The text of this section will in principle be based on the general classification of types of security, which can be understood as a model expression of the issue in question.
2.1. Classification of security types
In the security environment, the premise is accepted to a certain extent that security is a state when threats are reduced to the lowest possible level and the risks of the selected asset are minimized to the lowest possible level or acceptable level, and when the asset is effectively equipped for these minimization [
25]. This premise to a certain extent points to the indivisibility of security as a scientific field. In general, however, the opinion can be taken that security measures belonging to the Safety group reflect unintentional security threats, and security measures belonging to the Security group reflect intentional security threats and the risks resulting from them [
26]. However, it is necessary to admit the fact that in security practice there would be examples that might not fully confirm this claim or would be a combination of both groups of measures.
The aspect of security threats and the risks resulting from them is therefore a fundamental basis for the definition and determination of types of security. Therefore, the formulation of types of security reflects to a certain extent the basic classification of security threats, which according to [
27] is categorized into external threats (i.e. political, economic, social, technological, legislative, and ecological) and internal threats (i.e. procedural, personnel, and material).
Article [
28] described another philosophical view on the classification of security types from the point of view of security models. Security models are understood in this context as "conceptual models" that describe the essence and method of ensuring the security of the reference object using verbal and visual methods. The model reflects the essence of measures through which security is ensured. Security can be ensured by a system of measures of a logical or physical nature. Logical measures include rules, management, education, negotiation, prediction, deterrence, encryption, etc. These measures are based on information and work with them. Physical type measures include barriers (fences, walls), shock absorbers, physical security, forces and assets of the armed forces, warning and alarm systems, supplies, etc. Basic security assurance models include mode model, proactive model, barrier model, preparedness model, model of collective security/common interest, reactive model, rule enforcement model, and deterrence model.
However, it should be noted that in a few models the essence of ensuring security is implemented in several ways. Therefore, they include several model variants. The rule enforcement model and the deterrence model are specific models and are auxiliary in their nature. When ensuring security itself, one the type of security model is used only in rare cases. Usually, security is ensured by a combination of measures falling under the agenda of several security models [
29].
From the point of view of defining the type of security in the context of converged security, type of security represents a set of measures solving a specific group of security problems. This is a certain continuity of solving negative phenomena associated with security breaches. The goal of the introduced and implemented measures is to prevent damage or at least minimize the effects caused by security breaches. An example of a type of security is physical security, information security, occupational health and safety, road traffic safety and international security. Converged security combines operational security, physical security, and cyber security [
8].
2.2. Converged resilience assessment
As it was declared in the introduction, the presented article is based on and ultimately practically materializes the article [
8]. It is therefore logical, especially for the understanding of the concept of converged security assessment to describe Converged Resilience Assessment (CRA) method.
Considering the specifics and importance of the SCI and the relevant need to reflect current security threats, the Converged Resilience Assessment (CRA) method was presented in the aforementioned article. The added value of this method is the use of the security convergence philosophy for the needs of objective assessment of resilience. In this context, there is a selected security types convergence, which are the most important from the selected infrastructures functionality ensuring point of view. These are physical, cyber and operational security. The mentioned CRA method uses information and situational management, integrating sensors systems and their data flows into an effective managing and solving security events system. This methodology can be used for the individual assets that the evaluated SCI element contains and at the same time for the strategic level of electricity supply ensuring. The resulting value is subsequently expressed by the aggregation of individual resiliencies. [
8].
The added value of the CRA method is the ability to identify the resulting value of the selected SCI elements protection system resilience in context of converged security by determining the resilience indicator of the reference object . The resilience indicator therefore reflects the security level of the reference object assets in relation to the identified risks and in relation to their convergence. The value of the dimensionless resilience indicator ranges from 100 to 0, where the value 100 reflects the upper limit and the value 0 the lower limit of resilience.
It is clear from practice that converged security is related to several security types and simultaneously to several assets, logically, resilience must be assessed for each security type referring to the selected asset. Aggregation will then make it possible to determine the resulting resilience indicator for a different type of security (physical, cyber operational). The determination of the resulting resilience indicator for the reference object is subsequently based on the arithmetic mean of the individual asset’s resilience indicator. The connection between the above variables is expressed in equation (1):
where
= reference object resilience indicator;
= i-th security type resilience indicator;
= converged security types number;
= j-th variable of asset physical security resilience;
= j-th variable of asset cyber security resilience;
= j-th variable of asset operational security resilience;
= assessed assets number.
The presented approach enables aggregation through individual assets, which is the basis for computing the final value of resilience indicator. The final value of reference object resilience indicator
is made up of the resilience indicator of all assets. For these purposes, the arithmetic mean of converged resilience expressed by the following computation method is used in equation (2):
where
= reference object resilience indicator;
= j-th asset converged resilience indicator;
= j-th normalized weight of the j-th asset;
= assessed assets number.
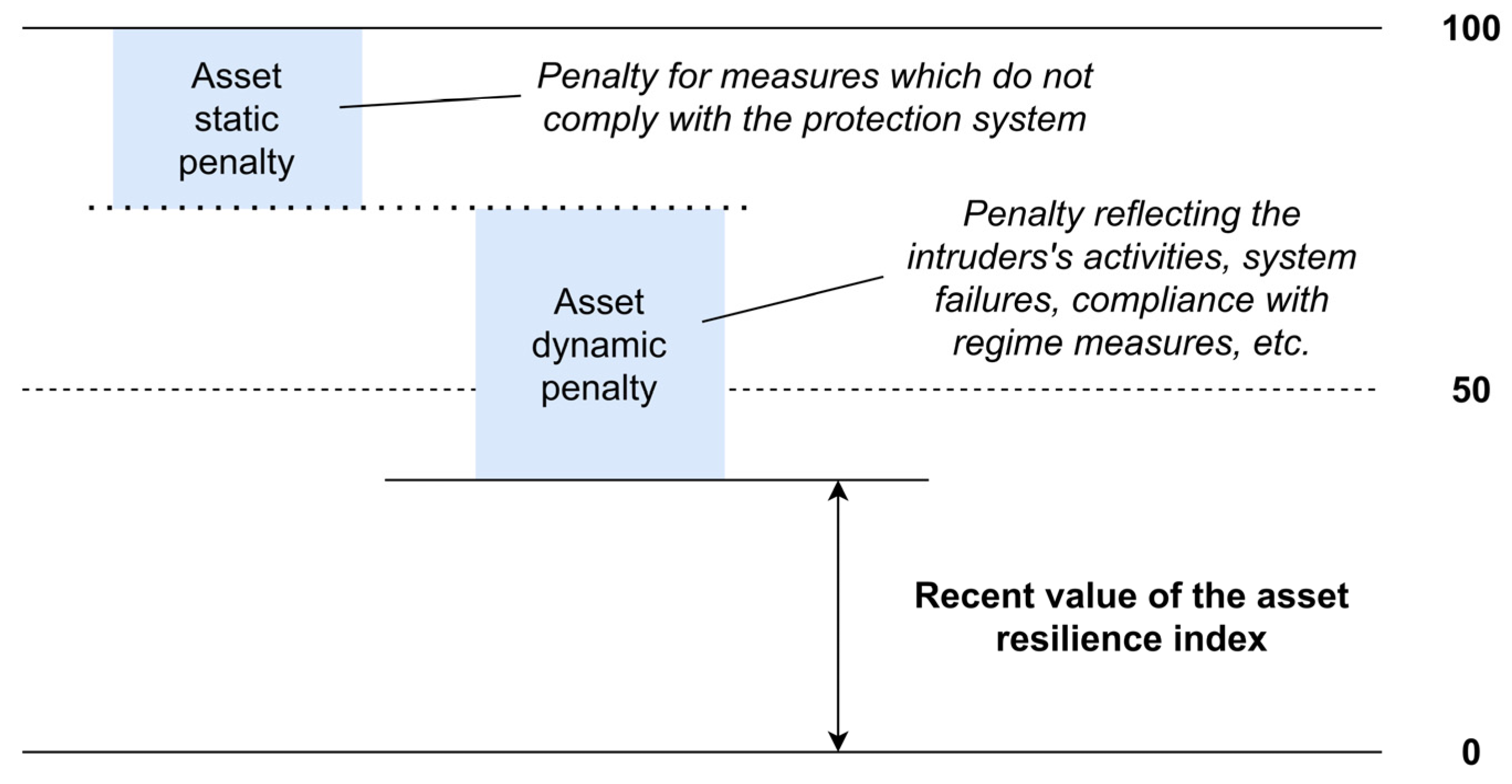
The resulting resilience indicator of the assessed object is expressed as an abstract value taking on a value in the interval from 0 to 100 points. For computation purposes, the initial resilience value is set at 100 points. It is based on the assumption that this value reflects an ideal state and thus the protection system of the reference object achieves and fulfils all the required measures and no penalizing factor is currently acting on it. The real state and value of the resilience indicator is in practice conditioned by the action of the penalty factor, which reduces the initial 100-point value. The lower limit and value of the resilience indicator was set at 0. This state then reflects the fact of the absence of the required measures or the state of penalizing factors action. Likewise, this situation is unlikely in practice, even considering the small probability of the simultaneous occurrence and action penalizing factors.
The value of the reference object assessed asset converged resilience I is expressed by the aforementioned aggregation, based on the selected security types resilience value, i.e. , , . Considering the formulation of the previous conditions, even in this case the value of the indicator ranges from 0 to 100 points. Also in this case, the computation is conditioned by the action of penalty factors and the reduction of the initial value. In practice, penalization factors are divided into static and dynamic factors, i.e. factors that take into account static penalization obtained for measures that the protection system should have but does not have at the given time, and dynamic penalization, which is obtained by the action of the intruder, non-compliance with regime measures or failure states of individual protection system components. The value based on the dynamic factors subsequently adjusts the value of the static penalty.
Subsequently, the indicator of converged asset resilience is computed, through the reference object selected assets resilience indicators arithmetic aggregation for selected security types (see equation 3).
where
= asset converged resilience indicator;
= asset physical security resilience indicator;
= asset cyber security resilience indicator;
= asset operational security resilience indicator.
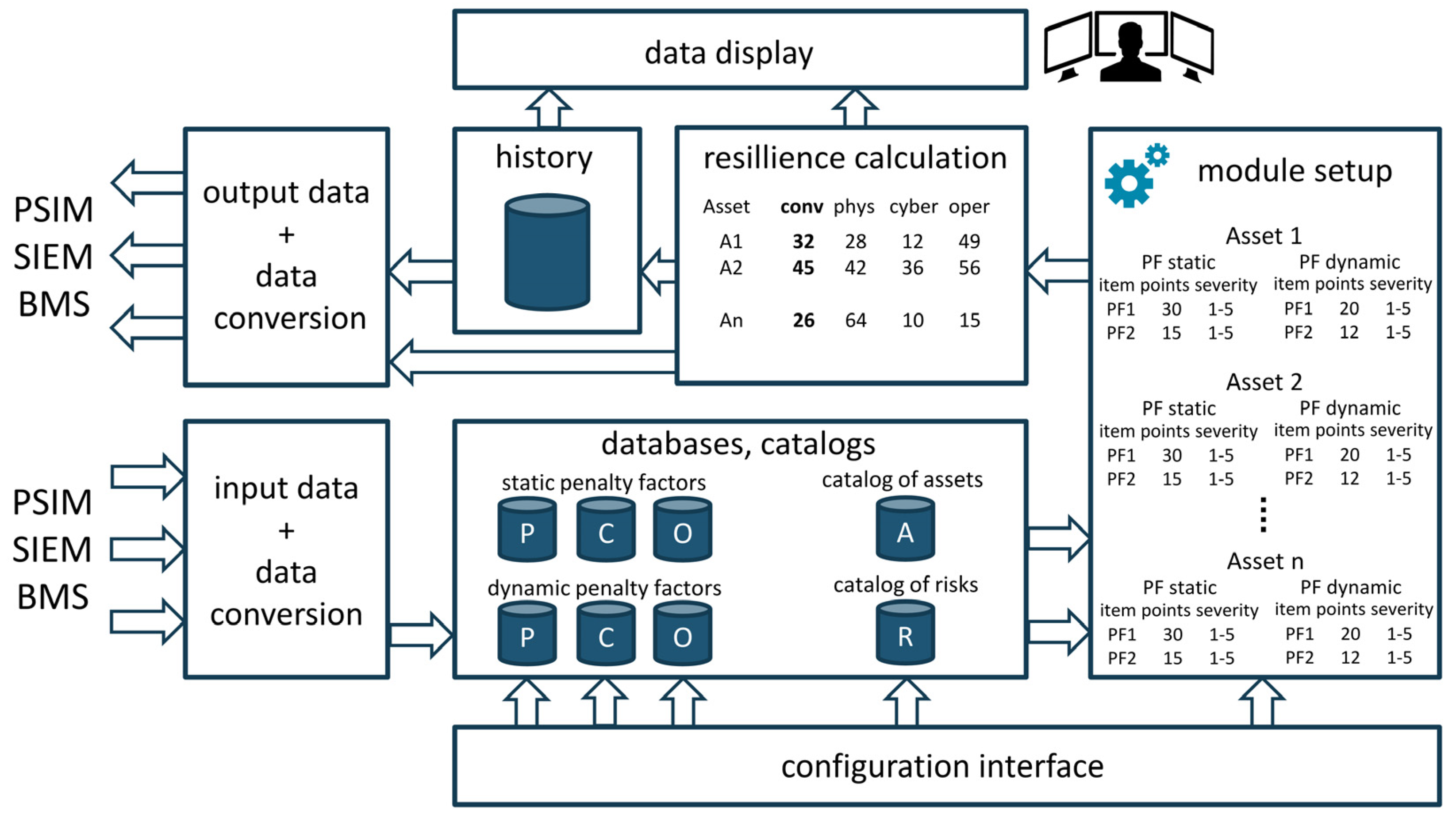
Logic and visualization of the actual computation of the asset resilience indicator with respect to the selected security types
,
,
is expressed in
Figure 1.
The mathematical model for asset resilience indicator computation will be presented in the introductory part of the fourth chapter of the article as a certain form of algorithmization of system and sensory data into Converged Security and Information Management System computing core.
2.3. PSIM/SIEM category systems convergence as a data source for resilience assessment
The previous section explained the issue and importance of assessing the resilience of a protected asset and described a new approach of resilience assessment using penalty factors. The aim of this section is to seamlessly follow up on the previous topic and to focus especially on the issue of resilience level change based on information from technological means through dynamic penalty factors. For these purposes, it is most appropriate to use sophisticated additional smart security alarm systems, which are used in security monitoring centres for security management, and which can provide a lot of important information [
30].
The world trend of recent years is the process of globalization, and it is no different in the field of security and security systems. This trend provides new approaches, possibilities, and above all the effort to integrate individual types of security. Currently, add-on systems of the Physical Security Information Management (PSIM) category are among the most advanced and sophisticated smart security alarm systems on the market. They are suitable for large-scale applications with a significant number of integrated physical, operational, and cyber security subsystems [
31]. Add-on and very advanced analytical systems for cyber security include systems of the category Security Information and Event Management (SIEM). The mentioned systems integrate a few subsystems from which they receive data. They analyse, correlate, evaluate and transform these data into meaningful information that can be effectively used in resilience assessment [
32].
In the previous part of the text, there was a logical division of penalty factors into static and dynamic factors. This division took into account partial security and therefore physical, cyber and operational as well as converged security. Thanks to the static penalty factors and the subsequent application of the resilience assessment algorithm, the immediate value of the resilience of the protected asset can be determined. This value corresponds to the immediate level of security and the asset's ability to withstand the manifestation of a specific risk. Data from technological means do not affect static penalty factors, and therefore it is not necessary to use technological means to determine resilience, apart from the program itself, which computed resilience. Static penalty factors are thus manifested during the introduction of means for assessing the resilience of the protected asset or in regular iterations, when new risks and newly created measures are evaluated. Therefore, if a resilience assessment system is deployed, for example, for a protected asset of a railway station, it is necessary to use the existing risk analysis of the object or to carry out a security audit so that individual penalties can be applied in relation to the risk. In this phase, as part of the resilience assessment, it is decided, for example, whether an evacuation plan is created for the railway station or whether one of the physical security technical protection systems protects it [
33].
If a resilience assessment is to be effective and meaningful, resilience must be addressed over time, and if, for example, smoke is detected in a railway station and the electronic fire signalization system raises an alarm, there must be some reduction in resilience. In the event of the occurrence of this type of alarm, the relevance of this alarm must be assessed. The response to the event and overall resilience then depend on the relevance of the alarm. The relevance of an alarm can be confirmed based on the correlation of multiple events. For example, if a fire in a building is spreading, information comes from other fire detectors in the building, and it is therefore evident that it is not a false alarm. Or the relevance is verified by the operator based on the view from the camera or by the service in the location. For that reason, dynamic penalty factors have been introduced, which are linked to data from technological means and thus enable the resilience to be reduced according to how the situation develops over time. In the event of such a serious event as a fire, there is a cascading effect and a link to other areas of security - for example, the failure of operational technologies, information systems, disruption of mechanical prevention systems and other means to ensure the security/safety and operation of the organization. For that reason, additional related dynamic physical, cyber, and operational security penalty factors are applied that affect the overall converged security resilience [
34].
In order for resilience to be reduced using dynamic penalty factors, information about which dynamic penalty factor is to be applied must be transferred to the software module for resilience assessment. For that reason, it is essential to find suitable means that will provide this information. Resilience assessment over time has two approaches:
Continuous resilience reduction based on the resilience recomputation when applying individual dynamic penalty factors (for example, at each alarm from individual fire signalization);
Leap resilience reduction based on an already assessed and categorized event with a certain severity, for example "High" or "Critical", possibly based on sub-events that are related to the occurrence of this event, for example "Outage of information passenger system", "Radio outage", etc.
In the case of continuous resilience reduction, a large amount of data is processed, which is not suitable to be left to the software for the resilience assessment. Superstructure security systems of a higher category, i.e. PSIM or SIEM, are intended for mass processing of data, and their use is therefore very effective for processing and assessing data from subsystems and subsequent linking to dynamic penalty factors [
35].
2.3.1. PSIM systems
Systems of the PSIM category are add-on information security systems that enable the integration of a few diverse security systems and sensors, information systems and specialized business systems from different manufacturers under a unified operational view. Incoming data from various sources correlates with each other, determines their meaning and optimizes the speed of response to emerging situations [
36]. This can be a crisis, a security event (incident) or a solution to technological malfunctions and routine activities. Crises occur rarely. Security events can occur several times a week or even daily depending on the type of organization or industry in which the system is deployed. Solving technological malfunctions and routine activities is the order of the day. The goal of PSIM systems is to ensure the continuity of the activity of the given organization or segment in which they are applied.
When dealing with security incidents, timely information of all security forces and stakeholders plays a vital role. If information spreads quickly, dispatchers can reduce the time it takes to get an incident under control and reduce the time it takes to resolve it. Among the first questions when a security incident occurs is “What happened? Where did it happen? How should I react to that?".
And it is to these questions that PSIM systems answer. They correlate information from various security systems and sensors, including operational information, which they interpret in real time on clear map bases, display relevant cameras and thus provide a better overview of the current situation. They filter redundant information and thus create a comprehensive overview for an effective response. Individual malfunctions, security events or crises then have pre-prepared scenarios in the system that enable the system to react automatically, while operators are assigned specific tasks that help manage the given situation. Comprehensive situation management detailed reporting and retrospective analysis of security situations and routine activities is ensured. The
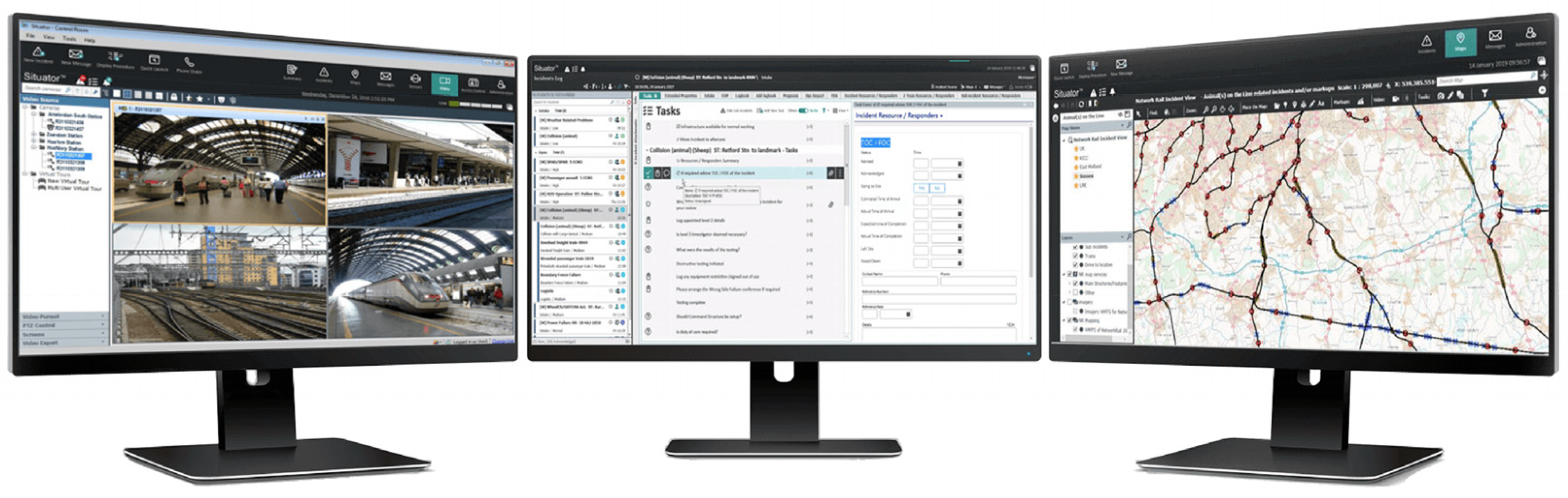
Figure 2 shows the workplace of a security dispatcher who uses the PSIM system.
The most important part of the systems of the PSIM category is the correlation core, which makes it possible to compare information from different integrated sources. A simple example can be a situation where it is necessary to respond to an event only at the moment when several sensors from different security systems report an alarm for a specific period of time at the same time. Before this defined time elapses, the alarm system displays but does not attach importance to them in the form of a security event and does not burden the operator. A security event occurs only when the conditions are met. Systems in this category respond to the needs of organizations where lower category systems are not sufficient and a more robust solution is needed.
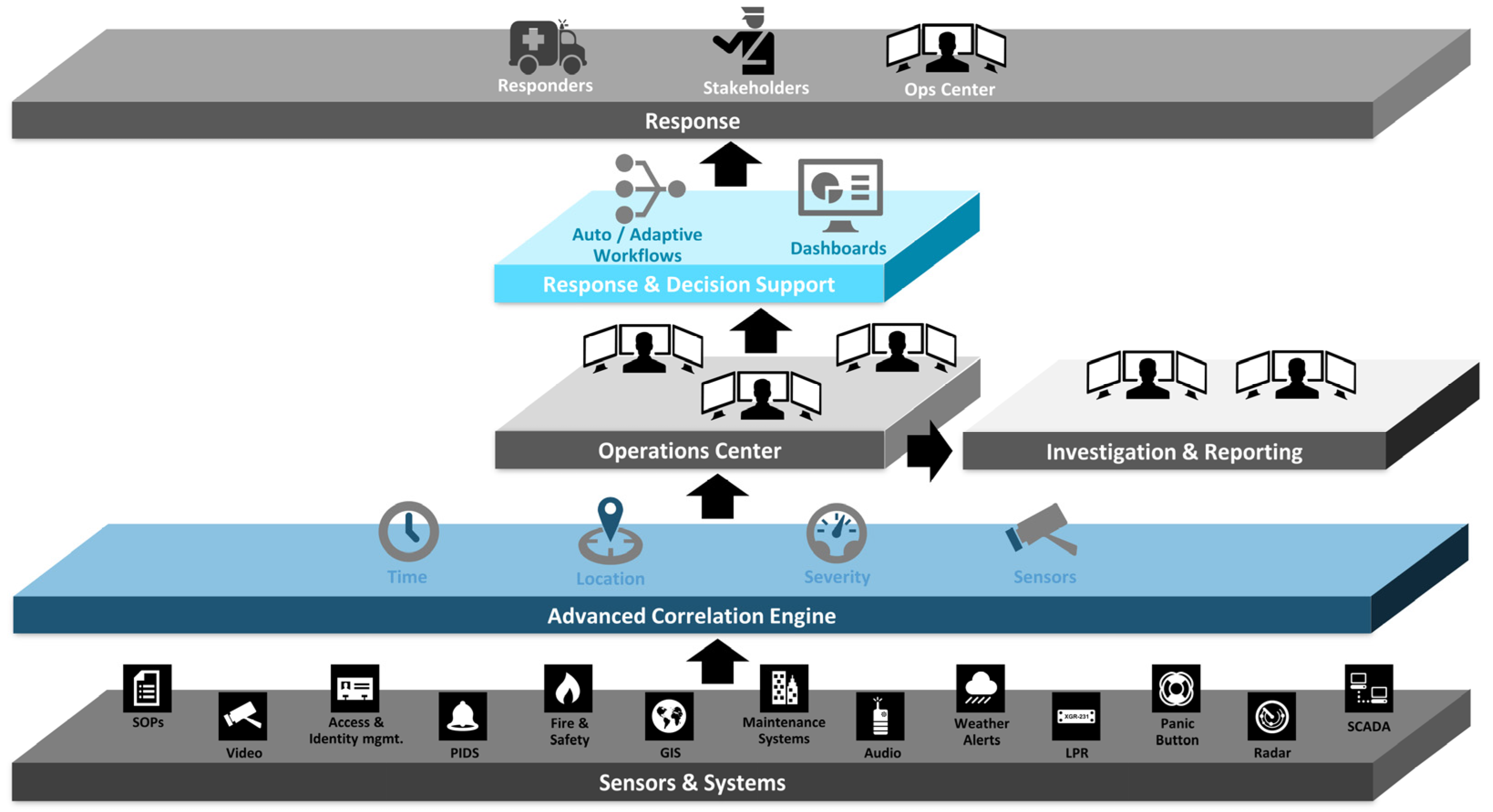
As can be seen in the
Figure 3, data from embedded technologies comes into the correlation core, where it is assigned attributes such as time, location, data type (such as a sensor-triggered alarm), and priority. On the basis of data correlation (e.g. an alarm from a camera system and a simultaneous alarm from a fire system), pre-prepared workflows (scenarios) are triggered. Workflow, in the context of PSIM systems, is a set of automatic interrelated activities in which PSIM uses pre-defined procedures. The operator whose task it is to solve the problem interprets meaningful information at the security workplace. Alternatively, it is possible for the system to assess the information independently, react using automatic operations, and not burden the operator. This results in an effective response to the given situation and the reaction time is significantly reduced. All system and operator steps are available for audit or investigation of unsatisfactorily resolved security events.
The PSIM system assess security situations from a global perspective based on the correlation of data obtained from diverse systems. It puts this data into context and starts automatic operations and workflows based on it. This is a diametrical difference compared to earlier approaches, when the system only interpreted the raw data from the subsystem to the operator without any context. It was then up to the operator to interpret the data for informational value.
The input contains disparate data, which are normalized and correlated in the next step. Using situational analysis, they are assigned to procedures that trigger appropriate user workflows (scenarios) – operators are shown relevant maps, cameras, work procedures and perform automatic operations using supporting decision-making systems. All these activities provide operators with a comprehensive overview of the situation, the so-called Common Operational Picture (COP) for the needs of incident resolution.
The aforementioned workflows represent the capital I of the PSIM system - "Information". All work manuals, procedures, guidelines and corporate regulations can be implemented into the system using clear workflows. In the event of an emergency, the operator can fully concentrate on solving partial tasks, as the system will offer clear work procedures. The system then enables overall archiving of the incident resolution process, both for evidentiary material and for the need for retrospective control and streamlining of processes and maintaining the continuity of the organization's activities. It ensures that information reaches the right people at the right time and that information is regularly updated. In this way, COP is obtained not only by all clients of the system (dispatch workplaces, field workers), but also by other interest groups (Integrated rescue system, police, superior components, service components, maintenance workers, companies, etc.) who are informed using data messages to their own information systems or obtain information by phone, email, SMS or through specialized early notification systems.
Without the use of the PSIM system, the prediction of security events is almost zero or is solved at the tactical level, where measures are built in advance to minimize the probability of exposure to the threat to the lowest possible level. Prediction in this case is a situation where the system is able to draw attention to any deviations from the normal state. For example, on the basis of information about the weather at approaching tropical temperatures, it is possible to predict the occurrence of a fire, overheating of a certain technology, increased workload of employees, the possible possibility of an accident, etc.
The system also draws on knowledge from the past. A number of events can be eliminated thanks to the system. If an incident occurs, chaos, misinformation can occur without the use of superstructure systems, and it takes some time before at least a certain consistent idea of the situation is formed. In contrast, the PSIM system will provide all available information, start the appropriate workflow and, thanks to this, make this process more efficient and significantly reduce its duration. It also provides sophisticated tools for managing and managing the situation. After closing a security event, it generates detailed reports, every step is recorded, and no additional resources need to be spent to investigate the event.
2.3.2. PSIM systems and data sources for smart security alarm systems
Systems that provide data sources for smart security alarm systems and therefore can be integrated under PSIM can be categorized into security systems and sensors, localization system, graphic systems, information and database systems, control and operational systems, business systems and communication systems [
35]. In order to effectively connect subsystems, the PSIM system must address and connect all supervised systems and devices into a unified platform, which is then processed by the system's control core. This method of integration is usually provided with the help of appropriate software interfaces.
Security systems
Basic security systems that can be integrated into PSIM systems include the following [
38]:
VSS with video analysis and specialized video analysis tools - means for monitoring events in real time using cameras including the ability to detect different types of events;
I&HAS – I&HAS control panels, evaluating various types of motion, shock, contact, linear light, radio types of intrusion detectors and other types of means to ensure comprehensive technical protection against unauthorized entry into objects and systems for triggering an intentional emergency alarm;
ACS – systems for controlling access to objects, using various types of identification technologies, such as magnetic cards, Radio Frequency IDentification (RFID) chips and biometric data. Access control systems may be used even for location determination;
EFS – electrical fire signalization control panels evaluating and controlling various types of fire detectors and devices;
Perimeter systems – perimeter protection systems in the form of detection cables, infrared barriers, microwave barriers, etc. with specialized software for perimeter detection;
Radar and sonar systems (as part of I&HAS) – systems for searching and determining the location of various types of assets (e.g. people and means of transport) with specialized software.
Location systems
Localization systems are an important means for the PSIM system to be able to interpret the position of individual forces and resources (persons, vehicles, etc.) on map data. The localization systems that are commonly integrated into PSIM can be divided into [
38]:
Systems for external localization – systems based on GPS;
Systems for localization inside the building – systems based on the technology of active RFID tags and suitably placed fixed or mobile RFID readers or radio localization systems.
Graphics systems
All the outputs from the integrated subsystems are interpreted on map data in the form of a map visualization platform. The map visualization platform can be interpreted using [
38]:
Geographic Information Systems (GIS) - sophisticated systems that work with spatial data and which make it possible to locate all entities of the PSIM system (assets, sensors, available forces and resources) on map bases;
Computer Aided Design (CAD) – project drawings of buildings of various types;
vector / raster graphics – map materials in the form of vector or raster graphics;
3D – some types of PSIM systems also work with 3D models for the presentation of graphic materials.
Database systems
The PSIM system enables integration with various types of corporate and specialized information and database systems according to the segment in which the PSIM system is implemented. The system makes it possible to draw data from these information and database systems, evaluate them and write them back. Bidirectional communication between PSIM systems and these types of subsystems is therefore ensured.
Control and operating systems
PSIM systems should not primarily interfere with control systems. Only in exceptional cases, when dealing with specific security events that immediately require this intervention. However, they can integrate data outputs from control systems and correlate that data with other outputs, evaluate them and create effective responses based on that. A typical example of control systems is Supervisory Control and Data Acquisition (SCADA) - specialized systems for supervision, control, and data collection with use, for example, in energy and other industries. Another segment is operational systems such as measurement and regulation, systems in buildings, elevators, etc. In operational systems, communication is usually two-way.
Enterprise systems
Enterprise systems are specific systems with which PSIM systems can have integrated two-way communication. In this way, it is possible to contribute to ensuring the continuity of the activity of the given organization. An example can be integration with the corporate Service desk system, which primarily serves as a means of solving technical failures. If the PSIM system detects a technical failure of a specific technology, it automatically creates a dynamic form with information about the failure and sends it to the Service Desk system. The latter takes responsibility for solving the problem and, after solving it, informs the PSIM system about the solution of the matter. The PSIM system is therefore a means for solving the clearance of the malfunction, but the Service desk fulfilled the greater part of it. PSIM systems commonly integrate business systems such as Enterprise Resource Planning (ERP), Customer Relationship Management (CRM), help desk / service desk, etc.
Communication systems
Communication systems represent an important element for PSIM systems, as timely information of interest groups plays an important role. PSIM systems can be connected to various communication systems, such as [
35]:
early notification systems – ensure mass notification of people by means of calls or SMS, providing functionalities such as Text to Speech or Speech to Text, etc.;
radio stations – they enable the playback of predefined announcements to certain branches of the system and ensure a certain degree of automation in the distribution of information in the locality;
SMS gateways – systems for sending SMS;
IP telephones and dispatch terminals – these devices enable the control workplace to initiate telephone calls directly from the PSIM system workplace and create complex conferences, ensure communication with radio resources, etc.
It makes sense to integrate all the above subsystems from the point of view of effective security management in the organization if the organization is equipped with them. Each subsystem provides a series of data that the PSIM system logically processes and uses. Not all data are suitable for resilience assessment. Therefore, in the last subsection of this article, the options of selected subsystems and examples of important information for the resilience assessment are presented.
2.3.3. SIEM systems
One of the subsystems of PSIM can be systems of the SIEM category, the issues of which are presented in this subsection. With this integration, PSIM systems can be upgraded to systems for converged security, the so-called Converged Security and Information Management System (CSIM). This is a new, modern approach to security management, where emphasis is placed on the interconnectedness of individual types of security, mainly physical, operational, and cyber. From the point of view of resilience assessment and the link to dynamic penalty factors, it is possible to use these systems independently, but it depends on the concept of each organization.
SIEM systems are superstructure security systems in the field of cyber security. It is therefore not a clearly defined protection functionality, such as an antivirus or firewall, but a system that detects intrusions, warns of possible problems and collects information that gives ICT administrators a comprehensive overview about the current situation. In real time, these systems can analyse both the logs themselves and data from various applications, e.g. Intrusion Prevention Systems (IPS) or Intrusion Detection Systems (IDS), as well as from firewalls or switches. A comprehensive overview makes it possible to put individual events in a logical context and create models of relevant correlations. Today's networks tend to be quite heterogeneous, and although individual elements (from different manufacturers) generate reports about their operation, these reports are usually available in different formats and need to be unified. The unified overview provided by these systems significantly simplifies the following evaluation and other follow-up actions, e.g. early warning, security audit [
39].
The main objectives of SIEM systems include:
more flexible and faster response to any anomalies and threats in the ICT infrastructure;
more successful detection of these anomalies and attacks;
streamlining of ICT infrastructure management.
Systems in the SIEM category are relatively new technologies. The security management of information and events in the ICT structure arose as a natural response to the ever-increasing risk of threats within the cyber environment.
The mentioned SIEM technology originally arose from two already established and well-known technologies:
Security Information Management (SIM) - technology dealing with the long-term storage of events, their analysis and reporting of problems;
Security Event Management (SEM) – technology dealing with infrastructure monitoring, event correlations and creating alarms in real time.
The merger of the two technologies was mainly due to the increasing costs of each of them and the demands on the complexity of the solution.
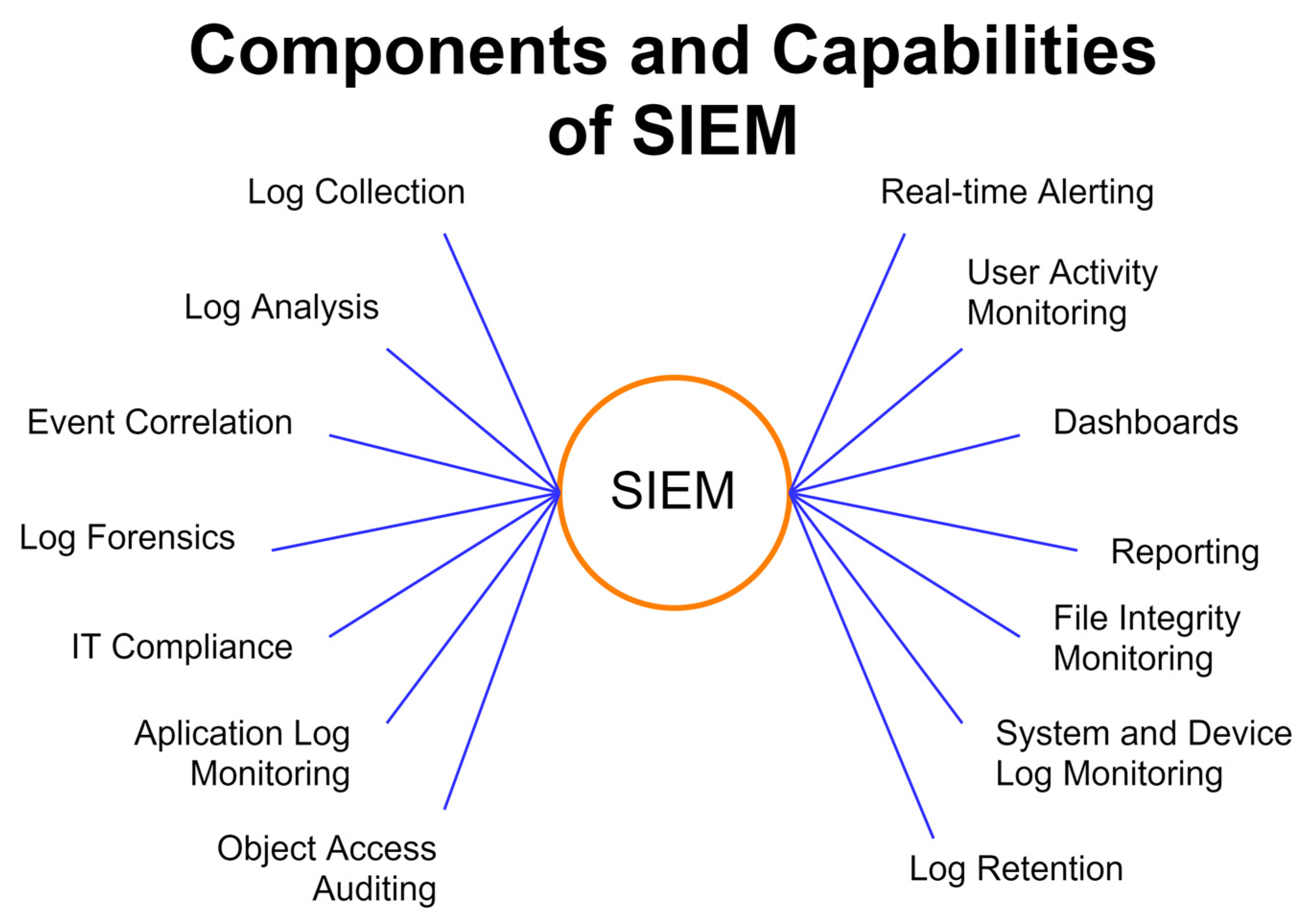
Therefore, SIEM systems provide the possibility of monitoring, storing, and managing security events represented by log records that are collected from defined devices located in the ICT infrastructure of the organization. Using analytical functions, SIEM can identify security threats that can become the basis for security incidents. The graphical interface of SIEM makes it possible to centrally assess events from many heterogeneous sources, among which we can include operating, database, application and network systems and devices. SIEM products also include archiving modules that can be used to store collected logs for forensic analysis purposes. In
Figure 4 shows an example of logs from individual ICT systems, which the SIEM system analyses, assess, and categorizes based on its own algorithms.
With the help of SIEM systems, organizations can also make conceptual decisions about the further development of their infrastructure, deployment of new tools, applications, etc. Information from SIEM systems therefore represents an important basis for the organization's management when deciding on future investments.