1. Introduction
In the past decade, numerous organizations have incurred expenses amounting to hundreds of millions of dollars or euros due to unforeseen disruptions and weaknesses in their supply chains. At the heart of these problems is the absence of dependable mechanisms to identify and effectively mitigate the escalating supply chain risks that result from increased global interconnectedness. As a consequence, the evaluation of supply chain risk is progressively gaining importance. There has been an exponential increase in the quantity of risk analysis papers published since the beginning of the century [
1]. Considering the quantity of scholarly articles dedicated to the most widely used risk analysis techniques and pragmatic implementations of FMEA in diverse domains, the supply chain would rank last on this list [
1]. Notwithstanding this, a multitude of concerns pertaining to the FMEA methodology continue to be unresolved in the recently published FMEA (released in [
2]). In regard to supply chain risk analysis, there remain uncharted territories.
The evaluation and selection of suppliers are critical components of the supply chain. Dickson established the initial classification system in 1966 [
3], and Cheraghi subsequently revised it in 2011 [
4]. Huang et al. [
1] published a systematic literature review in 2021 that demonstrates the exponential growth of risk analysis publications over the past two decades. Keyword analysis reveals that "FMEA", "system", "risk evaluation", "criticality analysis", and "failure mode" have risen to prominent positions. Similar findings were published by Liu et al. [
5] in 2013. It can be concluded that the FMEA continues to be the most widely utilized tool for risk assessment; however, it is presently employed in conjunction with alternative evaluation approaches [
1,
5].
Several authors [
6,
7,
8] have explored the factors contributing to the infrequent utilization of FMEA and other risk analysis approaches within the supply chain. The researchers conducted an investigation and successfully identified the underlying factors: the primary obstacle hindering broader implementation seems to stem from a deficiency in comprehending the application of FMEA within a supply chain context.
Numerous scholarly articles have highlighted the limitations of the FMEA [
5,
9,
10,
11].
The AIAG-VDA FMEA 1st Edition, a novel FMEA framework, was published in the year 2019 [
2]. The recent update to the system includes the addition of a chapter titled "Monitoring and System Response." In this update, the Risk Priority Number (RPN) has been replaced with Action Priority Tables. Furthermore, a comprehensive approach consisting of seven steps, namely planning, structure analysis, function analysis, failure analysis, risk analysis, optimization, and documentation of results, has been implemented. The utilization of the Severity (S), Occurrence (O), and Detection (D) scales persists, and it is advisable for the team to evaluate them in a manner consistent with a conventional FMEA. The utilization of the Action Priority Level, which is determined based on the values of the S, O, and D components from a designated Action Priority Table, has replaced the use of RPN. The table for AP levels, which is suggested, is derived from the values assigned to the components S, O, and D. However, it is subject to modification based on factors such as the nature of the business, the specific process, or the industry involved. The AP table delineates the instances in which the organization is authorized to initiate action, as opposed to the responsibility falling upon the FMEA Team. No action is required for Low AP levels, while any lack of action for Medium AP levels should be adequately justified. In the case of High AP levels, immediate action must be taken to mitigate the risk. This suggests that instead of relying on the RPN value, the actions are selected based on the specific values of the factors. Regrettably, as evidenced in
Table A6, the current system is incapable of accurately discerning the actual amount of risk.
It may be inferred from the existing body of research that the supply chain industry use
risk analysis methods that closely resemble those employed in various other domains. The authors exclusively employ the FMEA [
12,
13,
14] assessment technique, or a modified version of FMEA with factors limited to 5 levels instead of 10 [
15]. Alternatively, they utilize mixed evaluation techniques such as Fuzzy-FMEA [
11,
16,
17,
18,
19], Fuzzy-AHP [
20,
21], FMEA-ANP [
22], or Fuzzy Bayesian-based FMEA [
14]. Fuzzy FMEA [
19] is considered the second most often utilized risk analysis technique, following the FMEA method. The three membership functions commonly utilized in Fuzzy FMEA are triangular, trapezoidal, and Gaussian [
23,
24,
25].
The conventional approach for assessing supply chain risk predominantly involves employing the FMEA framework, which incorporates three key
factors: Severity, Occurrence, and Detection. A limited number of authors argue against the adequacy of three factors and instead propose the utilization of models that incorporate either four (expense, time, flexibility, and quality) [
26] or five (likelihood, consequence of time/delay, consequence of additional expense, consequence of damage to quality, and visibility) [
27] factors. In the present case, commonly employed variables were assessed, namely Visibility and Consequence, with the latter being determined by the provider’s delay, cost associated with the supplier, and the quality of the given components.
In the context of supply chain risk analysis,
new factors have emerged, such as Quality, Time, Cost [
14,
26], Intensity [
13], Consequence [
8], Effect, Cause, Measure [
28], and others.
The aggregation function of multiplication remains the most frequently employed method when examining the utilization of aggregation functions in the context of [
6,
7,
8,
21,
28]. The second approach integrates Fuzzy analysis with FMEA [
11,
16,
17,
20].
The exposure of businesses, irrespective of their industry, to both internal and external risks is evident through supply chain disruption. This document does not provide an exhaustive compilation of potential failures; rather, it presents a limited number of illustrative instances.
Internal supply chain interruption can potentially arise due to:
Instances of internal operational disruptions,
Instances of significant management, staff, and operational procedure changes,
Instances of failure to implement contingency plans in response to problems,
Instances of inadequate implementation of cybersecurity policies and controls leading to cyberattacks and data breaches,
Instances of non-compliance with labor laws or environmental standards,
Instances of unavailability of products to meet customer demands (attributable to inventory issues, ERP system malfunctions, human errors, etc.).
The external supply chain risk might arise due to factors such as:
Unpredictable or misunderstood consumer demand,
Delays in the transportation and distribution of commodities, encompassing many types such as components, finished products, and raw materials,
The potential risks posed by terrorism, armed conflict, economic or political penalties, as well as social, governmental, and economic challenges,
The management of supplier risk include concerns regarding the physical infrastructure and regulatory compliance of a supplier,
Natural disasters, such as tornadoes, hurricanes, and earthquakes,
Human errors occur at all levels and in all locations.
In summary, there is a dearth of a relevant, practical, and flexible instrument for conducting supply network risk evaluations. This tool should be easily accessible to supply chain managers and risk analysts, considering the aforementioned activities and global developments affecting the supply chain. This tool ought to enhance its effectiveness in identifying authentic threats, encompass a broader range of risk variables beyond the current limit of three, and maintain a level of user-friendliness comparable to that of the conventional FMEA methodology.
This article undertakes a comprehensive literature study on supply chain risk management approaches and presents a summary of the various types and extent of elements considered. The paper examines supplementary aggregation methodologies for situations involving numerous components, beyond three in number, by building upon the widely adopted FMEA as a foundational framework. Additionally, this study conducts a comparative examination of several risk analysis methodologies within the context of the flexible TREF-based risk evaluation framework ([
29,
30]). The framework is further enhanced by incorporating the Fuzzy-FMEA approach, and the techniques are subsequently ranked using the TOPSIS method. This paper presents a case study that investigates the analysis of supply chain risks in an automotive manufacturing service firm, primarily focusing on Tier 2 suppliers. The company is situated in a central position within the supply chain, making it an ideal subject for examining the practical implementation of this analytical approach. The experienced staff of the organization validates the supplied approach by doing a comparative assessment with the provided instrument.
3. Case study
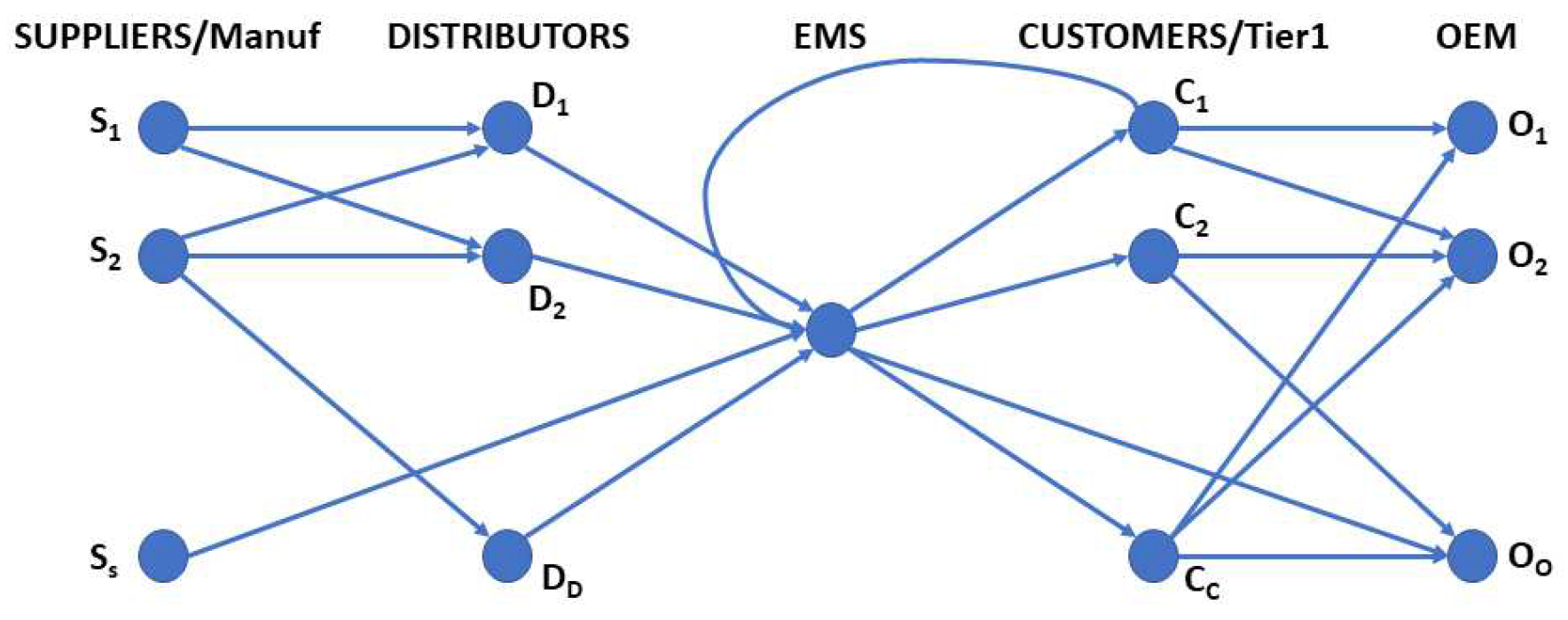
The study’s experimental focused on an electronic manufacturing services (EMS) supplier. Conducting testing within the comprehensive supply chain offers several advantages owing to the central location of the EMS (see
Figure 3).
In certain instances, manufacturers or, in extreme circumstances, direct customers are occasionally chosen as the source for larger quantities of raw materials or components, despite the customary practice of EMS firms to procure them via distributors . This holds particularly true in cases when the design of the final product is still undergoing development or when it becomes imperative to conduct tests on updated components. To facilitate the installation of these units by original equipment manufacturers (OEMs), the EMS delivers the goods to direct customers . Subsequently, these customers engage in further processes, such as the development of more intricate modules, testing, and programming.
Under some circumstances, the EMS may also provide the carmaker with goods directly, as indicated by the
connection in
Figure 3. The instances of
and
have been simplified in the EMS. They are treated as a single node or "location" because the EMS communicates with them through their Distribution Centers or offices, even though they consist of several factories/locations. Various logistical groups play a crucial role in facilitating the transportation of products between different nodes throughout the process. This case study offers a comprehensive opportunity to analyze a wide range of supply chain issues.
The automotive industry places significant importance on the availability of raw materials for manufacture, ensuring that they are provided in the appropriate time, quantity, and quality. Additionally, the industry recognizes the need for problem-free production, which is not the focus of this study, and the timely and accurate delivery of products to customers. Any departure from this stipulation leads to supplementary costs or a decrease in revenue.
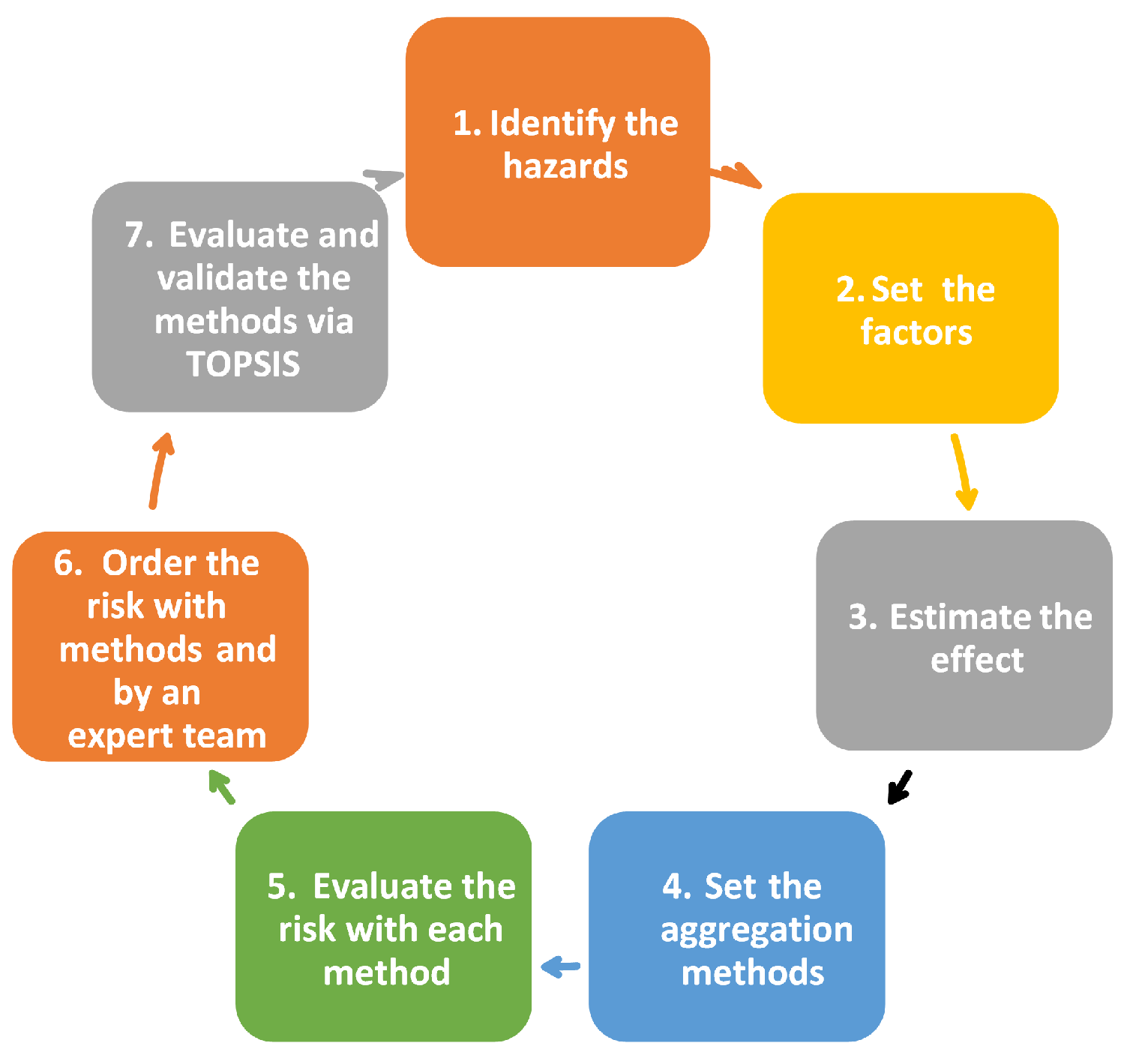
The assessment stages are depicted in
Figure 4, and they are employed in both the case study and the subsequent discussion of the theoretical framework underlying this methodology.
A team of professionals specializing in logistics, quality management, risk assessment, and FMEA was assembled within the EMS firm. The primary objective of this team was to conduct comprehensive testing, analysis, and validation of the entire approach. The establishment of such a team inside any automotive industry is facilitated by the requirement of their Quality Management System (QMS) to do so. The initial step, denoted as Step 0, might be conceptualized as the establishment of the team.
Step 1: The present study conducted an exhaustive analysis of various supply chain concerns, including claims, losses, and delays, spanning a period of four years. Subsequently, a comprehensive inventory of risks was compiled. In this particular case, a total of 20 unique concerns were identified.
Step 2: The criteria for evaluating each factor, specifically Occurrence, Severity, and Detection, are presented in
Table A1,
Table A2, and
Table A3 respectively. These tables may be found in the Appendix. The quantity of factors is contingent upon the intricacy of the business or logistic procedures, traffic patterns, business affiliations, and other pertinent considerations. It is imperative to assess these factors on a case-by-case basis for each company, as the level of risk may vary depending on factors such as geographical location, supply chain network, technological infrastructure, workforce availability and expertise, environmental conditions, and core technological capabilities. A severity rating was established to assess the most severe consequences resulting from a particular failure, with respect to both direct customers and OEMs. The decision should be made without considering the incidence, identification, or other relevant factors.
Step 3: The findings of the FMEA analysis, considering the aforementioned criteria, are presented in
Table A6. The result was generated by employing both the previous FMEA standard, which solely considered the initial three factors (Occurrence, Severity, and Detectability), and the present FMEA standard that included AP (Action Priority) levels.
The maximum RPN (Risk Priority Number) score observed in this particular instance for manual handling procedures is 162. This value slightly surpasses the commonly employed risk threshold. In the context of ISO9001, this threshold is typically regarded as the midpoint within the range of factors, resulting in a value of 125 for three factors (). In the automotive/IATF16949 industry, companies individually define this limit, which generally falls around 100 or lower, as determined by management. Moreover, when the most severe and imperceptible process flaw are amalgamated with a significantly low occurrence score, the Risk Priority Number (RPN) will amount to 100 (1x10x10), a value that falls below the commonly employed action criterion threshold by several firms. The implementation of the updated FMEA methodology will yield a marginally more accurate outcome. However, its effectiveness remains inadequate as the risk level was merely ty of implementing risk mitigation measures. If individuals are not justified, it is imperative that they become justified.
Table A6 illustrates three factors that are insufficient in appropriately highlighting the true level of threat. This is the reason why certain authors and researchers have started incorporating supplementary variables (such as doing analysis with four or five components).
Every organization has the autonomy to make a decision regarding whether to accept, mitigate, or acknowledge specific hazards. Based on the aforementioned information, the management of the company or the team of experts can ascertain the specific aspects that accentuate the level of risk. The upper echelons of management within this EMS company were engaged in consultation, resulting in the selection of two more elements, namely control and cost.
The cost refers to the estimated financial impact incurred due to errors or inefficiencies in handling or logistics. Within the realm of literature, this particular element is commonly referred to as "Value."
The second factor is the Control factor, which assesses the feasibility and effectiveness of controlling, preventing, or mitigating a process, and determines the extent to which it can be achieved. Please refer to
Table A4 and
Table A5 for a comprehensive overview of the established evaluation criteria pertaining to the supplementary components.
Step 4: The present set of factors include Severity, Occurrence, Detectability, Cost, and Control. The next step involves the selection of the aggregating functions that we intend to utilize for the purpose of analysis. The standard FMEA will be utilized as a fundamental framework and point of comparison. Due to the inclusion of three levels (L, M, and H) in the revised FMEA, it is important to note that these levels serve solely as indicators for subsequent evaluation and are not intended for the purpose of risk prioritization. Due to this rationale, the analysis will not incorporate the new FMEA. Additional aggregating functions that will be employed encompass Multiplication, Average, Sum, and Euclidean Distance, augmented with Fuzzy. These functions consist of five elements and are all encompassed inside the TREF technique. All of these topics are addressed in
Chapter 2.2.
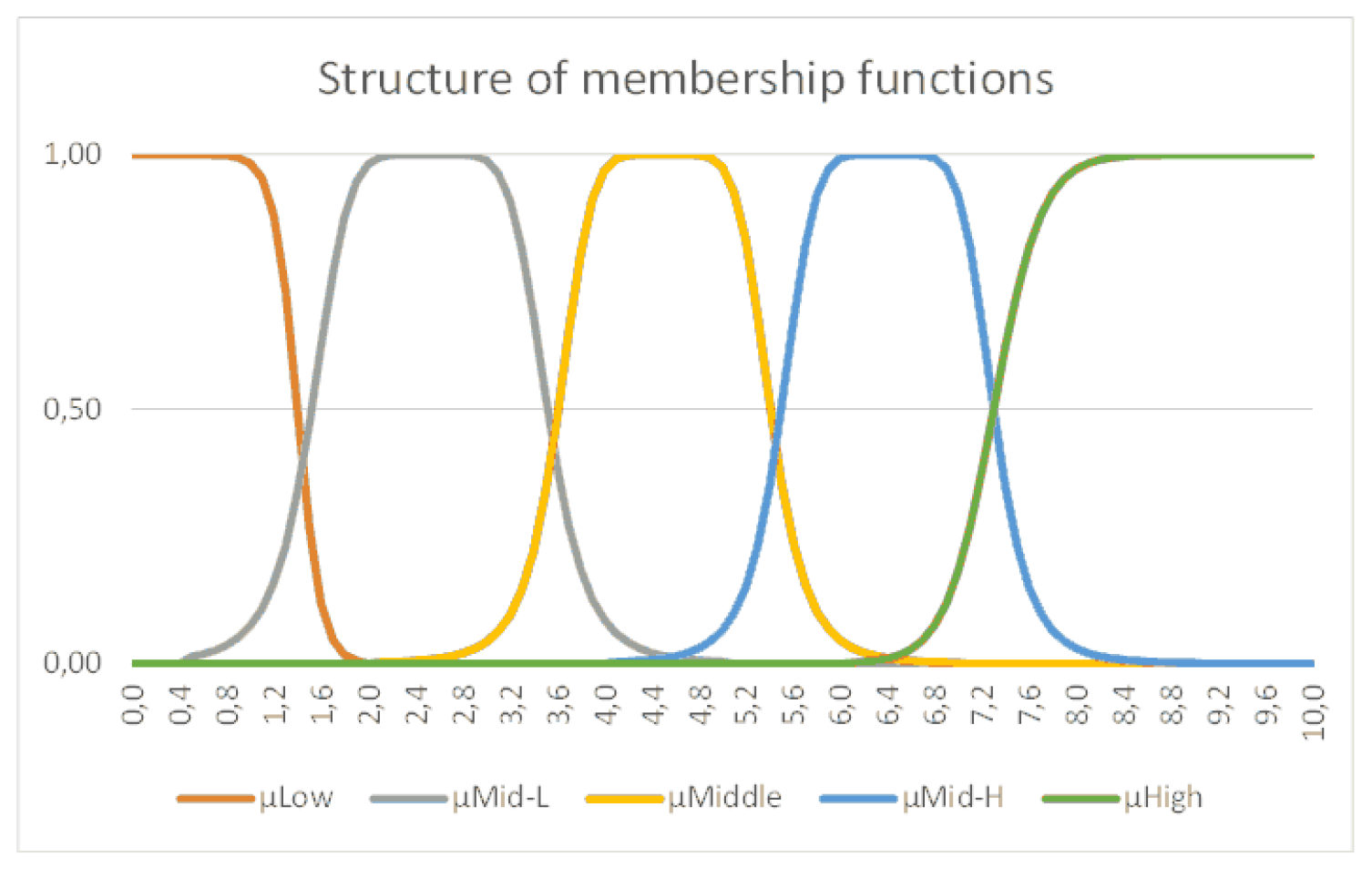
The fuzzyfication function, depicted in
Figure 1, is consistent across all five failure categories, namely severity, occurrence, detectability, cost, and controllability. With the exception of the initial and final functions, each function possesses a range in which its value is non-zero, and the midpoint is denoted. The variable
represents the midpoint, while
k denotes the number of linguistic variables utilized to describe each failure. In all instances, the membership function takes on values inside the range of 0 to 1. Here,
represents the count of non-zero elements in
,
, and
. The variables S, O, D, Cs, and Cn are used to denote the severity, occurrence, detection, cost, and controllability, respectively.
Step 5: The risk level can be determined by employing each of the six aggregating functions.
Step 6: This pertains to the arrangement of outputs resulting from aggregating functions. This step comprises two components: the application of the TOPSIS algorithm for ordering and the ordering process conducted by the expert team members.
The determination of the ranking by the TOPSIS method, employing the weight technique. The symbol
represents the average value of the membership function, with
i denoting the factors S, O, D, Cs, and Cn. Upon doing risk analysis using the aforementioned six risk analysis functions, the resulting risk values are calculated and subsequently arranged in a certain order. This process enables the risk analysis functions to be compared with one another, marking the completion of Step 6. The ranking outcomes are displayed in
Table 1 below:
The subsequent results are presented herein upon inputting all the data into R’s TOPSIS analysis program [
38] with uniform weights, while considering the assessment of impacts (see to
Table 2):
To illustrate the potential outcome in the absence of an expert-established importance matrix, a random impact matrix was employed, yielding the following result (see
Table A8).
Step 7: The evaluation of consequences holds significant importance in this stage and necessitates careful and strategic planning. The expert panel requested a group to allocate the incidents without considering the previously published rankings or the results of the risk assessment. This suggests that the aforementioned individuals lacked knowledge regarding the RPN values and the outcomes of the aggregation functions.
The ranking effect matrix (
Table A7) and the impact matrix (
Table A9) were generated using their respective scores. The precision of these matrices is of utmost importance as it exerts a substantial influence on the final result. This implies that the perspectives of a specific cohort of specialists with substantial expertise in evaluating the relative effects of each approach should be considered.
Table 3 displays the outcomes obtained from employing the matrices indicated earlier as weight and impact in the TOPSIS analysis program implemented in R [
38].
4. Discussion and Result
The ranking of the several aggregation approaches, ranging from the riskiest (method 1) to the safest (method 6), is provided in
Table 3. The finding that the basic FMEA with only three variables ranks as the riskiest is not unexpected, as experts emphasize the significance of two additional factors, namely Cost and Control, which are deemed highly important.
The ranking of the remaining five risk aggregation methods, which consider five factors as input and employ multiplicative, average, median, modified Euclidean distance, and fuzzy functions, is very interesting.
The utilization of the frequency perspective in the assessment process can prove to be useful. The
Crystal Ball application developed by Oracle, which is an add-in for Microsoft Excel, was employed for this purpose. For the examination of three variables, specifically for the conventional FMEA, the trial number was established at 10,000. In this particular case, the sensitivity for each element was 33.3In the case of evaluating five factors, the trial numbers were set to 100,000 in order to achieve equal sensitivity for each element, with each factor accounting for 20% of the total.
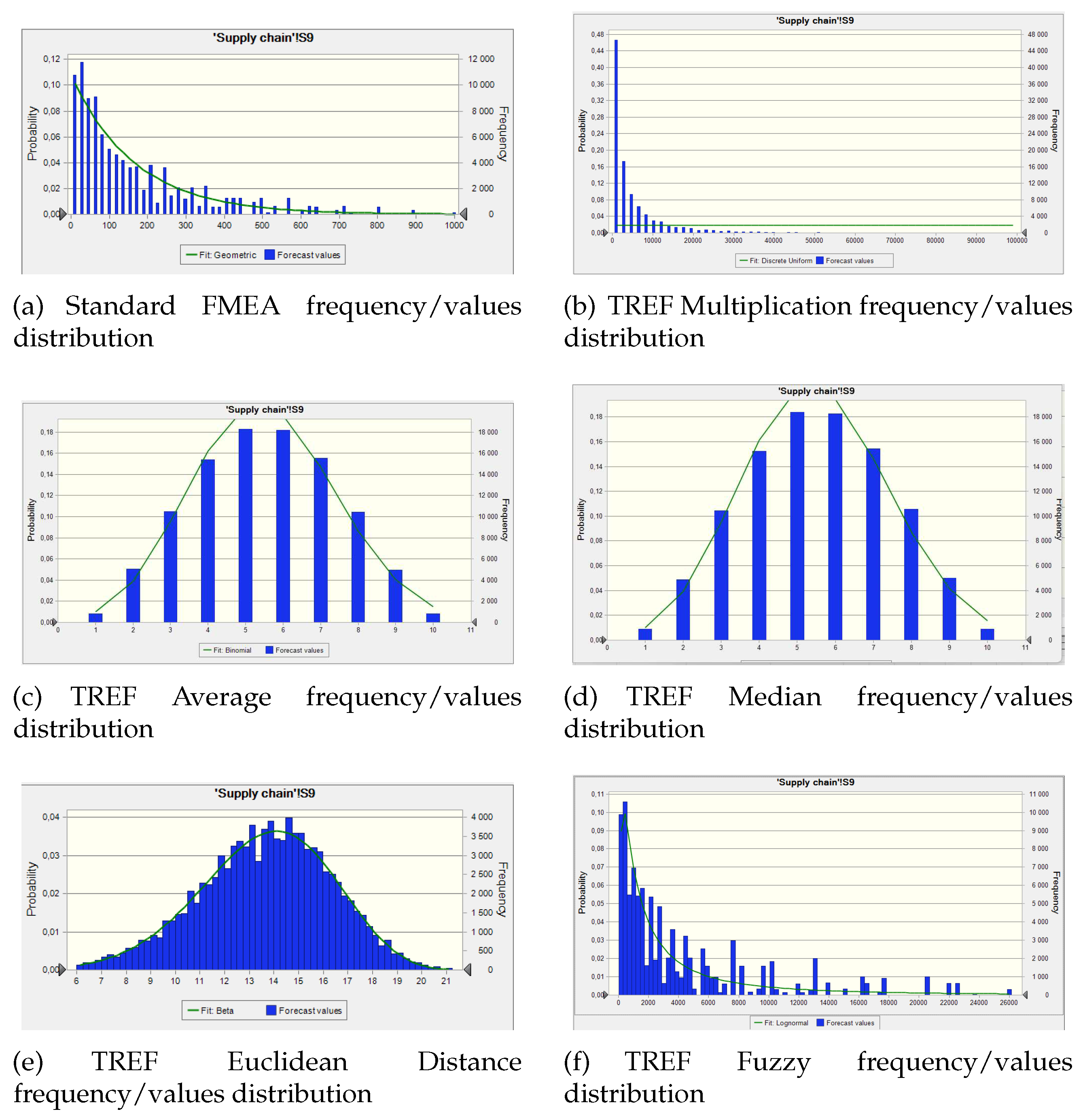
Figure 5 displays the generated figures.
Table 4 presents a comprehensive overview of the simulations.
The Skewness in
Table 4 pertains to the absence of symmetry in the dataset, whereas the Kurtosis assesses whether the data exhibit heavy (positive values) or light (negative values) tails relative to a normal distribution.
Upon examination of the simulation figure (
Figure 5)), it is evident that:
The results obtained via the
Multiplication Aggregation Method, as depicted in
Figure 5.b, exhibit a level of comparability to those obtained from a conventional FMEA. However, it should be noted that the former method involved the consideration of five components, whereas the latter method typically considers three components. The linearity of the Multiplication technique and the standard FMEA is commendable. Consequently, the outcome for a scenario including n factors will yield a range of
for each factor, where the range of each factor is
. The concerns of FMEA are equally relevant in this particular case.
The input range and output range for the
Average aggregate in
Figure 5.c are identical, spanning from 1 to 10. Demonstrates strong linearity. The presence of extreme values can pose challenges in some scenarios. In the event that one factor attains its maximum value and the remaining factors maintain low values, the resulting output will nevertheless fall below the midpoint of the output range. In this particular scenario, the presence of low-value components effectively mitigates the impact of any extreme values, hence impeding the identification and analysis of potential risks.
The
Median aggregation yields the lowest Skewness score, as depicted in
Figure 5.d, suggesting that the data exhibits a high degree of symmetry. The Kurtosis score of our dataset is rather low, suggesting a moderate level of customization in the data. This situation bears resemblance to the Average aggregation approach.
The linearity is only average and the computation is challenging in the case of the
Euclidean distance (generalized) aggregate (see Fig.
Figure 5.e). Interpretation is challenging in n-dimensional space where n>3. In the case of n factors, the output will be
for each factor’s range of values of
. The linearity of the Euclidean distance (generalized) aggregate is only average, and its computation is problematic, as depicted in
Figure 5.e. The task of interpretation becomes complex when dealing with n-dimensional space, where n exceeds three. For a given number of factors, denoted as n, the resulting output will range from 1 to
. This range applies to each individual factor within the set of factors, where each component’s values vary from 1 to 10.
The outcome data for the
Fuzzy aggregation method (refer to
Figure 5.f), which is determined by the used membership and defuzzification functions, exhibit similarities to those of the TREF Multiplication. However, it is important to note that the output consists of just five primary groups (see
Figure 1).
In conclusion, it is important to acknowledge that aggregations utilizing multiplication approaches, such as FMEA, generalized TREF Multiplication, and TREF Fuzzy with respect to defuzzification, yield the most unfavorable distribution. However, their significant contributions become essential in situations when elements exhibit elevated levels of risk.
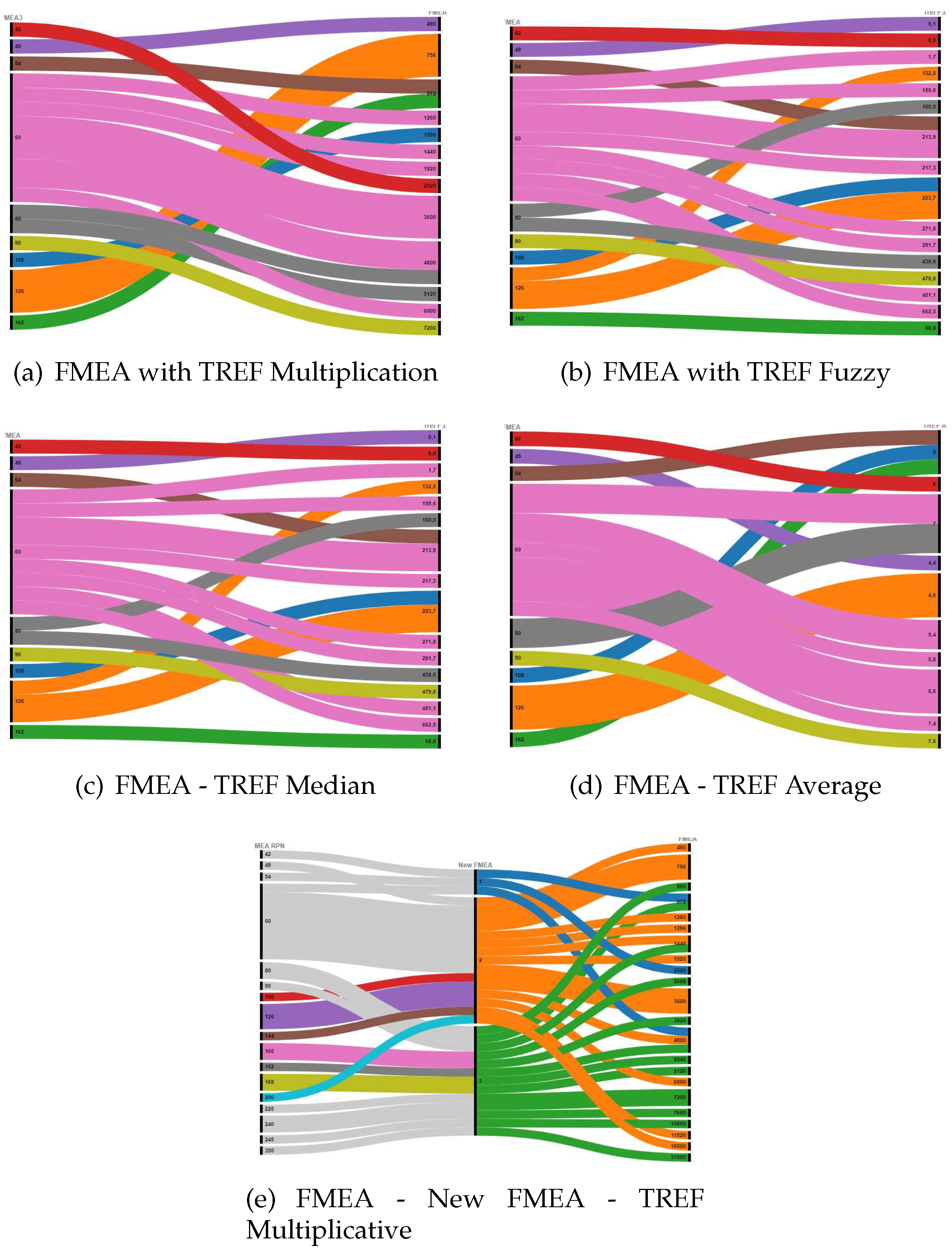
The reason for arranging each output in decreasing order was to ensure that this pattern was accurately represented. The comparative analysis of rank modifications for various aggregation functions is illustrated in
Figure 6.
The present graphic depiction of Alluvian representation serves to emphasize the discrepancies in ordering through the comparison of an initial state and a subsequent state. The depiction, however, commences with the conventional outcomes of the FMEA as a foundation, considering the sequential Risk Priority Number (RPN) or output values. Subsequently, it demonstrates the alteration in prioritization of the aforementioned risk subsequent to the implementation of the novel aggregate function. The final diagram encompasses a triple figure that visually represents the transition from the conventional FMEA to the enhanced FMEA incorporating risk levels. This diagram enables readers to discern the differences between the two approaches. Additionally, the diagram includes the TREF Multiplicative, which functions as a comprehensive representation of various components. Please refer to
Figure 6.e for further details.
The comparison between the conventional FMEA and the TREF Fuzzy method depicted in
Figure 6.b holds significant importance in this study as it demonstrates the optimal results achieved by the utilization of the TREF Fuzzy aggregation function, as indicated in
Table 3. The outcome was validated by the team of experts.
Outcome: The results obtained from this approach have been implemented, following the PDCA model (see
Figure 4), and are presently under close scrutiny. If a new type of failure or unforeseen outcomes arise, the analysis will be repeated. After a period of six months of usage, no variation was seen.
Remark: The purpose of this paper is to provide a comprehensive guide for the identification of risks connected with Supply Chain Management (SCM). Its objective is to facilitate a thorough understanding of various risk variables and their corresponding significance. This document imposes some limitations, with the exception of donations. The process of prioritizing risks is contingent upon the thorough examination, evaluation, and distinctive perspectives that have surfaced pertaining to the manufacturing facility in question, and at the specific moment of the expert’s deliberation. Consequently, a hasty method has the potential to significantly undermine the precision and reliability of the investigation.