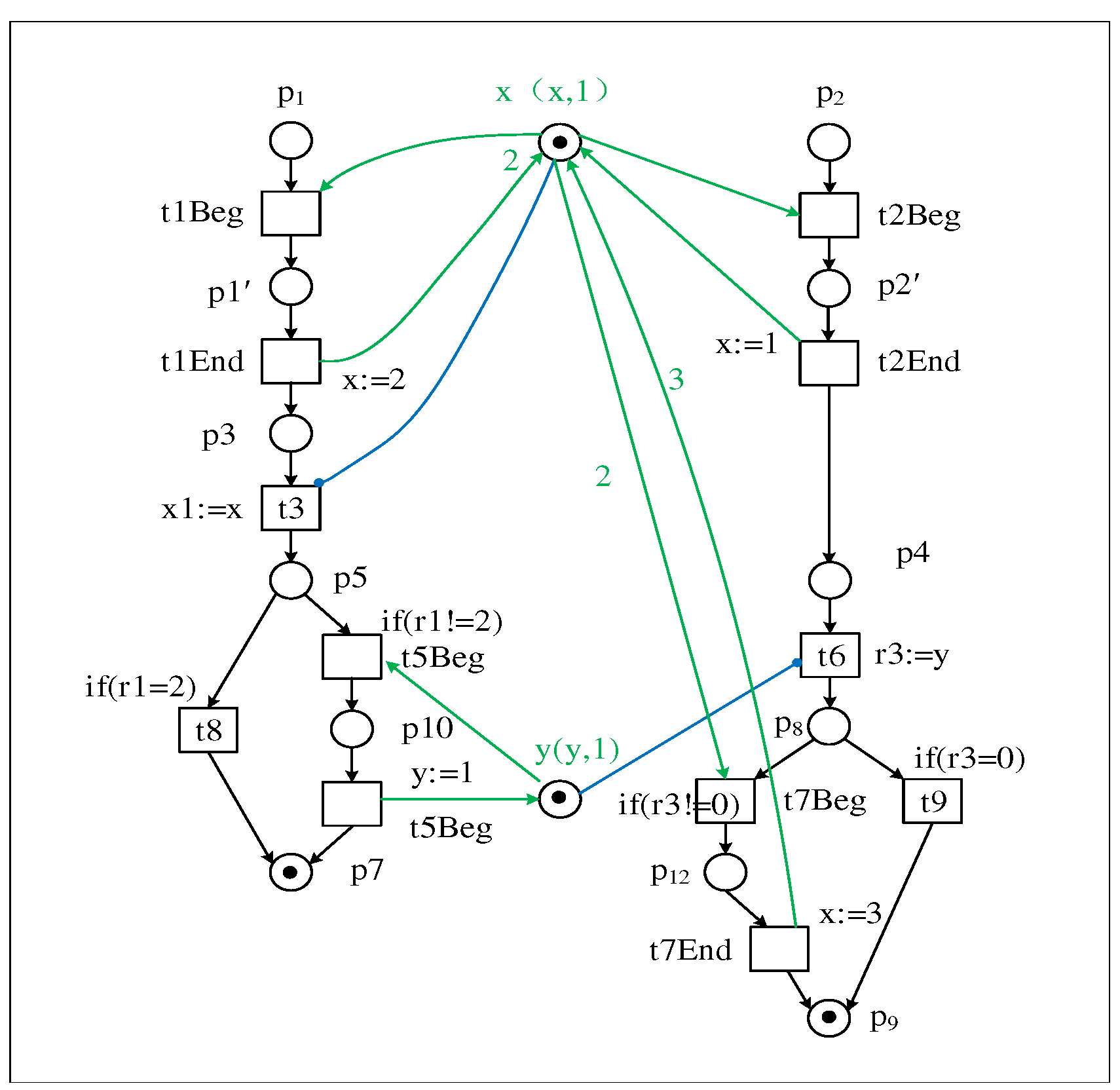
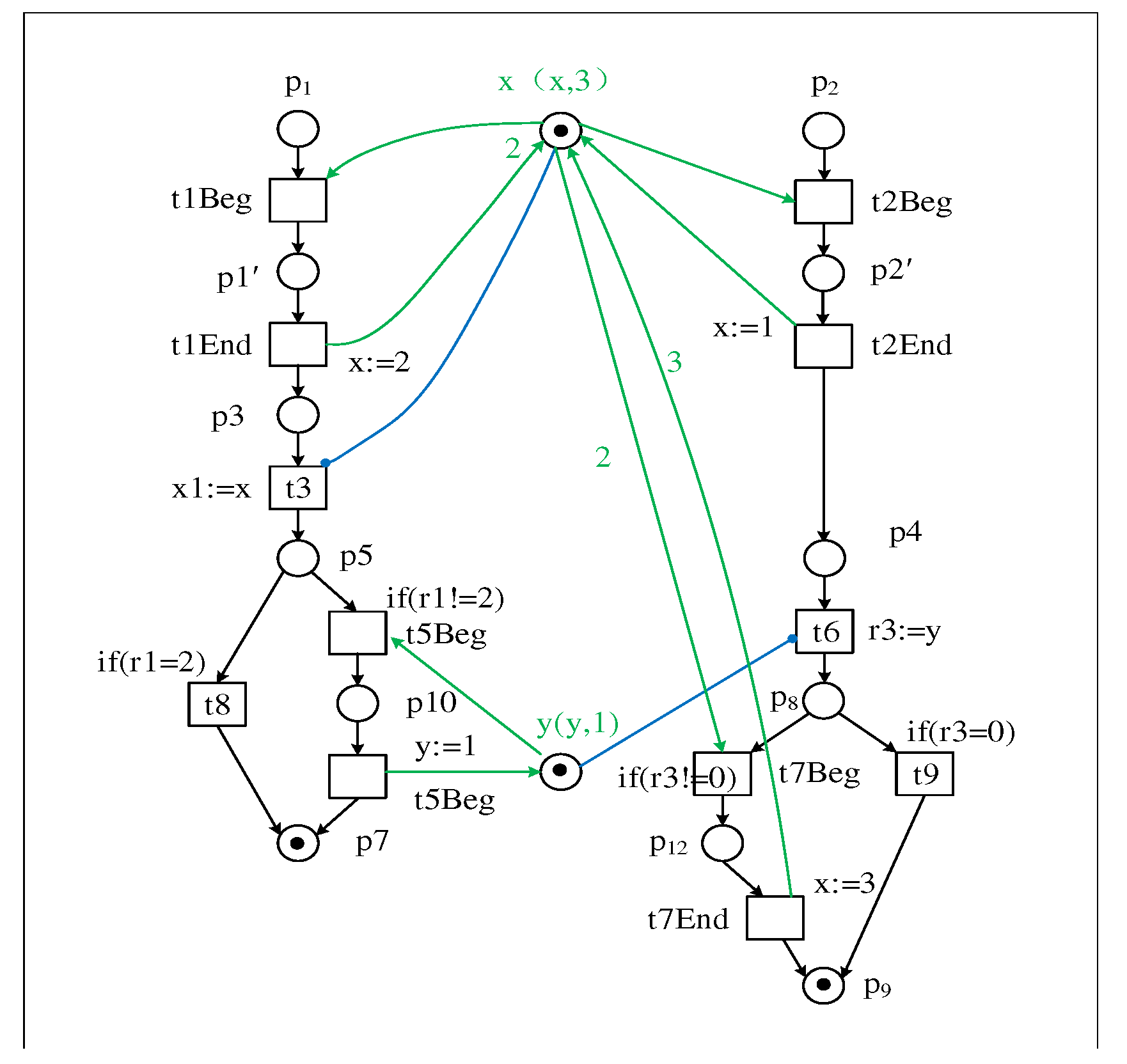
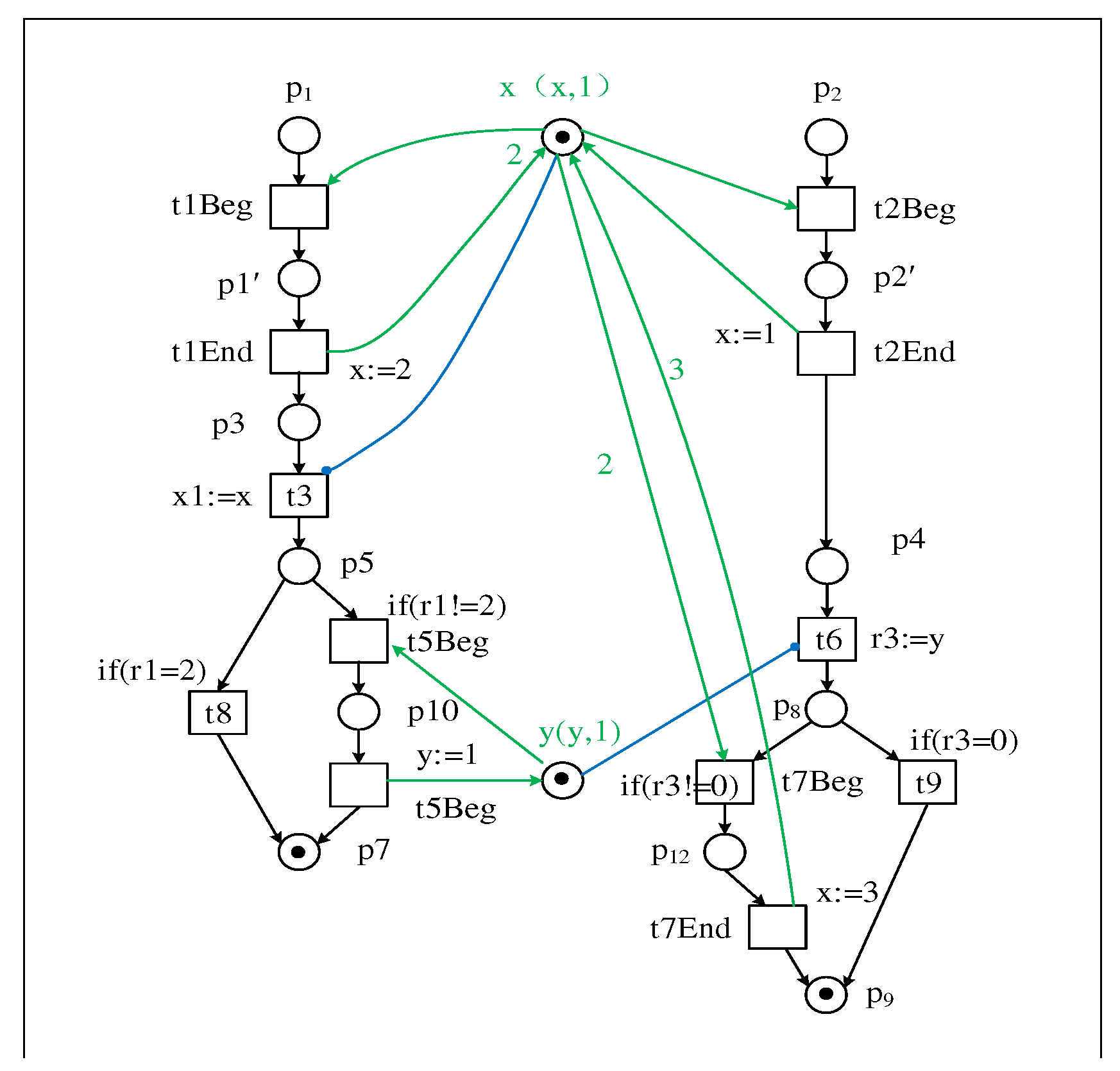
| Firing trace of transition | |
|---|---|
| T1 : Bt1, Et1, Bt2, Et2, t3, Bt5, Et5, t6, Bt7, Et7 | |
4. Conclusion
Funding
References
- Alglave, J.; Deacon, W.; Grisenthwaite, R.; Hacquard, A.; Maranget, L. Armed Cats: Formal Concurrency Modelling at Arm. ACM Trans. Program. Lang. Syst. 2021, 43, 8:1–8:54. [Google Scholar] [CrossRef]
- Alglave, J.; Kroening, D.; Nimal, V.; Poetzl, D. Don’t Sit on the Fence: A Static Analysis Approach to Automatic Fence Insertion. ACM Trans. Program. Lang. Syst. 2017, 39, 6:1–6:38. [Google Scholar] [CrossRef]
- Alglave, J.; Cousot, P. Ogre and Pythia: an invariance proof method for weak consistency models. Proceedings of the 44th ACM SIGPLAN Symposium on Principles of Programming Languages, POPL 2017, Paris, France, January 18-20, 2017; Castagna, G.; Gordon, A.D., Eds. ACM, 2017, pp. 3–18. [CrossRef]
- Janicki, R.; Kleijn, J.; Koutny, M.; Mikulski, L. Paradigms of Concurrency - Observations, Behaviours, and Systems - a Petri Net View; Vol. 1020, Studies in Computational Intelligence, Springer, 2022. [CrossRef]
- Janicki, R.; Koutny, M. Operational Semantics, Interval Orders and Sequences of Antichains. Fundam. Informaticae 2019, 169, 31–55. [Google Scholar] [CrossRef]
- Horn, A.; Alglave, J. Concurrent Kleene Algebra of Partial Strings. CoRR 2014, abs/1407.0385.
- Lutz-Ley, A.; López-Mellado, E. Stability Analysis of Discrete Event Systems Modeled by Petri Nets Using Unfoldings. IEEE Trans Autom. Sci. Eng. 2018, 15, 1964–1971. [Google Scholar] [CrossRef]
- de Visme, M.; Winskel, G. Causal Unfoldings. 8th Conference on Algebra and Coalgebra in Computer Science, CALCO 2019, June 3-6, 2019, London, United Kingdom; Roggenbach, M.; Sokolova, A., Eds. Schloss Dagstuhl - Leibniz-Zentrum für Informatik, 2019, Vol. 139, LIPIcs, pp. 9:1–9:18. [CrossRef]
- Janicki, R.; Kleijn, J.; Koutny, M.; Mikulski, L. Relational structures for concurrent behaviours. Theor. Comput. Sci. 2021, 862, 174–192. [Google Scholar] [CrossRef]
- Rodríguez, C. Verification based on unfoldings of Petri nets with read arcs. (Vérification à l’aide de dépliages de réseaux de Petri étendus avec des arcs de lecture). PhD thesis, École normale supérieure de Cachan, Paris, France, 2013.
- Baldan, P.; Bruni, R.; Corradini, A.; Gadducci, F.; Melgratti, H.C.; Montanari, U. Event Structures for Petri nets with Persistence. Log. Methods Comput. Sci. 2018, 14. [Google Scholar] [CrossRef]
- Baldan, P.; Gorla, D.; Padoan, T.; Salvo, I. Characterising spectra of equivalences for event structures, logically. Inf. Comput. 2022, 285, 104887. [Google Scholar] [CrossRef]
- Baldan, P.; Corradini, A.; Gadducci, F. Concurrent semantics for fusions: Weak prime domains and connected event structures. Inf. Comput. 2021, 281, 104770. [Google Scholar] [CrossRef]
- Kähkönen, K.; Heljanko, K. Testing Multithreaded Programs with Contextual Unfoldings and Dynamic Symbolic Execution. 14th International Conference on Application of Concurrency to System Design, ACSD 2014, Tunis La Marsa, Tunisia, June 23-27, 2014. IEEE Computer Society, 2014, pp. 142–151. [CrossRef]
- Janicki, R. On Interval Semantics of Inhibitor and Activator Nets. Application and Theory of Petri Nets and Concurrency - 40th International Conference, PETRI NETS 2019, Aachen, Germany, June 23-28, 2019, Proceedings; Donatelli, S.; Haar, S., Eds. Springer, 2019, Vol. 11522, Lecture Notes in Computer Science, pp. 192–212. [CrossRef]
- Gondelman, L.; Gregersen, S.O.; Nieto, A.; Timany, A.; Birkedal, L. Distributed causal memory: modular specification and verification in higher-order distributed separation logic. Proc. ACM Program. Lang. 2021, 5, 1–29. [Google Scholar] [CrossRef]
- Coti, C.; Petrucci, L.; Rodríguez, C.; Sousa, M. Quasi-optimal partial order reduction. Formal Methods Syst. Des. 2021, 57, 3–33. [Google Scholar] [CrossRef]
- Schemmel, D.; Büning, J.; Rodríguez, C.; Laprell, D.; Wehrle, K. Symbolic Partial-Order Execution for Testing Multi-Threaded Programs. Computer Aided Verification - 32nd International Conference, CAV 2020, Los Angeles, CA, USA, July 21-24, 2020, Proceedings, Part I; Lahiri, S.K.; Wang, C., Eds. Springer, 2020, Vol. 12224, Lecture Notes in Computer Science, pp. 376–400. [CrossRef]
- Nguyen, H.T.T.; Rodríguez, C.; Sousa, M.; Coti, C.; Petrucci, L. Quasi-Optimal Partial Order Reduction. Computer Aided Verification - 30th International Conference, CAV 2018, Held as Part of the Federated Logic Conference, FloC 2018, Oxford, UK, July 14-17, 2018, Proceedings, Part II; Chockler, H.; Weissenbacher, G., Eds. Springer, 2018, Vol. 10982, Lecture Notes in Computer Science, pp. 354–371. [CrossRef]
- Sousa, M.; Rodríguez, C.; D’Silva, V.V.; Kroening, D. Abstract Interpretation with Unfoldings. Computer Aided Verification - 29th International Conference, CAV 2017, Heidelberg, Germany, July 24-28, 2017, Proceedings, Part II; Majumdar, R.; Kuncak, V., Eds. Springer, 2017, Vol. 10427, Lecture Notes in Computer Science, pp. 197–216. [CrossRef]
- Xiang, D.; Liu, G.; Yan, C.; Jiang, C. Detecting data-flow errors based on Petri nets with data operations. IEEE/CAA Journal of Automatica Sinica 2018, 5, 251–260. [Google Scholar] [CrossRef]
- Zhao, F.; Xiang, D.; Liu, G.; Jiang, C. A New Method for Measuring the Behavioral Consistency Degree of WF-Net Systems. IEEE Transactions on Computational Social Systems 2022, 9, 480–493. [Google Scholar] [CrossRef]
- Xiang, D.; Liu, G.; Yan, C.; Jiang, C. Checking the Inconsistent Data in Concurrent Systems by Petri Nets with Data Operations. 2016 IEEE 22nd International Conference on Parallel and Distributed Systems (ICPADS), 2016, pp. 501–508. [CrossRef]
- Huang, Z.; Xu, X.; Zhu, H.; Zhou, M. An Efficient Group Recommendation Model With Multiattention-Based Neural Networks. IEEE Transactions on Neural Networks and Learning Systems 2020, 31, 4461–4474. [Google Scholar] [CrossRef] [PubMed]
- Zhu, H.; Liu, G.; Zhou, M.; Xie, Y.; Kang, Q. Dandelion Algorithm With Probability-Based Mutation. IEEE Access 2019, 7, 97974–97985. [Google Scholar] [CrossRef]
- He, L.; Liu, G.; Zhou, M. Petri-Net-Based Model Checking for Privacy-Critical Multiagent Systems. IEEE Transactions on Computational Social Systems 2022, pp. 1–14. [CrossRef]
- He, L.; Liu, G. Model Checking CTLK Based on Knowledge-Oriented Petri Nets. 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), 2019, pp. 1139–1146. [CrossRef]
- Tao, X.; Liu, G.; Yang, B.; Yan, C.; Jiang, C. Workflow Nets With Tables and Their Soundness. IEEE Transactions on Industrial Informatics 2020, 16, 1503–1515. [Google Scholar] [CrossRef]
- Yu, W.; Yan, C.G.; Ding, Z.; Jiang, C.; Zhou, M. Modeling and Verification of Online Shopping Business Processes by Considering Malicious Behavior Patterns. IEEE Transactions on Automation Science and Engineering 2016, 13, 647–662. [Google Scholar] [CrossRef]
- Yu, W.; Yan, C.; Ding, Z.; Jiang, C.; Zhou, M. Analyzing E-Commerce Business Process Nets via Incidence Matrix and Reduction. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2018, 48, 130–141. [Google Scholar] [CrossRef]
- Wang, M.; Ding, Z.; Zhao, P.; Yu, W.; Jiang, C. A Dynamic Data Slice Approach to the Vulnerability Analysis of E-Commerce Systems. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2020, 50, 3598–3612. [Google Scholar] [CrossRef]
- Ding, Z.; Wang, S.; Jiang, C. Kubernetes-Oriented Microservice Placement with Dynamic Resource Allocation. IEEE Transactions on Cloud Computing 2022, pp. 1–1. [CrossRef]
- Wang, C.; Wang, C.; Zhu, H.; Cui, J. LAW: Learning Automatic Windows for Online Payment Fraud Detection. IEEE Transactions on Dependable and Secure Computing 2021, 18, 2122–2135. [Google Scholar] [CrossRef]
- Cui, J.; Yan, C.; Wang, C. ReMEMBeR: Ranking Metric Embedding-Based Multicontextual Behavior Profiling for Online Banking Fraud Detection. IEEE Transactions on Computational Social Systems 2021, 8, 643–654. [Google Scholar] [CrossRef]
- Chen, X.; Wang, C.; Cui, J.; Yang, Q.; Teng, H.; Jiang, C. Incorporating Prior Knowledge in Local Differentially Private Data Collection for Frequency Estimation. IEEE Transactions on Big Data 2022, pp. 1–13. [CrossRef]
- Wang, C.; Yang, B.; Cui, J.; Wang, C. Fusing Behavioral Projection Models for Identity Theft Detection in Online Social Networks. IEEE Transactions on Computational Social Systems 2019, 6, 637–648. [Google Scholar] [CrossRef]
- Liang, Y.; Li, M.; Jiang, C.; Liu, G. CEModule: A Computation Efficient Module for Lightweight Convolutional Neural Networks. IEEE Transactions on Neural Networks and Learning Systems 2021, pp. 1–12. [CrossRef]
- Janicki, R.; Mikulski, L. Algebraic Structure of Step Traces and Interval Traces. Fundam. Informaticae 2020, 175, 253–280. [Google Scholar] [CrossRef]
- Lahav, O.; Boker, U. Decidable verification under a causally consistent shared memory. Proceedings of the 41st ACM SIGPLAN International Conference on Programming Language Design and Implementation, PLDI 2020, London, UK, June 15-20, 2020; Donaldson, A.F.; Torlak, E., Eds. ACM, 2020, pp. 211–226. [CrossRef]
- Lahav, O.; Boker, U. What’s Decidable About Causally Consistent Shared Memory? ACM Trans. Program. Lang. Syst. 2022, 44, 8:1–8:55. [Google Scholar] [CrossRef]
- Lahav, O.; Namakonov, E.; Oberhauser, J.; Podkopaev, A.; Vafeiadis, V. Making weak memory models fair. Proc. ACM Program. Lang. 2021, 5, 1–27. [Google Scholar] [CrossRef]
- Khyzha, A.; Lahav, O. Taming x86-TSO persistency. Proc. ACM Program. Lang. 2021, 5, 1–29. [Google Scholar] [CrossRef]
- Cho, M.; Lee, S.; Hur, C.; Lahav, O. Modular data-race-freedom guarantees in the promising semantics. PLDI ’21: 42nd ACM SIGPLAN International Conference on Programming Language Design and Implementation, Virtual Event, Canada, June 20-25, 2021; Freund, S.N.; Yahav, E., Eds. ACM, 2021, pp. 867–882. [CrossRef]
- Wang, P.; Ding, Z.; Jiang, C.; Zhou, M. Constraint-Aware Approach to Web Service Composition. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2014, 44, 770–784. [Google Scholar] [CrossRef]
- Wang, P.; Ding, Z.; Jiang, C.; Zhou, M.; Zheng, Y. Automatic Web Service Composition Based on Uncertainty Execution Effects. IEEE Transactions on Services Computing 2016, 9, 551–565. [Google Scholar] [CrossRef]
- Kähkönen, K.; Heljanko, K. Testing Multithreaded Programs with Contextual Unfoldings and Dynamic Symbolic Execution. 2014 14th International Conference on Application of Concurrency to System Design, 2014, pp. 142–151. [CrossRef]
- Lutz-Ley, A.; López-Mellado, E. Stability Analysis of Discrete Event Systems Modeled by Petri Nets Using Unfoldings. IEEE Transactions on Automation Science and Engineering 2018, 15, 1964–1971. [Google Scholar] [CrossRef]
- André, E.; Chatain, T.; Rodríguez, C. Preserving Partial-Order Runs in Parametric Time Petri Nets. ACM Trans. Embed. Comput. Syst. 2016, 16. [Google Scholar] [CrossRef]
- Xie, Y.; Liu, G.; Yan, C.; Jiang, C.; Zhou, M.; Li, M. Learning Transactional Behavioral Representations for Credit Card Fraud Detection. IEEE Transactions on Neural Networks and Learning Systems 2022, pp. 1–14. [CrossRef]
- Xie, Y.; Liu, G.; Yan, C.; Jiang, C.; Zhou, M. Time-Aware Attention-Based Gated Network for Credit Card Fraud Detection by Extracting Transactional Behaviors. IEEE Transactions on Computational Social Systems 2022, pp. 1–13. [CrossRef]
- Xiang, D.; Liu, G.; Yan, C.; Jiang, C. A Guard-Driven Analysis Approach of Workflow Net with Data. IEEE Transactions on Services Computing 2021, 14, 1650–1661. [Google Scholar] [CrossRef]
- Xiang, D.; Lin, S.; Wang, X.; Liu, G. Checking Missing-Data Errors in Cyber-Physical Systems Based on the Merged Process of Petri Nets. IEEE Transactions on Industrial Informatics 2022, pp. 1–10. [CrossRef]
- Kähkönen, K.; Heljanko, K. Testing Programs with Contextual Unfoldings. ACM Trans. Embed. Comput. Syst. 2018, 17, 23:1–23:25. [Google Scholar] [CrossRef]
- Kähkönen, K.; Saarikivi, O.; Heljanko, K. Unfolding based automated testing of multithreaded programs. Autom. Softw. Eng. 2015, 22, 475–515. [Google Scholar] [CrossRef]
- Bui, T.L.; Chatterjee, K.; Gautam, T.; Pavlogiannis, A.; Toman, V. The reads-from equivalence for the TSO and PSO memory models. Proc. ACM Program. Lang. 2021, 5, 1–30. [Google Scholar] [CrossRef]
- Agarwal, P.; Chatterjee, K.; Pathak, S.; Pavlogiannis, A.; Toman, V. Stateless Model Checking Under a Reads-Value-From Equivalence. Computer Aided Verification - 33rd International Conference, CAV 2021, Virtual Event, -23, 2021, Proceedings, Part I; Silva, A.; Leino, K.R.M., Eds. Springer, 2021, Vol. 12759, Lecture Notes in Computer Science, pp. 341–366. 20 July. [CrossRef]
- He, L.; Liu, G. Verifying Computation Tree Logic of Knowledge via the Similar Reachability Graphs of Knowledge-oriented Petri Nets. 2020 39th Chinese Control Conference (CCC), 2020, pp. 5026–5031. [CrossRef]
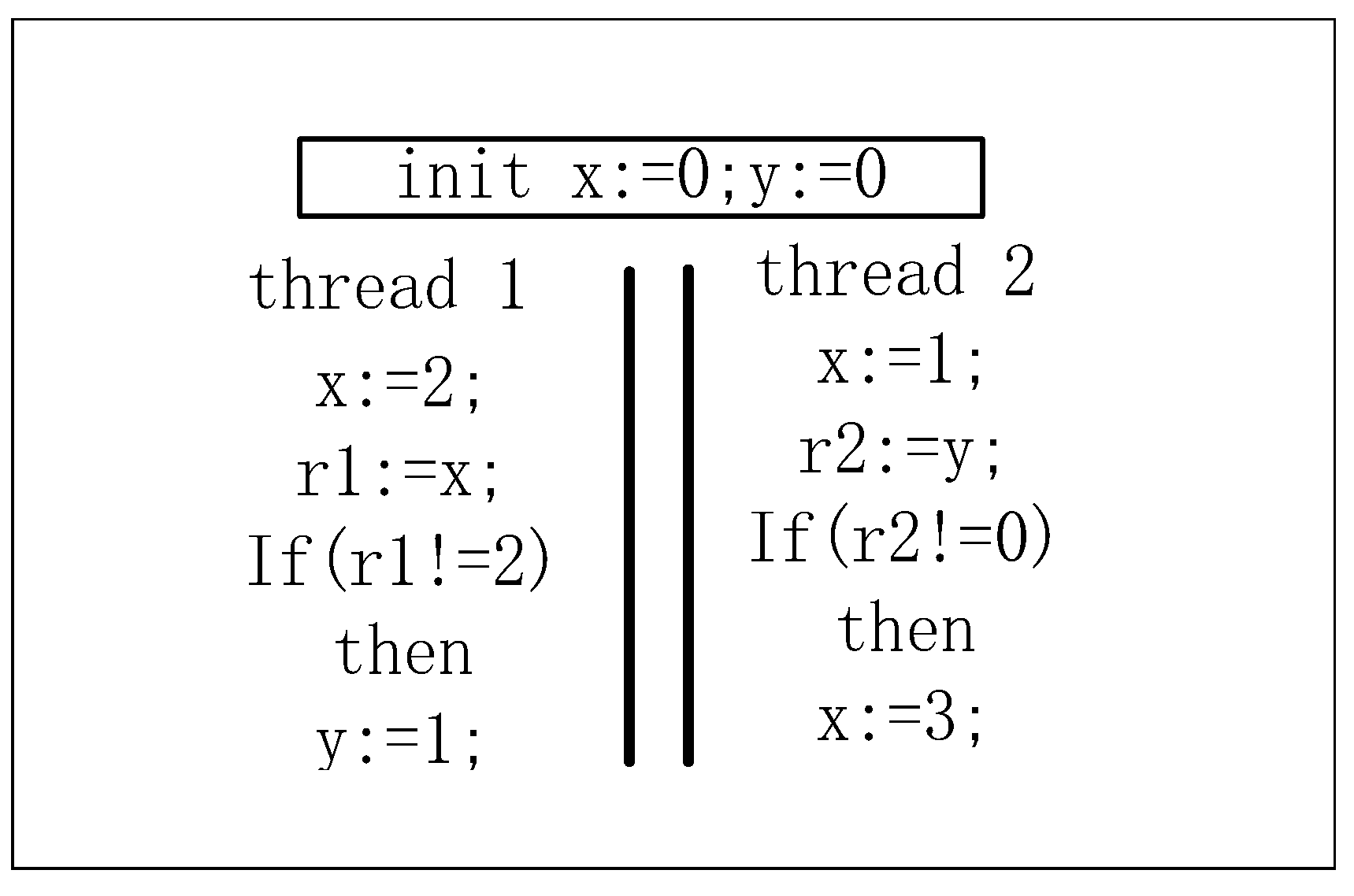
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





