1. Introduction and Motivation
In an era where digital communication underpins the fabric of global connectivity, the role of cryptography is more critical than ever. Ensuring the security and integrity of data in transit has led to the evolution of sophisticated cryptographic protocols. Traditional approaches often rely on the well-established mathematical frameworks of finite fields, but with the advent of advanced computational capabilities and emerging cyber threats, the need for innovative and more efficient cryptographic methods is evident. This paper contributes to this ongoing evolution by introducing a groundbreaking approach to key exchange protocols utilizing the untapped potential of tropical semirings and block matrices.
This research transcends the conventional boundaries of cryptographic solutions, delving into the realms of tropical mathematics to harness the simplicity and computational efficiency offered by tropical semirings. Coupled with this, the use of block matrices introduces a structural robustness that enhances security measures. This combination not only serves as a novel approach but also sets a new benchmark in operational efficiency, steering away from the computational complexities inherent in finite fields .
Historically, matrices have been instrumental in various cryptographic mechanisms. The lineage of matrix-based cryptosystems, stretching back to foundational works such as [
1], has been marked by continual advancements. Diverse matrix forms were incorporated, ranging from singular [
2,
3] and non-singular matrices [
4] to matrices over bit strings [
5]; Tribonacci matrices [
6]; Hadamar matrices [
7]; non-negative [
8] and lattice matrices [
9]. Tropical matrices are also of interest ([
10,
11,
12,
13,
14,
15]). Yet, despite these developments, vulnerabilities have persisted, as evidenced by different documented attacks (see, for example, [
16,
17,
18,
19]).
In recent years, a variety of block matrix cryptosystems have emerged: [
20] introduced a method employing the Hilbert matrix for authentication and confidentiality, emphasizing shared key encryption; [
21] constructed an invertible block matrix using Fibonacci sequences and devised an asymmetric cryptosystem utilizing the skewed affine cipher over elliptic curves; [
22] proposed a novel block-cipher mechanism for ensuring information security in cloud systems, prioritizing high defense, low complexity, and random operations. Together, these studies showcase the potential of block matrix cryptosystems in enhancing data security.
Our protocols are designed to counteract the vulnerabilities of the schemes based on tropical matrices by employing commutative properties of block matrices, resulting in a more streamlined and secure key exchange process.
The contributions of this study are multifaceted and significant:
- 1.
We introduce two key exchange protocols that exploit the commutative properties of tropical block matrices, thereby simplifying the key exchange process while enhancing security.
- 2.
A thorough analysis is presented, demonstrating the reduced operational overhead compared to existing block matrix schemes. This includes comparative evaluations showing lower computational complexity while maintaining equivalent key sizes.
- 3.
We anchor our security claims in the inherent difficulty of matrix decomposition within tropical semirings, a challenge that poses significant barriers to conventional attack methodologies.
- 4.
The paper also includes illustrative examples and comparative analyses to underscore the tangible efficiency gains our protocols offer.
This paper is structured to guide the reader through the critical aspects of our research.
Section 2 sets the mathematical foundation by introducing block matrices, tropical semirings, and commutative matrices.
Section 3 provides a detailed exposition of our proposed key exchange protocols.
Section 4 delves into the security analysis, benchmarking our approach against current cryptographic standards. Finally, we conclude in
Section 5 with reflections on the broader implications of our work and its potential to inspire future research in cryptography.
2. Preliminaries
Definition 1 (Block Matrix).
A block matrix is a matrix partitioned into submatrices, referred to as blocks. For instance, a block matrix M comprising four blocks can be denoted as:
where and D are such blocks. These blocks may vary in size, and the total number of blocks and their configuration is dependent on how the original matrix is partitioned.
Definition 2 (Semiring). A semiring is an algebraic structure represented by , where S is a set, and the operations ⊕ (addition) and ⊗ (multiplication) satisfy the following conditions:
forms a commutative monoid with identity element 0.
forms a monoid with identity element 1.
⊗ distributes over ⊕.
For all , .
The semiring is commutative if for all .
Definition 3 (Matrix Operations over Semirings). Given matrices A and B over a semiring , the operations are defined as follows:
Addition is the element-wise operation .
Multiplication is performed using the standard matrix multiplication rules applied with ⊗.
Scalar multiplication scales each matrix element by x to obtain .
These operations follow the distributive, associative, and commutative laws pertaining to the semiring.
2.1. Exponentiation of Block Matrices
We examine block matrices formed as:
where
and
C are square matrices of the same order over a considered semiring, and
O is the corresponding zero matrix.
Theorem 1.
[23] Let
be a block matrix. Then for any natural number k, it holds that
with
and furthermore,
with for all .
Theorem 2. [23] Let and E be square matrices of the same order such that , , and consider the block matrices and . Then for all .
2.2. Tropical Semirings
A tropical semiring, such as ( or ) is a set equipped with two operations that mimic conventional addition and multiplication, but instead are defined using the maximum and addition (or maximum and addition), respectively. This semiring and its operations enable the definition of tropical matrix operations and polynomials.
Definition 4 (Tropical Polynomial).
A tropical polynomial of a variable x with coefficients in a tropical semiring is an expression of the form
where n indicates the degree of the polynomial.
Proposition 1.
For tropical polynomials and , and a matrix M over a tropical semiring, it holds that
Proof. The commutativity follows from the properties of matrix multiplication in tropical semirings. □
2.3. Commutative Matrices in Tropical Semirings
Commutative matrices in tropical semirings have the property that their product, irrespective of the order, yields the same result. This property is crucial for the development of cryptographic protocols that rely on the difficulty of matrix decomposition in tropical semirings.
Definition 5 (Linde-de la Puente Matrix). A matrix L in the semiring is called a Linde-de la Puente matrix if it satisfies certain criteria based on specified non-negative real number c for its diagonal entries and its off-diagonal entries are from the range , where r is a non-positive real number. Such a matrix is denoted as: .
Theorem 3. [15] Given a tropical semiring . All Linde-de la Puente matrices A and B commute under the multiplication in this semiring.
Corollary 1. Given a tropical semiring . For Linde-de la Puente matrices A and B, and natural numbers m and n, the matrices and commute.
Proof. This result is a direct consequence of the commutative property of Linde-de la Puente matrices. □
3. Block Matrix Key Exchange Protocols
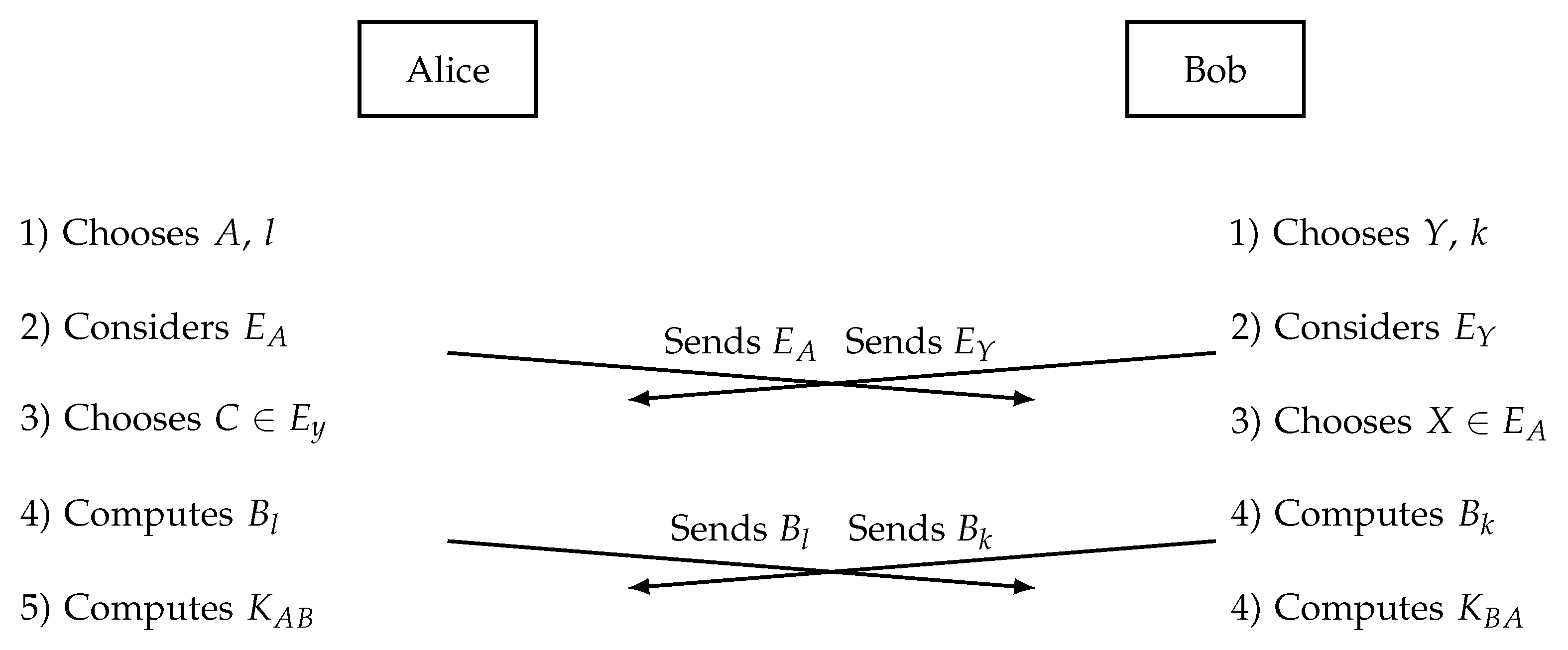
In this section, we propose an improvement on a well-known Block Matrix Key Exchange Protocol (BMKEP) proposed by [
23].
3.1. The original protocol
We first recall the BMKEP suggested in [
23]. The domain parameters of this protocol are prime number
p and a square matrix
B with entries from the finite field
(where
q is a power of
p).
- 1.
Alice chooses as her private keys: one positive integer l and a matrix . She transmits the set of matrices commuting with A.
- 2.
Bob chooses as his private keys: one positive integer k and a matrix . He transmits the set of matrices commuting with Y.
- 3.
Alice chooses her second private key: a matrix
. She calculates:
and sends
to Bob.
- 4.
Bob chooses his second private key: a matrix
. He calculates:
and sends
to Alice.
- 5.
Alice computes the common private key:
- 6.
Bob computes the common private key:
At the end of the protocol, the users get the same key, due to the fact that , , and the properties of the block matrices (Theorem 2).
This protocol requires the exchange of sets of matrices and commuting with A and Y, respectively. This means more time and space. To overcome this problem, we suggest avoiding these steps by using properly selected commutative matrices. In general, our idea for improving this protocol is as follows:
- 1.
Alice selects matrices A and B, and Bob selects matrices C and D with the property that A and C commute; B and D also commute. This means that A and C belong to the same set of commuting matrices, B and D belong to the same set of commuting matrices. Alice and Bob agree on a matrix T. The secret keys of the users are positive integers a and b, respectively,
- 2.
-
She sends her public key to Bob.
- 3.
-
He sends his public key to Alice.
- 4.
Alice computes the common key:
- 5.
Bob computes the common key:
The implementation of the protocol is shown in
Figure 1.
3.2. Proposed Solution
The main idea behind our protocols is to utilize block matrices with commutative matrix blocks to simplify the key exchange process. By selecting matrix blocks that commute, we eliminate the need to transmit sets of commuting matrices publicly.
We construct block matrices of the form:
Here
and
T are square matrices of the same order, and
O is the zero matrix of this order. Alice and Bob each select their own their own pair of matrices (
) and (
) such that
A commutes with
C, and
B commutes with
D. This allows them to compute a common key.
3.3. Protocol Steps
The refined protocol unfolds in the following sequence:
- 1.
Both parties agree on a common matrix T.
- 2.
Alice opts for matrices A and B, while Bob picks matrices C and D. They ensure that A commutes with C and B with D.
- 3.
Alice calculates . Her public key is set as .
- 4.
Bob, in a parallel manner, computes . He sets his public key as .
- 5.
They then exchange their public keys.
- 6.
Using Bob’s public key and her private matrices, Alice computes the shared key, .
- 7.
Similarly, using Alice’s public key and his private matrices, Bob computes the shared key, .
- 8.
Due to the inherent commutative properties, both parties find that .
Here we give two examples for implementation of the above presented protocol, based on a tropical semiring.
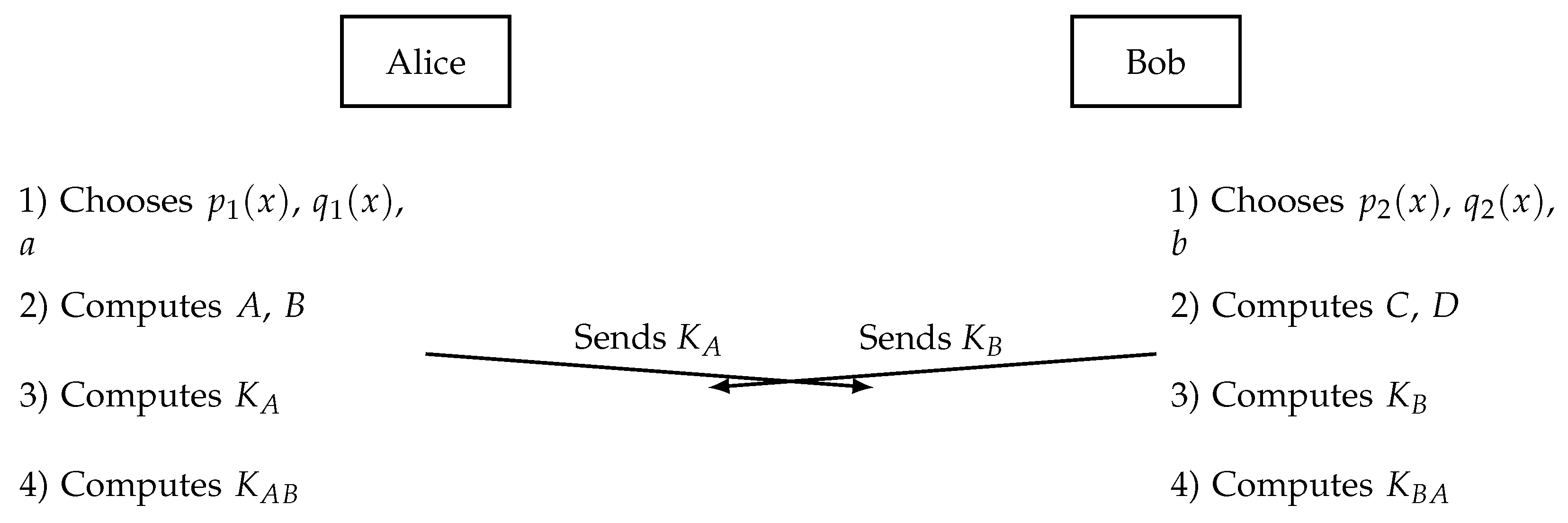
3.4. Implementation one - Tropical Block Matrix KEP using Polynomials of Matrices
The domain parameters of this protocol are: tropical semiring or , and three arbitrary square tropical matrices M, N, and T of order n over this semiring.
- 1.
-
Alice selects as her secret key two tropical polynomials
and
, and a positive integer
a. She computes:
She sends her public key to Bob.
- 2.
-
Bob selects as his secret key two tropical polynomials
and
, and a positive integer
b. He computes:
He sends his public key to Alice.
- 3.
Alice computes the common key:
- 4.
Bob computes the common key:
At the end of the protocol, the users obtain the same secret key due to the following:
Proof. In accordance with the choice of the matrices
A,
B,
C,
D, it follows that
(the multiplication of tropical polynomials of matrices is commutative). Additionally, conforming to Theorem 2:
□
The execution of this protocol is illustrated in
Figure 2.
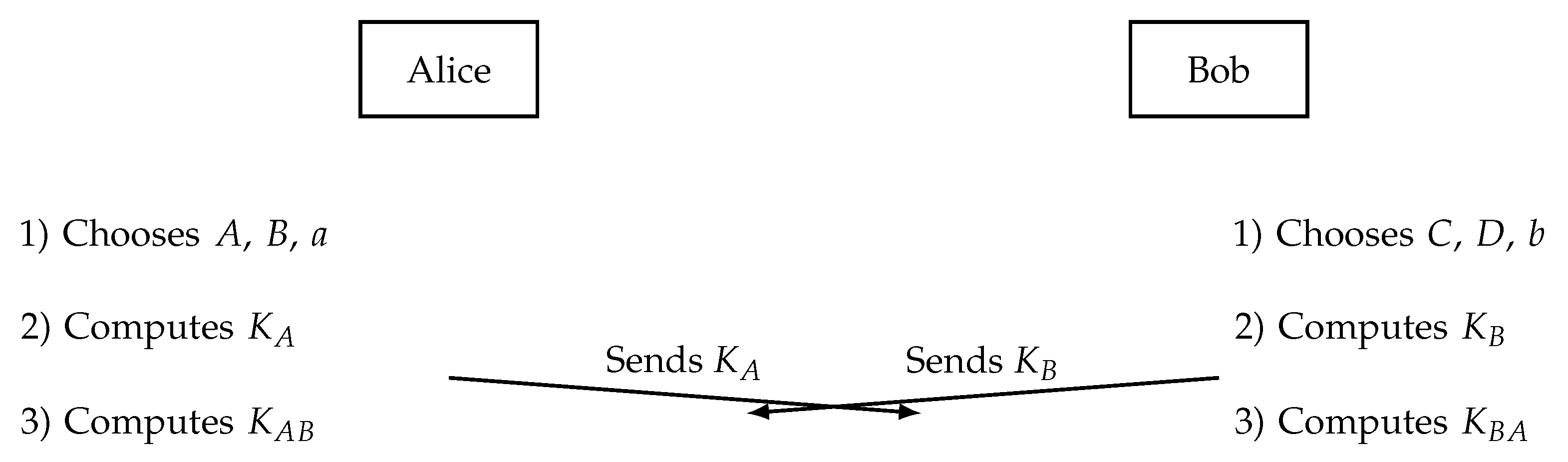
3.5. Implementation two - Tropical Block Matrix KEP using Linde-de la Puente Matrices
The domain parameters of this protocol are: tropical semiring , one negative real number r, one positive real number c, and an arbitrary square tropical matrix T of order n over this semiring.
- 1.
-
Alice selects as her secret key two Linde-de la Puente matrices
and
, and a positive integer
a. She computes:
where
She sends her public key to Bob.
- 2.
-
Bob selects as his secret key two Linde-de la Puente matrices
and
, and a positive integer
b. He computes:
where
He sends his public key to Alice.
- 3.
Alice computes the common key:
- 4.
Bob computes the common key:
At the end of the protocol, the users obtain the same secret key due to Theorem 3 and Corollary 3.1.
The execution of the protocol is shown in
Figure 3.
3.6. Advantages of our Protocols
Here we outline some of the advantages of our protocols:
In the protocol suggested in [
23], 4 messages are exchanged between users via a public (unsecured) channel. In our protocols, only two messages are exchanged. This results in Improved security and Saving time and resources.
Our protocols operate in tropical semirings, where the operations are only max/min and +. This means that operations in our protocols are significantly faster than operations in the finite field .
Our protocols do not use linear expressions for the general term, thus rendering traditional linear algebra tools ineffective.
4. Security Analysis
The security framework of our proposed tropical block matrix key exchange protocols is anchored in the computational hardness of the Matrix Decomposition Problem within tropical semirings. This problem is known for its formidable complexity, making it an ideal basis for cryptographic security. Crucially, our protocols are designed such that, even with knowledge of the communication transcript and public parameters, an adversary cannot feasibly distinguish the session key derived from the protocol from a random bitstring. This aligns with the contemporary standards for cryptographic protocol security [
24].
4.1. Matrix Decomposition Problem
The core challenge underpinning our protocols is the Matrix Decomposition Problem, defined as follows: Given matrices
, the problem is to find matrices
and an integer
a satisfying the equation:
Essentially, this entails decomposing the matrix
K into a series of operations involving its constituent block matrices. The complexity of this problem is a crucial aspect of our security argument. Notably, the best-known algorithms for such a decomposition, including Gauss-Jordan elimination and LU decomposition, exhibit exponential runtime complexity (
) for a matrix of dimension
n. This level of computational demand renders the problem intractable for practical purposes, especially when considering the suggested parameter sizes [
1].
4.2. Parameters for Enhanced Security
To strengthen the resistance against brute-force attacks and to align with the cryptographic principle that the session key should be indistinguishable from a random bitstring by an adversary, we recommend the following parameter settings for our protocols:
Employ tropical matrices of at least order 60, ensuring a substantial level of complexity in the matrix operations.
Select matrix entries randomly within the range , which expands the solution space significantly.
The secret integers a and b should be chosen to be no less than , further increasing the computational challenge for any potential attacker.
With these parameters, our protocols not only meet but exceed the contemporary requirements for cryptographic security, effectively mitigating the risk of key exposure and unauthorized decryption.
4.3. Comparison with Existing Protocols
Compared to conventional commutative matrix-based key exchange protocols, the proposed tropical matrix protocols exhibit several advantages:
Reduced key sizes are a feature since commuting matrix sets are not exchanged. For an matrix, only values are transmitted instead of .
The protocols leverage the computational efficiency of tropical semirings, where matrix multiplication is performed in time rather than time as in finite fields.
A decrease in the number of message exchanges is also observed, with the proposed protocols requiring only two exchanges compared to four in traditional approaches, thus reducing communication overhead.
The performance and resource usage metrics are detailed in
Table 1, which illustrates the duration (in seconds) and memory sizes (in MB) for each protocol variation across different matrix sizes. As matrix size increases, the resource demands also tend to increase, which is a crucial factor in evaluating the scalability of the protocols.
Table 2 depicts the private and public key sizes (in KB) for each protocol variation. It shows the growth of key sizes with an increase in matrix dimension, highlighting the trade-off between security and resource requirements. The disproportionality between private and public key sizes is also noteworthy, indicating the asymmetry in the computational load between key generation and verification processes.
5. Conclusion
In the dynamic realm of cryptographic research, innovations are imperative to address the ever-evolving challenges of digital security. Our study has ventured into the unique domain of tropical semirings and block matrices, presenting protocols that are poised to redefine the efficiency and security paradigms of key exchange mechanisms.
Central to our contribution is the operational efficiency that tropical semirings introduce. Moreover, our protocols do not employ linear expressions for the general term, which makes traditional linear algebra tools ineffective. By circumventing the computational intricacies typical of finite fields , our approach manifests both swiftness and an enhanced layer of security. This duality is paramount in today’s digital age, where secure communications underpin a plethora of applications, from financial transactions to personal messaging.
Furthermore, our research does not just stand as an endpoint but rather as a launchpad for future explorations. The mathematical properties of tropical semirings, juxtaposed with the versatility of block matrices, hint at vast cryptographic landscapes yet to be charted. There’s also the tantalizing opportunity of amalgamating our protocols with existing cryptographic frameworks, giving rise to hybrid systems that could potentially be more resilient than their individual counterparts.
In closing, our exploration underscores the profound impact that novel mathematical structures can impart to the field of cryptography. As we harness the capabilities of tropical semirings and block matrices, we’re not only charting a new course for key exchange protocols but also kindling a beacon for future endeavors in the realm of secure communications. The cryptographic community now has a fertile ground for further research, and it will be intriguing to witness the subsequent innovations that build upon our foundational work.
References
- Varadharajan, V.; Odoni, R. Extension of rsa cryptosystems to matrix rings. Cryptologia 1985, 9, 140–153. [Google Scholar] [CrossRef]
- Maxrizal. Public Key Cryptosystem Based on Singular Matrix. Trends in Sciences 2022, 19. [Google Scholar] [CrossRef]
- Maxrizal; Prayanti, B.; Sujono. Generalization of Public Key Cryptosystem Based on Singular Matrix Using Ring of Integer Modulo 2022. pp. 1–4. [CrossRef]
- Maxrizal; Irawadi, S. Nonsingular matrix as private key on ElGamal cryptosystem 2021. 1821. [CrossRef]
- Rahman, N.; Shpilrain, V. MOBS: Matrices Over Bit Strings public key exchange. IACR Cryptology ePrint Archive 2021, pp. 1–7. Also available at: https://ia.cr/2021/560.
- Gupta, S.; Sanghi, M. A New Digital Signature Scheme Using Tribonacci Matrices. International Journal of Computer and Information Technology(2279-0764) 2020, 9, 64–71. [Google Scholar] [CrossRef]
- Koukouvinos, C.; Simos, D. Encryption Schemes based on Hadamard Matrices with Circulant Cores Design of Cryptographic Algorithms. Unknown Journal 2013, 3, 17–41. [Google Scholar]
- Zhang, L., T. C.S.Y.H.H.T.H.; Lei, Z. Optical single-channel cryptosystem based on the non-negative matrix factorization and face biometric in cyan-magenta-yellow-black color space. Journal of the Optical Society of America. A, Optics, image science, and vision 2023, 40, 2146–2155. [Google Scholar] [CrossRef] [PubMed]
- Gudepu, R.; Rao, D. A public key cryptosystem based on lattice matrices. Journal of Mathematical and Computational Science 2020, 10, 2408–2421. [Google Scholar] [CrossRef]
- Durcheva, M. Semirings as building blocks in cryptography; Cambridge Scholars Publishing, 2020.
- Durcheva, M. TrES: Tropical Encryption Scheme Based on Double Key Exchange. European Journal of Information Technologies and Computer Science 2022, 2, 11–17. [Google Scholar] [CrossRef]
- Huang, H.; Li, C.; Deng, L. Public-Key Cryptography Based on Tropical Circular Matrices. Applied Sciences 2022, 12, 1–12. [Google Scholar] [CrossRef]
- Huang, H. Cryptosystems Based on Tropical Congruent Transformation of Symmetric Matrices. Symmetry 2022, 14. [Google Scholar] [CrossRef]
- Huang, H.; Li, C. Tropical Cryptography Based on Multiple Exponentiation Problem of Matrices. Security and Communication Networks 2022. [Google Scholar] [CrossRef]
- Muanalifah, A.; Sergeev, S. Modifying the Tropical Version of Stickel’s Key Exchange Protocol. Applications of Mathematics 2020, 65, 727–753. [Google Scholar] [CrossRef]
- Battarbee, C.; Kahrobaei, D.; Shahandashti, S. Cryptanalysis of Semidirect Product Key Exchange Using Matrices Over Non-Commutative Rings 2021. pp. 1–11.
- Battarbee, C.; others. On the efficiency of a general attack against the MOBS cryptosystem. Journal of Mathematical Cryptology 2022, 16, 289–297. [Google Scholar] [CrossRef]
- Jiang, X.; Huang, H.; Pan, G. Cryptanalysis of Tropical Encryption Scheme Based on Double Key Exchange. Journal of Cyber Security and Mobility 2023, 12, 205–220. [Google Scholar] [CrossRef]
- Brown, D.; Koblitz, N.; Legrow, J. Cryptanalysis of “ MAKE ”. Journal of Mathematical Cryptology 2022, 16, 98–102. [Google Scholar] [CrossRef]
- Raja, K. N..A.P. A Cryptosystem Based on Hilbert Matrix using Cipher Block Chaining Mode. ArXiv, abs/1110.1498, 2011. [Google Scholar]
- Jayanti, S., C. K..A.C. Cryptosystem of Skewed Affine Cipher Over Elliptic Curves with Block Matrix. ECS Transactions 2022, 07(1), 15071–15080. [Google Scholar] [CrossRef]
- Ramesh, M.; Kumar, B.H.; Srinagesh, A. A Novel Block-Cipher Mechanism for Information Security in Cloud System. 2016 IEEE 6th International Conference on Advanced Computing (IACC) 2016, pp. 524–528. [CrossRef]
- Zeriouh, M.; Chillali, A.; Boua, A. Cryptography based on the matrices. Boletim da Sociedade Paranaense de Matematica 2019, 37, 75–83. [Google Scholar] [CrossRef]
- An, J.H. Authenticated encryption in the public-key setting: Security notions and analyses. 169.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).