1. Introduction
Networks are the backbone of our interconnected world. They are therefore ubiquitous today. Internet, power grids, infrastructure, transportation, neural, computer and social networks play a crucial role in our daily lives.
Then, understanding the structural properties of the networks is of paramount importance to provide a comprehensive perspective on network dynamics that can help decision-makers and stakeholders across different domains.
In this paper we will focus on the study of two highly relevant properties of social or economic networks, namely, efficiency and vulnerability.
Efficiency in social networks refers to the network ability to connect individuals, facilitate communication, optimize interactions and the flow of information in order to enhance social cohesion. For economic networks informs on the network capacity to allocate resources, maximizing productivity, reducing transactions costs an minimizing waste.
On the other side, vulnerability in a social network denotes the exposure of the network or its members to external or internal risks as miss information, lost of information and harmful interactions. In the case of economic networks refers to the possibility that the network has weakness that can disrupt economic activities generating a negative impact in the productivity.
Game theory is devoted to analyze the strategic interactions and decision-making processes and thus it can be effectively used to analyze dynamics within networks. As mentioned, our goal in this paper is to analyze efficiency and vulnerability in a network, and we will do so from a game theoretical perspective. The analysis of efficiency networks from a game theoretical point of view is not new. Wireline and wireless networks have been widely studied but from a non-cooperative game perspective. Ozdaglar and Menache (2022) is a remarkable survey of this type of contribution. In our framework, we will assume that the nodes of the network are simultaneously players in a TU-game (a cooperative game with transferable utility) that represents their social or economic interests. In this way we will propose a family of game-theoretical measures of efficiency and vulnerability for a network that has as a parameter the game. That is to say, we will assume that efficiency and vulnerability depend on the purpose for which individuals use the network, where this purpose, whether it is information dissemination, economic productivity or communication, is modeled by a TU-game.
As mentioned, the analysis of networks from a game theoretical point of view has a long tradition. Myerson (1977) is the seminal work in which he proposed to analyze the impact of restrictions in the communication of players in a TU-game by means of a network (graph). Then, he defined a new TU-game, the graph-restricted game. Given the prominence of the Shapley value (Shapley, 1953), Myerson proposed as solution for graph-restricted games, the Shapley value. From this original work, there exists an extensive literature in games with cooperation restricted by a graph. Gómez et al. (2003) and González-Arangüena et al. (2017), used the Myerson value as a centrality measure for actors in a symmetrical TU-game with communication restricted by a graph. Trying to capture both the communication and the betweens centrality, they decompose the Myerson value in the within groups Myerson value (WG-Myerson value, for short)and the between groups Myerson value (BG-Myerson value, for short). These values, when calculated for a general game, respectively measure the productivity of the player in the game and his intermediation opportunities among the others.
The proposed measures of efficiency and vulnerability introduced in this paper use this decomposition of the Myerson value. In our proposal, the efficiency of a network, parameterized by a game, is the proportion of the value of the grand coalition that players can retain (the sum of the within groups Myerson values of all the players) as a consequence of the network topology. And thus more efficient economic networks allow players a greater proportion of productivity, reducing intermediates cost. These intermediation cost can be viewed precisely as a weakness with a negative impact in the productivity. Then, our proposal for the family of vulnerability measures (also parameterized by the game) is to calculate the proportion of the value of the grand coalition that players must expend in intermediation payments (the sum of the between groups Myerson values of players). These payments reduce productivity and expose the players to the disruption of economic activities generated by the lack of communication between different groups of players (coalitions). For social networks, roughly speaking, the efficiency is viewed as the proportion of the total centrality in the network due to communication among players. The vulnerability is the proportion of the total centrality due to betweeness. In this way, efficiency is measured in terms of the relational abilities of players whereas vulnerability increases when third-party control of communication between pairs of players increases. After defining the measures we explore the more relevant properties including their asymptotic behavior for particular games.
The remainder of the paper is organized as follows. After some preliminaries on games, graphs and communication situations (graph-games), in
Section 3 we introduce the family of efficiency measures, analyzing its properties. In
Section 4 we particularize the values of this family for several games and several structures including the asymptotic behaviour. In
Section 5 we propose the family of vulnerability measures. The paper ends with a section of conclusions and final remarks and the references.
2. Preliminaries
2.1. Games
A cooperative n-person game of transferable utility ( TU-game for short) is a pair where is the set of players an , satisfying , is the characteristic function that assigns to each coalition the payoff that its members can obtain by cooperating.
We will denote by
the vector space of all TU-games with players set
N. A very useful basis of
is the unanimity games basis
, with characteristic functions given by
Consequently, for each
we can write
v as the following linear combination,
in which the coefficients,
, known as
Harsanyi dividends (Harsanyi, 1959), can be calculated as:
We will say that is zero-normalized if for all , is superadditive if for all is convex if for all , and is almost-positive if for all . Almost-positive games are superaditive and convex.
Given , a player is a null player in if for all and is a necessary player (van den Brink and Gilles, 1996) if for all .
An
allocation rule or point solution
on
assigns to every
a vector
,
representing the outcome of the player
i in the game. A very relevant point solution was introduced in Shapley (1953). It assigns to every player
i in the game
the following expected value of his marginal contributions:
2.2. Graphs
A graph or a (network) is a pair , where is the set of nodes and is a set of links included in the complete graph . If the link we will say that i and j are directly connected. In other case, i and j could be connected if there exist a path, i.e., a sequence of nodes (intermediaries) , with , , such that , for .
A set , , is connected (internally connected) in if every pair of nodes in S are directly connected or they can be connected with intermediaries in S. Singletons will be considered connected. A connected component, C, of the graph is a maximal connected subset, that is, C is connected and, for all , if then, is not connected. A graph induces a partition of the set N into connected components.
A connected set in , , is a minimal connection set of if there is no with and connected. will denote the family (occasionally empty) of all minimal connection sets of S in .
Given and , will denote de set of all connected components in the restriction of to S, i.e., in , where .
A subgraph of a graph is with . Given and , is the subgraph obtained when the link l is removed; is the subgraph of of the links incident on i, i.e.: , and .
is a tree if it is connected and it has no cycles. We will denote the star with center in the node i and thus . will denote the chain ordered in the natural way (from 1 to n). is the wheel with .
2.3. Communications situations
Myerson (1977,1980) introduced the games with cooperation restricted by a graph (also graph-games or communications situations), , in which the players in the game are restricted to communicate using only the links in the graph . will denote the set of all communication situations with player-nodes set N and will denote the set of all communication situations with player-nodes set N and game v zero-normalized. Finally will be the subset of with a non null and superadditive game.
An allocation rule on is a map , representing the outcome for player i in the communication situation . An allocation rule defined on satisfies component efficiency if for all and all .
Following Myerson(1977), for
a new game
captures the impact of the restrictions in the communication imposed by
in the formation of coalitions (an thus in their value). The characteristic function is given by
Given the relevance of the Shapley value, Myerson defined , the allocation rule in (nowadays known as the Myerson value) given by . Exploring the possibilities of the Myerson value as a centrality measure Gómez et al. (2003) and González-Arangüena et al. (2017) highlight the vector character of the Myerson value decomposing it into two new allocation rules: the within groups Myerson value, , (the WG-Myerson value for short) and the between groups Myerson value, , (the BG-Myerson value for short). For each and each they are defined as and , where and
3. A family of efficiency measures
In the following definition we introduce a family of game-theoretical measures for the efficiency of a network. We will assume that nodes in the network are players in a TU-game, this game representing the economic or social interests that motivate the interaction of players. The network represents the feasible communications between players (and, as a consequence, also the existing restrictions that motivate the need for intermediaries when players have not direct communication). The proposed family of efficiency measures, assigns to each network and each TU-game a value representing which part of the total productivity of the game, , players can maintain given the geometry of the network.
We will use super-additive games in which cooperation between individuals is not detrimental to them. We will also assume that the games are zero-normalized so that the total absence of communication between players - the impossibility to cooperate, empty graph-, corresponds to the minimum (and null) efficiency.
Definition 3.1.
We define a measure of efficiency, , for each communication situation as:
Remark 3.1. In the special case in which is a symmetric game and is a connected graph, the defined measure represents the proportion of corresponding to the total communication centrality of players introduced in Gómez et al. (2003).
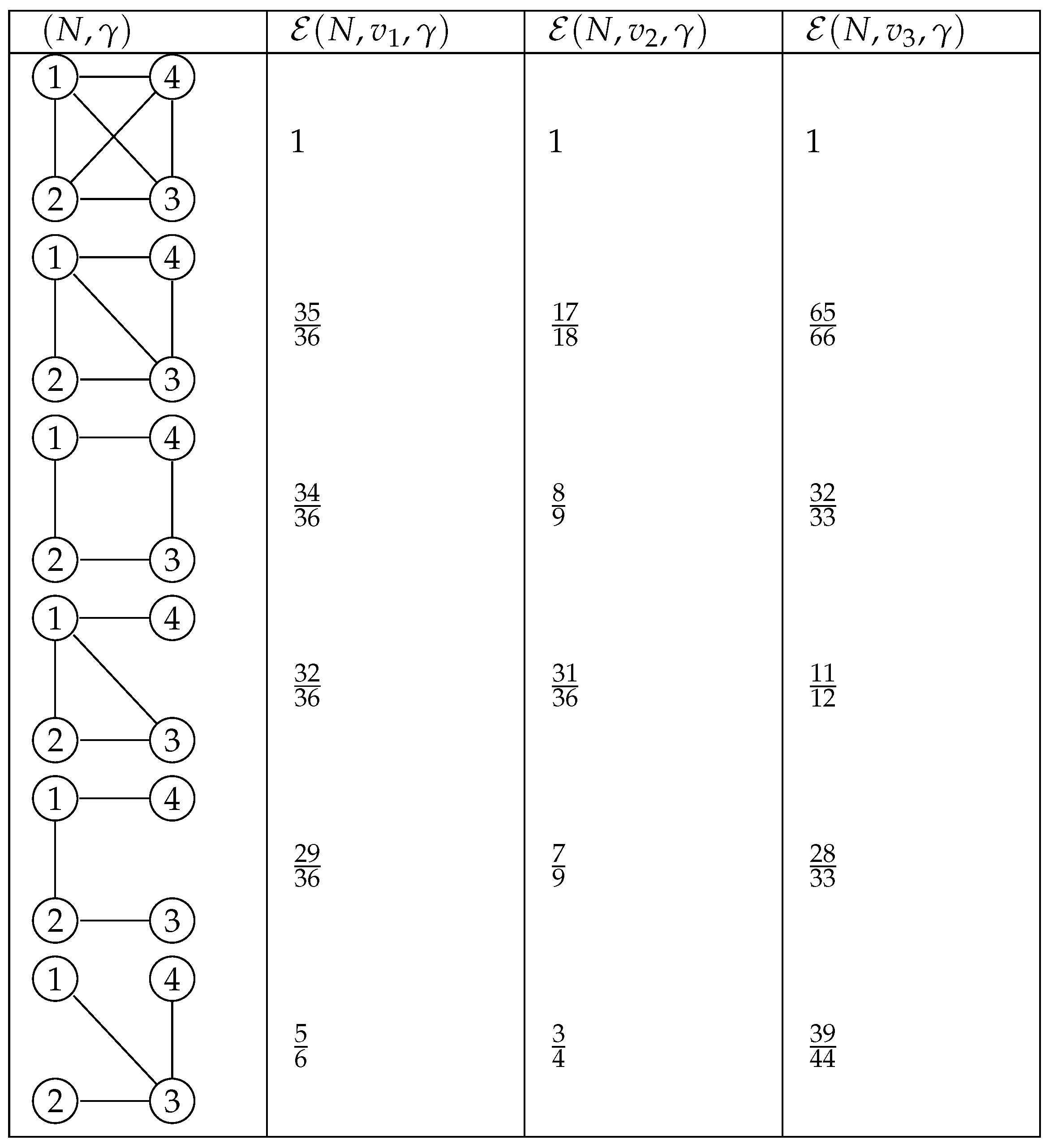
To motivate our definition let us consider the following example also included in Gómez et al. (2003).
Example 3.1. Let as denote with , and , respectively, the messages game, the zero-normalized overhead game and the conference game with characteristic functions given by:
-
i)
,
-
ii)
,
-
iii)
for . Suppose is one of the four-node connected graphs. Then, the efficiency (calculated with the proposed measure) of the (eighteen) different communication situations is given in the Table 1. For the within groups Myerson values of the nodes-players (communication centrality of the nodes), see Table 2 in Gómez et al. (2003).
Table 1.
for , and a four-node graph.
Table 1.
for , and a four-node graph.
Table 2.
Asymptotic behavior of the efficiency of chains, stars and wheels
Table 2.
Asymptotic behavior of the efficiency of chains, stars and wheels
|
|
|
|
|
|
0 |
|
|
|
|
|
|
1 |
|
|
0 |
|
|
|
We can observe some properties of the obtained figures that correspond to general properties of the introduced measures that will be proved throughout this paper. In particular, efficiency always remains between 0 and 1. It increases when adding edges if the game is convex, it equals 1 if the graph is complete, and among all trees, it is maximum in the star and minimum in the chain, provided that the game is almost-positive as in cases and .
The following proposition includes some properties related to the the range of values of the defined measures. The corresponding proofs can be found in Appendix I.
Proposition 3.1. Given , we have:
-
i)
Moreover, if is also a connected graph then
-
ii)
-
The lower and upper bounds of are reached, respectively, for the empty and the complete network. If is the complete graph and is the empty graph, then
and if the game is not zero-normalized, then
The following proposition lists some properties regarding the behavior of these measures in the face of changes in the network, ceteris paribus. Again, the corresponding proofs can be found in Appendix I.
Proposition 3.2. Given ,
-
i)
The disconnection of a player who is simultaneously null in the game and terminal in the graph does not affect the efficiency of the network. Then the network can be lightened by eliminating both null and terminal players, i.e., if is a null player in such that , we have that .
-
ii)
If we isolate an essential player in the game the efficiency of the network, whatever it is, becomes zero. This property can be seen as a possibility to override the efficiency of potentially dangerous networks (e.g. terrorist networks). Formally, if is an essential player in and isolated in the graph , then .
-
iii)
The star whose center is an essential player has maximum efficiency. This justifies that, in the construction of certain networks, a key player controls the entire communication flow. Formally, if is an essential player in which is also the hub of the star , then .
-
iv)
If the game is convex, the efficiency of a network does not decrease when adding a new link, i.e. if a convex game, then
In iv) of Proposition 3.2, the convexity condition cannot be weakened as it is seen in the following example.
Example 3.2.
Consider with and which is a superadditive but not convex game. Let and , then
As this example shows, in the case of a non-convex game, it may happen that a non-connected network is more efficient than a connected one.
The following proposition groups some more properties relating the measurements corresponding to different games. The proofs can be found in Appendix I.
Proposition 3.3. satisfied the following properties:
-
1.
It is invariant by strategic equivalence of the game. That is to say, efficiency is not changed if we transform the economic units in which the outcome of coalitions are measured, i.e., given and with and strategically equivalent, we have .
-
2.
When the measures are calculated for communication situations in which the network is not connected, it can be obtained as a linear combination of the efficiencies in the respective (component) communication situations, i.e., given , if , then,
-
3.
It is not linear in the game, ceteris paribus. Nevertheless the efficiency of a communication situation in which the game is the sum of other games, can be calculated as a convex linear combination of the efficiencies in the corresponding to these games communication situations, i.e., if , then it holds that,
-
4.
Fixed the network, we can obtain the efficiency in a communication situation in terms of efficiencies in communication situations with unanimity games, i.e., if , then,
-
v)
-
The efficiency of a connected network to communicate the coalition S is s times the probability of that coalition is connected in the graph, i.e., if , then
As a consequence of iv) and v) of previous proposition, we can easily obtain the expression of in terms of the Harsanyi dividends for some particular structures as trees, stars and chains.
Example 3.3. For superaditive and zero-normalized game,
-
1.
-
If is a tree then,
where is the connected hull of S in , i.e. the unique minimal connection set of S in .
-
2.
If is a chain ordered in the natural way then,
-
3.
If is a star with center at node 1 then,
In the following proposition we prove that, if the game is zero-normalized, symmetric and almost positive, then the maximum efficiency of the trees is attained in the star.
Let
and
two communication situations in which
is a zero-normalized, symmetric and almost positive game,
is the star with
as its hub and
is a tree. Then,
Proof.
As for , S not connected in , , to obtain the result it is sufficient to prove that, for , the number of connected sets in with s elements is greater or equal that the number of connected set in .
Effectively, for , the number of connected sets in of size s is , the total number of choosing links from the total links of the star. Clearly, the number of connected sets of size in a tree is bounded by as a connected set needs links and, in a tree, it is obvious that not all links generate a connected set of s elements.
□
In the following proposition we prove that, if the game is zero-normalized, symmetric and almost positive, among all the trees the minimum efficiency is reached in the chain.
Proposition 3.5.
Let and two communication situations in which is a zero-normalized, symmetric and almost positive game, is a chain and is a tree. Then,
Proof. Let us consider in the longest path (chain) and, without loss of generality, let us suppose that is labeled so that path is .
If , then and the result is proved.
Otherwise, we will transform in other in which the longest path has length strictly greater that r and such that . It is clear that repeating this process a finite number of times we prove the result.
Let us denote , the first node from 1 to r having degree greater that 2. As the longest path of differs from this node must exists.
Let k a node directly connected with h, and and let us define .
Consider the new tree defined as .
To prove that , let . Then we can distinguish three different situations:
- 1.
-
.
Then
and for these sets,
- 2.
-
.
Then clearly
and thus,
- 3.
-
and .
In this case,
. Let us denote
. Then,
If then the result is proved.
Otherwise, there is exactly one coalition such that,
is defined as
. If
then,
which concludes the proof.
□
Remark 3.2. The results of the last two propositions are not satisfied if the game is only superadditive or even convex. We have a counterexample in Example 3.1 where if the game is (overhead game), the chain efficiency is strictly higher than the star efficiency.
4. Efficiency and its asymptotic behavior in some particular cases
In this section we calculate the efficiency of the star, the chain and the wheel for a general superaditive symmetric an zero-normalized game. We particularize the obtained result for the three games considered in Example 3.1. Moreover, we analyze the asymptotic behavior of these efficiencies as the number of players/nodes increases.
4.1. The star
Consider the communication situation in which is a superaditive, symmetric and zero-normalized game and is a star with node 1 as the hub.
where the symmetry of the game is used in the third equality.
The within groups Myerson value for the node 2 (and thus for any other node different from the node 1) is:
the second equality holding as if the hub does not belong to a coalition, the connected components are singletons worthless (the game is zero-normalized) and the third equality holding as the game is symmetric.
Particularizing for the game
, with characteristic function
for all
, we have:
and thus
This means that, when the number of players increases the proportion of messages that can be sent without intermediation approaches to
.
If the game is
, which has characteristic function equal to
, for all
, we have:
which converges to
and thus, only half of the total value can be retained by the grand coalition in the limit.
Finally, for the game
, with
for all
we have,
and after some manipulations,
which converges to 1 when
n tends to infinity.
In this case the star is "efficient" in the sense that the total worth of the grand coalition can be retained by players as their number increases.
As it can be seen, the asymptotic behavior of the efficiency also depends on the game considered.
4.2. The chain
Consider the communication situation in which is a superaditive, symmetric and zero-normalized game and is a chain of n nodes that we assume to be numbered consecutively starting with 1 at one end.
In this case we have that,
The proof of this result is in the Appendix II.
In the following, we particularize the previous expression of the efficiency in the chain for the three games considered above. Also we analyze their asymptotic behavior.
For the game
, with characteristic function
for all
, we have:
If
we have
, with
K a constant between 0 and 1, and thus,
For the game
, with characteristic function
for all
, we have:
and thus,
For the game
, with characteristic function
for all
, we have:
and thus
4.3. The wheel
Consider the communication situation
in which
is a superaditive, symmetric and zero-normalized game and
is a wheel of
n nodes that we assume to be numbered consecutively.
We have,
and thus,
In the following we calculate expressions for the efficiency of the wheel in three games considered, and its asymptotic behavior as the number of players increases.
For the game
, with characteristic function
for all
, we have,
an thus,
For the game
, with characteristic function
for all
, we have:
and thus,
For the game
, with characteristic function
for all
, we have,
and,
.
In the following table we summarize the asymptotic behavior of the efficiency of chains, stars and wheels for the tree games considered. It can be seen that the introduced measure is sensible to the geometry of the network and the considered game.
5. A family of vulnerability measures
In this section we introduce a game theoretic family of measures for vulnerability of a network. We will continue with the same setting of communication situations used for efficiency measures. In our approach the vulnerability in can have two different origins.
On one hand it can be due to lack of connection between components of the graph. This causes that part of the value of the gran coalition
is lost and players can obtain only
. Then, we define the vulnerability due to disconnection in
as,
i.e., as the proportion of the total productivity in the game lost for lack of connection in the graph.
On the other side, by looking inside the components, lack of links generates costs of intermediation. The proportion of the productivity lost because of these intermediation costs can be seen as other type of vulnerability of the network, the betweenness vulnerability
. In our definition it is given by,
We will assume that these two types of vulnerability are additive and thus we propose the following definition.
Definition 5.1.
Given a communication situation , we define a measure of vulnerability of the network for the game as,
The following proposition includes some properties related to the the range of values of the defined measures. The corresponding proofs can be found in Appendix III.
Proposition 5.1. Given .
-
1.
We have that,
-
2.
-
3.
For connected graphs (ceteris paribus), the disconnection vulnerability vanishes, i.e, if is a connected graph, then,
-
4.
In any communication situation in which the network is complete, vulnerabilities due to lack of connection and intermediation are both null, i.e., for all , where is the complete graph, we have
-
5.
In the case of the empty graph all vulnerability is due to disconnection, i.e., for all , where is the empty graph, we have
The following proposition lists some properties regarding the behavior of these measures in the face of changes in the network, ceteris paribus. Again, the corresponding proofs can be found in Appendix III.
Proposition 5.2. Given .
-
1.
If is a terminal node in the graph and additionally, he is a null player in the game, the disconnection of neither nor changes, i.e., if such that , and is a null player in it holds that and
-
2.
If all the links incident in the node of an essential player in the game are broken, the disconnection vulnerability becomes 1 and the betweenness vulnerability vanishes, i.e., if is an essential player in we have that, and .
-
3.
reduces when adding links to a graph, ceteris paribus, i.e., given and with , we have This property is not satisfied for the other component of the vulnerability, the betweenness vulnerability, as the intermediation can increase. This is shown in the example following this proposition.
Example 5.1. Consider and with , and . Then, it is easy to verify that and .
The following proposition groups some more properties relating the measurements corresponding to different games. The proofs can be found in Appendix III.
Proposition 5.3. satisfied the following properties:
-
1.
The strategic equivalence between games preserves the vulnerability. And thus vulnerability does not depend on linear transformations, i.e., given and , and strategically equivalent, we have that and .
-
2.
The betweenness vulnerability of a not connected graph can be written in terms of the betweenness vulnerability in the graph restricted to different components, as it is proved in the next proposition, i.e.,suppose and Then,
-
3.
The betweenness vulnerability can be written as a linear combination of betweenness vulnerabilities in communication situations corresponding to unanimity games (fixed the graph), i.e., given we have,