Submitted:
08 February 2024
Posted:
12 February 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Provide a thorough background of cyber-physical system components of smart grid (SG-CPS).
- Explore wide ranges of vulnerabilities associated with the cyber-physical components of SG systems and the various load management applications related to various operations and functionalities of the SG paradigm.
- Overview of the security background related to the SG’s security goals, range of vulnerabilities, types of attacks and vulnerability mitigation techniques.
- Analysis of the scope of the simulation in SG paradigm in studying vulnerabilities found in the literature and methods to lessen these threats by strengthening the security of the smart energy system.
- Identify the research gaps from the current literature.
- Present directions in future research that address gaps and that will result in solutions for testing vulnerability to the SG system setup by measuring performance, correctness, and security before deployment.
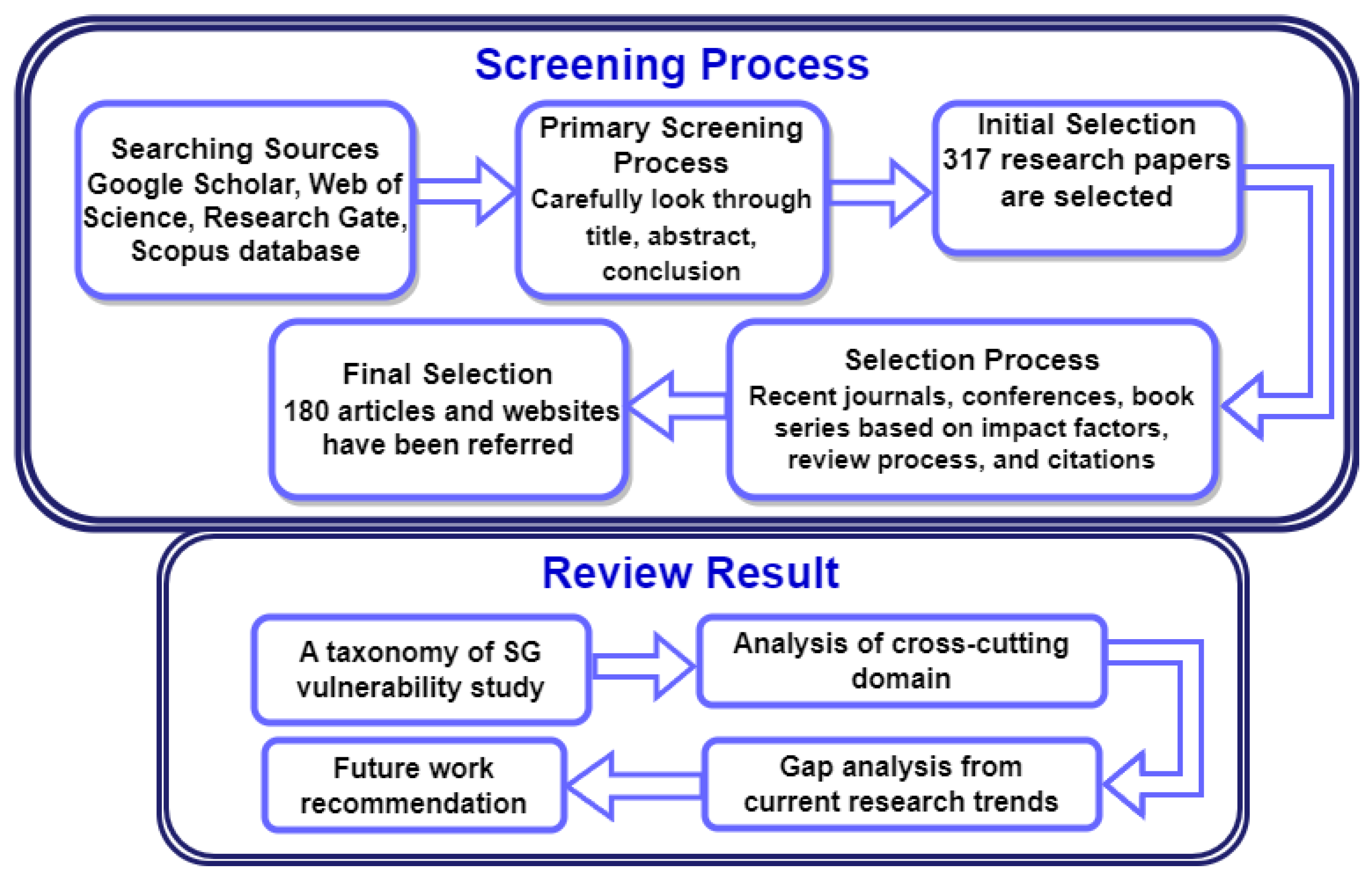
2. Survey Methodology
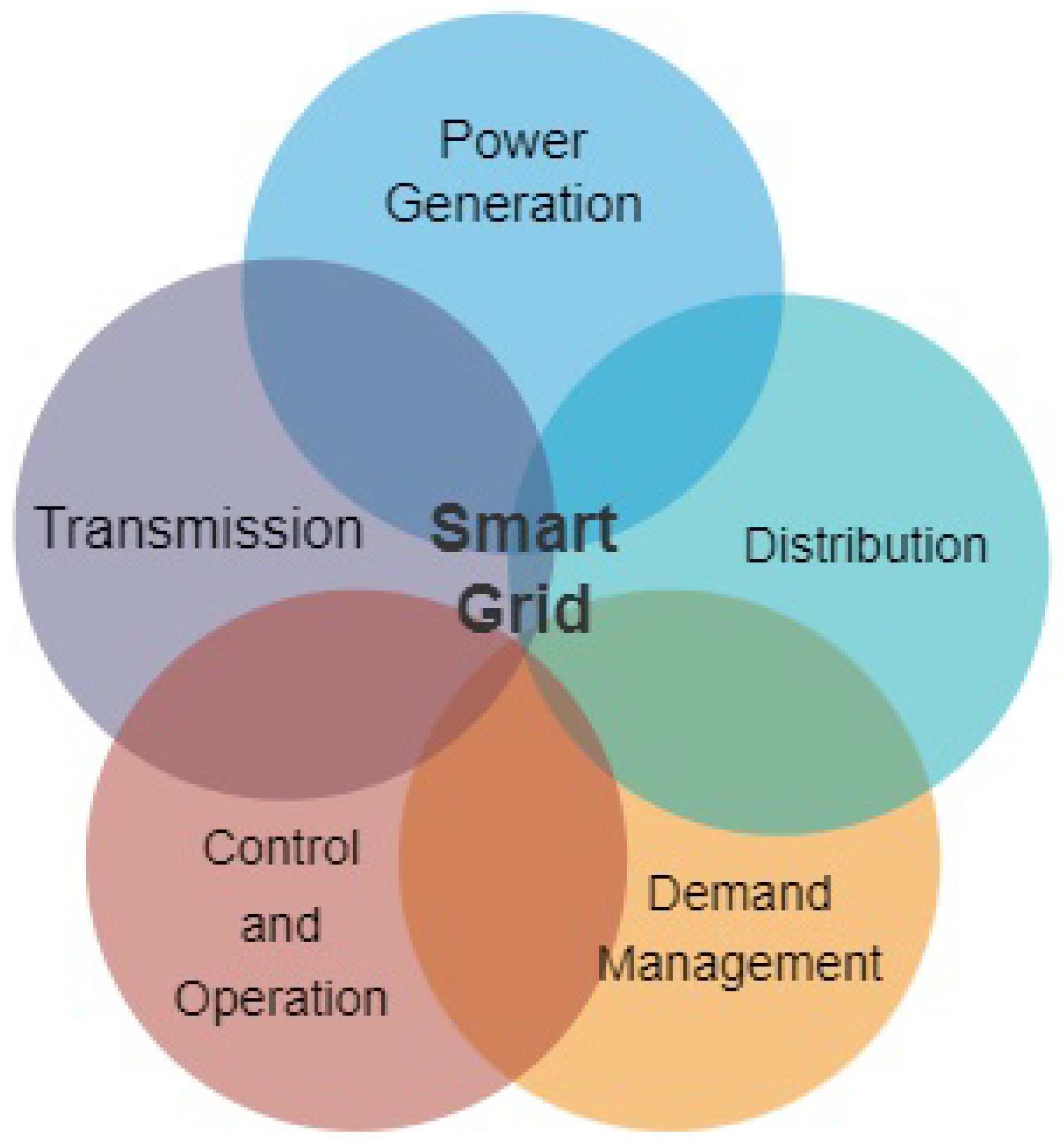
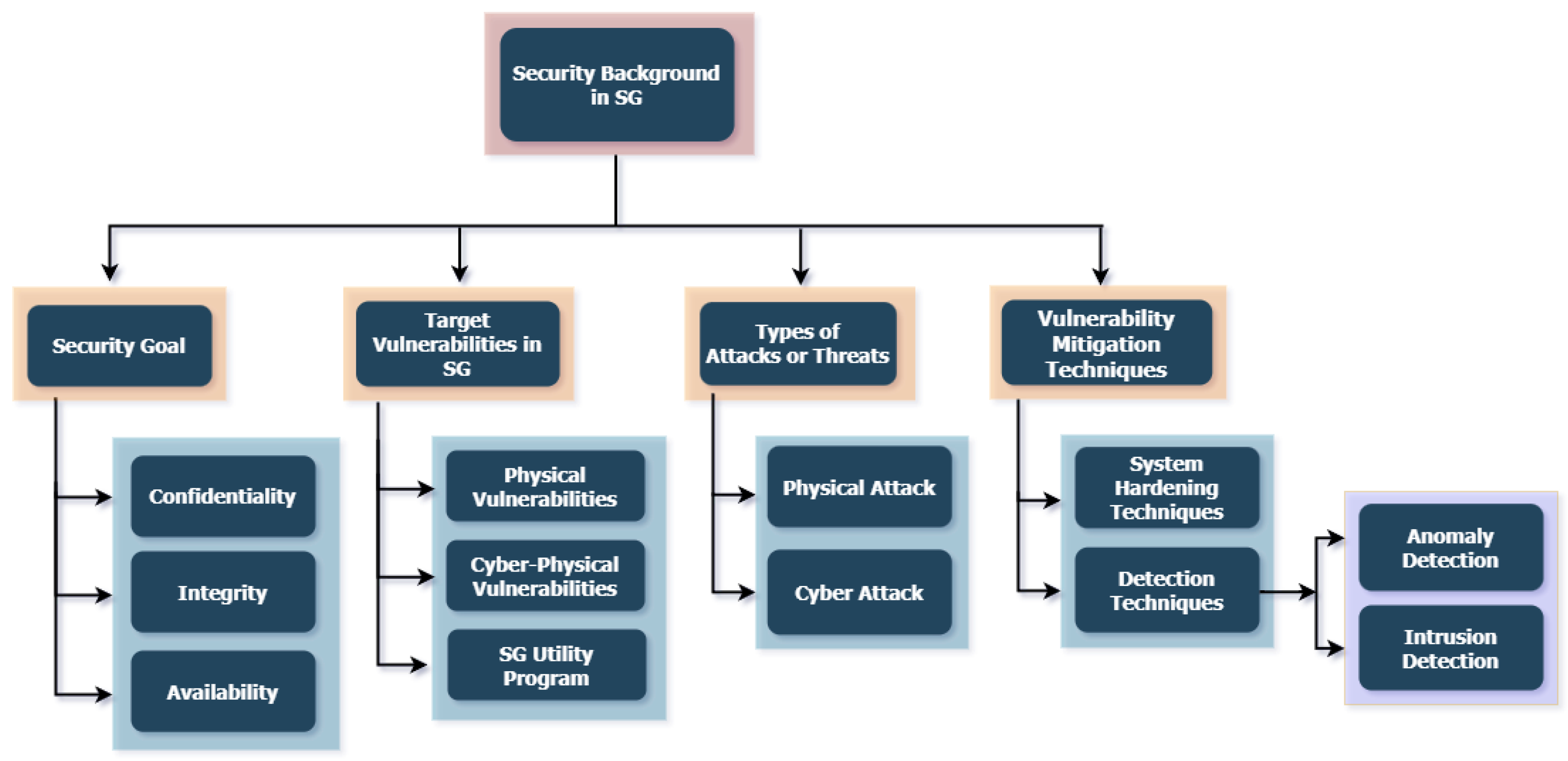
3. SG Security Background
- Smart Grid-Background
3.1. Security Goal in SG
- Confidentiality: Confidentiality is roughly equivalent to privacy. It prevents an enemy’s unwanted access to highly secured information, such as power usage, price data, and control instructions. Such unwanted access can invade customers’ privacy and divulge sensitive information about utilities.
- Integrity: Integrity refers to the ability to prevent the alteration of crucial data from sensors, electronic devices, such as smart meters (SM), software, and control commands that can impair decision-making and taint the data exchange of the SG. According to the authors in [14], improper data injection can alter state estimation, impair the SG’s integrity and lead to improper power management.
- Availability: Availability refers to the ability to stop an enemy from denying authorized people access to, or control over, a system. Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks can obstruct, delay, or corrupt information, resulting in an SG’s inability to share information or provide power. Control-command and price information must be available in this situation because a loss of revenue could result.
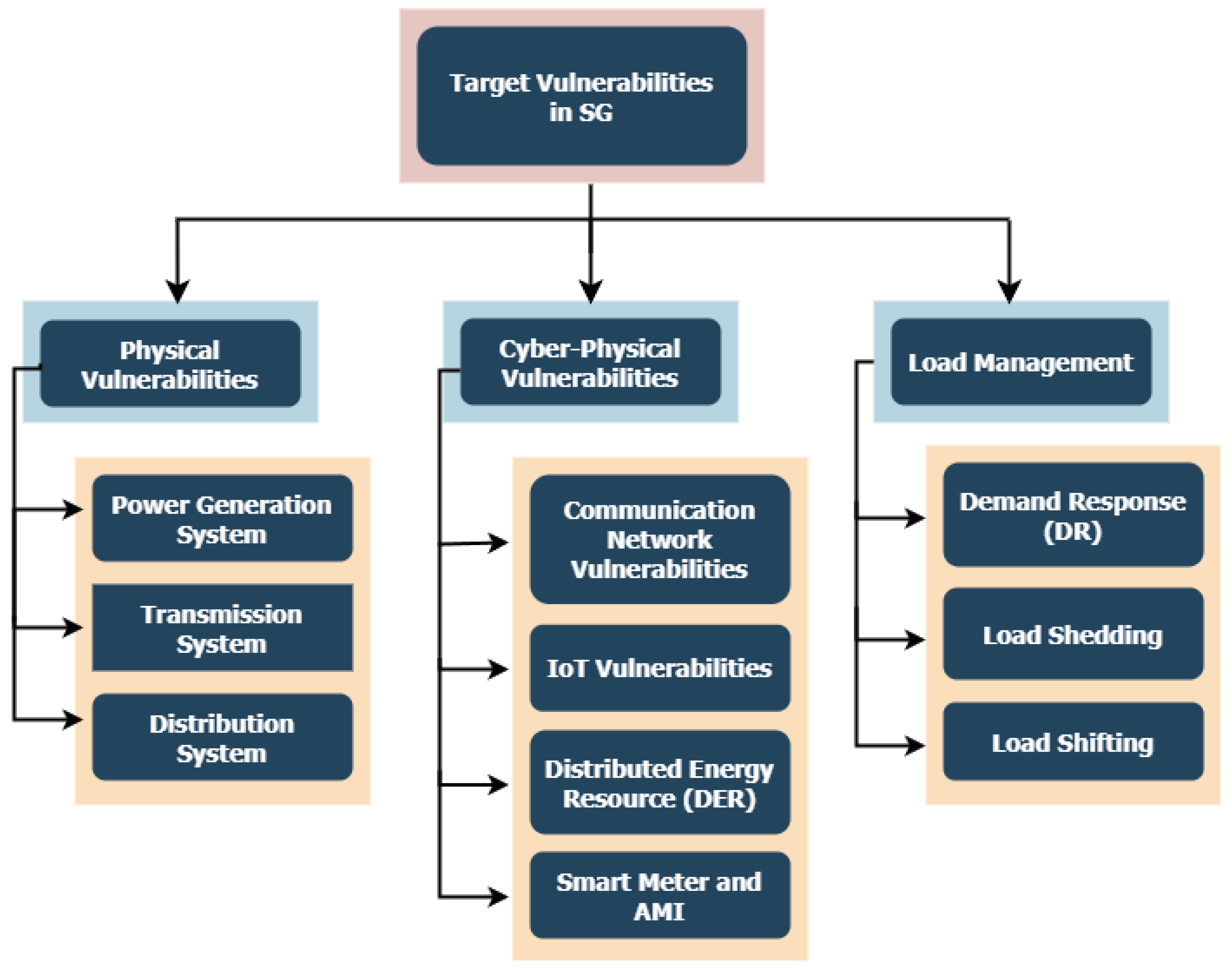
3.2. Target Vulnerabilities in SG
3.2.1. SG Physical Vulnerabilities
-
Power Generation Plant:
- Power generation components are monitored through SCADA systems, but traditional systems may have vulnerabilities that make them vulnerable to cyberattacks. Attackers can exploit these vulnerabilities to manipulate frequency measurements and affect the facility’s stability [16].
- Generation plant numerical relays use Ethernet-based IEC 61850. Attackers can cause malfunction or trip protection to damage power equipment [17].
- Local control loops are connected to the plant control center through Ethernet. Attackers can access the LAN, install a Trojan horse, or compromise digital control modules.
-
Transmission System:
- Transmission of significant volumes of energy using HVDC wires is becoming prevalent. HVDC lines need improved cyber security; therefore, their SCADA network incorporates permission and access control. When an opponent sends control signals to modify the commutation angle or block power flow, the targeted region loses power.
- RTUs and PLCs in the transmission system share generating system weaknesses. An opponent can build a URL and send it to any control center member. A networked HMI accesses the URL and tricks the web browser into running a malicious JavaScript code. After that, the network’s PLCs are automatically detected, compromising the system. These are CSRF attacks.
-
Distribution System:
- A key distributive mechanism in a smart grid is the smart meter. A conventional meter can be changed by reversing the internal consumption counter or influencing the electric current calculation. IEDs like SMs can be remotely controlled to perform preprogrammed tasks. This lets an attacker remotely connect or disconnect devices, change system operator data, or steal critical user data. An attacker sending false data packets to cause negative pricing and power shortages in the targeted region would cost the utility provider income. Protecting every node is difficult, with millions of conventional and SMs coupled to the system, increasing susceptibility.
- Anderson and Fuloria found that a remote attacker could disable millions of SMs [18]. SMs also violate OWASP, or Open Web Application Security Project, rules. These standards address function-level access control inadequacy, injection, authentication, XSS, unsafe direct object references, security misconfiguration, exposed sensitive data, and XSS.
- Consumers who have a net metering system implemented at their location can tamper with the data on their net energy consumption transmitted to the utility’s control center by breaking into the communication network of the AMI [19].
- Even if the customer is not sending power back to the grid, the attacker can cut costs or gain credits. Distribution companies lose more, yet the system doesn’t stop instantly.
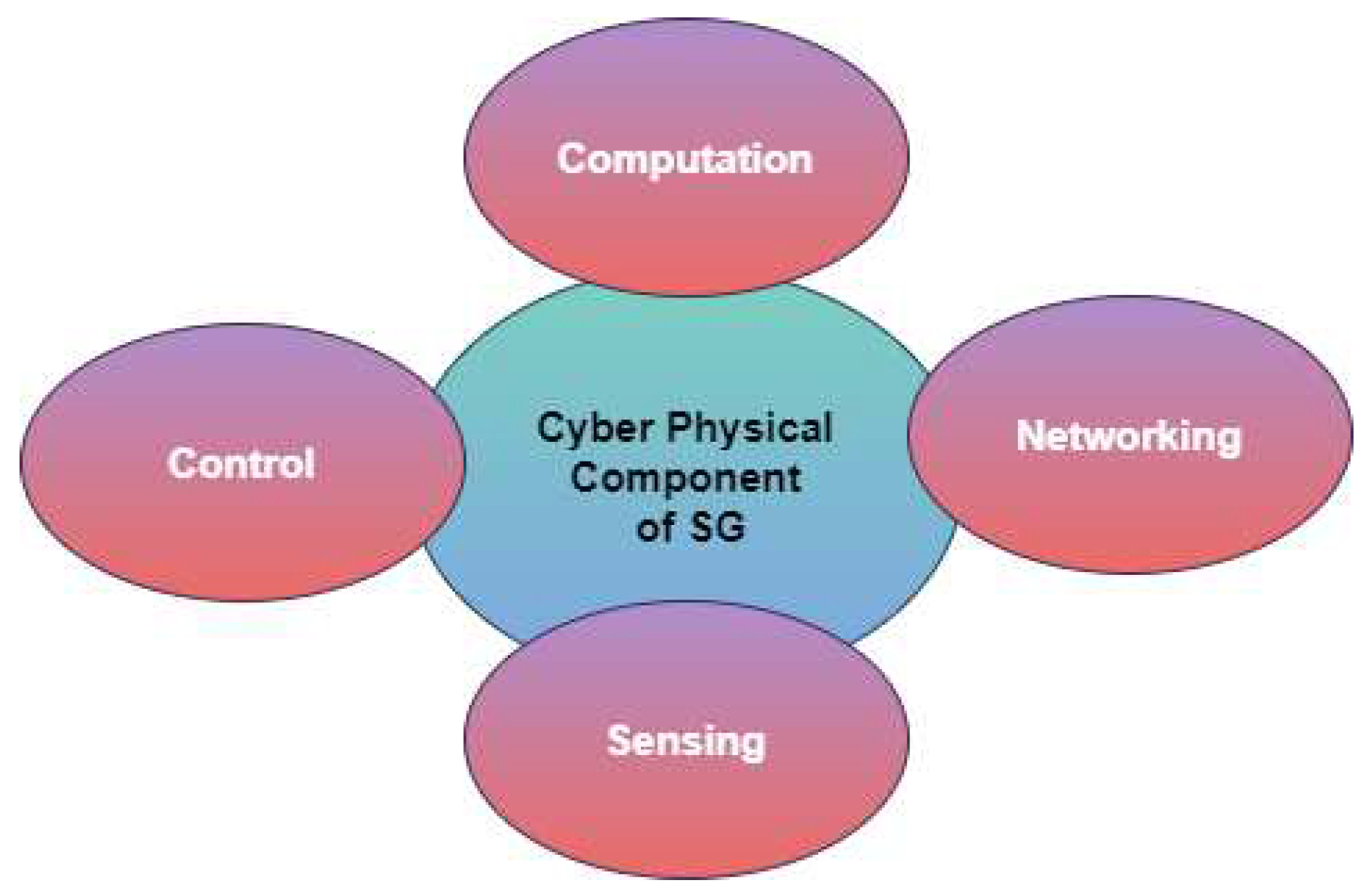
3.2.2. SG Cyber-Physical Vulnerabilities: Communication Network
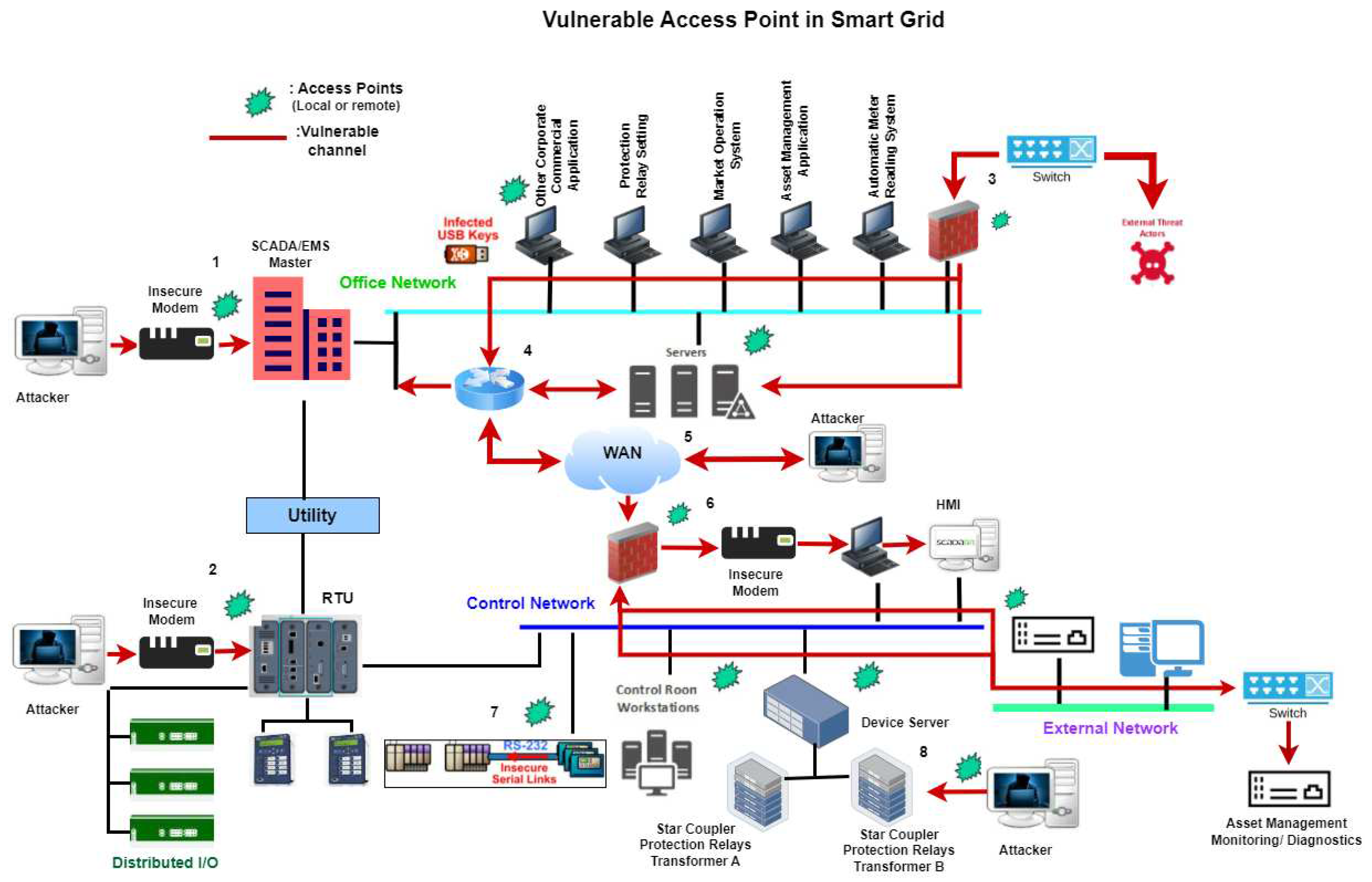
- SG Cyber Vulnerabilities: Protocol Level Integrating Information and Communications Technology (ICT) in a smart grid is extensive and closely connected to the power infrastructure. When combined with a power system, a cyber system creates a full Cyber-Physical System (CPS). Various cyber vulnerabilities, accessed via vulnerable access points shown in Figure 7, can pose security threats to the power system, leading to instability and unreliability of the CPS.
- SG Cyber-physical vulnerabilities: IoT-System
- SG Cyber-physical vulnerabilities: Distributed Energy Resource (DER)
- SG Cyber-physical Vulnerabilities: SM and Advanced Metering Infrastructure (AMI)
3.2.3. SG Vulnerabilities in Load Management
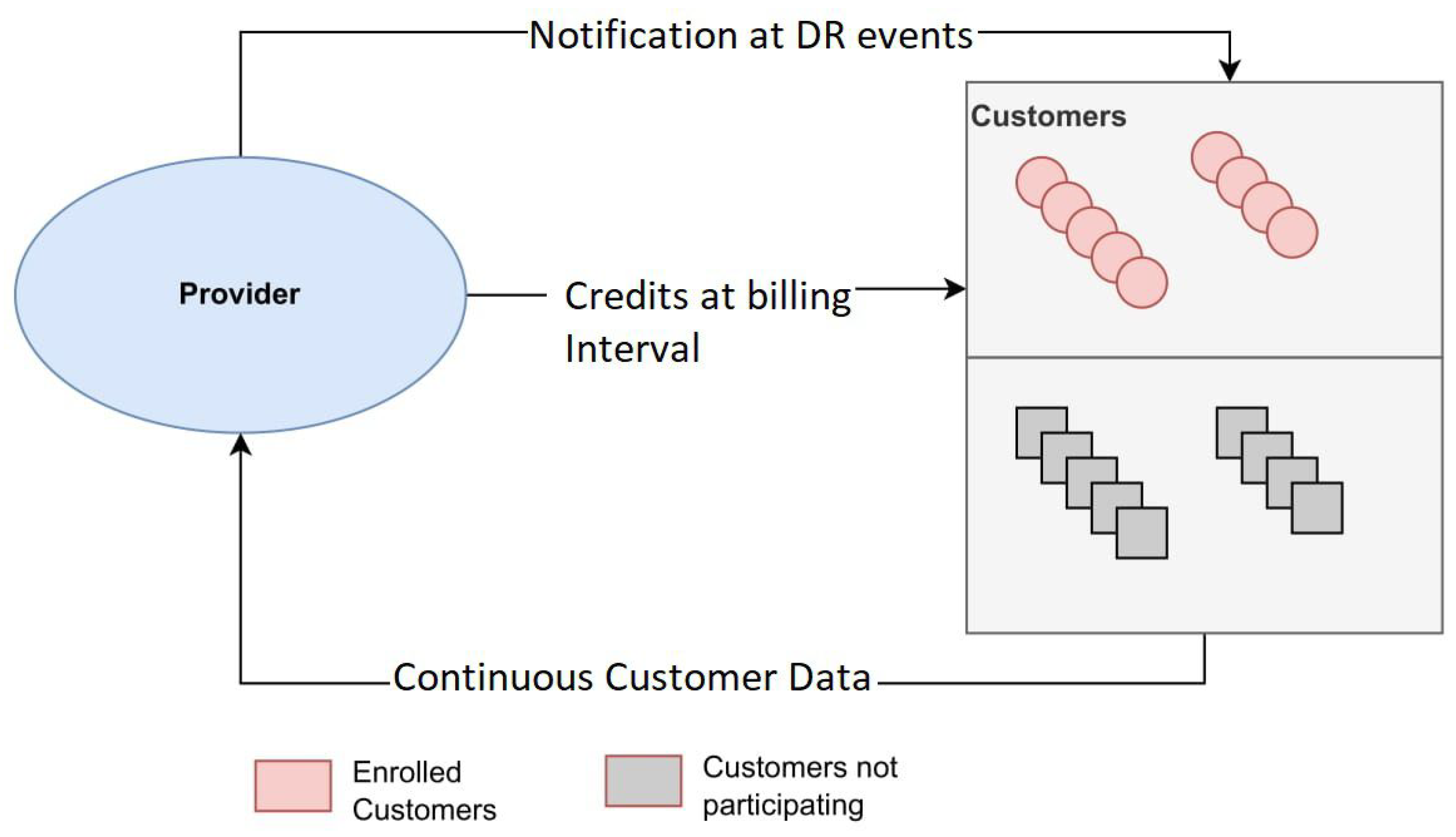
- SG Vulnerabilities in Load Management: Demand response (DR)
- SG Vulnerabilities in Load Management: Load Shedding
- SG Vulnerabilities in Load Management: Load Shifting
3.3. Types of Attack and Threats on Cyber-Physical Systems of the SG
3.4. Vulnerabilities Mitigation Techniques
3.4.1. System Hardening Techniques
- Securing AMI: Advanced metering infrastructures (AMIs) expose the grid to many attack routes and intruders, requiring secure key generation and dissemination. For the security of the AMI network, identity-based cryptography creates secret keys between nearby SMs without contact [75].
- Authentication: Power data tampering in SG communications may complicate demand control. SG device authentication across geographies is crucial. A secure authentication key agreement (AKA) technique may protect SG interaction privacy [76]. This method authenticates SG devices and utilities to create a secret session key. An energy-efficient authentication and key negotiation method for SG scenarios has been developed using Chebyshev polynomial computing [77].
- Machine Learning Approach: Many researchers have used machine learning to detect power theft. For example, a robust deep learning model using GoogleNet and gated recurrent units (GRU) has been developed [78].
- Cryptography and key management: Communication security and privacy are SG systems’ top priorities. Authentication allows users and service providers to connect securely. A biometric SG communication protocol uses elliptic curve (ECC) cryptography for mutual authentication [79]. A lightweight key management protocol uses hash and private keys to encrypt communication and facilitate key agreement [80].
-
Encrypted Tunneling via SSH or IPSEC:Devices must authenticate communication sources and recipients and provide secrecy in their communication. Both IPsec and TLS can provide for authentication and encryption. Likewise, homomorphic encryption can protect power-use data during transmission between SMs [81]. Strong authentication should verify identity. Organizations should utilize explicit access permissions to give network access with an implicit refuse policy. SG parties need a trustworthy authentication procedure for communication. The protocol must be real-time, have low communication and computation overhead, and be attack-resistant, especially against Denial-of-Service assaults. In [79,82], a secure mutual authentication mechanism for SGs was presented using edge computing.
- IPS & IDS: To strengthen host-based defences against both external and internal assaults, network intrusion prevention system (IPS) and network intrusion detection system (IDS) technologies should be used.
- Honeypots & Deception Techniques: Honeypots are used to conceal and defend the cyber-physical system as SG. Honeypots have been designed for CPS, such as networked robotic systems [15]. Simulations show that honeypots can deceive attackers into thinking their attacks work.
- Antivirus Software Validation: Antivirus software protects embedded and general-purpose devices from malware. Software for embedded devices must be manufacturer-approved. Each product must store keying material for software validation. To verify newly downloaded software, the system needs updated antivirus software.
- Human-Centric Mitigation Approaches: Unorganized communication teams frequently function as system attackers. If teams aren’t trained and structured when there are many interested parties, an "insider attack" may occur, resulting in many mistakes and accidental exposure.
- Upgrading Equipment: Older electrical power systems coexist alongside IT system components that are often more frequently replaced. Upgrading old equipment is recommended, as newer gear may not communicate with electrical grid devices or integrate with their security mechanisms.
3.4.2. Detection Techniques
- Anomaly Detection Techniques: Anomaly detection using SG data may be applied in several domains, such as cyber-security, fault detection, and power theft prevention. The unusual aberrant behaviours might have arisen due to several factors, such as peculiar consumption habits of users, malfunctioning grid systems, power outages, foreign cyber-attacks, or energy theft. Lately, identifying irregularities in the smart grid has gained significant attention from researchers and is extensively utilized in several influential domains. An important obstacle in the smart grid is the efficient implementation of anomaly detection for many abnormal behaviours.
- Intrusion Detection Techniques: The intrusion detection system (IDS) is a powerful safeguard and a protection mechanism against various cyber-attacks and threats in the SG system. Typically, IDS detection techniques in the SG system fall into three categories: abnormality-based, specification-based, and signature-based.
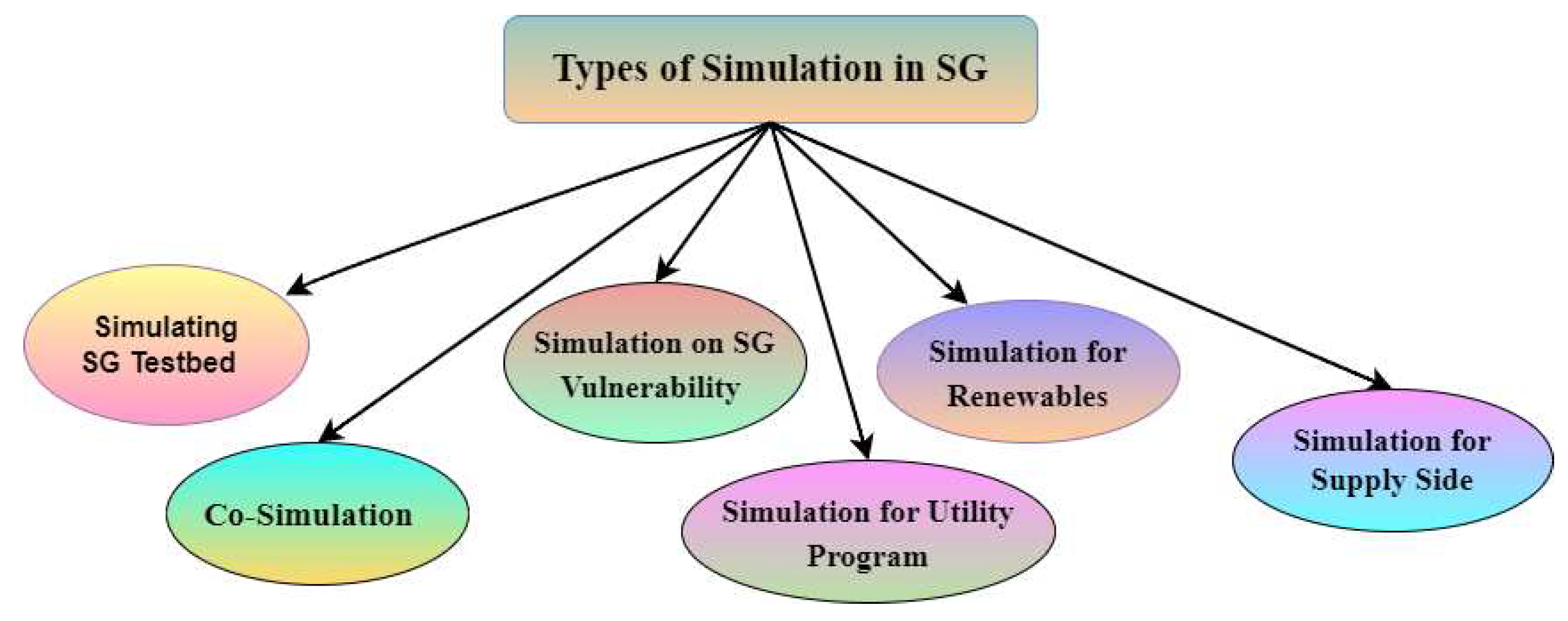
4. Role of Simulation for SG Security
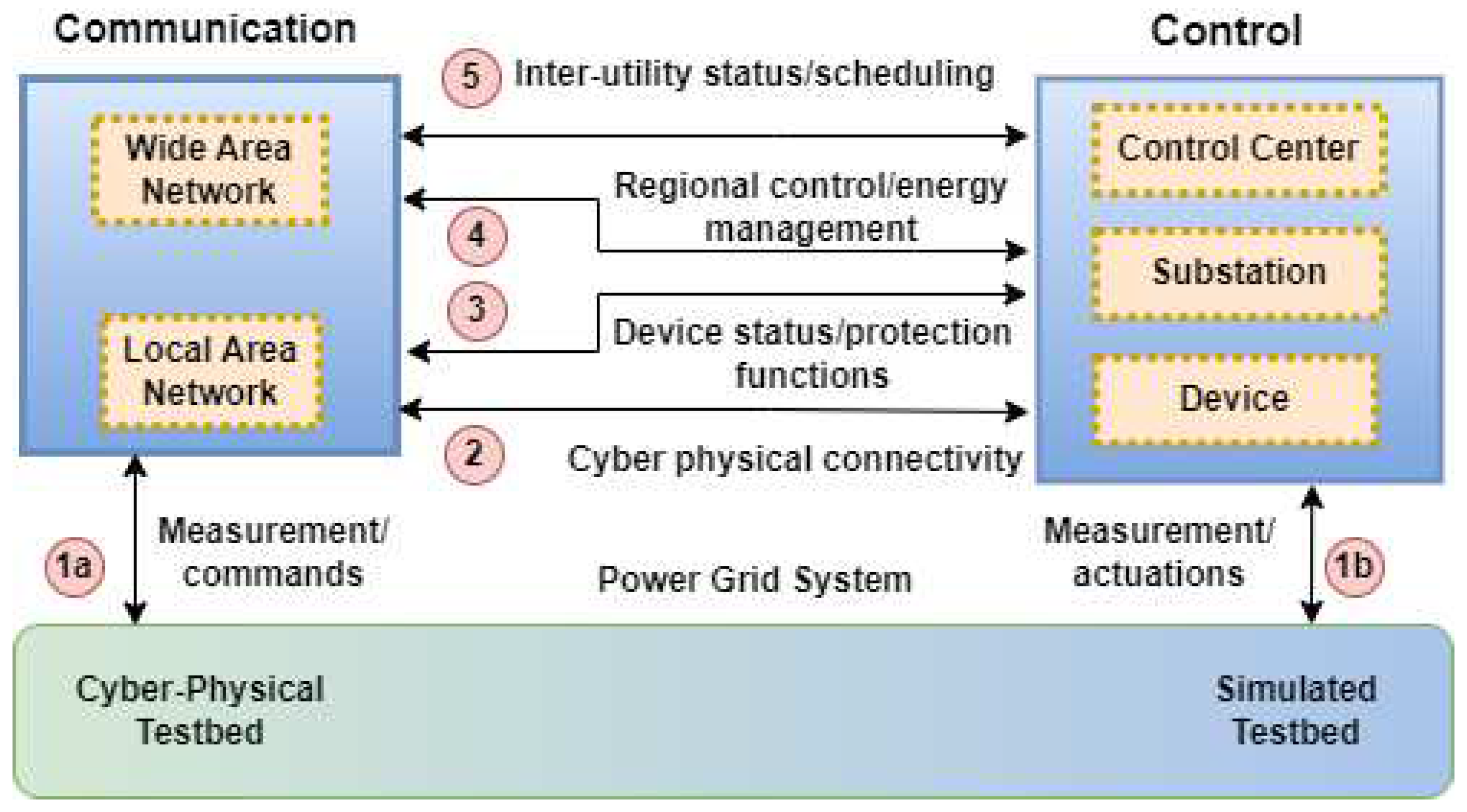
4.1. Testbed: A Simulated Smart Grid
- Software-based Testbeds: The deployment and implementation of these testbeds are thought to be more cost-effective because modelling processes are utilized in place of real devices and information systems. Modelling technologies like Matlab, Modelica, Ptolemy, and PowerWorld simulate real-world ICS operations in many virtual testbeds. In contrast, numerous ICS processes are modelled using software like OPNET, OMNet++, and, most recently, NS3. Low fidelity is a significant drawback to employing virtual devices in the techniques mentioned earlier. Although several attack scenarios have been presented in some recent works based on such software or virtual testbed [128,129], due to the lack of software models for particular devices, they are also limited in their capacity to simulate specific cybersecurity scenarios.
- Hardware-based Testbeds: A network intrusion detection system (NIDS) testbed developed in [130] acts as a bridge between theory and practice by expanding and exploiting "hardware-in-the-loop" and "cyber-in-the-loop" capabilities to detect anomalies in network traffic. Such CPS testbed’s advantages are (1) a large-scale power system’s behaviour can be reasonably simulated using power systems simulation tools like Real-Time Digital Simulator (RTDS), DIgSILENT, PowerWorld, TSAT, and PSS®E; (2) a testbed can be tailored to a specific field of security studies like distribution systems, transmission systems, SCADA systems, and AMI networks; and (3) a testbed can be expanded by connecting multiple testbeds via communications like the Internet and LAN.
- Hybrid Testbeds: The testbed has three distinct physical, cyber, and control layers. Substation hardware, such as Remote Terminal Units (RTUs), a Real-Time Digital Simulator (RTDS), and intelligent electronic devices (IEDs) make up the physical layer. An important piece of the electrical grid smart is the cyber layer. It allows for constant two-way interaction between the substation and the command post. It also improves SG automation in several other ways. New concepts and vulnerabilities must be evaluated, especially for hardware-in-the-loop test platforms [131]. For further research into the security holes in the IEC 61850 protocol and analysis of its possible impact in the context of smart grid connectivity, the authors in [132] have proposed a cyber-physical testbed, using OPAL-RT for HIL. The authors used the testbed to implement a realistic scenario of a power protection system’s components interacting with IEDs.
- Lab-based Testbeds: The goals of the cyber-physical system are achieved through the employment of hardware, software, communication protocols, and many forms of media. Construction of a testbed can be a considerable undertaking at a significant expense. Labs allow access to constructed testbeds to a wider audience. Such labs give researchers a new way to evaluate the tangible effects of various hacks on SG systems without having to recreate the testbed. Two types of labs with testbeds exist to study and analyze SG security: 1) National Level Testbed labs and 2) Testbed labs at Research Institutes. For instance, the ISAAC is an adaptive testbed designed by the University of Idaho CPS SCADA Cybersecurity [133] in a natural automation controller environment to investigate and observe the impact of prospective cyberattacks and evaluate novel cybersecurity solutions on the SG. The PowerCyber testbed was built at Iowa State University [134] with the architecture, applications, and novel capabilities like virtualization, Real-Time Digital Simulators (RTDS), and ISEAGE WAN emulation to evaluate the availability and integrity of attack scenarios and explore cyber-physical consequences. Lab testing methods for today’s electrical power systems use state-of-the-art co-simulation, Power hardware-in-the-loop, controller hardware-in-the-loop, and real-time simulation technologies. These methods expedite studying electrical systems and power electronics components by approving technological solutions in high-fidelity environments [135]. In this paper, experts from the Survey of Smart Grid International Research Facility Network’s task on advanced laboratory testing methods discuss their methods, procedures, studies, and experiences applying them to test various prototypes and new power system solutions for R&D.
4.2. Co-Simulation
4.3. Simulation on SG Vulnerability
4.4. SG Simulation for Load Management
4.5. SG Simulation for Renewable Energy Sources
4.6. SG Simulation for the Demand Side
5. Research Gap Analysis and Recommendation
- Policy design: A complete investigation needs to be done to formalize the policies for integrating security in the Smart Grid. These policies must be tailored for the various subsystems in the smart grid and integrated into the SG. For example, AMI has well-known security policies, such as the authentication requirement of key pair access. However, we have found no formal attempt to integrate the policies of various security components into an integrated, cohesive whole, nor have we found any attempt to integrate security policy management into SG simulation for testing and validation.
- Policy instancing: Additionally, tools must be developed to support policy implementation into SG simulation. Such tools should include libraries for commonly implemented security algorithms and protocols that are easy to integrate into the simulation, with support for HIL and co-simulation. Likewise, support for instancing policy with mechanisms should be included to test the various ways to enforce the security policies.
- Security Vulnerability Analysis and Testing support: SG simulation tools that support security testing should support enacting real-world attacks on the SG simulation, both at the device and network levels. Likewise, simulations should include tools that provide a component-by-component and holistic investigation of the effectiveness of the attack on targeted system vulnerabilities. For example, what would be the overall effect on the grid if a MODBUS write register attack occurred on a specific number of meters? Additional tools that indicate possible mitigation techniques would be useful. Furthermore, methods for generating synthetic data should be augmented with methods for integrating synthetic attack data needed to drive the simulation scenarios for vulnerability testing. The synthetic attack data must represent real-world attacks and must represent realistic attack frequency and severity.
6. Conclusions and Future works
Abbreviations
| AMI | Advanced Metering Infrastructure |
| SM | Smart Meter |
| CA | Cyber-attacks |
| DER | Distribute energy resources |
| DR | Demand response |
| IoT | Internet of Things |
| FDIA | False data injection attack |
| DoS | Denial of Service |
| ICT | Information and communication technologies |
| SG | Smart Grid |
| GEB | Grid-interactive Efficient Buildings |
| MiTM | Man-in-the-Middle |
| NIST | National Institute of Standards and Technology |
| SCADA | Supervisory Control and Data Acquisition |
| CIA | Confidentiality, Integrity, and Availability |
| CPS | Cyber-physic system |
| IDS | Intrusion detection system |
| DSM | Demand side management |
| DNP3 | Distributed network protocol version 3.0 |
| APT | Advanced Persistent Threat |
| CP-SG | Cyber-Physical-Smart-Grid |
| NIDS | Network Intrusion Detection System |
| ICS | Industrial Control System |
| IED | Intelligent Electronic Device |
| HIL | Hardware-in-the-loop |
| CF | Cascading failure |
References
- Smith, M.; Ton, D. Key connections: The us department of energy? s microgrid initiative. IEEE Power and Energy magazine 2013, 11, 22–27. [Google Scholar] [CrossRef]
- Mikalauskas, I. Economic, Social and Environmental Benefits of Smart Grids. European Journal of Interdisciplinary Studies 2015, 7. [Google Scholar]
- Gopstein, A.; Nguyen, C.; O’Fallon, C.; Hastings, N.; Wollman, D.; others. NIST framework and roadmap for smart grid interoperability standards, release 4.0; Department of Commerce. National Institute of Standards and Technology …, 2021.
- Chhaya, L.; Sharma, P.; Bhagwatikar, G.; Kumar, A. Wireless sensor network based smart grid communications: Cyber attacks, intrusion detection system and topology control. Electronics 2017, 6, 5. [Google Scholar] [CrossRef]
- Case, D.U. Analysis of the cyber attack on the Ukrainian power grid. Electricity Information Sharing and Analysis Center (E-ISAC) 2016, 388, 1–29. [Google Scholar]
- GICSP, E.H.; Assante, M.; Conway, T. An abbreviated history of automation & industrial controls systems and cybersecurity. SANS Institute, Tech. Rep. 2014.
- Kure, H.I.; Islam, S.; Razzaque, M.A. An integrated cyber security risk management approach for a cyber-physical system. Applied Sciences 2018, 8, 898. [Google Scholar] [CrossRef]
- Otuoze, A.O.; Mustafa, M.W.; Larik, R.M. Smart grids security challenges: Classification by sources of threats. Journal of Electrical Systems and Information Technology 2018, 5, 468–483. [Google Scholar] [CrossRef]
- Yu, X.; Xue, Y. Smart grids: A cyber–physical systems perspective. Proceedings of the IEEE 2016, 104, 1058–1070. [Google Scholar] [CrossRef]
- Ghansah, I. Smart grid cyber security potential threats, vulnerabilities and risks: Interim project report; California Energy Commission, 2012.
- Sun, C.C.; Liu, C.C.; Xie, J. Cyber-physical system security of a power grid: State-of-the-art. Electronics 2016, 5, 40. [Google Scholar] [CrossRef]
- Colak, I.; Sagiroglu, S.; Fulli, G.; Yesilbudak, M.; Covrig, C.F. A survey on the critical issues in smart grid technologies. Renewable and Sustainable Energy Reviews 2016, 54, 396–405. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A. s. Renewable and Sustainable Energy Reviews 2022, 163, 112423.
- Niu, X.; Li, J.; Sun, J.; Tomsovic, K. Dynamic detection of false data injection attack in smart grid using deep learning. 2019 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT). IEEE, 2019, pp. 1–6.
- Yaacoub, J.P.A.; Salman, O.; Noura, H.N.; Kaaniche, N.; Chehab, A.; Malli, M. Cyber-physical systems security: Limitations, issues and future trends. Microprocessors and microsystems 2020, 77, 103201. [Google Scholar] [CrossRef] [PubMed]
- Chen, J.; Mohamed, M.A.; Dampage, U.; Rezaei, M.; Salmen, S.H.; Obaid, S.A.; Annuk, A. A multi-layer security scheme for mitigating smart grid vulnerability against faults and cyber-attacks. Applied Sciences 2021, 11, 9972. [Google Scholar] [CrossRef]
- Pandey, R.K.; Misra, M. Cyber security threats—Smart grid infrastructure. 2016 National power systems conference (NPSC). IEEE, 2016, pp. 1–6.
- Ackerman, P. Industrial Cybersecurity: Efficiently secure critical infrastructure systems; Packt Publishing Ltd, 2017.
- Krebs, B.; FBI: Smart meter hacks likely to spread. Krebs on Security. 2012. Available online: http://krebsonsecurity. com/2012/04/fbi-smart-meter-hacks-likely-to-spread/ (accessed on 25 April 2012).
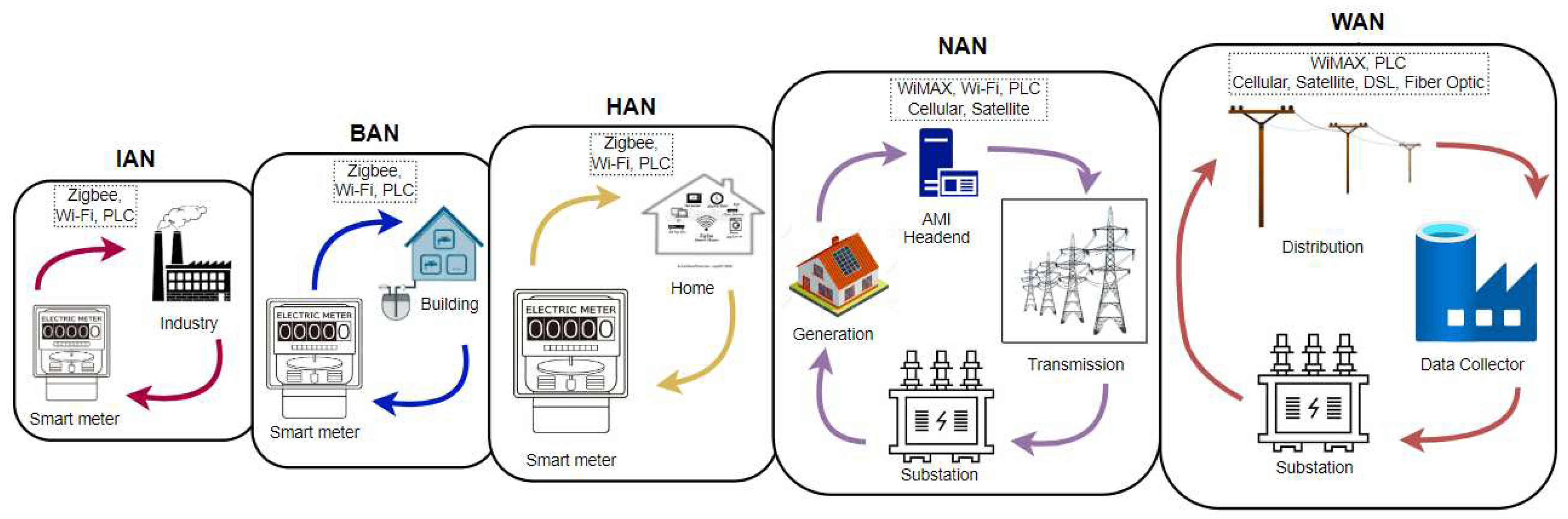
- Kuzlu, M.; Pipattanasomporn, M.; Rahman, S. Communication network requirements for major smart grid applications in HAN, NAN and WAN. Computer Networks 2014, 67, 74–88. [Google Scholar] [CrossRef]
- Islam, S.N.; Baig, Z.; Zeadally, S. Physical layer security for the smart grid: Vulnerabilities, threats, and countermeasures. IEEE Transactions on Industrial Informatics 2019, 15, 6522–6530. [Google Scholar] [CrossRef]
- Khoei, T.T.; Slimane, H.O.; Kaabouch, N. Cyber-Security of Smart Grids: Attacks, Detection, Countermeasure Techniques, and Future Directions. Communications and Network 2022, 14, 119–170. [Google Scholar]
- Baig, Z.A.; Amoudi, A.R. An Analysis of Smart Grid Attacks and Countermeasures. J. Commun. 2013, 8, 473–479. [Google Scholar] [CrossRef]
- Batalla, J.M.; Vasilakos, A.; Gajewski, M. Secure smart homes: Opportunities and challenges. ACM Computing Surveys (CSUR) 2017, 50, 1–32. [Google Scholar] [CrossRef]
- Efstathopoulos, G.; Grammatikis, P.R.; Sarigiannidis, P.; Argyriou, V.; Sarigiannidis, A.; Stamatakis, K.; Angelopoulos, M.K.; Athanasopoulos, S.K. Operational data based intrusion detection system for smart grid. 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD). IEEE, 2019, pp. 1–6.
- El Mrabet, Z.; Kaabouch, N.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Computers & Electrical Engineering 2018, 67, 469–482. [Google Scholar] [CrossRef]
- Chen, B.; Pattanaik, N.; Goulart, A.; Butler-Purry, K.L.; Kundur, D. Implementing attacks for modbus/TCP protocol in a real-time cyber physical system test bed. 2015 IEEE International Workshop Technical Committee on Communications Quality and Reliability (CQR). IEEE, 2015, pp. 1–6.
- Bashendy, M.; Eltanbouly, S.; Tantawy, A.; Erradi, A. Design and implementation of cyber-physical attacks on modbus/tcp protocol. World Congress on Industrial Control Systems Security (WCICSS-2020), 2020.
- Radoglou-Grammatikis, P.; Siniosoglou, I.; Liatifis, T.; Kourouniadis, A.; Rompolos, K.; Sarigiannidis, P. Implementation and detection of modbus cyberattacks. 2020 9th International Conference on Modern Circuits and Systems Technologies (MOCAST). IEEE, 2020, pp. 1–4.
- Darwish, I.; Igbe, O.; Saadawi, T. Experimental and theoretical modeling of DNP3 attacks in smart grids. 2015 36th IEEE Sarnoff Symposium. IEEE, 2015, pp. 155–160.
- Tightiz, L.; Yang, H. A comprehensive review on IoT protocols’ features in smart grid communication. Energies 2020, 13, 2762. [Google Scholar] [CrossRef]
- Pliatsios, D.; Sarigiannidis, P.; Lagkas, T.; Sarigiannidis, A.G. A survey on SCADA systems: secure protocols, incidents, threats and tactics. IEEE Communications Surveys & Tutorials 2020, 22, 1942–1976. [Google Scholar] [CrossRef]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Communications Surveys & Tutorials 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Kumar, N.M.; Chand, A.A.; Malvoni, M.; Prasad, K.A.; Mamun, K.A.; Islam, F.; Chopra, S.S. Distributed energy resources and the application of AI, IoT, and blockchain in smart grids. Energies 2020, 13, 5739. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Hatziargyriou, N.D.; Konstantinou, C. Distributed energy resources cybersecurity outlook: Vulnerabilities, attacks, impacts, and mitigations. IEEE Systems Journal 2023. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Computer networks 2020, 169, 107094. [Google Scholar] [CrossRef]
- Naderi, E.; Pazouki, S.; Asrari, A. A coordinated cyberattack targeting load centers and renewable distributed energy resources for undervoltage/overvoltage in the most vulnerable regions of a modern distribution system. Sustainable Cities and Society 2023, 88, 104276. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Konstantinou, C.; Hatziargyriou, N.D. Distributed energy resources cybersecurity outlook: Vulnerabilities, attacks, impacts, and mitigations. arXiv preprint arXiv:2205.11171 2022.
- Pazouki, S.; Naderi, E.; Asrari, A. A remedial action framework against cyberattacks targeting energy hubs integrated with distributed energy resources. Applied Energy 2021, 304, 117895. [Google Scholar] [CrossRef]
- Xu, S.; Tu, H.; Xia, Y. Resilience enhancement of renewable cyber–physical power system against malware attacks. Reliability Engineering & System Safety 2023, 229, 108830. [Google Scholar] [CrossRef]
- Tuyen, N.D.; Quan, N.S.; Linh, V.B.; Van Tuyen, V.; Fujita, G. A comprehensive review of cybersecurity in inverter-based smart power system amid the boom of renewable energy. IEEE Access 2022, 10, 35846–35875. [Google Scholar] [CrossRef]
- Ma, R.; Chen, H.H.; Huang, Y.R.; Meng, W. Smart grid communication: Its challenges and opportunities. IEEE transactions on Smart Grid 2013, 4, 36–46. [Google Scholar] [CrossRef]
- Santamarta, R. Here be backdoors: A journey into the secrets of industrial firmware. Black Hat USA 2012. [Google Scholar]
- Takiddin, A.; Ismail, M.; Nabil, M.; Mahmoud, M.M.; Serpedin, E. Detecting electricity theft cyber-attacks in AMI networks using deep vector embeddings. IEEE Systems Journal 2020, 15, 4189–4198. [Google Scholar] [CrossRef]
- Yao, J.; Venkitasubramaniam, P.; Kishore, S.; Snyder, L.V.; Blum, R.S. Network topology risk assessment of stealthy cyber attacks on advanced metering infrastructure networks. 2017 51st Annual Conference on Information Sciences and Systems (CISS). IEEE, 2017, pp. 1–6.
- Murrill, B.J.; Liu, E.C.; Thompson, R.M. Smart meter data: Privacy and cybersecurity. Congressional Research Service, Library of Congress, 2012.
- Ünal, F.; Almalaq, A.; Ekici, S.; Glauner, P. Big data-driven detection of false data injection attacks in smart meters. IEEE Access 2021, 9, 144313–144326. [Google Scholar] [CrossRef]
- Giaconi, G.; Gunduz, D.; Poor, H.V. Smart meter data privacy. arXiv preprint arXiv:2009.01364 2020. arXiv:2009.01364 2020.
- Shoreh, M.H.; Siano, P.; Shafie-khah, M.; Loia, V.; Catalão, J.P. A survey of industrial applications of Demand Response. Electric Power Systems Research 2016, 141, 31–49. [Google Scholar] [CrossRef]
- Fan, S.; Li, Z.; Yang, L.; He, G. Customer directrix load-based large-scale demand response for integrating renewable energy sources. Electric Power Systems Research 2020, 181, 106175. [Google Scholar] [CrossRef]
- Chen, Y.; Xu, P.; Gu, J.; Schmidt, F.; Li, W. Measures to improve energy demand flexibility in buildings for demand response (DR): A review. Energy and Buildings 2018, 177, 125–139. [Google Scholar] [CrossRef]
- Iqbal, S.; Sarfraz, M.; Ayyub, M.; Tariq, M.; Chakrabortty, R.K.; Ryan, M.J.; Alamri, B. A comprehensive review on residential demand side management strategies in smart grid environment. Sustainability 2021, 13, 7170. [Google Scholar] [CrossRef]
- Tang, D.; Fang, Y.P.; Zio, E. Vulnerability analysis of demand-response with renewable energy integration in smart grids to cyber attacks and online detection methods. Reliability Engineering & System Safety 2023, 235, 109212. [Google Scholar] [CrossRef]
- Sperstad, I.B.; Kjølle, G.H.; Gjerde, O. A comprehensive framework for vulnerability analysis of extraordinary events in power systems. Reliability Engineering & System Safety 2020, 196, 106788. [Google Scholar] [CrossRef]
- Abedi, A.; Gaudard, L.; Romerio, F. Review of major approaches to analyze vulnerability in power system. Reliability engineering & System safety 2019, 183, 153–172. [Google Scholar] [CrossRef]
- Anuebunwa, U.R.; Rajamani, H.S.; Abd-Alhameed, R.; Pillai, P. Investigating the impacts of cyber-attacks on pricing data of home energy management systems in demand response programs. 2018 IEEE Power & Energy Society General Meeting (PESGM). IEEE, 2018, pp. 1–5.
- Heussen, K.; Tyge, E.; Kosek, A.M. Residential demand response behaviour modeling applied to cyber-physical intrusion detection. 2017 IEEE Manchester PowerTech. IEEE, 2017, pp. 1–6.
- Manicavasagam, R.; Palmer, A.; Rogers, M.; Mahajan, S.; Craven, R.; Emeghara, C.; Senz, R. Testbed for Evaluating and Analyzing Smart Grid Behavior in Demand Response Scenarios. 2022 14th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT). IEEE, 2022, pp. 122–127.
- Su, Q.; Li, S.; Gao, Y.; Huang, X.; Li, J. Observer-based detection and reconstruction of dynamic load altering attack in smart grid. Journal of the Franklin Institute 2021, 358, 4013–4027. [Google Scholar] [CrossRef]
- Yan, J.; Guo, F.; Wen, C. Attack detection and isolation for distributed load shedding algorithm in microgrid systems. IEEE Journal of Emerging and Selected Topics in Industrial Electronics 2020, 1, 102–110. [Google Scholar] [CrossRef]
- Khalaf, M.; Ayad, A.; Salama, M.M.; Kundur, D.; El-Saadany, E.F. Mitigation of Cyber-attacks on Wide-Area Under-Frequency Load-Shedding Schemes. IEEE Transactions on Smart Grid 2022. [CrossRef]
- Pilz, M.; Naeini, F.B.; Grammont, K.; Smagghe, C.; Davis, M.; Nebel, J.C.; Al-Fagih, L.; Pfluegel, E. Security attacks on smart grid scheduling and their defences: a game-theoretic approach. International Journal of Information Security 2020, 19, 427–443. [Google Scholar] [CrossRef]
- Praveen, M.; Rao, G.S. Ensuring the reduction in peak load demands based on load shifting DSM strategy for smart grid applications. Procedia Computer Science 2020, 167, 2599–2605. [Google Scholar] [CrossRef]
- Jamil, M.; Mittal, S. Hourly load shifting approach for demand side management in smart grid using grasshopper optimisation algorithm. IET Generation, Transmission & Distribution 2020, 14, 808–815. [Google Scholar] [CrossRef]
- Zeeshan, M.; Jamil, M. Adaptive moth flame optimization based load shifting technique for demand side management in smart grid. IETE Journal of Research 2022, 68, 778–789. [Google Scholar] [CrossRef]
- Nasir, T.; Bukhari, S.S.H.; Raza, S.; Munir, H.M.; Abrar, M.; Muqeet, H.A.u.; Bhatti, K.L.; Ro, J.S.; Masroor, R. Recent challenges and methodologies in smart grid demand side management: State-of-the-art literature review. Mathematical Problems in Engineering 2021, 2021, 1–16. [Google Scholar] [CrossRef]
- Abdelsalam, A.A.; Zedan, H.A.; ElDesouky, A.A. Energy management of microgrids using load shifting and multi-agent system. Journal of Control, Automation and Electrical Systems 2020, 31, 1015–1036. [Google Scholar] [CrossRef]
- Logenthiran, T.; Srinivasan, D.; Vanessa, K. Demand side management of smart grid: Load shifting and incentives. Journal of Renewable and Sustainable Energy 2014, 6, 033136. [Google Scholar] [CrossRef]
- Youssef, E.N.S.; Labeau, F.; Kassouf, M. Detection of Load-Altering Cyberattacks Targeting Peak Shaving Using Residential Electric Water Heaters. Energies 2022, 15. [Google Scholar] [CrossRef]
- Amini, S.; Pasqualetti, F.; Mohsenian-Rad, H. Dynamic Load Altering Attacks Against Power System Stability: Attack Models and Protection Schemes. IEEE Transactions on Smart Grid 2018, 9, 2862–2872. [Google Scholar] [CrossRef]
- Dabrowski, A.; Ullrich, J.; Weippl, E. Grid Shock: Coordinated Load-Changing Attacks on Power Grids: The Non-Smart Power Grid is Vulnerable to Cyber Attacks as Well. 2017, pp. 303–314. [CrossRef]
- Cui, P.; Feng, L.; Xun, P.; Zhu, P. Load Scheduling of Thermostatical House-Hold Appliances Against Abrupt Changes in Smart Grid. 2017 10th International Symposium on Computational Intelligence and Design (ISCID), 2017, Vol. 1, pp. 470–475. [CrossRef]
- Delgado-Gomes, V.; Martins, J.F.; Lima, C.; Borza, P.N. Smart grid security issues. 2015 9th International conference on compatibility and power electronics (CPE). IEEE, 2015, pp. 534–538.
- Kwon, Y.; Kim, H.K.; Koumadi, K.M.; Lim, Y.H.; Lim, J.I. Automated vulnerability analysis technique for smart grid infrastructure. 2017 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT). IEEE, 2017, pp. 1–5.
- Seferian, V.; Kanj, R.; Chehab, A.; Kayssi, A. Identity based key distribution framework for link layer security of AMI networks. IEEE Transactions on Smart Grid 2016, 9, 3166–3179. [Google Scholar] [CrossRef]
- Xiang, X.; Cao, J. An efficient authenticated key agreement scheme supporting privacy-preservation for smart grid communication. Electric Power Systems Research 2022, 203, 107630. [Google Scholar] [CrossRef]
- Zhang, L.; Zhu, Y.; Ren, W.; Wang, Y.; Choo, K.K.R.; Xiong, N.N. An energy-efficient authentication scheme based on Chebyshev chaotic map for smart grid environments. IEEE Internet of Things Journal 2021, 8, 17120–17130. [Google Scholar] [CrossRef]
- Shehzad, F.; Javaid, N.; Almogren, A.; Ahmed, A.; Gulfam, S.M.; Radwan, A. A robust hybrid deep learning model for detection of non-technical losses to secure smart grids. IEEE Access 2021, 9, 128663–128678. [Google Scholar] [CrossRef]
- Khan, A.A.; Kumar, V.; Ahmad, M. An elliptic curve cryptography based mutual authentication scheme for smart grid communications using biometric approach. Journal of King Saud University-Computer and Information Sciences 2022, 34, 698–705. [Google Scholar] [CrossRef]
- Moghadam, M.F.; Nikooghadam, M.; Mohajerzadeh, A.H.; Movali, B. A lightweight key management protocol for secure communication in smart grids. Electric Power Systems Research 2020, 178, 106024. [Google Scholar] [CrossRef]
- Deepak, K.; Chandrasekaran, K. Investigating elliptic curve cryptography for securing smart grid environments. 2020 Third ISEA Conference on Security and Privacy (ISEA-ISAP). IEEE, 2020, pp. 1–7.
- Chen, C.M.; Chen, L.; Huang, Y.; Kumar, S.; Wu, J.M.T. Lightweight authentication protocol in edge-based smart grid environment. EURASIP Journal on Wireless Communications and Networking 2021, 2021, 1–18. [Google Scholar] [CrossRef]
- Gopstein, A.; Hastings, N.; Feldman, L.; Agarwal, R.; Bartol, N. Distributed Energy Resource Security: Potential Guidelines and Research Topics 2021.
- Pour, M.M.; Anzalchi, A.; Sarwat, A. A review on cyber security issues and mitigation methods in smart grid systems. SoutheastCon 2017 2017, pp. 1–4.
- Tufail, S.; Parvez, I.; Batool, S.; Sarwat, A. A survey on cybersecurity challenges, detection, and mitigation techniques for the smart grid. Energies 2021, 14, 5894. [Google Scholar] [CrossRef]
- Ghafouri, M.; Au, M.; Kassouf, M.; Debbabi, M.; Assi, C.; Yan, J. Detection and mitigation of cyber attacks on voltage stability monitoring of smart grids. IEEE Transactions on Smart Grid 2020, 11, 5227–5238. [Google Scholar] [CrossRef]
- Karimipour, H.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R.; Leung, H. A deep and scalable unsupervised machine learning system for cyber-attack detection in large-scale smart grids. IEEE Access 2019, 7, 80778–80788. [Google Scholar] [CrossRef]
- Yılmaz, Y.; Uludag, S. Timely detection and mitigation of IoT-based cyberattacks in the smart grid. Journal of the Franklin Institute 2021, 358, 172–192. [Google Scholar] [CrossRef]
- Shahinzadeh, H.; Mahmoudi, A.; Moradi, J.; Nafisi, H.; Kabalci, E.; Benbouzid, M. Anomaly detection and resilience-oriented countermeasures against cyberattacks in smart grids. 2021 7th International Conference on Signal Processing and Intelligent Systems (ICSPIS). IEEE, 2021, pp. 1–7.
- Panthi, M. Anomaly detection in smart grids using machine learning techniques. 2020 First International Conference on Power, Control and Computing Technologies (ICPC2T). IEEE, 2020, pp. 220–222.
- Liu, X.; Nielsen, P.S. Regression-based online anomaly detection for smart grid data. arXiv preprint arXiv:1606.05781 2016.
- Himeur, Y.; Ghanem, K.; Alsalemi, A.; Bensaali, F.; Amira, A. Artificial intelligence based anomaly detection of energy consumption in buildings: A review, current trends and new perspectives. Applied Energy 2021, 287, 116601. [Google Scholar] [CrossRef]
- Feng, C.; Li, T.; Chana, D. Multi-level anomaly detection in industrial control systems via package signatures and LSTM networks. 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). IEEE, 2017, pp. 261–272.
- Fengming, Z.; Shufang, L.; Zhimin, G.; Bo, W.; Shiming, T.; Mingming, P. Anomaly detection in smart grid based on encoder-decoder framework with recurrent neural network. The journal of china universities of Posts and Telecommunications 2017, 24, 67–73. [Google Scholar] [CrossRef]
- Zhang, J.E.; Wu, D.; Boulet, B. Time series anomaly detection for smart grids: A survey. 2021 IEEE Electrical Power and Energy Conference (EPEC). IEEE, 2021, pp. 125–130.
- Hyndman, R.J.; Wang, E.; Laptev, N. Large-scale unusual time series detection. 2015 IEEE international conference on data mining workshop (ICDMW). IEEE, 2015, pp. 1616–1619.
- Zhang, L.; Shen, X.; Zhang, F.; Ren, M.; Ge, B.; Li, B. Anomaly detection for power grid based on time series model. 2019 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC). IEEE, 2019, pp. 188–192.
- Wei, Q.; Ma, R.; Wang, Y.; Chen, M.; Sun, Y.; Liu, M.; Lin, X. Glad: A method of microgrid anomaly detection based on esd in smart power grid. 2020 IEEE International Conference on Power, Intelligent Computing and Systems (ICPICS). IEEE, 2020, pp. 103–107.
- Gaddam, A.; Wilkin, T.; Angelova, M. Anomaly detection models for detecting sensor faults and outliers in the IoT-a survey. 2019 13th International Conference on Sensing Technology (ICST). IEEE, 2019, pp. 1–6.
- Erhan, L.; Ndubuaku, M.; Di Mauro, M.; Song, W.; Chen, M.; Fortino, G.; Bagdasar, O.; Liotta, A. Smart anomaly detection in sensor systems: A multi-perspective review. Information Fusion 2021, 67, 64–79. [Google Scholar] [CrossRef]
- Marino, D.L.; Wickramasinghe, C.S.; Amarasinghe, K.; Challa, H.; Richardson, P.; Jillepalli, A.A.; Johnson, B.K.; Rieger, C.; Manic, M. Cyber and physical anomaly detection in smart-grids. 2019 Resilience Week (RWS). IEEE, 2019, Vol. 1, pp. 187–193.
- Liu, X.; Nielsen, P.S. Scalable prediction-based online anomaly detection for smart meter data. Information Systems 2018, 77, 34–47. [Google Scholar] [CrossRef]
- Yuan, Y.; Jia, K. A distributed anomaly detection method of operation energy consumption using smart meter data. 2015 international conference on intelligent information hiding and multimedia signal processing (IIH-MSP). IEEE, 2015, pp. 310–313.
- Jaiswal, R.; Maatug, F.; Davidrajuh, R.; Rong, C. Anomaly detection in smart meter data for preventing potential smart grid imbalance. 2021 4th Artificial Intelligence and Cloud Computing Conference, 2021, pp. 150–159.
- Yen, S.W.; Morris, S.; Ezra, M.A.; Huat, T.J. Effect of smart meter data collection frequency in an early detection of shorter-duration voltage anomalies in smart grids. International journal of electrical power & energy systems 2019, 109, 1–8. [Google Scholar] [CrossRef]
- Rossi, B.; Chren, S.; Buhnova, B.; Pitner, T. Anomaly detection in smart grid data: An experience report. 2016 ieee international conference on systems, man, and cybernetics (smc). IEEE, 2016, pp. 002313–002318.
- Banik, S.; Saha, S.K.; Banik, T.; Hossain, S.M. Anomaly Detection Techniques in Smart Grid Systems: A Review. 2023 IEEE World AI IoT Congress (AIIoT). IEEE, 2023, pp. 0331–0337.
- Feng, L.; Xu, S.; Zhang, L.; Wu, J.; Zhang, J.; Chu, C.; Wang, Z.; Shi, H. Anomaly detection for electricity consumption in cloud computing: framework, methods, applications, and challenges. EURASIP Journal on Wireless Communications and Networking 2020, 2020, 1–12. [Google Scholar] [CrossRef]
- El-Awadi, R.; Fernández-Vilas, A.; Redondo, R.P.D. Fog computing solution for distributed anomaly detection in smart grids. 2019 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob). IEEE, 2019, pp. 348–353.
- Jaiswal, R.; Chakravorty, A.; Rong, C. Distributed fog computing architecture for real-time anomaly detection in smart meter data. 2020 IEEE sixth international conference on big data computing service and applications (BigDataService). IEEE, 2020, pp. 1–8.
- Radoglou Grammatikis, P.; Sarigiannidis, P.; Efstathopoulos, G.; Panaousis, E. ARIES: A novel multivariate intrusion detection system for smart grid. Sensors 2020, 20, 5305. [Google Scholar] [CrossRef]
- Mitchell, R.; Chen, R. Behavior-rule based intrusion detection systems for safety critical smart grid applications. IEEE Transactions on Smart Grid 2013, 4, 1254–1263. [Google Scholar] [CrossRef]
- Karimipour, H.; Geris, S.; Dehghantanha, A.; Leung, H. Intelligent anomaly detection for large-scale smart grids. 2019 IEEE Canadian conference of electrical and computer engineering (CCECE). IEEE, 2019, pp. 1–4.
- Hong, J.; Liu, C.C.; Govindarasu, M. Detection of cyber intrusions using network-based multicast messages for substation automation. ISGT 2014. IEEE, 2014, pp. 1–5.
- Yang, Y.; Xu, H.Q.; Gao, L.; Yuan, Y.B.; McLaughlin, K.; Sezer, S. Multidimensional intrusion detection system for IEC 61850-based SCADA networks. IEEE Transactions on Power Delivery 2016, 32, 1068–1078. [Google Scholar] [CrossRef]
- Zhang, K.; Hu, Z.; Zhan, Y.; Wang, X.; Guo, K. A smart grid AMI intrusion detection strategy based on extreme learning machine. Energies 2020, 13, 4907. [Google Scholar] [CrossRef]
- Liu, Q.; Hagenmeyer, V.; Keller, H.B. A review of rule learning-based intrusion detection systems and their prospects in smart grids. IEEE Access 2021, 9, 57542–57564. [Google Scholar] [CrossRef]
- Ali, M.Q.; Al-Shaer, E. Randomization-based intrusion detection system for advanced metering infrastructure. ACM Transactions on Information and System Security (TISSEC) 2015, 18, 1–30. [Google Scholar] [CrossRef]
- Liu, X.; Zhu, P.; Zhang, Y.; Chen, K. A collaborative intrusion detection mechanism against false data injection attack in advanced metering infrastructure. IEEE Transactions on Smart Grid 2015, 6, 2435–2443. [Google Scholar] [CrossRef]
- Alseiari, F.A.A.; Aung, Z. Real-time anomaly-based distributed intrusion detection systems for advanced Metering Infrastructure utilizing stream data mining. 2015 International Conference on Smart Grid and Clean Energy Technologies (ICSGCE). IEEE, 2015, pp. 148–153.
- Banik, S.; Banik, T.; Banik, S. Intrusion Detection System in Smart Grid-A Review 2023.
- Smadi, A.A.; Ajao, B.T.; Johnson, B.K.; Lei, H.; Chakhchoukh, Y.; Abu Al-Haija, Q. A Comprehensive survey on cyber-physical smart grid testbed architectures: Requirements and challenges. Electronics 2021, 10, 1043. [Google Scholar] [CrossRef]
- Zhang, C.; Kuppannagari, S.R.; Kannan, R.; Prasanna, V.K. Generative adversarial network for synthetic time series data generation in smart grids. 2018 IEEE international conference on communications, control, and computing technologies for smart grids (SmartGridComm). IEEE, 2018, pp. 1–6.
- Tushar, W.; Huang, S.; Yuen, C.; Zhang, J.A.; Smith, D.B. Synthetic generation of solar states for smart grid: A multiple segment Markov chain approach. IEEE PES Innovative Smart Grid Technologies, Europe. IEEE, 2014, pp. 1–6.
- Zheng, X.; Wang, B.; Xie, L. Synthetic dynamic PMU data generation: A generative adversarial network approach. 2019 International Conference on Smart Grid Synchronized Measurements and Analytics (SGSMA). IEEE, 2019, pp. 1–6.
- Cintuglu, M.H.; Mohammed, O.A.; Akkaya, K.; Uluagac, A.S. A survey on smart grid cyber-physical system testbeds. IEEE Communications Surveys & Tutorials 2016, 19, 446–464. [Google Scholar] [CrossRef]
- Ashok, A.; Krishnaswamy, S.; Govindarasu, M. PowerCyber: A remotely accessible testbed for Cyber Physical security of the Smart Grid. 2016 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT). IEEE, 2016, pp. 1–5.
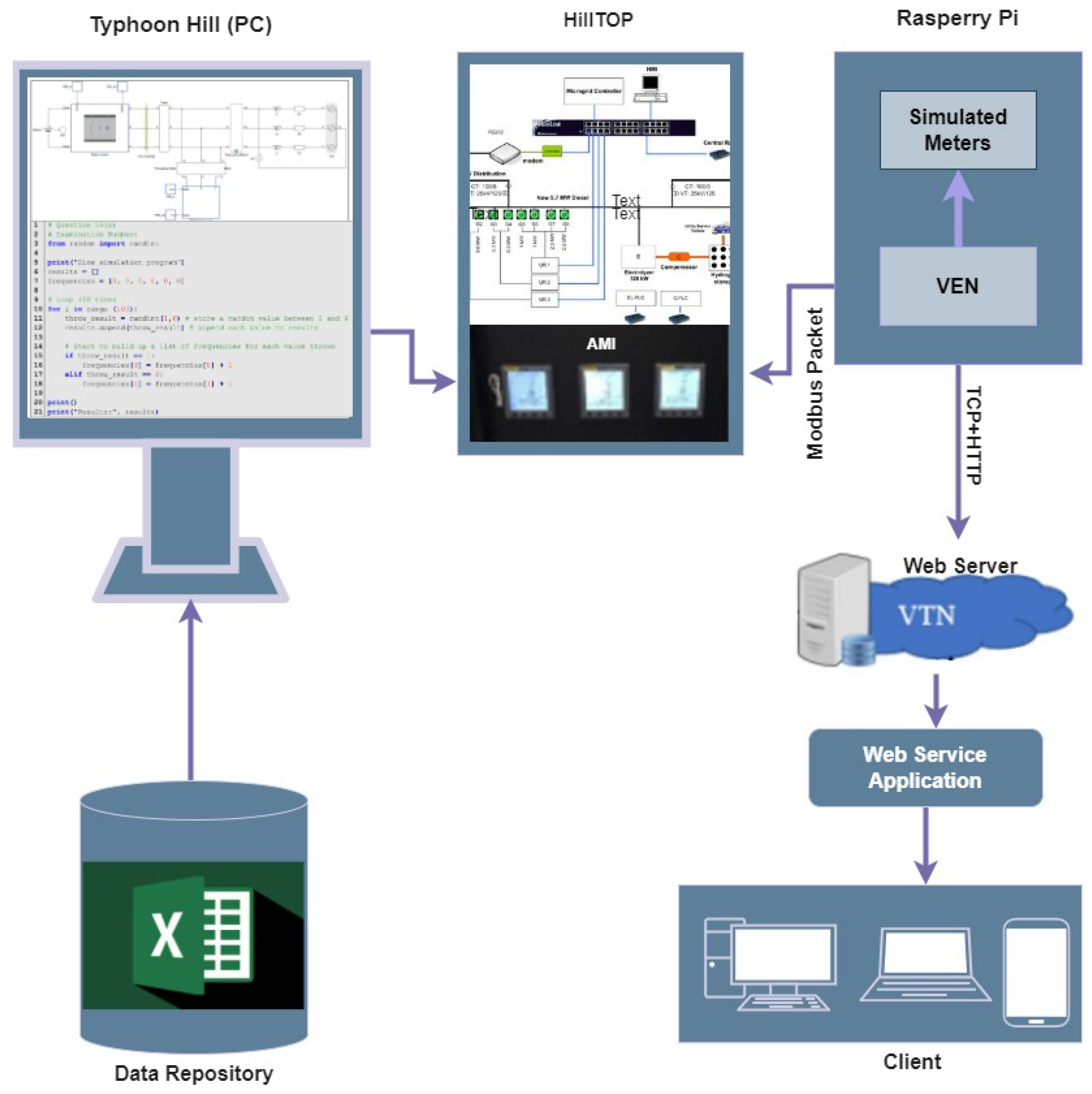
- Shampa Banik, T.; Manicavasagam, R.; Banik, T.; Banik, S. Simulation and Analysis of Cyber-Attack on Modbus Protocol for Smart Grids in Virtual Environment 2023. [CrossRef]
- Banik, S.; Banik, T.; Hossain, S.M.; Saha, S.K. Implementing man-in-the-middle attack to investigate network vulnerabilities in smart grid test-bed. 2023 IEEE World AI IoT Congress (AIIoT). IEEE, 2023, pp. 0345–0351.
- Koutsandria, G.; Gentz, R.; Jamei, M.; Scaglione, A.; Peisert, S.; McParland, C. A real-time testbed environment for cyber-physical security on the power grid. Proceedings of the First ACM Workshop on Cyber-Physical Systems-Security and/or PrivaCy, 2015, pp. 67–78.
- Adepu, S.; Kandasamy, N.K.; Mathur, A. Epic: An electric power testbed for research and training in cyber physical systems security. Computer Security: ESORICS 2018 International Workshops, CyberICPS 2018 and SECPRE 2018, Barcelona, Spain, September 6–7, 2018, Revised Selected Papers 2. Springer, 2019, pp. 37–52.
- Reda, H.T.; Ray, B.; Peidaee, P.; Anwar, A.; Mahmood, A.; Kalam, A.; Islam, N. Vulnerability and impact analysis of the IEC 61850 GOOSE protocol in the smart grid. Sensors 2021, 21, 1554. [Google Scholar] [CrossRef]
- Oyewumi, I.A.; Jillepalli, A.A.; Richardson, P.; Ashrafuzzaman, M.; Johnson, B.K.; Chakhchoukh, Y.; Haney, M.A.; Sheldon, F.T.; de Leon, D.C. Isaac: The idaho cps smart grid cybersecurity testbed. 2019 IEEE Texas Power and Energy Conference (TPEC). IEEE, 2019, pp. 1–6.
- Hahn, A.; Ashok, A.; Sridhar, S.; Govindarasu, M. Cyber-physical security testbeds: Architecture, application, and evaluation for smart grid. IEEE Transactions on Smart Grid 2013, 4, 847–855. [Google Scholar] [CrossRef]
- Montoya, J.; Brandl, R.; Vishwanath, K.; Johnson, J.; Darbali-Zamora, R.; Summers, A.; Hashimoto, J.; Kikusato, H.; Ustun, T.S.; Ninad, N.; others. Advanced laboratory testing methods using real-time simulation and hardware-in-the-loop techniques: A survey of smart grid international research facility network activities. Energies 2020, 13, 3267. [Google Scholar] [CrossRef]
- Alves, T.; Das, R.; Morris, T. Virtualization of industrial control system testbeds for cybersecurity. Proceedings of the 2nd Annual Industrial Control System Security Workshop, 2016, pp. 10–14.
- Meghwani, A.; Srivastava, S.; Srivastava, A. Development of real-time distribution system testbed using co-simulation. 2020 21st National Power Systems Conference (NPSC). IEEE, 2020, pp. 1–6.
- Ahmad, I.; Kazmi, J.H.; Shahzad, M.; Palensky, P.; Gawlik, W. Co-simulation framework based on power system, AI and communication tools for evaluating smart grid applications. 2015 IEEE Innovative Smart Grid Technologies-Asia (ISGT ASIA). IEEE, 2015, pp. 1–6.
- Mylonas, E.; Tzanis, N.; Birbas, M.; Birbas, A. An automatic design framework for real-time power system simulators supporting smart grid applications. Electronics 2020, 9, 299. [Google Scholar] [CrossRef]
- Venkataramanan, V.; Srivastava, A.; Hahn, A. Real-time co-simulation testbed for microgrid cyber-physical analysis. 2016 Workshop on Modeling and Simulation of Cyber-Physical Energy Systems (MSCPES). IEEE, 2016, pp. 1–6.
- Ciraci, S.; Daily, J.; Fuller, J.; Fisher, A.; Marinovici, L.; Agarwal, K. FNCS: A framework for power system and communication networks co-simulation. Proceedings of the symposium on theory of modeling & simulation-DEVS integrative, 2014, pp. 1–8.
- Mihal, P.; Schvarcbacher, M.; Rossi, B.; Pitner, T. Smart grids co-simulations: Survey & research directions. Sustainable Computing: Informatics and Systems 2022, 35, 100726. [Google Scholar] [CrossRef]
- Le, T.D.; Anwar, A.; Loke, S.W.; Beuran, R.; Tan, Y. Gridattacksim: A cyber attack simulation framework for smart grids. Electronics 2020, 9, 1218. [Google Scholar] [CrossRef]
- Joubert, G.D.; Raji, A.K. Development and validation of a real-time testbed for renewable energy integration studies: South African grid code case study. Journal of Engineering, Design and Technology 2023.
- Tundis, A.; Egert, R.; Mühlhäuser, M. Attack scenario modeling for smart grids assessment through simulation. Proceedings of the 12th International Conference on Availability, Reliability and Security, 2017, pp. 1–10.
- Darwish, I.; Igbe, O.; Saadawi, T. Vulnerability assessment and experimentation of smart grid DNP3. Journal of Cyber Security and Mobility 2016, pp. 23–54.
- Paul, S.; Ni, Z. Vulnerability analysis for simultaneous attack in smart grid security. 2017 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT). IEEE, 2017, pp. 1–5.
- Rashed, M.; Kamruzzaman, J.; Gondal, I.; Islam, S. Vulnerability Assessment framework for a Smart Grid. 2022 4th Global Power, Energy and Communication Conference (GPECOM). IEEE, 2022, pp. 449–454.
- Queiroz, C.; Mahmood, A.; Tari, Z. SCADASim—A framework for building SCADA simulations. IEEE Transactions on Smart Grid 2011, 2, 589–597. [Google Scholar] [CrossRef]
- Mets, K.; Ojea, J.A.; Develder, C. Combining power and communication network simulation for cost-effective smart grid analysis. IEEE Communications Surveys & Tutorials 2014, 16, 1771–1796. [Google Scholar] [CrossRef]
- Anderson, K.; Narayan, A. Simulating integrated volt/var control and distributed demand response using GridSpice. 2011 IEEE First International Workshop on Smart Grid Modeling and Simulation (SGMS). IEEE, 2011, pp. 84–89.
- Wermann, A.G.; Bortolozzo, M.C.; da Silva, E.G.; Schaeffer-Filho, A.; Gaspary, L.P.; Barcellos, M. ASTORIA: A framework for attack simulation and evaluation in smart grids. NOMS 2016-2016 IEEE/IFIP Network Operations and Management Symposium. IEEE, 2016, pp. 273–280.
- Barbierato, L.; Estebsari, A.; Pons, E.; Pau, M.; Salassa, F.; Ghirardi, M.; Patti, E. A distributed IoT infrastructure to test and deploy real-time demand response in smart grids. IEEE Internet of Things Journal 2018, 6, 1136–1146. [Google Scholar] [CrossRef]
- Abedi, A.; Romerio, F. Multi-period vulnerability analysis of power grids under multiple outages: An AC-based bilevel optimization approach. International Journal of Critical Infrastructure Protection 2020, 30, 100365. [Google Scholar] [CrossRef]
- Jarrah, M. Modeling and simulation of renewable energy sources in smart grid using DEVS formalism. Procedia Computer Science 2016, 83, 642–647. [Google Scholar] [CrossRef]
- Mongrain, R.S.; Yu, Z.; Ayyanar, R. A real-time simulation testbed for hierarchical control of a renewable energy-based microgrid. 2019 IEEE Texas Power and Energy Conference (TPEC). IEEE, 2019, pp. 1–6.
- Ahmad, A.; Khan, J.Y. Real-time load scheduling, energy storage control and comfort management for grid-connected solar integrated smart buildings. Applied Energy 2020, 259, 114208. [Google Scholar] [CrossRef]
- Yassine, B.I.; Boumediene, A. Renewable energies evaluation and linking to smart grid. International Journal of Power Electronics and Drive Systems 2020, 11, 107. [Google Scholar] [CrossRef]
- Mccarty, M.; Johnson, J.; Richardson, B.; Rieger, C.; Cooley, R.; Gentle, J.; Rothwell, B.; Phillips, T.; Novak, B.; Culler, M.; others. Cybersecurity Resilience Demonstration for Wind Energy Sites in Co-Simulation Environment. IEEE Access 2023, 11, 15297–15313. [Google Scholar] [CrossRef]
- Panda, D.K.; Das, S. Smart grid architecture model for control, optimization and data analytics of future power networks with more renewable energy. Journal of Cleaner Production 2021, 301, 126877. [Google Scholar] [CrossRef]
- Logenthiran, T.; Srinivasan, D.; Shun, T.Z. Demand side management in smart grid using heuristic optimization. IEEE transactions on smart grid 2012, 3, 1244–1252. [Google Scholar] [CrossRef]
- Gaur, G.; Mehta, N.; Khanna, R.; Kaur, S. Demand side management in a smart grid environment. 2017 IEEE International Conference on Smart Grid and Smart Cities (ICSGSC). IEEE, 2017, pp. 227–231.
- Samadi, P.; Mohsenian-Rad, H.; Schober, R.; Wong, V.W. Advanced demand side management for the future smart grid using mechanism design. IEEE Transactions on Smart Grid 2012, 3, 1170–1180. [Google Scholar] [CrossRef]
- Amin, B.R.; Taghizadeh, S.; Rahman, M.S.; Hossain, M.J.; Varadharajan, V.; Chen, Z. Cyber attacks in smart grid–dynamic impacts, analyses and recommendations. IET Cyber-Physical Systems: Theory & Applications 2020, 5, 321–329. [Google Scholar] [CrossRef]
- Abdelrahman, M.S.; Kharchouf, I.; Nguyen, T.L.; Mohammed, O.A. A Hybrid Physical Co-Simulation Smart Grid Testbed for Testing and Impact Analysis of Cyber-Attacks on Power Systems: Framework and Attack Scenarios. Energies 2023, 16, 7771. [Google Scholar] [CrossRef]
- Athari, M.H.; Wang, Z. Impacts of wind power uncertainty on grid vulnerability to cascading overload failures. IEEE Transactions on Sustainable Energy 2017, 9, 128–137. [Google Scholar] [CrossRef]
- Le, T.D.; Anwar, A.; Beuran, R.; Loke, S.W. Smart grid co-simulation tools: Review and cybersecurity case study. 2019 7th International Conference on Smart Grid (icSmartGrid). IEEE, 2019, pp. 39–45.
- Moulema, P.; Yu, W.; Griffith, D.; Golmie, N. On effectiveness of smart grid applications using co-simulation. 2015 24th International Conference on Computer Communication and Networks (ICCCN). IEEE, 2015, pp. 1–8.
- Darwish, I.; Igbe, O.; Celebi, O.; Saadawi, T.; Soryal, J. Smart grid DNP3 vulnerability analysis and experimentation. 2015 IEEE 2nd International Conference on Cyber Security and Cloud Computing. IEEE, 2015, pp. 141–147.
- Jokar, P.; Leung, V.C. Intrusion detection and prevention for ZigBee-based home area networks in smart grids. IEEE Transactions on Smart Grid 2016, 9, 1800–1811. [Google Scholar] [CrossRef]
- Caire, R.; Sanchez, J.; Hadjsaid, N. Vulnerability Analysis of Coupled Heterogeneous Critical Infrastructures: a Co-simulation approach with a testbed validation. IEEE PES ISGT Europe 2013. IEEE, 2013, pp. 1–5.
- Danilczyk, W.; Sun, Y.L.; He, H. Smart grid anomaly detection using a deep learning digital twin. 2020 52nd North American Power Symposium (NAPS). IEEE, 2021, pp. 1–6.
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. Ieee Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, L.; Sun, W.; Green II, R.C.; Alam, M. Distributed intrusion detection system in a multi-layer network architecture of smart grids. IEEE Transactions on Smart Grid 2011, 2, 796–808. [Google Scholar] [CrossRef]
- Boumkheld, N.; Ghogho, M.; El Koutbi, M. Intrusion detection system for the detection of blackhole attacks in a smart grid. 2016 4th International Symposium on Computational and Business Intelligence (ISCBI). IEEE, 2016, pp. 108–111.
- Beigi-Mohammadi, N.; Mišić, J.; Khazaei, H.; Mišić, V.B. An intrusion detection system for smart grid neighborhood area network. 2014 IEEE International Conference on Communications (ICC). IEEE, 2014, pp. 4125–4130.
- Palahalli, H.; Ragaini, E.; Gruosso, G. Smart grid simulation including communication network: A hardware in the loop approach. IEEE Access 2019, 7, 90171–90179. [Google Scholar] [CrossRef]
- Lo, C.H.; Ansari, N. CONSUMER: A novel hybrid intrusion detection system for distribution networks in smart grid. IEEE Transactions on Emerging Topics in Computing 2013, 1, 33–44. [Google Scholar] [CrossRef]
- Flechais, I.; Mascolo, C.; Sasse, M.A. Integrating security and usability into the requirements and design process. International Journal of Electronic Security and Digital Forensics 2007, 1, 12–26. [Google Scholar] [CrossRef]
- Potter, B.; McGraw, G. Software security testing. IEEE Security & Privacy 2004, 2, 81–85. [Google Scholar] [CrossRef]

| Attack Vector | Description | Threat |
|---|---|---|
| Lack of interoperability | DER architectural diversity and implementation specification | DER denial of legitimate messages and control commands |
| (e.g., security requirements) | ||
| can result in intersystem insecure communications. | ||
| Data integrity violations | Stored, transmitted, or received data are modified without violation, | Malicious modification of control parameter |
| causing DER malfunction | ||
| or allowing unauthorized access to control/log information | ||
| Implementation errors | Security flaws within systems and/or communication modules enabling the remote control | Command and control of load/demand-side devices |
| of DER assets and exfiltration of historical generation data | ||
| Supply-chain compromises | Installment of malicious hardware-based eavesdropping programs, worms, and oversights | Sensitive information disclosure |
| during manufacturing components, devices, or systems. | ||
| Insecure firmware | Digital signatures of firmware updates are not verified, granting malware (viruses, worms, trojans, etc.) | DER systems privilege escalation |
| access to secure systems otherwise. |
| Attack | Target Components | Security Goals | Risk Mitigation Techniques | Countermeasures | ||
|---|---|---|---|---|---|---|
| C | I | A | ||||
| Injection Attacks | Data Link, Transport, Application | ✔ | ✔ | D, P & C | Hybrid IDS, ML, BYOD Policy | |
| Flooding Attack | Data Link, Network, Transport, Application | ✔ | D, P | Timestamp, Filtering, Random Session Keying | ||
| Man-in-the-Middle Attacks | Data Link, Network, Session | ✔ | ✔ | D, P | Encrypting the transmitted messages | |
| Eavesdropping Attack | Physical, Network | ✔ | D, P | HTTPS/SSH Encryption, Personal Firewalls, VPNs | ||
| Replay Attack | Transport | ✔ | D, P | Running an executable program that sends safe values to Basic | ||
| Process Contro System (BPCS) | ||||||
| Brute Force Attacks | Network, Session, Presentation | ✔ | ✔ | D, P | Timestamp, Filtering, Random Session Keying | |
| Teardrop Attack | Network | ✔ | D, P | Timestamp, Filtering, Random Session Keying | ||
| Jamming Attacks | Physical, Data, Network | ✔ | D, P | Timestamp, Filtering, Random Session Keying | ||
| Spoofing Attacks | Physical, Data, Network, Transport | ✔ | ✔ | ✔ | D, P | Isolating the attacker node from the LAN |
| Social Engineering Attacks | Application | ✔ | D, P | Employee Training & Awareness | ||
| Buffer Overflow Attack | Transport, Application | ✔ | D, P | Timestamp, Filtering, Random Session Keying | ||
| Popping the HMI Attack | Application | ✔ | ✔ | ✔ | D, P | Timestamp, Filtering, Random Session Keying |
| DDoS Attack | Application, Network, MAC | ✔ | D, P | Backups, Secondary Devices, IDS, Leverage to Clouds | ||
| Phishing Attack | Application, Network, MAC | ✔ | ✔ | D, P | IDS, Anti-Phishing, Software/Training | |
| Port Scanning | Control Center | ✔ | D, P | IDS, Anti-Phishing, Software/Training | ||
| Botnets | AMI | ✔ | ✔ | ✔ | D, C & P | IDS, Anti-Malware |
| Reconnaissance Attack | Control Protocol | ✔ | ✔ | ✔ | D, C & P | Redirecting the attacker to a honeypot |
| Malicious Software | Control Center, RTU | ✔ | ✔ | ✔ | D, P | Anti-virus, Installing Software Update Patches |
| Denial of Service | Field Devices, AMI | ✔ | ✔ | ✔ | D, P | Dropping packets coming from HMI, Generating an alert |
| Buffer Overflow | Field Devices, SCADA | ✔ | D, P | IDS, Anti-Phishing, Software/Training | ||
| Unauthorized Access | Control Center, RTU | ✔ | D, P | IDS, Anti-Phishing, Software/Training | ||
| Password Cracking | Control Center, RTU | ✔ | P & C | Password Policy, Periodic Password Changing | ||
| SM Tampering Attacks | AMI | ✔ | D, P & C | Anti-theft device, Detecting unauthorized access | ||
| SQL Injection | Control Center | ✔ | D, P | Least Privilege, Strong Code, Whitelisting | ||
| Data manipulation | SCADA | ✔ | ✔ | D, P | IDS, Anti-Phishing, Software/Training | |
| Replay Attack | Field Devices | ✔ | D, P | IDS, Anti-Phishing, Software/Training | ||
| Spyware | Control Center | ✔ | D, P | Anti-Spyware, Defence in Depth | ||
| Malware | Control Center | ✔ | ✔ | D, P, & C | IDS, Firewalls, Anti-Malware,Anti-Virus | |
| Ransomware | Control Center | ✔ | ✔ | ✔ | D, C | Honeypot, Verified Backup/Update, Lesson Learnt |
| Worms | SCADA | ✔ | ✔ | ✔ | D, C | Honeypot, Verified Backup/Update, Lesson Learnt |
| ID | FAMILY | ID | FAMILY |
|---|---|---|---|
| AC | Access Control | PE | Physical and Environmental Protection |
| AT | Awareness & Training | PL | Planning |
| AU | Audit & Accountability | PM | Program Management |
| CA | Assessment, Authorization & Monitoring | PS | Personal Security |
| CM | Configuration Management | PT | Processing & Transparency |
| CP | Contingency Planning | RA | Risk Assessment |
| IA | Identification & Authentication | SA | System and Services Acquisition |
| IR | Incident Response | SC | System & Communication Protection |
| MA | Maintenance | SI | System & Information Integrity |
| MP | Media Protection | SR | Supply Chain Risk Management |
| Simulation on SG testbed |
Simulation on SG Technology & Application |
Simulation on SG Communication Network |
Simulation on SG power grid & Communication Network |
|
|---|---|---|---|---|
| Vulnerabilities Assessment | [58,122,127,137,164,165] | [40,64,166,167,168] | [16,140,145,146,169,170] | [143,165,168,171] |
| [132,136,140,147,164] | [148,149,152,159] | |||
| Vulnerability Mitigation | [89,101,147,154,164,164] | [75,94,115,156,159,172,173] | [114,170,174,175,176] | [115,130,177] |
| [134,178] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




