1. Introduction
Mutual exclusion (ME) [
1,
2] is a fundamental problem in the concurrent, distributed, real-time programming domains [
3,
4,
5,
6,
7]. It can stated as follows. We have a software system with
processes which compete for the use of a shared resource
. For predictability and deterministic evolution of the system behavior, only one process at a time should be allowed to be in use of the resource. The code executed by the process when it is using the resource constitutes its atomic
critical section. Other properties of a ME algorithm include: (a)
progress, that is a process competing for accessing the resource eventually gets the permission to use the resource; (b) absence of
deadlocks; (c) no process should experiment
starvation, in other terms a competing process should not suffer from an unbounded waiting, or an unbounded number of by-passes/overtakings from other competing processes.
ME solutions typically can be provided by a high-level or low-level abstraction context. High-level ME mechanisms can directly be provided by a programming language (e.g., Java) and accompanying library, and include semaphores, locks or monitor constructs [
8]. Such solutions, though, ultimately depend on the mechanisms implemented in the underlying Operating Systems. Primitive ME solutions are required to give support to high-level mechanisms. Primitive ME solutions can be based on specialized hardware mechanisms, e.g., machine instructions like
test-and-set, or they can be designed as
pure software algorithms which depend on a (hopefully) few shared variables and a purposely designed, often ingenious, protocol which establishes the
entry and
exit code sections which processes have to obey respectively for competing and entering the resource and for releasing the resource at the end of the critical section.
This paper focusses on pure software ME primitive algorithms, whose properties can be very difficult to assess. In the literature, such algorithms are normally studied by peer-review and intuitive reasoning. More structured tools are represented by theorem provers [
9] which can need a not easy formal mathematical representation of the algorithms and their data variables. Theorem provers, though, can be unable to reason on the time dimension of an ME solution.
This paper proposes an original modelling and verification approach based on the Timed Automata [
10] and the Uppaal toolbox [
11] which enable an automatic assessment of the properties of an ME algorithm through exhaustive model checking. Although the approach necessarily is not scalable due to the
state explosion problems which inevitably intervene when considering a number of processes
, it is of great practical value for detecting true properties of ME solutions and to go beyond conjectures often formulated in the literature, particularly about the number of by-passes a process can be affected when competing together with its peers.
The paper significantly extends preliminary work and results of the authors as reported in two conference papers [
12,
13]. Differences from the previous authors’ work are as follows.
The modelling and verification method is completely re-designed and its semantics and transformation on to the Timed Automata of Uppaal clarified.
The novel approach is applied to several ME algorithms proposed in the literature, thus retrieving known results and properties but also, sometimes, discovering new features about specific ME solutions.
Both exhaustive model checking (MC) and statistical model checking (SMC) [
14,
15] can be exploited for property checking. Although SMC is based on simulations, properties of an ME algorithm for N ﹥ 5 processes can be extrapolated by estimations and probability, thus furnishing further arguments to the indications emerged by the exhaustive verification work accomplished until N = 5 processes.
The paper is structured as follows.
Section 2 presents an overview of the basic concepts of Timed Automata and Uppaal modelling.
Section 3 describes the proposed modelling and verification method for mutual exclusion algorithms, and its semantic transformation on to Uppaal.
Section 4 demonstrates by several examples the application and the experimental verification work carried out by using the proposed approach on representative mutual exclusion algorithms. Both the atomic and the week memory models are considered. The inter-play between the exhaustive model checking and the statistical model checking activities is clarified.
Section 5, finally, concludes the paper and indicates some on-going and future work.
2. An Overview of Uppaal Timed Automata Modelling
Uppaal [
15] is a popular modelling and verification toolbox for concurrent/distributed real-time systems. Power and flexibility of Uppaal derive from the adoption of a high-level version of Timed Automata (TA) [
10] which are formal concurrent entities with an easy to understand graphical formulation. A model consists of a network of interacting TA. Interactions are based on unicast and broadcast channels and on global data of primitive types like integers and bools, plus structs and arrays. Unicast channels ensure two-way synchronizations in couples of TA (also said template processes, or parameterizable processes). The sender process of a unicast channel transmits (!) a signal toward a single receiver. The sender, though, gets blocked until the receiver is ready to receive (?) and vice versa (
rendezvous). The synchronization does not carry any data or parameters which can easily be provided through the mediation of some global data variables. After the synchronization, both the sender and receiver resume their concurrent execution. Broadcast channels, instead, enable one-way synchronizations, where a single sender can synchronize with zero, one or multiple receivers. In other terms, the sender of a broadcast channel never blocks. Uppaal models are time-sensitive. The passage of time is controlled by
clocks. A clock can be reset. A clock measures the time units elapsed from its last reset. All the clocks of a model grow according to the same rate. Time is assumed to be dense. A process automaton consists of
locations linked by directed
edges annotated by
guarded commands. A location denotes a local state where the automaton can remain for a certain amount of time (including zero or possibly infinite time units). A normal location (see the NCS location in
Figure 1) denotes a state where the automaton can stay for an arbitrary time. An invariant, that is a logical condition, e.g., based on a clock constraint, can restrict the permanence of the automaton in a normal location. In this case the location has to be abandoned before its invariant is up to become false. An urgent location (see locations with the internal U in
Figure 3) has to be exited immediately, without time passage. A committed location (see the initial location with the internal C in
Figure 2) is similar to an urgent location. However, Uppaal gives priority to committed locations which will be exited before the urgent ones. Among a same group of committed or urgent locations, the exit order is non-deterministic. A guarded command is composed of three optional attributes: a
guard (a logical condition based on clock and/or data constraints) which is true by default when it is missing; a
channel synchronization operation (? or !); an
update component, that is a comma separated sequence of variable assignments and clock resets. A void command denotes a spontaneous edge. A spontaneous edge originating from a normal location, can be taken at any time, also after an infinite amount of time, that is the edge can possibly not taken at all. A guarded command represents the
unit of concurrency of the Uppaal modelling language. When a channel synchronization involves two or more locations in different automata, a joint instantaneous exiting of the corresponding locations will occur. Semantics of Uppaal prescribes, in a joint synchronization in multiple automata, that the update operations in the sender precede the updates of the receivers (the order of the receiver updates is defined in the system declaration section).
Unicast and broadcast channels can be declared to be urgent. In this case, an enabled command involving an urgent synchronization, will be executed before any time passage. However, the order of exiting from multiple simultaneous urgent locations and normal locations with an exiting edge annotated with an enabled guard and an urgent synchronization is non-deterministic.
A distinguishing feature of the Uppaal modelling language which contributes to the creation of compact models is the possibility of exploiting C-like functions (see Algorithm 5 for an example) for defining the guard and/or the update components of commands.
The formal semantics of a Uppaal model can be defined by a Timed Transition System (TTS) defined as where is a set of execution states of the model, is the initial state and denotes the state relation which moves the current state to the next one. Two basic relations exist: the delay transition and the action transition. An action transition represents an instantaneous state change, e.g., tied to a joint synchronization in multiple automata. All the action transitions enabled in the current system state will be executed before time advancement. When no more actions exist to be executed at current time, the system time can be increased of a quantity δ whose amount is constrained by the fact of not falsifying any invariant in the whole model. The amount δ is added to all the model clock valuations. A particular model execution is represented by a sequence of delay/action transitions.
The Uppaal model checker (here refereed as U-MC), accepts a query formula (see
Table 1 for examples) expressed according to a subset of the Timed Computational Tree Logic (TCTL) [
11], builds the TTS of the model, referred to as the model
state graph, and navigates the graph to prove/disprove the query. A query captures a property to be checked. Properties can be of
safety (checking that a bad state is never reached) or
liveness (checking that a good state is eventually reached) nature. A counterexample (said a diagnostic trace) can be built by U-MC to reproduce a sequence of transitions (events) which the modeler can analyze, in the symbolic simulator, to detect why a given formula was satisfied or not satisfied by the state graph. Nodes (execution states) of the state graph are made up of two parts: a
data part, and a
time zone. The time zone represents, by a system of clock inequalities, all the possible (also infinite) time instants for reaching the given state. A node of the state graph is actually an equivalence class: it represents all the states having the same data, and whose occurrence times are solutions of the time zone inequality system. Each arc exiting from a state node and linking to a next state node is labelled with the delay or action transition which causes it.
Complexity of the state graph is exponential in the number of clocks. However, it is not the absolute number of clocks used in the model which matters, but rather the maximum number of simultaneous active clocks, that is the maximum parallelism degree of the model. An active clock is one which is currently used in an invariant or in a constraint in a guard. The number of active clocks affects the complexity of the state graph. In addition, the memory demand critically increases as more data variables are introduced by the modeler. Another measure of the state graph complexity is represented by the degree of action interleaving (partial-order), mirrored by the number of exiting arcs from a state node. The Uppaal model checker (U-MC) navigates the state graph by exploring all the possible execution paths, and then the action interleavings, which originate from the initial state node.
In the last years Uppaal was equipped also of a Statistical Model Checker (U-SMC) [
14,
15] which does not build the state graph but uses instead simulations for estimating properties. The memory consumption of U-SMC is linear with the model requirements. U-SMC gives the modeler the possibility of interpreting the basic TA as Stochastic Timed Automata. To a normal location the rate of a negative exponential probability distribution can be attached, which is sampled to furnish the dwell time for remaining in the location. In the case a normal location is provided of an invariant on a clock
of the type
, where
is the maximal time the automaton can stay in the location, and an exiting edge with a guard like
, with
, under U-MC the automaton can exit the location at any time non-deterministically chosen in the dense interval
. Under U-SMC a delay is sampled by a uniform probability distribution in the same interval, which constitutes the dwell time before abandoning the location. U-SMC supports queries written in the Metric Interval Temporal Logic (MITL) [
15] (see
Table 2 for examples). As a simple example, U-SMC can estimate the probability of an event occurrence by executing a certain number of simulations (whose amount can be automatically inferred), each one lasting after an assigned time limit, and counting how many times the event occurs in the various runs, divided by the total number of runs. As a further benefit, U-SMC can accumulate data from a simulation so as to display them graphically thus favoring a better understanding of a dynamic behavior.
Uppaal Timed Automata are used in this work to model and analyze mutual exclusion algorithms by model checking. A key feature offered by Uppaal is the possibility of investigating the effects of time on the behavior of such algorithms.
3. A Modelling Method for Mutual Exclusion Algorithms
Mutual exclusion algorithms can be studied according to two memory models: the common strong memory model (SMM) and the Weak Memory Model (WMM) [
6]. According to SMM, the write and read operations issued by processes on a memory cell are atomic. In the WMM model, though, a memory cell under writing can be simultaneously read by other processes and a non-deterministic value can be achieved (
flickering). In this paper both models will be considered.
In the following, N processes identified by unique numbers from 1 to N, compete for the use of a shared resource. The abstract code structure of the generic Process(i) is assumed to be a never ending loop as in Algorithm 1.
|
Algorithm 1. General code structure of a process involved with mutual exclusion. |
global shared communication variables
Process(i):
local variables of the process
loop
NCS //Non Critical Section
Entry
CS //Critical Section
Exit
end-loop
|
In the NCS section the process does something unrelated from the shared resource. More in particular, the duration of NCS is arbitrary and can include 0 time units (the NCS is immediately abandoned) and infinite time units (in the NCS the process can block or terminate). Process i follows a specific protocol for accessing the resource. The Entry part is what is called the competing part. The process signals its interest in accessing the resource. However, it has to wait until the process gets the grant to actually access the resource. The Exit part consists of the final operations which the process execute to let partners be informed it has finished with this access to the resource.
Both the Entry and the Exit code sections depend on and make use of the global and shared communication variables. On the other hand, each process owns some private, inaccessible to other processes, local variables. The original design of a mutual exclusion algorithm concerns devising a minimal number of shared communication variables whose use is capable of ensuring the mutual exclusion and the related properties.
A correct mutual exclusion algorithm should guarantee the following properties are fulfilled.
(safety) Absence of deadlocks in the processes attempting to use the shared resource.
(safety) At any time, only one process should be allowed to enter its critical section.
(bounded liveness) A competing process eventually enters its critical section. In other terms, the waiting time for a competing process should be finite and hopefully small. Equivalently, the number of by-passes or the overtaking factor which a waiting process experiments from other competing processes should be bounded. This property also expresses, for a competing process, the absence of starvation.
(liveness) A process in its non-critical section should never impede a competing process to enter its critical section.
3.1. Uppaal Modelling Method
Mutual exclusion (ME) algorithms normally do not make any assumption about the time duration of the operations in the Entry, the Exit and the CS sections (see Algorithm 1). In the proposed Uppaal method for a generic process (see
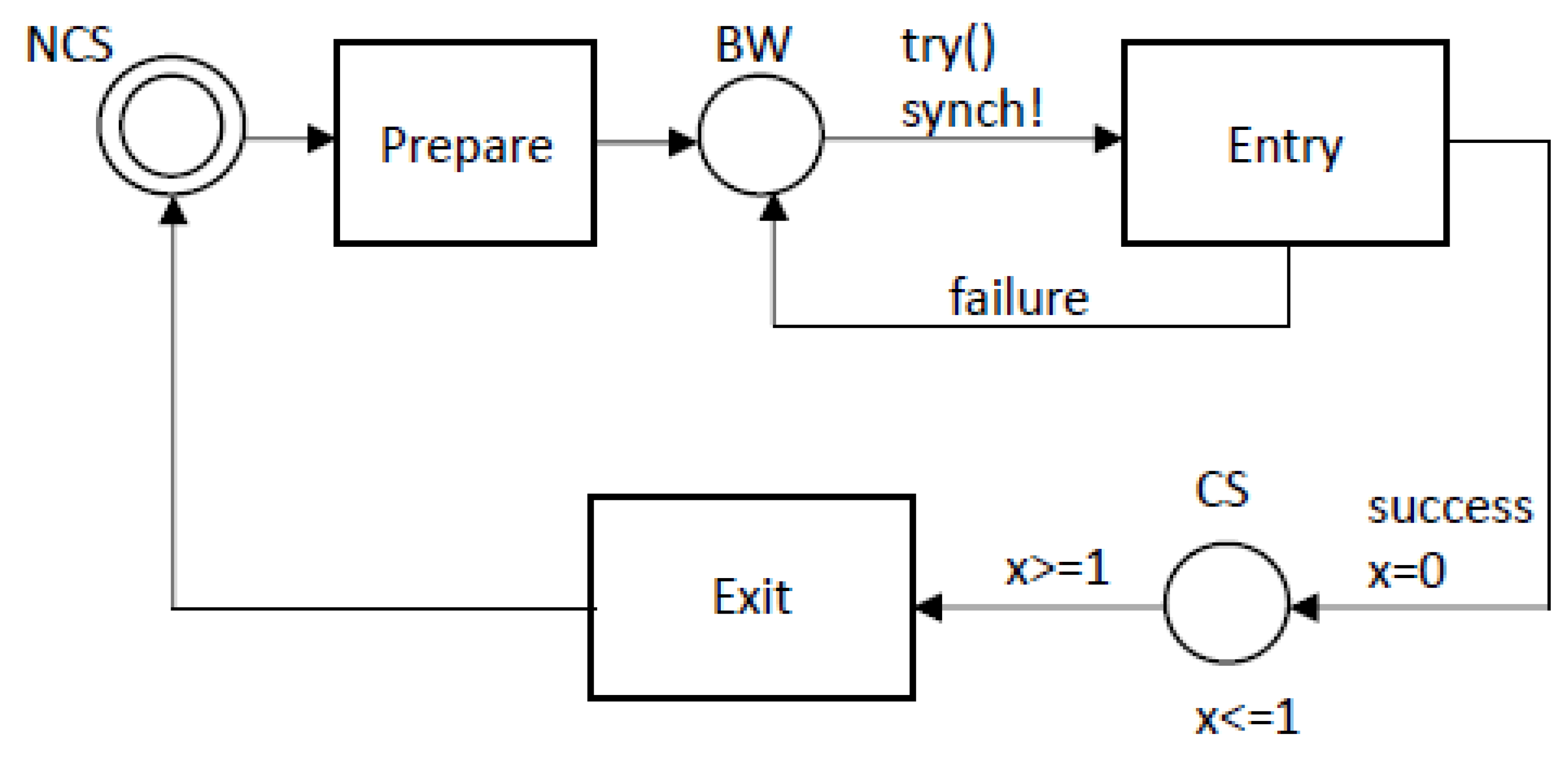
Figure 1), all the elementary operations are modelled by
urgent locations, thus having a 0 duration. The consequence is a high-degree of interleaving or partial-order in the nodes of the state graph, particularly when the number
of processes increases. A significant degree of interleaving complicates the generation and the navigation of the state graph during the model checking. These considerations suggested a refinement of the ME modelling method as follows. First, the execution of the Entry actions, although they are continuously executed (
busy-waiting) in the physical process, perhaps running on a separate processor/core, in the Uppaal model can be conveniently postponed (lazy modelling) until there is an “evidence” that changes in the shared communication variables occurred which require the process to actually check if it really can prosecute toward the critical section or not. All of this in no case introduces changes in the logic of the ME algorithm, but it can reduce the burden of an excessive interleaving degree in the model.
In
Figure 1, the ME model-dependent
boolean function is introduced, which returns true if something is changed in the shared communication variables which motivates the process to execute the Entry actions. If the guess expressed by try(), for non-determinism and concurrent execution with partner processes, would result in a failure, that is the process has still to continue waiting in the competing state, the BW location will be re-entered. If instead the Entry actions end with a success, the process continues by entering its critical section. It is worth noting that BW is immediately exited at any time the optimistic try() function returns true. Toward this, a (fictitious) signal sent over the urgent and broadcast channel
is used. Note that no receiver exists for this asynchronous message.
The CS section (see Algorithm 1) is purposely modelled as a normal location with a dwell time of exactly 1 time unit (see the invariant
on CS and the guard
on the edge exiting the location CS). The use of an unitary duration for any critical section makes the model time-sensitive, facilitates the prediction of the overtaking factor (see later in this paper) and does not affect the mutual exclusion algorithm evolution. On the other hand, the CS behavior can naturally break possible zeno-cycles [
16], that is those infinite sequences of events executed in 0 time, which could arise in a model with a lot of urgent actions.
The non-critical section NCS is instead modelled as a normal location with a spontaneous exiting edge. As a consequence, NCS can be abandoned in 0 time units or the process automaton can remain in it also an infinite number of time units. The last situation models the process which can be stopped into NCS.
Special care is required in the modelling of the actions of both the Entry and the Exit sections. Under both the Strong Memory Model (SMM) and the Weak Memory Model (WMM) it is fundamental to realize that individual shared communication variables must be set (written) or get (read) in separated edges of the Uppaal process model. All of this mirrors the fact that each single shared communication variable has to be accessed from a different memory location. As a consequence, a condition based on multiple shared variables has to be split and its result calculated by evaluating separately its basic components. This way the evaluation of the condition can be correctly affected by the non-determinism and interleaving of the various processes. The situation is different for local variables of a process. Such variables can be supposed to be held in separate registers so that multiple local variables can be operated in a single edge command without errors.
The above mentioned constraints on the use of shared communication variables, do not apply in the formulation of the try() function body, where the goal is to “rapidly” predict, e.g., that the process can possibly enter its critical section. It has to be stressed, though, that a true result of try() expresses only an optimistic prediction which can be falsified in the actual non-deterministic execution of the Entry actions.
As one can see from
Figure 1, the initial location of a process model is represented by NCS. The overall model with
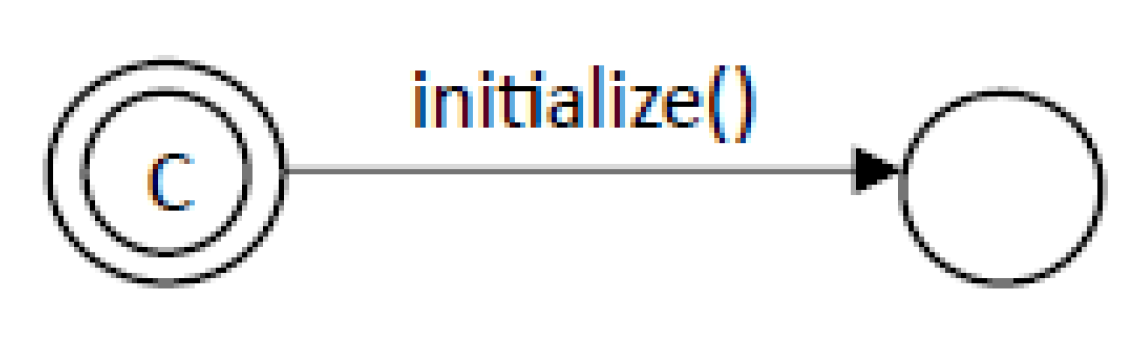
process instances can be initialized by a Bootstrap automaton (see
Figure 2) whose initial location is marked as committed so as to be sure, through the initialize() function, all the global shared data get initialized before any process starts executing. After the execution of the initialize() function, the Bootstrap moves to a final normal location without exits thus disconnecting from the model.
3.2. Predicting the Overtaking Factor
In the model of
Figure 1 time can advance not only because the CS location has one time unit duration but also because of the unpredictable staying of the process into the NCS. The interplay of CS/NCS timing is a key factor for predicting the number of overtakings. Since all the processes are identical, one of them can be elected for measuring the overtakings. Let it be denoted by tp (target process, by default the process 1). Some common global declarations of a mutual exclusion Uppaal model are the following:
const int N=…; //the number of processes
typedef int [1,N] pid; //the type of process unique identifiers
const pid tp=1; //target process example
clock x[pid]; //one clock per process
The clock x[tp] is reset as soon as the target process starts competing. The following reset(i) function can be used for this purpose:
void reset(const pid i){
if(i==tp) x[tp]=0;
}//reset
After its reset, x[tp] grows as other competing processes enter their critical sections. Since the unitary duration of the location CS (see
Figure 1), the maximal value reached by x[tp] measured before entering its CS, can furnish the number of overtakings. Such a number coincides with the number of CSs executed by competing processes before the tp process is allowed to enter its CS.
Semantic correctness of this approach, despite the timing introduced by NCS, can be stated as in the following. Of course, by design, a mutual exclusion algorithm is expected to ensure a finite number of overtakings to be suffered by any process and also by the tp process. Let be the finite amount of time that the (competing) tp process has to wait before entering its CS. Let tc be a competing process which gets its CS before tp, and then enters its NCS which is finally abandoned after a time , when a new competition for tc is started. In the case it necessarily follows that the process tp eventually enters its CS and a new competition phase is then launched. Would instead be , this means that the time spent by tc into its NCS naturally occurs, by concurrency/parallelism, as part of the time spent for waiting by tp, mirrored by the clock valuation x[tp]. Therefore, the time behavior of processes into NCS does not forbit the correct detection of the maximal number of overtakings by observing the clock x[tp].
An important consequence of the mutual exclusion property and of the choice of the target process tp for observing the number of overtakings, is that, at any moment of the model verification, despite the number of the processes, at most two clocks can be active: that of the process tp and the one of the competing process which is allowed to enter its critical section.
3.3. Model Checking and TCTL Queries
A basic set of TCTL [
11] queries which can be used to study a mutual exclusion algorithm expressed in Uppaal according to the general process model of
Figure 1, are suggested in
Table 1.
The 1st query of
Table 1 asks if it is always true (A[]) or invariantly, that in all the states of the state graph there is no deadlock. The 2nd query checks if, invariantly, the number of processes that are in the CS location is always less than or equal to 1 (the fundamental mutual exclusion property). The 3rd query based on the
operator
[
11], states that starting from the BW location, it inevitably follows that the process enters its CS. The 4th existential query (E<>) verifies that a process in the NCS does not forbid another process to be in the CS. The 5th query, finally, asks to quantify the maximal number of overtakings suffered by the chosen target process. Different locations, not necessarily the BW, can be chosen for observing the suprema value of x[tp]. For example, a (urgent) location just before entering the CS could be adopted as well.
3.4. Statistical Model Checking and MITL Queries
The basic process model in
Figure 1 can easily be adapted for it to be exploited also under the Uppaal Statistical Model Checker (U-SMC) [
15]. Basically, the possibility of time not advancing in the NCS location can be avoided by attaching to NCS the rate of an exponential probability distribution function which can conveniently be established as
, where EOF is the expected overtaking factor. Some MITL queries useful for checking the model of a mutual exclusion algorithm through simulations, are proposed in
Table 2. It is to be anticipated, though, that it can be difficult, in simulation, to observe the effective number of overtakings. This is because U-SMC, during a simulation, follows a particular execution path of the actions interleaving, whereas the model checker analyzes
all the possible paths.
The query 1 of
Table 2 asks U-SMC to estimate, using an inferred number of simulation runs each lasting 10000 time units, the occurrence probability of the event “
is there any state in which the number of processes in CS is greater than 1?”. U-SMC proposes a confidence interval (by default with the confidence degree 95%) for the event probability. Of course, the confidence interval should indicate an almost impossible event. With the default parameters setting of U-SMC [
15], a typical “impossible” event is witnessed by the interval
. Similarly, an almost “certain” event is denoted by a confidence interval of
. The 2nd query monitors the number of processes simultaneously in CS in a simulation, e.g., lasting 100 time units. Following the query execution, U-SMC can show graphically the accumulated data. The 3rd query quantifies the probability of a process, e.g., the tp, to effectively enter its critical section. Such a query is expected to suggest an almost sure event. The 4th and 5th queries ask U-SMC to quantify the confidence interval of the probability that the target process experiments a number of overtakings respectively greater than the expected bound (an event which should be impossible) or that such a number is always found to be less than the expected bound (an event which should be certain).
5. Conclusions
Reasoning on a concurrent/parallel software system [
4,
5,
6] can be very complex. The origin of this difficulty stands in the non-determinism and action interleaving which dominate the evolution of the system. All of this can jeopardize the human intuition and peer-review normally adopted to predict the properties of a concurrent system.
This paper proposes an original approach based on formal modelling for the automated analysis of mutual-exclusion algorithms, which are at the heart of concurrent/parallel, real-time and operating systems. The approach is based on the Timed Automata [
10] as implemented in the popular and continually evolved Uppaal toolbox [
11]. The major limitation of the proposed method is the well-known state explosion problem, which arises in complex algorithms which makes use of or generate too many data. As an example, solutions like the Lamport’s bakery algorithm [
27] which grants the access to the critical section on the basis of an ever increasing service number, is difficult to handle by the exhaustive model checking. It could be studied by the statistical model checker. The state explosion restriction forbids, even for addressable algorithms, the analysis when the number
of the involved processes is greater than 5. Another reason for having chosen Uppaal for the experiments, rests on the fact that the tool also provides a statistical model checker [
14,
15] which does not build the model state graph but instead relies on simulations and stochastic behavior. This way, the tool permits an exploration of the properties of a complex algorithm by estimating event probabilities which can be of great practical value by providing further arguments about the correctness of a given algorithm for not trivial values of
.
The paper applies the proposed modelling and verification approach to several algorithms defined in the literature, of which known results are retrieved and confirmed but also, in some cases, unexpected results emerge, for example about the bounded degree of the overtaking which a competing and waiting process can suffer before getting the grant to enter its critical section.
The paper investigates the mutual exclusion algorithms from the point of view of the classic memory model with read/write atomic operations. However, the modelling and verification aspects when the weak memory model is adopted, that is when multiple readers can simultaneous access an under writing memory cell with the uncertainty (
flickering) [
6,
9] which accompanies the reading process, are also investigated.
Prosecution of the research will address the following points. First to apply the proposed approach to other mutual exclusion algorithms. Second to optimize the implementation of the approach and deepen the differences from alternative methods like the theorem provers which normally are unable to deal with the timing aspects. Third to exploit parallel simulation [
28] for studying large models on a multi-core machine.
Figure 1.
Proposed abstract Uppaal model for a mutual exclusion process.
Figure 1.
Proposed abstract Uppaal model for a mutual exclusion process.
Figure 2.
The Bootstrap automaton.
Figure 2.
The Bootstrap automaton.
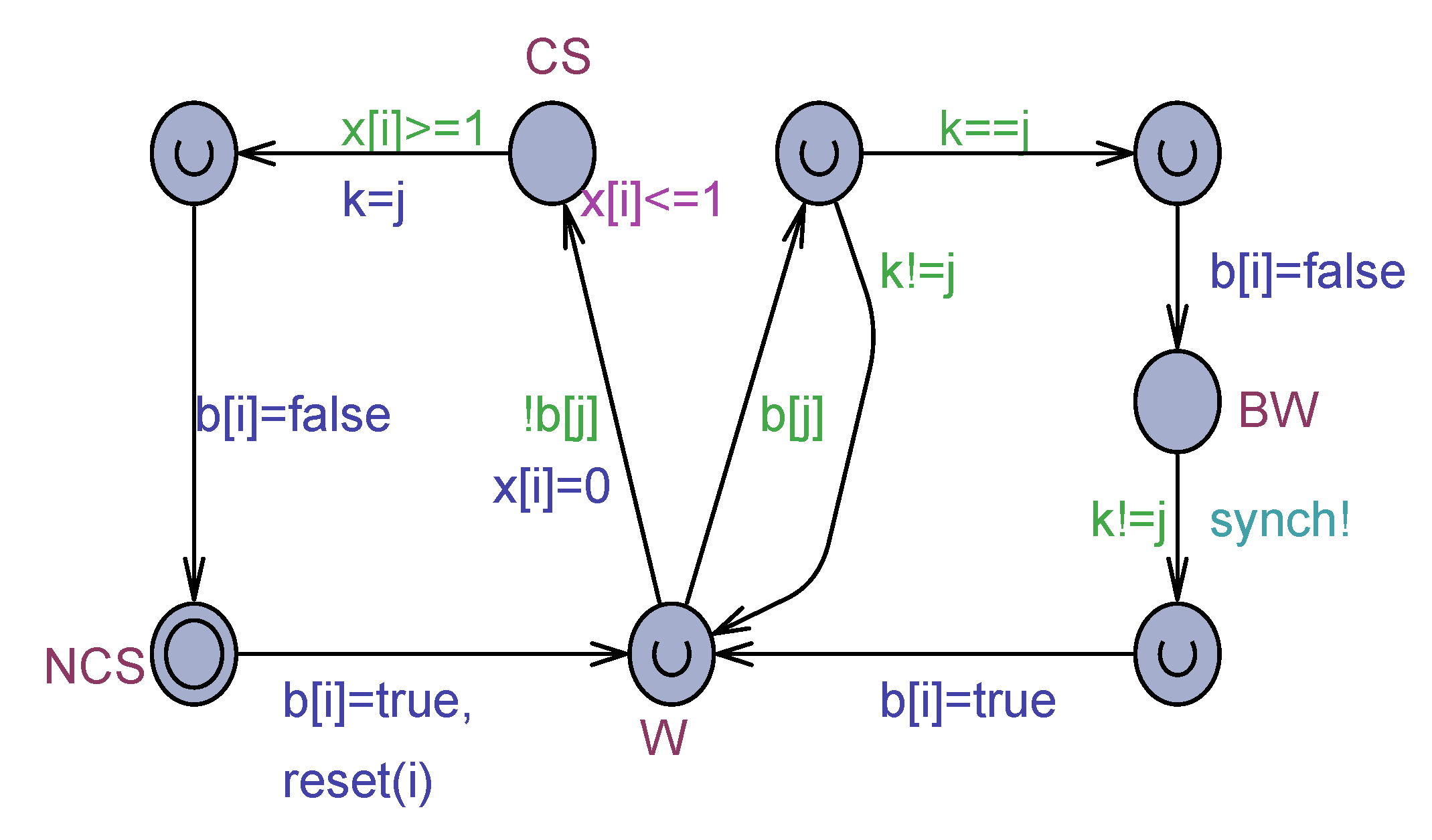
Figure 3.
Uppaal model of the Dekker’s Process(i).
Figure 3.
Uppaal model of the Dekker’s Process(i).
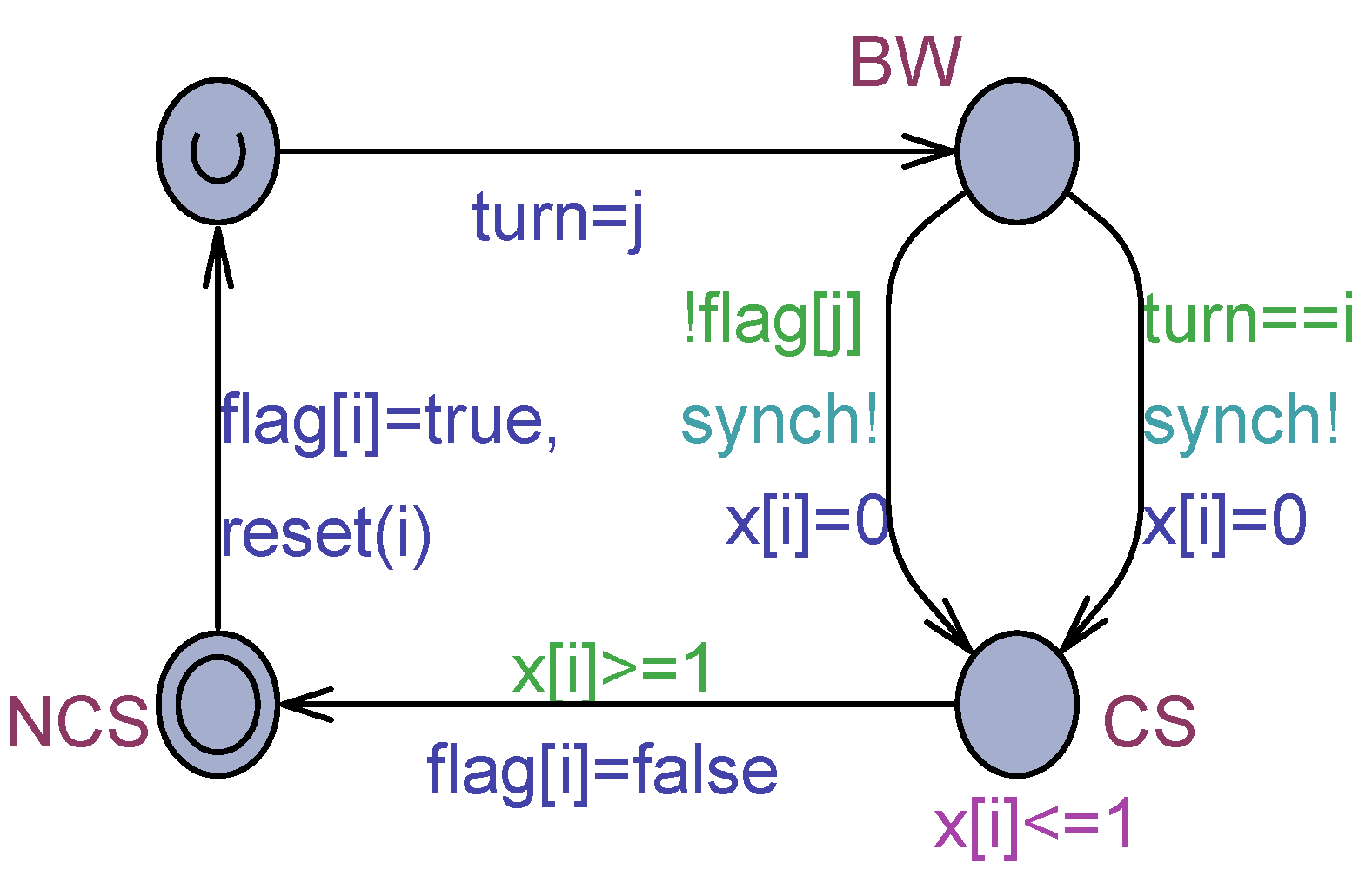
Figure 4.
Uppaal model of the Peterson’s Process(i).
Figure 4.
Uppaal model of the Peterson’s Process(i).
Figure 5.
Uppaal model for the Dijkstra’s algorithm.
Figure 5.
Uppaal model for the Dijkstra’s algorithm.
Figure 6.
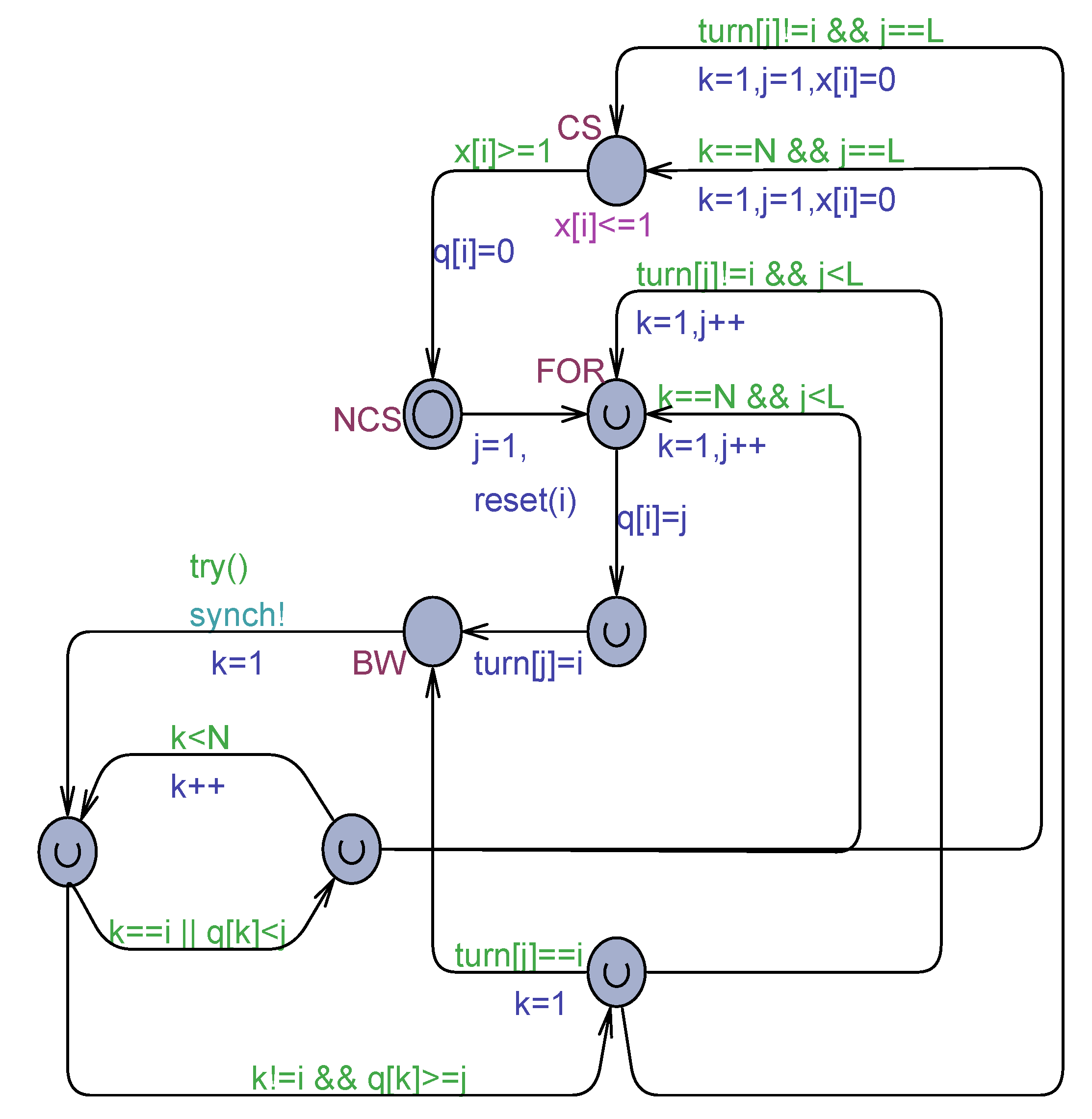
Uppaal model of the Knuth’s algorithm of Algorithm 6.
Figure 6.
Uppaal model of the Knuth’s algorithm of Algorithm 6.
Figure 7.
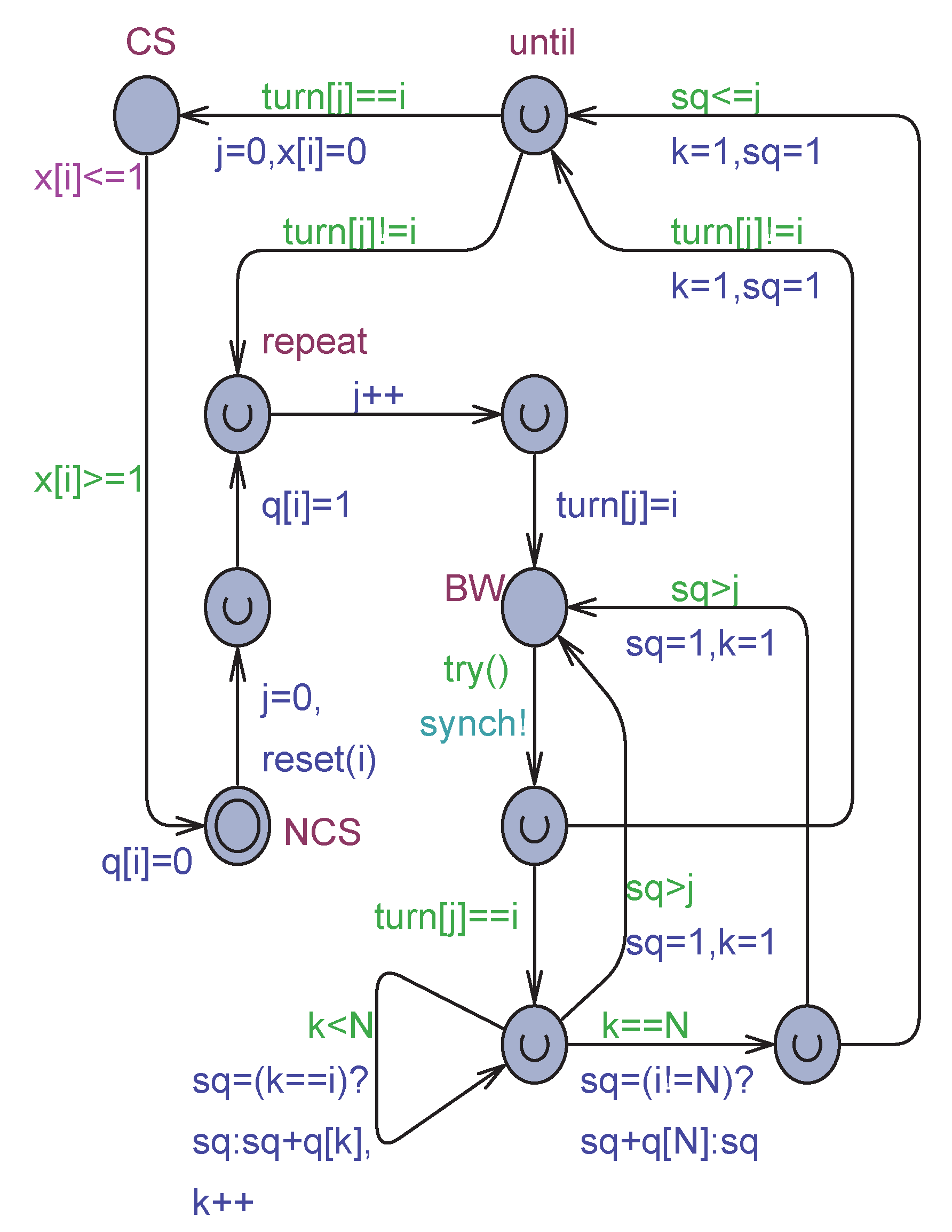
Uppaal model of the de Bruijn’s algorithm.
Figure 7.
Uppaal model of the de Bruijn’s algorithm.
Figure 8.
Uppaal model of the de Eisenberg & McGuire’s algorithm.
Figure 8.
Uppaal model of the de Eisenberg & McGuire’s algorithm.
Figure 9.
Uppaal model for the Peterson’s algorithm for
Figure 9.
Uppaal model for the Peterson’s algorithm for
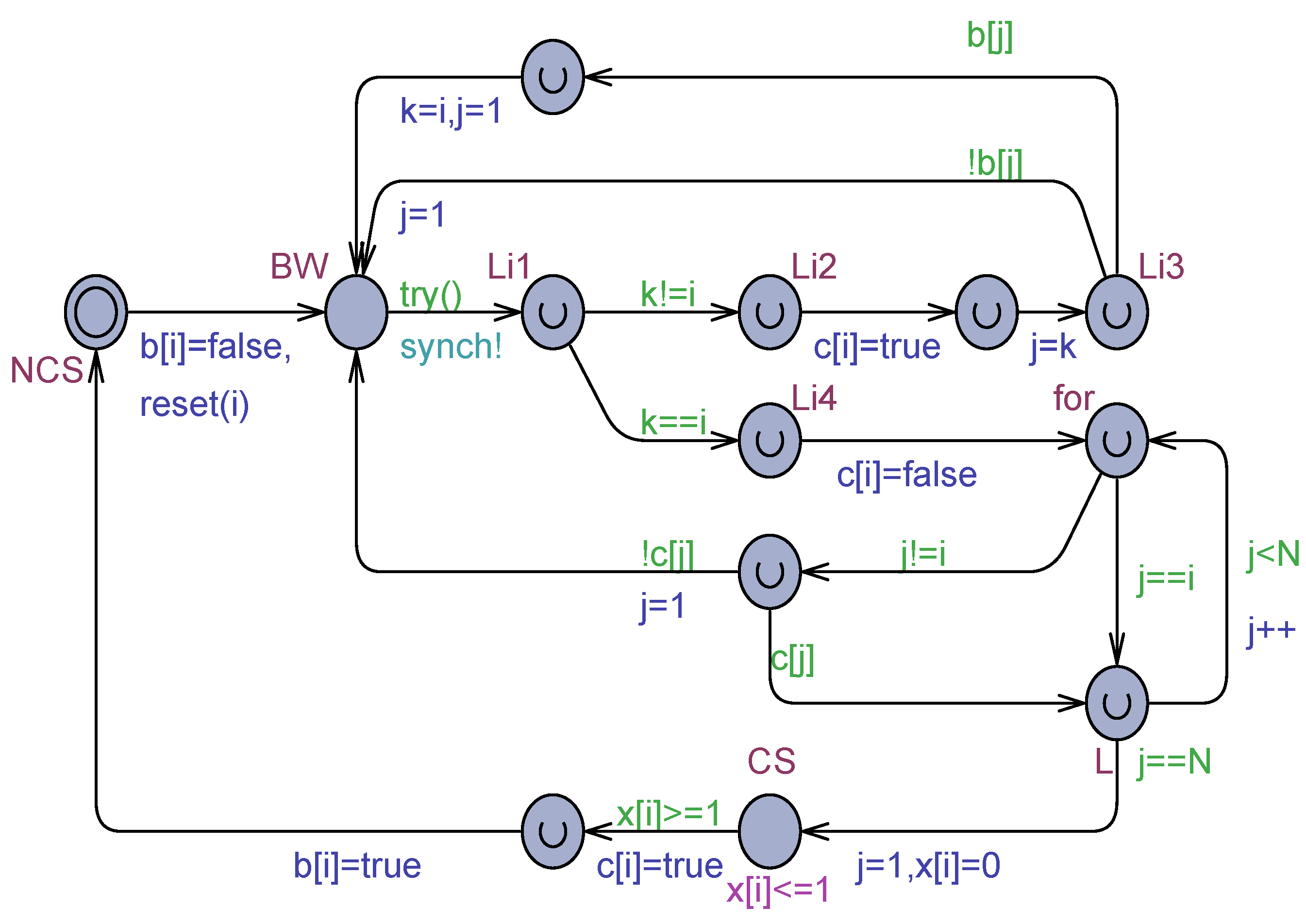
Figure 10.
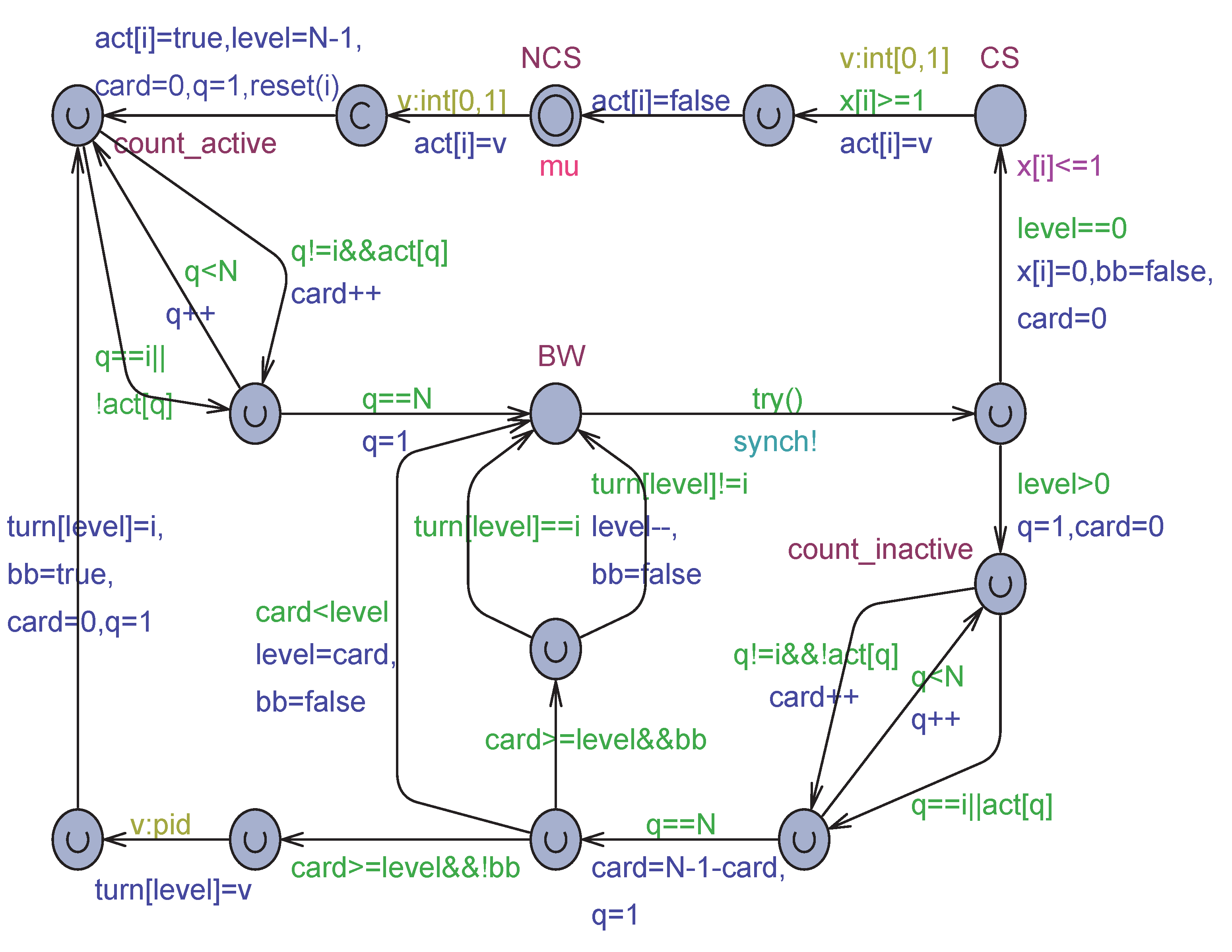
Uppaal model for the Block & Woo algorithm for processes.
Figure 10.
Uppaal model for the Block & Woo algorithm for processes.
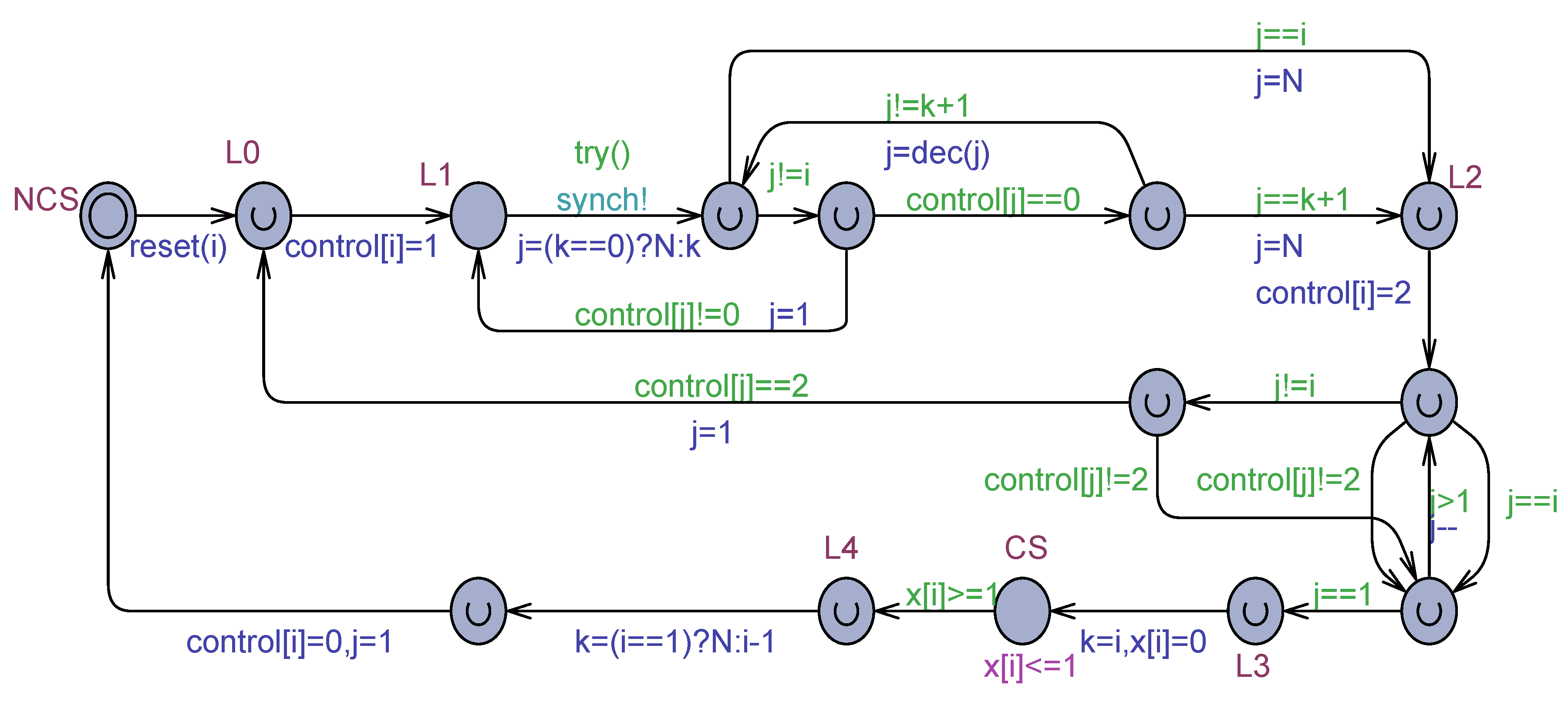
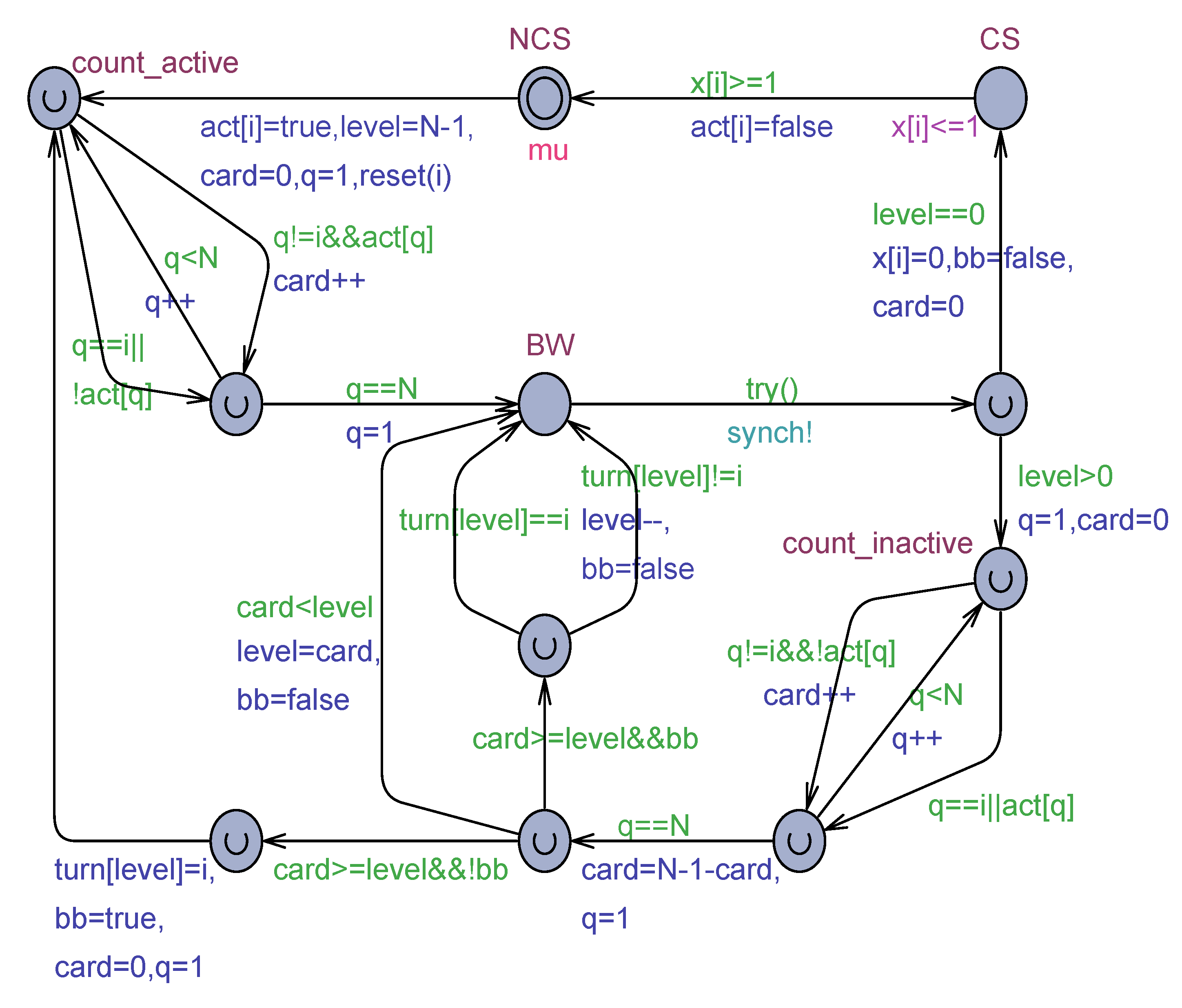
Figure 11.
Uppaal model for the Aravind & Hesselink algorithm for processes.
Figure 11.
Uppaal model for the Aravind & Hesselink algorithm for processes.
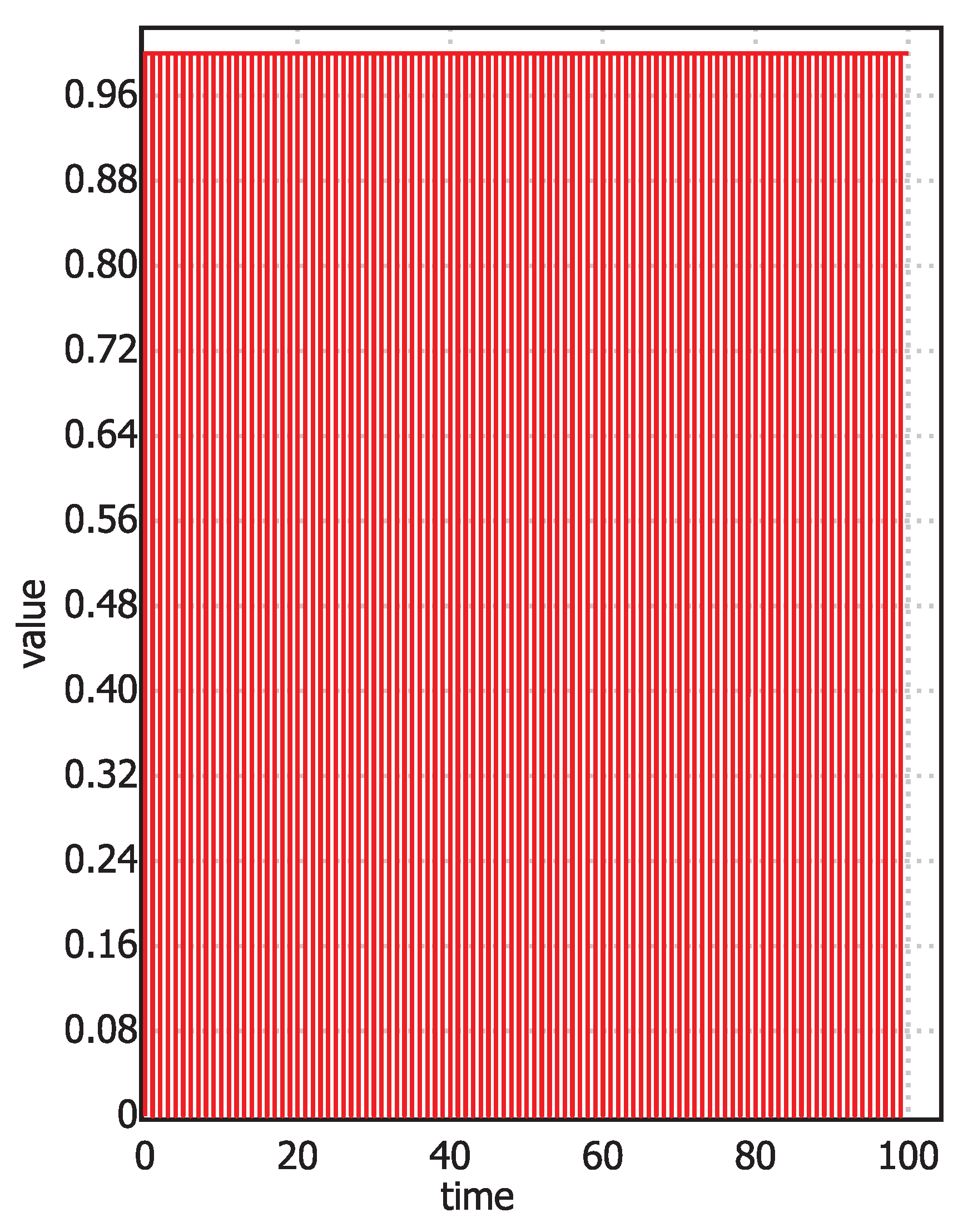
Figure 12.
Number of processes, vs. time, simultaneously found in their CS for .
Figure 12.
Number of processes, vs. time, simultaneously found in their CS for .
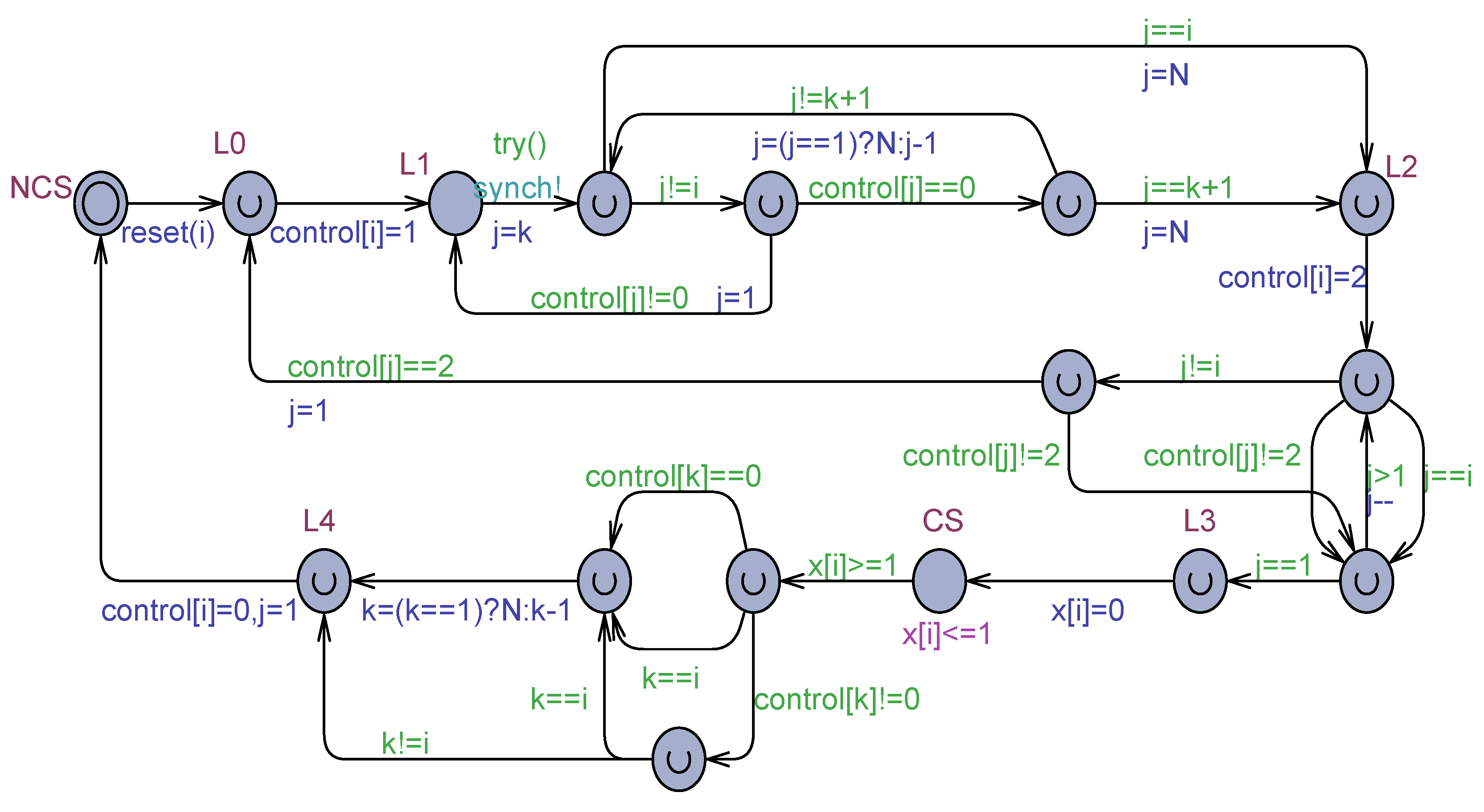
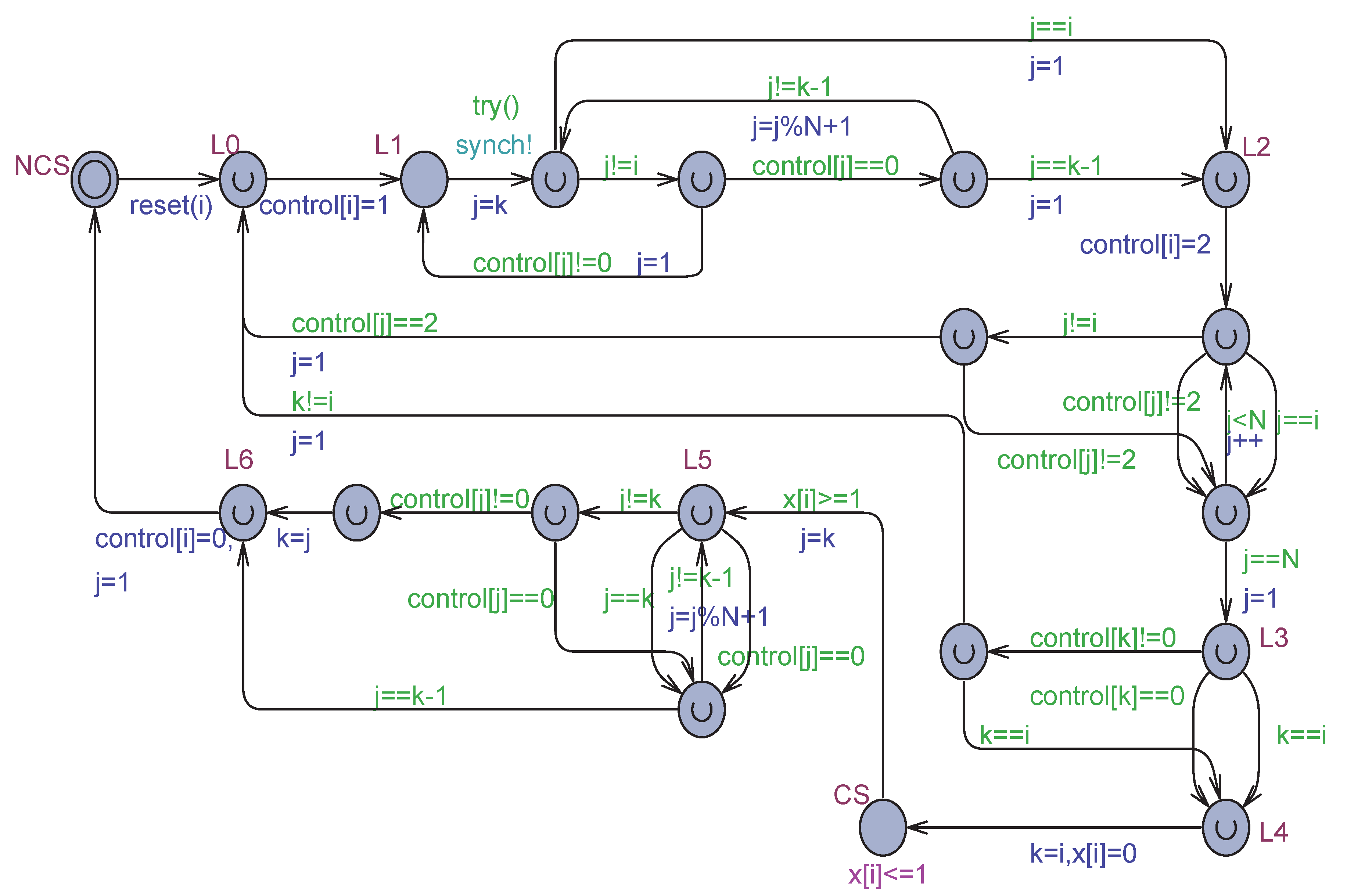
Figure 13.
The Uppaal model of the Aravind & Hesselink algorithm under weak memory model and flickering.
Figure 13.
The Uppaal model of the Aravind & Hesselink algorithm under weak memory model and flickering.
Table 1.
Some TCTL queries for checking a modelled mutual exclusion algorithm.
Table 1.
Some TCTL queries for checking a modelled mutual exclusion algorithm.
| # |
TCTL query |
Property |
| 1 |
A[] !deadlock |
Absence of deadlocks. |
| 2 |
A[] (sum(i:pid)Process(i).CS)<=1 |
At most one process can be in its critical section (CS). |
| 3 |
Process(tp).BWProcess(tp).CS |
A process in BW eventually enters the critical section. |
| 4 |
E<> Process(1).NCS && Process(2).CS |
A process in NCS does not forbid another process from entering the CS. |
| 5 |
sup{ Process(tp).BW } : x[tp] |
The suprema value of the overtaking factor. |
Table 2.
Some MITL queries for monitoring the overtaking factor.
Table 2.
Some MITL queries for monitoring the overtaking factor.
| # |
MITL query |
Property |
| 1 |
Pr[<=10000](<>(sum(i:pid)Process(i).CS)>1) |
Probability that more than one process can be in CS. |
| 2 |
simulate[<=100]{sum(i:pid)Process(i).CS} |
Monitoring the number of processes simultaneously in CS in a simulation of 100 time units. |
| 3 |
Pr[<=1000](<>Process(tp).CS) |
Probability that a process can actually enter its CS. |
| 4 |
Pr[<=10000](<>Process(tp).BW &&
x[tp]>expected-value) |
Probability that the overtaking factor (x[tp]) can be found greater than the expected-value. |
| 5 |
Pr[<=10000]([] Process(tp).NCS ||
x[tp]<=expected-value) |
Probability that x[tp] is always found less than or equal its expected-value. |
Table 3.
Observed overtakings vs. for the Knuth’s algorithm.
Table 3.
Observed overtakings vs. for the Knuth’s algorithm.
Table 4.
Observed overtakings vs. N for the de Bruijn’s algorithm.
Table 4.
Observed overtakings vs. N for the de Bruijn’s algorithm.
Table 5.
Observed overtakings vs. N for the Eisenberg & McGuire’s algorithm.
Table 5.
Observed overtakings vs. N for the Eisenberg & McGuire’s algorithm.
Table 6.
Observed overtakings vs. N for the generalized Peterson’s algorithm.
Table 6.
Observed overtakings vs. N for the generalized Peterson’s algorithm.