1. Introduction
Embedded software is widely used in cell phones, TVs, and cars, and the complexity of both hardware and software has increased over time. Many tests are required for embedded systems because they are subject to many errors. For example, in the automotive industry, safety-critical automotive software requires high reliability, resiliency, and recovery. This affects its design, development, test, and maintenance. In addition, many verifications make them more time-consuming and costly. Not only testing but also strict rules are needed. Formal methods are effective for this purpose. In this paper, we also focus on model checking [
1]. The model checker in the existing C language is hardware-independent, so it is intended for ANSI-C verification [
2]. To verify an embedded system, it is necessary to construct a verification system that takes into account many hardware-dependent functions. In a program written in C, for some types of Interrupt Service Routine (ISR) the point in time of the execution is unpredictable or hard to predict. This causes problems with the verification of time constraints that embedded and safety-critical software usually has. And since each state in which an instruction is executed represents a state of each block of Control Flow Graph (CFG) or CFA, the state explosion problem occurs. B. Schlich et al. developed an interrupt handling execution reduction (IHER) [
3] algorithm to suppress the generation of these interrupts. IHER is an algorithm that prevents the interrupt handler (IH) from processing interrupts that occur at specific locations in the program. The core idea is to reduce execution with no dependencies [
3]. We will explain `dependency’ in
Section 3. If there is a dependency, it is allowed to occur, but if there is no dependency, it is not allowed to occur. In B. Schlich’s study, although he uses timers in the experiments, there is no mention of periodic timer interrupts. However, timer interrupts are often used in the construction of embedded systems. Therefore, the introduction of the concept of time can contribute to reducing not only simple event interrupts but also periodic interrupts, the so-called timer interrupts. In this paper, in order to reduce timer interrupts, we define a Timed CFA that can handle time, and propose Timed IHER.
2. Related Works
In this section, we explain the position of this research in terms of timed models and interrupt processing methods in reducing timer interrupts, based on related research.
-
B. Schlich studies a new method for verifying the assembly code of model checking software for microcontrollers [
4]. A simulator based on static analysis constructs a state space, abstracts time, handles non-determinism, and over-approximates the behavior exhibited by the actual microcontroller. On the other hand, our previous paper has developed a model checker that uses static and dynamic analysis, such as undefined values [
5]. This paper and the reference [
4] adopt different approaches as follows. In the reference, when the model checker requests a successor to a state it has not yet generated, the state space generates the successor on the fly using the simulator. In this paper, the verification system completes the state transition system and passes it to the simulator.
This article generates the entire CFG upfront. The latter is bette [
4]r and we will achieve it in the future.
B. Schlich et al. have studied IHER to reduce the number of Interrupt Handler executions [
3]. B. Schlich et al. also study various abstraction techniques based on static program analysis [
6]. In this paper, we extend this IHER.
S. Yamane and others conducted a study using IHER to enable verification using SMT solvers [
7] together with Assembly Code Block (ACB) [
8]. We focus on timer interrupt and does not use SMT solver for verification.
Matthew Kuo and others [
9] calculate the Worst-Case Response Time (WCRT) using reachability to analyze the assembly code. However, the model is different from our study, Matthew Kuo and others generate TCCFG (Timed Concurrent Control Flow Graph) by static analysis from each assembly code, but we verify microcontrollers that run on a single thread and perform model checking.
Wu Yajun [
10] defined a timed Kripke structure and verified its real-time nature. Timed Kripke structure is nondeterministic finite automaton but it is not appropriate for our study because its model does not hold the instruction element of the program. We have to control a model by the value of the program counter and the edges should hold the instruction.
R. Alur and D. L. Dill studied timed automata [
11]. Timed automaton is an extension of a finite state automaton and is a model that describes the system by both discrete event and continuous time-lapse according to state transitions. On the other hand, in this study, we develop timed CFA for the execution time of assembly program. Our study is different from timed automata. The proposed structure deals with discrete time in our study, and we use the execution time of each instruction of the assembly program in each state.
The previous study in reference [
12] reduces timer interrupts to include real-time performance. On the other hand, this study differs in that it does not consider real-time performance but defines the algorithm more concretely and conducts experiments using multiple timer interrupts in a case study.
Recently, L. Lihao et al. proposed an efficient verification of low-level embedded C software with interrupts based on partial-order coding and symbolic execution [
13]. On the other hand, this paper verifies an assembly program with an algorithm that also reduces timer interrupts based on the reduction of the number of interrupt handlers by IHER; if the method of Lihao Liang et al. is adopted, nested interrupts can be handled effectively in this paper.
3. IHER
IHER is a method developed by B.Schlich et al. to block the execution of IHs as much as possible. It is an abstraction technique based on partial order reduction [
14]. If there is no dependency between the IH and the main program, the IH’s execution is reduced by blocking the IH. The core idea of dependency is that one instruction influences the other.
For example, when an assembly instruction of IH and the main program read/write in the same memory location, the overall processing behavior of the program may change if the interrupt is blocked or not. This technique was developed to execute IH only when such behavior changes. IHER consists of the following four steps.
-
Detect dependencies between IHs
Step 1 performs when two or more IHs exist. IH depend on each other if either of the following conditions is true. Access here means both writing and reading.
one IH enables or disables the other IH,
one IH writes to a memory location accessed by the other IH, or
one IH writes to the memory location used in an atomic proposition (AP).
Examples of APs include a variable being equal to a certain value. IHs that manipulate the memory location of an AP manipulate the core of the program. So, It is therefore necessarily associated with all IHs. In other words, only one IH is mentioned, and if one IH writes the memory location used by the AP, then all IHs are dependent on each other.
-
Detect dependencies between program locations and IHs
step 2 shows the conditions under which two labels, the label and the label, are attached on locations to detect dependencies between the program and IH. An label allows the execution of an IH executed after the execution of the program instruction. On the other hand, the label denotes that there exists a dependency between that program location and an IH, and therefore, this IH needs to be executed before the instruction at that location is executed. In determining the label, we assume that program location k is a direct predecessor of program location l. Let program location k be a direct predecessor of program location l. Formally, for each , l is labeled with if one of the following conditions is satisfied:
Also, for each IH, a program location l is labeled with if one of the following conditions is satisfied.
i writes a memory location that l accessed,
l enables or disables i,
l writes a memory location that i accessed, or
l writes a memory location that is used in an AP.
-
Refine results
Step 3 performs refinement on the label. Each label is moved until one of the following conditions is satisfied.
a program location labeled with is reached,
a loop entry is found, or
a loop exit is found.
-
Label blocking locations
In the last step, all program node positions are labeled IH. At this point IH, we assign a label to any location without an label.
IHER can reduce the number of program locations where an interrupt handler (IH) may execute. In this paper, we use IHER to reduce the state space. The paper by B.Schlich proves that the model checking of CTL*-X is valid even though IHER reduces the number of program locations where the execution of an interrupt handler (IH) must be considered. Here, CTL*-X is defined as prohibiting the nexttime operator X in the CTL* formulas [
15]. In this paper, since safety is verified for assembly code using a subclass of CTL*-X, the verification is valid even if the IHER reduces the location of the assembly program.
4. Formal Model of an Assembly Program
In this paper, the assembly program is applied to CFA (Control Flow Automata) [
16] because IH can occur at every assembly instruction. In Shlich’s study [
3], IHER was explained using CFG [
17,
18], which is different from CFA. Nodes in CFA are program locations, and directed edges between nodes are instructions that execute when a control moves from the source to the destination. In this paper, since time must be calculated when dealing with timer interrupts in the static analysis, we use the execution time of instructions to calculate the time. Therefore, we define Timed CFA, which extends CFA and introduces a concept of time. While Toth et al.’s TCFA represents real number time, our time CFA represents natural number time to handle program execution time [
19]. We deal with exact program execution times, while Ermedahl et al. deal with worst-case and best-case response times [
20]. The paper by G. Hou et al. treats interrupts as randomly occurring [
21]. Our paper covers all possible interruptions.
The Timed CFA of the assembly program is defined as where
- -
L : a set of program locations,
- -
: L, and the initial location of the program,
- -
O : a finite set of instructions in main (non-interrupt),
- -
I : a finite set of executinos of interrupt handlers,
- -
T : execution times such as OT and IT of each instruction in O and I at each program location,
- -
→ : →⊆, the set of transition relations.
“execution time of each instruction in O and I” means a single natural number. Also it is a point in time since program execution started. There’s O and I within the same transition - which both O and I executed in the transition.
We consider only the fact that the execution time of interrupt handler has to be always constant. We represent branching based on data by timed CFA with branched structures.
In addition, each node is shown as follows.
, where . The assumption is that i is the number of each interrupt and j is the number of each node. is the current location of the Timed CFA, is the instruction of the program, is the execution time of the instruction in the program, is the interrupt handler, is the execution time of the interrupt handler executions, is the next location of the Timed CFA.
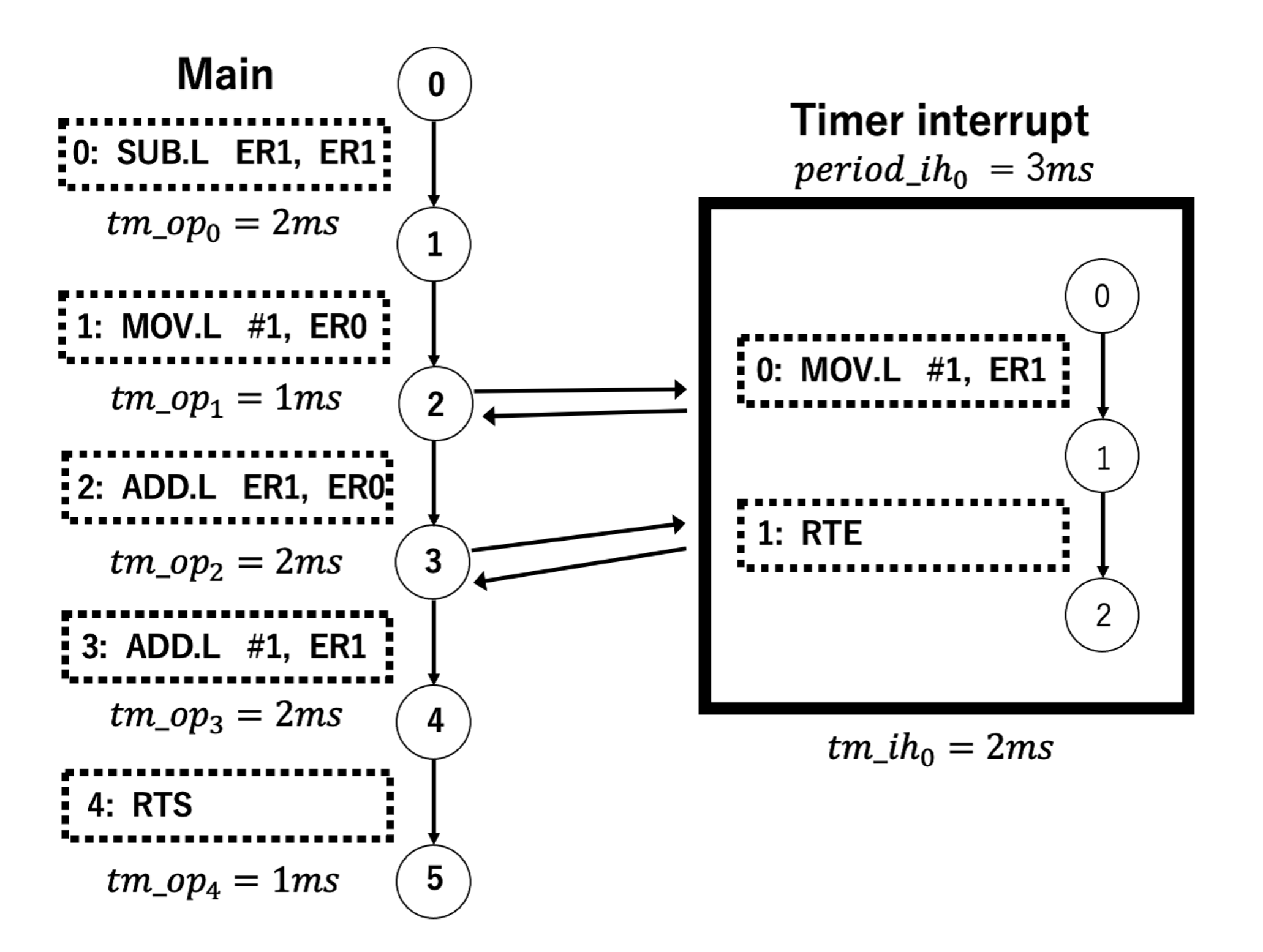
An example of Timed CFA is shown in
Figure 1. The right side of the figure represents a timer interrupt, and the
represents the timer period. The time can be accurately calculated by having each node hold the execution time of instruction. Instructions are microcontroller instructions, such as SUB.L and MOV.L. Instructions are associated with transitions.
5. Proposed Method of timed IHER
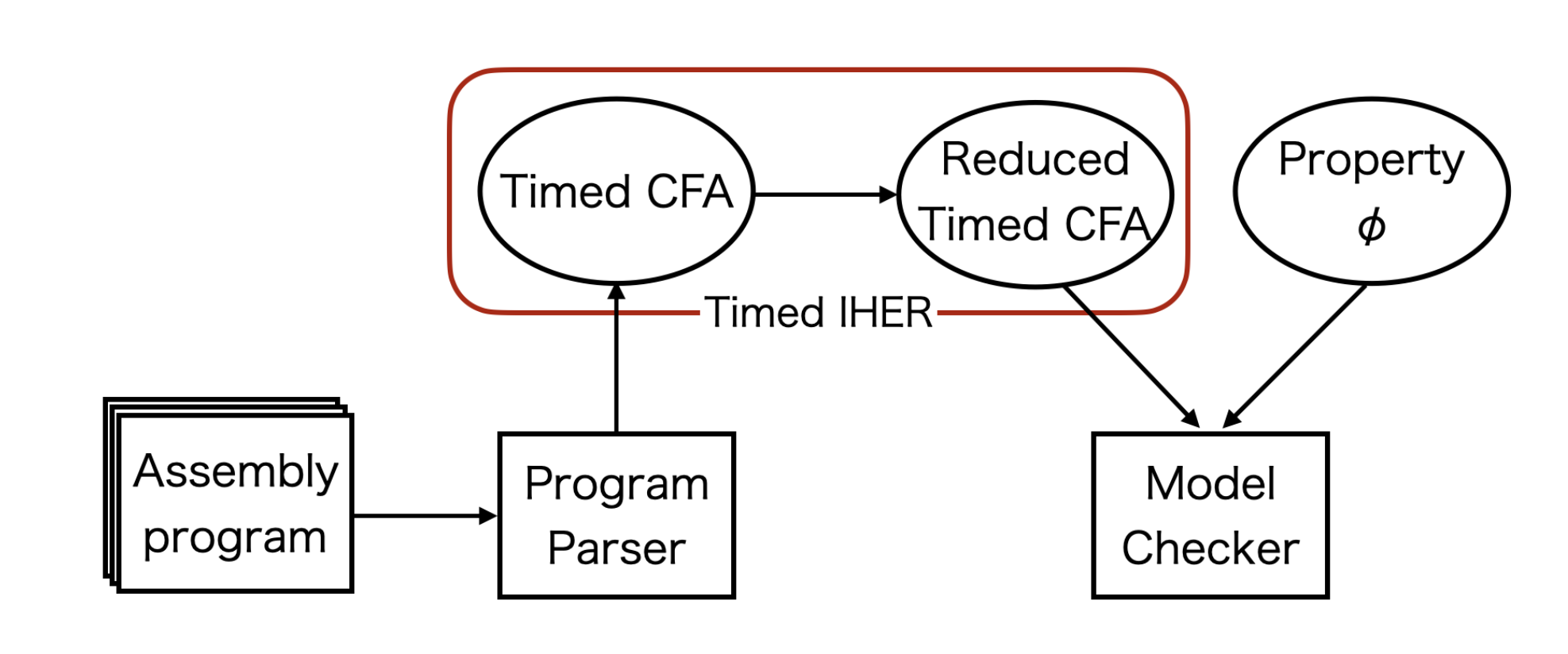
5.1. Verification system
This subsection describes the verification system used in this paper. As a premise, this study uses the assembly code corresponding to the H8/3687F microcontroller [
22] manufactured by Electronics Corporation as the verification target and conducts implementation and experiments. The details are explained in the experiment chapter. First, the assembly code is lexical analysis and syntax analysis by the lexer and parser, respectively. We use JFlex [
23], and BYACC/J [
24] for Java to develop Lexer and Parser. Next, Timed CFA is constructed from the memory map and the parsed code. Then, a static analysis called Timed IHER, the proposed method, is performed to output a Timed CFA with reduced interrupt executable locations. The Timed CFA is then input to the model checker along with the verification properties to confirm that the state space can be reduced.
Figure 2.
Verification system.
Figure 2.
Verification system.
5.2. Algorithm
The Timed IHER algorithm is described in Algorithm 1. The central idea is to suppress execution at the node of occurrence by strictly calculating the execution time not only for interrupts due to events but also for timer interrupts.
In step 1, the dependencies between interrupts are detected. This is detected under the same conditions as in existing research [
3]. If the timer interrupt is ready to be executed, it must be executed in the same way as when the dependent interrupt is executed.
In step 2, the execution time is calculated and the label is determined. For this purpose, the labels are determined for each interrupt in order of execution priority, and the cases are divided into timer interrupts and other interrupts. In the latter case, the conventional
and
are used to determine the label. In the former case, it first determines whether the total instruction execution time
exceeds the
, which is the timer period. Then, if the same conditions as for the
label are satisfied, the
is labeled with the node, and the execution time of the interrupt process is added to all
, and
is assigned to it divided by
. If
has not exceeded
, the current timer time is stored in
for use in step 3,
is assigned by subtracting it by
, and
is labeled. Also, if the same conditions for the
label are satisfied, then the node should be labeled
. Finally, the instruction time of the main program of the current node is added, and the next node is checked.
|
Algorithm 1:Timed IHER |
 |
 |
In step 3, refinements are made to the and labels. The label is moved until reaching the label, the entrance or exit of the loop. The label is moved until reaching the label, the entrance or exit of the loop. If one of the following is satisfied, we label the node with the or and x is the node number after the transition. On the other hand, in case of label, we add the execution time of the instruction of the node which has passed to including instruction of interrupt when it reaches a node satisfied with the same conditions as the label in the transition. If this exceeds the , the is labeled, and we add the execution time of the interrupt to after the transitioned node destination. In other words, even if the timer period has not been elapsed in step 2, if it is elapsed at the destination, the execution of the timer interrupt is permitted. We can accurately calculate the time by adding the execution time to the timer of label and other timer interrupt after the node after the transition, to the extent that we did not add them in step 2.
In step 4, is labeled to block interrupts at node positions other than those where no or are labeled. This is the algorithm of proposed method.
The reason for the subtraction at line 24 is to distinguish from the label and to prevent execution even though permission to execute has not been granted. For example, if both nodes before and after the label are converted to the label at step 3, and the node is actually executed, the timer at the later node may not have overflowed.
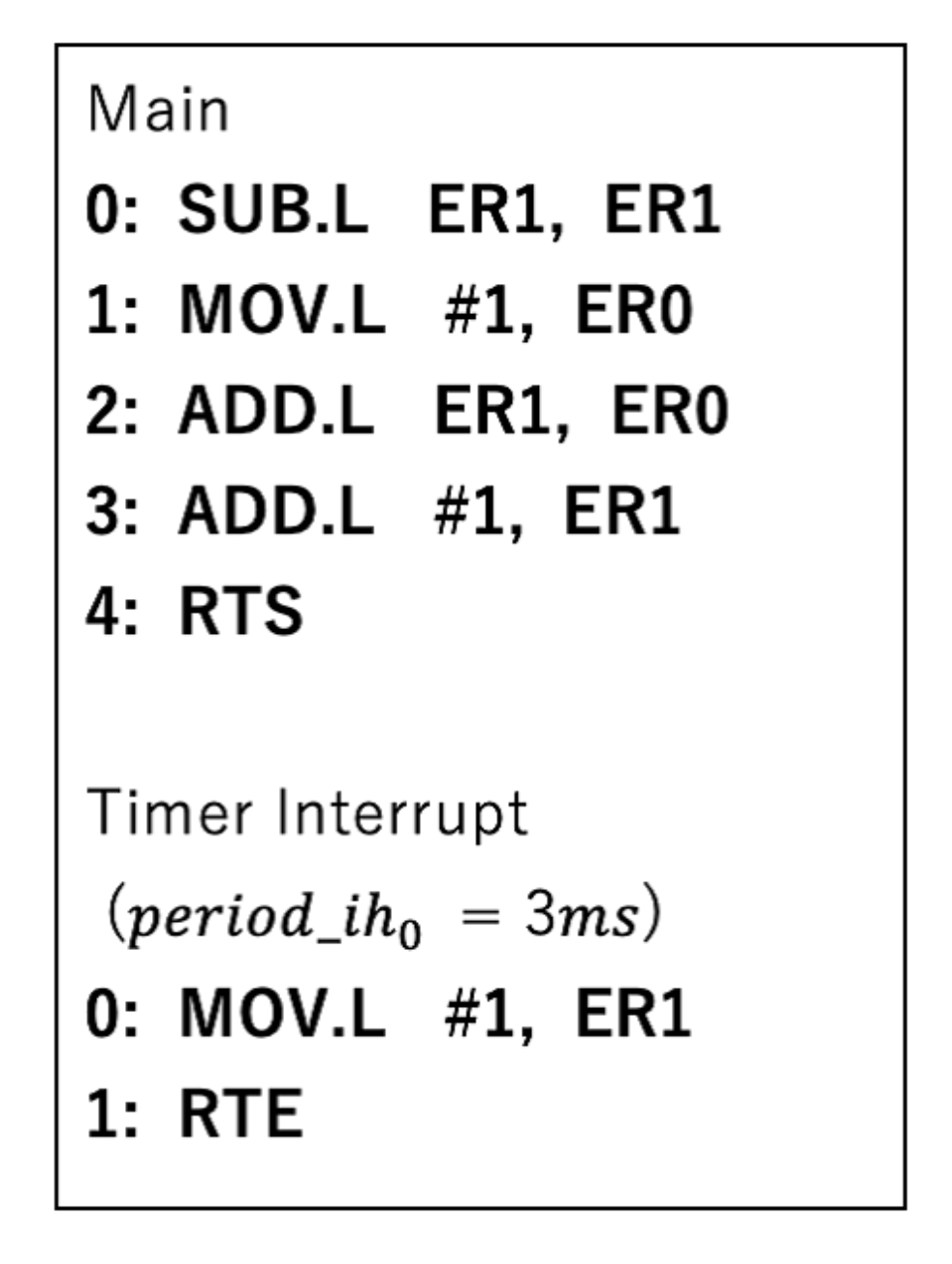
5.3. Example
To help you understand the algorithm, we will explain a simple example. We apply Timed IHER on the simple code written in
Figure 3. To simplify the time, we have one timer interrupt with a period of 3
and put the execution time of each instruction as shown in
Figure 4. Then,
label is green,
label is blue, and
label is hexagonal.
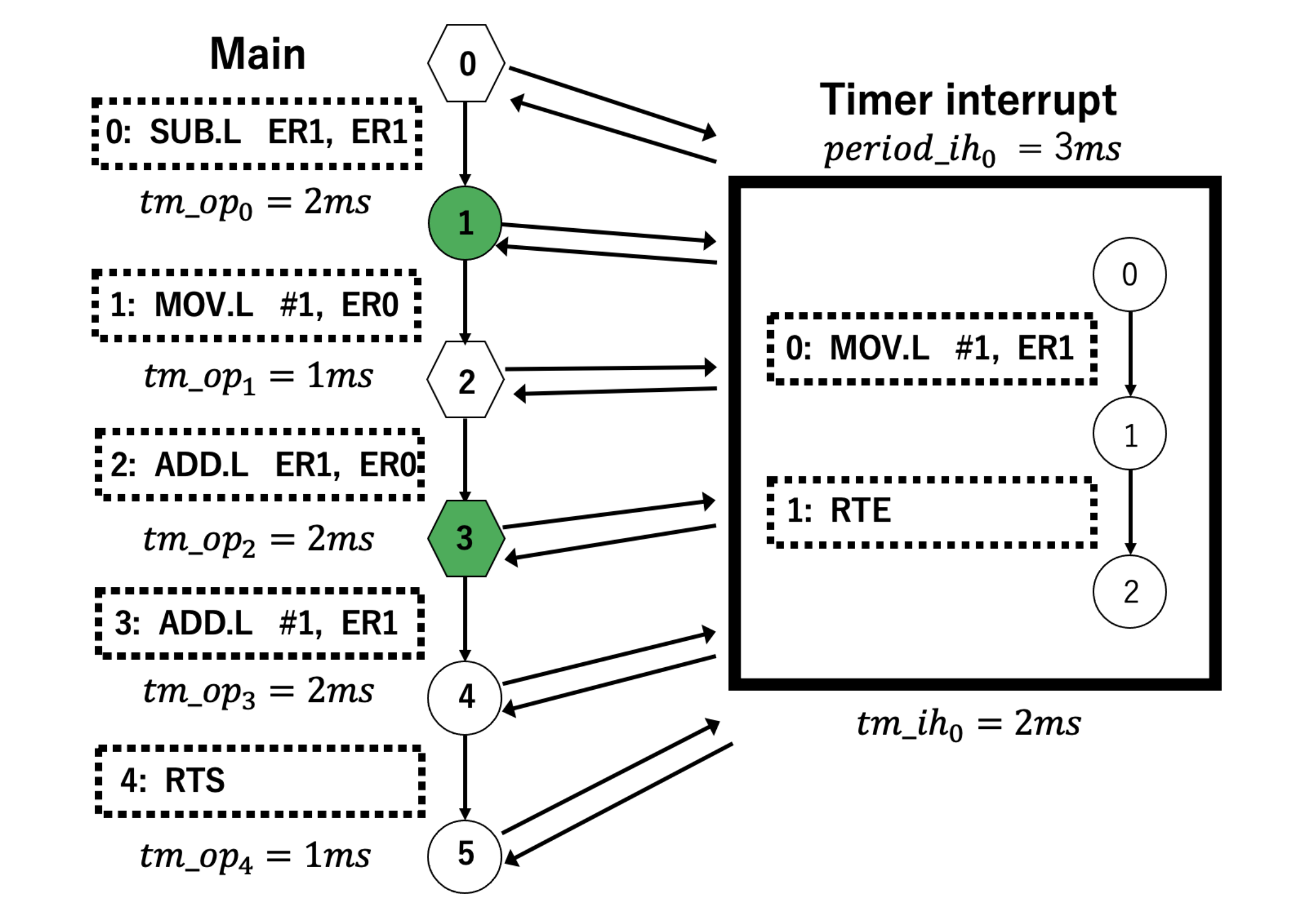
First, we perform labeling in step 2. At
, the condition of
is satisfied. At
, since
is 2
, it is less than the period and the condition of
is satisfied. Then, after
is assigned to
,
is subtracted from
. At
, condition of
is satisfied and
is 0
. At
,
is 2
, so the condition of
is satisfied as with
. Then, after assigning
to
,
is subtracted from
. The condition of
is also satisfied, so it is labeled. Since
and
don’t satisfy any of the conditions, step 2 becomes like
Figure 4.
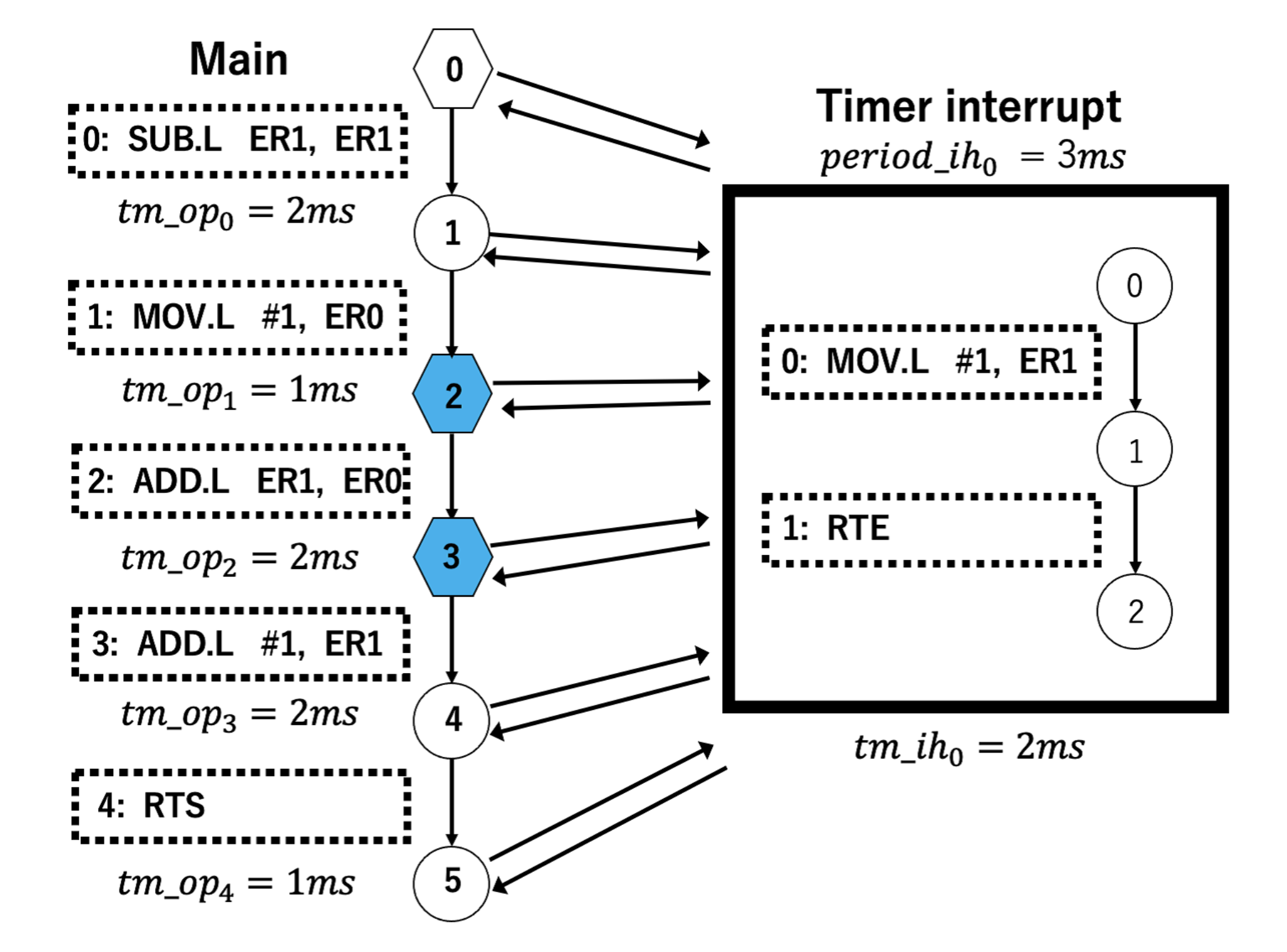
Next, we perform refinement in step 3. First,
of
is transitioned to
labeled
. At this time, the 1
of the
instruction is added to the 2
stored in
, resulting in 3
, which is equal to 3
of the timer period, allowing the execution. Therefore,
is labeled
. So, the execution time of the timer interrupt must be added to
after
. Therefore, since 2
of timer interrupt is added to 2
stored in
to get 4
and
is labeled
,
is labeled. Step 3 is shown in
Figure 5.
Finally, in step 4, the execution of the timer interrupt is suppressed by labeling
for the nodes that are not labeled with
. The result is as shown in
Figure 6.
is labeled as multiple locations 0, 1, 4, 5 with no interruptions.
5.4. The correctness of timed IHER
According to the reference [
3], we can show the correctness of the time interrupt reduction by defining the semantics of a timed CFA by a labeled transition system. Only a summary of the correctness is given below. We define the labeled transition system
of a timed CFA
G,and the labeled transition system
of a reduced timed CFA
by timed IHER. We can establish the correctness of our timed IHER by showing that the original timed CFA
G and the reduced timed CFA
are equivalent. More concretely we can show that the original timed CFA
G and the reduced timed CFA
are related by divergence-sensitive stutter bisimulation [
15,
25].
6. Experiment
We developed our own model checker. We performed our validation in the environment shown in
Table 1.
In this experiment, the assembly code for the Renesas Electronics H8/3687F microcontroller [
22] is used as the verification target, and implementation and experiments are conducted. All general-purpose registers are 16 bits wide, and 16 registers (
-
and
-
) are installed. When general-purpose registers are used as data registers, they can be accessed as 8, 16, or 32-bit registers. When 32-bit registers are accessed, E and R are integrated and handled as ER registers, of which ER7 functions as the stack pointer (
). On the other hand, the control register consists of one 24-bit wide program counter register (
) and one 8-bit wide condition code register (
). The total address space for the program and data area is 64 Kbytes.
We examine three cases. In each case, we conduct experiments for several combinations of the number of timer interrupts (TI) and software interrupts (SI).The case 1 is used for transfer by the serial communication interface (SCI3) with two timer interrupts. The case 2 uses two LEDs. Two timer interrupts are used, one to light one LED at a prime number and the other to light the other LED at an even number, adding 1 every 0.5 seconds until the number goes from 0 to 10. The case 3 is a PID control program. One timer interrupt acquires the sensor value and sets a new target current value when a timer overflow occurs. When the other timer overflows, the timer interrupt performs PID control for a fixed cycle based on the current target value and the measured current value, and outputs the value to the motor. All three cases are implemented in e-nuvo WHEEL [
26], and the verification property is
. e-nuvo WHEEL is a microcomputer-controlled robot. The reference language is Japan. Only a manual in Japanese exists.
Table 2 shows the required memory, execution time, and state space reduction rate for cases 1 through 3. The required memory is computed by Activity Monitor. We confirmed a reduction of about 90% for case 1 and case 3, and about 60% for case 2, but the reduction rate and execution time vary greatly depending on the number of programs and interrupts.
7. Conclusions
In this paper, we proposed the formal model and algorithm based on IHER that can reduce timer interrupts. 12000 lines of java code were used to develop the entire system, including model building and model checking, and its effectiveness was demonstrated. However, it does not strictly take into account priority and multiple interrupts and is limited to verification when the program is executed in a possible position. Also, the optimal refinement of timers when loops exist in the program is unknown. Therefore, handling loops, including strict timer understanding, must be studied. Currently, we are considering algorithms that can reduce the number of states more, and expanding the scope of application of the proposed method.
References
- Edmund, M. Clarke Jr., Orna Grumberg, Doron Peled. Model Checking. The MIT Press, 1999.
- Schlich, B.; Kowalewski, S. Model checking C source code for embedded systems. Int. J. Softw. Tools Technol. Transf. 2009, 11, 187–202. [Google Scholar] [CrossRef]
- Bastian Schlich, Thomas Noll, Jorg Brauer, and Lucas Brutschy. Reduction of interrupt handler executions for model checking embedded software. In Haifa Verification Conference, pp. 5?20. Springer, 2009.
- Schlich, B. Model Checking of Software for Microcontrollers. ACM Trans. Embed. Comput. Syst. 2010, 9, 1–27. [Google Scholar] [CrossRef]
- Yamane, S.; Konoshita, R.; Kato, T. Model checking of embedded assembly program based on simulation. IEICE Trans. Inf. Syst. 2017, 100, 1819–1826. [Google Scholar] [CrossRef]
- Schlich, B.; Brauer, J.; Kowalewski, S. Application of static analyses for state-space reduction to the microcontroller binary code. Sci. Comput. Program 2011, 76, 100–118. [Google Scholar] [CrossRef]
- Armando, A.; Mantovani, J.; Platania, L. Bounded model checking of software using SMT solvers instead of SAT solvers. Int. J. Softw. Tools Technol. Transf. 2009, 11, 69–83. [Google Scholar] [CrossRef]
- Yamane, Satoshi; Kobashi, Junpei; Uemura, Kosuke. Verification Method of Safety Properties of Embedded Assembly Program by Combining SMT-Based Bounded Model Checking and Reduction of Interrupt Handler Executions. Electronics, 2020, 9.7: 1060.
- Matthew Kuo, Roopak Sinha, and Partha Roop. 2011. Efficient WCRT analysis of synchronous programs using reachability. In Proceedings of the 48th Design Automation Conference (DAC ’11). Association for Computing Machinery, New York, NY, USA, 480?485.
- Wu, Yajun, and Satoshi Yamane. "Model Checking of Real-Time Properties for Embedded Assembly Program Using Real-Time Temporal Logic RTCTL and Its Application to Real Microcontroller Software." IEICE TRANSACTIONS on Information and Systems 103.4 (2020): 800-812.
- Alur, Rajeev, and David Dill. "The theory of timed automata." Real-Time: Theory in Practice: REX Workshop Mook, The Netherlands, ?7, 1991 Proceedings. Springer Berlin Heidelberg, 1992. 3 June.
- KIRIYAMA, Taro; WU, Yajun; YAMANE, Satoshi. Reduction of Timer Interrupts for Embedded Assembly Programs Based on Reduction of Interrupt Handler Executions. In: 2021 IEEE 10th Global Conference on Consumer Electronics (GCCE). IEEE, 2021. p. 464-466.
- Liang, L.; Melham, T.; Kroening, D.; Schrammel, P.; Tautschnig, M. Effective Verification for Low-Level Software with Competing Interrupts. ACM Trans. Embed. Comput. Syst. 2018, 17, 36:1–36:26. [Google Scholar] [CrossRef]
- Peled, D. : Ten years of partial order reduction. In: Y. Vardi, M. (ed.) CAV 1998. LNCS, vol. 1427, pp. 17?28. Springer, Heidelberg (1998).
- Browne, M.C.; Clarke, E.M.; Grumberg, O. Characterizing Finite Kripke Structures in Propositional Temporal Logic. Theor. Comput. Sci. 1988, 59, 115–131. [Google Scholar] [CrossRef]
- Dirk Beyer, Thomas A Henzinger, Ranjit Jhala, and Rupak Majumdar, The software model checker blast. International Journal on Software Tools for Technology Transfer, Vol. 9, No. 5-6, pp. 505 525, 2007.
- Muchnick, S. Advanced Compiler Design and Implementation; Morgan Kaufmann Publishers Inc.: Burlington, MA, USA, 1997. [Google Scholar]
- Aho, A.V.; Sethi, R.; Ullman, J.D. Compilers: Principles, Techniques and Tools, 2 Revised ed of International ed.; Pearson: London, UK, 2006. [Google Scholar]
- Toth, T.; and Majzik, I. : Formal Modeling of Real-Time Systems with Data Processing. In Pataki, B., editor(s), Proceedings of the 23rd PhD Mini-Symposium, pages 46-49, 2016.
- Andreas Ermedahl, Jakob Engblom: Execution Time Analysis for Embedded Real-Time Systems. 2007.
- Gang Hou, Weiqiang Kong, Kuanjiu Zhou, Jie Wang, Xun Cao, Akira Fukuda: Analysis of Interrupt Behavior Based on Probabilistic Model Checking. IIAI-AAI 2018: 86-91.
- Corporation, R. E. : Renesas Electronics, Renesas Electronics Corporation (online), http://japan.renesas.com/.
- JFlex-The Fast Scanner Generator for Java. 2015. Available online: http://jflex.de/ (accessed on 3 September 2022).
- BYACC/J Java Extension. 2013. Available online: http://byaccj.sourceforge.net/ (accessed on 3 September 2022).
- van Glabbeek, R., Weijland, W.: Branching time and abstraction in bisimulation semantics. Journal of the ACM 43(3), 555-600 (1996).
- ZMP Inc. Nuvo R WHEEL. 2010. Available online: https://robot.watch.impress.co.jp/cda/news/2006/07/12/81.html (accessed on 3 September 2022).
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).