Submitted:
02 May 2023
Posted:
02 May 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
- 1
- Extending and balancing the CIDAD dataset using GANs.
- 2
- Focusing on the CoAP level features to ensure securing CoAP in its vicinity.
- 3
- Build a machine learning model that can classify the benign against malware with an accuracy of 98% using the decision tree algorithm.
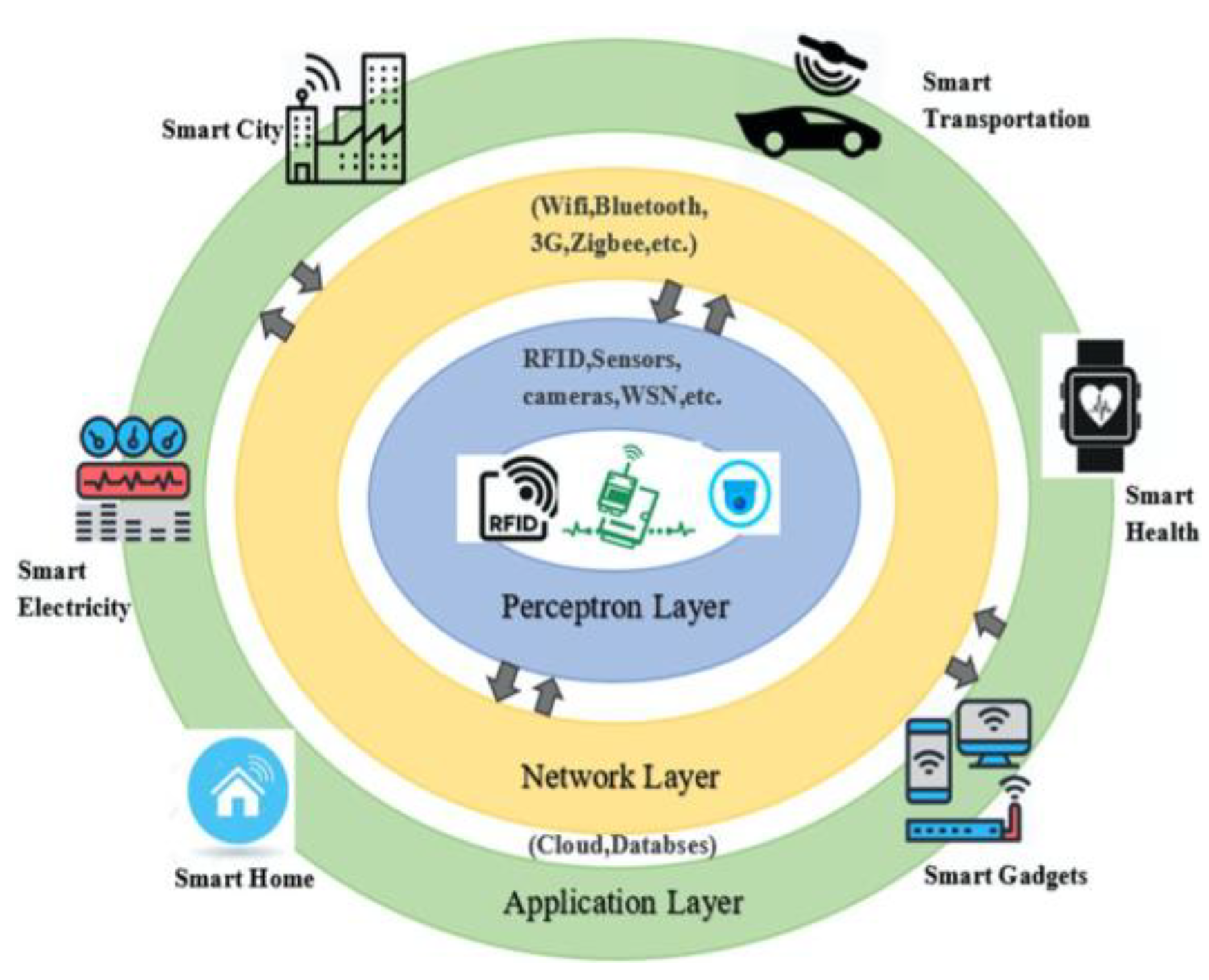
1.1. IoT Overview
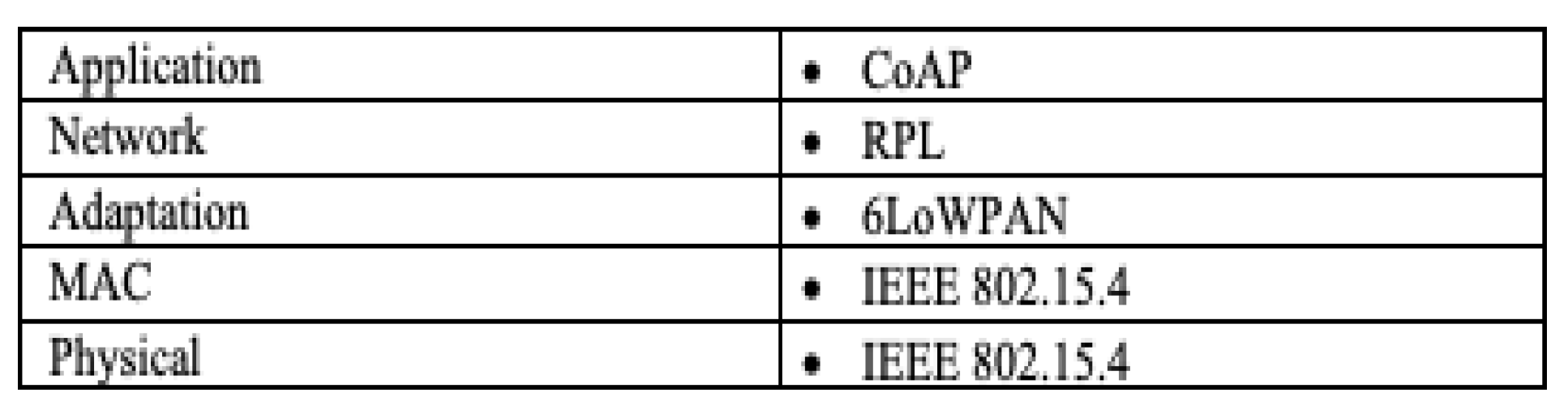
1.2. IoT Protocols
- 1
- IEEE 802.15.4 Protocol
- 2
- 6LoWPAN protocol
- 3
- Routing – RPL protocol
- 4
- CoAP Protocol
1.2.1. CoAP Architecture
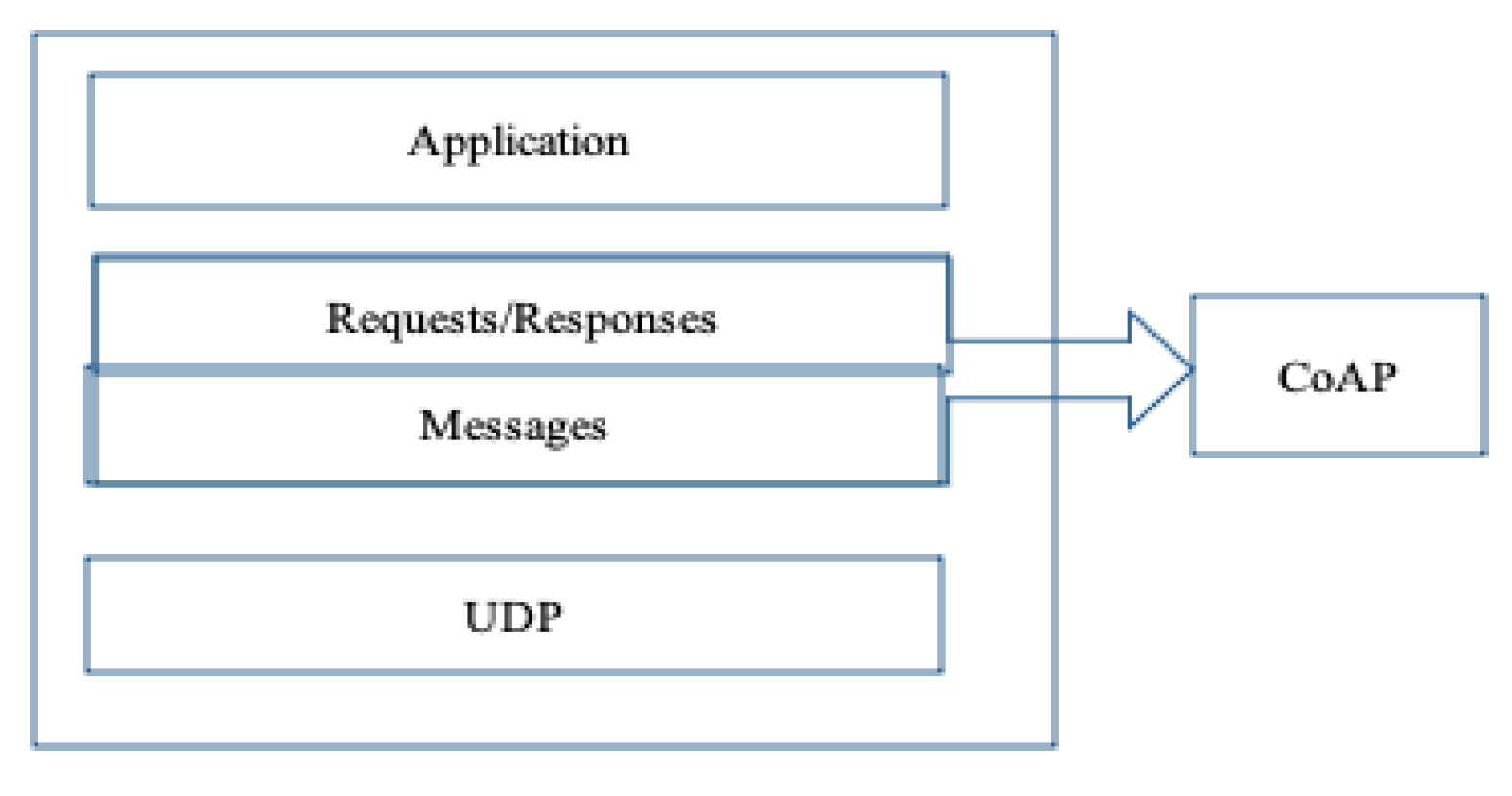
1.2.2. Messaging Model
- 1
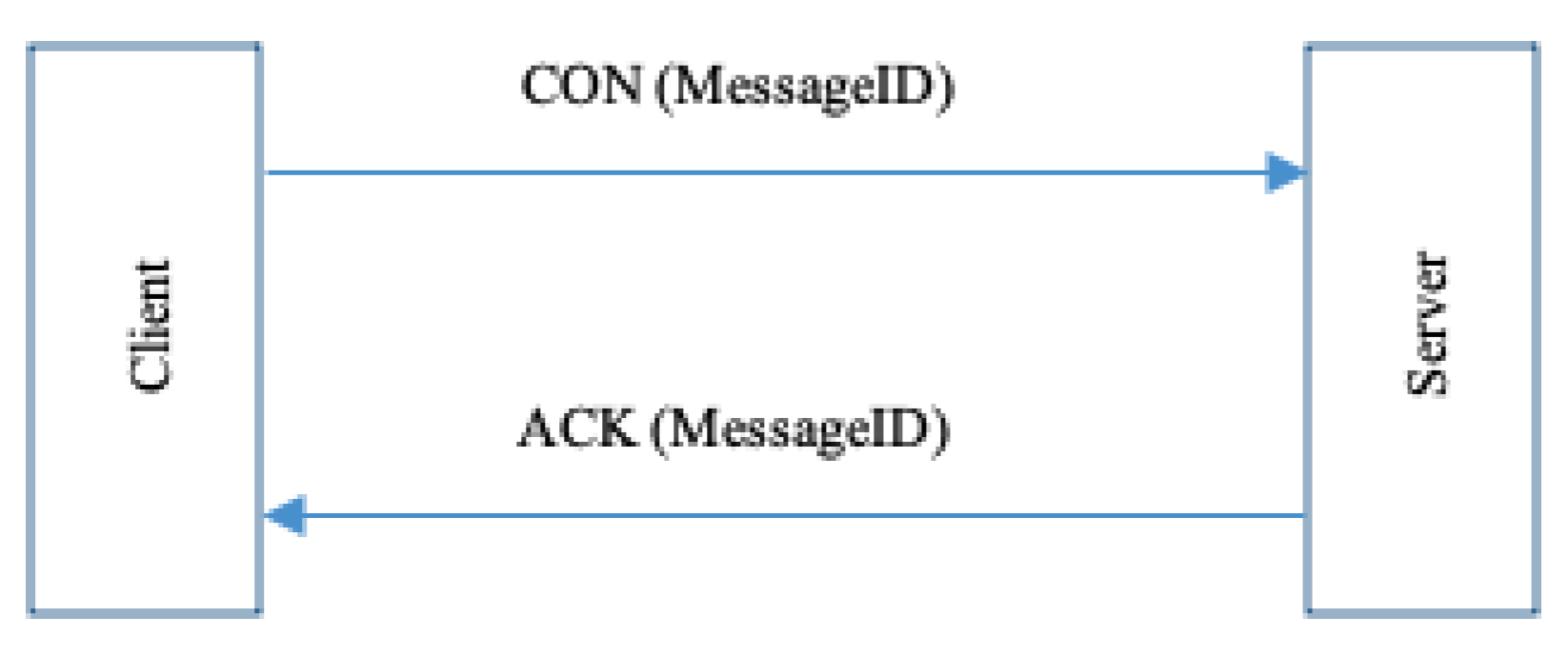
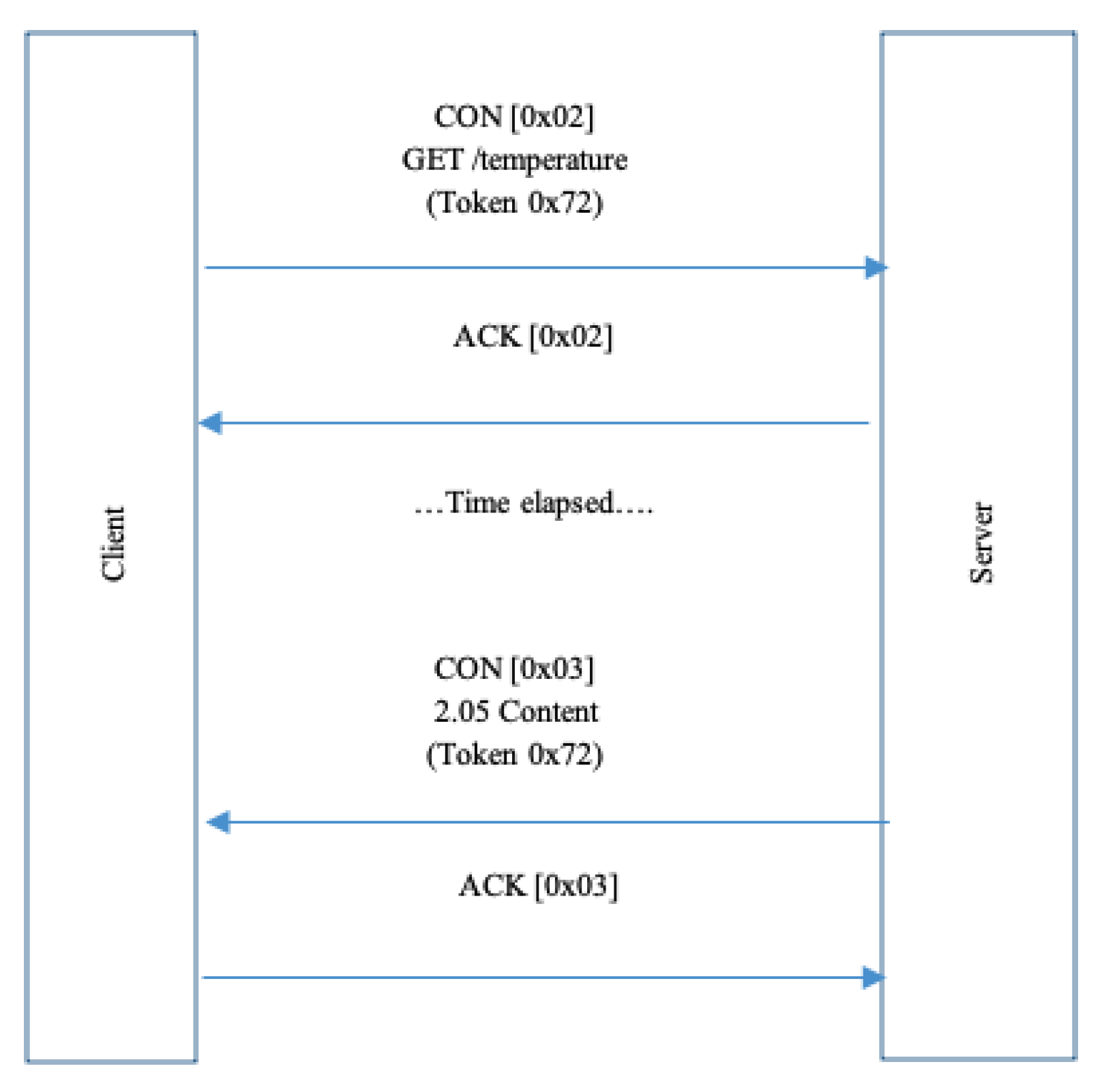
- Confirmable Message (CON): in this mode, all messages are marked as confirmable messages (reliable mode). The message is resent using a default timeout till receiving an Acknowledgement from the recipient with the same messageID as the sender. If the recipient failed to process the confirmable message, the recipient will send a reset message (RST) instead of (ACK) to reset the communication. Figure 4 shows the confirmable mode between the client and the server.
- 2
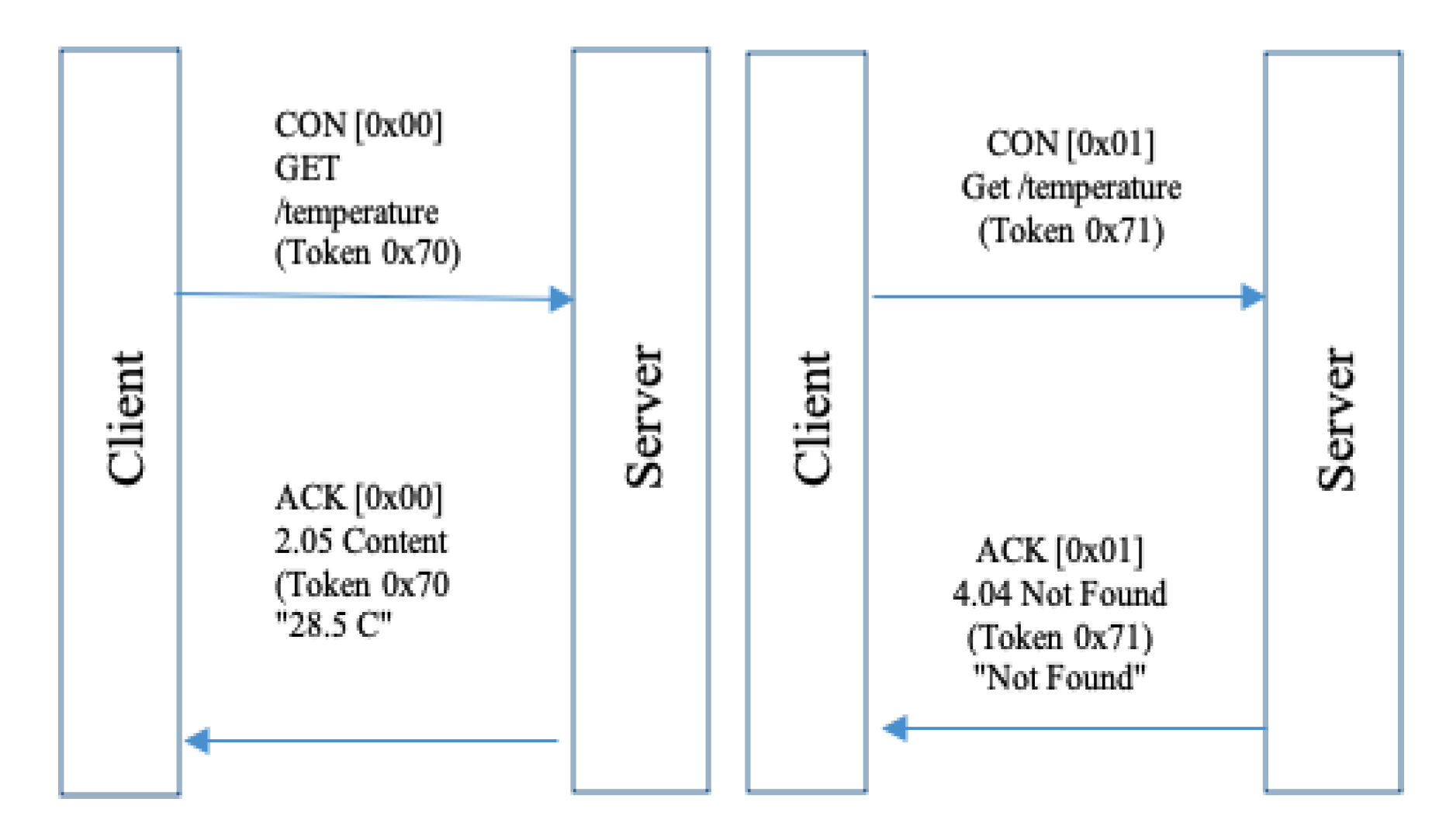
- Non-Confirmable Message (NON): if reliable delivery is not desired, the message can be sent as a non-confirmable message (unreliable mode). For duplication check purposes, the message is not acknowledged but still has a messageID. Besides, the recipient could send a reset message if it failed to respond to the NON-message. Figure5 depicts the NON-message between the client and the server.
1.2.3. Request/Response Model
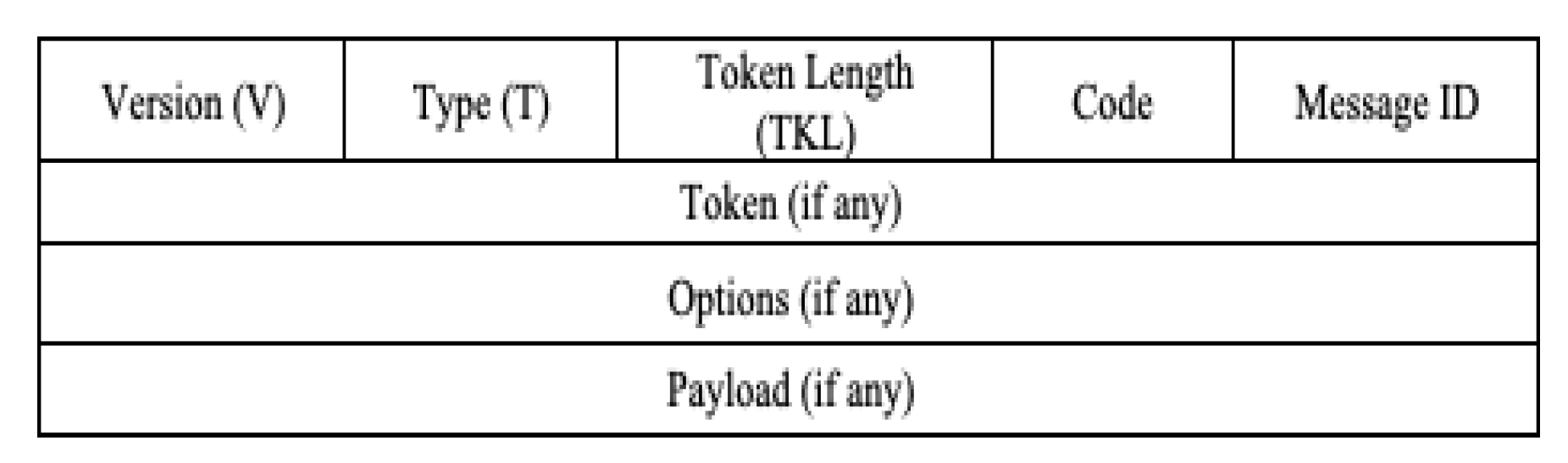
1.2.4. Message Format
- (1)
- Version (V): unsigned integer (2-bit) that represents the CoAP version number. This field takes (01 binary), and other values are reserved for future versions. If the message comes with unknown version numbers, it must be ignored.
- (2)
- Type (T): unsigned integer (2-bit) that represents 0 for Confirmable, 1 for Non-Confirmable, 2 for Acknowledgement, or 3 for reset as illustrated in the previous section.
- (3)
- Token Length (TKL): unsigned integer (4-bit) with a length of 0 to 8 bytes. Lengths 9-15 are specialized for message format errors.
- (4)
- Code: unsigned integer (8-bit) that is divided into the most significant bits (3-bit) and the least significant bit (5-bit). It is represented as "c.dd" ("c" can be 0-7 as a digit for the 3-bit, and "dd" can be two digits in the range from 00 to 31 for the 5-bit). The most significant bits view 0 for a request, 2 for a successful response, 4 for a client error response, or 5 for a server error response. The other most significant bits are reserved. The code 0.00 represents an Empty message as a special case.
- (5)
- MessageID: unsigned integer (16-bit) used for duplicate vetting purposes. It is also used to match Acknowledgement/Reset messages to messages of type Confirmable or Non-Confirmable, respectively.
- (6)
- Token: maybe 0 to 8 bytes based on the length stated in the TKL field. It is used to correlate requests and responses.
- (7)
- Options: can be 0, by another option, or by the payload.
- (8)
- Payload: if exists, it is prefixed by a (0xFF) marker as a benchmark for payload start. To calculate the length of the payload, it is counted from the end of the marker until the UDP datagram end.
1.2.5. Method Definitions
GET
POST
PUT
DELETE
1.2.6. CoAP URIs
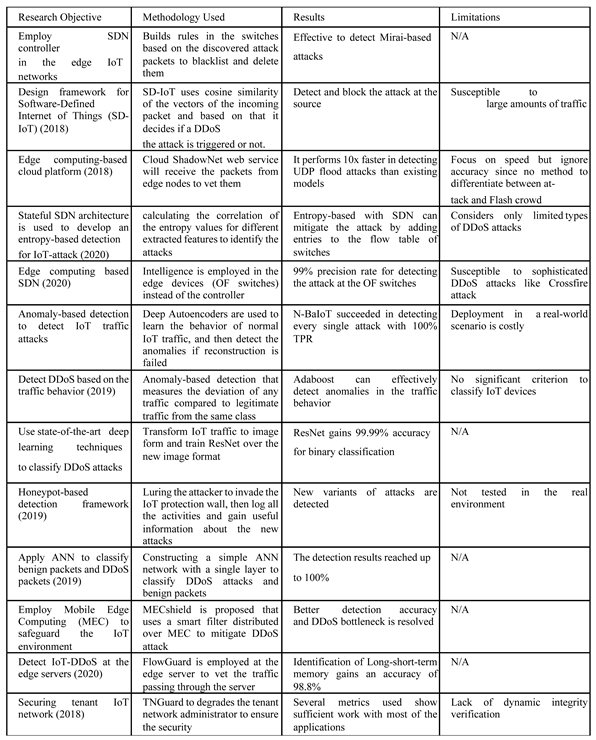
2. Literature Review
2.1. DDoS attacks in IoT
- A.
- Mirai
- B.
- Wirex
- C.
- Reaper
- D.
- Torri
Taxonomy of DDoS attacks in IoT network
2.2. Proposed defense mechanisms for IoT Network
2.2.1. SDN Platform for IoT network security
2.2.2. Machine Learning and Deep Learning for IoT network security
2.2.3. Cloud Platform for IoT network security
2.3. CoAP Security Overview
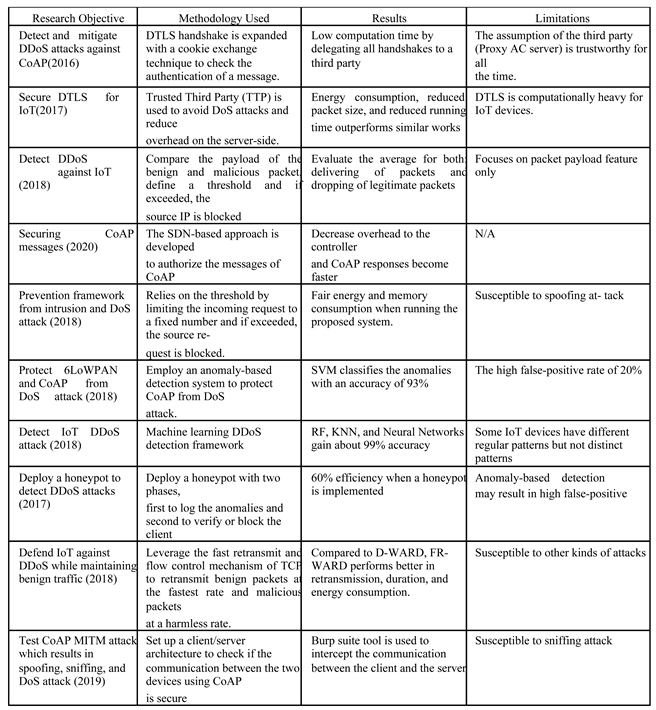
2.3.1. Proposed defense mechanisms for Securing CoAP against DDoS Attacks
DTLS for CoAP Security
SDN for CoAP Security
Machine Learning for CoAP Security
Other Methods for CoAP Security
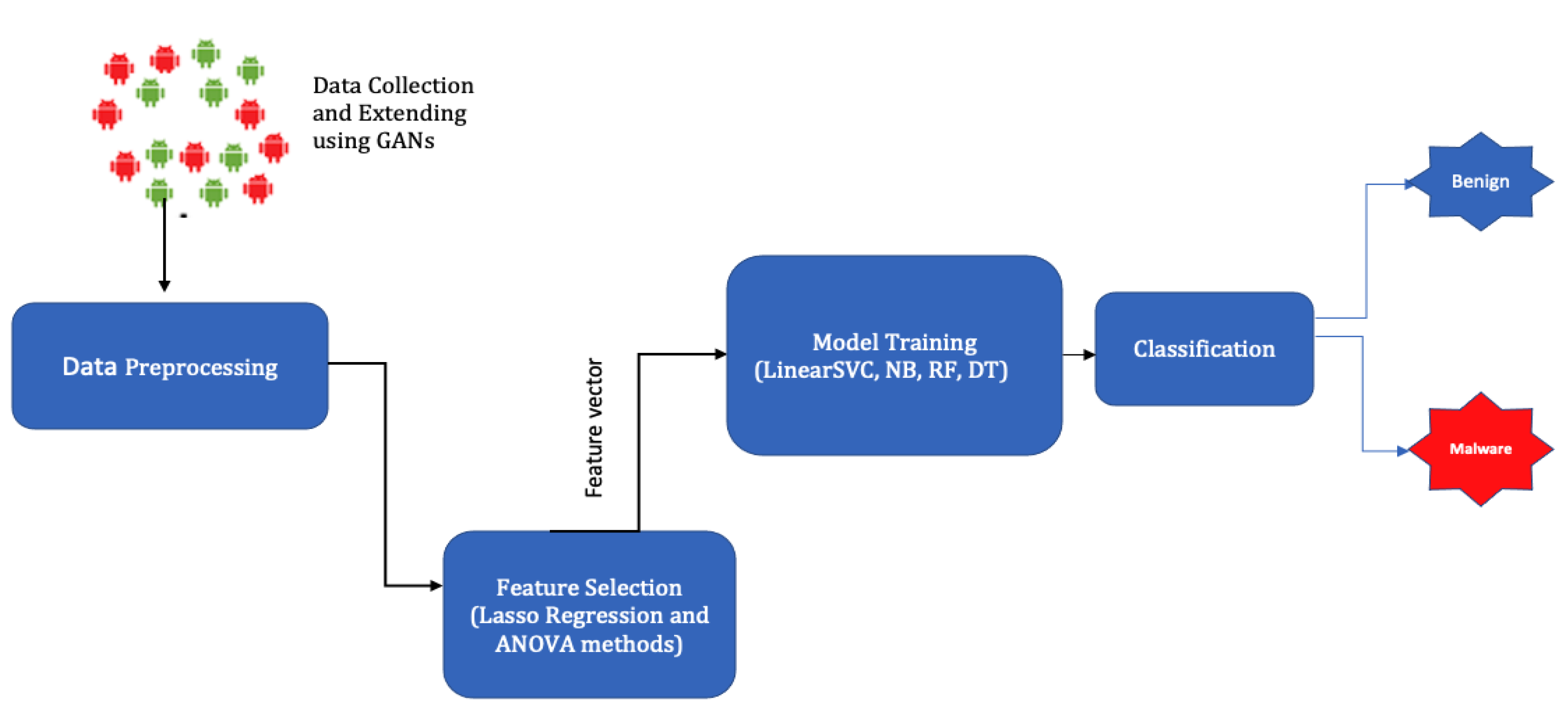
3. Materials and Methods
3.1. Dataset Collection
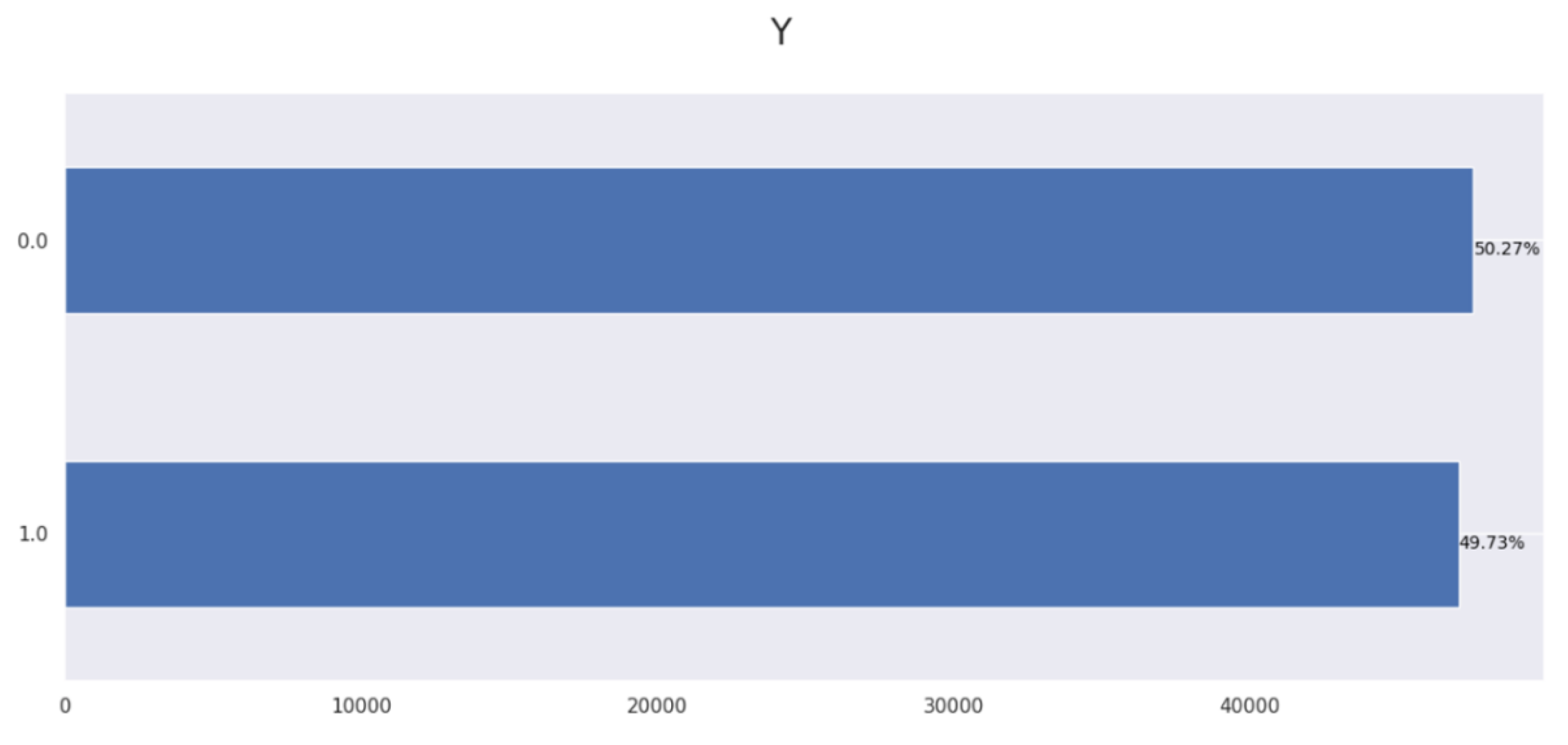
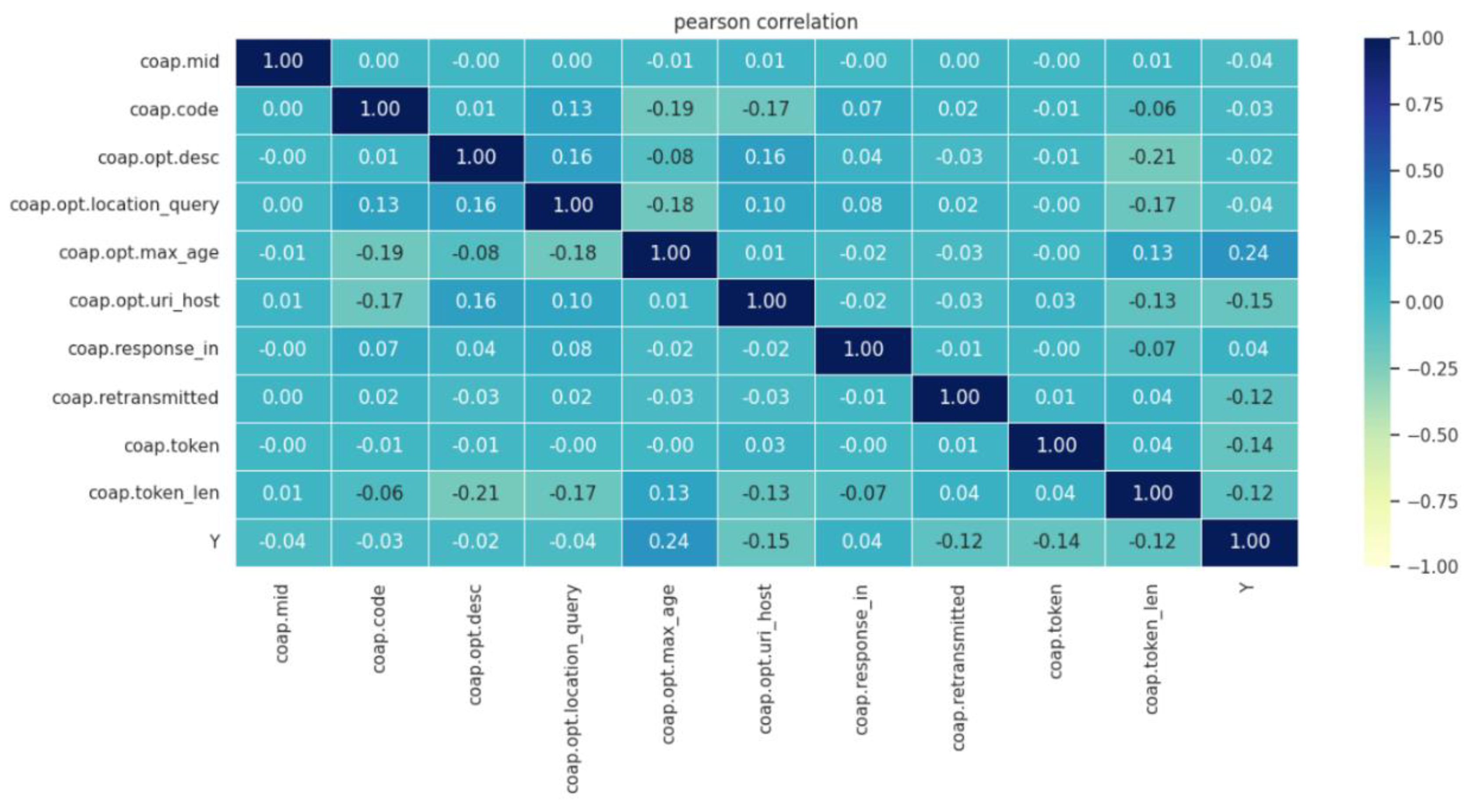
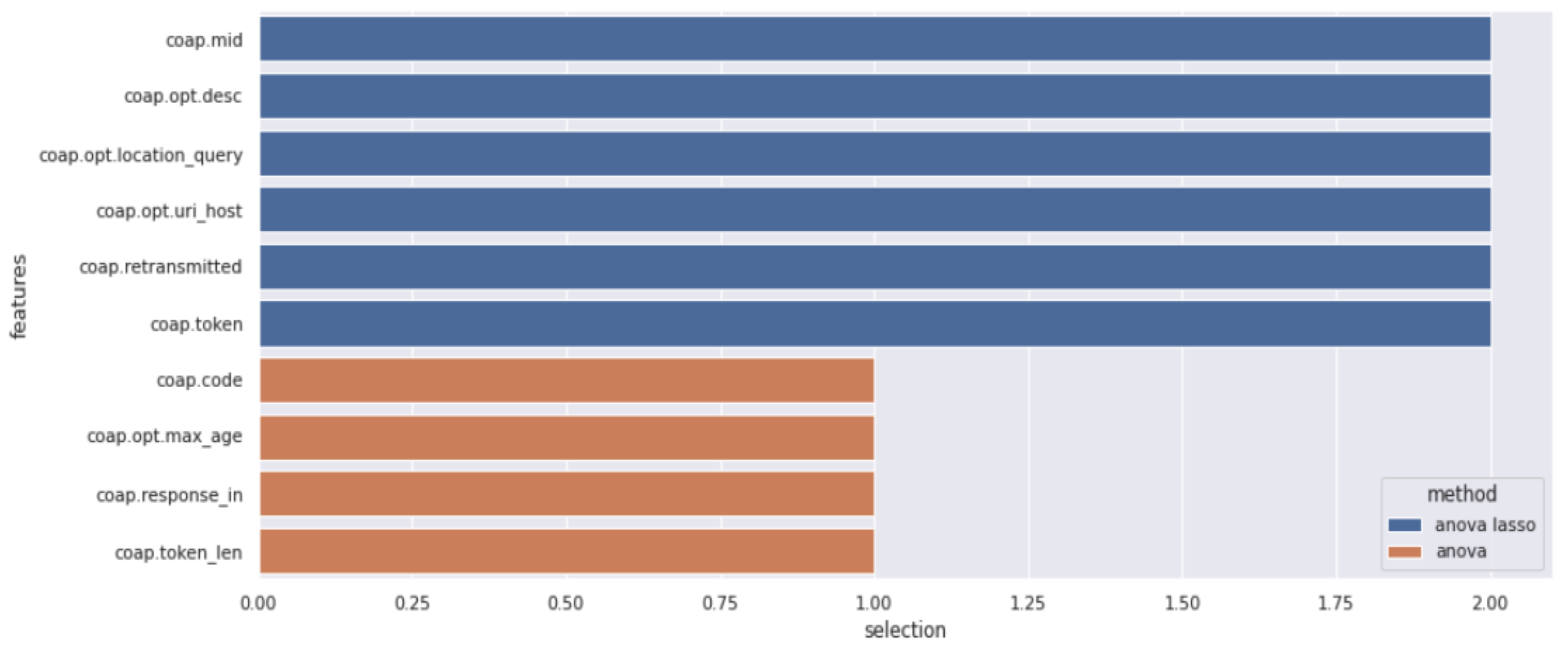
3.2. Feature Extraction
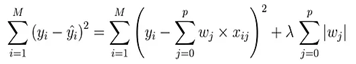
3.3. Model Training
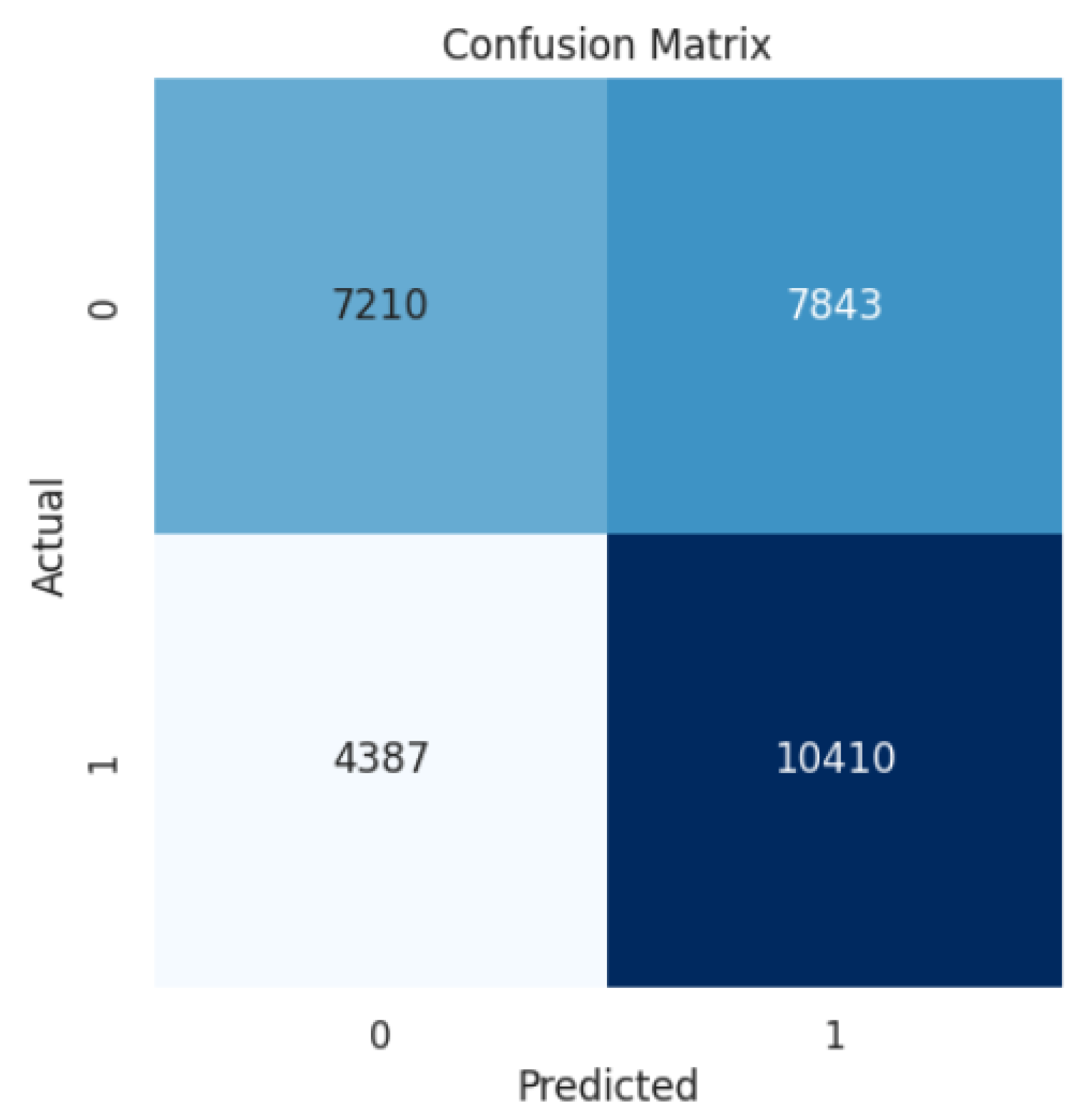
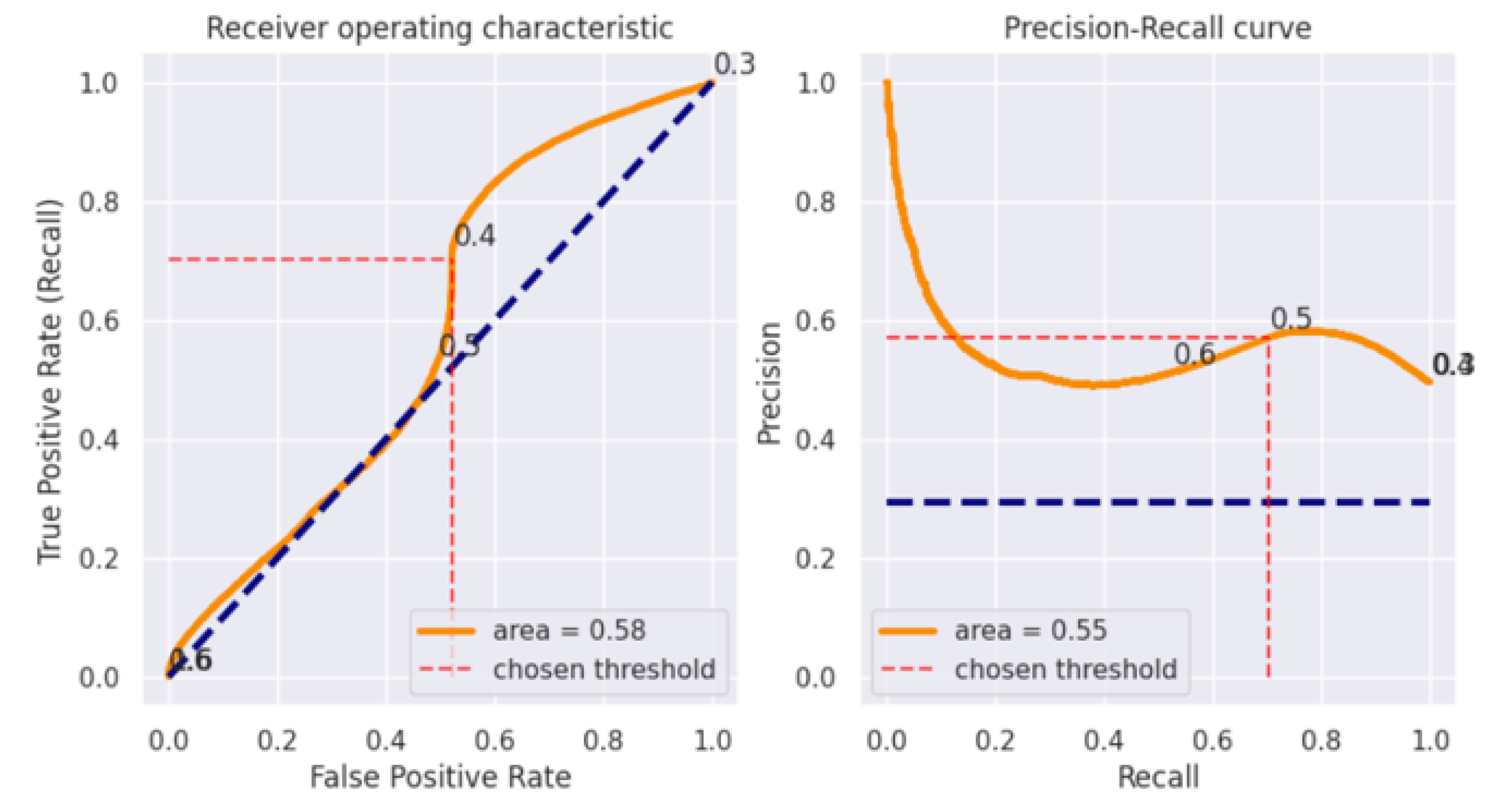
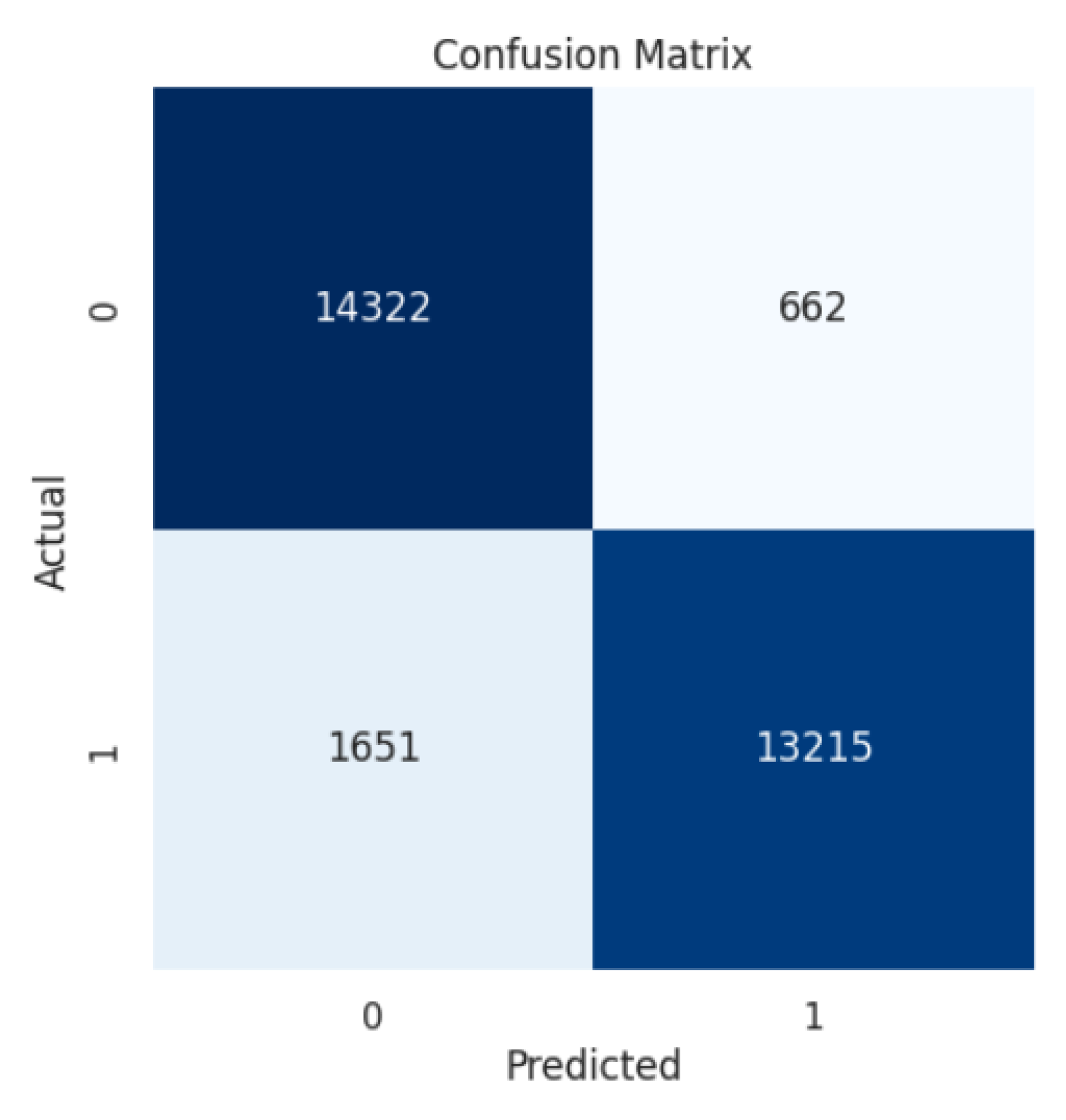
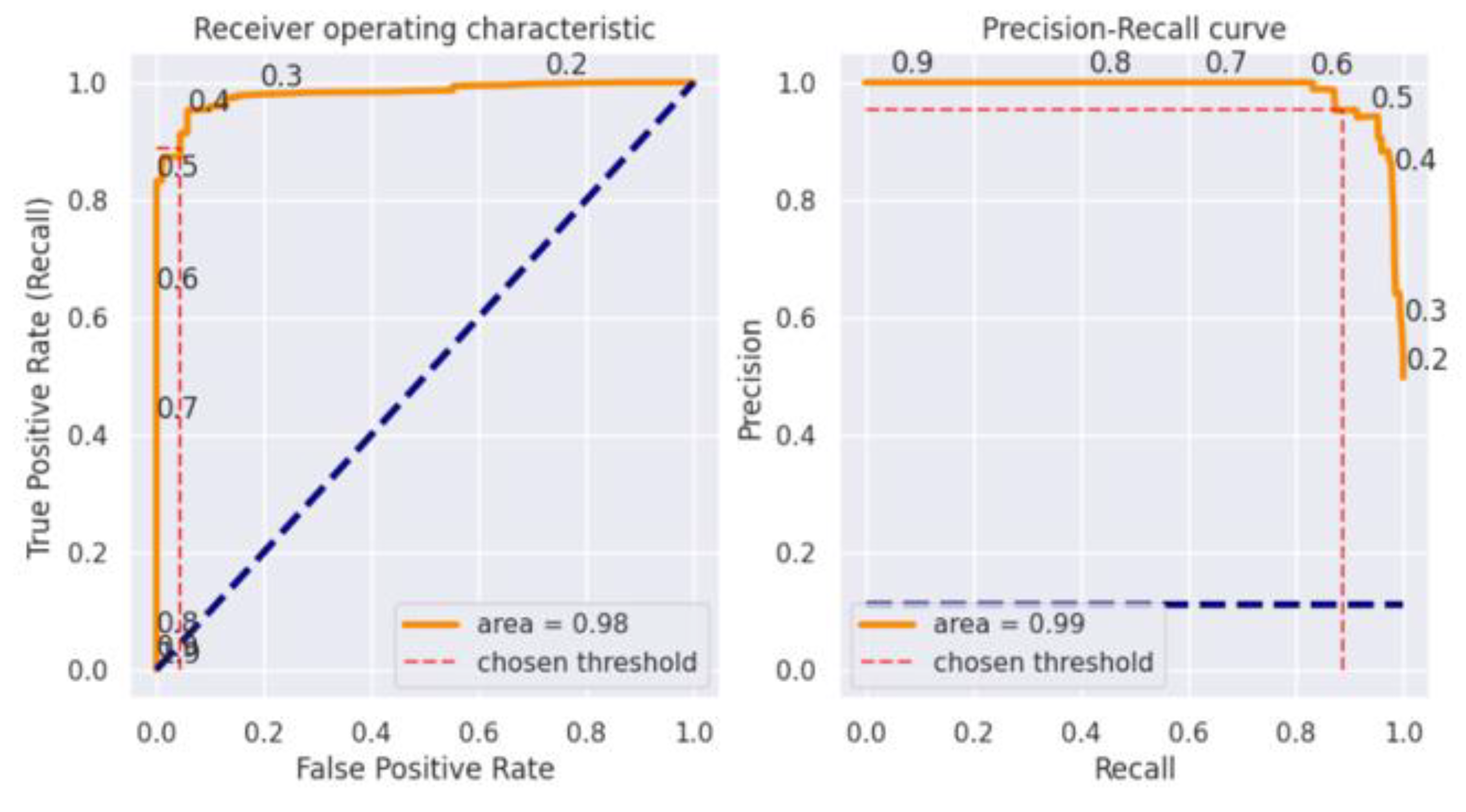
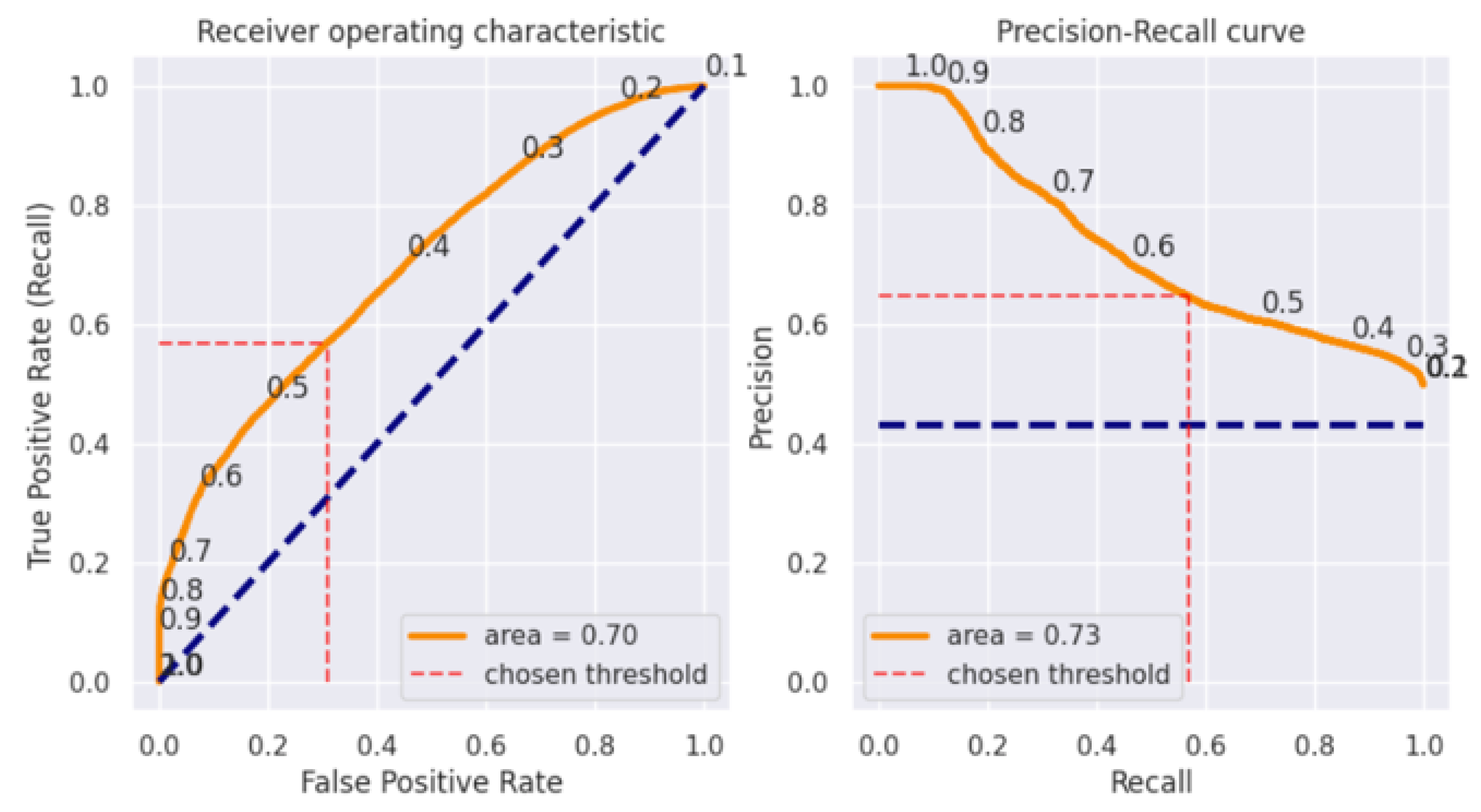
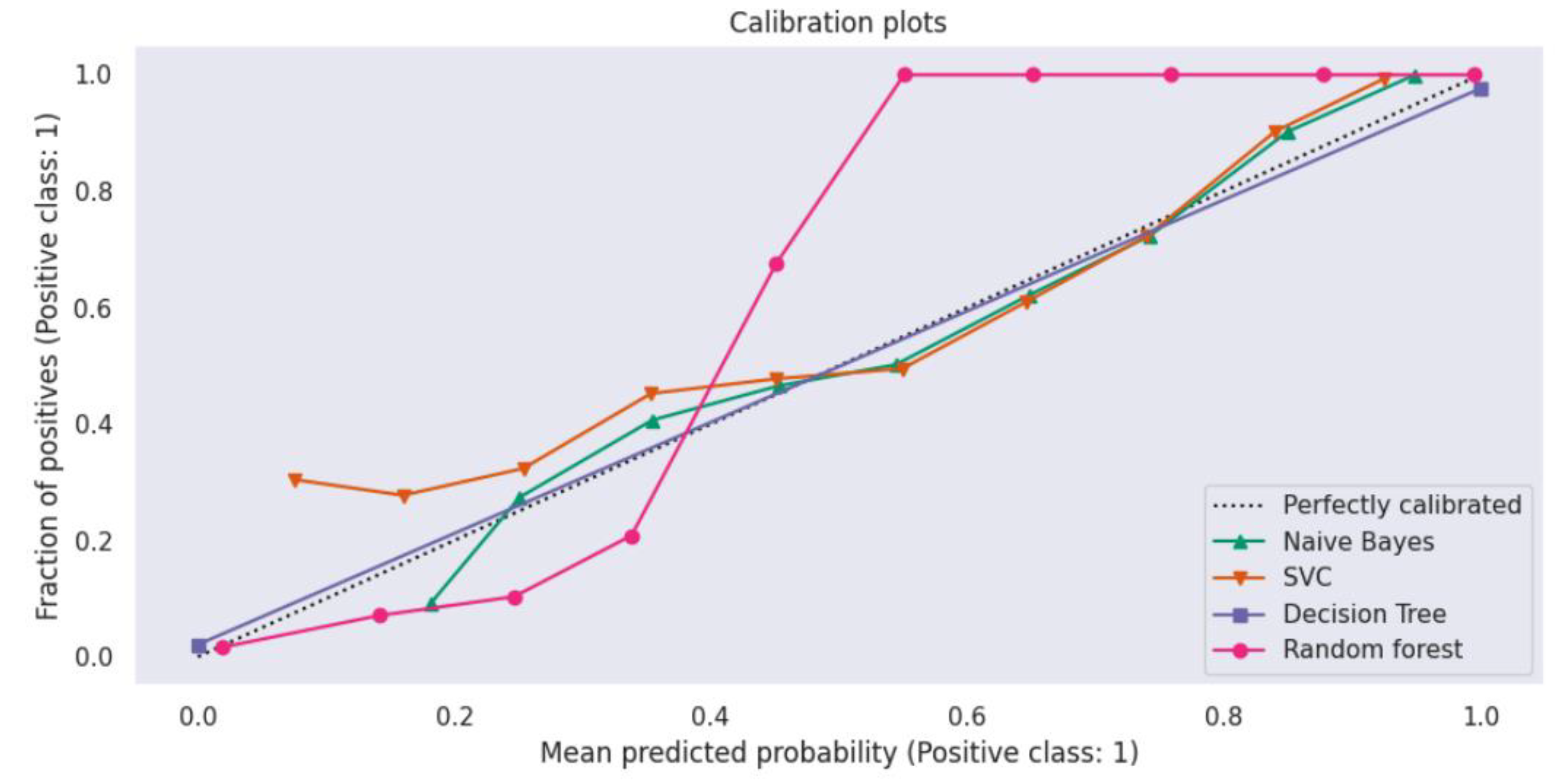
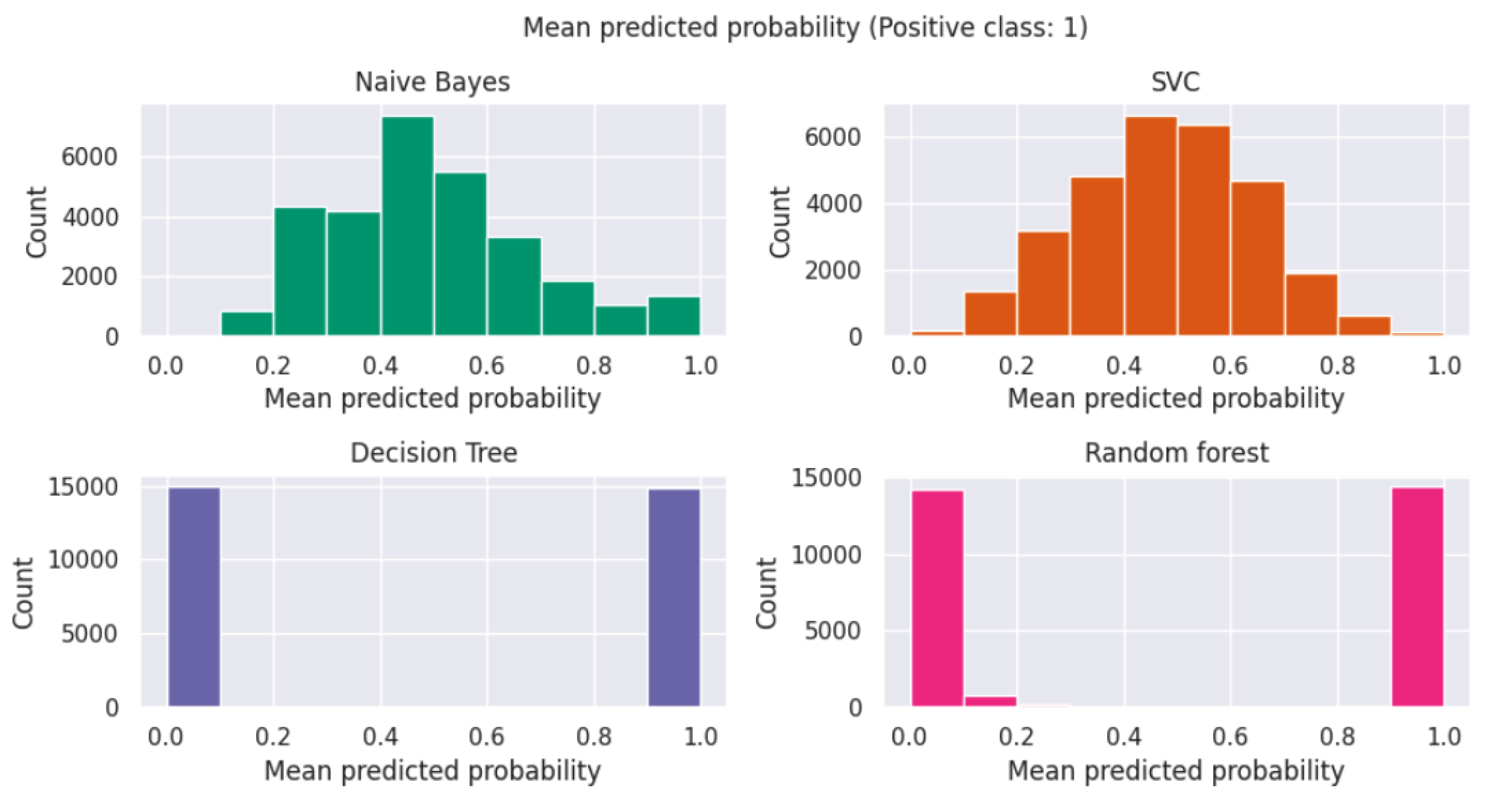
4. Results
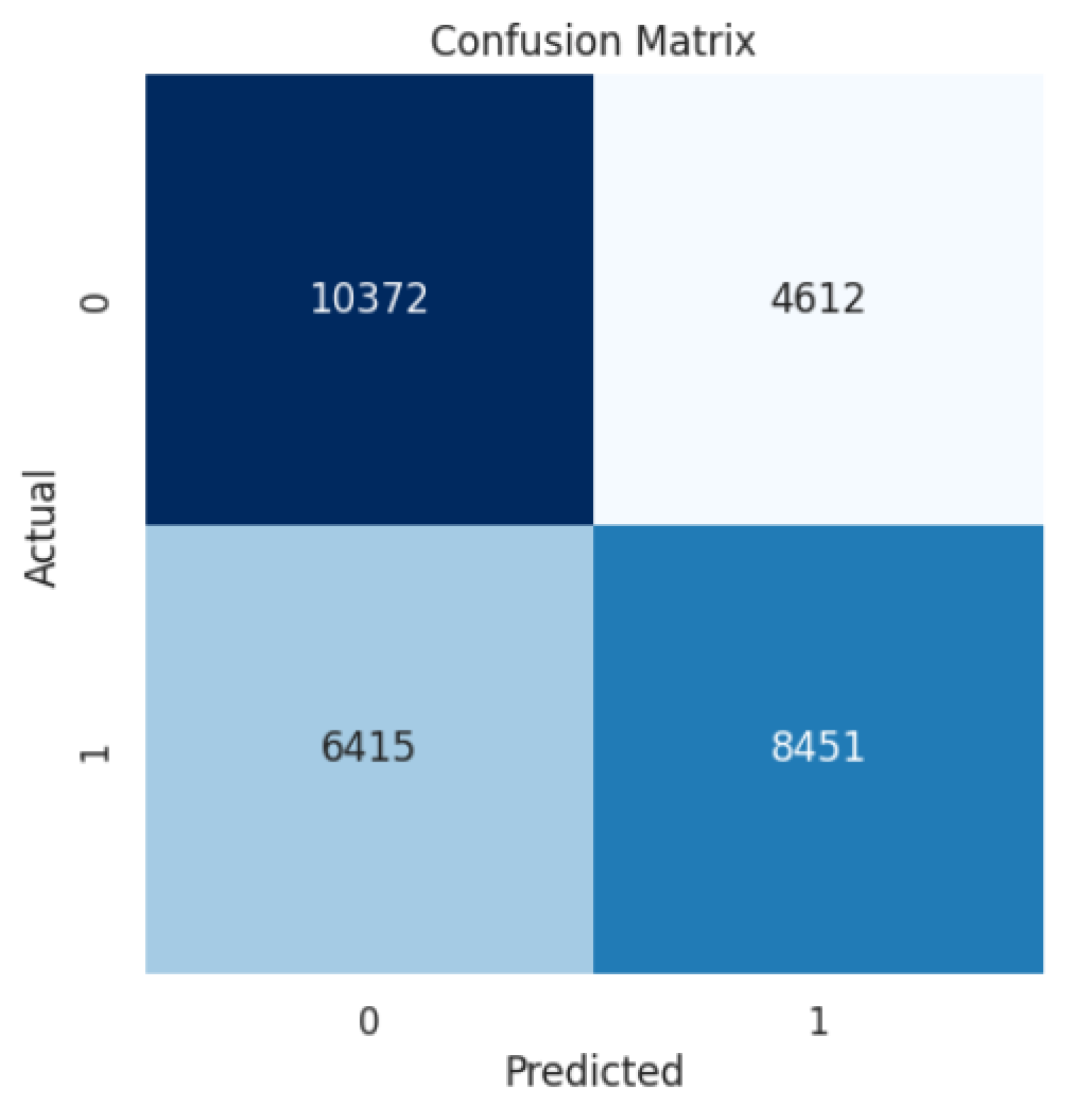
4.1. LinearSVC
4.2. Random Forest
4.3. Decision Tree
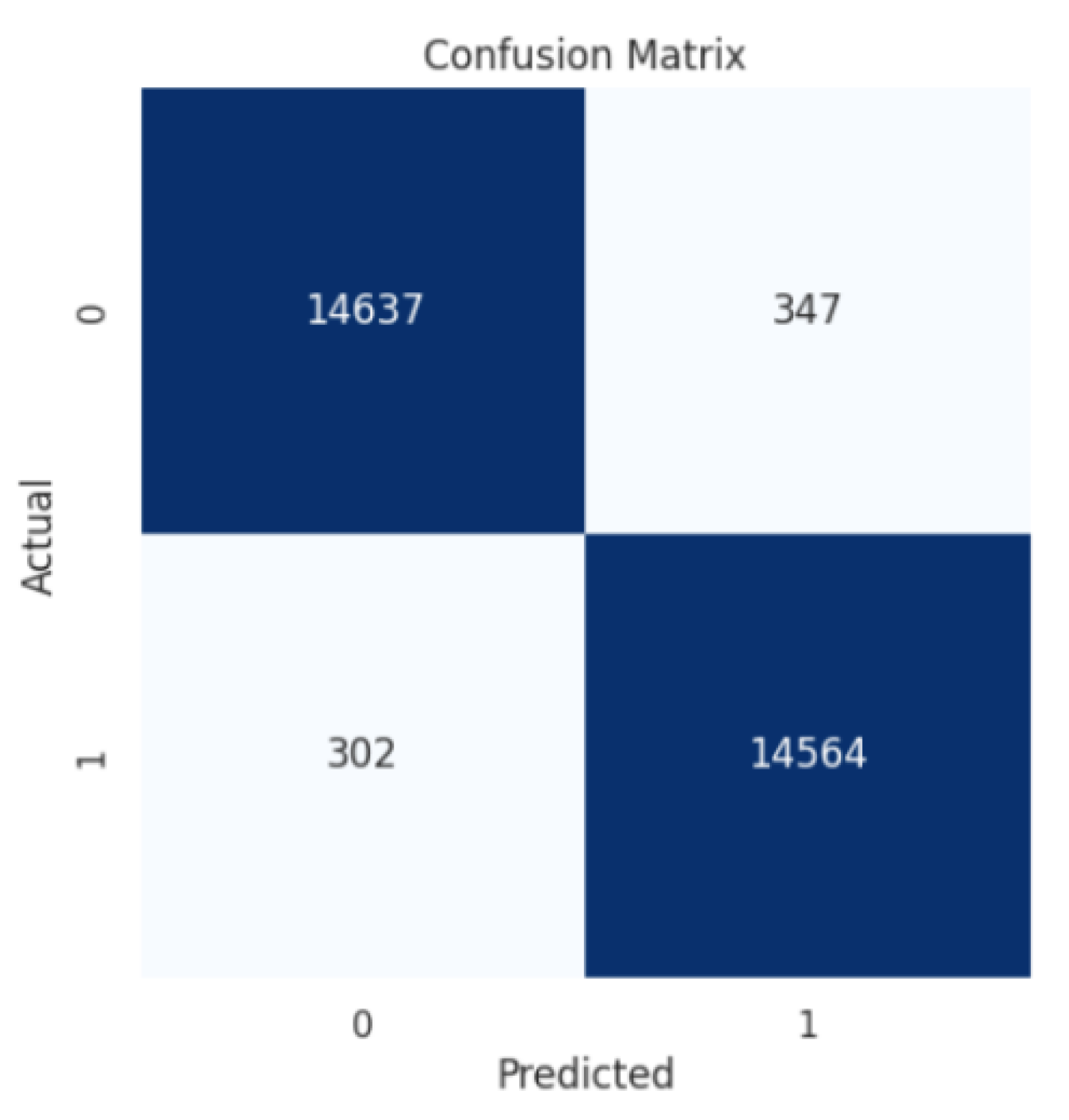
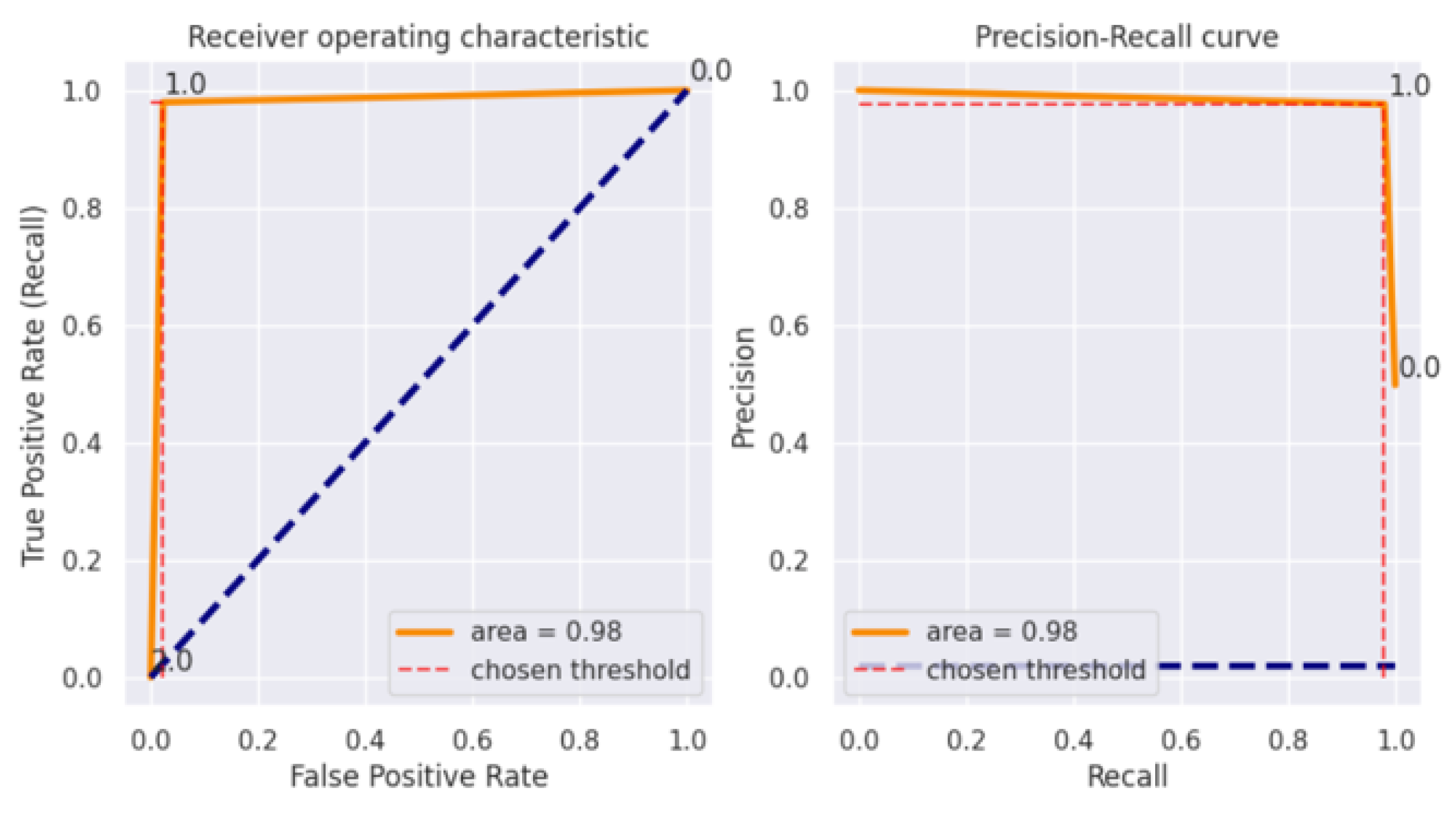
4.4. Naïve Byes
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Vishwakarma, R.; Jain, A.K. ‘A survey of DDoS attacking techniques and defense mechanisms in the IoT network’. Telecommunication systems 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Syed, N.F. IoT-MQTT based denial of service attack modeling and detection. 2020. [Google Scholar]
- Hussain, F.; Abbas, S.G.; Husnain, M.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. ‘IoT dos and DDoS attack detection using resnet’. arXiv 2020, arXiv:2012.01971. [Google Scholar]
- Deng, L.; Li, D.; Yao, X.; Cox, D.; Wang, H. ‘Mobile network intrusion detection for IoT system based on transfer learning algorithm’. Cluster Computing 2019, 22, 9889–9904. [Google Scholar] [CrossRef]
- Iglesias-Urkia, M.; Orive, A.; Urbieta, A.; Casado-Mansilla, D. Analysis of coap implementations for the industrial internet of things: a survey. Journal of Ambient Intelligence and Humanized Computing 2019, 10, 2505–2518. [Google Scholar] [CrossRef]
- Alhaidari, F.A.; Alqahtani, E.J. Securing communication between fog computing and IoT using constrained application protocol (coap): A survey. Journal of Communications 2020, 15, 14–30. [Google Scholar] [CrossRef]
- Bhardwaj, K.; Miranda, J.C.; Gavrilovska, A. Towards IoT-DDoS prevention using edge computing, in ‘{USENIX} Workshop on Hot Topics in Edge Computing (HotEdge 18)’. 2018. [Google Scholar]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and bot-IoT attacks traffic identification for the internet of things in the smart city. Future Generation Computer Systems 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A honeypot with machine learning-based detection framework for defending IoT based botnet DDoS attacks. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI); 2019; pp. 1019–1024. [Google Scholar]
- Rahman, R.A.; Shah, B. Security analysis of IoT protocols: A focus in coap. In Proceedings of the 2016 3rd MEC international conference on big data and smart city (ICBDSC); 2016; pp. 1–7. [Google Scholar]
- Mohamadi, M.; Djamaa, B.; Senouci, M.R. ‘Industrial internet of things over IEEE 802.15. 4 tsch networks: design and challenges’. International Journal of Internet Technology and Secured Transactions 2020, 10, 61–80. [Google Scholar] [CrossRef]
- Musaddiq, A.; Zikria, Y.B.; Kim, S.W.; et al. ‘Routing protocol for low-power and lossy networks for heterogeneous traffic network’. EURASIP Journal on Wireless Communications and Networking 2020, 2020, 1–23. [Google Scholar] [CrossRef]
- Shelby, Z.; Hartke, K.; Bormann, C. ‘The constrained application protocol (coap)’. 2014. [Google Scholar]
- Munshi, A.; Alqarni, N.A.; Almalki, N.A. DDoS attack on IoT devices. In Proceedings of the 2020 3rd International Conference on Computer Applications & Information Security (ICCAIS); 2020; pp. 1–5. [Google Scholar]
- Conti, M.; Kaliyar, P.; Lal, C. ‘Censor: Cloud-enabled secure IoT architecture over SDN paradigm’. Concurrency and Computation: Practice and Experience 2019, 31, e4978. [Google Scholar] [CrossRef]
- Özçelik, M.; Chalabianloo, N.; Gür, G. Software-defined edge defense against IoT-based DDoS. In Proceedings of the 2017 IEEE International Conference on Computer and Information Technology (CIT); 2017; pp. 308–313. [Google Scholar]
- Yin, D.; Zhang, L.; Yang, K. ‘A DDoS attack detection and mitigation with software-defined internet of things framework’. IEEE Access 2018, 6, 24694–24705. [Google Scholar] [CrossRef]
- Galeano-Brajones, J.; Carmona-Murillo, J.; Valenzuela-Valdés, J.F.; Luna-Valero, F. ‘Detection and mitigation of dos and DDoS attacks in IoT-based stateful Sdn: An experimental approach’. Sensors 2020, 20, 816. [Google Scholar] [CrossRef] [PubMed]
- Yang, Y.; Wang, J.; Zhai, B.; Liu, J. IoT-based DDoS attack detection and mitigation using the edge of sdn. In ‘International Symposium on Cyberspace Safety and Security; Springer, 2019; pp. 3–17. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. ‘N-baIoT—network-based detection of IoT botnet attacks using deep autoencoders’. IEEE Pervasive Computing 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Botica, M. ‘Novel approach for detection of IoT generated DDoS traffic’. Wireless Networks 2019, 1–14. [Google Scholar] [CrossRef]
- Soe, Y.N.; Santosa, P.I.; Hartanto, R. DDoS attack detection based on simple ann with smote for IoT environment. In Proceedings of the 2019 Fourth International Conference on Informatics and Computing (ICIC); 2019; pp. 1–5. [Google Scholar]
- Dao, N.-N.; Phan, T.V.; Kim, J.; Bauschert, T.; Cho, S.; et al. ‘Securing heterogeneous IoT with intelligent DDoS attack behavior learning’. arXiv 2017, arXiv:1711.06041. [Google Scholar] [CrossRef]
- Jia, Y.; Zhong, F.; Alrawais, A.; Gong, B.; Cheng, X. ‘Flowguard: an intelligent edge defense mechanism against IoT DDoS attacks’. IEEE Internet of Things Journal 2020, 7, 9552–9562. [Google Scholar] [CrossRef]
- Dai, W.; Wan, P.; Qiang, W.; Yang, L.T.; Zou, D.; Jin, H.; Xu, S.; Huang, Z. ‘Tnguard: Securing IoT oriented tenant networks based on sdn’. IEEE Internet of Things Journal 2018, 5, 1411–1423. [Google Scholar] [CrossRef]
- Djouani, R.; Djouani, K.; Boutekkouk, F.; Sahbi, R. A security proposal for IoT integrated with sdn and cloud. In Proceedings of the 2018 6th International Conference on Wireless Networks and Mobile Communications (WINCOM); 2018; pp. 1–5. [Google Scholar]
- Muthanna, A.; AAteya, A.; Khakimov, A.; Gudkova, I.; Abuarqoub, A.; Samouylov, K.; Koucheryavy, A. ‘Secure and reliable IoT networks using fog computing with software-defined networking and blockchain’. Journal of Sensor and Actuator Networks 2019, 8, 15. [Google Scholar] [CrossRef]
- Maleh, Y.; Ezzati, A.; Belaissaoui, M. An enhanced dtls protocol for internet of things applications. In Proceedings of the 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM); 2016; pp. 168–173. [Google Scholar]
- Haroon, A.; Akram, S.; Shah, M.A.; Wahid, A. E-lithe: A lightweight secure dtls for IoT. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall); 2017; pp. 1–5. [Google Scholar]
- Kajwadkar, S.; Jain, V.K. A novel algorithm for dos and DDoS attack detection in internet of things. In Proceedings of the 2018 Conference on Information and Communication Technology (CICT); 2018; pp. 1–4. [Google Scholar]
- Alzahrani, B.; Fotiou, N. ‘Enhancing internet of things security using software-defined networking’. Journal of Systems Architecture 2020, 110, 101779. [Google Scholar] [CrossRef]
- Granjal, J.; Pedroso, A. ‘An intrusion detection and prevention framework for internet-integrated coap wsn’. Security and Communication Networks 2018. 2018. [CrossRef]
- Granjal, J.; Silva, J.M.; Lourenço, N. ‘Intrusion detection and prevention in coap wireless sensor networks using anomaly detection’. Sensors 2018, 18, 2445. [Google Scholar] [CrossRef]
- Doshi, R.; Apthorpe, N.; Feamster, N. Machine learning ddos detection for consumer internet of things devices. In Proceedings of the 2018 IEEE Security and Privacy Workshops (SPW); 2018; p. 29. [Google Scholar]
- Anirudh, M.; Thileeban, S.A.; Nallathambi, D.J. Use of honeypots for mitigating dos attacks targeted on IoT networks. In Proceedings of the 2017 International conference on computer, communication and signal processing (ICCCSP); 2017; pp. 1–4. [Google Scholar]
- Mergendahl, S.; Sisodia, D.; Li, J.; Cam, H. Fr-ward: Fast retransmit as a wary but ample response to distributed denial-of-service attacks from the internet of things. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN)’; 2018; pp. 1–9. [Google Scholar]
- Arvind, S.; Narayanan, V.A. An overview of security in coap: Attack and analysis. In Proceedings of the 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS); 2019; pp. 655–660. [Google Scholar]
- Vigoya, L.; Fernandez, D.; Carneiro, V.; Cacheda, F. (8135, 01 January). Cidad.pcap Dad-Repository/CIDAD@A109B87. Retrieved 14 April 2023, from https://github.com/dad-repository/cidad/commit/a109b8706174af5d6b1cb06f6afac5fe0ce2b28e.
- Kahng, M.; Thorat, N.; Chau, D.H.; Viégas, F.B.; Wattenberg, M. Gan lab: Understanding complex deep generative models using interactive visual experimentation. IEEE transactions on visualization and computer graphics 2018, 25, 310–320. [Google Scholar] [CrossRef] [PubMed]
- Vigoya, L.; Fernandez, D.; Carneiro, V.; Cacheda, F. Annotated dataset for anomaly detection in a data center with IoT sensors. Sensors 2020, 20, 3745. [Google Scholar] [CrossRef] [PubMed]

| Feature | Description | Type |
| coap.mid | Message ID | Unsigned integer (2 bytes) |
| coap.opt.desc | Opt Desc | Character string |
| coap.opt.location_query | Location-Query | Character string |
| coap.opt.uri_host | Uri-Host | Character string |
| coap.retransmitted | Retransmitted | Label |
| coap.code | Code | Unsigned integer (1 byte) |
| Model | Accuracy | Precision | Recall | F1-Score |
| LinearSVC | 59% | 62% | 48% | 54% |
| Decision Tree | 98% | 98% | 98% | 98% |
| Random Forest | 92% | 90% | 96% | 93% |
| Naïve Byes | 63% | 62% | 69% | 65% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).






