1. Introduction
Digital payments have become an essential aspect of modern society, offering increased convenience, speed, and cost-effectiveness to consumers and businesses alike. These payment systems encompass card payment, e-payment, mobile payment, and cryptocurrencies, with each having their unique characteristics [
1]. Digital payments are increasingly being leveraged to drive financial inclusion, support economic growth, and promote innovation and technological advancement. As digital payment platforms such as WeChat continue to gain popularity, factors such as service quality, perceived security, and ease of use play a significant role in determining global consumer adoption [
2]. Studies have shown that the Technology Acceptance Model (TAM) and the Unified Theory of Acceptance and Use of Technology (UTAUT) model, which consider people’s attitudes and perceived risks, are often used to understand consumer adoption of digital payment solutions [
3]. Stakeholders should be mindful of these factors and develop policies and regulations to facilitate effective use of digital payment technologies in various sectors [
1,
4].
One such innovative digital payment solution is the Lightning Network (LN), a second-layer protocol built on top of the Bitcoin blockchain. The LN offers unique features such as instant settlement finality, extremely low transaction fees, practically infinite throughput, and lightning-fast transaction speeds [
5,
6]. These features make the LN an ideal solution for various applications, including micropayments and low-value transactions that may not be feasible on the Bitcoin blockchain. The network also serves as an interoperability bridge among different financial networks, offering the potential for real-time, low-cost cross-network transactions [
6]. In addressing the "Blockchain Trilemma," the LN successfully balances security, scalability, and decentralization, thus maintaining the network’s integrity and security [
7]. By enabling off-chain transactions and reducing the load on the main blockchain, the LN has made significant progress in development, liquidity, and user adoption [
8]. This approach ensures that the base layer remains immutable and decentralized while accommodating innovation at higher levels [
8,
9].
Technically speaking, the LN functions as a decentralized layer 2 solution intended to address the scalability challenge faced by the Bitcoin network. Its primary goal is to significantly enhance the speed of transactions. The LN, proposed by [
10] in 2016 and implemented as open-source software in 2018, employs user-generated micropayment channels to enable real-time transactions. The LN uses "channels" to transfer Bitcoins between two parties, with each transaction requiring both signatures. The Bitcoin public ledger records this connection, and both parties must agree on the new balance for further transactions. The most recent transaction with both signatures determines the current balance. When making a payment, both parties sign a new exit transaction, invalidating previous ones. Exiting a channel doesn’t require counterparty involvement, and with access to multiple multisignature channels, funds can be transferred across the network. The LN has two types of channel closures: cooperative and non-cooperative. In a cooperative closure, one side initiates and both parties work together to close the channel, which is done immediately with one or more confirmations. In a non-cooperative closure, if one party disappears, a force closure may be necessary, which takes longer, usually around one to three days.
The LN offers a solution that enables fast and high-volume Bitcoin transactions between users without waiting for network confirmations. By opening Lightning channels off-chain, users can transact with each other indefinitely and only settle the final amount. Payments are made using Hashed Timelock Contracts (HTLCs). HTLCs are contractual arrangements employed in the cryptocurrency realm for facilitating conditional payments. Essentially, HTLCs enable payments in which the recipient must confirm receipt before a specified time or predetermined deadline, eliminating the need for custodial trust and enabling dynamic, open participation [
10]. Payment routing in the LN is based on the balance of an edge between two nodes, and the distribution of the balance is unknown, so payments are sent through a trial and error process that is probabilistic in nature [
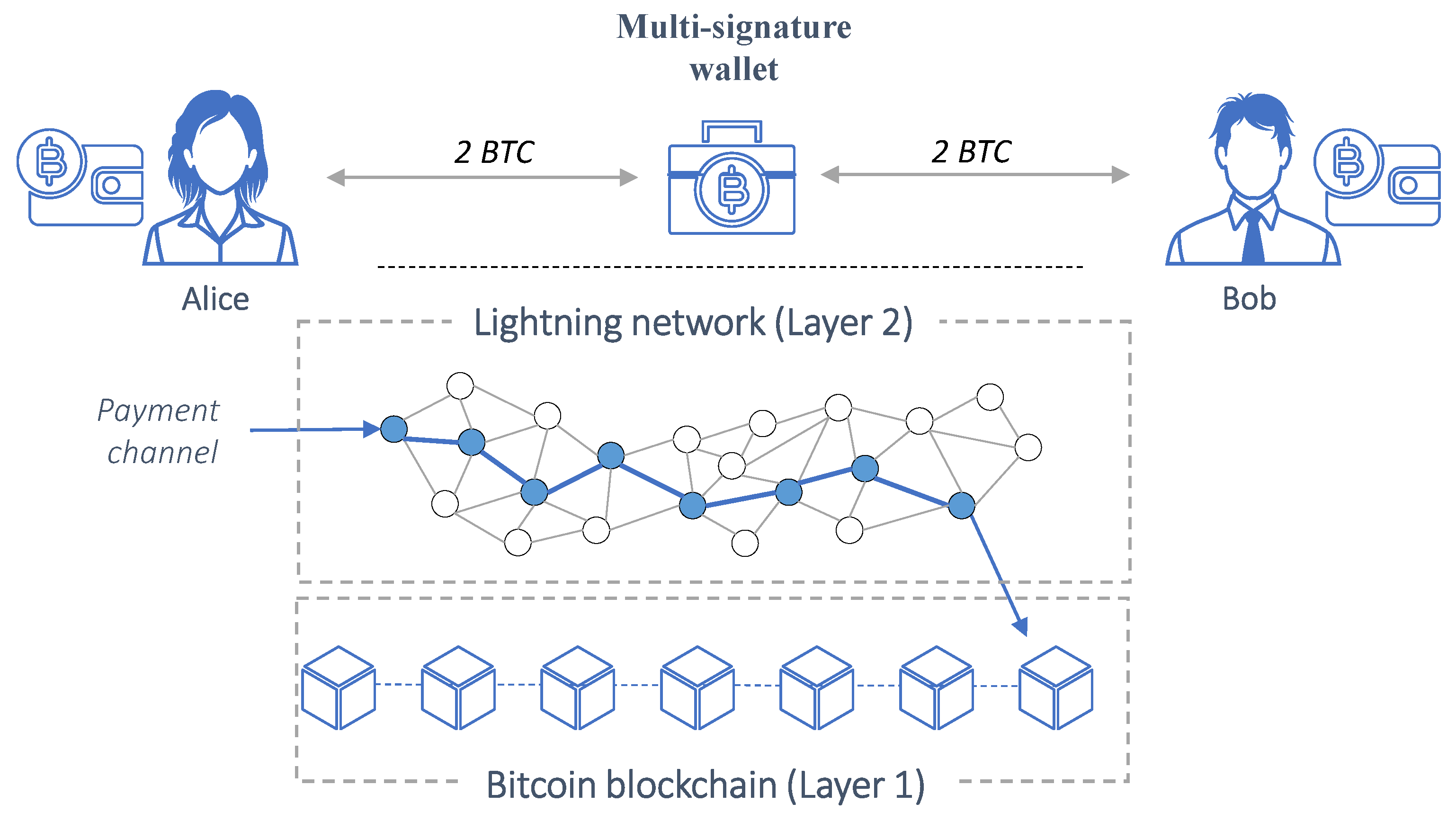
11]. The LN enables users to transact without directly moving Bitcoins. Users lock up Bitcoin in a multi-signature address, maintaining a record of each party’s share of the funds. To settle, they submit the most recent address statement to the Bitcoin blockchain, allowing for fair distribution of the unlocked Bitcoin. Alice and Bob can use the LN to handle their transactions, generating invoices and making payments without actually transferring Bitcoin. Although closing the channel involves the usual Bitcoin fees, using the LN only requires fees for opening and closing the channel, providing instant and cost-free money transfers. In particular, as depicted in
Figure 1, a LN transaction involves the following steps:
Alice and Bob, both with bitcoin wallets, agree to create a channel between them. Alice funds the channel with a specific amount (e.g., 2 BTC). Currently, only one user can fund a channel, but developers aim to enable both parties to contribute.
Both participants exchange public keys, which are required for BTC blockchain transactions.
A new BTC address, a "2-of-2 multisig address," is created using their public keys. This special address type requires signatures from both participants to validate a transaction.
Before the channel is built, a refund transaction is created to ensure Alice can retrieve her funds without trusting Bob. This transaction, signed by both parties, becomes valid once the Lightning channel is funded. It remains off-chain, shared only between Alice and Bob.
After validating the refund transaction, the funding transaction takes place, with Alice depositing 2 BTC into the multisig address. The Lightning Channel is now open for further transactions, and Alice can reclaim her Bitcoins through the refund transaction, which can be executed by publishing it on the bitcoin blockchain.
The LN could transform the digital payment landscape with its remarkably low fees, providing significant advantages to merchants burdened by high payment expenses. Credit card processing fees are a major issue for merchants since they frequently need to accept credit card payments. Unfortunately, these fees can erode profits, particularly for businesses operating on slim margins. Commonly, credit card companies like Visa
1 , Mastercard
2 , and American Express
3 charge fees ranging from 1.5% to 3.5%. The same holds for remittance payments. According to a recent report from the World Bank, the average cost of sending remittances on a global scale is 6.3% of the transferred amount
4. In the LN, routing nodes charge fees for forwarding payments via HTLCs, promoting efficient capital allocation. Channel fees are the difference between incoming and outgoing HTLCs for a routing node. Fees apply only to successful payments and are charged once per peer and per channel. Peers can set their own fee policies for their channels, allowing them to charge fees when pushing payments to neighbors. There are two types of fees: base fees, which are fixed amounts per forwarded HTLC, and fee rates, which are proportional fees based on the value of each forwarded HTLC
5. At present, the median fee rate on the Lightning Network consists of a base fee of 1 satoshi (or 0,02€) and a fee rate of 0.00022 per satoshi [
8].
The LN provides numerous benefits for businesses, such as enabling instant, low-cost remittance payments through companies like Strike [
6]. In addition, the network’s integration with platforms like Shopify and payment provider Clover allows merchants to accept Bitcoin payments with ease and at lower costs than traditional card networks. As a result, the LN has the potential to be considered the standard monetary network for payments, providing nearly instant transactions, extremely low transaction fees, and increased capacity [
5,
12]. The LN can also facilitate financial inclusion for over 2 billion unbanked individuals worldwide, who are mainly concentrated in poorer parts of Africa, Latin America, and Asia [
8]. This technology has the potential to provide greater access to financial services for these populations, improving their economic prospects.
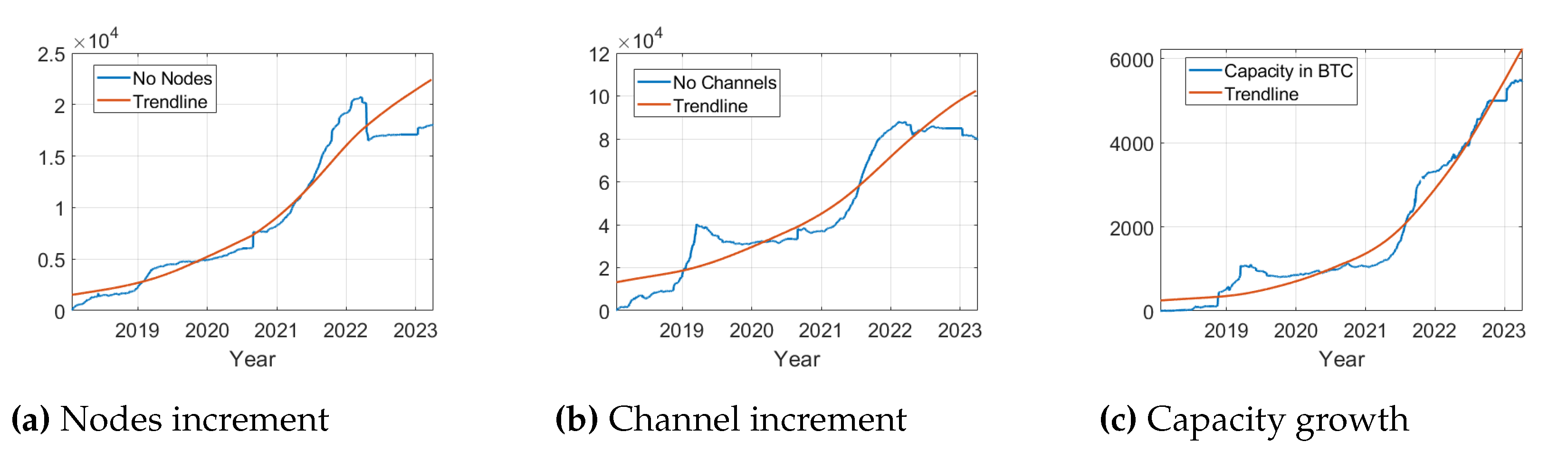
The LN has experienced tremendous growth since its launch in 2018. The widespread adoption of both custodial and noncustodial LN wallets, its official integration in regions like El Salvador and Lugano and its integration with platforms like Shopify and payment provider Clover have proved to be advantageous for the LN. In particular, the number of LN nodes, which are computers running the LN software, has been steadily increasing. Additionally, the total capacity of the LN, which is the amount of Bitcoin that can be transacted through the network, has also been increasing. A crucial factor for the extensive adoption of the LN lies in the augmentation of nodes underpinning the network and the enhancement of channel capacity. These attributes hold considerable implications for the system’s security and functionality. As depicted in
Figure 2, there is a linear progression in the growth of these components over time, which is also observed in the number of channels established. As of April 2023, the LN holds a bitcoin capacity of almost 5,600 bitcoins, with about 18,000 nodes operating on the network and nearly 80,000 unique channels connecting nodes from across the globe.
1.1. Motivation and contribution
Despite the growing importance of digital payments and the increasing interest in the LN as a solution for various transaction-related use cases, there is limited literature available on the characteristics of this nascent technology, the depth and breadth of the various LN-related applications as well as relevant adoption/implementation challenges. For example, some authors have focused on the LN’s development, potential non-monetary uses, along with legal challenges that may impact LN adoption [
13]. Other authors discuss recent advancements and applications of the LN in various domains such as international remittances, energy trading, decentralized trade finance, micropayments, consumer IoT devices, food safety management and securities settlement [
14,
15,
16,
17,
18,
19,
20,
21]. However, it is not clear from the available literature the added value brought forward by the LN as well as the various challenges underpinning the adoption of the LN by merchants and the business sector. Therefore, the motivation behind this study is to contribute to the understanding of the LN’s potential in enhancing business operations and its applicability across different sectors, while taking into account adoption/implementation challenges.
This gap in research represents a significant opportunity for further exploration and analysis, particularly as businesses across various industries continue to seek innovative, cost-effective, and secure payment solutions. By addressing the current gap in the literature relevant to the particularities of the LN, this research will contribute to the broader understanding of digital payment technologies and their impact on various industries. Besides, by providing a comprehensive analysis of the business applications of the LN, this research aims to expand the knowledge base and offer valuable insights for businesses, policymakers, and researchers. Ultimately, the findings of this study will help businesses make more informed decisions about adopting and leveraging the LN to improve their operations and enhance customer experiences, while considering adoption/implementation challenges. Therefore, the primary contributions of this research include:
An exploration of the various technical characteristics of the LN as well as its main attributes with respect to network’s topology, performance, privacy and security, among others. By examining these aspects, businesses and the research community can gain insights into how the technical characteristics of the LN can give rise to a new global, monetary network.
An exploration of applications and use cases of the LN across different industries, including retail, e-commerce, and remittance services, particularly emphasizing its low transaction costs, near-instant transaction speeds, and scalability. By examining these practical applications, businesses can gain insights into how the LN can be effectively utilized to address specific transaction-related challenges.
Identification of potential challenges and limitations associated with the LN, such as liquidity constraints, privacy concerns, and technical complexities. This information will provide businesses and policymakers/researchers with a more comprehensive understanding of the LN and inform future research and development efforts.
The rest of the paper is organised as follows. In
Section 2 we present the methodology adopted for conducting our review. The classification of the available LN-derived literature is presented in
Section 3. In
Section 4 we classify the prevalent LN-related business models. In
Section 5 we discuss various challenges and open issues prevalent to the LN. The paper ends with some concluding remarks.
2. Methodology
We have chosen a narrative review methodological approach for conducting our research. In this section we provide background information with respect to the methodological underpinnings of narrative reviews, proper justification for choosing such a methodological approach as well as the relevant steps for practically conducting our research.
A narrative review is a form of literature review that focuses on interpretation and critique of a body of literature to provide a compelling argument based on primary evidence [
22]. It summarizes and combines evidence from various sources, such as primary studies, theoretical papers, and other relevant literature, without strict methodology or inclusion and exclusion criteria [
23]. The authors’ expertise and interpretation play a crucial role in narrative reviews, but they should strive for objective conclusions based on the reviewed literature [
24].
Narrative reviews have various benefits. In particular, narrative reviews provide a comprehensive summary of a topic, considering various types of evidence sources, historical and theoretical perspectives, and identifying gaps in the literature [
22]. They offer a broader and more flexible perspective on a subject, allowing for greater interpretation and critique, which can help pinpoint areas requiring further research [
23]. Narrative reviews are accessible and easier to read, making them valuable for researchers, clinicians, and policymakers seeking a quick understanding of the current state of knowledge on a particular subject [
24]. They can also be particularly useful when limited empirical evidence is available or when the research question is intricate or multi-dimensional [
24].
Compared to systematic literature reviews, narrative reviews have attracted significant criticism. However, different approaches to literature reviews, such as narrative and systematic reviews, should be considered complementary rather than hierarchical, as each type of review serves distinct purposes and offers unique insights [
22,
23]. Policymakers, stakeholders, and research commissioners should reassess the lower status assigned to narrative reviews and recognize their potential to enhance knowledge within a field [
23]. It is crucial to avoid being misled by a false hierarchy of secondary evidence and acknowledge the limitations of systematic reviews [
23]. Meta-narrative reviews, which aim to provide a comprehensive overview of the research landscape on a particular topic across multiple traditions or disciplines, can follow the RAMESES publication standards for transparent and comprehensive reporting, emphasizing the importance of being open to different perspectives, critical debate, and reflection on biases [
25].
This study will employ a narrative review methodology using a semi-systematic approach to examine new and emerging business models empowered by the LN as well as characteristics of the LN and relevant adoption/implementation challenges. The choice of a narrative review over a systematic review is driven by three primary arguments. First, the nascent nature of the LN and its applications in business models requires a more exploratory and flexible approach to account for the limited and diverse research available. In particular, a narrative review can provide a deeper exploration of underlying concepts and relationships between them. In a systematic literature review, the focus is on quantitatively synthesizing the data, which may not be appropriate for a topic with limited literature. A narrative review, on the other hand, allows for a more qualitative exploration of the underlying concepts and relationships, which can be valuable for developing a deeper understanding of the topic. Second, narrative reviews can incorporate a wider range of sources, such as grey literature, which may be particularly valuable when studying emerging technologies. Finally, narrative reviews are better equipped to address the evolving nature of the LN, as they can capture the rapid advancements and shifting perspectives in this dynamic field.
We opted for a semi-systematic approach rather than a mere narrative review approach for various reasons. A semi-systematic approach to literature reviews combines elements of both systematic and narrative reviews, offering a balance between rigor and flexibility. This approach involves a systematic search for literature with predefined search terms and inclusion criteria, while allowing for additional sources, such as grey literature or expert opinions, to provide a more comprehensive view of the topic. The researcher then employs narrative synthesis to analyze and present the findings, organizing sources thematically or chronologically and providing a narrative description of key findings and implications. A semi-systematic narrative review can be particularly useful for topics with limited literature or when a fully systematic review is not feasible due to time or resource constraints, maintaining a structured and transparent approach to the review process. To this end, we have utilized various aspects of the approach outlined in [
26] to conduct our review. In particular, our review protocol comprises five steps: 1) Defining the scope of the review, 2) Search strategy, 3) Assessing the eligibility of the retrieved literature, 4) Content Analysis and 5) Synthesis and Reporting.
2.1. Defining the scope of the review
The first step in conducting a narrative review is to define the scope of the review by setting relevant research questions and objectives (as seen in
Table 1. The research questions should be broad enough to capture the key themes and trends in the literature, but focused enough to provide a clear direction for the review.
2.2. Search strategy
The search strategy for this narrative review involved a systematic search for literature using predefined search terms and inclusion criteria. Our primary source of locating LN-related papers was the Scopus electronic database. We conducted a systematic search in February 2023 (which was updated in mid-April 2023) without any time-frame limitations. We used the term "Lightning Network" to search in the titles of all available literature in Scopus. For streamlining our assessment, we also used Google to locate grey literature sources, especially reports covering the current status of the LN.
2.3. Assessing the eligibility of the retrieved literature
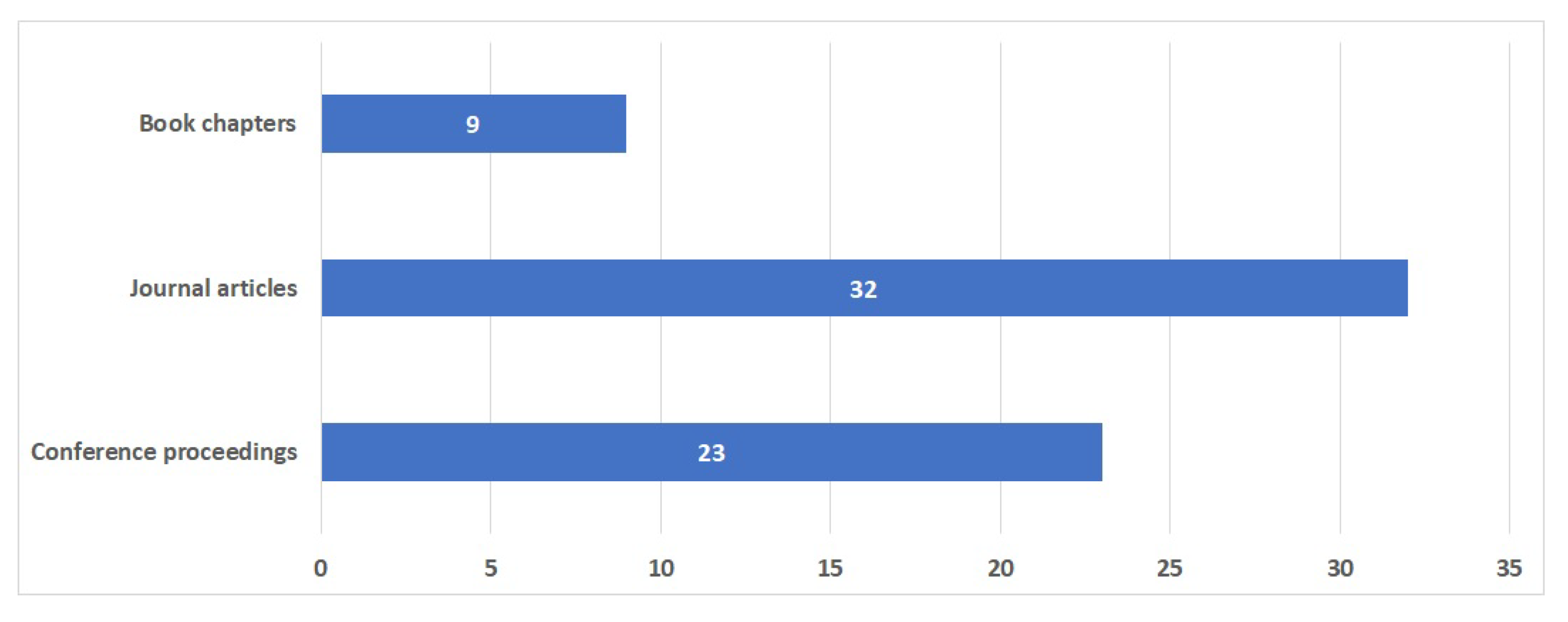
Given the relatively limited literature relevant to LN, we incorporated all English papers found in Scopus into our analysis. It is worth noting that some papers were excluded due to their focus on meteorology (as the term "lightning" generates a conflict). As a result, our analysis encompassed all pertinent papers published in journals, conference proceedings, and book chapters, without considering quality assessment approaches.
2.4. Content Analysis
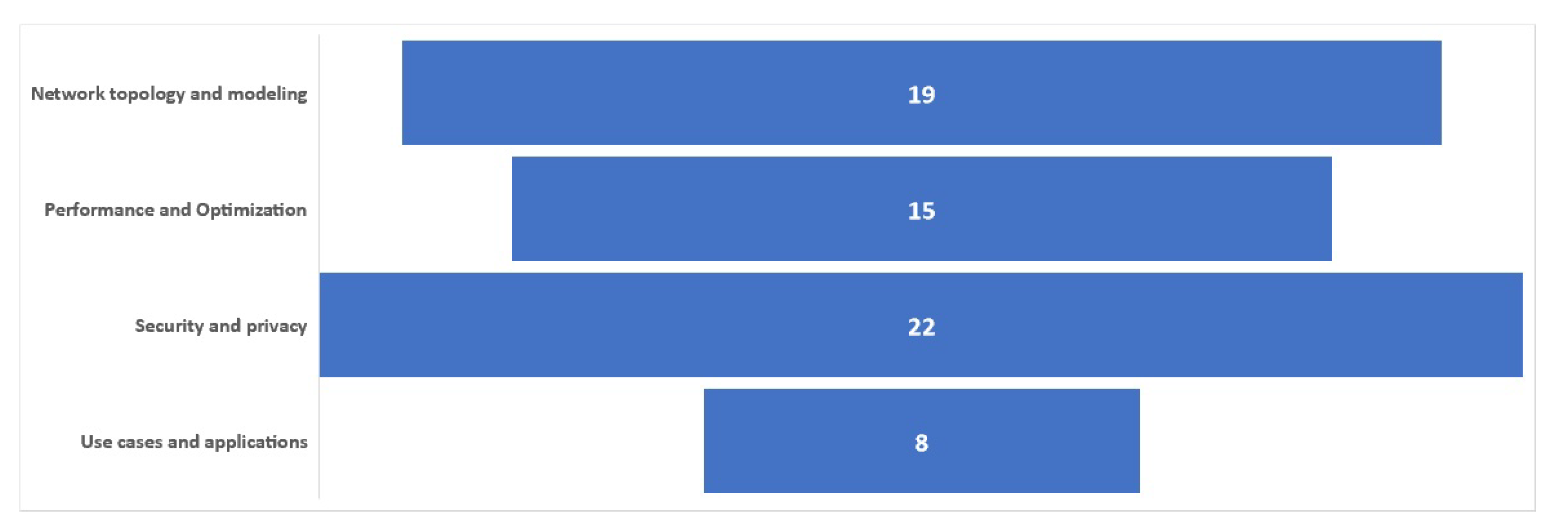
Once the relevant articles have been selected, we extracted the data from each study. In particular, we employed a thematic content analysis approach to extract research areas and common themes from the relevant literature. For the thematic content analysis of the chosen literature, we utilized qualitative analysis software (MAXQDA2020).
Figure 3.
Distribution of the publication types
Figure 3.
Distribution of the publication types
2.5. Synthesis and Reporting
In the last step of our methodological approach we provide a synthesis of the available literature and we report the main research findings. The synthesis process entails organizing sources thematically, based on research questions, and delivering a narrative description of the findings and their implications. We have tried to synthesize the data to identify key themes and trends in the literature, offering a critical analysis of the strengths and weaknesses of existing research. Additionally, we provide recommendations for future research in the field.
4. Business models empowered by the Lightning Network
The Bitcoin community takes a cautious approach to modifying its base layer to ensure the preservation of decentralization, stability, and security. Layer 2 solutions, such as the LN, tackle the scalability trilemma by offering near-instant and affordable transactions without compromising security or decentralization. Since Bitcoin’s base layer isn’t well-suited for small transactions, the implementation of additional layers becomes crucial. Layer 2 solutions, in conjunction with Layer 3 applications like SPHINX and ZEBEDEE, deliver decentralized and censorship-resistant experiences in areas like social networking and gaming. These advancements uphold Bitcoin’s core principles while expanding its capabilities and practical applications.
The LN has the potential to increase the adoption of Bitcoin and other cryptocurrencies by making them more usable and accessible for everyday transactions. This could lead to increased business opportunities and new use cases that were previously not possible on the Bitcoin blockchain and the cyberspace in general. In the original paper describing the LN published by [
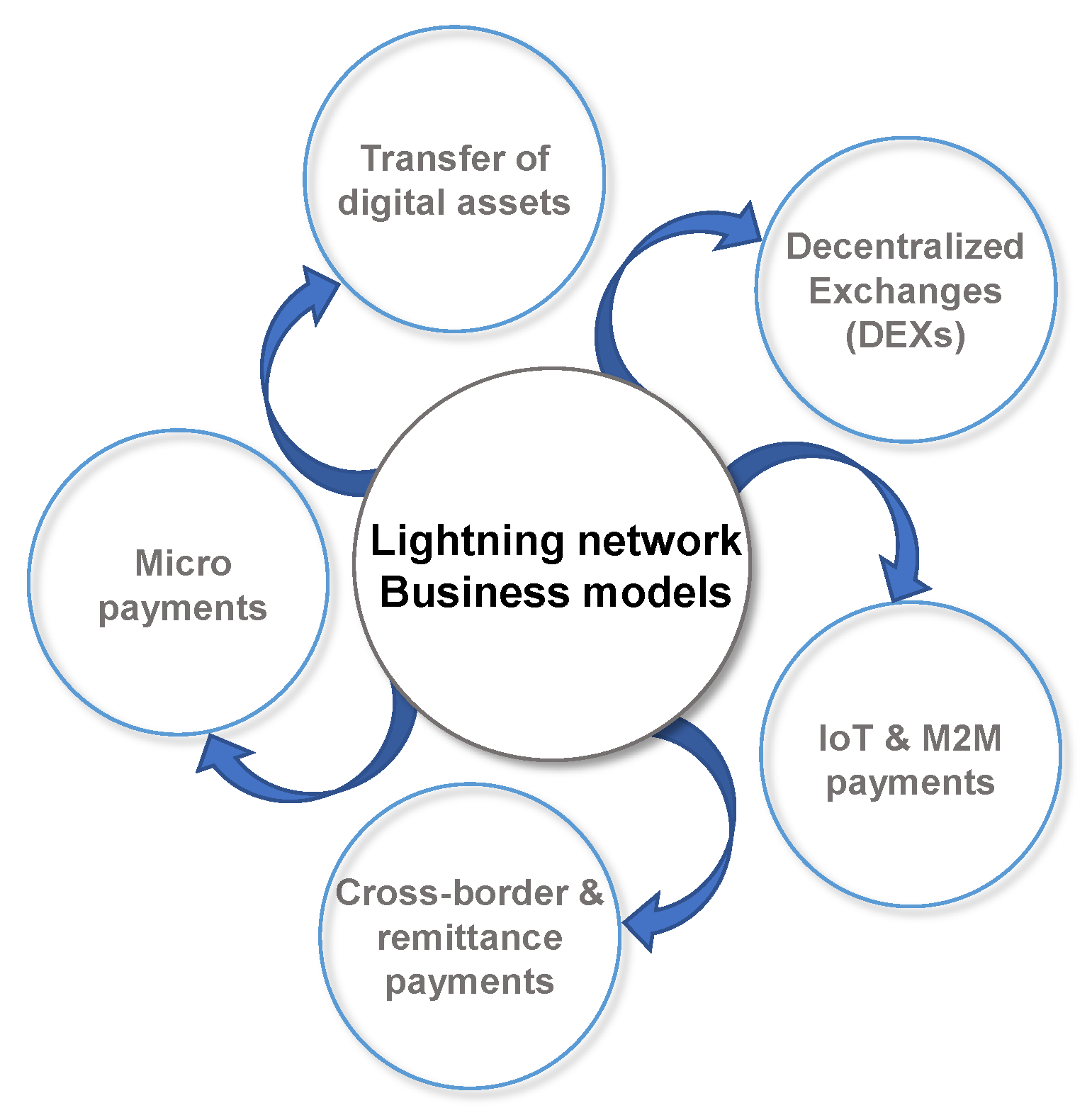
10], the authors portray four (4) possible use case scenarios for the LN, namely instant transactions, micropayments, financial Smart Contracts and escrow and cross-chain Payments. In the sequence, we provide a classification of the various business models (
Figure 6) empowered by the LN as derived by the relevant literature (both grey and scientific).
4.1. Micropayments
The LN enables micropayments on the Bitcoin blockchain, creating opportunities for new business models that rely on microtransactions, such as pay-per-use services, in-game purchases, and online content tipping [
10]. In particular, the LN holds significant promise in transforming micropayments, providing businesses and individuals with avenues to enhance productivity and monetize their offerings. Micropayments have existed since the mid-1990s but were limited by high transaction fees. LN’s low fees make it an essential component of micropayment channels, supporting use cases like value-for-value models, where content creators trust users to evaluate the worth of the content and compensate accordingly [
8]. The LN also facilitates nanopayments, reducing financial inefficiencies and optimizing business models by minimizing costs from payment processing and intermediaries.
Blockchain micropayments can impact crowdsourcing by enabling direct donations to recipients, eliminating intermediaries, and reducing overhead costs. However, this may require a rating and auditing system to prevent fraud [
17]. Pay-per-use models can leverage micropayments to provide shorter subscription durations, improving consumer choice and access to content. Digital property rights, royalties, and referrals can also benefit from the simplicity and low minimum limits of micropayments. The LN can be used for purposes beyond payments, as demonstrated by the Zion app, which allows users to share content in an encrypted message through minuscule Lightning payments, maintaining privacy and avoiding central intermediaries [
13].
The LN is an ideal solution for high-frequency payments across various sectors due to its instant, affordable, and relatively secure transactions. In stock trading, it can streamline high-frequency trading by minimizing latency and speeding up trade execution, optimizing profits for trading firms. In retail, it can improve customer experience through fast and secure payments at various outlets, complementing contactless and mobile payment methods. Additionally, online advertising platforms can benefit from the LN’s capacity to manage real-time bidding systems effortlessly, ensuring smooth auctions. In gaming, incorporating the LN results in seamless in-game purchases and microtransactions, enhancing user experience. Finally, freelance marketplaces can utilize the LN’s quick and dependable payment processing to ensure timely payments, fostering trust and satisfaction among users.
Another interesting micropayment use case scenario refers to employee and customer rewards. For example, MicroStrategy has developed the MicroStrategy Lightning Rewards platform
6. The platform provides enterprises with a tool to incentivize any behavior and maximize engagement with instant Satoshi redemption. The Lightning Rewards platform is designed for unlimited scalability and the highest security with an open, extensible microservices architecture. Companies can create and configure reward rules via the administrative portal, and build rules that combine events, users, dates, and reward amounts. The platform allows any enterprise to reward their employees, customers, partners, and prospects for their engagement, and is expected to integrate directly into MicroStrategy Lightning as an out-of-the-box application or payment partner.
4.2. Cross-border and remittance payments
The LN’s efficiency makes it suitable for cross-border payments, reducing transaction friction for businesses and financial institutions. LN’s low fees and instant transactions can reduce the
$40 billion lost annually in remittance payments, benefiting both the sender and the recipient regardless of their currency preference [
8]. The LN allows for quick and inexpensive transfer of funds in various currencies, which are automatically converted into bitcoins and then into the local currency of the receiver. This helps to reduce processing times and costs associated with traditional remittance services. The LN can also assist the unbanked population, which comprises over two billion people worldwide, by providing easy access to financial services.
Companies like Strike and Bottlepay use it for global payments due to its speed, low cost, and convenience. In particular, Strike
7 is a payment application that uses the LN layer to provide fast and cost-effective transactions. It allows individuals and businesses to send and receive money instantly and without fees, using only a smartphone and an Internet connection. Strike’s new feature enables companies to send US dollars through the LN, without having to deal with the volatility of bitcoin. Payments can be completed in seconds, and currently there are no fees involved to send or receive payments or to withdraw funds from your account. The app also makes it easy to invoice and track payments, and it integrates with popular accounting software. Galoy
8, a Lightning enterprise software provider, offers cost-effective risk hedging solutions for exchange rate fluctuations (stablesats.com). Bitcoin’s high liquidity, combined with the LN’s capabilities, allows users to quickly convert and transfer funds across borders.
It is clear form the above-mentioned business solutions that the LN enables businesses to expand their customer base globally, without the need for middlemen or high fees. We should also note that the LN has the potential to benefit the banking industry by reducing transaction costs, increasing transaction speed, and enabling micropayments. The LN can be used to facilitate faster and cheaper payments between suppliers and buyers in supply chain finance. By opening a payment channel, immediate payment for goods or services delivered can be received and subsequent transactions can be settled instantly and at a lower cost. This reduces payment delays, increases speed and efficiency, and lowers costs for both suppliers and buyers.
4.3. IoT and Machine-to-Machine payments
The Internet of Things (IoT) has vast potential, but one obstacle to its full realization is the lack of a straightforward monetization model. Micropayments on the blockchain could be the solution, enabling data collection and sharing for various applications, such as traffic planning and road maintenance, while compensating users and protecting their privacy [
19]. Machine-to-machine (M2M) payments through the LN can facilitate direct, automated, and anonymous payments for services like electric car charging or autonomous taxis. Such payments can be split and forwarded to different parties, streamlining transactions and reducing administrative costs [
19]. In the energy market, financial inefficiencies hinder progress, with payments for electricity taking longer to process than the electricity flow itself. The LN and smart contracts could significantly reduce these inefficiencies by allowing for instant payment routing and M2M payments for electricity consumption [
15]. A mobile energy trading scheme utilizing the LN and smart contracts has been proposed, featuring an off-blockchain exchange of value to eliminate transaction lag [
15]. Additionally, a study examined the requirements of various blockchain technologies for IoT micro-payments, benchmarking the LN’s performance against similar solutions, integrating it into an existing IoT ecosystem, and designing a novel algorithm for payment channel fee reduction [
20].
4.4. Decentralized Exchanges
Centralized exchanges (CEXs) serve as the primary venue for trading digital assets, providing infrastructure similar to that of traditional equities markets. CEXs facilitate the exchange of tokens and currencies, offering liquidity and enabling price discovery. However, due to the unregulated nature of the cryptocurrency market and the significant exchange counterparty risk exposure, investors are subject to significant risk of loss. Public records indicate that billions of dollars have been stolen from prominent CEXs by hackers over the last few years, highlighting the vulnerabilities of these centralized platforms [
78].
On the other hand, a decentralized exchange (DEX) is a type of cryptocurrency exchange that operates on a decentralized, peer-to-peer (P2P) network, rather than a centralized platform. Unlike centralized exchanges, which are owned and operated by a single entity and require users to deposit their funds onto the exchange’s platform, a decentralized exchange enables direct, P2P trading between users without the need for a central authority [
78,
79]. DEXs can be implemented using an on-chain order book, which records every order on the blockchain, or an off-chain order book, which records orders elsewhere and only uses the blockchain for settlement [
80]. Decentralized exchanges (DEXs) can use automated market makers (AMMs) instead of an order book system. AMMs allow traders to place orders with the market maker, which algorithmically provides a price, rather than relying on matches between price and volume orders provided by buyers and sellers. Liquidity for an AMM to act as a DEX is provided by owners of various tokens placing their tokens within a liquidity pool. AMM prices are determined algorithmically, but can be aligned with external reference markets through arbitrage or allowing the reference market to act as an oracle [
78,
80]. The LN and it’s characteristics provide an interesting fit in this use case scenario. In [
16], the authors propose a decentralized trade finance system that leverages smart contracts and blockchain technology to improve efficiency, security, and accessibility. This system increases trust and transparency, enabling smaller businesses to participate in the global economy and contribute to economic growth. The model involves a community-owned liquidity pool that facilitates trade finance for importers and exporters using the LN. The platform validates invoices and provides funds from the liquidity pool, with the platform being compensated after trade completion. Participants receive trade tokens as incentives for successful transactions, promoting good behavior within the network.
4.5. Transfers of digital assets
The LN offers an innovative solution for transferring digital tokens, including stablecoins, using the RGB protocol
9. This protocol, a set of open-source smart contracts, provides a scalable and confidential way to execute complex transactions. RGB leverages the Bitcoin blockchain for state commitment while keeping smart contract code and data off-chain. This approach mitigates saturation and excessive resource usage, common issues in other blockchain-based smart contract systems. By employing Bitcoin transactions and Script as an ownership control system, smart contract evolution is defined through an off-chain scheme, with all validations occurring on the client side. RGB smart contracts are directed acyclic graphs (DAGs) of state changes, following specific rules dictating their evolution. Fungible assets in RGB follow the LNP/BP RGB-20 specification, while non-fungible tokens (NFTs) adhere to the LNP/BP RGB-21 specification. RGB-20 allows for the creation, management, and transfer of fungible tokens, while RGB-21 enables NFT creation and management, including custom data attachment via an engraving procedure.
The RGB protocol offers several advantages over other NFT platforms, such as reduced dependence on expensive blockchain storage and the elimination of the need for specialized data management solutions or the InterPlanetary File System (IPFS). Instead, Bifrost, a LN extension, is utilized, providing end-to-end encryption, built-in DRM encryption, and ownership management. Furthermore, RGB supports multiple monetization methods beyond just selling the NFT. The LM’s integration of stablecoins and other digital assets paves the way for decentralized exchange (DEX) functionalities directly on LN. This enables users to atomically swap Bitcoin against other assets with the same speed and cost of a Lightning payment, eliminating counterparty risks. Consequently, more users may transition away from centralized exchanges, removing the need to trust third parties with their collateral.
4.6. Lightning Network-related services
The LN ecosystem consists of a diverse array of companies and participants, each contributing to the network’s maintenance and growth in their unique way. Key LN-related services and participants include LN nodes, Lightning wallet providers, LN service providers, and LN developers. These participants work together to create a more decentralized, democratic, and efficient payment system for Bitcoin blockchain users. Some popular players in this ecosystem include Zap, BlueWallet, Wallet of Satoshi, Bitrefill, Lightning Labs, and ACINQ.
The main players within the LN ecosystem are merchants accepting payments, developers building LN native projects, existing crypto companies adopting LN technology, wallet and gaming app developers focusing on consumer use cases, and users engaging in earning, stacking, tipping, and other micropayment activities. The growth of the ecosystem is driven primarily by LN native projects, focusing on building the infrastructure layer. Financial infrastructure and LiFi solutions are also significant segments. Gaming is the largest category within the ecosystem, followed by wallets and payments, and merchant services.
5. Discussion
Arguably, the Bitcoin network exhibits a layered scaling structure. At its foundation lies the primary Bitcoin blockchain, which serves as a platform for recording and settling transactions. However, due to constraints in transaction throughput and escalating fees, supplementary layers have emerged to tackle these scalability challenges. The most notable example of a second-layer solution within the Bitcoin network ecosystem is the LN, which facilitates swift, cost-effective transactions via off-chain payment channels. Consequently, the Bitcoin blockchain could operate as a global, distributed financial infrastructure and monetary value settlement protocol, while the LN could act as a worldwide decentralized payment system. These stratified scaling solutions pave the way for a plethora of payment options and innovative business models within cyberspace, as described earlier in our analysis.
The LN brings forward significant added value for both the economy and society. The conventional banking system is often complicated, resulting in higher costs and wasted time for merchants and customers. Remittance payments, which are essential for many developing countries, have high fees averaging 6.4% in 2021. The LN can help reduce these fees and positively impact millions of people who rely on remittances for their livelihood [
8]. The LN offers instant, borderless, and intermediary-free payments with instant settlement and lower fees, leading to potential discounts for customers and reduced chargeback risks for businesses. Besides, the LN has the potential to revolutionize how businesses perform their financial transactions and improve customer experience. Although it might sound as an overstatement, but we believe that businesses may face several risks by not paying attention to disruptive technologies like the LN. Failure to adopt this technology can result in missed opportunities, lack of competitive disadvantage, vulnerability to disruption, and negative impact on reputation and customer trust. Early adoption of disruptive technologies can give businesses a competitive advantage over those who are slower to adopt. It is important for businesses to stay up-to-date with emerging technologies, understand their potential benefits and risks, and develop strategies to adapt to these changes to remain competitive in the market.
Predicting the scale of the LN adoption is a challenging task, especially considering that we are still in the early stages of this emerging technology. With limited knowledge of how various players will respond to the technology, it becomes challenging to anticipate the extent of its adoption. In this context, we have identified a set of catalysts that could drive the adoption of the LN. In particular, we try to understand the strategic decision-making of various players and anticipate the potential outcomes of their interactions in view of certain catalysts that could accelerate the adoption of the LN. Such an approach provides insights into the complex dynamics involved in the adoption of LN, which can inform the development of strategies and policies to support its growth and adoption. To this end, we have identified the following catalysts that we expect will drive the LN’s adoption in the long run:
Sustainability of the Bitcoin network: The LN relies upon the Bitcoin blockchain network and, therefore, the sustainability of the underlying Bitcoin network becomes crucial for almost all aspects and functionalities of the LN. Although the sustainability of the Bitcoin network depends on a multitude of factors, we strongly believe that energy consumption is found at the centre of the current debate with respect to the environmental costs associated with Bitcoin mining and the maintenance of the Bitcoin network (namely through the Proof of Work consensus mechanism).
The energy consumption of the Bitcoin network is significant, and although direct comparisons with the financial sector are difficult, Bitcoin mining has been found to be highly unsustainable in some cases [
81]. However, according to other studies, Bitcoin mining operations can contribute to reducing greenhouse gas emissions and support the transition to renewable energy [
82]. Besides, other studies suggest that Bitcoin mining’s environmental impact is lower than that of traditional banking systems and that its negative impact could be mitigated by using renewable energy sources [
83]. The environmental impact of Bitcoin mining may decrease per terahash (TH) mined in the future due to improvements in mining equipment efficiency and geographical distribution of miners [
84]. A recent study suggests that Bitcoin mining in US states that have cheap and sustainable electricity, high share of renewable energy, and low electricity prices could be economically viable, and carbon capture technology could be a cost-effective solution for reducing CO2 emissions [
85].
It is worth noting that Bitcoin miners utilize stranded energy assets in remote areas, which would have been wasted otherwise, and they reduce methane emissions by capturing waste methane from industrial processes and converting it into hash rate for the Bitcoin network. Therefore, in the near future, Bitcoin mining could transition from a “low carbon” and “net zero” mining process to a “Climate positive” global monetary infrastructure directly linked to net greenhouse gas (GHG) emissions reductions and corresponding net positive climate benefits. According to a recent report published by the Bitcoin Mining Council, which represents 53 mining companies accounting for 48.4 percent of the global network, the amount of global energy used by Bitcoin mining is inconsequential (17bps), and it generates minimal carbon emissions (11bps). Although the hash rate of Bitcoin mining has increased by 45% YoY, energy usage has only increased by 25% YoY due to improved efficiency (16%). Furthermore, Bitcoin is leading the industry in sustainability with a sustainable energy mix of 58.9% [
86].
Inclusiveness, neutrality and censorship-resistant properties of the LN:
While the LN primarily serves as a scaling solution to address Bitcoin’s transaction throughput limitations, it does have some properties that can be seen as inclusive, neutral, and censorship-resistant. This is particularly true if we consider the economic polarization observed in nowadays and the way global financial assets are used [
87]. For instance, SWIFT, despite emphasizing its apolitical nature, has become a geopolitical tool that could be compromised and weaponized [
88].
On the other hand, LN nodes operate in a decentralized network, which means that there is no central authority controlling the network. This makes it a neutral platform, with no single entity controlling access or influencing the flow of payments. Additionally, LN payments are encrypted and routed through multiple nodes, making it difficult to track or censor individual transactions. In addition, the LN enables micropayments, which allows for a greater degree of inclusiveness by enabling transactions that would otherwise be too small to be economically viable on the Bitcoin blockchain. This makes it possible for individuals and businesses with lower income or limited access to traditional financial services to participate in the digital economy. However, as mentioned previously, the LN is not entirely immune to centralization or censorship. While LN nodes are currently operated by a diverse group of individuals and organizations, it is possible for certain nodes or groups of nodes to gain a significant degree of control over the network. Additionally, while censorship-resistant, LN payments are still subject to the laws and regulations of the jurisdictions in which they operate.
Decentralized ownership property rights and financial gains:
The global monetary system depends on centralized structures, with banks and central banks managing and maintaining payment infrastructure. While providing stability and oversight, these centralized systems may lack flexibility, accessibility, and decentralized control offered by the LN [
89]. The LN serves as a tool for ordinary individuals to attain decentralized ownership property rights and financial gains, allowing users to develop and maintain their own nodes, making them owners of a global payment infrastructure. This decentralized ownership fosters a more democratic payment system, where users have greater control and contribute to the network’s security and success.
The LN also enables users to benefit from lower transaction fees and faster processing times. It promotes decentralized ownership and financial gains by allowing node operators to earn interest income without default risk, through a unique mechanism where operators provide the digital energy needed to route bitcoins while retaining custody. By opening payment channels and locking up bitcoins, operators facilitate faster, off-chain transactions and earn fees for routing payments. Continued custody of bitcoins with node operators ensures decentralized ownership and eliminates the need for a centralized authority. HTLCs provide a secure, trustless environment, with locked-up bitcoins as collateral, guaranteeing payment to node operators without default risk.
It’s no exaggeration to say that we foresee a prosumer model in the context of the LN. The term "prosumer" refers to individuals who are both producers and consumers, a concept that has similarities to business models involving external parties in the value chain architecture, such as in the energy sector. In the case of the LN, users can develop and maintain their own nodes, effectively making them owners of a global payment infrastructure and allowing them to contribute to the network’s overall security and success. At the same time, they benefit from the lower transaction fees and faster transaction times that the LN offers. Therefore, the prosumer model in the LN is similar to the energy sector’s prosumer concept, where individuals both produce and consume energy. In this case, users contribute to the payment infrastructure (production) while also benefiting from its services (consumption). This decentralized and democratic payment infrastructure empowers users to take control of their participation in the network and can lead to a more robust and resilient system.
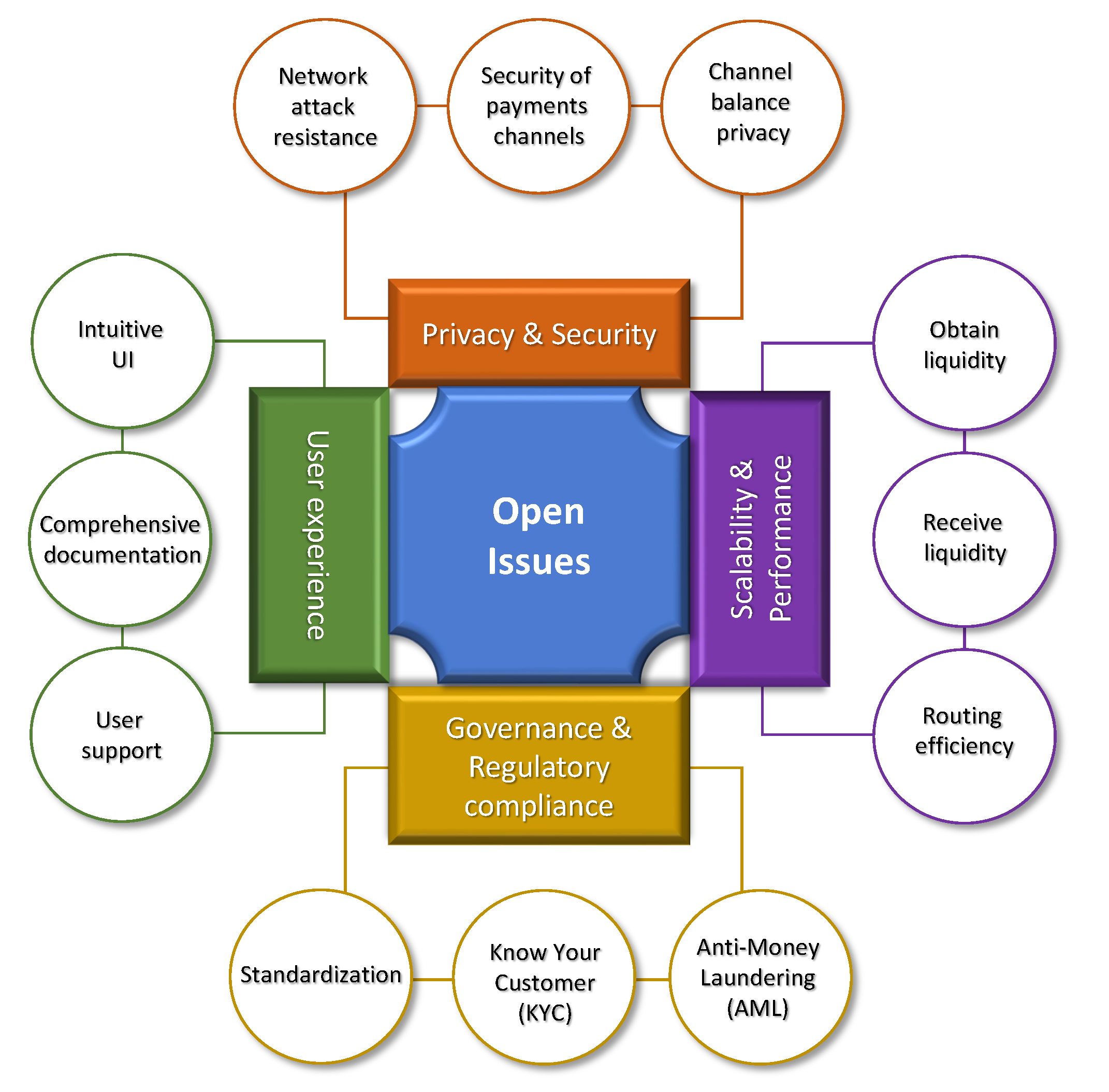
5.1. Open issues and adoption challenges
Despite its promising advantages, the LN remains in the early stages of development and adoption. Its current state, characterized by a limited number of peers and channels with restricted capacities, presents several challenges and risks that must be addressed to facilitate its widespread acceptance as a global payment system, as seen in
Figure 7. This explains a number of weaknesses that have been observed through simulations such as in the work of [
63]. In the sequence, we provide a classification of the main adoption challenges prevalent to the LN.
Privacy and security: Privacy and security are critical components of any financial system, and the LN is no exception. In recent years, several researchers have conducted investigations into the privacy and security issues that may arise in the context of the LN. The most significant issues identified so far include the risk of network breaches, routing attacks, and node privacy. While these concerns are not unique to the LN and affect other payment systems, they are particularly relevant to the LN due to its decentralized nature. The main security and privacy challenges of the LN include:
Channel balance privacy: the risk of exposing channel balances during routing, which could reveal sensitive information about users’ funds. For example, the balance disclosure attack could reveal the balance of a channel by carrying out multiple non-finalized payments. The use of a multi-payment method, called Torrent, has been proposed by [
43,
59] as a mitigation strategy. Additionally, an attacker could obtain sensitive payment information by controlling just 2% of nodes, as presented in [
48], by performing a wormhole attack. To decrease the exposure to this risk, users are suggested to open channels only with trusted parties.
Security of payment channels: payment channels could be insecure, particularly in scenarios involving channel closure or uncooperative participants. For example, as mentioned in [
12], an attacker could steal funds from nodes on the LN by causing congestion on the Bitcoin blockchain and exploiting the use of time locks to route payments. In another example, presented in [
90], malicious actors could disable channels by repeatedly sending small payments through them and holding onto the corresponding HTLCs, causing channels to become frozen.
Network attack resistance: the network may not always be able to resist in potential attack vectors, such as denial-of-service or eclipse attacks. For example, as presented in [
90], an attacker can isolate a victim node, shut down Lightning channels, and steal funds without the victim being aware. Research has also found that the scale-free network topology used in the LN, makes it resistant to random disruptions but vulnerable to targeted attacks on highly connected hub nodes [
28,
41]. This means that removing a small number of key nodes can lead to a significant decrease in the efficiency of the network, and in some cases, cause the network to break down into disconnected parts [
30,
34,
36]. Note, also, that an attacker could obtain sensitive payment information by controlling just 2% of nodes, as presented in [
48], by performing a wormhole attack. To decrease the exposure to this risk, users are suggested to open channels only with trusted parties.
Scalability and performance: Scalability and performance are critical aspects of the LN, as it was specifically designed to address Bitcoin’s inherent limitations in transaction throughput and latency. The network’s core purpose is to enable a higher volume of transactions to be processed swiftly and at a fraction of the cost associated with on-chain transactions.
Obtaining and receiving liquidity is a vital issue for the scalability and performance of the LN. Non-custodial users must secure receiving liquidity from another node, which presents a fundamental limitation. Custodial solutions can bypass this issue but compromise control over funds. Limited liquidity is a significant problem, as highlighted in [
31], since payments require intermediaries to transmit collateral through multiple channels, necessitating sufficient Bitcoins in each channel for the payment’s direction. Insufficient channel capacities often lead to payment route unavailability. This can be addressed by establishing channels with adequate capacity or using more sophisticated methods like Atomic Multi-Path Payments [
63,
73,
77]. These methods break down large payments into smaller ones, which can be transmitted through lower capacity channels and recombined by the recipient. Several attacks have been reported related to the issue of channel liquidity, which can have a significant impact on performance and even network operation. The Griefing Attack for example, as mentioned in [
53], could allow an adversary to deliberately drain the channel capacity, blocking it for an extended period and causing harm to several nodes by preventing them from processing future transaction requests.
Routing efficiency is also a crucial challenge for the scalability and performance of the LN, as it directly impacts transaction success rates, speed, and overall user experience. The network relies on decentralized, multi-hop routing to facilitate transactions. As pointed out by [
64], the routing issue is contingent on the fee structure used by LN nodes for processing payments, as intermediate nodes impose a fixed fee plus a fee proportional to the payment being forwarded. Therefore, inefficient routing can lead to increased payment failures, higher transaction latency, and a diminished user experience. As the network expands and the number of channels and nodes increases, optimizing routing efficiency becomes even more critical. As presented in [
76], the three crucial elements of the LN - fees, channel imbalances, and routing path lengths - are in conflict and cannot be optimized simultaneously. Therefore, there is a need for development of robust algorithms that can swiftly identify optimal payment routes. Some researchers have worked towards this direction like [
76], where they proposed having fees proportional to the square root of the channel capacity, allowing for reasonably short path lengths and well-balanced channel capacities.
To fully realize the LN’s potential in promoting widespread Bitcoin adoption for everyday transactions, it is crucial to address the challenges related to channel capacity and routing efficiency. Overcoming these obstacles will enhance user experience and facilitate the network’s scalability and performance.
Governance and regulatory compliance: One of the primary governance open issues in the LN is standardization. Arguably, effective governance structures help to establish the rules and procedures necessary for developing and implementing technical standards. Without effective governance, it can be difficult to reach a consensus on the adoption of common standards, and competing interests may result in fragmentation and inconsistency in the development and implementation of the LN. The LN requires a high degree of interoperability and compatibility across various implementations. The development and adoption of technical standards is needed to ensure seamless communication between nodes and maintain consistency in the network’s operation. Standardization could also help reduce potential fragmentation that could arise from divergent implementations, which could hamper the network’s growth and user experience. As the LN continues to evolve, fostering collaboration among developers, researchers, and industry stakeholders is essential in establishing widely-accepted standards that promote a unified and reliable system.
Regulatory compliance is also a significant concern, as the evolving legal landscape for cryptocurrencies and digital assets necessitates adherence to various rules and regulations due to the complex legal environment that varies across jurisdictions. Ensuring compliance with existing laws, such as those related to consumer protection, securities, and taxation, is essential to maintain the network’s legitimacy and foster wider adoption. Additionally, keeping abreast of regulatory developments and adapting to new requirements will be crucial for the network’s long-term success and stability. Engaging with regulators and policymakers to promote a clear understanding of the technology and its potential benefits can help facilitate a more conducive regulatory environment for the LN and other decentralized financial systems.
In addition, an aspect of regulatory compliance in the LN is addressing Anti-Money Laundering (AML) and Know Your Customer (KYC) requirements. While the LN’s privacy-preserving features offer significant benefits to users, they can also present challenges in meeting AML/KYC obligations. Developing and implementing mechanisms that strike a balance between preserving user privacy and complying with regulatory requirements is vital. By demonstrating a commitment to regulatory compliance and responsible innovation, the LN can cultivate trust among users, regulators, and the broader financial ecosystem, ultimately contributing to its growth and widespread acceptance.
User experience: One of the primary adoption challenge faced by the LN is the need to improve user experience. As a layer-two solution for Bitcoin, the network aims to provide faster, more scalable transactions. However, for the LN to gain mainstream acceptance, it must be accessible and user-friendly for both merchants and consumers. Simplifying the process of setting up and managing channels, securing liquidity, and handling transactions is essential to attract a broader audience. Developing intuitive interfaces, comprehensive documentation, and user support will not only help drive adoption but also build trust in the network’s capabilities. For example, Speed
10 is a company focusing on Bitcoin payment solutions and supports both online and offline transactions. It offers both static and dynamic QR codes, and it’s system is developer-friendly. Speed facilitates bitcoin payments, manages business operations over the LN, and is available for use by individuals and businesses worldwide.
Another crucial challenge for the LN’s adoption is its integration with existing systems and services. For the network to become a viable payment solution, it must seamlessly interact with traditional financial infrastructure, as well as other blockchain-based systems. Facilitating compatibility and interoperability with existing payment gateways, e-commerce platforms, and point-of-sale systems will be critical to encourage merchants to adopt the LN as a payment method. Additionally, integration with popular wallets, exchanges, and other cryptocurrency services will further promote its usage. By addressing these adoption challenges and bridging the gap between the LN and current financial systems, the network can position itself as a reliable, efficient, and accessible solution for instant, low-cost Bitcoin transactions.
5.2. Key findings and future research suggestions
In the sequence, we present a synopsis of the primary outcomes of our investigation in line with the different research questions we had at the outset. Additionally, we suggest several possibilities for future research that are relevant to the LN and its acceptance as a viable global payment infrustructure.
RQ1: According to the relevant literature, the LN has several current and potential business-related applications, including micropayments, cross-border and remittance payments, IoT and machine-to-machine payments, decentralized exchanges, transfers of digital assets, and LN-related services. In particular, the LN enables businesses to expand their customer base globally, without the need for middlemen or high fees. It can enhance productivity, monetize offerings, reduce transaction costs, increase transaction speed, and streamline payment processes across various sectors. The LN ecosystem consists of a diverse array of companies and participants, each contributing to the network’s maintenance and growth in their unique way. Overall, the LN represents a promising innovation in the blockchain space, with significant potential to transform the way businesses operate and transact.
RQ2: The LN has undergone significant research and development, with interesting progress made in its network topology, performance, privacy, and security. However, there are still technical challenges that need to be addressed to ensure its widespread adoption and effectiveness for business-related applications. In terms of network topology, the LN has been found to exhibit scale-free and small-world characteristics, making it susceptible to targeted attacks and DDoS attacks. Moreover, several studies have shown that the network is becoming more centralized, with a few highly active nodes holding the majority of bitcoins, making it vulnerable to split attacks. These findings highlight the importance of improving the network’s structure for enhanced security and potential. With respect to performance, several studies have focused on optimizing global transaction paths and improving the efficiency of the LN. However, researchers have identified technical challenges such as convergence delays, payment attempt failures, and network imbalance that need to be addressed to improve the protocol’s effectiveness for business-related applications. Regarding privacy, research has proposed various countermeasures to address the vulnerabilities of the LN, including balance disclosure attacks and collusion attacks. Additionally, researchers have proposed methods to improve transaction privacy, such as approximate differential privacy and space-efficient key management schemes. However, there are still concerns about privacy breaches, particularly in the case of jamming-enhanced probing, which can extract full balance information. Finally, with respect to security, researchers have identified several vulnerabilities in the LN, including channel balance disclosure attacks, node isolation attacks, and wormhole attacks. There are also concerns about the increasing centralization of the network and the resulting vulnerabilities, making it susceptible to split attacks and targeted attacks. Arguably, while the LN’s potential is vast, it may face challenges in adoption and implementation due to the above-mentioned technical challenges.
RQ3: Businesses may face several adoption challenges when using the LN. One of the primary challenges is the need to improve user experience, as the current process of setting up and managing channels, securing liquidity, and handling transactions can be complex and challenging. This may deter businesses from adopting the LN as a payment solution, particularly those with less technical expertise. Limited liquidity is also a significant problem that can have a significant impact on performance and even network operation. Payments require intermediaries to transmit collateral through multiple channels, necessitating sufficient bitcoins in each channel for the payment’s direction. Insufficient channel capacities often lead to payment route unavailability, which can cause inconvenience and delays for businesses that need to process a high volume of transactions. Regulatory compliance is another significant challenge for businesses using the LN. Ensuring compliance with existing laws, such as those related to consumer protection, securities, and taxation, can be complex and time-consuming, particularly as the legal environment for cryptocurrencies and digital assets continues to evolve. Adapting to new regulatory requirements and keeping abreast of regulatory developments can also be challenging, particularly for small and medium-sized enterprises with limited resources. Finally, businesses may also face challenges related to integrating the LN with existing systems and services. Facilitating compatibility and interoperability with existing payment gateways, e-commerce platforms, and point-of-sale systems can be complex and require significant technical expertise. Integration with popular wallets, exchanges, and other cryptocurrency services may also be necessary to promote the LN’s usage, but this may require additional resources and investment.
Based on the aforementioned findings, some fruitful areas for future research directions with respect to the LN, it’s characteristics and adoption, include:
Scalability, interoperability, and performance: Research should focus on improving the LN’s scalability to handle a growing number of transactions while ensuring interoperability with other blockchain platforms and payment systems. This includes optimizing the network topology to enhance resilience against attacks, addressing performance challenges such as convergence delays and network imbalance, and designing incentive mechanisms to encourage a decentralized distribution of nodes and channels.
Security and privacy: Future research should examine security risks and privacy concerns associated with the LN, developing methods to mitigate these issues while maintaining the network’s efficiency and speed. This includes creating advanced privacy solutions to counterbalance various attacks and examining the trade-offs between privacy, performance, and network security. Researchers should work on identifying and addressing security vulnerabilities in the LN and developing adaptive routing protocols that can dynamically respond to network changes, congestion, and potential attacks, in order to maintain high transaction throughput and low latency.
Regulatory frameworks and market adoption: Investigating appropriate regulatory frameworks for successful LN implementation and adoption is crucial, addressing compliance, consumer protection, and taxation issues. Additionally, understanding factors that influence LN adoption across industries and exploring innovative financial services and products through the LN will help expand its applications. To understand the adoption of the LN, we can use game theory to model the behavior of various actors, such as bitcoin users, merchants, payment processors, and developers.
Integration with IoT, M2M ecosystems, and existing systems: Studying potential LN use cases in the context of IoT and M2M ecosystems is essential, as well as examining technical requirements for integration. Additionally, research should focus on seamless integration of the LN with existing payment systems and explore tailored solutions for small and medium-sized enterprises to address their specific challenges and resource limitations.
Economic, social impact, and impact assessment: Investigating the broader economic and social implications of widespread LN adoption, such as financial inclusion and global economic growth, is essential. Evaluating the impact of LN adoption on businesses and developing metrics to assess the effectiveness of LN integration and adoption efforts will help drive informed decision-making. Analyzing the potential implications of LN adoption for traditional financial institutions is important for understanding how they might need to adapt their business models and strategies to remain competitive in a blockchain-driven financial landscape.
Education and awareness: Developing educational resources and initiatives to increase LN awareness among businesses, policymakers, and the general public is crucial for facilitating its adoption and integration into mainstream financial systems.
Usability, user experience, and liquidity management: Research should focus on improving the LN’s usability and user experience, addressing onboarding, user interface, and user support. Enhancing the user experience by simplifying channel management and securing liquidity, as well as developing innovative solutions to address liquidity and channel capacity issues, will make LN adoption more accessible for businesses with varying technical expertise.
5.3. Limitations
Narrative reviews, while valuable for understanding crucial policy issues and shaping future research, possess several limitations that merit acknowledgement. One limitation is that narrative reviews are founded upon the author’s interpretation of the literature, which can lead to cherry-picking evidence to support a specific viewpoint, consequently affecting the credibility of the review [
22,
23]. This issue can be particularly concerning if the authors have a vested interest in the outcome or a strong pre-existing belief about the topic under review. In our analysis, however, we utilized all available scientific literature, striving to minimize inclusion bias.
Another weakness of narrative reviews is the lack of transparency in their methodology. In contrast to systematic reviews, which adhere to a rigorous set of guidelines for selecting and analyzing studies, narrative reviews may be less transparent in their approach. This lack of clarity can make it challenging for readers to assess the quality of the review and determine whether the author’s conclusions are substantiated by the evidence. To address this particular limitation, we employed a semi-systematic narrative review approach.
Despite these limitations, when conducted effectively, narrative reviews can still prove valuable for comprehending vital policy issues and informing the direction of future research programs [
23].