1. Introduction
As many illicit contents providers supply copyright-infringing IPTV content for free, they often rely on intrusive advertising, tracking, scams, and malware to make a profit. Illicit content providers also get paid by malware authors to infect their own illicit IPTV websites or software, which are frequently malware families that can generate indirect income with ease, such as cryptocurrency-mining malware [
1,
2].One study found that dozens of illicit IPTV websites contained “download now” adverts, redirecting users to landing pages with instructions for downloading malicious browser extensions [
3]. Another study found that for the Australian population, 99% of advertisements on illicit content-sharing websites were categorised as high risk, with 46% of these advertisements classified as malicious [
4]. Overall, this implies that using copyright-infringing IPTV technologies pose a significant risk to users’ devices, as illicit content providers cannot be trusted, and may use malware to increase their revenue.
Internet Protocol Television (IPTV) is a service that provides TV programmes and on-demand video content over the TCP/IP internet protocols[
5]. Most legal IPTV services supply video content as part of a TV licence, one-time purchase, or paid subscription, whereas free alternatives usually incorporate advertisements. While IPTV services each have many different genres of video content, users often need to subscribe to multiple services to view the specific films and TV programmes they want to watch. Due to the limited effort, convenience, and monetary costs of these legal IPTV services, many users instead choose to use copyright-infringing IPTV technologies to view video content illegally. A report by Sandvine estimates that “roughly 6% of all households in North America currently have a Kodi device configured to access unlicensed files and streams” [
6]. This implies that many IPTV users are willing to risk compromising their home network by installing potentially infected software to access unlicensed video content, in addition to possible legal action from copyright infringement.
One of the reasons why infringing IPTV users are willing to risk legal action or exposure to malware and scams is that illegal IPTV services are usually either free, or have low monetary costs, in comparison to legal IPTV services[
7]. Additionally, software for accessing infringing content can be installed on physical set-top boxes, which appeals to users due to its ease of use, facilitating a “wide range of illicit content being available in one place, without the need for multiple subscriptions” [
8].Because of the lower perceived costs, these users are willing to accept the risks of trusting and potentially disclosing credit card or personal information to illicit content providers who cannot be trusted and could be frauds.
The addition of the malware threat to this criminal environment adds another dimension to the criminal activities, creating a poly-criminal environment. This was observed in the technical report on the online investigation of IP crime [
9], which found that in many cases the financial gain in one criminal activity supports the other, thus creating a vicious many-folded criminal ecosystem. Another importance in illuminating the malware ecosystem behind illegal IPTV is that it will challenge the judicial process behind the illegal IPTV ecosystem, by stressing the fact that the severity of crime increases, once the malware is added into the mix.
Our research found that currently, there is insufficient forensic investigation studies and actionable intelligence collections available, to effectively identify the risks and threats of malware from using illegal IPTV technologies [
10]. This is in part due to an inadequate number of studies and malware analyses that have assessed the likelihood and severity of malware threats in the illegal IPTV ecosystem. Moreover, malware threats are constantly changing, necessitating malware analyses to be completed consistently on an ongoing basis, to provide timely threat intelligence about the risks of infringing IPTV technologies [
11,
12,
13,
14].Although there are a small number of indicators of compromise (IOCs) relating to illegal IPTV technologies that exist, such as the AlienVault Open Threat Exchange intelligence platforms, our research shows that there is minimal threat intelligence about the main types of malware used, its severity, and the prominent Tactics, Techniques, and Procedures (TTPs) used by threat actors to exploit the devices of infringing IPTV technology users.
However, in other areas of research the prevalent malware families, their severity, and the likelihood of infection from using copyright-infringing technologies has been identified. For example, Bosco and Shalaginov, while not focusing specifically on infringing IPTV technology, identified the malware families found in technologies, providing copyright-infringing digital content and actionable threat intelligence into the main malware threats from digital content piracy technologies, although these may be less relevant for threat intelligence researchers in the future, due to the ever-changing nature of malware threats [
15,
16].
For example, a security report by Ponemon Institute found that fileless malware[
17,
18,
19] attacks have been steadily increasing over time, while the number of zero-day attacks nearly doubled between 2019 to 2020 [
20].Additionally, Bosco and Shalaginov found that when searching for popular films in a web browser to identify illicit IPTV websites, 20% of websites had been removed from the search results and replaced with new sites between two rounds of analysis, with 8% of the websites classified as malicious by VirusTotal [
15]. These results suggest that both malware threats, and the copyright-infringing IPTV ecosystem, are changing continuously. This, may be partially due to legal “whack-a-mole” enforcement that removes illicit websites, coupled with the development of zero-day malware to exploit new vulnerabilities. Therefore, to address this issue, in this paper, we present a framework for analysing malware threats in illegal IPTV technologies, the illegal IPTV Technologies Malware Analysis Framework (IITMAF).
IITMAF has been designed to identify new threats and risks and encourage ongoing evaluation of these. The framework consists of a methodology for securely detecting, collecting, and analysing malware from infringing IPTV technology, in addition to identifying and assessing the risks of using these technologies. Moreover, the framework provides a software solution for automating the collection and analysis of malware found in illegal IPTV websites and software, with the focus of the automated software solution being the provision of actionable information.
Actionable information should be relevant, timely, accurate, complete, and ingestible [
21]. IITMAF aims to meet these actionable information requirements for malware in infringing IPTV technologies by providing a solution that can quickly analyse identified URLs for illicit IPTV websites, app stores, and software files, using static and dynamic analysis techniques, and consecutively generate a comprehensive report in a structured format. In addition to identification of the malicious URLS and malware analysis capabilities, the framework has also shown to be useful for generating cyber threat intelligence, TTPs and similar attack patterns as can be found in the evaluation section. The rest of the paper is structured as follows:
Section 2 provides a comprehensive review of the relevant literature of cyber threat intelligence in the IPTV ecosystem and makes the necessary definitions.
Section 3 outlines the high-level methodology, including the data collection and data flow diagram of the framework.
Section 4 presents and discusses the implementation, the test case and evaluation. Section 5 critically evaluates the main findings and their implications and
Section 6 concludes the paper while presenting the limitations.
2. Background
Illegal IPTV technologies consist of physical set-top boxes, websites, or software in the form of standalone applications or illicit add-ons to legal software [
7].Supplying these technologies for use without paying for the content they transmit is a crime. One study identified trojan, adware, spyware, and backdoor malware from content theft websites, [
15], implying that illicit IPTV providers may include malware in their websites and software, or advertise malware disguised as a desirable application, to increase their profits. Thus, as illicit IPTV providers are already committing a crime, it appears that, in addition, many of these providers elect to also distribute malware as part of the delivery to supplement their income. The following sections will define the illegal IPTV technologies used and their risks, in addition to outlining relevant malware collection and analysis techniques for these technologies.
Illicit Streaming Devices (ISDs) are physical boxes or USB sticks that connect to a TV to provide free television and film content that you would usually pay for to view[
8]. Many physical IPTV boxes, such as Kodi boxes, are legal, but third-party software can be installed to illegally stream IPTV content for free. Conversely, other physical IPTV boxes, often described as “fully loaded” or “jailbroken”, already include software for facilitating illegal IPTV streaming. Because ISD providers are already willing to commit copyright infringement, they are more likely to commit further breaches of law, as it could increase their profits. Therefore, ISD providers cannot be trusted, as they could supply users with ISDs infected with malware.
Overall, ISD providers are unlikely to infect the products they sell with high-impact malware when they are already making a profit from selling ISDs. However, potential users would likely purchase an ISD from a website, which itself could be a scam, designed to try and get individuals to disclose their credit card details. Moreover, fake websites that advertise illegal IPTV boxes, could also distribute fileless malware when visited by users. Therefore, there are other risks to purchasing and using ISDs, as the providers cannot be trusted and could be attempting to scam people.
Websites for streaming IPTV content illegally are available over the surface web, with examples including PutLocker and FlixTor. IPTV content is usually freely available on these websites, which is attractive to users who aren’t willing to pay for a streaming service or risk purchasing an ISD. However, as the illicit content provided is often free, IPTV websites are untrustworthy as they are more likely to rely on trackers, scams, and malware to gain a profitable income.
Illegal IPTV websites have different strategies for providing infringing IPTV content. Many sites host and potentially live-stream IPTV content on their website, although these websites are more likely to be detected by anti-piracy organisations. To reduce the risk of legal action, some websites collect and contain lists of hyperlinks to websites for accessing IPTV content illegally, known as “link aggregators” [
9].Link aggregators can also be found on legitimate websites, such as GitHub repositories and forum posts.
Once more, using illegal IPTV websites or aggregators is risky, as they cannot be trusted. In comparison to ISDs, IPTV websites are potentially riskier, because they receive no income for providing free IPTV content, whereas ISDs are purchased. Hence, IPTV websites rely on intrusive advertising and malware to gain a profit, with adverts often redirecting users to malicious or scam websites when clicked on [
7]. This is known as malvertising (malicious advertising), which distributes malware by injecting online advertisements with malicious code [
22]Cybersecurity company RiskIQ found that 1 in 3 content theft websites expose visitors to malware, with hackers paying the providers
$70 million to add malware to their websites [
1].This implies there is a significant chance of users getting infected with high-severity malware, especially if hackers are willing to pay a total of
$70 million.
Malware can be distributed to users of illegal IPTV websites when users download video files for watching IPTV content, such as MP4 files. When an infected file is opened, the malware will execute on the user’s device, which could be anything from ransomware to a remote access trojan (RAT). Although users may not realise the risks of downloading files from an untrustworthy source, technically proficient users will be aware of the risks and are likely to mitigate the risk of infecting their device by using an antivirus that scans files or a virtual machine (VM).
However, this is not the only risk of using IPTV websites. Another risk is fileless malware. Fileless malware does not require a user to download a malicious file, rather it exploits vulnerable applications on a victim’s device, to enable the injection of malicious code into its main memory [
23]. Fileless malware is a high risk to users, as it is unlikely to be detected by antivirus signatures, and could potentially infect a user as soon as they visit a website[
24].
Furthermore, many threat intelligence platforms such as VirusTotal and AlienVault Open Threat Exchange (OTX) do not recognise these sites as malicious. To illustrate, we scanned 1555 illicit IPTV websites and aggregators gained from an IPTV GitHub repository in VirusTotal. Of these websites, only 34 were identified as malicious or had an association with malware for both VirusTotal and AlienVault OTX, even though many of these websites contained intrusive advertisements attempting to scam user’s into downloading potentially unwanted programs (PUPs), which may have been malicious.
Infringing IPTV Software includes standalone desktop and mobile phone applications, in addition to add-ons or plugins for legitimate IPTV software, such as Kodi. Using standalone applications to access IPTV content illegally, often requires paid subscriptions. A study found that a business, SET TV, offered infringing IPTV content to over 180,000 users with a
$20 monthly or
$200 annual subscription via a standalone software application [
7]. Again, it is less likely that providers would infect IPTV applications with malware, if they were already making a profit. In comparison to using websites for IPTV, there is more incentive for IPTV website providers to include malware, as the content provided is usually free. However, downloading and executing an application infected with malware could have a greater impact if users don’t have antivirus software installed.
While studies suggest that standalone infringing IPTV applications have a considerable number of users, another study found that 26 million Kodi users (68% of the total user base) were pirating illegal IPTV content using Kodi software add-ons [
25].Although these add-ons are often downloaded from likely benign GitHub repositories, the Digital Citizens Alliance found that third-party Kodi add-ons, were used to distribute cryptocurrency-mining malware [
2]. Similarly, Warrior et al. found that 1.4% of Kodi add-ons resolved to domain IP addresses found on malicious blacklists (131 out of 9146 add-on’s studied) [
10]. This implies that add-ons facilitating the streaming of illicit IPTV content, are more widely used than standalone applications and may be more likely to be infected with malware.
3. Implementation
Requirements for the framework were elicited through secondary research of existing literature on the topics of malware forensics and the illegal IPTV ecosystem, which enables the gathering of requirements for the collection and analysis of malware from illegal IPTV technologies. Exploratory research consisting of analysing a sample of 1555 illicit IPTV websites in AlienVault OTX and VirusTotal was also completed to obtain requirements. The research results allowed identification of the types of malware in illicit IPTV websites, determining the approaches for detecting and collecting malware from these websites, and establishing the methodology and best practices of the framework for collecting and analysing a dataset of illegal IPTV technologies.
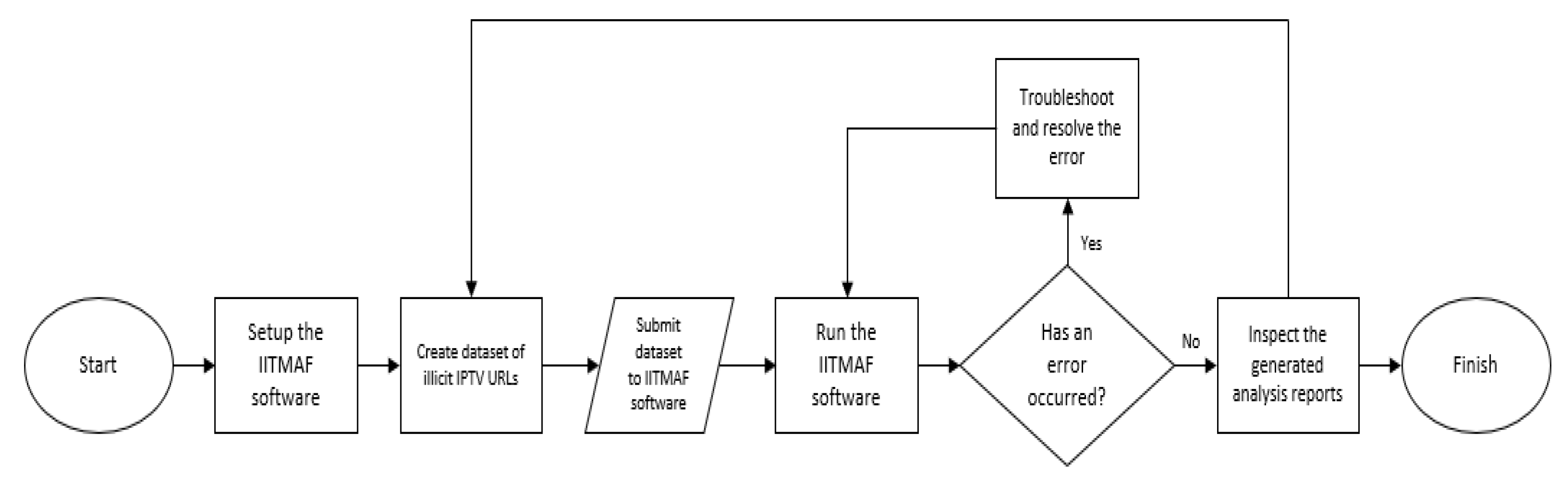
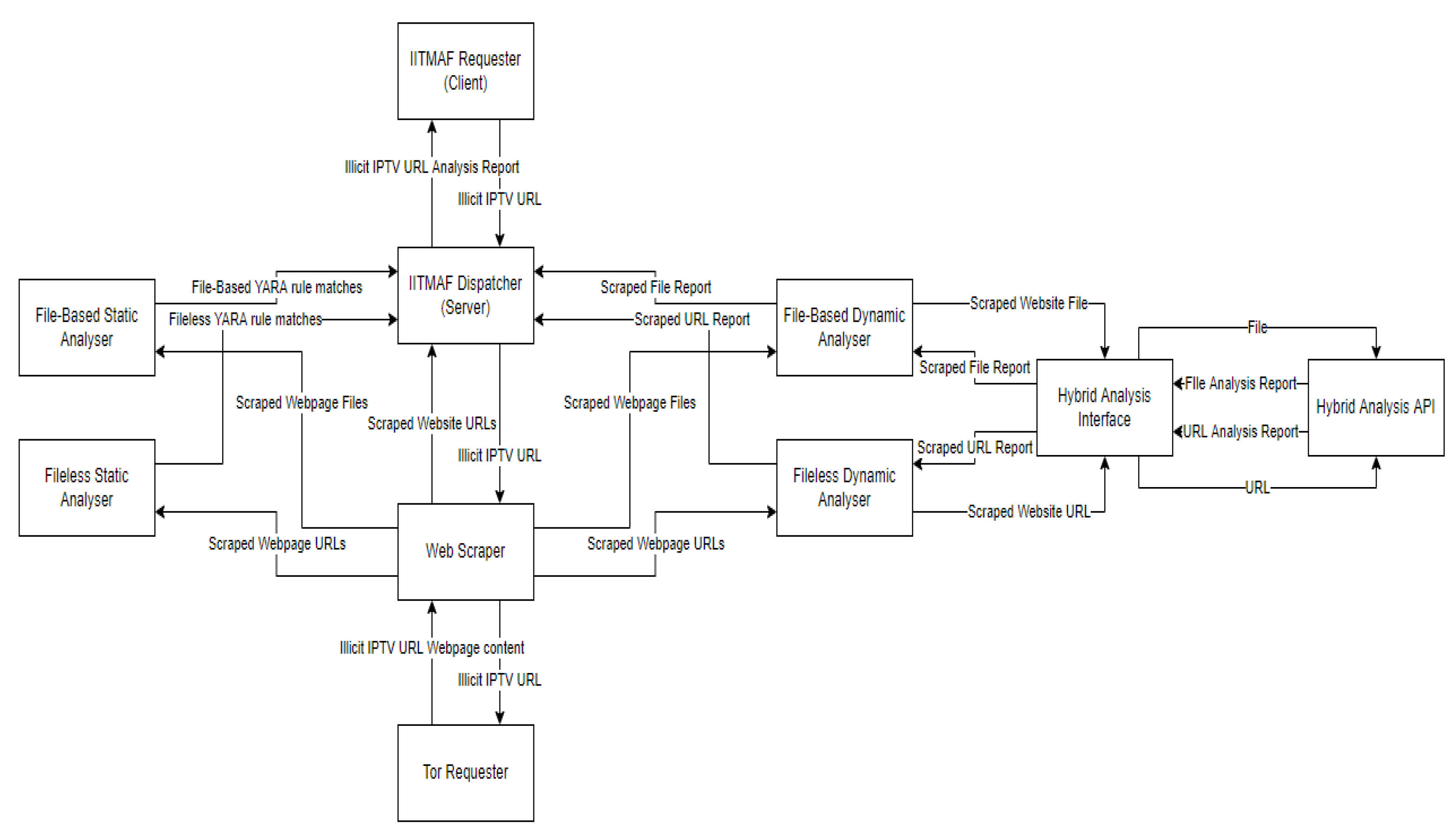
Figure 1 and
Figure 2 presents the overall methodology and a high-level data flow diagram respectively. The software solution has a client-server structure, with an API “dispatcher” server to handle requests from a “requester” client. This can enable multiple users with requester clients to issue requests to the dispatcher, providing scalability.
The IITMAF framework consist of the several components working together to support the investigations for the IPTV ecosystem. A web scraper is designed and implemented for the collection of the malicious scripts and files. A Tor requester is implemented in the scraper so that the anonymity of the investigator is ensured. For the collected artefacts, both file-based and fileless static analysers are included in the framework since, as explained previously, malicious actions and objectives are sometimes provided within a shellcode/script format. In the
Figure 2 below, a detailed data flow diagram on how these modules interact with each other is given.
The development environment of the IITMAF framework’s automated software solution consisted of a Windows 10 PC with Python 3.8.6 installed. Visual Studio Code was selected for the IDE, as it supports Python and integrates with GitHub. Moreover, Tor was installed and configured to run as a Windows service to enable the IITMAF software solution to make anonymous HTTP requests.
The dispatcher (see
Figure 2) provides a REST API that enables the collection and analysis of malware from illegal IPTV technologies. It serves several API endpoints that are called by the requester client to submit URLs. While the API is currently configured to run locally, it can be configured to make the API accessible over the internet, enabling any cybersecurity professional to identify and analyse malware in the illegal IPTV ecosystem. Additionally, the API endpoints can be accessed using Curl, Postman, or any programming language that can initiate and handle HTTP endpoints, potentially allowing organisations such as intellectual property offices to use the IITMAF framework as a threat feed for providing cyber threat intelligence.
The dispatcher has four endpoints, consisting of: endpoints for scraping URLs from a webpage; iteratively scraping URLs from a website; static analysis; and dynamic analysis. The requester client is used to submit the dataset of illicit IPTV URLs to the dispatcher API server sequentially and process the results to generate a report for each URL submitted. This allows multiple URLs to be submitted to the API and be analysed without having to manually submit every URL.
3.1. Malware collection and analysis
For the malware analysis functions, file and webpage URLs are collected from a given webpage URL using a website scraper, which are then added to a list and queued for analysis, with the given webpage’s URL and domain appended to the front of this list. If a URL pointing to a non-webpage file is submitted, the webpage scraper collects URLs and files from the URL path with the filename removed instead, which will include the original URL submitted.
Once the URLs have been collected, they are queued for either file-based or fileless static analysis. If a URL contains a webpage file type or no file type, it is submitted to static fileless analysis. Otherwise, URLs are submitted to file-based static analysis, with the files downloaded first.
The URLs and downloaded files are then compared with either file-based malware or fileless malware YARA rules, identifying any binary or textual patterns that indicate a file or webpage has malicious capabilities. Any YARA rule matches for a URL or file are then recorded and stored as a JSON object to be used in the generated report. When the static analysis process is complete, the collected URLs are submitted to either file-based or fileless dynamic analysis, similar to the static analysis process. However, JavaScript (JS) files are submitted to both file-based and fileless dynamic analysis, as JS files can contain malware and hence analysing JS files in different environments could provide more accurate results.
The dynamic analysis entails submitting the collected URLs and files to an isolated sandbox environment for automated analysis using the Hybrid Analysis API
1, with a generated analysis report returned once the analysis is done.
3.2. Report generation
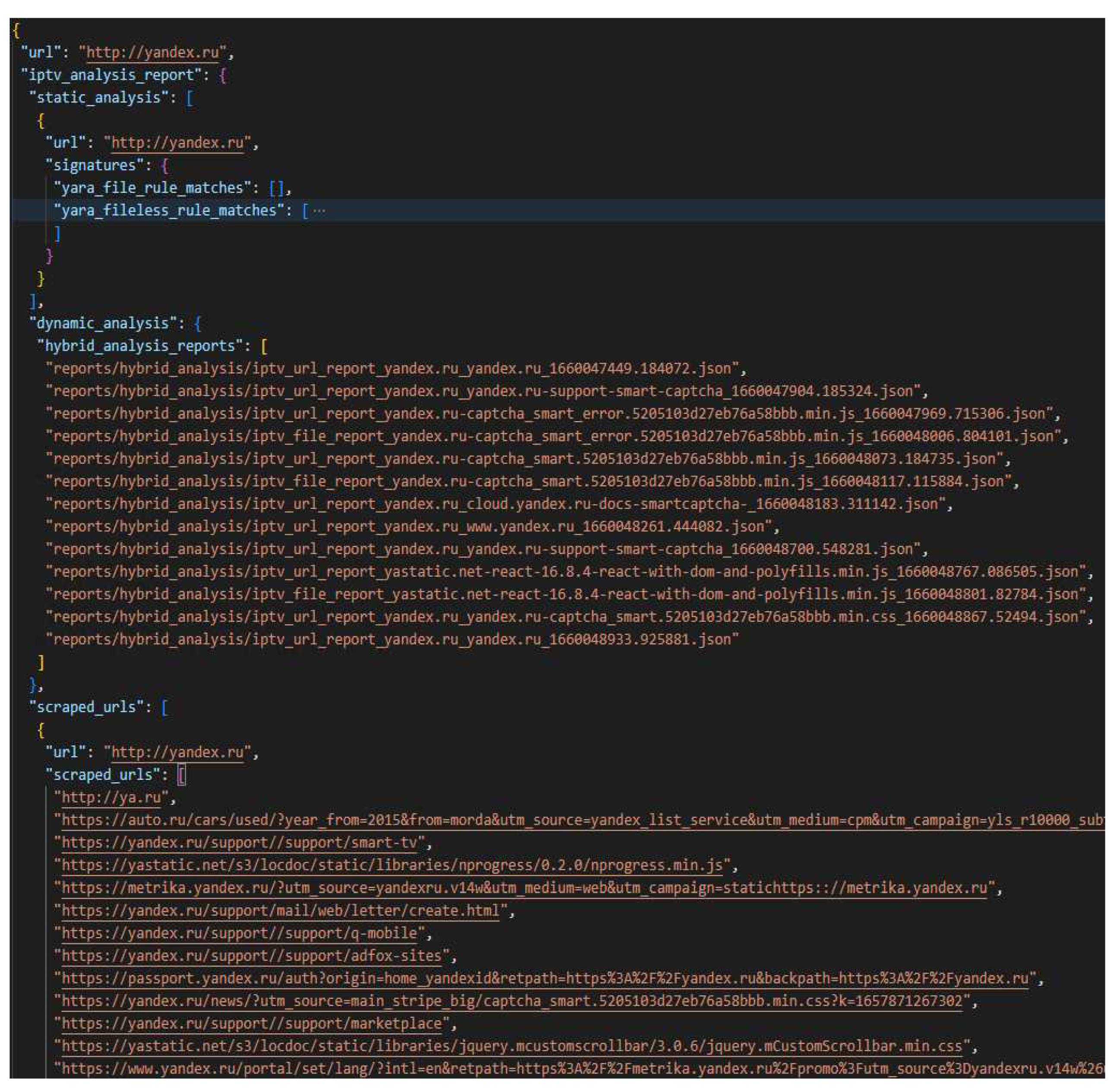
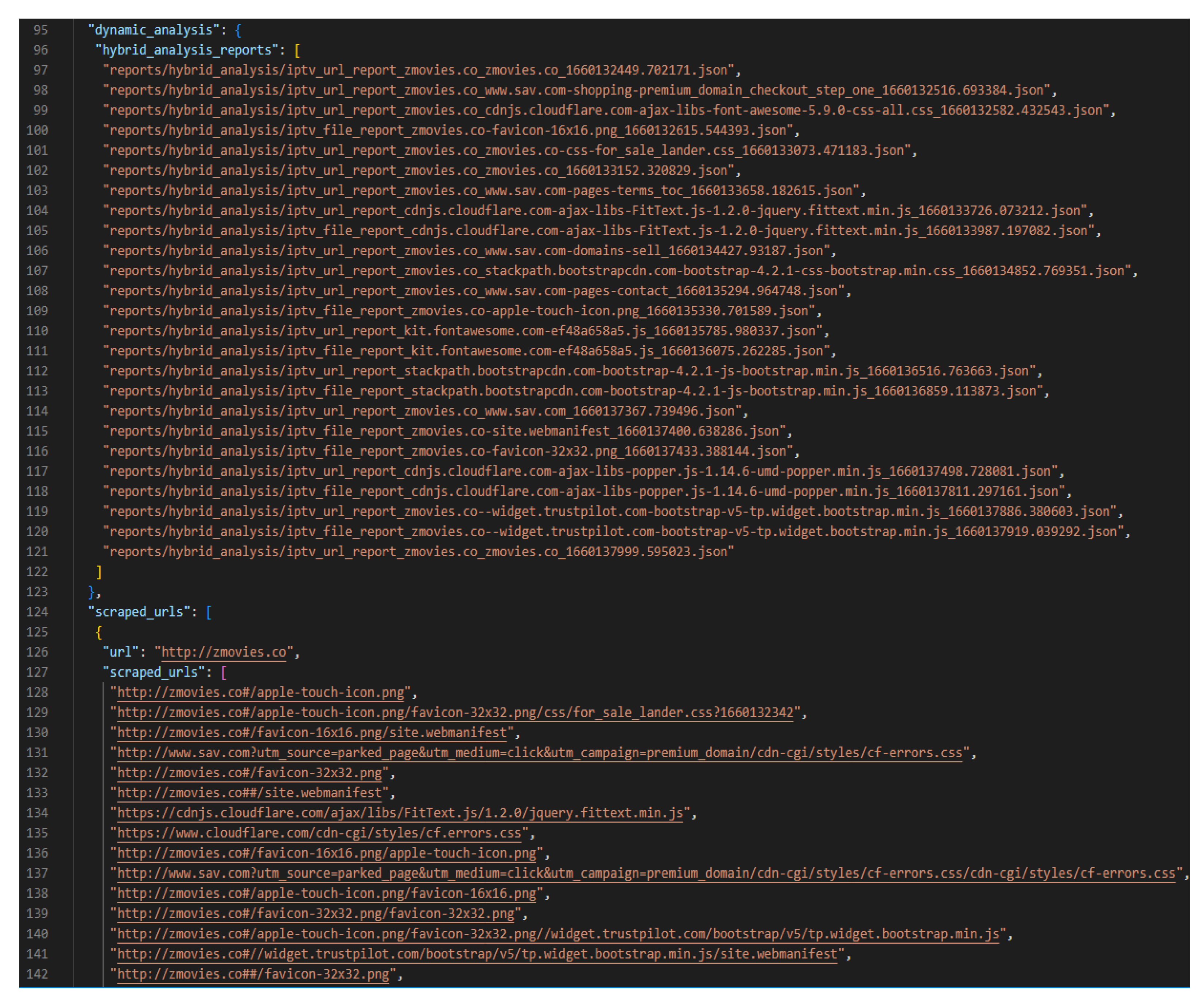
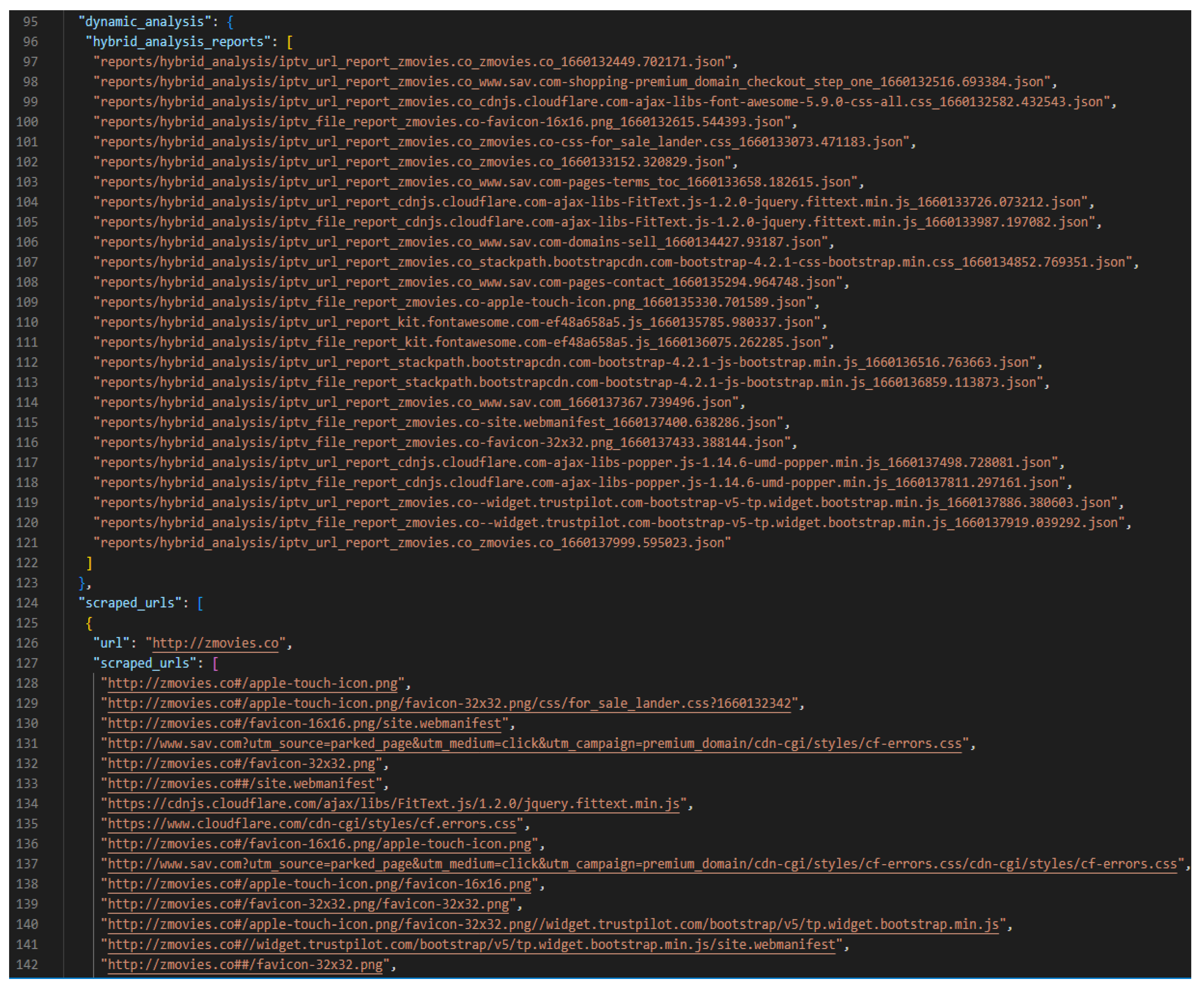
When all the collected files and URLs have been analysed, a single report is generated for each URL submitted to the dataset text file. Each report contains a section for the URLs retrieved from the iterative URL collection function, static analysis results and dynamic analysis report file paths. The report only contains the file paths of the Hybrid Analysis reports generated from the dynamic analysis or else the report would be too large.
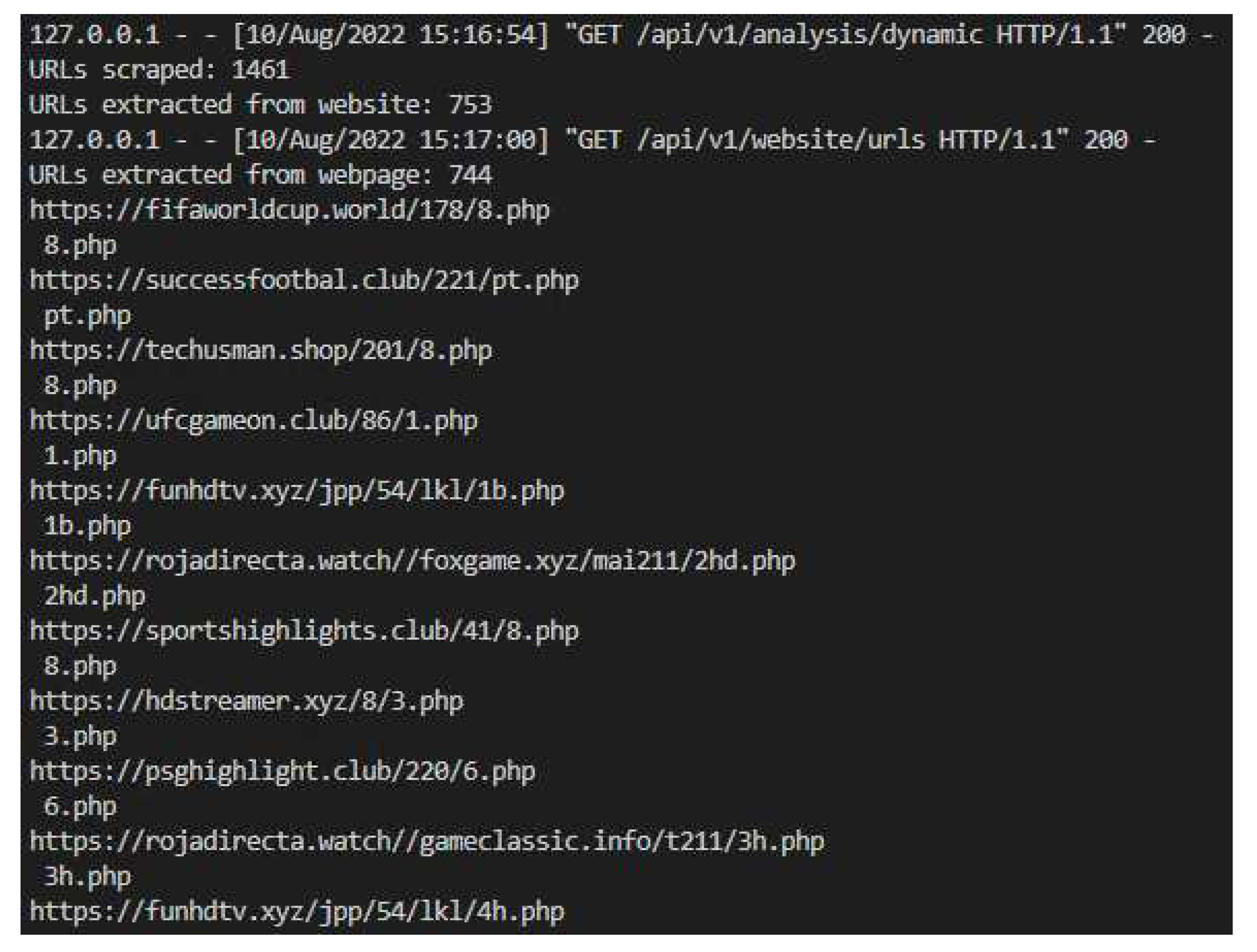
Figure 4 displays a sample of a generated analysis report, showing the dynamic analysis reports generated and the URLs scraped from the given URL webpage.
3.3. Evaluation
To evaluate IITMAF and showcase the main features of the IITMAF framework’s automated software solution, we trialled the software on an illicit IPTV website, zmovies.co applying the automated methodology of the framework outlined in section 3.1.
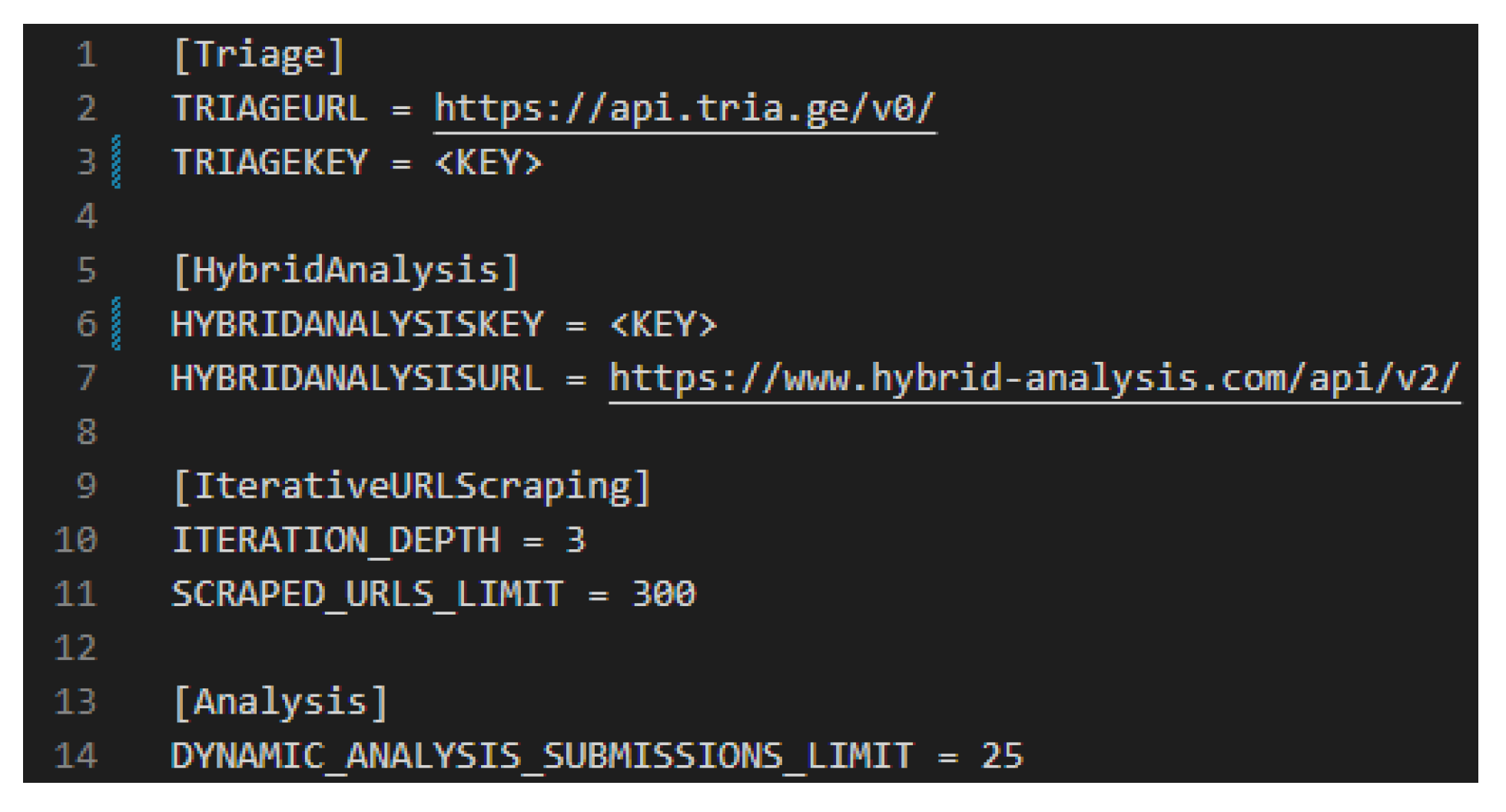
Before submitting the URL of zmovies.co to the dataset and running the IITMAF software solution, we made some modifications to the solutions configuration file. The configuration file enables the user to set limits to the collection and analysis to shorten the duration of a dataset’s analysis or to increase the volume of information reported. We set the scraper depth to 3, the maximum number of URLs scraped to 300, and the dynamic analysis submission limit to 25 as shown in
Figure 5.
Once the configuration was done, the dispatcher API and requester client of the IITMAF software solution were executed, initiating the iterative URL collection as shown in
Figure 6.
The iterative URL collection function extracted 87 unique URLs from the given website URL, with any duplicate URLs removed from the list, while 20 URLs were extracted from the webpage of the given URL and queued for analysis.
For the analysis, any URLs pointing to files were downloaded, with some of the files downloaded shown in
Figure 7. Once the static and dynamic analysis was complete, a report was generated, with a sample of the report presented in
Figure 7.
Although the submitted URL and its scraped files and URLs returned no YARA rule matches, the iterative URL collection and dynamic analysis functions supplied a high number of results, with
Figure 7 showing some of the URLs scraped from the given website and the Hybrid Analysis reports generated.
To determine if zmovies.co was associated with malware or malicious activity, we submitted some of the internal and external URLs collected from the website to VirusTotal and checked the generated Hybrid Analysis reports for malicious indicators. While we found few malicious indicators from the URLs collected, the Hybrid Analysis report of a file scraped from zmovies.co indicated malicious activity.
Figure 8 shows the Hybrid Analysis report for a JavaScript file downloaded from zmovies.co which marks the file as “suspicious” and classifies it as a Trojan HTML Agent.
To get further information about whether the collected JS file was malicious, we checked the SHA-256 hash of the file in VirusTotal
2. While only one antivirus tool detected the file as malicious, the relations show that the collected file is often created by known malware files when they are executed.
In conclusion, the IITMAF framework software solution was able to detect a potentially malicious file collected from an illicit IPTV website and classify it. This shows that the framework can collect URLs and files from illicit IPTV websites and identifying malicious activity.
4. Findings
The experiment completed for evaluating IITMAF entailed submitting a research sample of illegal IPTV technology URLs to IITMAF and comparing the analysis results with results from VirusTotal. The research sample had a total of 60 URLs, consisting of 35 illicit IPTV website URLs, 13 app store URLs (from 7 app stores), and 12 standalone software executable and add-on URLs. Less illicit IPTV app store and software URLs are included in the research sample, as they were more difficult to locate in comparison to websites, which are more accessible using search engines.
For the evaluation (Section 33), each sample URL submitted to IITMAF collected up to 25 URLs, which were then submitted for analysis in addition to the research sample URL. Once the analysis reports had been generated for the research sample, the number of URLs in the research sample identified as malicious were recorded and compared with the results of the research sample URLs submitted to VirusTotal (
Table 1). Moreover, the number of URLs in the research sample that scraped URLs or files identified as malicious by IITMAF were recorded. These results were then compared with the number of URLs in the research sample that identified malicious related files from 2022 for the domain of the URLs in VirusTotal. Only malicious files from 2022 were used to determine the number of malicious relations for a URL, as VirusTotal is a community-based threat intelligence platform which identifies malware previously submitted that may not be relevant to URLs in 2022. Hence, only recent malware from 2022 will be counted.
Table 1 presents the findings of the experiment completed to evaluate the IITMAF software solution, which was conducted from the 8th to the 16th of August 2022. As VirusTotal identifies related malicious files by a URLs domain, we used the domains of the URLs in the research sample to determine whether a URL had related malicious files. Therefore, the related malicious file results for app stores are out of seven, as the thirteen app store URLs in the research sample only include seven different domains.
The experiment results show that the IITMAF solution detected more URLs as malicious than VirusTotal overall, with IITMAF identifying 32 out of the 60 URLs of the research sample as malicious, while VirusTotal only identified 23 as malicious. Additionally, the IITMAF solution detected related malicious files or URLs for 31 of the research sample URLs, whereas VirusTotal identified 26 malicious relations from 2022.
6. Discussion
Although IITMAF identified more illicit IPTV technologies as malicious than VirusTotal, VirusTotal classified a greater number of illicit IPTV app store and software URLs as malicious than IITMAF. This is because app store and software URLs often pointed to Android APK files or had relations with these files, which the dynamic analysis feature of the IITMAF solution is unable to execute and analyse as it uses a Windows sandbox environment by default. Conversely, IITMAF was still able to identify 12 of the 25 app store and software URLs as suspicious, and thus only 8 out of 25 were classified as benign. Moreover, IITMAF identified ransomware TTPs for three files scraped from an illicit IPTV app store included in the research sample. This demonstrates that IITMAF is still capable of providing actionable information for a range of illegal IPTV technologies, even if it has limitations when analysing APK files. Finally, the IITMAF framework primarily focuses on the analysis of illicit IPTV websites and the extraction of files and URLs from them. Hence, due to time constraints, the dynamic analysis of Android files that require a different sandbox environment was not implemented.
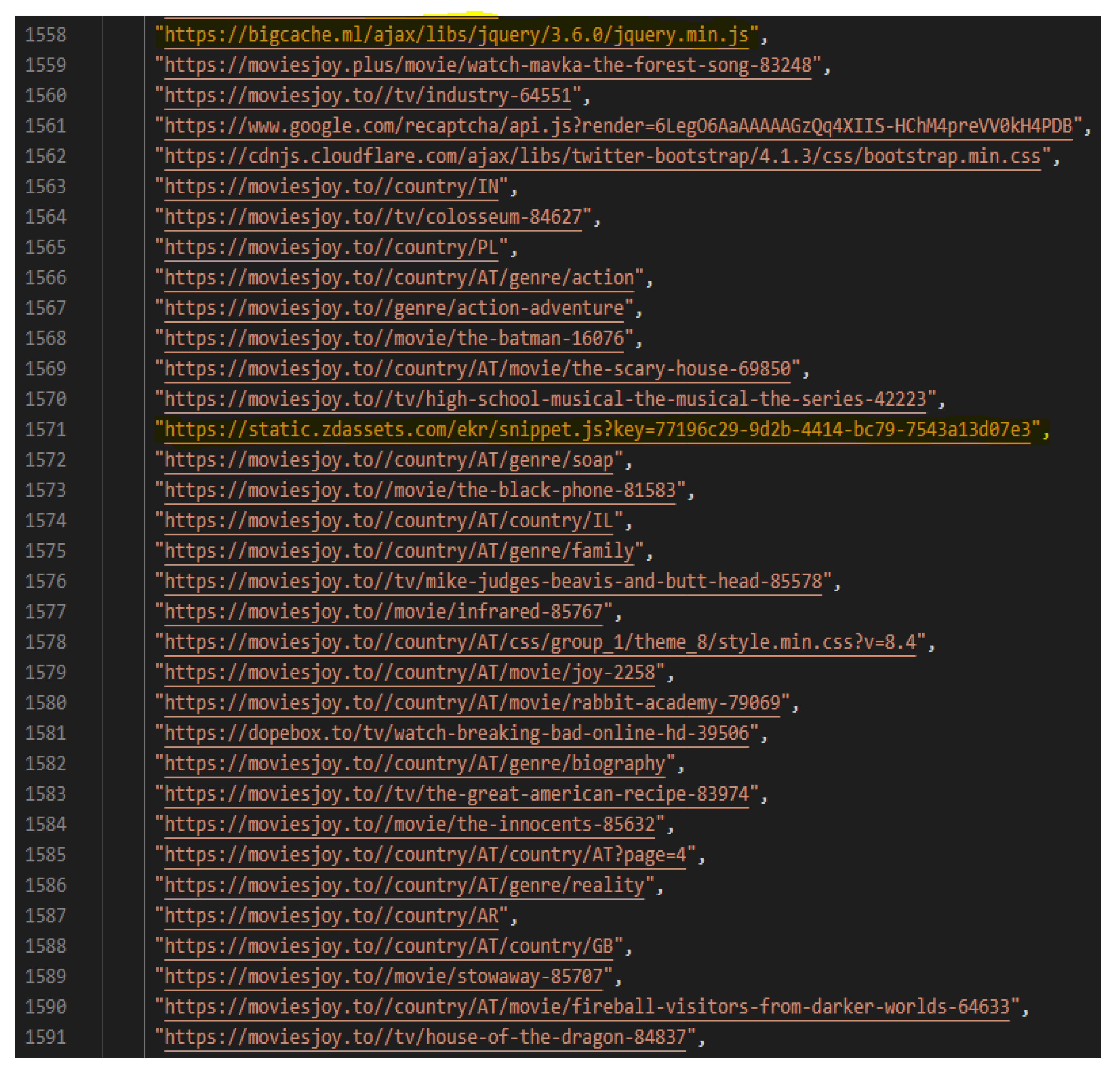
Figure 10 shows some of these collected URLs for an illicit IPTV website (moviesjoy.to) which includes URLs with external domains, potentially used for malvertising. The VirusTotal report for one of the external domains collected for this IPTV website, namely ‘static.zdassets.com’, identified many recent malicious related files, that had file names used in intrusive advertisements, common in illicit IPTV websites such as “AntiVirusExe.exe” and “PCCleaner” [3]. Moreover, another URL to an external domain, bigcache.ml, had a URL path pointing to an alleged JQuery library JavaScript file. The VirusTotal report of this URL reported two malicious and one suspicious antivirus alert, in addition to classifying the domain as a malware site. This implies that the iterative URL collection function is effective at collecting URLs from a website including any external domains which could be used for malvertising. Hence, the IITMAF framework is capable of iteratively scraping potentially malicious URLs from a website.
Thus, this demonstrates that the webpage URL collection function is effective at collecting files and URLs from a webpage and submitting them for analysis. Conversely, a limitation of both the URL collection functions is that website CAPTCHA security mechanisms are often triggered when scraping a website, limiting the number of URLs and files that are collected. The likelihood of a CAPTCHA mechanism triggering is increased further where the HTTP requests made by the URL collection functions are routed through Tor. While disabling Tor for the URL collection functions could enable more URLs to be collected, this would make the IITMAF host’s public IP address visible to potentially malicious websites, posing a security risk. Therefore, this limitation has been accepted, as the results of the evaluation experiment conducted suggest that the URL collection functions are sufficient even with this limitation in place.
Table 2 shows the correlation from CTI sources collected for all the IPTV websites investigated in this research (Section 4.3). The table includes details of the following fields:
Signatures: Potentially malicious behavioural/static signatures raised by Hybrid analysis.
Number of Files: The number of files that are extracted from a webpage.
Number of Compromised Hosts: From all the urls that are linking out from this webpage, the number of them that are marked malicious.
Maximum Threat Score: A metric calculated by Hybrid Analysis (Hybrid Analysis 2022) demonstrating the threat score of a link.
Malicious File and Fileless Signatures: The number of alerts raised by the crafted YARA rules analysis for file malware or fileless malware signatures respectively.
Extracted URLs: number of URLS that are extracted from a webpage.
Thus,
Table 2 shows that the signature and number of files that a webpage tries to download highly correlates with the visitor’s signatures (value 0.936017738). Further, a correlation of ~0.67 was observed between the number of fileless signatures and the extracted URLs. This latter correlation can be explained with the form of delivery of fileless threats, which is the general case through the browser exploitations.
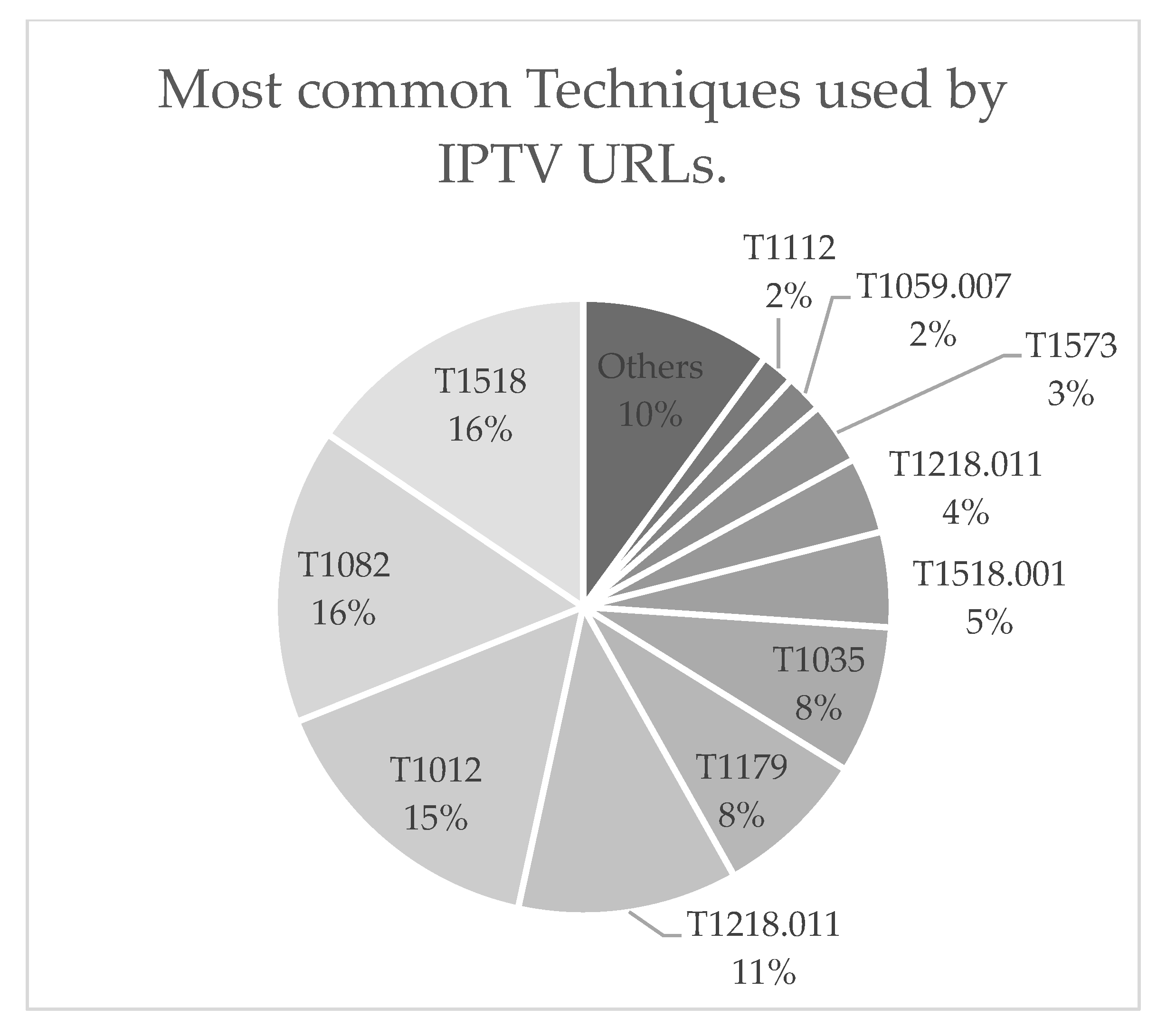
Another important observation that we have collected from this dataset is the most common techniques that have been utilised on these IPTV sources. The titles of the most common techniques encountered in the experiments of this study can be found in the following list:
T1518: Software Discovery
T1082: System Information Discovery
T1012: Query Registry
T1218.011: System Binary Proxy Execution
T1179 also moved to T1056.004: Input Capture: Credential API Hooking
T1035: System Services: Service Execution
T1518.001: Security Software Discovery
T1218.011: RunDLL
T1573: Encrypted Channel
T1059.007: Command and Scripting Interpreter: JavaScript
T1112: Modify Registry
The breakdown of the use of these techniques can be found in
Figure 11.
7. Conclusion
This paper presented the IITMAF framework, an effective tool for automatically detecting, collecting, and analysing malware from illegal IPTV technologies. We evaluated the framework through a series of use cases and collection where we demonstrated the effectiveness of the IITMAF framework and showcased the results that can be achieved using IITMAF when compared with existing solutions. The evaluation results show that the IITMAF framework is more effective at detecting malicious capabilities and behaviour from illicit IPTV technologies overall, while VirusTotal is more effective at detecting malware from illicit IPTV app stores and software files.
Although VirusTotal identified a greater volume of app store and software URLs as malicious, the IITMAF framework was intended primarily for analysing illicit IPTV websites, with its iterative URL collection results capable of identifying possible external malvertising domains for an illicit website.
Moreover, the IITMAF framework produces a more comprehensive analysis report than other solutions, with matched YARA rules and dynamic analysis results classifying malware and supplying related TTPs. From the findings (
Section 4), YARA rules detected malicious capabilities in an executable file relating to privilege escalation and a malicious document format. Likewise, the behavioural analysis results of an HTML webpage, classified detected malicious behaviour as an indicator of ransomware. This demonstrates that the IITMAF framework is capable of supplying actionable threat intelligence for malware detected in the illicit IPTV ecosystem.
7.1. Limitations and future work
While the experiment results imply that the IITMAF framework is effective at collecting and analysing malware from illegal IPTV technologies, it does have limitations. One limitation of the IITMAF framework software is that the duration of the analysis is high, as multiple URLs and files are submitted to dynamic analysis which can take time. However, dynamic analysis and URL collection limits can be set to shorten this duration, providing configurability for the IITMAF framework.
Another limitation of the framework is that it provides limited analysis results for archive and Android-specific files, as they cannot be executed in the default Windows sandbox. Despite any limations, the IITMAF framework focuses chiefly on the analysis of illicit IPTV websites, but we plan to address these limitations in the future work section.
Overall, the IITMAF framework provides a successful solution to the defined problem, providing cybersecurity professionals with both manual and automatic methodologies for identifying malware threats in the illicit IPTV ecosystem, in addition to an automated solution for detecting, collecting, and analysing malware from illegal IPTV technologies.
Although the URL and file analysis functionality meets the core requirements and detected a greater number of URLs as malicious than VirusTotal in the evaluation experiment, it has two minor limitations. One of these limitations is that for the submitted research sample in the evaluation experiment, only 4 out of the 60 URLs analysed had YARA rule matches indicating malicious capabilities. Nonetheless, 31 of the URLs had YARA rule matches for base64 encoded functions, implying that the static analysis functionality works properly. Additionally, one of the URLs pointing to an executable file had multiple YARA matches suggesting that it was malicious, as shown in
Figure 14. This indicates that the signature-based malware detection functionality for IITMAF using YARA rules is still relevant and can detect malicious capabilities.
The other limitation of the IITMAF analysis functionality is that it was unable to conduct dynamic analysis for ZIP files, as Hybrid Analysis does not automatically extract files from them. This suggests that the IITMAF framework has limitations when analysing illicit IPTV add-ons, as they are frequently distributed using ZIP files.
In summary, the automated URL and file analysis functions of the IITMAF framework are effective at detecting malware and supplying detailed information about a file or URL’s capabilities and behaviour. While there are some minor limitations, the analysis functionality meets the key requirements set and passes all the major unit tests.
In the future, we intend to improve the IITMAF framework by implementing additional features to the automated solution. One of these features would be downloading files from scraped webpage URLs depending on if a URL HTTP request header’s content type relates to a non-webpage file. This would ensure that non-webpage files referenced by URLs that do not identify a file extension in the URL path are downloaded. Additional functionality to be developed would be mechanisms to bypass website CAPTCHAs, providing more accurate analysis results of malicious activity in illicit IPTV websites. Moreover, we plan to implement a Hybrid Analysis interface function for performing dynamic analysis on Android APK files, as many illicit IPTV technologies consist of Android applications that cannot be dynamically analysed in a standard Windows-based Sandbox. Finally, as the Hybrid Analysis API is unable to automatically unpack archive files, we aim to implement functionality that automatically unpacks downloaded archive files and submits the contents for analysis, as illicit IPTV software add-ons can be distributed in an archive format.
Author Contributions
Conceptualization, Adam Lockett and Cagatay Yucel; Investigation, Adam Lockett; Methodology, Adam Lockett; Project administration, Vasilis Katos; Software, Adam Lockett; Supervision, Cagatay Yucel and Vasilis Katos; Validation, Adam Lockett, Ioannis Chalkias, Cagatay Yucel and Jane Henriksen-Bulmer; Writing – original draft, Adam Lockett; Writing – review & editing, Ioannis Chalkias and Jane Henriksen-Bulmer.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
Notes
| 1 |
https://www.hybrid-analysis.com/. |
| 2 |
https://www.virustotal.com/gui/domain/bmovies.vip/relations, https://www.virustotal.com/gui/domain/bmovies.vip/relations, https://www.virustotal.com/gui/url/499df4b49ada07ff706a56bc1bf8483f8f78940b4047926d91bc349786bef920/detection, |
References
- Digital Citizens Allience How Digital Platforms Are Being Overrun by Bad Actors and How the Internet Community Can Beat Them at Their Own Game; 2017.
- Digital Citizens Allience Fishing in the Piracy Stream: How Dark Web of Entertainment Is Consumers to Harm; 2019.
- Hsiao, L.; Ayers, H. The Price of Free Illegal Live Streaming Services. 2019.
- Watters, P. A Systematic Approach to Measuring Advertising Transparency Online: An Australian Case Study. SSRN Electronic Journal 2013. [CrossRef]
- Simpson, W.; Greenfield, H. What Is Internet Protocol, and Why Use It for Video? In IPTV and Internet Video; Elsevier, 2009; pp. 1–14.
- 2017; 6. Sandvine Subscription Television Piracy Sandvine Global Internet Phenomena Spotlight CASE STUDY 2 GLOBAL INTERNET PHENOMENA SPOTLIGHT; 2017.
- Pandey, P.; Aliapoulios, M.; McCoy, D. Iniquitous Cord-Cutting: An Analysis of Infringing IPTV Services. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW); IEEE, June 2019; pp. 423–432.
- Intellectual Property Office UK Government Response to the Call for Views Regarding Illicit IPTV Streaming Devices; 2018.
- EUIPO ILLEGAL IPTV IN THE EUROPEAN UNION; 2019.
- Warrior, M.A.; Xiao, Y.; Varvello, M.; Kuzmanovic, A. De-Kodi: Understanding the Kodi Ecosystem. In Proceedings of the Proceedings of The Web Conference 2020; ACM: New York, NY, USA, April 20 2020; pp. 1171–1181.
- Samtani, S.; Chinn, K.; Larson, C.; Chen, H. AZSecure Hacker Assets Portal: Cyber Threat Intelligence and Malware Analysis. IEEE International Conference on Intelligence and Security Informatics: Cybersecurity and Big Data, ISI 2016 2016, 19–24. [CrossRef]
- Piplai, A.; Mittal, S.; Abdelsalam, M.; Gupta, M.; Joshi, A.; Finin, T. Knowledge Enrichment by Fusing Representations for Malware Threat Intelligence and Behavior. Proceedings - 2020 IEEE International Conference on Intelligence and Security Informatics, ISI 2020 2020. [CrossRef]
- Miles, C.; Lakhotia, A.; Ledoux, C.; Newsom, A.; Notani, V. VirusBattle: State-of-the-Art Malware Analysis for Better Cyber Threat Intelligence. 7th International Symposium on Resilient Control Systems, ISRCS 2014 2014. [CrossRef]
- Tan, H.; Chandramohan, M.; Cifuentes, C.; Bai, G.; Ko, R.K.L. ColdPress: An Extensible Malware Analysis Platform for Threat Intelligence. 2021.
- 15. EUIPO IDENTIFICATION AND ANALYSIS OF MALWARE ON SELECTED SUSPECTED COPYRIGHT-INFRINGING WEBSITES; 2018.
- Theocharidou, M.; Malatras, A.; Lella, I.; Tsekmezoglou, E. ENISA Threat Landscape 2021; 2021.
- 17. Vala Khushali A Review on Fileless Malware Analysis Techniques. International Journal of Engineering Research and 2020, V9, 46–49. [CrossRef]
- Saad, S.; Mahmood, F.; Briguglio, W.; Elmiligi, H. JSLess: A Tale of a Fileless Javascript Memory-Resident Malware. Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) 2019, 11879 LNCS, 113–131. [CrossRef]
- Kara, I. Fileless Malware Threats: Recent Advances, Analysis Approach through Memory Forensics and Research Challenges. Expert Syst Appl 2023, 214, 119133. [CrossRef]
- 2020; 20. Ponemon Institute The Third Annual Study on the State of Endpoint Security Risk; 2020.
- Yucel, C.; Chalkias, I.; Mallis, D.; Karagiannis, E.; Cetinkaya, D.; Katos, V. On the Assessment of Completeness and Timeliness of Actionable Cyber Threat Intelligence Artefacts. In; 2020; pp. 51–66.
- Xing, X.; Meng, W.; Lee, B.; Weinsberg, U.; Sheth, A.; Perdisci, R.; Lee, W. Understanding Malvertising Through Ad-Injecting Browser Extensions. In Proceedings of the Proceedings of the 24th International Conference on World Wide Web; International World Wide Web Conferences Steering Committee: Republic and Canton of Geneva, Switzerland, May 18 2015; pp. 1286–1295.
- Sudhakar; Kumar, S. An Emerging Threat Fileless Malware: A Survey and Research Challenges. Cybersecurity 2020, 3, 1. [CrossRef]
- Sanjay, B.N.; Rakshith, D.C.; Akash, R.B.; Hegde, Dr.V. V. An Approach to Detect Fileless Malware and Defend Its Evasive Mechanisms. In Proceedings of the 2018 3rd International Conference on Computational Systems and Information Technology for Sustainable Solutions (CSITSS); IEEE, December 2018; pp. 234–239.
- Sheppard, J. Cloud Investigations of Illegal IPTV Networks. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE); IEEE, August 2018; pp. 1942–1947.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).