I. Introduction
The international standard for the network communication system is becoming a necessity because of its early success. The whole network communication system is standardized and organized into seven different layers, named as the Open System Interconnection (OSI) model [
1]. The OSI model is a model for understanding the internet and how it works.
The main objective of this article is to provide overview of different layers of the OSI Model. At first, a brief description of the OSI model has been presented in this article, followed by an example to demonstrate the operation of interent.
II. Open System Interconnection Model
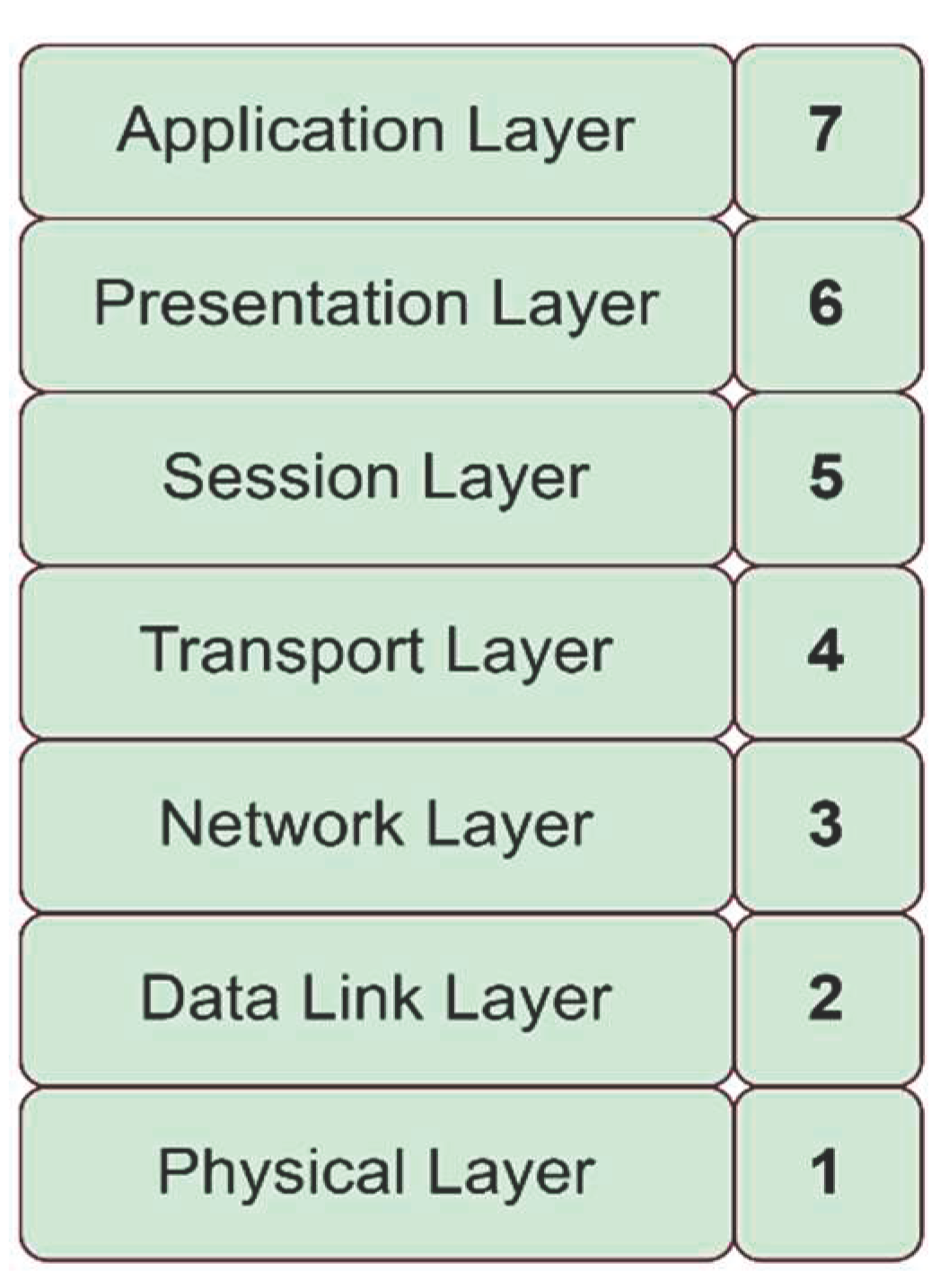
The OSI model consists of seven different layers as shown in Fig 1. Each layer is a packet of protocols [
2], and they are named according to their functions.
Figure 1.
OSI model layers (client side top to bottom; server side bottom to top).
Figure 1.
OSI model layers (client side top to bottom; server side bottom to top).
A. Application Layer
Network applications use the application layer. Network application means computer application that uses the internet. Google Chrome, Zoom, Skype, and Outlook are examples of computer applications. It does not mean that it includes all these computer applications, but it provides application-layer protocols that are required to make these applications operate correctly on the network. The Application layer contains all services or protocols required by application software or operating system to communicate on the network [
3]. It represents the services that directly support the user application (Google Chrome, Zoom, Skype, outlook) and looks at what the user sees or does. Email and messaging can be done with the help of the application layer. File transfer is also supported in this layer.
The different application uses different application layer protocols. Web browsers (Chrome, Firefox, etc.) use an application layer protocol named Hyper Text Transfer Protocol (HTTP) or HTTPs to do web surfing. Email uses Post Office Protocol version 3 (POP3) to read emails and Simple mail transport protocol (SMTP) to send an email. File Transfer Protocol (FTP) is used for transferring files [
4].
B. Presentation Layer
The presentation layer receives data from the application layer. In this layer, the data is converted into a machine-readable format (a combination of 0 and 1) for outgoing messages, and for incoming messages, the machine-readable binary format (a combination of 0 and 1) is then converted into a human-readable format. The process of converting data is known as translation.
The presentation layer also reduces the size of the data before transmitting it. It reduces the number of bits (a combination of 0 and 1) that are used to represent the original data. This bit-reduction process is called data compression [
5]. It could be lossy or lossless. Data compression reduces the amount of space that is used to store the original files. As the file size is reduced, it can be reached the destination in less possible time. As a result of this process, data transmission happens faster. It is very helpful for real-time video or audio streaming.
Before transmission, the data is encrypted to maintain the integrity of the data. Encryption enhances the security of the data. Data encryption takes place on the sender’s side and it is decrypted on the receiving side. Secure Sockets Layer (SSL) protocol is used in the presentation layer for encryption and decryption. This process protects the data from interception.
C. Session Layer
The session layer set up and manage the connection between two devices by enabling sending and receiving data, followed by the opening, and closing of the session. The session layer uses ports to initiate communication between two devices. The time between when this connection is opened and closed is known as a session. This layer ensures that the session will stay open until all the data are transferred and then closes the session to avoid wasting resources.
The session layer also helps to synchronize data with the help of a checkpoint. In case of a disconnection or crash of data transmission, the session could be resumed from the checkpoint's last transfer of data. Without a checkpoint, the entire transfer would have to begin from scratch [
6].
The session layer contains its own command sets named Application Program Interfaces (APIs). One popular example of APIs is the Network Basic Input Output System (NetBIOS which allows applications on different computers to communicate.
D. Transport Layer
The transport layer transfers the packets of data from the network layer to the session layer. It takes data from the session layer and then splits it up into segments for sending the data. On the other hand, it reassembles the segments into data in the receiving device. Each segment contains a source and destination port number with a sequence number. The Port number helps to direct each segment to reach the correct application (Google Chrome, Zoom, Skype, Outlook). The sequence number helps to reassemble the segments into precise order to form the right message on the receiving end. This process is called segmentation.
One of the key functions of the transport layer is controlling the data flow. If the sending device and the receiving device have different data rates, then the transport layer helps adjust the data rate according to the receiving device so that no data gets lost. This layer also helps in error control. If some data does not reach the destination, it uses an automatic repeat request scheme to retransmit the missing data.
The transport layer mainly uses two protocols: 1) Transport Layer Protocol (TCP) and 2) User Datagram Protocol (UDP). It performs both connectionless transmission and connection-oriented transmission. UDP does the connectionless transmission, and TCP does the connection-oriented transmission [
7]. UDP is comparatively faster than TCP because it does not provide any feedback on whether the data was delivered or not. On the other hand, TCP provides feedback. As a result, lost data can be retransmitted in TCP protocol. Online streaming movies, songs, and video games use UDP because it is less important for these applications, whether the data is received fully or not. World Wide Web (WWW), email, and File Transfer Protocol (FTP) use TCP.
E. Network Layer
The network layer takes data segments from the transport layer and transmits the data from one device to another device located in two different networks [
8]. It breaks up the data segments into smaller units called packets in the sender device and reassembles these packets on the receiver device. This layer performs mainly three functions: 1) Logical addressing, 2) Routing, and 3) Path determination.
Internet Protocol (IP) addressing (such as IPv4, IPv6) is done in the network layer known as logical addressing. Every device in a network that can be connected to the internet has an IP address as a form of digital identification. IP addresses are assigned in order to ensure that each data packet can reach the correct destination device. The IP address can be considered as a mailing address of an apartment. It is an address to devices so that the data can reach a particular device.
Routing is a process to transfer data packets from source to destination based on the logical address. A device can connect to the internet server or any other device in different paths or ways. Selecting the best possible route for data delivery from sender to receiver is known as path determination. Broder Gateway Protocol (BGP), Open Shortest Path First (OSPF), Intermediate System to Intermediate System (IS-IS) protocols are used to determine the best possible path for data delivery.
F. Data Link Layer
The data link layer takes packets of data from the network layer and turns the data packet into frames. The data packet contains the IP addresses of the sender and receiver. There are two types of addressing: Logical addressing and physical addressing [
9]. Logical addressing happens in the network layer, as discussed in the network layer, where the sender and receiver IP addresses are assigned to each data segment to form data packets. Physical addressing happens in the data link layer where MAC (Media Access control) addresses of the sender and receiver are added to each data packet to form a frame [
10]. This process of creating frames of data is known as a framing technique. MAC address is an alphanumeric number that is embedded in the Network Interface Controller (NIC) of a device by the device manufacturer.
The data link layer allows the OSI model’s upper layer to access media (copper wires, optical fibers, wireless antenna, etc.) using the framing technique.
G. Physical Layer
This layer includes all the physical equipment that is associated with data transfer. In this layer, the binary bitstreams (the combination of 0 and 1) convert into different signals on the receiving side, and reverse conversion has happened on the sending side.
As from the above discussion, it is clear that data from the application layer has been segmented by the transport layer, turned into the packet in the network layer, and framed by the data link layer, which is a sequence of bitstreams (the combination of 0 and 1). The physical layer converts this bitstream into signals and transmits it into the media (copper cable, optical fiber, etc.). Signals generated by the physical layer depend on the types of media used to connect two devices. The signal could be an electrical signal for Cooper wire media, a light signal for optical fiber, and raido a signal for wireless media.
III. An Example: Electronic mail
An Example of sending electronic mail (email) is considered here to illustrate the operation process of the Internet.
The sender first needs to compose a message in an email application on his computer to send an email. As soon as s/he hits the send button, the email application will pass the message (data) to the application layer. It will take a protocol (e.g. Simple Mail Transfer Protocol) and pass the data to the presentation layer, where the email is converted into binary form. Translation, compression, and encryption of the data take place in this layer. Secure Sockets Layer (SSL) protocol is used in the presentation layer for data encryption and decryption. The presentation layer will send the data to the session layer, and the session layer will initiate the communication session. The session layer uses ports to initiate communication. Then the transport layer will split the data into segments. Each data segment contains a source and destination port number with the sequence number. Email uses TCP protocol in the transport layer. The segment will be transformed into a packet in the network layer. The network layer assigns the sender and receiver IP address to each segment to form a data packet, which will be again turned into frames at the data link layer. The Media Access Control (MAC) address of the sender and receiver is added to the data packet to form the frame. The data link layer will send those frames to the physical layer where the data will be converted into bitstreams of 1 and 0 and delivered it through a physical media (such as wire, optical fiber, etc.).
When the receiver computer receives the bitstreams, the data will flow through the same series but in the opposite order. First, the physical layer will convert the bitstream into frames, and then it will pass it to the data link layer. The Data link layer reassembles the frames into a data packet for the network layer, and the network layer makes data segments from this packet of data. The transport layer reassembles the segments into one piece of data. Data will then flow to the receiver’s session layer, which will pass the data to the presentation layer and then close the communication session. The presentation layer will remove the compression and pass the data to the application layer. At last, the application layer will then make the data into a human-readable format. In the application layer, the POP3 protocol is used to read the email.
IV. Conclusion
This article presents a brief overview of the different layers of the OSI model. It is important to understand the OSI model to properly underatnd the working principle of the internet. With the help of the OSI model, the working process of the internet can be demonstrated in an easier way. Different interconnected networking systems are utilized for the operation of the Internet. For example, A device is typically connected to another device (s) via an optical fiber cable network. Devices like computers or mobile phones are connected to the internet via Wi-Fi or mobile cellular data, and the antenna of the cellular company or the Wi-Fi router is connected to the optical fiber cable. Therefore, ultimately our devices are connected to this optical fiber cable network. An example of sending electronic mail has been included in this article to describe the operating process of the internet.
References
- Aarushi Madan, Aarushi Tuteja and Bharti, “OSI Reference Model”, International Journal of Advanced Research in Computer Science and Software Engineering, Vol. 4, Issue 9, P 55-58 September 2014.
- H. Zimmermann, "OSI Reference Model - The ISO Model of Architecture for Open Systems Interconnection," in IEEE Transactions on Communications, vol. 28, no. 4, pp. 425-432, April 1980. [CrossRef]
- J. D. Day and H. Zimmermann, "The OSI reference model," in Proceedings of the IEEE, vol. 71, no. 12, pp. 1334-1340, Dec. 1983. [CrossRef]
- T.P Cavaiani, “Using the OSI model to teach problem”, Journal of information systems Education, P 191-192, 2002.
- P. Kritzinger, "A Performance Model of the OSI Communication Architecture," in IEEE Transactions on Communications, vol. 34, no. 6, pp. 554-563, June 1986. [CrossRef]
- M. E. Ilchenko, A. V Moshinskaya and L. A. Urywsky, “Levels separation and merging in the OSI reference model for information–telecommunication systems”, Cybernetics and Systems Analysis, Vol. 47, No. 4, P 598-605, July 2011. [CrossRef]
- M. Zafirovic-Vukotic and I. G. Niemegeers, "Multimedia communication systems: upper layers in the OSI reference model," in IEEE Journal on Selected Areas in Communications, vol. 10, no. 9, pp. 1397-1402, Dec. 1992. [CrossRef]
- T. Stergiou, M.S. Leeson and R.J. Green, “An alternative architectural framework to the OSI security model”, Computers & Security, 23, P 137-153 (2004).
- V. Salvi and P. Bapat “Mode of Data Flow in the OSI Model”, International Journal of Innovations in Engineering Research and Technology [IJIERT], ISSN: 2394-3696, VOLUME 2, ISSUE, P 1-7, 3 MARCH 2015.
- J. Conard, "Character-Oriented Data Link Control Protocols," in IEEE Transactions on Communications, vol. 28, no. 4, pp. 445-454, April 1980. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).