Submitted:
20 December 2023
Posted:
21 December 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
- An overview of blockchain and IPFS technology is briefly highlighted and analyzed.
- The benefits and drawbacks of existing cloud storage blockchain-based studies are discussed.
- The blockchain-based cloud storage applications are explored e.g., IPFS.
- The fundamental components of blockchain-based distributed cloud storage solutions are analyzed based on a-various factors.
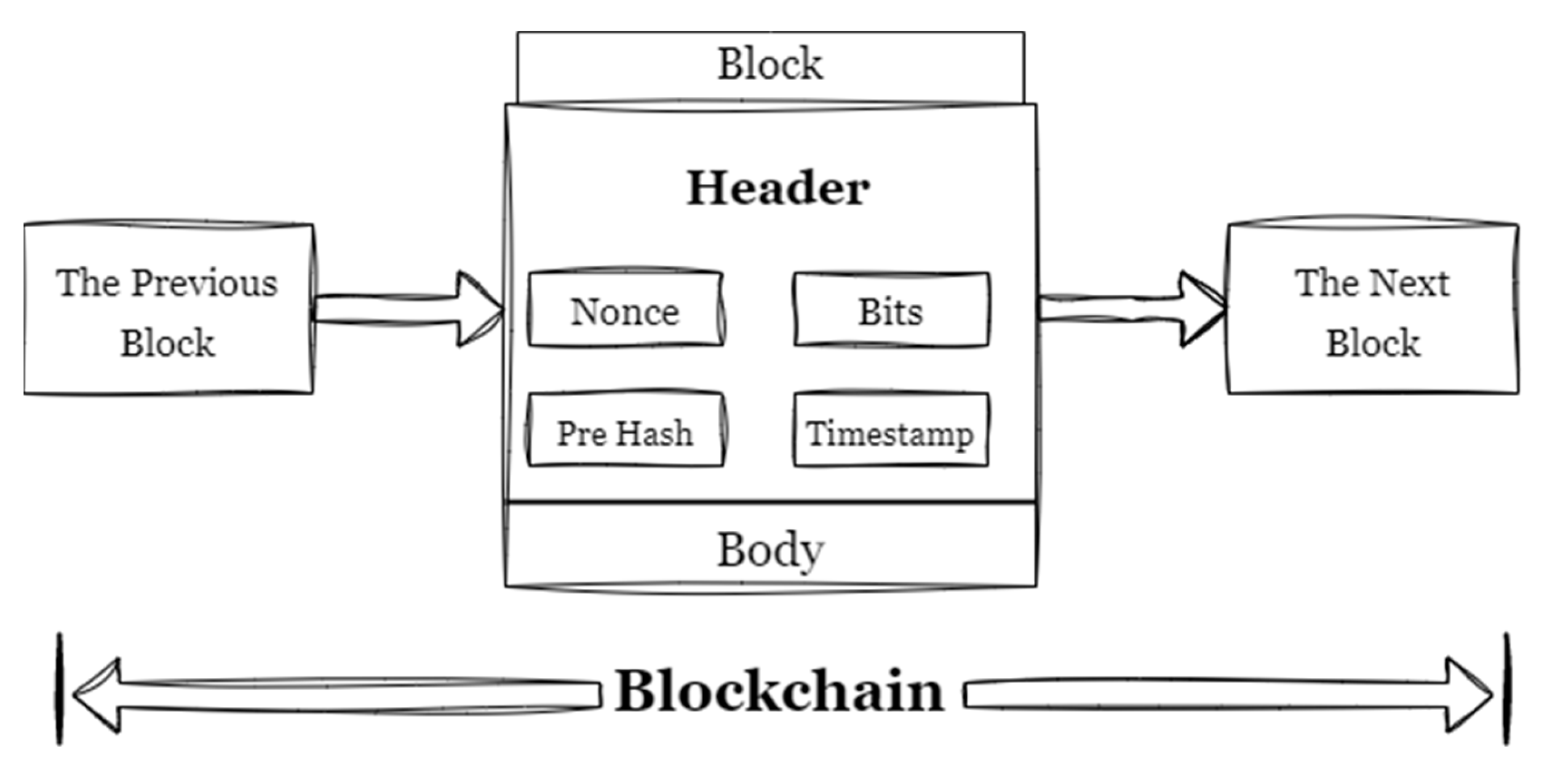
2. Systematic Literature Review
2.1. String Development
2.2. Searching Protocol
2.3. Selection of Publication
2.3.1. Inclusion Criteria
2.3.2. Exclusion Criteria
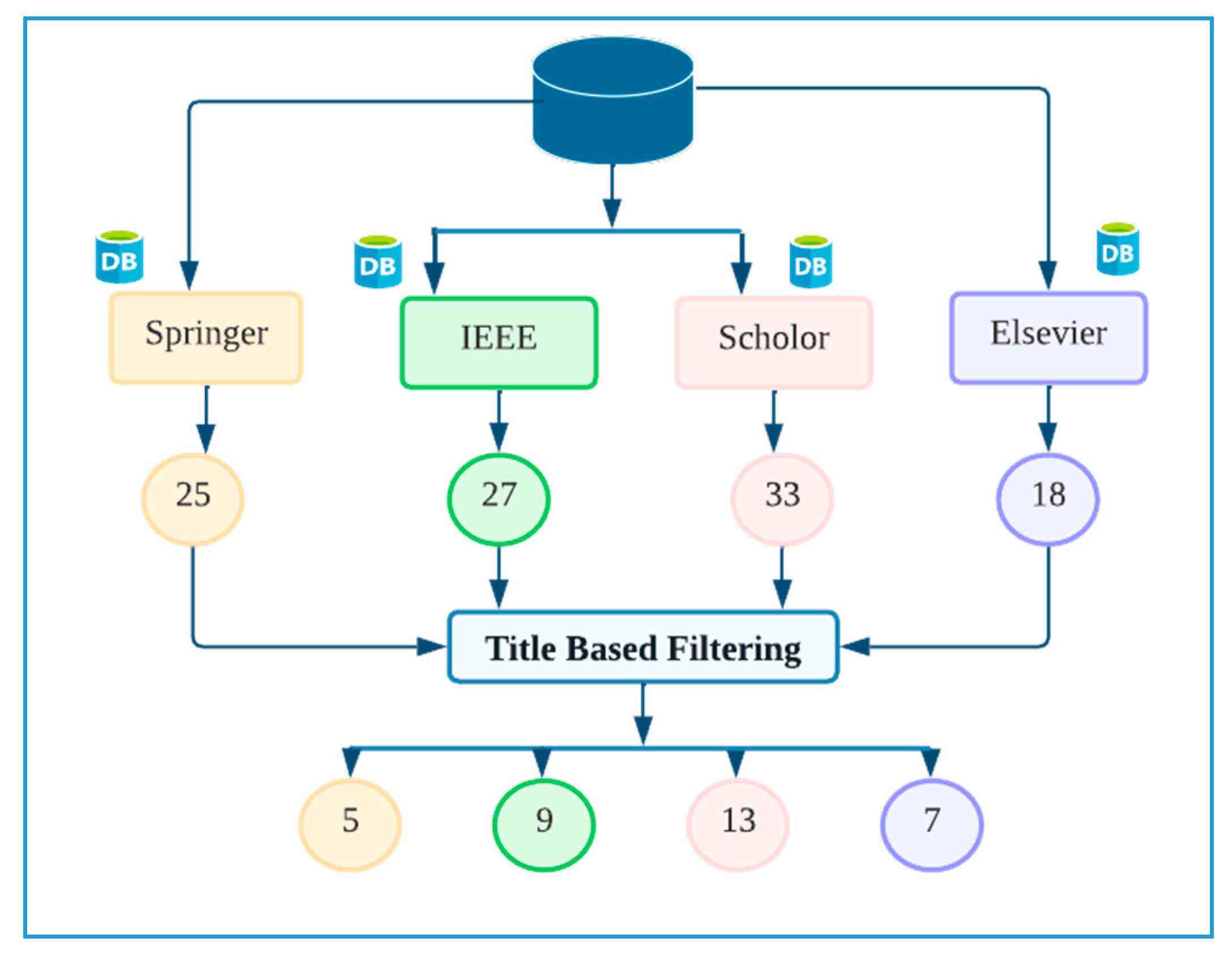
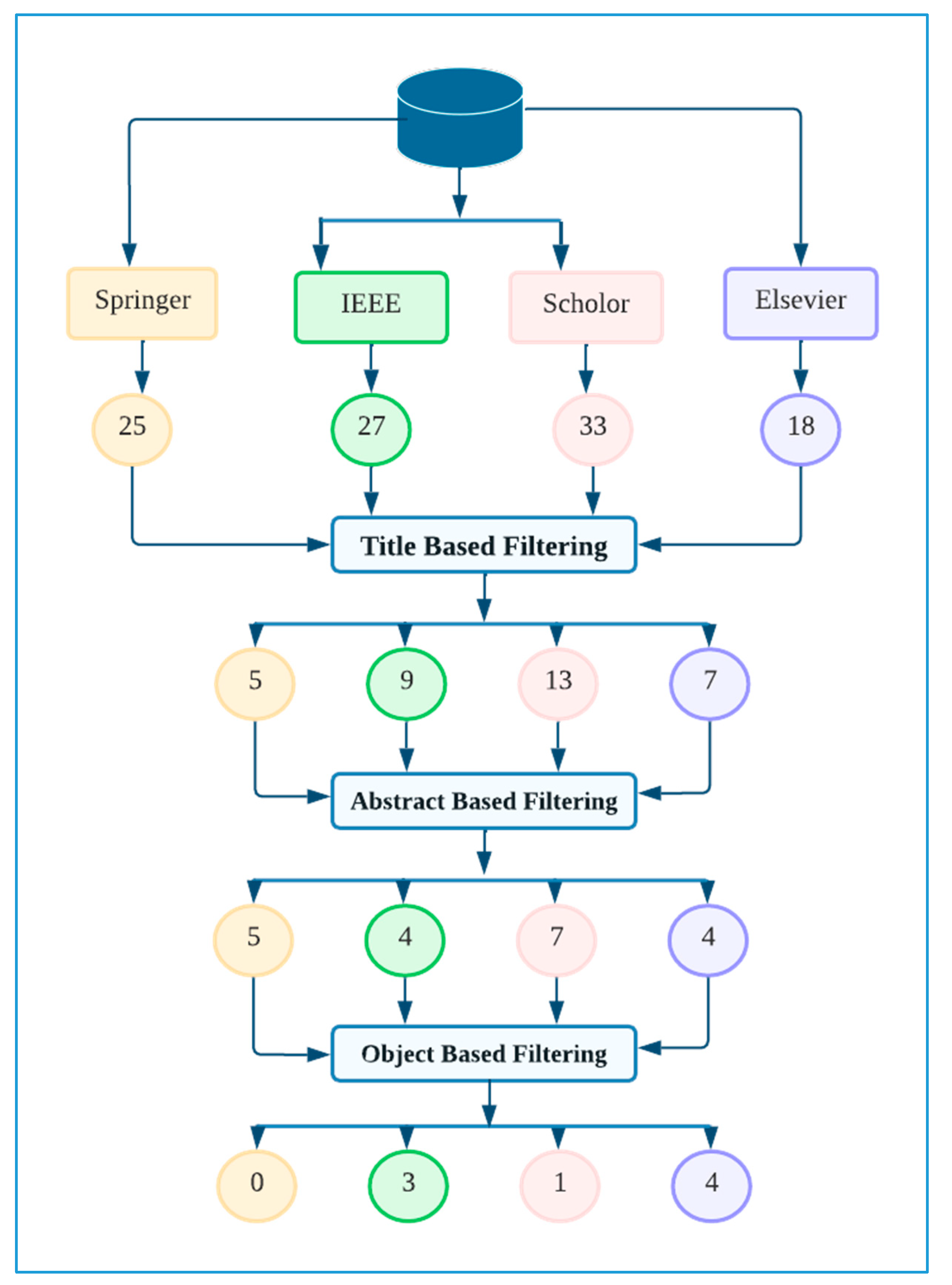
2.4. Filtering
- Title-based Filtering
- Abstract-based Filtering
- Object-based Filtering
- Technique-based Filtering
2.4.1. Title Based Filtering
2.4.2. Abstract Based Filtering
2.4.3. Objective Based Filtering
2.4.4. Technique-Based Filtering
2.5. Detailed Literature
2.5.1. InterPlanetary File System (IPFS) Based System
2.5.2. Consensus Protocol Based System
- 1)
- To complete the PoW (Proof-of-Work) algorithm, a hash must meet a predetermined threshold.
- 2)
- PoS (Proof-of-Stake) has been presented as a solution to the problem of energy usage in PoW.
- 3)
- Practical Byzantine Fault Tolerance (PBFT) enables quick consensus.
2.5.3. Key Based Protocol System
2.6. Critical Review
5. Identified Challenges
5.1. Need to Work with Scalability
5.2. Need to Work on Encryption Methods in Blockchain
6. Optimal Solutions
| Problem | Solution |
| Scalability with Key Management | Consortium Hierarchical Key Management [16] |
| Dynamic Consensus Protocol [17] | |
| Partitioning, Sharding, And Off-Chain Storage [18] | |
| Encryption Strategy | Advanced Encryption Standard (AES) and Elliptic Curve Cryptography (ECC) [19] |
| Public-Key Cryptography and Homomorphic Encryption [20] | |
| Multi-Layered Approach [21] |
- The first layer focuses on the use of strong encryption algorithms, such as AES and ECC, to protect data on the blockchain. This layer also includes the use of secure key management techniques to ensure that keys are properly protected and not vulnerable to attacks.
- The second layer focuses on the use of regular security audits to identify potential weaknesses in the blockchain encryption. This layer includes the use of both manual and automated techniques to detect vulnerabilities and security issues.
- The third layer focuses on the use of additional security measures, such as access controls and intrusion detection systems, to further protect the blockchain from attacks.

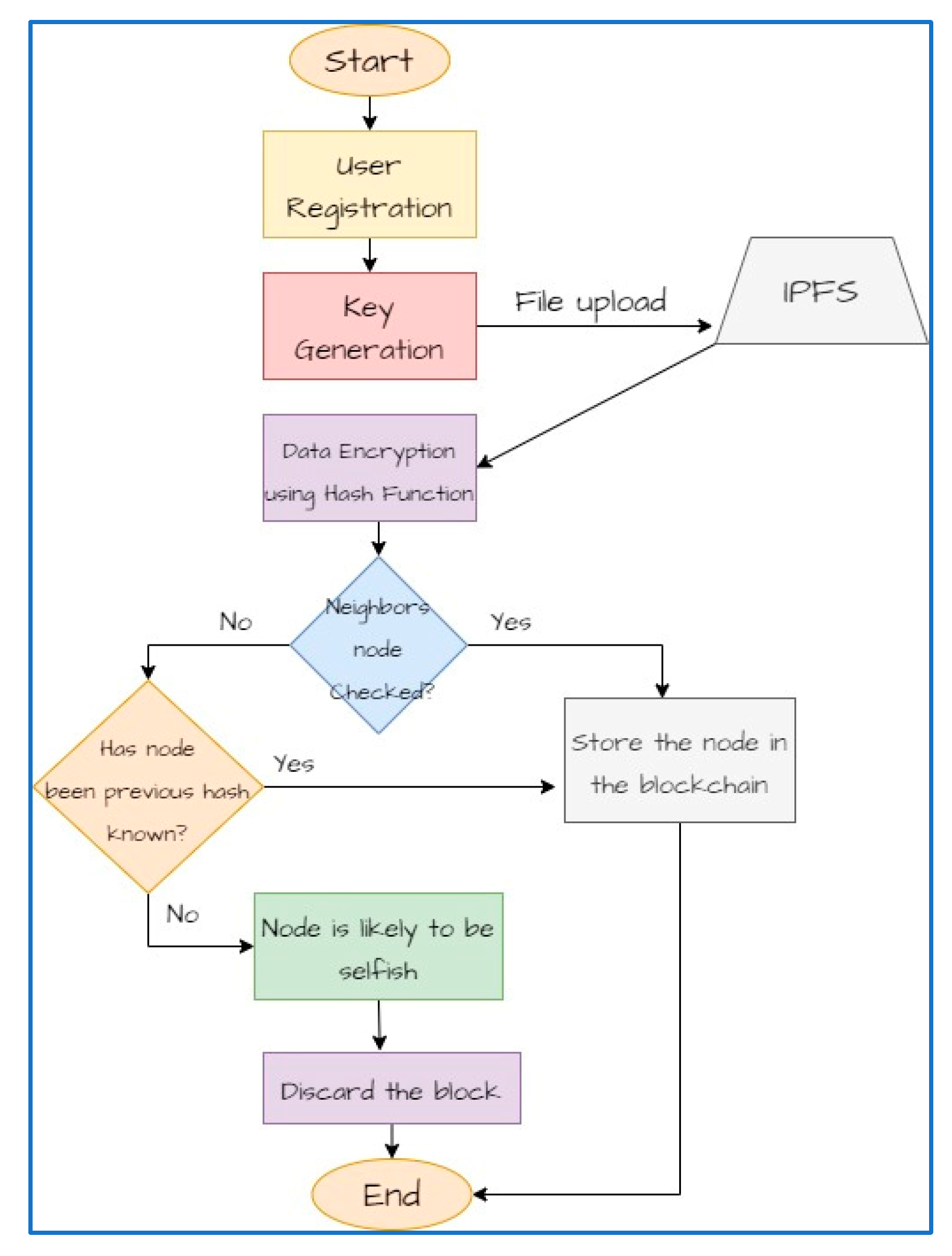
- Step 1.
- Start
- Step 2.
- Prompt the user to provide a unique username and password.
- Step 3.
- Verify that the username is not already taken by checking against existing usernames in the database.
- Step 4.
- If the username is taken, display an error message and ask the user to choose a different username.
- Step 5.
- If the username is available, store the username and password securely in the database.
- Step 6.
- Display a success message indicating that the user has been registered.
- Step 1.
- Prompt the user to enter their username and password.
- Step 2.
- Retrieve the stored username and password from the database for the entered username.
- Step 3.
- If the username does not exist in the database, display an error message indicating that the username is not found.
- Step 4.
- If the username exists, login to the system
- Step 1.
- Generate a random sequence of bits or bytes as the symmetric key.
- Step 2.
- Drive the corresponding public key from the private key.
- Step 3.
- Create the key pair object with the private and public keys
- Step 4.
- Store the public key.
- Step 5.
- Encrypt the private key.
- Step 1.
- Prompt the user to select a file for uploading.
- Step 2.
- Read the file.
- Step 3.
- − Create an IPFS node connection
- Step 4.
- Add the file to the IPFS network.
- Step 1.
- Apply the hash function to the data, which will produce a fixed-size hash value.
- Step 2.
- Store or transmit the hash value separately from the original data.
- Step 1.
- Retrieve the list of neighboring nodes from the IPFS node
- Step 2.
- IF the neighboring node list is empty THEN retrieve its hash value
- a.
- IF Found THEN store the result in blockchain
- Step 1.
- Discard the node
- Step 2.
- Stop
Conclusion:
References
- H. HUAWEI, L. JIANRU and Z. BAICHUAN, "When Blockchain Meets Distributed File Systems:," p. 13, 10 March 2020.
- S. Ramachandran, O. K. O, A. Ramasamy, V. R and S. Mukherjee, "A Review on Blockchain-Based Strategies for Management of Electronic Health Records (EHRs)," in Proceedings of the International Conference on Smart Electronics and Communication (ICOSEC 2020), 2020.
- Benisi, N.Z.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. Journal of Network and Computer Applications 2020, 162, 102656. [Google Scholar] [CrossRef]
- Li, D.; Du, R.; Fu, Y.; Au, M.H. Meta-Key: A Secure Data-Sharing Protocol Under Blockchain-Based Decentralized Storage Architecture. IEEE Netw. Lett. 2019, 1, 30–33. [Google Scholar] [CrossRef]
- Blockchain-Based Secure Storage and Access Scheme For Electronic Medical Records in IPFS. Digital Object Identifier 2020, 8, 59389–59401.
- Van-Hoan, H.; Elyes, L.; Ghamri-Doudane, Y. Privacy-Preserving Blockchain-Based Data Sharing Platform for Decentralized Storage Systems. Information Processing & Management 2021, 58, 102627. [Google Scholar]
- Dwivedi, S.K.; Amin, R.; Vollala, S. Blockchain-Based Secured IPFS-Enable Event Storage Technique With Authentication Protocol in VANET. Ieee/caa J. Autom. Sin. 2021, 8, 1913–1922. [Google Scholar] [CrossRef]
- Sharma, P.; Jindal, R.; Borah, M.D. Blockchain-based decentralized architecture for cloud storage system. J. Inf. Secur. Appl. 2021, 62, 102970. [Google Scholar] [CrossRef]
- Li, D.; Han, D.; Zheng, Z.; Weng, T.-H.; Li, H.; Liu, H.; Castiglione, A.; Li, K.-C. MOOCsChain: A blockchain-based secure storage and sharing scheme for MOOCs learning. Comput. Stand. Interfaces 2022, 81. [Google Scholar] [CrossRef]
- Shah, M.; Shaikh, M.H. Decentralized Cloud Storage Using Blockchain. In Proceedings of the 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184), 2020.
- Zhu, Z.; Qi, G.; Zheng, M.; Sun, J.; Chai, Y. Blockchain based consensus checking in decentralized cloud storage. Simul. Model. Pr. Theory 2019, 102, 101987. [Google Scholar] [CrossRef]
- Abdollahi, M. Simultaneous Sensor and Actuator Fault Detection, Isolation and Estimation of Nonlinear Euler-Lagrange Systems Using Sliding Mode Observers. 2018 IEEE Conference on Control Technology and Applications (CCTA). LOCATION OF CONFERENCE, DenmarkDATE OF CONFERENCE; pp. 392–397.
- Ivan, "InterPlanetary File System Explained – What is IPFS?," acadmy, 8 April 2021. [Online]. Available: https://academy.moralis.io/blog/interplanetary-file-system-explained-what-is-ipfs#:~:text=All%20files%20in%20the%20IPFS,to%20256%20KBs%20of%20data.
- Yang, L. The blockchain: State-of-the-art and research challenges. Journal of Industrial Information Integration 2019, 15, 80–90. [Google Scholar]
- Consensus Algorithms: Proof of Work. Bitpanda. Available Online: https://www.bitpanda.com/academy/en/lessons/consensus-algorithms-proof-of-work/.
- Zhang, L.; Liu, X.; Hu, H.; Xu, L.; Wang, *!!! REPLACE !!!*. Secure Data Sharing and Searching for Industrial IoT Networks Based on Consortium Blockchain. Internet of Things 2020, 7, 11285–11297. [Google Scholar]
- Chen, G.; Huang, J. A Scalable Blockchain-Based Storage System for IoT Data. Internet of Things Journal 2019, 6, 6611–6621. [Google Scholar]
- Z. H. S., Z.; Kardan, Y. M. H. A Survey on Secure Storage Systems in Blockchain. J. Information Security and Applications 2019, 59–71. [Google Scholar]
- Dorri Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Securing the Internet of Things with Blockchain: Theoretical and Methodological Approaches. IEEE Communications Magazine 2019, 9, 68–94. [Google Scholar]
- Bano, Z. S., Arshad; Hassan, S. Blockchain-based security and privacy solutions: A survey. Network and Computer Applications 2020, 10, 2589. [Google Scholar]
- Basu, P. S.; Rawat D., B.; Jeschke, S. A Framework for Identifying and Mitigating Weaknesses in Blockchain Encryption. IEEE Transactions on Industrial Informatics 2021, 6, 4083–4093. [Google Scholar]
- Sharma, P.; Jindal, R.; Borah, M. D. Blockchain Technology for Cloud Storage: A Systematic Literature Review. ACM Comput 2020, 4, 32. [Google Scholar] [CrossRef]
- Shafiq, M., Ashraf; Humayun, M. Robust Cluster-Based Routing Protocol for IoT-Assisted Smart Devices in WSN. Computers Materials Continua 2021, 67. [Google Scholar] [CrossRef]
- Lim, M.; Abdullah, A.; Jhanjhi, N.; Supramaniam, M. Hidden Link Prediction in Criminal Networks Using the Deep Reinforcement Learning Technique. Computers 2019, 8, 8. [Google Scholar] [CrossRef]
- Gouda, W.; Sama, N.U.; Al-Waakid, G.; Humayun, M.; Jhanjhi, N.Z. Detection of Skin Cancer Based on Skin Lesion Images Using Deep Learning. Healthcare 2022, 10, 1183. [Google Scholar] [CrossRef]
- Sennan, S.; Somula, R.; Luhach, A.K.; Deverajan, G.G.; Alnumay, W.; Jhanjhi, N.Z.; Ghosh, U.; Sharma, P. Energy efficient optimal parent selection based routing protocol for Internet of Things using firefly optimization algorithm. Trans. Emerg. Telecommun. Technol. 2021, 32. [Google Scholar] [CrossRef]
- Alsaade, F.; Zaman, N.; Has, M.F.; Abdullah, A. An Improved Software Development Process for Small and Medium Software Development Enterprises Based on Client's Perspective. Trends Appl. Sci. Res. 2014, 9, 254–261. [Google Scholar] [CrossRef]
- Humayun, M.; Jhanjhi, N.; Almufareh, M.F.; Khalil, M.I. Security Threat and Vulnerability Assessment and Measurement in Secure Software Development. Comput. Mater. Contin. 2022, 71, 5039–5059. [Google Scholar] [CrossRef]
- Kaur, R.; Verma, S.; Kavita, *!!! REPLACE !!!*; Jhanjhi, N.; Talib, M.N. A Comprehensive Survey on Load and Resources Management Techniques in the Homogeneous and Heterogeneous Cloud Environment. J. Phys. Conf. Ser. 2021, 1979. [Google Scholar] [CrossRef]
- Alotaibi, A.F. A comprehensive survey on security threats and countermeasures of cloud computing environment. Turkish Journal of Computer and Mathematics Education (TURCOMAT) 2021, 12, 1978–1990. [Google Scholar]
- Bashir, I. R. A. M.; Hamid, B. U. S. H. R. A.; Jhanjhi, N. Z.; Humayun, M. A. M. O. O. N. A. Systematic literature review and empirical study for success factors: client and vendor perspective. J Eng Sci Technol 2020, 15, 2781–2808. [Google Scholar]
- Lim, M.; Jhanjhi, N.; Abdullah, A. Data Fusion-Link Prediction for Evolutionary Network with Deep Reinforcement Learning. Int. J. Adv. Comput. Sci. Appl. 2020, 11. [Google Scholar] [CrossRef]
- Alwakid, G.; Gouda, W.; Humayun, M.; Jhanjhi, N.Z. Diagnosing Melanomas in Dermoscopy Images Using Deep Learning. Diagnostics 2023, 13, 1815. [Google Scholar] [CrossRef] [PubMed]
- Tayyab, M.; Marjani, M.; Jhanjhi, N.; Hashem, I.A.T.; Usmani, R.S.A.; Qamar, F. A comprehensive review on deep learning algorithms: Security and privacy issues. Comput. Secur. 2023, 131. [Google Scholar] [CrossRef]
- Pal, S.; Jhanjhi, N.Z.; Abdulbaqi, A.S.; Akila, D.; Almazroi, A.A.; Alsubaei, F.S. A Hybrid Edge-Cloud System for Networking Service Components Optimization Using the Internet of Things. Electronics 2023, 12, 649. [Google Scholar] [CrossRef]
- Almuayqil, S.N.; Humayun, M.; Jhanjhi, N.Z.; Almufareh, M.F.; Khan, N.A. Enhancing Sentiment Analysis via Random Majority Under-Sampling with Reduced Time Complexity for Classifying Tweet Reviews. Electronics 2022, 11, 3624. [Google Scholar] [CrossRef]


| Year | Main Focus | Major Contribution | Developments in Paper |
|---|---|---|---|
| 2020 | Focusing on blockchain based distributed file system |
[1] reviewed DF systems IPFS and Swarm, the advantages and disadvantages of these systems are listed along. However, the solution of scalability issue and incase of malicious attack is not discussed | Our survey provides a thorough analysis of the literature as well the solution of the gaps identifies in the scheme |
| 2020 | Review different blockchain standards for management of storing data of EHRs. | [2] presented the review of the existing models which stores the medical records on blockchain. However, the drawbacks of each system not specified. | Our Research presents the comprehensive critical analysis of all the systems. |
| 2020 | Survey on various decentralized storage networks | [3] presented distributed file and storage systems. Furthermore, the solution of the issues of the systems are not discussed. Also, the presented survey was not systematic. | Our survey presents a detailed systematic literature review of all the existing methods of blockchain file systems. Moreover, solutions are specified for future research. |
| 2020 | Systematic literature review on blockchain-based cloud storage applications | [4] The pros and cons of existing cloud storage technologies and blockchain-based studies are discussed. However, there was neither a critical analysis of schemes nor a quality assessment of research articles. |
A thorough critical analysis of all present systems is provided in our survey. Research limitations and challenges are also mentioned. |
| Word | Synonym 1 | Synonym 2 | Synonym 3 |
|---|---|---|---|
| Blockchain | Distributed ledger | Digital ledger | Immutable ledger |
| Information Retrieval | Information Retrieval | Information Retrieval | Information Retrieval |
| Storage system of distributed ledger | |||
| Information retrieval system of digital ledger | |||
| Immutable ledger of information retrieval system | |||
| Data storage system of blockchain based technology | |||
| Searching protocol of blockchain based technology | |||
| Blockchain based search engine system | |||
| Acronyms. | Definition |
|---|---|
| PBFT | Practical Byzantine Fault Tolerance |
| SBFT | Synchronous Byzantine Fault Tolerance |
| IPFS | Interplanetary File System |
| MOOCs | Massive Open Online Courses |
| ELRs | Electronic Learning Records |
| MIPSA | Multi-Platform Interoperable Scalable Architecture |
| VANET | Vehicular Ad-Hoc Network |
| Research Papers | Techniques |
|---|---|
| [4] | Meta-Key protocol, Public-Key and Symmetric-Key Encryption |
| [5] | IPFS, Advanced Encryption Standards |
| [6] | Consensus mechanism |
| [7] | IPFS |
| [8] | Advanced Encryption Standards Algorithm |
| [9] | Consensus Protocol |
| [10] | IPFS, Advanced Encryption Standards |
| [11] | Consensus Protocol, practical Byzantine fault tolerance(PBFT) |
| Papers | Consistency | Reliability | Efficiency | Security | Scalability |
|---|---|---|---|---|---|
| [4] | ✔ | ✔ | ✔ | - | - |
| [5] | - | ✔ | - | ✔ | - |
| [6] | - | - | ✔ | ✔ | - |
| [7] | ✔ | ✔ | - | - | - |
| [8] | ✔ | ✔ | - | ✔ | ✔ |
| [9] | - | ✔ | ✔ | ✔ | - |
| [10] | - | - | - | ✔ | - |
| [11] | - | ✔ | ✔ | - | ✔ |
| Papers | Meta-Key Protocol | AES Algorithm | Consensus Protocol | Identity Anonymity | IPFS |
|---|---|---|---|---|---|
| [4] | ✔ | - | - | - | |
| [5] | - | ✔ | - | - | ✔ |
| [6] | - | - | ✔ | ✔ | - |
| [7] | - | - | - | - | ✔ |
| [8] | ✔ | - | - | ✔ | |
| [9] | - | - | ✔ | - | - |
| [10] | - | - | ✔ | - | ✔ |
| [11] | - | - | ✔ | - |
| Ref. | Scheme | Methodology |
|---|---|---|
| [4] | Meta-Key Protocol | It uses a combination of public-key and symmetric-key encryption techniques. where the user's private key protects data decryption keys that are kept in a blockchain as part of the metadata. |
| [5] | Encryption Algorithm with InterPlanetary File System (IPFS) | It uses advanced encryption to encrypt the EMRs. Then the InterPlanetary File System (IPFS) to provide a decentralized storage system for the encrypted EMRs. After that the doctor decrypts the ciphertext with its own secure private key and obtains the original medical records. |
| [6] | Blockchain-based distributed storage technologies | The aim to provide a taxonomy that can help researchers, developers, and practitioners understand the different types of Blockchain-based distributed storage technologies and their characteristics. |
| [7] | InterPlanetary File System (IPFS) | In the blockchain mechanism it presents a protocol for securing event information and vehicle authentication. Then to get the information securely from the interplanetary file system (IPFS). |
| [8] | Advanced Encryption Algorithm and optimization algorithm | For authentication and key generation techniques used AES. Then saves the data in blockchain structure and apply the optimization algorithm to minimize the time complexity. |
| [9] | Consensus Algorithm | This algorithm uses two sub-methods 1) PoW (Proof-of-Work) algorithm is done by finding a hash that matches a target threshold. 2) PoS (Proof-of- Stake) for the purpose of reduce the energy consumption |
| [10] | Advanced Encryption Algorithm and IPFS | This scheme is used to encrypt the file because it needs to be highly secure. It used for protecting sensitive data in financial transactions, securing communications in networks, and encrypting stored data in databases. The IPFS peer to peer file transfer protocol is used to save the users data. |
| [11] | Practical Byzantine Fault Tolerance (PBFT) | This method is the special type of blockchain and it enables quick consensus. The objective of using this is to maintain the data consistency and eliminate the factors which affects the data. |
| Papers | Year | Technique | Shortcoming |
|---|---|---|---|
| [4] | 2019 | Meta-Key protocol | It heavily relies on secret keys to encrypt and decrypt the data, which can be difficult to manage and secure. Lack of scalability [4] |
| [5] | 2020 | IPFS | It led to issues such as governance disputes, network fragmentation, and lack of accountability [13] |
| [6] | 2021 | Key Management & IPFS | It can be difficult to address the scalability and throughput limitations of blockchain. This can limit the usefulness of these technologies for applications that require data sharing and collaboration between multiple parties. [14] |
| [7] | 2021 | IPFS | There is a risk that content may not be available if nodes hosting the content go offline or become unavailable. This could potentially impact the accessibility of important data or information. [7] |
| [8] | 2020 | IPFS, Consensus Mechanism | IPFS result in slow download times and lower performance compared to traditional centralized systems. Consensus protocols require a lot of computational power to function. [8] |
| [9] | 2022 | Proof-of-Stake (PoS) consensus protocol. | PoS requires a high level of participation from validators to maintain network security. If there is low participation, then the network may become vulnerable to attacks and less secure overall. [9] |
| [10] | 2020 | IPFS, Consensus Protocol | Retrieving data from a IPFS cloud storage system can be slower than retrieving data from a centralized system. [10] |
| [11] | 2020 | Proof-of-Work (PoW) Distributed Consensus Protocol | PoW is vulnerable to 51% attacks, where an attacker with more than 50% of the network's computational power can control the network and potentially double-spend transactions. [15] |
| Issues Type | Challenges |
|---|---|
|
Scalability (Key Management) [4] - [6] |
Each user or participant in the blockchain network will typically have their own secret keys for encryption and decryption, and these keys must be stored securely. As the number of users in the network grows, the number of keys that need to be managed also grows. This can lead to issues with key management. |
|
Accessibility (Single Point of Failure) [7] |
It is difficult to maintain the server active because the server's capacity to supply the requested information is essential to the scheme's overall operation. Their system won't function if the computer server mysteriously goes down or crashes. |
|
Encryption Algorithms [8] |
Encryption algorithms are not perfect, and new weaknesses or vulnerabilities may be discovered over time. The algorithms used in blockchain systems. While encryption is used to protect the privacy of users in blockchain systems, there are concerns about the potential for data leaks and the use of personal information for targeted advertising and other purposes. |
|
Consensus Protocol [9] - [10] |
Consensus mechanisms require decision-making around protocol upgrades and changes, which can be challenging in decentralized systems. In addition, retrieving data from centralized system can be slower. It effects the system efficiency. |
|
Proof-of-Work (PoW) Distributed Consensus Protocol [11] |
The system uses this type of consensus protocols can be vulnerable to attacks. Moreover, Proof-of-Work (PoW), require significant amounts of energy to validate transactions and add blocks to the blockchain. This energy consumption can be environmentally unsustainable and result in high costs for participants. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





