Submitted:
08 November 2023
Posted:
08 November 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Unlike centrally managed clouds, massively heterogeneous systems in the continuum (including IoT devices, edge devices and cloud infrastructures) are significantly more complex to manage. Furthermore, distributed data management raises an additional level of complexity by classifying data infrastructures, collecting vast and diverse data volumes, providing transparent data access methods, optimizing the internal dataflow, and effectively preserving data collections [13].
- Heterogeneity of the involved devices and associated technologies. Hence, hardware and technology agnostic protocols are important not only to manipulate a large number of interconnected entities, but also to enable scalability which is a key concept in the IEC continuum.
- The continuum needs to be effectively managed to optimally meet the application demands during service execution, taking into account multiple constraints, such as the location of the involved nodes (edge or IoT), their transmission and processing capabilities, as well as their energy footprint. Optimum resource allocation in multi-node heterogeneous environments might lead to highly non-convex problems. In this context, machine learning (ML) algorithms have emerged as a promising approach that can solve various optimization problems providing near-optimal solutions [14,15]. In traditional centralized ML approaches, all collected data are sent to a high-performance computing node for proper model training and inference. However, on one hand the collection of heterogeneous data from all involved nodes of the continuum might increase pre-processing load, and on the other hand centralized ML training might jeopardize latency requirements in critical applications. Therefore, as it will also be described in Section II, the support of distributed and decentralized ML approaches is a key concept in IEC systems [16,17,18].
- Due to the distributed and dynamic nature of the continuum, with plenty of devices from different owners and provenance, the application of reliability and trustiness becomes fundamentally challenging. Secure mechanisms to access the distributed nodes, data privacy preservation, and providing open and transparent operation is fundamental to enhance trustworthiness [19].
- As it was previously mentioned, the continuum puts together a broad and diverse space with multiple heterogeneous devices and protocols. Although there are several standards, open-source projects and foundations that focus on global communication and management protocols, the envisioned continuum must also consider that some constrained devices will not support any specific tool. Therefore, contributing to an open ecosystem favors interoperability with existing and emerging frameworks, which is a key challenge towards next generation broadband wireless networks [20].
1.1. Related Works
1.2. Contributions
- Recent works in the IEC continuum are presented, with emphasis on the challenges they deal with, as well as on the supporting technologies.
- Basic limitations are identified, and open research directions are analyzed as well. This discussion on open issues takes into consideration the coexistence of IEC systems with next generation broadband wireless networks.
- Indicative use cases are presented, where the synergy among IoT, edge and cloud nodes is highlighted towards optimum service deployment and user experience.
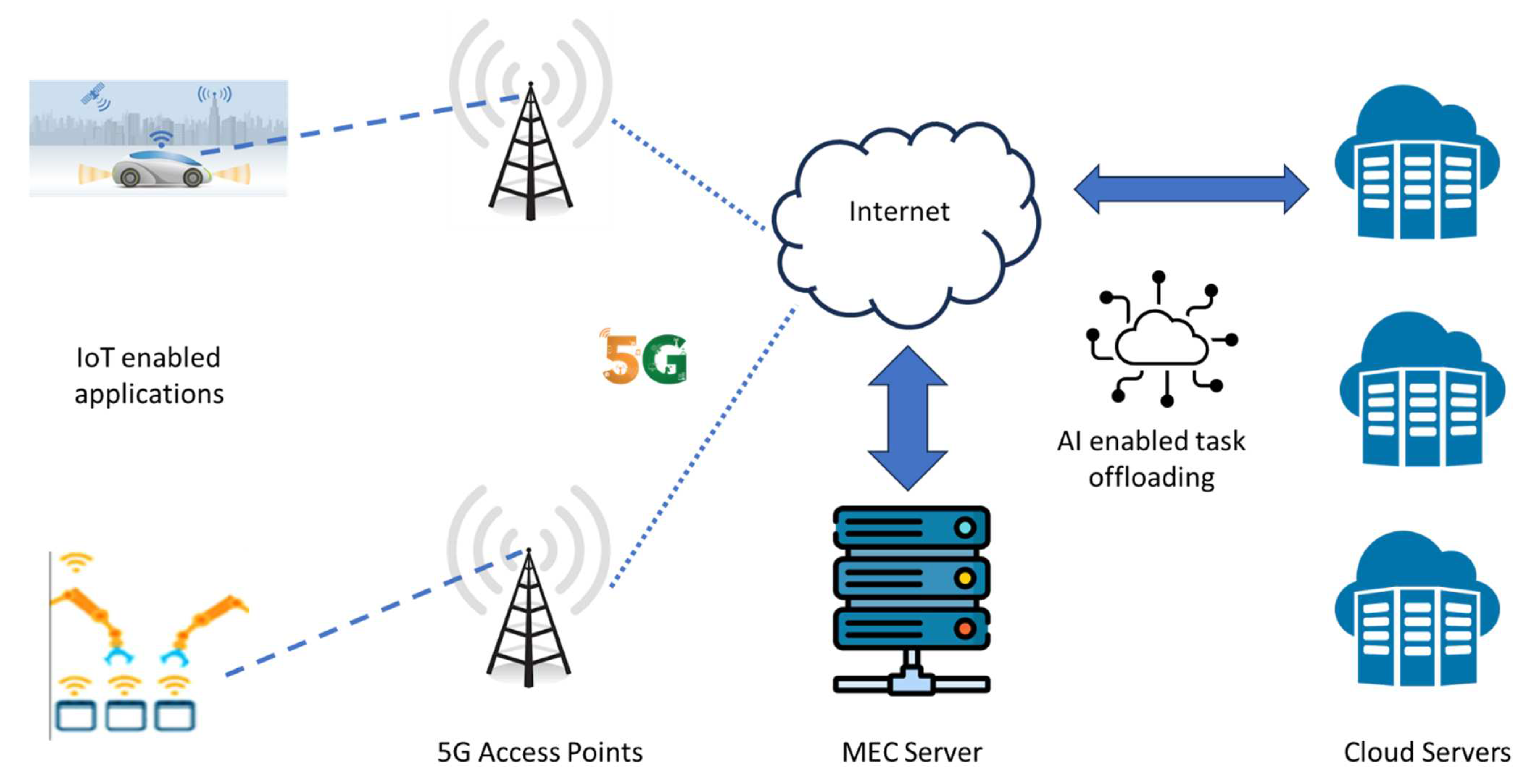
2. Supporting Technologies in the IoT Edge Cloud Continuum
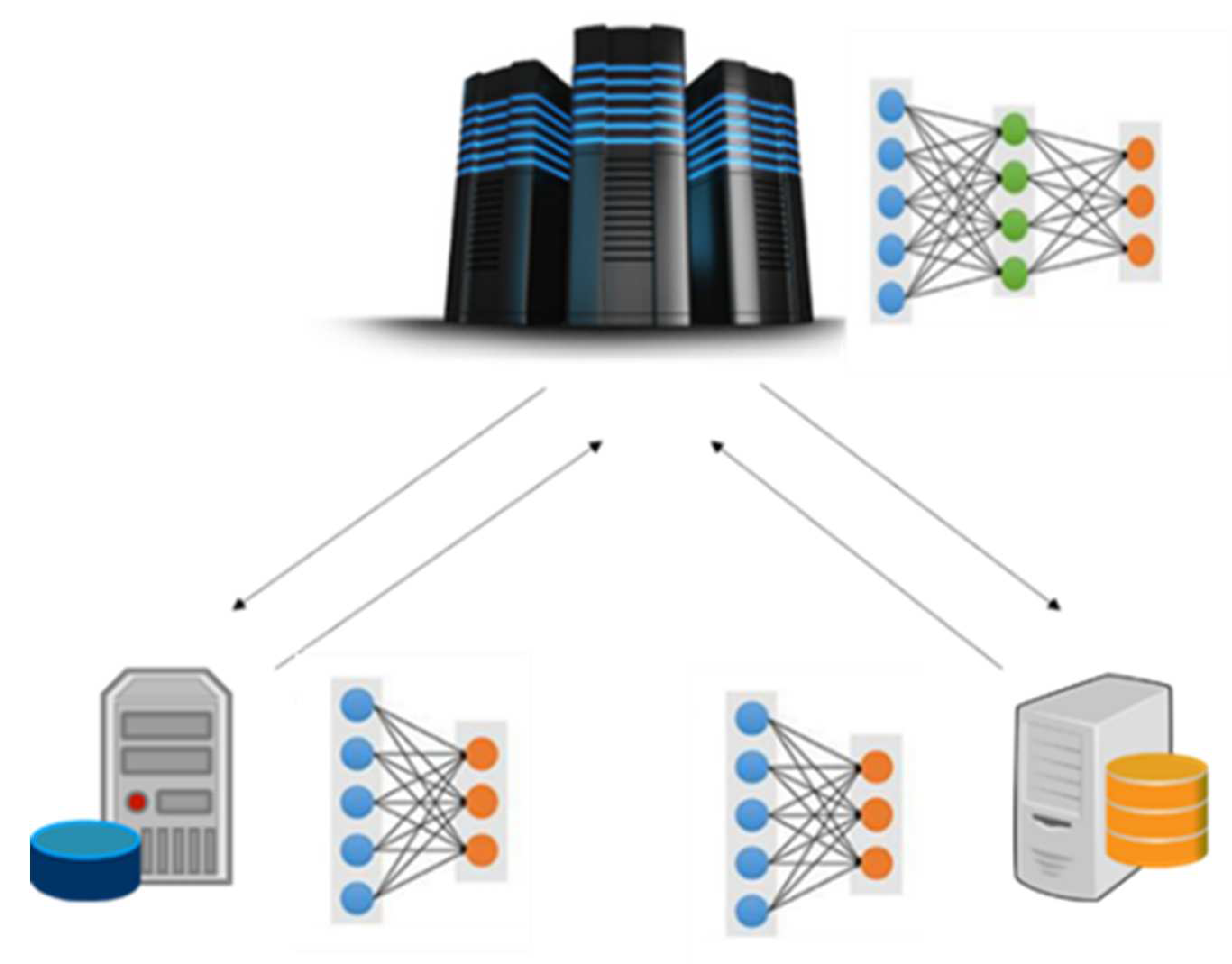
2.1. Distributed and Decentralized Machine Learning
2.2. Serverless Computing
2.3. Blockchain Technology
2.4. Subnetworks
2.5. Device to Device Communications
3. Indicative Use Cases
3.1. IoT in Agriculture
3.2. Energy Management and Decision Support System
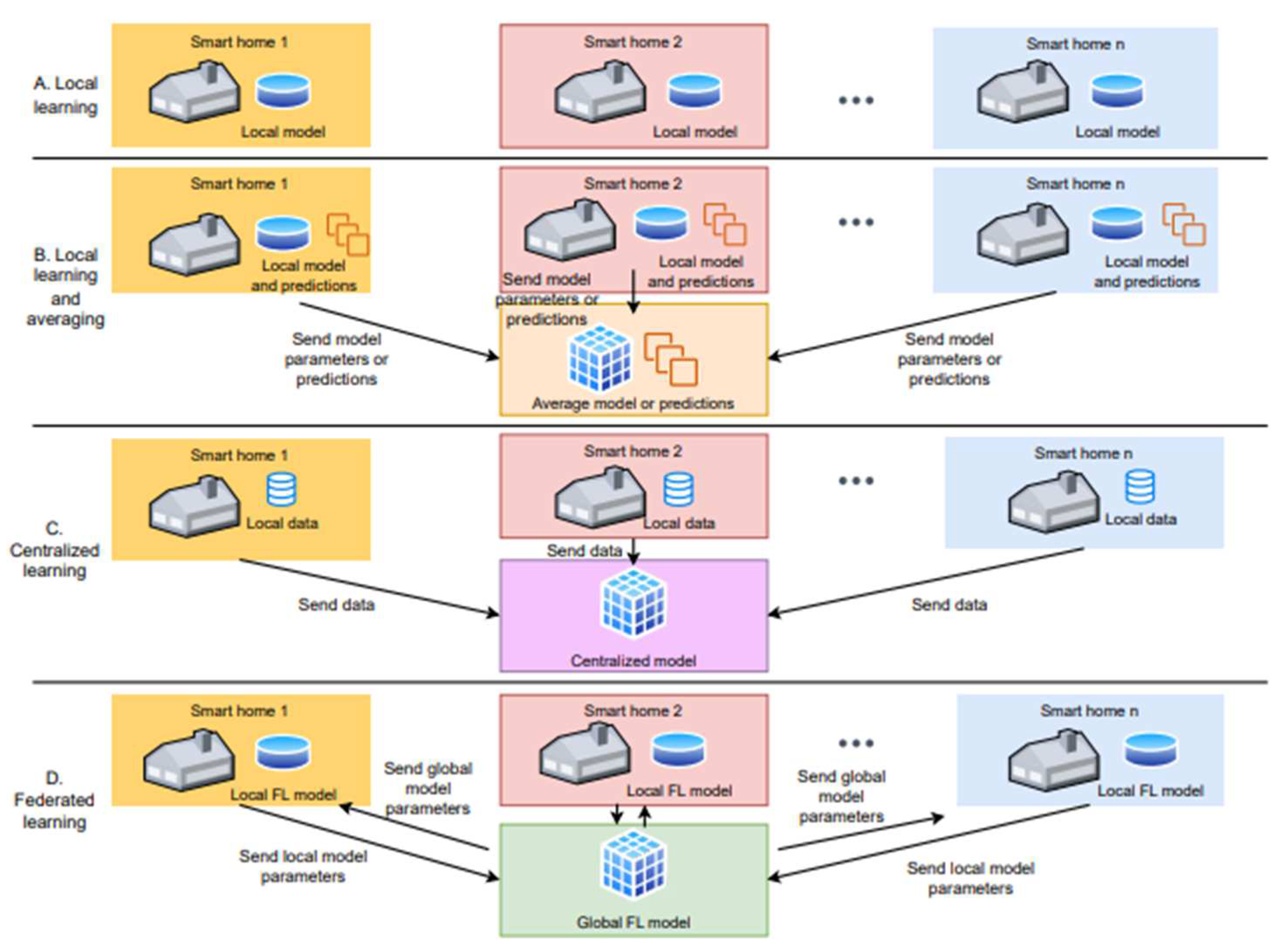
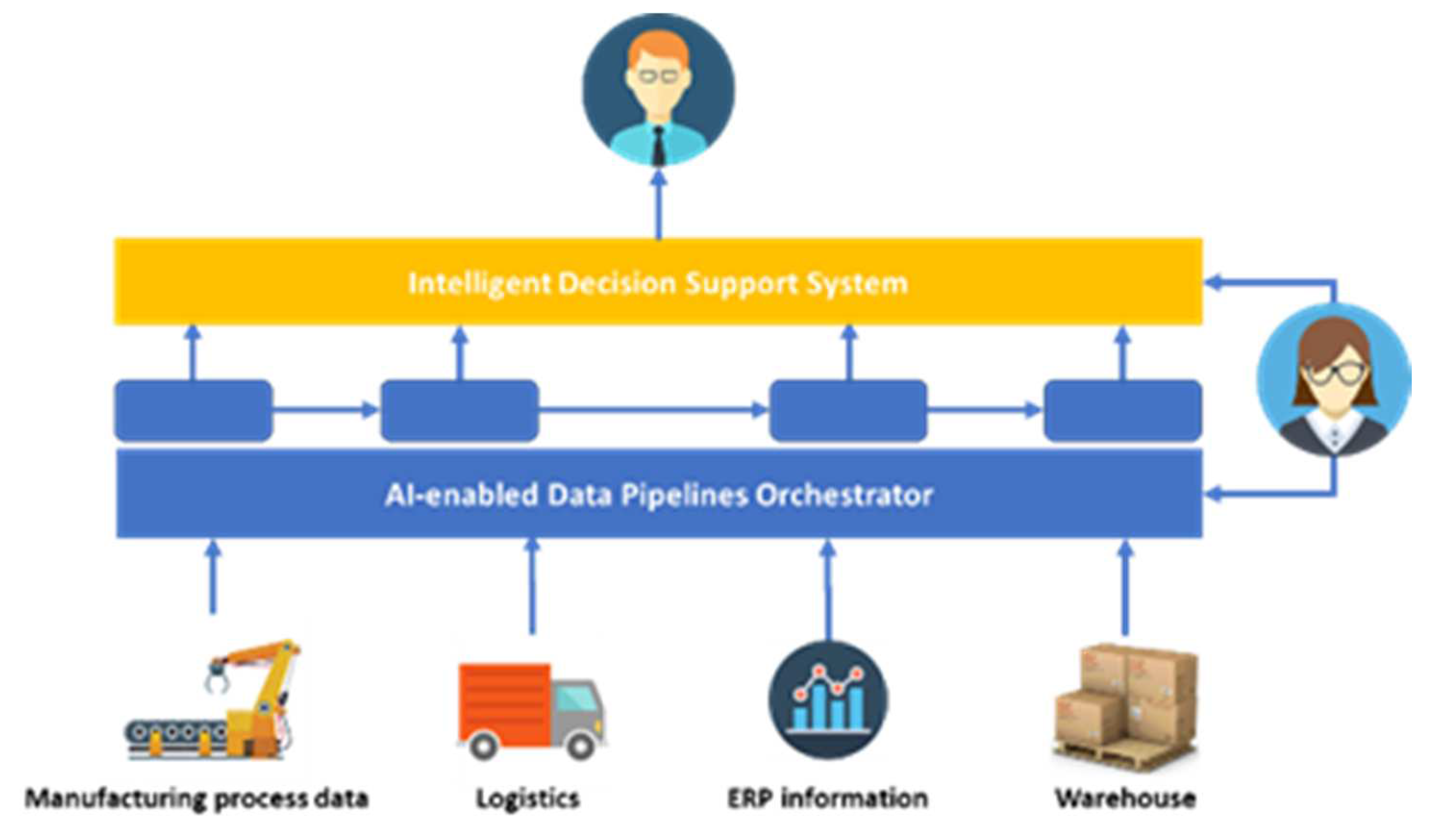
3.3. Smart Manufacturing
3.4. Smart Cities
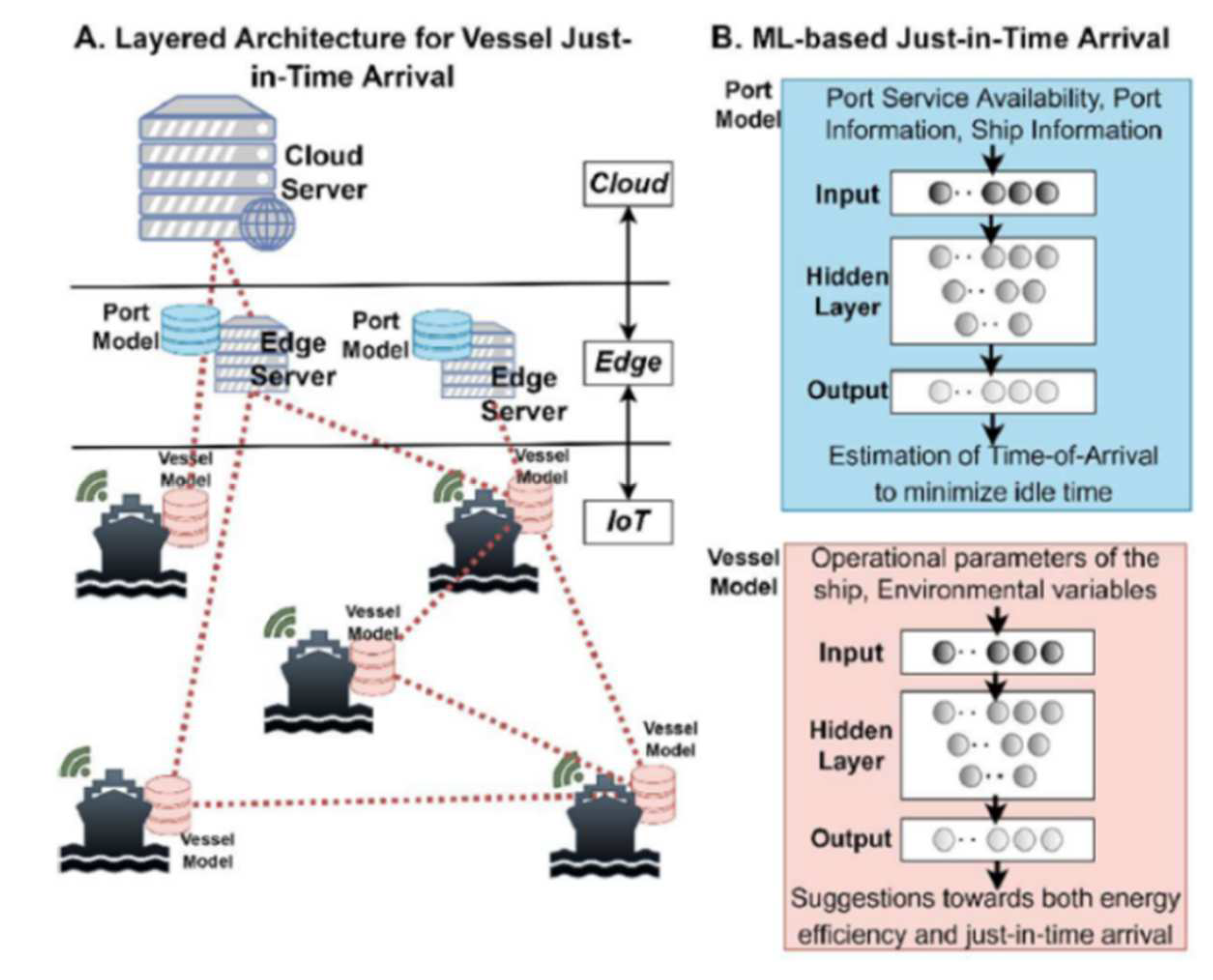
3.5. Maritime Applications
4. Recent Works in IoT-Edge-Cloud Continuum Architectures
5. Discussion – Open Issues
- In the cases of ML model training, then in the majority of the studied works, such as in [75], [80], [102], [107], DRL approaches have been considered, as they can adapt more effectively to various network deployments and reconfigurations. The alternative approaches of supervised or unsupervised learning would involve data collection from scratch and retraining that can increase the computational load and deteriorate system’s latency.
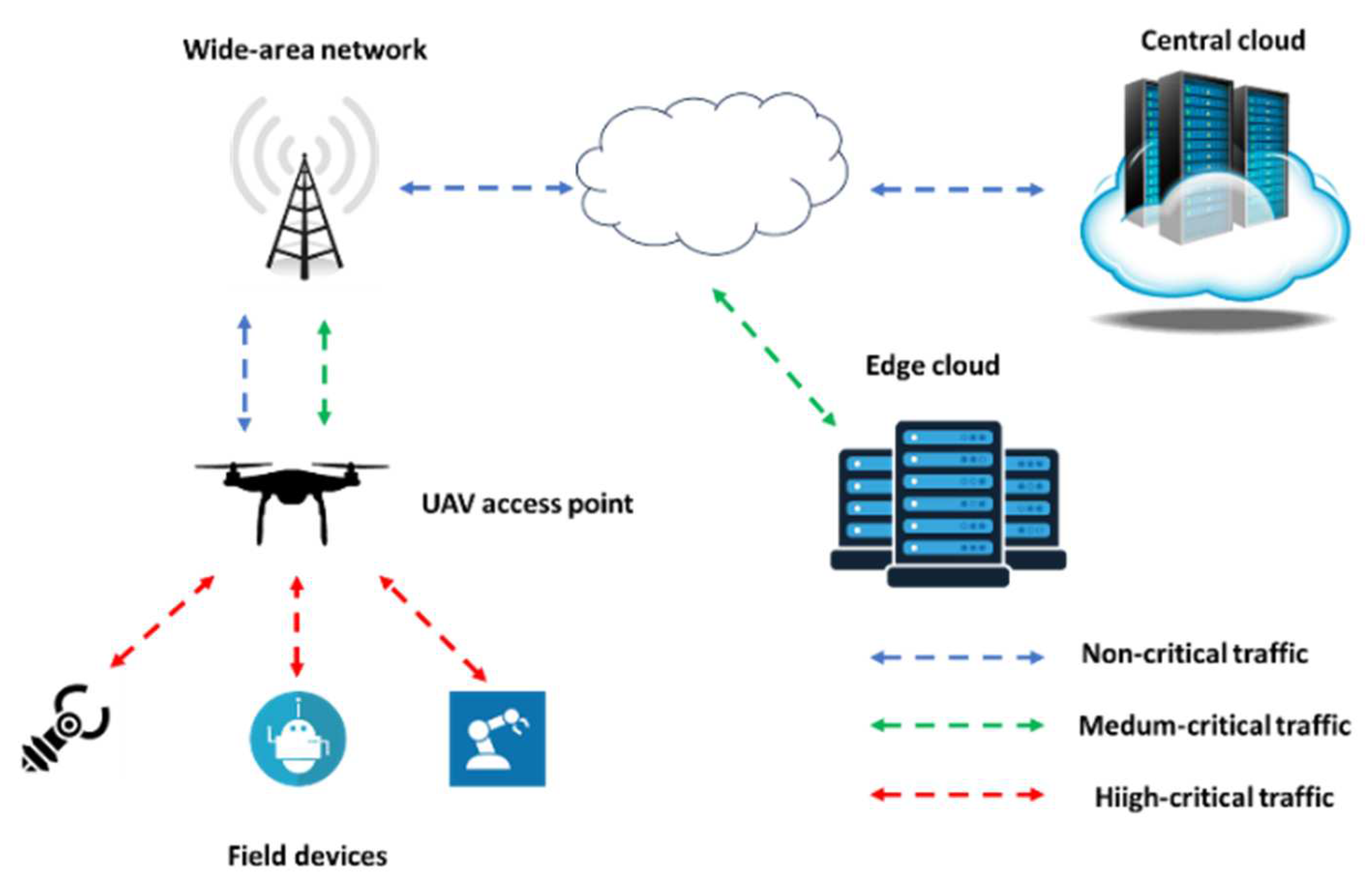
- The full deployment of highly demanding latency applications, such as autonomous driving or zero touch smart manufacturing could be leveraged by private IEC infrastructures to avoid imbalance in the computational load of edge or cloud servers from other applications and public networks’ latency. In this case, private 5G infrastructures can be deployed within the premises of a manufacturing unit along with dedicated edge servers that process data and train ML models. In cases of dispersed units, these data can be then sent to private cloud domains for further analysis and macroscopic KPI optimization.
- There is a fundamental tradeoff among the enforcement of strict security policies in every data transfer procedure among IoT nodes and edge cloud/servers and computational load. In these cases, the concept of trusted nodes can be applied: IoT nodes enter the IEC only after their robustness against specific security attacks has been verified. Even so, this does not rule out the possibility of future attacks. Therefore, anomaly detection algorithms in the edge or cloud domain can detect unusual data patterns.
- Serverless computing along with blockchain technology can be quite effective towards the concept of PaaS in IEC systems, due to the elimination of third-parties involvement. By decomposing service computations as a set of microservices, service providers could make the most out of the cloud and edge computing exploiting their elasticity. During its lifetime, the service could scale-in or scale-down to adjust the number of instances of each microservice to the workload, thus, reducing the operational expenditures of the service.
- In the same context, as derived from the presented works, there are still open issues to be addressed prior to the full deployment of the IEC continuum:
- Resource optimization is important in the IEC continuum, due to the magnitude of involved infrastructures and applications. Therefore, the employed ML models should be in position to collect and aggregate a vast amount of heterogeneous data from diverse sources. Moreover, the developed ML models should be applicable to multiple scenarios in the IEC framework.
- Although hardware and computational complexity along with latency reduction during task execution and efficient task offloading are the main KPIs under evaluation in an IEC ecosystem, the design and development of «green» networks is extremely important towards the new era of 6G communications. In this context, the mass number of interconnected devices may have a severe impact on the energy footprint which should be taken into account during IEC design as well. In addition, ML algorithms consume more energy compared to regular algorithms due to the increasing complexity of running and training models. Therefore, the design and implementation of less complex algorithms while maintaining the accuracy rate, is also a key challenge towards green-based architectures.
- While some recent ML research works address intelligent orchestration and control of different edge-cloud systems, there is still a lack of integrated AI solutions to optimize the edge-cloud continuum. Therefore, it is essential to integrate ML techniques at different layers of the architecture while dynamically optimizing the edge-cloud continuum software, data and resources orchestration as a whole. A range of techniques such as federated learning for privacy, transfer learning for model reuse at the device, and different deep reinforcement learning architectures can be applicable for various optimization goals.
- The vast majority of related works considers performance evaluation of the proposed approach per case in limited orientations (e.g., laboratory evaluation or moderate number of participating nodes). Therefore, large scale evaluation is important not only to examine scalability issues, but also to identify potential limitations when full deployment takes place.
- The full deployment of the IEC computing systems is inextricably connected with an integration of diverse hardware elements and infrastructures, thus leading not only to a highly heterogeneous environment, but also to functions and features that cannot be anticipated at the time of design. The distributed, dynamic, and programmable nature of the entire IEC continuum along with the fragmentation of data as well as the need for supporting cross-platforms interoperability, makes the application of security and trust fundamentally challenging. Since such systems unavoidably lead to a corresponding increase in the number and types of potential attacks, such attacks need to be predicted and anticipated with the help of AI systems.
- The IEC framework should be able to provide autonomous reconfigurability according to network conditions, user and application requirements, as well as according to other design goals such as minimization of the energy footprint which was previously mentioned. Indeed, the requirement for increased autonomous reconfigurability is emerging due to the ever more demanding services and the impact these services have on daily human activities (e.g., e-health applications).
- Although there are many open-source frameworks for various functionalities involved in the IEC continuum, such as Apache Kafka for telemetry and data streaming [109], TensorFlow for machine learning [110], and Flower for federating learning deployment [111], there is not until now a unified open-source framework that can support scalability over large IEC infrastructures. This diversity in programming frameworks and models hinders the efficient development of the continuum solutions.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 2D/3D Two/Three Dimensional |
| 5G Fifth Generation |
| 6G Sixth Generation |
| AI Artificial Intelligence |
| AP Access Point |
| CCM Container Cluster Manager |
| CPU Central Processing Unit |
| D2D Device to Device |
| DL Deep Learning |
| DRL Deep Reinforcement Learning |
| DNS Domain Name Server |
| DNSNA DNS Name Autoconfiguration |
| DQL Deep Q-Learning |
| E2E End-to-End |
| EC Edge Computing |
| ECN Edge Computing Node |
| EV Electrical Vehicle |
| FL Federated Learning |
| IEC IoT-Edge-Cloud |
| IIoT Industrial Internet of Things |
| IoE Internet of Energy |
| IoT Internet of Things |
| IoTEF Internet of Things Edge-Cloud Federation |
| IoV Internet of Vehicles |
| ECDriven-IoT Edge Computing Driven IoT |
| KPI Key Performance Indicator |
| LAN Local Area Network |
| MEC Multi-access Edge Computing |
| ML Machine Learning |
| NAN Neighborhood Area Network |
| NB NarrowBand |
| NN Neural Network |
| NFV Network Function Virtualization |
| OS Operating System |
| P2P Peer to Peer |
| PaaS Platform-as-a-Service |
| PA Precision Agriculture |
| PDS Post-Decision State |
| QoS Quality of Service |
| RSSI Received Signal Strength Indicator |
| SAR Search and Rescue |
| SDN Software Defined Networking |
| UAV Unmanned Aerial Vehicle |
| USV/UUV Unmanned Surface/ Underwater Vehicle |
| V2V Vehicle to Vehicle |
| VNE Virtual Network Embedding |
References
- Masip, X.; Marín-Tordera, E.; Tashakor, G.; Jukan, A.; Ren, G.-J. Foggy clouds and cloudy fogs: A real need for coordinated management of fog-to-cloud (F2C) computing systems. IEEE Wirel. Commun. Magazine 2016, 23, 120–128. [Google Scholar] [CrossRef]
- Pan, J.; McElhannon, J. Future edge cloud and edge computing for internet of things applications. IEEE Internet Things J. 2018, 5, 439–449. [Google Scholar] [CrossRef]
- Zhou, I. Internet of things 2.0: Concepts, applications, and future directions. IEEE Access, 2021; 9, 70961–71012. [Google Scholar] [CrossRef]
- Bhuiyan, M. N.; Rahman, M. M.; Billah, M. M.; Saha, D. Internet of Things (IoT): A review of its enabling technologies in healthcare applications, standards protocols, security, and market opportunities. IEEE Internet Things J. 2021, 8, 10474–10498. [Google Scholar] [CrossRef]
- Filali, A.; Abouaomar, A.; Cherkaoui, S.; Kobbane, A.; Guizani, M. Multi-access edge computing: A Survey. IEEE Access 2020, 8, 197017–197046. [Google Scholar] [CrossRef]
- Jiang, K.; Zhou, H.; Chen, X.; Zhang, H. Mobile edge computing for ultra-reliable and low-latency communications. IEEE Commun. Stand. Magazine 2021, 5, 68–75. [Google Scholar] [CrossRef]
- Belcastro, L.; Marozzo, F.; Orsino, A.; Talia, D.; Trunfio, P. Edge-Cloud continuum solutions for urban mobility prediction and planning. IEEE Access 2023, 11, 38864–38874. [Google Scholar] [CrossRef]
- Cohen, I.; Chiasserini, C. F.; Giaccone, P.; Scalosub, G. Dynamic service provisioning in the edge-cloud continuum with bounded resources. IEEE/ACM Transactions on Networking 2023. [Google Scholar] [CrossRef]
- Al-Quzweeni, A. N.; Lawey, A. Q.; Elgorashi, T. E. H.; Elmirghani, J. M. H. Optimized energy aware 5G network function virtualization. IEEE Access 2019, 7, 44939–44958. [Google Scholar] [CrossRef]
- Cisneros, J. C.; Yangui, S.; Hernández, S. E. P.; Drira, K. A survey on distributed NFV multi-domain orchestration from an algorithmic functional perspective. IEEE Commun. Mag. 2022, 60, 60–65. [Google Scholar] [CrossRef]
- Cox, J. H. Advancing software-defined networks: A survey. IEEE Access, 2017; 5, 25487–25526. [Google Scholar]
- Raeisi-Varzaneh, M.; Dakkak, O.; Habbal, A.; Kim, B.-S. Resource scheduling in edge computing: Architecture, taxonomy, open issues and future research directions. IEEE Access 2023, 11, 25329–25350. [Google Scholar] [CrossRef]
- Cuzzocrea, A. Effective and efficient big data management in distributed environments: Models, issues, and research perspectives. In Proceedings of the 19th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID), Larnaca, Cyprus; 2019; pp. 556–560. [Google Scholar] [CrossRef]
- Samie, F.; Bauer, L.; Henkel, J. From cloud down to things: An overview of machine learning in internet of things. IEEE Internet Things J. 2019, 6, 4921–4934. [Google Scholar] [CrossRef]
- Giannopoulos, A.; Spantideas, S.; Kapsalis, N.; Karkazis, P.; Trakadas, P. Deep reinforcement learning for energy-efficient multi-channel transmissions in 5G cognitive HetNets: Centralized, decentralized and transfer learning based solutions. IEEE Access 2021, 9, 129358–129374. [Google Scholar] [CrossRef]
- Alsagheer, D.; Xu, L.; Shi, W. Decentralized machine learning governance: Overview, opportunities, and challenges. IEEE Access 2023, 11, 96718–96732. [Google Scholar] [CrossRef]
- Trakadas, P.; Masip-Bruin, X.; Facca, F.M.; Spantideas, S.T.; Giannopoulos, A.E.; Kapsalis, N.C.; Martins, R.; Bosani, E.; Ramon, J.; Prats, R.G.; et al. A reference architecture for cloud–edge meta-operating systems enabling cross-domain, data-intensive, ML-assisted applications: Architectural overview and key concepts. Sensors 2022, 22, 9003. [Google Scholar] [CrossRef] [PubMed]
- Chochliouros, I.P. OASEES: An Innovative scope for a DAO-based programmable swarm solution, for decentralizing AI applications close to data generation locations. In Artificial Intelligence Applications and Innovations. AIAI 2023 IFIP WG 12.5 International Workshops. AIAI 2023. IFIP Advances in Information and Communication Technology; Maglogiannis, I., Iliadis, L., Papaleonidas, A., Chochliouros, I., Eds.; Springer: Cham, Switzerland, 2023; Volume 677. [Google Scholar] [CrossRef]
- Garg, S.; Kaur, K.; Kaddoum, G.; Garigipati, P.; Aujla, G. S. Security in IoT-driven mobile edge computing: New paradigms, challenges, and opportunities. IEEE Network 2021, 35, 298–305. [Google Scholar] [CrossRef]
- Zhao, L.; Zhou, G.; Zheng, G.; I, C.-L.; You, X.; Hanzo, L. Open-source multi-access edge computing for 6G: Opportunities and challenges. IEEE Access 2021, 9, 158426–158439. [Google Scholar] [CrossRef]
- Firouzi, F. Fusion of IoT, AI, edge–fog–cloud, and blockchain: Challenges, solutions, and a case study in healthcare and medicine. IEEE Internet Things J. 2023, 10, 3686–3705. [Google Scholar] [CrossRef]
- Khan, L. U.; Yaqoob, I.; Imran, M.; Han, Z.; Hong, C. S. 6G wireless systems: A vision, architectural elements, and future directions. IEEE Access 2020, 8, 147029–147044. [Google Scholar] [CrossRef]
- Letaief, K. B.; Chen, W.; Shi, Y.; Zhang, J.; Zhang, Y.-J. A. The roadmap to 6G: AI empowered wireless networks. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef]
- Kong, L. Edge-computing-driven internet of things: A Survey. ACM Computing Surveys 2022, 55. [Google Scholar] [CrossRef]
- Fazeldehkordi, E.; Grønli, T.-M. A survey of security architectures for edge computing-based IoT. IoT 2022, 3, 332–365. [Google Scholar] [CrossRef]
- Alwarafy, A.; Al-Thelaya, K. A.; Abdallah, M.; Schneider, J.; Hamdi, M. A survey on security and privacy issues in edge-computing-assisted internet of things. IEEE Internet Things J. 2021, 8, 4004–4022. [Google Scholar] [CrossRef]
- Singh, R.; Gill, S. S. Edge AI: A survey. Internet of Things and Cyber-Physical Systems 2023, 371–392. [Google Scholar] [CrossRef]
- Abkenar, F. S. A survey on mobility of edge computing networks in IoT: State-of-the-art, architectures, and challenges. IEEE Commun. Surv. Tutor. 2022; 24. [Google Scholar] [CrossRef]
- Rosendo, D.; Costan, A.; Valduriez, P.; Antoniu, G. Distributed intelligence on the edge-to-cloud continuum: A systematic literature review. Journal of Parallel and Distributed Computing 2022, 166, 71–94. [Google Scholar] [CrossRef]
- Kong, X.; Wu, Y.; Wang, H.; Xia, F. Edge computing for internet of everything: A survey. IEEE Internet Things J. 2022, 9, 23472–23485. [Google Scholar] [CrossRef]
- Chiang, Y. , Management and orchestration of edge computing for IoT: A comprehensive survey. IEEE Internet Things J. 2023, 10, 14307–14331. [Google Scholar] [CrossRef]
- Liu, B.; Luo, Z.; Chen, H.; Li, C. A survey of state-of-the-art on edge computing: Theoretical models, technologies, directions, and development paths. IEEE Access, 2022; 10, 54038–54063. [Google Scholar] [CrossRef]
- et al. Cost-efficient 5G non-public network roll-out: The Affordable5G approach. In Proceedings of the IEEE International Mediterranean Conference on Communications and Networking (MeditCom, Athens, Greece, 2021; 2021; pp. 221–227. [Google Scholar] [CrossRef]
- Guo, S.; Lu, B.; Wen, M.; Dang, S.; Saeed, N. Customized 5G and beyond private networks with integrated URLLC, eMBB, mMTC, and positioning for industrial verticals. IEEE Commun. Stand. 2022, 6, 52–57. [Google Scholar] [CrossRef]
- Cheng, Y.; Zhang, H.; Huang, Y. Overview of communication protocols in internet of things: Architecture, development and future trends. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence (WI), Santiago, Chile; 2018; pp. 627–630. [Google Scholar] [CrossRef]
- Coronado, E.; Cebrián-Márquez, G.; Riggio, R. Enabling autonomous and connected vehicles at the 5G network edge. In Proceedings of the 6th IEEE Conference on Network Softwarization (NetSoft), Ghent, Belgium; 2020; pp. 350–352. [Google Scholar] [CrossRef]
- Bartsiokas, I. A.; Gkonis, P. K.; Kaklamani, D. I.; Venieris, I. S. ML-based radio resource management in 5G and beyond networks: A Survey. IEEE Access, 2022; 10, 83507–83528. [Google Scholar] [CrossRef]
- Hu, S.; Chen, X.; Ni, W.; Hossain, E.; Wang, X. Distributed machine learning for wireless communication networks: Techniques, architectures, and applications. IEEE Commun. Surv. Tutor. 2021, 23, 1458–1493. [Google Scholar] [CrossRef]
- Marozzo, F.; Orsino, A.; Talia, D.; Trunfio, P. Edge computing solutions for distributed machine learning. In Proceedings of the IEEE Intelligent Conference on Dependable, Autonomic and Secure Computing, Intelligent Conference on Pervasive Intelligence and Computing, Intelligent Conference on Cloud and Big Data Computing, Intelligent Conference on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Falerna, Italy; 2022. [Google Scholar] [CrossRef]
- Li, T.; Sahu, A. K.; Talwalkar, A.; Smith, V. Federated learning: Challenges, methods, and future directions. IEEE Signal Process. Mag. 37, 50–60.
- Rahman, K. M. J. Challenges, applications and design aspects of federated learning: A survey. IEEE Access 2021, 9, 124682–124700. [Google Scholar] [CrossRef]
- Ali, M.; Naeem, F.; Tariq, M.; Kaddoum, G. Federated learning for privacy preservation in smart healthcare systems: A comprehensive survey. IEEE J. Biomed. Health Inform. 2023, 27, 778–789. [Google Scholar] [CrossRef]
- Li, Y.; Lin, Y.; Wang, Y.; Ye, K.; Xu, C. Serverless computing: State-of-the-art, challenges and opportunities. IEEE Trans. Serv. Comput. 2023, 16, 1522–1539. [Google Scholar] [CrossRef]
- Patros, P.; Spillner, J.; Papadopoulos, A. V.; Varghese, B.; Rana, O.; Dustdar, S. Toward sustainable serverless computing. IEEE Internet Computing 2021, 25, 42–50. [Google Scholar] [CrossRef]
- Ali, M. S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M. H. Applications of blockchains in the internet of things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 1676–1717. [Google Scholar] [CrossRef]
- Xu, L. D.; Lu, Y.; Li, L. Embedding blockchain technology into IoT for security: A survey. IEEE Internet Things J. 2021, 8, 10452–10473. [Google Scholar] [CrossRef]
- Shammar, E. A.; Zahary, A. T.; Al-Shargabi, A. A. A survey of IoT and blockchain integration: Security perspective. IEEE Access 2021, 9, 156114–156150. [Google Scholar] [CrossRef]
- Kemmoe, V. Y.; Stone, W.; Kim, J.; Kim, D.; Son, J. Recent advances in smart contracts: A technical overview and state of the art. IEEE Access 2020, 8, 117782–117801. [Google Scholar] [CrossRef]
- Abuhashim, A.; Tan, C. C. Smart contract designs on blockchain applications. In Proceedings of the IEEE Symposium on Computers and Communications (ISCC), Rennes, France; 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Adeogun, R.; Berardinelli, G.; Mogensen, P. E.; Rodriguez, I.; Razzaghpour, M. Towards 6G in-X subnetworks with sub-millisecond communication cycles and extreme reliability. IEEE Access 2020, 8, 110172–110188. [Google Scholar] [CrossRef]
- Berardinelli, G.; Adeogun, R. Hybrid radio resource management for 6G subnetwork crowds. IEEE Commun. Mag. 2023, 61, 148–154. [Google Scholar] [CrossRef]
- Ding, Z.; Shen, L.; Chen, H.; Yan, F.; Ansari, N. Energy-efficient topology control mechanism for IoT-oriented software-defined WSNs. IEEE Internet Things J. 2023, 10, 13138–13154. [Google Scholar] [CrossRef]
- Berardinelli, G. Extreme communication in 6G: Vision and challenges for ‘in-X’ subnetworks. IEEE OJ-COMS 2021, 2, 2516–2535. [Google Scholar] [CrossRef]
- Areqi, M. A.; Zahary, A. T.; Ali, M. N. State-of-the-art device-to-device communication solutions. IEEE Access 2023, 11, 46734–46764. [Google Scholar] [CrossRef]
- Sarma, S. S.; Hazra, R.; Mukherjee, A. Symbiosis between D2D communication and industrial IoT for industry 5.0 in 5G mm-wave cellular network: An interference management approach. IEEE Trans. Ind. Inform. 5527, 18, 5527–5536. [Google Scholar] [CrossRef]
- Kavitha, A. Security in IoT mesh networks based on trust similarity. IEEE Access 2022, 10, 121712–121724. [Google Scholar] [CrossRef]
- Nurlan, Z.; Kokenovna, T. Z.; Othman, M.; Adamova, A. Resource allocation approach for optimal routing in IoT wireless mesh networks. IEEE Access 2021, 9, 153926–153942. [Google Scholar] [CrossRef]
- Zhang, X.; Cao, Z.; Dong, W. Overview of edge computing in the agricultural internet of things: Key technologies, applications, challenges. IEEE Access 2020, 8, 141748–141761. [Google Scholar] [CrossRef]
- Moradi, S.; Bokani, A.; Hassan, J. UAV-based smart agriculture: A review of UAV sensing and applications. In Proceedings of the 32nd International Telecommunication Networks and Applications Conference (ITNAC), Wellington, New Zealand; 2022; 181-184. [Google Scholar] [CrossRef]
- Orlando, M. A smart meter infrastructure for smart grid IoT applications. IEEE Internet Things J. 2022, 9, 12529–12541. [Google Scholar] [CrossRef]
- Alohali, B.; Kifayat, K.; Shi, Q.; Hurst, W. Group authentication scheme for neighbourhood area networks (NANs) in smart grids. J. Sens. Actuator Netw. 2016, 5. [Google Scholar] [CrossRef]
- Skianis, K.; Giannopoulos, A.; Gkonis, P.; Trakadas, P. Data aging matters: Federated learning-based consumption prediction in smart homes via age-based model weighting. Electronics 2023, 12, 3054. [Google Scholar] [CrossRef]
- Trakadas, P.; Simoens, P.; Gkonis, P.; Sarakis, L.; Angelopoulos, A.; Ramallo-González, A.P.; Skarmeta, A.; Trochoutsos, C.; Calvο, D.; Pariente, T.; et al. An artificial intelligence-based collaboration approach in industrial IoT manufacturing: Key concepts, architectural extensions and potential applications. Sensors 2020, 20, 5480. [Google Scholar] [CrossRef]
- Zafeiropoulos, A., et al; et al. Benchmarking and profiling 5G verticals applications: An industrial IoT use case. In Proceedings of the 6th IEEE Conference on Network Softwarization (NetSoft), Ghent, Belgium; 2020; pp. 310–318. [Google Scholar] [CrossRef]
- Karamplias, T.; Spantideas, S. T.; Giannopoulos, A. E.; Gkonis, P.; Kapsalis, N.; Trakadas, P. Towards closed-loop automation in 5G open RAN: Coupling an open-source simulator with xApps. In Proceedings of the Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Grenoble, France; 2022; pp. 232–237. [Google Scholar] [CrossRef]
- Laroui, M.; Khedher, H. I.; Moungla, H.; Afifi, H.; Kamal, A. E. Virtual mobile edge computing based on IoT devices resources in smart cities. In Proceedings of the IEEE International Conference on Communications (ICC), Dublin, Ireland; 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Nomikos, N.; Gkonis, P. K.; Bithas, P. S.; Trakadas, P. A survey on UAV-aided maritime communications: Deployment considerations, applications, and future challenges. OJ-COMS 2023, 4, 56–78. [Google Scholar] [CrossRef]
- Nomikos, N.; Giannopoulos, A.; Trakadas, P.; Karagiannidis, G. K. Uplink NOMA for UAV-aided maritime internet-of-things. In Proceedings of the 19th International Conference on the Design of Reliable Communication Networks (DRCN), Vilanova i la Geltru, Spain; 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Giannopoulos, A.; Gkonis, P.; Bithas, P.; Nomikos, N.; Ntroulias, G.; Trakadas, P. Federated learning for maritime environments: Use cases, experimental results, and open issues,” submitted for publication in the Intelligent Transportation Systems Magazine. Available online: https://www.techrxiv.org/articles/preprint/Federated_Learning_for_Maritime_Environments_Use_Cases_Experimental_Results_and_Open_Issues/22133549/1.
- Giannopoulos, A.; Nomikos, N.; Ntroulias, G.; Syriopoulos, T.; Trakadas, P. Maritime Federated Learning for Decentralized On-Ship Intelligence. In Artificial Intelligence Applications and Innovations. AIAI 2023. IFIP Advances in Information and Communication Technology; Maglogiannis, I., Iliadis, L., MacIntyre, J., Dominguez, M. (eds), Eds.; Springer: Cham, Switzerland, 2023; Volume 676. [Google Scholar] [CrossRef]
- Trakadas, P.; Nomikos, N.; Michailidis, E.T.; Zahariadis, T.; Facca, F.M.; Breitgand, D.; Rizou, S.; Masip, X.; Gkonis, P. Hybrid clouds for data-intensive, 5G-enabled IoT applications: An overview, key Issues and relevant architecture. Sensors 2019, 19, 3591. [Google Scholar] [CrossRef] [PubMed]
- Ahn, Y. J.; Kim, M.; Lee, J.; Shen, Y.; Jeong, J. P. IoT edge-cloud: An internet-of-things edge-empowered cloud system for device management in smart spaces. IEEE Network 2023. [Google Scholar] [CrossRef]
- Brzozowski, M.; et al. UNITE: Integrated IoT-edge-cloud continuum. In Proceedings of the IEEE 8th World Forum on Internet of Things (WF-IoT), Yokohama, Japan; 2022; pp. 1–6. [CrossRef]
- Babar, M. An optimized IoT-enabled big data analytics architecture for edge–cloud computing. IEEE Internet Things J. 20 March 2023; 10, 3995–4005. [Google Scholar]
- Ghosh, A. M.; Grolinger, K. Edge-cloud computing for internet of things data analytics: Embedding intelligence in the edge with deep learning. IEEE Trans. Ind. Inform. 2021, 17, 2191–2200. [Google Scholar] [CrossRef]
- Pham, C.; Nguyen, D. T.; Njah, Y.; Tran, N. H.; Nguyen, K. K.; Cheriet, M. Share-to-run IoT services in edge cloud computing. IEEE Internet Things J. 2022, 9, 497–509. [Google Scholar] [CrossRef]
- Zhou, M.-T.; Shen, F.-G.; Ren, T.-F.; Feng, X.-Y. Blockchain-based volunteer edge cloud for IoT applications. In Proceedings of the IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), Helsinki, Finland; 2021. [Google Scholar] [CrossRef]
- Jassas, M. S.; Mahmoud, Q. H. Evaluation of failure analysis of IoT applications using edge-cloud architecture. In Proceedings of the IEEE International Systems Conference (SysCon), Montreal, QC, Canada; 2022. [Google Scholar] [CrossRef]
- Zhang, W.-Z. Secure and optimized load balancing for multitier IoT and edge-cloud computing systems. IEEE Internet Things J. 2021, 8, 8119–8132. [Google Scholar] [CrossRef]
- Chen, L. IoT microservice deployment in edge-cloud hybrid environment using reinforcement learning. IEEE Internet Things J. 2021, 8, 12610–12622. [Google Scholar] [CrossRef]
- Liu, G.; Huang, B.; Liang, Z.; Qin, M.; Zhou, H.; Li, Z. Microservices: architecture, container, and challenges. In Proceedings of the IEEE 20th International Conference on Software Quality, Reliability and Security Companion (QRS-C), Macau, China; 2020; pp. 629–635. [Google Scholar] [CrossRef]
- Heidari, A.; Navimipour, N. J.; Jamali, M. A. J.; Akbarpour, S. A green, secure, and deep intelligent method for dynamic IoT-edge-cloud offloading scenarios. Sustainable Computing: Informatics and Systems 2023, 38. [Google Scholar] [CrossRef]
- Militano, L.; Arteaga, A.; Toffetti, G.; Mitton, N. The Cloud-to-Edge-to-IoT Continuum as an Enabler for Search and Rescue Operations. Future Internet 2023, 15, 55. [Google Scholar] [CrossRef]
- The NEPHELE project, https://nephele-project.eu/, Available online: https://flower.dev/ (accessed on 7/11/2023).
- Zhang, Y.; Yu, H.; Zhou, W.; Man, M. Application and Research of IoT Architecture for End-Net-Cloud Edge Computing. Electronics 2023, 12, 1. [Google Scholar] [CrossRef]
- Almutairi, J.; Aldossary, M. A novel approach for IoT tasks offloading in edge-cloud environments. J. Cloud Comp. 2021, 10. [Google Scholar] [CrossRef]
- Rong, G.; Xu, Y.; Tong, X.; Fan, H. An edge-cloud collaborative computing platform for building AIoT applications efficiently. J. Cloud Comp. 2021, 10. [Google Scholar] [CrossRef]
- Yao, J. Edge-cloud polarization and collaboration: A comprehensive survey for AI. IEEE Trans. Knowl. Data Eng. 2023, 35, 6866–6886. [Google Scholar] [CrossRef]
- Kelaidonis, D.; Rouskas, A.; Stavroulaki, V.; Demestichas, P.; Vlacheas, P. A federated edge cloud-IoT architecture. In Proceedings of the European Conference on Networks and Communications (EuCNC), Athens, Greece; 2016; pp. 230–234. [Google Scholar] [CrossRef]
- Fang, J.; Ma, A. IoT application modules placement and dynamic task processing in edge-cloud computing. IEEE Internet Things J. 2021, 8, 12771–12781. [Google Scholar] [CrossRef]
- Yousuf Khan, E. U.; Rahim Soomro, T.; Nawaz Brohi, M. iFogSim: A tool for simulating cloud and fog applications. In Proceedings of the International Conference on Cyber Resilience (ICCR), Dubai, United Arab Emirates; 2022. [Google Scholar] [CrossRef]
- Javed, A.; Robert, J.; Heljanko, K.; Främling, K. IoTEF: A federated edge-cloud architecture for fault-tolerant IoT applications. J. Grid Computing 2020, 18, 57–80. [Google Scholar] [CrossRef]
- Mutichiro, B.; Tran, M.-N.; Kim, Y.-H. QoS-based service-time scheduling in the IoT-edge cloud. Sensors 2021, 21, 5797. [Google Scholar] [CrossRef] [PubMed]
- Song, H.; Dautov, R.; Ferry, N.; et al. Model-based fleet deployment in the IoT–edge–cloud continuum. Softw Syst Model 2022, 21, 1931–1956. [Google Scholar] [CrossRef]
- Zamora-Izquierdo, M. A.; Santa, J.; Martínez, J. A.; Martínez, V.; Skarmeta, A. F. Smart farming IoT platform based on edge and cloud computing. Biosystems Engineering 2019, 177. [Google Scholar] [CrossRef]
- Alharbi, H. A.; Aldossary, M. Energy-efficient edge-fog-cloud architecture for IoT-based smart agriculture environment. IEEE Access 2021, 9, 110480–110492. [Google Scholar] [CrossRef]
- Chen, B.; Wan, J.; Celesti, A.; Li, D.; Abbas, H.; Zhang, Q. Edge computing in IoT-based manufacturing. IEEE Commun. Mag. 2018, 56, 103–109. [Google Scholar] [CrossRef]
- Qi, Q.; Tao, F. A smart manufacturing service system based on edge computing, fog computing, and cloud computing. IEEE Access 2019, 7, 86769–86777. [Google Scholar] [CrossRef]
- Yu, W.; Liu, Y.; Dillon, T.; Rahayu, W. Edge computing-assisted IoT framework with an autoencoder for fault detection in manufacturing predictive maintenance. IEEE Trans. Ind. Inform. 2023, 19, 5701–5710. [Google Scholar] [CrossRef]
- Lee, C. K. M.; Huo, Y. Z.; Zhang, S. Z.; Ng, K. K. H. Design of a smart manufacturing system with the application of multi-access edge computing and blockchain technology. IEEE Access 2020, 8, 28659–28667. [Google Scholar] [CrossRef]
- Wu, H.; Zhang, Z.; Guan, C.; Wolter, K.; Xu, M. Collaborate edge and cloud computing with distributed deep learning for smart city internet of things. IEEE Internet Things J. 2020, 7, 8099–8110. [Google Scholar] [CrossRef]
- Nwebonyi, F. N.; Martins, R.; Correia, M. E. Security and fairness in IoT based e-Health system: A case study of mobile edge-clouds. In Proceedings of the International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain; 2019; pp. 318–323. [Google Scholar] [CrossRef]
- Hu, B.; Isaac, M.; Abdul Majeed, A. P. P.; Liu, H. Edge intelligence-based e-health wireless sensor network systems. In Proceedings of the IEEE/ACIS 23rd International Conference on Computer and Information Science (ICIS), Wuxi, China; 2023; pp. 55–59. [Google Scholar] [CrossRef]
- Gao, H.; Huang, H.; Xue, L.; Xiao, F.; Li, Q. Blockchain-enabled fine-grained searchable encryption with cloud–edge computing for electronic health records sharing. IEEE Internet Things J. 2023, 10, 18414–18425. [Google Scholar] [CrossRef]
- Xiang, Z.; Deng, S.; Zheng, Y.; Wang, D.; Tehari, J.; Zheng, Z. Energy-effective IoT services in balanced edge-cloud collaboration systems. In Proceedings of the IEEE International Conference on Web Services (ICWS), Chicago, IL, USA; 2021; pp. 219–229. [Google Scholar] [CrossRef]
- Li, Y.; Zhou, Z.; Xue, X.; Zhao, D.; Hung, P. C. K. Accurate anomaly detection with energy efficiency in IoT–Edge–Cloud collaborative networks. IEEE Internet Things J. 2023, 10, 16959–16974. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C.; Jiang, L.; Xie, S.; Zhang, Y. Intelligent edge computing for IoT-based energy management in smart cities. IEEE Network 2019, 33, 111–117. [Google Scholar] [CrossRef]
- Nammouchi, A.; Aupke, P.; Kassler, A.; Theocharis, A.; Raffa, V.; Felice, M. D. Integration of AI, IoT and edge-computing for smart microgrid energy management. In Proceedings of the IEEE International Conference on Environment and Electrical Engineering and 2021 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I&CPS Europe); 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Apache Kafka, Available online:. Available online: https://kafka.apache.org/ (accessed on 7/11/2023).
- TensorFlow, Available online:. Available online: https://www.tensorflow.org/ (accessed on 7/11/2023).
- Flower, A Friendly Federated Learning Framework, Available online:. Available online: https://flower.dev/ (accessed on 7/11/2023).
| Survey Paper | Year | Contributions |
|---|---|---|
| [24] | 2022 | Edge-computing-driven IoT under various technological aspects |
| [25] | 2022 | Security considerations in edge-based IoT |
| [26] | 2021 | Security and privacy considerations in IEC continuum systems and classification of attacks |
| [27] | 2023 | Edge AI |
| [28] | 2022 | Analysis of different node categories in an edge-cloud-IoT environment |
| [29] | 2022 | Frameworks and simulation tools for the support of distributed intelligence in the edge to cloud environments |
| [30] | 2022 | Integration of edge computing with novel technologies |
| [31] | 2023 | Management and orchestration in edge computing IoT systems |
| [32] | 2022 | Recent advances in edge computing |
| This work | - | Analysis of recent works in IEC continuum systems in the context of various challenges and key enabling technologies |
| Survey Paper | Year | Contributions | Methodology | Limitations – Open issues |
|---|---|---|---|---|
| [71] | 2019 | Decentralized hybrid cloud MEC architecture | AI, security and privacy, serverless computing | Evaluation in real world scenarios |
| [72] | 2023 | Localization of IoT devices | DNS naming, IPv6 | Secure communication and multi-user management |
| [73] | 2022 | Resources integration via virtualization |
ML for resource optimization, agnostic application development |
Security mechanisms, efficient task offloading |
| [74] | 2023 | Parallel data ingestion | ML for resource optimization, ensemble learning | Security mechanisms |
| [75] | 2021 | Data reduction prior to cloud processing | Feature learning | Extension of the proposed framework in additional applications |
| [76] | 2022 | Multiple edge/cloud providers | Resource allocation and sharing optimization model |
Evaluation in real world scenarios |
| [77] | 2021 | Node utilization in IoT environments |
Security via blockchain technology |
Evaluation in real world scenarios |
| [78] | 2022 | Task failure minimization | Task offloading according to network, security, and latency requirements | Optimum task offloading for complex applications |
| [79] | 2021 | Efficient task offloading via security mechanisms |
Advanced encryption standard cryptographic technique Low complexity load balancing and computation offloading |
ML for efficient computational offloading |
| [80] | 2021 | IoT microservice deployment problem | Deep reinforcement learning | Load balancing in multi-cloud environment deployment strategies Decentralized training approaches for privacy enhancement |
| [82] | 2023 | Delay, job failure, computational overhead, energy consumption improvement |
Deep Post-Decision State (PDS) for learning efficiency Blockchain technology during task offloading |
ML in large scale MEC orientations |
| [83] | 2023 | Cloud-to-Edge-to-IoT Continuum for SAR applications | NFV, virtual objects at the edge | Advanced AI approaches and computer vision for additional post-disaster scenarios |
| [85] | 2023 | Integration of multiple use case scenarios in a common architectural approach |
Reference architecture based on end-edge, net-edge, cloud-edge | Construction of a multi-tier EC-IoT architecture with one central cloud and multiple edge clouds with unified regulation and standards |
| [86] | 2021 | Task offloading for latency minimization | Application characteristics and heterogeneity of the infrastructure |
Evaluation in real world scenarios |
| [87] | 2021 | AI in edge-cloud-IoT environments | Sophon edge framework for ML model training and inference |
Distributed ML for latency reduction and privacy enhancement |
| [88] | 2023 | Interaction between Cloud-IoT environments | Cognitive management of services |
Evaluation in real world scenarios and security mechanisms |
| [89] | 2016 | Software in edge-cloud-IoT environments |
Model-based approach to automatically assigning multiple software deployment plans to hundreds of edge gateways | Performance evaluation in additional scenarios apart from e-Health |
| [90] | 2021 | IoT application modules placement |
Particle swarm optimization to acquire the best application module placement strategy | Extension in multiple IoT application services |
| [92] | 2020 | Multi-cluster IoT applications | Four-layered architecture | Extension in additional use case scenarios |
| [93] | 2021 | Optimum cluster usage | Task scheduling problem at the edge | Performance evaluation in real world scenarios |
| [94] | 2022 | Model fleet deployment | Μodel-based techniques | Evaluation in real worlds scenarios |
| [95] | 2019 | IoT platform based on edge and cloud computing for smart agriculture | Three-tier open-source software platform at local, edge and cloud planes. | Performance evaluation in additional farming scenarios |
| [96] | 2021 | IoT-Edge-Fog-Cloud architecture for agricultural applications |
Optimization of energy consumption, CO2 emission, and network traffic | Machine learning approaches |
| [97] | 2018 | IoT-based manufacturing | Interlayer coordination | Performance evaluation in large-scale orientations |
| [98]-[99] | 2019, 2023 | Smart manufacturing based on a three-layered architecture | Edge-fog-cloud cooperation Efficient task offloading |
Performance evaluation in large-scale orientations |
| [100] | 2020 | IoT-based manufacturing | Edge computing with blockchain Task assignment based on particle swarm optimization |
Performance evaluation in large-scale orientations |
| [101] | 2020 | IEC collaboration in smart cities |
Distributed deep learning task offloading | Blockchain-based decentralized offloading scheme Metalearning in offloading decisions |
| [102] | 2019 | IEC in e-health applications | Lightweight security mechanism based on trusted nodes | Scalability |
| [103] | 2023 | IEC in e-health applications | FL for data transfer reduction D2D communications |
Single cell wireless sensor network scenario with one MEC server |
| [104] | 2023 | IEC in e-health applications | Blockchain and smart contacts | Efficient consensus algorithms |
| [105] | 2023 | Energy efficiency in IEC systems | Problem formulation, iterative optimization and comparison to baseline approaches | Energy prediction algorithms |
| [106] | 2023 | Anomaly detection in IEC systems | Interpolation and marching squares algorithm | Extension in additional real world scenarios |
| [107] | 2019 | Energy efficient task offloading | Deep reinforcement learning in an IEC smart city scenario | Extension in additional real world scenarios |
| [108] | 2021 | Load forecasting in microgrids | Edge servers in microgrids, data collection, ML for load forecasting | Federared learning, transfer learning, insertion of historical data via deep learning |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





