1. Introduction
In modern days, iCloud data transmission replaces the physical mails to speed up the time spent on exchanging information. Needless to mention, the Internet is a key element in the transmission process. Digital activities involve both virtual world and physical world can be foreseen in the near future. If a hospital technician uploads an x-ray image, a CT-scan photo, or its patient’s information to a data center for a list of specific doctors to download them to discuss various treatments over an online meeting. To protect the privacy of the patient, no one should see the information other than related doctors. Encrypting and decrypting of these digital information are getting more and more important to increase the security. At the same time, there can be diagnostics information to be passed to one or some particular doctors. Data hiding then plays another crucial role in these data transitions [
1].
When a content owner wants to send an image to a data receiver, the owner would like to add a secret message in the image before transmitting it to the receiver. Adding the secret message normally needs to go through a data hider and it may not be desirable for the data hider to see the image content, the owner encrypts the the image before sending the image to hide the message. A receiver holding the encryption key can recover the image and a receiver having the data hiding key can extract the secret information.
There are various data hiding schemes designed to protect data effectively in different application circumstances and demonstrated exceptional results. Data hiding is branched out to reversible data hiding (RDH) [
2] and non-reversible data hiding depending on if the image content can be recovered or not. A wider range of applications adopted RDH schemes because of their reversibility and thus RDH studies became more popular in the recent decades. According to the hiding carriers, the hiding schemes can be catalogued into four different domains: spatial, frequency, compression and encryption. When in the spatial domain, digital cover images are modified directly to embed data. As for the frequency domain, images are transformed by wavelet transform methods before embedding data. Images are first compressed by compression technique prior to embedding information in the compression domain. In the encryption domain, images are encrypted using encryption keys before sending to data hider to hide secret in the encrypted image [
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24,
25,
26]. Reversible data hiding in encrypted images (RDH-EI) combines cryptography and RDH technology to achieve higher levels of protection. In order to better secure information privacy, our scheme focuses on using encrypted images to hide data. Our research goal is to achieve larger embedding capacity without degrading visual quality of recovered images. The core contributions of the scheme are described as below:
The scheme offers large embedding capacity.
To sustain the visual quality of encrypted images.
Extracting secret messages and recovering images can be independent.
The rest of the paper is structured as the follows:
Section 2 discusses the related works which including the LSB encryption, the sorting applied and the key index reordering method.
Section 3 describes the details of the novel scheme and
Section 4 shows the experiments conducted and their analyses. Finally,
Section 5 is the conclusion.
2. Related Work
Our novel scheme employs the principle idea of a vector quantization (VQ) [
12] codeword index reordering scheme [
13] as the basic technique to embed and extract data. This section describes the data embedding and data extraction using the codeword index reordering.
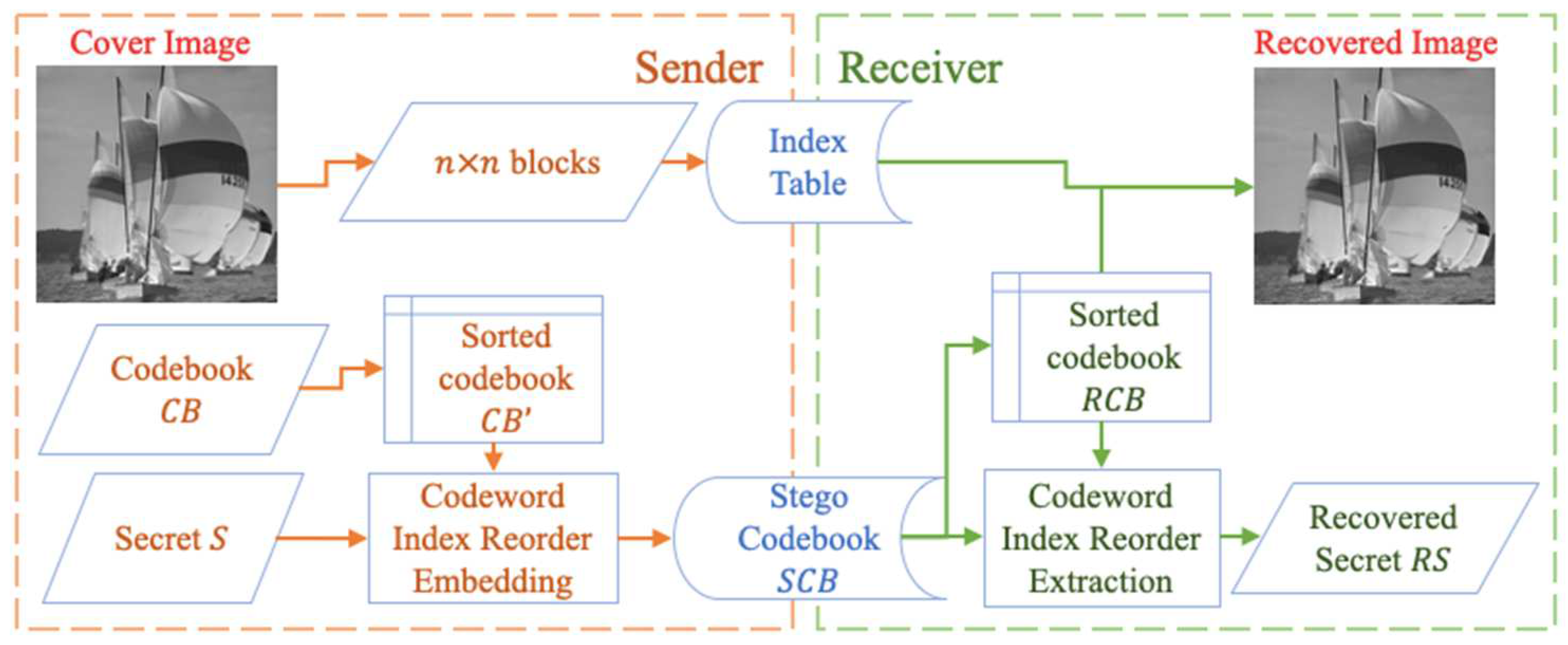
When there is a codebook, it is sorted first before embedding secret data. The data is embedded through the new indices in a stego codebook.
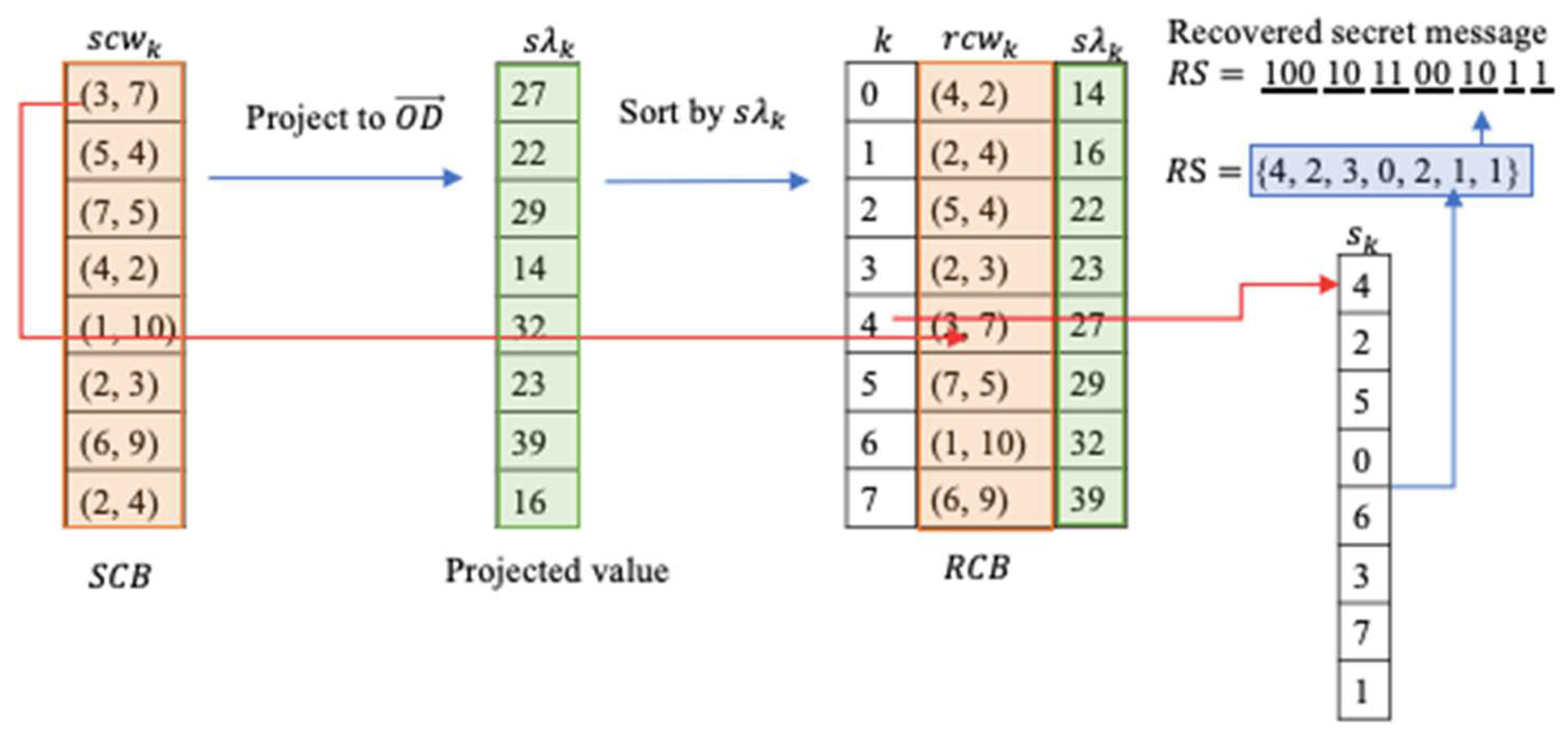
Figure 1 indicates the flow of the codeword index reordering scheme including data embedding, data extraction and image recovery. The stego codebook with the new ordered indices is then sent to receivers to extract the data.
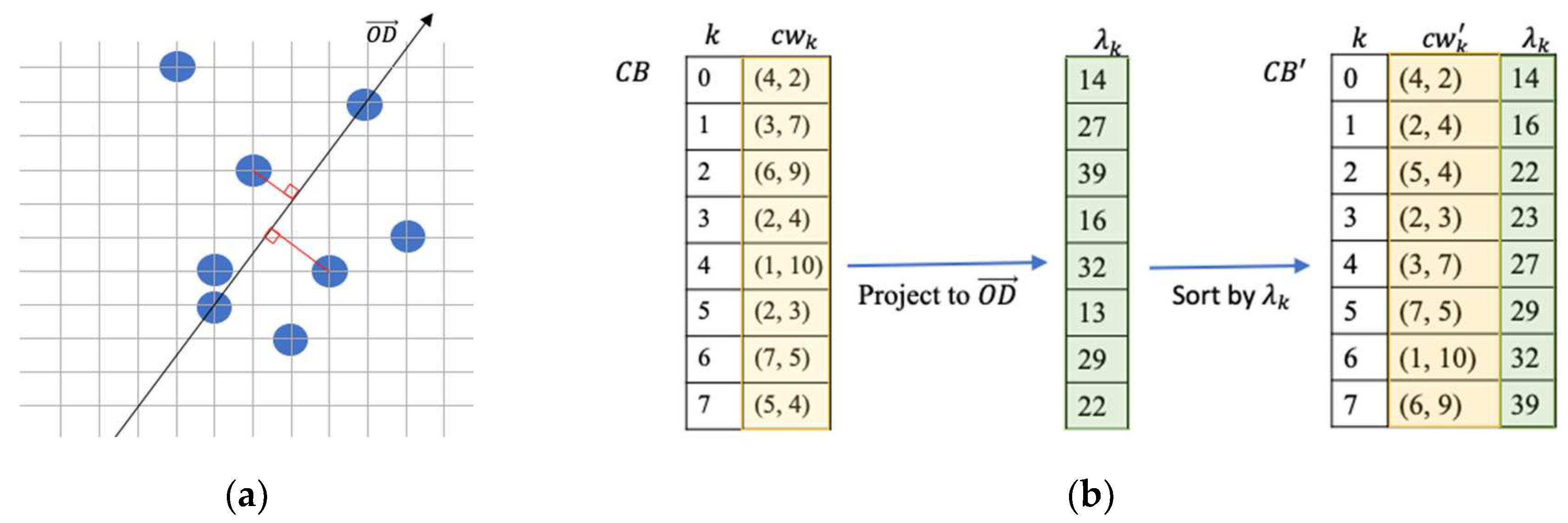
2.1. Sort Codewords by Projected Values
A sorted codebook is an essential component for a codeword index reordering scheme [
13]. There is a VQ codebook
, where
is the number of the codewords in the codebook. A data hider will find an n-dimensional point
,
are randomly generated using a random seed. A line
connecting
and the origin
is a line that codewords in a codebook can project and get their projected values. These projected values are denoted as
,
, ....,
using Eq. (1) and to be used to sort the codewords in the codebook.
The codebook is sorted and resulted to a sorted codebook .
An example of a codebook consists of eight 2-dimensional codewords is demonstrated in
Figure 2 for better understanding of projected values and the sorting result according to their projected values.
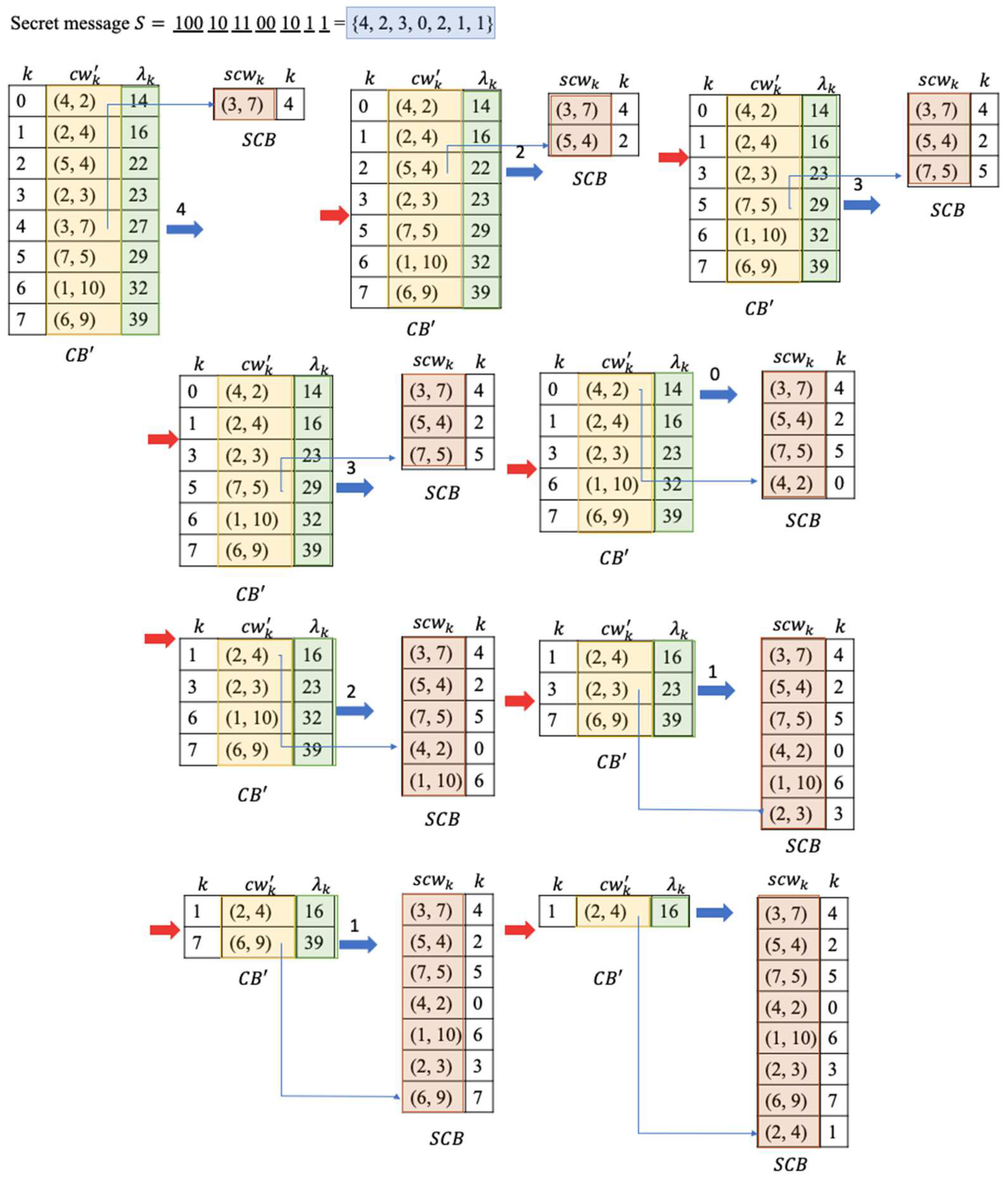
2.2. Data Embedding of the Codeword Index Reordering
When there is a secret data , embedding procedure is stepped as the following:
Step 1: Initialize a stego codebook .
Step 2: Calculate the number of bits to embed
Step 3: Convert secret bits to a decimal index
Step 4: Move the codeword out from and add to .
Step 5: Repeat Step 2 thru Step 4 until there is no codeword in .
Step 6: Send to receivers.
Using the example in
Figure 1, the embedding results is illustrated in
Figure 3.
2.3. Data Extraction of the Codeword Index Reordering
When a receiver receives a stego codebook , the stego codebook needs to be sorted by the projected values of codewords using the received projecting line before extracting secret data. The following steps showing how the secret data are extracted:
Step 1: Project the codewords in to the line and sort the codebook by using the projected values of the codewords to get the recovered codebook .
Step 2: Initialize recovered secret .
Step 3: Initialize the current codeword index c to 0.
Step 4: Match the current codeword with the codewords in the recovered codebook and get the index in the .
Step 5: Convert to a binary bit stream .
Step 6: Append to .
Step 7: Increase the current codeword index c by 1.
Step 8: Repeat Step 4 thru Step 7 until all codewords in are exhausted.
Continue to use the example above,
Figure 4 demonstrates how the data are extracted from the stego codebook
.
3. Proposed Scheme
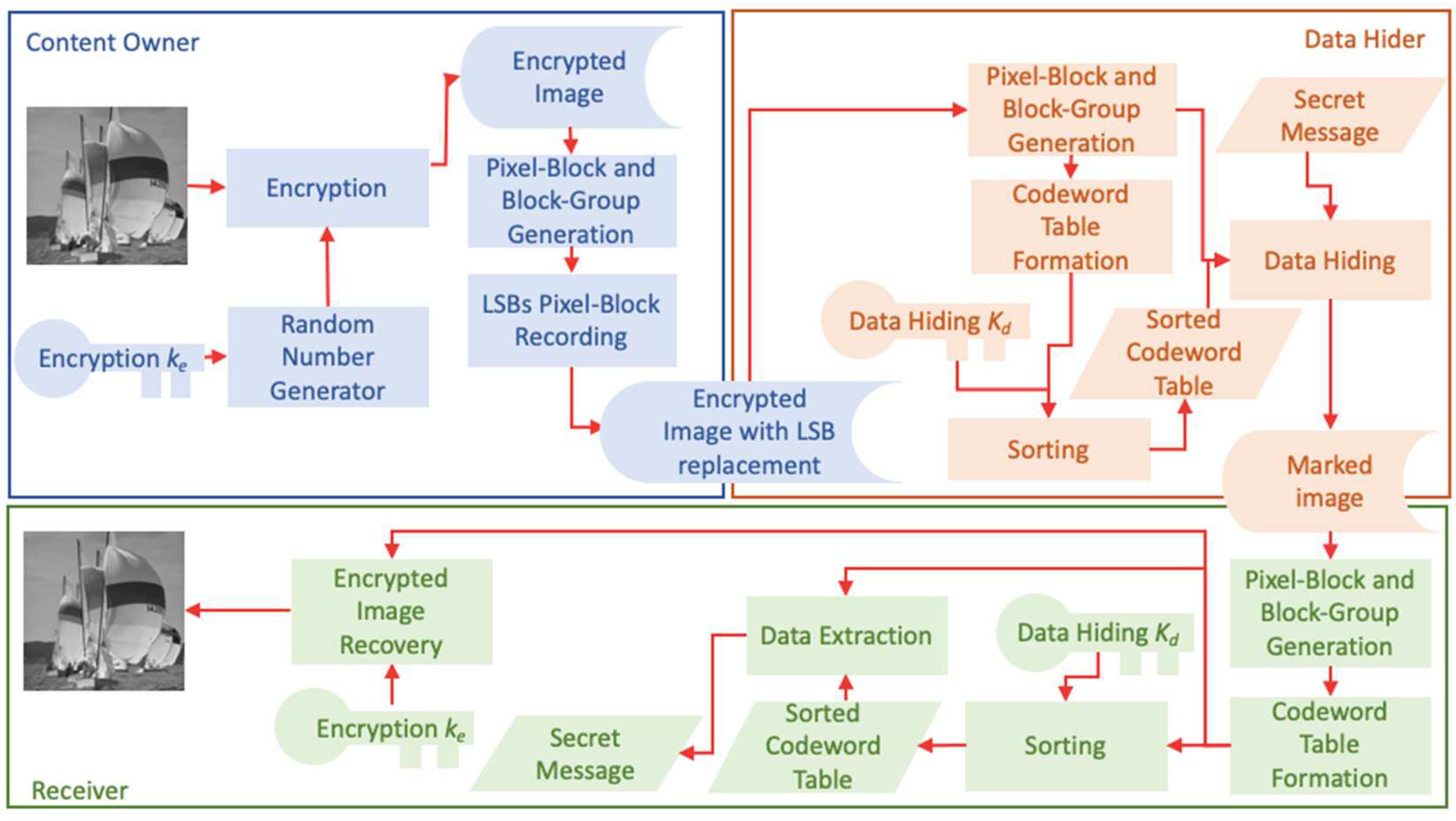
To protect the privacy of original cover images, our novel scheme encrypts the cover image before data embedding using an encryption key. A content owner sends the encrypted image to a data hider to hide secret messages. The data hider sends the marked images, the encryption key and the data hiding key to designated receivers after hiding data.
3.1. Image Encryption
Content owners can use any of the existing encryption methods to protect the privacy of the original images and send the encrypted images to third-party data hiders. The Stream Cipher technique [
14], an exclusive OR operation to encrypt a cipher stream generated by using an encryption key
, is a well-known, simple and efficient method to encrypt images. When there is an original image
of size
, a pseudorandom matrix used as an encryption key
with the matching size of the image
and whose values are ranged between 0 and 255 is generated by using a random seed value. The stream cipher is a symmetrical encryption algorithm which uses the encryption key
in both encryption and decryption. A pixel value and its corresponded encryption key value are converted to 8-bit binary system using Eqs. (4) and (5),
where
represents the
coordinates, 1
i
and 1
j
.
where
represents the
coordinates, 1
i
, 1
j
and
is the bit order from right to left can be represented as
=1,2,⋯,8. After binary conversion, a bit-level XOR as Eq. (6) is applied,
Encrypted image
is converted back to decimal encrypted image
3.2. Codeword Table Generation
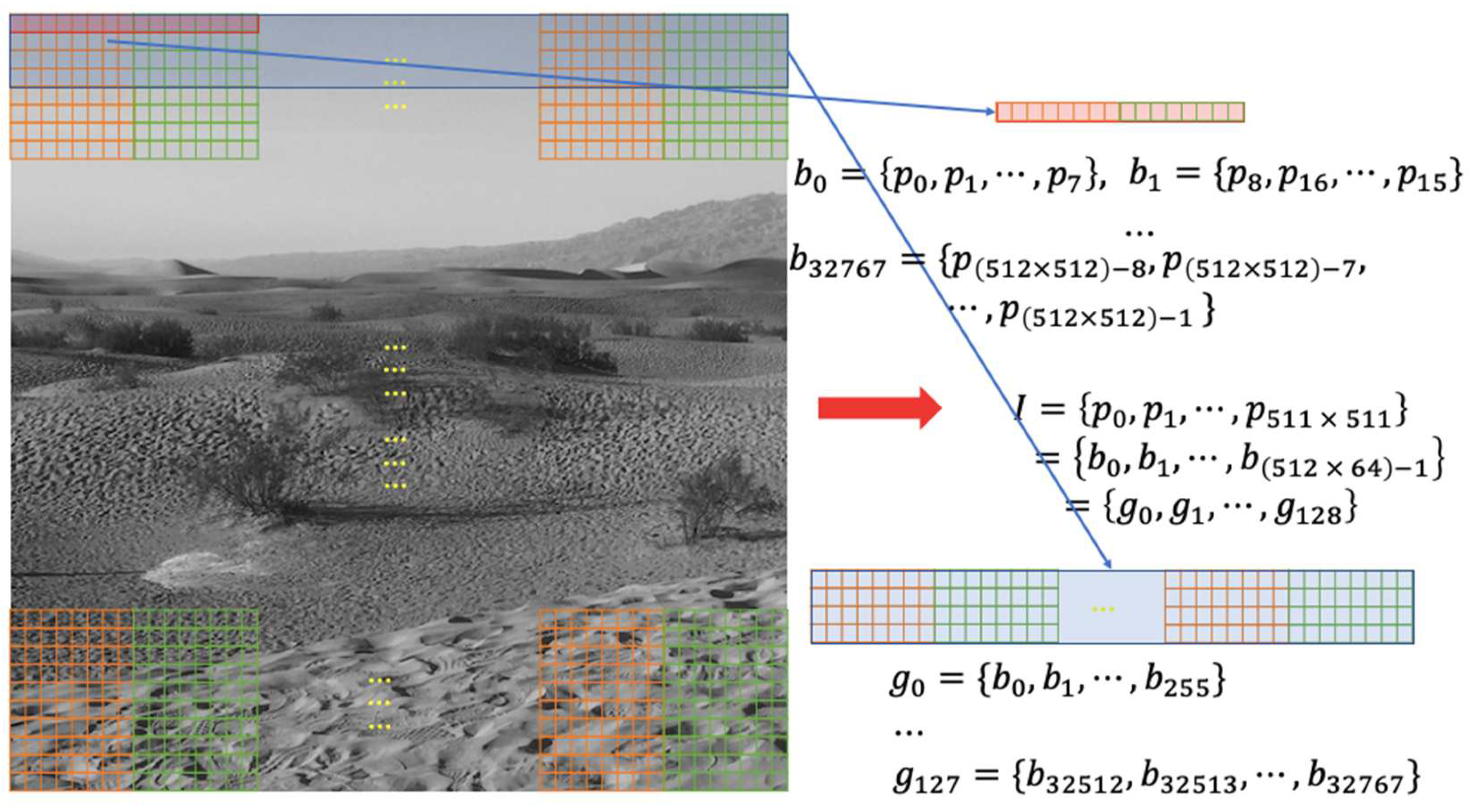
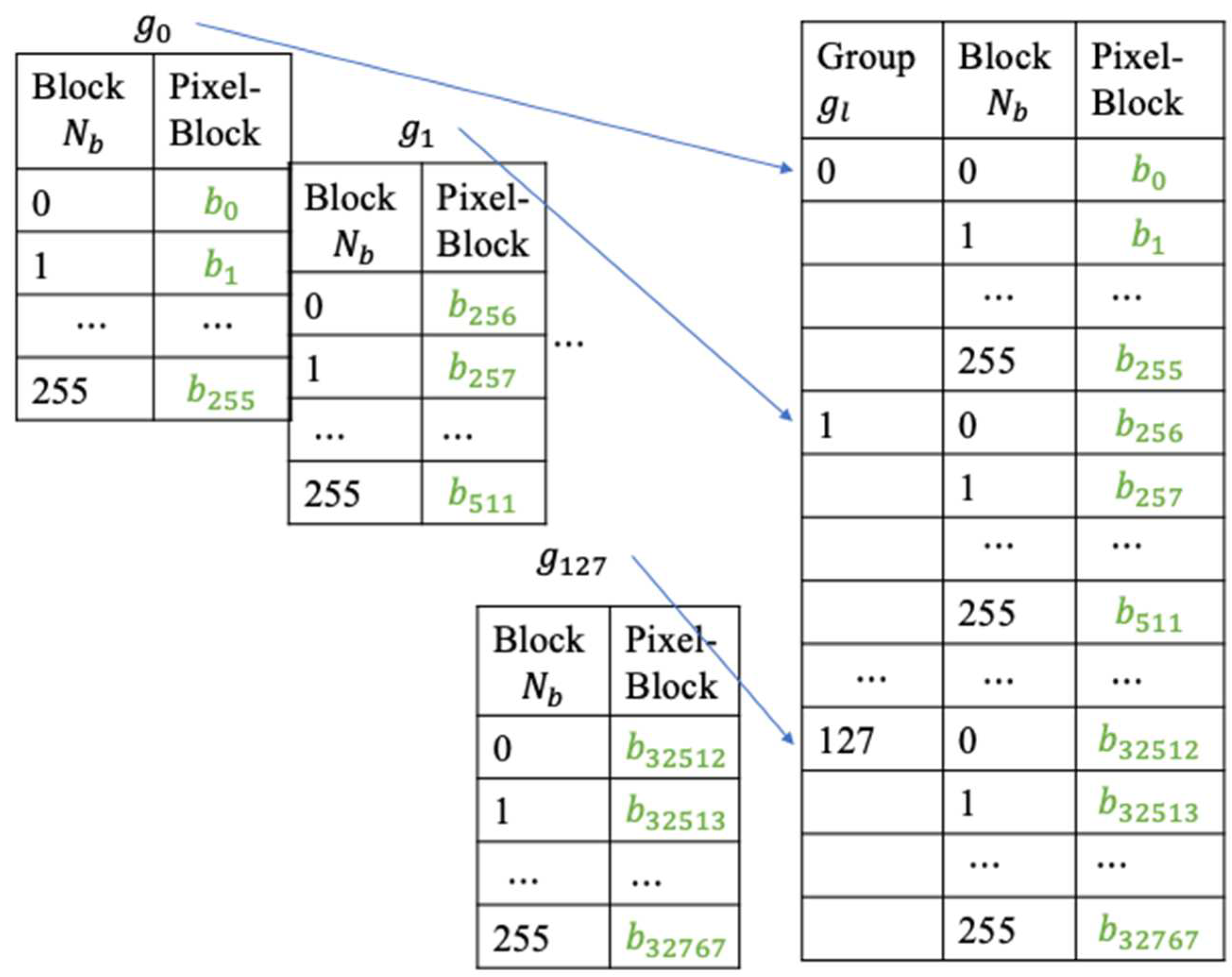
After a data hider obtains the encrypted image , it is converted into a pixel stream. Depending on the block size desired, it is broken into pixel blocks. An owner can set the number of blocks in a group to perform the index reordering technique which is derived from the codeword index reordering.
After obtaining the encrypted image
which consists of
pixels, it is denoted as
. The encrypted image is cut into pixel-blocks and each pixel-block contains
contiguous pixels. A current pixel-block can be denoted as
, where
is the number of the current pixel-block. After pixel-blocks are formed,
pixel-blocks are grouped together to be a block-group
, where
is the number of the current block-group and m is the length of a desired codeword table for the codeword index reordering detailed in
Section 2. The total number of block-groups is
and the block-groups in the encrypted image
can be represented as
. A codeword table containing
n-dimensional codewords is generated for each corresponding block-group
.
Figure 6 is an example on how pixel-blocks and block-groups are created for a
image. When a pixel-block consisting of 8 pixels and a block-group combining 255 blocks, there are 32768 pixel-blocks and 128 block-groups are formed in total for the encrypted image.
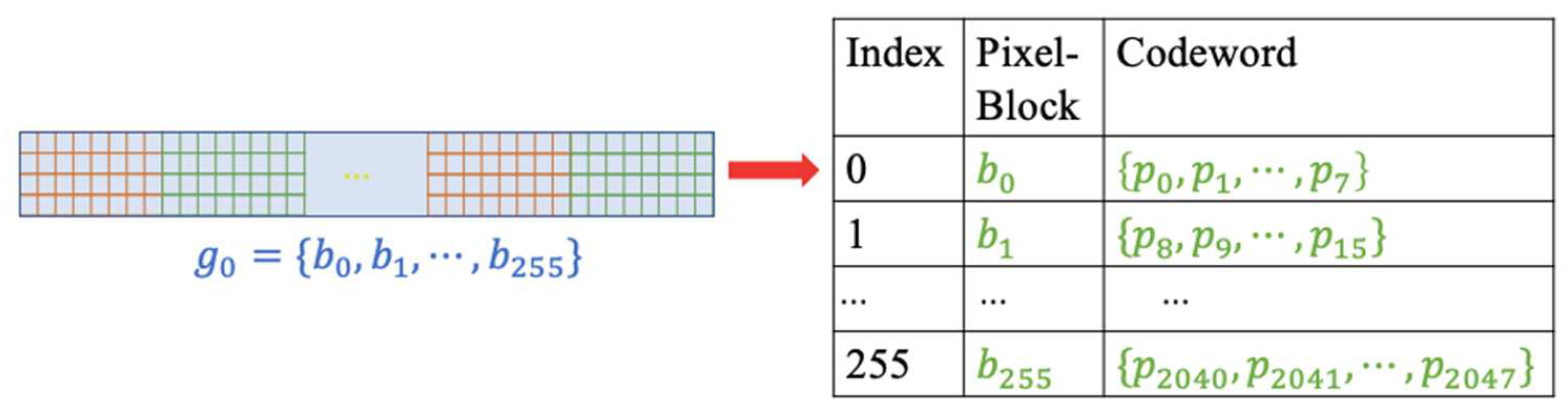
A codeword table for the block-group
of the example in
Figure 6 is illustrated in
Figure 7. The codeword table is treated as a codebook used in the codeword index reordering to hide data at a later stage.
3.3. Pixel-Block Number Embedding
Before hiding data, recording the indices of pixel-blocks in a block group is needed for the image recovery. The original index of a pixel-block
in a block-group is calculated based on
where
is the number of pixel-blocks in a block-group and
is the current pixel-block. For example, the number of pixel-block
in block-group
is 2 and the number of pixel-block
in block-group
is 1.
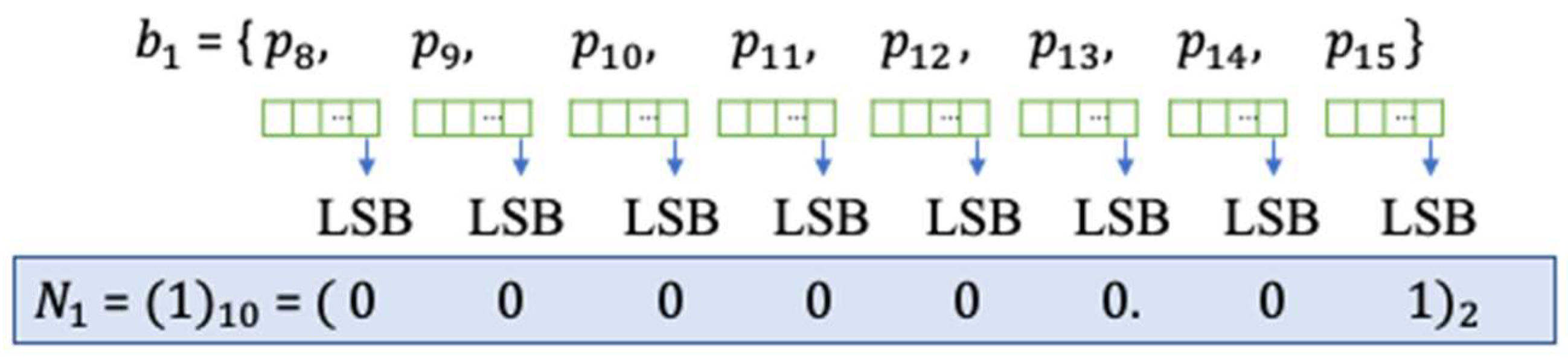
Figure 8 shows a diagram on how pixel-blocks are numbered in each block-group.
Since there are
pixels in a pixel-block, the least significant bit (LSB) [
15] of each pixel in the block is used to indicate its pixel block number in a block group.
Figure 9 demonstrates how to embed a calculated block number
to LSBs. The LSB bit in each pixel inside of a pixel-block is replaced with the binary bit value of its calculated block number in its group. The example shows the decimal value of 1 which is the calculated block number for
in
.
After embedding the calculated block numbers as metadata into the LSBs, the encrypted image is now an encrypted image embedded with image recovery information. It is then sent to the data hider to hide secret data.
3.4. Data Hiding
When the data hider receives the encrypted image with embedded block numbers, a data hiding key and a secret message , an n-dimensional line is generated according to the extraction key . The pixels in each pixel-block form a codeword and get a projected value by projecting the codeword to the line . A codeword table is created for each block group by using these codewords and sorted by their projected values. The sorted codeword table is then used to embed the secret bits by applying the codeword index reordering technique described in Subsection 2.2.
The Algorithm 1 detailed the steps of how to embed the secret message :
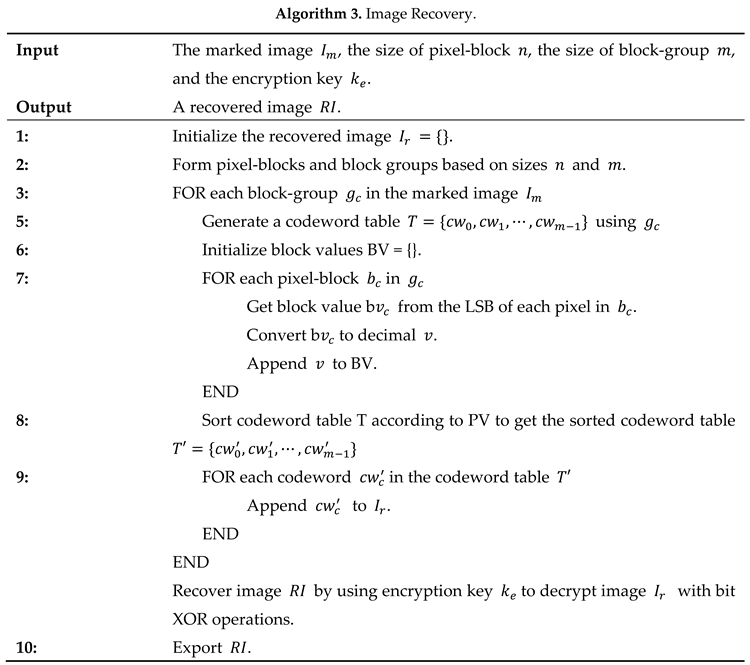
3.5. Data Extraction and Image Recovery
After receiving the marked image , the secret message can be extracted when a receiver has the data hiding key . When a receiver has the encryption key , a recovered image with high visual quality can be obtained. If a receiver has both keys, the secret message can be extracted and the recovered image can be obtained.
3.5.1. Data Extraction
If a receiver has a data extraction key , the secret data can be extracted. The marked image is converted into a pixel stream first. Depending on the size of a pixel-block and the number of blocks in a block-group received, it is divided into pixel-blocks and block-groups first. A n-dimensional line is generated by using the extraction key . The pixels in each pixel-block form a codeword and get a projected value by projecting the codeword to the line . A codeword table is created for each block group of the marked image by using these codewords and is sorted by their projected values. Both the sorted codeword table and the codeword table created from the marked image are used to extract the secret data. The detailed steps are in Algorithm 2.
3.5.2. Image Recovery
If a receiver has an encryption key , a recovered image with high visual quality can be obtained. The marked image is converted into a pixel stream first. Depending on the size of a pixel-block and the number of blocks in a block-group received, the marked pixel stream is broken into pixel-blocks and block-groups. The pixels in each pixel-block form a codeword and a codeword table is created for each block group of the marked image by using these codewords. We can extract the original pixel-blocks’ indices by extracting the values from the LSBs of pixels in pixel-blocks and recover the pixel values by using the encryption key . Algorithm 3 goes through the recovery steps in more details.
4. Experimental Results
n this section, we conducted experiments utilizing the MATLAB environment, version 2017a, within the Windows PC operating system, to assess the performance of the proposed solution and compare it with some state-of-the-art (SOTA) schemes.
We evaluated the performance of the proposed data hiding scheme through experimental analysis. A binary data stream
, generated by a random number generator, was employed as the secret information. The two key factors that we pay attention during data hiding are good visual quality and high embedding quantity. To keep the visual quality means that the recovered images look as similar to the original cover images as possible. To efficiently measure the embedding quantity, embedding capacity (EC) is calculated, representing the total number of bits that the proposed scheme could embed in the image. With the evolution of data hiding techniques, numerous metrics have been utilized to assess the visual quality of the restored images. The commonly employed metrics include Peak Signal-to-Noise Ratio (PSNR) and Structural Similarity Index (SSIM). The calculation formulas are provided below:
where
and
represent the width and height of the images,
and
denote the pixel values at position
for the cover image and the restored image.
represents the mean value used as an estimate for luminance; and
is the standard deviation used as an estimate of contrast;
denotes the covariance between the original image
and the restored image
and serves as a metric for structural similarity.; and
, and
are two constants close to zero.
A higher PSNR value indicates less distortion caused by the hidden data. Typically, with PSNR values exceeding 30 dB suggests imperceptible image distortion to the human eye. SSIM combines three factors—luminance, contrast, and structure—to assess the similarity between two images. The SSIM range is from -1 to 1. As the value of SSIM approaches 1, it demonstrates a higher degree of similarity between the two images.
At the same time, information entropy is selected to test the security of the encrypted image, that is, the randomness of the image histogram is calculated by the following method:
where
represents the image pixel value between 0 and 255, and
is the probability of the image pixel value
occurring. An information entropy value closer to 8 means that the encrypted image has higher randomness.
In
Section 4.1, we evaluate the performance of our proposed scheme under different test images. We give some execution results and security analysis in
Section 4.2.
Section 4.3 gives comparisons with other SOTA schemes.
4.1. Performances of our proposed scheme
The embedding capacity of the proposed scheme is contingent upon the pixel block size and the codeword table size. Therefore, we initially conducted performance tests on different test images by varying the pixel block sizes in a codeword table. The group size in
Table 1 and
Table 2 is what we call the codebook table size.
Table 1 lists the results of applying the proposed scheme to the test images for different pixel block size configurations with the same codebook table size. We observed that, when pixel blocks have an identical number of pixels, the shapes of the pixel blocks had no effect at all on EC values depicted in
Table 1; the shapes also had no significant impact on PSNR, and SSIM. Therefore, we could simplify our scheme by converting the encrypted images to a pixel stream first and specifying the size of a pixel-block without the necessity of specifying the width and the height of a pixel-block. However, the number of pixels within a pixel block had a significant effect on EC, and the larger the size of the pixel block, the less EC the proposed scheme could provide. Moreover, the larger the pixel block, the higher the PSNR and SSIM values of the recovered image when the size of the codebook table was the same. Simultaneously, we observed that the most efficient partitioning is to have
pixel-blocks within a block-group when the size of a pixel-block is n.
In addition to these metrics, we also employed the number of pixels changing rate (NPCR), unified average changed intensity (UACI), and mean absolute error (MAE) to evaluate image distortion between the original and the restored images. The calculation formulas for these metrics are as follows:
where
and
represent the width and height of the images,
and
denote the pixel values at position
for the cover image and the restored image.
NPCR is employed to compute the number of differing pixels between two images, while UACI is utilized to calculate the average change in pixels between two images. Unlike
Table 1,
Table 2 is a test of the proposed scheme with various codebook table sizes. From
Table 2, it can be clearly found that, as the size of the codebook table becomes larger, the EC of the proposed scheme also becomes larger. Since the efficient pairing of codebook table size and pixel block size was utilized, the LSB of each pixel in a pixel block was used to record the original pixel block index in a group and the PSNR values of all tested scenarios were around 51dB. The PSNR values indicated that our recovered image had a good visual quality. As shown in
Table 2, the proposed scheme involves replacing the LSB of pixels with the initial block index in a group after encrypting the image. Consequently, after extracting information and decrypting the image, the LSB of each pixel cannot be fully restored, with a 50% probability of being flipped. As a result, NPCR values are around 50% across various test images. UACI values are notably low, with the highest UACI not exceeding 0.2%, indicating that the average pixel changes induced by the proposed scheme are small even the images cannot be fully recovered. Mean Absolute Error (MAE) is also an indicator for assessing image quality, where a smaller MAE value corresponds to better image quality. From
Table 2, we can find that the MAE values are small for all images. In summary, the proposed scheme causes very little damage to the cover images when embedding the secret data and the recovered images are very similar to the cover images.
4.2. Execution results and security analysis
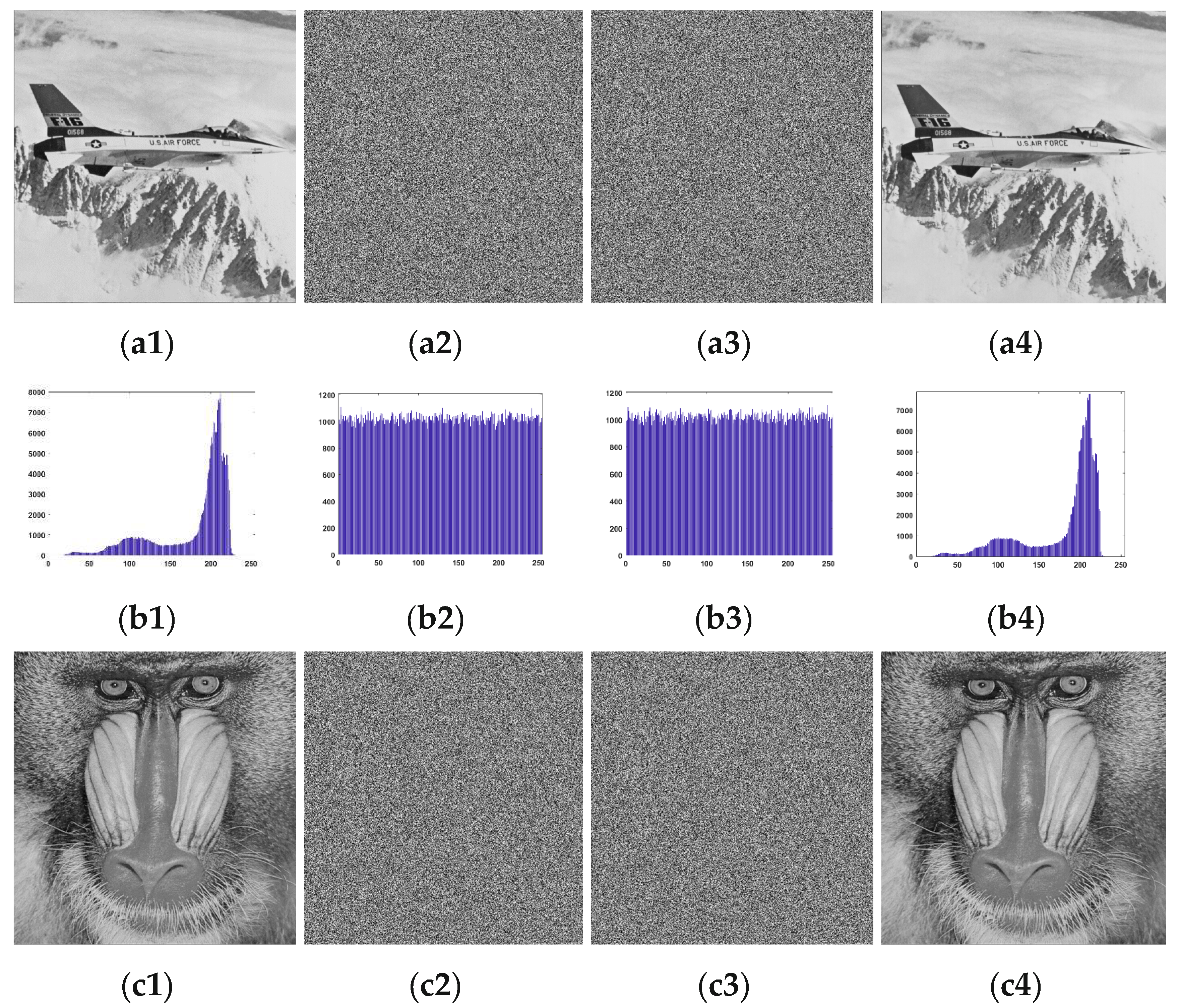
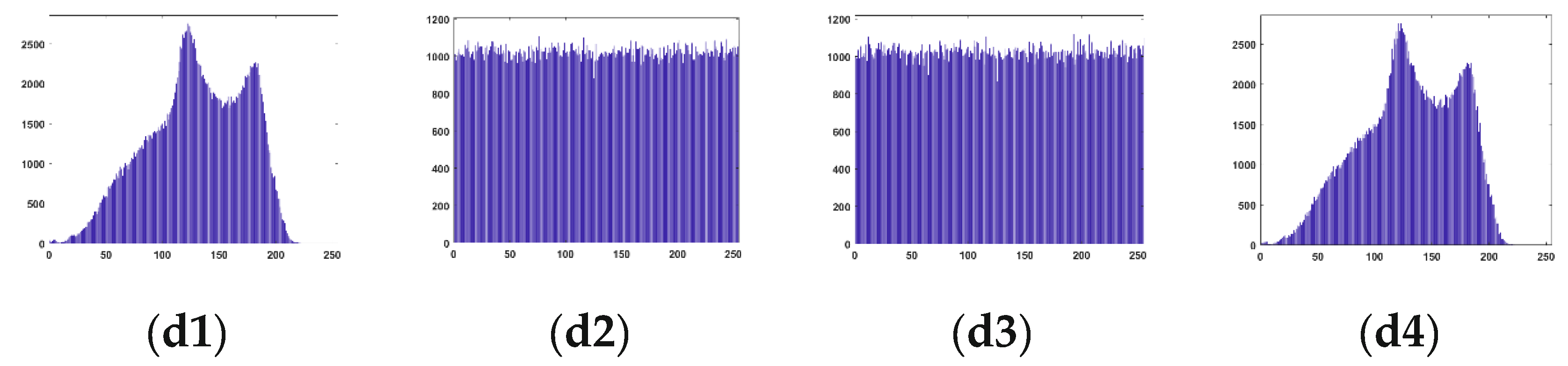
Figure 10 presents the performance results of various test images at different stages. After image encryption, pixel values become disordered, rendering meaningful information indiscernible, and the pixel distribution in the histogram of the encrypted image is uniform consequently. Since our proposed data embedding scheme involves merely scrambling the positions of encrypted pixels after recording the original block indices using LSB replacements, the distribution of pixel values in the encrypted image does not undergo substantial changes. The histogram distributions of the recovered images that we are able to obtain after extracting the information are also very similar to the original histogram distributions.
In addition to information entropy, another way to analyze the differences between adjacent pixels is to use the correlation coefficient to assess the correlation between adjacent pixels. A natural image has a high correlation between neighboring pixels normally, but for a secure encrypted image, the lower the correlation between its neighboring pixels, the more secure it is. It is defined as
We divide the image into pixel pairs, take the former of all pixel pairs as
and the latter of all pixel pairs as
,
denotes the number of pixel pairs, and then calculate the correlation coefficient between them.
Table 3,
Table 4 and
Table 5 were tested with the pixel block size of 8 and the codebook table size of 256. The information entropy and the pixel correlation results for horizontal and vertical pairs are shown in
Table 3 and
Table 4, respectively.
Table 3 provides measurements for the original, encrypted, and embedded encrypted images of different test images. Clearly, the entropy values for the encrypted and embedded encrypted images of each image are quite similar, as our proposed scheme only employs one-bit LSB replacement on encrypted pixels and subsequently scramble the pixel positions. On the other hand, the entropy values for different encrypted images are consistently close to 8, significantly higher than the entropy values of the original images. Consequently, the distribution of pixel values in encrypted images exhibits heightened randomness, thereby enhancing security.
As shown in
Table 4, neighboring pixel values in the original image have strong positive correlation both horizontally and vertically. While the pixels of encrypted and marked images have only very low correlation both horizontally and vertically. Also, the correlation between the marked image and the encrypted image does not change much compared to the encrypted image both horizontally and vertically. This indicates that the Stream Cipher encryption completely encrypts the image, and the proposed scheme that utilizes the reordering of the codebook table to embed the secret data inherits this feature and does not make the correlation between the pixels higher due to the embedded data.
The security of the proposed scheme is further analyzed in
Table 5 using two metrics, NPCR and UACI. The definition and computation of both NPCR and UACI have been mentioned in subsection 4.1. In terms of security analysis, the higher the NPCR value, the more effective the encryption algorithm is, because the higher the number of different pixels, the harder the encrypted image is to crack. For two uncorrelated images, the theoretical value of UACI is 33.33%. As shown in
Table 5, for both encrypted and marked images, the NPCR value and UACI value of the proposed scheme are close to the theoretical optimal value, which indicates that our scheme can provide a high level of security against potential attacks.
4.3. Comparison with state-of-the-art schemes
In this section, we primarily compare our proposed scheme with some state-of-the-art schemes for data hiding in encrypted images in terms of PSNR, SSIM, and embedding capacity. In
Table 6, the embedding capabilities of our proposed schemes all outperform the other schemes. Moreover, our proposed scheme consistently provides stable embedding capacity for any image, as long as the pixel block size and the number of blocks within a group remain unchanged. The independence of embedding capacity from image content is attributed to our utilization of indices within each group for data embedding. So as long as the number of blocks in the group and the size of the pixel blocks are consistent, images of the same size will have the same embedding capacity. From
Table 6, it is evident that our proposed scheme also outperforms most of SOTA methods based on the PSNR values and SSIM values. Even though the PSNR is slightly lower than [
18], our proposed scheme achieves a PSNR of approximately 51 dB, which is adequate for visual quality of a recovered image.
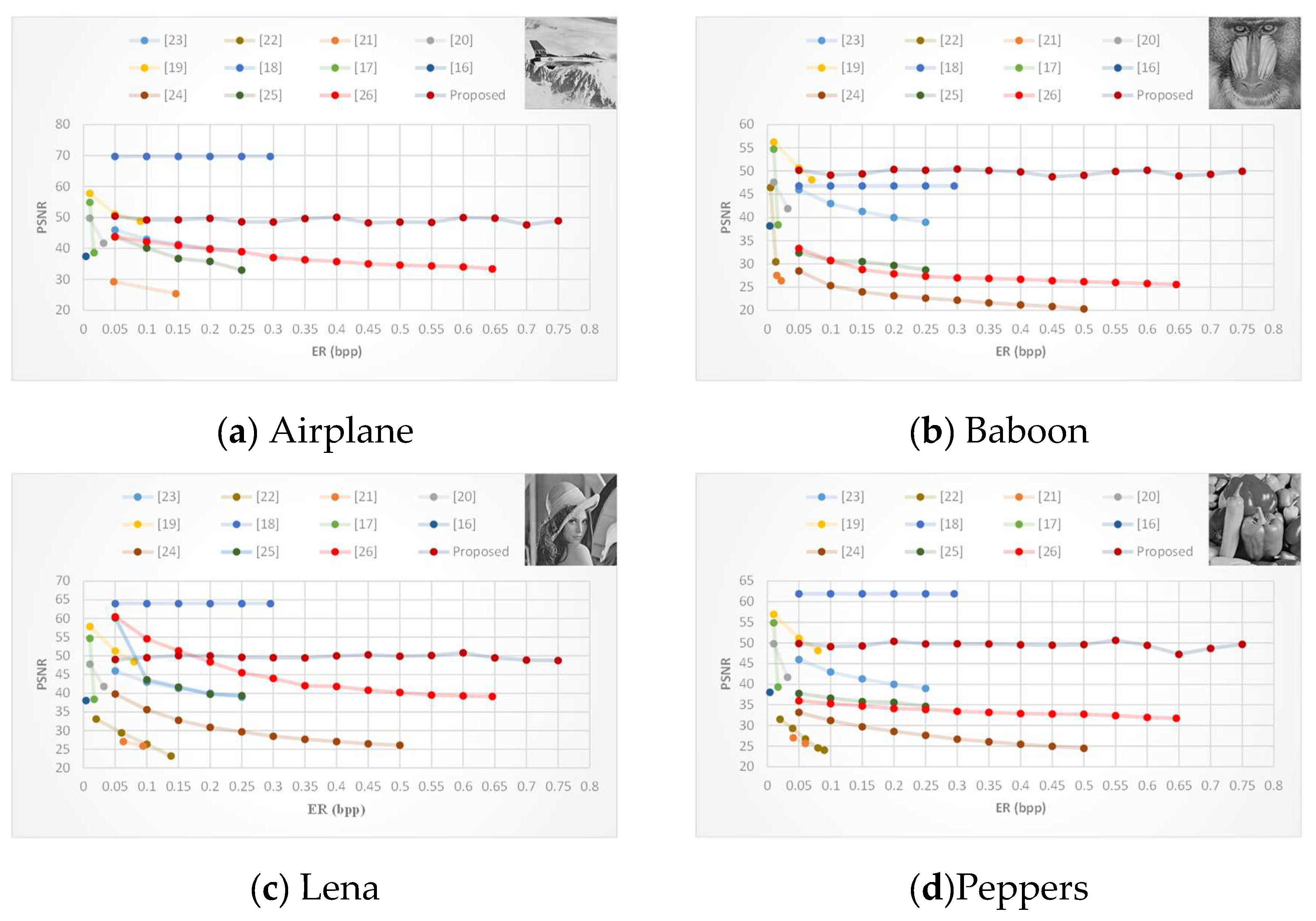
In
Figure 11, we further compare the PSNR of our scheme with more SOTA schemes under different embedding capacities, with a pixel block size of 18 and 256 blocks within a codeword table. In
Figure 11, we use the embedding ratio (ER) to represent the embedding capacity (ER = EC/ total number of pixels). As depicted in
Figure 11, in most cases, the PSNR values of other schemes tends to decrease with increasing embedding capacity. In contrast, our proposed scheme consistently has a stable PSNR for the recovered image. Therefore, as the amount of embedded secret data increases, the advantages of our proposed scheme become more pronounced in terms of the PSNR and the SSIM of the recovered image. As long as the embedding rate is greater than 0.25 bpp, the proposed scheme has better visual quality and higher embedding capability than other schemes.
5. Conclusions
In the proposed scheme, a content owner encrypts an image first using the Stream Cipher technique with an encryption key and embedding pixel-block numbers in each block-group by replacing LSBs of pixels in each pixel-block. The encrypted image with embedding pixel-block numbers is then sent to a data hider to embed secret message and create a marked image by a data hiding key and the codeword table index reordering technique. The marked image is sent to the receivers. When a receiver has the data hiding key, the secret message can be extracted. When a receiver has the encrypted key, the image can be reconstructed.
With our experiment results, we assured that the proposed scheme could achieve our goal of increasing embedding capacity by significant amount comparing to the SOTA schemes. Our experiments showed that the consistency of embedding capability with any cover image as long as the sizes of pixel-blocks and block groups were the same. As for PSNRs, the results showed the proposed scheme could outperform the SOTA schemes as well.
Author Contributions
Conceptualization and methodology, Jui-Chuan Liu, Hengxiao Chi, Ching-Chun Chang and Chin-Chen Chang; software, Hengxiao Chi; validation, Jui-Chuan Liu, Hengxiao Chi, Ching-Chun Chang and Chin-Chen Chang; data curation, Hengxiao Chi; writing—original draft preparation, Jui-Chuan Liu, and Hengxiao Chi; writing—review and editing, Jui-Chuan Liu, and Hengxiao Chi; supervision, Chin-Chen Chang. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- U. Fiore, “Selective Redundancy Removal: A Framework for Data Hiding”, Future Internet, 2010, 2, 30–40. [CrossRef]
- Y. Q. Shi, X. Li, X. Zhang, H. T. Wu, and B. Ma, “Reversible data hiding: Advances in the past two decades,”. IEEE Access 2016, 4, 3210–3237. [CrossRef]
- W. Zhang, H. Wang, D. Hou, and N. Yu, “Reversible data hiding in encrypted images by reversible image transformation. IEEE Trans. Multimedia 2016, 18, 1469–1479. [CrossRef]
- K. Ma, W. Zhang, X. Zhao, N. Yu, and F. Li, “Reversible data hiding in encrypted images by reserving room before encryption. IEEE Trans. Inf. Forensics Secur. 2013, 8, 553–562. [CrossRef]
- P. Puteaux and W. Puech, “A recursive reversible data hiding in encrypted images method with a very high payload,” IEEE Trans. Multimedia, 2020, 23, 636–650. [CrossRef]
- Y. Wu, Y. Xiang, Y. Guo, J. Tang, and Z. Yin, “An improved reversible data hiding in encrypted images using parametric binary tree labeling. IEEE Trans. Multimedia 2020, 22, 1929–1938. [CrossRef]
- P. Pauline and P. William, “An efficient MSB prediction-based method for high-capacity reversible data hiding in encrypted images. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1670–1681. [CrossRef]
- F. Chen, Y. Yuan, H. He, M. Tian, and H. M. Tai, “Multi-MSB compression based reversible data hiding scheme in encrypted images,” IEEE Trans. Circuits Syst. Video Technol., 2021, 31, 905–916. [CrossRef]
- S. Yi and Y. Zhou, “Separable and reversible data hiding in encrypted images using parametric binary tree labeling. IEEE Trans. Multimedia 2019, 21, 51–64. [CrossRef]
- X. Zhang, “Separable reversible data hiding in encrypted image. IEEE Trans. Inf. Forensics Secur. 2012, 7, 826–832. [CrossRef]
- S. Yi and Y. Zhou, “Parametric reversible data hiding in encrypted images using adaptive bit-level data embedding and checkerboard-based prediction. Signal Process. 2018, 150, 171–182. [CrossRef]
- C. C. Chang, J. F. Chang, W. J. Kao, and J. H. Horng, “Two-Layer Reversible Data Hiding for VQ-Compressed Images Based on De-Clustering and Indicator-Free Search-Order Coding,” Future Internet, 2021, 13, 215. [CrossRef]
- 13. J. C. Liu, C. C. Chang, C. C. Lin, and C. C. Chang. Hiding Information in a Well-Trained Vector Quantization Codebook. ACM International Conference on Signal Processing and Machine Learning (SPML), 20 July. [CrossRef]
- S. D. Mohd Satar, M. Hussin, Z. M. Hanapi, and M. A. Mohamed, “Towards Virtuous Cloud Data Storage Using Access Policy Hiding in Ciphertext Policy Attribute-based Encryption”, Future Internet, 2021, 13, 279. [CrossRef]
- Celik MU, Sharma G, Tekalp AM, and Sable E, “Lossless generalized-LSB data embedding. IEEE Trans Image Process, 2005; 14, 253–266. [CrossRef]
- W. Hong, T. S. Chen, and H. Y. Wu, "An improved reversible data hiding in encrypted images using side match. IEEE Signal Processing Letters 2012, 19, 199–202. [CrossRef]
- X. Zhang, "Separable reversible data hiding in encrypted image. IEEE Transactions on Information Forensics and Security 2011, 7, 826–832. [CrossRef]
- Z. Qian and X. Zhang. Reversible data hiding in encrypted images with distributed source encoding. IEEE Transactions on Circuits and Systems for Video Technology 2015, 26, 636–646. [CrossRef]
- X. Wu and W. Sun. High-capacity reversible data hiding in encrypted images by prediction error. Signal Processing, 2014, 104, 387–400. [CrossRef]
- C. Qin, W. Zhang, F. Cao, X. Zhang, and C.-C. Chang. Separable reversible data hiding in encrypted images via adaptive embedding strategy with block selection. Signal Processing 2018, 153, 109–122. [CrossRef]
- F. Huang, J. Huang, and Y.-Q. Shi, "New framework for reversible data hiding in encrypted domain. IEEE Transactions on Information Forensics and Security 2016, 11, 2777–2789. [CrossRef]
- H. Ge, Y. Chen, Z. Qian, and J. Wang, "A high capacity multi-level approach for reversible data hiding in encrypted images,". IEEE Transactions on Circuits and Systems for Video Technology 2018, 29, 2285–2295. [CrossRef]
- R. Bhardwaj and A. Aggarwal, "An improved block based joint reversible data hiding in encrypted images by symmetric cryptosystem,". Pattern Recognition Letters 2020, 139, 60–68. [CrossRef]
- X. Wang, C. C. Chang, C. C. Lin, and C. C. Chang, "Reversal of pixel rotation: A reversible data hiding system towards cybersecurity in encrypted images,". Journal of Visual Communication and Image Representation 2022, 82, 103421. [CrossRef]
- M. Yu, H. Yao, and C. Qin, "Reversible data hiding in encrypted images without additional information transmission. Signal Processing: Image Communication 2022, 105, 116696. [CrossRef]
- K. Gao, J. H. Horng, and C. C. Chang, "Dual Mode Data Hiding in Fully Encrypted Images with Pixel-Shuffling for Cloud Applications. Displays 2023, 102609.
Figure 1.
Flow of codeword index reordering scheme.
Figure 1.
Flow of codeword index reordering scheme.
Figure 2.
(a) Project to line (b) Sort codewords using line-projected values.
Figure 2.
(a) Project to line (b) Sort codewords using line-projected values.
Figure 3.
Data embedding of a codeword index reordering scheme.
Figure 3.
Data embedding of a codeword index reordering scheme.
Figure 4.
Data extraction of a codeword index reordering scheme.
Figure 4.
Data extraction of a codeword index reordering scheme.
Figure 5.
Framework of block group index reordering scheme.
Figure 5.
Framework of block group index reordering scheme.
Figure 6.
Cutting pixel stream into pixel-blocks and forming block-groups.
Figure 6.
Cutting pixel stream into pixel-blocks and forming block-groups.
Figure 7.
Constructing a codeword table for a block-group.
Figure 7.
Constructing a codeword table for a block-group.
Figure 8.
Block numbers in block groups.
Figure 8.
Block numbers in block groups.
Figure 9.
LSB replacements in pixels according to the calculated block number in a block- group.
Figure 9.
LSB replacements in pixels according to the calculated block number in a block- group.
Figure 10.
Execution results of our proposed scheme: (a1) is original “Airplane” image with pixels. (a2) and (a3) are encrypted image and embedded encrypted image (block size = , codeword table size = 256). (a4) is the decrypted image. (b1-b4) are the corresponding histograms of (a1-a4). In (c) and (d), the results of “Baboon” (block size = , codeword table size = 256), are given.
Figure 10.
Execution results of our proposed scheme: (a1) is original “Airplane” image with pixels. (a2) and (a3) are encrypted image and embedded encrypted image (block size = , codeword table size = 256). (a4) is the decrypted image. (b1-b4) are the corresponding histograms of (a1-a4). In (c) and (d), the results of “Baboon” (block size = , codeword table size = 256), are given.
Figure 11.
PSNR Comparisons with SOTA schemes.
Figure 11.
PSNR Comparisons with SOTA schemes.
Table 1.
Performance of different block sizes with the same group size of 256.
Table 1.
Performance of different block sizes with the same group size of 256.
| Image name |
Block size |
Group size |
EC |
PSNR |
SSIM |
| Airplane |
|
256 |
197888 |
51.1497 |
0.9956 |
|
256 |
197888 |
51.1327 |
0.9956 |
|
256 |
197888 |
51.1491 |
0.9956 |
|
256 |
98944 |
54.1349 |
0.9978 |
|
256 |
64932 |
55.9329 |
0.9985 |
| Baboon |
|
256 |
197888 |
51.1499 |
0.9987 |
|
256 |
197888 |
51.1469 |
0.9987 |
|
256 |
197888 |
51.1329 |
0.9987 |
|
256 |
98944 |
54.1787 |
0.9994 |
|
256 |
64932 |
55.9347 |
0.9996 |
| Barbara |
|
256 |
197888 |
51.1360 |
0.9972 |
|
256 |
197888 |
51.1542 |
0.9972 |
|
256 |
197888 |
51.1450 |
0.9972 |
|
256 |
98944 |
54.1392 |
0.9986 |
|
256 |
64932 |
55.9208 |
0.9991 |
| Boat |
|
256 |
197888 |
51.1419 |
0.9972 |
|
256 |
197888 |
51.1469 |
0.9972 |
|
256 |
197888 |
51.1410 |
0.9972 |
|
256 |
98944 |
54.1624 |
0.9986 |
|
256 |
64932 |
55.9081 |
0.9991 |
| Couple |
|
256 |
197888 |
51.1399 |
0.9975 |
|
256 |
197888 |
51.1316 |
0.9975 |
|
256 |
197888 |
51.1489 |
0.9975 |
|
256 |
98944 |
54.1454 |
0.9987 |
|
256 |
64932 |
55.9446 |
0.9992 |
| Lena |
|
256 |
197888 |
51.1344 |
0.9960 |
|
256 |
197888 |
51.1447 |
0.9960 |
|
256 |
197888 |
51.1509 |
0.9960 |
|
256 |
98944 |
54.1487 |
0.9980 |
|
256 |
64932 |
55.9430 |
0.9987 |
| Peppers |
|
256 |
197888 |
51.1362 |
0.9963 |
|
256 |
197888 |
51.1452 |
0.9963 |
|
256 |
197888 |
51.1435 |
0.9963 |
|
256 |
98944 |
54.1419 |
0.9981 |
|
256 |
64932 |
55.8990 |
0.9988 |
Table 2.
Performance with different block-group sizes and different pixel-block.
Table 2.
Performance with different block-group sizes and different pixel-block.
| Image name |
Block size |
Group size |
EC |
PSNR |
NPCR |
UACI |
MAE |
| Airplane |
|
256 |
197888 |
51.15 |
49.90 |
0.1957 |
0.4990 |
|
64 |
180048 |
51.15 |
49.89 |
0.1957 |
0.4989 |
|
8 |
155648 |
51.14 |
49.98 |
0.1960 |
0.4998 |
|
4 |
131072 |
51.14 |
50.06 |
0.1963 |
0.5006 |
| Baboon |
|
256 |
197888 |
51.15 |
49.90 |
0.1957 |
0.4990 |
|
64 |
180048 |
51.12 |
50.22 |
0.1969 |
0.5022 |
|
8 |
155648 |
51.14 |
50.05 |
0.1963 |
0.5005 |
|
4 |
131072 |
51.14 |
50.01 |
0.1961 |
0.5001 |
| Barbara |
|
256 |
197888 |
51.14 |
50.06 |
0.1963 |
0.5006 |
|
64 |
180048 |
51.15 |
49.95 |
0.1959 |
0.4995 |
|
8 |
155648 |
51.14 |
49.98 |
0.1960 |
0.4998 |
|
4 |
131072 |
51.14 |
50.02 |
0.1961 |
0.5002 |
| Boat |
|
256 |
197888 |
51.14 |
49.99 |
0.1960 |
0.4999 |
|
64 |
180048 |
51.15 |
49.88 |
0.1956 |
0.4988 |
|
8 |
155648 |
51.14 |
50.00 |
0.1961 |
0.5000 |
|
4 |
131072 |
51.13 |
50.07 |
0.1964 |
0.5007 |
| Couple |
|
256 |
197888 |
51.14 |
50.01 |
0.1961 |
0.5001 |
|
64 |
180048 |
51.14 |
49.97 |
0.1960 |
0.4997 |
|
8 |
155648 |
51.14 |
49.99 |
0.1960 |
0.4999 |
|
4 |
131072 |
51.13 |
50.08 |
0.1964 |
0.5008 |
| Lena |
|
256 |
197888 |
51.13 |
50.08 |
0.1964 |
0.5008 |
|
64 |
180048 |
51.14 |
49.98 |
0.1960 |
0.4998 |
|
8 |
155648 |
51.14 |
49.97 |
0.1960 |
0.4997 |
|
4 |
131072 |
51.14 |
49.97 |
0.1960 |
0.4997 |
| Peppers |
|
256 |
197888 |
51.14 |
50.06 |
0.1963 |
0.5006 |
|
64 |
180048 |
51.14 |
50.04 |
0.1962 |
0.5004 |
|
8 |
155648 |
51.15 |
49.93 |
0.1958 |
0.4993 |
|
4 |
131072 |
51.14 |
50.05 |
0.1963 |
0.5005 |
Table 3.
Entropy values of test images.
Table 3.
Entropy values of test images.
| Image name |
Original image entropy |
Encrypted image entropy |
Marked image entropy |
| Airplane |
6.705888 |
7.9993 |
7.9993 |
| Baboon |
7.357949 |
7.9993 |
7.9993 |
| Barbara |
7.632119 |
7.9993 |
7.9992 |
| Boat |
7.19137 |
7.9994 |
7.9993 |
| Couple |
7.058103 |
7.9992 |
7.9993 |
| Lena |
7.445507 |
7.9992 |
7.9992 |
| Peppers |
7.594429 |
7.9993 |
7.9993 |
Table 4.
Horizontal and vertical correlation analysis.
Table 4.
Horizontal and vertical correlation analysis.
| Image name |
Original image |
Encrypted image |
Marked image |
| Hor |
Ver |
Hor |
Ver |
Hor |
Ver |
| Airplane |
0.9606 |
0.9584 |
-0.0019 |
-0.0033 |
-0.0019 |
-0.0080 |
| Baboon |
0.8667 |
0.7498 |
0.0010 |
-0.0034 |
0.0010 |
-0.0131 |
| Barbara |
0.8956 |
0.9588 |
-0.0009 |
-0.0028 |
-0.0009 |
-0.0138 |
| Boat |
0.9383 |
0.9715 |
0.0000 |
-0.0052 |
0.0000 |
-0.0087 |
| Couple |
0.9433 |
0.9534 |
-0.0035 |
-0.0027 |
-0.0034 |
-0.0091 |
| Lena |
0.9719 |
0.9850 |
0.0002 |
-0.0012 |
0.0001 |
-0.0112 |
| Peppers |
0.9730 |
0.9762 |
-0.0012 |
-0.0028 |
-0.0012 |
-0.0103 |
Table 5.
NPCR and UACI analysis of test images.
Table 5.
NPCR and UACI analysis of test images.
| Image name |
Encrypted image |
Marked image |
| NPCR |
UACI |
NPCR |
UACI |
| Airplane |
99.8096 |
32.3892 |
99.61624 |
32.43519 |
| Baboon |
99.8096 |
27.9032 |
99.60213 |
27.58626 |
| Barbara |
99.8096 |
29.8222 |
99.60213 |
29.86593 |
| Boat |
99.8096 |
28.5168 |
99.61014 |
28.54057 |
| Couple |
99.8096 |
28.2082 |
99.63608 |
27.8268 |
| Lena |
99.8096 |
28.6750 |
99.61281 |
28.81635 |
| Peppers |
99.8096 |
29.6210 |
99.60632 |
29.64995 |
Table 6.
EC, PSNR and SSIM comparisons.
Table 6.
EC, PSNR and SSIM comparisons.
| Image |
|
[18] |
[23] |
[24] |
Group size=16 |
Group size=64 |
Group size=256 |
| Lena |
EC |
77385 |
65536 |
131072 |
155648 |
180048 |
197888 |
| |
PSNR |
64 |
39 |
26.1 |
51.14 |
51.14 |
51.13 |
| |
SSIM |
0.9781 |
0.9417 |
0.8965 |
0.9960 |
0.9960 |
0.9960 |
| Peppers |
EC |
77385 |
65536 |
131072 |
155648 |
180048 |
197888 |
| |
PSNR |
61.9 |
39 |
24.5 |
51.15 |
51.14 |
51.14 |
| |
SSIM |
0.9837 |
0.9446 |
24.5 |
0.9963 |
0.9963 |
0.9963 |
| Baboon |
EC |
77385 |
65536 |
131072 |
155648 |
180048 |
197888 |
| |
PSNR |
46.8 |
39 |
20.31 |
51.15 |
51.12 |
51.15 |
| |
SSIM |
0.9918 |
0.9805 |
0.7739 |
0.9987 |
0.9987 |
0.9987 |
| Airplane |
EC |
77385 |
65536 |
130915 |
155648 |
180048 |
197888 |
| |
PSNR |
69.7 |
39 |
25.73 |
51.14 |
51.15 |
51.15 |
| |
SSIM |
0.9824 |
0.9403 |
0.9073 |
0.9956 |
0.9956 |
0.9956 |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).