Submitted:
03 August 2023
Posted:
07 August 2023
Read the latest preprint version here
Abstract
Keywords:
1. Introduction
- In any classical implementation of k nearest-neighbour clustering, it is possible to change the dissimilarity and loss function. This observation carries over to hybrid quantum-classical implementations of k-nearest neighbour algorithms which utilize quantum methods only to estimate the dissimilarity. This is indeed what we do in this work, change to a dissimilarity that is more suitable for quantum embedding.
- The encoding of classical data into quantum states has been proven to be a complex task which significantly reduces the advantage of known quantum machine learning algorithms [12]. Due to this, we focus on (in hindsight) more natural embedding of classical data in quantum states.
1.1. Related Work
1.2. Contribution
2. Preliminaries
2.1. Experimental Setup
2.2. Bloch Sphere
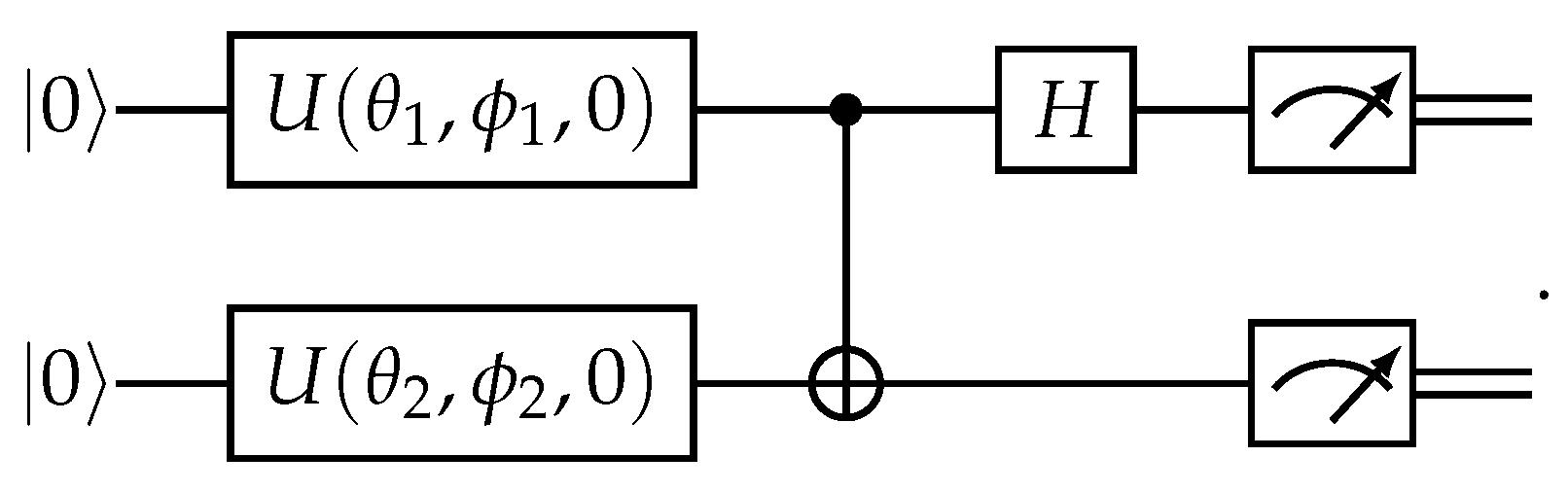
2.3. Bell-state measurement and Fidelity
2.4. Nearest-neighbour clustering algorithms
- is a subset called dataset of points called datapoints
- is a list (of size k) of points called centroids
- is a lower bounded function called dissimilarity function , or dissimilarity for short.
2.5. Euclidean dissimilarity and classical clustering
2.6. Cosine dissimilarity
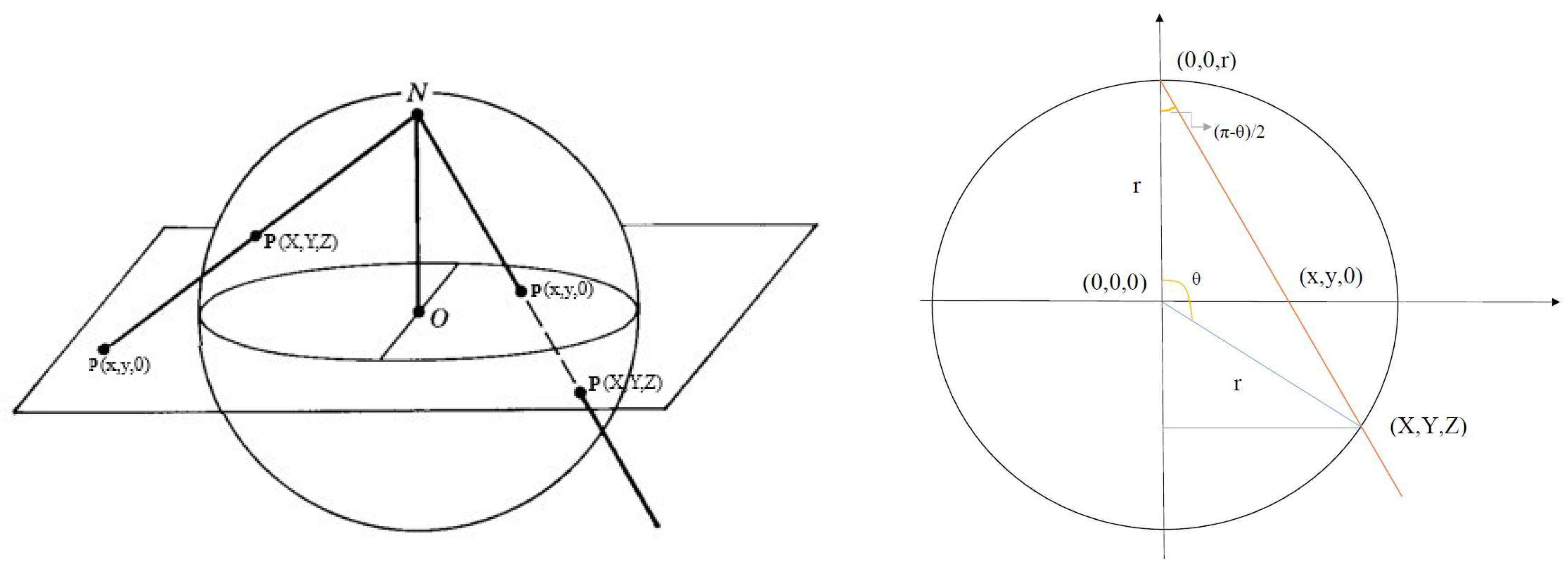
2.7. Stereographic projection
3. Stereographic Quantum Nearest-Neighbour Clustering (SQ-kNN)
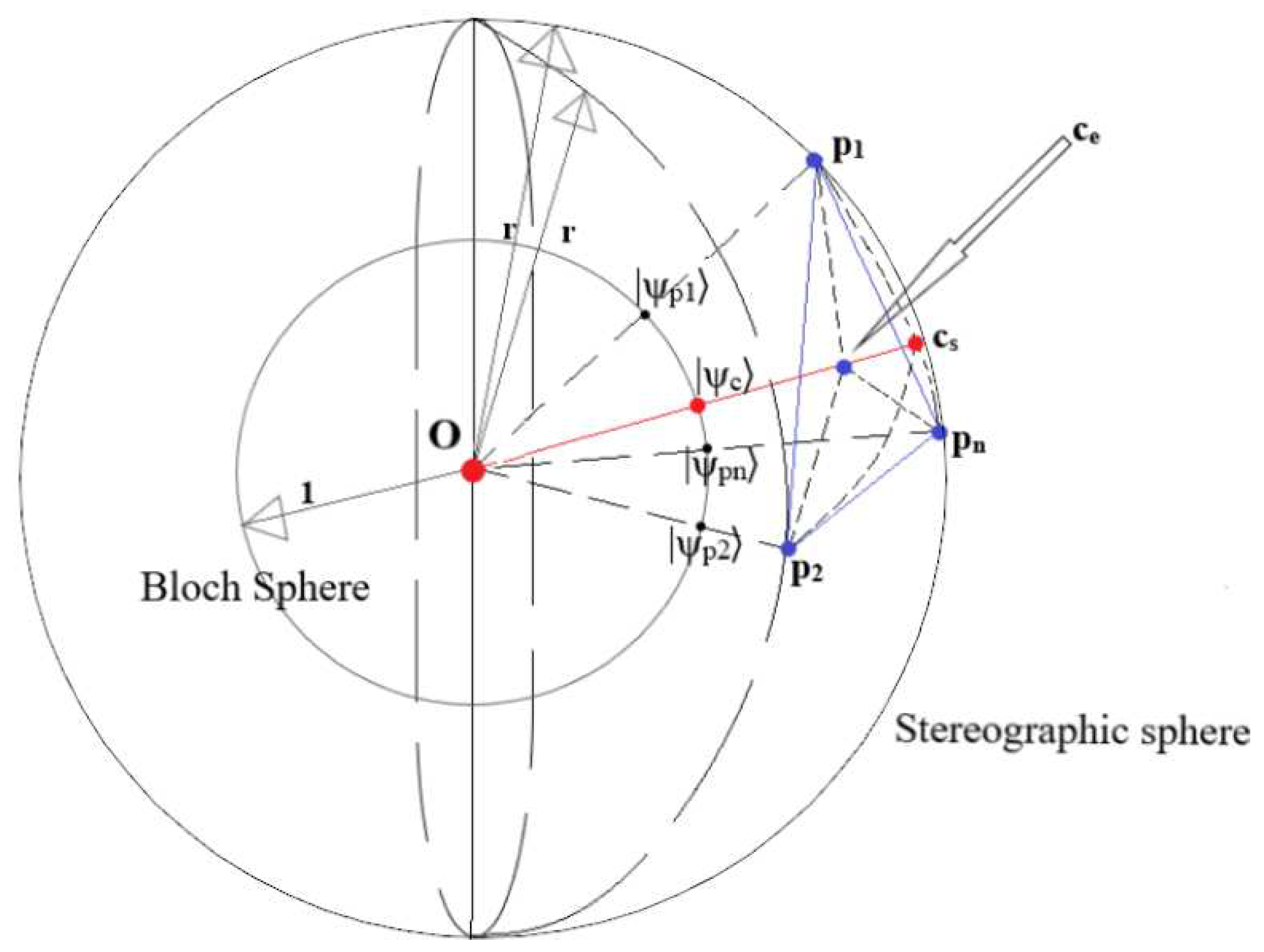
3.1. Stereographic Embedding, Bloch Embedding and Quantum Dissimilarity
- 1.
- projecting the 2D point into a point on the sphere of radius r in 3D space through the ISP:
- 2.
- Bloch embedding into .
3.2. The SQ-kNN Algorithm
- 1.
- First, prepare to embed the classical data and initial centroids into quantum states using the ISP: project the 2-dimensional datapoints and initial centroids (in our case, the alphabet) into a sphere of radius r and calculate the polar and azimuthal angles of the points. This first step is executed entirely on a classical computer.
- 2.
- Cluster Update: The calculated angles are used to create the states using Bloch embedding (Definition 7). The dissimilarity between the centroid and point is then estimated by using the Bell-state measurement. Once the dissimilarities between a point and all the centroids have been obtained, the point is assigned to the cluster of the ‘closest’ centroid. This is repeated for all the points that have to be classified. This step is entirely handled by the quantum circuit and classical controller. The controller feeds in the classical values at the appropriate times, stores the results of the various shots and classifies the point to the appropriate cluster.
- 3.
- Centroid Update: Since any non-zero point on the subspace of (see Corollary 1, Figure 4) is an equivalent choice, to minimise computational expense, the centroids are updated as the sum point of all points in the cluster - as opposed to the average, for example, which minimizes the Euclidean dissimilarity (Equation (26)).
-
The stereographic embedding of the 2D datapoints is done by inverse stereographic projecting the point into a sphere of a chosen radius and then producing the quantum state obtained by rescaling the sphere to radius one.In contrast, in angle embedding, the coefficients of the vectors are used as the angles of the Bloch vector (also known as dense angle embedding [46]), while in amplitude embedding they are used as the amplitudes in the standard basis. For 2D vectors, amplitude embedding allows one to encode only one coefficient (instead of two) in one qubit, and sometimes angle embedding would also encode only one coefficient by using a single rotation (standard angle embedding [47]). Both angle and amplitude embeddings require the lengths of the vectors to be stored classically beside the quantum state, which is not needed in Bloch embedding.
- No post-processing is needed after the overlap estimation of stereographically embedded data as the obtained estimate is already a linear function of the inner product, as opposed to standard approaches using angle or amplitude encoding. Amplitude embedding also requires non-trivial computational time in the state preparation process. In contrast, in angle embedding, though the state preparation time is constant, the process of recovering a useful dissimilarity (e.g. Euclidean) may involve many post-processing steps.
3.3. Complexity Analysis and Scaling
3.3.1. Using qubit-based system
3.3.2. Using qudit-based system
3.4. SQ-kNN and Mixed states
4. Quantum-Inspired Stereographic K Nearest-Neighbour Clustering
- 1.
- Stereographically project all the 2-dimensional data and initial centroids into the sphere of radius r. Notice that the initial centroids will lie on the sphere by construction.
- 2.
- Cluster Update: Form the clusters using the method defined in Equation (22), i.e. form all . Here, and dissimilarity (Definition 5 and Lemma 2).
- 3.
- Centroid Update: A closed-form expression for the centroid update was calculated in Equation (41) . This expression recalculates the centroid once the new clusters have been formed. Once all the centroids are updated, Step 2 (cluster update) is then repeated, and so on, until a stopping condition is met.
4.1. Equivalence
- 1.
- ,
- 2.
- and ,
- 3.
- for all and any .
4.2. Complexity Analysis and Scaling
5. Experiments and Results
- The hardware performance and availability of quantum computers (NISQ devices) is currently so much worse than that of classical computers that most likely no advantage can be obtained with the quantum algorithm.
- The goal of this paper is not to show a “quantum advantage” over the classical k-means in the NISQ context - it is to show that stereographic projection can both lead to better learning for classical clustering and be a better embedding for quantum clustering. In particular, the equivalence between 2DSC-KNN and SQ-KNN proves that the only limitation for the stereographic quantum algorithm to achieve the performance of the quantum-inspired algorithm is noise.
- 1.
- Radius: the radius of the stereographic sphere into which the 2-dimensional points are projected.
- 2.
- Number of points: the number of points upon which the clustering algorithm was performed. For every experiment, the selected points were a random subset of all the 64-QAM data (of a specific noise) with cardinality equal to the required number of points.
- 3.
- Dataset Noise: As explained in Section 2.1, data was collected for four different input powers. As such, the data is divided into four datasets labelled with powers 2.7, 6.6, 8.6 and 10.7 dBm.
- 4.
- Natural endpoint: The natural endpoint of a clustering algorithm occurs when for all , i.e. when all the clusters remained unchanged even after the centroid update. It is the natural end-point since if the clusters do not change, the centroids will not change either in the next iteration, in turn leading to the same clusters and centroids for all future iterations.
- 2DSC-kNN: The quantum-analogue algorithm of Definition 12, the classical equivalent of the stereographic quantum algorithm SQ-KNN and the most important candidate for our testing.
- 2DEC-kNN: The standard classical k nearest-neighbour algorithm of Definition 4 implemented upon the original 2-dimensional dataset () which serves as a baseline for performance comparison.
- 3DSC-kNN: The standard classical k nearest-neighbour algorithm, but implemented upon the stereographically projected 2-dimensional dataset, as defined in Definition 6. We emphasize once again that in contrast to the 2DSC-kNN the centroid lies within the sphere, and in contrast to the 2DEC-kNN, the clustering takes place in . This algorithm serves as another control, to gauge the relative impacts of stereographically projecting the dataset versus restricting the centroid to the surface of the sphere. It is an intermediate step between the 2DSC-kNN and the 2DEC-kNN algorithms.
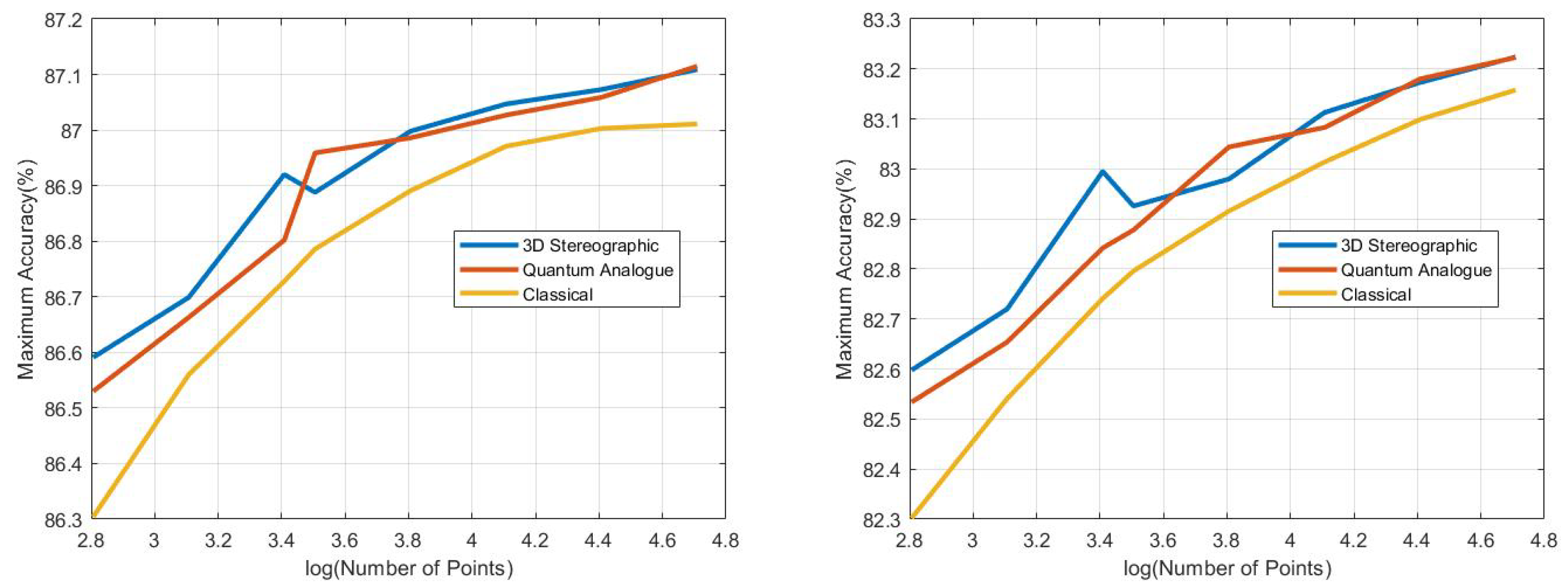
- Accuracy: Since we have the true labels of the datapoints available, we can measure the accuracy of the algorithm as the percentage of points that have been given the correct label, i.e. symbol accuracy rate. As mentioned in Appendix A, due to Gray encoding, the bit error rate is approximately of the symbol error rate. All accuracies are recorded as a percentage.
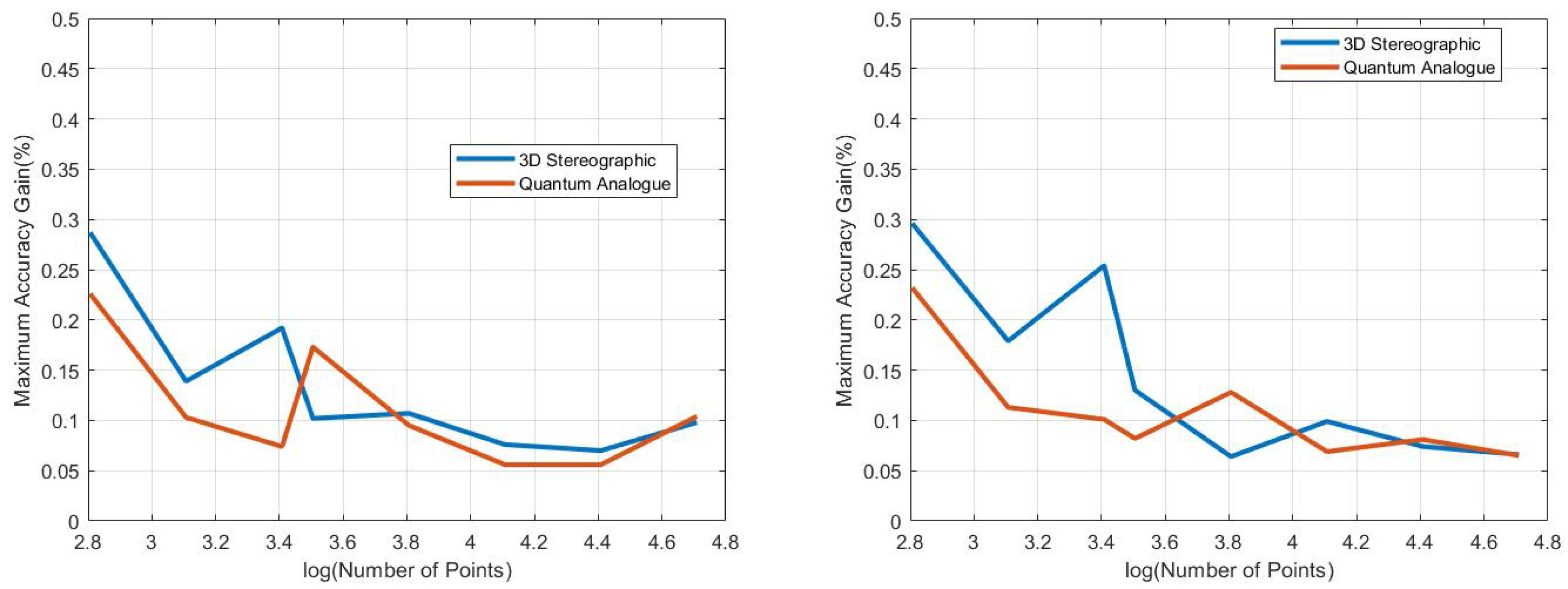
- Accuracy gain: The gain is calculated as (accuracy of candidate algorithm - accuracy of 2-dimensional classical k-means clustering algorithm), i.e. it is the increase in accuracy of the algorithm over the baseline, defined as the accuracy of the classical k-means clustering algorithm acting on the 2D dataset for those number of points.
- Number of iterations: One iteration of the clustering algorithm occurs when the algorithm performs the cluster update followed by the centroid update (the algorithm must then perform the cluster update once again). The number of times the algorithm repeats these 2 steps before stopping is the number of iterations. We use the number of iterations required by the algorithm to reach its ‘natural endpoint’ as a proxy for convergence performance. Clearly, the lesser the number of iterations performed, the faster the convergence of the algorithm. The number of iterations does not directly correspond to time performance since the time taken for one iteration differs between all algorithms.
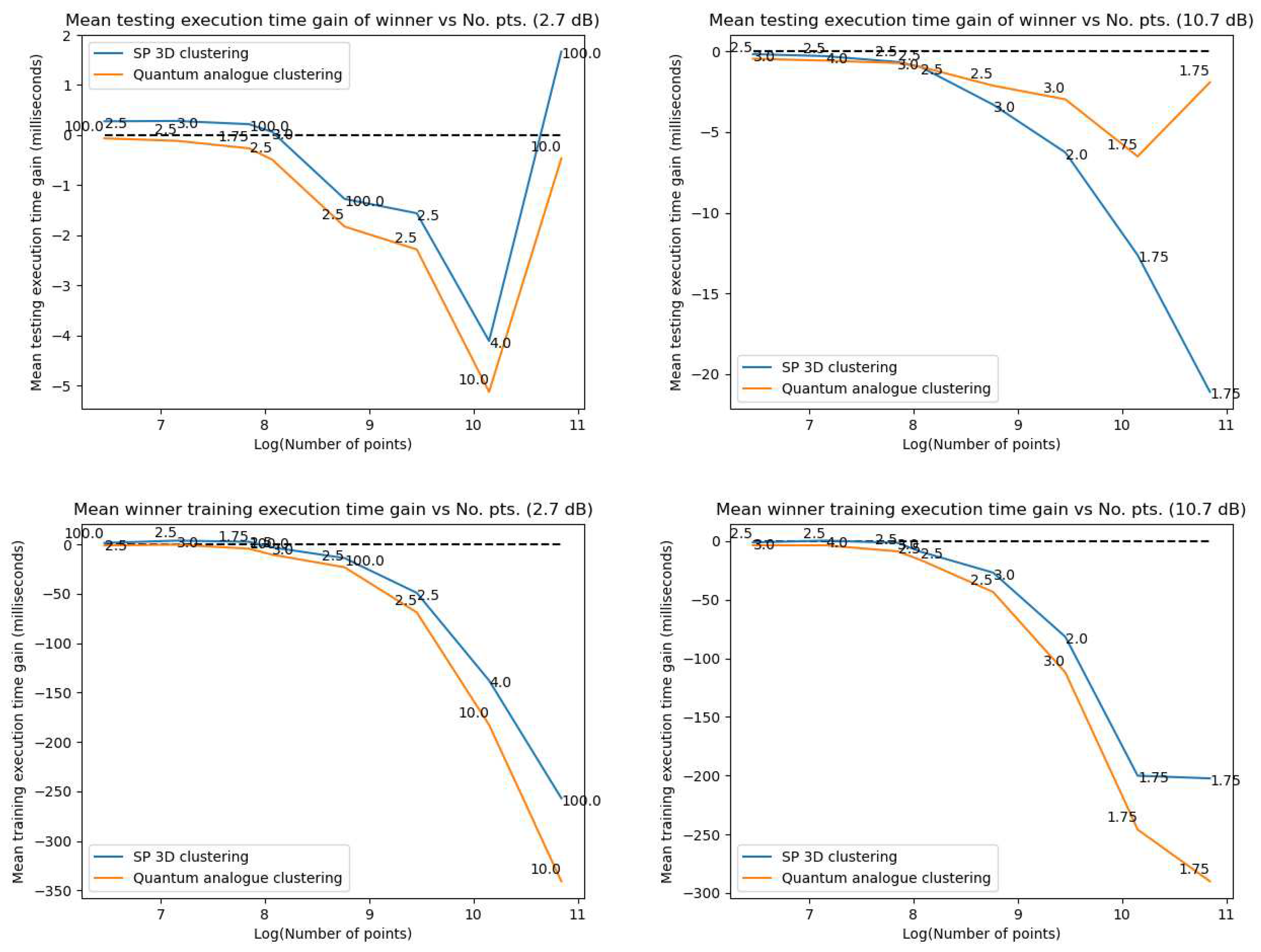
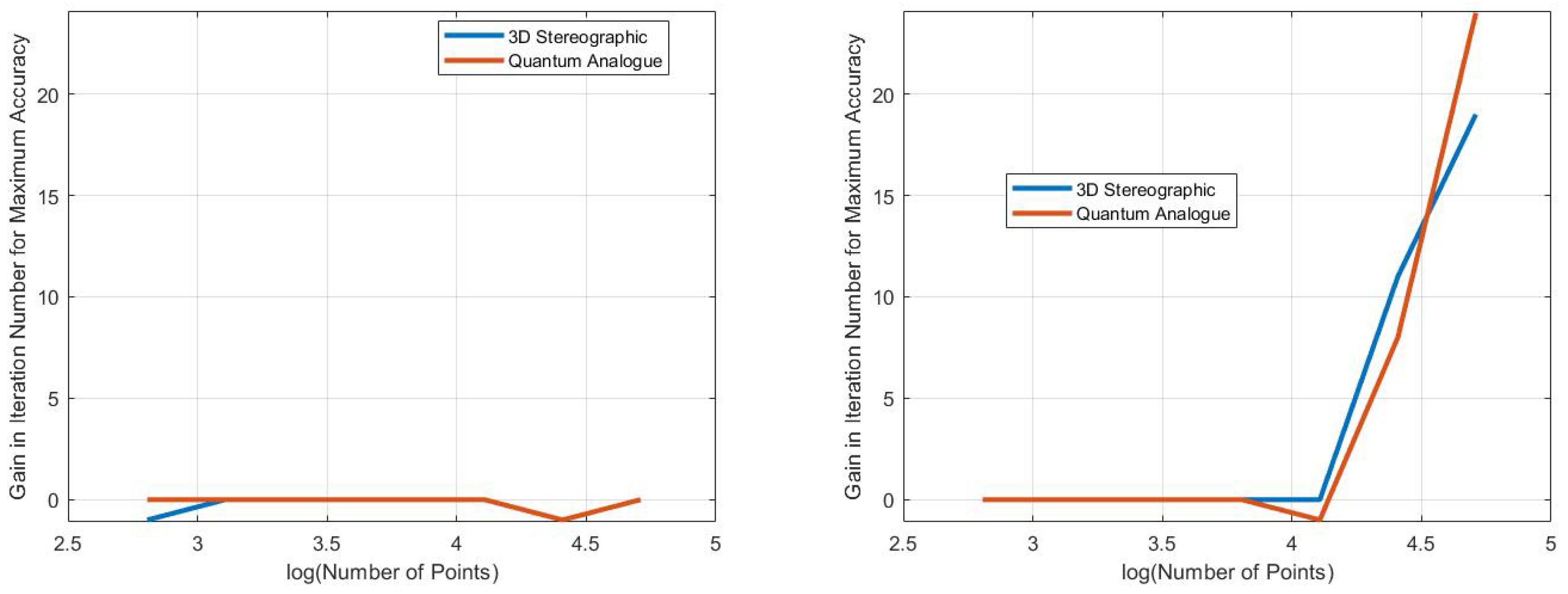
- Iteration gain: The gain in iterations is defined as (the number of iterations of 2D k-means clustering algorithm - the number of iterations of candidate algorithm), i.e. the gain is how many fewer iterations the candidate algorithm took than the 2DEC-kNN algorithm to reach its natural endpoint.
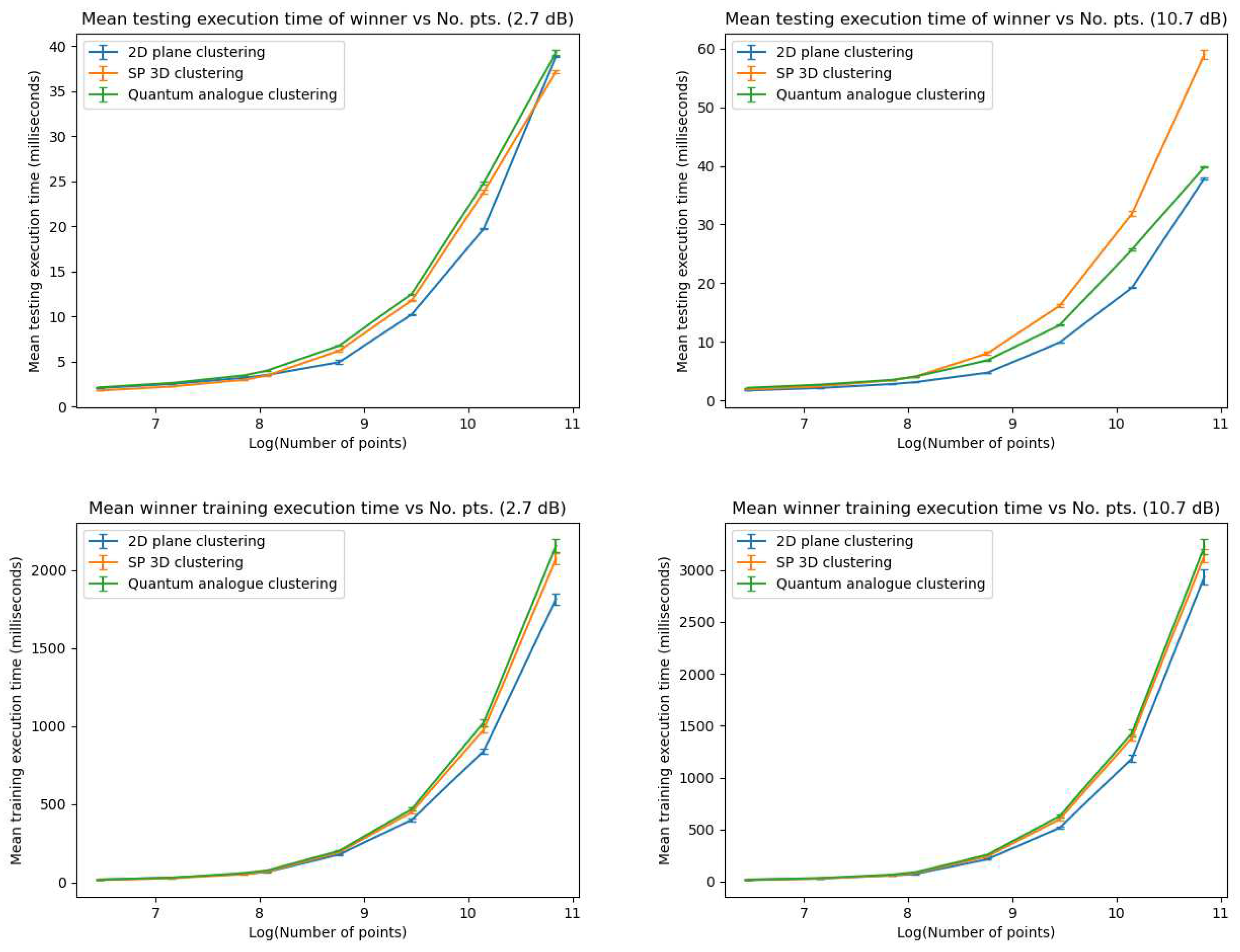
- Execution time: The amount of time taken for a clustering algorithm to give the final output (the final centroids and clusters) given the 2-dimensional data points as input, i.e. the time taken end to end for the clustering process. All times in this work are recorded in milliseconds (ms).
- Execution time gain: This gain is calculated as (the execution time of 2DEC-kNN k-means clustering algorithm - the execution time of candidate algorithm).
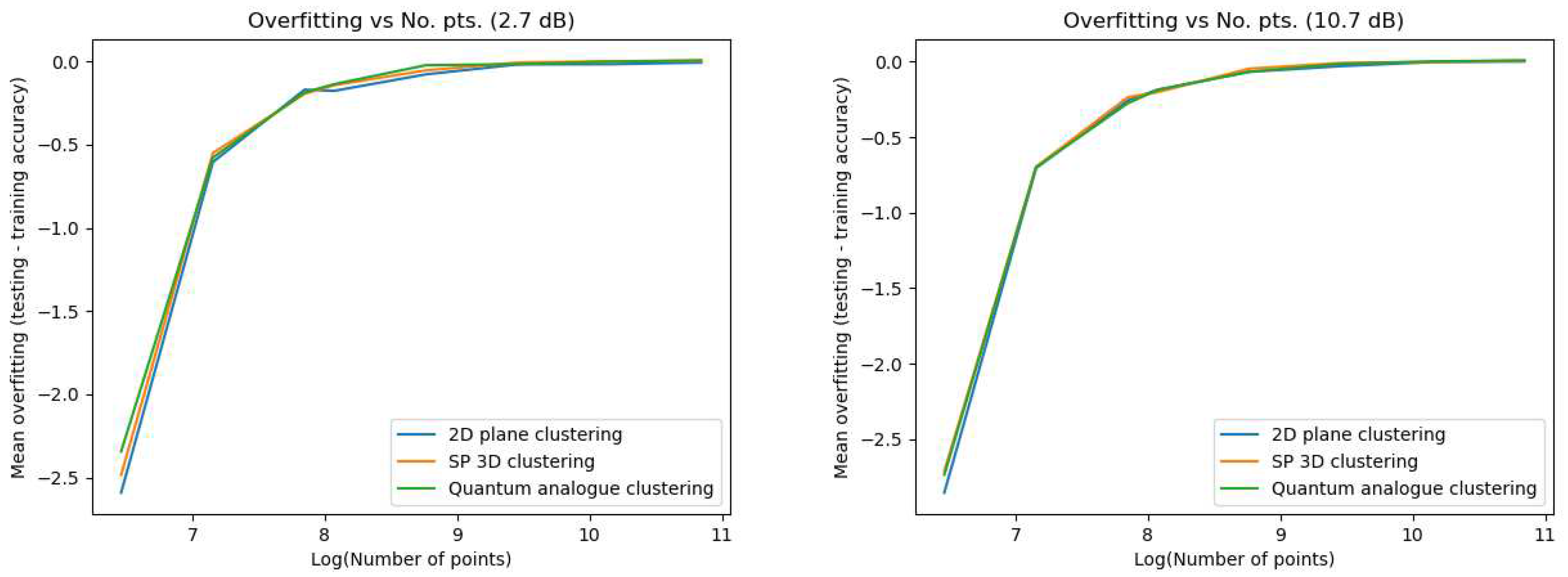
- Overfitting Parameter: (accuracy in testing−accuracy in training).
- 1.
- The Overfitting Test: The dataset is divided into a ‘training’ and a ‘testing’ set, to characterise the clustering and classification performance of the algorithms.
- 2.
- The Stopping criterion Test: The iterations and other performance parameters are varied, to test whether and what kind of stopping criterion is required.
5.1. Experiment 1: Overfitting
- It exhaustively covers all the parameters that can be used to quantify the performance of the algorithms. We were able to observe very important trends in the performance parameters with respect to the choice of radius and the effect of the number of points (affecting the choice of when one should trigger the clustering process on the collected received points).
- It avoids the commonly known problem of overfitting. Though this approach is not usually used in the testing of the k nearest-neighbour algorithm due to its iterative nature, we felt that from a machine learning perspective, it is useful to know how well the algorithms perform in a classification setting as well.
- Another reason that justifies the approach of training and testing (clustering and classification) is the nature of the real-world application setup. When transmitting QAM data through optic fibre, the receiver receives only one point at a time and has to classify the received point to a given cluster in real-time using the current centroid values. Once a number of data points have accumulated, the kNN algorithm can be run to update the centroid values; after the update, the receiver will once again perform classification until some number of points has been accumulated. Hence, we can see that in this scenario the clustering, as well as the classification performance of the chosen method, becomes important.
5.1.1. Results
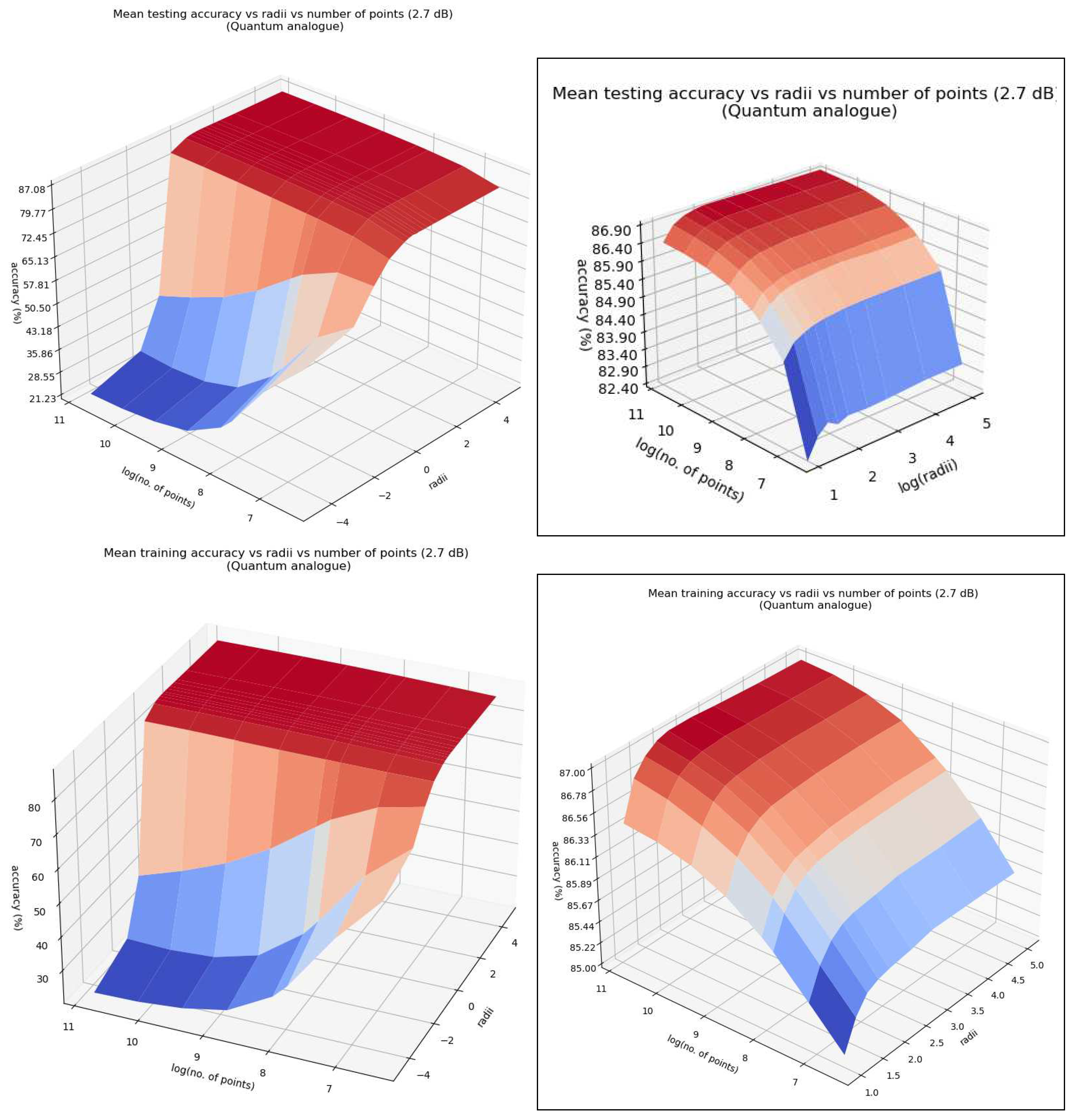
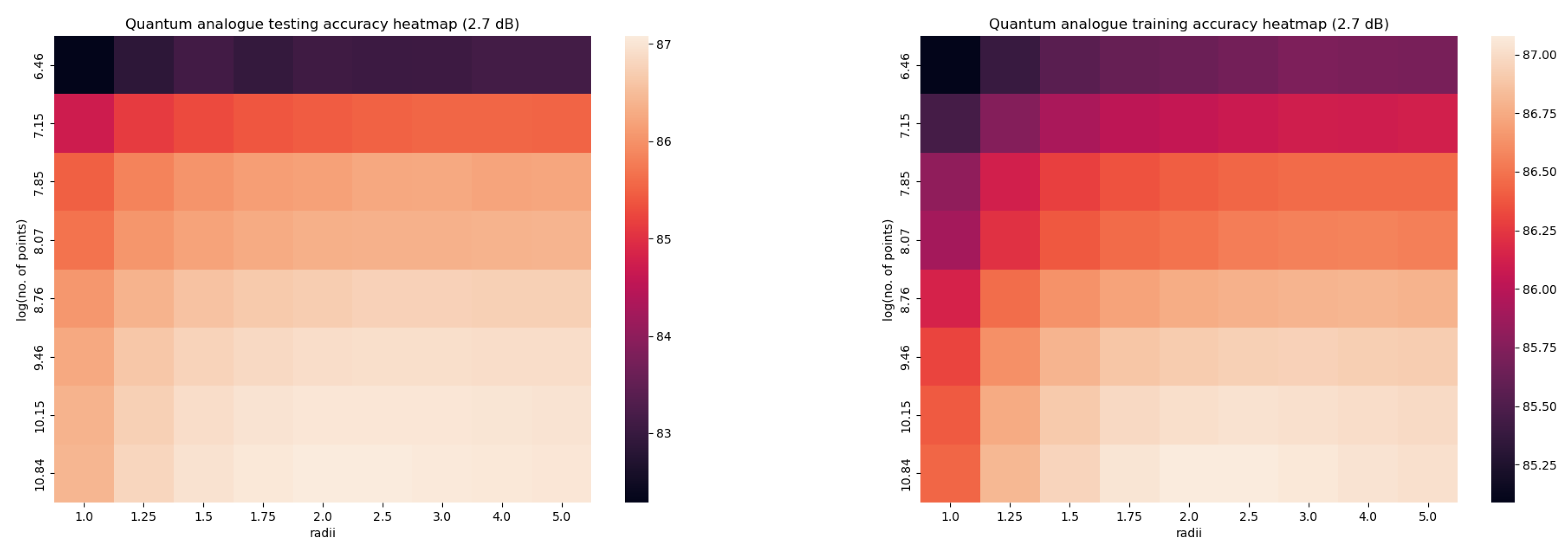
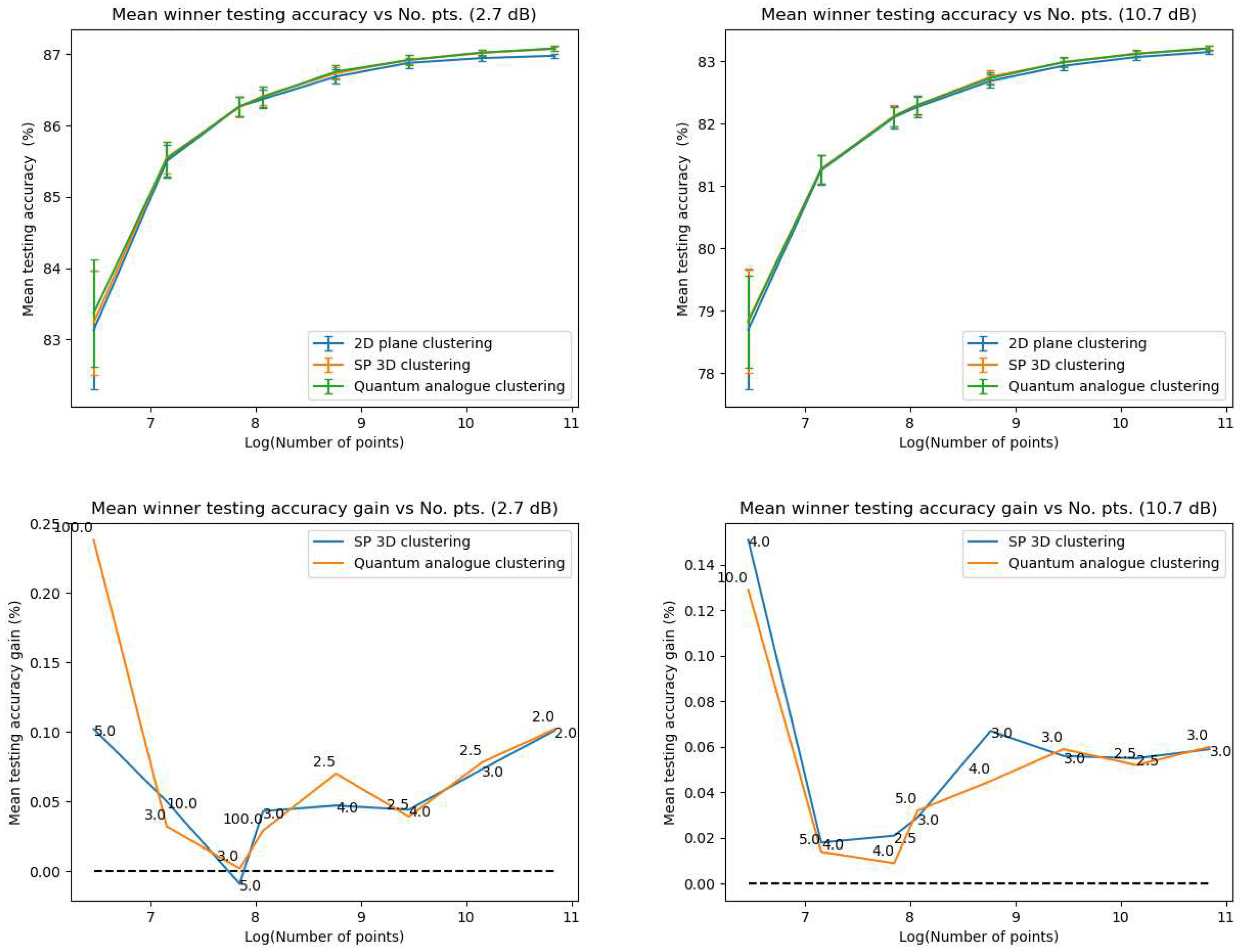
- Accuracy performance
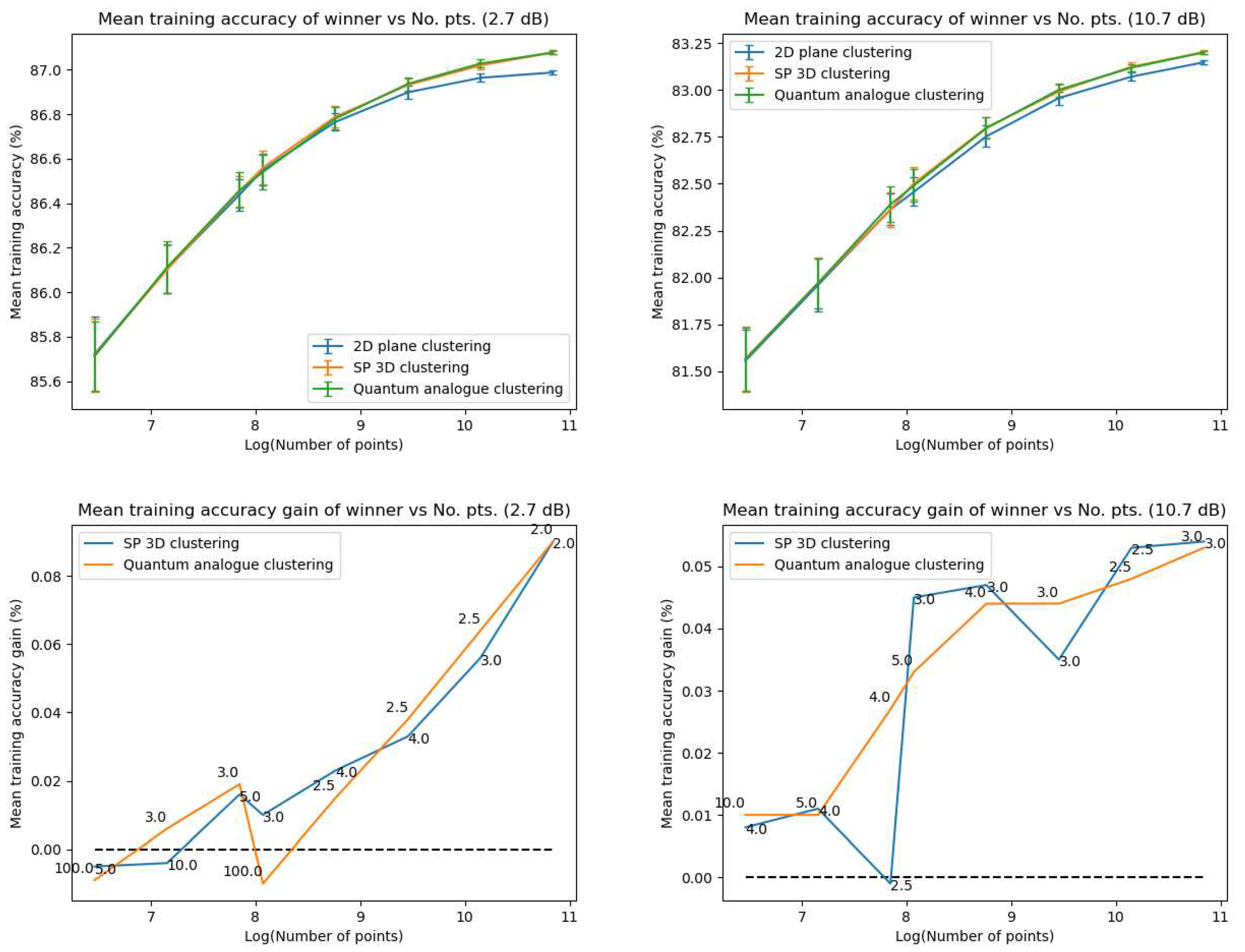
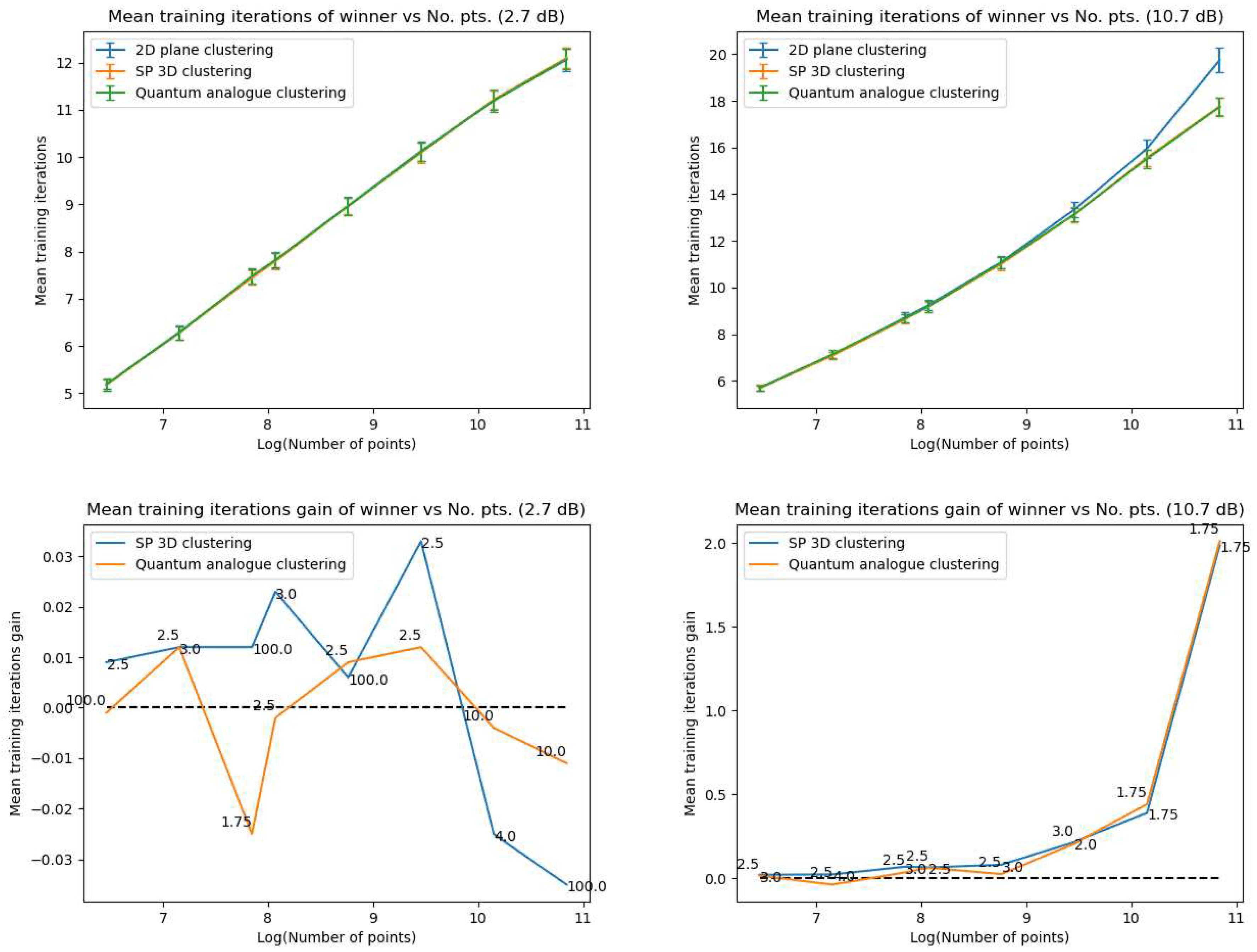
- Iteration Performance
- Time Performance
- Overfitting Performance
5.1.2. Discussion and Analysis
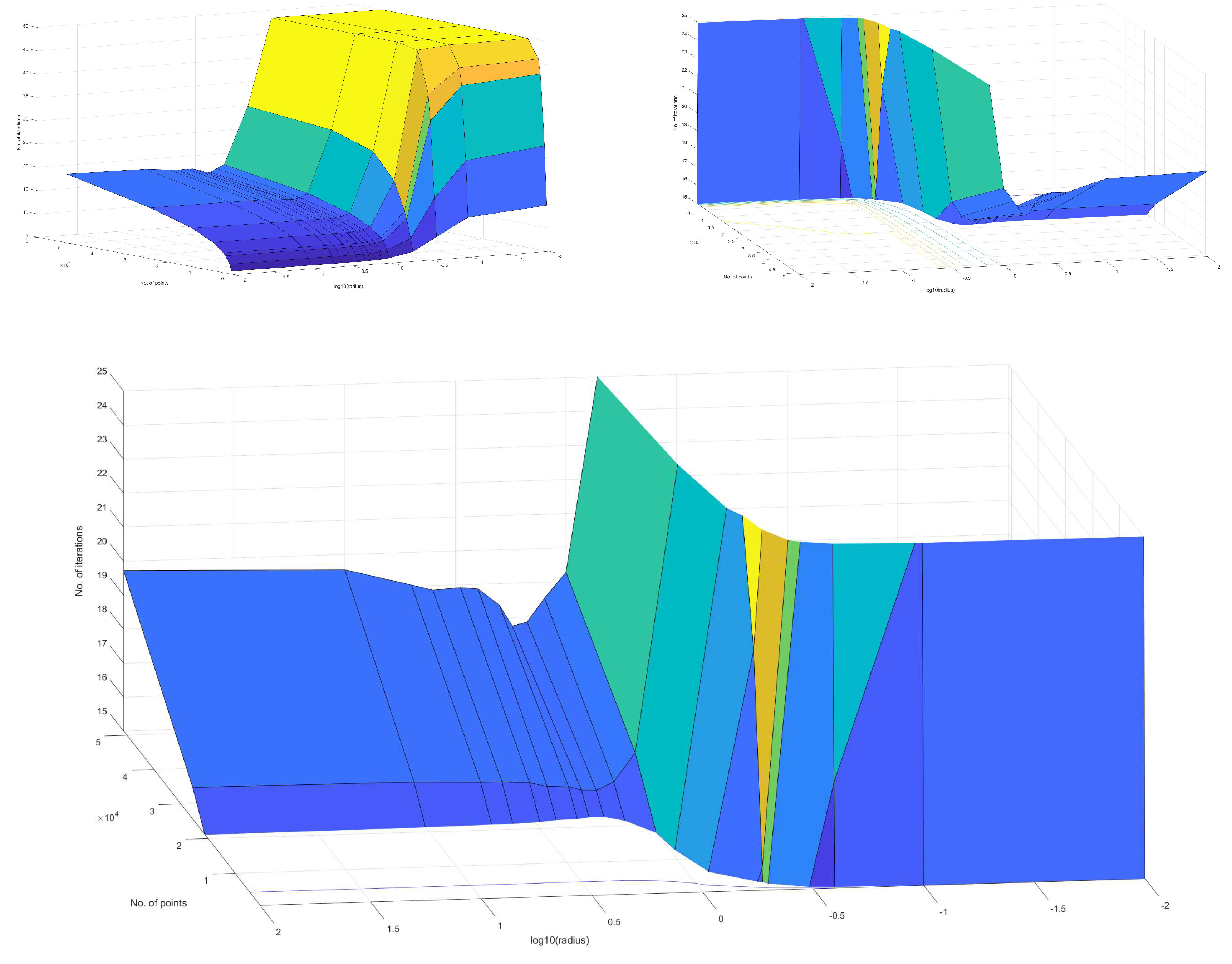
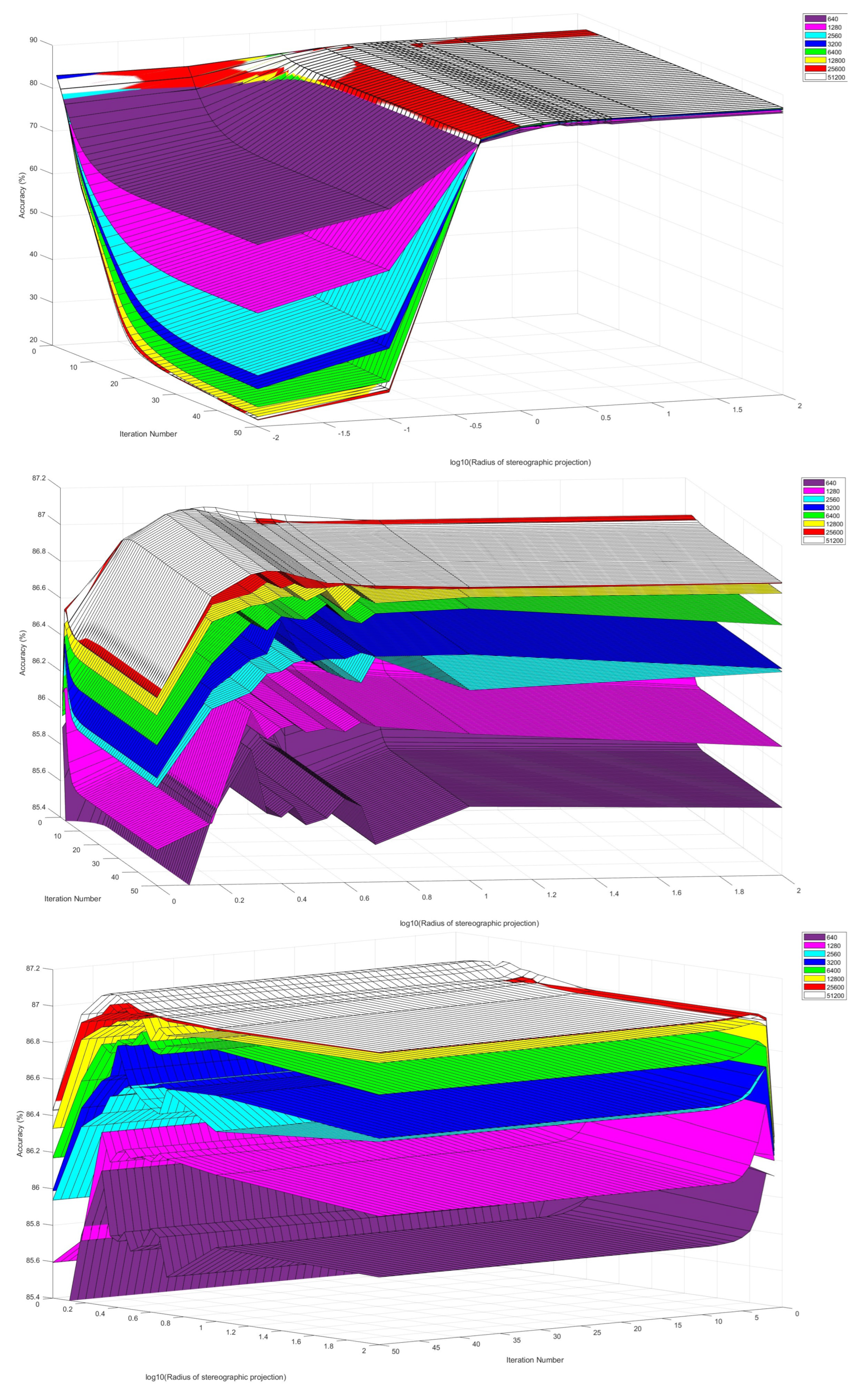
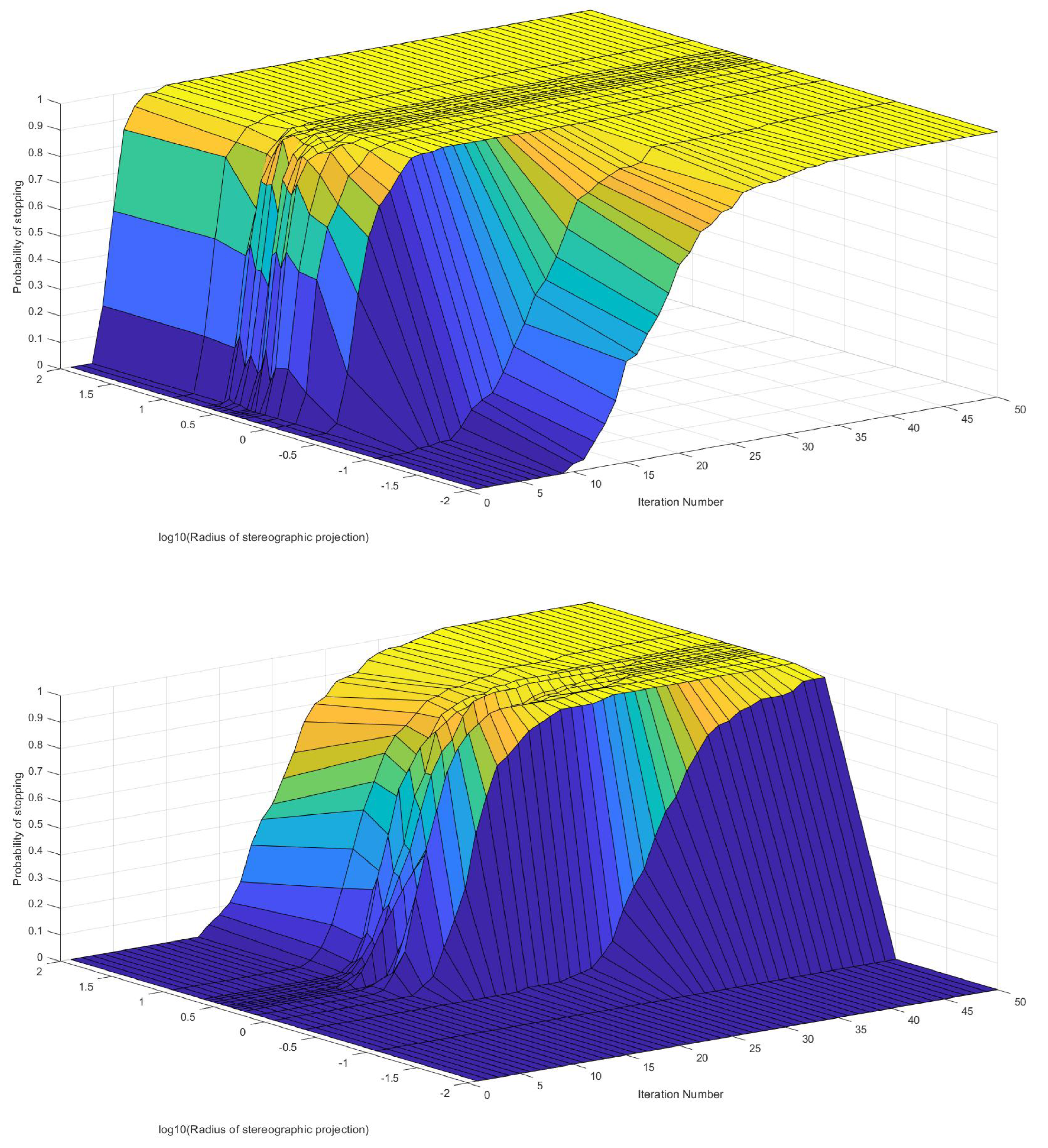
5.2. Experiment 2: Stopping criterion
5.2.1. Results
- Characterisation of the 2DSC-kNN algorithm
- Comparison with 2DEC-kNN and 3DS-kNN K-Means Clustering
5.2.2. Discussion and Analysis
5.3. Overall Observations
- Overall observations from Experiment 1
- 1.
- The ideal radius of projection is greater than 1 and between 2 and 5. At this ideal radius, one achieves maximum testing and training accuracy, and minimum iterations.
- 2.
- In general, the accuracy performance is the same for 3DSC-kNN and 2DSC-kNN algorithms - this shows a significant contribution of the ISP to the advantage as opposed to ‘quantumness’. This is a very significant distinction, not made by any other previous work. The 2DSC-kNN algorithm generally requires fewer iterations to achieve the ideal accuracy, however.
- 3.
- 2DSC-kNN and 3DSC-kNN algorithms lead to an increase in the accuracy performance in general, with the increase most pronounced for the 2.7 dBm dataset.
- 4.
- The 2DSC-kNN algorithm and 3DSC-kNN algorithm give more iteration performance gain (fewer iterations required than 2DEC-kNN) for high noise datasets and for a large number of points.
- 5.
- Generally, increasing the number of points works in favour of the 2DSC-kNN and 3DSC-kNN algorithms, with the caveat that a good radius must be carefully chosen.
- Overall observations from Experiment 2
- 1.
- These results further stress the importance of choosing a good radius (2 to 5 in this application) and a better stopping criterion. The natural endpoint is not suitable.
- 2.
- The results clearly justify the fact that the developed 2DSC-kNN algorithm has significant advantages over 2DEC-kNN k-means clustering and 3DSC-kNN clustering.
- 3.
- The 2DSC-kNN algorithm performs nearly the same as the 3DSC-kNN algorithm in terms of accuracy, but for iterations to achieve this max accuracy, the 2DSC-kNN algorithm is better (especially for high noise and a high number of points).
- 4.
- The developed 2DSC-kNN algorithm and 3DSC-kNN algorithm are better than the 2DEC-kNN algorithm in general - in terms of both accuracy and iterations to reach that maximum accuracy.
6. Conclusion and Further work
6.1. Future work
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ADC | Analog-to-digital converter |
| CD | Chromatic dispersion |
| CFO | Carrier frequency offset |
| CPE | Carrier phase estimation |
| DAC | Digital-to-analog converter |
| DP | Dual Polarisation |
| ECL | External cavity laser |
| FEC | Forward error correction |
| GHz | Gigahertz |
| GBd | Gigabauds |
| GSa/s | samples per second |
| DSP | Digital signal processing |
| ISP | Inverse stereographic projection |
| MIMO | Multiple input multiple output |
| M-QAM | M-ary Quadrature Amplitude Modulation |
| QML | Quantum Machine Learning |
| QRAM | Quantum Random Access Memory |
| TR | Timing recovery |
| SQ access | Sample and query access |
| kNN | K Nearest Neighbour (Definition 3) |
| FF-QRAM | Flip flop QRAM |
| NISQ | Near-intermediate scale quantum |
| Dataspace | |
| D | Dataset |
| D | 2-dimensional dataset |
| set of all M centroids | |
| Cluster associated to a centroid | |
| Dissimilarity (measure function) | |
| Euclidean dissimilarity | |
| Cosine dissimilarity | |
| ISP into a sphere of radius r | |
| n-sphere of radius r | |
| Hilbert space of one qubit | |
| nDEC-kNN | n-dimensional Euclidean Classical k Nearest-Neighbour algorithm (Definition 4) |
| SQ-kNN | Stereographic Quantum k Nearest-Neighbour algorithm (Definition 10) |
| 2DSC-kNN | 2D Stereographic Classical k Nearest-Neighbour algorithm (Definition 12) |
| 3DSC-kNN | 3D Stereographic Classical k Nearest-Neighbour algorithm (Definition 6) |
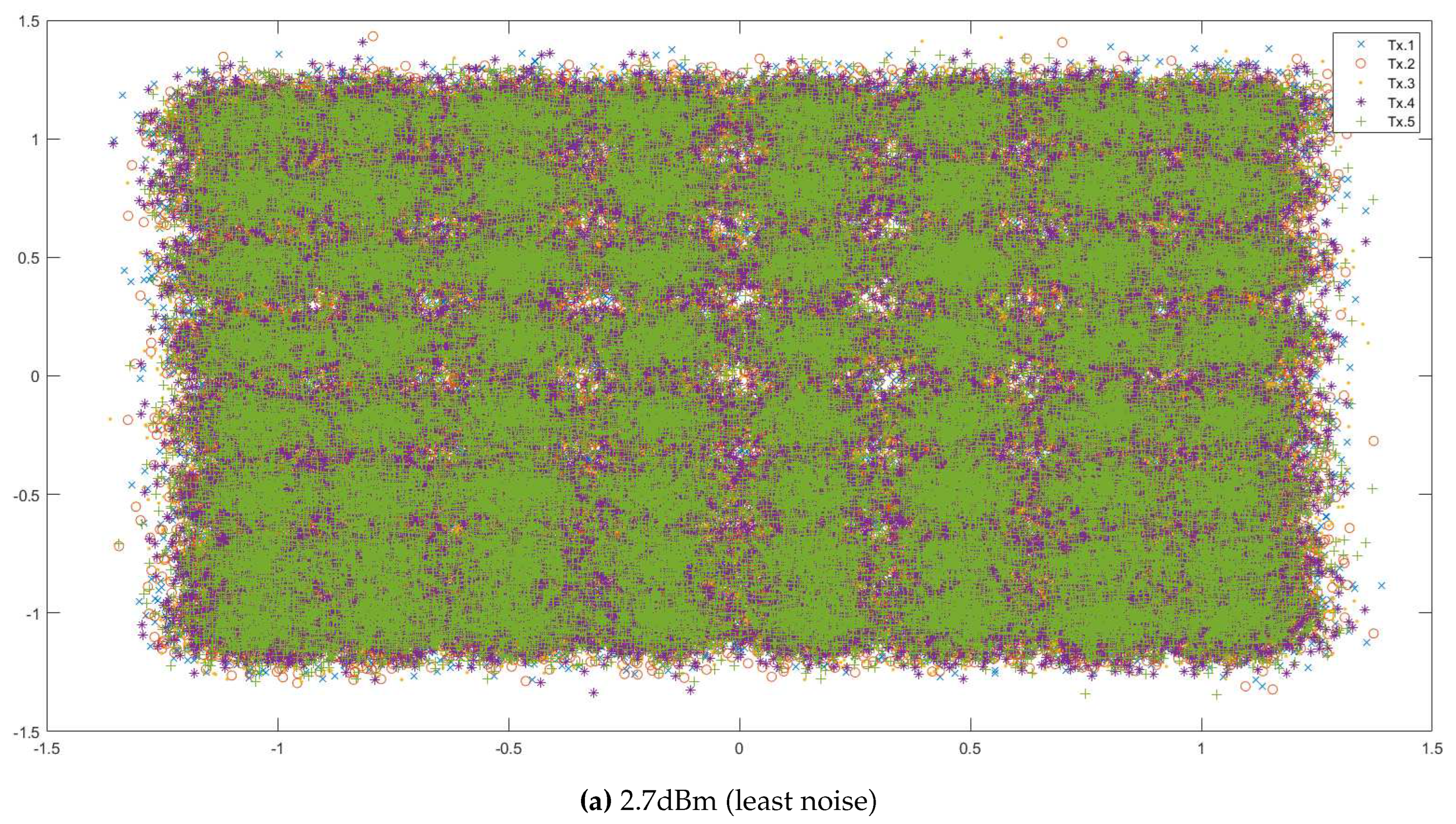
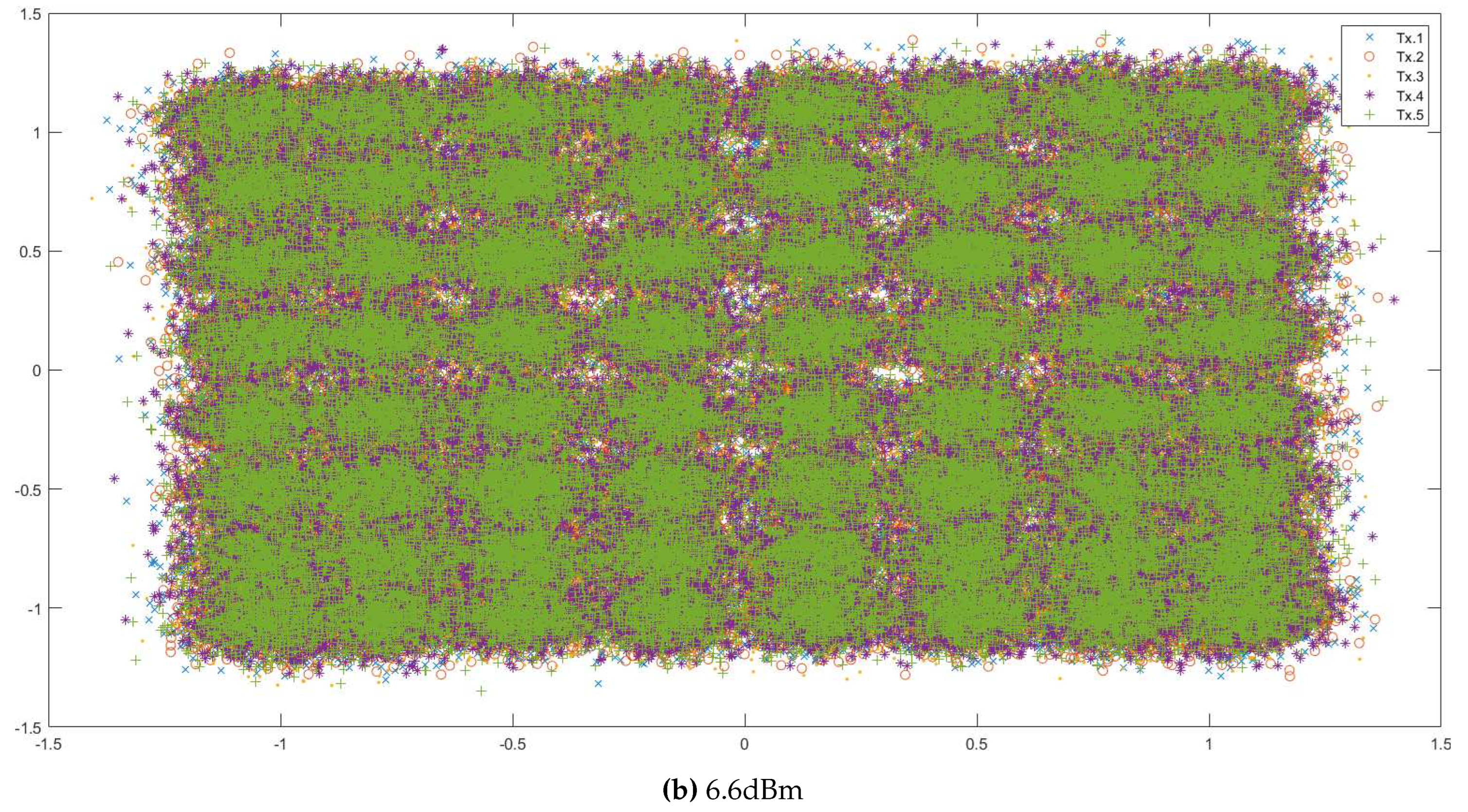
Appendix A. QAM and Data Visualisation
Appendix A.1. Description of 64-QAM Data
- ‘alphabet’: The initial analog values at which the data was transmitted, in the form of complex numbers i.e. for an entry (), the transmitted signal was of the form . Since the transmission protocol is 64-QAM, there are 64 values in this variable. The transmission alphabet is the same irrespective of the nonlinear distortions.
- ‘rxsignal’: The received analog values of the signal by the receiver. This data is in the form of a matrix. Each datapoint was transmitted 5 times to the receiver, and so each row contains the values detected by the receiver during the different instances of the transmission of the same datapoint. The values in different rows represent unique datapoint values detected by the receiver.
- ‘bits’: This is the true label for the transmitted points. This data is in the form of a matrix. Since the protocol is 64-QAM, each analog point represents 6 bits. These 6 bits are the entries in each column, and each value in a different row represents the correct label for a unique transmitted datapoint value. The first 3 bits encode the column and the last 3 bits encode the row - see Figure A3.
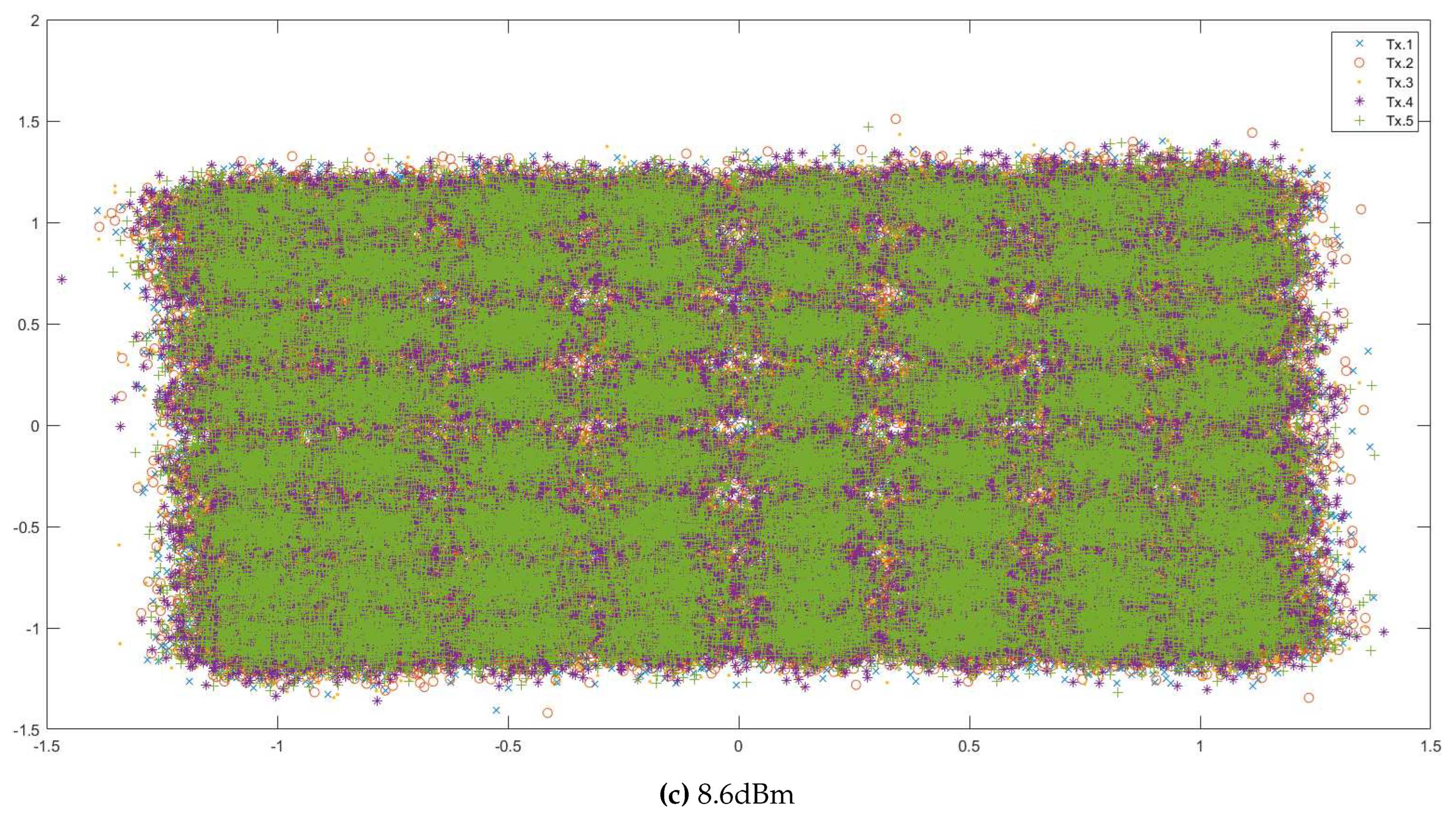
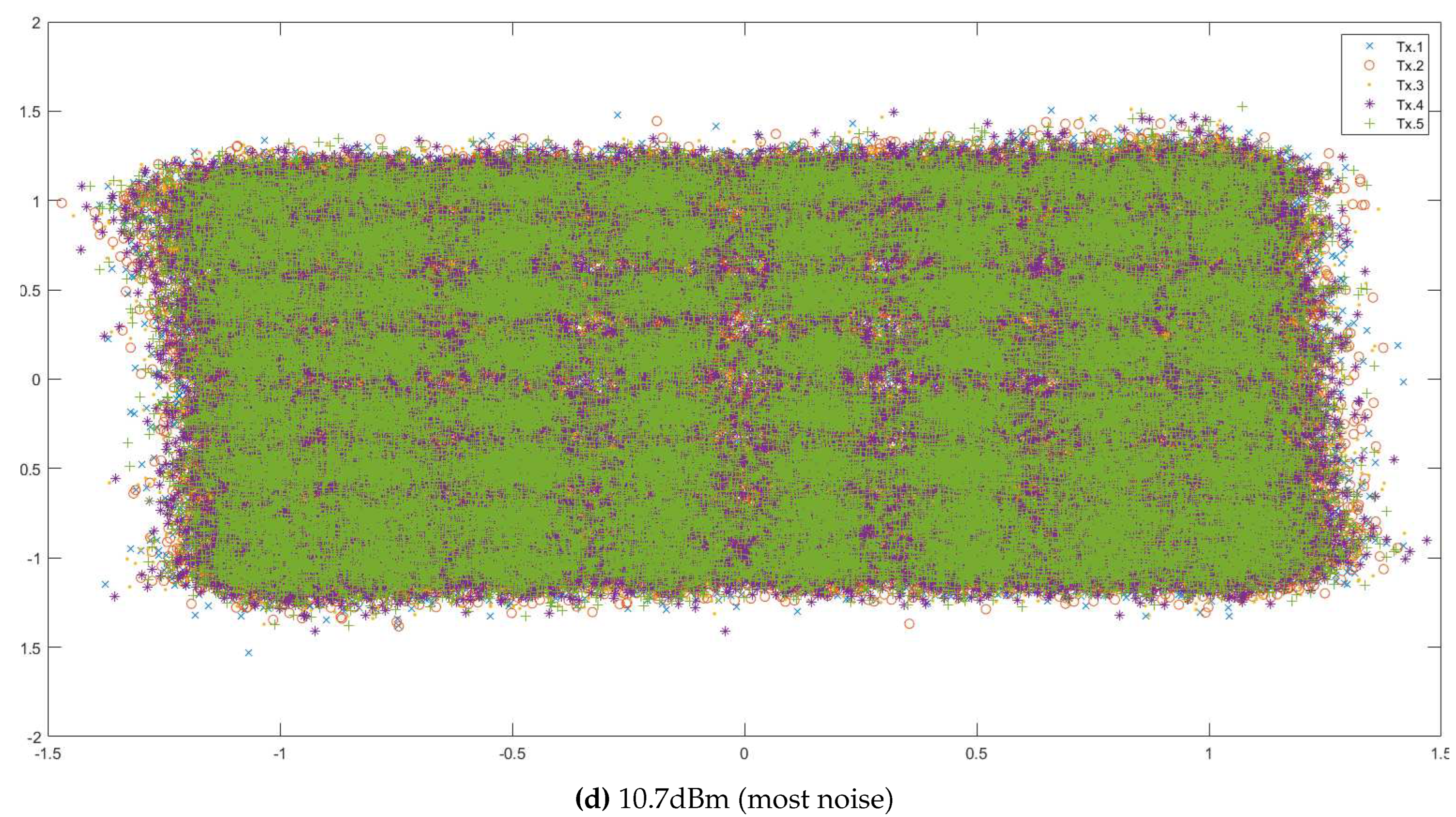
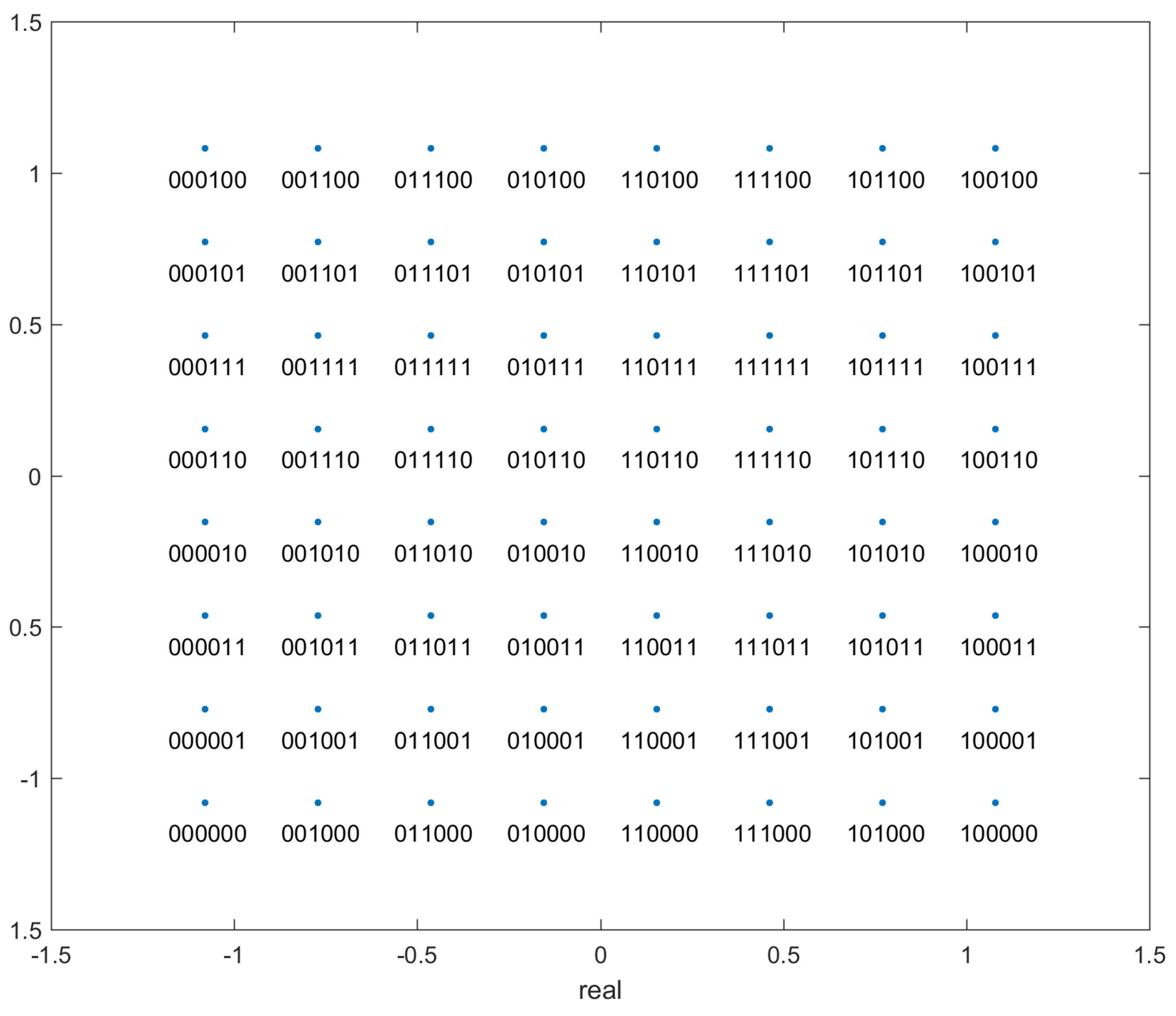
Appendix B. Data Embedding
| Embedding | Encoding | Num. qubits required | Gate Depth |
|---|---|---|---|
| Basis | per data point | ||
| Angle | |||
| Amplitude | gates | ||
| QRAM | queries |
Appendix B.1. Angle Embedding
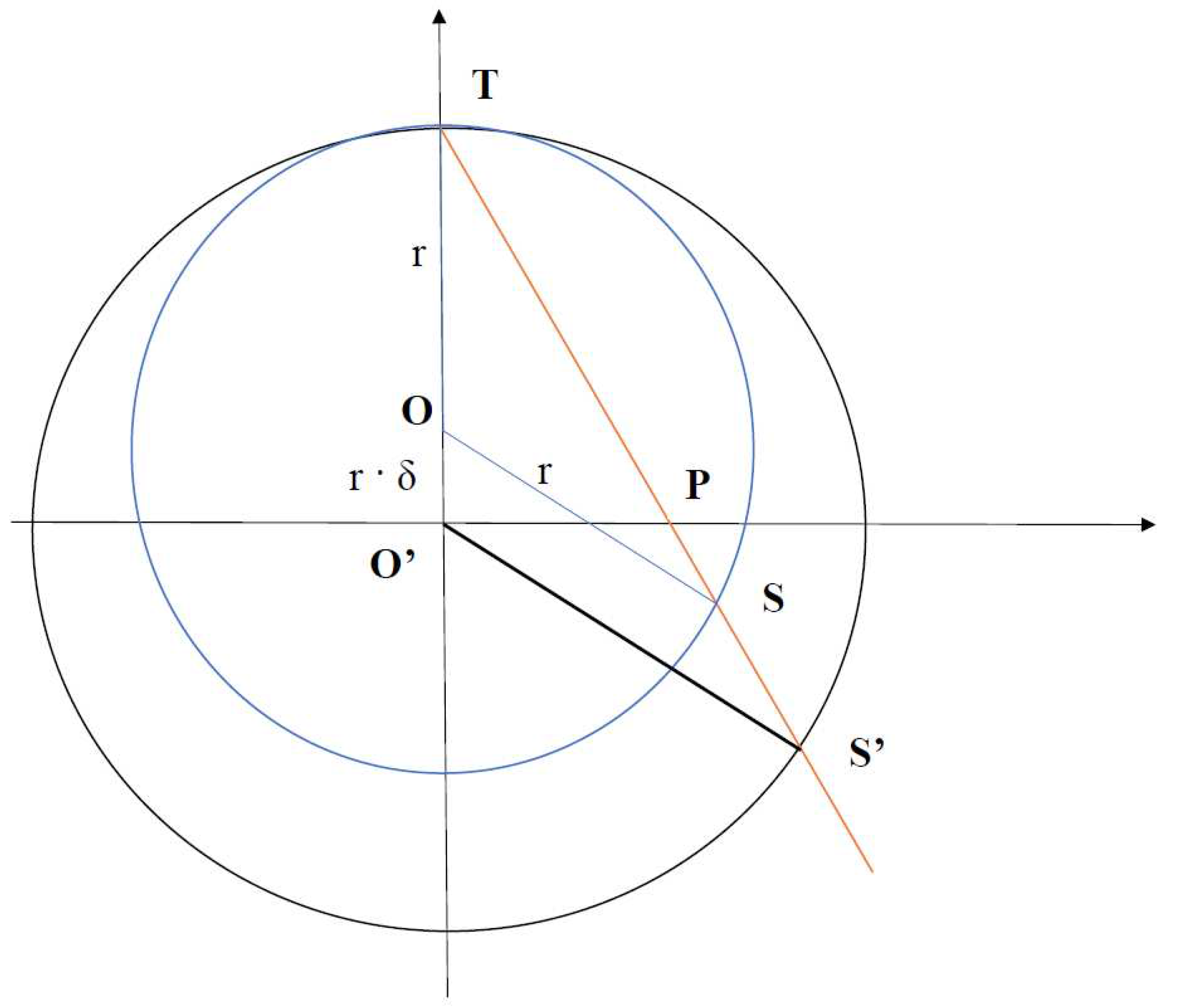
Appendix C. Stereographic Projection
Appendix C.1. ISP for General Radius
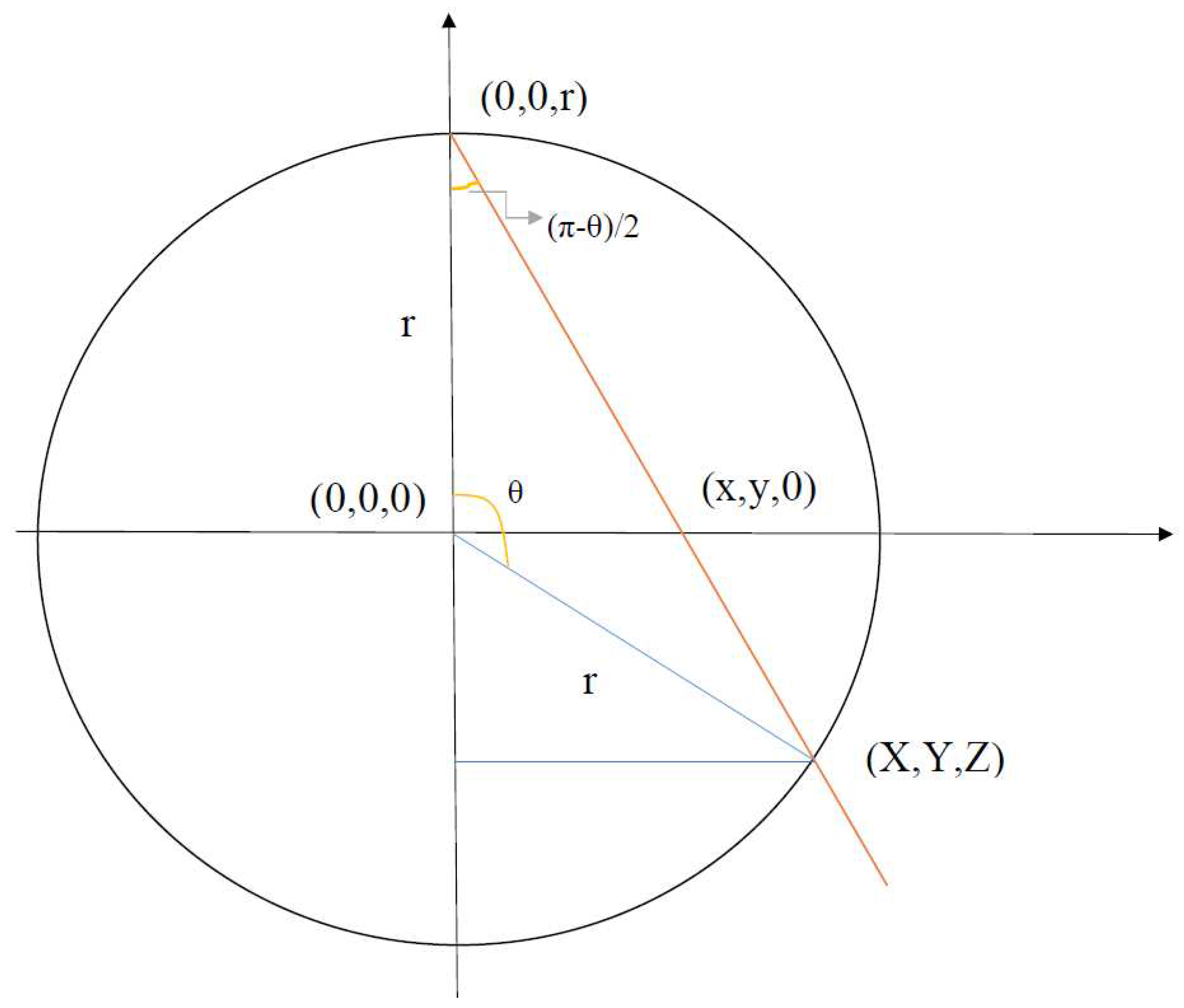
- 1.
- Azimuthal angle of the original point and the projected point must be the same, i.e. the original point, projected point, and the top of the sphere (the point from which all projections are drawn) lie on the same plane, which is perpendicular to the 2D plane.
- 2.
- The projected point lies on the sphere.
- 3.
- The triangle with vertices , and is similar to the triangle with vertices , and :
Appendix C.2. Equivalence of displacement and scaling
Appendix D. Ellipsoidal Embedding
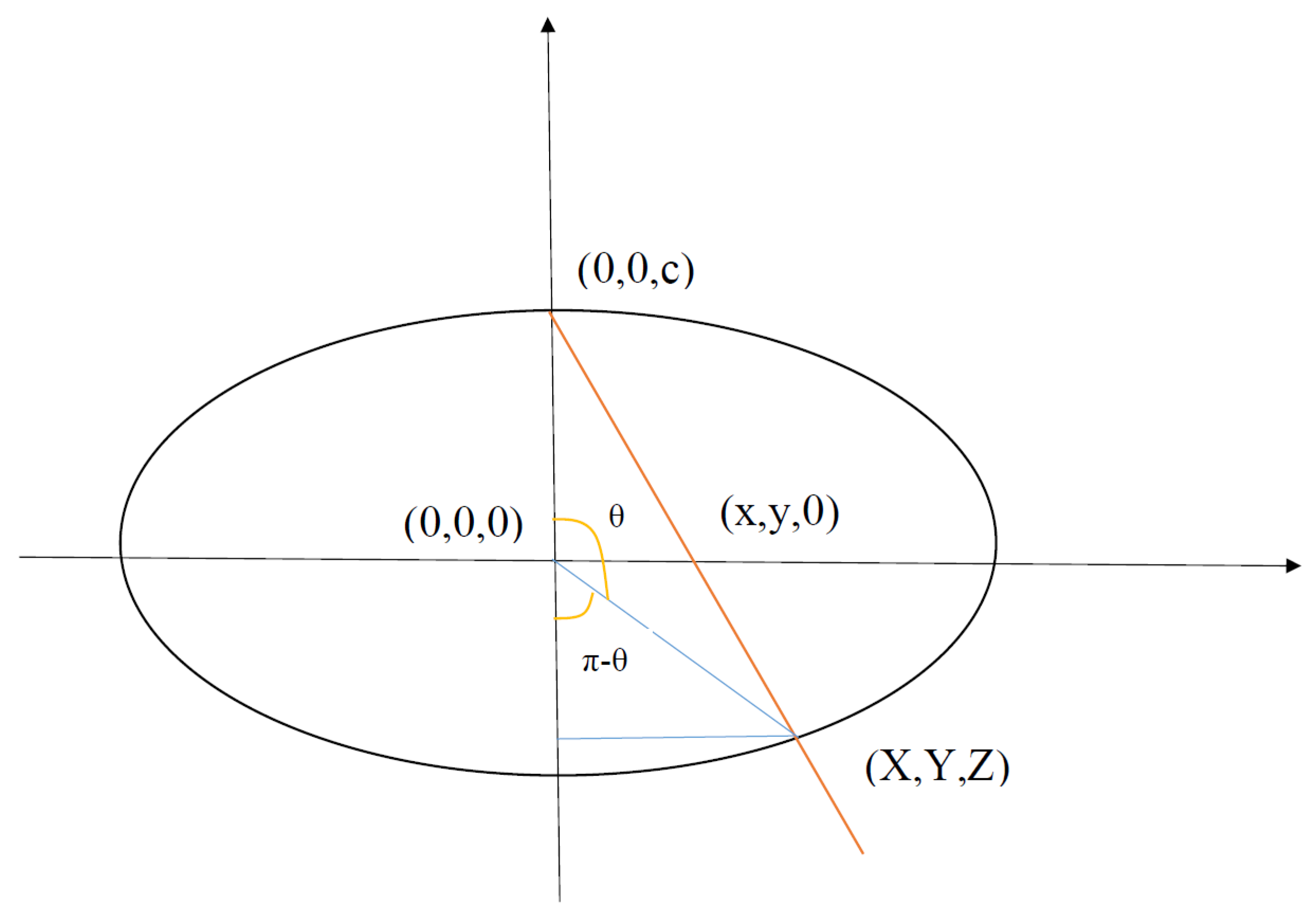
- 1.
- Azimuthal angle -
- 2.
- The projected point lies on the ellipsoid -
- 3.
- The triangle with vertices , and is similar to the triangle with vertices , and -
Appendix E. Distance Estimation using Stereographic Embedding
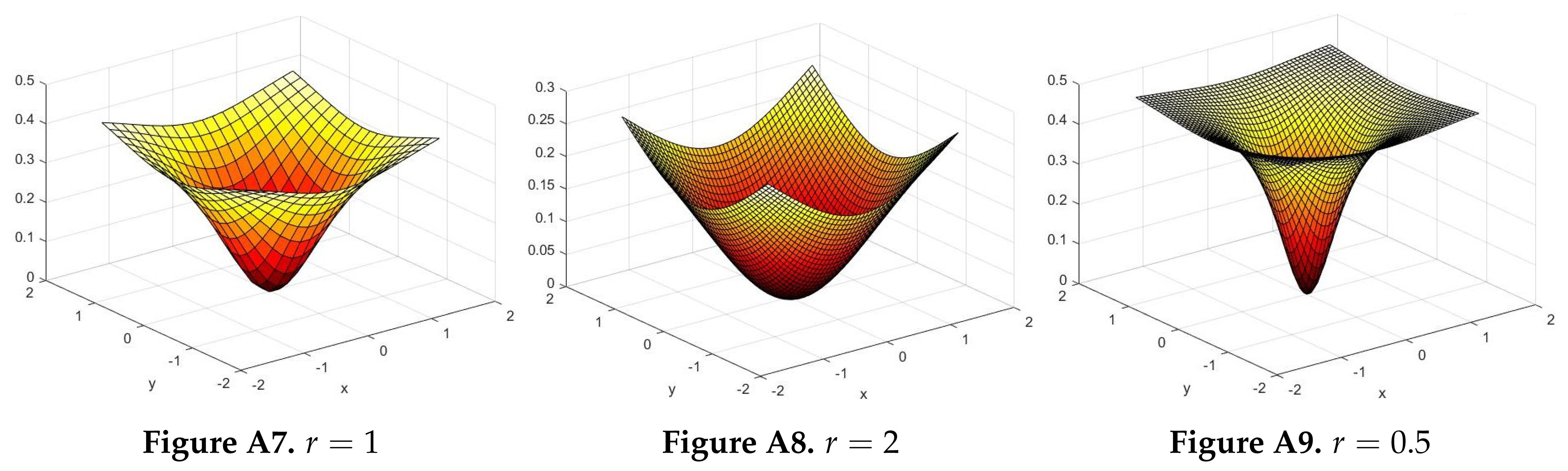 |
Appendix F. Rotation Gates and the UGate
References
- Harrow, A.W.; Hassidim, A.; Lloyd, S. Quantum Algorithm for Linear Systems of Equations. Physical Review Letters 2009, 103. [Google Scholar] [CrossRef] [PubMed]
- Lloyd, S.; Mohseni, M.; Rebentrost, P. Quantum algorithms for supervised and unsupervised machine learning. arXiv 2013, arXiv:1307.0411 2013. [Google Scholar]
- Preskill, J. Quantum Computing in the NISQ era and beyond. Quantum 2018, 2, 79. [Google Scholar] [CrossRef]
- Tang, E. Quantum Principal Component Analysis Only Achieves an Exponential Speedup Because of Its State Preparation Assumptions. Physical Review Letters 2021, 127. [Google Scholar] [CrossRef]
- Arute, F.; Arya, K.; Babbush, R.; Bacon, D.; Bardin, J.; Barends, R.; Biswas, R.; Boixo, S.; Brandao, F.; Buell, D.; Burkett, B.; et al. Quantum Supremacy using a Programmable Superconducting Processor. Nature 2019, 574, 505–510. [Google Scholar] [CrossRef] [PubMed]
- Schuld, M.; Petruccione, F. Supervised Learning with Quantum Computers; Quantum Science and Technology; Springer International Publishing, 2018. [Google Scholar]
- Schuld, M.; Sinayskiy, I.; Petruccione, F. An introduction to quantum machine learning. arXiv 2014, arXiv:1409.3097. [Google Scholar] [CrossRef]
- Kerenidis, I.; Prakash, A. Quantum Recommendation Systems. In Proceedings of the 8th Innovations in Theoretical Computer Science Conference (ITCS 2017); Leibniz International Proceedings in Informatics (LIPIcs). Papadimitriou, C.H., Ed.; Schloss Dagstuhl–Leibniz-Zentrum fuer Informatik: Dagstuhl, Germany, 2017; Volume 67, pp. 49:1–49:21. [Google Scholar] [CrossRef]
- Kerenidis, I.; Landman, J.; Luongo, A.; Prakash, A. q-means: A quantum algorithm for unsupervised machine learning. arXiv 2018, arXiv:1812.03584 2018. [Google Scholar]
- Pakala, L.; Schmauss, B. Non-linear mitigation using carrier phase estimation and k-means clustering. Photonic Networks; 16. ITG Symposium. VDE. 2015; 1–5. [Google Scholar]
- Zhang, J.; Chen, W.; Gao, M.; Shen, G. K-means-clustering-based fiber nonlinearity equalization techniques for 64-QAM coherent optical communication system. Optics express 2017, 25, 27570–27580. [Google Scholar] [CrossRef]
- Tang, E. Quantum Principal Component Analysis Only Achieves an Exponential Speedup Because of Its State Preparation Assumptions. Phys. Rev. Lett. 2021, 127, 060503. [Google Scholar] [CrossRef]
- Gambetta, J. IBM’s roadmap for scaling quantum technology.
- Martyn, J.M.; Rossi, Z.M.; Tan, A.K.; Chuang, I.L. A grand unification of quantum algorithms. arXiv 2021, arXiv:2105.02859 2021. [Google Scholar] [CrossRef]
- Kopczyk, D. Quantum machine learning for data scientists. arXiv 2018, arXiv:1804.10068 2018. [Google Scholar]
- Esma Aimeur, G.B.; Gambs, S. Quantum clustering algorithms. ICML ’07: Proceedings of the 24th international conference on Machine learning June 2007. 2007; 1–8. [Google Scholar]
- Cruise, J.R.; Gillespie, N.I.; Reid, B. Practical Quantum Computing: The value of local computation. arXiv 2020, arXiv:2009.08513 2020. [Google Scholar]
- Johri, S.; Debnath, S.; Mocherla, A.; Singh, A.; Prakash, A.; Kim, J.; Kerenidis, I. Nearest centroid classification on a trapped ion quantum computer. npj Quantum Information 2021, 7, 122. [Google Scholar] [CrossRef]
- Khan, S.U.; Awan, A.J.; Vall-Llosera, G. K-Means Clustering on Noisy Intermediate Scale Quantum Computers. arXiv 2019, arXiv:1909.12183 2019. [Google Scholar]
- Cortese, J.A.; Braje, T.M. Loading classical data into a quantum computer. arXiv 2018, arXiv:1803.01958 2018. [Google Scholar]
- Giovannetti, V.; Lloyd, S.; Maccone, L. Quantum Random Access Memory. Physical Review Letters 2008, 100. [Google Scholar] [CrossRef]
- Buhrman, H.; Cleve, R.; Watrous, J.; De Wolf, R. Quantum fingerprinting. arXiv 2001. [Google Scholar] [CrossRef]
- Ripper, P.; Amaral, G.; Temporão, G. Swap Test-based characterization of decoherence in universal quantum computers. Quantum Information Processing 2023, 22, 1–14. [Google Scholar] [CrossRef]
- Foulds, S.; Kendon, V.; Spiller, T. The controlled SWAP test for determining quantum entanglement. Quantum Science and Technology 2021, 6, 035002. [Google Scholar] [CrossRef]
- Tang, E. A Quantum-Inspired Classical Algorithm for Recommendation Systems. In Proceedings of the 51st Annual ACM SIGACT Symposium on Theory of Computing; STOC 2019. Association for Computing Machinery: New York, NY, USA, 2019; pp. 217–228. [Google Scholar] [CrossRef]
- Chia, N.H.; Lin, H.H.; Wang, C. Quantum-inspired sublinear classical algorithms for solving low-rank linear systems. arXiv 2018, arXiv:1811.04852 2018. [Google Scholar]
- Gilyén, A.; Lloyd, S.; Tang, E. Quantum-inspired low-rank stochastic regression with logarithmic dependence on the dimension. arXiv 2018, arXiv:1811.04909 2018. [Google Scholar]
- Arrazola, J.M.; Delgado, A.; Bardhan, B.R.; Lloyd, S. Quantum-inspired algorithms in practice. Quantum 2020, 4, 307. [Google Scholar] [CrossRef]
- Chia, N.H.; Gilyén, A.; Li, T.; Lin, H.H.; Tang, E.; Wang, C. Sampling-based sublinear low-rank matrix arithmetic framework for dequantizing Quantum machine learning. In Proceedings of the 52nd Annual ACM SIGACT Symposium on Theory of Computing; 2020. [Google Scholar] [CrossRef]
- Arrazola, J.M.; Delgado, A.; Bardhan, B.R.; Lloyd, S. Quantum-inspired algorithms in practice. Quantum 2020, 4, 307. [Google Scholar] [CrossRef]
- Chia, N.H.; Gilyén, A.; Lin, H.H.; Lloyd, S.; Tang, E.; Wang, C. Quantum-Inspired Algorithms for Solving Low-Rank Linear Equation Systems with Logarithmic Dependence on the Dimension. In Proceedings of the 31st International Symposium on Algorithms and Computation (ISAAC 2020); Leibniz International Proceedings in Informatics (LIPIcs). Cao, Y., Cheng, S.W., Li, M., Eds.; Schloss Dagstuhl–Leibniz-Zentrum für Informatik: Dagstuhl, Germany, 2020; Volume 181, pp. 47:1–47:17. [Google Scholar] [CrossRef]
- Sergioli, G.; Santucci, E.; Didaci, L.; Miszczak, J.A.; Giuntini, R. A quantum-inspired version of the nearest mean classifier. Soft Computing 2018, 22, 691–705. [Google Scholar] [CrossRef]
- Sergioli, G.; Bosyk, G.M.; Santucci, E.; Giuntini, R. A quantum-inspired version of the classification problem. International Journal of Theoretical Physics 2017, 56, 3880–3888. [Google Scholar] [CrossRef]
- Subhi, G.M.; Messikh, A. Simple quantum circuit for pattern recognition based on nearest mean classifier. International Journal on Perceptive and Cognitive Computing 2016, 2. [Google Scholar] [CrossRef]
- Nguemto, S.; Leyton-Ortega, V. Re-QGAN: an optimized adversarial quantum circuit learning framework. arXiv 2022. [Google Scholar] [CrossRef]
- Eybpoosh, K.; Rezghi, M.; Heydari, A. Applying inverse stereographic projection to manifold learning and clustering. Applied Intelligence 2022, 52, 4443–4457. [Google Scholar] [CrossRef]
- Poggiali, A.; Berti, A.; Bernasconi, A.; Del Corso, G.; Guidotti, R. Quantum Clustering with k-Means: a Hybrid Approach. arXiv 2022, arXiv:2212.06691 2022. [Google Scholar]
- de Veras, T.M.L.; de Araujo, I.C.S.; Park, D.K.; da Silva, A.J. Circuit-Based Quantum Random Access Memory for Classical Data With Continuous Amplitudes. IEEE Transactions on Computers 2021, 70, 2125–2135. [Google Scholar] [CrossRef]
- Hornik, K.; Feinerer, I.; Kober, M.; Buchta, C. Spherical k-Means Clustering. Journal of Statistical Software 2012, 50, 1–22. [Google Scholar] [CrossRef]
- Feng, C.; Zhao, B.; Zhou, X.; Ding, X.; Shan, Z. An Enhanced Quantum K-Nearest Neighbor Classification Algorithm Based on Polar Distance. Entropy 2023, 25. [Google Scholar] [CrossRef] [PubMed]
- Diedolo, F.; Böcherer, G.; Schädler, M.; Calabró, S. Nonlinear Equalization for Optical Communications Based on Entropy-Regularized Mean Square Error. In Proceedings of the European Conference on Optical Communication (ECOC) 2022; Optica Publishing Group. 2022; p. We2C.2. [Google Scholar]
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information; Cambridge University Press, 2000. [Google Scholar]
- Lloyd, S. Least squares quantization in PCM. IEEE Transactions on Information Theory 1982, 28, 129–137. [Google Scholar] [CrossRef]
- Schubert, E.; Lang, A.; Feher, G. Accelerating Spherical k-Means. Similarity Search and Applications; Reyes, N., Connor, R., Kriege, N., Kazempour, D., Bartolini, I., Schubert, E., Chen, J.J., Eds.; Springer International Publishing: Cham, 2021; pp. 217–231. [Google Scholar]
- Ahlfors, L.V. Complex Analysis, 2nd ed.; McGraw-Hill Book Company, 1996. [Google Scholar]
- LaRose, R.; Coyle, B. Robust data encodings for quantum classifiers. Physical Review A 2020, 102. [Google Scholar] [CrossRef]
- Weigold, M.; Barzen, J.; Leymann, F.; Salm, M. Expanding Data Encoding Patterns For Quantum Algorithms. Proceedings of the 2021 IEEE 18th International Conference on Software Architecture Companion (ICSA-C) 2021, 95–101. [Google Scholar] [CrossRef]
- Fanizza, M.; Rosati, M.; Skotiniotis, M.; Calsamiglia, J.; Giovannetti, V. Beyond the Swap Test: Optimal Estimation of Quantum State Overlap. Physical Review Letters 2020, 124. [Google Scholar] [CrossRef]
- Foulds, S.; Kendon, V.; Spiller, T. The controlled SWAP test for determining quantum entanglement. Quantum Science and Technology 2021, 6, 035002. [Google Scholar] [CrossRef]
- Microsystems, B. Digital modulation efficiencies.
- Frenzel, L.E. Electronics Explained: Fundamentals for Engineers, Technicians, and Makers; Newnes, 2018. [Google Scholar]
- Plesch, M.; Brukner, Č. Quantum-state preparation with universal gate decompositions. Physical Review A 2011, 83, 032302. [Google Scholar] [CrossRef]
- Quantum Computing Patterns. Available online: https://quantumcomputingpatterns.org/ (accessed on 30 October 2021).
- Roy, B. All about Data Encoding for Quantum Machine Learning. 2021. Available online: https://medium.datadriveninvestor.com/all-about-data-encoding-for-quantum-machine-learning-2a7344b1dfef.
| 1 | This might not be true for other definitions of quantum dissimilarity, as for example in Section 3.4 where we redefine it to include embedding into mixed states. |
| 2 | This is obtained as in Figure 2 where the Hadamard is replaced with the Fourier transform and the CNOT with . If instead of qudits we have multiple qubits then the solution is even simpler: just perform a qubit Bell measurement with each pair of qubits. This is because . |
| Algorithm | Reference | Dataset | Initial | Dataspace | Dissimilarity | Centroid |
| Centroids | Update | |||||
| D | d | |||||
| 2DEC-kNN | Definition 4 | D | ||||
| 3DSC-kNN | Definition 6 | |||||
| 2DSC-kNN | Definition 12 | (or ) | ||||
| SQ-kNN | Definition 10 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





