Submitted:
08 December 2023
Posted:
11 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Related Works
2.1. Security Issues on FANET
2.2. Gray Hole and Sybil attacks and mitigations
2.3. Main Contributions
- In order to counteract Sybil attacks the adoption of elliptic curve cryptography (ECC) to ensure drones’ message authentication by means of Elliptic Curve Digital Signature Algorithm (ECDSA) has been proposed allowing for recognizing messages that are generated by fake identities drones, without using dedicated devices but only relying on the already available resources and computation capabilities provided in each drone.
- Following the work proposed in [24], we proposed a mitigation technique based on a trustiness metric to counteract the smarter version of the Black Hole attack, namely the Grey Hole. To the best of our knowledge, this is the first attempt to provide a security countermeasure to a Gray Hole attack for the GPSR protocol. The proposed mitigation technique is able to determine whether a drone of the network is acting as a Gray Hole node by keeping track of its behavior over time and, if needed, isolating it from the topology.
- As far as we know, there have been no proposals that combine the use of lightweight cryptographic primitives along with a mathematical detection algorithm to counteract the Sybil and Gray Hole attack.
3. Background
3.1. Flying Ad-Hoc NETworks (FANETs)
3.1.1. Greedy Perimeter Stateless Routing (GPSR)
- Greedy forwarding, used where possible;
- Edge forwarding, used where the technique cannot be used greedy.
- Relative Neighborhood Graph, ie a graph in which if there is an arc between two nodes A and B, then there must not exist a third node C such that its distance from A or B is less than the distance of A from B.
- Gabriel Graph, i.e. a graph in which if there is an arc between two nodes A and B, then there must be no other nodes in the area of the circumference having AB as diameter.
3.2. Public Key Cryptography
- Each communication party is associated with two keys: the public key and the private key.
- As their name suggests, the public key is publicly available while the private key must be kept private.
- When one of the keys is used to encrypt data, the other one must be used to decrypt that data. Generally, if public key cryptography is used to guarantee confidentiality the public key of the receiver party is used to encrypt data. Then the receiver will use its private key to decrypt it. If public key cryptography is used to generate digital signatures, the sender uses its private key to sign the message that the receiver will verify retrieving the public key of the sender.
3.2.1. Elliptic Curve Cryptography
3.3. Considered Attacks in the FANET
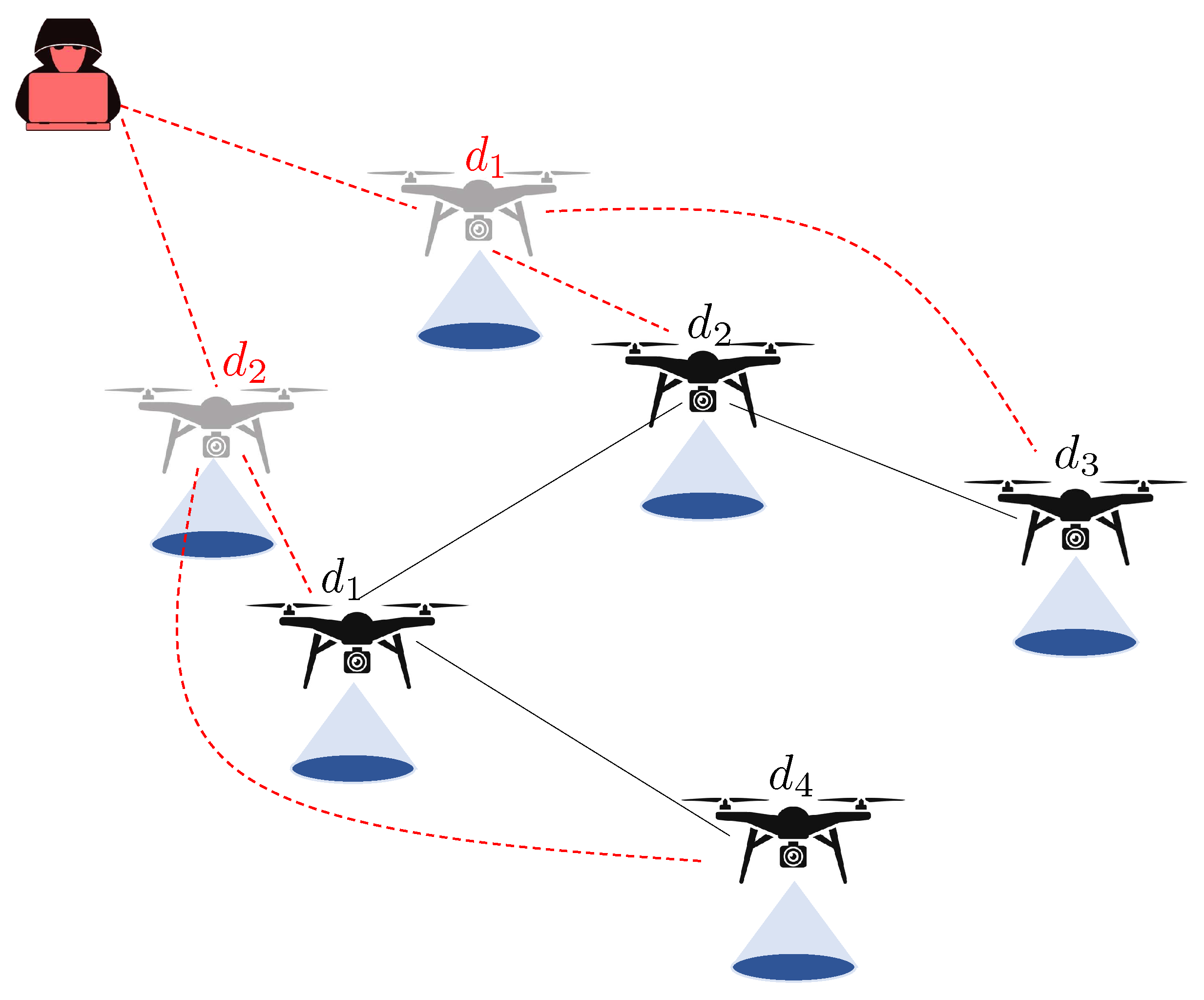
3.3.1. Sybil Attack
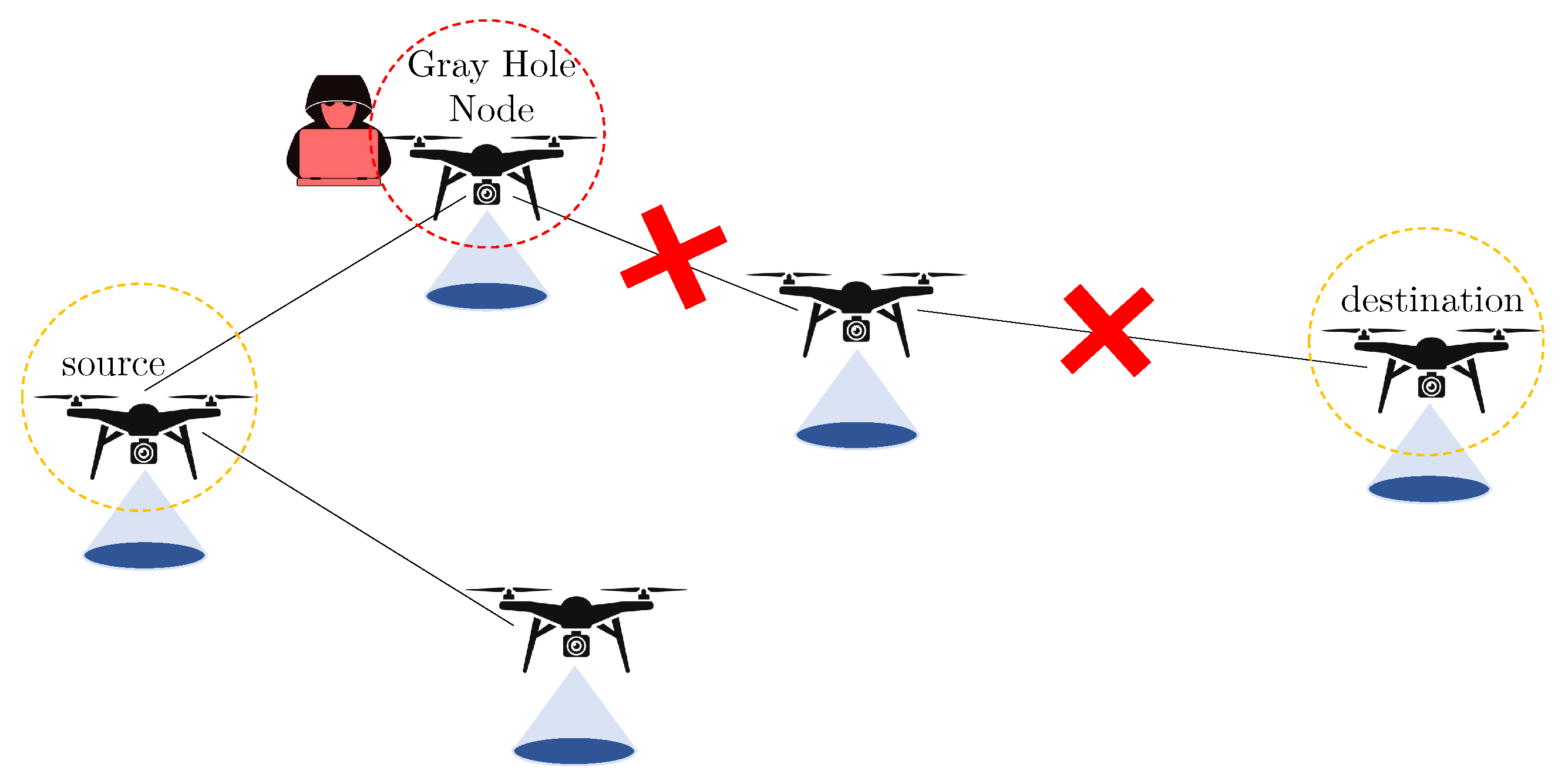
3.3.2. Gray Hole Attack
- Node Dependant Policy: only packets coming from or directed to a specific node of the network get discarded (e.g. packets from node “X” get dropped).
- Time Dependant Policy: Packets are dropped based on predetermined trigger time (e.g. each five seconds drop a packet).
- Protocol Dependant Policy: a packet is dropped according to the protocol to which it belongs (e.g. drop every TCP packet).
- Likelihood Dependant Policy: a packet is dropped based on the value that a variable, that follows a specific likelihood distribution, can take (e.g. following a random uniform likelihood distribution, each packet is dropped with a likelihood of 50%).
4. Proposed Secure GPSR (SecGPSR)
System Model
- A set of drones such that that compose the FANET.
- A set of drone identifiers . More specifically, each drone will be univocally identified in the system using with .
- Each drone is associated with a public and private key and .
- The framework involves a set of trusted Certificate Authorities (CAs) indicated with the acronym that issue a certificate to create the binding between a drone and its public key . Each CA also checks the authenticity of the binding and manages the certificate life cycle (Enrollment, Renewal, and Revocation). With no loss of generality and for the sake of simplicity we considered a unique CA that handles all the entities of the system.
- A set elliptic curves with supported by each drone .
Threat Model
- The unique CA used to issue and verify the certificate of the drones’ public key (), has been considered trusted. This means that the used CA is verified and approved by a Root Certificate Authority.
- It is supposed that the CA cannot be fooled by an attacker who wants to create a fake entity-public key binding issuing a crafted and fake certificate request to the CA.
- Each drone will act following the GPSR protocol specifications. No assumptions are made about unexpected wrong behaviors of drones (that are not related to malicious activities) that lead them to deviate from the normal behavior of the GPSR.
- It is assumed that each drone of the system can be hijacked by a malicious user who wants to turn the drone into a Sybil and/or Gray Hole node.
- No assumptions are considered on the resources available for the attacker. In other words, we built the proposal considering that the attacker has potentially infinite available resources.
- No assumptions have been made regarding the amount of possible fake identities that the attacker can create when launching a Sybil attack. We built the proposal considering that the attacker can craft an unlimited number of fake identities.
- The proposal does not rely on any assumption about how severe could be the dropping policy used for the Gray Hole attack.
4.1. Sybil Attack: Mitigation
- Extracting from .
- Computing
- If will be correctly authenticated and allowed to enter the network.
- If the node will not be allowed to join the network.
4.2. Gray Hole Attack: Mitigation
- The malicious drone receives a packet m.
- Based on a chosen dropping policy p it decides whether to drop or not m.
- If the result of the policy p is “drop” then the packet will be dropped.
- Otherwise the packet will be routed following the legacy routes and the routing protocol towards the destination.
5. Performance Evaluation
| Parameter | Value |
|---|---|
| Simulation Area (m) | 1500x800x300 |
| Simulation Time (s) | 600 |
| Number of Drones | 50 |
| Mobility model | TurtleMobility |
| Beacon Transmission Interval (s) | 1 |
| Protocol Type | UDP |
| Bit Rate (Mbps) | 24 |
| Communication Range (m) | 300 |
| Packet Size (Byte) | 128 |
| Types of attack | Sybil and Gray Hole |
| Maximum Number of Sybil nodes | 25 |
| Maximum Number of Gray Hole nodes | 25 |
| Gray Hole Drop Rate (DR) | 0.6 |
| 0.7 |
5.1. Sybil and Gray Hole Attacks: GPSR Performance
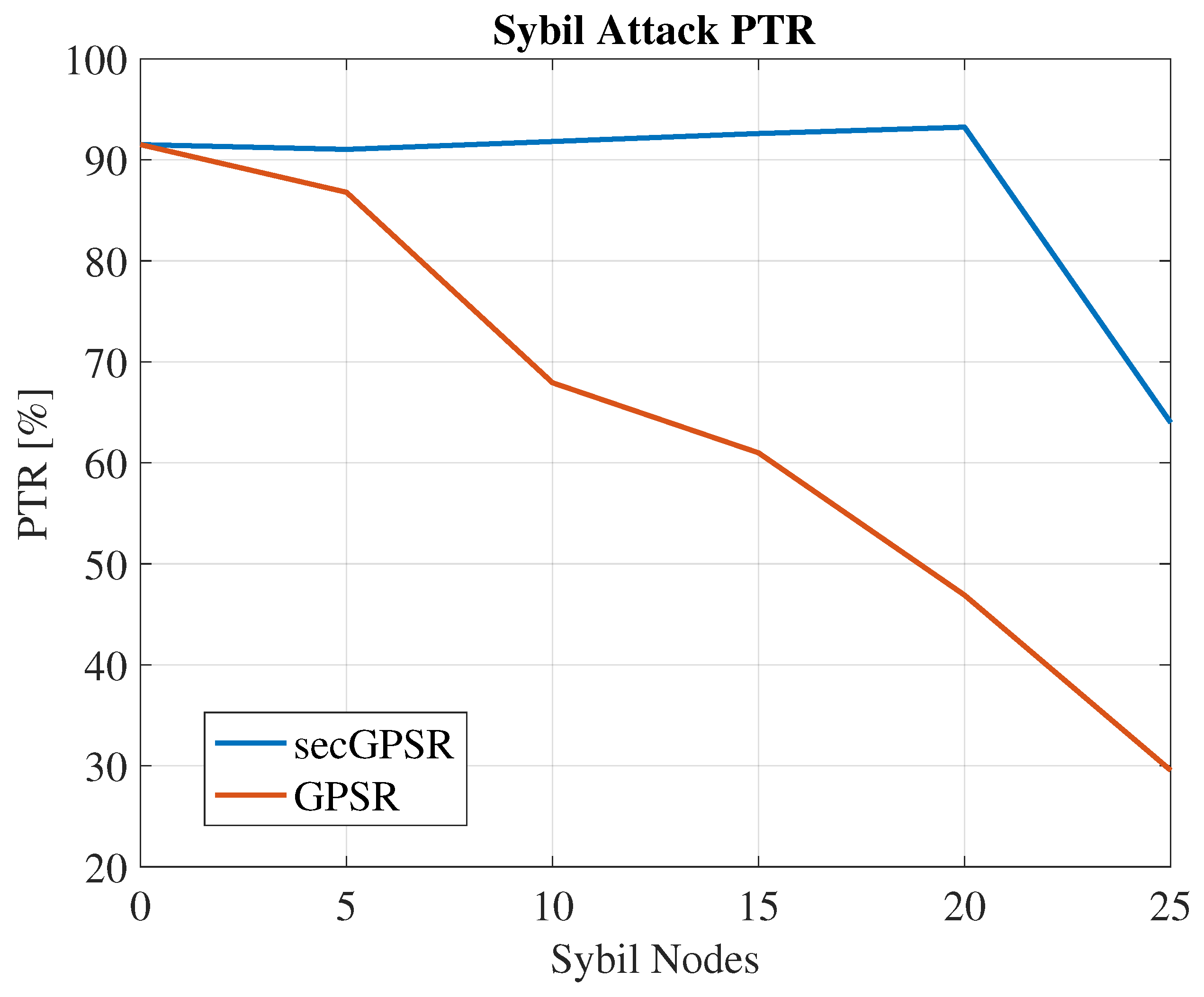
5.2. Sybil and Gray Hole Attacks: secGPSR Performance
5.3. secGPSR: Combined Attack Sybil and Gray Hole
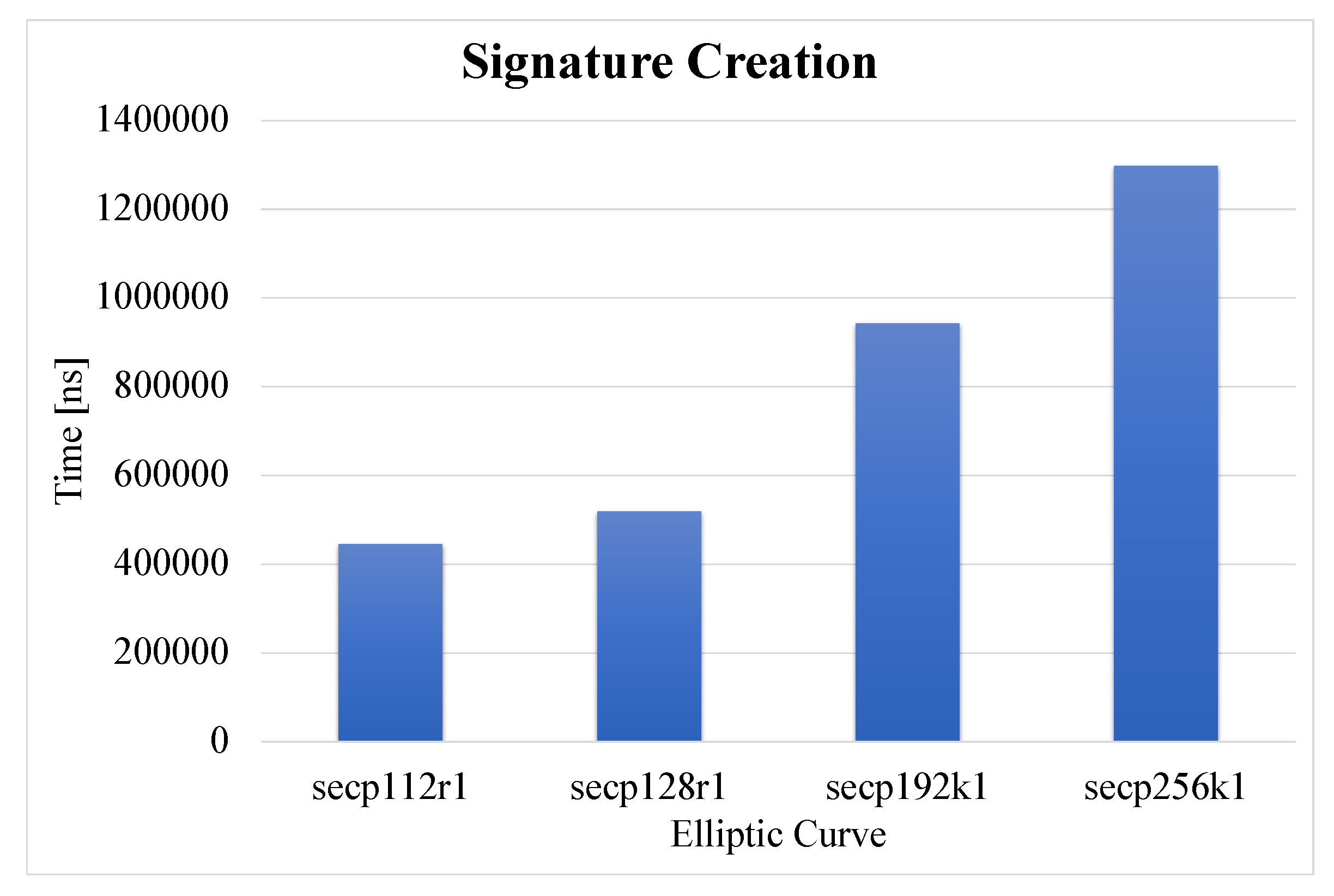
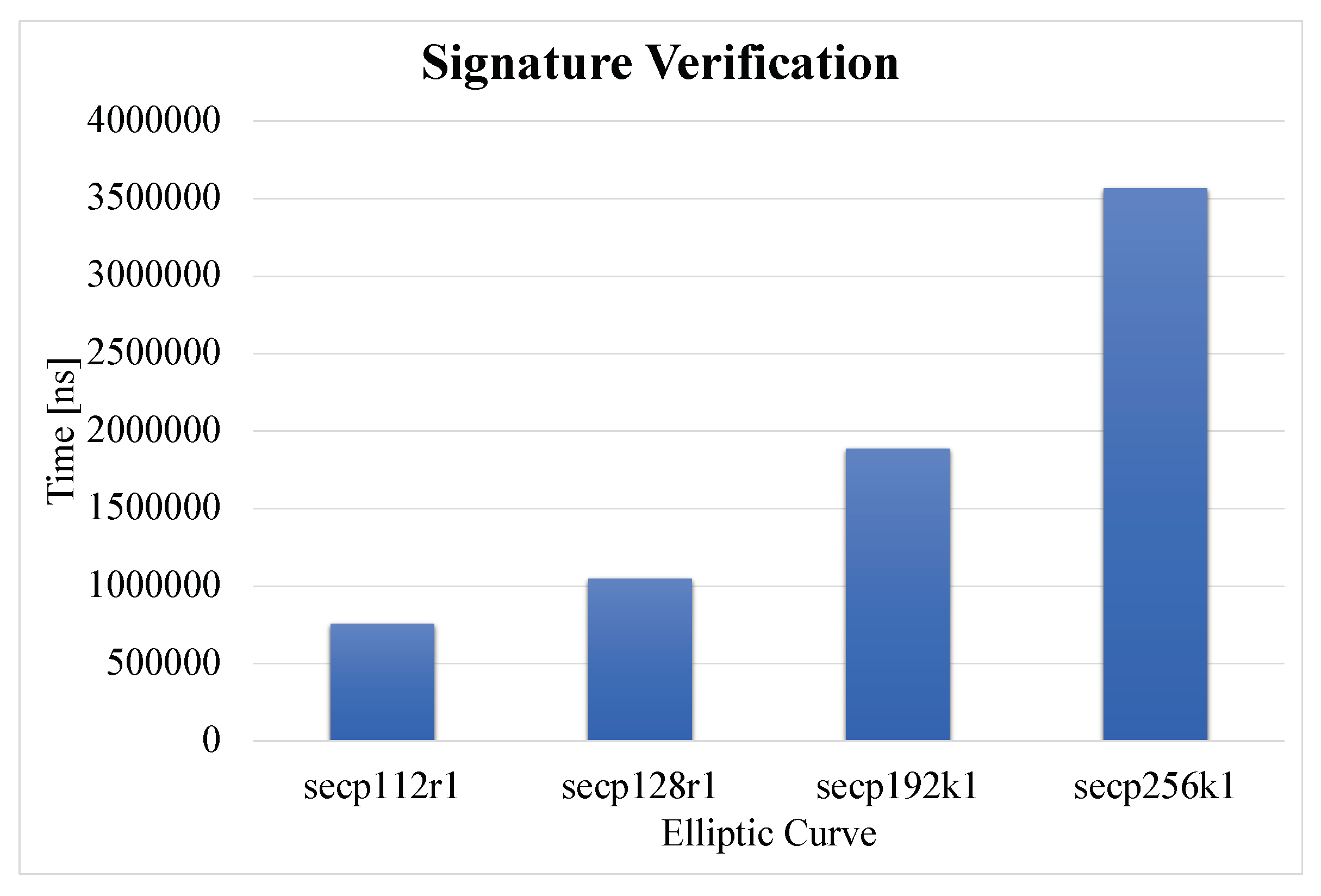
5.4. secGPSR Overhead Analysis
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Radoglou-Grammatikis, P.; Sarigiannidis, P.; Lagkas, T.; Moscholios, I. A compilation of UAV applications for precision agriculture. Comput. Netw. 2020, 172, 107148. [Google Scholar] [CrossRef]
- Tropea, M.; Spina, M.G.; De Rango, F. Supporting Dynamic IDS Deployment with Load Balancing Strategy for SDN-Enabled Drones in Emergency Scenarios. Proceedings of the Int’l ACM Conference on Modeling Analysis and Simulation of Wireless and Mobile Systems; Association for Computing Machinery: New York, NY, USA, 2023; MSWiM ’23; pp. 297–300. [Google Scholar] [CrossRef]
- Tropea, M.; Spina, M.G.; De Rango, F. SDN-driven Dynamic Deployment of IDS with Load Balancing for Drones in Emergency Scenarios. 2023 International Conference on Information and Communication Technologies for Disaster Management (ICT-DM), 2023, pp. 1–6. [CrossRef]
- Pasandideh, F.; da Costa, J.P.J.; Kunst, R.; Islam, N.; Hardjawana, W.; Pignaton de Freitas, E. A review of flying ad hoc networks: Key characteristics, applications, and wireless technologies. Remote. Sens. 2022, 14, 4459. [Google Scholar] [CrossRef]
- Oubbati, O.S.; Chaib, N.; Lakas, A.; Lorenz, P.; Rachedi, A. UAV-assisted supporting services connectivity in urban VANETs. IEEE Transactions on Vehicular Technology 2019, 68, 3944–3951. [Google Scholar] [CrossRef]
- Tropea, M.; Fazio, P.; De Rango, F.; Cordeschi, N. A new fanet simulator for managing drone networks and providing dynamic connectivity. Electronics 2020, 9, 543. [Google Scholar] [CrossRef]
- Amponis, G.; Lagkas, T.; Sarigiannidis, P.; Vitsas, V.; Fouliras, P.; Wan, S. A survey on FANET routing from a cross-layer design perspective. J. Syst. Archit. 2021, 120, 102281. [Google Scholar] [CrossRef]
- De Rango, F.; Tropea, M.; Fazio, P. Bio-inspired routing over fanet in emergency situations to support multimedia traffic. Proceedings of the ACM MobiHoc workshop on innovative aerial communication solutions for FIrst REsponders network in emergency scenarios, 2019, pp. 12–17.
- Karp, B.; Kung, H.T. GPSR: Greedy perimeter stateless routing for wireless networks. Proceedings of the 6th annual international conference on Mobile computing and networking, 2000, pp. 243–254.
- Oubbati, O.S.; Lakas, A.; Zhou, F.; Güneş, M.; Yagoubi, M.B. A survey on position-based routing protocols for Flying Ad hoc Networks (FANETs). Veh. Commun. 2017, 10, 29–56. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Choo, K.K.R.; Vinel, A.; Huang, X. Security and privacy for the internet of drones: Challenges and solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Jasim, K.S.; Alheeti, K.M.A.; Alaloosy, A.K.A.N. A review paper on secure communications in FANET. 2021 International Conference of Modern Trends in Information and Communication Technology Industry (MTICTI). IEEE, 2021, pp. 1–7.
- Kumar, C.; Mohanty, S. Current trends in cyber security for drones. 2021 International Carnahan Conference on Security Technology (ICCST). IEEE, 2021, pp. 1–5.
- Yang, W.; Wang, S.; Yin, X.; Wang, X.; Hu, J. A review on security issues and solutions of the Internet of Drones. IEEE Open J. Comput. Soc. 2022. [Google Scholar] [CrossRef]
- Tsao, K.Y.; Girdler, T.; Vassilakis, V.G. A survey of cyber security threats and solutions for UAV communications and flying ad-hoc networks. Ad Hoc Netw. 2022, 133, 102894. [Google Scholar] [CrossRef]
- Tangade, S.; Kumaar, R.A.; Malavika, S.; Monisha, S.; Azam, F. Detection of Malicious Nodes in Flying Ad-hoc Network with Supervised Machine Learning. 2022 Third International Conference on Smart Technologies in Computing, Electrical and Electronics (ICSTCEE). IEEE, 2022, pp. 1–5.
- Hassija, V.; Chamola, V.; Agrawal, A.; Goyal, A.; Luong, N.C.; Niyato, D.; Yu, F.R.; Guizani, M. Fast, reliable, and secure drone communication: A comprehensive survey. IEEE Commun. Surv. Tutorials 2021, 23, 2802–2832. [Google Scholar] [CrossRef]
- Remya Krishnan, P.; Arun Raj Kumar, P. Detection and mitigation of smart blackhole and gray hole attacks in VANET using dynamic time warping. Wirel. Pers. Commun. 2022, 1–36. [Google Scholar] [CrossRef]
- Younas, S.; Rehman, F.; Maqsood, T.; Mustafa, S.; Akhunzada, A.; Gani, A. Collaborative detection of black hole and gray hole attacks for secure data communication in VANETs. Appl. Sci. 2022, 12, 12448. [Google Scholar] [CrossRef]
- Hamdan, S.; Hudaib, A.; Awajan, A. Detecting Sybil attacks in vehicular ad hoc networks. Int. J. Parallel, Emergent Distrib. Syst. 2021, 36, 69–79. [Google Scholar] [CrossRef]
- Cui, Y.; Zhang, Q.; Feng, Z.; Li, X.; Wei, Z.; Zhang, P. Seeing is Believing: Detecting Sybil Attack in FANET by Matching Visual and Auditory Domains. arXiv 2023, arXiv:2306.16339. [Google Scholar]
- Aissaoui, R.; Deneuville, J.C.; Guerber, C.; Pirovano, A. A survey on cryptographic methods to secure communications for UAV traffic management. Veh. Commun. 2023, 100661. [Google Scholar] [CrossRef]
- Ren, S.; Li, D.; Hu, Q.; Liu, Y.; Liu, J. An Improved Security OLSR Protocol against Black Hole Attack based on FANET. 2022 13th Asian Control Conference (ASCC). IEEE, 2022, pp. 383–388.
- Zhou, Y.; Zhichao, M.; Wang, H.; Lu, Y.; Tian, Y. SZLS-GPSR: UAV Geographic Location Routing Protocol Based on Link Stability of Communication Safe Zone. 2023 15th International Conference on Computer Research and Development (ICCRD). IEEE, 2023, pp. 258–267.
- Klima, K. Cryptology:Classical and Modern; Taylor & Francis: Andover, England, UK, 2018. [Google Scholar] [CrossRef]
- Guide to Elliptic Curve Cryptography; Springer-Verlag, 2004. [CrossRef]
- Barker, E. Recommendation for key management; 2020. [CrossRef]
- Shanmuganathan, V.; Anand, T. A survey on gray hole attack in manet. IRACST–International Journal of Computer Networks and Wireless Communications (IJCNWC) 2012, 2. [Google Scholar]
- De Rango, F.; Palmieri, N.; Tropea, M.; Potrino, G. UAVs Team and Its Application in Agriculture: A Simulation Environment. Simultech 2017, 2017, 374–379. [Google Scholar]
- Imem, A.A. Comparison and evaluation of digital signature schemes employed in ndn network. arXiv 2015. [Google Scholar] [CrossRef]
| Hosts Number | Sybil Number | Sent Packets | Received Packets | PTR (%) |
|---|---|---|---|---|
| 50 | 0 | 636 | 582 | 91.51 |
| 45 | 5 | 636 | 552 | 86.79 |
| 40 | 10 | 636 | 430 | 67.61 |
| 35 | 15 | 636 | 383 | 60.22 |
| 30 | 20 | 636 | 295 | 46.38 |
| 25 | 25 | 636 | 188 | 29.56 |
| Hosts Number | Gray Hole Number | Sent Packets | Received Packets | PTR (%) |
|---|---|---|---|---|
| 50 | 0 | 636 | 582 | 91.51 |
| 45 | 5 | 636 | 561 | 88.21 |
| 40 | 10 | 636 | 491 | 77.20 |
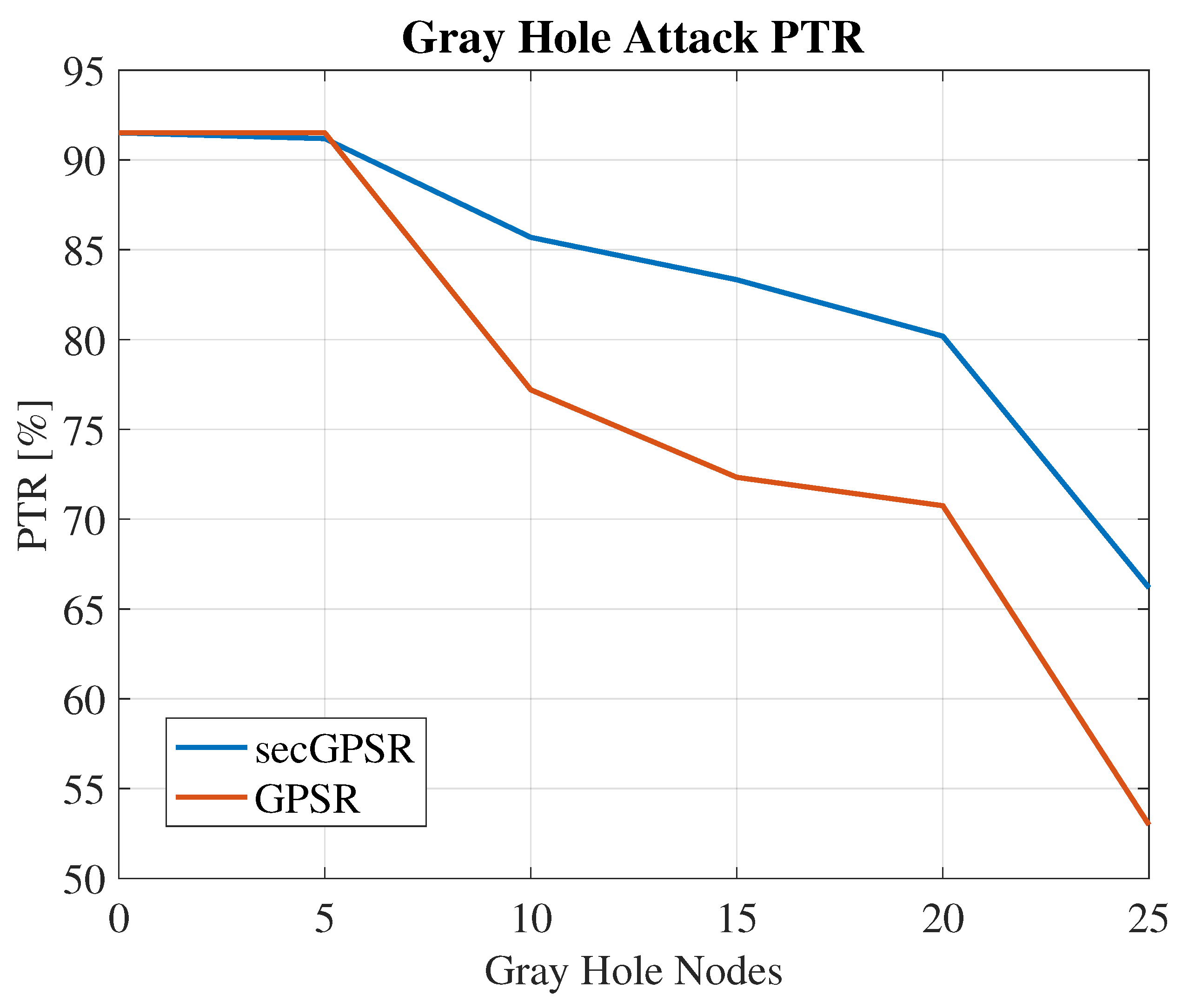
| 35 | 15 | 636 | 460 | 72.33 |
| 30 | 20 | 636 | 450 | 70.75 |
| 25 | 25 | 636 | 337 | 52.99 |
| Hosts Number | Sybil Number | Sent Packets | Received Packets | PTR (%) |
|---|---|---|---|---|
| 50 | 0 | 636 | 582 | 91.51 |
| 45 | 5 | 636 | 579 | 91.04 |
| 40 | 10 | 636 | 584 | 91.82 |
| 35 | 15 | 636 | 589 | 92.61 |
| 30 | 20 | 636 | 593 | 93.24 |
| 25 | 25 | 636 | 407 | 64.00 |
| Hosts Number | Gray Hole Number | Sent Packets | Received Packets | PTR (%) |
|---|---|---|---|---|
| 50 | 0 | 636 | 582 | 91.51 |
| 45 | 5 | 636 | 580 | 91.19 |
| 40 | 10 | 636 | 545 | 85.69 |
| 35 | 15 | 636 | 530 | 83.33 |
| 30 | 20 | 636 | 489 | 80.19 |
| 25 | 25 | 636 | 421 | 66.19 |
| Gray Hole Nodes | |||||
|---|---|---|---|---|---|
| 5 | 10 | 15 | 20 | 25 | |
| TP | 84 | 64 | 57 | 52 | 38 |
| FN | 1 | 1 | 1 | 0 | 0 |
| FP | 0 | 1 | 3 | 2 | 5 |
| TN | 2 | 4 | 10 | 11 | 22 |
| Hosts Number | Gray Hole Number | Sybil Number | Sent Packets | Received Packets | PTR (%) |
|---|---|---|---|---|---|
| 50 | 0 | 0 | 636 | 582 | 91.51 |
| 44 | 3 | 3 | 636 | 560 | 88.05 |
| 40 | 5 | 5 | 636 | 455 | 71.54 |
| 34 | 8 | 8 | 636 | 400 | 62.89 |
| 30 | 10 | 10 | 636 | 321 | 50.47 |
| 24 | 13 | 13 | 636 | 228 | 35.06 |
| Hosts Number | Gray Hole Number | Sybil Number | Sent Packets | Received Packets | PTR (%) |
|---|---|---|---|---|---|
| 50 | 0 | 0 | 636 | 578 | 91.19 |
| 44 | 3 | 3 | 636 | 577 | 90.72 |
| 40 | 5 | 5 | 636 | 575 | 90.25 |
| 34 | 8 | 8 | 636 | 542 | 88.05 |
| 30 | 10 | 10 | 636 | 512 | 82.39 |
| 24 | 13 | 13 | 636 | 359 | 63.05 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





