Introduction
In the current age of rapidly evolving urban development and technology advancement, smart cities have become symbols of contemporary living. 'Smart cities' is a concept that has emerged from the unprecedented integration of digital technologies into urban infrastructures at the start of the twenty-first century. Of course, the implementation of cutting-edge technologies helps smart cities accomplish their primary goals (Sharma et al., 2021), which include expanded economic growth, better public services, sustainable urban development, and increased citizen involvement. The diversity of urban growth is reflected in these technologies, which cover a range of industries including energy management, healthcare, transportation, and governance (Umair et al., 2021). An illustration of smart cities is depicted in
Figure 1 (Ma, 2021).
The Internet of Things (IoT), a network of connected devices and sensors that promises to transform urban living, is central to this paradigm shift (Costa and Duran-Faundez, 2018; Rejeb et al., 2022; Hashem et al., 2016). But as technology has advanced, a wide range of challenging cybersecurity issues have also emerged, calling for strong and innovative solutions.
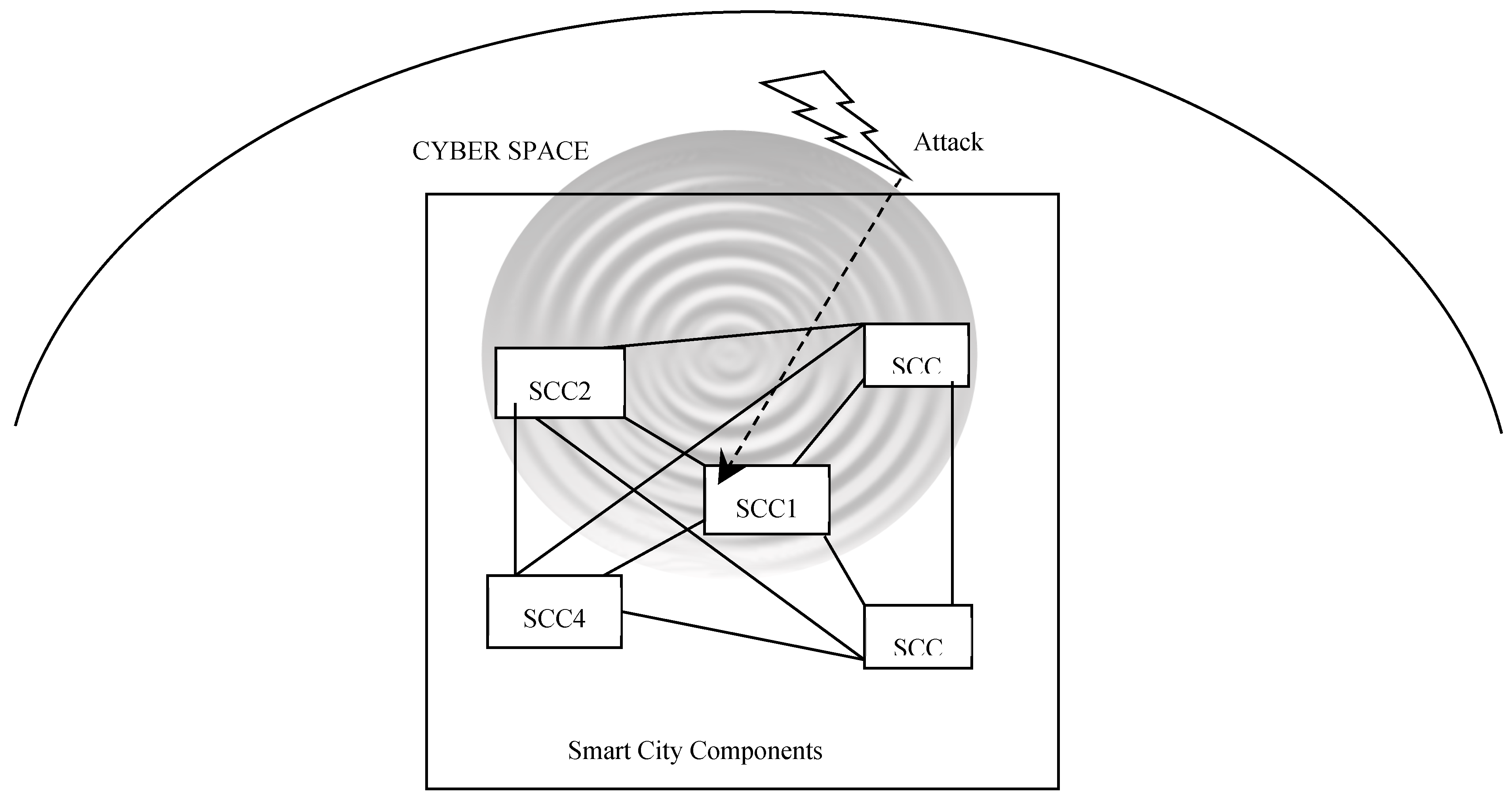
The integration of diverse Internet of Things (IoT) devices in urban landscapes has revolutionized city management and resident experience, resulting in increased energy efficiency, better traffic management, public safety, and overall quality of life. These developments have been made possible in large part by the implementation of IoT in smart cities (Batty et al., 2012; Neirotti et al., 2014; Caragliu et al., 2011; Hashem et al., 2016; Andrade et al., 2020). Urban networks are becoming much more complicated due to the widespread use of IoT technology (Magaia et al., 2020), which exposes them to a wide range of cybersecurity risks. IoT networks, which are essential to the infrastructure of smart cities, are distinguished by a diverse range of devices and protocols, each with a different degree of security (Konstantopoulou et al, 2023; Wu et al., 2020). Due to frequently insufficient security measures and the sensitivity of the data they handle, this diversity—which was once a strength in functionality—has turned into a security vulnerability, making these networks easy targets for cyberattacks (Kitchin, 2014; Weber, 2010; Alaba et al., 2017; Lu et al., 2018; Ziegeldorf et al., 2014, Demertzi et al., 2023). Moreover, and as a result of this interconnectedness, a security breach on one device could have repercussions for the entire network. This means that if a cyberattack occurs in one of the smart city components (SCC), the other components will be adversely affected. As shown in
Figure 2, a cyberattack on SCC1 will negatively impact SCC2 - SCC5.
Traditional cybersecurity techniques, which were usually created for more homogeneous and smaller networks, are insufficient given the size and diversity of IoT installations (Jing et al., 2014; Granjal et al., 2015; Tamane et al., 2021; Huber et al; 2023). The delicate nature of the data handled by IoT networks exacerbates these vulnerabilities even more, with possible repercussions ranging from invasions of privacy to the interruption of vital services (Roman et al., 2013; Sicari et al., 2015). Globally, there were over 25 billion active IoT devices as of 2020; by 2025, that number is expected to rise to over 75 billion (Statista, 2020). These networks are extremely vulnerable to cyberattacks because of their rapid expansion and the diverse range of IoT devices. Indeed, from roughly 639 million in 2019 to over 1.5 billion in 2020, IoT cyberattacks more than doubled in a single year (Kaspersky, 2020), and a very recent survey shows that IoT devices, such as smart home devices and routers, are projected to exceed 29 billion by 2030 (Kaspersky, 2023).
Artificial Intelligence (AI) offers a potentially effective answer to these problems (de Azambuja, 2023), especially in the area of anomaly detection, which is crucial for detecting and reducing cybersecurity risks (Hasan et al., 2019; Ahmed et al., 2016). IoT network cybersecurity can be improved by using AI-driven methods because of their capacity to identify intricate patterns and evaluate large volumes of data (Liu et al., 2018). Artificial Intelligence has enormous potential in this field. For example, machine learning models can be trained to identify anomalous patterns or behaviors in network traffic that may indicate a cybersecurity concern (Hado et al., 2016; Xu et al., 2014).
Table 1 lists the comparative advantages that AI has over traditional methods in cybersecurity.
In smart city contexts, where prompt detection and reaction to security issues can avert major disruptions, these capabilities are essential (Mehta et al., 2020). Still, a significant gap exists in the literature regarding having thorough frameworks that methodically outline how AI might be applied to anomaly detection in smart city IoT networks (Ferrag et al., 2018; Zhang et al., 2019).
In order to bridge this gap, and drawing on a solid theoretical framework comprising the Complex Adaptive Systems (Holland, 1995), Technology Acceptance Model (Davis, 1989), the Theory of Planned Behavior (Ajzen, 1991), and the Socio-Technical Systems Theory (Trist, 1981), the purpose of this study is to propose a conceptual framework that elucidates how artificial intelligence (AI) may improve the cybersecurity of Internet of Things (IoT) networks in smart cities. The framework will examine and incorporate the different factors that affect the relationship between AI-driven anomaly detection and enhanced smart city cybersecurity, including technological, environmental, and human factors. More specifically, it will look at the moderating effects of cybersecurity culture, policy, and technological advancements, as well as the mediating role of the human factor in the anomaly detection process itself. Accordingly, the study aims to address the following research questions:
RQ1: How do AI-driven anomaly detection techniques (independent variable) impact cybersecurity (dependent variable) in smart city IoT networks?
RQ2: What role do technological advancements (moderating variable) play in the relationship between AI-driven anomaly detection and cybersecurity in smart city IoT networks?
RQ3: How does the regulatory and policy framework (moderating variable) affect the effectiveness of AI-driven anomaly detection in improving cybersecurity in smart city IoT networks?
RQ4: In what way do human factors (mediating variable) influence the effectiveness of AI-driven anomaly detection in enhancing cybersecurity in smart city IoT networks?
By attempting to answer these questions, the study will add to the growing body of knowledge on smart city cybersecurity. It will also provide researchers and practitioners with a comprehensive roadmap for comprehending, implementing, and navigating the complexities of AI-driven cybersecurity solutions. Finally, the framework presented will provide a methodical approach to implementing AI-driven solutions to protect our increasingly growing digital urban spaces.
The remaining of this paper will proceed as follows. The following section provides a thorough analysis of the literature, examining the state of artificial intelligence in cybersecurity today and concentrating on anomaly detection in IoT networks in smart cities. Next, the pertinent theoretical frameworks are presented. The study then goes on to give the suggested conceptual framework while examining the relationships and possible effects between the factors that have been identified in the context of smart cities. After that, the focus of the conversation switches to the framework's consequences, taking into account both its theoretical contributions and its applicability to those involved in technology and urban development. The study's contributions to improving AI-driven cybersecurity tactics in the dynamic context of smart cities are summed up in the conclusion, which also discusses limitations and offers suggestions for further research.
Materials and Methods
The review explores the complex topic of AI-driven anomaly detection in the literature, as the field is developing and is at the forefront of addressing cybersecurity concerns in IoT networks in smart cities. Building on this, the review looks at the crucial role that IoT plays in urban settings, illuminating the opportunities and difficulties that these technologies present.
This review's main focus is on the cybersecurity environment in smart cities, an increasingly important subject in light of rising cyberthreats. After that, the review shifts to the topic of artificial intelligence, with a special emphasis on anomaly detection methods for thwarting cybersecurity attacks.
In addition, this literature study lays the groundwork for the conceptual framework that will be developed later, with the goal of combining these various threads into a coherent understanding of AI-driven anomaly detection in IoT networks in smart cities.
Smart Cities and the Role of IoT
With the integration of digital technology into the urban fabric, the notion of "smart cities" has developed as a critical response to the issues posed by urbanization (Ejaz et al., 2019; Batty et al., 2012). These cities attempt to improve sustainability, operational efficiency, and quality of life by combining technology, infrastructure, and urban planning (Shahidehpour, 2018).
Building on this base, the development of smart cities is characterized by an increase in complexity and capacity. Smart cities have developed into dynamic ecosystems (Linde et al, 2021) that include a wide range of applications and services, having initially concentrated on certain technical implementations. The objectives of sustainability, citizen welfare, and economic development are driving this transformation (Neirotti et al., 2014).
The Internet of Things (IoT), which is essential to the development of smart cities, is at the center of this technological revolution. In order to collect and exchange data, sensors and connection are embedded into physical items and infrastructure as part of the Internet of Things. According to Hashem et al. (2016), this data serves as the engine for intelligent city services and operations. IoT has many different and revolutionary uses in smart city applications. According to Almaba et al. (2017), they range from energy management smart grids that guarantee efficient power distribution and consumption to traffic and transportation systems that use sensors to control and improve traffic flow. This variety demonstrates how adaptable and far-reaching IoT technology are in city settings (Krichen and Lahami, 2020; Sharma and Jain, 2023).
Urban spaces are becoming more interactive, connected, and efficient places. However, integrating IoT technologies has also presented some serious challenges. With the vast amount of data generated and technologies integrated, privacy, security, and data management become major challenges (Elmaghraby and Losavio, 2014; Al-Turjman ey al, 2022). Strong and sophisticated security solutions are required to safeguard this complex network of devices and data from cybersecurity threats, which has become a top priority (Lu et al., 2018).
Cybersecurity Challenges in Smart City IoT Networks
IoT networks, which are essential to the infrastructure of smart cities, have particular risks because of how large and diverse they are. These systems produce a complex security environment since they are frequently made up of a wide range of devices with different security protocols and degrees of vulnerability (Shrama and Arya, 2023; Lu et al., 2018). This diversity presents a wide range of possible security vulnerabilities in addition to adding to the richness of functionality found in smart cities.
The widespread connectivity of IoT networks presents a big challenge to security. Although this connectedness makes it easier for data to flow and integrate, which is crucial for the smart cities to run efficiently, it also creates many opportunities for potential cyberattacks. These vulnerabilities are made worse by the disparate security protocols used by various devices, since less secure devices might serve as gateways to compromise the network as a whole (Alaba et al., 2017; Roman et al., 2013).
Furthermore, there is a dual risk introduced by smart cities' integration of digital networks and physical infrastructure. A cyberattack may impact vital city services and result in immediate physical repercussions (Baig et al., 2017; Demertzi et al., 2023). These interruptions can result in large financial losses as well as serious threats to public safety (Jing et al., 2014). An assault on traffic management systems, for instance, may result in extensive traffic disruptions, a delay in emergency response times, and even accidents. Similar to this, assaults on utility networks may cause service interruptions and safety risks, which would have a major influence on city residents' day-to-day life (Sicari et al., 2015). This poses a significant challenge since, according to Granjal et al. (2015), standard cybersecurity solutions might not be sufficiently prepared to handle the physical effects of digital breaches.
In conformity with the above discussion, a 2019 article by Deloitte highlighted three factors that cyber risk in the ecosystem of a smart city is influenced by: (Pandey et al., 2019)
1. The merging of the virtual and physical worlds, which results from the convergence of information technology and operational technology. This convergence blurs the divide between the physical and the cyber worlds;
2. Compatibility of new and legacy systems, which is considered due to the simultaneity of new and old systems in the smart city environment; and
3. The integration of various city services and supporting infrastructure, which is supported by IoT and a variety of digital systems and technologies. This last factor is depicted in
Figure 3.
Prominent cyberattacks, like the Mirai botnet event, have demonstrated the ability of attacks focused at the Internet of Things to inflict extensive disruption. These attackers launched massive distributed denial-of-service (DDoS) attacks by taking control of thousands of IoT devices (Ashraf et al., 2023). Such occurrences demonstrate the extent of damage that IoT vulnerabilities can permit, in addition to disrupting internet services. This emphasizes the crucial necessity for strong cybersecurity measures in smart city infrastructures (Antonakakis et al., 2017). Another example is the Emotet virus, which penetrated the city administration of Allentown in 2018 (Blake, 2018). Emotet started out as a banking trojan but over time it developed to be able to steal passwords for networks, financial information, address books, and perform DDoS attacks. It propagated via malicious scripts attached to emails, severely disrupting government activities in Allentown by infecting nearly every system and causing huge disruptions to traffic and tax collecting systems, among other areas (Blake, 2018).
AI-Driven Anomaly Detection in Cybersecurity
An important advancement in combating cyberthreats is the incorporation of Artificial Intelligence (AI) into cybersecurity. Traditional security measures
frequently fail to keep up with the increasing complexity and sophistication of cyberattacks, particularly in dynamic and networked contexts such as smart cities (Ahmed et al., 2016). This changing environment demands a move toward more sophisticated and flexible security solutions.
This change is being driven by artificial intelligence (AI) and machine learning (ML) technologies, which are bringing advanced data analytics to cybersecurity (Ullah et al., 2020; Bokhari and Myeong, 2023). The enormous amounts of data produced by IoT devices in smart cities can be processed by these technologies with ease. In the complex network of smart city IoT infrastructures, they make it possible to identify trends and abnormalities that can point to possible security breaches (Liu et al., 2018).
One important use of AI in cybersecurity is anomaly detection, which is the process of spotting odd patterns or behaviors that depart from accepted standards. Robust security in smart cities requires the ability to detect anomalies in real-time, as IoT devices are heavily networked and constantly exchange data (Xu et al., 2014). To proactively handle possible risks before they materialize into significant security problems, real-time detection is essential. For example, AI/ML models are used by contemporary intrusion detection systems (IDSs) to detect anomaly-based attacks and to detect new or zero-day threats (Ali et al., 2022). Traditional IDSs are passive security solutions that find anomalies and mark them as possible risks so that more research may be done on them. The main difficulty with those models is balancing false positives with false negatives, which is crucial for accurate threat detection (Schmitt, 2023).
Several supervised and unsupervised machine learning approaches are used in anomaly detection implementation. Unsupervised learning techniques find anomalies by spotting departures from known patterns in data, but supervised learning models need labeled datasets to discern between normal and abnormal behaviors (Mehta et al., 2020). The individual needs and data that are accessible in each smart city context determine which technique is best.
However, maintaining the model's accuracy and reducing false positives present a challenge in anomaly detection (Himeur et al., 2021). This is especially important for applications in smart cities, since false alarms can cause needless disruptions
and resource consumption (Ferrag et al., 2018). Thus, a primary goal in the creation and application of AI models is their accuracy in recognizing dangers.
Even if AI has the potential to improve cybersecurity, there are particular difficulties in using it in smart city settings. Because data-driven models are so important, large, varied, and high-quality datasets must be accessible in order to train and validate AI algorithms efficiently (Liu et al., 2018). There is a big data management and gathering challenge with this request.
Moreover, further challenges are presented by the advent of hostile AI attacks. These attacks involve the intentional manipulation of data or inputs by attackers to trick AI systems into making inaccurate predictions or classifications (Guembe et al., 2022). AI models must be updated and strengthened continuously to fend against such sophisticated attacks in light of the dynamic threat landscape (Papernot et al., 2016).
In addition, there are important questions about the ethical use of AI, especially when it comes to privacy and monitoring in smart cities (Ahmad et al., 2022). Deploying these technologies requires a delicate and important balance between the rights and privacy of citizens and the benefits of AI-driven security measures. To preserve public confidence and guarantee responsible use, it is imperative that AI systems function within moral and legal bounds (Jing et al., 2014).
Human and Policy Aspects in Smart City Cybersecurity
The effective adoption of AI-driven cybersecurity solutions in smart cities is highly impacted by human variables, like the attitudes and behaviors who interact with these systems (Shin, 2021). This has high relevance to the Technology Acceptance Model (TAM), where perceived usefulness and ease of use are important factors that influence the acceptance, adoption, and use of new technologies (Davis, 1989). This translates to evaluating how different stakeholders—from public authorities to city officials—perceive the usability and advantages of AI-driven security systems in the context of smart cities.
Extending this comprehension, behavioral intentions, which are impacted by attitudes, subjective norms, and perceived behavioral control, also play a role in shaping the adoption of AI in cybersecurity. This aligns well with the Theory of Planned Behavior (Ajzen, 1991). For example, the possibility of widespread acceptance and effective utilization increases if city managers and inhabitants believe that utilizing AI technologies will greatly enhance security and if such use corresponds with social norms and rules.
In addition to perceptions, attitudes, and behavioral intentions, research highlights the value of education, skills, and awareness campaigns to improve stakeholders' understanding of cybersecurity in smart cities (Malhorta et al., 2019). By providing people with the knowledge and abilities to recognize and effectively address cyberthreats, these programs significantly reduce risk and enhance the security culture across the smart city ecosystem (Kitchin, 2014).
In addition to the human factor, the environment of AI-driven cybersecurity in smart cities is influenced by legislative and regulatory frameworks (Badran, 2023). These frameworks play a crucial role in establishing cybersecurity best practices and standards, and they have a big impact on public acceptance and confidence in AI technologies (Nautiyal et al.,, 2018). They set the boundaries that AI systems must work inside, making sure they follow accepted standards and laws (Weber, 2010).
For example, regulations pertaining to privacy and data protection, like the GDPR in the European Union, are crucial in defining how AI systems in smart cities manage personal data. Adhering to these standards is crucial because it has an immediate effect on how AI-driven security solutions are designed, run, and perceived by the general public (Badii et al., 2020; Roman et al., 2013). These laws guarantee that AI systems uphold strong security protocols and preserve the privacy of citizens.
Finally, it is imperative to create cybersecurity regulations that are customized to the requirements of smart cities. The complexity of developing technologies must be addressed by such rules, which must strike a balance between several issues such as data sovereignty, cross-border data flows, and the security of linked IoT devices (Badii et al., 2020). Developing policies that are both flexible and adaptive in the face of swift technological improvements, and strong and comprehensive enough to guarantee security and privacy, is the major difficulty (Sicari et al., 2015).
Conceptual Model and Propositions
Theoretical Framework
This study's theoretical framework is based on a synergistic combination of multidisciplinary theories. These were carefully selected to thoroughly investigate how AI-enabled anomaly detection affects cybersecurity in the complex setting of smart cities.
To start with, the Theory of Complex Adaptive Systems (CAS) theory (Holland, 1995) – the main theory underpinning this study - offers a strong foundation for comprehending how different parts of smart city ecosystems interact dynamically, particularly with regard to cybersecurity. According to Holland (1995), as demonstrated in the "Complex Adaptive Systems” book, agents are the building blocks of complex adaptive systems, which are made up of pieces that interact with other agents to learn or adapt. All CAS have lever points, or places where a tiny directed movement results in massive, predictable changes in aggregate behavior. There are three levels of activity for all CAS agents: rule-discovery (creating new capabilities), credit-assignment (evaluating the use of existing capabilities), and performance (moment-by-moment capabilities). The adaptive interactions among its constituents always produce a CAS's behavior. These interactions also produce the hierarchical structure that distinguishes CASs—specific combinations of agents at one level become agents at the next higher level.
AI-enabled anomaly detection systems are a great fit for the idea of Complex Adaptive Systems (CAS), particularly when it comes to cybersecurity in smart cities. Let's examine the description given and discuss how AI systems work with anomaly detection.
CAS Structure Using Adaptive Agents:
Agents in CAS adjust to each other based on their interactions. These agents, which are AI-enabled anomaly detection systems, can be thought of as standalone AI models or algorithms that are always learning and changing in response to fresh information and system interactions. These agents, or AI models, in a smart city, for example, adjust by picking up on novel user behavior patterns, network traffic patterns, and possible security risks.
CAS Lever Points
Similar to how AI algorithms in anomaly detection can have a big influence, the notion of lever points in CAS describes how small directed actions can result in substantial changes in behavior. The AI's capacity to identify abnormalities can be significantly enhanced by making minor adjustments to its settings or learning method. This is consistent with the idea of optimizing AI models for enhanced efficacy in detecting possible cyberthreats.
Three CAS Agent Activity Levels
The functions of AI systems in anomaly detection are correlated with the performance, rule-discovery, and credit-assignment levels of CAS agents.
Performance: This refers to the day-to-day activities of the AI system, such as its ability to analyze network data in real-time and spot anomalies.
Credit Allocation: This can be thought of in terms of AI as the process of assessing and ranking how well various models or techniques identify security issues.
Rule-discovery is the process by which an artificial intelligence system learns or develops new algorithms or techniques to identify abnormalities, improving its capacity to counter new and unidentified cyberthreats.
Hierarchical Structure and Adaptive Interactions
The behavior of the system in AI-enabled anomaly detection is the outcome of the adaptive interactions between different AI models and algorithms. These interactions result in the creation of a complex, tiered cybersecurity strategy, guided by data and learning outcomes.
The way distinct AI models or layers function at different levels inside an anomaly detection system is similar to the hierarchical structure found in CAS. In order to create a multi-layered defense system, certain AI models may concentrate on preliminary data filtering and preprocessing, while others may concentrate on in-depth analysis or prediction.
In conclusion, the CAS principles offer a framework for comprehending the behavior and evolution of AI-enabled anomaly detection systems, especially in intricate contexts like smart city networks. Advanced AI systems in the field of cybersecurity are characterized by their hierarchical system structure, adaptive learning, and agent (AI model) interaction. Based on the above discussion of Holland’s CAS theory (Holland, 1995), the relevance of the CAS theory to this study is summarized in
Table 2.
Three other theories prove essential to the holistic proposed model in our study. These are the TAM, or Technology Acceptance Model (Davis, 1989), Theory of Planned Behavior (Ajzen, 1991), and the Theory of Socio-Technical Systems (Emery & Trist, 1960). Davis's (1989) Technology Acceptance Model (TAM) describes how people adopt and utilize technology. It can be used to comprehend how AI-driven technologies are received and deployed in smart cities. Moreover, according to Ajzen's (1991) Theory of Planned Behavior (TPB), an individual's attitude toward a behavior, subjective standards, and perceived behavioral control all influence their behavioral intentions, which in turn drive behavior. Of course, TPB provides a structure for comprehending the intentional behavioral goals underlying the integration of AI in cybersecurity in smart cities. The decision to adopt AI-driven security measures is influenced by a number of factors, including attitudes, subjective norms, and perceived behavioral control. This idea emphasizes how crucial it is to match AI integration with the expectations and behavioral tendencies of different stakeholders in smart cities. Finally, according to the Theory of Socio-Technical Systems, organizational work systems are made up of social and technological components that need to work together in order for them to function properly. This theory emphasizes how social systems—such as the smart city environment and its residents—interact with technology in smart cities, specifically AI-driven anomaly detection. It highlights the necessity of designing and implementing AI systems in a way that not only takes into account technological specifications but also takes organizational, social, and cultural aspects of urban environments into account.
Study Propositions and Conceptual Model
AI-enabled Anomaly Detection and Enhanced Cybersecurity in Smart City IoT Networks
Smart city environments with AI-enabled anomaly detection technologies are prime examples of complex adaptive systems in action (Ismail and Buyya, 2022), which aligns with the context of CAS framework. These technologies, which include a wide range of data analysis and machine learning capabilities, are dynamic by nature and are made to change and adapt to the ever-evolving threats and patterns in cybersecurity. Because of their adaptive nature, they are able to continuously improve their detection tactics, which is an essential ability considering how quickly cyber threats are changing (Schmitt, 2023; Ahmed et al., 2016). De facto, the ability of AI-driven anomaly detection to continuously adapt and learn from the IoT network (Liu et al., 2018) is what makes it effective in improving cybersecurity. The security and integrity of urban digital networks that are continually evolving and interconnected depend on this capability (Schmitt, 2023). These AI systems are essential for protecting smart cities from a wide range of cyberattacks since they are always learning to identify new patterns of risks (Ferrag et al., 2018).
Utilizing AI in cybersecurity arises as a tactical reaction to the complex and dynamic dangers present in Internet of Things networks, building on the adaptability of AI systems. Artificial intelligence (AI)-enabled solutions greatly improve the resilience and robustness of smart city cybersecurity infrastructures by continuously analyzing data and making adjustments in response to new information (Abdullahi et al., 2022; Ismail and Buyya, 2022). In addition to being reactive, this continuous process of adaptation and monitoring is proactive as well, seeing possible risks before they materialize as breaches (Schmitt, 2023; Xu et al., 2014).
Moreover, with a focus on zero-day threats, Ali et al. (2022) provides a thorough analysis of AI-based anomaly detection for cybersecurity. It emphasizes the necessity for cutting-edge AI techniques like deep learning and machine learning by highlighting the growth of cyber threats and the shortcomings of conventional security measures. In order to compare several methods for detecting zero-day attacks, the article addresses a variety of AI models, datasets, and evaluation criteria. It comes to the conclusion that deep learning-based AI techniques are more successful at spotting and stopping complex cyberattacks, proving the beneficial correlation between improved cybersecurity and AI-based anomaly detection.
As a result, inside this intricate network of relationships, cybersecurity risks, IoT infrastructure, and AI systems are all integrated components rather than separate entities. The efficacy of artificial intelligence (AI) in augmenting cybersecurity is based on its capacity to maneuver and adjust inside this intricate system, reacting instantly to changing hazards. Thus, in light of this comprehensive analysis, the following proposition can be made:
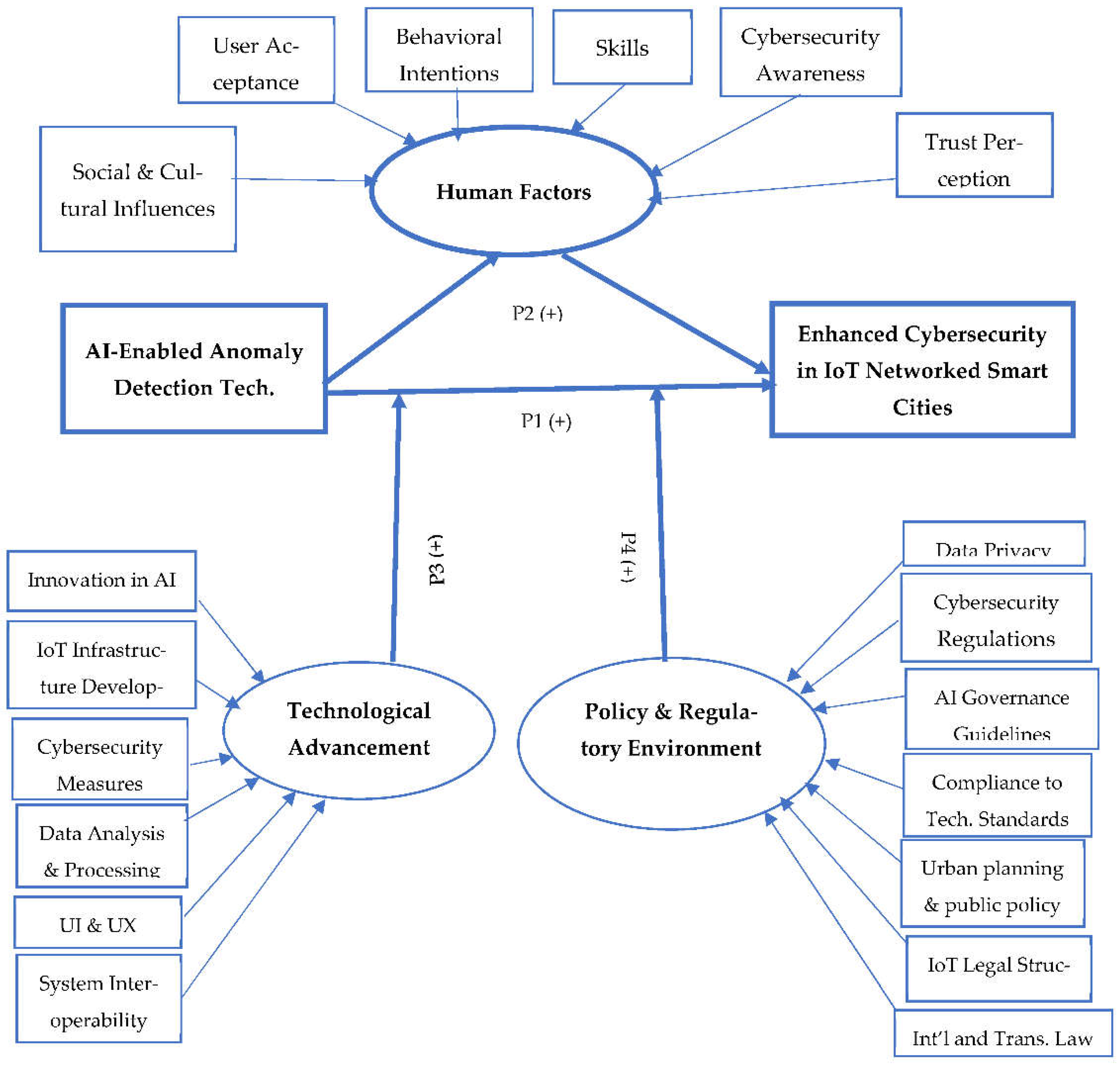
P1: AI-enabled anomaly detection technologies are positively related to improved cybersecurity in the complex adaptive system of smart city IoT networks.
Role of Human Factors in the Relationship between AI-enabled Anomaly Detection and Enhanced Cybersecurity in Smart City IoT Networks
The AI-powered solutions' efficacy aforementioned above isn't only based on how advanced their technology is. In this equation, the human aspect is a crucial factor. User perceptions, such as perceived ease of use and perceived usefulness, have a substantial impact on the acceptance and effective use of technology (Ahmad et al., 2020). This conforms to TAM (Davis et al, 1989), and applies into how residents and city officials alike view and engage with AI-driven cybersecurity solutions in smart cities. The usefulness of AI-enabled anomaly detection in strengthening cybersecurity is vitally impacted by their engagement, confidence, and desire to employ these technologies.
In addition, by taking into account the impact of behavioral intentions, which are influenced by attitudes and subjective norms, as the Theory of Planned Behavior (TPB) (Ajzen, 1991) suggests, this effect will be even more clarified. The alignment of AI-enabled systems with human behavioral tendencies is necessary for these technologies to effectively improve cybersecurity (Chow et al., 2023). User-friendly interfaces, sufficient training, and awareness campaigns that improve comprehension and efficient application of AI technology in smart city ecosystems are all part of this alignment (Kitchin, 2014).
Consequently, human variables play a significant role in the effectiveness of AI-enabled anomaly detection systems in detecting and reducing cybersecurity threats. These comprise user attitudes, actions, and the general social and cultural preparedness to incorporate these technologies into day-to-day activities.
On the basis of this thorough comprehension, the following proposition can be put forth:
P2: In IoT networked smart city environments, human factors—such as user perceptions, behaviors, and social readiness to accept and efficiently utilize AI technologies—mediate the relationship between AI-enabled anomaly detection and enhanced cybersecurity.
Role of Technological Advancement and Policy and Regulatory Environment in the Relationship between AI-enabled Anomaly Detection and Enhanced Cybersecurity in Smart City IoT Networks
Although there is a clear and direct link between cybersecurity and AI-enabled anomaly detection, this relationship is not absolute or isolated. A number of moderating factors may have an impact, either strengthening or weakening it. These elements include the regulatory environment, policy frameworks, and technology developments.
Innovations in technology have a significant impact on how effective AI-powered anomaly detection systems are. These systems get more advanced with time, able to handle increasingly complex attacks and adjust to new cybersecurity difficulties (Yigitcanlar et al., 2020). The degree of technical maturity can have a big impact on how well AI technologies recognize and address cybersecurity threats and breaches in smart city settings (Liu et al., 2018).
Moreover, the regulatory framework and policies also play a crucial role in this relationship. The capabilities of AI systems in cybersecurity applications can be either enabled or restricted by laws and policies pertaining to data privacy, security requirements, and the use of AI technology. AI-enabled systems can have a more significant impact on cybersecurity if effective legislative frameworks are in place to encourage innovation while maintaining security and privacy (Zhou and Kankanhalli, 2021; Chakrabarty and Engels, 2020). On the other hand, outmoded or restrictive policies could limit their potential (Weber, 2010; Roman et al., 2013).
Therefore, the relationship between improved cybersecurity in smart cities and AI-enabled anomaly detection technologies is not linear; rather, it is driven by the dynamic interaction between current policy and regulatory frameworks and technical improvements. The degree to which AI technologies may be successfully applied and incorporated into smart city cybersecurity infrastructure depends on these moderating elements.
This sophisticated comprehension allows for stating the following propositions
P3: Technological advancement moderates the relationship between AI-enabled anomaly detection and enhanced cybersecurity in IoT networked smart cities.
P4: Policy and regulatory environment moderates the relationship between AI-enabled anomaly detection and enhanced cybersecurity in IoT networked smart cities.
These factors collectively influence the efficacy and application of AI technologies in urban cybersecurity frameworks.
Based on the above discussion and derived propositions, the conceptual model of the study could be depicted as shown in
Figure 4.
Conceptual Model Constructs and Dimensions
The main constructs of the model and their dimensions are discussed in the following sections.
- A.
AI-Driven Anomaly Detection Techniques: These are the AI-driven approaches used to recognize and address cybersecurity risks (Hassan et al., 2023) in IoT networks seen in smart cities (Caiazzo et al, 2023). By modeling the actions that are deemed typical within a system and recognizing prospective assaults from behaviors that differ from the established normal behavior pattern, the anomaly-based approach seeks to discover new (unknown) attacks (Panagiotou, 2021).
- B.
Cybersecurity Enhancement in Smart City IoT Networks: this outcome variable measures how much smart city IoT networks' security and resistance to cyber threats have improved overall (Khatoun and Zeadally, 2017; Rawat and Ghafoor, 2018). The main indicators of enhanced IoT-networked smart city cybersecurity are social welfare, urban mobility solutions, operational resilience, and sustainability of the city. (Alahi et al., 2023). Of course, operational resilience is essential to ensure and maintain continuity in services and high up time (Chakrabarty and Engels, 2020).
- C.
Human factors, which include user behavior, acceptance, and knowledge of cybersecurity measures driven by AI. The relationship between AI-driven anomaly detection and cybersecurity enhancing effectiveness is mediated by human variables, including: (Chow et al., 2023; Adel, 2023; Ahmad et al., 2022; Cao et al., 2021)
- a.
Acceptance and Adoption by Users: this dimension deals with how people accept and employ AI technologies, from citizens to municipal officials. It involves views of utility and simplicity of use, perceived performance expectancy, and perceived effort expectancy, which are crucial in determining the desire to interact with and use new technologies.
- b.
Behavioral Intentions: this dimension examines how users' beliefs, subjective standards, and perceived behavioral control affect their intents and behaviors. It discusses how social forces and perceptions affect how AI technologies are used in smart cities.
- c.
Training and Development of Skills: the degree of instruction and skill-building that AI system users can access. This aspect is essential for guaranteeing that people possess the skills and knowledge required to communicate with and operate AI-driven cybersecurity solutions.
- d.
Cybersecurity Awareness: users' overall knowledge and comprehension of cybersecurity issues. This covers being aware of possible dangers, following safe procedures, and how AI can help reduce the risk of cyberattacks.
- e.
Perception of Trust and Reliability: A key component influencing AI solution acceptability and efficacy is trust. This encompasses users' opinions of these technologies' reliability in identifying and countering cybersecurity risks, as well as their faith in AI systems.
- f.
Social and Cultural Influences: this dimension acknowledges the substantial influence that social settings and cultural norms can have on attitudes and behaviors regarding technology.
- D.
Technology Advancement: technological advancements play a crucial role in shaping the efficacy of AI-enabled anomaly detection systems. As technology evolves, these systems become more sophisticated, capable of handling more complex threats and adapting to new cybersecurity challenges. The level of technological maturity can significantly influence how effectively AI tools identify and respond to threats in smart city environments. The concept of technology advancement could encompass: (Son et al., 2023; Alahi et al., 2023; Adel, 2023; Fatima et al., 2020; Shneiderman et al., 2016; Liu et al., 2018):
- a.
Technological Innovation in AI and Machine Learning: this component deals with the creation and application of novel machine learning and artificial intelligence algorithms. It covers innovations especially suited for cybersecurity applications in fields like deep learning, neural networks, and predictive analytics.
- b.
IoT Infrastructure Development: the degree of IoT infrastructure integration and sophistication in smart cities. This involves the implementation of sophisticated sensors, network systems, and connected devices that enable large-scale data gathering and exchange.
- c.
Capabilities for Data Analysis and Processing: the capacity to effectively handle and evaluate massive amounts of data produced by IoT networks in smart cities. This encompasses developments in edge computing, cloud computing, and big data technologies that improve the ability to manage and analyze large, complicated datasets.
- d.
Cybersecurity Measures: the creation and use of cutting-edge cybersecurity policies and procedures. This dimension includes advancements in intrusion detection systems, network security, encryption, and other security technologies meant to fend off dynamic cyberthreats.
- e.
System Interoperability & Integration: the degree of integration and coherence among diverse technology systems in smart cities. This dimension is centered on the creation of protocols and standards that provide smooth interoperability between various platforms and technologies.
- f.
Interface and Experience Design for Users: developments in the creation of user experiences and interfaces that accommodate a variety of user groups. Creating more logical, user-friendly mechanisms that make interacting and interacting with technology easier is part of this.
- E.
Policies & Regulatory Framework: Policies and regulations governing data privacy, security standards, and the use of AI technology can either enable or restrict the capabilities of AI systems in cybersecurity applications. Effective policy frameworks that support innovation while ensuring security and privacy can enhance the impact of AI-enabled systems on cybersecurity. Conversely, restrictive or outdated policies may hinder their potential. This framework includes (Alahi et al., 2023; Zhou and Kankanhalli, 2021; Chakrabarty and Engels, 2020; Wang et al., 2021; Weber, 2010; Roman et al., 2013)
- a.
Data Privacy & Protection Law: regulations that control data collection, storage, processing, and sharing are included in this dimension. They have an effect on the development and functionality of AI systems by dictating how private and sensitive data must be treated.
- b.
Regulations pertaining to cybersecurity: cybersecurity measures are mandated by these particular laws and standards. These include specifications for data encryption, network security, and breach reporting, making sure AI systems in smart cities follow strict security guidelines.
- c.
AI Governance Guidelines: policies that particularly address the creation and application of AI technologies fall under this category. To guarantee that AI is utilized responsibly and ethically, it comprises accountability measures, requirements for algorithmic transparency, and ethical norms.
- d.
Compliance to Technology Standards: this dimension includes standards and compliance requirements for quality assurance, interoperability, and technology implementation. By ensuring that AI and IoT technologies adhere to global norms and industry best practices, they promote dependability and compatibility.
- e.
Urban planning and public policy: policies pertaining to public welfare and urban development that affect how AI and IoT technologies are integrated in smart cities. This includes policies for public participation, resource allocation, and strategic planning that influence how technology is used to meet urban demands.
- f.
Legal Structure for the Implementation of IoT: laws that particularly control the implementation of IoT, with an emphasis on network security, device security, and ecosystem management. This dimension makes sure that IoT networks and devices run effectively and safely in smart cities.
- g.
International and Transnational Law: laws and regulations that deal with worldwide collaboration in AI and IoT governance, cross-border cybersecurity risks, and international data sharing. For smart cities to be a part of a global network and communicate with global data and technological standards, this dimension is essential.
The various theories underpinning the above relationships with justification of each are outlined in
Table 3.
Discussion
Drawing on a solid theoretical framework, this study proposed a multi-lens model that added to the body of literature emphasizing that integrating AI-enabled anomaly detection into smart city IoT networks significantly improves cybersecurity (e.g., Villegas-Ch et al., 2023; Jia et al., 2023; Ullah et al., 2020). The theory of Complex Adaptive Systems (CAS), which forms the basis of this study's model, offers a thorough foundation for comprehending this integration. According to research by Liu et al. (2018) and Ahmed et al. (2016), the capacity of artificial intelligence for adaptation and learning is essential for mitigating the ever-changing nature of cyber threats. The model also highlights how important human aspects and social and environmental factors are to AI technologies' efficacy, which is consistent with the ideas of the Theory of Planned Behavior (TPB) (Ajzen, 1991), the Technology Acceptance Model (TAM) (Davis, 1989), and the Socio-Technical Systems Theory (Emery and Trist, 1960).
The examination of AI-enabled anomaly detection in smart city IoT networks by this study reveals a complicated yet intriguing nexus between policy, human factors, and technology. The suggested model offers a comprehensive understanding of the cybersecurity environment in smart cities since it is based on a multi-lens perspective. It draws attention to the significant contributions made by technology as well as the general impact of policy and regulatory
At the forefront of this paradigm is AI-enabled anomaly detection, which embodies a critical technological development in cybersecurity. In line with the discoveries of Ahmed et al. (2016) and Liu et al. (2018), our model emphasizes how important AI systems' adaptability and learning capacities are to fending off the constantly changing cybersecurity threats in smart city settings. A defining feature of CAS theory, these systems, furnished with advanced algorithms, are dynamic agents that can adapt to novel threats rather than existing as static entities. This flexibility is especially important in the complex web of IoT devices that serves as the foundation for smart cities.
Moving from technology to human role, our model highlights that human variables play a critical role in the success of AI-enabled anomaly detection, a component that is frequently disregarded in conventional cybersecurity techniques. In fact, people's opinions of the technology's utility and usability will determine whether AI systems are accepted, adopted, and used effectively in smart cities. By extending this concept to the field of cybersecurity, our model proposes that in order for AI systems to be genuinely effective, they should not only be technologically sophisticated, but also conform to the psychological and behavioral preferences of its end users. Within this context, taking the various stakeholders’ abilities into consideration, enhancing their skills with proper and continuous training, and updating their knowledge with awareness programs are of paramount importance.
Furthermore, according to Weber (2010) and Roman et al. (2013), among others, the policy and regulatory environment is identified in our model as a crucial moderating component. This dimension recognizes that laws and regulations have a significant impact on the implementation and performance of AI-enabled technologies in smart cities. These frameworks determine the requirements for security procedures, data protection, and general AI technology governance. As a result, they influence how cybersecurity measures are implemented in practice.
Although our model corroborates with the extant literature regarding the impact of AI-based anomaly detection on enhanced smart city cybersecurity, it differs from previous research in that it is holistic and tri-lens. The model incorporates all relevant factors that impact cybersecurity in smart cities. Although prior research has frequently concentrated on discrete features like technology capabilities (Liu et al., 2018) or policy consequences (Weber, 2010), our model integrates these components with the occasionally disregarded issue of human factors. This all-encompassing strategy fills in a knowledge gap on the ways in which different elements interact and affect AI's effectiveness in cybersecurity.
To sum up, this work adds a great deal to the extant body of information by providing a model that both complements and advances the existing literature. With the integration of human elements, regulatory issues, and technology innovation, the model provides a more nuanced and comprehensive view of cybersecurity in smart city IoT networks. It emphasizes the significance of a well-rounded strategy that takes into account the technical aptitude of AI systems, the perceptual and behavioral characteristics of users, and the directing impact of legal and regulatory frameworks. This model emphasizes the necessity for various tactics in addressing the intricate difficulties of cybersecurity in smart cities and serves as a blueprint for future study and practice.
Conclusion and Future Research Recommendations
The growing complexity of cybersecurity issues in smart cities and the lack of existing models that adequately combine technological, human, and external aspects are the driving forces behind the necessity of this study and the model it proposes. In order to fill these gaps, this study provides a comprehensive framework that takes into account the many demands of stakeholders as well as the complex and multifaceted character of smart city environments. The model addresses present needs and paves the way for future developments in urban cybersecurity. It is a significant contribution to the area because of its emphasis on adaptability, user-centricity, and response to external factors.
By bridging the previously unexplored gap in cybersecurity literature between AI-enabled anomaly detection and human aspects in smart cities, this study enhances the theoretical landscape. Using TAM, TPB, and the Socio-Technical Systems theories as a guide, it presents a sophisticated understanding of the relationship between technology advancement and user engagement. Furthermore, the model draws attention to the often-overlooked crucial role that outside variables like laws and technology developments have in influencing cybersecurity measures.
At the practical level, the study provides a thorough framework for putting AI-driven cybersecurity into urban IoT networks. It offers a practical and efficient framework for AI deployment that is both technologically sound and user-centric by combining human factors and external moderators. This model emphasizes flexible and responsive approaches for changing urban cybersecurity concerns, acting as a guide for policymakers, cybersecurity experts, and city planners.
Future research should concentrate on empirically validating the model in a variety of metropolitan and non-urban contexts using surveys, case studies, or experimental techniques. This empirical method is essential for evaluating the model's efficacy and relevance in the real world. Furthermore, investigating user interactions with AI systems, evaluating the effects of changing laws and regulations, and staying up to date with technology developments continue to be important fields. In the dynamic field of smart city cybersecurity, such thorough and empirical study will offer deeper insights and improve the model's applicability.
As we stand at the nexus of urban evolution and technology change, this study envisions a future where our digital and urban domains are protected with unparalleled accuracy and foresight by tying together the threads of AI-enabled anomaly detection, human-centric design, and dynamic policy landscapes. Our model serves as more than just a roadmap for this trip; it is a lighthouse that points the way to an urban future that is safer, smarter, and more secure.
Funding
This research received no external funding
Data Availability Statement
Not Applicable.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Adel, A. Unlocking the Future: Fostering Human–Machine Collaboration and Driving Intelligent Automation through Industry 5.0 in Smart Cities. Smart Cities 2023, 6, 2742–2782. [Google Scholar] [CrossRef]
- Ahmad, K.; Maabreh, M.; Ghaly, M.; Khan, K.; Qadir, J.; Al-Fuqaha, A. Developing future human-centered smart cities: Critical analysis of smart city security, Data management, and Ethical challenges. Computer Science Review 2022, 43, 100452. [Google Scholar] [CrossRef]
- Ahmad, K.; Maabreh, M.; Ghaly, M.; Khan, K.; Qadir, J.; Al-Fuqaha, A. Developing future human-centered smart cities: Critical analysis of smart city security, interpretability, and ethical challenges. arXiv arXiv:2012.09110, 2020.
- Ahmed, M.; Mahmood, A.N.; Hu, J. A survey of network anomaly detection techniques. Journal of Network and Computer Applications 2016, 60, 19–31. [Google Scholar] [CrossRef]
- Ajzen, I. The theory of planned behavior. Organizational behavior and human decision processes 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. Journal of Network and Computer Applications 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Alahi, M.E.E.; Sukkuea, A.; Tina, F.W.; Nag, A.; Kurdthongmee, W.; Suwannarat, K.; Mukhopadhyay, S.C. Integration of IoT-Enabled Technologies and Artificial Intelligence (AI) for Smart City Scenario: Recent Advancements and Future Trends. Sensors 2023, 23, 5206. [Google Scholar] [CrossRef]
- Ali, S.; Rehman, S.U.; Imran, A.; Adeem, G.; Iqbal, Z.; Kim, K.I. Comparative Evaluation of AI-Based Techniques for Zero-Day Attacks Detection. Electronics 2022, 11, 3934. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Zahmatkesh, H.; Shahroze, R. An overview of security and privacy in smart cities' IoT communications. Transactions on Emerging Telecommunications Technologies 2022, 33, e3677. [Google Scholar] [CrossRef]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; ... & Lever, C. (2017). Understanding the Mirai Botnet. In 26th USENIX Security Symposium (USENIX Security 17) (pp. 1093-1110).
- Ashraf, J.; Keshk, M.; Moustafa, N.; Abdel-Basset, M.; Khurshid, H.; Bakhshi, A.D.; Mostafa, R.R. IoTBoT-IDS: A novel statistical learning-enabled botnet detection framework for protecting networks of smart cities. Sustainable Cities and Society 2021, 72, 103041. [Google Scholar] [CrossRef]
- Badii, C.; Bellini, P.; Difino, A.; Nesi, P. Smart city IoT platform respecting GDPR privacy and security aspects. IEEE Access 2020, 8, 23601–23623. [Google Scholar] [CrossRef]
- Badran, A. Developing smart cities: Regulatory and policy implications for the State of Qatar. International Journal of Public Administration 2023, 46, 519–532. [Google Scholar] [CrossRef]
- Baig, Z.A.; Szewczyk, P.; Valli, C.; Rabadia, P.; Hannay, P.; Chernyshev, M. . & Peacock, M. Future challenges for smart cities: Cyber-security and digital forensics. Digital Investigation 2017, 22, 3–13. [Google Scholar]
- Batty, M.; Axhausen, K.W.; Giannotti, F.; Pozdnoukhov, A.; Bazzani, A.; Wachowicz, M. . & Portugali, Y. Smart cities of the future. European Physical Journal Special Topics 2012, 214, 481–518. [Google Scholar]
- Blake, A. (2018). Malware infection poised to cost $1 million to Allentown (February 21, 2018). Retrieved from: https://www.washingtontimes.com/news/2018/feb/21/malware-infection-posed-cost-1-million-allentown-p/.
- Bokhari, S.A.A.; Myeong, S. The influence of artificial intelligence on e-Governance and cybersecurity in smart cities: A stakeholder’s perspective. IEEE Access 2023. [CrossRef]
- Caiazzo, B.; Murino, T.; Petrillo, A.; Piccirillo, G.; Santini, S. An IoT-based and cloud-assisted AI-driven monitoring platform for smart manufacturing: design architecture and experimental validation. Journal of Manufacturing Technology Management 2023, 34, 507–534. [Google Scholar] [CrossRef]
- Cao, G.; Duan, Y.; Edwards, J.S.; Dwivedi, Y.K. Understanding managers’ attitudes and behavioral intentions towards using artificial intelligence for organizational decision-making. Technovation 2021, 106, 102312. [Google Scholar] [CrossRef]
- Caragliu, A.; Del Bo, C.; Nijkamp, P. Smart cities in Europe. Journal of Urban Technology 2011, 18, 65–82. [Google Scholar] [CrossRef]
- Chakrabarty, S.; Engels, D.W. (2020, December). Secure smart cities framework using IoT and AI. In 2020 IEEE Global Conference on Artificial Intelligence and Internet of Things (GCAIoT) (pp. 1-6). IEEE.
- Chow, C.S.K.; Zhan, G.; Wang, H.; He, M. Artificial Intelligence (Ai) Adoption: An Extended Compensatory Level Of Acceptance. Journal of Electronic Commerce Research 2023, 24, 84–106. [Google Scholar]
- Costa, D.G.; Duran-Faundez, C. Open-source electronics platforms as enabling technologies for smart cities: Recent developments and perspectives. Electronics 2018, 7, 404. [Google Scholar] [CrossRef]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS quarterly 1989, 319–340. [Google Scholar] [CrossRef]
- de Azambuja, A.J.G.; Plesker, C.; Schützer, K.; Anderl, R.; Schleich, B.; Almeida, V.R. Artificial Intelligence-Based Cyber Security in the Context of Industry 4.0—A Survey. Electronics 2023, 12, 1920. [Google Scholar] [CrossRef]
- Demertzi, V.; Demertzis, S.; Demertzis, K. An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities. Applied Sciences 2023, 13, 790. [Google Scholar] [CrossRef]
- Demertzi, V.; Demertzis, S.; Demertzis, K. An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities. Applied Sciences 2023, 13, 790. [Google Scholar] [CrossRef]
- Ejaz, W.; Anpalagan, A.; Ejaz, W.; Anpalagan, A. Internet of things for smart cities: overview and key challenges. Internet of Things for Smart Cities: Technologies, Big Data and Security 2019, 1–15. [Google Scholar]
- Elmaghraby, A.S.; Losavio, M.M. Cyber security challenges in Smart Cities: Safety, security and privacy. Journal of advanced research 2014, 5, 491–497. [Google Scholar] [CrossRef] [PubMed]
- Fatima, S.; Desouza, K.C.; Dawson, G.S. National strategic artificial intelligence plans: A multi-dimensional analysis. Economic Analysis and Policy 2020, 67, 178–194. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. . & Raza, I. Blockchain technologies for the Internet of Things: Research issues and challenges. IEEE Internet of Things Journal 2018, 6, 2188–2204. [Google Scholar]
- Granjal, J.; Monteiro, E.; Sa Silva, J. Security for the Internet of Things: A survey of existing protocols and open research issues. IEEE Communications Surveys & Tutorials 2015, 17, 1294–1312. [Google Scholar]
- Guembe, B.; Azeta, A.; Misra, S.; Osamor, V.C.; Fernandez-Sanz, L.; Pospelova, V. The emerging threat of ai-driven cyber attacks: A review. Applied Artificial Intelligence 2022, 36, 2037254. [Google Scholar] [CrossRef]
- Hasan, K.; Shetty, S.; Ullah, S. (2019, December). Artificial intelligence empowered cyber threat detection and protection for power utilities. In 2019 IEEE 5th International Conference on Collaboration and Internet Computing (CIC) (pp. 354-359). IEEE.
- Hashem, I.A.T.; Chang, V.; Anuar, N.B.; Adewole, K.; Yaqoob, I.; Gani, A. . & Chiroma, H. The role of big data in smart city. International Journal of Information Management 2016, 36, 748–758. [Google Scholar]
- Hassan, M.M.; Abrar, M.F.; Hasan, M. (2023). An Explainable AI-Driven Machine Learning Framework for Cybersecurity Anomaly Detection. In Cyber Security and Business Intelligence (pp. 197-219). Routledge.
- Himeur, Y.; Ghanem, K.; Alsalemi, A.; Bensaali, F.; Amira, A. Artificial intelligence based anomaly detection of energy consumption in buildings: A review, current trends and new perspectives. Applied Energy 2021, 287, 116601. [Google Scholar] [CrossRef]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. (2016, May). Threat analysis of IoT networks using artificial neural network intrusion detection system. In 2016 International Symposium on Networks, Computers and Communications (ISNCC) (pp. 1-6). IEEE.
- Holland, J.H. 'Complex adaptive systems (CAS)', Complexity: A Very Short Introduction, Very Short Introductions (Oxford, 2014; online edn, Oxford Academic, 24 July 2014).
- Huber, B.; Kandah, F.; Skjellum, A. BEAST: Behavior as a Service for Trust management in IoT devices. Future Generation Computer Systems 2023, 144, 165–178. [Google Scholar] [CrossRef]
- Ismail, L.; Buyya, R. Artificial intelligence applications and self-learning 6G networks for smart cities digital ecosystems: Taxonomy, challenges, and future directions. Sensors 2022, 22, 5750. [Google Scholar] [CrossRef] [PubMed]
- Jia, Y.; Gu, Z.; Du, L.; Long, Y.; Wang, Y.; Li, J.; Zhang, Y. Artificial intelligence enabled cyber security defense for smart cities: A novel attack detection framework based on the MDATA model. Knowledge-Based Systems 2023, 276, 110781. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: perspectives and challenges. Wireless Networks 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Kaspersky (2023). Kaspersky unveils an overview of IoT-related threats in 2023(September). Retrieved from: https://www.kaspersky.com/about/press-releases/2023_kaspersky-unveils-an-overview-of-iot-related-threats-in-2023.
- 46. Kaspersky. (2020). IoT report: Year in figures. Kaspersky Lab.
- Khatoun, R.; Zeadally, S. Cybersecurity and privacy solutions in smart cities. IEEE Communications Magazine 2017, 55, 51–59. [Google Scholar] [CrossRef]
- Kitchin, R. The real-time city? Big data and smart urbanism. GeoJournal 2014, 79, 1–14. [Google Scholar] [CrossRef]
- Konstantopoulou, E.; Sklavos, N.; Ognjanovic, I. (2023). Securing Public Safety Mission-Critical 5G Communications of Smart Cities. In Internet of Everything for Smart City and Smart Healthcare Applications (pp. 61-74). Cham: Springer Nature Switzerland.
- Krichen, M.; Lahami, M. Towards a runtime testing framework for dynamically adaptable internet of things networks in smart cities. Smart Infrastructure and Applications: Foundations for Smarter Cities and Societies 2020, 589–607. [Google Scholar]
- Linde, L.; Sjödin, D.; Parida, V.; Wincent, J. Dynamic capabilities for ecosystem orchestration A capability-based framework for smart city innovation initiatives. Technological Forecasting and Social Change 2021, 166, 120614. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, P.; Zhou, J. Using AI to enhance the security of Internet of Things. Sensors 2018, 18, 403. [Google Scholar]
- Lu, Y.; Xu, L.D.; Xu, J. Internet of Things (IoT) cybersecurity research: A review of current research topics. IEEE Internet of Things Journal 2018, 6, 2103–2115. [Google Scholar] [CrossRef]
- Ma, C. Smart city and cyber-security; technologies used, leading challenges and future recommendations. Energy Reports 2021, 7, 7999–8012. [Google Scholar] [CrossRef]
- Magaia, N.; Fonseca, R.; Muhammad, K.; Segundo, A.H.F.N.; Neto, A.V.L.; de Albuquerque, V.H.C. Industrial internet-of-things security enhanced with deep learning approaches for smart cities. IEEE Internet of Things Journal 2020, 8, 6393–6405. [Google Scholar] [CrossRef]
- Malhotra, C.; Srivastava, A.; Gandotra, V. Cybersecurity and Smart Cities: Establishing the Need for Capacity Building. CYBERNOMICS 2019, 1, 6–15. [Google Scholar]
- Mehta, P.; Pandit, A.K.; Modi, C. Machine learning-based anomaly detection techniques for smart cities: A survey. Information Processing & Management 2020, 57, 102181. [Google Scholar]
- Nautiyal, L.; Malik, P.; Agarwal, A. Cybersecurity system: an essential pillar of smart cities. Smart Cities: Development and Governance Frameworks 2018, 25–50. [Google Scholar]
- Neirotti, P.; De Marco, A.; Cagliano, A.C.; Mangano, G.; Scorrano, F. Current trends in Smart City initiatives: Some stylised facts. Cities 2014, 38, 25–36. [Google Scholar] [CrossRef]
- Panagiotou, P.; Mengidis, N.; Tsikrika, T.; Vrochidis, S.; Kompatsiaris, I. Host-based intrusion detection using signature-based and ai-driven anomaly detection methods. Information & Security 2021, 50, 37–48. [Google Scholar]
- Pandey, P.; Golden, D.; Peasley, S.; and Kelkar, M. (2019). Making smart cities cybersecure. Retrieved from: https://www2.deloitte.com/us/en/insights/focus/smart-city/making-smart-cities-cyber-secure.html.
- Papernot, N.; McDaniel, P.; Wu, X.; Jha, S.; Swami, A. (2016). Distillation as a defense to adversarial perturbations against deep neural networks. In 2016 IEEE Symposium on Security and Privacy (SP) (pp. 582-597).
-
Smart cities cybersecurity and privacy; Rawat, D.B., Ghafoor, K.Z., Eds.; Elsevier, 2018. [Google Scholar]
- Rejeb, A.; Rejeb, K.; Simske, S.; Treiblmaier, H.; Zailani, S. The big picture on the internet of things and the smart city: a review of what we know and what we need to know. Internet of Things 2022, 19, 100565. [Google Scholar] [CrossRef]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Computer Networks 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Schmitt, M. Securing the Digital World: Protecting smart infrastructures and digital industries with Artificial Intelligence (AI)-enabled malware and intrusion detection. Journal of Industrial Information Integration 2023, 36, 100520. [Google Scholar] [CrossRef]
- Shahidehpour, M.; Li, Z.; Ganji, M. Smart cities for a sustainable urbanization: Illuminating the need for establishing smart urban infrastructures. IEEE Electrification magazine 2018, 6, 16–33. [Google Scholar] [CrossRef]
- Sharma, A.; Jain, P. Adaptability of IoT and Cloud for Enabling the Smart City: Applications and Challenges. Handbook of Research on Network-Enabled IoT Applications for Smart City Services 2023, 54–74. [Google Scholar]
- Sharma, H.; Haque, A.; Blaabjerg, F. Machine learning in wireless sensor networks for smart cities: a survey. Electronics 2021, 10, 1012. [Google Scholar] [CrossRef]
- Sharma, R.; Arya, R. Security threats and measures in the Internet of Things for smart city infrastructure: A state of art. Transactions on Emerging Telecommunications Technologies 2023, 34, e4571. [Google Scholar] [CrossRef]
- Shin, D. The effects of explainability and causability on perception, trust, and acceptance: Implications for explainable AI. International Journal of Human-Computer Studies 2021, 146, 102551. [Google Scholar] [CrossRef]
- Shneiderman, B.; Plaisant, C.; Cohen, M.; Jacobs, S.; Elmqvist, N.; Diakopoulos, N. Designing the user interface: strategies for effective human-computer interaction; Pearson, 2016. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Computer Networks 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Singh, A.P. (2023). AI in Cyber Security: Advantages, Applications and Use Cases. Retrieved from: https://www.analyticsvidhya.com/blog/2023/02/future-of-ai-and-machine-learning-in-cybersecurity/.
- Son, T.H.; Weedon, Z.; Yigitcanlar, T.; Sanchez, T.; Corchado, J.M.; Mehmood, R. Algorithmic urban planning for smart and sustainable development: Systematic review of the literature. Sustainable Cities and Society 2023, 104562. [Google Scholar] [CrossRef]
- 76. Statista. (2020). Number of Internet of Things (IoT) connected devices worldwide in 2019, 2020 and 2025. Statista Research Department.
-
Security and Privacy Applications for Smart City Development; Tamane, S.C., Dey, N., Hassanien, A.E., Eds.; Springer, 2021; p. 308. [Google Scholar]
- Trist, E.L. (1981). The evolution of socio-technical systems (Vol. 2). Toronto: Ontario Quality of Working Life Centre.
- Ullah, Z.; Al-Turjman, F.; Mostarda, L.; Gagliardi, R. Applications of artificial intelligence and machine learning in smart cities. Computer Communications 2020, 154, 313–323. [Google Scholar] [CrossRef]
- Umair, M.; Cheema, M.A.; Cheema, O.; Li, H.; Lu, H. Impact of COVID-19 on IoT adoption in healthcare, smart homes, smart buildings, smart cities, transportation and industrial IoT. Sensors 2021, 21, 3838. [Google Scholar] [CrossRef] [PubMed]
- Umpleby, S.A.; Dent, E.B. The origins and purposes of several traditions in systems theory and cybernetics. Cybernetics & Systems 1999, 30, 79–103. [Google Scholar]
- Villegas-Ch, W.; Govea, J.; Jaramillo-Alcazar, A. IoT Anomaly Detection to Strengthen Cybersecurity in the Critical Infrastructure of Smart Cities. Applied Sciences 2023, 13, 10977. [Google Scholar] [CrossRef]
- Wang, K.; Zhao, Y.; Gangadhari, R.K.; Li, Z. Analyzing the adoption challenges of the Internet of things (Iot) and artificial intelligence (ai) for smart cities in china. Sustainability 2021, 13, 10983. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things – New security and privacy challenges. Computer Law & Security Review 2010, 26, 23–30. [Google Scholar]
- Wu, H.; Han, H.; Wang, X.; Sun, S. Research on artificial intelligence enhancing internet of things security: A survey. IEEE Access 2020, 8, 153826–153848. [Google Scholar] [CrossRef]
- Xu, L.D.; He, W.; Li, S. Internet of Things in industries: A survey. IEEE Transactions on Industrial Informatics 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Yampolskiy, R.V. AI-complete, AI-hard, or AI-easy? Classification of problems in AI. arXiv arXiv:1308.1458, 2013.
- Yigitcanlar, T.; Desouza, K.C.; Butler, L.; Roozkhosh, F. Contributions and risks of artificial intelligence (AI) in building smarter cities: Insights from a systematic review of the literature. Energies 2020, 13, 1473. [Google Scholar] [CrossRef]
- Zhang, Y.; Deng, R.H.; Liu, X.; Zheng, D.; Mahmood, A. Analysis and outlook: From network security to cybersecurity. Journal of Computer Research and Development 2019, 56, 1–21. [Google Scholar]
- Zhou, Y.; Kankanhalli, A. AI regulation for smart cities: Challenges and principles. Smart Cities and Smart Governance: Towards the 22nd Century Sustainable City 2021, 101–118. [Google Scholar]
- Ziegeldorf, J.H.; Morchon, O.G.; Wehrle, K. Privacy in the Internet of Things: Threats and challenges. Security and Communication Networks 2014, 7, 2728–2742. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).