Introduction to Cryptography
Cryptography is derived from the Ancient Greek words kryptós "hidden, secret"; and γράφειν "to write", or -λογία -logia, "study", implying it is the study of secure and hidden writing. It is fundamentally the science of encoding and decoding information to protect it from unauthorised access. Cryptography is crucial for secure communication, especially in the presence of malicious third parties, known as adversaries. It involves two main processes: encryption, where data is converted into a secret code, and decryption, where the secret code is converted back to its original form (Adomey, n.d.). This field has evolved to include a variety of techniques and types, such as Secret Key Cryptography, which ensures the confidentiality, integrity, and authenticity of information.
Three Key Points on Why Cryptography is not Cybersecurity
In modern-day computing systems, cryptography is predominately used for security, resulting in a common misperception that cryptography is cybersecurity. In this paper, we will discuss and explore a different perspective of cryptography related to the less-known use cases of cryptography. Before we engage in that discussion, we first need to understand the three key points that explain how even the most sophisticated cryptography can be pretty useless if cybersecurity is not conducted as a holistic solution to cyber risk management.
First, the strength of cryptographic algorithms is directly proportional to the difficulty of mathematical problems they pose. For instance, the RSA public-key encryption algorithm (Rivest et al., 1978) is founded on the challenge of factoring the product of two large prime numbers. If intruders solve this mathematical hurdle, they can access the encrypted data. With the new types of quantum computers expected in 5 to 15 years, the current mathematical cryptography would be rendered useless (Shor, 1997). A large-scale quantum computer could easily crack the current cryptographic algorithms. The National Institute of Standards and Technology (NIST) is already looking at how to prevent this, (NIST, 2022, 2023a, 2023b) but this is just one example of how cryptography is not a silver bullet for cybersecurity risks.
Secondly, proper implementation of cryptographic algorithms is paramount to guarantee security. Symmetric algorithms, such as AES (Daemen and Rijmen, 2003) and Blowfish, demand that the secret key remains confidential. Any vulnerability in the implementation, such as insecure key storage or transmission, could expose the secret key, thereby putting the security of the encrypted data at risk.
Thirdly, securing cryptographic keys is paramount in ensuring the security and privacy of cryptographic systems. Private-key cryptography necessitates that the sender and receiver possess the same secret key for secure communication. Yet, unauthorised individuals can decrypt sensitive information if this key is compromised due to inadequate security measures.
Cryptography, Romance, and War
Throughout history, cryptography has been a crucial tool for encoding messages. It has played a particularly important role during times of war and conflict. This paper explores the intricate connection between cryptography, romance, and war. It examines the way encrypted communication has facilitated love in chaotic battlefields.
Throughout history, cryptography has been used in warfare to ensure secure communication and safeguard confidential information from being intercepted by the enemy. A prominent example of cryptography being employed during World War II is highlighted in novels like Neal Stephenson’s "Cryptonomicon" (Stephenson, 1999), which emphasises the significance of cryptography in modern-day as well as wartime scenarios.
Cryptography, although commonly associated with war and conflict, has also been intertwined with the subject of romance. One noteworthy example comes from the time of the French Revolution, where Marie Antoinette and Axel von Fersen exchanged encrypted letters to conceal their passionate feelings and relationship. These letters were imbued with heartfelt expressions of love and carefully guarded to protect their clandestine affair from detection.
The review section shows how cryptography, romance, and war have been portrayed in literature. Ken Follett’s "The Key to Rebecca" (Follett, 1980) is a spy novel set in World War II that follows the protagonists’ efforts to decipher a book cypher while exploring the themes of war, cryptography, and human relationships. This blending of literary themes showcases the human yearning for communication and connection, even in times of hardship and discord.
Cryptography’s influence extends far beyond its tactical advantages in times of war. It has served as a means of expressing affection and sustaining relationships during tumultuous periods. Thanks to the capacity to send covert messages, people have been able to communicate their feelings and maintain their connections despite being separated by the upheaval of battle.
Exploring cryptography’s impact on war and romance provides a nuanced understanding of its historical and cultural importance. It has played a crucial role in safeguarding communication during conflict, acted to express forbidden love, and served as a literary motif that mirrors the intricacies of human relationships. The convergence of cryptography, romance, and war highlights our innate need to bond and communicate, even when challenging situations.
Cryptography and Romance
When contemplating the subject matter of "Romance," one can acknowledge its metaphorical significance as emblematic of the complex and multifaceted nature of interpersonal romantic relationships, akin to encrypted codes. This analogy underscores the process of comprehending and unravelling one another’s innermost thoughts, emotions, and sentiments, not unlike decoding messages to unveil their veiled meanings. This comparison serves to highlight the crucial importance of clear understanding and communication in both the realm of cryptography and romantic relationships, thereby emphasising the intricate and delicate nature of both.
Alice & Bob - A Cryptographic Romance
Alice and Bob have become iconic cryptographic characters, representing two communicating entities in cryptographic algorithms and protocols. These fictional characters were created to help simplify the complex concepts of cryptology by acting as metaphors to explain the dynamics of secure communication. While their existence is theoretical, their interactions have been useful in demonstrating the essence of cryptographic systems.
Alice and Bob have been introduced to the world of cryptography in order to simplify the complexities of cryptographic research. In cryptographic communications, they are the representative sender and receiver, providing a concrete context for abstract cryptographic principles. Their creation has resulted in a significant change in the communication and understanding of cryptographic concepts, making the field more accessible to both researchers and enthusiasts alike.
In the world of cryptography, Eve is often portrayed as an eavesdropper who represents the potential threats and vulnerabilities in communication systems. Eve’s character is passive and submissive, lurking in the shadows to intercept and decipher messages between Alice and Bob. The inclusion of Eve in the cryptographic dialogue highlights the significance of safeguarding communications from unauthorised access, while also underlining the ongoing tension between privacy and intrusion.
The dynamic between Alice and Bob in the cryptographic realm is often compared to a romantic dance. Their secure message exchange is akin to hushed whispers between lovers, shrouded in layers of secrecy. However, the presence of Eve adds an alluring element of danger to their conversations. To keep her from intercepting their communication, Alice and Bob utilise complex cryptographic techniques. This dance of concealed messages and private chats highlights the connection between cryptography and romance, underscoring the human desire for intimacy and closeness in a world fraught with risks.
Within the educational aspects of cryptography, Alice and Bob serve as crucial personas, adding a human touch to a discipline that can often seem detached and numerical. Their communication and interactions illustrate the essence of human connection, emphasising the importance of safeguarding these connections from potential threats. As their exchanges reveal, the human desire for privacy and security is a driving force behind the creation and utilisation of cryptographic systems, and their conversations provide a poignant reminder of this innate inclination.
The enduring legacy of Alice and Bob lies in their ability to humanise the abstract world of cryptography. They have become the face of countless cryptographic scenarios, elucidating complex concepts through their interactions. The romantic metaphor embedded in their communications has enriched the narrative of cryptography, blending the logical with the emotional, the technical with the personal. Their enduring presence in cryptographic discourse continues to inspire and enlighten, fostering a deeper understanding of the importance of secure communication in the preservation of privacy and intimacy.
The most famous cryptographic couple in the world, Alice and Bob, have transcended their fictional existence to become enduring symbols of secure communication in the field of cryptography. Their interactions, rich in romantic metaphors, have shed light on the complexities of cryptographic systems, making them more understandable to a wider audience. The silent presence of Eve in their storey emphasises the ongoing struggle for privacy in a world filled with unseen threats. The story’s intertwining of cryptography and romance highlights the universal human desire for secure and intimate connections, emphasising the importance of cryptography in protecting the sanctity of human relationships.
Romantic Cryptography
Frank Stajano and William Harris from the University of Cambridge have proposed a method for Alice and Bob to determine their mutual feelings for each other without risking any potential embarrassment. This method ensures that neither party reveals their emotions if the other does not reciprocate. Frank Stajano and William Harris delve into an intriguing concept termed as "Romantic Cryptography." (Stajano and Harris, n.d.). This concept is a metaphorical representation of secure multiparty computation, particularly focusing on the AND function. In this scenario, Alice and Bob, the archetypal characters in cryptographic narratives, are used to demonstrate a situation where two entities are trying to establish mutual feelings of love.
This unique cryptographic scenario enables both parties to determine if their feelings are mutual without disclosing their individual emotions unless they are reciprocated. It involves a secure multiparty computation of the AND function, where the participants collaborate to generate the AND result, but without revealing the input bit contributed by the other party, unless the outcome suggests it.
In essence, Alice and Bob collaborate to produce the result of the AND function, but they remain unaware of each other’s input bit unless the outcome reveals it. This methodology ensures that neither party has to endure an awkward situation if their sentiments are not mutual. This ground-breaking application of cryptography not only highlights the flexibility and breadth of cryptographic concepts but also incorporates a human and emotional aspect into the domain.
Cryptography and War: Cryptography Throughout the History
Across the ages, individuals have employed a variety of techniques to safeguard their messages from prying eyes. The earliest recorded instance of encryption dates to 1900 BC in ancient Egypt, where hieroglyphs were utilised to encode messages.
Throughout history, encryption has been a crucial tool in transmitting secret messages. The ancient Greeks created their own encryption device called the scytale, which involved wrapping a strip of cloth around a stick. Julius Caesar, during the Roman Empire, used encryption to cipher his letters and communications. Encryption has been widely used in military circles and proved to be an important asset in many battles. The enigma was a cipher machine utilised by Nazi Germany’s military command to encode strategic messages before and during World War II. In the United Kingdom, Alan Turing is recognised as the father of computer science, honouring his significant contributions to the field.
Ancient Egypt - The Use of ’hieroglyph’
The practice of cryptography, which entails the encryption of messages, has played a significant role in human history, particularly in times of strife and confrontation. Its origins can be traced back to approximately 1900 BC in ancient Egypt, where it was employed as a vital means of safeguarding and conveying covert messages. The Egyptians, who were known for their advanced writing system, utilised non-standard hieroglyphs to encode messages. This practice was most likely utilised to protect confidential information or to secretly transmit messages, possibly concerning military strategy or diplomatic communications.
During ancient Egyptian times, the context of war and conflict required the development of secure communication methods. Cryptography was likely essential in maintaining the security of military strategies and state secrets. This allowed pharaohs and military leaders to communicate without fear of interception by adversaries. The encrypted messages may have contained vital information about troop movements, battle plans, and alliances. All of these were crucial for gaining a strategic advantage in conflicts.
Although direct evidence is lacking, it is believed that ancient Egyptian warfare used cryptography to conceal information. The use of non-standard hieroglyphs indicates a deliberate effort to keep messages secret. This practice of information concealment laid the foundation for developing cryptography as a scientific discipline. It reflects humanity’s need for secure communication during times of war and peace.
The significance of cryptography during ancient Egypt highlights its importance as a safeguard for confidential information and a tool for undercover activities. It formed a critical part of the strategic arsenal of the ancient Egyptian civilisation, enabling the secure transfer of sensitive data and playing a key role in shaping military and political landscapes. The importance of cryptography in ancient Egypt highlights its dual function as a safeguard of confidential information and an enabler of clandestine activities. It played a crucial role in the strategic arsenal of the ancient Egyptians, ensuring the safe exchange of sensitive data and influencing the development of military and political strategies.
Ancient Greece – The Scytale
The ancient Greeks used a scytale, in which the person sending a message wound a strip of cloth around a stick.
During the time of ancient Greece, the Scytale was a coveted cryptographic device that played a pivotal role in maintaining secure communication. It functions as a transposition cipher by enveloping a strip of parchment around a cylindrical object and inscribing the message across it. Once unfurled, the parchment displays a sequence of seemingly unconnected characters that can only be decoded with a cylinder of matching dimensions. Despite its apparent simplicity, the Scytale remains a remarkably ingenious and successful encryption technique that has endured through the ages.
During military operations, the Spartan military relied on the Scytale as a crucial tool to maintain the secrecy of sensitive information. This device was a testament to the Spartans’ ingenuity and dedication to ensuring the safety of their communications. The Scytale employed cryptographic principles to implement a sophisticated encryption and coding system that provided a strategic approach to secure communication during wartime. The encryption and coding system used by the Scytale made it difficult for enemies to intercept and decode sensitive military information. The Scytale was a vital tool that played a crucial role in the success of Spartan military operations, and it remains an important artefact that reflects the advanced knowledge and skills of the Spartan civilisation.
In today’s military landscape, the effectiveness of communication channels is a critical component of successful operations. To ensure the secure transmission of information, modern military strategies have come to rely on advanced cryptographic methods. Interestingly, the foundation for these methods can be traced back to an ancient tool known as the Scytale. By utilising principles of transposition and substitution ciphers, the Scytale laid the groundwork for modern cryptographic algorithms that have been instrumental in fortifying communication channels for military operations and ongoing war efforts. With the help of these advanced techniques, military personnel can communicate with confidence, knowing that their messages are secure and protected from prying eyes.
Throughout history, secure communication has been a crucial element in military operations. From ancient times to modern strategic missions, the Scytale has played a pivotal role in cryptography. This foundational tool has been utilised to ensure the confidentiality of messages being transmitted, emphasising the importance of keeping sensitive information from falling into the wrong hands. Its use has enabled military personnel to communicate without fear of interception or decoding by enemies, allowing for more effective and efficient communication in the most critical of situations.
Ancient Rome – The Caesar Cipher
The Caesar Cipher is a substitution cipher that traces its roots to Ancient Rome and is attributed to Julius Caesar. He relied on this technique to encrypt his military communications. This cryptographic method is significant since it underscores the relationship between the key and algorithm, which are fundamental principles in cryptography.
The Caesar Cipher, also known as a "shift cipher," operates by utilising a simple shifting mechanism. Each letter in the original message is replaced with a corresponding letter in the alphabet that is fixed in relation to it. The key, or shift value, determines the amount of displacement between the letters. For example, with a shift of 1, ’A’ becomes ’B,’ ’B’ becomes ’C,’ and so on. This method ensures that the original message, or plaintext, is transformed into an unintelligible string of characters known as ciphertext.
To employ the Caesar Cipher for encrypting a message, begin by selecting a shift value. Next, substitute each letter in the plaintext with the letter located at the corresponding position in the alphabet, based on the shift value. This procedure will encode the original message, ensuring confidentiality from unintended recipients. Nevertheless, this method is vulnerable to attacks due to its uncomplicated nature, particularly via frequency analysis. This method examines the occurrence rate of letters in the ciphertext to decipher the original message.
Deciphering is the opposite of enciphering, as it transforms the ciphertext back into its original form. To do this, it is crucial to comprehend the shift value. The inverse of the shift value replaces each letter in the ciphertext with the corresponding letter in the alphabet, revealing the original message. While seemingly straightforward, the Caesar Cipher played a pivotal role in the evolution of advanced cryptographic techniques, highlighting the indispensable role of secure communication in military tactics.
Deciphering requires undoing the enciphering process to restore the original message from the ciphertext. To achieve this, knowledge of the shift value utilised during encryption is crucial. Each letter in the ciphertext should be substituted with its corresponding letter in the alphabet positioned inversely to the shift value to uncover the original message. Though the Caesar Cipher is a basic encryption method, it paved the way for more sophisticated cryptographic techniques, underscoring the significance of secure communication in military tactics.
USA – Early Cryptography
George Washington, the first President of the United States and one of the Founding Fathers, had a keen interest in codes and ciphers. He used an alphabet code sheet to encrypt messages, ensuring secure communication when information leaks could have had catastrophic consequences. Washington’s use of such cryptographic techniques highlights the significance of secure communication channels, even in the country’s early stages of formation. It also indicates his profound understanding of information security in military and governance contexts.
During his tenure as Secretary of State under George Washington, Thomas Jefferson invented the wheel cipher - a remarkably sophisticated and secure method for encrypting and decrypting messages. The machine was an innovation for its time, utilising a series of wheels or discs to replace letters in the plaintext and create the ciphertext. Unfortunately, cryptographers were unaware of Jefferson’s ingenious cryptographic technique until it was unearthed in his papers during the 1920s. The wheel cipher exemplifies Jefferson’s ingenuity and commitment to creating secure methods of communication, highlighting the vital importance of cryptography in ensuring national security and effective governance.
The early attempts at cryptography by notable figures like George Washington and Thomas Jefferson were instrumental in the advancement of more sophisticated cryptographic techniques. Their appreciation of the importance of secure communication in military tactics and government matters has had a significant impact on the field of cryptography, highlighting its relevance and usage in various areas related to national security and management.
UK - Alan Turing and the Enigma Cipher
The Enigma Code played a significant role in World War II as it was used by the military command of Nazi Germany to encrypt strategic messages. The Allies succeeded in breaking the German "Enigma" Cipher, which was the most significant codebreaking event of the war. Alan Turing, a British scientist, is widely recognised as the "Father of Computer Science" for inventing a machine that helped break the German Enigma code. He also laid the foundation for modern computing and proposed theories on artificial intelligence. After the war, many of the first computers were designed to make or break codes. Even though the NSA was established in 1952, its work was not widely known at the time, and some people joked that the initials stood for "No Such Agency." Cryptography and cyber-security encryption were popular even before the advent of the Internet.
In the early to mid-20th century, the Enigma machine was a highly advanced ciphering tool utilised by the military command of Nazi Germany. It was instrumental in safeguarding the communications of the Nazi fleet and troops. However, the Allies successfully decoded the German "Enigma" cipher, which marked a pivotal turning point in the war. This remarkable achievement enabled the Allies to access a wealth of Morse-coded radio communications from the Axis powers, providing them with invaluable intelligence that ultimately played a decisive role in the outcome of the war.
Alan Turing is considered the forefather of computer science. He was a British scientist who made significant contributions to the field. His work during World War II led to the development of a machine that played a crucial role in breaking the German Enigma code. Turing’s innovative approach and relentless pursuit of knowledge laid the foundation for modern computing and paved the way for the development of artificial intelligence theories.
Turing’s ground-breaking ideas and inventions have profoundly impacted the realm of computer science. His invaluable contributions during the war era spurred the creation of the initial computers, which were instrumental in decoding and encoding messages. These early machines were the forerunners of the ubiquitous computing systems today, bearing testimony to Turing’s enduring legacy on technology and information processing.
Contrary to popular belief, the National Security Agency (NSA) was not founded as a secretive organisation in 1952. Nevertheless, the agency functioned covertly during that period, resulting in humorous comments that the initials represented "No Such Agency." This highlights the clandestine and confidential character of cryptography and intelligence operations during that time.
The field of cryptography has undergone significant evolution since the time of Turing, and it has become a vital aspect of cybersecurity. Encryption and secure communication principles that played a crucial role in World War II still play a significant role in protecting information in today’s digital age. Cryptographic advancements have been instrumental in establishing secure communication channels, protecting data, and preserving privacy in the increasingly interconnected world of the internet.
Encryption has been crucial for secure communication even before the internet. Throughout history, there has been a constant demand to safeguard sensitive information, leading to the development of various methods and techniques to keep communications confidential. From the Enigma machine to modern cryptographic algorithms, the evolution of encryption methods indicates the ongoing pursuit of security and privacy in a constantly changing technological environment.
Alan Turing’s contributions to computer science and cryptography shall forever be etched in history. His instrumental role in breaking the Enigma cypher proved critical in securing an Allied victory during the Second World War. Furthermore, his theories have profoundly impacted the advancement of modern computing and artificial intelligence. Turing’s legacy and cryptography’s evolution underscore the paramount importance of secure communication and the relentless pursuit of knowledge and innovation, particularly during challenging times.
State of the art in Cryptography in 2023
In 2023, the Advanced Encryption Standard (AES) (Daemen and Rijmen, 2003) from the National Institute of Standards and Technology (NIST) remains a critical cryptographic algorithm. AES uses cryptographic keys of 128, 192, and 256 bits to encrypt and decrypt data in blocks of 128 bits, protecting electronic data. NIST regularly updates and improves AES, with the most recent update published on May 9, 2023, ensuring its relevance and effectiveness in an ever-changing field. AES is a state-of-the-art cryptographic solution that meets contemporary data protection and security needs, as demonstrated by its continued prominence and advancements. In this chapter, the review includes all cryptographic algorithms that are currently in use.
Symmetric vs. Asymmetric Cryptography
Symmetric encryption, also known as symmetric-key cryptography, involves using a single key to encrypt and decrypt information. The Advanced Encryption Standard (AES) is a widely recognised standard in this category and was selected by the United States National Institute of Standards and Technology (NIST) in 2000. Since 2001, it has been an official standard.
Asymmetric cryptography, also called public-key cryptography, uses two different keys: a public key for encryption that is available to everyone, and a private key for decryption that only one party has access to. The RSA cryptosystem, created in 1977, is the most popular algorithm for public-key cryptography. Although this algorithm was created in the US, in the same time, there was another secret algorithm being developed, with parallel functions (Cocks, 1973).
There are several commonly utilised algorithms for ensuring secure communication and data protection. Among them are the Digital Signature Algorithm, which uses a mathematical process to verify the authenticity of digital messages and documents, the Diffie-Hellman key exchange method, which allows two parties to agree upon a shared secret key over an insecure communication channel, and Elliptic-curve cryptography, which employs elliptic curves to generate and exchange keys for encryption and decryption. These algorithms are widely recognised for their effectiveness in ensuring digital information’s confidentiality, integrity, and authenticity.
Quantum Cryptography
Cryptography is dependent on mathematical algorithms and the complexity of computational processes to safeguard sensitive information. On the other hand, quantum cryptography is established on the principles of physics and the behaviour of quantum particles. It is anticipated that once a large-scale quantum computer is constructed, it will have the ability to break all current public-key cryptography, including those utilised in major blockchains such as EC/EdDSA, VRFs, and ZK proofs. This could lead to security breaches and the compromise of valuable data.
Quantum cryptography is a highly regarded method for securing communications and data transfer. One of its most well-known protocols is the "quantum key distribution" (QKD), which involves the transmission of random sequences of quantum bits or "qubits" between two parties (NIST, 2023b). These qubits are encoded in various physical systems, making them extremely difficult to intercept and decode. The BB84 protocol, first proposed by Bennett and Brassard in 1984 (Bennett and Brassard, 2014), is the most widely used form of QKD. Its foundation lies in the fact that quantum cryptography is believed to be impervious to decryption attempts, making it an invaluable tool for secure communication.
Public Key (PK) Cryptography
Public Key (PK) cryptography is a type of asymmetric cryptography that is widely used to ensure secure communication and facilitate various cryptographic functions. Unlike symmetric cryptography, which utilises a single key for both encryption and decryption, asymmetric cryptography utilises two separate keys: a public key and a private key. As its name suggests, the public key is made available to anyone who wishes to communicate securely with the holder of the private key. On the other hand, the private key is kept secret and is used to decrypt encrypted messages with the public key.
PK cryptography plays a vital role in ensuring secure communication in today’s digital world. It enables secure key exchange, digital signatures, and data encryption, among other functions. Some examples of use cases for PK cryptography include secure email, secure web browsing (HTTPS), secure file transfer (SFTP), and secure messaging platforms. By providing a secure and confidential means of communication between parties without requiring a shared secret key, PK cryptography is an essential tool for protecting sensitive information and ensuring privacy. Its use is particularly important in situations where data confidentiality is critical, such as in financial transactions, healthcare, and government communications.
Key Pair Generation (Public Key and Private Key)
The public and private keys have a mathematical connection that allows the public key to be generated from the private key. However, it is impossible to determine the private key from the public key using computation. This feature guarantees secure communication and prevents unauthorised access to encrypted data. The connection between the two keys relies on simple mathematical operations to perform in one direction but challenging in the other. This guarantees that even though the public key can be effortlessly obtained from the private key, determining the private key from the public key is almost impossible.
Encryption and Decryption
When a sender crafts a message intended for a recipient, it can comprise any form of data, be it a text message, file, or digital information. To safeguard the message, the sender encrypts it with the recipient’s public key. This encryption method converts the message into an unintelligible format, rendering it unreadable to anyone without access to the corresponding private key.
Upon receiving an encrypted message, the intended recipient utilises their privately held key (which is kept in the strictest of confidence) to decode the message. The private key is intricately connected to the public key through complex mathematical algorithms and has the ability to undo the encryption process. This means that as a result of the decryption process, the original message is successfully restored back to its original form, with all of its intended meaning and content preserved.
Digital Signatures
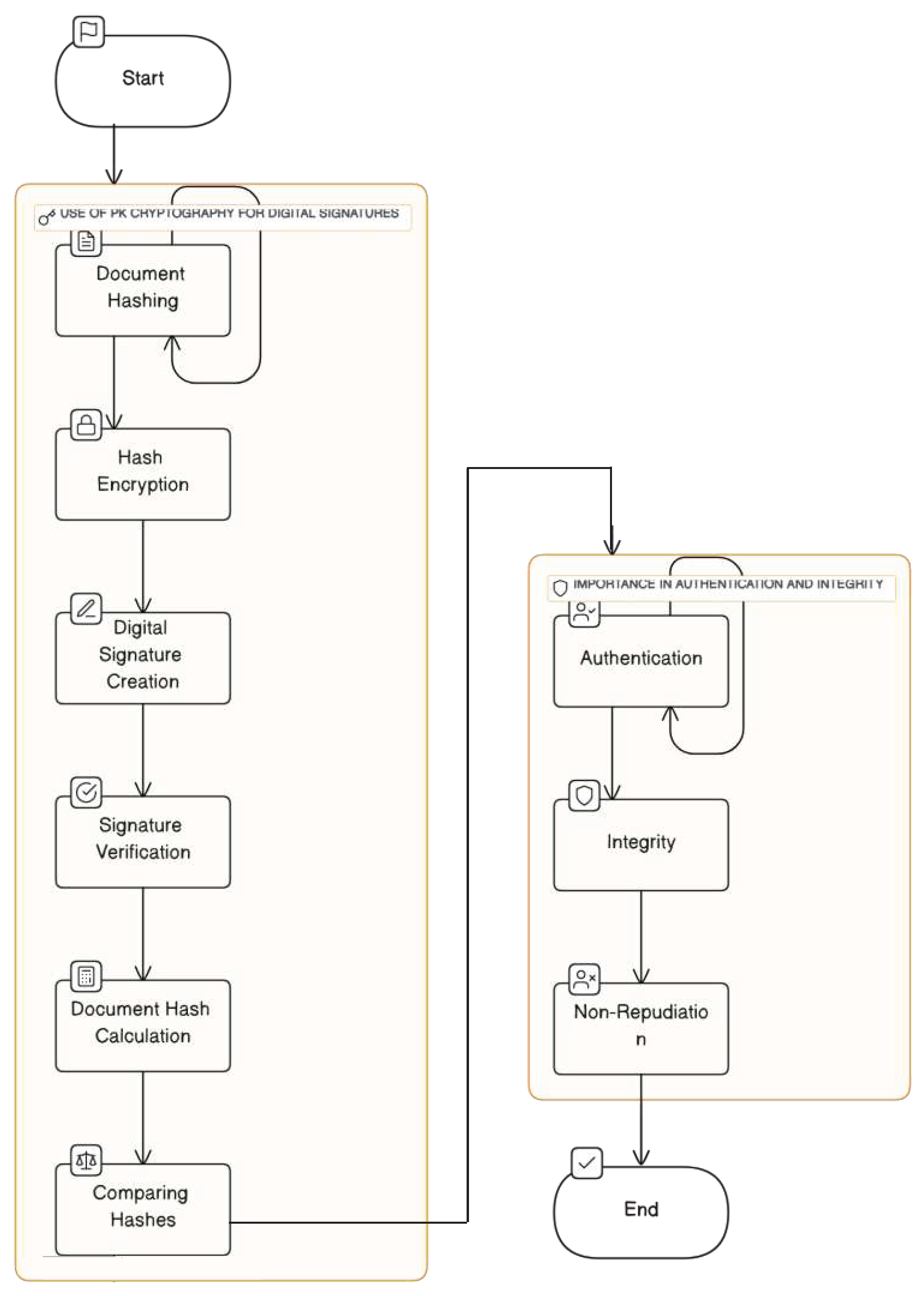
Electronic signatures entail the utilisation of Public Key (PK) cryptography to produce digital signatures, as well as the encryption of document hashes. The creation of digital signatures is a pivotal step in ensuring the authentication and integrity of documents. This is accomplished using PK cryptography to produce digital signatures, document hashing and signature verification. Furthermore, the calculation and comparison of document hashes are vital to this process. These steps collectively contribute to the non-repudiation of electronic signatures, which is crucial in guaranteeing the authenticity and trustworthiness of electronic signatures.
Here is a clear overview of Digital Signatures in
Figure 1. It highlights two important aspects: Public Key (PK) cryptography and its role in ensuring authentication and integrity. The first section of the figure explains the steps involved in using PK cryptography to create digital signatures. This includes Document Hashing, Hash Encryption, Digital Signature Creation, Signature Verification, Document Hash Calculation, and Comparing Hashes. The second section emphasises the importance of digital signatures in maintaining Authentication, Integrity, and Non-Repudiation. These are crucial elements in safeguarding digital communications and transactions.
After examining
Figure 1, it’s important to discuss how the different components of digital signatures work together. The process of creating a digital signature is careful and involves hashing and encryption to make sure that the signature is unique and secure. Verifying and comparing hashes is crucial to guarantee that the document is authentic and hasn’t been tampered with. Additionally, the figure emphasises the importance of Authentication, Integrity, and Non-Repudiation in digital signatures, highlighting their multifaceted role as not only a tool for verification but also as a means of enforcing accountability and trust in digital interactions. In today’s digital landscape, digital signatures are essential.
Key Exchange
Public key cryptography, commonly referred to as PK cryptography, is a highly secure method utilised by two parties to establish a shared secret key over an insecure communication channel. This process involves several intricate steps, starting with key generation, whereby the two parties generate a pair of mathematically related keys. One of the keys is kept private and is only known to the owner, while the other key is made public and shared with the other party involved.
The next step in the process is public key exchange, where the two parties exchange their public keys via the insecure channel. This ensures that the keys are never compromised since only the intended parties have access to the private keys. After the public key exchange, the parties proceed to encrypt their respective secret keys using the public key of the other party.
The encrypted keys are then sent back to each other over the insecure channel. The final step involves key decryption, where each party decrypts the received encrypted key using their private key. This produces a shared secret key that can be used for secure communication between the two parties.
Overall, PK cryptography guarantees secure communication between two parties, ensuring confidentiality and privacy of information shared over an insecure channel.
The process of exchanging keys through PK cryptography offers a secure way to establish a shared secret key. This enables secure communication and encryption of sensitive information. Many protocols, such as SSL/TLS for secure web browsing, SSH for secure remote access, and VPNs for secure communication over public networks, rely on this method to ensure the safety and privacy of important data.
RSA Algorithm
RSA encryption is based on the difficulty of factoring large numbers into their prime factors. A public key includes a modulus (which is a product of two large prime numbers) and an exponent. The private key also has the same modulus and a different exponent. To encrypt a message, the plaintext is raised to the power of the public exponent and then the modulus is taken. Decryption requires raising the ciphertext to the power of the private exponent and taking the modulus. This mathematical relationship guarantees that only the private key holder can decrypt the message successfully.
Elliptic Curve Cryptography (ECC)
The process of Elliptic Curve Cryptography (ECC) involves utilising the mathematical qualities of elliptic curves to establish a connection between the public and private keys. The public key is obtained from a point on the elliptic curve, while the private key is a scalar value that is randomly chosen. The ECC operations guarantee that computing the private key from the public key is an exceptionally challenging task.
Diffie-Hellman Key Exchange
The Diffie-Hellman key exchange algorithm was created by Whitfield Diffie and Martin Hellman in 1976. It is commonly used in modern encryption systems to facilitate secure communication between two parties without requiring them to pre-share a secret key. Instead, they can generate a shared secret key by performing mathematical operations on publicly exchanged information. The Diffie-Hellman key exchange’s security is based on the difficulty of the discrete logarithm problem. Even if someone intercepts the public keys exchanged between Alice and Bob, it is extremely challenging to obtain the secret numbers "a" and "b" or the shared secret key "s" based on that information only.
Blockchain Technologies
Self-executing contracts known as smart contracts have their terms of an agreement written directly into code. These contracts operate on blockchain platforms such as Ethereum and can execute actions automatically based on predefined conditions, eliminating the need for intermediaries. Smart contracts are applicable in various fields, including Decentralised Finance (DeFi), Supply Chain Management, Insurance, Real Estate, Voting Systems, and Intellectual Property Management.
Blockchain in Supply Chain Management
Smart contracts have the potential to revolutionise supply chain management, bringing about significant improvements. By streamlining and automating various processes, these contracts provide a reliable and transparent means of monitoring goods, validating transactions, and ensuring secure transfers of ownership or payments based on predetermined conditions. As a result, smart contracts can lead to increased efficiency, reduced instances of fraud, and greater transparency across the supply chain.
Blockchain’s Potential for Transparent Governance and Voting Systems
The examples listed are just a few examples of how smart contracts are applied across various industries. The versatility and automation capabilities of smart contracts make them a powerful tool for creating trust, efficiency, and transparency in a wide range of applications.
Cybersecurity and Quantum Computing Integration
Quantum-Safe Cryptography and Its Importance in Cybersecurity
As we move further into the age of quantum computing, the security of sensitive data becomes a crucial concern. The power of quantum computing has the potential to break traditional encryption methods, leaving confidential information vulnerable to malicious actors. Therefore, it is imperative that organisations take proactive measures to secure their data. This may include implementing quantum-resistant encryption techniques, such as lattice-based cryptography, and regularly updating security protocols to stay ahead of emerging threats. By prioritising data security in the age of quantum computing, organisations can protect their sensitive information and maintain the trust of their customers.
Quantum-Resistant Algorithms and Post-Quantum Cryptography
The development and standardisation of algorithms that can resist quantum computing attacks are currently in progress. Organisations like the National Institute of Standards and Technology (NIST) in the United States have started working on evaluating and standardising cryptographic algorithms that can withstand quantum computing attacks. This process involves thoroughly analysing, testing, and evaluating different candidate algorithms to determine their security, efficiency, and suitability for various applications.
Discussion
Throughout history, cryptography has played a crucial role, especially during times of war, by providing secure communication channels. From early cipher devices to complex algorithms, cryptography has progressed alongside technological advancements and the growing demand for secure communication.
During times of conflict and war, the use of cryptography has proven to be an invaluable tool for safeguarding vital information and messages from falling into the wrong hands. Over the years, the evolution of cryptography in warfare has been marked by the development of increasingly intricate methods for both constructing and deciphering codes, underscoring its pivotal role in determining the outcomes of battles.
Combining the idea of romance with cryptography provides an innovative viewpoint. With digital interactions being prevalent in today’s world, cryptography could potentially contribute to maintaining the privacy and security of romantic interactions and exchanges. In the future, cryptography’s worth in romance could be predicted by developing secure communication platforms solely aimed at encouraging sincere and confidential interactions while protecting users’ sensitive information and communications from unauthorized access and potential breaches.
The objective of this study was to encourage additional investigation and contemplation of the diverse uses of cryptography. This will help to gain a deeper comprehension of its potential to influence interactions and communications in different settings. The outcomes of this study are expected to appeal to the academic community, initiating discussion and motivating future research in the interconnected fields of cryptography, romance, and warfare. The innovative method and fresh outlook presented in this study are anticipated to act as a driving force for exploring new frontiers in cryptography research and its various applications.
Conclusion
In conclusion, the anticipated requirements associated with academic journal publication must be emphasised, and the paper’s contribution to the existing knowledge base must be expounded upon. Journals play a crucial role in disseminating novel research and ideas, and as such, they must adhere to high benchmarks of quality, originality, and valuable contributions to academic discourse. Furthermore, I would like to inform you that I will only use British English in our future discussions to ensure consistency.
This work examines the interconnections among cryptography, romance, and war. Its objective is to deepen comprehension by delving into the various applications of cryptography, transcending conventional boundaries, and examining how cryptographic technologies could potentially influence and be employed in the sphere of romance. This endeavour ultimately broadens the dialogue on cryptography. The article explored the versatility and adaptability of cryptographic techniques in detail. It blends elements of secure communication with facets of human connection and emotional resonance. Moreover, delving into the evolution of cryptography and its pivotal role in times of war enhances our understanding of its historical significance and ongoing relevance in safeguarding privacy and security.
This paper has explored various aspects of cryptography, including its connections with love and war, as well as its representation and importance in literature and cultural contexts. Cryptography, which originates from the Greek words for secure and hidden writing, is essential in understanding how information can be encoded and decoded to safeguard it from unauthorized access. Historically, cryptography has played a crucial role not only in securing communication during times of conflict but also as a means of expressing and protecting love and affection during turbulent periods. The examples of Marie Antoinette and Axel von Fersen during the French Revolution, as well as the portrayal of cryptography in novels like "The Key to Rebecca" and "Cryptonomicon," illustrate how cryptography, romance, and war intersect, reflecting humanity’s desire for communication and connection even in challenging times.
Furthermore, the paper offers a nuanced perspective on the cultural interpretations of cryptographic characters Alice and Bob, as well as their symbolic representation in cryptographic communications. Srini Parthasarathy’s proposal to reinterpret these characters in a cultural context, replacing them with Hindu mythological figures, emphasises the importance of cultural diversity in understanding cryptographic communication. The metaphorical significance of romance has been investigated to emphasise the importance of clear understanding and communication in both cryptography and romantic relationships. The enduring legacy of Alice and Bob, intertwined with romantic metaphors, has enriched the cryptography narrative, blending the logical with the emotional, and the technical with the personal, fostering a deeper understanding of the importance of secure communication in preserving privacy and intimacy.