Submitted:
31 December 2023
Posted:
03 January 2024
You are already at the latest version
Abstract
Keywords:
I. Introduction
- Proposing a permanent fault aware scheduling method that tolerates permanent faults.
- Enabling TP3M scheme to manage peak power overlaps between concurrently executing tasks.
II. Related Work
A. Energy Consumption management
B. Peak Power Reduction
C. Reliability-Aware Peak Power Management
III. System Models and Assumptions
A. System and Task Model
B. Power Consumption Model
IV. Our Proposed Method
A. Overview
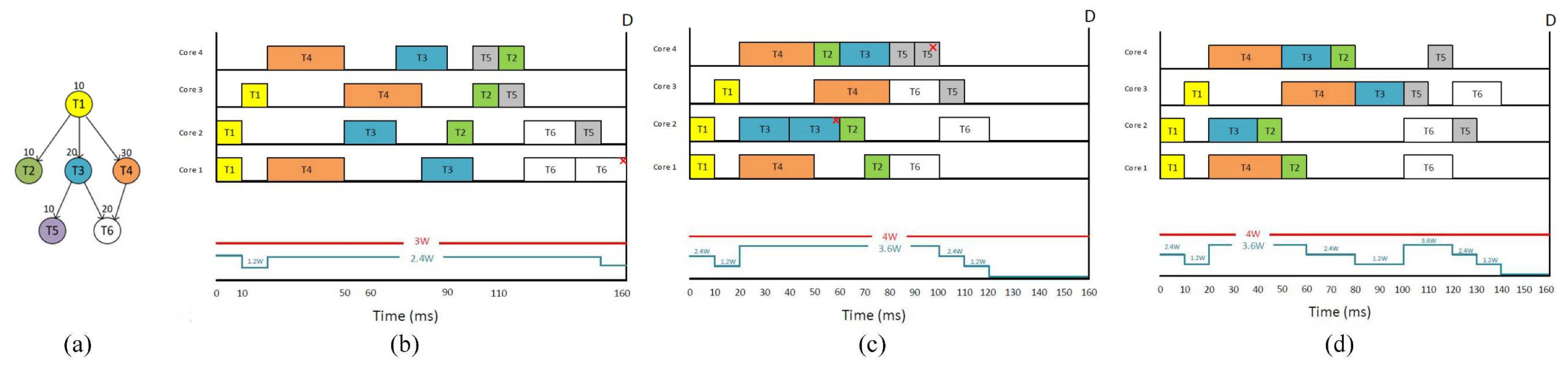
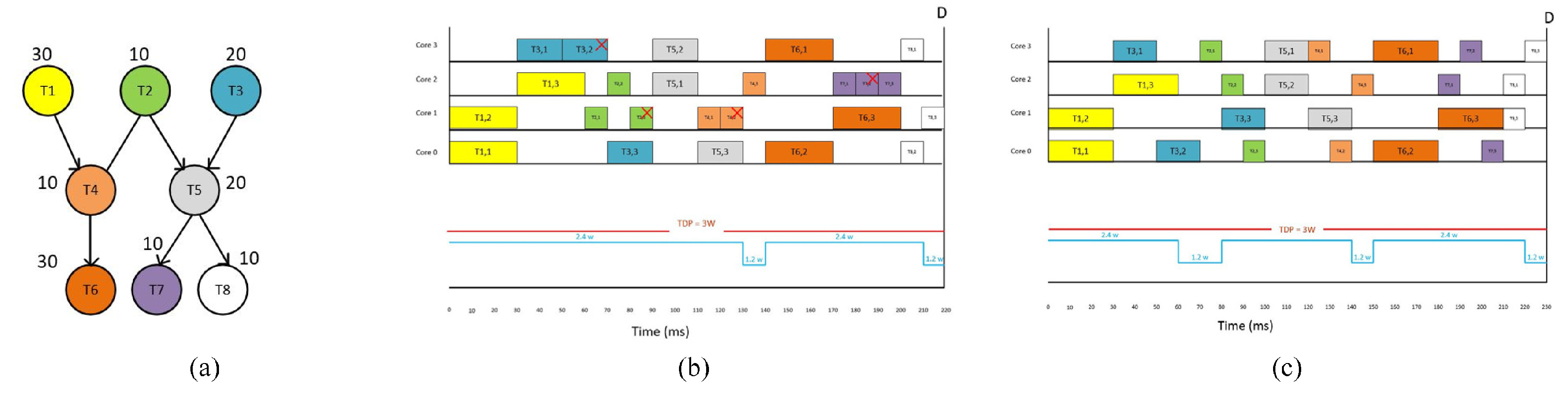
B. Illustrative Example
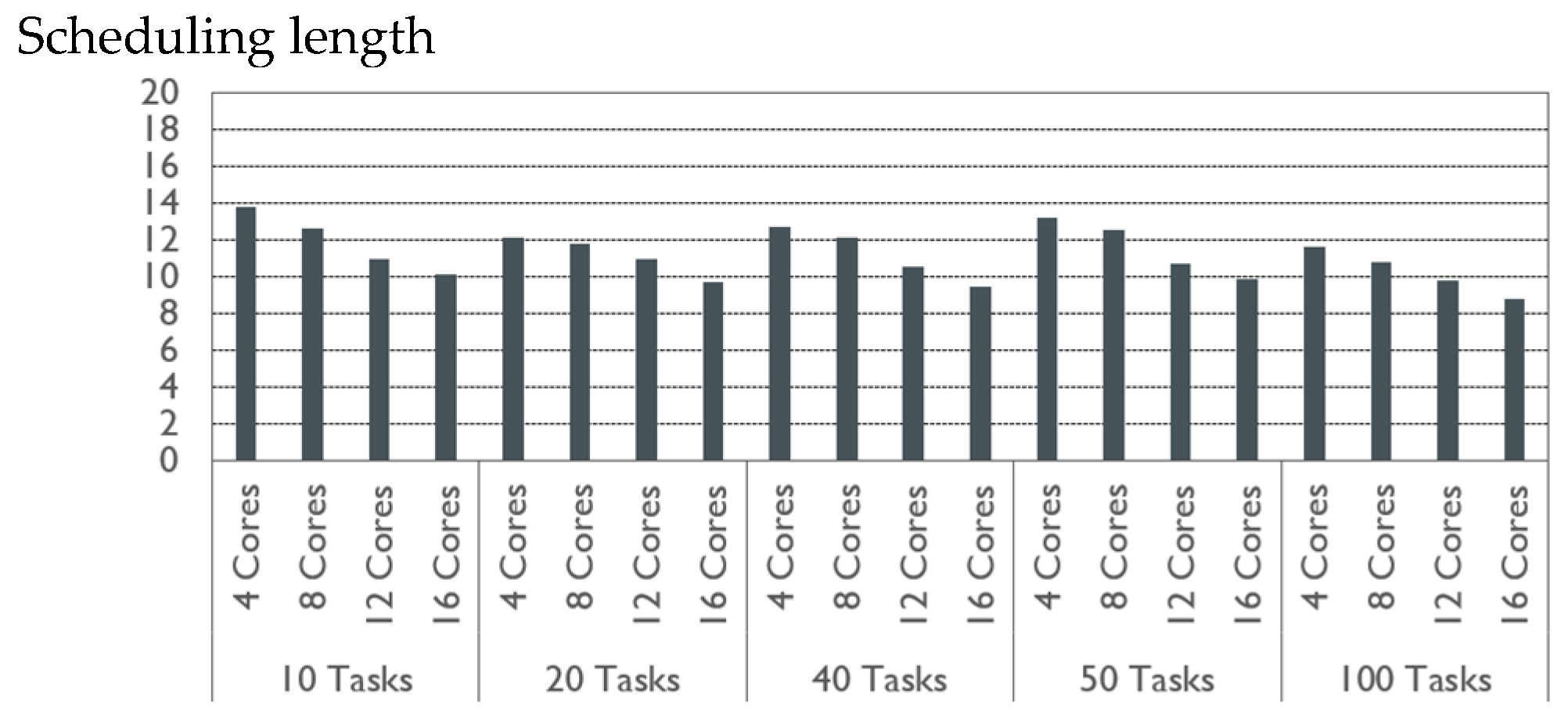
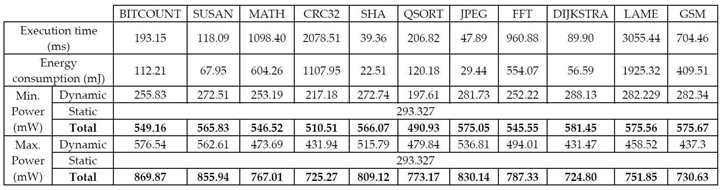
V. Experimental Evaluation
VI. Conclusions
References
- Ansari, Mohsen, Sepideh Safari, Amir Yeganeh-Khaksar, Mohammad Salehi, and Alireza Ejlali. "Peak power management to meet thermal design power in fault-tolerant embedded systems." IEEE Transactions on Parallel and Distributed Systems 30, no. 1 (2018): 161-173. [CrossRef]
- Salehi, Mohammad, Alireza Ejlali, and Bashir M. Al-Hashimi. "Two-phase low-energy N-modular redundancy for hard real-time multi-core systems." IEEE Transactions on Parallel and Distributed Systems 27, no. 5 (2015): 1497-1510. [CrossRef]
- Mireshghallah, FatemehSadat, Mohammad Bakhshalipour, Mohammad Sadrosadati, and Hamid Sarbazi-Azad. "Energy-efficient permanent fault tolerance in hard real-time systems." IEEE Transactions on Computers 68, no. 10 (2019): 1539-1545. [CrossRef]
- Lee, Jinkyu, Buyoung Yun, and Kang G. Shin. "Reducing peak power consumption inmulti-core systems without violatingreal-time constraints." IEEE Transactions on Parallel and Distributed Systems 25, no. 4 (2013): 1024-1033. [CrossRef]
- Lee, BongKi, Jaehwan Kim, Yeuncheul Jeung, and Jongwha Chong. "Peak power reduction methodology for multi-core systems." In 2010 International SoC Design Conference, pp. 233-235. IEEE, 2010.
- Munawar, Waqaas, Heba Khdr, Santiago Pagani, Muhammad Shafique, Jian-Jia Chen, and Jörg Henkel. "Peak power management for scheduling real-time tasks on heterogeneous many-core systems." In 2014 20th IEEE International Conference on Parallel and Distributed Systems (ICPADS), pp. 200-209. IEEE, 2014.
- Pagani, Santiago, Jian-Jia Chen, and Jörg Henkel. "Energy and peak power efficiency analysis for the single voltage approximation (SVA) scheme." IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems 34, no. 9 (2015): 1415-1428. [CrossRef]
- Ansari, Mohsen, Mohammad Salehi, Sepideh Safari, Alireza Ejlali, and Muhammad Shafique. "Peak-Power-Aware Primary-Backup Technique for Efficient Fault-Tolerance in Multicore Embedded Systems." IEEE Access 8 (2020): 142843-142857. [CrossRef]
- Yeganeh-Khaksar, Amir, Mohsen Ansari, and Alireza Ejlali. "ReMap: Reliability Management of Peak-Power-Aware Real-Time Embedded Systems through Task Replication." IEEE Transactions on Emerging Topics in Computing (2020). [CrossRef]
- Ansari, Mohsen, Amir Yeganeh-Khaksar, Sepideh Safari, and Alireza Ejlali. "Peak-power-aware energy management for periodic real-time applications." IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems 39, no. 4 (2019): 779-788. [CrossRef]
- Ansari, Mohsen, Mostafa Pasandideh, Javad Saber-Latibari, and Alireza Ejlali. "Meeting thermal safe power in fault-tolerant heterogeneous embedded systems." IEEE Embedded Systems Letters 12, no. 1 (2019): 29-32. [CrossRef]
- Ansari, Mohsen, Javad Saber-Latibari, Mostafa Pasandideh, and Alireza Ejlali. "Simultaneous management of peak-power and reliability in heterogeneous multicore embedded systems." IEEE Transactions on Parallel and Distributed Systems 31, no. 3 (2019): 623-633. [CrossRef]
- Buttazzo, Giorgio C. Hard real-time computing systems: predictable scheduling algorithms and applications. Vol. 24. Springer Science & Business Media, 2011.
- Guthaus, Matthew R., Jeffrey S. Ringenberg, Dan Ernst, Todd M. Austin, Trevor Mudge, and Richard B. Brown. "MiBench: A free, commercially representative embedded benchmark suite." In Proceedings of the fourth annual IEEE international workshop on workload characterization. WWC-4 (Cat. No. 01EX538), pp. 3-14. IEEE, 2001.

 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




