Submitted:
06 November 2023
Posted:
07 November 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Literature Review
-
AIS Data-Based Studies
-
Radar Data-Based Studies
-
Optical Systems-Based Studies
-
Data Fusion Studies
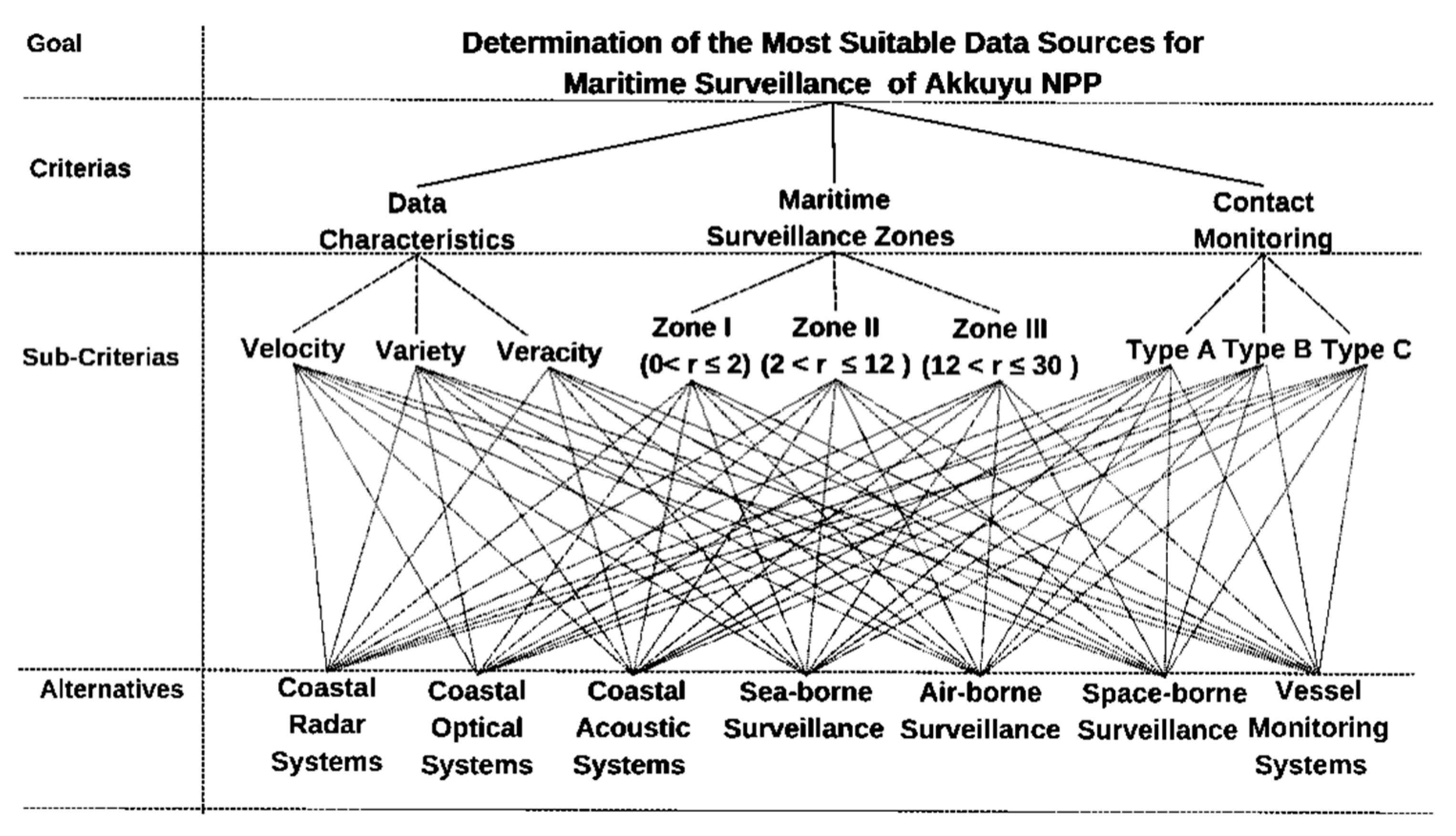
3. Methodology
| n | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| Rİ | 0 | 0.52 | 0.89 | 1.11 | 1.25 | 1.35 | 1.40 | 1.45 | 1.49 |
3.1. Criteria
3.1.1. Data Characteristics Criterion
- Data velocity;
- Data variety;
- Data veracity.
3.1.2. Maritime Surveillance Zones Criterion
- Zone I: A circle with a radius of 2 nm towards the sea;
- Zone II: A circle with a radius of 2-12 nm (territorial water limit);
- Zone III: A circle with a radius of 12-30 nm (territorial sea border - international waters).
3.1.3. Contact Tracing Capability Criterion
- Type A: Vessels mandated to possess AIS and LRIT devices in compliance with international regulations;
- Type B: Vessels required to equipped with AIS, Fishing Vessels Monitoring System (FVMS) and Vessel Tracing Module (VTM) devices in accordance with national regulations;
- Type C: Private boats, small boats, sailboats, dinghies, rowboats, kayaks, canoes, pedal boats, jet-skis, USVs, swimmers, etc. which are exempt from having any vessel tracking systems according to national and international regulations.
3.2. Alternatives
3.2.1. Coastal Radar Systems Alternative
3.2.2. Coastal Radar Systems Alternative
3.2.3. Coastal Acoustic Systems Alternative
3.2.4. Sea-borne Surveillance Alternative
3.2.5. Air-borne Surveillance Alternative
3.2.6. Space-Borne Surveillance
3.2.7. Coastal Radar Systems Alternative
3.3. Expert Opinion
4. Findings and Discussions
- 47% for "data characteristics";
- 29% for "contact monitoring capability";
- 24% for "size of the maritime area to be monitored" (Table 4).
| Criteria | Weight | Radar | Optics | Acoustics | Sea Assets | Air Assets | Space Assets | VMS |
|---|---|---|---|---|---|---|---|---|
| Data Characteristics | 0.469 | 0.083 | 0.077 | 0.031 | 0.106 | 0.095 | 0.034 | 0.045 |
| Data Speed | 0.071 | 0.018 | 0.012 | 0.010 | 0.012 | 0.012 | 0.001 | 0.005 |
| Data Diversity | 0.124 | 0.015 | 0.011 | 0.006 | 0.031 | 0.031 | 0.013 | 0.017 |
| Data Accuracy | 0.274 | 0.050 | 0.054 | 0.014 | 0.063 | 0.052 | 0.019 | 0.022 |
| Size of Sea Area to be Monitored |
0.238 | 0.061 | 0.033 | 0.010 | 0.054 | 0.047 | 0.017 | 0.017 |
| Zone I | 0.069 | 0.015 | 0.017 | 0.005 | 0.016 | 0.011 | 0.002 | 0.003 |
| Zone II | 0.126 | 0.036 | 0.014 | 0.004 | 0.028 | 0.027 | 0.008 | 0.009 |
| Zone III | 0.043 | 0.010 | 0.002 | 0.001 | 0.009 | 0.009 | 0.006 | 0.005 |
| Contact Tracing Capability |
0.293 | 0.057 | 0.040 | 0.009 | 0.058 | 0.042 | 0.012 | 0.021 |
| Type A | 0.044 | 0.011 | 0.006 | 0.001 | 0.008 | 0.008 | 0.003 | 0.007 |
| Type B | 0.069 | 0.019 | 0.011 | 0.002 | 0.014 | 0.010 | 0.003 | 0.010 |
| Type C | 0.126 | 0.027 | 0.023 | 0.006 | 0.036 | 0.024 | 0.006 | 0.004 |
4.1. Evaluation of Sub-Criteria
4.2. Evaluation of Alternatives
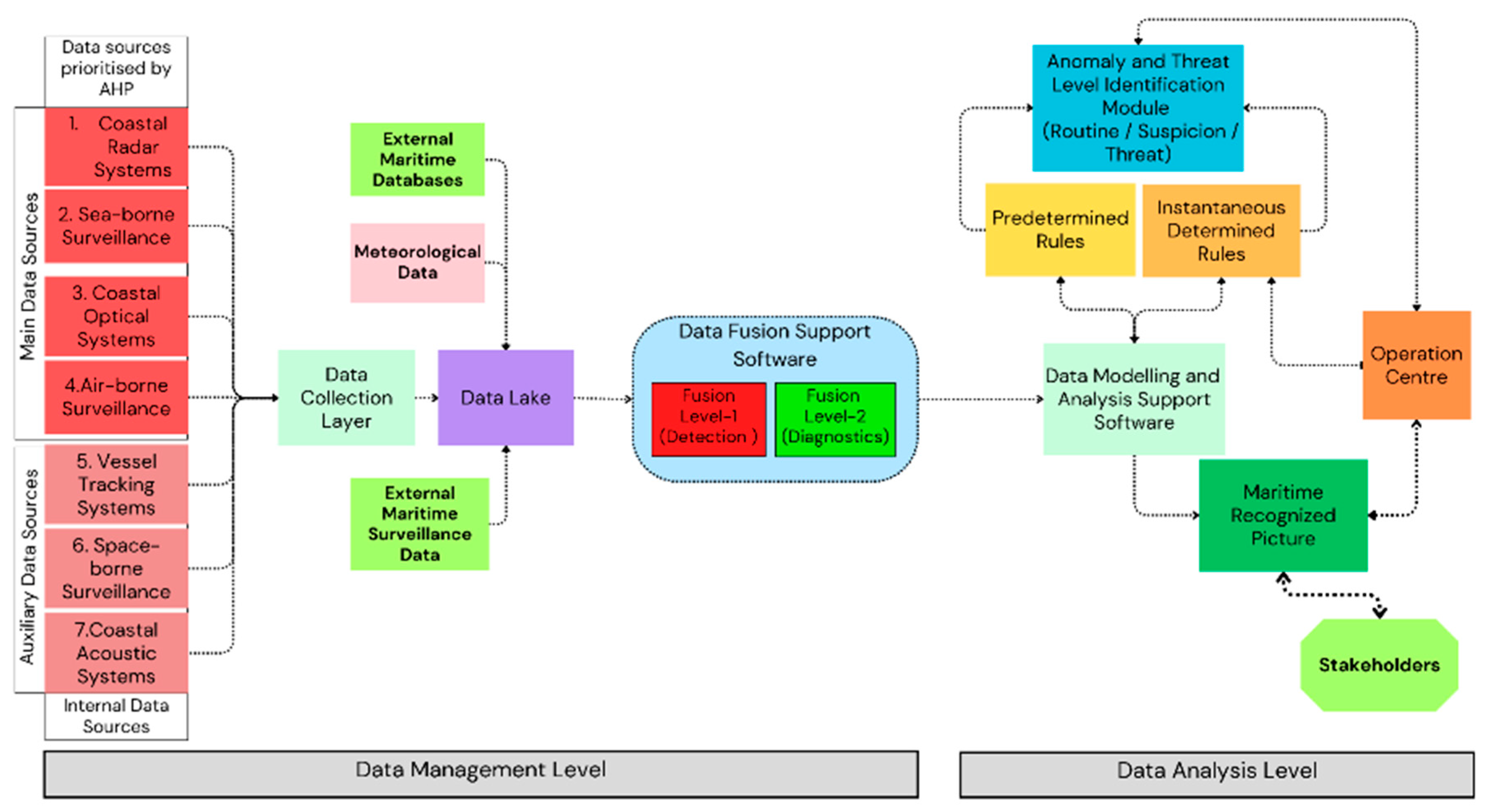
4.3. Maritime Surveillance System Model Proposal and Scenarios
4.3.1. Scenarios
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bueger, C.; Edmunds, T. Beyond Seablindness: A New Agenda for Maritime Security Studies. International Affairs 2017, 93, 1293–1311. [Google Scholar] [CrossRef]
- Commercial Crime Services, I. Request Piracy & Armed Robbery Report Markating. www.icc-ccs.org. https://www.icc-ccs.org/piracy-reporting-centre/request-piracy-report.
- IMO. Marine Casualties and Incidents. GISIS. https://gisis.imo.org/Public/MCI/Search.aspx (accessed 2023-10-01).
- UNCTAD. Review of Maritime Transport; United Nations Publications: New York, 2023; https://unctad.org/system/files/official-document/rmt2023_en.pdf (accessed 2023-10-01). [Google Scholar]
- Department of Homeland Security. THE NATIONAL STRATEGY for MARITIME SECURITY OCTOBER 2005; https://www.dhs.gov/sites/default/files/publications/HSPD_MDAPlan_0.pdf. (accessed 2023-08-01).
- Borchert, H. The Future of Maritime Surveillance in an Era of Contested Maritime Domains; 2011.
- Ramongassie, S.; Taveneau, N.; Calmettes, T.; Richard, J.; Challamel, R.; Autran, O.; Foix, V.; Durand, P. RADAR and AIS Sensors Constellation for Global Maritime Surveillance. 2010. [CrossRef]
- Bloisi, D.D.; Iocchi, L.; Nardi, D.; Fiorini, M. Integrated Visual Information for Maritime Surveillance. Clean Mobility and Intelligent Transport Systems 2015, 237–264. [Google Scholar] [CrossRef]
- Stróżyna, M.; Abramowicz, W.; Węcel, K.; Filipiak, D.; Małyszko, J. Data Analysis in the Maritime Domain; PUEB Press, 2022. [CrossRef]
- Bloisi, D.D.; Previtali, F.; Pennisi, A.; Nardi, D.; Fiorini, M. Enhancing Automatic Maritime Surveillance Systems with Visual Information. IEEE Transactions on Intelligent Transportation Systems 2017, 18, 824–833. [Google Scholar] [CrossRef]
- Martineau, E.; Roy, J. Maritime Anomaly Detection: Domain Introduction and Review of Selected Literature; Defence R&D Canada – Valcartier, 2011. https://apps.dtic.mil/sti/tr/pdf/ADA554310.pdf (accessed 2023-10-02).
- Aktan, E. Büyük Veri: Uygulama Alanları, Analitiği ve Güvenlik Boyutu. Bilgi Yönetimi 2018, 1, 1–22. [Google Scholar] [CrossRef]
- Liang, T.-P.; Liu, Y.-H. Research Landscape of Business Intelligence and Big Data Analytics: A Bibliometrics Study. Expert Systems with Applications 2018, 111, 2–10. [Google Scholar] [CrossRef]
- Gandomi, A.; Haider, M. Beyond the Hype: Big Data Concepts, Methods, and Analytics. International Journal of Information Management 2015, 35, 137–144. [Google Scholar] [CrossRef]
- Chahal, H.; Gulia, P. Big Data Analytics. International Journal of Mining, Metallurgy and Mechanical Engineering 2016, 4. [CrossRef]
- Rawat, R.; Yadav, R. Big Data: Big Data Analysis, Issues and Challenges and Technologies. IOP Conference Series: Materials Science and Engineering 2021, 1022, 012014. [Google Scholar] [CrossRef]
- Mirović, M.; Miličević, M.; Obradović, I. Big Data in the Maritime Industry. Naše more 2018, 65, 56–62. [Google Scholar] [CrossRef]
- İşleyen, S.K.; Uçar, U.; Balo, F. A New Solution Approach for Maritime Surveillance Operation: The Case of Aegean Sea. Mathematical Problems in Engineering 2019, 2019, 1–16. [Google Scholar] [CrossRef]
- Filipiak, D.; Stróżyna, M.; Węcel, K.; Abramowicz, W. Anomaly Detection in the Maritime Domain : Comparison of Traditional and Big Data Approach. Semantic Scholar. https://api.semanticscholar.org/CorpusID:172134741 (accessed 2023-10-07).
- Stróżyna, M.; Małyszko, J.; Węcel, K.; Filipiak, D.; Abramowicz, W. Architecture of Maritime Awareness System Supplied with External Information. Annual of Navigation 2016, 23, 135–149. [Google Scholar] [CrossRef]
- Zissis, D.; Xidias, E.K.; Lekkas, D. A Cloud Based Architecture Capable of Perceiving and Predicting Multiple Vessel Behaviour. Applied Soft Computing 2015, 35, 652–661. [Google Scholar] [CrossRef]
- Cepeda, M.; Simões, R.; Moita, J.; Caprace, J.D. Big Data Analysis of AIS Records to Provide Knowledge for Offshore Logistic Simulation. Semantic Scholar. https://api.semanticscholar.org/CorpusID:210171474 (accessed 2023-10-08).
- Yitao, W.; Lei, Y.; Xin, S. Route Mining from Satellite-AIS Data Using Density-Based Clustering Algorithm. Journal of Physics: Conference Series 2020, 1616, 012017. [Google Scholar] [CrossRef]
- Huang, W.; Wu, X.; Lund, B.; El-Darymli, K. Advances in Coastal HF and Microwave (S- or X-Band) Radars. International Journal of Antennas and Propagation 2017, 1–2. [Google Scholar] [CrossRef]
- Ilcev, D.S. Introduction to Coastal HF Maritime Surveillance Radars. Polish Maritime Research 2019, 26, 153–162. [Google Scholar] [CrossRef]
- Ma, H.; Antoniou, M.; Pastina, D.; Santi, F.; Pieralice, F.; Bucciarelli, M.; Cherniakov, M. Maritime Moving Target Indication Using Passive GNSS-Based Bistatic Radar. IEEE Transactions on Aerospace and Electronic Systems 2018, 54, 115–130. [Google Scholar] [CrossRef]
- Pantazis, A. LIDARs Usage in Maritime Operations and ECO – Autonomous Shipping, for Protection, Safety and Navigation for NATO Allies Awareness. 2019.
- Zardoua, Y.; Astito, A.; Boulaala, M. A Comparison of AIS, X-Band Marine Radar Systems and Camera Surveillance Systems in the Collection of Tracking Data. arXiv (Cornell University) 2022. [CrossRef]
- Karabulut Kurt, G.; Khoshkholgh, M.G.; Alfattani, S.; Ibrahim, A.; Darwish, T.S.J.; Alam, M.S.; Yanikomeroglu, H.; Yongacoglu, A. A Vision and Framework for the High Altitude Platform Station (HAPS) Networks of the Future. IEEE Communications Surveys Tutorials 2021, 23, 729–779. [Google Scholar] [CrossRef]
- Cubber, G.; Shalom, R.; Coluccia, A.; Borcan, O.; Chamrád, R.; Radulescu, T.; Izquierdo, E.; Zhelyazko Gagov. The SafeShore System for the Detection of Threat Agents in a Maritime Border Environment. 2017. [CrossRef]
- Zhao, Z.; Ji, K.; Xing, X.; Zou, H.; Zhou, S. Ship Surveillance by Integration of Space-Borne SAR and AIS – Review of Current Research. Journal of Navigation 2013, 67, 177–189. [Google Scholar] [CrossRef]
- Galdelli, A.; Mancini, A.; Ferrà, C.; Tassetti, A.N. A Synergic Integration of AIS Data and SAR Imagery to Monitor Fisheries and Detect Suspicious Activities. Sensors 2021, 21, 2756. [Google Scholar] [CrossRef]
- Saaty, T.L. The Analytic Hierarchy Process—What It Is and How It Is Used. Mathematical Modelling 1987, 9, 161–176. [Google Scholar] [CrossRef]
- Wulan, H.S.; Martharaharja, J.; Sutrasna, Y. Application of Analytical Hierarchy Process (AHP) in Determining Maritime Defense Strategy as a Follow-up to Conflict in Natuna Sea. 2020.
- De Mauro, A.; Greco, M.; Grimaldi, M. A Formal Definition of Big Data Based on Its Essential Features. Library Review 2016, 65, 122–135. [Google Scholar] [CrossRef]
- Lugmayr, A.; Stockleben, B.; Scheib, C.; Mailaparampil, M.A. Cognitive Big Data: Survey and Review on Big Data Research and Its Implications. What Is Really “New” in Big Data?. Journal of Knowledge Management 2017, 21, 197–212. [Google Scholar] [CrossRef]
- Sun, Z.; Strang, K.; Li, R. Big Data with Ten Big Characteristics. Proceedings of the 2nd International Conference on Big Data Research - ICBDR 2018 2018. [CrossRef]
- Farooqi, M.M.; Shah, M.A.; Wahid, A.; Akhunzada, A.; Khan, F.; Amin, N.U.; Ali, I. Big Data in Healthcare: A Survey. EAI/Springer Innovations in Communication and Computing 2018, 143–152. [CrossRef]
- Manyika, J.; Chui, M.; Brown, B.; Bughin, J.; Dobbs, R.; Roxburgh, C.; Byers, A.H. Big Data: The next Frontier for Innovation, Competition, and Productivity; James Manyika Michael Chui Brad Brown Jacques Bughin Richard Dobbs Charles Roxburgh Angela Hung Byers McKinsey Global Institute, 2011.
- Zikopoulos, P.C.; Eaton, C.; Deroos, D.; Deutsch, T.; Lapos, G.; Sit, S. Understanding Big Data : Analytics for Enterprise Class Hadoop and Streaming Data; New York Mcgraw Hill Professional, 2012.
- Chen, H.; Chiang, R.H.L.; Storey, V.C. Business Intelligence and Analytics: From Big Data to Big Impact. MIS Quarterly 2022, 36, 1165. [Google Scholar] [CrossRef]
- Rodger, M.; Guida, R. Classification-Aided SAR and AIS Data Fusion for Space-Based Maritime Surveillance. Remote Sensing 2020, 13, 104. [Google Scholar] [CrossRef]
- Zhang, W.; Wu, Q.M.J.; Yang, Y.; Akilan, T.; Li, M. HKPM: A Hierarchical Key-Area Perception Model for HFSWR Maritime Surveillance. IEEE Transactions on Geoscience and Remote Sensing 2022, 60, 1–13. [Google Scholar] [CrossRef]
- Lu, Y.; Ma, H.; Smart, E.; Vuksanović, B.; Chiverton, J.; Prabhu, S.R.; Glaister, M.; Dunston, E.; Hancock, C. Fusion of Camera-Based Vessel Detection and AIS for Maritime Surveillance. 2021. [CrossRef]
- Leggat, J.; Livak, T.; Parker, I.; Sinha, A.; Vidalis, S.; Wong, A. Study on Persistent Monitoring of Maritime, Great Lakes and St. Lawrence Seaway Border Regions; 2011. https://apps.dtic.mil/sti/citations/ADA555505 (accessed 2023-10-07).
- Kunz, G.J.; Bekman, H.; Benoist, K.W.; Coen, L.H.; Van Den Heuvel, L.C.; Van Putten, F. Detection of Small Targets in a Marine Environment Using Laser Radar. Proceedings of SPIE 2005. [CrossRef]
- Kanjir, U.; Greidanus, H.; Oštir, K. Vessel Detection and Classification from Spaceborne Optical Images: A Literature Survey. Remote Sensing of Environment 2018, 207, 1–26. [Google Scholar] [CrossRef] [PubMed]
- Teseï, A.; Been, R.; Williams, D.P.; Cardeira, B.; Cecchi, D.; Garau, B.; Maguer, A. Passive Acoustic Surveillance of Surface Vessels Using Tridimensional Array on an Underwater Glider. OCEANS 2015. [CrossRef]
- Rice, J.S.; Wilson, G.R.; Barlett, M.; Smith, J.O.; Chen, T.; Fletcher, C.L.; Creber, B.; Rasheed, Z.; Taylor, G.; Haering, N. Maritime Surveillance in the Intracoastal Waterway Using Networked Underwater Acoustic Sensors Integrated with a Regional Command Center. 2010. [CrossRef]
- Moutray, R.E.; Ponsford, A.M. Integrated Maritime Surveillance: Protecting National Sovereignty. 2004. [CrossRef]
- Department of the Prime Minister and Cabinet Wellington. MARITIME PATROL REVIEW; DPMC: New Zealand, 2001; https://www.dpmc.govt.nz/sites/default/files/2017-03/maritime_patrol_review.pdf (accessed 2023-10-07). [Google Scholar]
- Tares, T.; Greidanus, H.; Jurquet, G.; Hélie, P. Wide Maritime Area Airborne Surveillance SoS. Systems Conference, 3rd Annual IEEE 2009. [CrossRef]
- Martorella, M.; Aboutanios, E. BalSAR: A Stratospheric Balloon-Borne SAR System. NATO science for peace and security series 2020. [CrossRef]
- Soldi, G.; Gaglione, D.; Forti, N.; Simone, A.D.; Daffina, F.C.; Bottini, G.; Quattrociocchi, D.; Millefiori, L.M.; Braca, P.; Carniel, S.; Willett, P.; Iodice, A.; Riccio, D.; Farina, A. Space-Based Global Maritime Surveillance. Part I: Satellite Technologies. IEEE Aerospace and Electronic Systems Magazine 2021, 36, 8–28. [Google Scholar] [CrossRef]
- Santamaria, C.; Alvarez, M.; Greidanus, H.; Syrris, V.; Soille, P.; Argentieri, P. Mass Processing of Sentinel-1 Images for Maritime Surveillance. Remote Sensing 2017, 9, 678. [Google Scholar] [CrossRef]
- EMSA. COPERNICUS MARITIME SURVEILLANCE PRODUCT CATALOGUE; European Maritime Safety Agency: Lisbon, 2019; https://www.copernicus.eu/sites/default/files/2019-10/Copernicus_Product_Catalogue_20190725_0.pdf (accessed 2023-10-07). [Google Scholar]
- Hang, J.C.; Clay, D.E. IGrow Corn: Best Management Practices. In iGrow Corn: Best Management Practices; South Dakota State University, 2016.
- Mano, J.-P.; Georgé, J.; Gleizes, M.P. Adaptive Multi-Agent System for Multi-Sensor Maritime Surveillance. Advances in intelligent and soft computing 2010, 285–290. [Google Scholar] [CrossRef]
- Melillos, G.; Themistocleous, K.; Danezis, C.; Michaelides, S.; Hadjimitsis, D.; Jacobsen, S.; Tings, B. Mashup Tools for Big Data Analysis in Maritime Surveillance. Ktisis at Cyprus University of Technology (Cyprus University of Technology) 2020. [CrossRef]
- Newland, F.T.; Coleshill, E.; Dsouza, I.; Cain, J. Nanosatellite Tracking of Ships—Review of the First Year of Operations; 2009.
- International Maritime Organization. Long-range identification and tracking (LRIT). www.imo.org. https://www.imo.org/en/OurWork/Safety/Pages/LRIT.aspx (accessed 2023-10-12).
- Kilby, P.; Mercer, G.N. Examining Methods for Maximising Ship Classifications in Maritime Surveillance. In 18th World IMACS / MODSIM Congress; Australia, 2009; pp. 1629–1635.
- Leclerc, M.; Tharmarasa, R.; Florea, M.C.; Boury-Brisset, A.-C.; Kirubarajan, T.; Duclos-Hindie, N. Ship Classification Using Deep Learning Techniques for Maritime Target Tracking. 2018 21st International Conference on Information Fusion (FUSION) 2018. [CrossRef]
- Jović, M.; Tijan, E.; Marx, R.; Gebhard, B. Big Data Management in Maritime Transport. Pomorski zbornik 2019, 57, 123–141. [Google Scholar]
- Yan, Z.; Song, X.; Zhong, H.; Yang, L.; Wang, Y. Ship Classification and Anomaly Detection Based on Spaceborne AIS Data Considering Behavior Characteristics. Sensors 2022, 22, 7713. [Google Scholar] [CrossRef]
- Teixeira, E.; Araujo, B.; Costa, V.; Mafra, S.; Figueiredo, F. Literature Review on Ship Localization, Classification, and Detection Methods Based on Optical Sensors and Neural Networks. Sensors 2022, 22, 6879. [Google Scholar] [CrossRef] [PubMed]
- Ponsford, T.; D’Souza, I.; Kirubarajan, T. Surveillance of the 200 Nautical Mile EEZ Using HFSWR in Association with a Spaced-Based AIS Interceptor. 2009. [CrossRef]
- Ganesh, E.N.; Rajendran, V.; Ravikumar, D.; Kumar, P. Sai. ; Revathy, G.; Harivardhan, P. Remote Sensing Analysis Framework for Maritime Surveillance Application. International Journal of Remote Sensing 2021, 15, 11–17. [Google Scholar]
- Lane, R.O. ; Nevell, David. A.; Hayward, S.D.; Beaney, T.W. Maritime anomaly detection and threat assessment. IEEE Xplore. [CrossRef]
- Gorokhov, V. Scientific Investigation, Technological Development and Economical Governmental Support: The Historical Development of RADAR Science and Technology. Institute for Philosophy of the Russian Academy of Sciences 1999.
- Sevgi, L.; Ponsford, A.M. An HF Radar Based Integrated Maritime Surveillance System. 1999.
- Braca, P.; Maresca, S.; Grasso, R.; Bryan, K.; Horstmann, J. Maritime Surveillance with Multiple Over-The-Horizon HFSW Radars: An Overview of Recent Experimentation. IEEE Aerospace and Electronic Systems Magazine 2015, 30, 4–18. [Google Scholar] [CrossRef]
- Xu, H.; Moreira, L.; Guedes Soares, C. Maritime Autonomous Vessels. Journal of Marine Science and Engineering 2023, 11, 168. [Google Scholar] [CrossRef]
- Rüssmeier, N.; Hahn, A.; Nicklas, D.; Zielinski, O. A Research Port Test Bed Based on Distributed Optical Sensors and Sensor Fusion Framework for Ad Hoc Situational Awareness. Journal of Sensors and Sensor Systems 2017, 6, 37–52. [Google Scholar] [CrossRef]
- Prasad, D.K.; Rajan, D.; Rachmawati, L.; Rajabaly, E.; Quek, C. Video Processing from Electro-Optical Sensors for Object Detection and Tracking in Maritime Environment: A Survey. arXiv (Cornell University) 2016. [CrossRef]
- Elechi, P.; Orike, S. Performance Analysis of Unmanned Aerial Vehicles (UAV) for Improved Aerial Surveillance. Zenodo (CERN European Organization for Nuclear Research) 2023. [CrossRef]
- Shi, J.; Liu, Z. Deep Learning in Unmanned Surface Vehicles Collision-Avoidance Pattern Based on AIS Big Data with Double GRU-RNN. Journal of Marine Science and Engineering 2020, 8, 682–682. [Google Scholar] [CrossRef]
- Milios, A.; Bereta, K.; Chatzikokolakis, K.; Zissis, D.; Matwin, S. Automatic Fusion of Satellite Imagery and AIS data for Vessel Detection. IEEE Xplore. [CrossRef]
- Shabbir, Z.; Sarosh, A.; Nayyer, M. Space Technology Applications for Maritime Intelligence, Surveillance, and Reconnaissance. Astropolitics 2019, 17, 104–126. [Google Scholar] [CrossRef]
| Project | Platform | Surveillance Range | Oversight Purpose / Activities | Sensors | Database | Executor |
|---|---|---|---|---|---|---|
| COPERNICUS | Satellite-Ground Observation (Land-Sea-Air) | EU maritime Jurisdiction | Obtaining large amounts of global data by fusing data collected from Copernicus satellites, air and sea sensors, and ground stations, transforming this data into meaningful information and using it in the services needed | Satellite family (Satellite-1A/1B [SAR], Satellite-2A/2B [Multispectral Optical Sensors], Satellite-3A/3B [Medium Resolution Optical Sensor and Altimeter], Satellite-5P [Atmospheric Chemistry Sensor], Earth observation data [S-AIS, VTS, VMS, LRIT, IFS] | Surface meteorological and oceanographic data, Landforms and ice formations, Sea maps, Sea surface temperature, Chlorophyll-a and pollutant data | European Union |
| SCANMARIS | Software Family | Up to 200 Nautical Miles (nm) | Uninterrupted monitoring of EU maritime jurisdictions, making sense of large amounts of complex data from different sources, autonomously detecting anomalies in the sea with modelling and machine learning algorithms and notifying users | - | Data from satellite, Radar, AIS, RDF, VTS sensors and Traffic2000, Lloyds, Paris MoU, ICCATT, TF2000, EQUASIS, TROCS, SATI databases within the EU | French National Research Center |
| I2C | Land - Sea (Ships - Naval Aircraft) - Air (Aircraft - Airship) | Up to 200 nm | Creating a new generation of innovative maritime border surveillance systems to monitor all vessel movements at sea in order to detect maritime anomalies/suspicious events and to identify and report associated threats in advance | HFSWR and FMCW Radars, AIS | Flag state information, meteorological data, intelligence database | Naval Group (French) |
| COMPASS2020 | Land (Operation Center) - Sea (1 Patrol Ship, 1 Unmanned Underwater Vehicle) - Air (1 High, 2 Medium-Low Altitude Unmanned Air Vehicle) | Up to 200 nm |
Demonstrating that the coordinated use of manned and unmanned technology and vehicles in air, sea and submarine can achieve more successful results in information gathering and rapid response to maritime surveillance needs, increasing situational awareness at sea by providing cost-effective and reliable operational solutions to the coast guard and maritime authorities | Zephyr (Radar and infrared camera) AR3 (electro optical camera) AR5 (S-AIS, Radar, electro-optical and infrared camera) |
Naval picture transferred to the maritime operations center | Portugal General Directorate of Maritime Enterprises |
| MARINE-EO | Software Family | EU Maritime Jurisdiction | Within the scope of Copernicus security service, to contribute to the development of EUROSUR legislation and CISE by creating an improved change detection detection system for monitoring anomalies around critical infrastructures and combating irregular migration, and strengthening international cooperation on maritime situational awareness | - | Copernicus System Sensors, CISE | Greek National Center for Scientific Research |
| EFFECTOR | Software Family | EU Maritime Jurisdiction | To create a data lake in order to detect different and new types of events that may be encountered at sea faster and more accurately, to improve maritime surveillance capabilities by applying data fusion and data analysis methods, to improve decision support and to increase the interoperability of maritime stakeholders | - | CISE and EUROSUR integrated national and international databases | French Naval General Secretariat |
| SPYGLASS | Land-Sea (Buoy / Platform) | EU Maritime Jurisdiction | To develop a low-cost, stealthy and environmentally friendly contact detection method by collecting the refracted and reflected signals of GNSS signals over contacts on the ground with passive radars deployed on land, sea and air platforms | Passive Bistatic Radar (PRB) | Naval image database was created in the command centre | ASTER S.P.A. Ltd. (Italy) |
| SAFESHORE | Land (Mobile-Fixed Trailer) | Up to 1 nm | Developing an effective system to detect small Unmanned Air Vehicle (UAVs) that can be flown from civilian ships when they cross the country's maritime border, creating an autonomous and mobile maritime surveillance system to detect low-altitude flying targets | Meteorological sensors lidar (3D/2D) Short/long range (0-1800 meters) thermal and electro-optical camera passive acoustic sensor, passive radio detection | Created target characteristic database | Royal Military Academy of Belgium |
| RANGER | Land | Up to 200 nm | To create a high-capacity and innovative surveillance platform by combining innovative radar technologies with state-of-the-art early warning solutions to detect, track, recognize and identify ships at greater distances than existing maritime surveillance systems, to reduce the response times of operational units and to increase the response capacity of operational units | OTH Radar PE-MIMO Radar | Copernicus Meteorology AIS,VTS, CISE |
UNEX SOFTWARE Ltd. (United Kingdom) |
| PROMENADE | Software Family | EU Maritime Jurisdiction | To carry out maritime surveillance activities with maximum efficiency by using big data and artificial intelligence technologies, to generate meaningful information from maritime big data, to identify risky vessels before they enter EU maritime jurisdictions | - | VDES System Data Lake National databases | Greek Ministry of Maritime and Island Policy |
| Alternative | System/Project Used | Pros | Cons |
|---|---|---|---|
| Coastal radar systems |
I2C, Spyglass, Ranger |
Widespread usage High detection capability Wide area surveillance Continuous surveillance Relatively low cost Integrated operation |
Affected by meteorological conditions Risk of not being able to detect small, fast and non-metallic boats and the people on the water |
| Sea-borne surveillance |
I2C, Spyglass |
Possibility of continuous movement Containing different sensors High detection and diagnostic capability |
Affected by meteorological conditions Being widely manned and the risks of human error High costs Failure to perform the task without interruption |
| Coastal optical systems | Safeshore | Ability to provide high resolution images in day and night conditions Continuous surveillance High diagnostic capability Integrated operation |
Affected by meteorological conditions such as fog, haze and precipitation Diminishing effectiveness as distance increases |
| Air-borne surveillance |
Compass2020, I2C | High mobility Ability to scan large areas quickly and efficiently Containing different sensors High detection and diagnostic capability |
Affected by meteorological conditions Being widely manned and the possibility of human error High costs Failure to perform the task without interruption |
| Vessel Monitoring Systems | Copernicus, Scanmaris, Compass2020, MarineEO, Effector, Ranger, Promenade |
Ability to present large amounts of diverse and accurate data Integrated operation Covering a large number of vessels by regulatory obligation |
System shutdown / spoofing / malfunction Need to be supported with other systems |
| Space-borne Surveillance | Copernicus, Cleanseanet, Effector, Promenade |
Wide area surveillance High resolution sea image transmission through SAR and optical sensors |
High cost Technical and technological limitations Data communication and data rate problems |
| Coastal acoustic systems | Safeshore | Low cost Ability to work in secrecy Integrated operation |
Ineffective in detecting overwater contacts Effected by environmental conditions Restricted range |
| No. | Experience | Education | Graduation | Sector |
|---|---|---|---|---|
| 1 | 23 years | PhD | Maritime Transportation Management Engineering | Public-Education |
| 2 | 23 years | PhD | Electrical and Electronics Engineering | Private-Defense Industry |
| 31 | 22 years | MSc | Electrical and Electronics Engineering | Public-Maritime Safety |
| 4 | 19 years | MSc | Radar Specialization | Public-Maritime Safety |
| 5 | 18 years | MSc | Electrical and Electronics Engineering | Public-Maritime Safety |
| 61 | 6 years | BSc | Maritime Transportation Management Engineering | Public-Maritime Safety |
| 71 | 3 years | BSc | Maritime Transportation Management Engineering | Public-Maritime Safety |
| No. | Alternative | Percent (%) |
|---|---|---|
| 1 | Coastal Radar Systems | 23,56 |
| 2 | Sea-borne Surveillance | 23,20 |
| 3 | Coastal Optical Systems | 17,04 |
| 4 | Air-borne Surveillance | 16,21 |
| 5 | VMS | 9,73 |
| 6 | Space-borne Surveillance | 5,63 |
| 7 | Coastal Acoustic Systems | 4,63 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).





