1. Introduction
The next-generation "Industrial Internet of Things" (IIoT) will support "Machine-to-Machine" (M2M) communications, for the future smart Cyber-Physical-Systems (CPSs), Industry 4.0, and the critical infrastructure of the 21-st century. The future CPSs include Smart Cities, Smart Transportation Systems, Smart Heathcare, the Smart Power Grid, and Smart Manufacturing. These future CPSs will require complex electronic control systems that rely upon ultra-reliable and ultra-low-latency M2M communications with full immunity to cyber-attackers. "Ultra-Reliable Low-Latency-Communications" (URLLC) for 5G/6G wireless systems are described in [
1,
2,
3]. Hence, the next-generation Industrial-IoT is expected to support a "Deterministic" service model, where billions of M2M traffic flows for smart CPSs receive deterministic (i.e., guaranteed) service, with proven "Quality of Service" (QoS) guarantees, with ultra-reliable and ultra-low-latency communications, and with strict immunity to external cyber-attacks.
In contrast, the existing "Consumer Internet of Things" (Consumer-IoT) has supported "Consumer-Oriented" communications for 4 decades. It supports consumer services such as electronic shopping/e-commerce ( i.e., Amazon and Alibaba), the "voice over Internet-Protocol" (i.e., voice-over-IP), video-over-IP (i.e., Netflix, Amazon Prime), music-over-IP (i.e., Spotify, Apple and Amazon Music), and social networking (i.e., Facebook, LinkedIn, and TikTok). The Consumer-IoT is based upon the layer-3
"Internet Protocol" (IP), as all traffic must pass through IP. Unfortunately, IP is over 4 decades old, and only provides a
"Best-Effort" (BE) service model, with no strict (i.e., mathematically-provable) QoS guarantees [
4,
5]. IP is subject to significant congestion and "BufferBloat" [
6,
7], has poor reliability/availability, and even the layer-3 routing is insecure [
8,
9]. IP provides no guarantees that traffic will be delivered by a given deadline, or delivered at all.
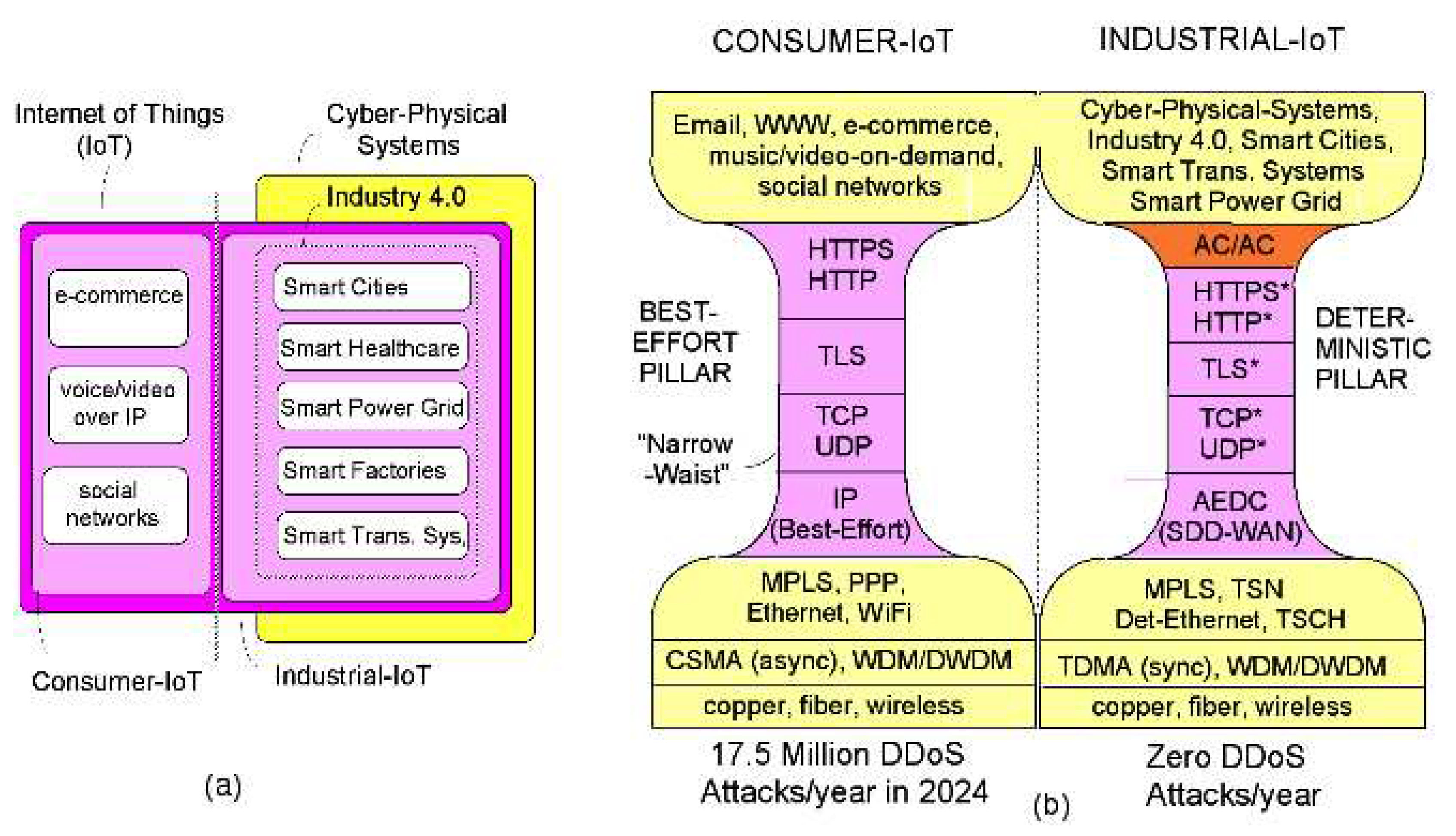
Figure 1a illustrates a Venn Diagram, with the Consumer-IoT, the Industrial-IoT, Cyber-Physical Systems and Industry 4.0. The next-generation IoT will comprise 2 branches, the Consumer-IoT focussing on consumers, and the Industrial-IoT focussing on Industrial Automation and Industry 4.0. (
Figure 1a builds upon a simpler Venn diagram illustrated in [
16].) Kleinrock proposed a "Narrow-Waist" model for the protocol stack of the Consumer-IoT three decades ago in 1994.
Figure 1b illustrates an evolution of the IoT protocol stack, from the "Narrow-Waist" model of the Consumer-IoT, towards a proposed
"Dual Pillar" model with a "Wider-Waist", which supports both a Best-Effort pillar for the Consumer-IoT (using IP), and a Deterministic pillar for the Industrial IoT (using FPGAs and no IP).
The Consumer-IoT is also vulnerable to numerous layer-3 cyber-attacks. According to Cisco, the Consumer-IoT will suffer from ≈ 17.5 million
"Distributed Denial of Service" (DDoS) attacks in 2024, which can disrupt all layer-3 services [
10,
11]. At a growth rate of 14%, the Consumer-IoT will suffer from ≈ 20 million DDoS attacks in 2025. According to the cyber-security firm Norton, a DDoS attack is one of the
"most powerful weapons on the Internet". It is a cyber-attack targeting a web-server or network, that floods it with more Internet traffic than it can handle, resulting in a loss of service. Cloudflare’s global IoT network spans over 300 cities in 100 countries. It serves up to 64 million HTTP requests per second at peak times, and serves about 2.3 billion Domain Name Server (DNS) queries each day. Cloudflare mitigated over 140 billion cyber-threats per day in 2023. In 2023-Q3, Cloudflare detected and mitigated 8.9 trillion HTTP DDoS attack requests. Cloudflare estimates that the average DDoS attack lasted 8 hours in 2022, rending the targeted services unavailable for significant periods of time (several seconds, minutes or hours). Kaspersky Labs estimates that ≈ 20% of DDoS attacks last for weeks.
At the annual meeting of the "World Economic Forum" in Davos, Switzerland in Jan. 2024, the bank "JPMorgan Chase" reported that it receives billions of Internet accesses per day, many of which are attempted cyber-attacks. It reported that it spends US$15 billion a year on technology, and that it employs 62,000 technologists each year, more than Google or Amazon, many to fight cyber-attacks. In 2023, Google, Amazon, Microsoft and Cloudflare suffered record-setting DDoS attacks, called "TCP Middlebox Reflection" DDoS attacks which exploited middle-boxes, with an intensity of ≈ 200 million packets per second. Industry estimates that a DDoS attack takes up to 277 days to contain, and the average cost of a data-breach is ≈ US$10 million. DDoS attacks are also used as weapons of war, as the war between Ukraine and Russia illustrates. Clearly, the world is in the midst of a rather-severe cyber-security crisis, which grows worse every year.
The solutions proposed in this paper allow each nation to significantly-strength its national security. Each nation can achieve full immunity to external cyber-attacks, guaranteed through hardware-enforced intrusion detection, and exceptionally-strong immunity to internal cyber-attacks, for critical infrastructures on the Industrial-IoT. However, consumer-oriented entities such as banks and governments can also use the Industrial-IoT, to configure their own "Deterministic Virtual Private Networks" (D-VPNs) with exceptionally-strong cyber-security. (An "external" cyber-attacker cannot access a secured machine. An "internal" cyber-attacker has managed to obtain the secret keys needed to access a secured machine.)
Six protocols form the
"Narrow-Waist" of the Consumer-IoT, as all traffic must pass through these protocols [
12,
13,
14,
15]. As shown in
Figure 1b, these six protocols include:
IP (Internet-Protocol),
TCP ("Transmission Control Protocol"),
UDP ("User Datagram Protocol")
TLS ("Transport Layer Security") protocol,
HTTP ("Hypertext Transfer Protocol"),
HTTPS (HTTP-over-TLS).
As a result of the "Narrow-Waist" model, all Consumer-IoT traffic inherits the weaknesses of IP, i.e., the lack of deterministic QoS guarantees, and the vulnerability to layer-3 cyber-attacks, especially DoS/DDoS attacks.
According to the US CISA ("Cyber-security and Infrastructure Security Agency"), there are 16 critical infrastructure sectors in the USA, some of which are shown in
Table 1 [
17]. According to a recent "EU-NATO Task Force on the Resilience of Critical Infrastructure", the EU shares many of these same critical infrastructures, i.e., Energy, Transport, Digital Infrastructure, and Space [
18]. The ENISA ("European Union Agency for Cybersecurity") outlines several recommendations and challenges for securing Industry 4.0.
The control-systems for these distributed critical infrastructures will require a layer-3 "Wide Area Network" (WAN) with 4 key attributes:
(1) Ultra-High Reliability/Availability, with at least 99.999% availability (with less than 1 hour of down-time in 10 years of operation);
(2) "Ultra-Low-Latency" (ULL) communications;
(3) Deterministic end-to-end QoS guarantees, i.e., delay and jitter guarantees; and
(4) Guaranteed immunity to external cyber-attacks, especially layer-3 DoS/DDoS attacks.
There is currently no known layer-3 WAN network which can meet these 4 goals. The next-generation IIoT, if it can meet these 4 key attributes, will thus provide a critical infrastructure that will support much of the world’s economic activity. General Electric has estimated that the next-generation IIoT will control about one-half of global economic production by year 2030, approaching $US100 trillion in economic activity.
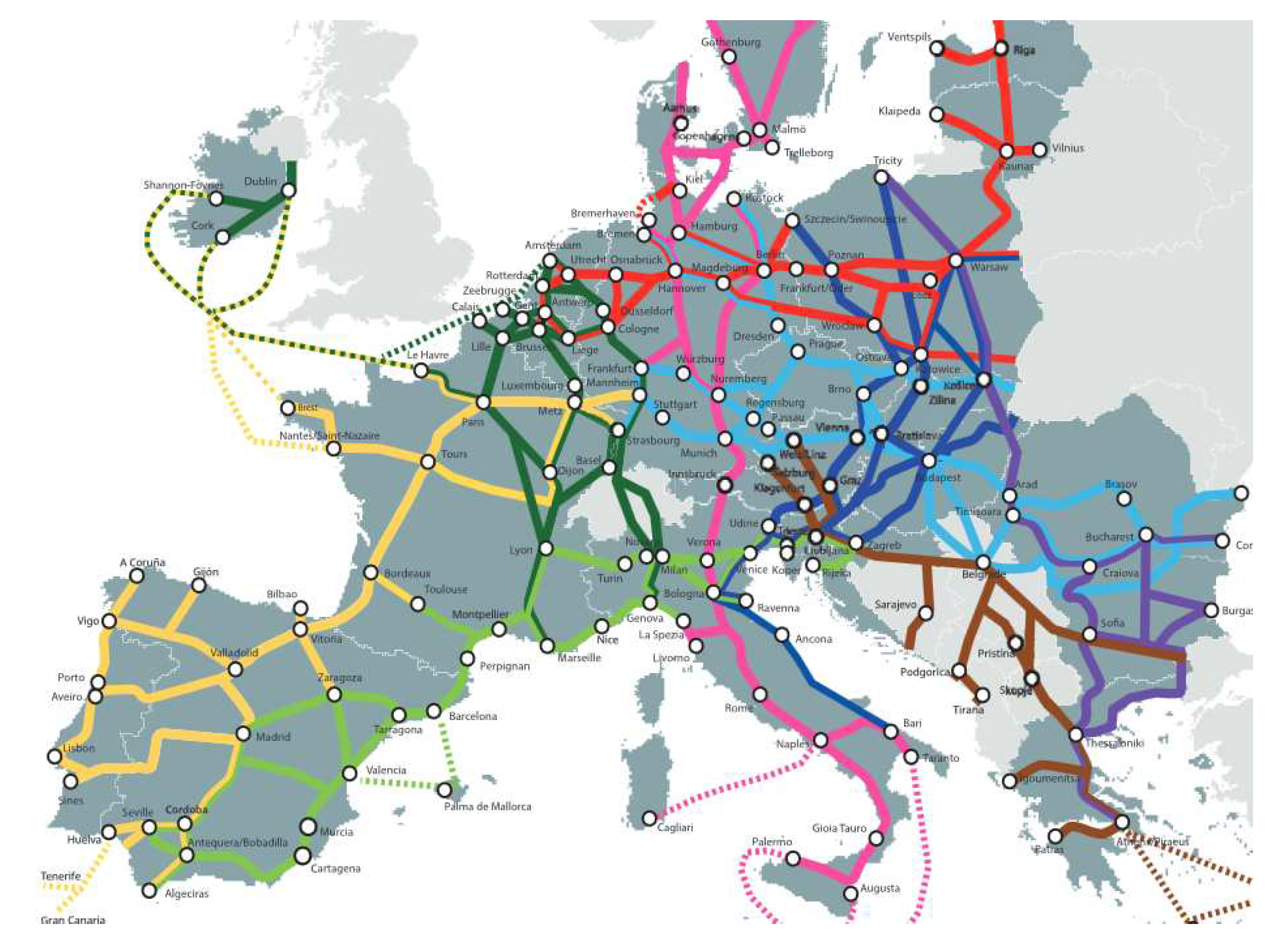
Figure 2 illustrates the critical infrastructure comprising the main transportation corridors for the EU, which includes roads and railways. These corridors will support future "Smart Transportation Systems", which may include a vast number of automated self-driving transport trucks. Cyber-attacks targeting critical infrastructures could have serious consequences. The firm McAfee has estimated that the global costs of cybercrime were ≈
$1 Trillion in 2020. The firms Cybersecurity Ventures and Statistica estimate that the global costs of cybercrime will be ≈ US
$10.5 trillion and US
$17.5 trillion by 2025. The existing Consumer-IoT provides little protection against the growing threat of cyber-attacks, and cannot support the next-generation of Cyber-Physical Systems and Industry 4.0.
In 2008, the US "National Academy of Engineering" (NAE) identified 14 "Grand-Challenge" problems of the 21-st century. These problems include achieving: (i) clean water for the world, (ii) carbon sequestration, (iii) fusion energy, and
"Security in Cyberspace" [
19]. This paper explores a hardware-based approach to address the NAE grand-challenge problem of "Security in Cyber-space" for critical infrastructure. Specifically, it explores a layer-3 "Software-Defined Deterministic WAN" (SDD-WAN) architecture which can provide hardware-enforced immunity to external cyber-attacks and exceptionally-strong immunity to internal cyber-attacks, against critical infrastructure connected to the Industrial-IoT.
The proposed SDD-WANs eliminate 3 cyber-security vulnerabilities that have existed in layer-3 IP for many decades: The use of: (i)
unencrypted IP packet headers; (ii)
un-authenticated IP packet headers; and (iii)
"middle-boxes" that implement functions such as IP address translation. The proposed SDD-WANs do not process IP packet headers, and hence they are logically-immune to all traditional IP-based cyber-attacks, in which a cyber-attacker modifies IP packet headers to perform the cyber-attack. The SDD-WANs are controlled by the SDN control-plane, not by IP packets created by cyber-attackers. The SDD-WANs enable the "Deterministic Pillar" of communications shown in
Figure 1b. The Industrial-IoT replaces the IP protocol in the Best-Effort pillar, with a programmable SDD-WAN with exceptionally-strong cyber-security, in the Deterministic pillar. Hence, IP-based cyber-attacks have zero influence on the Deterministic pillar, which completely ignores IP.
As shown in
Figure 1b, the Deterministic pillar can support critical infrastructure, such as the Smart Power Grid, "Quantum Key Distribution" (QKD) networks, and the future Quantum-Internet. It is well-known that critical-infrastructure such as the QKD networks (and the Quantum-Internet) require
"authenticated classical channels" for control, and these channels are usually provided by dedicated point-to-point links [
20]. These "authenticated classical channels" must achieve the 4 key attributes outlined earlier, including ultra-high reliability, ultra-low latency, QoS guarantees and immunity to cyber-attacks. The proposed SDD-WANs implement "Authenticated and Encrypted Deterministic Channels" (AEDCs), which can provide "authenticated classical channels" to QKD networks, in a programmable deterministic layer-3 network.
Table 2.
Vulnerabilities/Problems of the Best-Effort Consumer-IoT.
Table 2.
Vulnerabilities/Problems of the Best-Effort Consumer-IoT.
| Vulnerability |
Summary |
| Best-Effort (BE) |
• Provides "Best-Effort" service (no deterministic QoS guarantees). |
| service model |
Inconsistent transmission rates, causing interference and congestion. |
| Access-Control |
• Estimated 33 billion devices in the Consumer-IoT in 2024. No "Admission- |
| or Rate-Control |
Control/Access-Control" to control transmissions. Any device can transmit |
| |
to any other device, at any data-rate, at any-time, causing congestion. |
| Congestion and |
• Congestion causes "BufferBloat"; Buffer-sizes given by "Bandwidth-Delay- |
| BufferBloat |
Product" rule. 4 Tbps IP router with 1/4 sec. delay requires 1 Terabit buffer. |
| |
Impossible to fit a BE-IP router with 4 Tbps capacity onto a single FPGA. |
| Un-encrypted and |
• IP uses unencrypted & un-authenticated packet headers. Cannot |
| Un-authenticated |
"authenticate" the sender (verify that it is who it claims to be). IoT users can |
| IP packet headers |
modify IP packet headers to masquerade as trusted peers. Cyber-attackers |
| |
can modify IP packet headers to masquerade as trusted peers. |
| Middle-Boxes |
• Middle-Boxes perform essential functions, i.e., Address-Translation, |
| |
lntrusion Detection Systems, & firewalls. Middle-boxes are insecure. |
| DoS and |
• A cyber-attacker in a compromised middle-box can generate millions of |
| DDoS attacks |
malicious IP packets causing DoS attacks. A cyber-attacker controlling many |
| |
compromised IoT devices can generate millions of IP packets, causing DDoS |
| |
attacks. DDoS attacks among "the most significant weapons on the Internet". |
| |
• ≈ 17.5 million DDoS attacks in the Consumer-IoT in 2024 (Cisco). |
| |
• The average DDoS attack lasted for 8 hours in 2022 (Cloudflare). |
| "Isolation Control" |
• Cannot isolate sub-networks within the BE-IP, to contain cyber-attacks. |
| Over-Provisioning |
• The IoT is "over-provisioned" & operates at ≤ 40% of peak capacity. |
| |
• ≥60% of IoT capacity is unused (for very-high capital & energy costs). |
The Narrow-Waist Model: The IP protocol in the Consumer-IoT supports a "Best-Effort" (BE) service model. It is vulnerable to congestion, BufferBloat, and layer-3 cyber-attacks, especially DoS/DDoS attacks, considered by industry as one of "the most powerful weapons on the Internet". DDoS attacks can disable a service or a sub-network for many hours, days or weeks. Hence, BE-IP traffic can be delayed by seconds, minutes, hours, days or weeks, or may never be delivered at all. DDoS attacks are discussed in [
21,
22,
23,
24,
25,
26,
27,
28,
29].
The layer-4 TCP will guarantee that any data is delivered in the
correct order. The TLS protocol will provide
"cryptographic security" for end-to-end traffic flows [
30]. ("Cryptographic security" can be defined as immunity to cryptographic attacks which attempt to perform eavesdropping, message tampering and message forgery [
30].) However, both TCP and TLS inherit all the vulnerabilities of layer-3 IP, i.e., they rely upon the BE service of IP, and they are also vulnerable to congestion, BufferBloat, and layer-3 cyber-attacks, especially DoS/DDoS attacks. TCP and TLS flows can be delayed by seconds, minutes, hours, days or weeks, or may never be delivered at all.
As a result of congestion and BufferBloat, BE-IP routers can buffer 10s-100s of millions of packets for congested TCP and TLS flows. In the worst-case, BE-IP routers simply start "dropping" packets to relieve congestion or DoS/DDoS attacks. Hence, TLS-flows in the Consumer-IoT are effectively "unusable" for industrial control-systems.
DDoS Attacks against Servers and Networks: There are 2 types of layer-3 DoS/DDoS attacks, (i) attacks that target a web-server, and (ii) attacks that target the layer-3 network, i.e., the BE-IP routers and "Domain Name Servers" (DNSs). Cyber-attackers can easily flood a targeted web-server with millions of malicious IP packets per second, overloading the web-server and rendering the service unavailable. Web-servers using TLS-flows, with perfectly-secret keys from a QKD Network, are still vulnerable to layer-3 DoS/DDoS attacks, as the web-server is flooded with malicious traffic and unable to respond to valid traffic.
In a DoS/DDoS network attack, the attack-surface is larger than the targeted web-server, and includes every layer-3 router that supports the TLS-flow, and the DNSs in the Consumer-IoT. Each router or name-server can also be flooded with a DoS/DDoS attack, to disrupt the TLS-flow. Hence, packets in a TLS-flow suffering from a layer-3 DoS/DDoS attack can be severely delayed, or may never reach the desired web-server, rendering the TLS-flow unusable for industrial control-systems.
TLS Provides Excellent "Secrecy", but Limited "Security" against general Cyber-attacks:
Table 3 illustrates several quotes on the security of the TLS protocol. The TLS protocol is perhaps the most studied Internet protocol ever, given its importance. Several quotes endorse the view that TLS provides very strong "end-to-end security" on the Internet. A few quotes question whether TLS can provide such security. Given that the world is in the midst of a deep cyber-security crisis, it is useful to determine precisely how "secure" TLS is.
According to the Internet Society, TLS provides
"end-to-end security" for data sent over the Internet. According to the NIST, TLS provides a "safe communications channel" over the Internet. According to the IETF, TLS prevents "eavesdropping, forgery and message tampering" [
30]. According to a 2020 ACM paper, "TLS is the defacto standard for secure communication on the Internet".
The security of TLS is established in several theoretical papers, i.e., [
31,
32,
33,
34]. These papers establish that TLS is "secure", given very specific assumptions on the types of cyber-attacks that could occur in the BE Internet. These papers typically consider Man-in-the-Middle-attacks, replay attacks, and reorder attacks. The definitions of "security" are also very specific. Reference [
31] defines "security" of TLS as follows: (i) The protocol includes a secure authentication phase, and (ii) all data is transmitted using "Symmetric Key Cryptography" (SKC), to ensure confidentially. Hence, these proofs of "security" imply that the data is transmitted confidentially, and this type of security can be called "cryptographic-security". These proofs do not imply protection from any other types of cyber-attacks, other than those assumed to exist.
Table 3.
Does "Transport Layer Security" (TLS) Achieve Security against all Threats?
Table 3.
Does "Transport Layer Security" (TLS) Achieve Security against all Threats?
| Source |
Quotes supporting TLS Security |
| Internet |
• "TLS is a cryptographic protocol that provides end-to-end security of data sent between |
| Society |
applications over the Internet". Please see definition of "Security" below. |
| NIST |
"TLS and SSL are widely used in the Internet to provide a safe communications
|
| |
channel for sending sensitive information". |
| IETF [30] |
• "TLS allows client/server applications to communicate over the Internet in a way that is |
| |
designed to prevent eavesdropping, tampering, and message forgery." |
| IEEE [33] |
• "TLS is possibly the most used protocol for secure communications, with a 18-year history |
| |
of flaws and fixes". |
| ACM [34] |
• TLS "is the defacto standard for secure communication on the internet." |
| Source |
Quotes questioning TLS Security |
| NIST [40] |
• "There are no known ways to prevent flooding DoS attacks against hosts visible on the Internet. |
| IEEE [26] |
• "DDoS attacks are some of the most devastating attacks against Web applications." Application |
| |
layer DoS attacks are "a major threat because of the difficulty in adopting the defenses". |
| firm |
• "A DDoS attack is one of the most powerful weapons in the Internet." It is an attack against a |
| Norton |
web-server or network that floods it with more Internet traffic than it can handle. Sophisticated |
| |
cyber-criminals sell and lease software (i.e., Botnets) to create DDoS attacks on the dark web. |
| Dictionary |
Definition of a word |
| Oxford |
• SECURITY: "The activities involved in protecting a country, building or person against attack, |
| |
danger, etc". |
| Oxford |
• PRIVACY: "The state or condition of being free from being observed or disturbed by other |
| |
people." |
| Oxford |
• SECRECY: "The action of keeping something secret or the state of being kept secret." |
It is very important to note that these theoretical proofs of TLS "cryptographic-security" [
31,
32,
33,
34] do not consider DoS/DDoS attacks, and hence they do not apply to the Consumer-IoT. DDoS attacks have been around since 1996, and the importance of DDoS attacks was highlighted in a 2004 paper [
21]. Unfortunately, there are no known ways to stop these attacks.
According to NIST, "there are no known ways to prevent flooding DoS attacks against a host visible on the Internet" [
40]. According to the firm Norton, DoS/DDoS attacks are one of the most "significant weapons on the Internet". According to Cisco, there will be ≈ 17.5 million DoS/DDoS attacks on the Consumer-Internet in 2024. Hence, the reader should note that the "TLS Security" established in theoretical papers, i.e., [
31,
32,
33,
34], implies "cryptographic security" rather than general security against all types of cyber-attacks. These theoretical papers assume that the most significant attacks on the Internet in 2024 (i.e., DoS/DDoS attacks) do not exist, and their proofs do not apply to the Consumer-IoT.
Unfortunately, the TLS protocol suffers from several vulnerabilities [
35,
36,
37,
38,
39]. Most importantly, TLS-flows in the Consumer-IoT are vulnerable to layer-3 DoS/DDoS attacks. Even TLS-flows, using perfectly-secret keys from a QKD Network, are vulnerable to DoS/DDoS attacks. The US "National Security Agency" (NSA) acknowledges that QKD Networks are vulnerable to DoS attacks.
Given that DoS/DDoS attacks must be considered, it is clear that TLS cannot provide unconditional "end-to-end security" on the Consumer-IoT against arbitrary external cyber-attacks, as the TLS traffic might be delivered very late, or never at all. Having accurate definitions is important, given the significant costs that society incurs due to cyber-attacks.
This paper argues that TLS provides excellent "Secrecy", but limited "Security" to all types of cyber-attacks. Specifically, the TLS protocol provides excellent immunity against eavesdropping, but limited immunity to other common layer-3 external cyber-attacks, especially DoS/DDoS flooding attacks.
The Layer-3 Problems: In 2024, there is no known layer-3 network architecture which can meet the 4 key attributes stated earlier. In this paper, a "Software-Defined Deterministic Industrial Internet of Things" (SDD-IIoT) that meets these 4 goals is explored. As shown ahead in
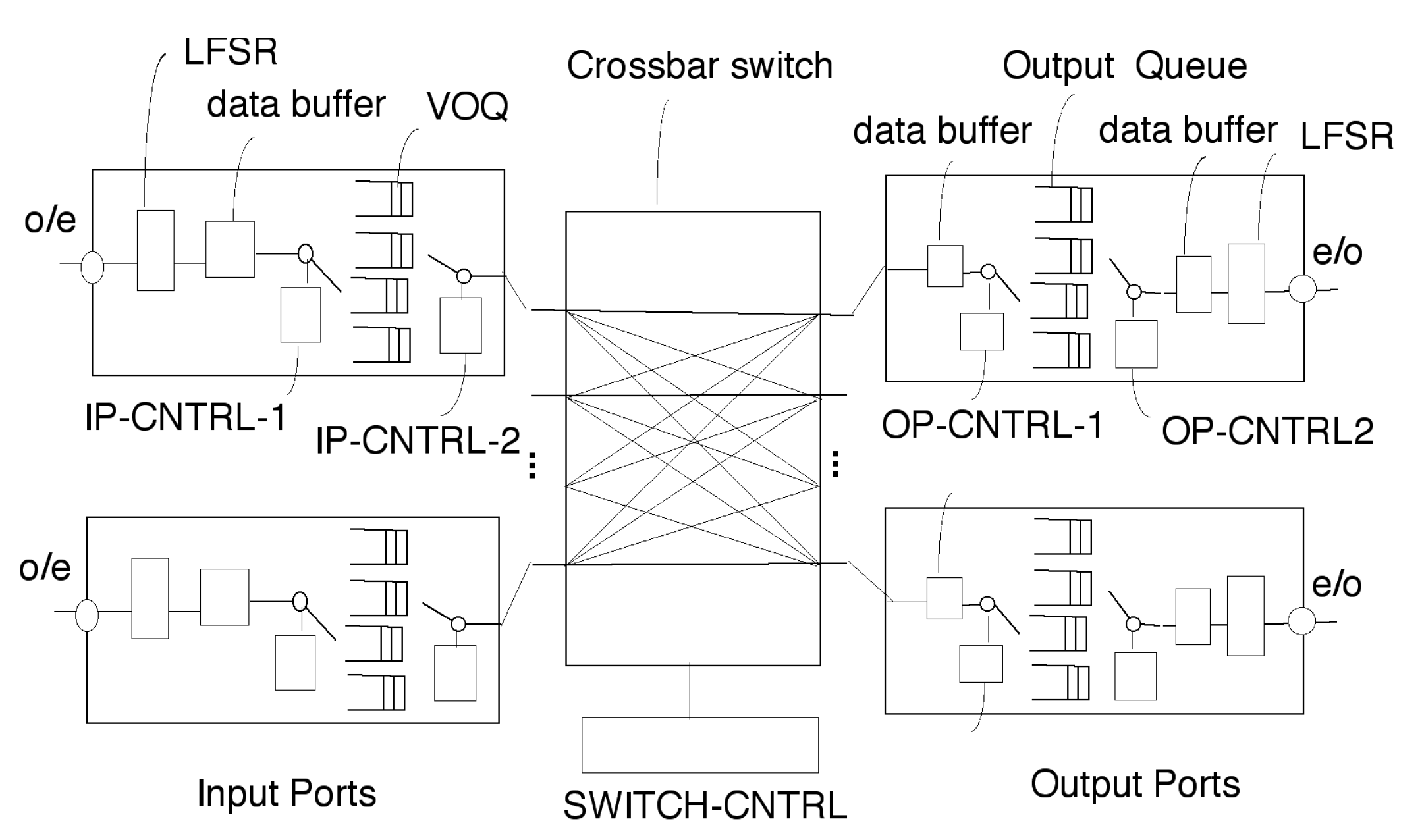
Figure 4a, a new forwarding-plane (i.e., sub-layer-3a) is introduced, to support ultra-low-latency M2M communications using "Authenticated and Encrypted Deterministic Channels" (AEDCs), also called D-flows. The forwarding-plane comprises a "Software Defined Networking" (SDN) control-plane and many authenticated SDD-WANs. Each SDD-WAN comprises many "deterministic packet switches" (D-switches), realized with "Field Programmable Gate Arrays" (FPGAs). The SDN control-plane can create millions of programmable M2M D-flows, through a network of 1,000s of authenticated D-switches, to enable the ultra-reliable and ultra-low-latency communications needed for critical infrastructure. The SDD-WANs can implement millions of programmable AEDCs in the forwarding-plane (sub-layer-3a), in FPFA hardware.
Two unique aspects of proposed SDD-IIoT will achieve exceptionally-strong hardware-enforced cyber-security: (a) The SDN control-plane implements an
"Admission-Control/ Access-Control" (AC/AC) system, to control access to network bandwidth, as shown in
Figure 1b. The AC/AC system comprises many "Artificial Intelligence" (AI) rule-based "Zero Trust Architectures" (ZTAs), to implement the fine-grain access-control to network bandwidth. Only M2M traffic flows that have been explicitly-approved by the AC/AC system will have reservations to communicate over the SDD-WANs in the SDD-IIoT. All other communications do not have reservations and are anomalies, i.e., malicious packets due to cyber-attacks; (b) The FPGAs will "enforce" the communications in the SDD-WANs, and will implement the "Guaranteed Intrusion Detection Systems" in hardware.
According to Cisco, the Consumer-IoT transmits about 10 billion Gigabytes of traffic per day. The FPGAs can easily process 10-100 billions of Gigabytes of IoT traffic per day, corresponding to 100s of billions of transmitted IoT packets/second, to detect and eliminate all malicious communications by external cyber-attackers, in hardware and in real-time. Hardware-based security is explored in [
46,
47,
48,
49]. Reference [
47] explored hardware implementations of cryptographic functions, and identified 2 very important techniques to combat IoT vulnerabilities: (i) redundancy of hardware and (ii) redundancy of information. This paper exploits these 2 very important techniques, to achieve exceptionally-strong hardware-enforced cyber-security.
The use of an AC/AC system in the Industrial-IoT offers several benefits (some of these benefits have been established previously, and are repeated here for completeness):
(1) It eliminates all congestion, interference, BufferBloat, and DoS/DDoS attacks [
42,
43,
44,
45];
(2) It reduces buffer sizes in D-switches by factors of 100,000+ times, relative to a BE-IP router [
42,
43,
44,
45];
(3) It reduces end-to-end layer-3 delays to "Ultra-Low Latencies" (ULL), i.e., the speed-of-light in fiber; [
42,
43,
44,
45];
The use of "Quantum-Safe" SDD-WANs offers several benefits:
(4) Packets are encrypted and authenticated with Quantum-Safe ciphers, to withstand attacks by Quantum Computers [
41];
(5) Each nation can significantly-strengthen its national security. The annual number of successful "external" cyber-attacks targeting a nation’s critical infrastructure can be reduced to zero [
41].
(6) The global costs of cyber-crime to society, estimated to exceed
$10 trillion annually (in 2025), can be significantly reduced [
41].
(7) The global cost savings in layer-3, achieved by introducing SDN, FPGAs and determinism into layer-3, can reach US
$100s of Billions per year (see section 7. This result improves upon the estimated savings of US
$10s of billions presented in [
41].)
(8) The SDD-WANs can enable QKD Networks and the future Quantum Internet, by providing a programmable forwarding-plane with "authenticated classical channels" with full-immunity to external cyber-attacks (see section 5).
(9) According to the US "National Security Agency" (NSA), QKD networks cannot authenticate the source, and are vulnerable to insider attacks and DoS attacks. The solutions typically require the use of "Pre-Shared (secret) Keys" (PSKs) and "Symmetric Key Cryptography", which lowers the security of QKD networks to the computational hardness of cracking SKC. As a result, the US NSA does not recommend QKD networks. The SDD-WANs offer comparable security to QKD networks in practice, secured by the computational hardness of cracking SKC. Hence, the SDD-WANs can provide a solution to today’s cyber-security crisis, until that time when QKD networks are ready to be deployed on a large-scale to millions of users (see section 5).
An Analogy to the Aviation Industry: The goal to significantly-reduce the number of successful external cyber-attacks per year against critical-infrastructure, to zero given appropriate conditions, requires some reflection. One can ask "Is there any precedent of any other global system, which has significantly-reduced the annual number of harmful events to society to nearly zero ?". The answer is "Yes".
The global aviation system currently moves about 4 billion people per year, over many independent commercial airlines. The number of terrorists which successfully defeat the "Border Security Services" to enter the EU or USA illegally via commercial airlines is close to zero. The Border Security Services implement a basic AC/AC system: Every passenger must be (i) "authenticated" with a passport and government-issued Identification (ID), (ii) have a valid reason for travel, and (iii) must have a reservation for one seat on each flight, to track their movement and to avoid interference and congestion. The commercial airline system enforces a basic AC/AC system, using rules written on paper, enforced by humans to significantly-reduce the number of harmful events to society.
Quite remarkably, the Consumer-IoT has not used any AC/AC system for over 4 decades. The BE-IP protocol does not provide any means to authenticate the sender, and hence it cannot perform a key feature of an AC/AC system, i.e., to authenticate the users being admitted to the system. This vulnerability has existed in the Consumer-IoT for over 4 decades, and it will continue to exist for several more decades until it is addressed.
In this paper, an AC/AC system is added to the Internet, to achieve both determinism and exceptionally-strong cyber-security. This new system requires the means the authenticate the users admitted into the system, which necessitates the addition of the new Deterministic pillar, along with the new sub-layer-3a, i.e., the SDD-WAN. Artificial Intelligence (AI) is used to maintain a large "knowledge-base" of rules, potentially thousands of rules, to implement a number of "ZTAs", to yield an AC/AC system with exceptionally-strong cyber-security. FPGAs provide hardware-enforcement of the rules, and can easily process all of the global IoT traffic, to detect any and all un-authorized traffic in real-time.
Relationship to Prior Work: The links between determinism and cyber-security were first explored in 2022, i.e., an SDD-IoT and SDD-WANs and their benefits were first presented in [
41]. These benefits are repeated here for completeness. Related papers on a Deterministic IoT were presented in [
42,
43,
44,
45]. Reference [
41] presented some experimental results for a USA SDD-WAN. This paper focusses on Industrial Automation and the Industrial-IoT. It presents a "Dual-Pillar" model for the IoT with a "widening waist", comprising a Best-Effort pillar for the Consumer-IoT, and a Deterministic pillar for the Industrial-IoT. It presents an updated flow-chart for the SDN control-plane, which includes: (i) the IETF "Authenticated Encryption" (AE) algorithm to authenticate/encrypt M2M D-flows, and (ii) several options for key exchange, including Post-Quantum key exchange. This paper also focusses on capabilities of the hardware-enforced cyber-security, when using the latest Intel STRATIX FPGAs. It establishes that the FPGA hardware can detect cyber-attacks within 10s-100s of billions of Gigabytes of Internet traffic per day, well-above the capacity of the global Consumer-IoT in 2023. It argues that the SDD-WANs can enable QKD Networks, by providing authenticated classical channels and immunity to external cyber-attacks. It also argues that in practical deployments, the SDD-WANs have comparable cyber-security to QKD Networks (see section 5). It presents extensive experimental results for a SDD-WAN over the European-Union, operating at 100% loads using the Intel STRATIX FPGAs.
This paper is organized as follows:
Section 2 briefly reviews several topics.
Section 3 presents the key features of the "Deterministic IIoT".
Section 4 presents the SDN control-plane.
Section 5 presents the security properties.
Section 6 presents experimental results for the European Union.
Section 7 presents a cost analysis of layer-3.
Section 8 concludes the paper. Section 9 contains the appendices; (i) a list of common acronyms, and (ii) a list of common cyber-attacks in the Consumer-IoT.
5. Security Properties of the Deterministic IIoT
This section summarizes the security properties of the proposed SDD-WANs
Property 1: Communications of Secured Components: The SDD-WAN consists of several secured-components (the D-transceivers, D-switches, and the SDN control-plane), which communicate over D-flows with Quantum-Safe ciphers, typically at security levels AES-256, AES-512 or AES-1024. It takes billions of years for a superconducting Quantum Computer to crack the AES-256 security level [
41]. Hence, the probability that any secured-component can be compromised by an external cyber-attacker is effectively 0.
Property 2: Majority Voting in De-centralized SDN control-plane: The SDN control-plane realizes an Admission-Control/Access-Control system, using 3 types of AI rule-based ZTA controllers (the IoT-Controller, WAN-Controller, and Enterprise-Controller), typically implemented as software systems running in data-centers. A single control-system is vulnerable to performance and reliability issues [
125,
126]. For maximum reliability/availability, multiple copies of each system will execute in separate data-centers, and majority voting is used to confirm each decision, i.e., 3 out of 5 copies must agree to confirm a decision. (This property exploits the principles of redundancy of hardware and redundancy of information, described in [
47].) Hence, the SDN control-plane can be logically viewed as a "centralized entity" that controls the SDD-WAN(s), but it is actually a
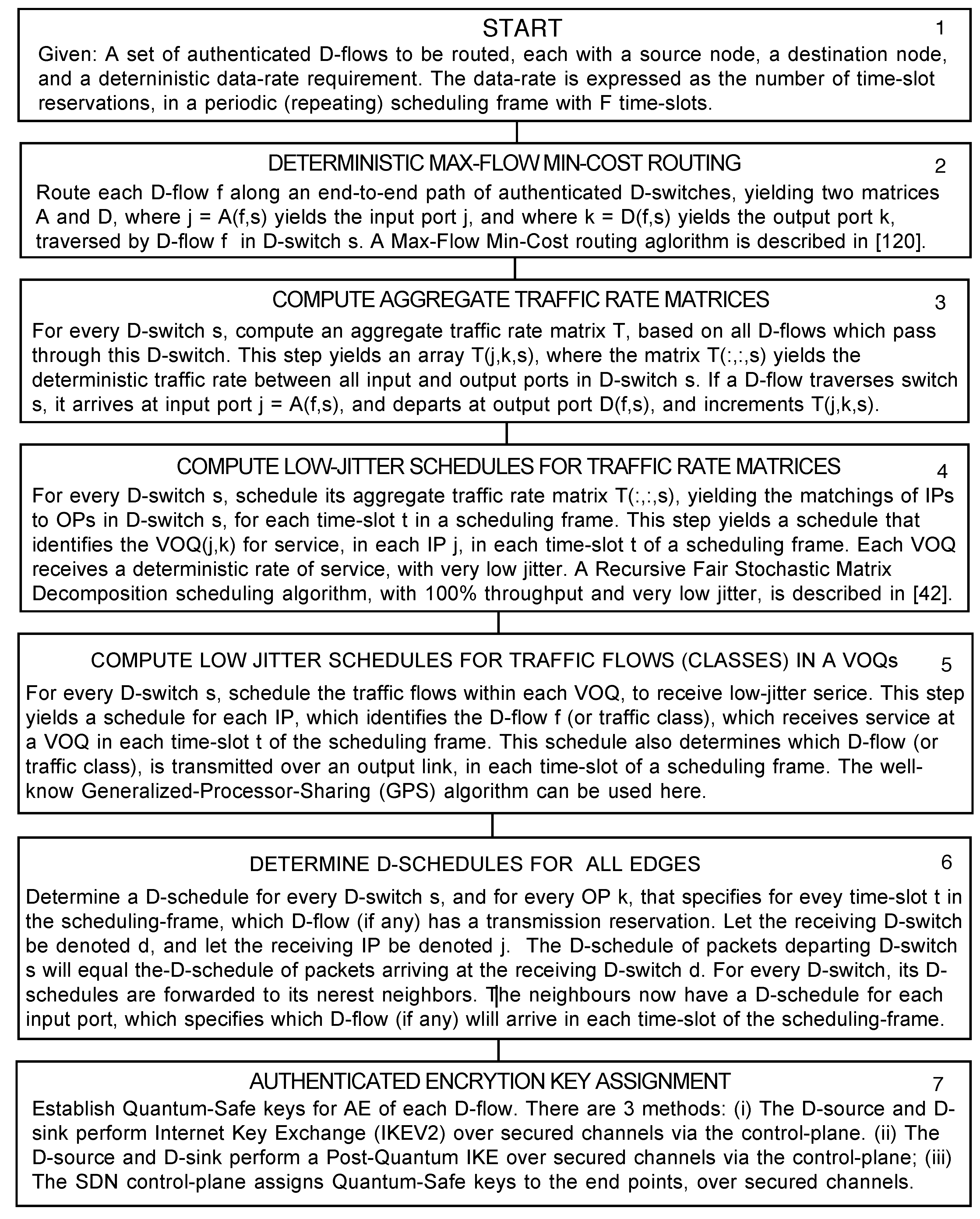
highly-distributed system, running software on multiple data-centers, and using majority-voting to consolidate the results. It is highly-protected from natural disasters (i.e., hurricanes, earthquakes), terrorist-attacks (i.e., explosions/missile strikes), and cyber-attacks (i.e., information-based attacks which attempt to compromise the communications of any secured components).
Property 3: Only Authorized D-flows Reserve Bandwidth: A request for a new D-flow will only be approved if a rule in the WAN-controller’s knowledge-base explicitly allows for the creation of the D-flow. If approved, the SDN control-plane will pre-compute several values for the new D-flow, i.e., the (i) routing, (ii) the scheduling, (iii) the D-schedules, and (iv) the Quantum-Safe secret keys for the "Authenticated Encryption" of the D-flow. A D-schedule for an edge in the SDD-WAN will define the time-slots in a periodic (repeating) scheduling-frame, in which the D-flow has a reservation to transmit data. Any data transmission in a time-slot for which no transmission reservation exists is an anomaly, i.e., a malicious packet from a cyber-attack. The anomaly is immediately detected by the FPGAs, reported to the SDN control-plane, and the data is not forwarded.
Property 4 - D-flows Reserve Guaranteed Data-Rates: Every D-flow will reserve a deterministic (or guaranteed) data-rate through a path of D-switches in a SDD-WAN, from a D-source to a D-sink. The deterministic data-rate equals a guaranteed number of time-slot reservations within a periodic scheduling-frame consisting of F time-slots. Assuming that: (i) fiber-optic links support a data-rate of 800 Gbps, (ii) 1 Kbyte packets are transmitted in each time-slot, (iii) a scheduling-frame comprises F=16K time-slots, then each time-slot requires ≈ 20.48 nanoseconds, and the scheduling-frame requires ≈ 0.672 milliseconds.
Property 5 - Routing/Scheduling can Achieve ≈ 100% Utilization: The SDN control-plane will route every D-flow along a fixed path of D-switches, using a "Max-Flow Min-Cost" routing algorithm [
120], which can achieve ≈ 100% utilization in sub-layer 3a. The control-plane will determine a D-schedule for every edge in the SDD-WAN. Each D-schedule identifies the D-flow (or traffic class) with a transmission reservation, in each time-slot of the scheduling frame. Using the scheduling algorithms in [
42], the D-schedules can be circularly-rotated and still minimize buffer sizes and queuing delays, so that the D-switches do not need to be tightly synchronized. In practice, each D-switch must recognize a
’Start-of-Frame’ signal/packet from each of its neighbours, roughly once every millisecond [
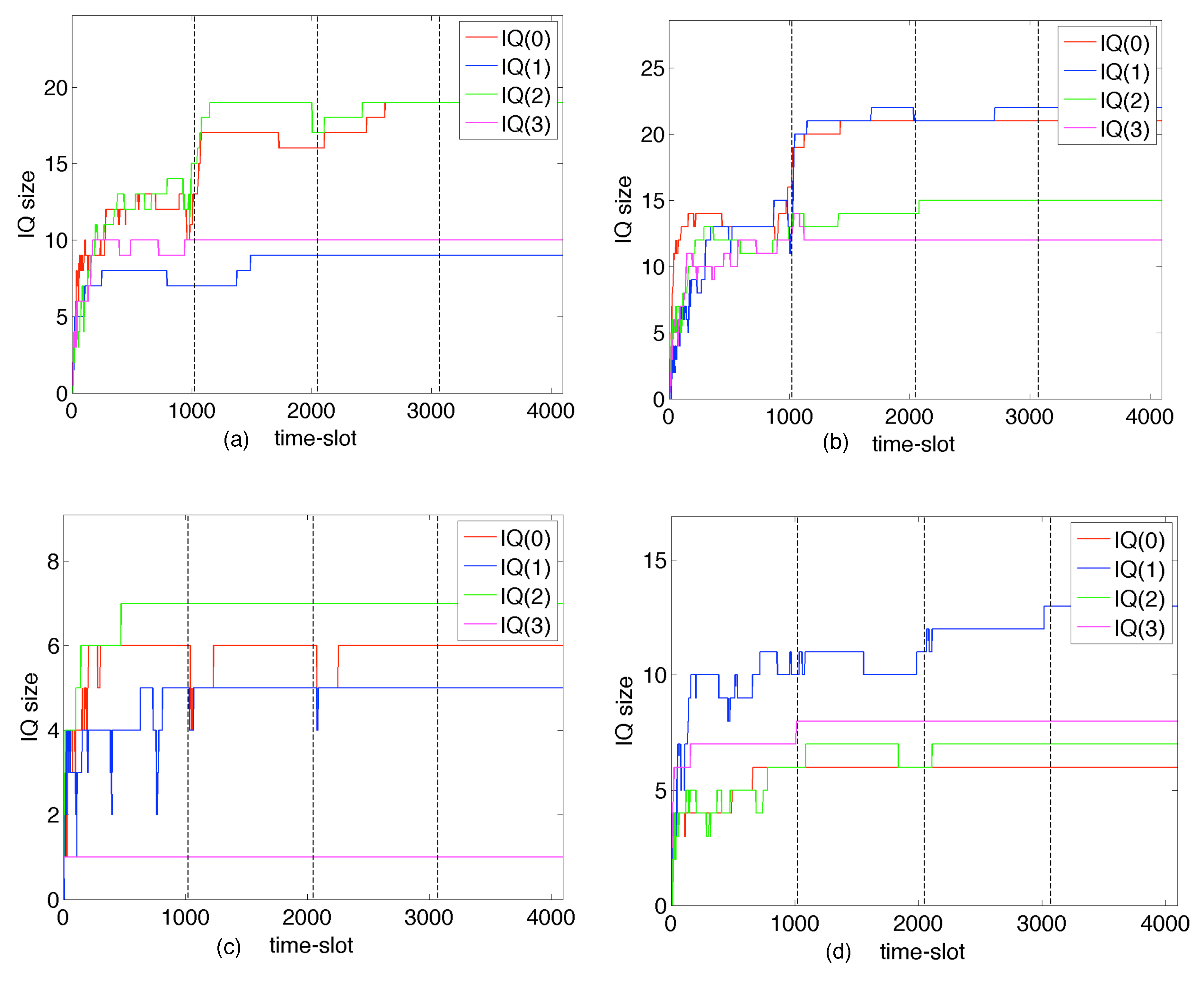
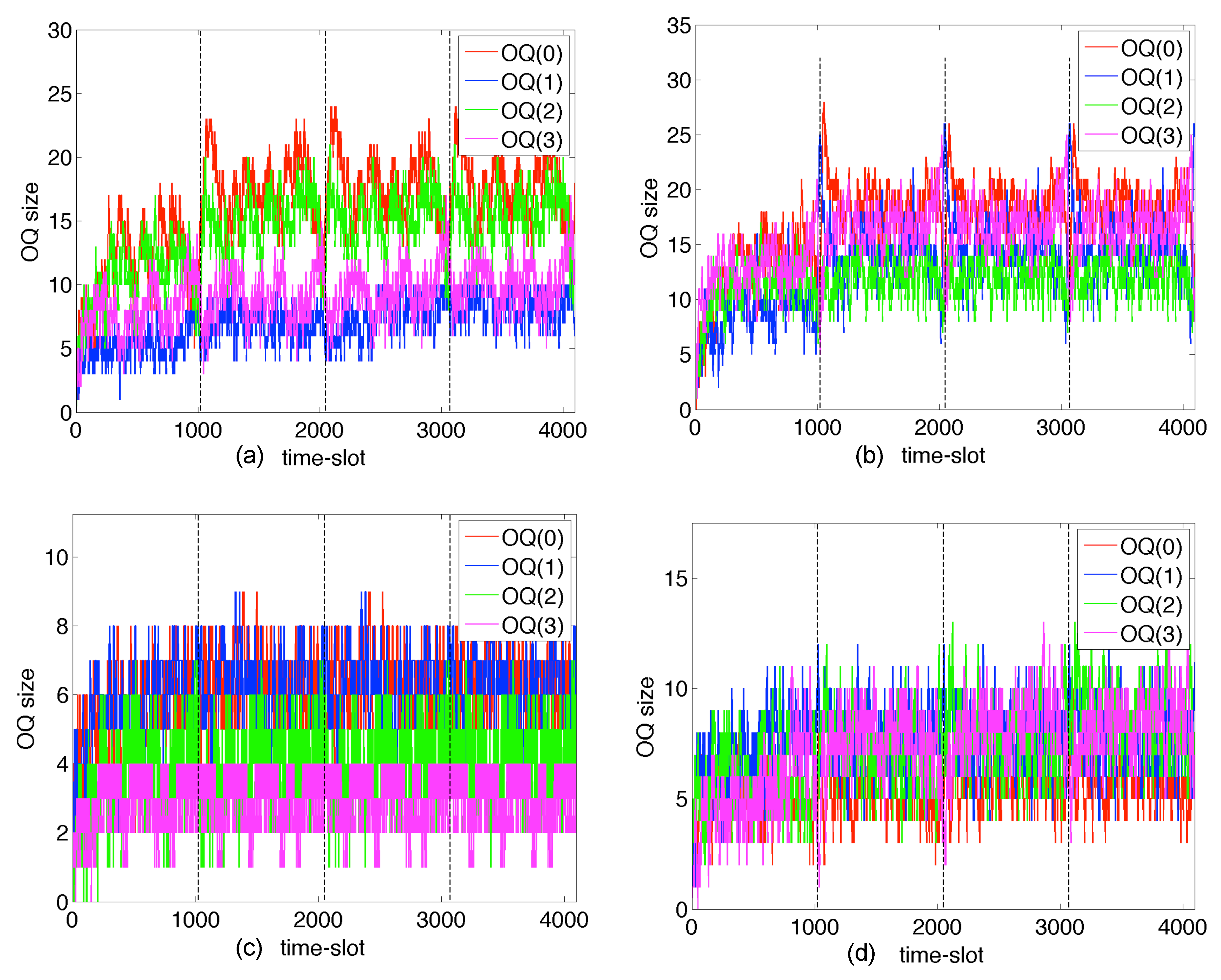
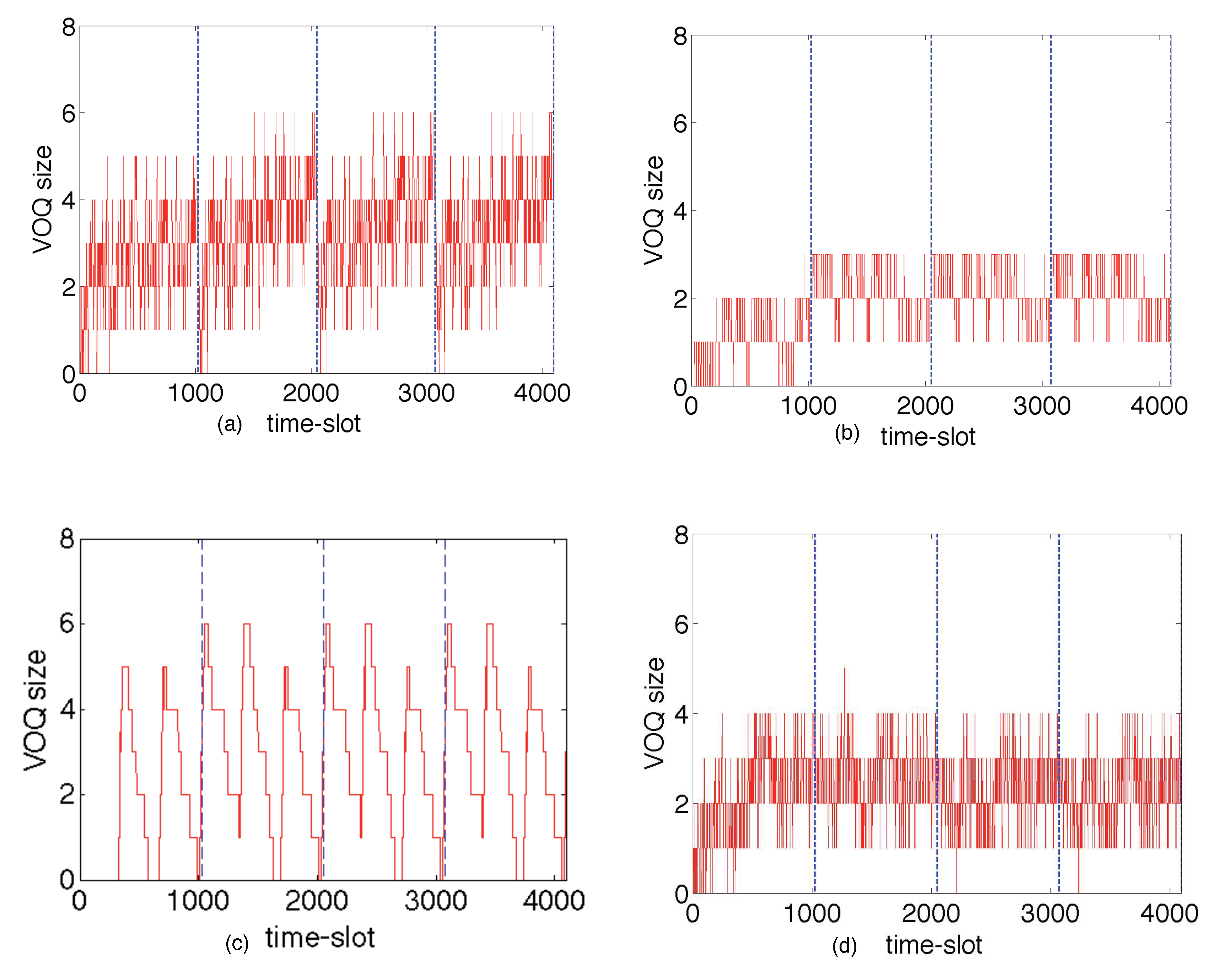
41]. The size of the packet queues can be reduced by factors of about 100,000 - 1,000,000 times compared to a BE-IP router (see section 6), and the end-to-end queueing delays can be reduced to the speed-of-light in fiber.
Property 6 - D-flows use End-to-End Quantum-Safe Encryption: The packets of D-flows within a D-VPN are encrypted at the D-source using Quantum-Safe AE ciphers, and can remain fully encrypted as they traverse the SDD-WAN from end-to-end. The packet headers do not need to be examined at intermediate D-switches to make layer-3 routing decisions. This property solves several significant weaknesses of the BE-IP network: (a) The insecure "Border Gateway Protocol" (BGP) routing used in layer-3 is eliminated; (b) The insecure "Domain Name Servers" (DNSs) used in layer-3 routing are eliminated; (c) The use of unencrypted and un-authenticated IP packet headers in layer-3 is eliminated. These headers are insecure and vulnerable to manipulation by cyber-attackers. (d) The need for middle-boxes to perform "Network Address Translation" (NAT) is eliminated.
Property 7 - Authorization-Checks at D-transceivers: Every packet received at a D-transceiver must undergo an "Authorization-Check". The packet will be decrypted and authenticated, using the secret AE keys associated with the D-flow at the D-transceiver. If the packet fails the authorization-check, then the packet is not delivered to any secured-computer, and the SDN control-plane is immediately informed of the anomaly. In order for a malicious packet from an external cyber-attacker to pass the authorization-check, the cyber-attacker must crack the Quantum-Safe AE key(s) used to authenticate/encrypt the packet. Assuming the AE keys support security levels AES-256 and higher, then it takes billions of years for a superconducting Quantum Computer to crack the AE ciphers. Hence, the probability a malicious packet can pass an Authorization-Check is zero.
Property 8 - The Guaranteed Intrusion Detection System: The D-switches/D-transceivers implement a "Guaranteed Intrusion Detection System" in FPGA hardware, where any un-authorized or malicious packet from an external cyber-attacker is detected in real-time. Consider 2 cases. Case 1: A packet that is transmitted over an edge in the SDD-WAN, in a time-slot for which no transmission-reservation exists. This anomaly is immediately detected at the receiving D-switch/D-transceiver. That packet is not forwarded, and the SDN control-plane is immediately informed. Case 2: Suppose an external cyber-attacker has compromised the SDD-WAN fiber, and managed to overwrite a valid packet transmission with a malicious packet transmission. That malicious packet will be delivered to the ultimate destination D-transceiver. However, by Property 7, it will fail the Authorization Check and be detected. That packet is not forwarded, and the SDN control-plane is immediately informed.
Property 9 - Redundant Paths for Reliability: For mission-critical applications, each "primary" D-flow is replaced with multiple (i.e., R >= 3) redundant D-flows, within one SDD-WAN. Each redundant D-flow is routed over an "edge-disjoint" path, i.e.., it does not share any edges with the primary path or any of the redundant paths. Every packet logically transmitted over the primary D-flow is replaced with R packets, transmitted over the R redundant paths. A receiving D-transceiver will eliminate duplicate copies and keep one copy of each packet. This scheme is similar to the IEEE 802.1 TSN FRER ("Frame Replication and Elimination for Reliability") proposal used in layer-2 networks. It is also similar to the IETF DetNet PREOF ("Packet Replication, Elimination and Ordering Function") protocol used in layer-3. (Mission-critical applications may also use "Forward-Error Correcting" (FEC) codes.) In order for the transmission of a packet in a primary D-flow to fail, all R redundant transmissions of the same packet must fail. Equivalently, all R redundant paths in one SDD-WAN must fail simultaneously. (This property exploits the principles of redundancy of hardware and redundancy of information, described in [
47].) The cost of providing multiple redundant paths in sub-layer-3a (using inexpensive D-switches) is much lower than the cost of providing multiple paths in layer-3 (using expensive BE-IP routers).
Property 10 - Redundant Paths for Cyber-security: The redundancy technique described in property 9, will also significantly improve cyber-security within one SDD-WAN. Let each independent path use an independent Quantum-Safe AE cipher. In order to insert an undetected malicious packet, a cyber-attacker must over-write R legitimate packets with R malicious packets, on R redundant paths within one SDD-WAN. In order to pass the R authorization checks, the cyber-attacker must also crack the R Quantum-Safe AE ciphers, used in these R redundant paths. However, it takes billions of years to crack even one AE-256 cipher. Hence, the use of redundant hardware paths and redundant information (packets) within one SDD-WAN will also significantly-improve cyber-security. (This property exploits the principles of redundancy of hardware and redundancy of information, described in [
47].) The probability a cyber-attacker can insert an undetected malicious packet into an SDD-WAN, when R redundant paths are used, is effectively zero. The use of multiple independent SDD-WANs, managed by independent cloud services providers, will also further improve cyber-security (see property 11).
Property 11 - Protecting Critical Infrastructure: Each nation will protect its critical infrastructures shown in
Table 1 from external cyber-attacks. Each nation will likely have multiple independent SDD-WANs, managed by independent service providers, such as Google or Amazon Web Services. The service providers can generate new revenue streams by offering SDD-WANs and D-VPNs, with ultra-reliable and ultra-low-latency communications, along with exceptionally cyber-security and with immunity to external cyber-attacks, as a new service.
For each M2M-flow for critical infrastructure, a service-provider could engage independent SDD-WANs, and utilize redundant edge-disjoint paths within each SDD-WAN. Each redundant path is protected with an independent Quantum-Safe AE cipher, with a security level of at least AES-256. Assuming all paths are operational, an attempted cyber-attack is detected if any one of the packets associated with the M2M-flow fails the authorization check. To insert an undetected malicious packet into an M2M D-flow, a cyber-attacker must overwrite R legitimate encrypted packets with R malicious packets, in each of S SDD-WANs, and pass all authorization checks. (It is difficult if not impossible to associate one encrypted packet with any one M2M-flow, as transmissions are encrypted, so just finding encrypted packets belonging to one M2M-flow in S SDD-WANs is virtually-impossible.) In order to pass all the authorization checks, the cyber-attacker must crack all of the AE ciphers used. However, it is infeasible for a cyber-attacker to crack even one Quantum-Safe cipher, let alone ciphers. It is impossible for a cyber-attacker to insert an undetected malicious packet into an M2M D-flow, assuming all paths are operational. The same argument applies if only some paths are operational. Hence, it is impossible for a cyber-attacker to insert an undetected malicious packet into an M2M D-flow, provided that at least one redundant path from the source to the destination is operational in the S independent SDD-WANs. The probability of a successful undetected external cyber-attack is zero, provided that at least one redundant path from the source to the destination is operational in at least one SDD-WAN.
Property 12 - Protection from Internal Cyber-Attackers: Internal cyber-attackers are defined as users who have obtained the secret keys or passwords needed to access a secured-system. Internal cyber-attackers can log into a secured-computer, and in absence of any other control-system, they could access critical resources and perform significant damage. To combat internal cyber-attackers, the US government implemented Executive Order 14028, which requires US industries to adopt the ZTA to control access to all critical resources [
66].
Network managers can develop a knowledge-base of rules, to detect all internal cyber-attackers, including: (i) un-authorized users, and (ii) authorized users trying to perform un-authorized tasks. Un-authorized users can be detected and eliminated by using rules that exploit biometric data. Authorized users trying to perform un-authorized tasks can be detected and eliminated by using rules to explicitly identify what authorized users are allowed to do.
The performance of exceptionally-important tasks could have rules to require the approval of multiple senior-level approved-users, so that any one authorized user cannot compromise the system. For example, access to a secured-computer with "top-secret" information could require the approval of multiple senior-level users, each authenticated with biometric data. Hence, the use of ZTAs with a comprehensive knowledge-base of rules, is the best-known method to achieve exceptionally-strong protection against internal cyber-attackers.
5.1. QKD Networks versus the SDD-WAN
In principle, QKD ("Quantum Key Distribution") Networks can supply "perfectly-secret" keys between pairs of users, thus enabling "Perfect-Secret" communications. The "perfectly-secret" nature of the keys is guaranteed by the Laws of Physics. However, the US "National Security Agency" (NSA) does not recommend the use of QKD networks [
86]. The "National Cyber Security Center" (NCSC) in the UK, and the "Agence National de la Securite des Systems d’Information" (ANSSI) in France also do not recommend the use of QKD networks.
The US NSA outlines 5 drawbacks to QKD networks, as shown in
Table 4. Several papers have also discussed these drawbacks of QKD networks [
127,
128,
129,
130,
131].
Problem 1: QKD Networks cannot Authenticate the Source: It is well-known that QKD networks require "classical authenticated channels" for control. According to NIST, QKD Networks cannot authenticate the source. External hardware must be added to authenticate the source, which is usually achieved using dedicated point-to-point links, along with Pre-Shared (secret) Keys (PSK) and Symmetric Key Cryptography (SKC). Post-Quantum Cryptography (PQC) can also be used. Hence, the security of QKD network is now limited by the security of SKC or PQC, i.e., the computational hardness of cracking SKC/PQC.
Problem 2: QKD Networks Vulnerable to Insider Attackers: As shown in
Table 5, according to the US NIST, QKD networks are vulnerable to insider (internal) cyber-attackers. Internal cyber-attackers could compromise the trusted relays in a QKD network, to compromise the security of the QKD keys. As stated in Property 12, these insider attacks can be mitigated with an AC/AC system, using Zero-Trust-Architectures, to control which "insiders" are authorized to access the system, and what these insiders are authorized to do. Network managers can develop a knowledge-base of rules, to detect (i) un-authorized users, and (ii) authorized users trying to perform un-authorized tasks. Un-authorized users can be detected by using rules that exploit biometric data. Authorized users trying to perform un-authorized tasks can be detected by using rules to explicitly identify what authorized users are allowed to do. The administration/control of the AC/AC system typically requires PSK, along with SKC or PQC. Hence, the security of QKD network is again limited by the computational hardness of cracking SKC/PQC.
Problem 3: QKD Networks Vulnerable to DoS/DDoS Attacks: As shown in
Table 5, according to the US NIST "there is no known way to prevent a flooding DoS attack against hosts visible on the Internet". As shown in
Table 5, according to the US NIST, even QKD networks are vulnerable to DoS flooding attacks. According to the industry, DoS/DDoS attacks have been called "one of the most powerful weapons on the Internet". QKD networks are vulnerable to such attacks, to prevent the perfectly-secret keys from being delivered. Even TLS-flows in the Consumer-IoT, using perfectly-secret keys from a QKD network, are vulnerable to layer-3 DoS/DDoS attacks. According to [
128], the vulnerability of QKD networks to DoS/DDoS attacks has no clear defense.
Problem 4: QKD Networks will require Software "Key Management Systems": A "Key Management System" (KMS) will allow for the scaling upwards, from small link-to-link quantum key generation systems, towards large-scale quantum key distribution networks [
132,
133]. The ETSI is working to define standards for the KMS and the software interface to access the KMS and keys. The administration/control of these software systems typically requires pre-shared secret keys, along with SKC or PQC. Hence, the security of QKD network is again limited by the computational hardness of cracking SKC/PQC.
SDD-WANs Can Support QKD Networks: Prior to this paper, there is no known multi-user layer-3 WAN with immunity to external cyber-attacks, which can provide "authenticated classical channels" to control QKD networks. The SDD-WANs proposed in this paper can thus enable QKD networks, by providing the "classical authenticated channels" needed for the control of QKD networks, in a programmable layer-3 network which is immune to external cyber-attacks.
SDD-WANs versus QKD Networks: In practice, the security of QKD networks is strongly limited by the drawbacks shown in
Table 5. It is said that "a chain is as strong as its weakest link", and the use of QKD networks entails several "weakest links" shown above. The security of the QKD network is limited by: (i) The cryptography used to authenticate the source (i.e., SKC/PQC); (ii) The cryptography used to administer/control the AC/AC system, necessary to control internal cyber-attackers (i.e., SKC/PQC); (iii) The cryptography used to administer/control the AC/AC system, necessary to control the vulnerabilities to DoS/DDoS flooding attacks against QKD networks (i.e., SKC/PQC); (iv) The cryptography used to administer/control the AC/AC system, necessary to control the Key Management System (i.e., SKC/PQC). For these reasons, the US NSA, the UK NCSC and the France ANSSI do not recommend the use of QKD networks.
Fortunately, the use of SDD-WAN can address all 4 of these problems, by adding an AC/AC system, and thus the SDD-WANs can enable/support the use of QKD networks. However, given these vulnerabilities and given that the security of QKD networks is now limited to the computational hardness of cracking SKC/PQC due to several "weakest links", one can also question whether the use of QKD is necessary.
Several researchers have stated that the drawbacks of QKD networks shown in
Table 5 may be solved with time. Reference [
134] states that "more research is needed to develop a comprehensive security ecosystem". Reference [
130] states that "the best that can be done at present is to integrate QKD with cryptographic schemes based on computational problems". Suppose it will take 20-30 years to fix the problems of QKD networks, to allow QKD networks to be deployed on a large-scale to millions/billions of users world-wide. The world then needs a temporary solution for today’s cyber-security crisis, a solution that can last for the next 20-30 years, until QKD networks are ready to be deployed on a large scale. The SDD-WANs can provide a solution to today’s cyber-security crisis, as they offer comparable security to QKD networks in practice, secured by the computational hardness of cracking SKC/PQC. The SDD-WANs also offer significant cost savings.
7. The Costs of the layer-3 BE-IP Network
Table 6 shows the 2022 annual revenues for many layer-3 equipment manufacturers in US dollars (please see their 2022 annual reports). (Alcatel/Lucent Technologies was purchased by Nokia in 2015). In 2022, Cisco reported revenues of US
$51.6 billion. About 75% of this figure represents products, while about 25% represents services. In 2022, the total global revenue is ≈ US
$180 Billion USD. Assuming 50% of the total represents the revenue for layer-3 equipment, then the global capital costs of layer-3 BE-IP equipment can be estimated at ≈ US
$90 Billion in 2022.
Cisco estimates that about 95% of configuration changes in layer-3 equipment (i.e., routers and firewalls) are performed manually [
10,
11], and that the annual operational costs of layer-3 are about 2.5 times the annual capital costs. Hence, the global operational costs can be estimated at ≈ US
$225 billion annually (in 2022). The combined global capital and operational costs for layer-3 are about US
$315 billion annually in 2022.
According to Cisco, the global Internet carried about 9.1 billion Gigabytes of traffic per day in 2021, corresponding to an average global Internet traffic rate of 847 Tbps (Terabits per second) [
10,
11]. According to Google, layer-3 links operate at ≈ 25% utilization [
100]. Hence, the global costs (capital and operational) due to "over-provisioning" can be estimated at 75% of the total global costs, i.e., US
$236 billion annually in 2022. The use of SDD-WANs can improve the performance of the global Consumer-IoT network, by migrating traffic from the Best-Effort pillar to the Deterministic pillar shown in
Figure 1b. The SDD-WAN in sub-layer-3a offers a much higher capacity with much lower delays, and much lower costs.
Consider the SDD-WAN for the EU shown in
Figure 2b with 28 cities, each with a D-switch. Let each D-switch uses 10 parallel Intel Stratix FPGAs, for a capacity of ≈ 35 Tbps. The cost of 280 FPGAs is ≈ US
$2.1 million. Each FPGA requires some extra components (i.e., transducers (i.e., electrical-to-optical), D-transceivers, and power supplies), costing ≈
$150K. The total capital cost for the EU network is ≈ US
$44 million, a relatively small value. The peak capacity is ≈ 980 Tbps, slightly larger than the average global Internet traffic rate of 847 Tbps (in 2021). The peak capacity of the SDD-WAN equals ≈ 10.5 billion Gigabytes of traffic per day.
Assuming 1 Kbyte packets, the FPGAs can transmit about 119 billion packets per second over the EU. Recall that the FPGAs implement "Guaranteed Intrusion Detection Systems" in hardware. The FPGAs can easily detect even a single un-authorized or malicious packet, sent from any type of external cyber-attacker, out of ≈ 119 billion transmitted packets/second. Equivalently, the FPGAs can can detect even a single un-authorized/malicious packet, embedded within ≈ 10.5 billion Gigabytes of traffic/day traversing the SDD-WAN. The SDD-WAN over the EU offers a vast capacity for a negligible cost, and provides exceptionally-strong hardware-enforced cyber-security.
The same technology can improve cyber-security for critical infrastructure, in smaller Regional Area, Metro Area and Local Area Networks. If twenty times as many FPGAs are introduced into the EU (i.e., 4480 FPGAs), then the peak capacity is ≈ 19,600 Tbps, and the capital cost is ≈ US$880 million (which is relatively small, compared to global capital and operational costs of layer-3).
According to Cisco, the majority of layer-3 traffic in the Consumer-IoT was IP-video in 2021 (about 82%). Let the IP-video traffic be migrated to the SDD-WAN in the Deterministic pillar in
Figure 1b, and transported by D-flows. This migration can lower the capital and operational costs of the layer-3 Consumer-IoT by ≈ 82% each. The global cost savings can reach 82% of the combined global capital and operational costs of ≈ US
$315 billion annually, equalling a savings of about US
$260 billion annually. It is safe to say that the cost savings are in the range US
$100s of billion annually.
7.1. MPLS-like Flow-Labels in Sub-layer 3a
The layer-3 BE-IP network includes many "Multi Protocol Label Switching" (MPLS) WANs. An MPLS-WAN consists of an MPLS control-plane, and a forwarding-plane of many MPLS packet-switches, similar to
Figure 3a. Each MPLS packet includes a "flow-label" in its header, to identify the traffic flow. Each MPLS-switch maintains a "flow-table", that stores several values associated with each D-flow, i.e., the desired output port. The D-switches can be modified to perform some simple packet header processing in sub-layer-3a. The D-switches can still retain a dramatic simplification compared to a layer-3 BE-IP router, as they do not perform complex layer-3 routing and scheduling algorithms. The routing and scheduling is still performed in the SDN control-plane.
For example, packets in a D-flow can use "flow-labels" to identify the D-flow. Flow-labels typically have about 20-24 bits (MPLS flow-labels have 24 bits, and IPv6 flow-labels have 20 bits). Each input port in a D-switch can have a high-speed "flow-table", with an entry for each possible flow-label. When a packet arrives at an input port, its flow-label is used to access a row of the flow-table. The row yields the desired output port for the packet, and a new flow-label to be used for the outgoing packet. The SDN control-plane maintains the flow-tables in each D-switch. This approach offers three advantages: (a) it keeps the complex layer-3 routing and scheduling algorithms in the SDN control-plane, so that D-switches remain simple and secure; (b) it eliminates the need to loosely-synchronize D-switches in sub-layer-3a, as each packet will now carry a flow-label in its header to be used in a lookup-table in each D-switch; (c) it retains the security features of the proposed SDD-IIoT (as every packet in a D-VPN must still pass the "Authorization Check" at a D-transceiver).