3. The global burden of musculoskeletal
Trauma is a widespread and escalating issue, and the World Health Organization (WHO) has pinpointed it as the leading cause of mortality among individuals above the age of five. It claims more lives than a combination of malaria, tuberculosis, and human immunodeficiency virus/acquired immunodeficiency syndrome (HIV/AIDS) [
48,
49]. Hand trauma specifically poses a considerable burden on morbidity and offers an important avenue for intervention due to its detrimental effects on both quality of life and economic productivity.
Previously considered costly and less worthwhile, surgical treatments have now gained recognition as cost-effective measures to address global health challenges. However, in low- and middle-income countries (LMICs), where more than a third of the global population resides, merely 6% of surgical procedures are conducted. This disparity hinders the provision of essential surgical care. To mitigate this, organizations from high-income countries (HICs) financially support numerous medical missions each year, incurring expenses exceeding
$250,000 [
50,
51]. For instance, the Touching Hands Project has carried out 41 missions across 13 different countries, performing 2,467 procedures specifically focusing on the hands and upper extremities. Similarly, ReSurge International has conducted over 105,000 procedures during missions spanning more than 15 nations. Despite the impressive figures, these statistics might not accurately convey the true impact of these endeavors. Critical questions remain unanswered, such as the long-term functional status of each patient and their ability to resume work and provide for their families. Additionally, the handling of regional challenges by the local healthcare system remains uncertain. Due to limited data collection and relatively short follow-up periods during most missions, these important aspects often go unaddressed. Nonetheless, the availability of such information is pivotal for gauging the effectiveness, value, and overall impact of international outreach missions, as well as their contribution to the sustainability of local healthcare systems [
52,
53].
Over recent decades, a multitude of therapies has been implemented globally to improve the health of millions of individuals, extending beyond the scope of surgical diseases. Examples encompass the utilization of antibiotics, enhanced nutrition, and enhanced road safety measures to prevent accidents. Despite the success of these initiatives in reducing global morbidity and mortality, a new challenge emerges in ensuring the provision of quality care. Kruk et al. report that inadequate healthcare systems contribute to over 8 million annual fatalities and economic losses of $6 trillion. In light of this, the authors assert that poor-quality care has become a greater obstacle to reducing mortality compared to the issue of limited access.
Drawing parallels between the quality gap present in both the United States’ healthcare system and that of low- and middle-income countries (LMICs), it becomes crucial for outreach efforts in LMICs to embrace a culture change towards quality assessment and improvement similar to what has occurred in high-income countries (HICs). Prioritizing high-quality health systems, Kruk et al. and the Lancet Global Health Commission outline key objectives, including measuring and analyzing quality, enhancing quality through educational innovations, and developing effective methods and tools such as measurement surveys and patient-reported outcomes. The integration of electronic health records (EHRs), designed to be context-sensitive, cost-effective, and adaptable, can facilitate the achievement of these goals [
54].
This review aims to emphasize the advantages of EHRs in HICs, explore their potential benefits in LMICs, and assess their current utilization by outreach organizations. Additionally, a guide for implementing EHRs during outreach missions for hand surgery is provided. In HICs, data collection and documentation through EHRs form the cornerstone for safety, quality, accountability, and efficiency. The advantages of data gathering extend across clinical, organizational, and social realms, offering a deeper and more precise comprehension of the required and delivered treatments. EHRs establish a framework for communication, ensuring accessible care plans that prevent redundant or incompatible therapies while facilitating treatment harmonization. Clinically, EHR utilization has been widely documented to yield numerous benefits, such as decreased infant mortality, reduced adverse medication reactions, increased rates of postoperative outcome assessment, and adherence to evidence-based recommendations [
55].
The utilization of clinical decision support and electronic health records (EHRs) offers the potential to curtail costs associated with personnel and human resources as well as to eliminate redundant testing, presenting organizational benefits. Prior research has demonstrated enhanced compliance with legal and regulatory standards through heightened data security and improved patient confidentiality achieved via controlled and auditable processes. Evidenced by results from the Joint Commission on Accreditation of Healthcare Organizations, these measures contribute to improved quality assurance.
EHRs hold significant potential in enhancing patient treatment through avenues like root cause analysis, research, and outcome tracking. While their societal benefits may not be immediately apparent, EHRs serve as valuable tools for public policy and health services researchers. These systems facilitate investigations into epidemiology-related questions, guiding resource allocation, evaluating intervention effectiveness, and offering insights that steer future outreach initiatives. For instance, research on the impact of public policies on COVID-19 rates was made feasible through the aggregation of digital data collected from laboratory and county systems [
56,
57].
Information regarding EHR usage and quality assessment can be extracted from World Health Organization (WHO) data and other outreach organizations, although a comprehensive analysis of all such organizations remains pending. Notably, adoption rates are lower in lower-middle (35%) and low-income (15%) countries compared to more than 50% in high-income countries (HICs) that have established national EHR systems. Existing literature, as seen in a systematic review addressing basic surgical care standards in LMICs, tends to be single-center, observational, and lacking crucial details like follow-up periods. Inconsistencies in quality assessment methods are also evident, indicating a lack of measurement standardization [
58,
59]. Furthermore, existing quality measurement approaches for surgical missions in LMICs tend to focus disproportionately on systems and structures rather than outcomes.
To bridge this gap, the Global-QUEST (Quality in Upper Extremity Surgery and Training) initiative, comprising ten hand surgeons dedicated to advancing secure and high-quality care in LMICs, has developed quality standards for hand surgery outreach. These standards align with the WHO’s approach to monitor essential care components. However, for these measurements to be effectively benchmarked and utilized, reliable data collection processes are vital, mirroring the practices implemented in HICs (including structured workflows for data collection and analysis). Presently, data collection during outreach activities is predominantly done manually, often on paper or electronic spreadsheets. These methods pose challenges in accessibility, legibility, and retrospective use. Their limitations in effectively utilizing critical patient data for clinical care, guiding staged treatments, and acting as reference points for future surgeons are at the crux of these constraints. Empirically, data gathering before, during, or after missions is uncommon [
62,
63].
A recent survey involving 22 hand surgeons and outreach administrators revealed that a significant proportion-maintained records of the number of patients assessed (73%) and surgeries conducted (82%). However, the majority did not document crucial metrics such as the proportion of patients requiring reintervention (32% did not record, 23% were unsure), the post-surgery functional status of patients (68% did not record), or patient-reported outcome measures (77% did not record). This presents an opportunity to improve outcomes collection, aligning more closely with the intentions of outreach participants, which primarily involve enhancing patient function, akin to advancements observed in high-income countries (HICs).
Implementation of electronic health record (EHR) systems could offer a structured framework to enhance data collection and tracking rates, addressing this shortfall. This notion is supported by insights from qualitative interviews with surgeons and administrators from the same study, as well as from other sources. Increasingly, businesses are recognizing the paramount importance of utilizing EHR systems to gather data. An illustrative example is the charity organization Operation Smile, which provides surgical care across more than 30 countries. In 2014, they introduced a digitized patient assessment process. During a single mission to Vietnam, this transition enabled them to streamline their workflow by storing data from almost 300 patient evaluations in an EHR [
65].
Similarly, another group established the Surgical Services Quality Assessment Database (SQUAD) to collect information from the Mbarara Regional Referral Hospital in Uganda. Nonetheless, the utility of this infrastructure at the point of treatment was limited, primarily serving a retrospective purpose of evaluating surgical priority, perioperative complications, and program development [
66,
67].
When considering the shift toward global outreach approaches that mirror those of HICs, various organizational and cultural factors warrant attention and consideration. These elements play a crucial role in shaping the transition to care delivery that is aligned with the standards observed in HICs.
(a) Supportive leadership and culture
The effectiveness of implementation hinges on the presence of shared values within organizations and partnerships, coupled with a strong commitment to cultivating a culture centered on measurement, quality, and transparency. Effective leadership is essential in promoting viewpoints that prioritize excellence and involving all relevant stakeholders. The establishment of a culture that fosters both measurement and continuous improvement is vital to ensuring the adoption and utilization of measuring tools by the staff.
(b) The redesign of trip processes
The benefits of data collection through an EHR system become evident during patient care. However, for this to be effective, designated team members authorized to handle detailed data collection and utilization should be responsible for these tasks during outreach missions. Accomplishing this may involve adapting existing workflows to accommodate a reduced number of cases and redistributing responsibilities to ensure that conducted cases are both safely managed and properly documented. The implementation of an EHR system, for instance, should not overly burden staff, but could potentially require task shifting – the delegation of certain responsibilities from more experienced personnel to those with less advanced training.
(c) Collaborating for sustainability
Travel experiences that prioritize bidirectional exchange (both teaching and learning) are driven by specific needs and tailored to the local context. For example, efforts should be directed towards enhancing the capabilities of the local healthcare system to effectively manage prevalent illnesses. The approach to outreach should be centered around the requirements of the community and the learners, taking into account the variations that arise based on location and country. By identifying and addressing local needs, this strategy prevents misunderstandings where local surgeons might perceive HIC surgeons as replacing them, instead fostering an environment for training local surgeons to perform similar procedures safely. In a similar vein, just as certain EHR data elements, such as mortality rates, may remain constant, others that reflect the impact on the local community may change, such as the poverty probability index.
While this review primarily focuses on EHR utilization among outreach practitioners, even greater benefits could be reaped by facilitating collaboration between visiting surgeons and those who are already adept at using an EHR, or alternatively, by implementing a local EHR system.
(d) Results-driven
Surgical procedures conducted on patients in high-income countries (HICs) aim to improve function and alleviate pain. Similar approaches and evaluation methods should be applied to healthcare in low- and middle-income countries (LMICs). Efforts should be driven by objective outcomes that prioritize patients and communities, with a keen focus on long-term effects and the broader implications for patients and communities. These facets of care need to be integrated into the processes of incorporating electronic health records (EHRs), determining aspects like who is responsible for gathering outcomes data and how it is done. The outcomes should provide actionable insights, such as identifying patients who miss follow-up appointments or experience worsening pain. Such attributes enhance sustainability and the development of capacity, thereby fostering trust within both patient and community contexts.
(e) Public reporting
Integrating data into systems with a learning-oriented culture facilitates continuous quality improvement. This not only allows for benchmarking and sharing of best practices but also has the potential to drive initiatives for increased investment, improved quality and safety, and the establishment of international collaborations. Similar to the way public reporting encourages treatment enhancement in high-income countries (HICs), mechanisms for reporting could support the exchange of best practices among surgeons and outreach organizations. While HICs have already incorporated electronic health records (EHRs) into surgical procedures as a routine for patient safety and high-quality care, implementing such measures in low- and middle-income countries (LMICs) presents greater challenges due to factors like financial constraints, time limitations, and security concerns.
Despite these hurdles, we argue that well-implemented EHRs can elevate patient safety and the quality of care provided. They have the potential to more thoroughly review perioperative complications, enhance preoperative optimization and resource utilization, and glean insights to inform subsequent outreach efforts.
4. Concerns on privacy and security of electronic health records
Numerous surveys have highlighted concerns related to the privacy of health information. For instance, Win [
63] found that only 39% of respondents believed their health information to be safe and secure, with over two-thirds expressing worries about the privacy of their personal health records. In another study, respondents exhibited both concerns for data security and a lack of confidence in its safety [
45]. Perera et al. [
52] conducted a survey where half of the participants expressed apprehension about data security, particularly when data is transmitted over the internet. Ancker et al. [
7] reported that almost half of their research participants thought that sharing health information might compromise its privacy.
Meanwhile, privacy concerns have been identified as a significant factor influencing the successful development of electronic health records technology. The unique characteristics of Internet of Things (IoT) networks, which distinguish them from other systems, form the foundation of privacy and security concerns associated with IoT. These characteristics include heterogeneity, an unpredictable environment, limited resources, and the need for scalability. Even platforms with minimal processors now possess robust crypto engines and sufficient program memory for implementing essential security functions.
In light of these distinctive features, Lafky & Horan [
45] suggest that security requirements for IoT systems can be grouped into the following categories: identity management, network security, resilience and trust, and privacy. The authors assess a range of designs proposed for IoT in the academic community and analyze their compatibility with necessary security measures. Although no single architecture fully addresses all security requirements, careful consideration has been given to several security needs [
45], with special emphasis on trust and privacy requirements.
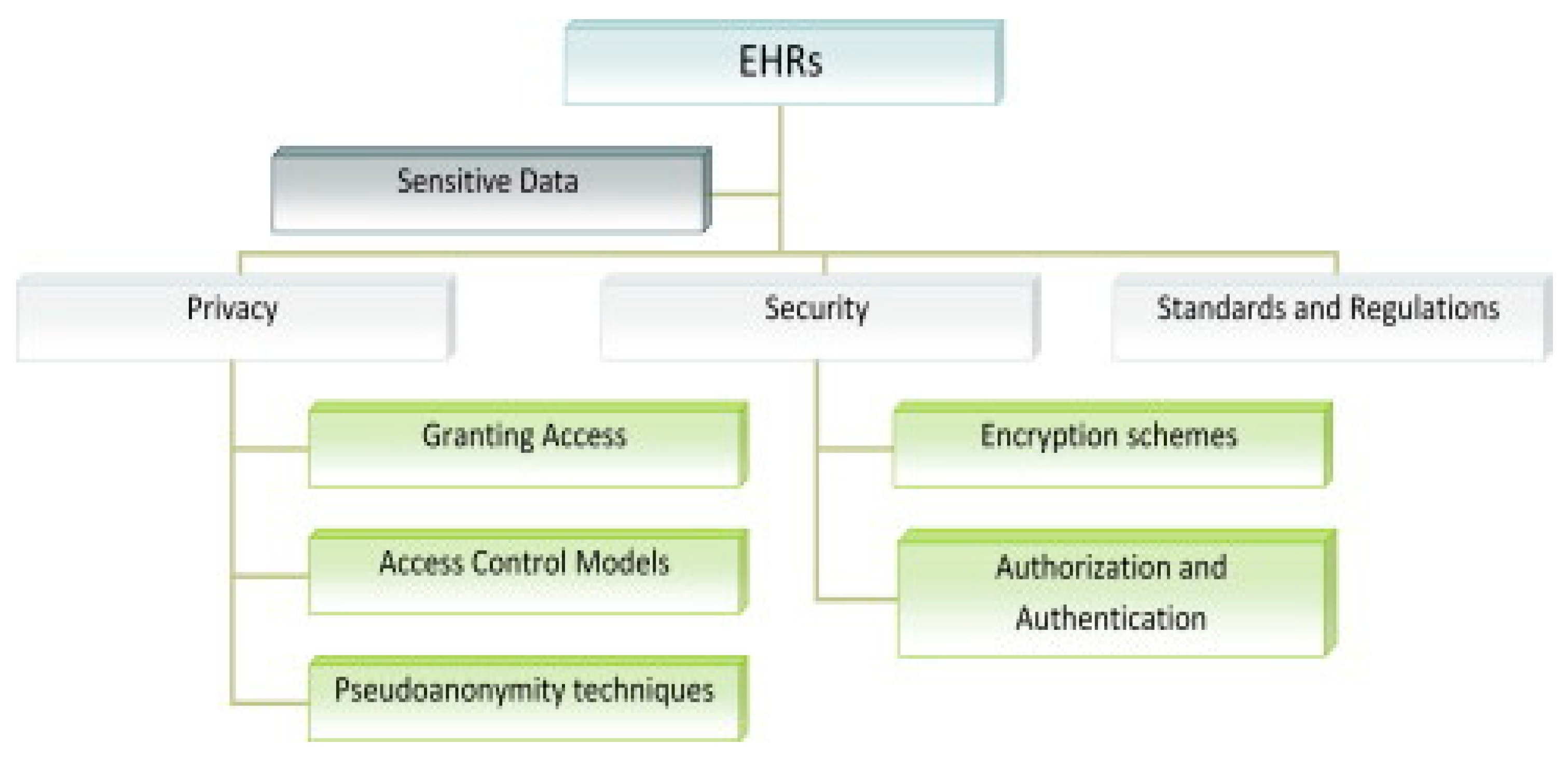
The widely accepted model for information technology security, based on the principles of confidentiality, integrity, and availability (commonly referred to as CIA), has been a consistent framework for evaluating security measures. These three principles have been represented as vertices of a triangle in this model. While the model has evolved over time to include additional primary characteristics, its core elements of CIA have remained constant. It’s important to note that these three characteristics cannot be fully achieved simultaneously, as they are often considered mutually exclusive. For example, enhancing overall availability within the same resource constraints may necessitate compromising accuracy, confidentiality, or both.
Figure 4.
Security and privacy in Electron Health record [
71].
Figure 4.
Security and privacy in Electron Health record [
71].
The primary focus of security measures in traditional computer systems has largely been on maintaining overall confidentiality. However, in the case of embedded and Internet of Things (IoT) systems, it could be argued that the other two aspects—integrity and availability—hold even greater significance than in typical office information systems [
38]. A noteworthy observation is that variations in approach often negatively impact collaboration between conventional IT systems and control system managers.
Studies have explored the relationship between individuals’ confidence in the confidentiality and security of their medical records and their willingness to engage with electronic health records. For example, Whetstone & Goldsmith [
61] found that trust in the confidentiality of medical records positively influenced individuals’ motivation to adopt electronic health records. Conversely, concerns about privacy hindered people’s willingness to share health information online [
11]. Anderson & Agarwal [
8] discovered that individuals’ willingness to provide access to their health information was negatively affected by concerns about privacy. On the other hand, Dinev et al. [
22] observed a limited correlation between attitudes towards electronic health records and concerns about privacy related to health information.
Worries about privacy have been shown to influence patients’ willingness to share medical data in cloud computing approaches [
25]. Privacy considerations are also crucial in determining trust when selecting healthcare providers. In fact, studies have highlighted that patients express concerns about health information privacy through various responses, including refusing to provide personal information, fabricating information, requesting data removal, and lodging complaints [
44]. Specific medical histories have been found to increase privacy concerns among consumers [
54]. Additionally, individuals’ preferences for sharing electronic health information depend on the type of information disclosed [
64].
These privacy concerns have significant implications for the development of electronic health records technology. IoT networks possess distinctive characteristics that give rise to privacy and security concerns, such as heterogeneity, unpredictable environments, limited resources, and scalability needs. While even platforms with minimal processors now include advanced crypto engines and sufficient program memory for security functions, these characteristics necessitate careful categorization of security requirements into identity management, network security, resilience, trust, and privacy for IoT systems [
45]. While no single architecture fully addresses all security demands, thorough analysis demonstrates that several security needs are being adequately considered [
45].
The notion of a widely accepted information technology security model, often abbreviated as CIA (Confidentiality, Integrity, and Availability), has persisted over time. These three characteristics have been visualized as vertices of a triangle, and while the model has evolved with additional primary characteristics, the core elements of CIA remain fundamental. It’s important to note that achieving all three characteristics simultaneously can be challenging due to their potential trade-offs.
6.1. Security and privacy features of current EHR systems
Several studies have examined security measures through the lenses of three primary safeguard categories: physical, technical, and administrative security. These categories encompass various security strategies employed by healthcare organizations to enhance the protection of sensitive health information contained within electronic health records.
The first area of focus is administrative safeguards, which involve practices like conducting audits, designating an information security officer, and establishing contingency plans [
62]. This category emphasizes the adoption of compliant security practices and guidelines. The second category, physical safeguards, aims to physically secure health information to prevent unauthorized access to hardware or software. It encompasses the organizational protective measures mentioned earlier [
62]. Notably, breaches in physical security are a significant contributor to security breaches overall, ranking second [
47]. Assigning specific security responsibilities exemplifies a physical safeguarding approach [
46].
The third category, known as technical safeguards, revolves around safeguarding the entire information system within a healthcare organization’s network [
47]. The critical role of this aspect in maintaining overall organizational security is underscored by the fact that a majority of security breaches involve computers and portable electronic devices [
47]. This category encompasses security measures such as firewalls, encryption, virus scanning, and methods for information authentication [
72]. Among these measures, firewalls and cryptography were identified as the most commonly used security methods. However, their implementation is often influenced by budget constraints. Other significant security measures include antivirus software, Chief Information Security Officers, and cloud computing [
27]. Research by Liu et al. [
73] revealed that firewalls and encryption serve as technical safeguards against electronic breaches, while physical safeguards, such as physical access control, prevent theft through mechanisms like locks on computers. Similarly, Amer’s study [
74] on the ethical use of electronic health records and genomic data indicated that while administrative safeguards de-identified samples or research, encryption provided technical protection. Technical safeguards involve elements like firewalls, encryption, and decryption, while administrative safeguards are achieved through education and security plans, Chief Information Security Officer roles, and thorough training [
74].
Wikina [
75] pointed out that physical safeguards encompass security camera installation, while administrative safeguards entail managerial authorization for the release of paper-based patient data and training on lost document handling. With advancing technology, healthcare institutions are becoming increasingly susceptible to security breaches. Organizations like the Clinical Engineering Information Technology Community, the American College of Clinical Engineering, and the Healthcare Information and Management Systems Society recognize the importance of risk management and staying abreast of technological advancements and threats. These organizations, alongside the risk assessment and management phases, ensure healthcare institutions are at the forefront of patient information protection within electronic health records.
The adoption of RFID (Radio-Frequency Identification) technology is gaining traction within healthcare organizations for enhanced security and privacy. This technology involves data storage within RFID tags and the establishment of access restrictions, thereby limiting data access to authorized personnel. Employing a Chief Information Security Officer can aid in overseeing and coordinating security methods and initiatives for electronic medical records [
76]. Among the technologies used to safeguard healthcare IT systems, Firefox is notable. Firefox effectively shields a company’s network and ensures the security of networks containing patient information. Its application spans both internal and external contexts, safeguarding the company’s information network from potential threats. These technologies come in diverse forms, each playing a role in fortifying information security.
The third category of firewalls is known as a level gateway. These firewalls act as gatekeepers for an organization’s network by inspecting IP web pages for threats before delivering them to end users. They facilitate external network connections for status inspection firewalls and prevent external networks from entering the organization’s intranet. This approach has effectively protected electronic health records by creating barriers that deter hackers from direct access to the system and private health data. However, implementing this type of firewall is challenging due to its complexity and high costs. Therefore, a comprehensive assessment of the organization’s internal and external factors is essential to determine the practicality and suitability of using this firewall.
The network address translator is the final group of firewalls. It conceals the intranet IP addresses of the organization, preventing external users from accessing them and potentially causing harm. This firewall configuration separates the organization’s intranet and local area networks. While firewalls significantly contribute to the security of electronic health records, it’s important to employ all four security methods: service control, direction control, user control, and behavior control, in that sequence. Prior to implementing any firewall type, organizations should conduct thorough needs, budget, and threat analyses both internally and externally. Neglecting these evaluations or the four security strategies could jeopardize the security of patients’ electronic health records and the organization’s overall information system.
The use of cryptography has successfully protected electronic health records, enhancing the security of health information transmission. Encryption has contributed to the secure exchange of health information, adhering to established guidelines for recording encryption activation or deactivation during data exchange. Encryption is supported by the Health Insurance Portability and Accountability Act (HIPAA), which expanded its security requirements through the 2003 Concluding Rule [
58]. The Concluding Rule broadened HIPAA’s scope to encompass the creation, reception, storage, and transmission of protected health information (PHI). Decryption has been instrumental in ensuring patient electronic health records’ security. Digital signatures have addressed the issue of compromised protected health records during patient access, effectively mitigating security breaches.
Implementing controls through username and password security methods is advantageous. Role-based restrictions limit data access for users through system administrators’ assigned usernames and passwords. However, this approach may not fully safeguard electronic health record data from internal threats, necessitating proper logging out after system use. Other commonly utilized security techniques include antivirus software, cloud computing, preliminary risk assessment sequencers, Chief Information Security Officer hiring, and radio frequency identification (RFID). Remote patient monitoring (RPM) is another innovative tool employed to secure data confidentiality and integrity in electronic health records. This approach uses various sensors to monitor patients’ vital signs remotely, alerting healthcare professionals when deviations from normal limits occur. Diabetes, congestive heart failure, and dementia are conditions well-suited for remote patient monitoring. The introduction of new technologies, despite legal frameworks like HIPAA, raises privacy concerns and presents breakthroughs in healthcare.
With the increasing use of technology, extensive research has explored the integration of cloud computing into EHR systems. Cloud computing allows organizations to rent storage space and computing power, as well as share information electronically. This approach reduces ownership and maintenance costs while integrating cryptographic protocols into EHR systems. However, antivirus software remains a more commonly employed security solution. Achampong [
1] also highlights concerns related to storing medical records on remote servers operated by independent cloud service providers [
33]. The 2009 HITECH Act emphasized mandatory reporting of data breaches and specified protocols for such incidents. It requires entities to provide specific information in case of data breaches affecting more than 500 individuals. [
62] Under the HITECH Act, Centers for Medicare and Medicaid Services (CMS) beneficiaries were required to use EHRs by 2015 to qualify for full reimbursements. The Office of the National Coordinator (ONC) established three “meaningful use” phases for EHR utilization by healthcare organizations. Meaningful use evaluates the effective utilization of EHRs compared to older documentation methods [
47]. Health care providers using Health Information Technology (HIT) must establish a robust security system due to ongoing IT-related security concerns. This system comprises security controls aligned with a security policy, which includes regulations governing security-related behaviors [
10]. An information technology security strategy ensures the confidentiality, integrity, and availability of an organization’s IT assets, including data, hardware, software, and personnel, in compliance with established requirements [
53].
5. Three decades of bibliometric research productivity analysis
The process of digitalization or digital transformation has been ongoing in various regions and countries, even amid the global economic downturn and financial crisis. This transformation, driven by factors like growing digital demands, evolving technologies like Information and Communication Technology (ICT), and the pressures from the so-called IRV4, has significantly impacted industries, including healthcare. Over the past thirty years, the healthcare sector has experienced a digital revolution that has reshaped many aspects of healthcare delivery systems. This transformation has aimed to enhance healthcare outcomes and practices, optimize resource utilization, and increase patient satisfaction. The recent COVID-19 pandemic has further emphasized the need for digitization in modern healthcare, challenging leaders in digital transformation to find solutions that adhere to health mandates, accommodate remote interactions, and meet heightened healthcare demands.
EHR and EMR adoption is often considered the initial step in the broader digital transformation of healthcare. While numerous success stories have highlighted improved outcomes through EHR deployment, challenges and limitations, such as the digital divide, have also been recognized. The adoption of EHRs has gone through various stages over the past two decades, with adoption rates gradually increasing. In the United States, for example, recent surveys indicate an adoption rate of 88%. However, achieving successful EHR adoption necessitates coordinated and integrated efforts due to the complexity of the process. This complexity is reflected in the American healthcare system’s Meaningful Use (MU) project.
The impact of MU-driven EHR adoption on healthcare performance metrics, including quality of care, patient safety, and satisfaction, has been well-documented in the literature. Different nations, including Saudi Arabia, India, Australia, Europe, and Arab and African countries, have shared their experiences and findings on this journey. The dedication of stakeholders, including governments and healthcare providers, has played a unifying role in these outcomes. However, challenges such as resistance to change and lack of support from healthcare and governmental bodies have also been noted.
The integration of EHRs with advanced technologies like blockchain, cloud computing, big data, mobile health apps, AI, and IoT has been extensively explored in literature. Comprehensive reviews of literature have also examined various aspects of EHR systems, underscoring their diversity and expansion. These evaluations have addressed specific issues like adoption barriers, perceptions, and utilization across different healthcare specializations.
In light of both specific and broader concerns surrounding EHRs, this study aims to uncover patterns and gaps in research from the last three decades. The rest of this article presents the organized findings of the study, analyzing the existing literature on EHRs and engaging in an in-depth discussion of these findings. Additionally, the article offers suggestions for further research in this field.
6.0. Conclusion and future work
This study focuses on the security and privacy aspects of electronic health record (EHR) systems. The research delves into numerous security and privacy concerns associated with the utilization of EHRs and explores potential solutions. EHRs have proven to be a useful tool in facilitating the sharing of medical data among healthcare professionals, ultimately enhancing the quality of patient care. The adoption of EHRs encourages a broader perspective on health and fosters collaboration among healthcare providers. EHRs allow for the seamless exchange of patient information, ensuring accessibility and updates throughout the course of treatment.
However, the convenience of EHRs also raises critical privacy and security concerns. The potential for unauthorized access to sensitive patient information becomes more significant, leading to potential breaches if private data falls into the hands of third parties. The study reveals that a variety of rules and requirements are in place to address privacy and security concerns related to EHR use. However, there is a need for harmonization among these standards to resolve potential discrepancies.
Numerous organizations have proposed various encryption techniques to enhance the security of EHRs. The implementation of effective encryption methods is strongly recommended to ensure the protection of both patient and medical professional data. Access control is a vital consideration in EHR systems, with Role-Based Access Control (RBAC) being the preferred control paradigm. Authentication methods, such as passwords, logins, and electronic signatures, play a pivotal role in managing EHRs. The effective management of EHRs requires a multidisciplinary approach involving technology, computer science, and communications to facilitate the secure exchange of medical information across wide geographical areas.