1. Introduction
A key problem is to guarantee cryptographic security of data transmission in the management of UAV [
1,
2], intelligent robots [
3], microsatellites [
4] and various mobile transport systems [
5]. Due to the security vulnerabilities of UAVs, and illegal and malicious attacks against UAVs, especially against communication data and UAV control, solutions to prevent such attacks are needed, and one of them is to encrypt UAV’s communication data [
6,
7,
8]. Unmanned Aerial Vehicles (UAVs) must be energy-efficient, especially in data processing, because of limited battery capacity [
9]. Solving this problem requires the development of neural network (NN) technology [
10,
11,
12] for cryptographic data protection, which is focused on use in UAV onboard communication systems. When developing onboard cryptographic data protection systems, it is necessary to provide real-time mode, increase cryptographic resistance, and noise immunity and reduce power consumption, weight, size and cost [
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23]. The usage of an auto-associative NN of direct propagation, which is trained on the basis of the principal components analysis, helps to conform such requirements. A specific feature of such neural networks is the ability of weight pre-calculation and to apply the tabular-algorithmic method for the implementation of neuro-like elements using the basis of elementary arithmetic operations. For NN cryptographic encryption and decryption of data, it is proposed to use symmetric keys, which include masking codes, NN architecture and a matrix of weights [
24,
25].
Through the extensive use of a modern component base and the development of new VLSI methods, algorithms and structures, high technical and operational rates of on-board cryptographic data protection systems are achieved. Onboard systems for NN cryptographic protection of data must have variable hardware for rapid changes in NN architecture. The use of modern element base (microcontrollers, programmable logic integrated circuits FPGA) in the development of onboard and embedded systems makes it possible to reduce their weight, size and power consumption [
26,
27], and in the development of onboard systems of NN cryptographic data protection provides a quick change of encryption and decryption keys.
NN cryptographic encryption and decryption of data in real-time is achieved through the application of parallel encryption and decryption of data, hardware implementation of neuro-like elements based on a multi-operand approach and macro-partial products tables.
Therefore, an urgent problem is to propose the approach to the implementation of NN for cryptographic data protection, focused on implementing in on-board systems with high technical and operational characteristics. The objective of the work is to study how to implement the onboard NN for real-time cryptographic data protection. In order to achieve this goal, the following tasks have to be solved:
development of the approach to NN cryptographic data protection;
development of the structure of the system of NN cryptographic protection and real-time data transmission;
development of components of onboard systems of NN cryptographic encryption-decryption of data;
implementation of the specialized hardware components of NN cryptographic data encryption on FPGA.
This article is structured as follows. In the introduction, we have considered the problem relevancy and the main objectives of this research.
Section 2 contains a brief review of the related works (the research context). The structure of NN technology for cryptographic data protection is described in
Section 3 and the main stages of NN data encryption/decryption are considered here as well.
Section 4 presents the structure of the system for NN cryptographic data protection and transmission (stationery and UAV onboard parts) developed using an integrated approach. The components of the onboard system for NN cryptographic data encryption and decryption are proposed in
Section 5, the diagrams for the specialized hardware are given.
2. Related Works
The study of the main trends in the area of UAV onboard systems development for real-time cryptographic data protection shows that NN methods are increasingly used for performing data encryption and decryption in such systems [
28,
29,
30,
31,
32]. These publications show that the implementation of NN methods of cryptographic data protection is performed generally by software. The critical drawback of software implementation of NN cryptographic data protection is the difficulty of providing real-time mode and the constraints imposed on on-board systems in terms of weight, size, power consumption and cost.
The possibilities of adapting the auto-associative NN with non-iterative learning for data protection tasks are considered in [
28,
29,
30,
31,
32]. The peculiarity of the functioning of such a NN is the preliminary calculation of weights as a result of its training based upon the principal component analysis (PCA). In this case a system of eigenvectors is used, that correspond to the eigenvalues of the covariance matrix of input data [
33]. To encrypt and decrypt data the auto-associative NN with pre-calculated weights is applied. In [
34] it was shown that the masking codes, the architecture of the NN and the matrix of weights are the basis to cryptographic encryption and decryption of data in neural networks.
Publications [
35,
36,
37] are devoted to the hardware implementation of neural networks showing that they are based on neural elements. The feature of such neural elements is that the number of inputs and their bit length are determined by the NN architecture, which is one of the characteristics of the data encryption key. The main operation of the neuroelement is the calculation of the scalar product using pre-calculated weights.
In [
37,
38,
39] the methods for calculating the scalar product using the basis of elementary arithmetic operations - addition and shift, are considered. The peculiarity of these methods is the formation of macro-partial products, their shift, and addition to the previously accumulated amount. Hardware implementation of such methods requires significant equipment costs. The implementation of a tabular-algorithmic method for calculating the scalar product, which is reduced to the operations of reading macro-partial products, addition and shift, requires fewer equipment costs and less computation time. The disadvantage of this method is that it is limited to fixed-point data format (for input data and weights).
Analyzing the works [
31,
41] it can be noted that NN tools for cryptographic symmetric encryption and decryption of data [
42] are implemented on the basis of microprocessors supplemented by hardware that implements time-consuming computational operations using FPGA [
43]. High speed of NN tools for cryptographic encryption and decryption of data is achieved through parallelization, pipeline computing processes and hardware implementation of neural elements. The disadvantage of the existing NN tools for cryptographic data protection is the difficulty of changing the encryption and decryption key rapidly.
3. The approach to NN implementation for cryptographic data protection
3.1. Structure of NN technology of cryptographic data protection
The implementation of NN for cryptographic protection of data transmission is focused on hardware and software implementation with high technical and operational characteristics. It is proposed to carry out such implementation on the basis of an integrated approach that includes:
research and development of theoretical foundations of neuro-like cryptographic data protection;
research and development of new algorithms and structures of neuro-like encryption and decryption of data focused on modern element base;
modern element base with the ability to program the structure;
means for automated design of software and hardware.
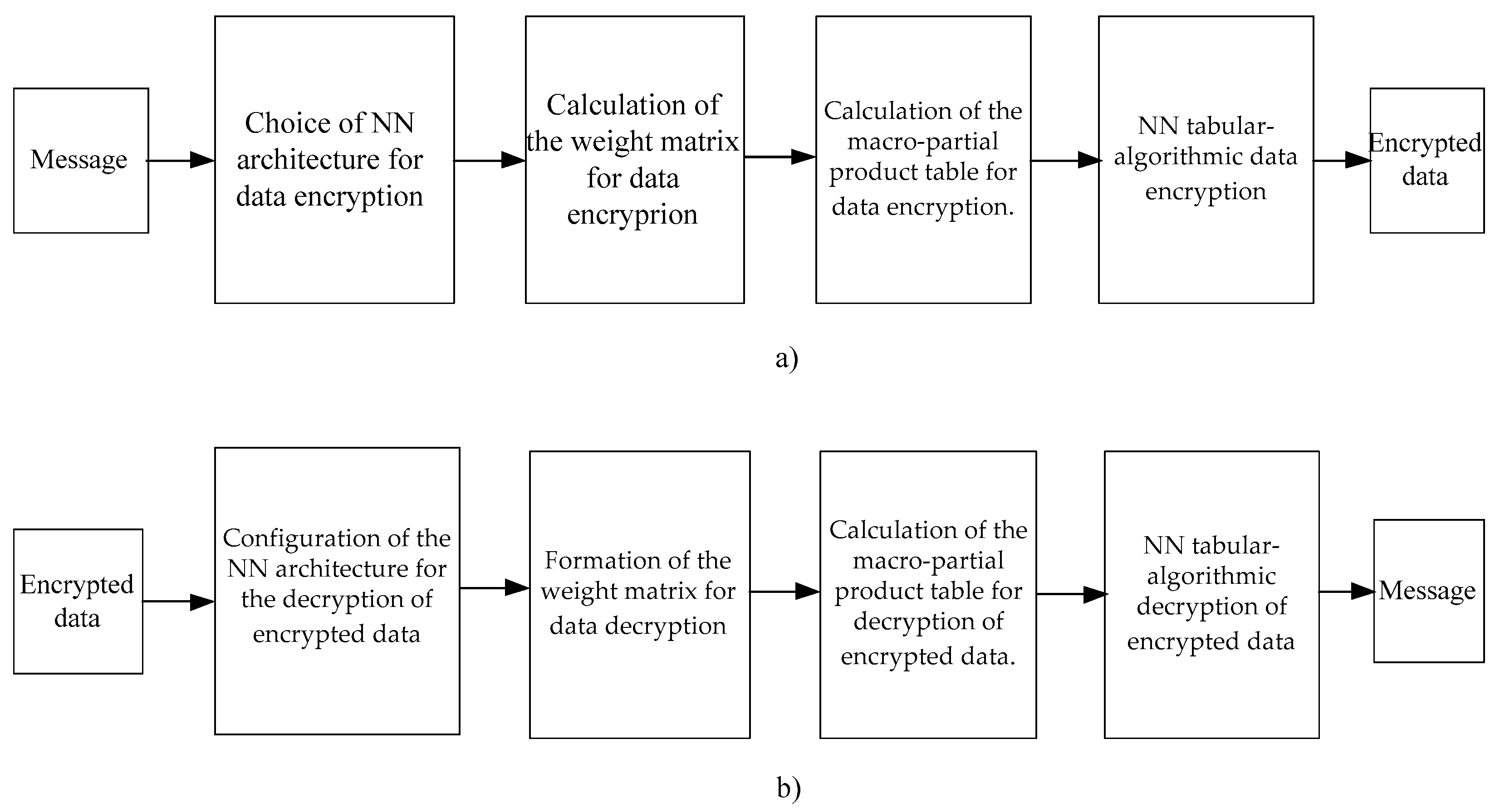
Figure 1 shows the developed structure of NN technology for cryptographic data protection, which is focused on hardware implementation and provides encryption with symmetric keys. When implementing the symmetric cryptosystem, the encryption key and the decryption key are the same or the decryption key is easily calculated from the encryption key.
For hardware implementation the proposed technology is based on the selection of auto-associative neural networks, which are trained non-iteratively. This allows us to calculate the matrix of weighting coefficients in advance and store them in the look-up tables, since they will be fixed for the selected NN configuration. The calculation of the output of the neuro-like element of this NN can be represented as the sum of the products of the weighting coefficients and the input data to be encrypted. To implement a quick calculation on the FPGA of the product of the fixed weighting coefficients and the input data, a table-algorithmic method of their calculation is applied. The tabular-algorithmic method makes it possible to implement high technical and operational characteristics of data encryption-decryption tools. A combination of these approaches ensures effective implementation on FPGAs.
The details of the above mentioned steps are described further in the article.
3.2. Main stages of NN encryption
The encryption uses a key consisting of neurons in the NN, a weight matrix and masking operations. The main stages of message encryption are considered below.
Choice of NN architecture. The number of neuro elements
, the number of inputs
and the bit inputs
determine the architecture of the NN. The number of neural elements is defined according to the following formula:
where
is the bit length of the message, and
– the bit length of the inputs.
The incoming messages which are encrypted can have different bit length () and different inputs number (), which is equal to the number of neuroelements . The architecture of the NN depends on the value of the bit length of the message n and the number of inputs k. Such configuration of the NN architecture is available to encrypt the bit message: , , ; , , ; , , , in case of they are: , , ; , , ; , , , , , ; , , ; , , .
Calculation of the weight matrix. For data encryption-decryption we will use an auto-associative NN, which learns non-iteratively using the principal components analysis (PCA), which performs a linear transformation following the formula:
According to formula (2), the matrix is used to convert the input vector into the output vector . The conversion is as follows. System of linearly independent vectors selects an orthonormal system of eigenvectors corresponding to the eigenvalues of the covariance matrix of the input data.
The input data is a set of
vectors
, with dimension
,
:
For
N vectors the autocovariance matrix
is:
where each of the elements is expressed by:
where
, and
,
– mathematical expectations of vectors
,
.
The eigenvalues of
symmetric non-negative matrix are real and positive numbers. They are arranged in descending order
. Similarly, the eigenvectors corresponding to
are placed. Therefore, a linear transformation (2) is defined by the matrix
W. Here
is a vector of the PCA principal components corresponding to the input data vector
. The number of principal components vectors
N conforms with the number of input data vectors
[
29]. The matrix of weights used to encrypt the data is as follows:
The basic operation of the NN used to encrypt data is the operation of calculating the scalar product. This operation should be implemented using the tabular-algorithmic method because the matrix of weights , where , , is pre-calculated.
Calculation of the table of macro-partial products for data encryption. The specificity of the scalar product calculation operation used in data encryption is that the weights are pre-calculated (constants) and set in floating point format, and the input data X_j is in fixed point format with its fixing before the high digit of a number. The scalar product is calculated by means of the tabular-algorithmic method according to the formula:
where
– number of products,
– input data,
–
-th weight coefficient,
– bit length of the input data,
– partial product,
– macro-partial product, formed by adding
partial products
, as follows:
.
Formation of the tables of macro-partial products for floating-point weights (where – mantissa of weight coefficient, – order of weight coefficient) foresees the following operations to be performed:
defining the largest common order of weights ;
calculation of the order difference for each weight coefficient: ;
shift the mantissa to the right by a difference of orders ;
calculation of macro-partial product for the case when ;
determining the number of overflow bits q in the macro-partial product for the case when ;
obtaining scalable mantissas by shifting them to the right by the number of overflow bits;
adding to the largest common order of weight the number of overflow bits q, as per formula .
The table of macro-partial products is calculated by the formula:
where
– address inputs of the table,
– mantissa of
weight coefficient brought to the greatest common order.
The possible combinations number of
macro-partial products and the table size is as follows:
Dividing all products by parts and we can reduce the table size. For each of these parts separate tables of macro-partial products and are formed and stored in separate memory blocks or a single memory block. When using two memory blocks, parts of the macro-partial products and are read in one clock cycle, and in one memory block - in two clock cycles. The sum of two macro-partial products and gives us the macro-partial product .
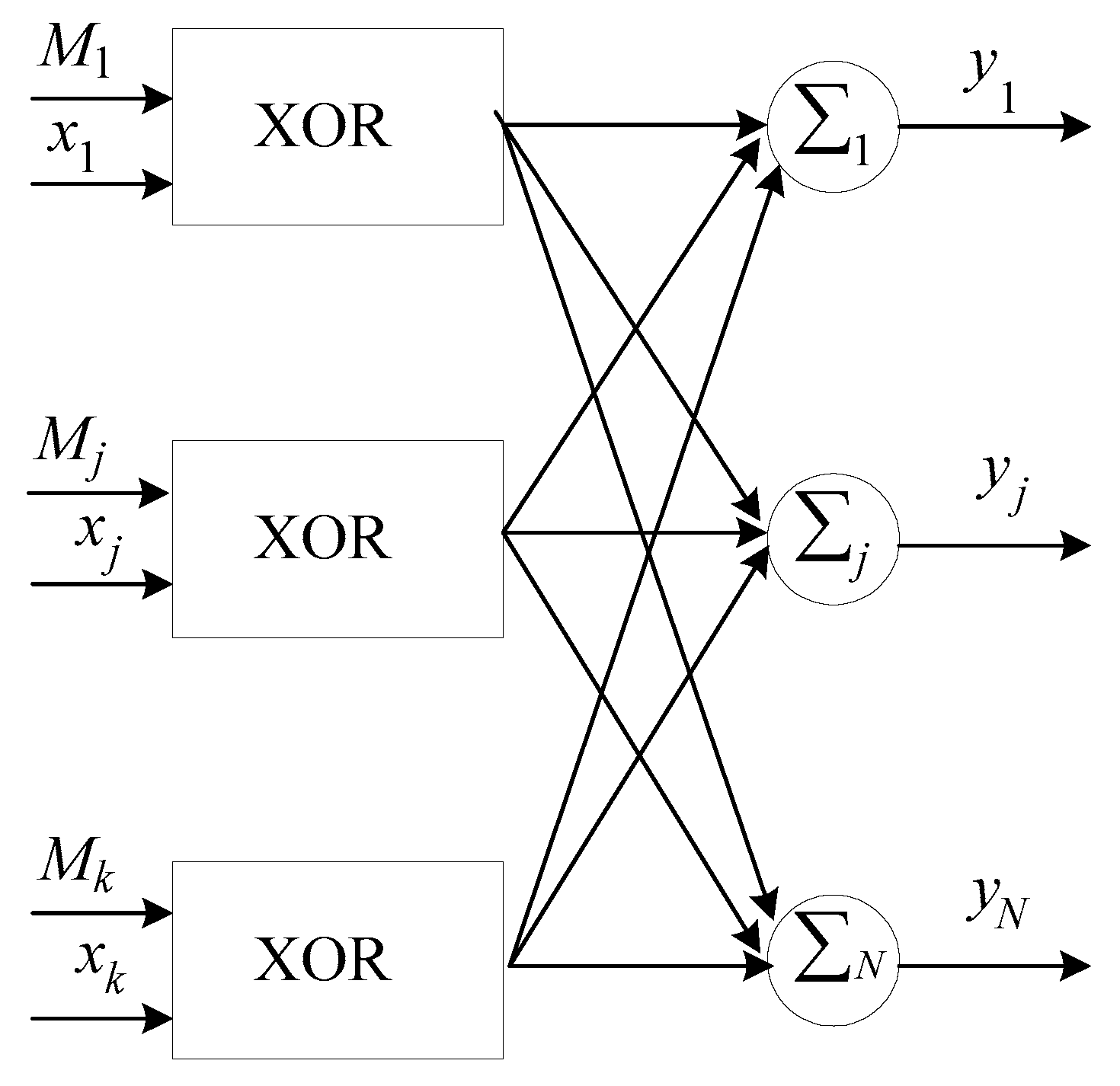
NN tabular-algorithmic data encryption. During the training of the NN the matrix of weights
W is determined.
Figure 2 shows the structure of auto-associative NN used for data encryption. Here
is the mask for the
-th input,
is the
-th input data, XOR is the masking operation using the exclusive OR elements.
To perform the NN data encryption we multiply the
matrix by the input data vector
according to the formula:
The multiplication of the matrix of weights
by the vector of input data
is reduced to performing
scalar product calculations:
where
– number of products,
.
The calculation of scalar products will be achieved using the tabular-algorithmic method, where the weights
are set in floating-point format, and the input data
– in a fixed-point format with fixation before the highest digit. Tabular-algorithmic calculation of the mantissa of the scalar product is reduced to reading the macro-partial product
from the j-th table (memory) at the address corresponding to the i-th bit slice of N input data, and adding it to the before accumulated sums according to:
where
,
,
– bit length of the input data. The number of tables of macro-partial products corresponds to
– the number of rows of the matrix (10). The result of calculating of the scalar product
consists of the mantissa
and the order
.
The time required to compute the mantissa of the scalar product (SP) is determined by the formula:
where
is the time of calculation of the scalar product,
is the time of reading from the table (memory),
is the time of reading (writing) from the register,
is the time of adding.
Data encryption can be performed either sequentially or in parallel, depending on the speed required. In the case of sequential encryption, the encryption time is the result of the formula:
where
– time required for encryption. The encryption time can be reduced by performing N operations of calculating the scalar product in parallel.
As a result of NN data encryption, we obtain encrypted data in the form , where – mantissa at the -th output, – order value at the -th output. It is advisable to bring all encrypted data to the highest common order for transmission and such reduction to the greatest common order is performed in three stages:
define the greatest order ;
for each encrypted data calculate the difference between the orders ;
by performing shift of the mantissa to the right by the difference of orders we obtain mantissa of the encrypted data reduced to the greatest common order.
The mantissa of the encrypted data reduced to the largest common order and the largest common order are sent for decryption.
3.3. The main stages of NN cryptographic data decryption
Now the encrypted data presented by mantissa , reduced to the largest common order need to be decrypted. The encrypted data will be decrypted according to the following procedure.
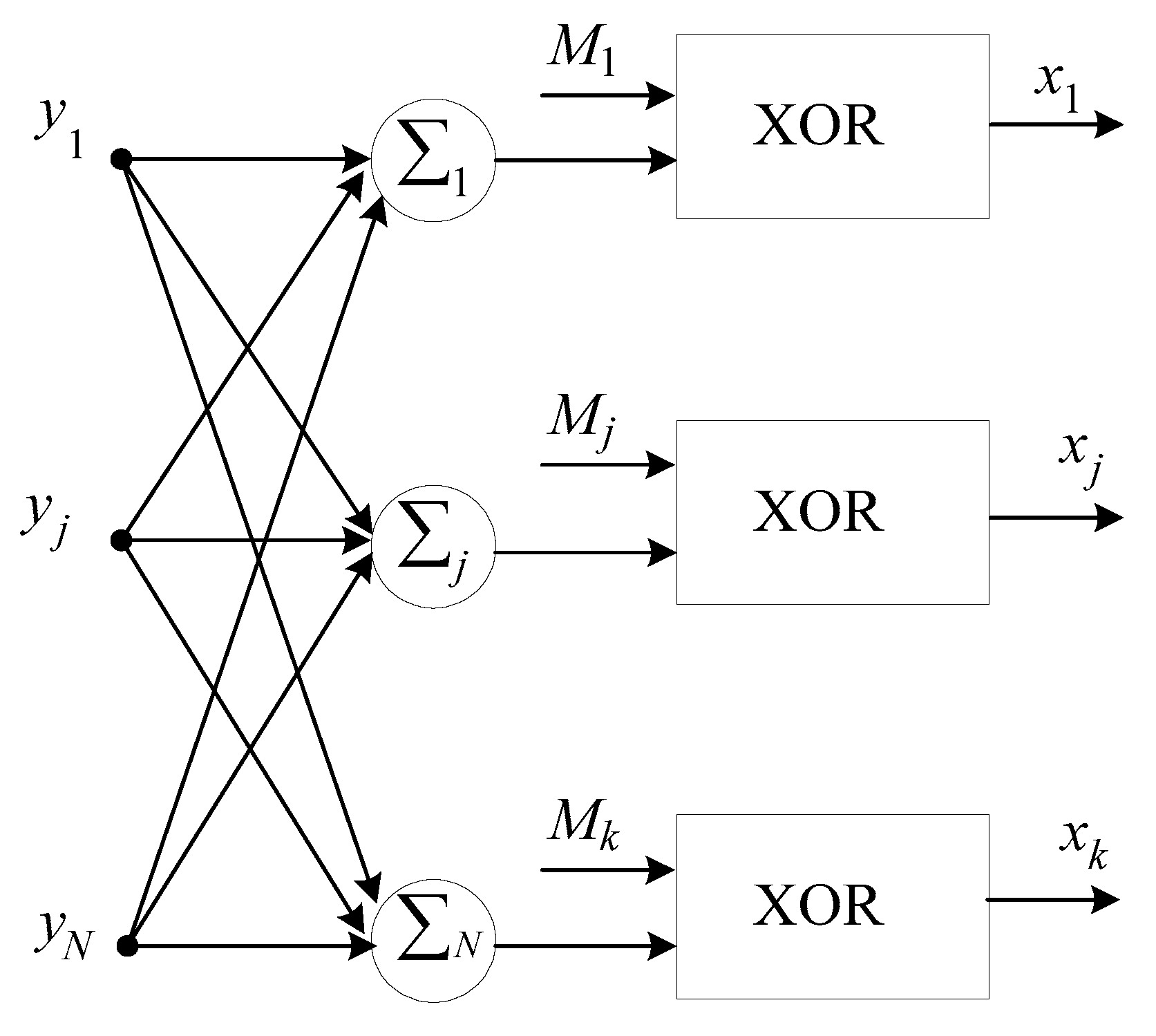
Configuration of the NN architecture for the decryption of encrypted data. The architecture of the NN for the decryption of encrypted data, in terms of the number of neural elements, is the same as the architecture of the NN used for the encryption of data. In this NN, the number of inputs and the number of neurons corresponds to the number of the encrypted mantissa
. The NN architecture used to decrypt encrypted data is presented in
Figure 3.
The bit rate of the inputs during decryption corresponds to the bit rate of the encrypted mantissa . Its value determines the decryption time and to reduce it the lower bits of the mantissa may be discarded, because they will not affect the original message recovery.
Formation of the weight matrix. The matrix of weights for decrypting encrypted data is formed from a matrix of weights for encrypting input data by transposing it:
The basic operation for encryption of input data and decryption of encrypted data is the calculation of the scalar product, which is implemented using a tabular-algorithmic method.
Calculation of the table of macro-partial products for decryption of encrypted data. A specific feature of the scalar product calculation operation used to decrypt encrypted data is that the weights are pre-calculated (constants) and set in floating-point format, while the encrypted data are received in block-floating-point format. The calculation of the scalar product using the tabular-algorithmic method is performed by formula (7). Preparation and calculation of possible variants of macro-partial products is performed as in the previous case under the formula (8).
Amount of encrypted data determines the number of macro-partial products and the size of the table. The largest common order is computed for each table.
NN tabular-algorithmic decryption of encrypted data. The NN decryption is specified by multiplying the
matrix by the encrypted data vector
:
The multiplication of the weights matrix
by the input data vector
is reduced to performing
scalar product calculations:
where
– number of products,
.
Tabular-algorithmic calculation of the mantissa of the scalar product is reduced to reading the macro-partial product
from the table (memory) at the address corresponding to the i-th bit-slice of k input data, and adding it to the previously accumulated sums, according to the formula:
where
,
– bit rate of the encrypted data. The time necessary to calculate the scalar product mantissa is defined under the formula:
where
– time for scalar product calculation,
– time for reading from a table (memory),
– time of reading (writing) from the register,
– time for adding. The result of the calculation of
scalar product consists of a mantissa
and order, which is equal to
.
At the output of the NN (see
Figure 3), we obtain
decrypted data in the following form
, where
is the mantissa at the
-th output,
is the value of the order at the
-th output. To obtain the input data, it is necessary to shift the
-th mantissa
by the value of the order
.
4. The structure of the system for NN cryptographic data protection and transferring in real-time mode
The development of the structure of the system for NN cryptographic data protection and transmission in real-time will be carried out using an integrated approach, which contains:
research and development of theoretical foundations of NN cryptographic data encryption and decryption;
development of new tabular-algorithmic algorithms and structures for NN cryptographic data encryption and decryption;
modern element base, development environment and computer-aided design tools.
A system for NN cryptographic data protection in real-time was developed using the following principles:
changeable composition of the equipment, which foresees the presence of the processor core and replaceable modules, with which the core adapts to the requirements of a particular application;
modularity, which involves the development of system components in the form of functionally complete devices;
pipeline and spatial parallelism in data encryption and decryption;
the openness of the software, which provides opportunities for development and improvement, maximising the use of standard drivers and software;
specialising and adapting hardware and software to the structure of tabular algorithms for encrypting and decrypting data;
the programmability of hardware module architecture through the use of programmable logic integrated circuits.
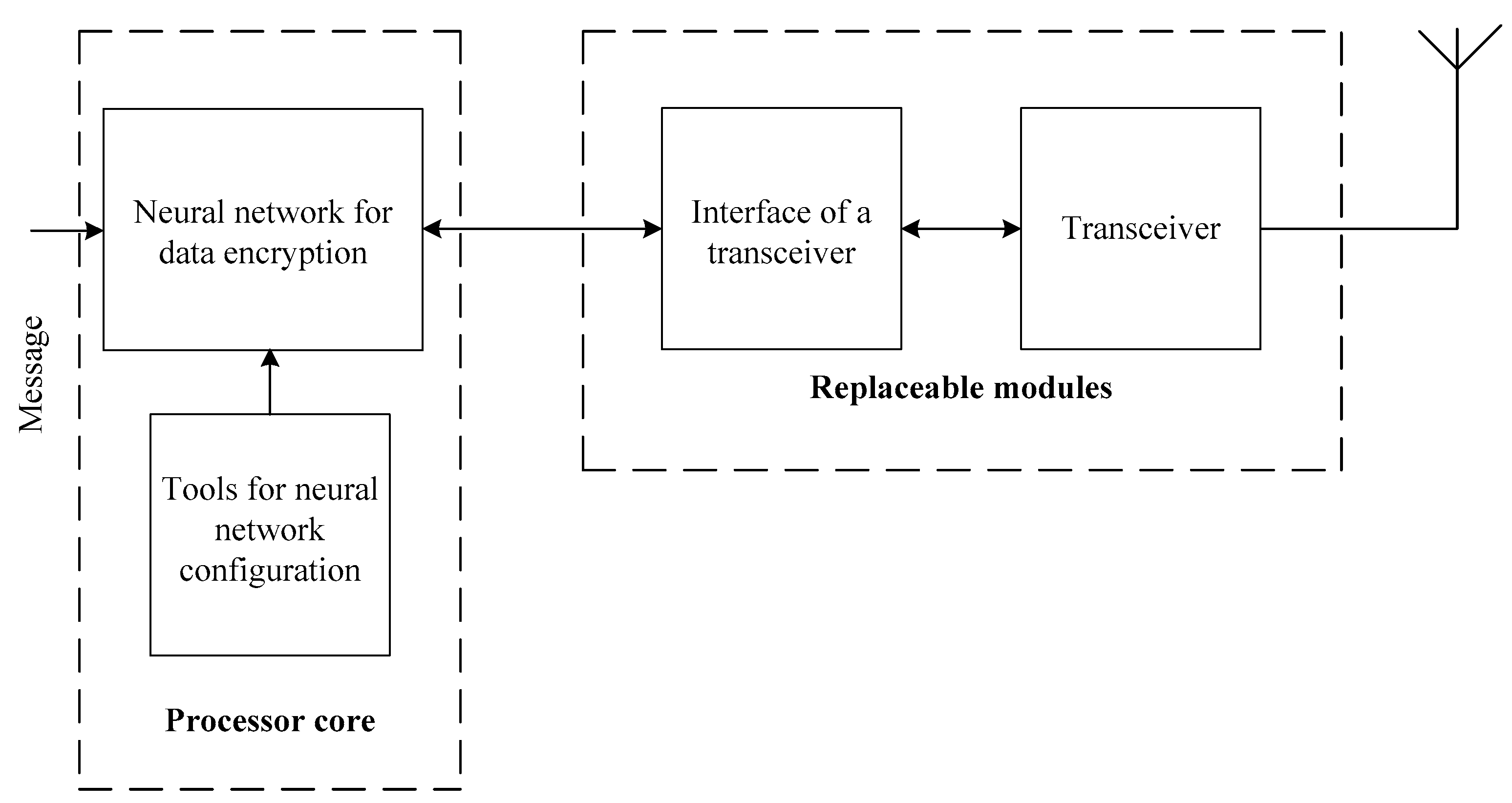
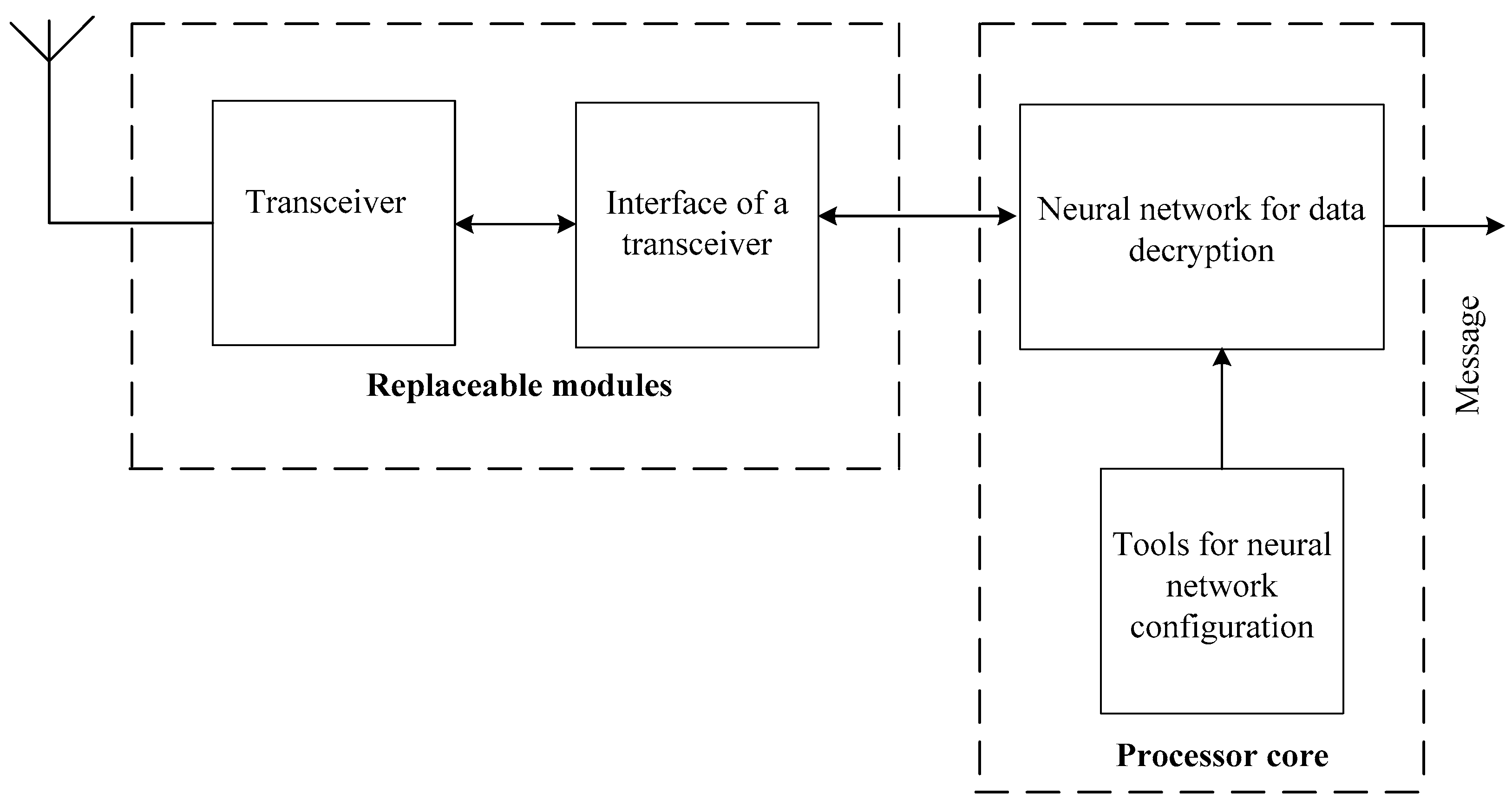
The system of NN cryptographic real-time data protection and transmission consists of a stationary part, which is a remote-control centre, and an UAV onboard part. The structure of the stationary part of the system of NN cryptographic data protection and transmission is shown in
Figure 4.
The processor core of the remote-control center is implemented on the basis of a personal computer. The transceiver is used to transmit encrypted data; it communicates with the processor core through the interface based on a microcontroller.
The UAV onboard part of the system for NN cryptographic real-time data protection and transmission is implemented on the processor core, which is supplemented by dedicated hardware and software. The processor core of the UAV onboard part of the system is designed on a microcomputer. The structure of the onboard part of the system of NN cryptographic data protection and receiving is depicted in
Figure 5.
The effective implementation of NN encryption-decryption and encoding-decoding algorithms in real time is achieved by combining universal and customized software and hardware. The use of modern elements (microcomputer, microcontroller, FPGA) in the development of the UAV onboard part ensures the accomplishment of the requirements for weight, dimensions and energy consumption.
The effectiveness of the system for NN cryptographic real-time data protection and transmission is directly associated with the choice of both hardware and software implementation.
5. Development of the components of the onboard system for NN cryptographic data encryption and decryption
In general, the problem of developing onboard systems for NN cryptographic encryption-decryption of data can be formulated as follows:
to develop an algorithm for the onboard system of NN encryption-decryption of data and present it in the form of a specified flow graph;
to design the structure of the onboard system for NN data encryption-decryption with the maximum efficiency of equipment use, taking into account all the limitations and providing real-time data processing;
to determine the main characteristics of neural elements and carry out their synthesis;
to choose exchange methods, determine the necessary connections and develop algorithms for exchange between system components;
to determine the order of implementation in time of NN data encryption-decryption processes and develop algorithms for their management.
Components of the onboard system of NN cryptographic data encryption and decryption should provide the implementation of the selected NN, the ability to change masks, calculate matrices of weights
and tables of macro-partial products
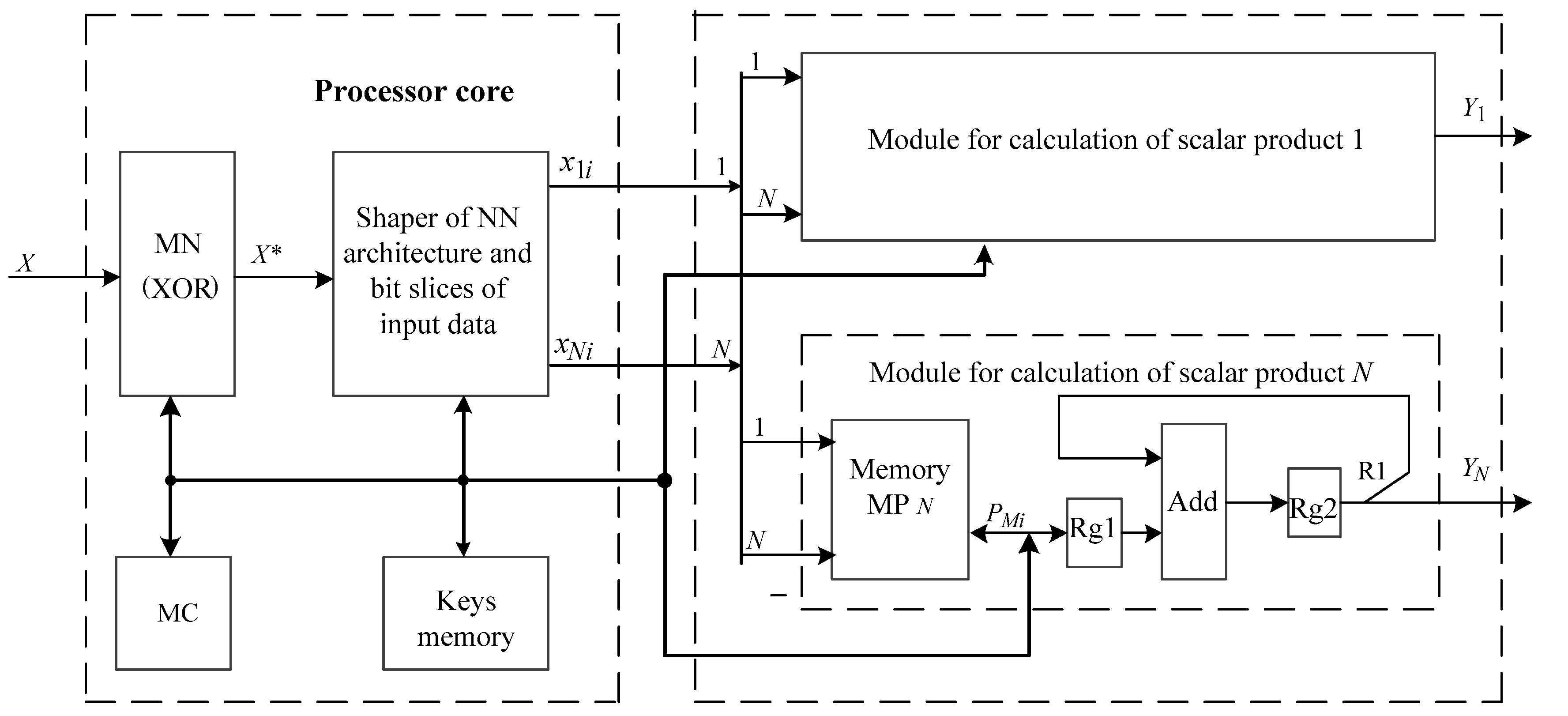
for possible NN options. To effectively implement the components of the onboard system of NN cryptographic encryption-decryption of data, it is proposed to use hardware-software implementation of the algorithms based on a microcontroller supplemented by specialized hardware. The structure of the component of NN cryptographic data encryption, which meets such requirements, is presented in
Figure 6, where MC – microcontroller, MN – mask node, MP – macro-partial product, Rg – register, Add – adder.
The developed component of NN cryptographic data encryption has a variable composition of equipment, which is based on the core of the system and a set of modules for calculating the scalar product. The system core is constant for all applications and consists of microcontroller MC, mask node MN, keys memory and module of the shaper of the NN architecture and bit slices of input data. The scalar product calculation modules implement the basic operation of the tabular-algorithmic method of scalar product calculation under the formula:
where
.
The number of modules for calculating the scalar product depending on the required speed is determined by the following formula:
where
is the number of neuro-like elements,
. The system of NN cryptographic data encryption reaches its highest speed when the number of computational modules of the scalar product corresponds to the number of neural elements
. To ensure real-time data encryption, it is proposed to implement the scalar product calculation modules, mask node module (MN), and module of the shaper of NN architecture and bit slices of the input data in the form of specialized hardware.
The NN cryptographic data encryption component works as follows. Before encrypting the data, the MC configures the NN architecture (determines the number of neural elements , the number of inputs and their bit-size ). For the selected NN architecture matrix of weights and tables of macro-partial products are calculated by MC, and then they are written in the memory of MP. In addition, the masks selected from the keys’ memory are stored in the MN node. The message Х to be encrypted comes to input of MN in fixed-point format, here it is masked. The masked message Х* from the output of MN comes to input of the module of the shaper of NN architecture and bit slices, where it is divided into N groups with m bit rate and bit slices are formed . It should be noted that forming of bit slices begins with lower bits. The formed bit slices are the addresses for reading macro-partial products from the MP memory. The read macro-partial product is written to the Rg1 register. The adder (Add) performs a summation of macro-partial products as per formula (20). The number of cycles required to calculate the scalar product is determined by the bit-size of input . Control of the encryption process in the onboard system of NN cryptographic data encryption is performed by MC.
6. Results and Discussion
For experimental verification of the proposed NN technology for cryptographic protection of data transmission system the simulation was performed. Nowadays, the hardware description languages such as VHDL, VHDL-AMS, Verilog, Verilog-AMS are widely used for creating behavioral descriptions and models of digital, analog and mixed-signal devices and systems [
44,
45].
The design of specialized on-board hardware systems for NN cryptographic data encryption was performed in the VHDL hardware programming language in the Quartus II ver. 13.1 development environment using its libraries. The Quartus II development environment supports the entire process of designing specialized hardware from user input to FPGA programming, debugging of both the chip itself and the tools as a whole.
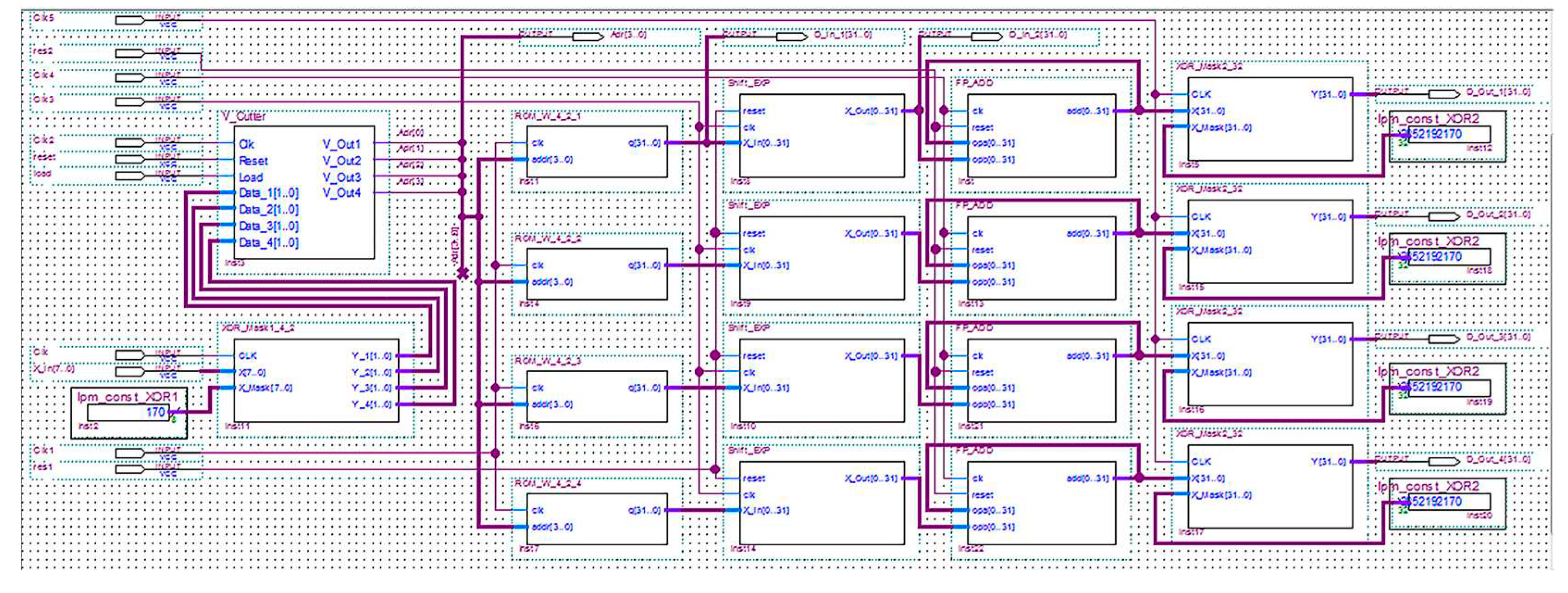
A schematic diagram of the specialized hardware components of NN cryptographic data encryption is shown in
Figure 7. The inputs of module XOR_Mask1_4_2: X[7..0] – are the input data; Clk – input sync for input data download; X_Mask[7..0] – 8-bit mask. At the output of this block N vectors with bit length m are formed. Synchronization is implemented on the leading edge of Clk pulses.
Block V_Cutter with input vectors of bit length consists of N registers of parallel-serial type and forms vertical bit slices. Input data: Data_1 [n-1..0],…, Data_N [n-1..0] – input vectors with bit length ; Clk – pulses of synchronization of forming vertical bit slices; Reset – the signal of the initial reset in the "0" output of the registers R_Par_Ser; Load – the signal to allow data to be loaded into the R_Par_Ser registers. Outputs: V_Out1,…, V_OutN – vertical bit slice. The formation of vertical sections begins with the lower bit.
The weights of the NN with inputs with a bit length of are stored in the FPGA ROM in the form of 4 tables. Each of them consists of 16 words with a bit length of 32 bits. Reading data from these tables is performed using blocks ROM_W_4_2_1,…, ROM_W_4_2_4.
Inputs of these blocks: addr [3..0] – the address of the cell of the table from which the data will be read; clk – synchronization pulses for reading data from the table. Synchronization is implemented on the leading edge of the pulses clk. Output: q [31..0] – data read from the cell with the input address.
The data read from the tables is transmitted to the input blocks Shift_EXP, which perform their multiplication by , where . Upon receipt of this block of data corresponding to the zero digit, the bit counter is reset. Synchronization of this block is carried out by means of clock pulses Clk. At the output X_Out [0..31] we get the input data multiplied by .
From the output of the Shift_EXP blocks, the data are sent to one of the inputs of the adders FP_ADD. The other input of the adders is connected to their output. Adder input signals: clk – synchronization pulses; reset – signal to reset the input data opa when implementing the adder with the battery; opa[0..31], opb[0..31] – terms. On the leading edge of the first pulse clk the adders are loaded into the adder, and on the leading edge of the second pulse the received sum is displayed. Adder output: the sum add[0..31].
From the output of the adders, FP_ADD data is fed to the input of the block XOR_Mask2_32, which performs the overlay of the 32-bit mask. Inputs of the block XOR_Mask2_32: X [31..0] – encrypted output data; Clk – synchronization of input data download; X_Mask [31..0] – 32-bit mask. Block output: vector Y [31..0]. Synchronization is implemented on the leading edge of Clk pulses. The encrypted data are obtained at the outputs D_Out_1, D_Out_2, D_Out_3, D_Out_4.
The timing diagram of the specialized hardware of NN cryptographic data encryption is presented in
Figure 8.
The time diagram (
Figure 8) shows an example of NN cryptographic encryption of eight-bit data, which are received in binary code at inputs X_In X[7..0]. An 8-bit mask 170=0xAA is received at the X_Mask[7..0] inputs, which is set using the lpm_const_XOR1 component (
Figure 7). It is used to mask input data using the XOR operation. For input X_In_1 – 01001100 XOR 10101010 = 11100110; for input X_In_2 – 01010100 XOR 10101010 = 11111110. For the first number 01001100 at the outputs Y_1[1…0], Y_2[1…0], Y_3[1…0], Y_4[1…0] of the XOR_Mask1_4_2 block, we get 11, 10, 01 and 10 respectively. When encrypting the first vector of input data at the Adr outputs, we get 4-bit slices starting from the lowest bits, which are sent to the address inputs of ROM_W4_2_1, ROM_W4_2_2, ROM_W4_2_3 and ROM_W4_2_4 blocks. These lookup tables contain pre-calculated neuroelements’ weights.
For lower bits 1010 from ROM_W4_2_1 block the 32-bit macro-partial product BEEBAE00 is read, which is fed to the input D_In_1 and to the input of the first block Shift_EXP, which performs the multiplication operation by shifting by 2j, where j =0, …, n-1. At the output of the first block Shift_EXP and at the input D_In_2 we get BEEBAE00. For the next 1101 bits, the 32-bit macro-partial product 3ED81E40 is read from ROM_W4_2_1 block. At the output of the first block Shift_EXP and at the input D_In_2 we get the macro-partial product multiplied by two, which is equal to 3F581E40.
In the first adder FP_ADD, we sum up the data from the outputs of the first block Shift_EXP and get the sum (its value is not displayed on the time charts), which is sent to the first block XOR_Mask2_32. In the first block XOR_Mask2_32 the XOR operation is performed with the sum in IEEE 754 format and mask 2852192170=0xAA00FFAA. At the D_Out_1 output we get the encrypted value 0x94C4712A.
For input data with a dimension of 1 byte X_In={01001100}, we get an encrypted value with a dimension of 16 bytes D_Out_1=0x94C4712A; D_Out_2=0x153912B0; D_Out_3=0x6A69F209; D_Out_4=0x6A01F74C.
The implementation of the specialized hardware for NN cryptographic data encryption based on the FPGA EP3C16F484C6 Cyclone III family [
46] requires 3053 logic elements and 745 registers. Approximately 160 nanoseconds are required to encrypt one input vector.
For comparison with the above described hardware implementation on FPGA, the same components were implemented exclusively as the software. The components were created in the C language using the Code::Blocks development environment version 20.03. The execution time of a similar NN cryptographic data encryption procedure using a NanoPi Duo microcomputer based on the Allwinner Cortex-A7 H2+ SoC was about 20 ms. The results of the comparison allow us to see a significant gain in time for the implementation of NN cryptographic data encryption and decryption.
The authors understand the importance of the issue of cryptographic stability. But this is beyond the scope of this study. The security of the neural network cryptographic approach mainly depends on the length of the key, which is determined by the masking codes, the neural network architecture, and the floating-point weighting matrix, as well as on the frequency of its change. The length of the key depends on the number of neural elements N, which determine the size of the matrix of weighting coefficients.
The operation of onboard communication cryptographic systems for UAV can be exposed to an attack on the secret key by breaking which it is possible to gain access to protected data. However, the time and resources required to crack the key and decrypt the encrypted data depend on the complexity of the algorithm for calculating the floating-point weighting matrix and the decryption algorithm. The number of operations required to calculate the matrix of weighting coefficients is approximately equal to N2n arithmetic operations (where n is the data bit width), and the number of operations required to decrypt encrypted data approximately equals N2 operations of multiplying floating-point numbers and N2 operations of adding floating-point numbers. Therefore, the computational complexity of the proposed NN approach is high. Obviously, the evaluation of security analysis could be performed in further studies.
7. Conclusions
The approach to the implementation of neural network for cryptographic protection of data transmission at UAV onboard communication systems has been presented in this work. This paper describes the UAV onboard system for NN cryptographic data protection in real-time using an integrated approach based on the following principles: variable equipment composition; modularity; conveyorization and spatial parallelism; software openness; suitability for hardware implementation on FPGA.
In the proposed implementation the keys are defined by masking codes, NN architecture and weigh matrix. It makes possible the effective hardware-software implementation with good technical and operational characteristics.
The tabular-algorithmic scalar product calculation method has been improved. This method is suitable for fast scalar product calculation of input data in fixed-point or floating-point format. It does this by finding the largest common order of weights and building tables of macro partial products for them.
Components of NN cryptographic data encryption/decryption have been designed on the basis of the processor core supplemented by the specialized scalar product calculation modules.
The specialized hardware for NN cryptographic data encryption was developed in the VHDL equipment programming language in the Quartus II environment and implemented using family Cyclone III FPGA EP3C16F484C6.
Author Contributions
Conceptualization, I.T. and V.T.; methodology, I.T., Y.O. and Y.L.; software, Y.L. and Y.O.; validation, Y.L., Y.O. and I.K.; formal analysis, I.T. and V.T.; investigation, A.L. and A.H.; resources, A.L. and I.K.; data curation, Y.L. and I.K.; writing—original draft preparation, I.T., I.K. and Y.O.; writing—review and editing, I.K., A.H. and A.L.; visualization, I.K. and Y.O.; supervision, V.T. and A.L.; project administration, I.T. and V.T. All authors have read and agreed to the published version of the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Han, B.; Qin, D.; Zheng, P.; Ma, L.; Teklu, M.B. Modeling and performance optimization of unmanned aerial vehicle channels in urban emergency management. ISPRS Int. J. Geo-Inf 2021, 10, 478. [Google Scholar] [CrossRef]
- Śledź, S.; Ewertowski, M.W.; Piekarczyk, J. Applications of unmanned aerial vehicle (UAV) surveys and Structure from Motion photogrammetry in glacial and periglacial geomorphology. Geomorphology 2021, 378, 107620. [Google Scholar] [CrossRef]
- Zhang, C.; Zou, W.; Ma, L.; Wang, Z. Biologically inspired jumping robots: A comprehensive review. Robotics Auton. Syst. 2020, 124, 103362. [Google Scholar] [CrossRef]
- Li, D.; Ma, G.; He, W.; Ge, S.S.; Lee, T.H. Cooperative Circumnavigation Control of Networked Microsatellites. IEEE Transactions on Cybernetics 2020, 50, 4550–4555. [Google Scholar] [CrossRef]
- Boreiko, O.; Teslyuk, V.; Zelinskyy, A.; Berezsky, O. Development of models and means of the server part of the system for passenger traffic registration of public transport in the “smart” city. EEJET 2017, 1, 40–47. [Google Scholar] [CrossRef]
- Kim, K.; Kang, Y. Drone security module for UAV data encryption. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea (South), 2020; pp. 1672–1674. [Google Scholar] [CrossRef]
- Samanth, S.; K V, P.; Balachandra, M. Security in Internet of Drones: A Comprehensive Review. Cogent Engineering 2022, 9, 2029080. [Google Scholar] [CrossRef]
- Kong, P.-Y. A survey of cyberattack countermeasures for unmanned aerial vehicles. IEEE Access 2021, 9, 148244–148263. [Google Scholar] [CrossRef]
- Shafique, A.; Mehmood, A.; Elhadef, M.; Khan, K.H. A lightweight noise-tolerant encryption scheme for secure communication: An unmanned aerial vehicle application. PLoS ONE 2022, 17, e0273661. [Google Scholar] [CrossRef]
- Verma, A.; Ranga, V. Security of RPL based 6LoWPAN Networks in the Internet of Things: A Review. IEEE Sensors J. 2020, 20, 5666–5690. [Google Scholar] [CrossRef]
- Srivastava, S.; Bhatia, A. On the Learning Capabilities of Recurrent Neural Networks: A Cryptographic Perspective. In Proceedings of the 2018 IEEE International Conference on Big Knowledge (ICBK), Singapore; 2018; pp. 162–167. [Google Scholar] [CrossRef]
- Zhu, Y.; Vargas, D.V.; Sakurai, K. Neural Cryptography Based on the Topology Evolving Neural Networks. In Proceedings of the 2018 Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan; 2018; pp. 472–478. [Google Scholar] [CrossRef]
- Duan, X.; Han, Y.; Wang, C.; Ni, H. Optimization of Encrypted Communication Length Based on Generative Adversarial Network. In Proceedings of the 2021 IEEE 4th International Conference on Big Data and Artificial Intelligence (BDAI), Qingdao, China; 2021; pp. 165–170. [Google Scholar] [CrossRef]
- Grodzki, W.; Łukaszewicz, A. Design and manufacture of unmanned aerial vehicles (UAV) wing structure using composite materials. Materialwissenschaft und Werkstofftechnik 2015, 46, 269–278. [Google Scholar] [CrossRef]
- Łukaszewicz, A.; Szafran, K.; Jóźwik, J. CAx techniques used in UAV design process. In Proceedings of the 2020 IEEE 7th International Workshop on Metrology for AeroSpace (MetroAeroSpace); 2020; pp. 95–98. [Google Scholar] [CrossRef]
- Łukaszewicz, A.; Skorulski, G.; Szczebiot, R. The main aspects of training in the field of computer aided techniques (CAx) in mechanical engineering. In Proceedings of the 17th International Scientific Conference on Engineering for Rural Development, Jelgava, Latvia, 23-25 May 2018; pp. 865–870. [Google Scholar] [CrossRef]
- Łukaszewicz, A.; Miatluk, K. Reverse Engineering Approach for Object with Free-Form Surfaces Using Standard Surface-Solid Parametric CAD System. Solid State Phenomena 2009, 147–149, 706–711. [Google Scholar] [CrossRef]
- Miatliuk, K.; Łukaszewicz, A.; Siemieniako, F. Coordination method in design of forming operations of hierarchical solid objects. In Proceedings of the 2008 International Conference on Control, Automation and Systems, ICCAS 2008; pp. 2724–2727. [CrossRef]
- Puchalski, R.; Giernacki, W. UAV Fault Detection Methods, State-of-the-Art. Drones 2022, 6, 330. [Google Scholar] [CrossRef]
- Zietkiewicz, J.; Kozierski, P.; Giernacki, W. Particle swarm optimisation in nonlinear model predictive control; comprehensive simulation study for two selected problems. International Journal of Control 2021, 94, 2623–2639. [Google Scholar] [CrossRef]
- Kownacki, C.; Ambroziak, L. Adaptation Mechanism of Asymmetrical Potential Field Improving Precision of Position Tracking in the Case of Nonholonomic UAVs. Robotica 2019, 37, 1823–1834. [Google Scholar] [CrossRef]
- Kownacki, C.; Ambroziak, L.; Ciężkowski, M.; Wolniakowski, A.; Romaniuk, S.; Bożko, A.; Ołdziej, D. Precision Landing Tests of Tethered Multicopter and VTOL UAV on Moving Landing Pad on a Lake. Sensors 2023, 23, 2016. [Google Scholar] [CrossRef] [PubMed]
- Basri, E.I.; Sultan, M.T.H.; Basri, A.A.; Mustapha, F.; Ahmad, K.A. Consideration of Lamination Structural Analysis in a Multi-Layered Composite and Failure Analysis on Wing Design Application. Materials 2021, 14, 3705. [Google Scholar] [CrossRef] [PubMed]
- Al-Haddad, L.A.; Jaber, A.A. An Intelligent Fault Diagnosis Approach for Multirotor UAVs Based on Deep Neural Network of Multi-Resolution Transform Features. Drones 2023, 7, 82. [Google Scholar] [CrossRef]
- Yang, J.; Gu, H.; Hu, C.; Zhang, X.; Gui, G.; Gacanin, H. Deep Complex-Valued Convolutional Neural Network for Drone Recognition Based on RF Fingerprinting. Drones 2022, 6, 374. [Google Scholar] [CrossRef]
- Duan, X.; Han, Y.; Wang, C.; Ni, H. Optimization of Encrypted Communication Model Based on Generative Adversarial Network. In Proceedings of the 2022 International Conference on Blockchain Technology and Information Security (ICBCTIS), Huaihua City, China; 2022; pp. 20–24. [Google Scholar] [CrossRef]
- Karakaya, B.; Celik, V.; Gulten, A. Realization of Delayed Cellular Neural Network model ON FPGA. In Proceedings of the 2018 Electric Electronics, Computer Science, Biomedical Engineerings’ Meeting (EBBT), Istanbul, Turkey, 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Volna, E.; Kotyrba, M.; Kocian, V.; Janosek, M. Cryptography Based On Neural Network. In Proceedings of the 26th European Conference on Modeling and Simulation (ECMS 2012), Koblenz, Germany, 29 May–1 June 2012; Troitzsch, K.G., Moehring, M., Lotzmann, U., Eds.; European Council for Modeling and Simulation; pp. 386–391. [Google Scholar] [CrossRef]
- Shihab, K. A backpropagation neural network for computer network security. Journal of Computer Science 2006, 2, 710–715. [Google Scholar] [CrossRef]
- Sagar, V.; Kumar, K. A symmetric key cryptographic algorithm using counter propagation network (CPN). In Proceedings of the 2014 ACM International Conference on Information and Communication Technology for Competitive Strategies, (ICTCS’14), Udaipur Rajasthan, India, 14-16 November 2014. [Google Scholar] [CrossRef]
- Arvandi, M.; Wu, S.; Sadeghian, A.; Melek, W.W.; Woungang, I. Symmetric cipher design using recurrent neural networks. In Proceedings of the IEEE International Joint Conference on Neural Networks; 2006; pp. 2039–2046. [Google Scholar] [CrossRef]
- Tsmots, I.; Tsymbal, Y.; Khavalko, V.; Skorokhoda, O.; Teslyuk, T. Neural-like means for data streams encryption and decryption in real time. In Proceedings of the 2018 IEEE Second International Conference on Data Stream Mining & Processing (DSMP), Lviv, Ukraine, 21-25 August 2018; pp. 438–443. [Google Scholar] [CrossRef]
- Scholz, M.; Fraunholz, M.; Selbig, J. Nonlinear principal component analysis: Neural network models and applications. In Principal Manifolds for Data Visualization and Dimension Reduction; Lecture Notes in Computational Science and Engineering; Gorban, A.N., Kégl, B., Wunsch, D.C., Zinovyev, A.Y., Eds.; Springer: Berlin, Heidelberg, 2008; Volume 58. [Google Scholar] [CrossRef]
- Rabyk, V.; Tsmots, I.; Lyubun, Z.; Skorokhoda, O. Method and Means of Symmetric Real-time Neural Network Data Encryption. In Proceedings of the 2020 IEEE 15th International Scientific and Technical Conference on Computer Sciences and Information Technologies (CSIT 2020); 2020; Volume 1, pp. 47–50. [Google Scholar] [CrossRef]
- Chang, A.X.M.; Martini, B.; Culurciello, E. Recurrent Neural Networks Hardware Implementation on FPGA. arXiv 2015. [Google Scholar] [CrossRef]
- Nurvitadhi, E.; et al. Can FPGAs beat GPUs in accelerating next-generation deep neural networks? In Proceedings of the 2017 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays. Monterey, California, USA, 22-24 February 2017; pp. 5–14. [Google Scholar] [CrossRef]
- Misra, J.; Saha, I. Artificial neural networks in hardware: A survey of two decades of progress. Neurocomputing 2010, 74, 239–255. [Google Scholar] [CrossRef]
- Guo, K.; et al. From model to FPGA: Software-hardware co-design for efficient neural network acceleration. In Proceedings of the 2016 IEEE Hot Chips 28 Symposium (HCS); 2016; pp. 1–27. [Google Scholar] [CrossRef]
- Ovtcharov, K.; et al. Accelerating Deep Convolutional Neural Networks Using Specialized Hardware. Microsoft Research Whitepaper. 2016. Available online: https://www.microsoft.com/en-us/research/wp-content/uploads/2016/02/CNN20Whitepaper.pdf (accessed on 29 April 2022).
- Wang, Y.; Xu, J.; Han, Y.; Li, H.; Li, X. DeepBurning: Automatic generation of FPGA-based learning accelerators for the neural network family. In Proceedings of the 53rd Annual Design Automation Conference (DAC’16); Association for Computing Machinery: New York, NY, USA Article 110. ; pp. 1–6. [CrossRef]
- Nurvitadhi, E.; Sheffield, D.; Sim, J.; Mishra, A.; Venkatesh, G.; Marr, D. Accelerating Binarized Neural Networks: Comparison of FPGA, CPU, GPU, and ASIC. In Proceedings of the 2016 International Conference on Field-Programmable Technology (FPT), 2016; pp. 77–84. [CrossRef]
- Yayik, A.; Kutlu, Y. Neural Network Based Cryptography. Neural Network Worldc 2014, 24, 177–192. [Google Scholar] [CrossRef]
- Govindu, G.; Zhuo, L.; Choi, S.; Prasanna, V. Analysis of high-performance floating-point arithmetic on FPGAs. In Proceedings of the 18th International Parallel and Distributed Processing Symposium (IPDPS 2004), Santa Fe, New Mexico, USA, 26-30 April 2004; Volume 149. [Google Scholar] [CrossRef]
- Khalil, K.; Dey, B.; Abdelrehim, M.; Kumar, A.; Bayoumi, M. An Efficient Reconfigurable Neural Network on Chip. In Proceedings of the 2021 28th IEEE International Conference on Electronics, Circuits, and Systems (ICECS), Dubai, United Arab Emirates, 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Dumesnil, E.; Beaulieu, P.-O.; Boukadoum, M. Fully parallel FPGA Implementation of an Artificial Neural Network Tuned by Genetic Algorithm. In Proceedings of the 2018 16th IEEE International New Circuits and Systems Conference (NEWCAS), Montreal, QC, Canada; 2018; pp. 365–369. [Google Scholar] [CrossRef]
- Cyclone III Device Handbook. Available online: https://www.intel.com/content/www/us/en/content-details/655197/cyclone-iii-device-handbook-volume-2-chapter-1-cyclone-iii-device-datasheet.html (accessed on 29 April 2022).
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).