1. Introduction
DLT employs a decentralized and distributed platform which ensures the safe sharing and utilization of data by allowing appropriate access rights, and transparent, secure, and reliable transaction processes not depending on a third party such as a government agency, reducing costs while expanding applications in digital assets, public facility, architecture, and real estate management. DLT, which is also represented as blockchain technology, supports real-time autonomous cooperation in IoT based on smart contracts. DLT provides a means to ensure security in digital networking and inter-object telecommunications (IoT). As financial processes based on IoT applications combined with mobile communications technology develop, “Fintech” becomes increasingly sophisticated, demanding more secure and reliability technologies such as DLT, which provides strong protection against system hacking and abuse (Queiroz and Wamba, 2019). Other approaches have attempted to improve storage through smart-contract transmission and execution strategies in DLT (Spataru et al., 2021).
Owing to its growing importance, it is becoming increasingly necessary to investigate factors that affect the acceptance of DLT, and a number of such applications have been implemented in various areas related to business processes, such as supply chain processes (Chang et al., 2019; Chen et al., 2020; Hong and Hales, 2021; Kshetri 2018; Queiroz and Wamba, 2019; Wamba and Queiroz, 2020), personnel management (Chen et al., 2019), and healthcare (Balasubramanian et al., 2021). There is also a growing need to use Blockchain technology in finance due to its secure transaction processing mechanism (Queiroz and Wamba, 2019).
This study is motivated for the following reasons. First, it is necessary to investigate the determinants of DLT acceptance based on a unified theory of acceptance and the use of technology. Previous studies have posited challenges and opportunities regarding the usage process of DLT platforms (Berdik et al., 2021; Chen et al., 2020; Dabbagh et al., 2021). For instance, the influence of technological, organizational and environmental factors with regard to DLT adoption has been investigated based on an innovation theory perspective (Clohessy and Acton, 2019; Drummer and Neumann, 2020)). In order to offer practical implications for businesses and policymakers, it is necessary to provide an empirical analysis that compares employees of both public and private sectors.
Second, there is a lack of empirical studies across industries that use DLT, such as the public, financial, medial, and logistics sectors. Given its early stage of diffusion, empirical studies targeting various industries’ platforms or services based on DLT are rare. Recent DLT studies focus on specific applications and not on a broad spectrum of areas, including the public and private sectors and associations related to DLT, due to the lack of a workforce to develop these platforms and services in the early stages of the maturity of this technology. Our study intends to bridge this gap by encompassing the public, financial, medial, and logistics sectors in the sample of DLT-adopting industries.
2. Literature Review
2.1. Distributed Ledger Technology
DLT is based on consensus algorithms such as the practical Byzantine fault tolerance (BFT), proof of work (PoW), proof of stake (PoS) algorithms and is developed as an algorithm to coordinate distributed ledgers owned by all network participants as well as smart contracts among network participants to prevent changes not agreed upon and/or alterations of contracts. DLT appears in the name of Bitcoin in the encryption technology community Gmane (Schwab, 2018). Nakamoto (2008) suggests three principles of DLT. First, DLT provides a solution for double payments in P2P (peer-to-peer) networks without third-party intervention. Second, DLT replaces a central trustful authority with a cryptography proof system. Third, DLT provides a means by which to trust a network without the intervention of a central trustful authority.
DLT is described as distributed ledger-network-based technology with self-executable programs through no existing server, where participants share cyber-transaction information pertaining to validation, storage, and management issues after recording each transaction in the distributed ledger across online P2P networks (Queiroz and Wamba, 2019); included is a backend database that provides open access to the distributed ledger, with P2P network transfers of individual transactions, valuables, and assets, as well as the methods to replace a traditional trust certification agency by providing transaction certification and validation using verifiable specially designed digital information with no risk of a double payment (Kshetri, 2018). DLT stores data in blocks eternally without the risk of data deletion, with the linking, updating, and storing pf blocks. It provides a distributed computing technology that enables the transfer of valuable assets by individuals and groups with reliability, stability, efficiency, security as well as economic efficiency due to the use of a distributed computing network without a central control server and due to lower maintenance costs and transparency to ensure the prevention of unauthorized data alterations. DLT is in its early stages in terms of technology maturity (Mckinsey, 2019) and was included as a top-ten promising future technologies in 2017, 2018, and 2019. Thus, the acceptance of DLT is expanding across public and private, and financial organizations. DLT is also considered as a core technology in the fourth industrial revolution, combining and integrating artificial intelligence, the IoT, and cloud computing. This study defines blockchain technology as a non-server-based and distributed infrastructure to ensure transparency, reliability, security and integrity while also providing strong prevention against hacking and deliberate data alterations.
The functions of DLT can be described as follows. First, when transaction information is initially recorded, it is stored through blocks distributed among participants, and the blocks are updated after new transactions occur and are transferred in an encrypted form. A newly created block has a header hash computed from existing stored information, pointing to an existing block. After new blocks are validated using existing blocks, they are linked to existing blocks. Transaction information such as that pertaining to a funds transfer from A to B is disclosed to every network participant, and in order to change transaction information deliberately, it is necessary to hack the computers of all participants. If users with malicious intent intend to create blocks, the creation of such blocks is prevented. Participant validation is conducted through codes embedded in the running DLT smart contracts.
It is possible to compensate participants based on economic activities and not indirect costs or broadcasting fees, and by using a distributed ledger, DLT ensures transparency by providing auditability for all DLT processes (Kshetri, 2018; Schwab, 2018; Zou et al., 2018) as well as traceability and accountability for the monitoring of the overall logistics process, preventing fraudulent activities and the appearance of fake products (Batara et al., 2017; Lu & Xu, 2017; Queiroz & Wamba, 2019). Further, a consensus among network participants increases cost reductions and increases operational efficiency among supply chain processes (Aste et al., 2017).
Types of DLT include public, private, and consortium DLT depending on the rights and role of the network participants, and permission and non-permission DLT according to the necessity of permission for network participation. Non-permission DLT allows any form of participation in managing the distributed ledger, and transaction details are open and distributed. Coordinating algorithms for creating blocks are based on PoW and are slowly expected to be replaced with the PoS approach.
In terms of usage types, DLT includes those intended for transfers of value, i.e., cryptocurrencies such as Bitcoin, Litecoin, Dash, ZCash, and Monero for payments. Others include platform-based forms implemented in smart contracts, such as Ethereum, NEO, and Qtum. The number of decentralized applications (DApp) using Ethereum amounted to 1000 in 2015 and 2000 in 2019, with more based on PoS than PoW.
Non-permission DLT has several technical limitations, which include scaling issues with expanding users, economic inefficiencies such as slow processing speeds, and questionable information security for open information. In order to increase the processing efficiency, block sizes are increasing, and lightening networks, with their high processing speeds and low fees, are crucial to run distributed applications efficiently. The block-creation time has been reduced and the coordinating procedures have been changed.
PoW increases energy usage and related expenses by creating competition among network participants in order to form the longest DLT. PoS creates blocks using votes based on cryptocurrency stakes, not requiring much processing or increasing the application processing speed, with lower expenses as well. Thus, in terms of efficiency, PoS is preferred over PoW. Delegated proof of stake (DPoS) (e.g., EOS, ICON) is another consensus algorithm that allows consensus rights to a few chosen participants.
Several technologies have been developed to enhance security and privacy in the non-permission type of DLT. Using the concept of zero knowledge proof, all transaction details are open to all network participants. Zero knowledge proof, developed by Zcash in 2016, allows no disclosure of any information other than whether it is true or false for any statement to ensure secure processes.
Permission DLT includes private and consortium DLT types. Private DLT allows one entity to control all blocks with established rights, and entities who have consensus or individuals allowed by the entities can participate in the networks. Only authorized individuals can create transactions and blocks. Permission DLT was developed in order to solve the issues of scaling (low performance) or security (privacy) of non-permission DLT and for better network control.
Consortium DLT is the mixed type of public and private DLT. N entities manage one node and transactions are possible only through a consensus among entities. Only organizations participating in a consortium which are in a strong trustful relationship have rights regarding transactions and blocks. For example, financial organizations such as banks and LGCNS form a R3CEV consortium. Samsung SDS, Coinplug, the Korea Stock Exchange, SK Telecom, Bloco, and The Roof participate in Hyperledger or EEA. It is faster to create transaction and blocks and easier to gain a consensus for system updates. DLT platforms have been launched by dozens of blockchain consortiums, such as R3CEV, the Hyperledger Project, and the Enterprise Ethereum Alliance, which intend to improve DLT and its standardization.
Table 1.
Types of DLT.
| Type |
Non-permission |
Permission |
| Class |
Pubic DLT |
Private DLT |
Consortium DLT |
| Concept |
Anybody can participate in DLT network and consensus. |
Permission required to participate in DLT network. |
Permission required to participate in DLT network. |
| Features |
It is hard to change the determined rules. |
It is easy to change rules according to decision making of central agency. |
It is possible to change rules through agreements of consortium participants. |
| Operator |
All transaction participants
(decentralized) |
Central agency (special operator) |
Organizations participating in consortium |
| Read rights |
All participants in DLT |
Users who are chosen to be allowed to have read rights including operators |
Organizations who are chosen to be allowed to have read rights |
| Rights of creating transaction |
All participants in DLT |
Users who are chosen to be allowed to have creating transaction rights |
Organizations who are chosen to be allowed to have creating transaction rights |
| Rights of creating blocks |
All participants in DLT |
DLT operator |
Organizations participating in consortium |
| Consensus algorithm |
PoW, PoS |
PoS, BFT, PoA |
PoS |
| Transaction speed |
Low |
High (network expansion is very easy) |
High (network expansion is very easy) |
| Example |
Bitcoin |
Linq (Nasdaq unlisted stock exchange platform |
Corda( Distributed ledger record system for financial institution) |
The international market for DLT will grow by more than 71.3% by 2022nsey, 2019), and industries adopting DLT are expanding and include those other than financial applications, with retailing, logistics, medicine, and public sectors now present, using an initial coin offering as a means to create funds. Amazon, MS, and IBM intend to apply DLT in various industries and compete fiercely to become the leader in the BaaS market (DLT as a service) which is a distributed network service for creating a DLT service development environment.
Korean DLT is directed toward improving Ethereum in terms of data processing, capacity, and smart contracts. Samsung SDS, LG CNS, Naver, and Kakao attempt to control the DLT market by developing separate main DLT networks. DLT has been applied to public security areas, such as digital assets and public facilities management, construction, real estate management, auto leases, and ownership certification. Cryptocurrency is the representative application of DLT for asset management and payments, and new forms of cryptocurrency are appearing. Further, in order to ensure the efficiency and security of IoT, DLT is being utilized in the areas of production, retailing, and shared economies as digital networks and IoT are expanding and requiring safe transactions and intellectual asset protection. DLT can fundamentally prevent double payments and facilitate payments of small amounts, representing a highly appropriate payment method for financial applications.
2.2. Unified Theory of Acceptance and Use of Technology
The unified theory of the acceptance and use of technology (UTAUT) refers to combining a technology acceptance model (TAM) with behavior intention. It has been utilized to explain factors affecting technology acceptance (Queiroz and Wamba, 2019). UTAUT posits that attitudes toward technology are the most important factor affecting usage behavior. UTAUT has added factors to overcome the lack of an explanation of individual-related or external factors (Venkatesh et al., 2012; Wang et al., 2018), applying performance expectations, efforts expectations, social impacts and facilitating conditions, and adjusting them to fit into general consumption environments. Price values, hedonic motivation, and habits have been added to the initial UTAUT, greatly improving its explanatory power of usage intention and behavior (Venkatesh et al., 2012). UTAUT adjusts and integrates theories of planned behavior, theories of rational behavior, TAM, social cognitive theories, innovation diffusion theories, and motivation theories.
Attitudes toward technology are a crucial factor directly affecting usage intentions of technology. UTAUT excludes attitudes toward technology due to their inconsistent mediating effects on technology usage. UTAUT uses gender, age, experiences, and voluntariness of use as moderators between four independent variables (performance expectancy, effort expectancy, social impact, and facilitating conditions) and behavioral intention. UTAUT is expected to improve explanatory power capabilities, especially for newly developed technologies, by overcoming the limitations of explaining technology acceptance compared to previous theories and models related to social psychology and technology acceptance, from 17~53% to 70% (Queiroz and Wamba, 2019). Recently, UTAUT was applied to explain the acceptance of technologies such as networking webs (Chua et al., 2018), cloud service utilization (Dwivedi et. al., 2017; Wang et al., 2018), DLT (Batara et al., 2017; Ksetri, 2018; Lu and Xu, 2017), mobile financial applications (Tai and Ku, 2013; Yu, 2012), and government systems used by government employees (Batara et al., 2017).
In an extended UTAUT, hedonic motivation, price value, and habits were added as independent factors of behavioral intention to use technology to consider individual desires and expectations as well as individual perceptions, with existing independent variables redefined in general consumer environments in order to overcome the limitations of explaining non-technology-related and individual consumer factors. The extended UTAUT shows improved explanatory power compared to the original UTAUT, from 56% to 74% for behavioral intention and from 40% to 52% for usage behavior (Queiroz & Wamba, 2019). Further, the explanatory power is improved of extended UTAUT by linking facilitating conditions with both behavioral intention and usage behavior (Venkatesh et al., 2012). The extended UTAUT has been applied to public or security applications (Batara et al., 2017; Kshetri, 2018; Li et al., 2019; Veuger,2018; Zou et al., 2018) and logistics (Aste et al., 2017; Viryasitavat et al., 2018).
DLT is posited to be safer and transparent, as well as verifiable for the entire process. It is also more efficient than any other form of transaction (Batara et al., 2017; Kshetri, 2018; Lu & Xu., 2017; Zou et al., 2018). DLT improves collaborative efforts among network participants while also reducing the cost and improving the efficiency along supply chains (Aste et al., 2017). It can support the tracking of supply chain flows, thus increasing reliability (Chang et al., 2019). The tracking mechanism in DLT can help find fake products and prevent fraudulent activities (Batara et al., 2017; Lu and Xu, 2017; Queiroz and Wamba, 2019).
3. Research Model
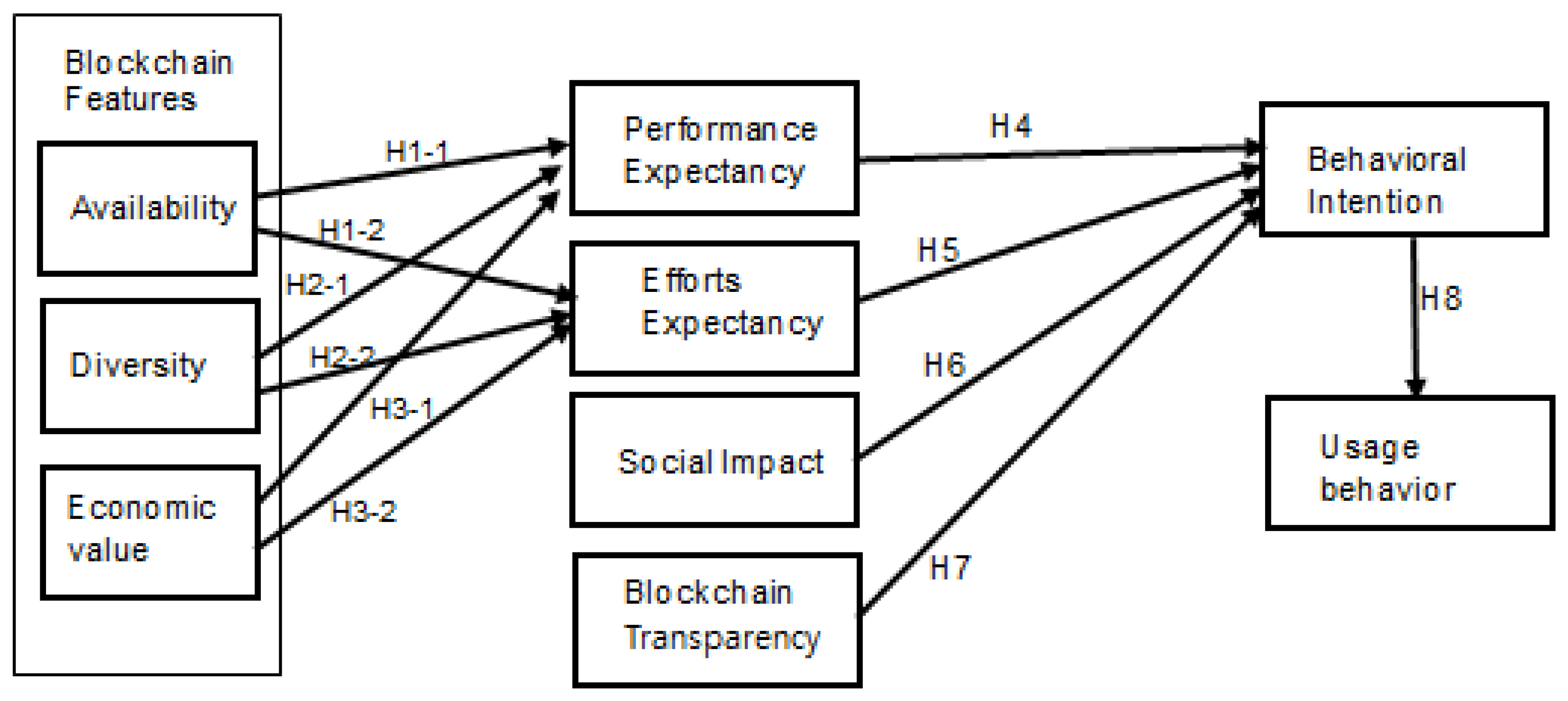
The research model is suggested based on TAM, UTAUT, and the extended UTAUT in order to suggest factors affecting behavioral intention and usage behavior in the context of DLT. This study adopts security, availability, trust, diversity, and economic efficiency as external factors representing the characteristics of DLT. Transparency and trust are added to the original set of endogenous variables, i.e., performance expectancy, effort expectation, social impact, and facilitating conditions, based on previous studies of DLT (e.g., Queiroz and Wamba (2019)).
Figure 1.
Research model.
Figure 1.
Research model.
We exclude moderators such as gender, age, and experience because DLT is in the early stage of diffusion and there are too few samples to investigate differences in the effects of independent variables on dependent variables.
The security of DLT can be described as focusing on the protection of the platform and service implemented by DLT from hackers’ attacks or from data manipulation by ensuring authorized access control to systems and data. Previous studies have suggested that DLT security affects performance and effort expectancy (Queiroz and Wamba, 2019; Venkatesh et al., 2012). Thus, the security of DLT can be suggested as a factor that positively influences performance and effort expectancy.
H1-1: The security of DLT positively influences performance expectancy.
H1-2: The security of DLT positively influences effort expectancy.
The availability of DLT is described as when the use of DLT is always possible without malfunctions across all network nodes. Availability is especially important as network participants share blocks, and a malfunction of any network node can have a detrimental influence on other nodes. Previous studies have indicated that the availability of DLT has effects on performance and effort expectancy (Queiroz and Wamba, 2019; Venkatesh et al., 2012). Thus, the security of DLT can be considered to be a factor that positively affects performance and effort expectancy.
H1-1: The availability of DLT positively influences performance expectancy.
H1-2: The availability of DLT positively influences effort expectancy.
The diversity of DLT can be described referring to the extent to which DLT can be utilized in diverse area to ensure its usefulness. Previous studies have posited that the diversity of DLT has an influence on performance and effort expectancy (Queiroz and Wamba, 2019; Venkatesh et al., 2012). Thus, the diversity of DLT can be hypothesized as a factor that positively affects performance and effort expectancy.
H2-1: The diversity of DLT positively influences performance expectancy.
H2-2: The diversity of DLT positively influences effort expectancy.
The economic value of DLT is described as the extent of added utility and benefits compensating for the costs paid by consumers. Economic value is considered as price value and added utility using functions for smart contracts and tokens for currency. Previous studies have shown that the economic value of DLT influences performance and effort expectancy (Queiroz and Wamba, 2019; Venkatesh et al., 2012). Thus, the economic value of DLT can be considered as a factor that positively affects performance and effort expectancy.
H3-1: The economic value of DLT positively influences performance expectancy.
H3-2: The economic value of DLT positively influences effort expectancy.
Performance expectancy represents the extent of the belief that the use of new technology improves task performance (Venkatesh et al., 2003). A smart-contract-based task, a characteristic of a distributed ledger of DLT, can minimize the complexity and uncertainty of related processes. Previous studies have shown that the economic value of DLT has an influence on performance and effort expectancy (Queiroz and Wamba, 2019; Venkatesh et al., 2012). Thus, the economic value of DLT can be considered as a factor that positively affects performance and effort expectancy.
H4: The performance expectancy of DLT positively influences behavioral intention to use.
Effort expectancy represents the extent that a new technology can be easily used by anyone (Venkatesh et al., 2003). Difficulties in using new technology include education and costs related to adjustments and can create a barrier to the acceptance of new technology despite its contributing role to the accomplishment of individual objectives (Venkatesh et al., 2003). Previous studies have posited that the effort expectancy of DLT influences behavioral intention to use (Queiroz and Wamba, 2019; Venkatesh et al., 2012). Thus, the effort expectancy of DLT can be considered as a factor that positively affects behavioral intention to use.
H5: The effort expectancy of DLT positively influences behavioral intention to use.
Social impact is described as the recognition of important related people or organizations by which a new technology should be used (Venkatesh et al., 2003). Social impact is the influence from the opinions and behaviors of peers, colleagues, or friends (Queiroz and Wamba, 2019). A person or organization should consider the opinions of peers and related organizations when deciding whether to use a new technology. Previous studies have asserted that the social impact of DLT produces an influence on behavioral intention to use (Queiroz and Wamba, 2019; Venkatesh et al., 2012). Thus, the social impact of DLT can be considered as a factor that positively affects behavioral intention to use.
H6: The social impact of DLT positively influences behavioral intention to use.
The transparency of information technology represents how information is not distorted or altered while being delivered to stakeholders to demonstrate publicity, communicativeness, and verifiability. Our study describes the transparency of technology as a type of communication among organizational members and related to the task visibility of related networks. Queiroz and Wamba (2019) asserted that the transparency of logistics represents the verifiability of the locations and statuses of logistic flows. Previous studies have shown that the transparency of DLT related to logistics exerts an influence on the transparency and accountability of logistics (Batara et al., 2017; Kshetri, 2018; Lu & Xu, 2017). The transparency of DLT increases cooperation among network members in a supply chain and results in large changes in large social groups in an industry (Aste et al., 2017). Previous studies have found that the transparency of DLT has an effect on behavioral intention to use (Queiroz and Wamba, 2019). Thus, the transparency of DLT can be considered as a factor that positively affects behavioral intention to use.
H7: The transparency of DLT positively influences behavioral intention to use.
Behavioral intention to use represents the tendency of a new technology to be used by consumers (Venkatash et al., 2003); it is considered to be a crucial factor in the determination of the usage behavior related to a technology, especially when applying UTAUT.
Previous studies have indicated that behavioral intention to use DLT has an effect on usage behavior (Queiroz and Wamba, 2019). Thus, the behavioral intention to use DLT can be considered as a factor that positively affects usage behavior.
H8: The behavioral intention to use DLT positively influences usage behavior.
4. Methods
The operational definitions and the research variables in this study are given in
Table 2 and
Table 3, respectively. Each item is measured using a five-point Likert-type scale.
The target respondents for our sample are individuals who work at public organizations, such as central or local governments in administrative departments, at public research institutes related to DLT development, and for Korean DLT associations and educational institution related to DLT. Further, the target respondents include private developers of DLT-based systems in the financial, medical/health, logistics/retail, and IT sectors (including LG CNS and Samsung SDS). The respondents in these organizations are developing DLT-based services, platforms, and/or are establishing policies or working at applying a DLT-based service or platform to their tasks. Participation by survey is persuaded through phone calls with staff members who are knowledgeable about DLT. Respondents participated in online and offline surveys from February to April of 2020. The online survey is based on social network sites, Messenger, Google-based survey, and email. The final sample includes 362 responses.
The industries of the respondents are largely public (23.2%) and IT (33.4%), as our study focuses on targeting central or local government administrative departments, and two major IT service companies and companies are DLT associations which have more invested in the potential of DLT than other smaller private companies. The majority of the respondents (62.4%) have participated in DLT for less than a year, a finding related to the initial stage of the diffusion of DLT.
Table 4.
Demographic Characteristics of the Respondents (N=362).
Table 4.
Demographic Characteristics of the Respondents (N=362).
| Class |
Frequency |
Percentage |
| Gender |
Male |
297 |
|
82.0 |
|
| Female |
65 |
|
18.0 |
|
| Age |
Less than 20 |
1 |
|
0.3 |
|
| 20s |
75 |
|
20.7 |
|
| 30s |
81 |
|
22.4 |
|
| 40s |
107 |
|
29.6 |
|
| More than 50 |
98 |
|
27.1 |
|
| Education (final degree) |
High school graduates |
12 |
|
3.3 |
|
| Community college graduates |
7 |
|
1.9 |
|
| Bachelor degree (or students) |
214 |
|
59.1 |
|
| Higher than master degree |
129 |
|
35.6 |
|
| Industry |
Public |
84 |
|
23.2 |
|
| Financial |
27 |
|
7.5 |
|
Medical or health
IT |
18 |
|
5.0 |
|
| 121 |
|
33.4 |
|
| Logistics or retail |
8 |
|
2.2 |
|
| Service |
29 |
|
8.0 |
|
| Manufacturing |
17 |
|
4.7 |
|
| Others |
58 |
|
16.0 |
|
| Position |
Employee |
71 |
|
19.6 |
|
| Assistant manager |
25 |
|
6.9 |
|
| Manager |
56 |
|
15.5 |
|
| Assistant executive manager |
39 |
|
10.8 |
|
| Executive manager |
76 |
|
21.0 |
|
| Senior executive |
74 |
|
20.4 |
|
| CEO |
21 |
|
5.8 |
|
| DLT usage period |
Less than one year |
226 |
|
62.4 |
|
| One – two years |
85 |
|
23.5 |
|
| Two – three years |
21 |
|
5.8 |
|
| Three – four years |
9 |
|
2.5 |
|
| Four– five years |
6 |
|
1.7 |
|
| More than five years |
15 |
|
4.1 |
|
5. Results
Our study tests the validity and reliability of the measures above by examining whether the items measuring each construct converge to measure the same construct or are differentiated from the items measuring other constructs (
Table 5 and
Table 6).
An exploratory factor analysis was conducted in order to exclude items with low factor loading values (0.5) or those that do not converge with the intended constructs.
The composite construct reliability and average variance extracted for all variables are greater than 0.7 and 0.5, respectively. The factor loading values for all items are greater than 0.5, demonstrating that reliability and convergent validity are established for all variables.
In
Table 7, the values in diagonals represent the average variance extracted, and they are greater than the squared values of the correlations among the variables. Further, the range within the correlation plus or minus two times the standard deviation of the correlation does not include one, which verifies that the correlation is significantly different from one and indicates that discriminant validity of the variables is established.
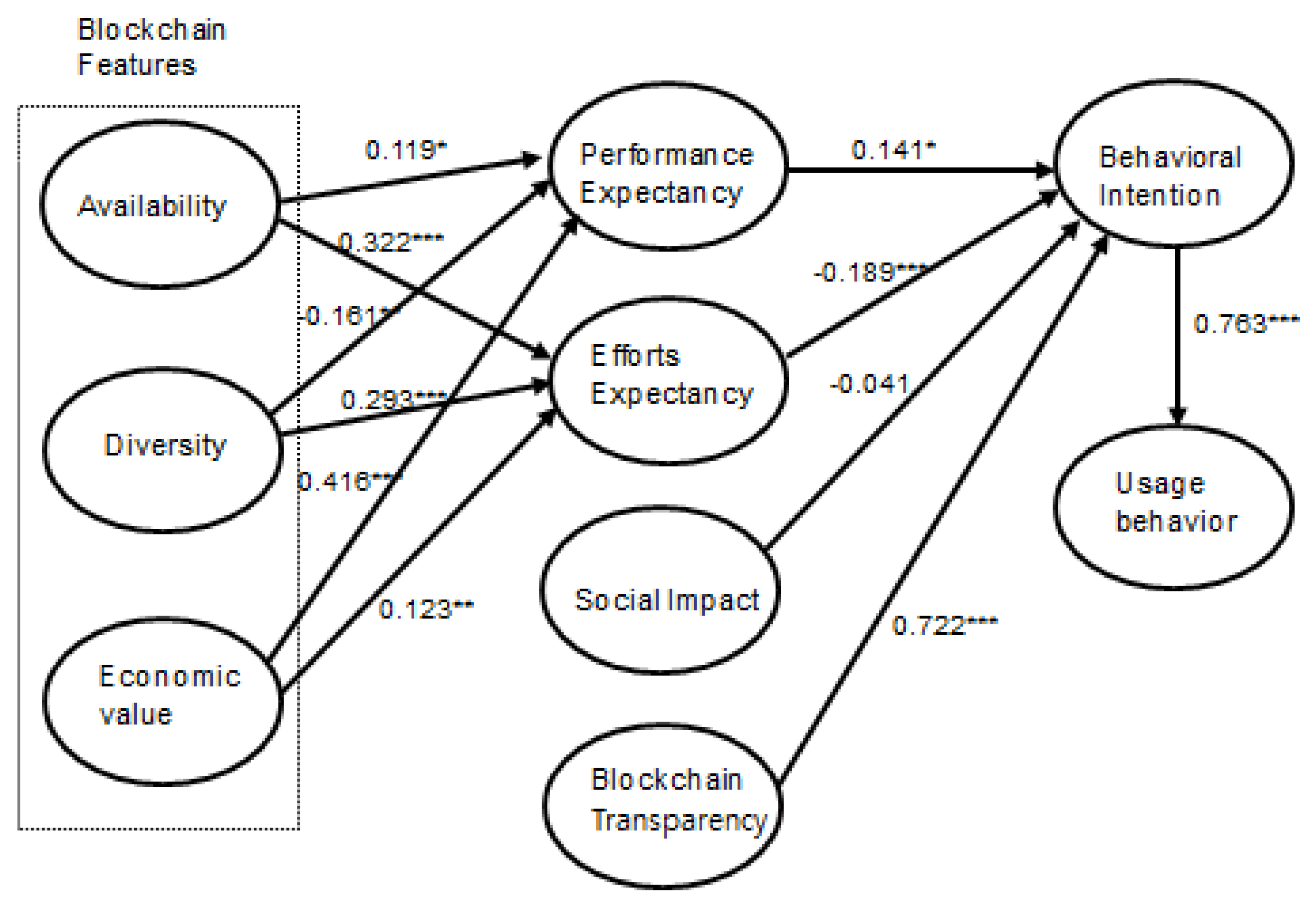
Figure 2 and
Table 8 show the structural model and hypotheses testing results of this study. Availability significantly affects performance and effort expectancy, consistent with the interview feedback from the survey participants and indicating that the more available the technology is, the greater the perceived performance and easiness of the technology is. The significant negative effect of diversity on performance expectancy indicates that diverse applications are not by themselves related to performance expectation; rather, a few focused applications can be associated with an expected performance improvement.
Because DLT is associated with diverse applications and services, the significant effects of availability and diversity on effort expectancy indicate that DLT can easily be utilized and applied to a range of other applications and services in the public and private sectors. With a greater extent of diversity in the applications of DLT, more users perceive the technology as easy to learn and understand.
The significant effect of economic value on performance and effort expectancy shows that one of the most important conditions for perceived performance impact and ease of its application is how much DLT can bring economic benefits to its adopters. The economic benefits of DLT are perceived to be directly related to the return on investment in IT and organizational competitiveness. The effects of DLT on effort expectancy show that if economic benefits are provided, the technology can be learned and can become familiar despite its complexity.
The effect of performance expectancy on behavioral intention is significant, a finding consistent with Queiroz and Wamba (2019), who found that in India and the US, the expectation of a performance improvement after adopting DLT is crucial to create a behavioral intention to use DLT. As long as DLT is expected to lead to better organizational performance, it will likely be adopted to enhance organizational innovation and growth.
The significant negative effect of effort expectancy on behavioral intention indicates that DLT is perceived as a complicated technology, which is not a hurdle to its adoption by itself. On the contrary, participants perceived DLT as a necessary system despite the complexity of facilitating the adoption of DLT. The interview feedback from the survey participants indicates that manpower with expertise in DLT is still weak, which contributes to the negative effect of effort expectancy on behavioral intention to use.
The effect of a social impact on behavioral intention is insignificant, which is consistent with Queiroz and Wamba (2019), who found that in US, the social influence related to the adoption of DLT does not importantly affect behavioral intention to use DLT. The interview feedback confirms that businesses in the public and private sectors adopt Blockchain technologies to enhance their competiveness and performance, but not from social pressure or any influence to adopt the technology.
The significant effect of DLT transparency on behavioral intention indicates that clear monitoring across production or retail business processes as enabled by DLT to ensure visibility of the processes is crucial to create a behavioral intention to use DLT.
The effect of behavioral intention on usage behavior is significant, which is consistent with Queiroz and Wamba (2019), indicating that having an intention to use DLT is a precondition to explain its usage behavior.
6. Conclusions and Implications
This study attempts to examine the factors affecting the usage intention of DLT based on the perspective of the unified theory of the acceptance and use of technology. Those in the study sample who provided the responses are adopters of DLT in the public and private sectors. Economic value is positively related to performance expectancy, while availability, diversity, and economic value affect effort expectancy. Performance expectancy and transparency have a positive influence on the intention to use DLT, which exerts a positive effect on usage behavior.
6.1. Implications for Researchers
This study provides implications for researchers in that it attempts to investigate the factors affecting the usage intention of DLT based on the perspective of the extended unified theory of the acceptance and use of technology as it pertains to DLT features. The participants here were adopters of DLT in various industries in the public and private sectors.
Due to the availability and diverse services of DLT, the technology is easy to learn and the leaning time is not very long. Because operational and maintenance costs are relatively lower than those in other IT areas, the expectations of development opportunities and performance improvements are increased. DLT enables visibility of processes, transparent information, collaboration among participants, and network accountability, all of which increase behavioral intention to use. Ease of use and the short learning time facilitate user participation in DLT, resulting in increased levels of user intention to use.
This study has both limitations and future research opportunities. First, the sample of the study can be expanded as the number of adopters of DLT increases such that diverse industries can be encompassed, such as those related to public, financial, retail, health, and logistics areas, which will enable comparison studies among different industries. Second, our study examines the perspectives of employees of organizations which are adopting DLT; the perspectives and responses of general customers who adopt DLT can also be investigated in the future studies.
6.2. Implications for Practitioners
The study results also have implications for researchers. Factors which are perceived by business practitioners as affecting performance expectancy levels for companies in the public and private sectors are availability, which ensures continuous operation, and economic value, which represents cost reductions and competitiveness compared to those factors in other IT areas.
The expectation of a greater organizational performance improvement through the adoption of DLT compared to other types of IT and the capability to monitor data processing and business processes at any time to enhance transparent progress all affect the behavioral intention to use.
A feedback interview with business employees found that the current education system for experts in DLT is not sufficiently meeting industry demand and that there are too few experts with knowledge and expertise. Moreover, employees consider DLT as difficult and complicated, but they continue to attempt to adopt it given its performance expectations and the transparent control of processes it offers. DLT education to produce more experts is necessary to break down the entry barrier to develop DLT.
The lack of a positive social impact indicates that a social consensus has not yet formed to enhance the diffusion of DLT. Moreover, this gap between state-of-the-art technology and social recognition can even negatively influence the adoption of the technology. Social recognition toward DLT must be improved, as some in Korean society still consider it as a means to speculative on business or investments. Thus, to continue the start-up businesses initiated by major IT service companies, associations, and local governments, policies and infrastructure regarding DLT, such as standardization of its core technologies, should be established. Our study results provide directions and insights for practitioners of DLT to facilitate its efficient application and diffusion in the organizational infrastructure of public, financial, retail, logistics, and health businesses.
References
- Agarwal, R.; Karahanna, E. Time flies when you’re having fun: Cognitive absorption and beliefs about information technology usage. MIS Quarterly, 2000, 24(4), 665-692. [CrossRef]
- Aste, T.; Tasca, P.; Matteo, T. Blockchain technologies: The foreseeable impact on society and industry. IEEE Computer, 2017, 50(9), 18–28. [CrossRef]
- Ajzen, I.; Fishbein, M. Understanding attitudes and predicting social behavior. Englewood Cliffs, N.J: Prentice-Hall, 1980.
- Ajzen, I. Ajzen, I. The theory of planned behavior. Organizational Behavior and Human Decision Processes, 1991, 50(2), 179-211. [CrossRef]
- Balasubramanian, S.;, Shukla, V.; Sethi, J.S.; Islam, N.; Saloum, R. A readiness assessment framework for blockchain adoption: A healthcare case study. Technological Forecasting & Social Change, 165, 120536. [CrossRef]
- Bandura, A. Self-efficacy: Toward a unifying theory of behavioral change. Psychological Review, 1977, 84(2), 191-215. [CrossRef]
- Batara, E.; Nurmandi, A.; Warsito, T.; Pribadi, U. Batara, E.; Nurmandi, A.; Warsito, T.; Pribadi, U. Are government employees adopting local e-government transformation? Transforming Government, 2017, 11(4), 612–638.
- Berdik, D.; Otoum, S.; Schmidt, N.; Porter, D.; Jararweh, Y. A survey on blockchain for information systems management and security. Information Processing and Management 2021, 58, 102397. [Google Scholar] [CrossRef]
- Chang, S.E.; Chen, Y.C.; Lu, M.F. Supply chain reengineering using blockchain technology: A case of smart contract based tracking process. Technological Forecasting Social Change 2019, 144, 1–11. [Google Scholar] [CrossRef]
- Chen, S.; Liu, X.; Yan, J.; Hu, G.; Shi, Y. Processes, benefits, and challenges for adoption of blockchain technologies in food supply chains: a thematic analysis. Information Systems and e-Business Management 2020. [Google Scholar] [CrossRef]
- Chen, J.; Lv, Z.; Song, H. Design of personnel big data management system based on blockchain. Future Generation Computer Systems 2019, 101, 1122–1129. [Google Scholar] [CrossRef]
- Chua, P.Y.; Rezaei, S.; Gu, M.L.; Oh, Y.; Jambulingam, M. Elucidating social networking apps decisions performance expectancy, effort expectancy and social influence. Nankai Business Review International, 2018, 9(2), 118–142.
- Clohessy, T.; Acton, T. Investigating the influence of organizational factors on blockchain adoption: An innovation theory perspective. Industrial Management & Data Systems, 2019, 119(7), 1457-1491. [CrossRef]
- Crofts, B.; Lam, D.; Kosmatos, J. Solving real world problems with blockchain. PWC 2018. [Google Scholar]
- Dabbagh, M.; Choo, K.-K.R.; Beheshti, A.; Tahir, M.; Safa, N.S. A survey of empirical performance evaluation of permissioned blockchain platforms: Challenges and opportunities. Computers & Security 2021, 100, 102078. [Google Scholar] [CrossRef]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly, 13(3), 1989, 319- 319-340. [CrossRef]
- Drummer, D.; Neumann, D. Is code law? Current legal and technical adoption issues and remedies for blockchain-enabled smart contracts. Journal of Information Technology, 2020, 35(4), 337-360. [CrossRef]
- Dwivedi, Y.K.; Rana, N.P.; Janssen, M.; Lal, B.; Williams, M.D.; Clement, M. An empirical validation of a unified model of electronic government adoption (UMEGA)", Government Information Quarterly, 2017, 34(2), 211–230. [CrossRef]
- Gartner, Top 10 Strategic Technology Trends for 2019, 2019.
- Hong, L.; Hales, D.N. Blockchain performance in supply chain management: application in blockchain integration companies. Industrial Management & Data Systems, 2021. [CrossRef]
- Islam, M.Z.; Low, P.K.C.; Hasan, I. Intention to use advanced mobile phone services(AMPS). MD, 2013, 51(4), 824-838. [CrossRef]
- Kshetri, N. Blockchain’s roles in meeting key supply chain management objectives. International Journal of Information Management 2018, 39, 80–89. [Google Scholar] [CrossRef]
- Li, H.; Tian, H.; Zhang, F.; He, J. Blockchain-based searchable symmetric encryption scheme. Computers & Electrical Engineering 2109, 73, 32–45. [Google Scholar] [CrossRef]
- Luarn, P.; Lin, H.H. Toward an understanding of the behavioral intention to use mobile banking. Computers in Human Behavior, 2005, 21(6), 873-891. [CrossRef]
- Lu, Q.; Xu, X. Adaptable blockchain-based systems: A case study for product traceability. IEEE Software, 2017, 34(6), 21–27. [CrossRef]
- Mckinsey, Our Top Ten Insights of 2019, 2019.
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System, 2008.
- Queiroz, M.M.; Wamba, S.F. Blockchain adoption challenges in supply chain: An empirical investigation of the main drivers in India and the USA. International Journal of Information Management 2019, 46, 70–82. [Google Scholar] [CrossRef]
- Rogers, E.M. Diffusion of Innovations, The Free Press, New York., 5th edition, 2003.
- Schwab, K. The Fourth Industrial Revolution–The Next, Eulyoo Publishing Co. LTd., 2018.
- Spataru, A.L.; Pungila, C.-P.; Radovancovici, M. A high-performance native approach to adaptive blockchain smart-contract transmission and execution. Information Processing and Management, 58, 102561. 0256. [CrossRef]
- Thompson, R.L.; Higgins, C.A.; Howell, J.M. Personal computing: toward a conceptual model of utilization. MIS quarterly, 1991, 15(1), 125-143. [CrossRef]
- Taylor, S.; Todd, P.A. Understanding information technology usage: A test of competing models. Information System Research, 1995, 6(2), 144-176. [CrossRef]
- Venkatesh, V.; Bala, H. TAM3 technology acceptance model 3 and a research agenda on interventions. Decision Sciences, 2008, 39(2), 273–315. [CrossRef]
- Venkatesh, V.; Brown, S.A. A longitudinal investigation of personal computers in homes: Adoption determinants and emerging challenges. MIS Quarterly, 2001, 25(1), 71-102. [CrossRef]
- Venkatesh, V.; Brown, S.A.; Maruping, L.M.; Bala, H. Predicting different conceptualizations of system use: The competing roles of behavioral intention, facilitating conditions, and behavioral expectation. MIS Quarterly, 2008, 32(3), 483-502. [CrossRef]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User acceptance of information technology: Toward a unified view. MIS Quarterly, 2003, 27(3), 425–478. [CrossRef]
- Venkatesh V.; Thong, J.; Xu, X. Consumer acceptance and user of information technology: Extending the unified theory of acceptance and use of technology", MIS Quarterly, 2012, 36(1), 157–178. [CrossRef]
- Viryasitavat, W.; Xu, L.D.; Bi, Z.; Sapsomboon, A. Blockchain-based business process management (BPM) framework for service composition in industry 4.0. Journal of Intelligent Manufacturing 2020, 31, 1737–1748. [Google Scholar] [CrossRef]
- Wamba, S.F.; Queiroz, M.M. Blockchain in the operations and supply chain management: Benefits, challenges and future research opportunities. International Journal of Information Management 2020, 52, 102064. [Google Scholar] [CrossRef]
- Wang, Y.Y.; Wang, Y.S.; Lin, T.C. Developing and validating a technology upgrade model. International Journal of Information Management, 2018, 38(1), 7–26. [CrossRef]
- Yu, Y.; Li, Y.; Than, J.; Liu, J. Blockchain-based solutions to security and privacy issues in the Internet of things, IEEE Wireless Communications, 2019, 25(6). 12-18. [CrossRef]
- Yahamandram, V.; White, L. Exploratory and confirmatory factor analysis of the perceived switching costs modeling the business services sector. Faculty of Commerce Papers, University of Wollongong Australia., 2006.
- Zhang, Y.; Deng, R.H.; Liu, X.; Zheng, D. Blockchain based efficient and robust fair payment for outsourcing services in cloud computing. Information Sciences, 2018, 462. [CrossRef]
- Zou, J.; Ye, B.; Qu, L.; Wang, Y.; Orgun, M.A; Li, L. A proof-of-Trust Consensus Protocol for Enhancing Accountability in Crowdsourcing Services. IEEE Transactions on Services Computing, 2018, 1374(c), 1–14. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).